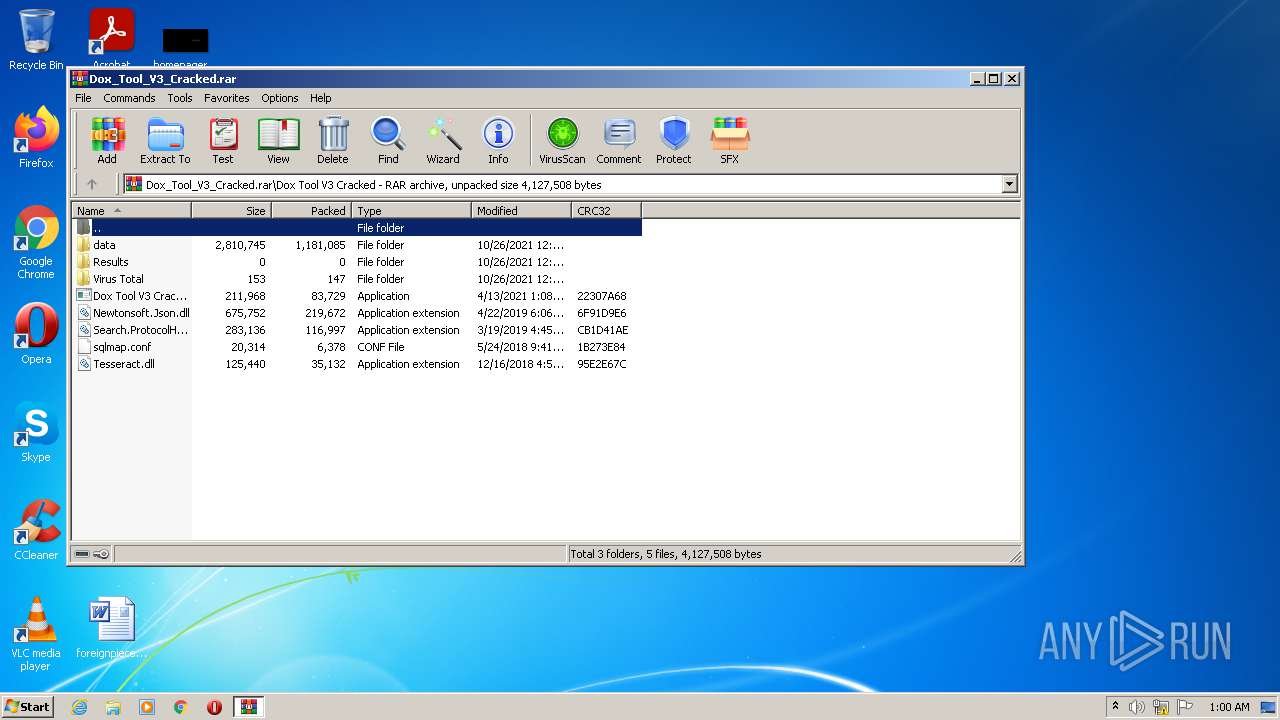
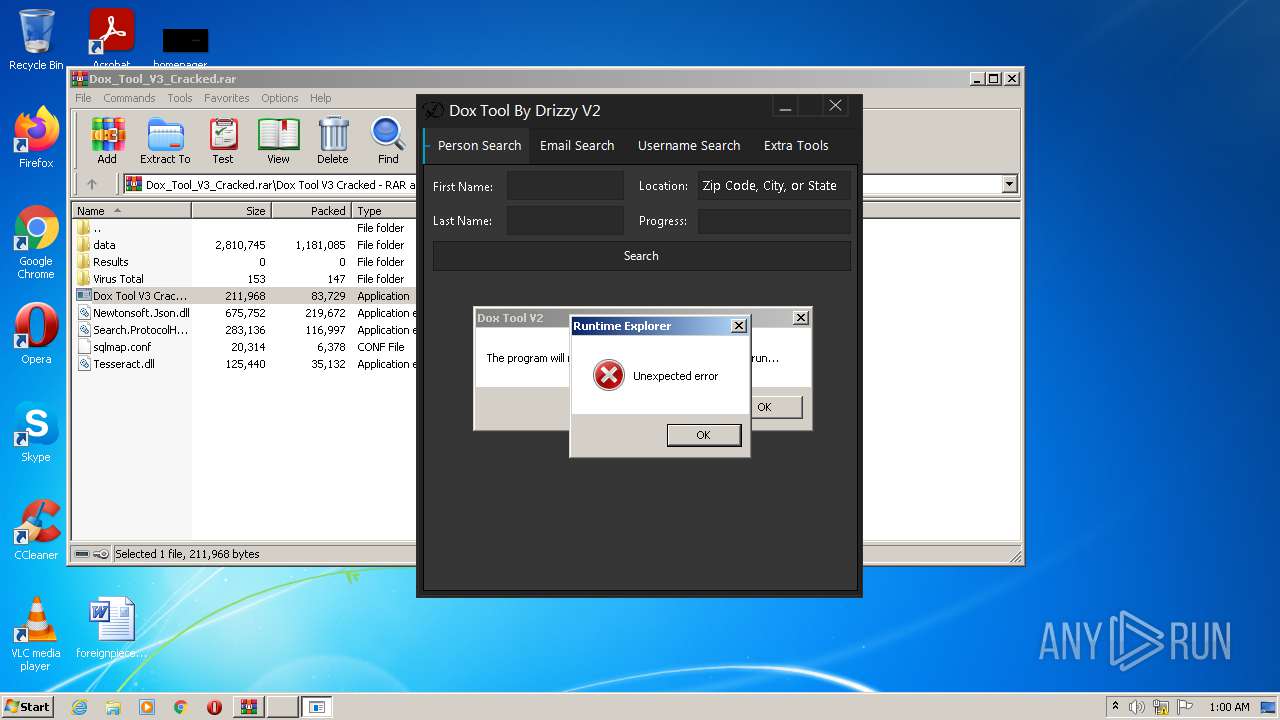
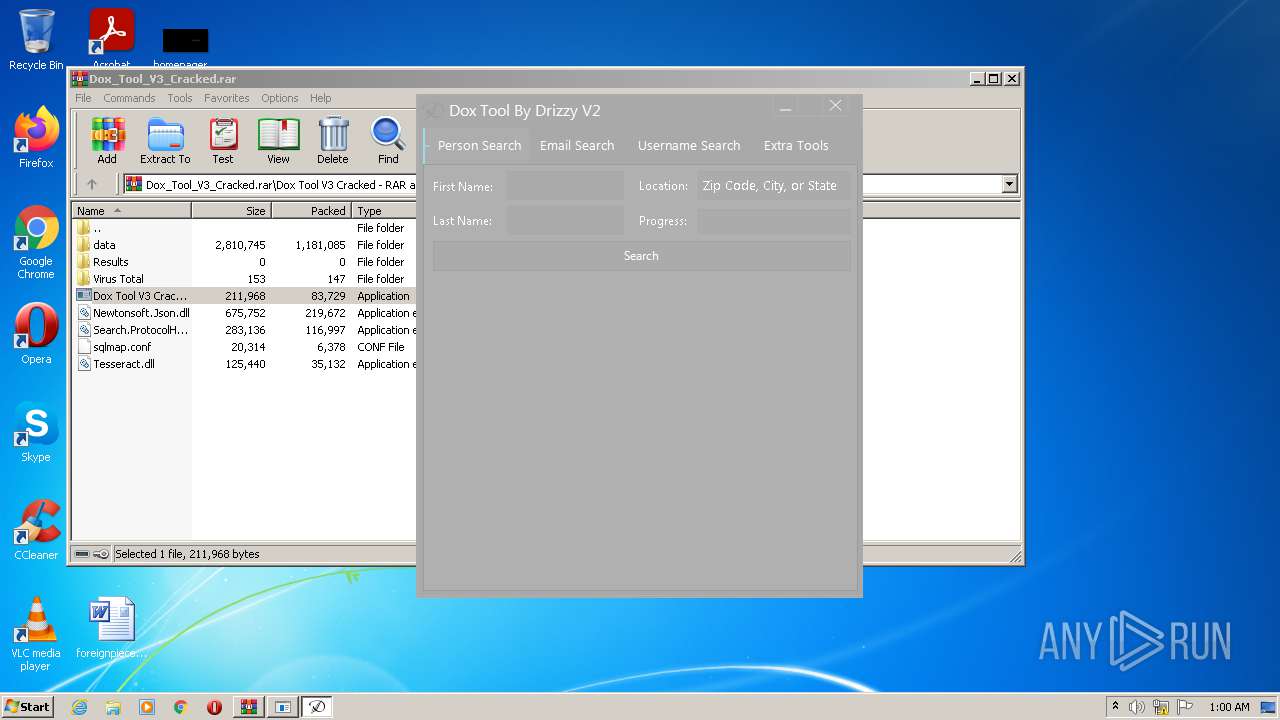
| File name: | Dox_Tool_V3_Cracked.rar |
| Full analysis: | https://app.any.run/tasks/4e1ccdea-9dba-4bb1-8628-aab9c3e34801 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | November 25, 2021, 01:00:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3644F99DDF506A39DA30126C9A0ABB6A |
| SHA1: | F04F0277FF79AEEA0D5CD0F28E8245F50A2C7D65 |
| SHA256: | 9C09DED5AE06EFDB1D52F183D70F6A3FC821618BCD60D6F4A9F0C46D20BF589A |
| SSDEEP: | 49152:cjBI5buvPNb4ah+utzurqOeJ35JwzY/yqlY:eC5SXNMKlurqxpyqa |
MALICIOUS
Application was dropped or rewritten from another process
- Launcher.exe (PID: 2332)
- Dox Tool V3 Cracked.exe (PID: 548)
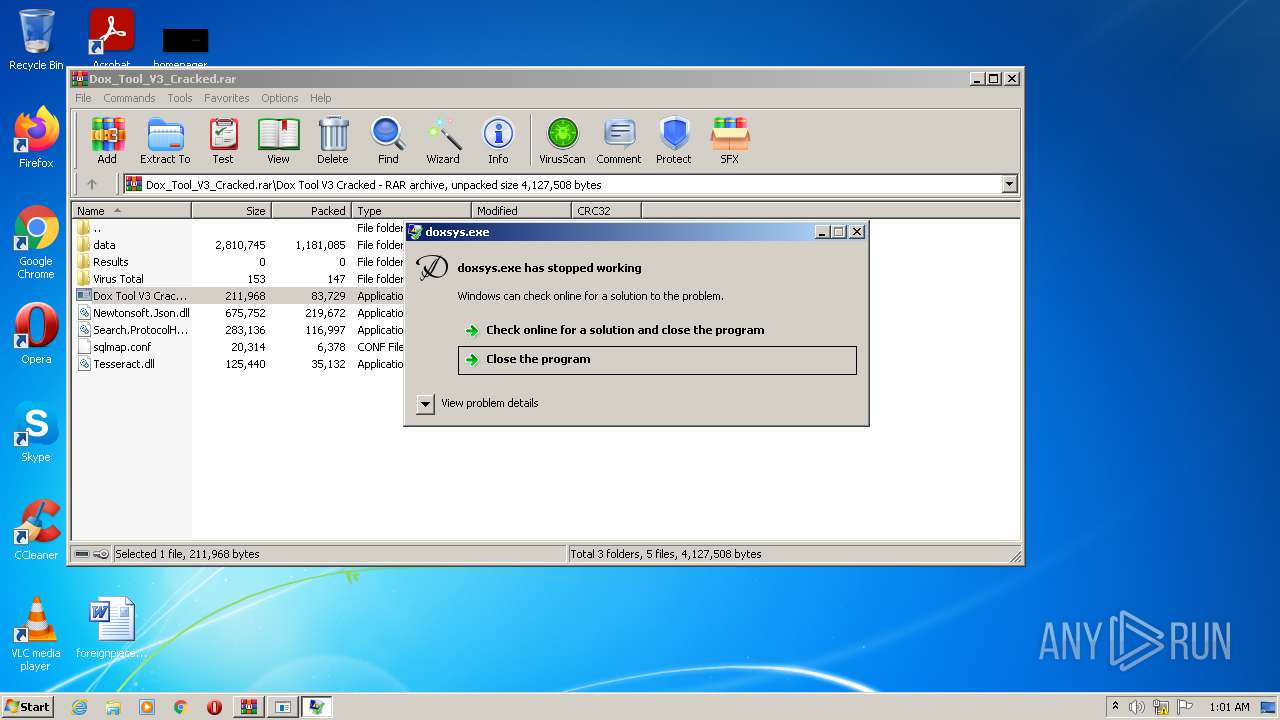
- doxsys.exe (PID: 2572)
- svchost.exe (PID: 3116)
- Windows Services.exe (PID: 2464)
- Secure System Shell.exe (PID: 2856)
- Runtime Explorer.exe (PID: 3784)
- Runtime Explorer.exe (PID: 1984)
- Dox Tool V3 Cracked.exe (PID: 1792)
- DOX.exe (PID: 1104)
- WindowsUpdate.exe (PID: 2128)
- SystemUpdate.exe (PID: 444)
- Runtime Explorer.exe (PID: 3232)
- Runtime Explorer.exe (PID: 2240)
- Runtime Explorer.exe (PID: 2572)
- Runtime Explorer.exe (PID: 3716)
- Runtime Explorer.exe (PID: 3132)
- Runtime Explorer.exe (PID: 2544)
- Runtime Explorer.exe (PID: 2604)
- HQUHlwGxWA.exe (PID: 2700)
- Dox Tool V3 Cracked.exe (PID: 3472)
- Runtime Explorer.exe (PID: 2264)
- doxsys.exe (PID: 3048)
- Launcher.exe (PID: 2940)
- svchost.exe (PID: 1232)
- HQUHlwGxWA.exe (PID: 1032)
Loads dropped or rewritten executable
- Launcher.exe (PID: 2332)
- HQUHlwGxWA.exe (PID: 2700)
- Launcher.exe (PID: 2940)
- HQUHlwGxWA.exe (PID: 1032)
Drops executable file immediately after starts
- doxsys.exe (PID: 2572)
- Dox Tool V3 Cracked.exe (PID: 1792)
Drops/Copies Quasar RAT executable
- Dox Tool V3 Cracked.exe (PID: 1792)
- WindowsUpdate.exe (PID: 2128)
Writes to a start menu file
- Launcher.exe (PID: 2332)
Changes the autorun value in the registry
- Launcher.exe (PID: 2332)
- svchost.exe (PID: 1232)
Uses Task Scheduler to autorun other applications
- WindowsUpdate.exe (PID: 2128)
- SystemUpdate.exe (PID: 444)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 4004)
- schtasks.exe (PID: 2928)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3652)
- doxsys.exe (PID: 2572)
- Dox Tool V3 Cracked.exe (PID: 1792)
- Launcher.exe (PID: 2332)
- WindowsUpdate.exe (PID: 2128)
- svchost.exe (PID: 3116)
- svchost.exe (PID: 1232)
Checks supported languages
- WinRAR.exe (PID: 3652)
- Dox Tool V3 Cracked.exe (PID: 548)
- Launcher.exe (PID: 2332)
- powershell.exe (PID: 3852)
- doxsys.exe (PID: 2572)
- svchost.exe (PID: 3116)
- WindowsUpdate.exe (PID: 2128)
- Dox Tool V3 Cracked.exe (PID: 1792)
- DOX.exe (PID: 1104)
- Windows Services.exe (PID: 2464)
- Secure System Shell.exe (PID: 2856)
- Runtime Explorer.exe (PID: 3784)
- SystemUpdate.exe (PID: 444)
- Runtime Explorer.exe (PID: 1984)
- Runtime Explorer.exe (PID: 3232)
- Runtime Explorer.exe (PID: 2544)
- Runtime Explorer.exe (PID: 2572)
- Runtime Explorer.exe (PID: 3716)
- Runtime Explorer.exe (PID: 2240)
- Runtime Explorer.exe (PID: 3132)
- Runtime Explorer.exe (PID: 2604)
- Runtime Explorer.exe (PID: 2264)
- HQUHlwGxWA.exe (PID: 2700)
- dw20.exe (PID: 3628)
- doxsys.exe (PID: 3048)
- Dox Tool V3 Cracked.exe (PID: 3472)
- Launcher.exe (PID: 2940)
- svchost.exe (PID: 1232)
- HQUHlwGxWA.exe (PID: 1032)
Reads the computer name
- Dox Tool V3 Cracked.exe (PID: 548)
- WinRAR.exe (PID: 3652)
- Launcher.exe (PID: 2332)
- powershell.exe (PID: 3852)
- doxsys.exe (PID: 2572)
- svchost.exe (PID: 3116)
- WindowsUpdate.exe (PID: 2128)
- DOX.exe (PID: 1104)
- Dox Tool V3 Cracked.exe (PID: 1792)
- Windows Services.exe (PID: 2464)
- Secure System Shell.exe (PID: 2856)
- SystemUpdate.exe (PID: 444)
- HQUHlwGxWA.exe (PID: 2700)
- dw20.exe (PID: 3628)
- svchost.exe (PID: 1232)
- Launcher.exe (PID: 2940)
- Dox Tool V3 Cracked.exe (PID: 3472)
- HQUHlwGxWA.exe (PID: 1032)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3652)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3652)
- Dox Tool V3 Cracked.exe (PID: 1792)
- svchost.exe (PID: 3116)
- svchost.exe (PID: 1232)
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3652)
Executes PowerShell scripts
- Launcher.exe (PID: 2332)
Creates executable files which already exist in Windows
- doxsys.exe (PID: 2572)
Reads Environment values
- svchost.exe (PID: 3116)
- WindowsUpdate.exe (PID: 2128)
- DOX.exe (PID: 1104)
- SystemUpdate.exe (PID: 444)
- svchost.exe (PID: 1232)
Creates files in the user directory
- Launcher.exe (PID: 2332)
- SystemUpdate.exe (PID: 444)
- svchost.exe (PID: 1232)
Creates files in the Windows directory
- WindowsUpdate.exe (PID: 2128)
- Launcher.exe (PID: 2332)
Starts itself from another location
- WindowsUpdate.exe (PID: 2128)
- svchost.exe (PID: 3116)
Checks for external IP
- WindowsUpdate.exe (PID: 2128)
- SystemUpdate.exe (PID: 444)
- svchost.exe (PID: 3116)
- svchost.exe (PID: 1232)
Searches for installed software
- svchost.exe (PID: 3116)
- svchost.exe (PID: 1232)
INFO
Checks Windows Trust Settings
- powershell.exe (PID: 3852)
Reads settings of System Certificates
- powershell.exe (PID: 3852)
Dropped object may contain Bitcoin addresses
- Launcher.exe (PID: 2332)
Checks supported languages
- schtasks.exe (PID: 4004)
- schtasks.exe (PID: 2928)
Reads the computer name
- schtasks.exe (PID: 4004)
- schtasks.exe (PID: 2928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
77
Monitored processes
31
Malicious processes
20
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Windows\system32\SubDir\SystemUpdate.exe" | C:\Windows\system32\SubDir\SystemUpdate.exe | WindowsUpdate.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\Dox Tool V3 Cracked.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\Dox Tool V3 Cracked.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1032 | "C:\Users\admin\AppData\Local\Temp\HQUHlwGxWA.exe" | C:\Users\admin\AppData\Local\Temp\HQUHlwGxWA.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.0.6473.36168 Modules
| |||||||||||||||
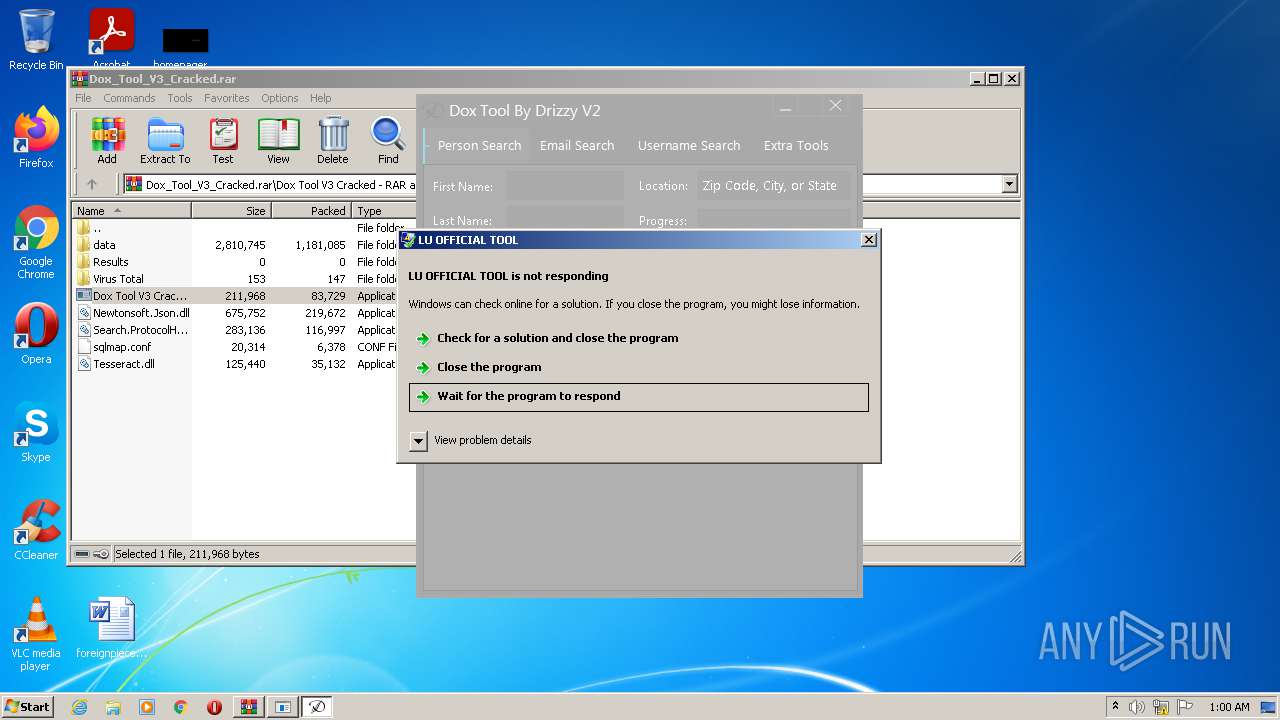
| 1104 | "C:\Users\admin\AppData\Local\Temp\DOX.exe" | C:\Users\admin\AppData\Local\Temp\DOX.exe | Dox Tool V3 Cracked.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: LU OFFICIAL TOOL Exit code: 3489660927 Version: 1.0 Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\AppData\Roaming\svchost.exe" C:\Users\admin\AppData\Local\Temp\svchost.exe | C:\Users\admin\AppData\Roaming\svchost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft @ 2015 Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\AppData\Local\Temp\Dox Tool V3 Cracked.exe" | C:\Users\admin\AppData\Local\Temp\Dox Tool V3 Cracked.exe | doxsys.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1984 | "C:\Windows\IMF\Runtime Explorer.exe" | C:\Windows\IMF\Runtime Explorer.exe | — | Windows Services.exe | |||||||||||
User: admin Company: Microsoft Windows Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2128 | "C:\Users\admin\AppData\Local\Temp\WindowsUpdate.exe" | C:\Users\admin\AppData\Local\Temp\WindowsUpdate.exe | Dox Tool V3 Cracked.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.3.0.0 Modules
| |||||||||||||||
| 2240 | "C:\Windows\IMF\Runtime Explorer.exe" | C:\Windows\IMF\Runtime Explorer.exe | — | Windows Services.exe | |||||||||||
User: admin Company: Microsoft Windows Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2264 | "C:\Windows\IMF\Runtime Explorer.exe" | C:\Windows\IMF\Runtime Explorer.exe | — | Windows Services.exe | |||||||||||
User: admin Company: Microsoft Windows Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
14 849
Read events
14 693
Write events
156
Delete events
0
Modification events
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Dox_Tool_V3_Cracked.rar | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
36
Suspicious files
16
Text files
9
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\data\LICENCE.dat | compressed | |
MD5:— | SHA256:— | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\data\Search.ProtocolHandler.MAPI2.dll | executable | |
MD5:1EFF11CED2866665F101892E9D097D14 | SHA256:A90C1A13965F534565F98B4A7C0DE5804B35482E9668F3D60DF8A1C039E51AD9 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\data\Launcher.exe | executable | |
MD5:C6D4C881112022EB30725978ECD7C6EC | SHA256:0D87B9B141A592711C52E7409EC64DE3AB296CDDC890BE761D9AF57CEA381B32 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\data\Newtonsoft.Json.dll | executable | |
MD5:4DF6C8781E70C3A4912B5BE796E6D337 | SHA256:3598CCCAD5B535FEA6F93662107A4183BFD6167BF1D0F80260436093EDC2E3AF | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\Virus Total\scan.txt | text | |
MD5:2E99FBAF1AD4F921EBE1BA0ADB710C25 | SHA256:F2F02C614C4A88B423AD0A404F7F5E7C1D33C5445E75F3D6F651AE6E791CDD57 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\Search.ProtocolHandler.MAPI2.dll | executable | |
MD5:1EFF11CED2866665F101892E9D097D14 | SHA256:A90C1A13965F534565F98B4A7C0DE5804B35482E9668F3D60DF8A1C039E51AD9 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\Dox Tool V3 Cracked.exe | executable | |
MD5:6C206CADF297A02C0AF977C65637A166 | SHA256:F4F78F44719AF71A363BD50107840F53F8EEBF3190505C10BAC2CF7BE3C29E59 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\data\Tesseract.dll | executable | |
MD5:8EEF5F1C4E31C2B9A240A906D87AC0C4 | SHA256:118C10D00E5B366CDEF45E334FF928513A3C6E1F55D19DEB3A1527796C5CA3B4 | |||
| 3652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3652.18599\Dox Tool V3 Cracked\Virus Total\desktop.ini | ini | |
MD5:C279803B27F13369AA54FC9B84B72468 | SHA256:D80758A34364CAB9DE42FF6ED57BCC753A0936DDDDF9952C5B4FB9FF0D7966C9 | |||
| 3852 | powershell.exe | C:\Users\admin\AppData\Local\Temp\h2xmrb1o.dhs.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
12
DNS requests
5
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2128 | WindowsUpdate.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 257 b | malicious |
3116 | svchost.exe | GET | 200 | 104.18.115.97:80 | http://icanhazip.com/ | US | text | 13 b | shared |
1232 | svchost.exe | GET | 404 | 162.243.129.169:80 | http://puu.sh/jMSLc.txt | US | text | 30 b | shared |
1232 | svchost.exe | GET | 200 | 104.18.115.97:80 | http://icanhazip.com/ | US | text | 13 b | shared |
444 | SystemUpdate.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 257 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3116 | svchost.exe | 162.243.129.169:80 | puu.sh | Digital Ocean, Inc. | US | suspicious |
2128 | WindowsUpdate.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
— | — | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
1104 | DOX.exe | 104.21.66.166:80 | drizzybot.com | Cloudflare Inc | US | suspicious |
— | — | 192.168.100.108:52173 | — | — | — | malicious |
1232 | svchost.exe | 162.243.129.169:80 | puu.sh | Digital Ocean, Inc. | US | suspicious |
— | — | 192.168.100.108:52855 | — | — | — | malicious |
— | — | 192.168.100.108:53206 | — | — | — | malicious |
1232 | svchost.exe | 104.18.115.97:80 | icanhazip.com | Cloudflare Inc | US | malicious |
3116 | svchost.exe | 104.18.115.97:80 | icanhazip.com | Cloudflare Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
puu.sh |
| shared |
ip-api.com |
| malicious |
drizzybot.com |
| malicious |
dns.msftncsi.com |
| shared |
icanhazip.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
444 | SystemUpdate.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
444 | SystemUpdate.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
1232 | svchost.exe | Potentially Bad Traffic | ET INFO GET to Puu.sh for TXT File with Minimal Headers |
1232 | svchost.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
2 ETPRO signatures available at the full report