| File name: | 185.215.113.16 |
| Full analysis: | https://app.any.run/tasks/b8243e43-8c95-4103-a7ef-d5ea6d3daae8 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 08, 2024, 15:08:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E435942CE05BDA77A97578BBCDFB5331 |
| SHA1: | B46E4D6B2B9F19073A886DE3A7712AD994748B48 |
| SHA256: | 9D41F3293F0B458A94D05B512542E701C1CCCF03B5391F927BF3CE9928E33A75 |
| SSDEEP: | 98304:VPAjR30n1atmPg7Uz98FmCsDVpn6iC7jMGUNBBOCZLPsVHJYhKbqE4c+m/EQB/Ay:LD |
MALICIOUS
AMADEY has been detected (SURICATA)
- explorti.exe (PID: 6656)
Connects to the CnC server
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
- 25d81991b1.exe (PID: 7020)
Changes the autorun value in the registry
- explorti.exe (PID: 6656)
Stealers network behavior
- 73f5e8c9a6.exe (PID: 7112)
- 25d81991b1.exe (PID: 7020)
STEALC has been detected (SURICATA)
- 73f5e8c9a6.exe (PID: 7112)
- 25d81991b1.exe (PID: 7020)
AMADEY has been detected (YARA)
- explorti.exe (PID: 6656)
Steals credentials from Web Browsers
- 73f5e8c9a6.exe (PID: 7112)
Actions looks like stealing of personal data
- 73f5e8c9a6.exe (PID: 7112)
SUSPICIOUS
Drops the executable file immediately after the start
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
Reads the BIOS version
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- explorti.exe (PID: 7280)
Reads security settings of Internet Explorer
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 9561f7117d.exe (PID: 6824)
- 73f5e8c9a6.exe (PID: 7112)
- 25d81991b1.exe (PID: 7020)
Executable content was dropped or overwritten
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
Reads the date of Windows installation
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 9561f7117d.exe (PID: 6824)
Starts itself from another location
- 185.215.113.16.exe (PID: 6500)
Contacting a server suspected of hosting an CnC
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
- 25d81991b1.exe (PID: 7020)
Potential Corporate Privacy Violation
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
Connects to the server without a host name
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
Searches for installed software
- 73f5e8c9a6.exe (PID: 7112)
Windows Defender mutex has been found
- 73f5e8c9a6.exe (PID: 7112)
- 25d81991b1.exe (PID: 7020)
Process requests binary or script from the Internet
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
The process drops Mozilla's DLL files
- 73f5e8c9a6.exe (PID: 7112)
The process drops C-runtime libraries
- 73f5e8c9a6.exe (PID: 7112)
Process drops legitimate windows executable
- 73f5e8c9a6.exe (PID: 7112)
There is functionality for VM detection (VirtualBox)
- 9561f7117d.exe (PID: 6824)
The process executes via Task Scheduler
- explorti.exe (PID: 7280)
Executes application which crashes
- 25d81991b1.exe (PID: 7020)
There is functionality for taking screenshot (YARA)
- 9561f7117d.exe (PID: 6824)
INFO
Checks supported languages
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 9561f7117d.exe (PID: 6824)
- 25d81991b1.exe (PID: 7020)
- 73f5e8c9a6.exe (PID: 7112)
- explorti.exe (PID: 7280)
- TextInputHost.exe (PID: 7444)
Reads Environment values
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
Reads the computer name
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 9561f7117d.exe (PID: 6824)
- 25d81991b1.exe (PID: 7020)
- 73f5e8c9a6.exe (PID: 7112)
- TextInputHost.exe (PID: 7444)
Create files in a temporary directory
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
Process checks computer location settings
- 185.215.113.16.exe (PID: 6500)
- explorti.exe (PID: 6656)
- 9561f7117d.exe (PID: 6824)
Checks proxy server information
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
- WerFault.exe (PID: 2212)
- 25d81991b1.exe (PID: 7020)
Creates files or folders in the user directory
- explorti.exe (PID: 6656)
- 73f5e8c9a6.exe (PID: 7112)
- WerFault.exe (PID: 2212)
- 25d81991b1.exe (PID: 7020)
Reads mouse settings
- 9561f7117d.exe (PID: 6824)
Application launched itself
- firefox.exe (PID: 6284)
- firefox.exe (PID: 6300)
Reads CPU info
- 73f5e8c9a6.exe (PID: 7112)
Reads product name
- 73f5e8c9a6.exe (PID: 7112)
Reads Microsoft Office registry keys
- firefox.exe (PID: 6300)
Creates files in the program directory
- 73f5e8c9a6.exe (PID: 7112)
Themida protector has been detected
- explorti.exe (PID: 6656)
Reads the software policy settings
- WerFault.exe (PID: 2212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(6656) explorti.exe
C2185.215.113.19
URLhttp://185.215.113.19/Vi9leo/index.php
Version4.41
Options
Drop directory0d8f5eb8a7
Drop nameexplorti.exe
Strings (119)AVG
\App
0123456789
SOFTWARE\Microsoft\Windows NT\CurrentVersion
os:
r=
zip
cmd /C RMDIR /s/q
Bitdefender
dm:
360TotalSecurity
-executionpolicy remotesigned -File "
.jpg
S-%lu-
POST
ESET
abcdefghijklmnopqrstuvwxyz0123456789-_
&&
2022
shutdown -s -t 0
/Plugins/
Content-Disposition: form-data; name="data"; filename="
un:
--
/quiet
ProductName
Comodo
cmd
Kaspersky Lab
"taskkill /f /im "
+++
|
:::
e1
"
random
GET
bi:
=
wb
"
Content-Type: application/octet-stream
-%lu
2019
kernel32.dll
\0000
pc:
shell32.dll
Startup
ComputerName
av:
ar:
lv:
DefaultSettings.XResolution
0d8f5eb8a7
Avira
&unit=
AVAST Software
%USERPROFILE%
explorti.exe
exe
-unicode-
2016
e0
id:
DefaultSettings.YResolution
vs:
%-lu
/k
Powershell.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
185.215.113.19
#
rundll32.exe
Sophos
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
CurrentBuild
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
<d>
https://
Content-Type: application/x-www-form-urlencoded
/Vi9leo/index.php
VideoID
d1
Main
cred.dll
rb
Doctor Web
4.41
http://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ProgramData\
msi
Norton
&& Exit"
cred.dll|clip.dll|
Panda Security
\
og:
" && ren
GetNativeSystemInfo
rundll32
st=s
e2
<c>
Programs
Content-Type: multipart/form-data; boundary=----
Rem
?scr=1
sd:
------
------
SYSTEM\ControlSet001\Services\BasicDisplay\Video
dll
clip.dll
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
" && timeout 1 && del
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ps1
WinDefender
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:25 12:12:00+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 321024 |
| InitializedDataSize: | 117248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4be000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
152
Monitored processes
22
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2296 -parentBuildID 20240213221259 -prefsHandle 2288 -prefMapHandle 2276 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {abe91b20-7b78-4ad0-b3fc-d449fa9276ca} 6300 "\\.\pipe\gecko-crash-server-pipe.6300" 2247d483110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2212 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7020 -s 1176 | C:\Windows\SysWOW64\WerFault.exe | 25d81991b1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1932 -parentBuildID 20240213221259 -prefsHandle 1860 -prefMapHandle 1840 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {4560a436-da69-44b9-a504-dc5809647fe1} 6300 "\\.\pipe\gecko-crash-server-pipe.6300" 2247fee4e10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5400 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6736 -parentBuildID 20240213221259 -sandboxingKind 1 -prefsHandle 6820 -prefMapHandle 7004 -prefsLen 34763 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7e8bd77a-3626-46fa-9427-78f70feeb149} 6300 "\\.\pipe\gecko-crash-server-pipe.6300" 2240fc1d310 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6152 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4532 -childID 2 -isForBrowser -prefsHandle 4524 -prefMapHandle 4520 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1428 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {3a57eba5-92d9-434c-96fa-b8bfb07f302e} 6300 "\\.\pipe\gecko-crash-server-pipe.6300" 2240fca5690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6184 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=3032 -childID 1 -isForBrowser -prefsHandle 3024 -prefMapHandle 3020 -prefsLen 26706 -prefMapSize 244343 -jsInitHandle 1428 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e4dc6af8-f1a0-40c6-b07c-182808d85116} 6300 "\\.\pipe\gecko-crash-server-pipe.6300" 2240fb67150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
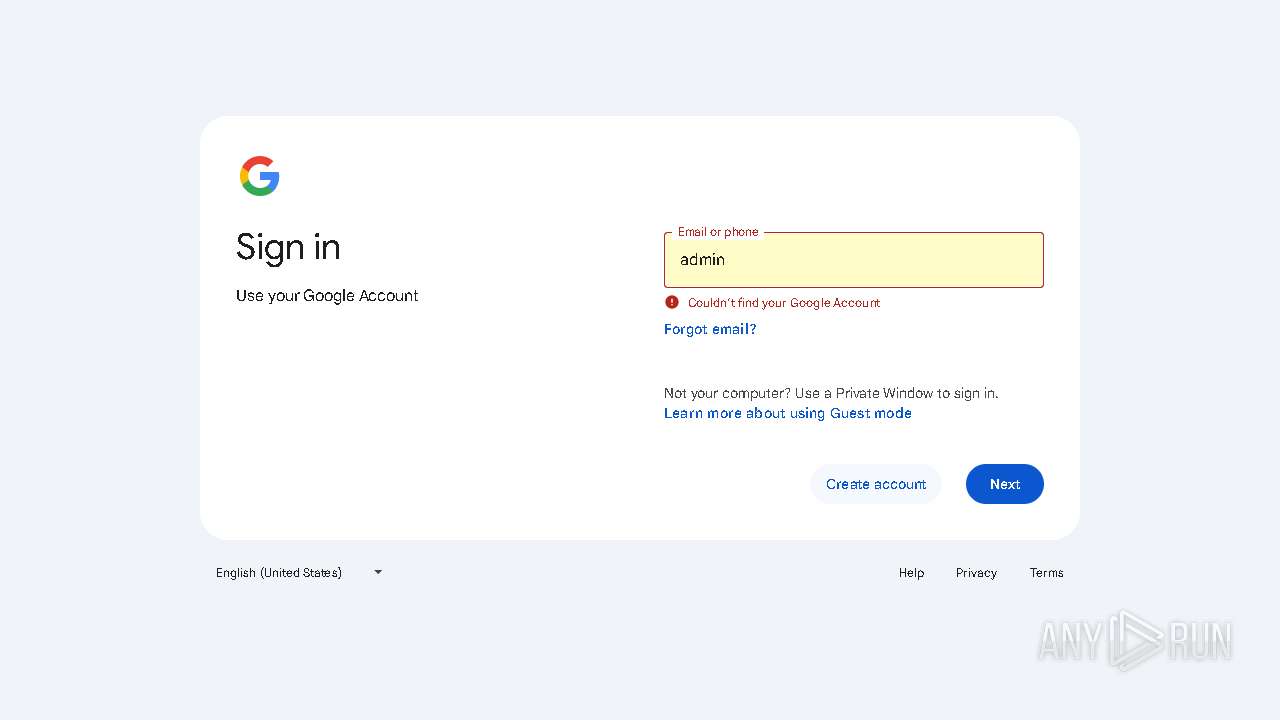
| 6284 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://accounts.google.com/ServiceLogin?service=accountsettings&continue=https://myaccount.google.com/signinoptions/password | C:\Program Files\Mozilla Firefox\firefox.exe | — | 9561f7117d.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6300 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://accounts.google.com/ServiceLogin?service=accountsettings&continue=https://myaccount.google.com/signinoptions/password | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6500 | "C:\Users\admin\AppData\Local\Temp\185.215.113.16.exe" | C:\Users\admin\AppData\Local\Temp\185.215.113.16.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6508 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6040 -childID 4 -isForBrowser -prefsHandle 5952 -prefMapHandle 6020 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1428 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ac85754b-e04e-492d-87a6-8ecc15beacf5} 6300 "\\.\pipe\gecko-crash-server-pipe.6300" 224144b14d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
31 901
Read events
31 805
Write events
95
Delete events
1
Modification events
| (PID) Process: | (6500) 185.215.113.16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6500) 185.215.113.16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6500) 185.215.113.16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6500) 185.215.113.16.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6656) explorti.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6656) explorti.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6656) explorti.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6656) explorti.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6656) explorti.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6656) explorti.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
19
Suspicious files
155
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6500 | 185.215.113.16.exe | C:\Windows\Tasks\explorti.job | binary | |
MD5:E4AE537954102DE143F4FD51E9973282 | SHA256:DCF99843E415FF3F6930B79BE62B3FD8B5BF68D30004305C9F8F5C1E8C02DE34 | |||
| 6500 | 185.215.113.16.exe | C:\Users\admin\AppData\Local\Temp\0d8f5eb8a7\explorti.exe | executable | |
MD5:E435942CE05BDA77A97578BBCDFB5331 | SHA256:9D41F3293F0B458A94D05B512542E701C1CCCF03B5391F927BF3CE9928E33A75 | |||
| 6300 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6656 | explorti.exe | C:\Users\admin\1000037002\25d81991b1.exe | executable | |
MD5:531C8A07AA1653227F3C4439F70A7C41 | SHA256:2B440BF18999EDBE082C4335E580A2EE4E8570025513296C15896BC229B9997B | |||
| 6656 | explorti.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[1].exe | executable | |
MD5:278EE1426274818874556AA18FD02E3A | SHA256:37257DDB1A6F309A6E9D147B5FC2551A9CAE3A0E52B191B18D9465BFCB5C18EB | |||
| 6656 | explorti.exe | C:\Users\admin\AppData\Local\Temp\1000038001\73f5e8c9a6.exe | executable | |
MD5:278EE1426274818874556AA18FD02E3A | SHA256:37257DDB1A6F309A6E9D147B5FC2551A9CAE3A0E52B191B18D9465BFCB5C18EB | |||
| 6300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6656 | explorti.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\random[1].exe | executable | |
MD5:755D382337411BA1DA5756194148A523 | SHA256:4FA3C1E2131B8733A0280DD9609D09F61D1443FB30FEACAD85B65DCF833B9618 | |||
| 6656 | explorti.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\random[1].exe | executable | |
MD5:531C8A07AA1653227F3C4439F70A7C41 | SHA256:2B440BF18999EDBE082C4335E580A2EE4E8570025513296C15896BC229B9997B | |||
| 6300 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
99
DNS requests
120
Threats
42
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6656 | explorti.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/Vi9leo/index.php | unknown | — | — | unknown |
6300 | firefox.exe | POST | 200 | 95.101.54.128:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6656 | explorti.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/Vi9leo/index.php | unknown | — | — | unknown |
6656 | explorti.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/well/random.exe | unknown | — | — | malicious |
6656 | explorti.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/Vi9leo/index.php | unknown | — | — | unknown |
6656 | explorti.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/steam/random.exe | unknown | — | — | unknown |
6656 | explorti.exe | POST | 200 | 185.215.113.19:80 | http://185.215.113.19/Vi9leo/index.php | unknown | — | — | unknown |
7112 | 73f5e8c9a6.exe | GET | 200 | 185.215.113.100:80 | http://185.215.113.100/ | unknown | — | — | unknown |
6656 | explorti.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/num/random.exe | unknown | — | — | unknown |
7112 | 73f5e8c9a6.exe | POST | 200 | 185.215.113.100:80 | http://185.215.113.100/e2b1563c6670f193.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1748 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2536 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6656 | explorti.exe | 185.215.113.19:80 | — | 1337team Limited | SC | malicious |
6656 | explorti.exe | 185.215.113.16:80 | — | 1337team Limited | SC | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2536 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7112 | 73f5e8c9a6.exe | 185.215.113.100:80 | — | 1337team Limited | SC | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
accounts.google.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6656 | explorti.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
6656 | explorti.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6656 | explorti.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6656 | explorti.exe | Misc activity | ET INFO Packed Executable Download |
6656 | explorti.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
6656 | explorti.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6656 | explorti.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6656 | explorti.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6656 | explorti.exe | Misc activity | ET INFO Packed Executable Download |
6656 | explorti.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
185.215.113.16.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
explorti.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
explorti.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|