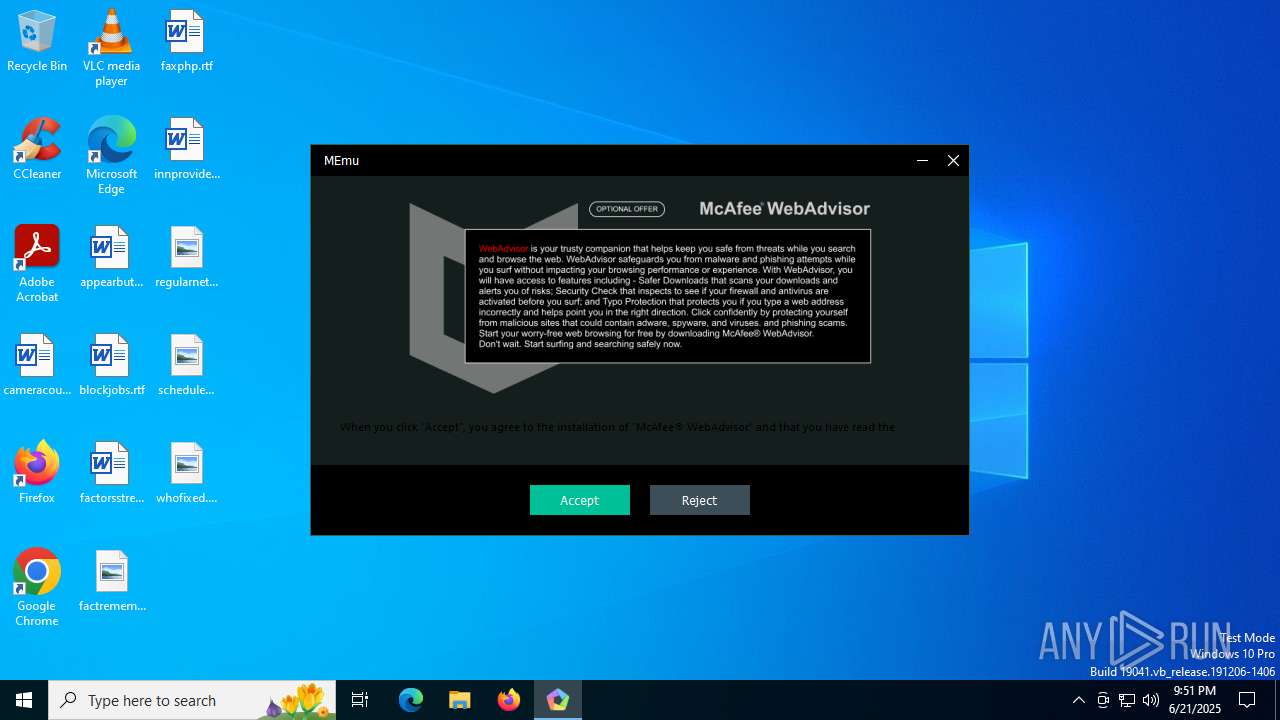
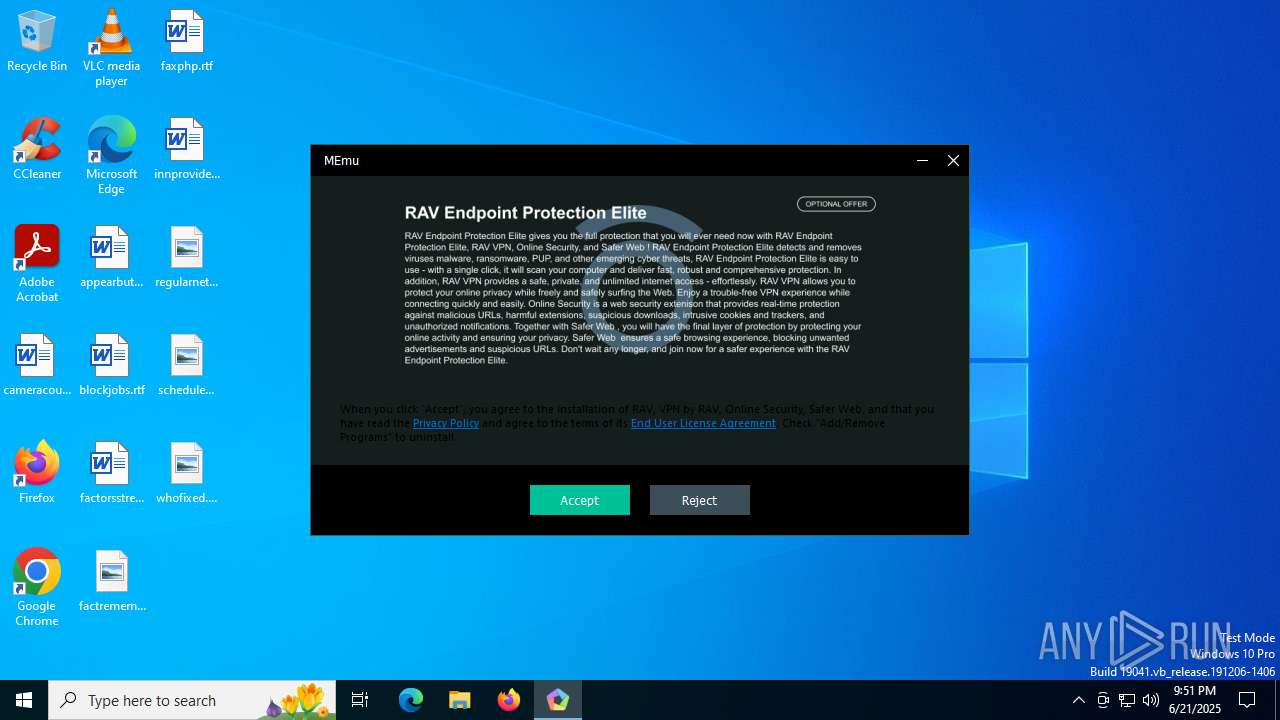
| URL: | https://www.memuplay.com/download-roblox-mod-menu-on-pc.html |
| Full analysis: | https://app.any.run/tasks/4663c7a4-7287-4f51-8e32-767f8d7d0a60 |
| Verdict: | Malicious activity |
| Threats: | First identified in 2024, Emmenhtal operates by embedding itself within modified legitimate Windows binaries, often using HTA (HTML Application) files to execute malicious scripts. It has been linked to the distribution of malware such as CryptBot and Lumma Stealer. Emmenhtal is typically disseminated through phishing campaigns, including fake video downloads and deceptive email attachments. |
| Analysis date: | June 21, 2025, 21:51:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8A05904013182FDB0806E96576E5D783 |
| SHA1: | 9E58A06E5F57187B0BC9E80EA6B1FBAC9BAC7A0A |
| SHA256: | 9C084817B95F0A7F582DFCAD9E1BDBDFF4FAC3897A1D9B2A36FBAEB8F35FE932 |
| SSDEEP: | 3:N8DSLdZ38JXm3gK8qNGn:2OLdZM8TQ |
MALICIOUS
Executing a file with an untrusted certificate
- MEmuDrvInst.exe (PID: 1332)
- MemuService.exe (PID: 10040)
Registers / Runs the DLL via REGSVR32.EXE
- Setup.exe (PID: 7724)
Changes the autorun value in the registry
- rundll32.exe (PID: 5652)
EMMENHTAL has been detected (YARA)
- rsEngineSvc.exe (PID: 6896)
METASTEALER has been detected (YARA)
- rsEngineSvc.exe (PID: 6896)
ICEDID has been detected (YARA)
- servicehost.exe (PID: 7052)
- uihost.exe (PID: 7908)
Scans artifacts that could help determine the target
- rsEDRSvc.exe (PID: 8532)
SUSPICIOUS
Executable content was dropped or overwritten
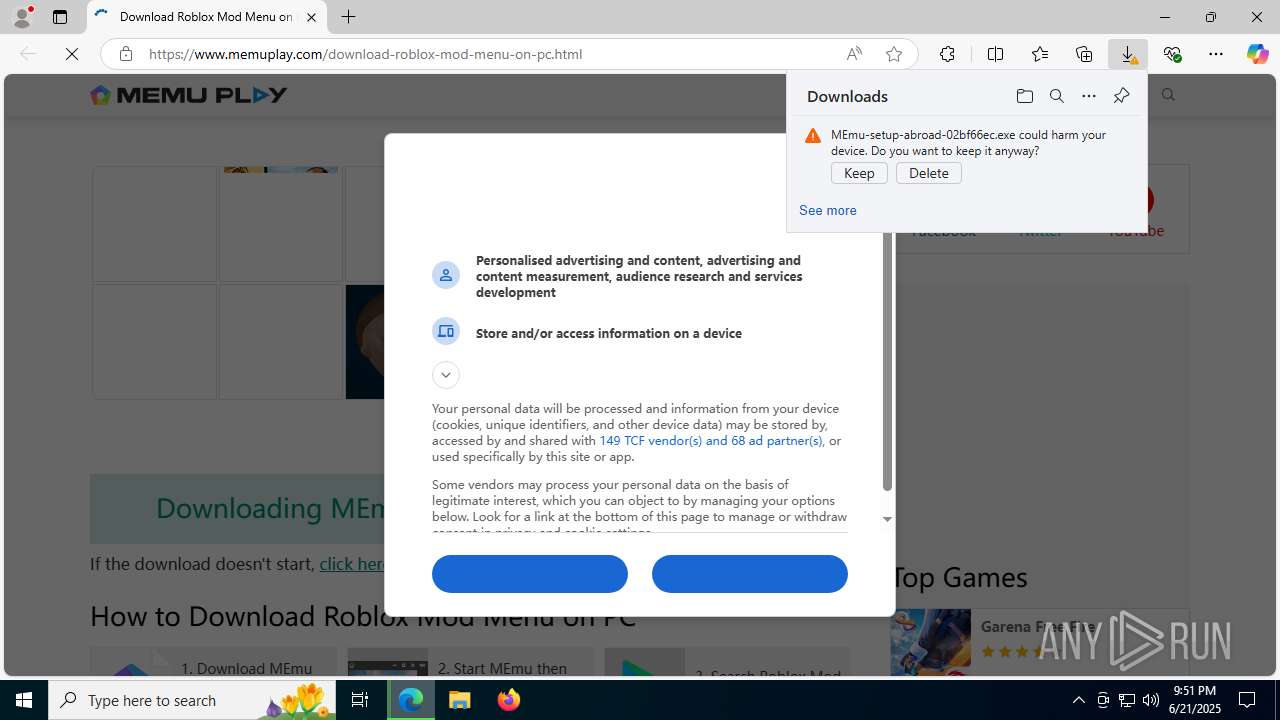
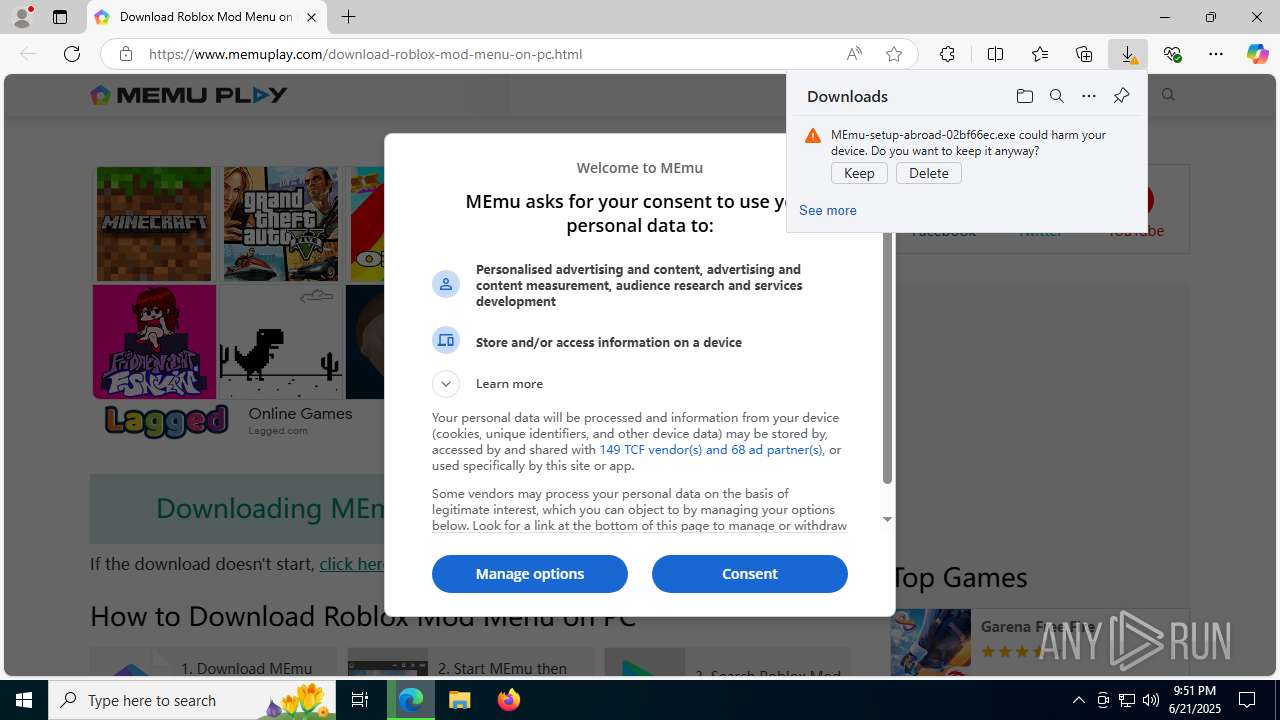
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- pcran05d.exe (PID: 8052)
- saBSI.exe (PID: 2716)
- saBSI.exe (PID: 3944)
- UnifiedStub-installer.exe (PID: 5480)
- installer.exe (PID: 2604)
- installer.exe (PID: 6472)
- Setup.exe (PID: 7724)
- 7za.exe (PID: 6140)
- 7za.exe (PID: 8432)
- 7za.exe (PID: 8256)
- MEmuDrvInst.exe (PID: 1332)
Potential Corporate Privacy Violation
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
Reads security settings of Internet Explorer
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- saBSI.exe (PID: 2716)
- rsStubActivator.exe (PID: 6104)
- saBSI.exe (PID: 3944)
- installer.exe (PID: 6472)
- UnifiedStub-installer.exe (PID: 5480)
- rsWSC.exe (PID: 6836)
- rsEngineSvc.exe (PID: 3736)
- uihost.exe (PID: 7908)
- rsEDRSvc.exe (PID: 7296)
- MEmuDrvInst.exe (PID: 1332)
- rsVPNSvc.exe (PID: 6304)
- rsDNSSvc.exe (PID: 10008)
- rsDNSSvc.exe (PID: 10096)
Process requests binary or script from the Internet
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
There is functionality for taking screenshot (YARA)
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- Setup.exe (PID: 7724)
- uihost.exe (PID: 7908)
Reads the date of Windows installation
- rsStubActivator.exe (PID: 6104)
- rsEDRSvc.exe (PID: 8532)
- rsEngineSvc.exe (PID: 6896)
Process drops legitimate windows executable
- pcran05d.exe (PID: 8052)
- UnifiedStub-installer.exe (PID: 5480)
- installer.exe (PID: 6472)
- Setup.exe (PID: 7724)
- 7za.exe (PID: 8432)
- 7za.exe (PID: 6140)
- 7za.exe (PID: 8256)
Adds/modifies Windows certificates
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- servicehost.exe (PID: 7052)
- rsEngineSvc.exe (PID: 6896)
Creates a software uninstall entry
- UnifiedStub-installer.exe (PID: 5480)
- installer.exe (PID: 6472)
- servicehost.exe (PID: 7052)
- Setup.exe (PID: 7724)
Searches for installed software
- UnifiedStub-installer.exe (PID: 5480)
- updater.exe (PID: 7784)
- rsEDRSvc.exe (PID: 8532)
- rsVPNSvc.exe (PID: 8624)
- rsEngineSvc.exe (PID: 6896)
- MEmuConsole.exe (PID: 9968)
- rsDNSSvc.exe (PID: 10096)
- MEmu.exe (PID: 5008)
Executes as Windows Service
- rsSyncSvc.exe (PID: 1216)
- rsClientSvc.exe (PID: 7204)
- rsEngineSvc.exe (PID: 6896)
- rsWSC.exe (PID: 3564)
- servicehost.exe (PID: 7052)
- rsEDRSvc.exe (PID: 8532)
- rsVPNClientSvc.exe (PID: 1212)
- rsVPNSvc.exe (PID: 8624)
- WmiApSrv.exe (PID: 8284)
- MemuService.exe (PID: 10040)
- rsDNSClientSvc.exe (PID: 7892)
- rsDNSResolver.exe (PID: 9924)
- rsDNSSvc.exe (PID: 10096)
The process verifies whether the antivirus software is installed
- saBSI.exe (PID: 3944)
- installer.exe (PID: 2604)
- installer.exe (PID: 6472)
- servicehost.exe (PID: 7052)
- uihost.exe (PID: 7908)
- cmd.exe (PID: 8304)
- updater.exe (PID: 7784)
- rsEngineSvc.exe (PID: 6896)
- cmd.exe (PID: 8404)
- rsVPNSvc.exe (PID: 8624)
- rsDNSSvc.exe (PID: 10096)
- rsEDRSvc.exe (PID: 8532)
The process creates files with name similar to system file names
- installer.exe (PID: 6472)
- UnifiedStub-installer.exe (PID: 5480)
- 7za.exe (PID: 8432)
Creates/Modifies COM task schedule object
- installer.exe (PID: 6472)
- MEmuManage.exe (PID: 8028)
- regsvr32.exe (PID: 9628)
- regsvr32.exe (PID: 9576)
The process drops C-runtime libraries
- UnifiedStub-installer.exe (PID: 5480)
- 7za.exe (PID: 6140)
- 7za.exe (PID: 8432)
- 7za.exe (PID: 8256)
Drops 7-zip archiver for unpacking
- UnifiedStub-installer.exe (PID: 5480)
- Setup.exe (PID: 7724)
- 7za.exe (PID: 6140)
Drops a system driver (possible attempt to evade defenses)
- UnifiedStub-installer.exe (PID: 5480)
- 7za.exe (PID: 8432)
- MEmuDrvInst.exe (PID: 1332)
Creates or modifies Windows services
- UnifiedStub-installer.exe (PID: 5480)
Creates files in the driver directory
- UnifiedStub-installer.exe (PID: 5480)
- MEmuDrvInst.exe (PID: 1332)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- UnifiedStub-installer.exe (PID: 5480)
Creates file in the systems drive root
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
Windows service management via SC.EXE
- sc.exe (PID: 8392)
- sc.exe (PID: 8572)
- sc.exe (PID: 8264)
- sc.exe (PID: 8332)
- sc.exe (PID: 8448)
- sc.exe (PID: 8508)
- sc.exe (PID: 8636)
- sc.exe (PID: 8760)
- sc.exe (PID: 8700)
- sc.exe (PID: 8816)
- sc.exe (PID: 8940)
- sc.exe (PID: 9000)
- sc.exe (PID: 9056)
- sc.exe (PID: 9116)
- sc.exe (PID: 8880)
- sc.exe (PID: 6192)
- sc.exe (PID: 9176)
- sc.exe (PID: 7996)
- sc.exe (PID: 9060)
- sc.exe (PID: 7956)
- sc.exe (PID: 7536)
- sc.exe (PID: 10092)
- sc.exe (PID: 9988)
- sc.exe (PID: 9864)
- sc.exe (PID: 9928)
- sc.exe (PID: 9800)
Reads Mozilla Firefox installation path
- uihost.exe (PID: 7908)
- servicehost.exe (PID: 7052)
Starts CMD.EXE for commands execution
- updater.exe (PID: 7784)
- rsDNSSvc.exe (PID: 10096)
- MEmu.exe (PID: 5008)
Reads the BIOS version
- rsEDRSvc.exe (PID: 8532)
- rsEngineSvc.exe (PID: 6896)
Process checks is Powershell's Script Block Logging on
- rsEDRSvc.exe (PID: 8532)
The process checks if it is being run in the virtual environment
- rsVPNSvc.exe (PID: 8624)
Application launched itself
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 5444)
Uses RUNDLL32.EXE to load library
- UnifiedStub-installer.exe (PID: 5480)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 10388)
- cmd.exe (PID: 6104)
There is functionality for communication over UDP network (YARA)
- rsEngineSvc.exe (PID: 6896)
Starts application with an unusual extension
- cmd.exe (PID: 6868)
INFO
Checks supported languages
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- identity_helper.exe (PID: 7796)
- identity_helper.exe (PID: 2632)
- saBSI.exe (PID: 2716)
- rsStubActivator.exe (PID: 6104)
- pcran05d.exe (PID: 8052)
- UnifiedStub-installer.exe (PID: 5480)
- saBSI.exe (PID: 3944)
- rsSyncSvc.exe (PID: 2388)
- rsSyncSvc.exe (PID: 1216)
- installer.exe (PID: 2604)
- installer.exe (PID: 6472)
- rsWSC.exe (PID: 6836)
- rsClientSvc.exe (PID: 7204)
- rsClientSvc.exe (PID: 5368)
- rsEngineSvc.exe (PID: 3736)
- Setup.exe (PID: 7724)
- rsEngineSvc.exe (PID: 6896)
- rsWSC.exe (PID: 3564)
- servicehost.exe (PID: 7052)
- uihost.exe (PID: 7908)
- rsEDRSvc.exe (PID: 7296)
- updater.exe (PID: 7784)
- rsEDRSvc.exe (PID: 8532)
- rsHelper.exe (PID: 9000)
- rsLitmus.A.exe (PID: 8224)
- 7za.exe (PID: 8256)
- 7za.exe (PID: 8432)
- MEmuSVC.exe (PID: 1208)
- MEmuDrvInst.exe (PID: 1332)
- MEmuManage.exe (PID: 8028)
- rsVPNClientSvc.exe (PID: 2512)
- rsVPNClientSvc.exe (PID: 1212)
- rsVPNSvc.exe (PID: 6304)
- rsVPNSvc.exe (PID: 8624)
- MEmuSVC.exe (PID: 3488)
- 7za.exe (PID: 6140)
- VPN.exe (PID: 1700)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8064)
- rsAppUI.exe (PID: 3052)
- EPP.exe (PID: 7808)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 8336)
- rsAppUI.exe (PID: 7600)
- rsAppUI.exe (PID: 7884)
- MEmuSVC.exe (PID: 9500)
- MEmuSVC.exe (PID: 9676)
- rsAppUI.exe (PID: 8344)
- rsAppUI.exe (PID: 9276)
- MemuService.exe (PID: 10040)
- MEmuManage.exe (PID: 10152)
- MEmuSVC.exe (PID: 9220)
- MEmuManage.exe (PID: 9696)
- MEmuManage.exe (PID: 9392)
- MEmuSVC.exe (PID: 10012)
- MEmuRepair.exe (PID: 9496)
- memuc.exe (PID: 9868)
- MEmuConsole.exe (PID: 9968)
- MEmuManage.exe (PID: 9812)
- MEmuManage.exe (PID: 9760)
- MEmuSVC.exe (PID: 8308)
- rsDNSClientSvc.exe (PID: 9396)
- MEmu.exe (PID: 7852)
- MEmuSVC.exe (PID: 9568)
- rsDNSResolver.exe (PID: 10156)
- rsDNSClientSvc.exe (PID: 7892)
- rsDNSSvc.exe (PID: 10008)
- rsDNSResolver.exe (PID: 9924)
- screenrecord.exe (PID: 416)
- MEmu.exe (PID: 3388)
- rsDNSSvc.exe (PID: 10096)
- MEmuRepair.exe (PID: 10184)
- DNS.exe (PID: 3540)
- rsAppUI.exe (PID: 5444)
- rsAppUI.exe (PID: 6344)
- rsAppUI.exe (PID: 9760)
- rsAppUI.exe (PID: 10228)
- identity_helper.exe (PID: 8144)
- MEmuHeadless.exe (PID: 3944)
- MEmu.exe (PID: 5008)
- MEmuSVC.exe (PID: 9176)
- chcp.com (PID: 11004)
- rsAppUI.exe (PID: 9908)
- rsAppUI.exe (PID: 8620)
- rsAppUI.exe (PID: 9564)
Reads the computer name
- identity_helper.exe (PID: 7796)
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- identity_helper.exe (PID: 2632)
- rsStubActivator.exe (PID: 6104)
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- saBSI.exe (PID: 3944)
- rsSyncSvc.exe (PID: 2388)
- rsSyncSvc.exe (PID: 1216)
- installer.exe (PID: 6472)
- rsWSC.exe (PID: 6836)
- rsWSC.exe (PID: 3564)
- rsClientSvc.exe (PID: 5368)
- rsClientSvc.exe (PID: 7204)
- rsEngineSvc.exe (PID: 3736)
- Setup.exe (PID: 7724)
- rsEngineSvc.exe (PID: 6896)
- servicehost.exe (PID: 7052)
- uihost.exe (PID: 7908)
- rsEDRSvc.exe (PID: 7296)
- 7za.exe (PID: 6140)
- updater.exe (PID: 7784)
- rsEDRSvc.exe (PID: 8532)
- rsHelper.exe (PID: 9000)
- 7za.exe (PID: 8256)
- 7za.exe (PID: 8432)
- MEmuDrvInst.exe (PID: 1332)
- MEmuManage.exe (PID: 8028)
- MEmuSVC.exe (PID: 1208)
- rsVPNClientSvc.exe (PID: 1212)
- rsVPNSvc.exe (PID: 6304)
- rsVPNSvc.exe (PID: 8624)
- rsVPNClientSvc.exe (PID: 2512)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8336)
- rsAppUI.exe (PID: 3052)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 7600)
- rsAppUI.exe (PID: 7884)
- MemuService.exe (PID: 10040)
- MEmuManage.exe (PID: 10152)
- MEmuSVC.exe (PID: 9676)
- MEmuManage.exe (PID: 9696)
- MEmuSVC.exe (PID: 10012)
- MEmuConsole.exe (PID: 9968)
- MEmuSVC.exe (PID: 9220)
- MEmuRepair.exe (PID: 9496)
- MEmuManage.exe (PID: 9392)
- MEmu.exe (PID: 7852)
- MEmuSVC.exe (PID: 9568)
- MEmuManage.exe (PID: 9760)
- MEmuManage.exe (PID: 9812)
- rsDNSClientSvc.exe (PID: 9396)
- rsDNSSvc.exe (PID: 10008)
- rsDNSResolver.exe (PID: 9924)
- rsDNSClientSvc.exe (PID: 7892)
- rsDNSResolver.exe (PID: 10156)
- MEmu.exe (PID: 3388)
- rsDNSSvc.exe (PID: 10096)
- MEmuSVC.exe (PID: 8308)
- MEmuRepair.exe (PID: 10184)
- rsAppUI.exe (PID: 5444)
- rsAppUI.exe (PID: 10228)
- rsAppUI.exe (PID: 9760)
- MEmu.exe (PID: 5008)
- MEmuSVC.exe (PID: 9176)
- identity_helper.exe (PID: 8144)
- MEmuHeadless.exe (PID: 3944)
- rsAppUI.exe (PID: 8620)
- rsAppUI.exe (PID: 9908)
- rsAppUI.exe (PID: 9564)
Executable content was dropped or overwritten
- msedge.exe (PID: 2040)
Application launched itself
- msedge.exe (PID: 2040)
- msedge.exe (PID: 8100)
- msedge.exe (PID: 11192)
Reads the machine GUID from the registry
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- saBSI.exe (PID: 3944)
- installer.exe (PID: 6472)
- rsWSC.exe (PID: 6836)
- rsWSC.exe (PID: 3564)
- rsEngineSvc.exe (PID: 3736)
- rsEngineSvc.exe (PID: 6896)
- servicehost.exe (PID: 7052)
- uihost.exe (PID: 7908)
- updater.exe (PID: 7784)
- rsEDRSvc.exe (PID: 7296)
- rsEDRSvc.exe (PID: 8532)
- rsHelper.exe (PID: 9000)
- MEmuDrvInst.exe (PID: 1332)
- rsVPNSvc.exe (PID: 6304)
- rsVPNSvc.exe (PID: 8624)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
- MEmuConsole.exe (PID: 9968)
- rsDNSSvc.exe (PID: 10008)
- rsDNSSvc.exe (PID: 10096)
- rsAppUI.exe (PID: 5444)
- MEmu.exe (PID: 5008)
- rsAppUI.exe (PID: 9908)
- rsAppUI.exe (PID: 8620)
- rsAppUI.exe (PID: 9564)
Creates files or folders in the user directory
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- UnifiedStub-installer.exe (PID: 5480)
- rsWSC.exe (PID: 6836)
- rsEngineSvc.exe (PID: 6896)
- rsVPNSvc.exe (PID: 8624)
- rsAppUI.exe (PID: 3052)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 7884)
- Setup.exe (PID: 7724)
- rsDNSSvc.exe (PID: 10096)
- rsAppUI.exe (PID: 10228)
- rsAppUI.exe (PID: 5444)
- MEmu.exe (PID: 5008)
- rsAppUI.exe (PID: 9908)
Checks proxy server information
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- saBSI.exe (PID: 3944)
- rsWSC.exe (PID: 6836)
- slui.exe (PID: 4512)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
- MEmuConsole.exe (PID: 9968)
- rsAppUI.exe (PID: 5444)
- rsDNSSvc.exe (PID: 10096)
- MEmu.exe (PID: 5008)
Reads Environment values
- identity_helper.exe (PID: 7796)
- identity_helper.exe (PID: 2632)
- rsStubActivator.exe (PID: 6104)
- UnifiedStub-installer.exe (PID: 5480)
- rsEngineSvc.exe (PID: 6896)
- rsEDRSvc.exe (PID: 8532)
- rsAppUI.exe (PID: 8268)
- rsVPNSvc.exe (PID: 8624)
- rsAppUI.exe (PID: 8428)
- rsDNSSvc.exe (PID: 10096)
- identity_helper.exe (PID: 8144)
Create files in a temporary directory
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- pcran05d.exe (PID: 8052)
- saBSI.exe (PID: 3944)
- UnifiedStub-installer.exe (PID: 5480)
- installer.exe (PID: 6472)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 5444)
Reads the software policy settings
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- saBSI.exe (PID: 3944)
- installer.exe (PID: 6472)
- rsWSC.exe (PID: 6836)
- servicehost.exe (PID: 7052)
- uihost.exe (PID: 7908)
- updater.exe (PID: 7784)
- rsEngineSvc.exe (PID: 6896)
- rsEDRSvc.exe (PID: 7296)
- rsEDRSvc.exe (PID: 8532)
- rsWSC.exe (PID: 3564)
- slui.exe (PID: 4512)
- MEmuDrvInst.exe (PID: 1332)
- rsVPNSvc.exe (PID: 6304)
- rsVPNSvc.exe (PID: 8624)
- rsDNSSvc.exe (PID: 10096)
- rsDNSSvc.exe (PID: 10008)
Disables trace logs
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- UnifiedStub-installer.exe (PID: 5480)
- rsEngineSvc.exe (PID: 6896)
- rsEDRSvc.exe (PID: 8532)
- rsVPNSvc.exe (PID: 8624)
- rsDNSSvc.exe (PID: 10096)
Reads CPU info
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- Setup.exe (PID: 7724)
- rsEngineSvc.exe (PID: 6896)
- rsEDRSvc.exe (PID: 8532)
- rsVPNSvc.exe (PID: 8624)
- MEmuConsole.exe (PID: 9968)
- MEmuRepair.exe (PID: 9496)
- MEmu.exe (PID: 3388)
- MEmuRepair.exe (PID: 10184)
- MEmu.exe (PID: 5008)
The sample compiled with english language support
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- rsStubActivator.exe (PID: 6104)
- pcran05d.exe (PID: 8052)
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- installer.exe (PID: 2604)
- installer.exe (PID: 6472)
- Setup.exe (PID: 7724)
- 7za.exe (PID: 6140)
- 7za.exe (PID: 8432)
- 7za.exe (PID: 8256)
- MEmuDrvInst.exe (PID: 1332)
Creates files in the program directory
- MEmu-setup-abroad-02bf66ec.exe (PID: 7744)
- saBSI.exe (PID: 2716)
- UnifiedStub-installer.exe (PID: 5480)
- installer.exe (PID: 2604)
- installer.exe (PID: 6472)
- saBSI.exe (PID: 3944)
- rsWSC.exe (PID: 6836)
- rsEngineSvc.exe (PID: 3736)
- Setup.exe (PID: 7724)
- servicehost.exe (PID: 7052)
- rsEngineSvc.exe (PID: 6896)
- uihost.exe (PID: 7908)
- rsEDRSvc.exe (PID: 7296)
- 7za.exe (PID: 6140)
- rsEDRSvc.exe (PID: 8532)
- 7za.exe (PID: 8432)
- 7za.exe (PID: 8256)
- rsVPNSvc.exe (PID: 6304)
- rsVPNSvc.exe (PID: 8624)
- MemuService.exe (PID: 10040)
- MEmuConsole.exe (PID: 9968)
- MEmuSVC.exe (PID: 9568)
- MEmuSVC.exe (PID: 10012)
- rsDNSResolver.exe (PID: 10156)
- rsDNSResolver.exe (PID: 9924)
- rsDNSSvc.exe (PID: 10008)
- rsDNSSvc.exe (PID: 10096)
- MEmu.exe (PID: 5008)
- MEmuHeadless.exe (PID: 3944)
Process checks computer location settings
- rsStubActivator.exe (PID: 6104)
- servicehost.exe (PID: 7052)
- rsVPNSvc.exe (PID: 8624)
- rsAppUI.exe (PID: 8064)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
- rsAppUI.exe (PID: 9276)
- rsAppUI.exe (PID: 8344)
- rsAppUI.exe (PID: 6344)
- rsAppUI.exe (PID: 5444)
SQLite executable
- UnifiedStub-installer.exe (PID: 5480)
Reads product name
- rsEDRSvc.exe (PID: 8532)
- rsEngineSvc.exe (PID: 6896)
- rsAppUI.exe (PID: 8268)
- rsAppUI.exe (PID: 8428)
Reads the time zone
- rsEngineSvc.exe (PID: 6896)
- rsEDRSvc.exe (PID: 8532)
- rsVPNSvc.exe (PID: 8624)
- runonce.exe (PID: 3900)
.NET Reactor protector has been detected
- UnifiedStub-installer.exe (PID: 5480)
- rsWSC.exe (PID: 3564)
- rsEngineSvc.exe (PID: 6896)
Reads security settings of Internet Explorer
- runonce.exe (PID: 3900)
- explorer.exe (PID: 9240)
- explorer.exe (PID: 10152)
Launching a file from a Registry key
- rundll32.exe (PID: 5652)
Process checks whether UAC notifications are on
- rsEDRSvc.exe (PID: 8532)
Detects InnoSetup installer (YARA)
- rsEngineSvc.exe (PID: 6896)
Drops encrypted JS script (Microsoft Script Encoder)
- rsEDRSvc.exe (PID: 8532)
Changes the display of characters in the console
- cmd.exe (PID: 6868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
413
Monitored processes
250
Malicious processes
21
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Program Files\Microvirt\MEmu\screenrecord.exe" | C:\Program Files\Microvirt\MEmu\screenrecord.exe | — | Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4208,i,632543674651880002,1740148177192917257,262144 --variations-seed-version --mojo-platform-channel-handle=3460 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1040 | "C:\WINDOWS\system32\regsvr32" /s /u "C:\Program Files\Microvirt\MEmuHyperv\MEmuC.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Microvirt\MEmuHyperv\MEmuSVC.exe" -Embedding | C:\Program Files\Microvirt\MEmuHyperv\MEmuSVC.exe | — | svchost.exe | |||||||||||
User: admin Company: Maiwei Corporation Integrity Level: HIGH Description: MemuHyperv Interface Exit code: 0 Version: 5.1.34.121010 Modules
| |||||||||||||||
| 1212 | "C:\Program Files\ReasonLabs\VPN\rsVPNClientSvc.exe" | C:\Program Files\ReasonLabs\VPN\rsVPNClientSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: Reason Client Service Version: 4.5.1.0 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe" -pn:EPP -lpn:rav_antivirus -url:https://update.reasonsecurity.com/v2/live -bn:ReasonLabs -dt:10 | C:\Program Files\ReasonLabs\Common\rsSyncSvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Reason Software Company Inc. Integrity Level: SYSTEM Description: Reason Security Synchronize Service Version: 1.8.5.0 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Microvirt\MEmuHyperv\MEmuDrvInst.exe" driver install "C:\Program Files\Microvirt\MEmuHyperv\MEmuDrv.inf" | C:\Program Files\Microvirt\MEmuHyperv\MEmuDrvInst.exe | Setup.exe | ||||||||||||
User: admin Company: Maiwei Corporation Integrity Level: HIGH Description: MemuHyperv Driver Installer Exit code: 0 Version: 5.1.34.121010 Modules
| |||||||||||||||
| 1352 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5316,i,10790480124074873322,6722199518932875117,262144 --variations-seed-version --mojo-platform-channel-handle=1716 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | wevtutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "c:\program files\reasonlabs\VPN\ui\VPN.exe" --minimized --focused --first-run | C:\Program Files\ReasonLabs\VPN\ui\VPN.exe | — | rsVPNSvc.exe | |||||||||||
User: admin Company: Reason Cybersecurity Ltd. Integrity Level: MEDIUM Description: RAV VPN Client Exit code: 0 Version: 2.20.0 Modules
| |||||||||||||||
Total events
156 810
Read events
154 810
Write events
956
Delete events
1 044
Modification events
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D24DB343B2962F00 | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9E0D8001-92F3-44AD-B05A-07731A677FBE} | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {564B4BA6-0541-41E2-9691-B04D56E8FB63} | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {AC40A3B3-ED48-4287-A79C-1062840EAB7A} | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {070F314F-E28C-4AFF-95FA-1BC92D624BE0} | |||
| (PID) Process: | (2040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459640 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {ECCF8BEF-0C3F-4636-992F-D0C11218639B} | |||
Executable files
1 088
Suspicious files
1 248
Text files
1 580
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF17688d.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF17688d.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF17688d.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17688d.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF17689d.TMP | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF17687e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
174
TCP/UDP connections
1 052
DNS requests
300
Threats
37
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2552 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7744 | MEmu-setup-abroad-02bf66ec.exe | GET | 200 | 154.85.69.55:80 | http://stat.microvirt.com/new_market/service.php?action=postmemusetupinfo&table=memusetupinfo&packageName=MEmu-setup-abroad-02bf66ec&insMode=ins&version=1.0.1.0&channel=cd5e1e00&silence=0&currPage=ShowWelcomePage&lifeCycle=0&exitCode=0&mac=9E:F0:EB:3D:A9:51&error=&initTime=0&initTime=0&acceptCount=-1&declineCount=-1&installOffers=-1 | unknown | — | — | unknown |
7744 | MEmu-setup-abroad-02bf66ec.exe | GET | 200 | 99.86.1.77:80 | http://d1s13cf1vqydcj.cloudfront.net/installer/394543/624398141519 | unknown | — | — | whitelisted |
7744 | MEmu-setup-abroad-02bf66ec.exe | GET | 200 | 154.85.69.55:80 | http://stat.microvirt.com/new_market/service.php?action=postmemusetupinfo&table=memusetupinfo&packageName=MEmu-setup-abroad-02bf66ec&insMode=ins&version=1.0.1.0&channel=cd5e1e00&silence=0&currPage=ShowAd_1&lifeCycle=0&exitCode=0&mac=9E:F0:EB:3D:A9:51&error=&initTime=2562&initTime=2562&acceptCount=0&declineCount=0&installOffers=-1 | unknown | — | — | unknown |
7380 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7744 | MEmu-setup-abroad-02bf66ec.exe | GET | 200 | 154.85.69.55:80 | http://stat.microvirt.com/new_market/service.php?action=postmemusetupinfo&table=memusetupinfo&packageName=MEmu-setup-abroad-02bf66ec&insMode=ins&version=1.0.1.0&channel=cd5e1e00&silence=0&currPage=ShowInstallPage&lifeCycle=0&exitCode=0&mac=9E:F0:EB:3D:A9:51&error=&initTime=2562&initTime=2562&acceptCount=2&declineCount=0&installOffers=-1 | unknown | — | — | unknown |
7744 | MEmu-setup-abroad-02bf66ec.exe | GET | 302 | 18.66.122.58:80 | http://www.memuplay.com/download-en.php?file_name=MEmu-Setup-9.2.3.0-haa98210ff&from=offline_installer | unknown | — | — | whitelisted |
5480 | UnifiedStub-installer.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBTh4QXD3xfHaxna9yfH20h%2Ft5LfbQQUZZ9RzoVofy%2BKRYiq3acxux4NAF4CEzMAAvj8yfO1LW1Z7wAAAAAC%2BPw%3D | unknown | — | — | whitelisted |
5480 | UnifiedStub-installer.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Identity%20Verification%20Root%20Certificate%20Authority%202020.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5708 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6336 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6336 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6336 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6336 | msedge.exe | 104.126.37.136:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
6336 | msedge.exe | 18.66.122.33:443 | www.memuplay.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.memuplay.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
dl.memuplay.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6336 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6336 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6336 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
6336 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7744 | MEmu-setup-abroad-02bf66ec.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
7744 | MEmu-setup-abroad-02bf66ec.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
7744 | MEmu-setup-abroad-02bf66ec.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7744 | MEmu-setup-abroad-02bf66ec.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
7744 | MEmu-setup-abroad-02bf66ec.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
7744 | MEmu-setup-abroad-02bf66ec.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
Process | Message |
|---|---|
MEmu-setup-abroad-02bf66ec.exe | Qt: Untested Windows version 10.0 detected!
|
MEmu-setup-abroad-02bf66ec.exe | QObject::connect: No such signal QNetworkReplyHttpImpl::error()
|
MEmu-setup-abroad-02bf66ec.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 21x14+320+100 on QWidgetWindow/'QCheckBoxClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
MEmu-setup-abroad-02bf66ec.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 55x14+320+100 on QWidgetWindow/'QLabelClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
MEmu-setup-abroad-02bf66ec.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 21x14+320+100 on QWidgetWindow/'QCheckBoxClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
MEmu-setup-abroad-02bf66ec.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 66x14+320+100 on QWidgetWindow/'QLabelClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
MEmu-setup-abroad-02bf66ec.exe | QObject::connect: No such signal QNetworkReplyHttpImpl::error()
|
MEmu-setup-abroad-02bf66ec.exe | QObject::connect: No such signal QNetworkReplyHttpImpl::error()
|
MEmu-setup-abroad-02bf66ec.exe | QObject::killTimer: Timers cannot be stopped from another thread
|
MEmu-setup-abroad-02bf66ec.exe | QObject::~QObject: Timers cannot be stopped from another thread
|