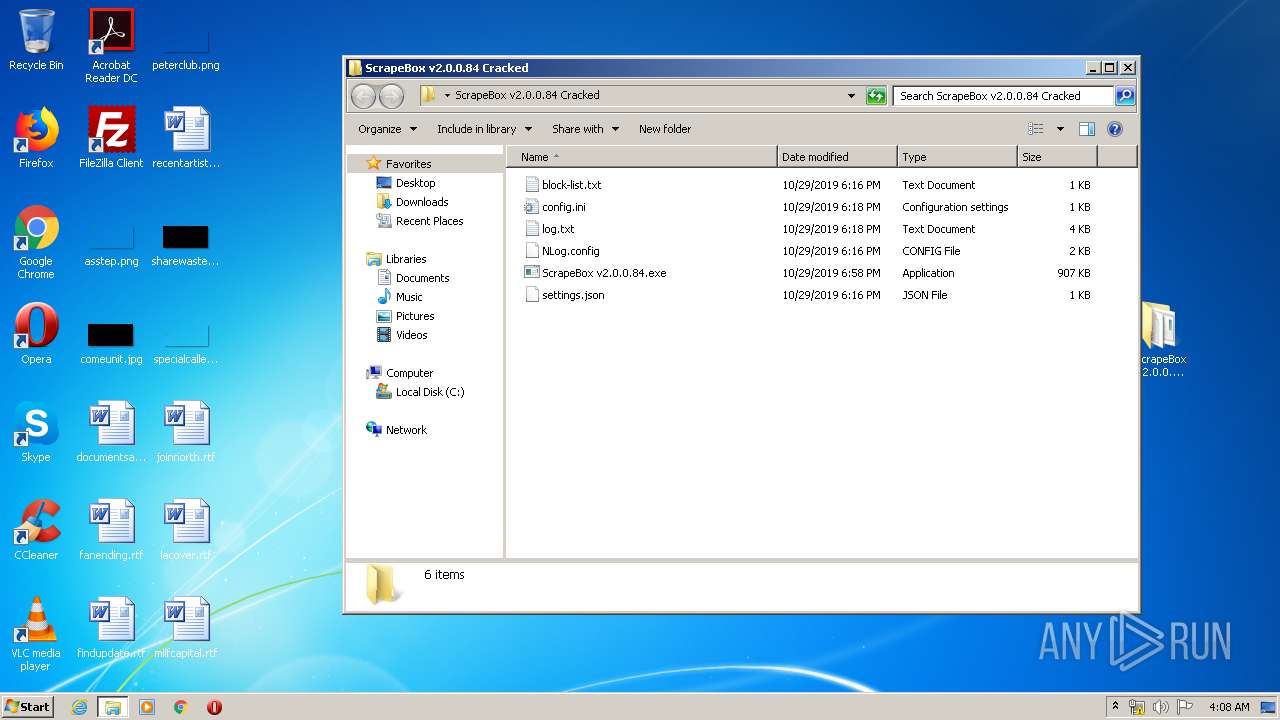
| File name: | ScrapeBox v2.0.0.84 Cracked.rar |
| Full analysis: | https://app.any.run/tasks/f890307e-f2c1-48c1-91f9-87afc05c2e1a |
| Verdict: | Malicious activity |
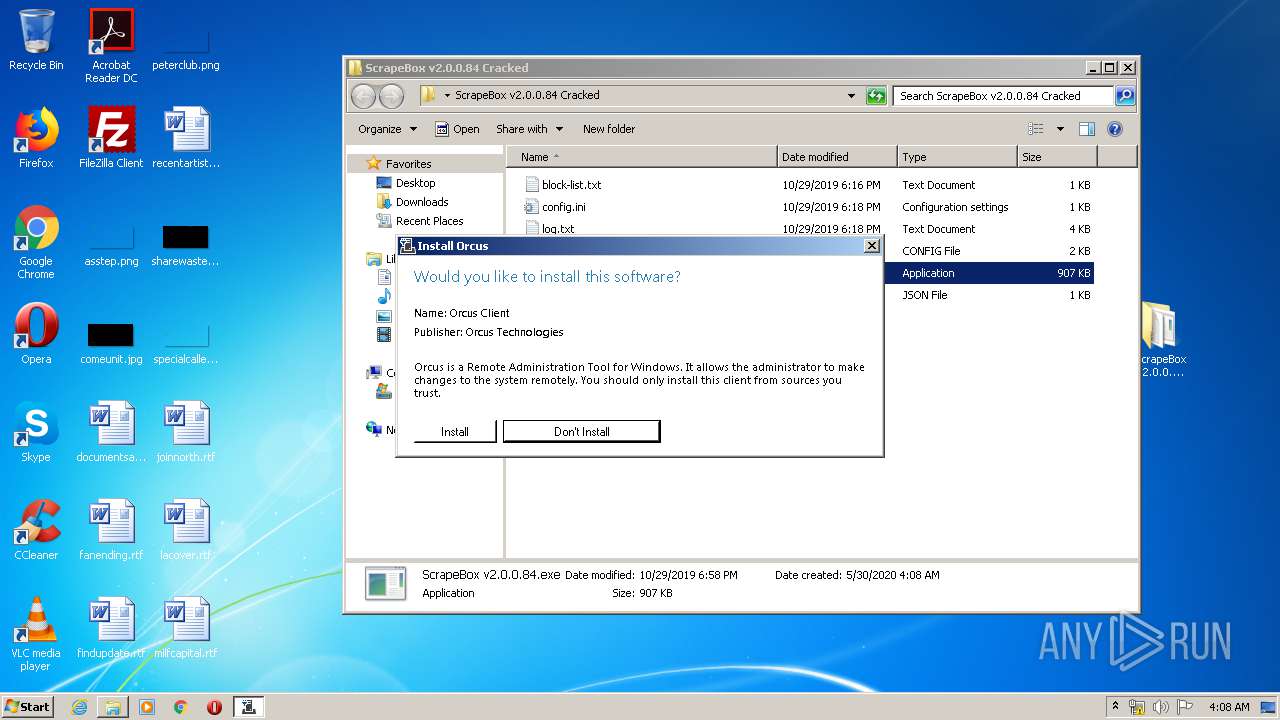
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | May 30, 2020, 03:07:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 05D40D1DBB5BEEBEB27883EFDE5A88D4 |
| SHA1: | F163921FD0E5064F01E1822C0EA3AEB0C2463610 |
| SHA256: | 9D2400E7A1F7C452916960EC8B04E1C8C7EAEFAA7B3B046113F234153AF35A62 |
| SSDEEP: | 12288:FKoyiyHSDe28q5jUp+TRCoP3dRpulSYkbWmvJjY3m+4Pv7kDwkUYj:YG8SDmsUpCxE0YkJ+mz4uYj |
MALICIOUS
ORCUS was detected
- ScrapeBox v2.0.0.84.exe (PID: 576)
- ScrapeBox v2.0.0.84.exe (PID: 3584)
- Orcus.exe (PID: 3836)
Starts Visual C# compiler
- ScrapeBox v2.0.0.84.exe (PID: 576)
- ScrapeBox v2.0.0.84.exe (PID: 3584)
Application was dropped or rewritten from another process
- ScrapeBox v2.0.0.84.exe (PID: 3584)
- ScrapeBox v2.0.0.84.exe (PID: 576)
- Orcus.exe (PID: 3836)
SUSPICIOUS
Application launched itself
- ScrapeBox v2.0.0.84.exe (PID: 576)
Creates files in the user directory
- ScrapeBox v2.0.0.84.exe (PID: 576)
Creates files in the program directory
- ScrapeBox v2.0.0.84.exe (PID: 3584)
Executable content was dropped or overwritten
- ScrapeBox v2.0.0.84.exe (PID: 3584)
Starts itself from another location
- ScrapeBox v2.0.0.84.exe (PID: 3584)
INFO
Manual execution by user
- ScrapeBox v2.0.0.84.exe (PID: 576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
49
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 576 | "C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe" | C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2168 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES16C2.tmp" "c:\Users\admin\AppData\Local\Temp\CSC16C1.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
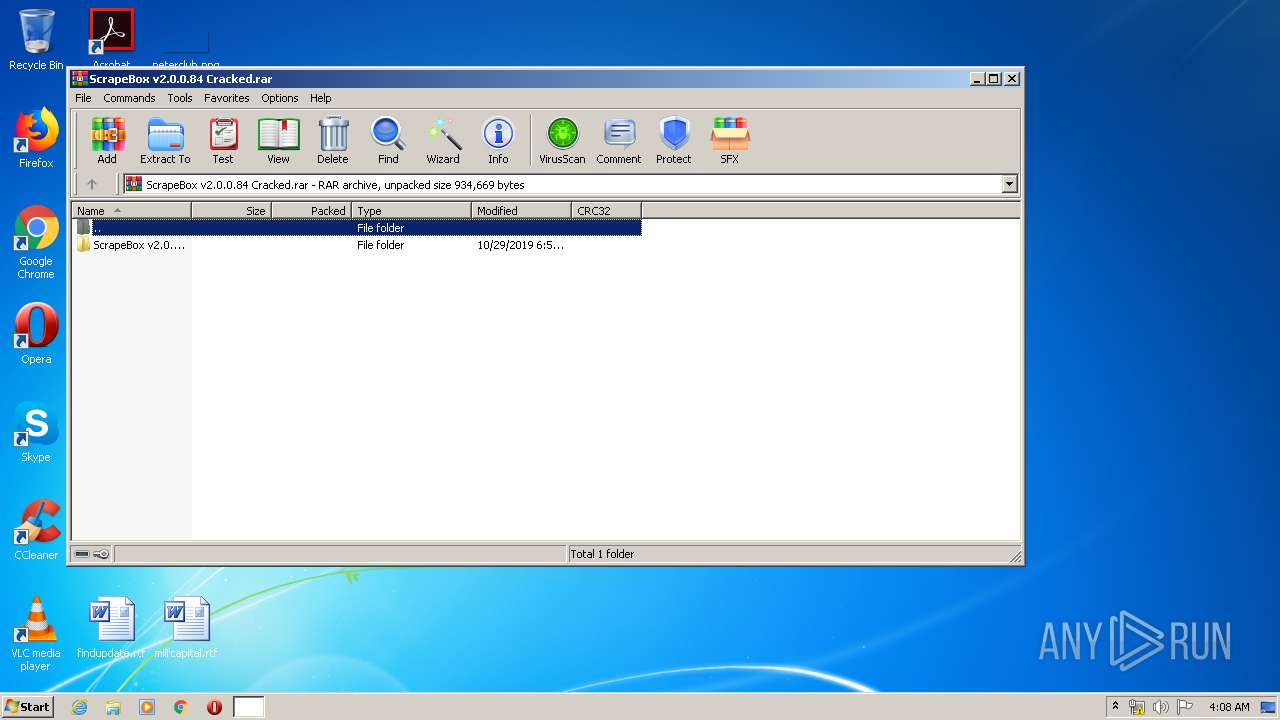
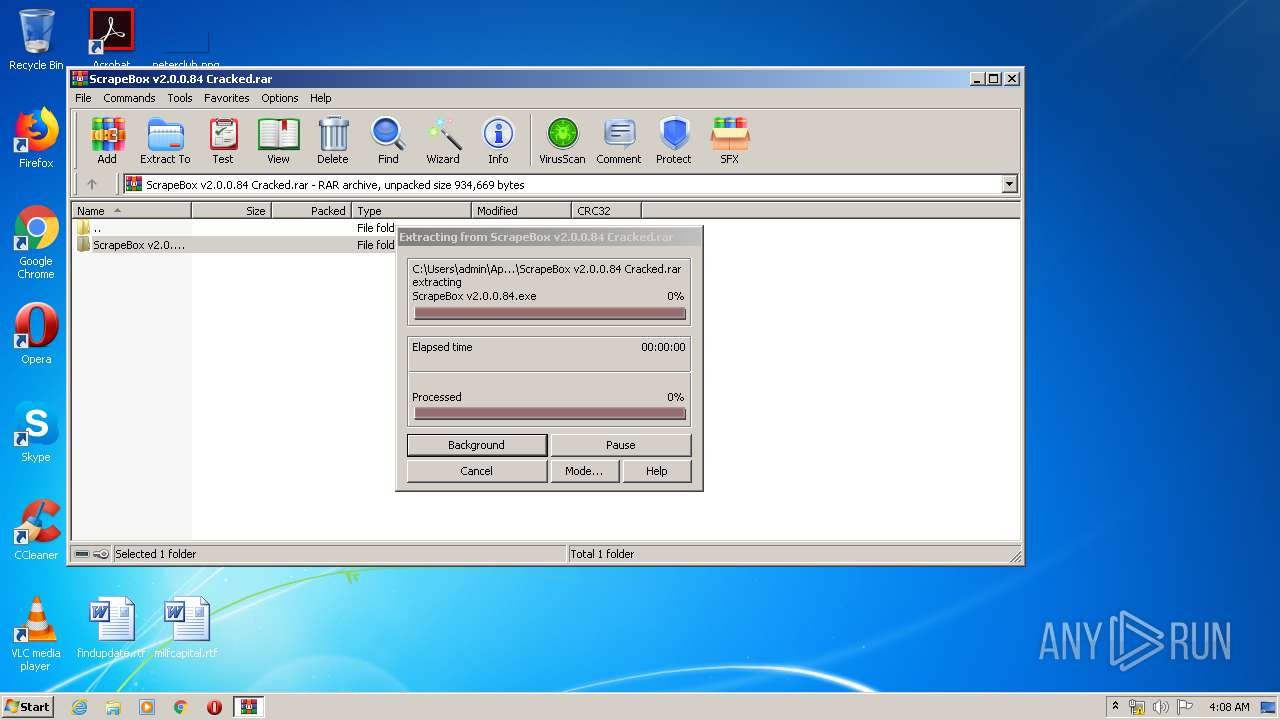
| 2384 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ScrapeBox v2.0.0.84 Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2444 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESDD72.tmp" "c:\Users\admin\AppData\Local\Temp\CSCDD71.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2816 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\ukuawecv.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | ScrapeBox v2.0.0.84.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 2916 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\-a_jqqr-.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | ScrapeBox v2.0.0.84.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe" /wait | C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe | ScrapeBox v2.0.0.84.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3836 | "C:\Program Files\Orcus\Orcus.exe" | C:\Program Files\Orcus\Orcus.exe | ScrapeBox v2.0.0.84.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
527
Read events
499
Write events
28
Delete events
0
Modification events
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ScrapeBox v2.0.0.84 Cracked.rar | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
1
Suspicious files
0
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2384.42922\ScrapeBox v2.0.0.84 Cracked\block-list.txt | — | |
MD5:— | SHA256:— | |||
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2384.42922\ScrapeBox v2.0.0.84 Cracked\config.ini | — | |
MD5:— | SHA256:— | |||
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2384.42922\ScrapeBox v2.0.0.84 Cracked\log.txt | — | |
MD5:— | SHA256:— | |||
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2384.42922\ScrapeBox v2.0.0.84 Cracked\NLog.config | — | |
MD5:— | SHA256:— | |||
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2384.42922\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe | — | |
MD5:— | SHA256:— | |||
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2384.42922\ScrapeBox v2.0.0.84 Cracked\settings.json | — | |
MD5:— | SHA256:— | |||
| 2444 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESDD72.tmp | — | |
MD5:— | SHA256:— | |||
| 2916 | csc.exe | C:\Users\admin\AppData\Local\Temp\-a_jqqr-.dll | — | |
MD5:— | SHA256:— | |||
| 2916 | csc.exe | C:\Users\admin\AppData\Local\Temp\-a_jqqr-.out | — | |
MD5:— | SHA256:— | |||
| 3584 | ScrapeBox v2.0.0.84.exe | C:\Users\admin\AppData\Local\Temp\ukuawecv.0.cs | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report