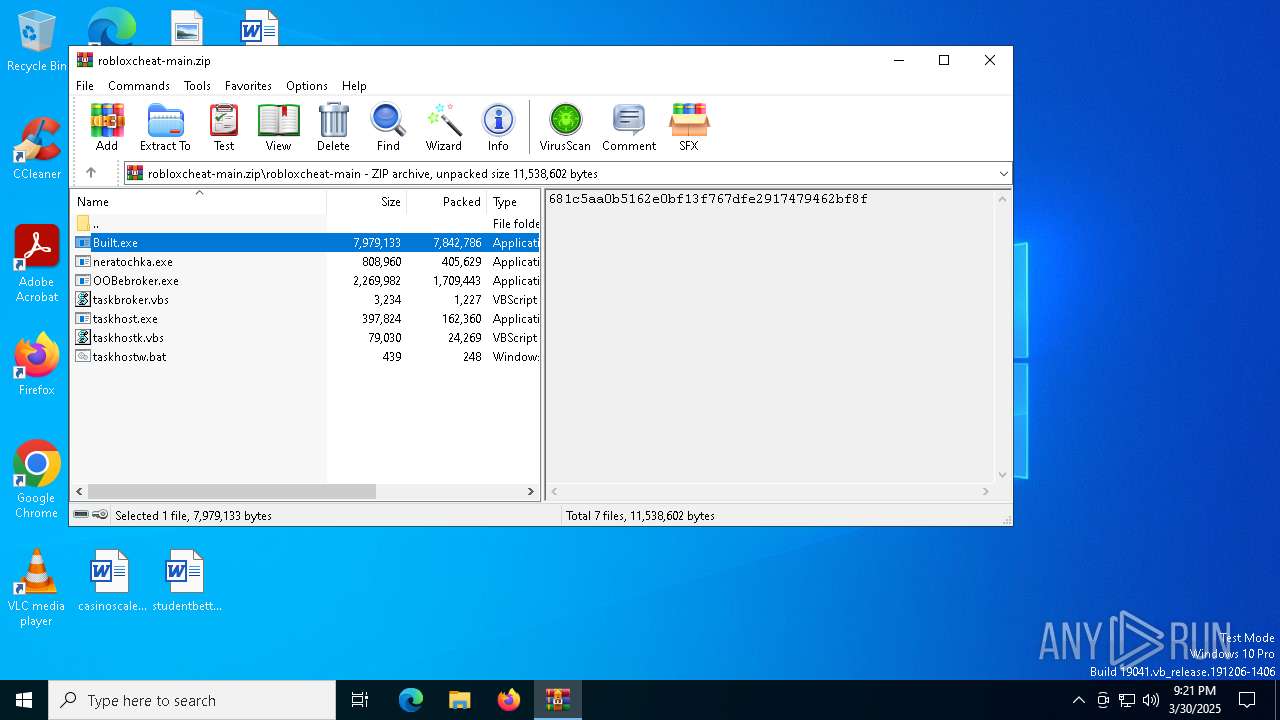
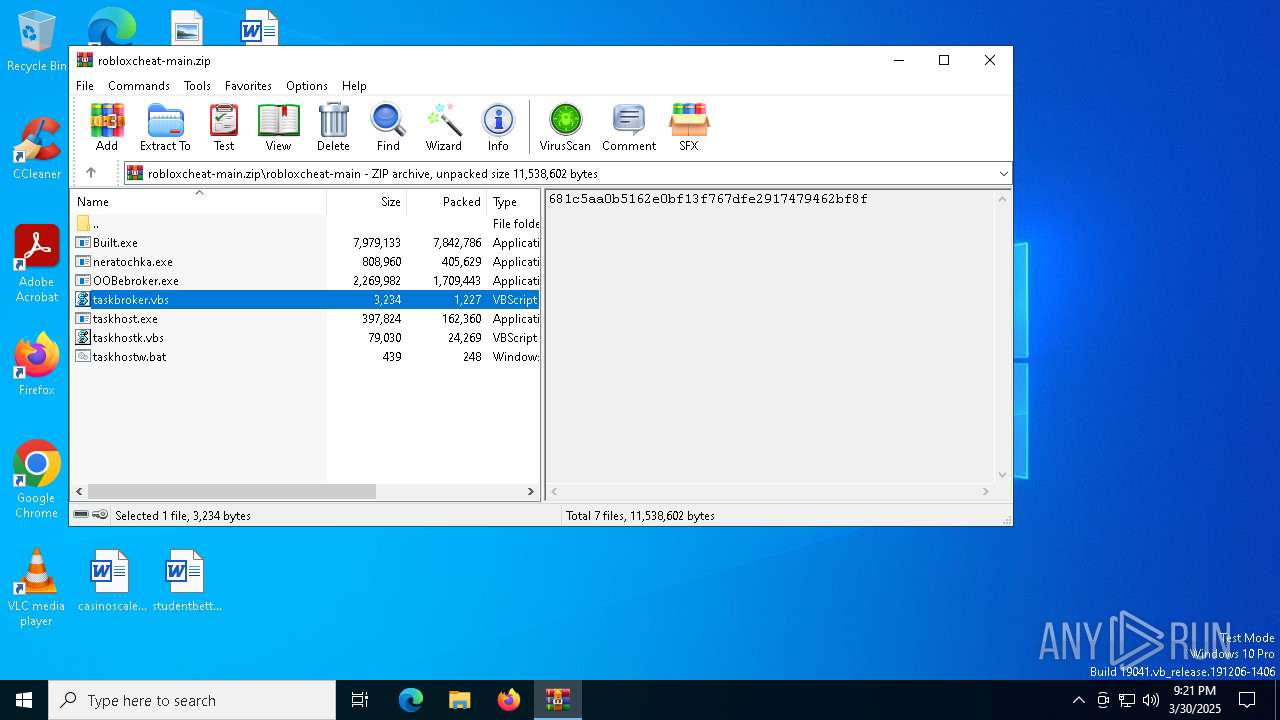
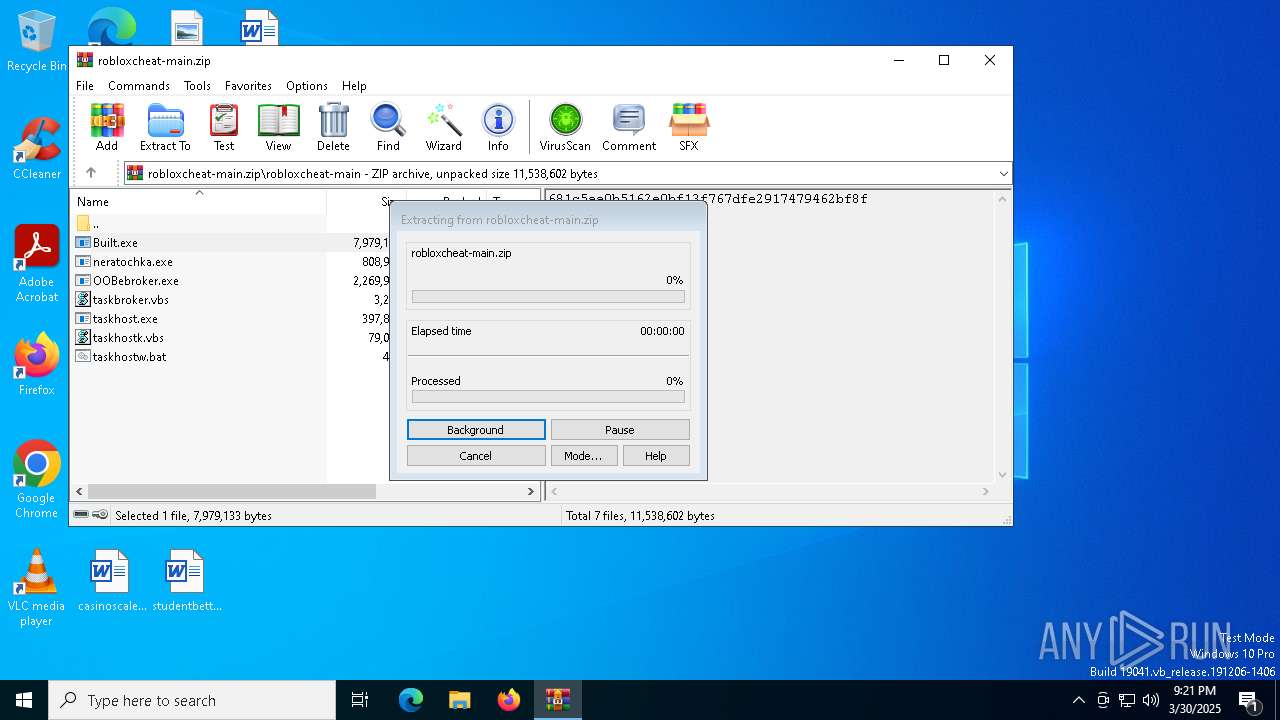
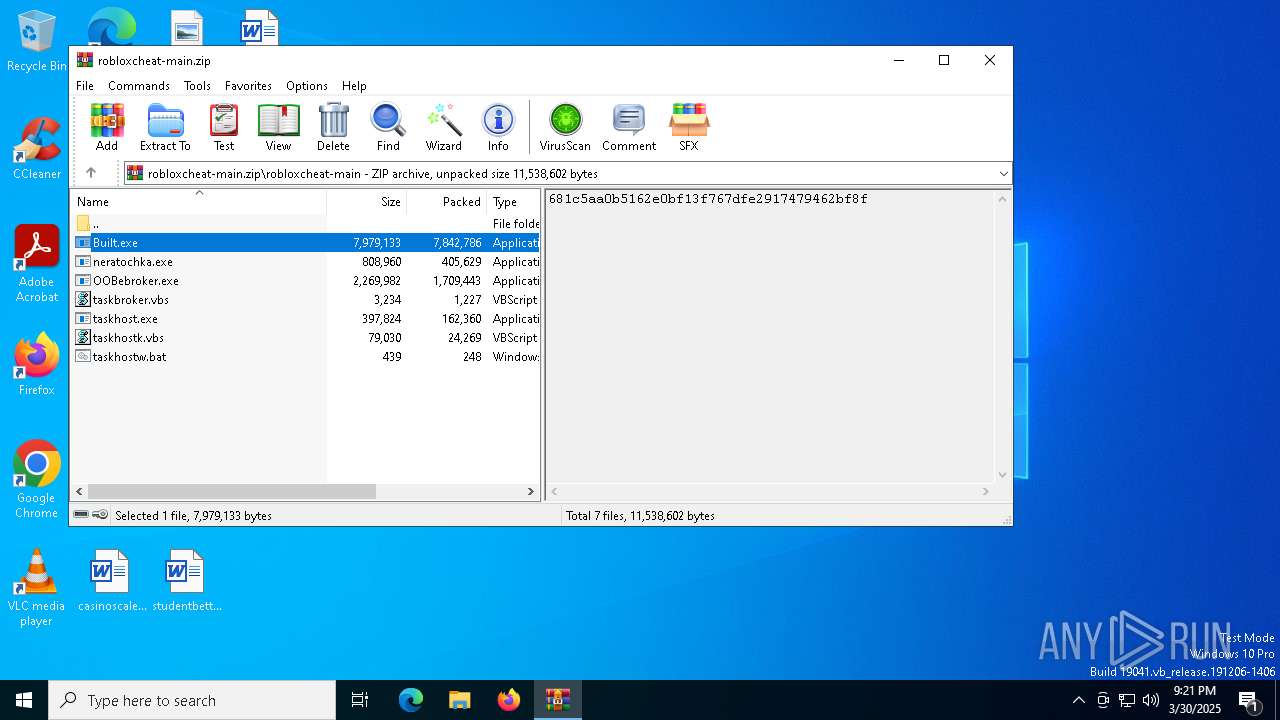
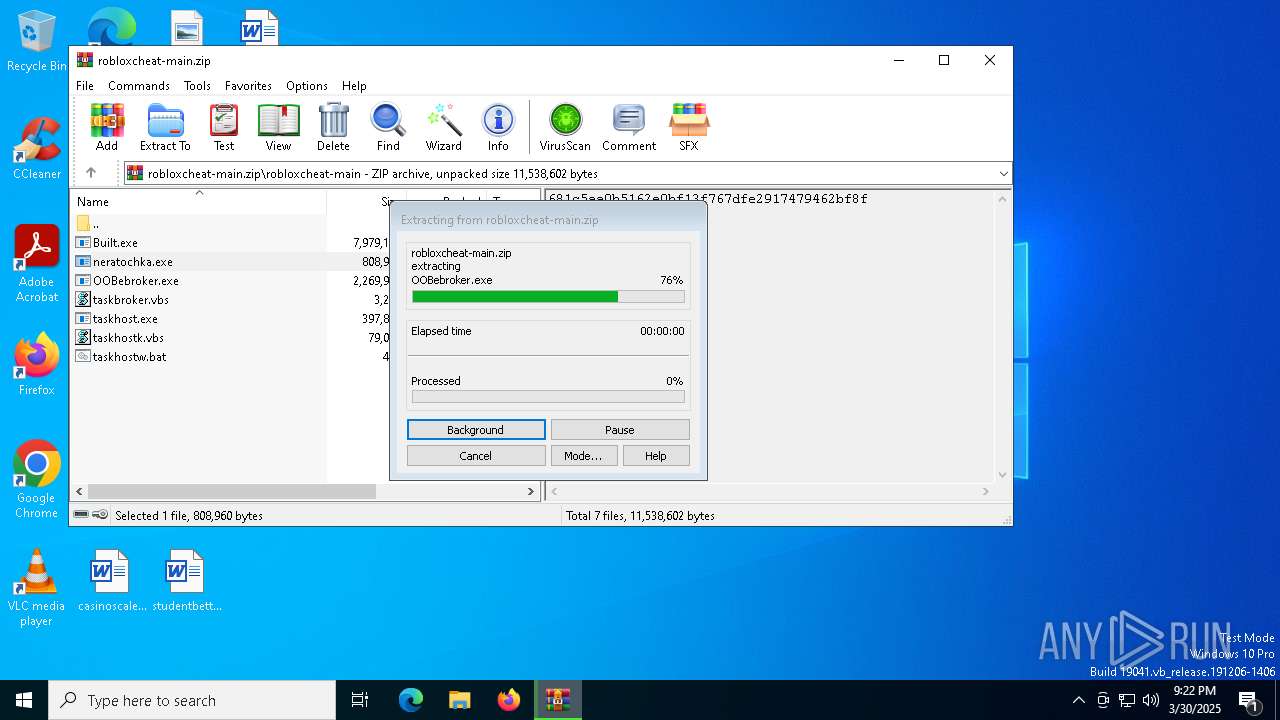
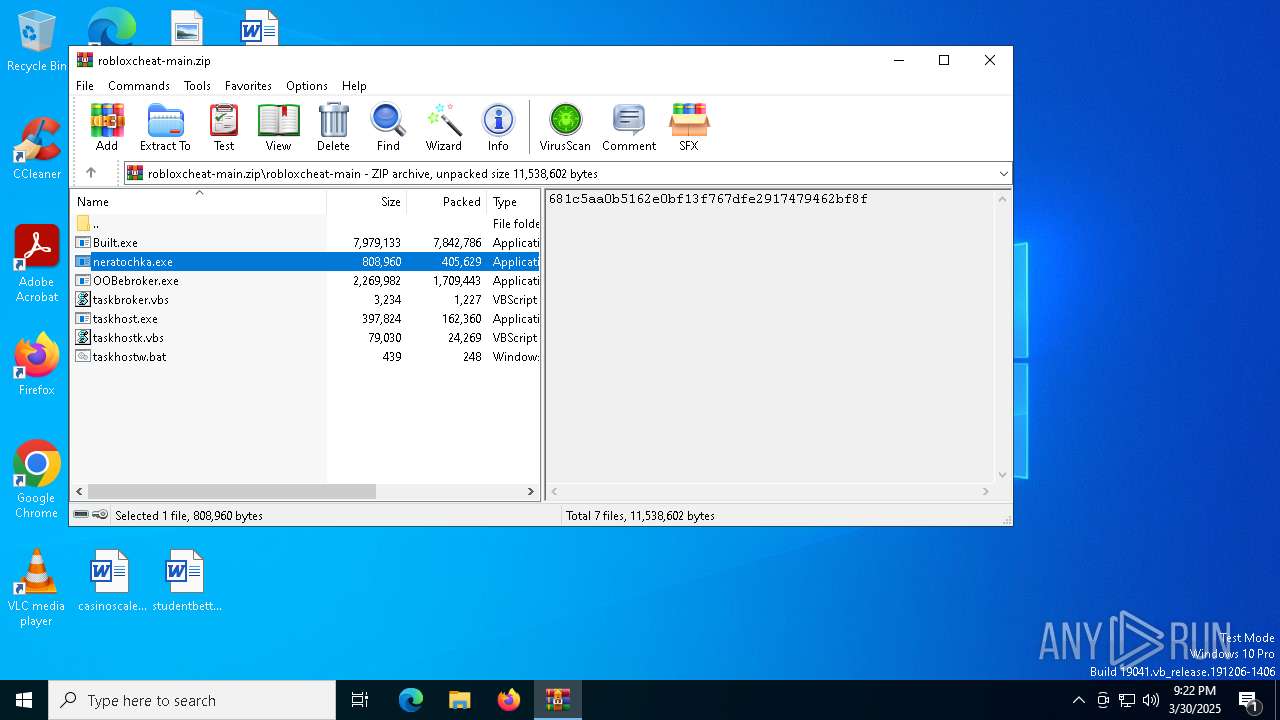
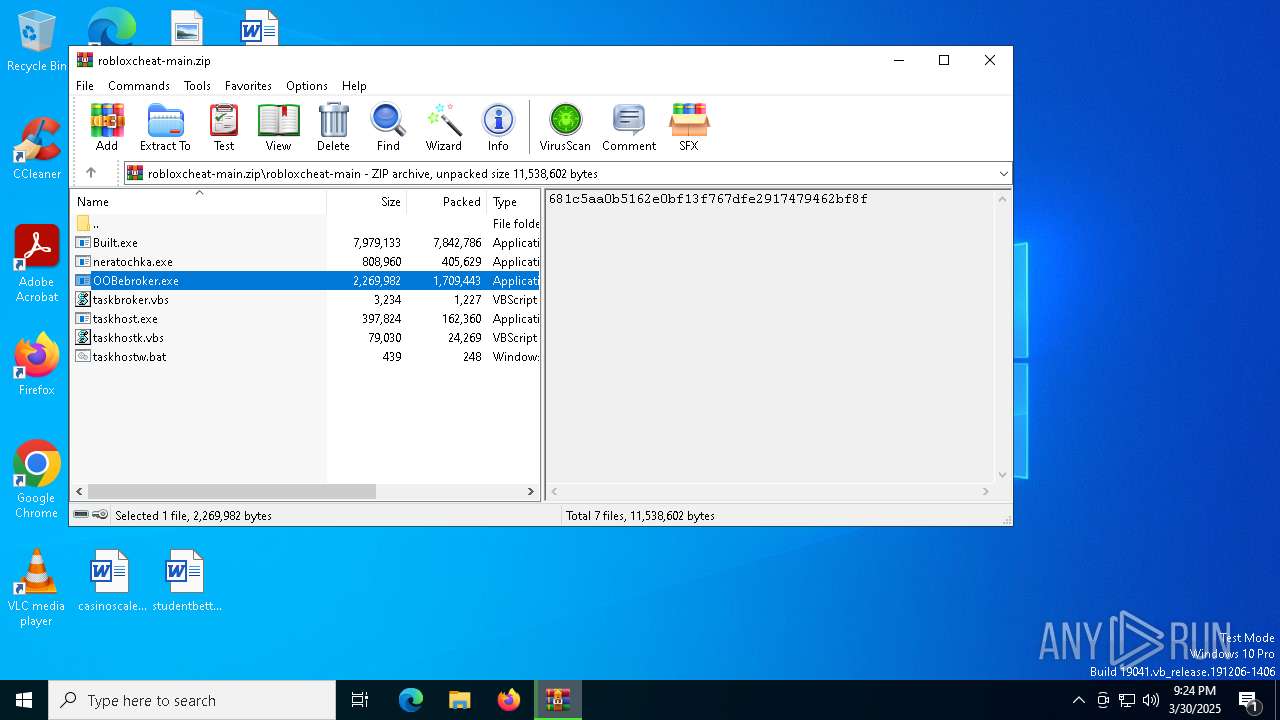
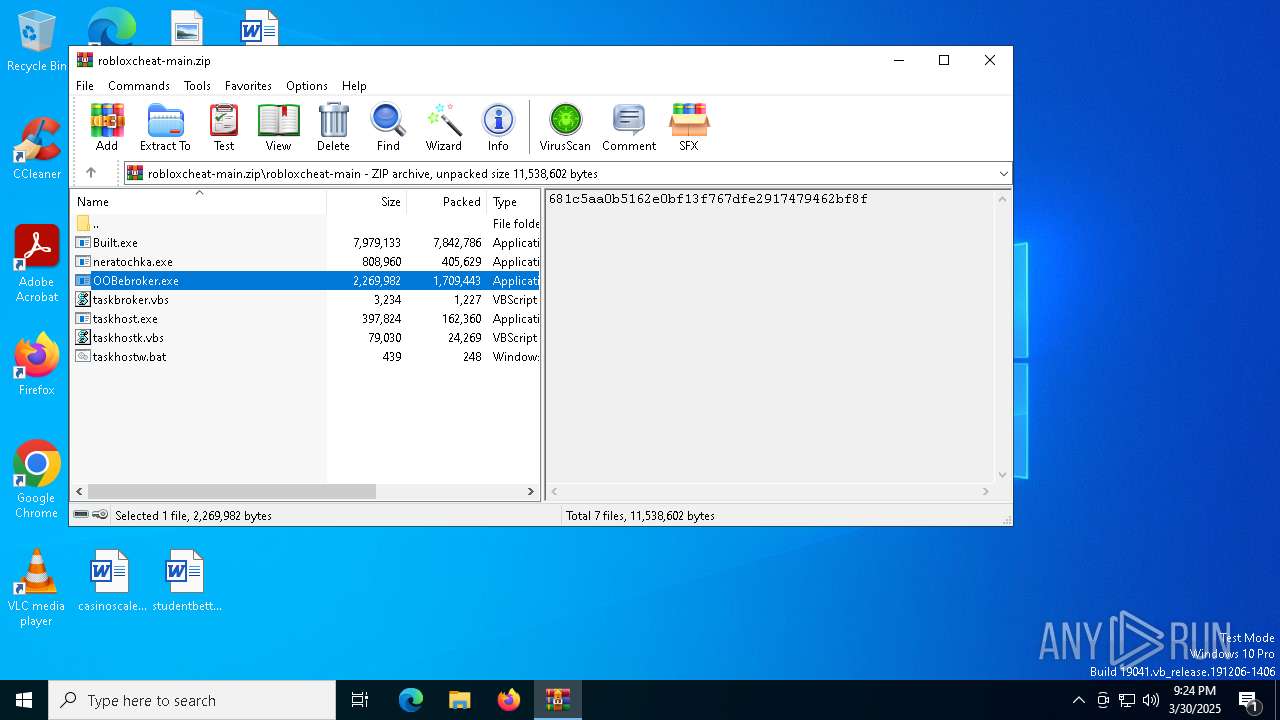
| File name: | robloxcheat-main.zip |
| Full analysis: | https://app.any.run/tasks/9e21a754-f2c0-4329-aa2a-d12f3c58f105 |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | March 30, 2025, 21:21:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | BD17F6D58DB7C08D4DE545D02B679108 |
| SHA1: | 83DAA43F9ABDA34C77F8370D537CA1090B4458FB |
| SHA256: | 9CBA95F358B2D0FD37B8FB2266253AB9323FFD889351C8F06CE2B1626C4A08B9 |
| SSDEEP: | 98304:UvXEhdjj8YlIUw+mfnfp7tO/bFWugjowVGOVVDOZPUCEKgtb020LknrWvbQfH6eF:XOcatoWQvMuRcJqQXcVbE |
MALICIOUS
Disables Windows Defender
- wscript.exe (PID: 6644)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 6644)
Changes settings for real-time protection
- powershell.exe (PID: 516)
- powershell.exe (PID: 8660)
Changes Windows Defender settings
- wscript.exe (PID: 6644)
- cmd.exe (PID: 5504)
- cmd.exe (PID: 8296)
- serverhost.exe (PID: 5408)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 5200)
- powershell.exe (PID: 8660)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 6036)
- powershell.exe (PID: 8660)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 728)
- powershell.exe (PID: 8660)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 8660)
Adds path to the Windows Defender exclusion list
- wscript.exe (PID: 6644)
- Built.exe (PID: 2148)
- cmd.exe (PID: 5504)
- serverhost.exe (PID: 5408)
UAC/LUA settings modification
- wscript.exe (PID: 6644)
Executing a file with an untrusted certificate
- Built.exe (PID: 968)
- Built.exe (PID: 8432)
- Built.exe (PID: 7180)
- Built.exe (PID: 2148)
BlankGrabber has been detected
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 684)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 7788)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 8296)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 8660)
Changes Controlled Folder Access settings
- powershell.exe (PID: 8660)
Steals credentials from Web Browsers
- Built.exe (PID: 2148)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7400)
Actions looks like stealing of personal data
- Built.exe (PID: 2148)
Bypass execution policy to execute commands
- powershell.exe (PID: 7628)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 4608)
SHEETRAT mutex has been found
- neratochka.exe (PID: 8476)
BLANKGRABBER has been detected (SURICATA)
- Built.exe (PID: 2148)
Starts CMD.EXE for self-deleting
- Built.exe (PID: 2148)
Changes the login/logoff helper path in the registry
- neratochka.exe (PID: 8476)
- serverhost.exe (PID: 5408)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 7148)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7412)
- cmd.exe (PID: 9048)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 7748)
- cmd.exe (PID: 8384)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 5984)
- cmd.exe (PID: 4244)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 1672)
- cmd.exe (PID: 8688)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7396)
- cmd.exe (PID: 8900)
- cmd.exe (PID: 8364)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 7504)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 3012)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 8052)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 6760)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 7472)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 5624)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 8796)
- cmd.exe (PID: 516)
- cmd.exe (PID: 7312)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 8156)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 5740)
- cmd.exe (PID: 8856)
- cmd.exe (PID: 7612)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 7328)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7264)
DCRAT mutex has been found
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
- sihost.exe (PID: 7224)
Changes the autorun value in the registry
- serverhost.exe (PID: 5408)
DARKCRYSTAL has been detected (SURICATA)
- sihost.exe (PID: 7224)
Connects to the CnC server
- sihost.exe (PID: 7224)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3332)
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
- serverhost.exe (PID: 5408)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 4988)
- wscript.exe (PID: 6644)
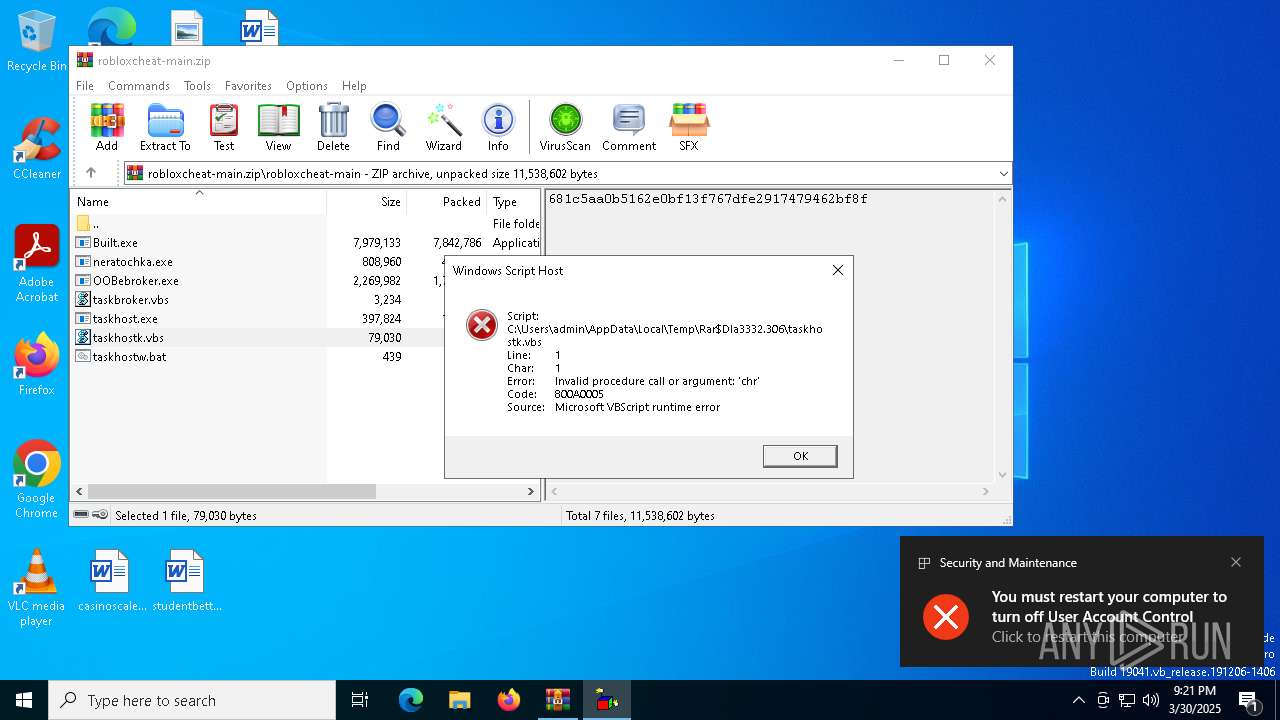
The process executes VB scripts
- wscript.exe (PID: 4988)
- WinRAR.exe (PID: 3332)
Application launched itself
- wscript.exe (PID: 4988)
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
- neratochka.exe (PID: 4628)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4988)
- wscript.exe (PID: 6644)
- wscript.exe (PID: 7264)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3332)
- ShellExperienceHost.exe (PID: 7896)
- neratochka.exe (PID: 4628)
- OOBebroker.exe (PID: 684)
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6644)
- cmd.exe (PID: 5504)
- cmd.exe (PID: 8296)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 7400)
- cmd.exe (PID: 8644)
- cmd.exe (PID: 6136)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 8712)
- serverhost.exe (PID: 5408)
Script disables Windows Defender's real-time protection
- wscript.exe (PID: 6644)
- cmd.exe (PID: 8296)
Script disables Windows Defender's behavior monitoring
- wscript.exe (PID: 6644)
Script adds exclusion path to Windows Defender
- wscript.exe (PID: 6644)
- cmd.exe (PID: 5504)
- serverhost.exe (PID: 5408)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 6644)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3332)
- OOBebroker.exe (PID: 684)
- serverhost.exe (PID: 5408)
Starts a Microsoft application from unusual location
- Built.exe (PID: 968)
- Built.exe (PID: 8432)
- Built.exe (PID: 7180)
- Built.exe (PID: 2148)
Executable content was dropped or overwritten
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
- csc.exe (PID: 8452)
- neratochka.exe (PID: 8476)
- OOBebroker.exe (PID: 684)
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
- csc.exe (PID: 8492)
- csc.exe (PID: 5084)
- csc.exe (PID: 7172)
- sihost.exe (PID: 7224)
The process drops C-runtime libraries
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2656)
- cmd.exe (PID: 8260)
- cmd.exe (PID: 4108)
Process drops python dynamic module
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
Starts CMD.EXE for commands execution
- Built.exe (PID: 8432)
- Built.exe (PID: 2148)
- neratochka.exe (PID: 8476)
- wscript.exe (PID: 7264)
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
Changes default file association
- reg.exe (PID: 684)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 6136)
- cmd.exe (PID: 7508)
Found strings related to reading or modifying Windows Defender settings
- Built.exe (PID: 8432)
- Built.exe (PID: 2148)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7492)
Get information on the list of running processes
- Built.exe (PID: 2148)
- cmd.exe (PID: 7416)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 3240)
Script disables Windows Defender's IPS
- cmd.exe (PID: 8296)
Starts application with an unusual extension
- cmd.exe (PID: 7316)
- cmd.exe (PID: 8228)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 7596)
- cmd.exe (PID: 8872)
- cmd.exe (PID: 8816)
- cmd.exe (PID: 6404)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7400)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7356)
Base64-obfuscated command line is found
- cmd.exe (PID: 7400)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7400)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6080)
- cmd.exe (PID: 5200)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 8732)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8452)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 7628)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7524)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7244)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 4408)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7460)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 616)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 300)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 8436)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Built.exe (PID: 2148)
Hides command output
- cmd.exe (PID: 4652)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 4652)
- cmd.exe (PID: 6404)
Reads the date of Windows installation
- neratochka.exe (PID: 4628)
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
Checks for external IP
- svchost.exe (PID: 2196)
- Built.exe (PID: 2148)
Connects to unusual port
- neratochka.exe (PID: 8476)
Executing commands from a ".bat" file
- wscript.exe (PID: 7264)
- serverhost.exe (PID: 5408)
Executed via WMI
- schtasks.exe (PID: 8996)
- schtasks.exe (PID: 8972)
- schtasks.exe (PID: 9000)
- schtasks.exe (PID: 9108)
- schtasks.exe (PID: 7732)
- schtasks.exe (PID: 7532)
- schtasks.exe (PID: 8424)
- schtasks.exe (PID: 4012)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 3300)
- schtasks.exe (PID: 8124)
- schtasks.exe (PID: 7432)
- schtasks.exe (PID: 6800)
- schtasks.exe (PID: 6480)
- schtasks.exe (PID: 8432)
- schtasks.exe (PID: 7604)
- schtasks.exe (PID: 5588)
- schtasks.exe (PID: 1616)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 3332)
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
- serverhost.exe (PID: 5408)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3332)
Checks supported languages
- ShellExperienceHost.exe (PID: 7896)
- Built.exe (PID: 968)
- Built.exe (PID: 8432)
- Built.exe (PID: 7180)
- Built.exe (PID: 2148)
- tree.com (PID: 9024)
- tree.com (PID: 6540)
- tree.com (PID: 8840)
- tree.com (PID: 8792)
- tree.com (PID: 8264)
- tree.com (PID: 8316)
- MpCmdRun.exe (PID: 4608)
- csc.exe (PID: 8452)
- cvtres.exe (PID: 7804)
- rar.exe (PID: 7524)
- neratochka.exe (PID: 4628)
- neratochka.exe (PID: 8476)
- OOBebroker.exe (PID: 684)
- serverhost.exe (PID: 7404)
- csc.exe (PID: 8492)
- serverhost.exe (PID: 5408)
- csc.exe (PID: 5084)
- cvtres.exe (PID: 3896)
- csc.exe (PID: 9116)
- cvtres.exe (PID: 7724)
- csc.exe (PID: 7172)
- cvtres.exe (PID: 5048)
- cvtres.exe (PID: 7816)
- chcp.com (PID: 8896)
- sihost.exe (PID: 7224)
Reads the computer name
- ShellExperienceHost.exe (PID: 7896)
- Built.exe (PID: 968)
- Built.exe (PID: 7180)
- Built.exe (PID: 2148)
- MpCmdRun.exe (PID: 4608)
- neratochka.exe (PID: 4628)
- neratochka.exe (PID: 8476)
- OOBebroker.exe (PID: 684)
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
- sihost.exe (PID: 7224)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 728)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 3676)
- powershell.exe (PID: 6540)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 5800)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5200)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 1052)
- powershell.exe (PID: 6132)
- powershell.exe (PID: 8660)
- powershell.exe (PID: 7612)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 7664)
- powershell.exe (PID: 2152)
- powershell.exe (PID: 7660)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 6576)
- powershell.exe (PID: 728)
- powershell.exe (PID: 516)
- powershell.exe (PID: 5800)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 3676)
- powershell.exe (PID: 5200)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 1052)
- powershell.exe (PID: 6540)
- powershell.exe (PID: 8660)
- powershell.exe (PID: 8388)
- powershell.exe (PID: 6132)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 7660)
- powershell.exe (PID: 4892)
- powershell.exe (PID: 2152)
- powershell.exe (PID: 7612)
- powershell.exe (PID: 7664)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3332)
Create files in a temporary directory
- Built.exe (PID: 968)
- Built.exe (PID: 8432)
- Built.exe (PID: 7180)
- Built.exe (PID: 2148)
- MpCmdRun.exe (PID: 4608)
- csc.exe (PID: 8452)
- cvtres.exe (PID: 7804)
- rar.exe (PID: 7524)
- cvtres.exe (PID: 5048)
- serverhost.exe (PID: 5408)
- cvtres.exe (PID: 7724)
- cvtres.exe (PID: 3896)
- cvtres.exe (PID: 7816)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 7788)
- WMIC.exe (PID: 8732)
- WMIC.exe (PID: 4408)
- WMIC.exe (PID: 616)
- WMIC.exe (PID: 5328)
- WMIC.exe (PID: 8436)
The Powershell gets current clipboard
- powershell.exe (PID: 5392)
Checks the directory tree
- tree.com (PID: 9024)
- tree.com (PID: 6540)
- tree.com (PID: 8792)
- tree.com (PID: 8840)
- tree.com (PID: 8264)
- tree.com (PID: 8316)
Reads the machine GUID from the registry
- csc.exe (PID: 8452)
- rar.exe (PID: 7524)
- neratochka.exe (PID: 4628)
- neratochka.exe (PID: 8476)
- serverhost.exe (PID: 7404)
- csc.exe (PID: 8492)
- serverhost.exe (PID: 5408)
- csc.exe (PID: 9116)
- csc.exe (PID: 5084)
- csc.exe (PID: 7172)
- sihost.exe (PID: 7224)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 2560)
Process checks computer location settings
- neratochka.exe (PID: 4628)
- serverhost.exe (PID: 7404)
- OOBebroker.exe (PID: 684)
- serverhost.exe (PID: 5408)
Reads the software policy settings
- slui.exe (PID: 7608)
Checks proxy server information
- slui.exe (PID: 7608)
- sihost.exe (PID: 7224)
Autorun file from Task Scheduler
- cmd.exe (PID: 9048)
- cmd.exe (PID: 7748)
- cmd.exe (PID: 7412)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 8384)
- cmd.exe (PID: 6960)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 5984)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 4244)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 1672)
- cmd.exe (PID: 8688)
- cmd.exe (PID: 6036)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 7396)
- cmd.exe (PID: 8900)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 8364)
- cmd.exe (PID: 2908)
- cmd.exe (PID: 7504)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 3012)
- cmd.exe (PID: 8052)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 6760)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 7472)
- cmd.exe (PID: 5344)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 5624)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 6700)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 7548)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 516)
- cmd.exe (PID: 8796)
- cmd.exe (PID: 7312)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 8156)
- cmd.exe (PID: 5740)
- cmd.exe (PID: 8856)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 7612)
Creates files in the program directory
- neratochka.exe (PID: 8476)
- csc.exe (PID: 5084)
- csc.exe (PID: 9116)
- csc.exe (PID: 7172)
Drops encrypted VBS script (Microsoft Script Encoder)
- OOBebroker.exe (PID: 684)
Reads Environment values
- serverhost.exe (PID: 7404)
- serverhost.exe (PID: 5408)
- sihost.exe (PID: 7224)
Creates files or folders in the user directory
- csc.exe (PID: 8492)
Changes the display of characters in the console
- cmd.exe (PID: 6404)
Disables trace logs
- sihost.exe (PID: 7224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:30 07:14:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | robloxcheat-main/ |
Total processes
498
Monitored processes
368
Malicious processes
25
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\system32\cmd.exe /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | Built.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | SchTaSKs /create /f /sc minute /mo -1 /tn "Outposts" /tr "C:\Users\admin\Documents\aops.exe" /RL HIGHEST | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 2147500037 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "CMD" /c SchTaSKs /create /f /sc minute /mo -1 /tn "Outposts" /tr "C:\Users\admin\Documents\aops.exe" /RL HIGHEST & exit | C:\Windows\System32\cmd.exe | — | neratochka.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147500037 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | reg add hkcu\Software\Classes\ms-settings\shell\open\command /v "DelegateExecute" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | ping localhost -n 3 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
165 857
Read events
165 787
Write events
64
Delete events
6
Modification events
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\robloxcheat-main.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6644) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
Executable files
76
Suspicious files
47
Text files
102
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i4hoaaed.tok.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zm4bsedw.zg2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3i100wuu.3jz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5200 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4yf2heyi.wpw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 728 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uf34rw15.vsj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3332.49140\taskbroker.vbs | text | |
MD5:EC056BDC0223F3F5DF9AE591CBA9B24C | SHA256:AF65072FD228A47CC3E8A8D1461688C1B53C2EC91949B472DECBA4D97289253B | |||
| 728 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jbjyqcwu.23z.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6576 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xggu2xrt.its.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2xnslg15.bva.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_005ezkiw.nrm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
70
TCP/UDP connections
38
DNS requests
21
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8496 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8496 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2148 | Built.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7224 | sihost.exe | POST | 200 | 198.91.81.15:80 | http://bosin53q.x10.bz/cpulongpolllinuxWordpress.php | unknown | — | — | malicious |
7224 | sihost.exe | POST | 200 | 198.91.81.15:80 | http://bosin53q.x10.bz/cpulongpolllinuxWordpress.php | unknown | — | — | malicious |
7224 | sihost.exe | POST | 200 | 198.91.81.15:80 | http://bosin53q.x10.bz/cpulongpolllinuxWordpress.php | unknown | — | — | malicious |
7224 | sihost.exe | POST | 200 | 198.91.81.15:80 | http://bosin53q.x10.bz/cpulongpolllinuxWordpress.php | unknown | — | — | malicious |
7224 | sihost.exe | POST | 200 | 198.91.81.15:80 | http://bosin53q.x10.bz/cpulongpolllinuxWordpress.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
8496 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8496 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
8496 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2148 | Built.exe | 142.250.185.163:443 | gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
gstatic.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
2196 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
2148 | Built.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2148 | Built.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
2148 | Built.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.ply .gg) |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |
2196 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Tunneling Service in DNS Lookup (* .ply .gg) |