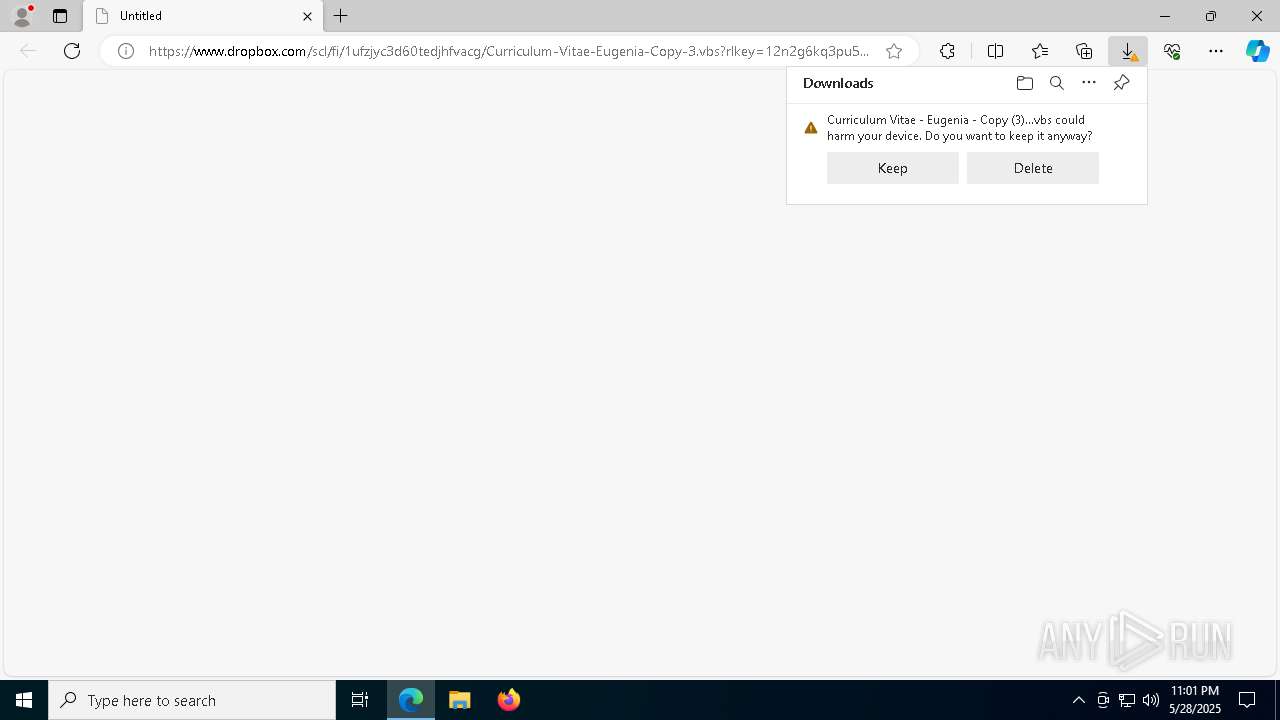
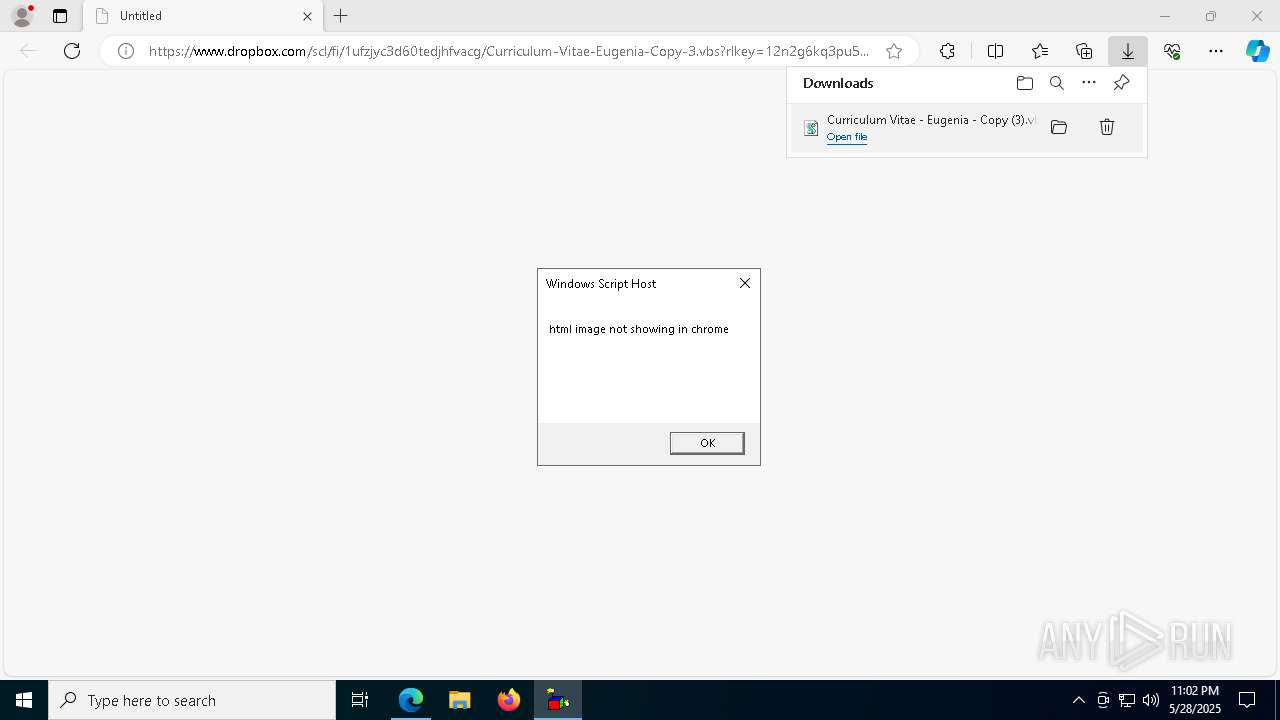
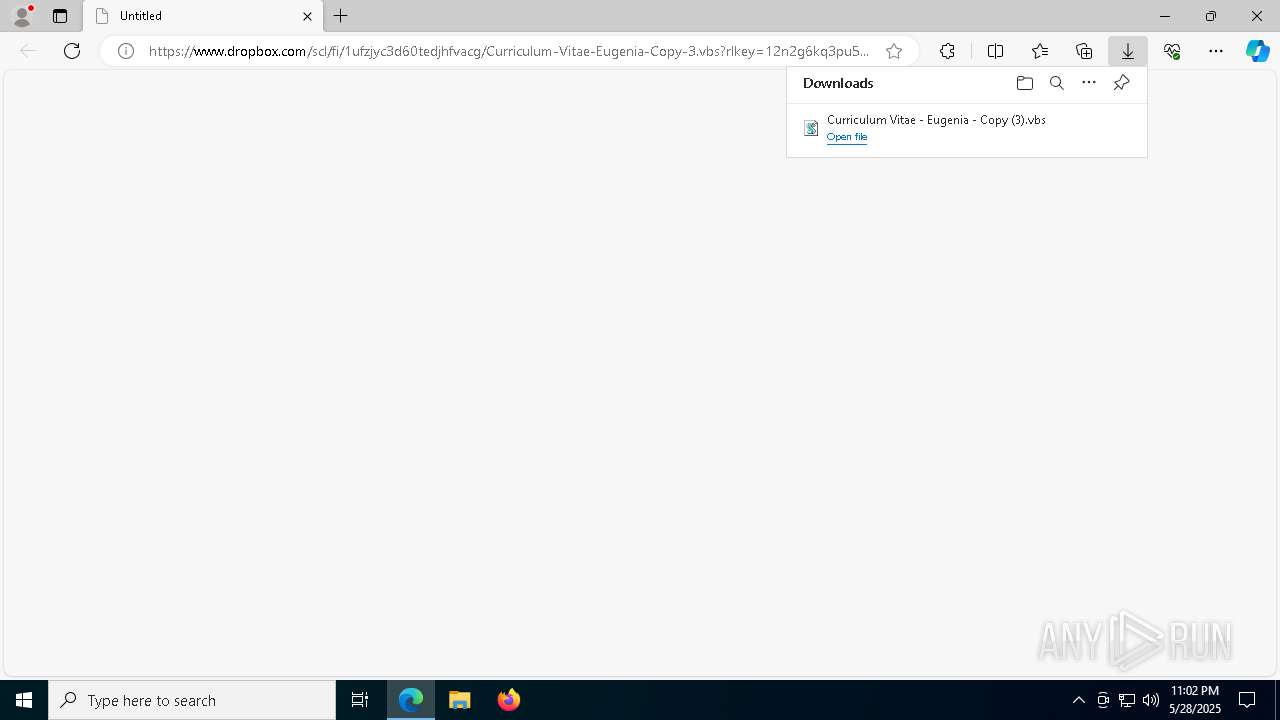
| URL: | https://www.dropbox.com/scl/fi/1ufzjyc3d60tedjhfvacg/Curriculum-Vitae-Eugenia-Copy-3.vbs?rlkey=12n2g6kq3pu5nrq0t1yzyiwoj&st=4vnibw8c&dl=1 |
| Full analysis: | https://app.any.run/tasks/ca3a9500-462e-437c-aad0-7cf3649f2d64 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 28, 2025, 23:01:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B684AB8A67F3E07166B5589DBF5ADAC1 |
| SHA1: | C0F0A4934B96D21003CD1856C56F435D0E323441 |
| SHA256: | 9ABD99C6493EA763E37D61F2B735FBA88E862AB8A2A3B21BDC686776B29323C9 |
| SSDEEP: | 3:N8DSLcVHGkG6UW22EgnnQdXBIteCXqXBDxCU:2OLHkhEgnQdxItJGCU |
MALICIOUS
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3872)
STEGOCAMPAIGN has been detected
- powershell.exe (PID: 8160)
ASYNCRAT has been detected (SURICATA)
- InstallUtil.exe (PID: 8800)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3872)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 3872)
ASYNCRAT has been detected (YARA)
- InstallUtil.exe (PID: 8800)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6700)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6700)
- wscript.exe (PID: 3872)
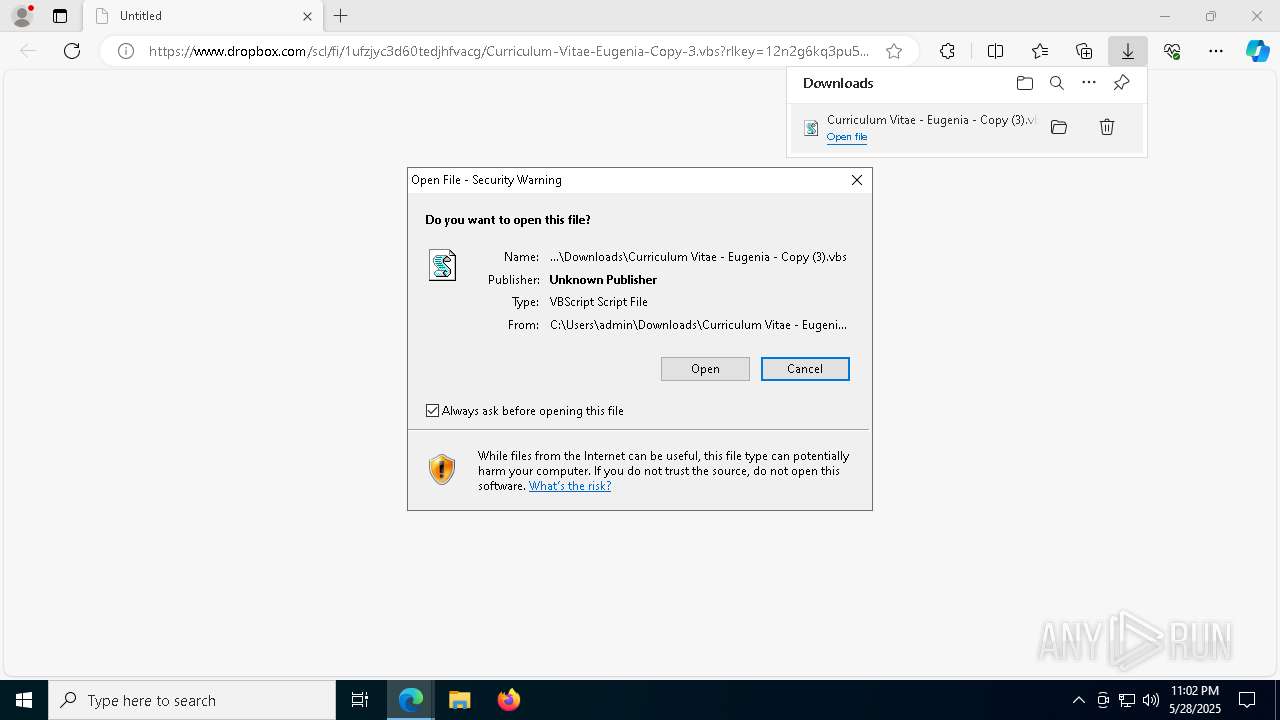
The process executes VB scripts
- msedge.exe (PID: 7412)
- wscript.exe (PID: 6700)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6700)
Execution of CURL command
- wscript.exe (PID: 6700)
Application launched itself
- wscript.exe (PID: 6700)
Potential Corporate Privacy Violation
- curl.exe (PID: 7244)
- wscript.exe (PID: 3872)
- powershell.exe (PID: 8160)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 6700)
Uses NETSH.EXE to add a firewall rule or allowed programs
- wscript.exe (PID: 3872)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 8160)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3872)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 3872)
Base64-obfuscated command line is found
- wscript.exe (PID: 3872)
Contacting a server suspected of hosting an CnC
- InstallUtil.exe (PID: 8800)
Connects to unusual port
- InstallUtil.exe (PID: 8800)
INFO
Application launched itself
- msedge.exe (PID: 7412)
- msedge.exe (PID: 8904)
Checks supported languages
- identity_helper.exe (PID: 6048)
- curl.exe (PID: 7244)
Reads Environment values
- identity_helper.exe (PID: 6048)
Reads the computer name
- identity_helper.exe (PID: 6048)
- curl.exe (PID: 7244)
Launch of the file from Downloads directory
- msedge.exe (PID: 7412)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7412)
Execution of CURL command
- cmd.exe (PID: 7212)
Checks proxy server information
- wscript.exe (PID: 3872)
- powershell.exe (PID: 8160)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 8160)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 8160)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 8160)
Disables trace logs
- powershell.exe (PID: 8160)
Executable content was dropped or overwritten
- msedge.exe (PID: 2320)
The sample compiled with english language support
- msedge.exe (PID: 2320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
263
Monitored processes
126
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --mojo-platform-channel-handle=8152 --field-trial-handle=2388,i,14155602858787914810,11525722693334993377,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Windows\System32\netsh.exe" advfirewall firewall add rule name="BlockIP_35.186.137.186" dir=out action=block remoteip=35.186.137.186 enable=yes | C:\Windows\System32\netsh.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6212 --field-trial-handle=2388,i,14155602858787914810,11525722693334993377,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 736 | "C:\Windows\System32\netsh.exe" advfirewall firewall add rule name="BlockIP_104.196.61.192" dir=out action=block remoteip=104.196.61.192 enable=yes | C:\Windows\System32\netsh.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6256 --field-trial-handle=2388,i,14155602858787914810,11525722693334993377,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8044 --field-trial-handle=2388,i,14155602858787914810,11525722693334993377,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3788 --field-trial-handle=2376,i,13349342780758387223,16676086531081599329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7724 --field-trial-handle=2388,i,14155602858787914810,11525722693334993377,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
38 720
Read events
38 546
Write events
170
Delete events
4
Modification events
| (PID) Process: | (7240) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7240) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7240) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7240) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (7240) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (7240) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (7412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
41
Suspicious files
630
Text files
159
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10a886.TMP | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10a886.TMP | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10a8b5.TMP | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10a8b5.TMP | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10a8f4.TMP | — | |
MD5:— | SHA256:— | |||
| 7412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
136
DNS requests
142
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 3.167.227.60:80 | http://r11.c.lencr.org/118.crl | unknown | — | — | whitelisted |
3884 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
9016 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1748971668&P2=404&P3=2&P4=GvQyJYARNDEnU64oOODyApEtCdkPbLL5mioOx%2bZ2nOO2dq23RDPQW272U4UGU%2fA9jfFoZgR4U1AA53GEoC4BSA%3d%3d | unknown | — | — | whitelisted |
3884 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
9016 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1748971668&P2=404&P3=2&P4=GvQyJYARNDEnU64oOODyApEtCdkPbLL5mioOx%2bZ2nOO2dq23RDPQW272U4UGU%2fA9jfFoZgR4U1AA53GEoC4BSA%3d%3d | unknown | — | — | whitelisted |
9016 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1748971668&P2=404&P3=2&P4=GvQyJYARNDEnU64oOODyApEtCdkPbLL5mioOx%2bZ2nOO2dq23RDPQW272U4UGU%2fA9jfFoZgR4U1AA53GEoC4BSA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5592 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5796 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7412 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7700 | msedge.exe | 162.125.65.18:443 | www.dropbox.com | DROPBOX | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.dropbox.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
uc977f614c841e0e3e40e34b7fa5.dl.dropboxusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
7244 | curl.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
3872 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
7700 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7700 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7700 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7700 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7700 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7700 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
7700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |