| File name: | 25.rar |
| Full analysis: | https://app.any.run/tasks/130a1e06-05f2-4151-9722-61ec68792c09 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | April 15, 2019, 08:54:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5BB9084F9D5EB2CEC5B0FE1E637E238D |
| SHA1: | AEA2F6D97B2E7275768EF1BA5AA0F03DA4F6BFFA |
| SHA256: | 9D16C593F0891955FEB0ED022EA8E1D18E164EA9C27A0D773910F7FB8769EDA5 |
| SSDEEP: | 98304:b+ni1xNHyGQX8+E3cTvrQmzXmWd4hUovOEY4Av6oi1BZOCFmymwFFglLK1LEGxNn:bplSZ8+E3cb05Wmh12Woy1DFGwrkIEJc |
MALICIOUS
Application was dropped or rewritten from another process
- sss.exe (PID: 1296)
Connects to CnC server
- sss.exe (PID: 1296)
AZORULT was detected
- sss.exe (PID: 1296)
Actions looks like stealing of personal data
- sss.exe (PID: 1296)
Loads dropped or rewritten executable
- sss.exe (PID: 1296)
SUSPICIOUS
Executable content was dropped or overwritten
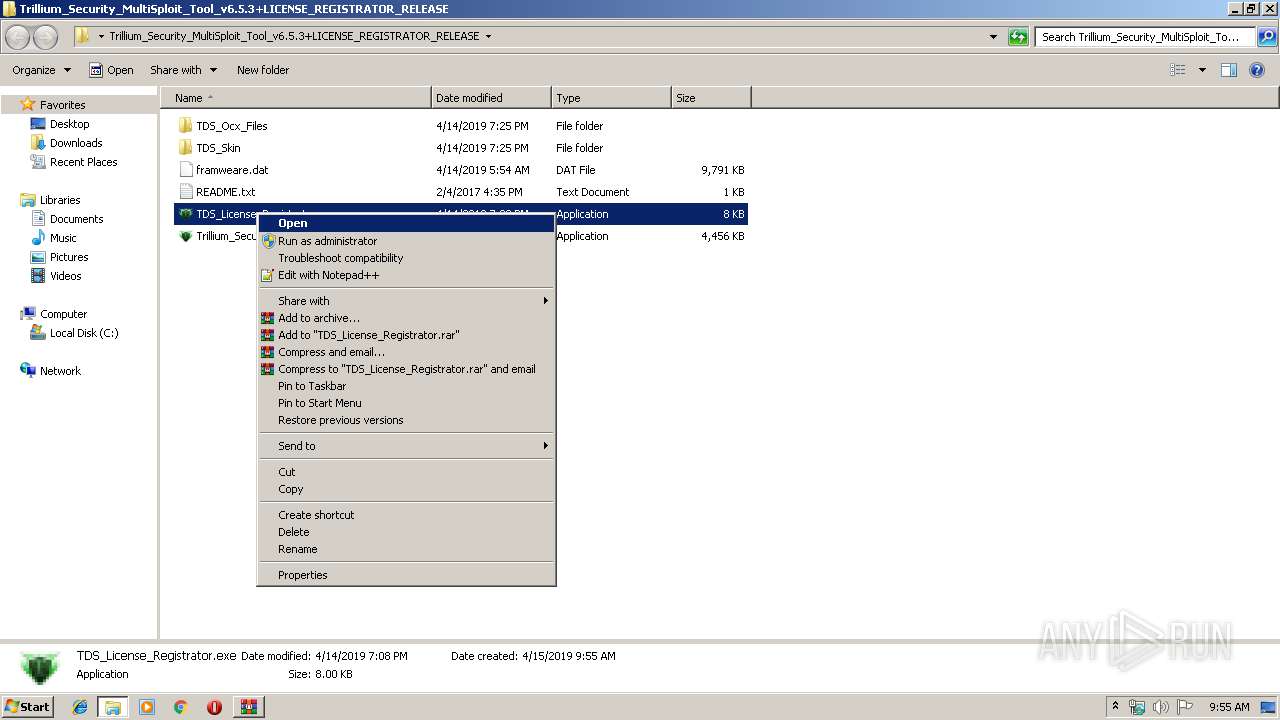
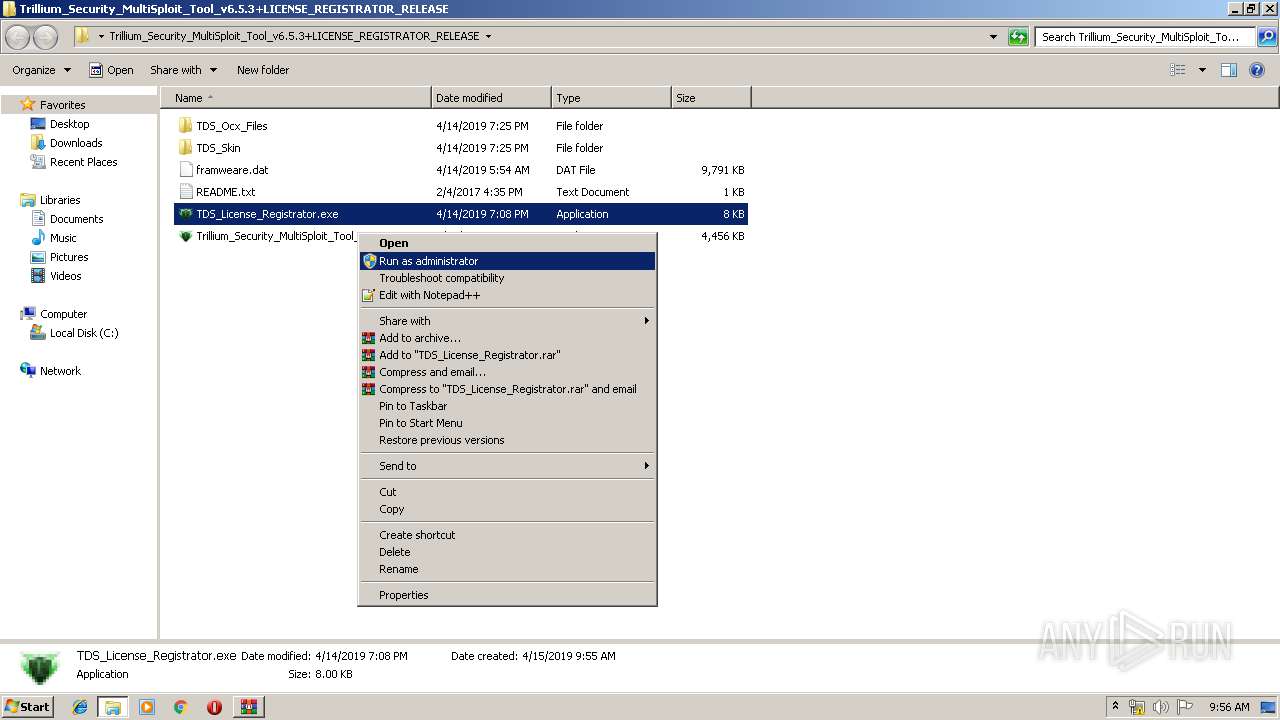
- TDS_License_Registrator.exe (PID: 2128)
- sss.exe (PID: 1296)
Reads the cookies of Google Chrome
- sss.exe (PID: 1296)
Reads the cookies of Mozilla Firefox
- sss.exe (PID: 1296)
Starts CMD.EXE for commands execution
- sss.exe (PID: 1296)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | C:\Windows\system32\timeout.exe 3 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
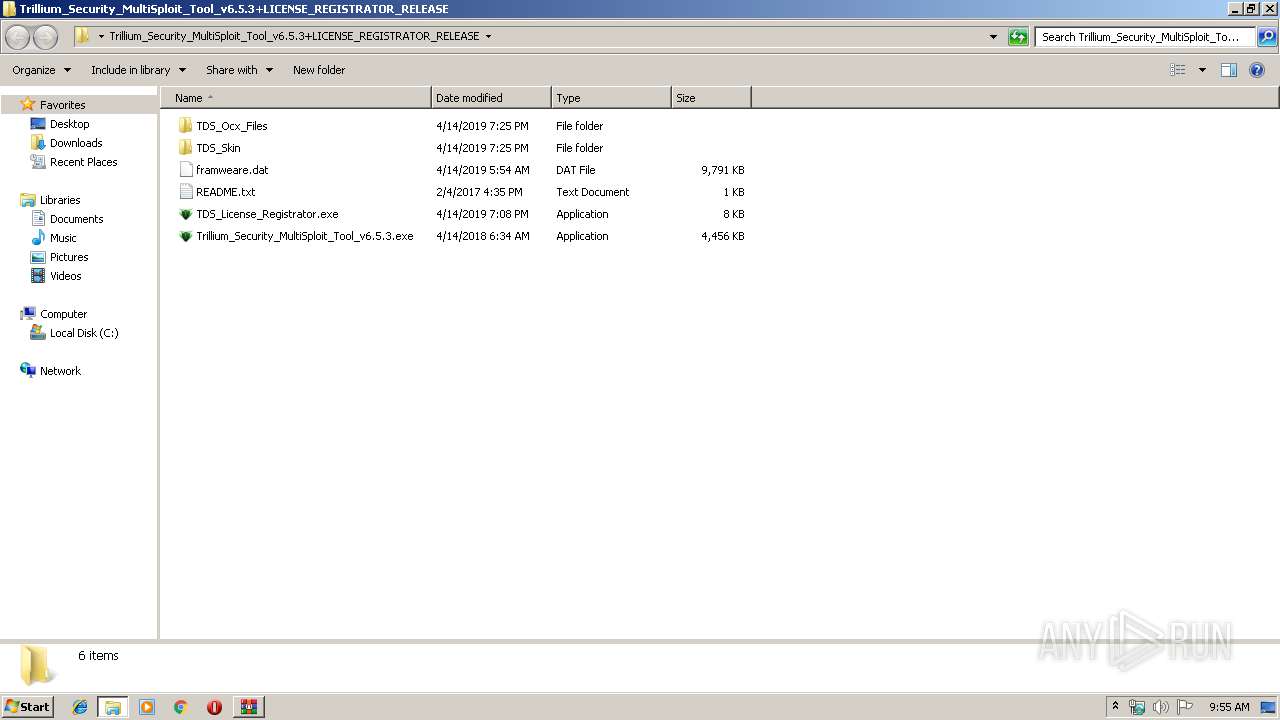
| 1296 | "C:\sss.exe" | C:\sss.exe | TDS_License_Registrator.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
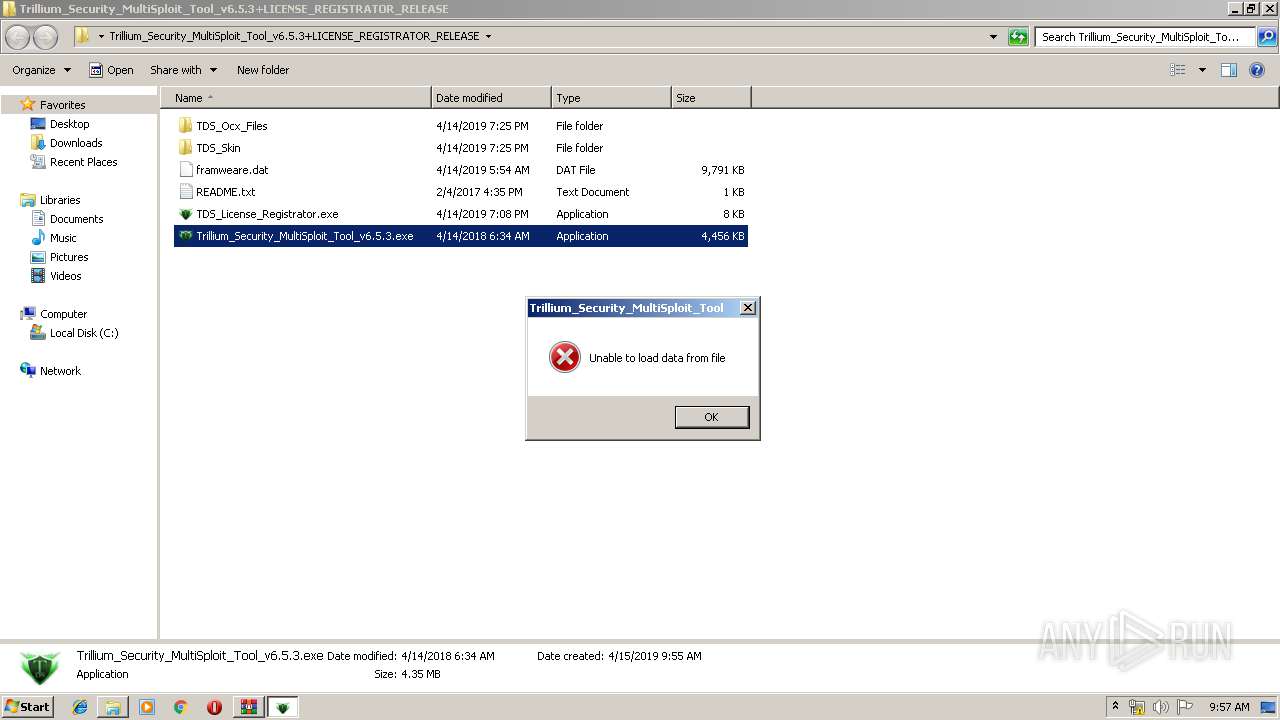
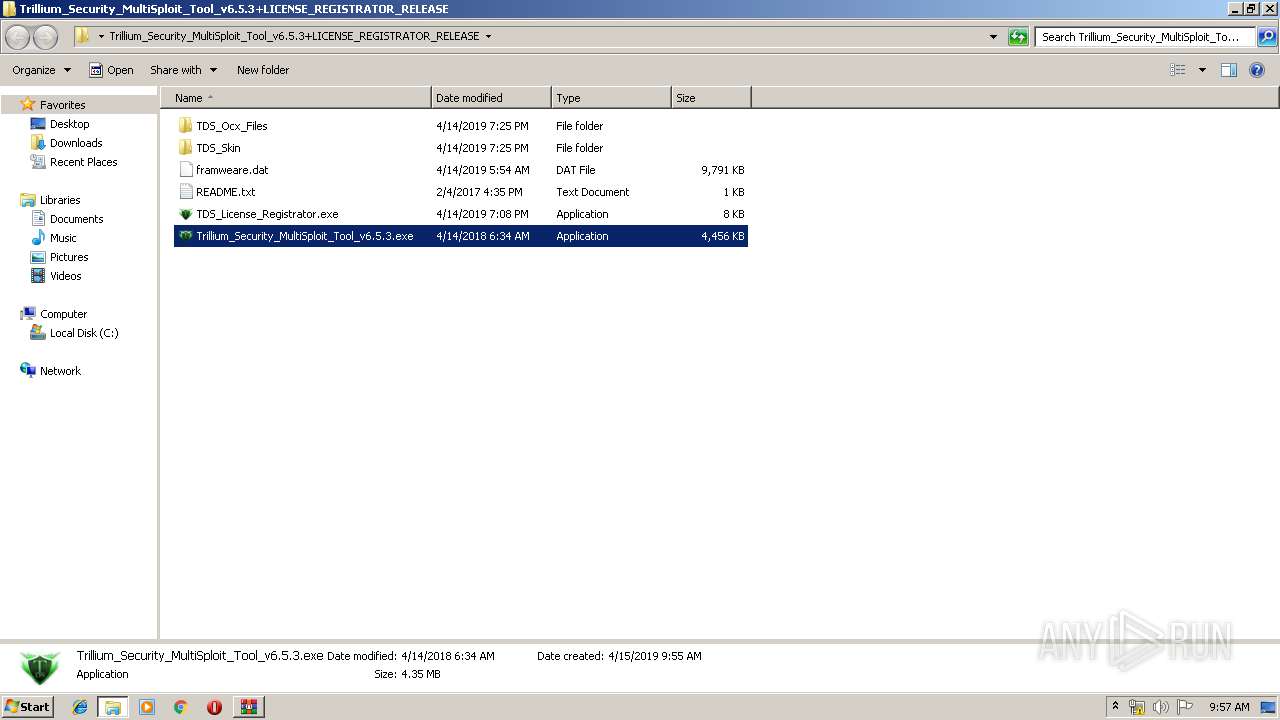
| 1732 | "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\Trillium_Security_MultiSploit_Tool_v6.5.3.exe" | C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\Trillium_Security_MultiSploit_Tool_v6.5.3.exe | explorer.exe | ||||||||||||
User: admin Company: Trillium Defense Solutions Integrity Level: HIGH Description: Trillium Security MultiSploit Tool v6.5.3 Exit code: 0 Version: 6.05.0003 Modules
| |||||||||||||||
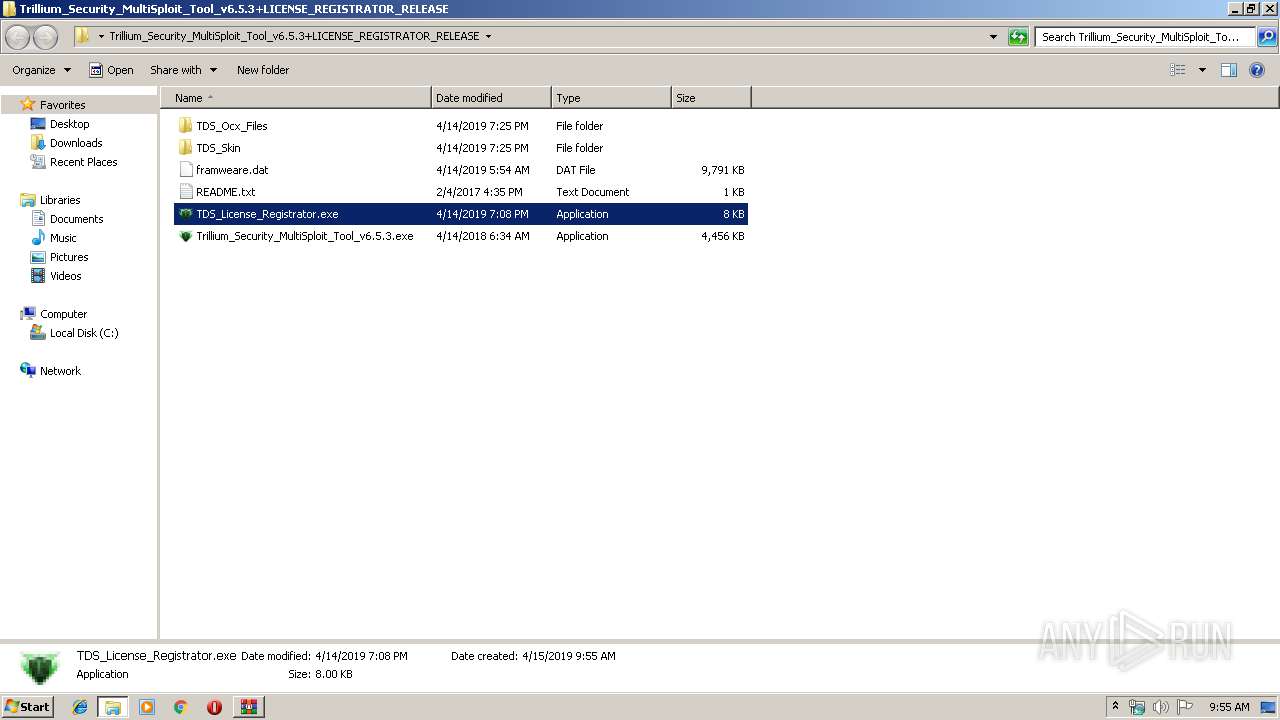
| 2128 | "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_License_Registrator.exe" | C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_License_Registrator.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Total Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\25.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3336 | "C:\Windows\system32\cmd.exe" /c C:\Windows\system32\timeout.exe 3 & del "sss.exe" | C:\Windows\system32\cmd.exe | — | sss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
566
Read events
524
Write events
42
Delete events
0
Modification events
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\25.rar | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2244) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2128) TDS_License_Registrator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\TDS_License_Registrator_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2128) TDS_License_Registrator.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\TDS_License_Registrator_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
49
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\framweare.dat | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\README.txt | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_License_Registrator.exe | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_Ocx_Files\Codejock.Controls.v15.2.1.ocx | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_Ocx_Files\Codejock.SkinFramework.v15.2.1.ocx | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_Ocx_Files\Trillium_Security_OCX_Registrator.exe | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\TDS_Skin\TDS_Skin.style | — | |
MD5:— | SHA256:— | |||
| 2244 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2244.1049\Trillium_Security_MultiSploit_Tool_v6.5.3+LICENSE_REGISTRATOR_RELEASE\Trillium_Security_MultiSploit_Tool_v6.5.3.exe | — | |
MD5:— | SHA256:— | |||
| 2128 | TDS_License_Registrator.exe | C:\sss.exe | text | |
MD5:— | SHA256:— | |||
| 1296 | sss.exe | C:\Users\admin\AppData\Local\Temp\2fda\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:94AE25C7A5497CA0BE6882A00644CA64 | SHA256:7EA06B7050F9EA2BCC12AF34374BDF1173646D4E5EBF66AD690B37F4DF5F3D4E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
1
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1296 | sss.exe | POST | 200 | 41.97.201.236:80 | http://hercule.servehttp.com/index.php | DZ | text | 2 b | malicious |
1296 | sss.exe | POST | 200 | 41.97.201.236:80 | http://hercule.servehttp.com/index.php | DZ | binary | 4.27 Mb | malicious |
2128 | TDS_License_Registrator.exe | GET | 200 | 41.97.201.236:80 | http://hercule.servehttp.com/test.txt | DZ | text | 150 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2128 | TDS_License_Registrator.exe | 41.97.201.236:80 | hercule.servehttp.com | Telecom Algeria | DZ | suspicious |
1296 | sss.exe | 41.97.201.236:80 | hercule.servehttp.com | Telecom Algeria | DZ | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hercule.servehttp.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2128 | TDS_License_Registrator.exe | Potentially Bad Traffic | ET INFO HTTP Connection To DDNS Domain Servehttp.com |
2128 | TDS_License_Registrator.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] PE EXE or DLL Windows file download HTTP (base64 encoded) |
1296 | sss.exe | A Network Trojan was detected | ET TROJAN AZORult Variant.4 Checkin M2 |
1296 | sss.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult client request |
1296 | sss.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult.Stealer HTTP Header |
1296 | sss.exe | Potentially Bad Traffic | ET INFO HTTP Connection To DDNS Domain Servehttp.com |
1296 | sss.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult encrypted PE file |
1296 | sss.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult.Stealer HTTP Header |
1296 | sss.exe | Potentially Bad Traffic | ET INFO HTTP Connection To DDNS Domain Servehttp.com |
1296 | sss.exe | A Network Trojan was detected | MALWARE [PTsecurity] AZORult client request |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
Trillium_Security_MultiSploit_Tool_v6.5.3.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|