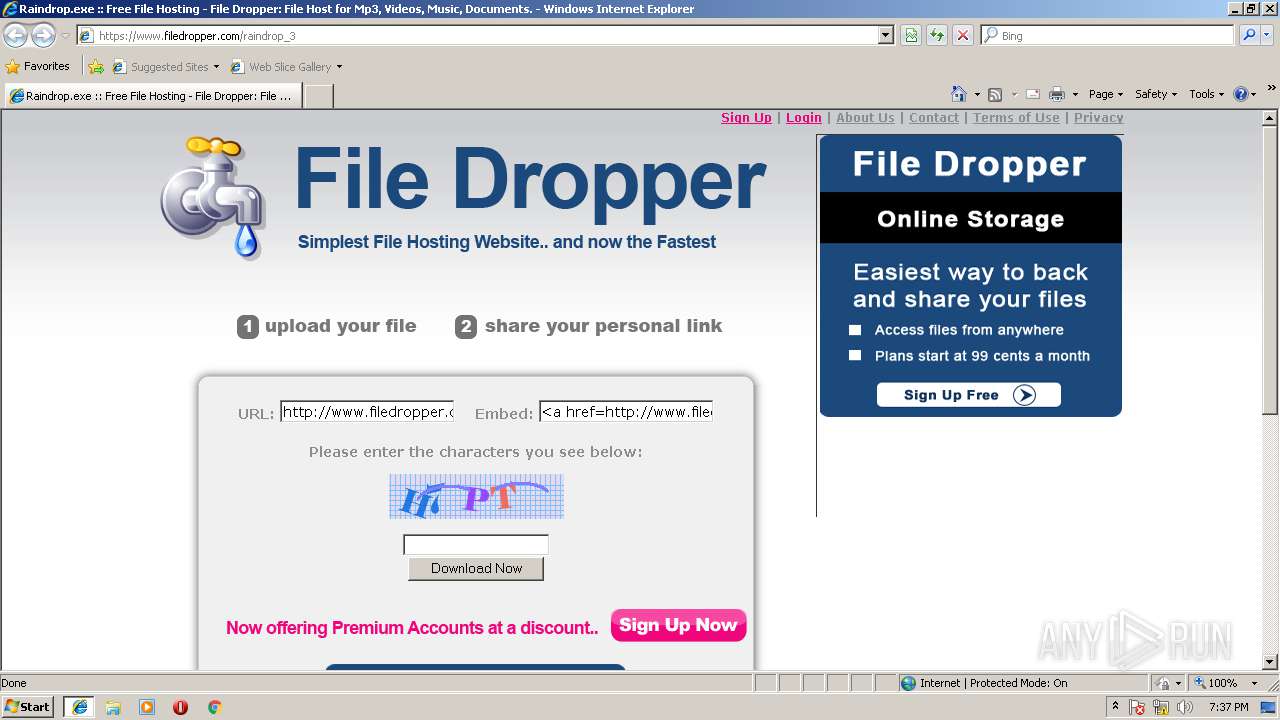
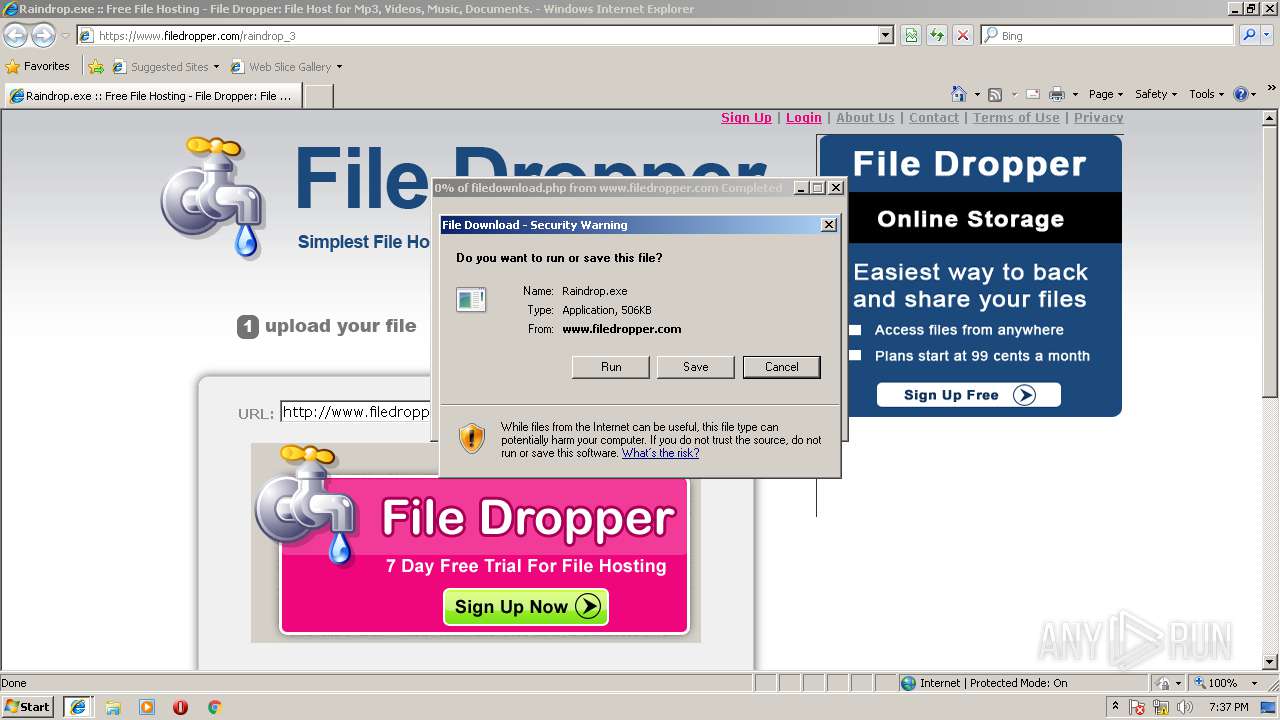
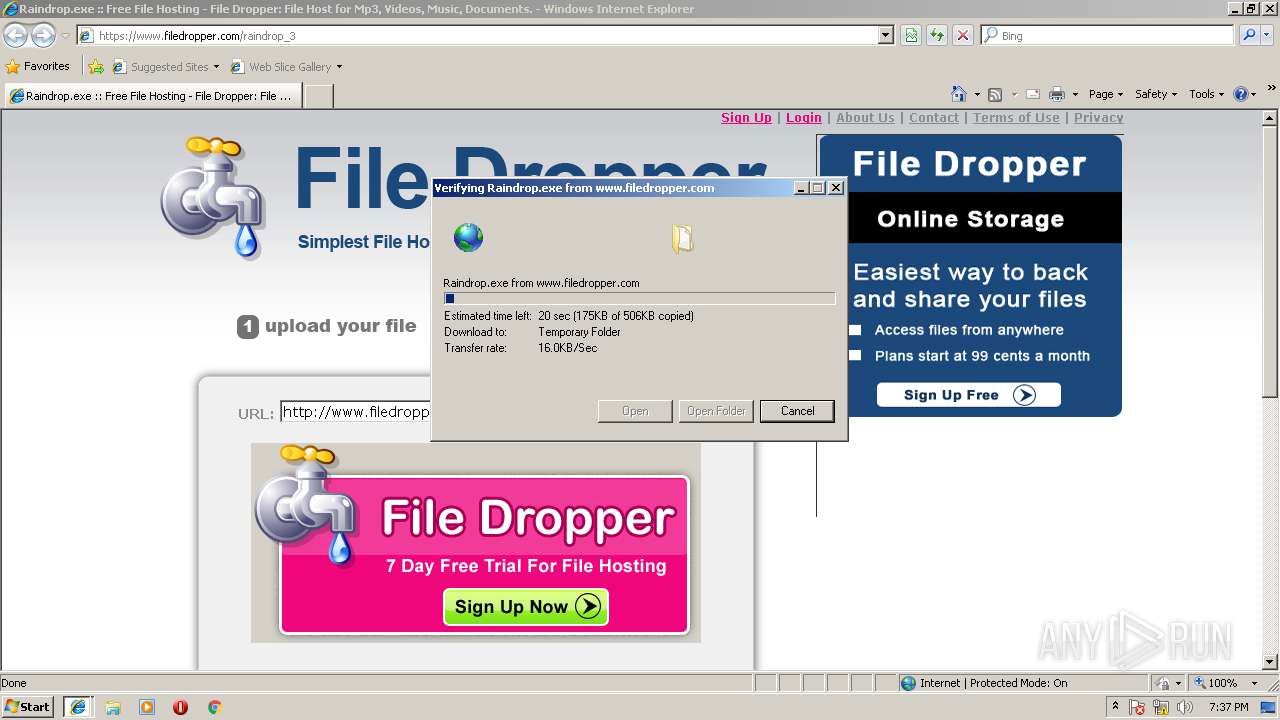
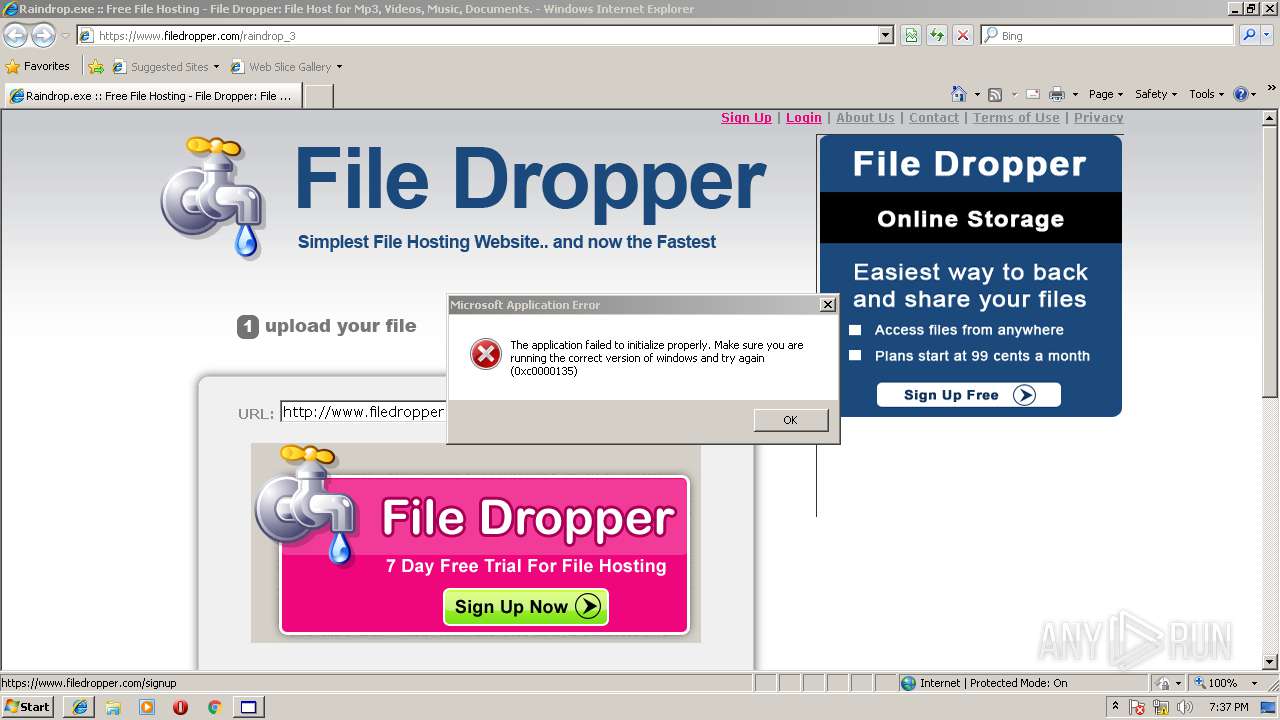
| URL: | http://www.filedropper.com/raindrop_3 |
| Full analysis: | https://app.any.run/tasks/b91aa6ae-df74-4ce7-b01f-ae3a7a28650b |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | June 16, 2018, 18:36:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 83317A1D0817685E2E3E9F9BAD87A73B |
| SHA1: | 38F100979AFAC9C0D37395C7711463BD03752B43 |
| SHA256: | 9B5176E77E0F2AE7041A4D6D4A654160C5479583683059F6ABE209069439C91F |
| SSDEEP: | 3:N1KJS4QuXrRKD:Cc4Qq8 |
MALICIOUS
Detected Hawkeye Keylogger
- filedownload[1].exe (PID: 2996)
Application was dropped or rewritten from another process
- filedownload[1].exe (PID: 2996)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 3244)
Creates files in the user directory
- filedownload[1].exe (PID: 2996)
Checks for external IP
- filedownload[1].exe (PID: 2996)
Executes scripts
- filedownload[1].exe (PID: 2996)
INFO
Dropped object may contain URL's
- iexplore.exe (PID: 2840)
- iexplore.exe (PID: 3244)
- filedownload[1].exe (PID: 2996)
Changes internet zones settings
- iexplore.exe (PID: 3244)
Reads Internet Cache Settings
- iexplore.exe (PID: 2840)
Creates files in the user directory
- FlashUtil32_26_0_0_137_ActiveX.exe (PID: 3884)
- iexplore.exe (PID: 2840)
Reads internet explorer settings
- iexplore.exe (PID: 2840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2840 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3244 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2996 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\filedownload[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\filedownload[1].exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Microsoft Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3328 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | filedownload[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 3844 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3884 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_137_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_137_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,137 Modules
| |||||||||||||||
| 4036 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | filedownload[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
Total events
899
Read events
808
Write events
90
Delete events
1
Modification events
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006B000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {4337C6EF-7194-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (3244) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070600060010001200250004006D01 | |||
Executable files
2
Suspicious files
9
Text files
31
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3244 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3244 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabFD3F.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarFD40.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarFD42.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabFDC0.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarFDC1.tmp | — | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PrivacIE\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94308059B57B3142E455B38A6EB92015 | binary | |
MD5:— | SHA256:— | |||
| 2840 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabFD41.tmp | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2840 | iexplore.exe | GET | 301 | 144.76.226.41:80 | http://www.filedropper.com/raindrop_3 | DE | html | 246 b | suspicious |
2996 | filedownload[1].exe | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 52.5 Kb | whitelisted |
2996 | filedownload[1].exe | GET | 403 | 104.16.20.96:80 | http://whatismyipaddress.com/ | US | text | 100 b | shared |
2840 | iexplore.exe | GET | 304 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | — | — | whitelisted |
2840 | iexplore.exe | GET | 301 | 144.76.226.41:80 | http://www.filedropper.com/images/filedropper_banner.png | DE | html | 265 b | suspicious |
2840 | iexplore.exe | GET | 200 | 104.20.2.47:80 | http://c.statcounter.com/3541212/0/872cdcc5/1/ | US | image | 49 b | whitelisted |
3244 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2840 | iexplore.exe | GET | 200 | 192.35.177.64:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | US | cat | 893 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3244 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2840 | iexplore.exe | 144.76.226.41:80 | www.filedropper.com | Hetzner Online GmbH | DE | unknown |
2840 | iexplore.exe | 144.76.226.41:443 | www.filedropper.com | Hetzner Online GmbH | DE | unknown |
2840 | iexplore.exe | 192.35.177.64:80 | apps.identrust.com | IdenTrust | US | malicious |
2840 | iexplore.exe | 2.16.186.81:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2840 | iexplore.exe | 172.217.22.2:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
2840 | iexplore.exe | 216.58.205.238:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2840 | iexplore.exe | 172.217.22.72:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
2996 | filedownload[1].exe | 104.16.20.96:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
2840 | iexplore.exe | 104.20.2.47:80 | c.statcounter.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.filedropper.com |
| suspicious |
apps.identrust.com |
| shared |
www.download.windowsupdate.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
adservice.google.co.uk |
| whitelisted |
c.statcounter.com |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |
whatismyipaddress.com |
| shared |