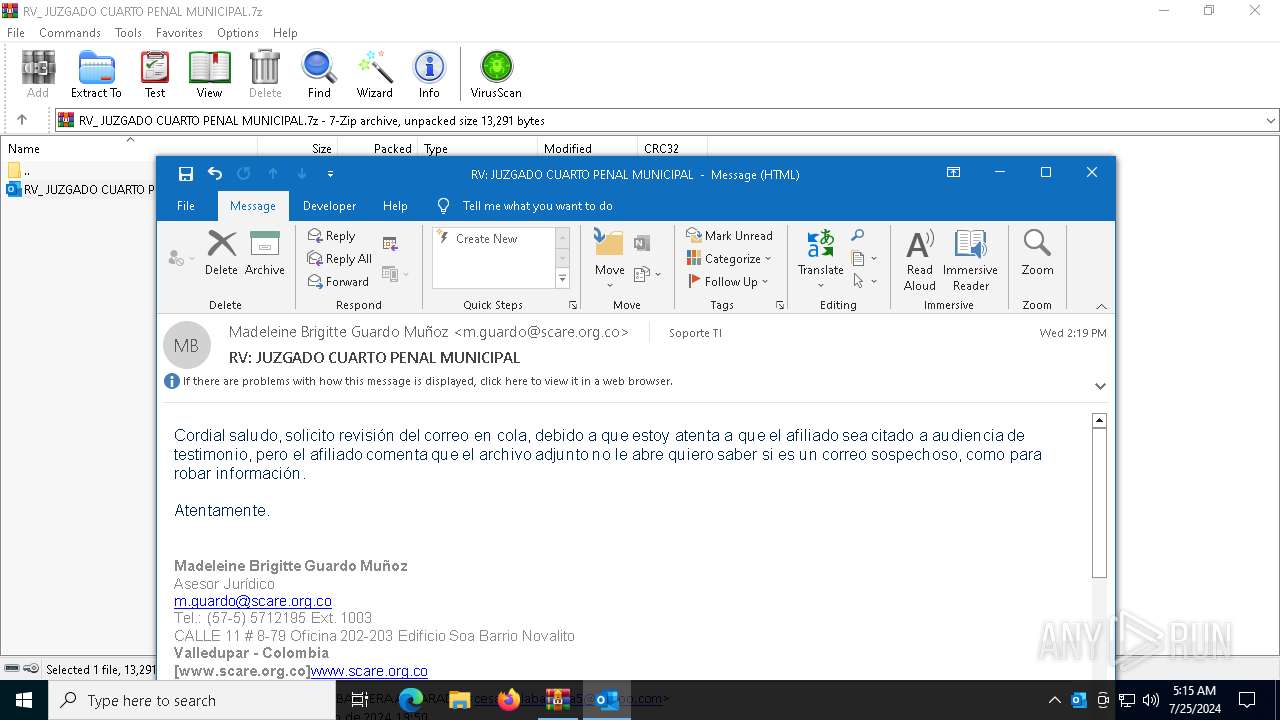
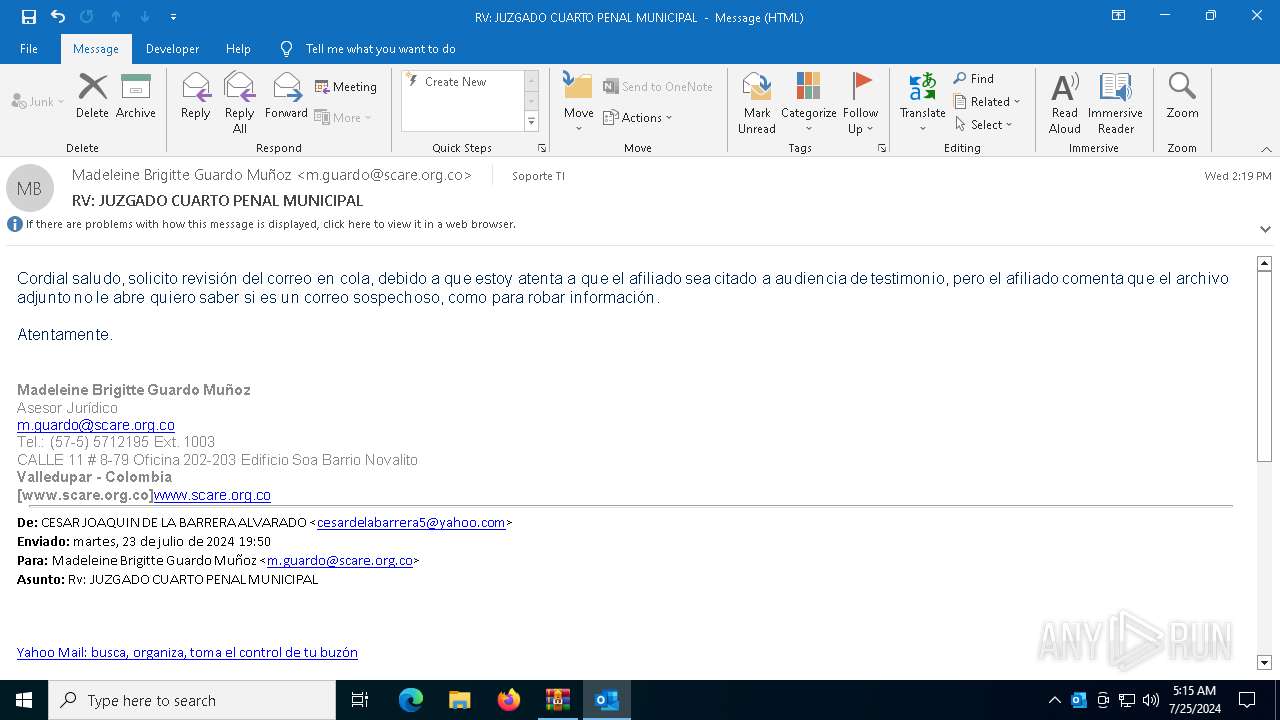
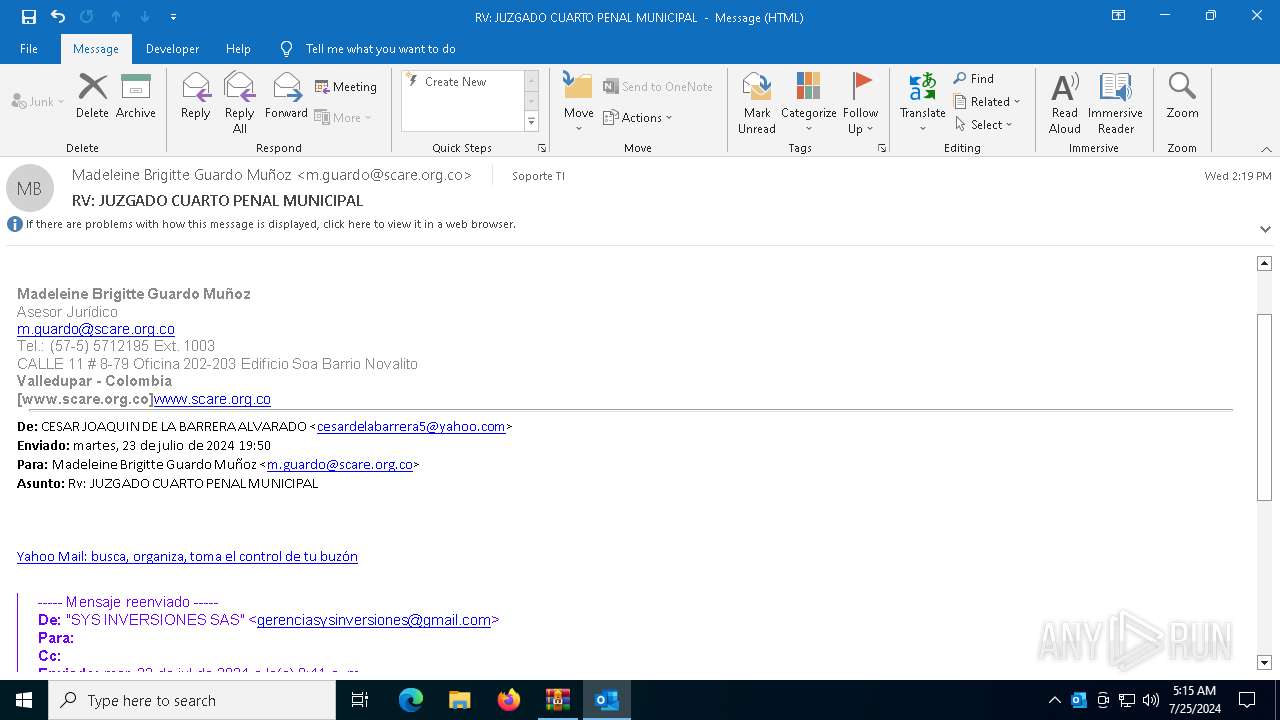
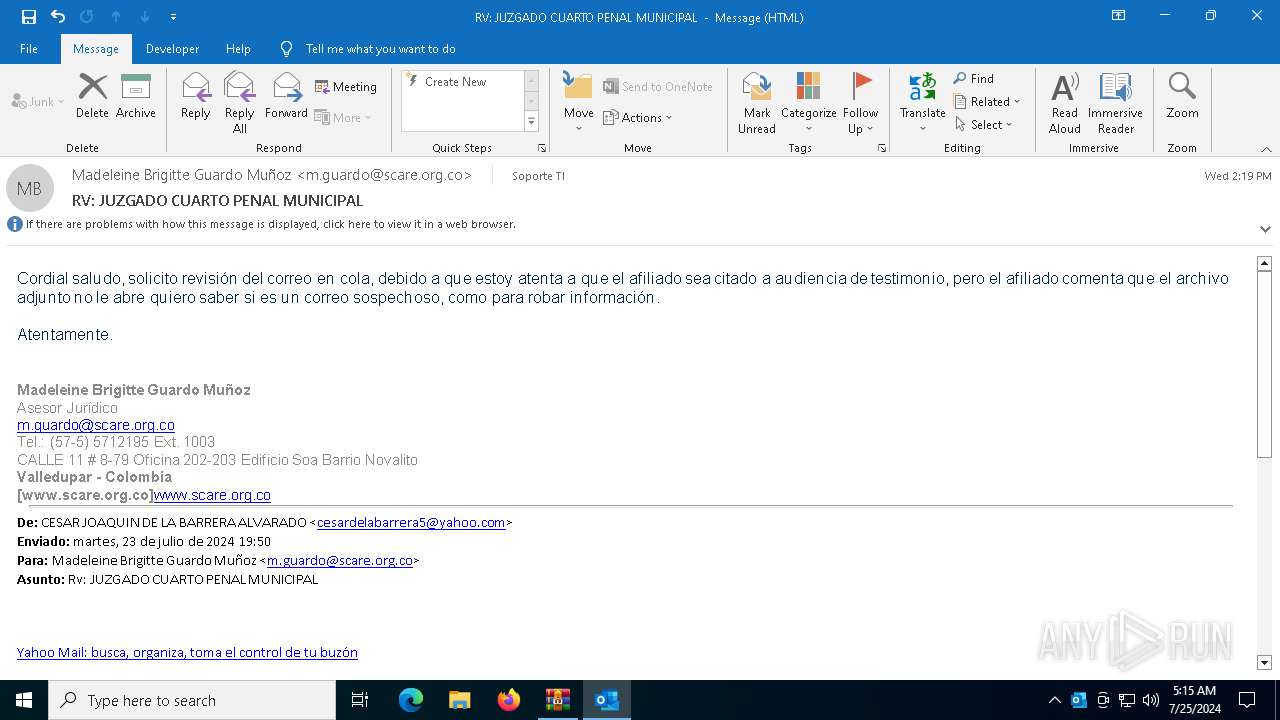
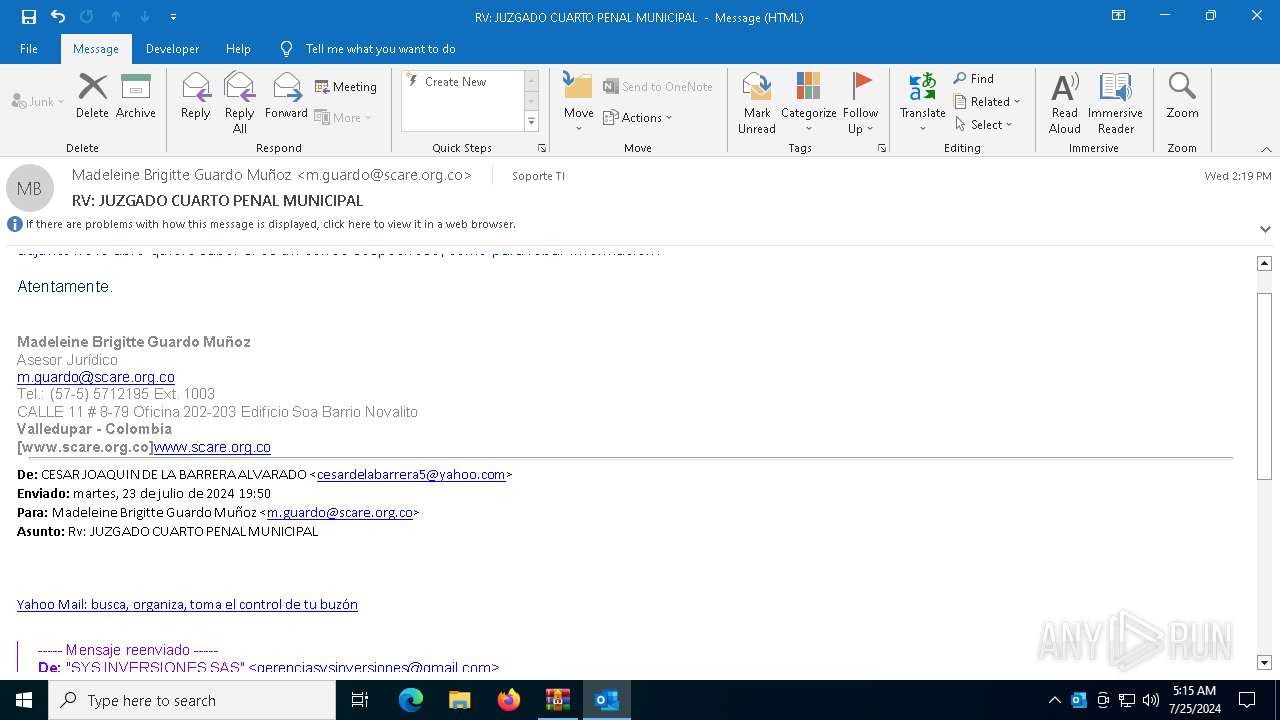
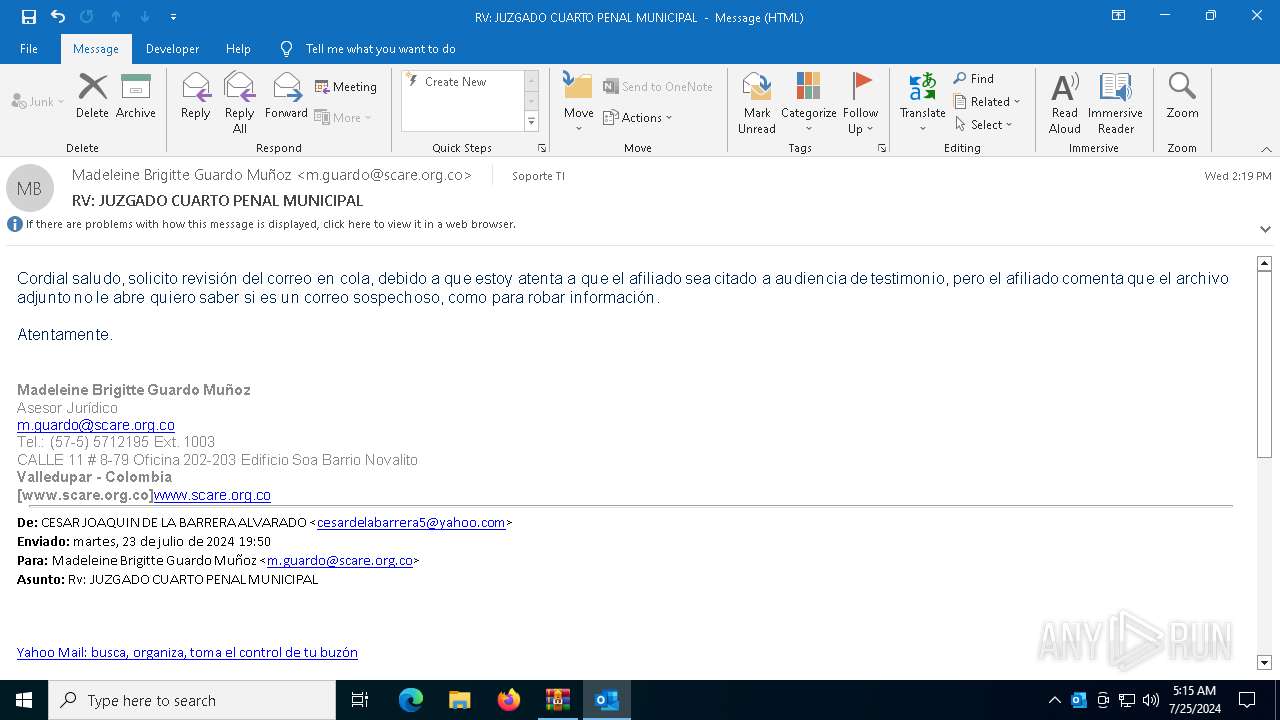
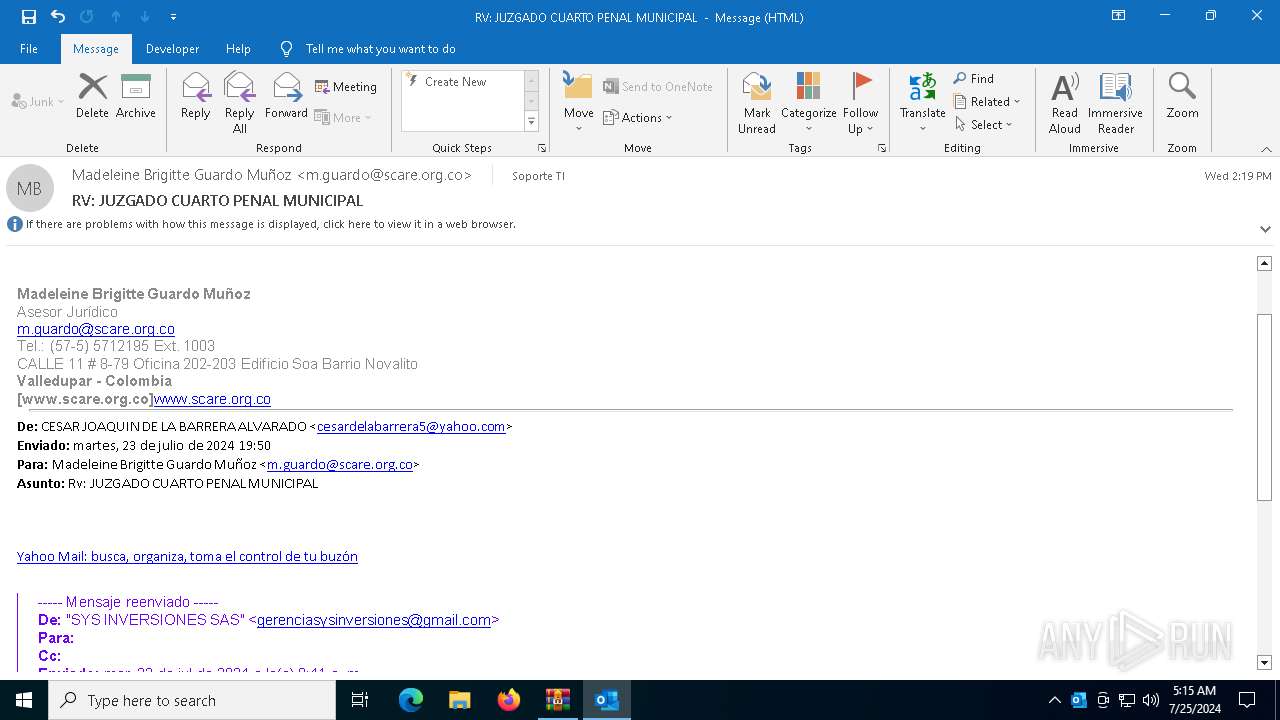
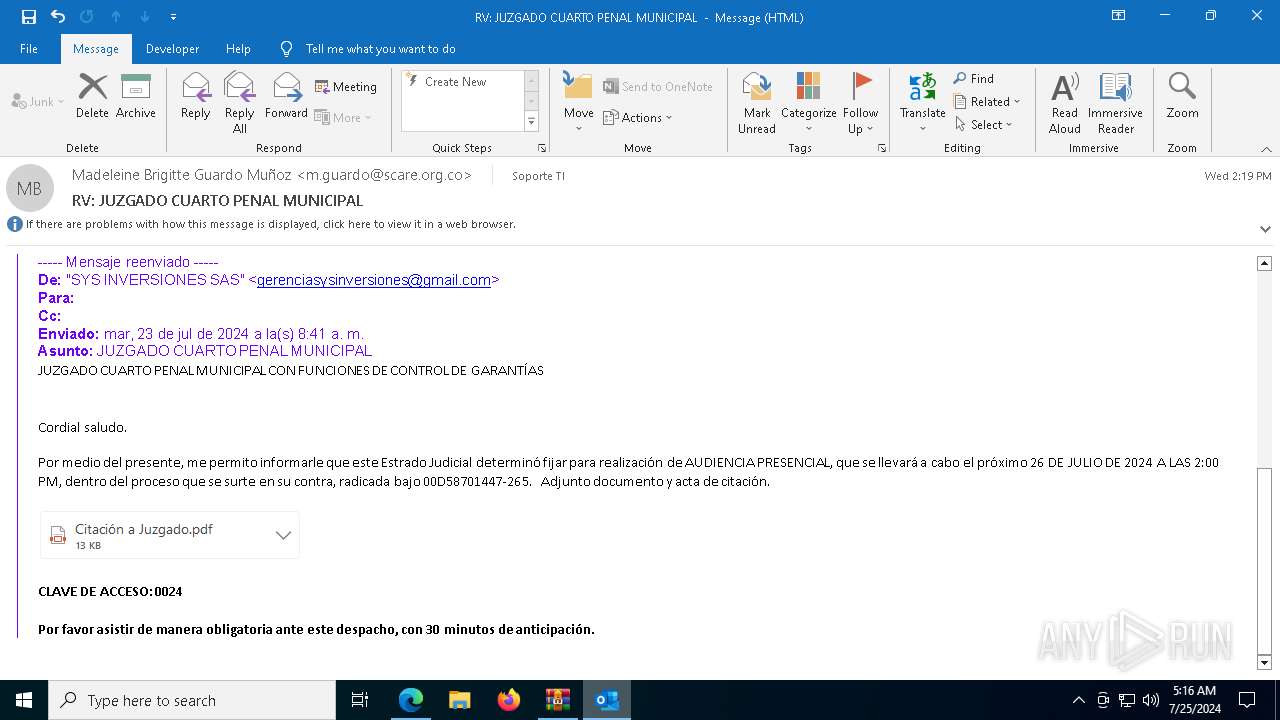
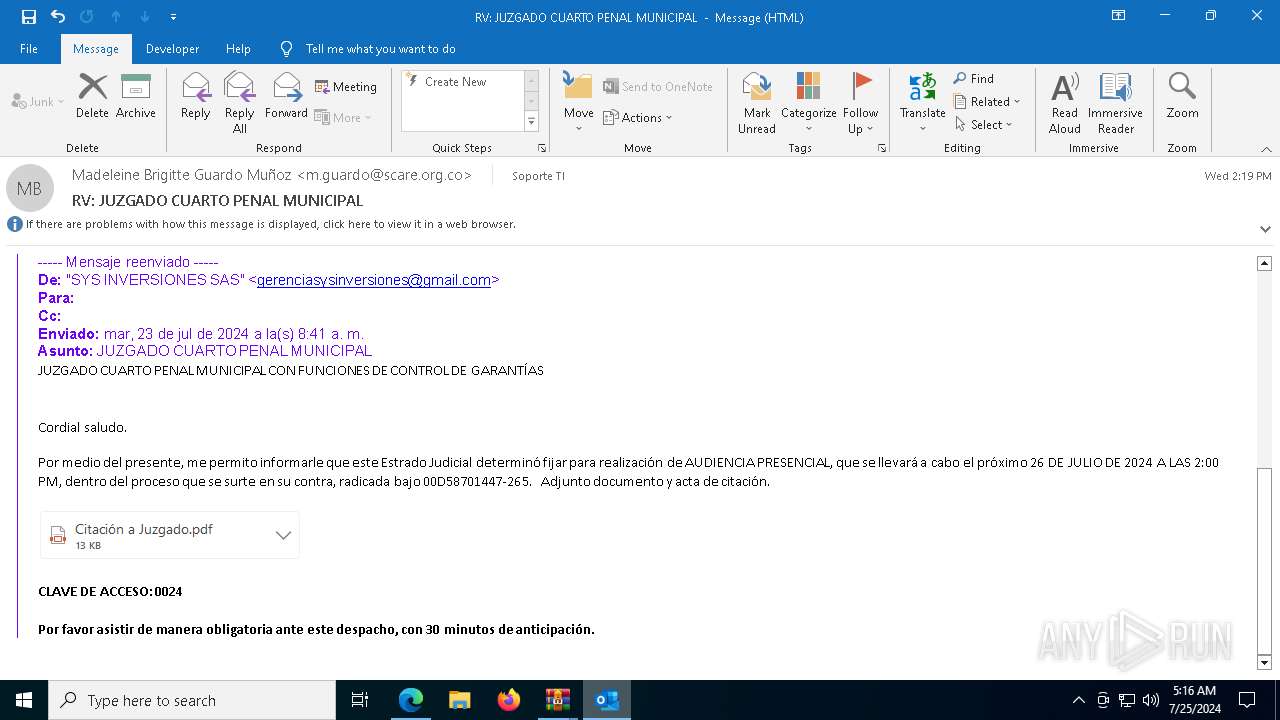
| File name: | RV_ JUZGADO CUARTO PENAL MUNICIPAL.7z |
| Full analysis: | https://app.any.run/tasks/4b7f30dc-81ba-48ba-ac0e-0fb307850767 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 25, 2024, 05:13:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A962186B3FC292873A6D69C3A1BEC624 |
| SHA1: | 5C8CB76633C22CE6071AA878A8031E3DB0949D05 |
| SHA256: | 9D19E2FDF596107CDC295A9163A72B6D8ADBC56D271D0E0E2BDA96951070CFDE |
| SSDEEP: | 192:I7nI1Rz0iIFZMpVFNM9JjQp4v/aWh74l2+aazTF:IeAWVFKTQOnaIuTF |
MALICIOUS
ASYNCRAT has been detected (SURICATA)
- RegAsm.exe (PID: 528)
ASYNCRAT has been detected (YARA)
- RegAsm.exe (PID: 528)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6220)
- WinRAR.exe (PID: 5236)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 6220)
Connects to unusual port
- RegAsm.exe (PID: 528)
Contacting a server suspected of hosting an CnC
- RegAsm.exe (PID: 528)
INFO
Reads the software policy settings
- slui.exe (PID: 5200)
- RegAsm.exe (PID: 528)
Checks proxy server information
- slui.exe (PID: 5200)
Reads the computer name
- TextInputHost.exe (PID: 1272)
- identity_helper.exe (PID: 6788)
- RegAsm.exe (PID: 528)
- RegAsm.exe (PID: 2172)
Reads Environment values
- identity_helper.exe (PID: 6788)
- RegAsm.exe (PID: 528)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6220)
- msedge.exe (PID: 4500)
Checks supported languages
- TextInputHost.exe (PID: 1272)
- identity_helper.exe (PID: 6788)
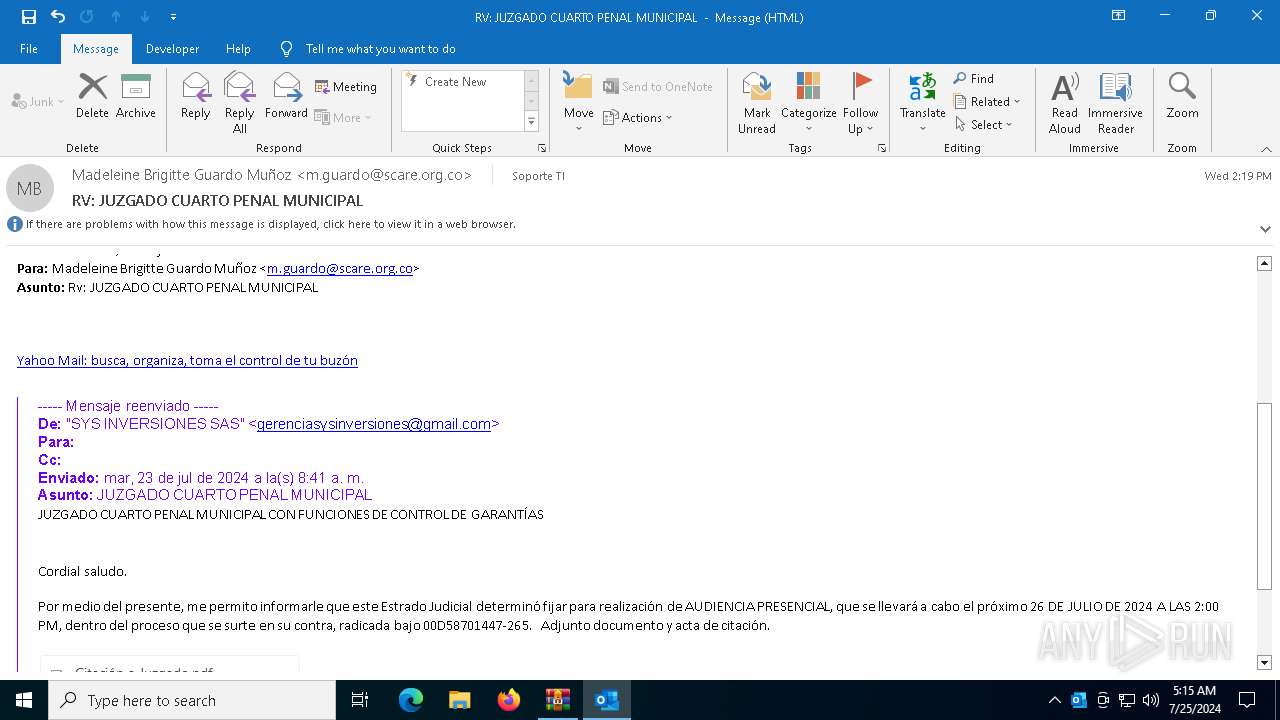
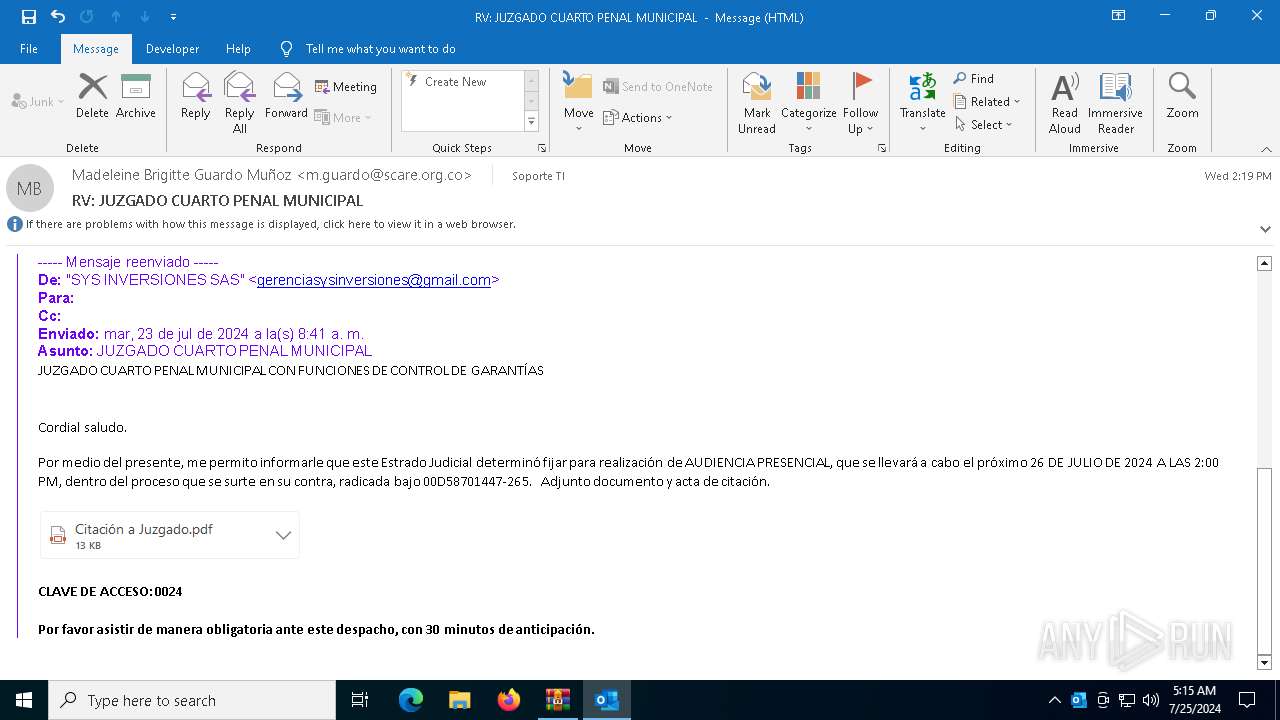
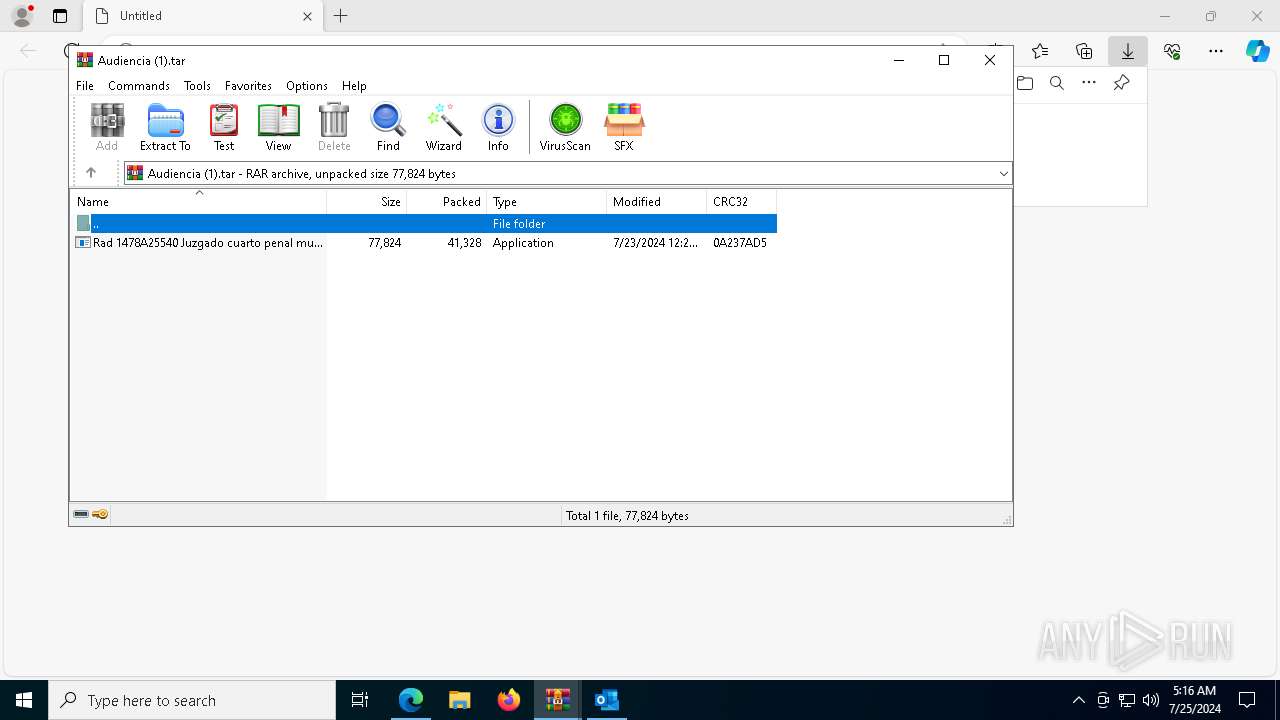
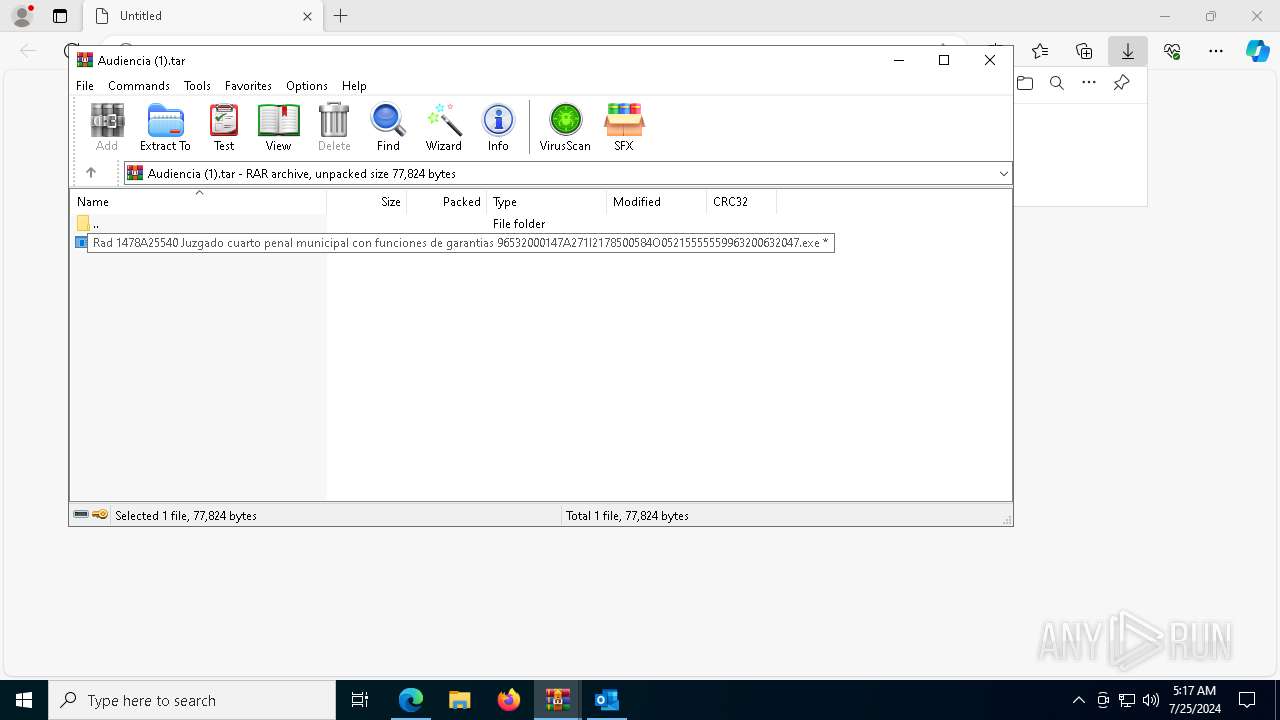
- Rad 1478A25540 Juzgado cuarto penal municipal con funciones de garantias 96532000147A271I2178500584O05215555559963200632047.exe (PID: 3108)
- RegAsm.exe (PID: 528)
- RegAsm.exe (PID: 2172)
- Rad 1478A25540 Juzgado cuarto penal municipal con funciones de garantias 96532000147A271I2178500584O05215555559963200632047.exe (PID: 2988)
The process uses the downloaded file
- msedge.exe (PID: 3140)
- msedge.exe (PID: 7016)
- msedge.exe (PID: 4500)
- WinRAR.exe (PID: 5236)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5236)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5236)
Application launched itself
- msedge.exe (PID: 4500)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 528)
- RegAsm.exe (PID: 2172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(528) RegAsm.exe
C2 (1)dxpam.duckdns.org
Ports (1)5999
Version1.0.7
Options
AutoRunfalse
MutexDcRatMutex_qwqdanchun
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVAIhNlmebb6nSe6ECHjMpYKJ1i7gvMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIxMDEyODA1MzU1N1oXDTMxMTEwNzA1MzU1N1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureeROjiuz0PWs+xgxamB7sdm3kB9OKtq8I1pPHgtkdiF0h9pw4eJzyp0fCw7zAO7/Q6+ftDqxvY+0OnHCoiErkMARDy55VYX6/gB5S0xXaoVgAqsvboJJN7EtFrwNTMUTPnslStHIwjEI/4a7JpzD5BLO0KCD9qZ2yVxSo7MwJXPE=
Keys
AESd87cc52fc4e6f60c76fd8ad033716334d5af6e39f2297effe8fadd57c01941a5
SaltDcRatByqwqdanchun
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
195
Monitored processes
49
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | Rad 1478A25540 Juzgado cuarto penal municipal con funciones de garantias 96532000147A271I2178500584O05215555559963200632047.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
AsyncRat(PID) Process(528) RegAsm.exe C2 (1)dxpam.duckdns.org Ports (1)5999 Version1.0.7 Options AutoRunfalse MutexDcRatMutex_qwqdanchun InstallFolder%AppData% Certificates Cert1MIICMDCCAZmgAwIBAgIVAIhNlmebb6nSe6ECHjMpYKJ1i7gvMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIxMDEyODA1MzU1N1oXDTMxMTEwNzA1MzU1N1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A... Server_SignatureeROjiuz0PWs+xgxamB7sdm3kB9OKtq8I1pPHgtkdiF0h9pw4eJzyp0fCw7zAO7/Q6+ftDqxvY+0OnHCoiErkMARDy55VYX6/gB5S0xXaoVgAqsvboJJN7EtFrwNTMUTPnslStHIwjEI/4a7JpzD5BLO0KCD9qZ2yVxSo7MwJXPE= Keys AESd87cc52fc4e6f60c76fd8ad033716334d5af6e39f2297effe8fadd57c01941a5 SaltDcRatByqwqdanchun | |||||||||||||||
| 704 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2396 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=4264 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=5540 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 916 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5648 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "7EA39DFE-1021-4774-8159-27AA4A66104B" "243921C3-FD5C-43FC-A6C4-5C47AAC518E9" "2204" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1560 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5192 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1560 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5304 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6864 --field-trial-handle=2312,i,6183926818321443200,5392445162217558241,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
42 236
Read events
41 641
Write events
510
Delete events
85
Modification events
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RV_ JUZGADO CUARTO PENAL MUNICIPAL.7z | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-157 |
Value: E-mail Message | |||
| (PID) Process: | (6220) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
245
Text files
105
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2204 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:6D4DE3C5917BAA7B9B0C272974B2FD4E | SHA256:EA295E017CCCD7A740EE9B7BFED3CC7C0FBBE82C991C26C051F8B3F549AB2F14 | |||
| 2204 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6220.30726\RV_ JUZGADO CUARTO PENAL MUNICIPAL.eml:OECustomProperty | binary | |
MD5:FFF73BBDB5467CC0D255D0C32E9D6674 | SHA256:0BE32E193D5AAAF9C3EDF7ACF925009F18CB830A0802953D9E5691E2BD83281D | |||
| 2204 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\BACE6E92.dat | image | |
MD5:CC2B612007FC5F38207E67561C8ECF22 | SHA256:39D26B625DAD789BA3C0C5CC15F9D547EC424F13DD3C1C83D4265FBE0C56D465 | |||
| 2204 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:B9B6D56C61E6087DE74CB42B5843E355 | SHA256:F2705AD04338426049AE332EAC508CDCD1B2DFC781A04920D654FE971F80E8FC | |||
| 2204 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:8E6B6237D8178924D1F8F7DAD9002889 | SHA256:5FAFDF7764A3102D2254F3832129CB45E531B7AA6A1C394FEFAB967D7ABF780C | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1005fd.TMP | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4500 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1005fd.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
93
DNS requests
63
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6884 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/42ecbc28-babc-4ca9-b065-ed0625b7b7c2?P1=1722452283&P2=404&P3=2&P4=bZwThjOINmdVOiOIvrGvej7IIbRI2KT%2bhCFxgLCBkZ3ArYYuq6QcNZnrBfPJIqyEpDzEikkDJroP4ZMD2Jju5Q%3d%3d | unknown | — | — | whitelisted |
6884 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/42ecbc28-babc-4ca9-b065-ed0625b7b7c2?P1=1722452283&P2=404&P3=2&P4=bZwThjOINmdVOiOIvrGvej7IIbRI2KT%2bhCFxgLCBkZ3ArYYuq6QcNZnrBfPJIqyEpDzEikkDJroP4ZMD2Jju5Q%3d%3d | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7016 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4340 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2204 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2204 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6884 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8bc315ba-54e5-49f4-9b75-997d7071eb06?P1=1722399009&P2=404&P3=2&P4=JSpMtyKHQWemMaxCrjoDMtIoAsJ6LN%2fIWFcuHqAFcqUjwX%2fUVb%2fs5vWZHz70GaNK9pCdPRCk%2faXm6Lec944Q6w%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3204 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3800 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4552 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5200 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
528 | RegAsm.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
2284 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2284 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
528 | RegAsm.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT) |
528 | RegAsm.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report