| File name: | ScrapeBox v2.0.0.84 Cracked.rar |
| Full analysis: | https://app.any.run/tasks/2f8edfa6-c2a2-49d9-b72b-5b2ec66fa727 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | July 08, 2024, 06:31:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 05D40D1DBB5BEEBEB27883EFDE5A88D4 |
| SHA1: | F163921FD0E5064F01E1822C0EA3AEB0C2463610 |
| SHA256: | 9D2400E7A1F7C452916960EC8B04E1C8C7EAEFAA7B3B046113F234153AF35A62 |
| SSDEEP: | 12288:FKoyiyHSDe28q5jUp+TRCoP3dRpulSYkbWmvJjY3m+4Pv7kDwkUYj:YG8SDmsUpCxE0YkJ+mz4uYj |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3424)
- csc.exe (PID: 2944)
- csc.exe (PID: 3584)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
Starts Visual C# compiler
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
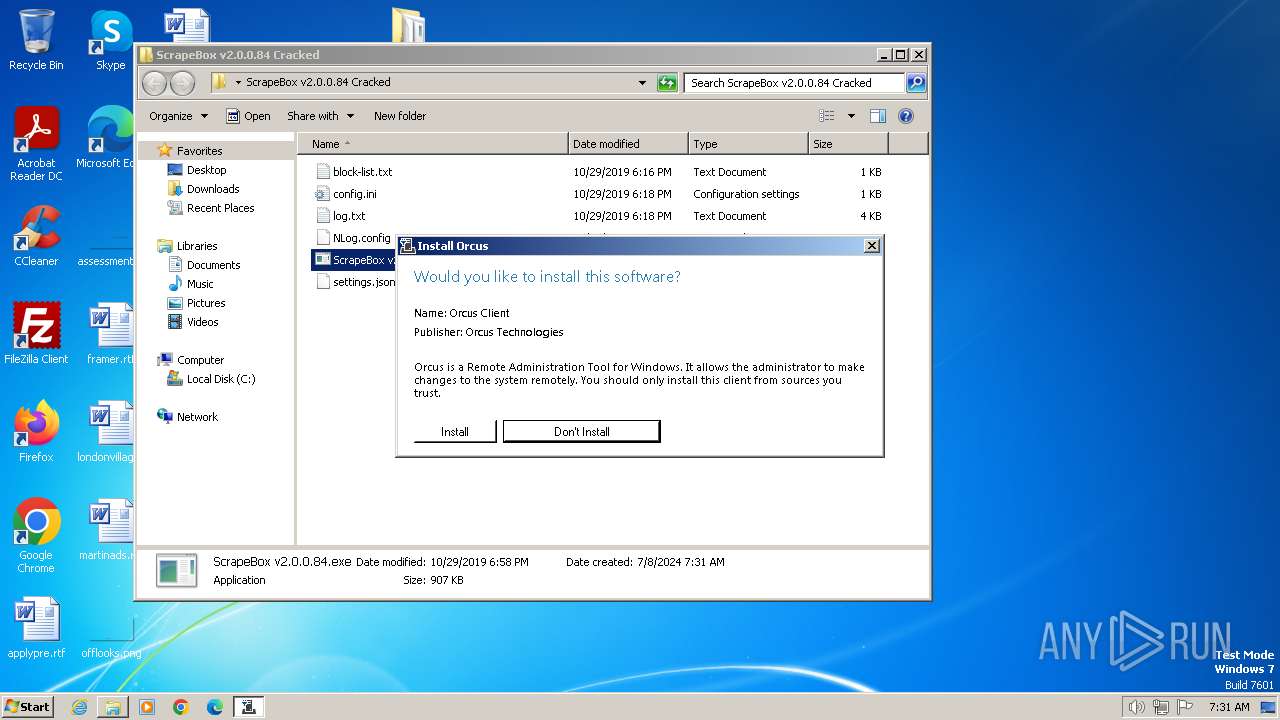
Orcus is detected
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
- Orcus.exe (PID: 3852)
ORCUS has been detected (YARA)
- Orcus.exe (PID: 3852)
SUSPICIOUS
Uses .NET C# to load dll
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
Executable content was dropped or overwritten
- csc.exe (PID: 2944)
- csc.exe (PID: 3584)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
Reads the Internet Settings
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
Reads security settings of Internet Explorer
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
Application launched itself
- ScrapeBox v2.0.0.84.exe (PID: 2300)
There is functionality for taking screenshot (YARA)
- Orcus.exe (PID: 3852)
Starts itself from another location
- ScrapeBox v2.0.0.84.exe (PID: 2420)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3424)
Reads the machine GUID from the registry
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- csc.exe (PID: 2944)
- cvtres.exe (PID: 2348)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
- csc.exe (PID: 3584)
- cvtres.exe (PID: 3364)
- Orcus.exe (PID: 3852)
Checks supported languages
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- csc.exe (PID: 2944)
- cvtres.exe (PID: 2348)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
- csc.exe (PID: 3584)
- cvtres.exe (PID: 3364)
- Orcus.exe (PID: 3852)
Create files in a temporary directory
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- csc.exe (PID: 2944)
- cvtres.exe (PID: 2348)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
- csc.exe (PID: 3584)
- cvtres.exe (PID: 3364)
Manual execution by a user
- ScrapeBox v2.0.0.84.exe (PID: 2300)
Reads the computer name
- ScrapeBox v2.0.0.84.exe (PID: 2300)
- ScrapeBox v2.0.0.84.exe (PID: 2420)
- Orcus.exe (PID: 3852)
Creates files or folders in the user directory
- ScrapeBox v2.0.0.84.exe (PID: 2300)
Creates files in the program directory
- ScrapeBox v2.0.0.84.exe (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Orcus
(PID) Process(3852) Orcus.exe
C2 (1)127.0.0.1:10134
Keys
AESc1409156d5263156a70da33a5edeed842c6211ec73e78d061a42b8b79d3c889b
Salt
Options
AutostartBuilderProperty
AutostartMethodDisable
TaskSchedulerTaskNameOrcus
TaskHighestPrivilegestrue
RegistryHiddenStarttrue
RegistryKeyNameOrcus
TryAllAutostartMethodsOnFailtrue
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationfalse
AssemblyTitlenull
AssemblyDescriptionnull
AssemblyCompanyNamenull
AssemblyProductNamenull
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2019-10-29T20:58:14.2812428+02:00
ChangeIconBuilderProperty
ChangeIconfalse
IconPathnull
ClientTagBuilderProperty
ClientTagnull
DataFolderBuilderProperty
Path%appdata%\Orcus
DefaultPrivilegesBuilderProperty
RequireAdministratorRightsfalse
DisableInstallationPromptBuilderProperty
IsDisabledfalse
FrameworkVersionBuilderProperty
FrameworkVersionNET35
HideFileBuilderProperty
HideFilefalse
InstallationLocationBuilderProperty
Path%programfiles%\Orcus\Orcus.exe
InstallBuilderProperty
Installtrue
KeyloggerBuilderProperty
IsEnabledfalse
MutexBuilderProperty
Mutex3869f62ea43243589f85c060feacc528
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegestrue
RespawnTaskBuilderProperty
IsEnabledfalse
TaskNameOrcus Respawner
ServiceBuilderProperty
Installfalse
SetRunProgramAsAdminFlagBuilderProperty
SetFlagfalse
WatchdogBuilderProperty
IsEnabledfalse
NameOrcusWatchdog.exe
WatchdogLocationAppData
PreventFileDeletionfalse
Plugins
PluginNameDisable Webcam Lights
PluginVersion1.0
ResourceNamee2c012dfd9a34995b5ce0be5a0f97525
ResourceTypeClientPlugin
Guide6ee5674-bb94-46c7-8bbc-5729af6e2c28
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
51
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2300 | "C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe" | C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2348 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES113E.tmp" "c:\Users\admin\AppData\Local\Temp\CSC113D.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe" /wait | C:\Users\admin\Desktop\ScrapeBox v2.0.0.84 Cracked\ScrapeBox v2.0.0.84.exe | ScrapeBox v2.0.0.84.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2944 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\hlapvw-6.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | ScrapeBox v2.0.0.84.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3364 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES242A.tmp" "c:\Users\admin\AppData\Local\Temp\CSC2429.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.5003 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3424 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ScrapeBox v2.0.0.84 Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3584 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\gl0-jubm.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | ScrapeBox v2.0.0.84.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 3852 | "C:\Program Files\Orcus\Orcus.exe" | C:\Program Files\Orcus\Orcus.exe | ScrapeBox v2.0.0.84.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
Orcus(PID) Process(3852) Orcus.exe C2 (1)127.0.0.1:10134 Keys AESc1409156d5263156a70da33a5edeed842c6211ec73e78d061a42b8b79d3c889b Salt Options AutostartBuilderProperty AutostartMethodDisable TaskSchedulerTaskNameOrcus TaskHighestPrivilegestrue RegistryHiddenStarttrue RegistryKeyNameOrcus TryAllAutostartMethodsOnFailtrue ChangeAssemblyInformationBuilderProperty ChangeAssemblyInformationfalse AssemblyTitlenull AssemblyDescriptionnull AssemblyCompanyNamenull AssemblyProductNamenull AssemblyCopyrightnull AssemblyTrademarksnull AssemblyProductVersion1.0.0.0 AssemblyFileVersion1.0.0.0 ChangeCreationDateBuilderProperty IsEnabledfalse NewCreationDate2019-10-29T20:58:14.2812428+02:00 ChangeIconBuilderProperty ChangeIconfalse IconPathnull ClientTagBuilderProperty ClientTagnull DataFolderBuilderProperty Path%appdata%\Orcus DefaultPrivilegesBuilderProperty RequireAdministratorRightsfalse DisableInstallationPromptBuilderProperty IsDisabledfalse FrameworkVersionBuilderProperty FrameworkVersionNET35 HideFileBuilderProperty HideFilefalse InstallationLocationBuilderProperty Path%programfiles%\Orcus\Orcus.exe InstallBuilderProperty Installtrue KeyloggerBuilderProperty IsEnabledfalse MutexBuilderProperty Mutex3869f62ea43243589f85c060feacc528 ProxyBuilderProperty ProxyOptionNone ProxyAddressnull ProxyPort1080 ProxyType2 ReconnectDelayProperty Delay10000 RequireAdministratorPrivilegesInstallerBuilderProperty RequireAdministratorPrivilegestrue RespawnTaskBuilderProperty IsEnabledfalse TaskNameOrcus Respawner ServiceBuilderProperty Installfalse SetRunProgramAsAdminFlagBuilderProperty SetFlagfalse WatchdogBuilderProperty IsEnabledfalse NameOrcusWatchdog.exe WatchdogLocationAppData PreventFileDeletionfalse Plugins PluginNameDisable Webcam Lights PluginVersion1.0 ResourceNamee2c012dfd9a34995b5ce0be5a0f97525 ResourceTypeClientPlugin Guide6ee5674-bb94-46c7-8bbc-5729af6e2c28 | |||||||||||||||
Total events
5 119
Read events
5 081
Write events
38
Delete events
0
Modification events
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ScrapeBox v2.0.0.84 Cracked.rar | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
5
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3424.11946\ScrapeBox v2.0.0.84 Cracked\block-list.txt | text | |
MD5:DC7AB9888897071C7FAC87BB3438E28B | SHA256:68816E76B153C5FD1D9FC06D6DB72772FBD13232E1481BCF74493474B6E000F7 | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3424.11946\ScrapeBox v2.0.0.84 Cracked\config.ini | ini | |
MD5:2152388780302946DAB15337ECFEAE05 | SHA256:D3527EBFB29B1AB7B02A50F47CEA3892527312FAEFDBCB8422A56F9DD97E03EE | |||
| 2944 | csc.exe | C:\Users\admin\AppData\Local\Temp\hlapvw-6.out | text | |
MD5:595081BCF63FB22BE0608B6504F3C31E | SHA256:A9DDDD5679DEAFCEB4CF21EEED45A659B37071760CD80934485397FC799EBF2F | |||
| 2300 | ScrapeBox v2.0.0.84.exe | C:\Users\admin\AppData\Roaming\.orcusInstallation | text | |
MD5:1C6E489EFA1DB2DC4D12F858199E0530 | SHA256:298CD773955F4F30FAE990C5CB0B4231E4922506D4CCFBDD227757F250CACBF9 | |||
| 2300 | ScrapeBox v2.0.0.84.exe | C:\Users\admin\AppData\Local\Temp\hlapvw-6.cmdline | text | |
MD5:3C051EA0B56E96949F954533ADE72EF1 | SHA256:63C2F53F9BA7141D1E1E64510B50B617B488A50FBC1B8BEE352892648B94A73A | |||
| 3584 | csc.exe | C:\Users\admin\AppData\Local\Temp\gl0-jubm.dll | executable | |
MD5:2CBFAA3342B428354AE69AF3F453FE93 | SHA256:59609C971799B45CA60B7F61C9D4B64802AD10ED605C6109868054251190EBFD | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3424.11946\ScrapeBox v2.0.0.84 Cracked\log.txt | text | |
MD5:E9795E29304468A5B9C9FC8517331268 | SHA256:9DBB5B0F72A3005355B31E4E14B031040EC9D7E4C710D9737B7C3BF5413ED920 | |||
| 2348 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES113E.tmp | binary | |
MD5:9EB80DE3743615160832FA1195979FC4 | SHA256:1B736E25A35AA885476AB63FA34907241DD69267AD5B02AC8C261DDC3801F4F7 | |||
| 2944 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC113D.tmp | res | |
MD5:55E3C2338D2B45C4B1A5D62CD779A6B3 | SHA256:FC9B1FD0CE73BA4AF3757EE9FCBEFB2B83468BDA77846209EAE0304882CED269 | |||
| 2944 | csc.exe | C:\Users\admin\AppData\Local\Temp\hlapvw-6.dll | executable | |
MD5:21FBB91BE644635E868BD95D2290B7A2 | SHA256:361D0BA0F5781CEEDECE9AFF1BBE20567416C9F99678CCE8BD73BA37F12A2CD2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 217.20.58.101:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 217.20.58.101:80 | ctldl.windowsupdate.com | — | US | unknown |
1372 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |