| File name: | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc |
| Full analysis: | https://app.any.run/tasks/05c0598b-44a1-40ce-933a-0200392fd5e8 |
| Verdict: | Malicious activity |
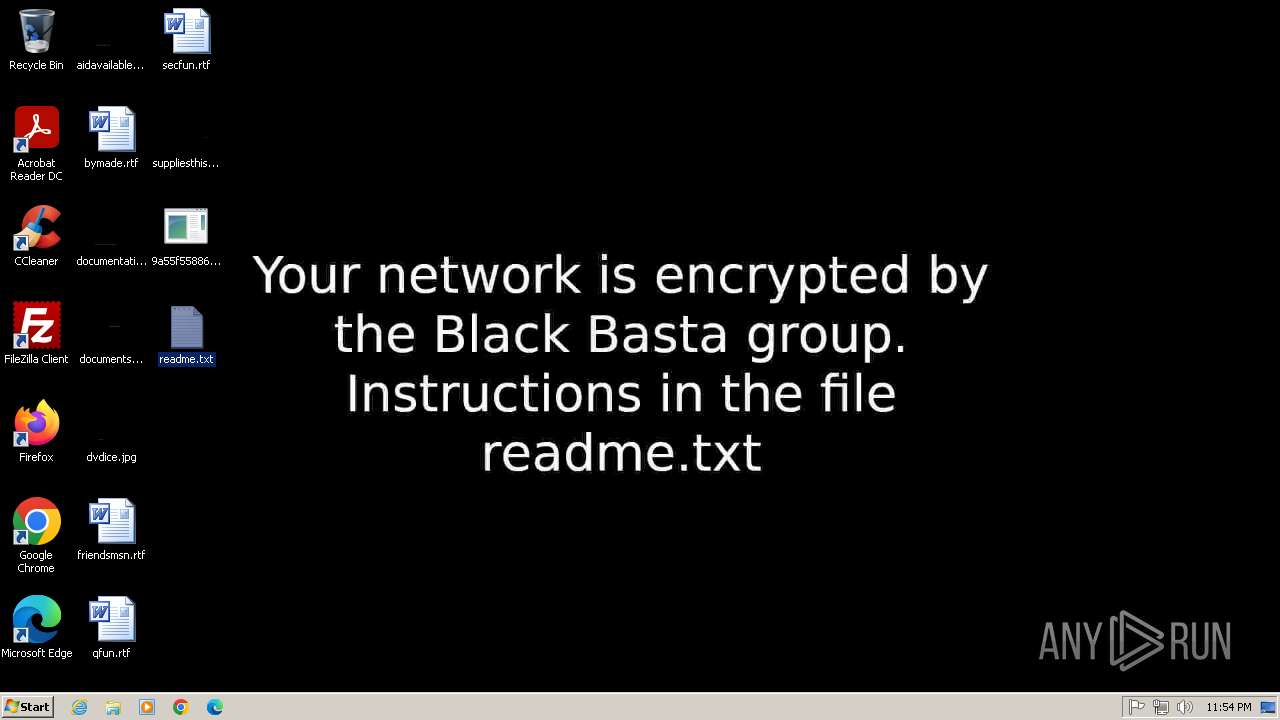
| Threats: | Black Basta is a ransomware-as-a-service operated by Storm-1811. It emerged in 2022 and uses double extortion tactics, encrypting data and stealing it for ransom. The malware often gains access through spear-phishing and uses tools like QakBot and Cobalt Strike. It's known for exploiting system vulnerabilities and using advanced obfuscation techniques. |
| Analysis date: | June 21, 2025, 22:53:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | C115BBBDB1A61F8C553D74802BFD78FB |
| SHA1: | 1F439569E3C1C14EA9F02235F8F45C49E2764160 |
| SHA256: | 9A55F55886285EEF7FFABDD55C0232D1458175B1D868C03D3E304CE7D98980BC |
| SSDEEP: | 12288:APKmMQzKox8wI7HC0d0tAUPSs9o1UHGdFfSoN5sHmShI7wq:sMQzdx5Ugas9I6oN5sHmShI |
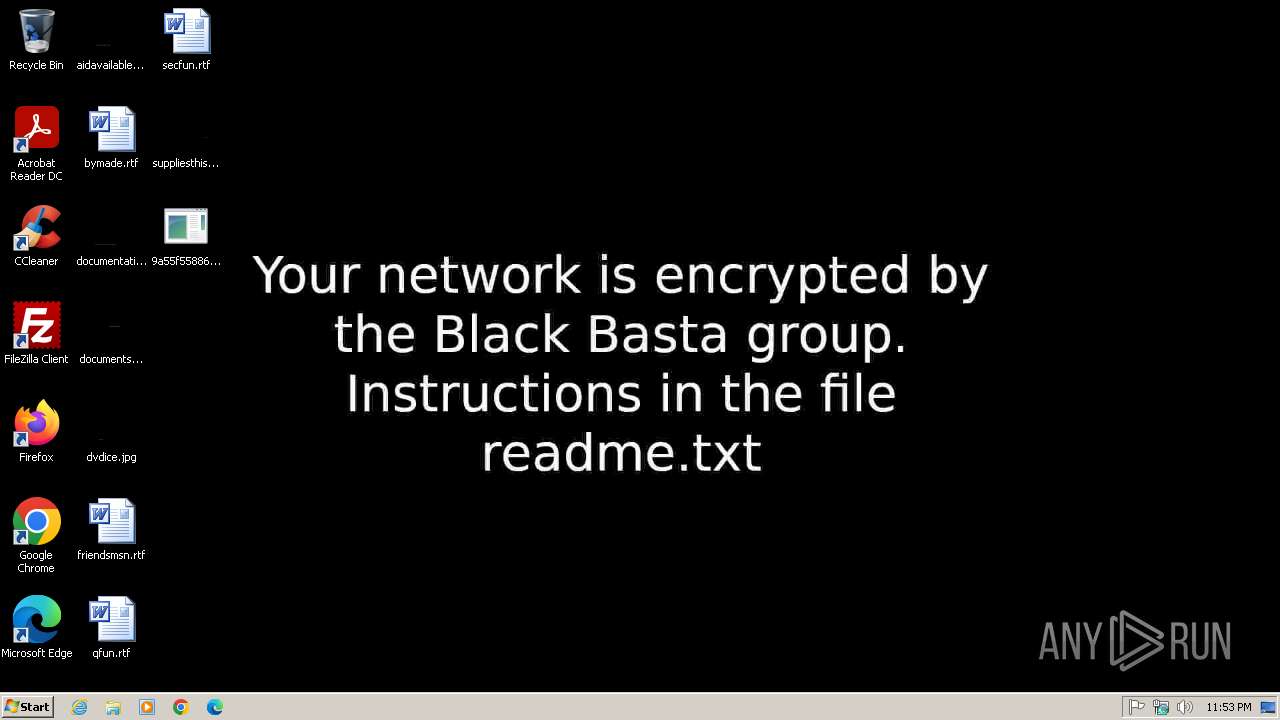
MALICIOUS
Deletes shadow copies
- cmd.exe (PID: 2212)
BLACKBASTA mutex has been found
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
BLACK BASTA has been detected
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
SUSPICIOUS
Starts CMD.EXE for commands execution
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
Creates file in the systems drive root
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
INFO
Checks supported languages
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
Creates files in the program directory
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
Create files in a temporary directory
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
Creates files or folders in the user directory
- 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe (PID: 2420)
Manual execution by a user
- notepad.exe (PID: 2884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:10:01 03:25:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.32 |
| CodeSize: | 396288 |
| InitializedDataSize: | 162816 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x34efb |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1500 | C:\Windows\system32\cmd.exe /c C:\Windows\SysNative\vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\cmd.exe | — | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2208 | C:\Windows\System32\vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2212 | C:\Windows\system32\cmd.exe /c C:\Windows\System32\vssadmin.exe delete shadows /all /quiet | C:\Windows\System32\cmd.exe | — | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe" | C:\Users\admin\Desktop\9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2884 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\readme.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
222
Read events
222
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
451
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
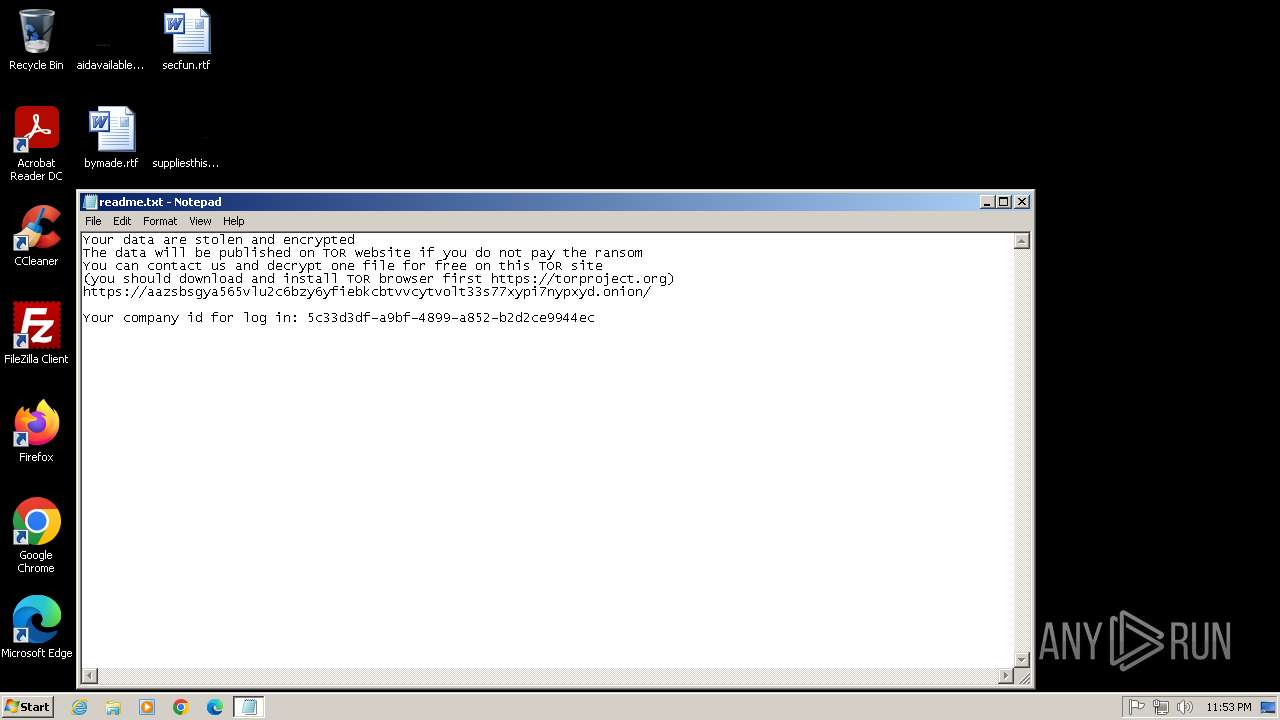
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\ProgramData\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\Users\Public\Documents\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\Users\admin\AppData\Local\Temp\fkdjsadasd.ico | image | |
MD5:6257F732BFC75408B14A445C224E2A78 | SHA256:EB07A24F63D7F56FB13E34DD60E45A4C8522C32892C8BE7DCA7D3F742FA86B0A | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\MSOCache\All Users\{90140000-0015-0412-0000-0000000FF1CE}-C\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\MSOCache\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\ProgramData\Adobe\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\ProgramData\Skype\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\Users\admin\readme.txt | binary | |
MD5:B4A2E3E446D794AB467364956096C047 | SHA256:5C7F7D725AE586B8914EB7E4514A6A52189CA3DC32AF6BE20D5A404E3F7FF298 | |||
| 2420 | 9a55f55886285eef7ffabdd55c0232d1458175b1d868c03d3e304ce7d98980bc.exe | C:\Users\admin\AppData\Local\Temp\dlaksjdoiwq.jpg | image | |
MD5:A70F03BEB3A8246595EAB83935227914 | SHA256:397A78DE041380082C5778818843EE9C2B65A9647FBC0D251244E6CAC76E170C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |