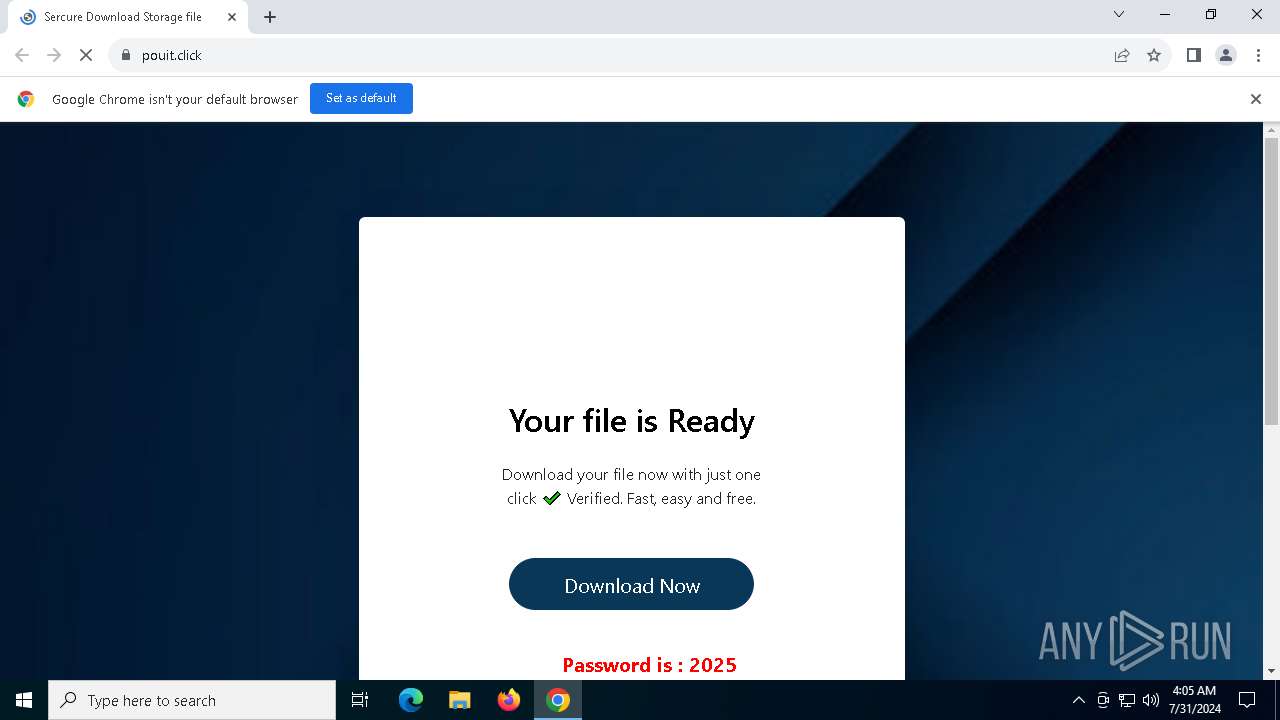
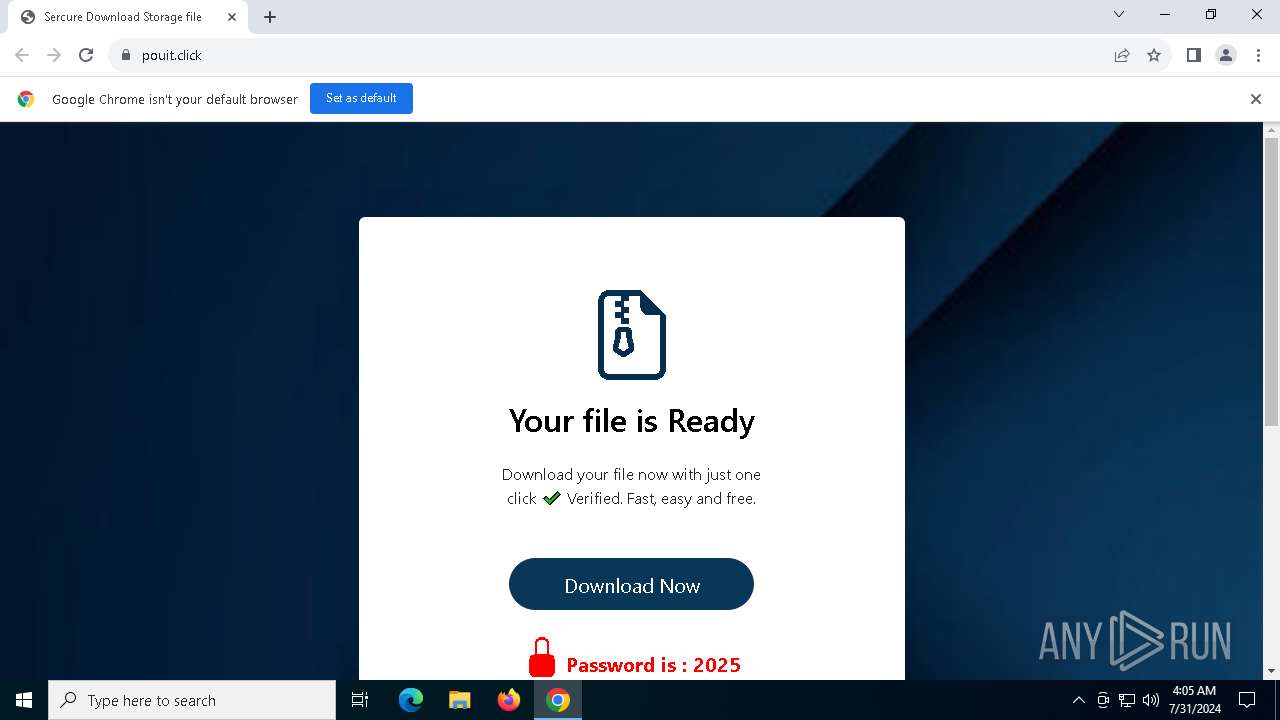
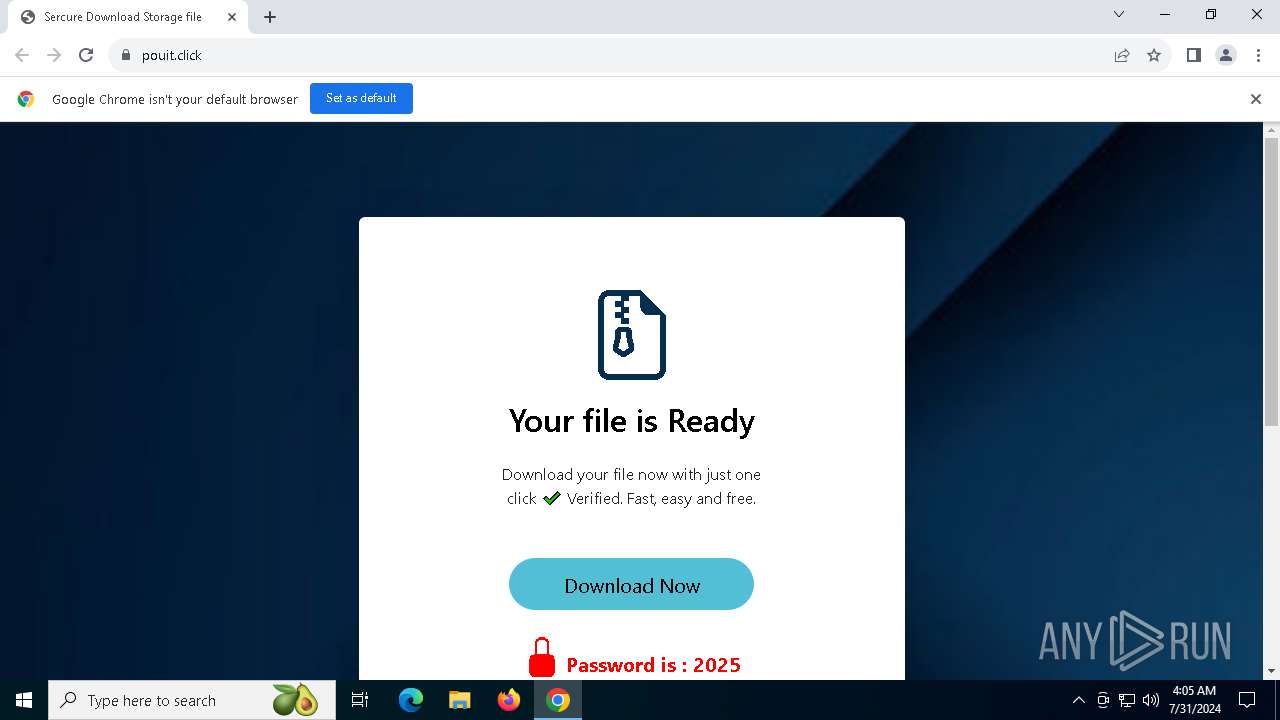
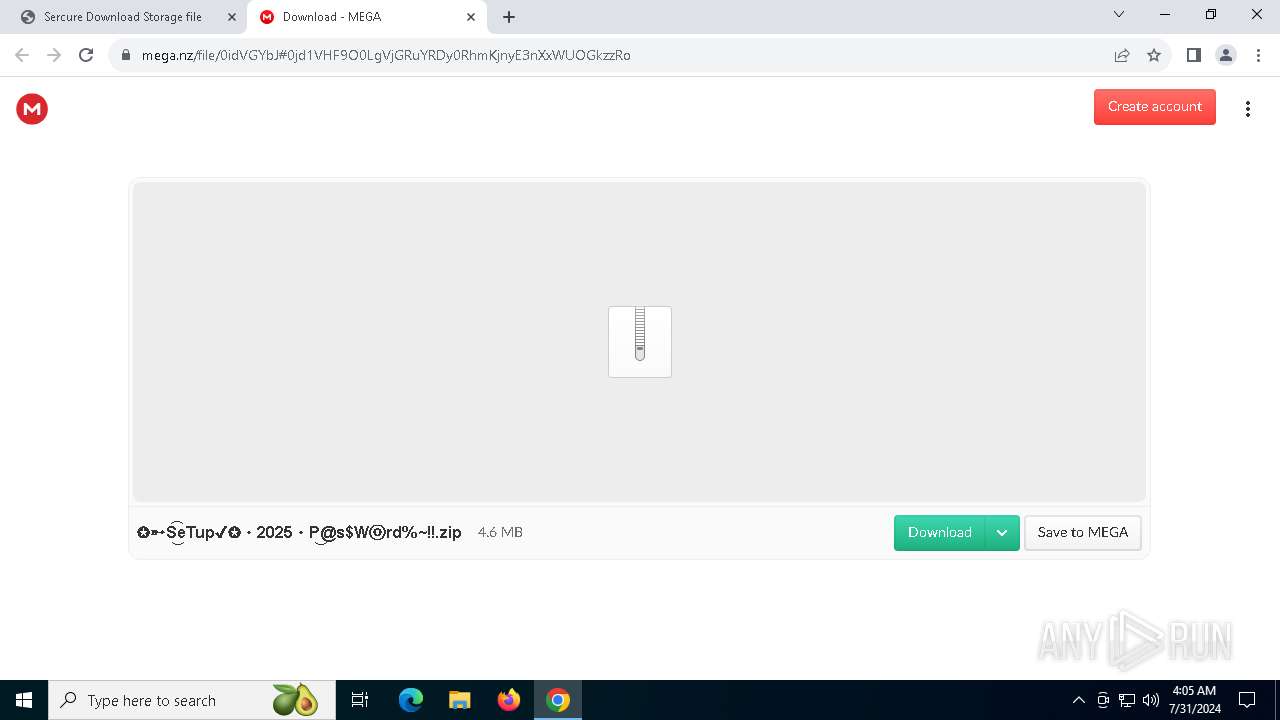
| URL: | https://www.google.com/url?sa=t&source=web&rct=j&opi=89978449&url=https://pouit.click/&ved=2ahUKEwiksJaUsdCHAxWbkO4BHSCGGBYQFnoECBgQAQ&usg=AOvVaw1Gd5F23UYvG9hoTc6GWVMS |
| Full analysis: | https://app.any.run/tasks/b6e66ecf-9bcd-4355-878f-f3d515329589 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 31, 2024, 04:05:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FE15E5A59922562DC1F3A90C59388988 |
| SHA1: | 46132CB9B53E454B691B1FA2734994A73EEDFD9C |
| SHA256: | 9A12AD0A0E5DFD268BEEC0B8261B5381C284DE99015B1F823A0D6141447B282A |
| SSDEEP: | 3:N8DSLI2sljXoW+PhIDNRRVYmZRyJuRNb/WhlBPR80SC09MHLS7mr36T1:2OLI2slQpUNRROmZRymNsjarWHLS7mrs |
MALICIOUS
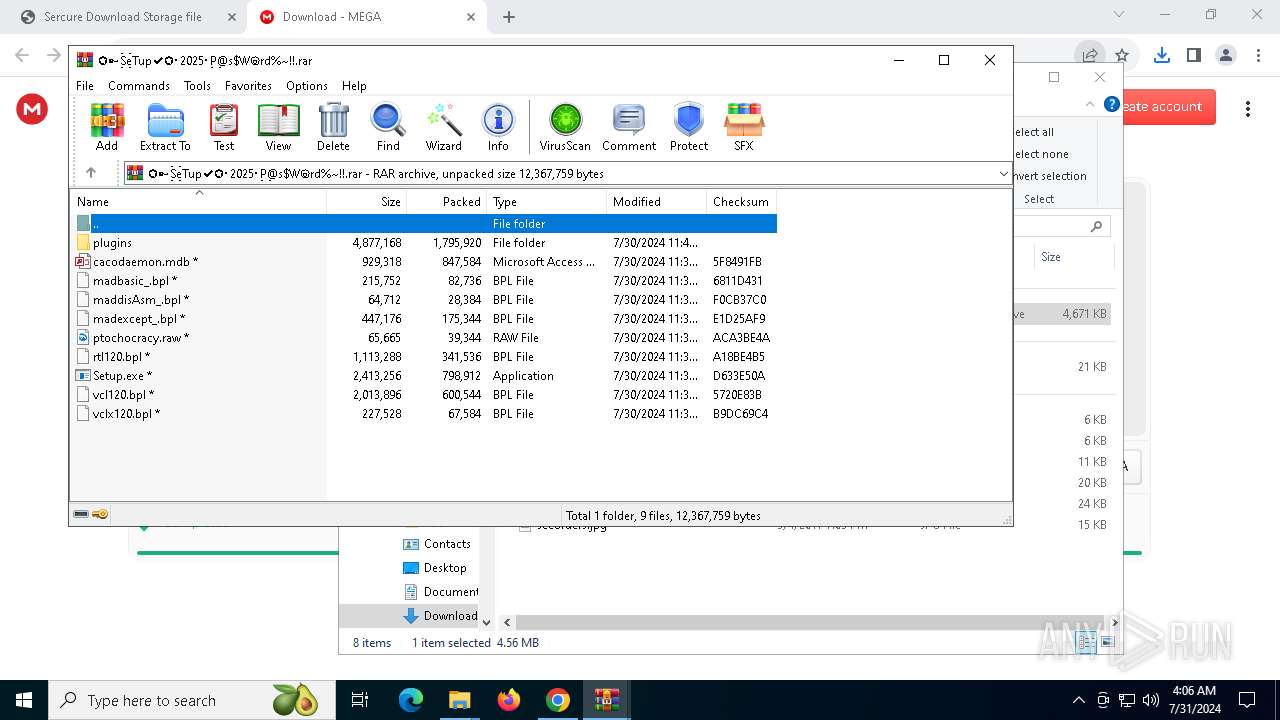
Drops the executable file immediately after the start
- Setup.exe (PID: 7304)
- more.com (PID: 308)
- NuptialsStride.pif (PID: 3940)
Stealers network behavior
- NuptialsStride.pif (PID: 3940)
LUMMA has been detected (SURICATA)
- NuptialsStride.pif (PID: 3940)
Changes powershell execution policy (Bypass)
- NuptialsStride.pif (PID: 3940)
Bypass execution policy to execute commands
- powershell.exe (PID: 7564)
Actions looks like stealing of personal data
- NuptialsStride.pif (PID: 3940)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 7564)
Connects to the CnC server
- explorer.exe (PID: 4320)
AMADEY has been detected (YARA)
- explorer.exe (PID: 4320)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 4320)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7200)
- WinRAR.exe (PID: 4236)
Application launched itself
- WinRAR.exe (PID: 7200)
Potential Corporate Privacy Violation
- chrome.exe (PID: 1328)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6260)
Executable content was dropped or overwritten
- Setup.exe (PID: 7304)
- more.com (PID: 308)
- NuptialsStride.pif (PID: 3940)
Starts application with an unusual extension
- Setup.exe (PID: 7304)
- more.com (PID: 308)
- K3PQN9TL4WOP7F3XMOQ2TQ.exe (PID: 3572)
Drops a file with a rarely used extension (PIF)
- more.com (PID: 308)
Searches for installed software
- NuptialsStride.pif (PID: 3940)
The process executes Powershell scripts
- NuptialsStride.pif (PID: 3940)
Starts POWERSHELL.EXE for commands execution
- NuptialsStride.pif (PID: 3940)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7564)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 7564)
Found regular expressions for crypto-addresses (YARA)
- InstallUtil.exe (PID: 6164)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 4320)
The process executes via Task Scheduler
- magnification.exe (PID: 5732)
INFO
The process uses the downloaded file
- chrome.exe (PID: 8172)
- WinRAR.exe (PID: 7200)
- WinRAR.exe (PID: 5628)
Application launched itself
- chrome.exe (PID: 4584)
Reads Microsoft Office registry keys
- chrome.exe (PID: 4584)
Manual execution by a user
- WinRAR.exe (PID: 7200)
- WinRAR.exe (PID: 5628)
- WinRAR.exe (PID: 6260)
- Setup.exe (PID: 7304)
Checks supported languages
- Setup.exe (PID: 7304)
- NuptialsStride.pif (PID: 3940)
- more.com (PID: 308)
- StrCmp.exe (PID: 3704)
- G56X75J2BFBJMV7H719DG.exe (PID: 7312)
- K3PQN9TL4WOP7F3XMOQ2TQ.exe (PID: 3572)
- more.com (PID: 7800)
- InstallUtil.exe (PID: 6164)
- InstallUtil.exe (PID: 7132)
- magnification.exe (PID: 5732)
Reads the computer name
- Setup.exe (PID: 7304)
- more.com (PID: 308)
- NuptialsStride.pif (PID: 3940)
- StrCmp.exe (PID: 3704)
- G56X75J2BFBJMV7H719DG.exe (PID: 7312)
- K3PQN9TL4WOP7F3XMOQ2TQ.exe (PID: 3572)
- more.com (PID: 7800)
- magnification.exe (PID: 5732)
Creates files or folders in the user directory
- Setup.exe (PID: 7304)
- G56X75J2BFBJMV7H719DG.exe (PID: 7312)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6260)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6260)
Create files in a temporary directory
- Setup.exe (PID: 7304)
- more.com (PID: 308)
- NuptialsStride.pif (PID: 3940)
- K3PQN9TL4WOP7F3XMOQ2TQ.exe (PID: 3572)
- more.com (PID: 7800)
Checks proxy server information
- slui.exe (PID: 7660)
- explorer.exe (PID: 4320)
Reads the software policy settings
- slui.exe (PID: 7660)
- NuptialsStride.pif (PID: 3940)
Reads the machine GUID from the registry
- G56X75J2BFBJMV7H719DG.exe (PID: 7312)
- magnification.exe (PID: 5732)
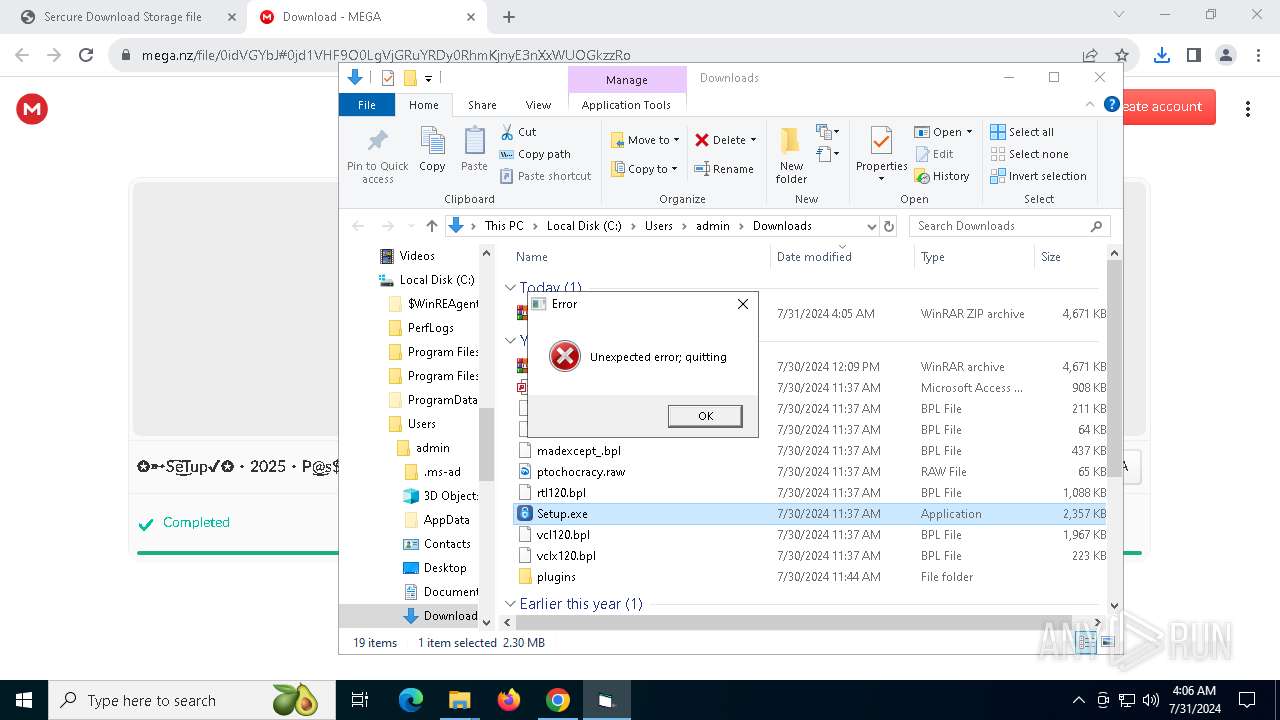
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7564)
.NET Reactor protector has been detected
- G56X75J2BFBJMV7H719DG.exe (PID: 7312)
Creates files in the program directory
- InstallUtil.exe (PID: 6164)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(4320) explorer.exe
C2brasseriehub.com
Strings (123)ProductName
vs:
ComputerName
"
AVG
https://
Bitdefender
\App
AVAST Software
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
rb
Content-Type: multipart/form-data; boundary=----
brasseriehub2.com
------
Kaspersky Lab
DefaultSettings.YResolution
+++
ps1
random
&& Exit"
/h9fmdW6/index.php
&unit=
id:
VideoID
shutdown -s -t 0
brasseriehub.com
rundll32
=
-unicode-
:::
Content-Disposition: form-data; name="data"; filename="
dm:
/h9fmdW5/index.php
-executionpolicy remotesigned -File "
dll
og:
r=
2022
cmd
un:
kernel32.dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Avira
\
/quiet
" && timeout 1 && del
Content-Type: application/x-www-form-urlencoded
http://
SOFTWARE\Microsoft\Windows NT\CurrentVersion
-%lu
ProgramData\
Norton
av:
lv:
wb
Programs
fa94c59947
<d>
e1
rundll32.exe
msi
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
abcdefghijklmnopqrstuvwxyz0123456789-_
ESET
/h9fmdW7/index.php
st=s
Rem
cmd /C RMDIR /s/q
SYSTEM\ControlSet001\Services\BasicDisplay\Video
GET
cred.dll|clip.dll|
d1
/Plugins/
0123456789
exe
cred.dll
e0
Powershell.exe
.jpg
POST
CurrentBuild
%USERPROFILE%
"
Content-Type: application/octet-stream
os:
sd:
360TotalSecurity
2019
Panda Security
\0000
shell32.dll
S-%lu-
WinDefender
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
bi:
&&
4.41
%-lu
Startup
clip.dll
------
pc:
Sophos
"taskkill /f /im "
e2
Hkbsse.exe
2016
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
brasseriehub.com3
" && ren
/k
--
Comodo
?scr=1
#
|
zip
Main
<c>
GetNativeSystemInfo
ar:
DefaultSettings.XResolution
Doctor Web
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Total processes
185
Monitored processes
36
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2172 --field-trial-handle=1952,i,18002293129452404710,4142507686131214483,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2000 --field-trial-handle=1952,i,18002293129452404710,4142507686131214483,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1956 --field-trial-handle=1952,i,18002293129452404710,4142507686131214483,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4004 --field-trial-handle=1952,i,18002293129452404710,4142507686131214483,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3028 --field-trial-handle=1952,i,18002293129452404710,4142507686131214483,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3572 | "C:\Users\admin\AppData\Local\Temp\K3PQN9TL4WOP7F3XMOQ2TQ.exe" | C:\Users\admin\AppData\Local\Temp\K3PQN9TL4WOP7F3XMOQ2TQ.exe | — | NuptialsStride.pif | |||||||||||
User: admin Company: ASUSTek Computer Inc. Integrity Level: MEDIUM Description: LightingService Exit code: 1 Version: 3.07.25.0 Modules
| |||||||||||||||
| 3704 | C:\Users\admin\AppData\Roaming\uico\BSXMRYFEUFPZQVQVZJJCIN\StrCmp.exe | C:\Users\admin\AppData\Roaming\uico\BSXMRYFEUFPZQVQVZJJCIN\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3940 | C:\Users\admin\AppData\Local\Temp\NuptialsStride.pif | C:\Users\admin\AppData\Local\Temp\NuptialsStride.pif | more.com | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4236 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa7200.6877\✪➳S͜͡eTup✔✪・2025・P͜@s$Wⓞrd%~!!.rar | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
29 720
Read events
29 601
Write events
118
Delete events
1
Modification events
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4584) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
22
Suspicious files
106
Text files
53
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1c1228.TMP | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1c1228.TMP | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 4584 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
95
DNS requests
62
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6476 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7732 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/p2zbkxfgkqyr6ljey2oe3bnzoy_2023.11.29.1201/ggkkehgbnfjpeggfpleeakpidbkibbmn_2023.11.29.1201_all_acqy67ncydhwie54b6ghdtndubgq.crx3 | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1704 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7732 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/p2zbkxfgkqyr6ljey2oe3bnzoy_2023.11.29.1201/ggkkehgbnfjpeggfpleeakpidbkibbmn_2023.11.29.1201_all_acqy67ncydhwie54b6ghdtndubgq.crx3 | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7732 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/p2zbkxfgkqyr6ljey2oe3bnzoy_2023.11.29.1201/ggkkehgbnfjpeggfpleeakpidbkibbmn_2023.11.29.1201_all_acqy67ncydhwie54b6ghdtndubgq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3332 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2956 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1328 | chrome.exe | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
www.google.com |
| whitelisted |
accounts.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in DNS Lookup (bablosoft .com) |
1328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in DNS Lookup (bablosoft .com) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in TLS SNI (bablosoft .com) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Fingerprinting Service in TLS SNI (customfingerprints .bablosoft .com) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Fingerprinting Service in DNS Lookup (customfingerprints .bablosoft .com) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Fingerprinting Service in DNS Lookup (customfingerprints .bablosoft .com) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in DNS Lookup (bablosoft .com) |
1328 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1328 | chrome.exe | Potential Corporate Privacy Violation | ET INFO Browser Automation Toolkit in TLS SNI (bablosoft .com) |
1 ETPRO signatures available at the full report