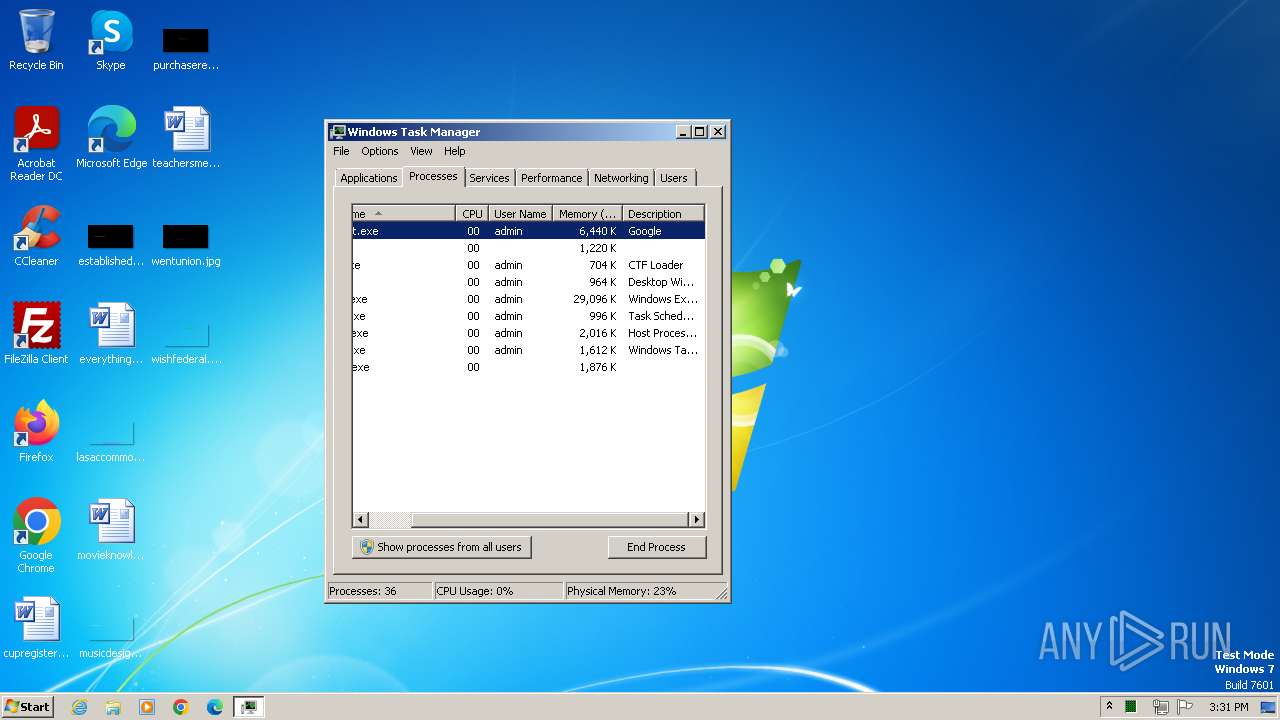
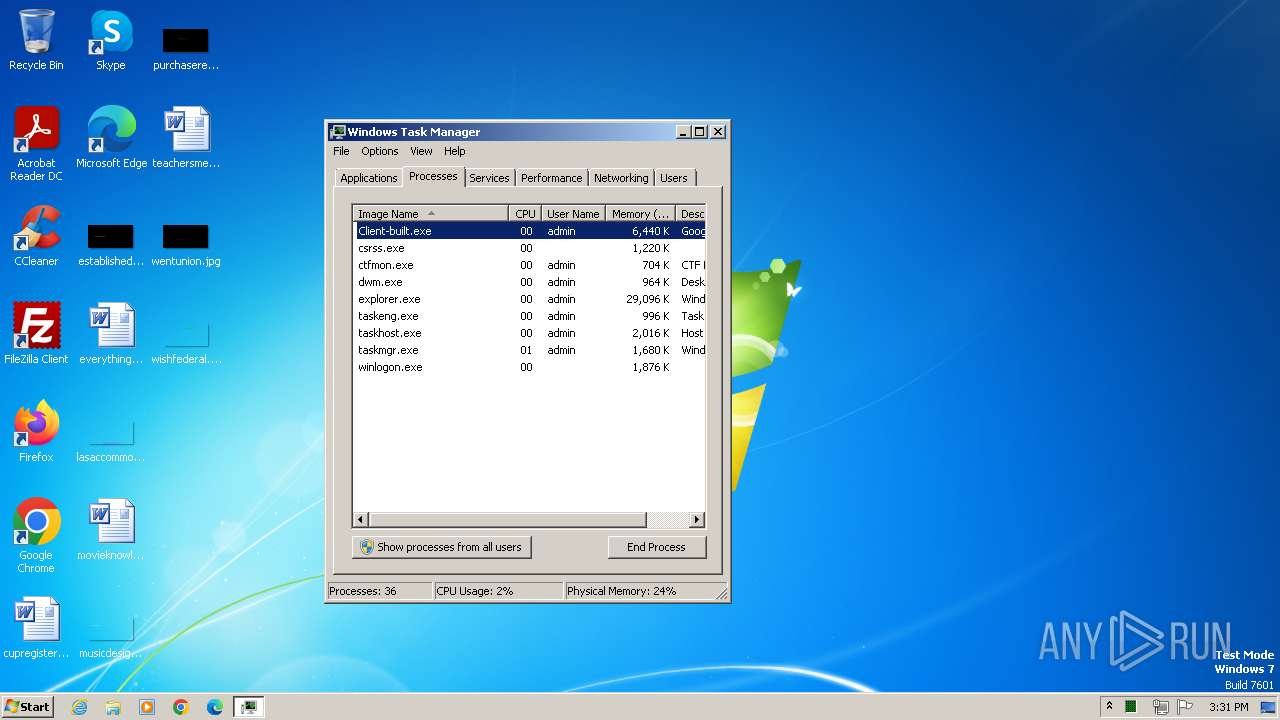
| File name: | Client-built.exe |
| Full analysis: | https://app.any.run/tasks/414d2f61-efba-4206-a8dc-f23cc0ef6171 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
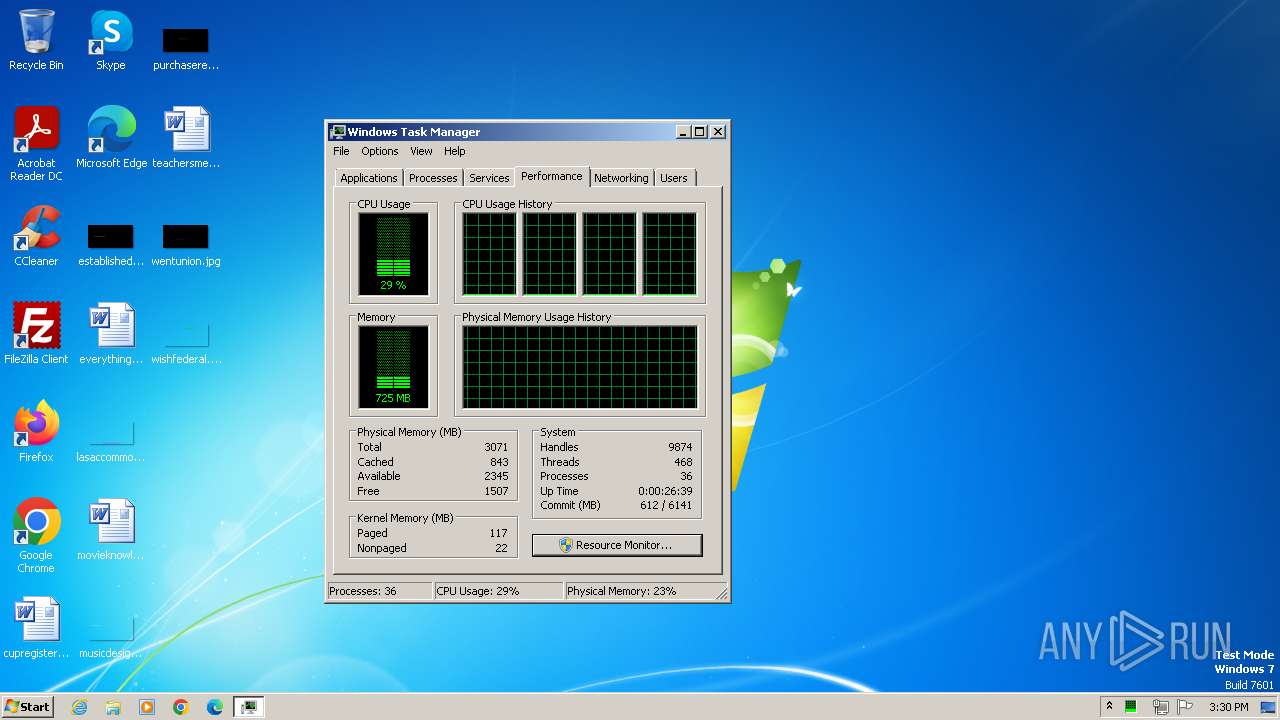
| Analysis date: | March 03, 2024, 15:30:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 3E9C711BD750D135ED317C73974FC231 |
| SHA1: | FF649E279A999BF3664055C7555225D0EB0E26C5 |
| SHA256: | 9CB34D20E19473DEBCDF1C16E92DA8C42B0D264FDAD683102C084F3CD26999A4 |
| SSDEEP: | 98304:t2nP6q3A6770DODdl/rADxRLDguHOeJHjM+F:sUgH |
MALICIOUS
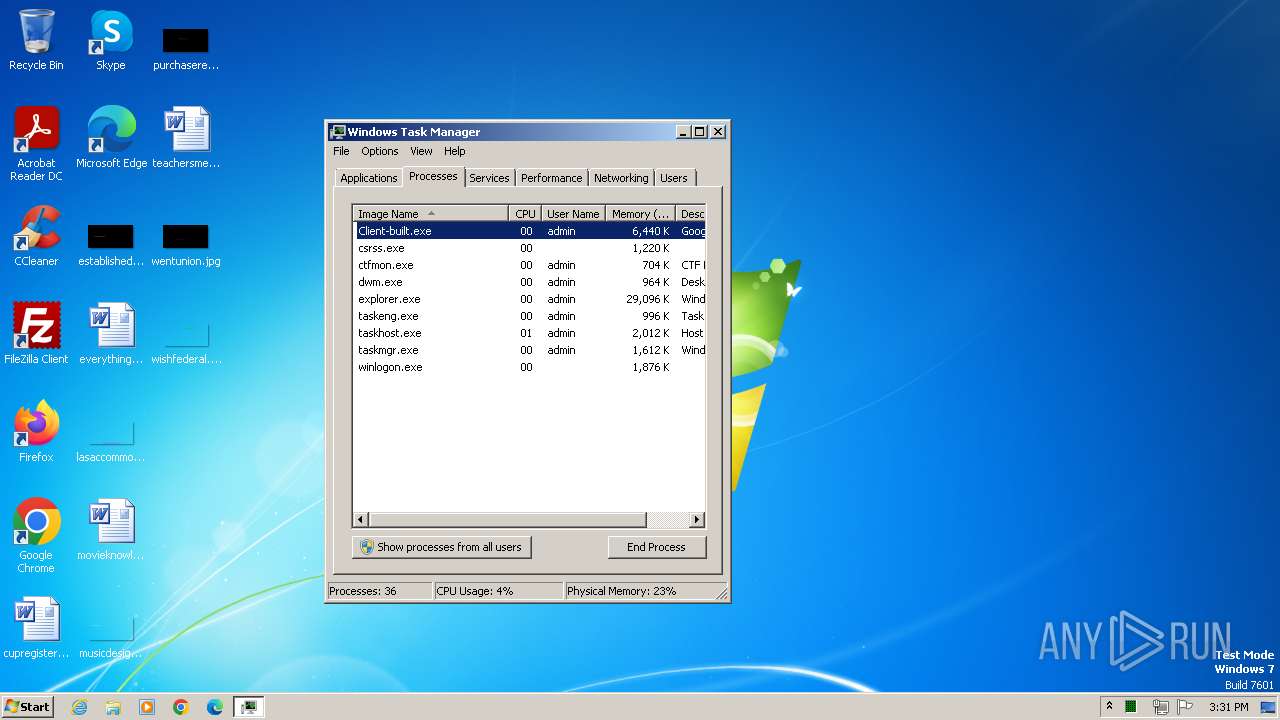
Drops the executable file immediately after the start
- Client-built.exe (PID: 2472)
QUASAR has been detected (YARA)
- Client-built.exe (PID: 2472)
SUSPICIOUS
Application launched itself
- taskmgr.exe (PID: 3304)
Reads the Internet Settings
- taskmgr.exe (PID: 3304)
INFO
Checks supported languages
- Client-built.exe (PID: 2472)
Reads the machine GUID from the registry
- Client-built.exe (PID: 2472)
Manual execution by a user
- taskmgr.exe (PID: 3304)
- explorer.exe (PID: 3952)
Reads Environment values
- Client-built.exe (PID: 2472)
Reads the computer name
- Client-built.exe (PID: 2472)
Reads security settings of Internet Explorer
- taskmgr.exe (PID: 3304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2472) Client-built.exe
Version1.4.1
C2 (2)tcp://0.tcp.ap.ngrok.io:16495
Sub_DirSubDir
Install_NameGoogleDB.exe
Mutex0cf68c40-b2d5-4f5b-9874-e8cdf8228b08
StartupGoogleDB
Tagvirus
LogDirLogs
SignatureJ6nD0vKwUbeRUMAc5A/TFMhYOP5MPDsZZ18F8ch3jaPkseOUdPKStiIt4Aj3OYlvOrKTZ0FkpOSTKrRaIy0qH/gaGMEN0sY5vX8WR3pr9i1lU8zTbOKaI0MKzdYeIgzPFoVRxbHyKX5mkoA5SUmJ8xW/bodxIxWODfFVHcUJpfBUELE52EaykKI1gIk/+einC3e1zpgNsez4ltd9VyKSY5dNOLFPSwZcsolPSik+CMxXyg+ofuICJpI/cil7BREeg2GOSywOkjssw6WaHP+WNBNNV1GyTe5ZxQhtv7+fCkzb...
CertificateMIIE9DCCAtygAwIBAgIQALZhw/kwCc12BVtsZ8SLKTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDExOTA4NTEwMFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAp26UqqHqgQP0305A5llzoSkbqaXOsIsACBgeglDh2MBNEhqLm2hf7EVtRmJ+5ZaQ3zzryqJw...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:03:12 16:16:39+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 3261440 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x31e3ce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 120.0.6099.225 |
| ProductVersionNumber: | 120.0.6099.225 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | |
| FileDescription: | |
| FileVersion: | 120.0.6099.225 |
| InternalName: | Google Chrome |
| LegalCopyright: | |
| LegalTrademarks: | Chrome™ browser |
| OriginalFileName: | Google Chrome |
| ProductName: | Chrome |
| ProductVersion: | 120.0.6099.225 |
| AssemblyVersion: | 120.0.6099.225 |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2472 | "C:\Users\admin\AppData\Local\Temp\Client-built.exe" | C:\Users\admin\AppData\Local\Temp\Client-built.exe | explorer.exe | ||||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Google Exit code: 0 Version: 120.0.6099.225 Modules
Quasar(PID) Process(2472) Client-built.exe Version1.4.1 C2 (2)tcp://0.tcp.ap.ngrok.io:16495 Sub_DirSubDir Install_NameGoogleDB.exe Mutex0cf68c40-b2d5-4f5b-9874-e8cdf8228b08 StartupGoogleDB Tagvirus LogDirLogs SignatureJ6nD0vKwUbeRUMAc5A/TFMhYOP5MPDsZZ18F8ch3jaPkseOUdPKStiIt4Aj3OYlvOrKTZ0FkpOSTKrRaIy0qH/gaGMEN0sY5vX8WR3pr9i1lU8zTbOKaI0MKzdYeIgzPFoVRxbHyKX5mkoA5SUmJ8xW/bodxIxWODfFVHcUJpfBUELE52EaykKI1gIk/+einC3e1zpgNsez4ltd9VyKSY5dNOLFPSwZcsolPSik+CMxXyg+ofuICJpI/cil7BREeg2GOSywOkjssw6WaHP+WNBNNV1GyTe5ZxQhtv7+fCkzb... CertificateMIIE9DCCAtygAwIBAgIQALZhw/kwCc12BVtsZ8SLKTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDExOTA4NTEwMFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAp26UqqHqgQP0305A5llzoSkbqaXOsIsACBgeglDh2MBNEhqLm2hf7EVtRmJ+5ZaQ3zzryqJw... | |||||||||||||||
| 3304 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3952 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3960 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\System32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 194
Read events
1 169
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2472) Client-built.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3304) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3304) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3304) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3304) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3304) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000004401000077000000DC0200005C0200000100000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000009C00000040000000210000004600000052000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000002000000010000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF02000000FFFFFFFF4F00000028000000970000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
| (PID) Process: | (3304) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |