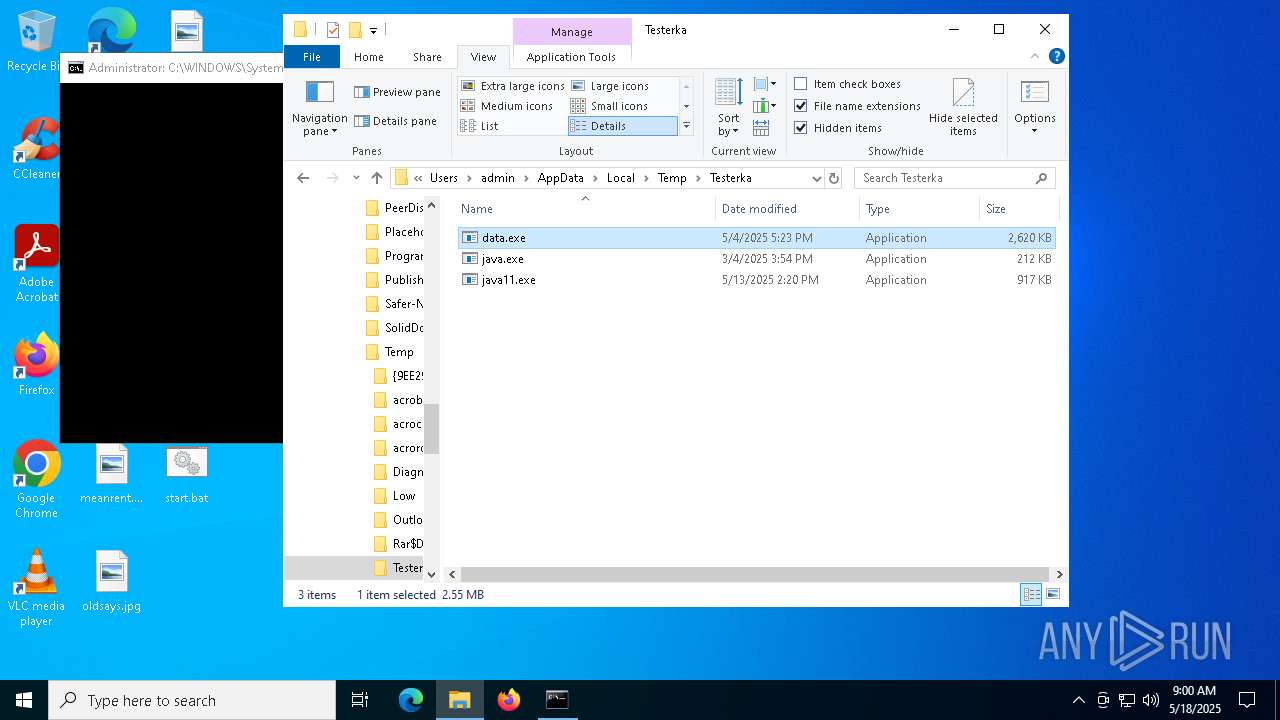
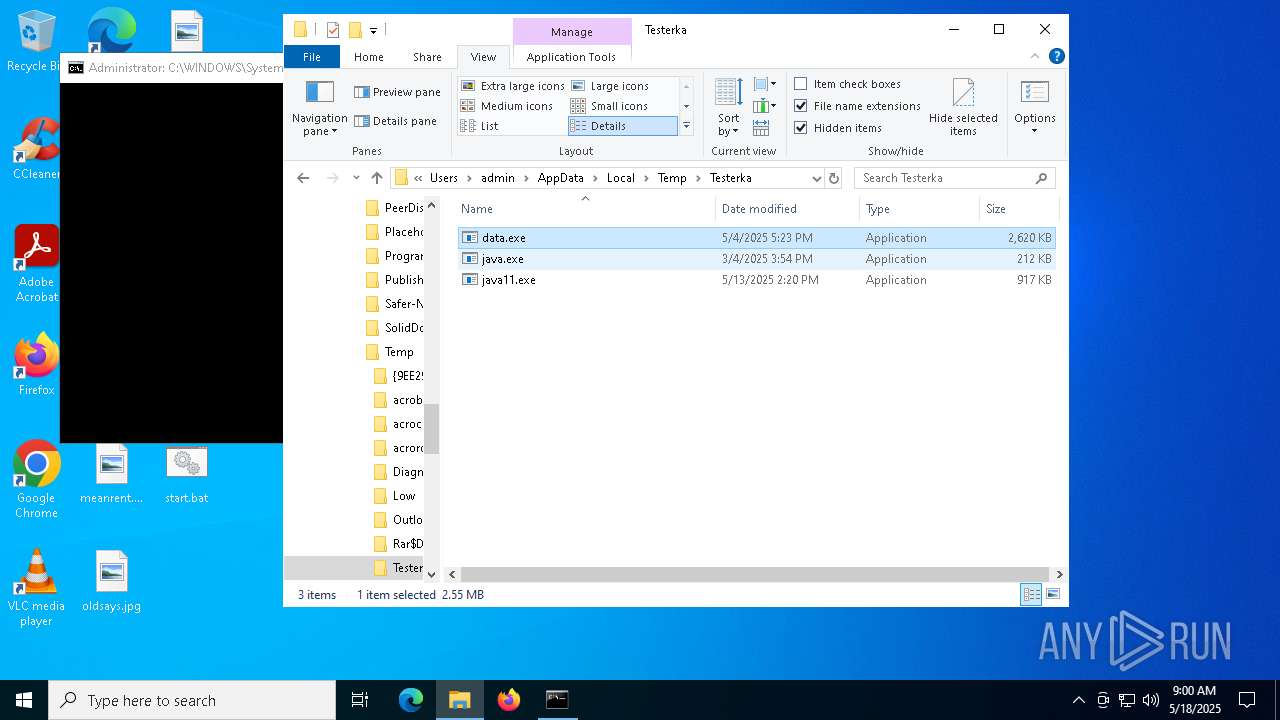
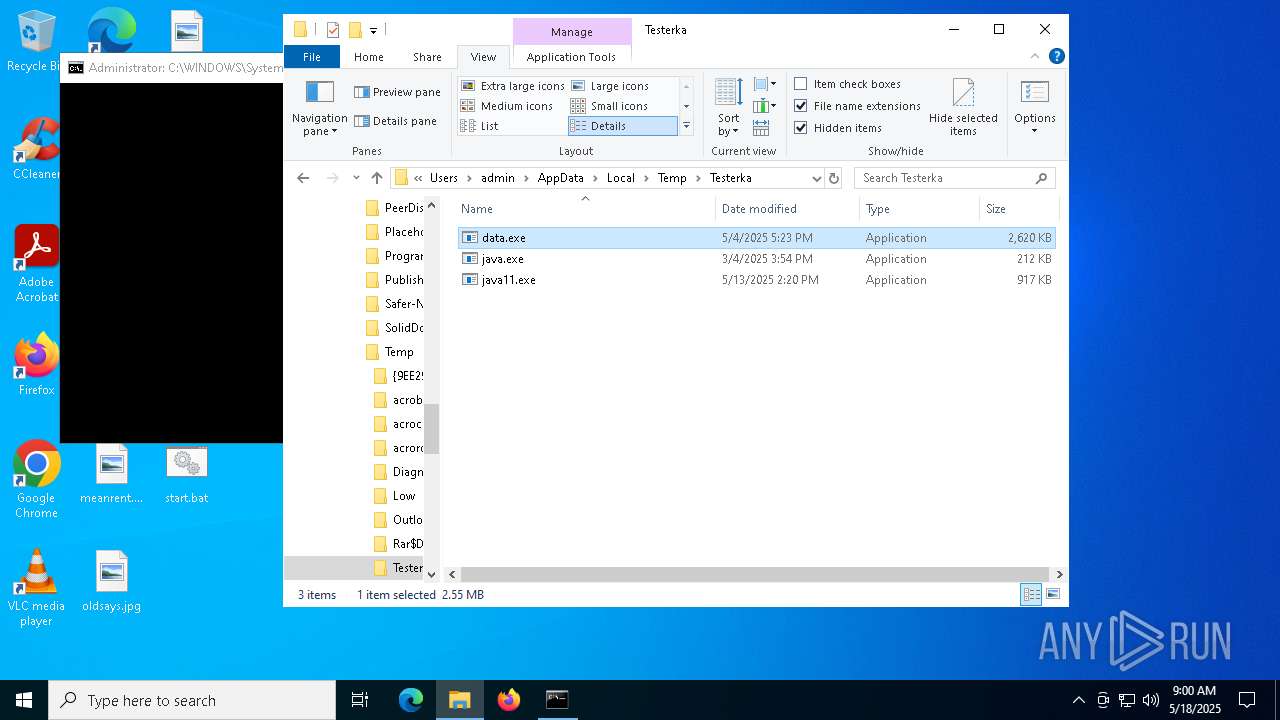
| File name: | start.bat |
| Full analysis: | https://app.any.run/tasks/be0a7cc1-2f03-4872-8170-b3009e72ec21 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 18, 2025, 08:55:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (3123), with CRLF line terminators |
| MD5: | A84DE9ACDD2D70C21A92CE5D66C772DE |
| SHA1: | E261181D3D2FD035E808EC83FC6137924C9A7120 |
| SHA256: | 9D10755C62BC41F8A8F281A6158260C5FDDC8263188554E7F5E3728C4C56D52E |
| SSDEEP: | 12288:/NgasirAuySxZQSaai+dmVrg5wj778U+AWphPvIne:V91yE0admpg5wH+AI3N |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7236)
- powershell.exe (PID: 7716)
- powershell.exe (PID: 4164)
- powershell.exe (PID: 1852)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 7196)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 1672)
- powershell.exe (PID: 6488)
- powershell.exe (PID: 7968)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 2420)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 7820)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Changes Windows Defender settings
- cmd.exe (PID: 8140)
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 8140)
Run PowerShell with an invisible window
- powershell.exe (PID: 7584)
- powershell.exe (PID: 2104)
- powershell.exe (PID: 872)
Executing a file with an untrusted certificate
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7516)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Adds extension to the Windows Defender exclusion list
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 4980)
- cmd.exe (PID: 7204)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 968)
Vulnerable driver has been detected
- gmstcccpdzbb.exe (PID: 7884)
- gmstcccpdzbb.exe (PID: 7352)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 4996)
- cmd.exe (PID: 7948)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 7812)
- cmd.exe (PID: 7588)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 5360)
- cmd.exe (PID: 7924)
- cmd.exe (PID: 4528)
- cmd.exe (PID: 5364)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5204)
- powershell.exe (PID: 7880)
- cmd.exe (PID: 8140)
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Application launched itself
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 7236)
- powershell.exe (PID: 1852)
- powershell.exe (PID: 4108)
- powershell.exe (PID: 6768)
- powershell.exe (PID: 1672)
- powershell.exe (PID: 7968)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 5740)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 7820)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
- data.exe (PID: 3032)
- data.exe (PID: 7516)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Starts application with an unusual extension
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Executes script without checking the security policy
- powershell.exe (PID: 5008)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 1628)
- powershell.exe (PID: 5176)
Lists computer manufacturer and model
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Starts NET.EXE to display or manage information about active sessions
- net.exe (PID: 4068)
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
- net.exe (PID: 2284)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Starts process via Powershell
- powershell.exe (PID: 7880)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 2104)
- powershell.exe (PID: 872)
- powershell.exe (PID: 7464)
Executing commands from a ".bat" file
- powershell.exe (PID: 7880)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 8140)
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8140)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8140)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 8140)
Process drops legitimate windows executable
- UnRAR.exe (PID: 4980)
Probably download files using WebClient
- cmd.exe (PID: 8140)
Executable content was dropped or overwritten
- UnRAR.exe (PID: 4980)
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Starts a Microsoft application from unusual location
- java.exe (PID: 6268)
Executes application which crashes
- java11.exe (PID: 920)
Manipulates environment variables
- powershell.exe (PID: 7620)
- powershell.exe (PID: 7420)
- powershell.exe (PID: 5292)
- powershell.exe (PID: 7824)
Script adds exclusion extension to Windows Defender
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Stops a currently running service
- sc.exe (PID: 7908)
- sc.exe (PID: 7236)
- sc.exe (PID: 7968)
- sc.exe (PID: 7692)
- sc.exe (PID: 1764)
- sc.exe (PID: 1188)
- sc.exe (PID: 7604)
- sc.exe (PID: 5640)
- sc.exe (PID: 8048)
- sc.exe (PID: 8024)
- sc.exe (PID: 7524)
- sc.exe (PID: 632)
- sc.exe (PID: 8112)
- sc.exe (PID: 8048)
- sc.exe (PID: 8016)
- sc.exe (PID: 6612)
- sc.exe (PID: 4844)
- sc.exe (PID: 4112)
- sc.exe (PID: 4776)
- sc.exe (PID: 1532)
- sc.exe (PID: 2852)
- sc.exe (PID: 6800)
Process uninstalls Windows update
- wusa.exe (PID: 6828)
- wusa.exe (PID: 6512)
- wusa.exe (PID: 3332)
- wusa.exe (PID: 7328)
Uses powercfg.exe to modify the power settings
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Windows service management via SC.EXE
- sc.exe (PID: 5384)
- sc.exe (PID: 3240)
- sc.exe (PID: 1088)
Creates a new Windows service
- sc.exe (PID: 6300)
Starts SC.EXE for service management
- data.exe (PID: 3032)
- gmstcccpdzbb.exe (PID: 7884)
- data.exe (PID: 7672)
- gmstcccpdzbb.exe (PID: 7352)
Executes as Windows Service
- gmstcccpdzbb.exe (PID: 7884)
- gmstcccpdzbb.exe (PID: 7352)
Drops a system driver (possible attempt to evade defenses)
- gmstcccpdzbb.exe (PID: 7884)
- gmstcccpdzbb.exe (PID: 7352)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
INFO
Application launched itself
- Acrobat.exe (PID: 7740)
- AcroCEF.exe (PID: 8020)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5352)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 5352)
- WMIC.exe (PID: 7680)
- WMIC.exe (PID: 684)
- WMIC.exe (PID: 7380)
- WMIC.exe (PID: 8132)
Manual execution by a user
- cmd.exe (PID: 5204)
- data.exe (PID: 7516)
Reads the software policy settings
- slui.exe (PID: 7332)
Changes the display of characters in the console
- cmd.exe (PID: 5204)
- cmd.exe (PID: 8140)
Checks supported languages
- chcp.com (PID: 1764)
The sample compiled with english language support
- UnRAR.exe (PID: 4980)
- data.exe (PID: 3032)
- data.exe (PID: 7672)
The executable file from the user directory is run by the Powershell process
- data.exe (PID: 3032)
- java.exe (PID: 6268)
- java11.exe (PID: 920)
- data.exe (PID: 7672)
The sample compiled with japanese language support
- gmstcccpdzbb.exe (PID: 7884)
- gmstcccpdzbb.exe (PID: 7352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
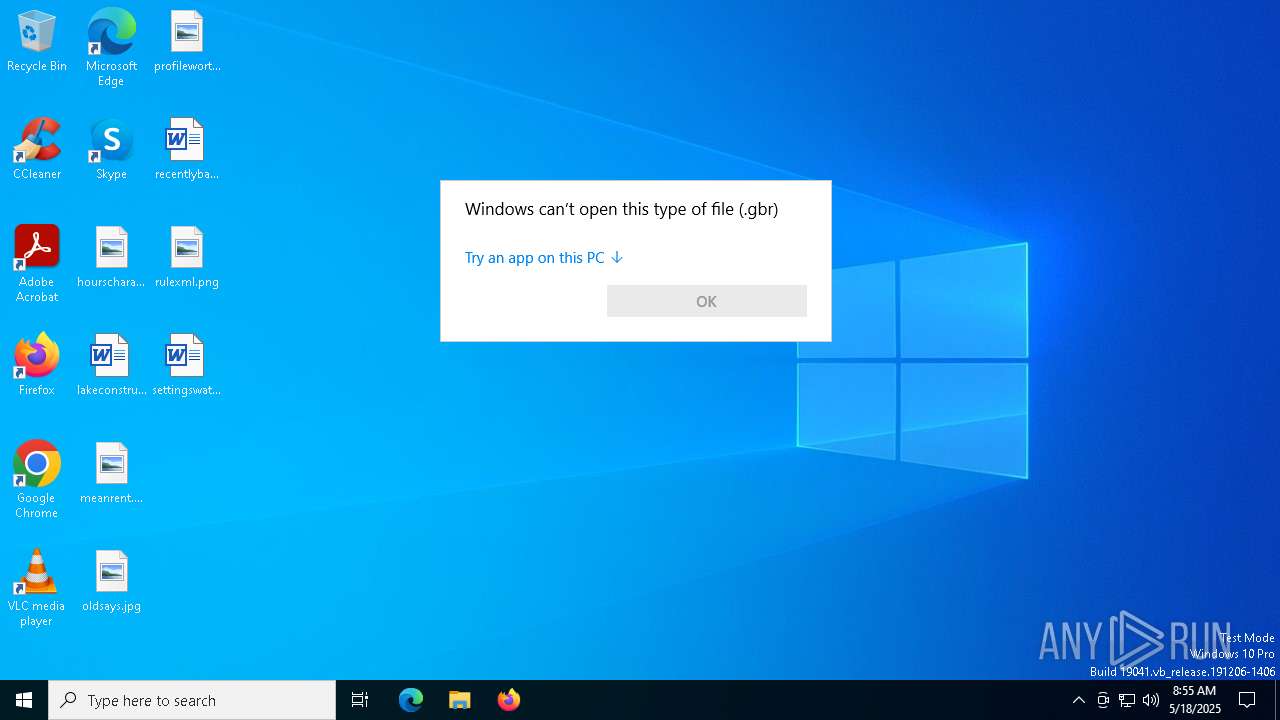
TRiD
| .gbr | | | Gerber format (100) |
|---|
Total processes
391
Monitored processes
251
Malicious processes
10
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | wmic computersystem get manufacturer /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | findstr /i "echo" "C:\Users\admin\Desktop\start.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | findstr /i "echo" "C:\Users\admin\Desktop\start.bat" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | C:\WINDOWS\system32\sc.exe stop UsoSvc | C:\Windows\System32\sc.exe | — | data.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\AppHost" /v "EnableWebContentEvaluation" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | wmic computersystem get manufacturer /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | doskey CHANGE=RECOVER | C:\Windows\System32\doskey.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Keyboard History Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | powershell -Command "Start-Process 'C:\Users\admin\AppData\Local\Temp\Testerka\java.exe' -WindowStyle Hidden" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Users\admin\AppData\Local\Temp\Testerka\java11.exe" | C:\Users\admin\AppData\Local\Temp\Testerka\java11.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Systems Exit code: 2148734499 Version: 1.0.0.0 Modules
| |||||||||||||||
| 960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
180 658
Read events
180 482
Write events
163
Delete events
13
Modification events
| (PID) Process: | (7740) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\HomeWelcomeFirstMile |
| Operation: | write | Name: | iCardCountShown |
Value: 3 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F4241545F475549445F4E474C5F44554D4D5900 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F5F5245534944554500 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\DLLInjection |
| Operation: | write | Name: | bBlockDLLInjection |
Value: 0 | |||
| (PID) Process: | (7824) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | delete value | Name: | ProductInfoCache |
Value: | |||
Executable files
7
Suspicious files
139
Text files
139
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7740 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 7824 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 7824 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2025-05-18 08-56-03-514.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
| 8020 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old | text | |
MD5:2EF1F7C0782D1A46974286420D24F629 | SHA256:D3A9BB7E09E1F4B0C41FF7808E930DDACF5DB3BACD98ECCF5BC7DB4863D1FCF5 | |||
| 7824 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 8020 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old~RF112bef.TMP | text | |
MD5:D012E5B4EB91B61F6E8AE2F8EC3C623E | SHA256:1BDA750084F20306722008016420E1912BA608CA8EFB9C661F7E7EFCF5E89673 | |||
| 7824 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.7824 | binary | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 8020 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:DCC46C51CB6649C5BF4A11F743470944 | SHA256:9977C26FD26FEC25BEC9DCDD43036B9DD3A06B3E9111875682C9B781752CDF05 | |||
| 8020 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:AE4982D26E104054268250084BE68A3D | SHA256:9EC49D5C4662ECD023A3B8866B4657B48A8BFFD649A4ACA2B60484F403100D1A | |||
| 8020 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:4A72C82508438B7D604F687BB63F2D3B | SHA256:ED38153BEFD9F40C6E7C65EDFBA1775F4DAA0E3558CDFB860D2367AC66D725FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
88
DNS requests
29
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7464 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7740 | Acrobat.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
7464 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2432 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Crypto Currency Mining Activity Detected | ET COINMINER CoinMiner Domain in DNS Lookup (pool .hashvault .pro) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |