| File name: | 99e41bc7e38faf44b40023884d4e14168c6e259f807ab5fbe3b1ba2e1512ce4c.docx |
| Full analysis: | https://app.any.run/tasks/f3563c39-db1c-475a-bfcc-904cf2674931 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | November 08, 2018, 06:35:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 05BF3453CC17CF2FB0CC849FEAD0D3C2 |
| SHA1: | A58D0068723F3F3340C9F111460C6D9B5DAD794C |
| SHA256: | 99E41BC7E38FAF44B40023884D4E14168C6E259F807AB5FBE3B1BA2E1512CE4C |
| SSDEEP: | 192:htmm0ZQf4QtK57yMtWNU00mqQTnhr5OWQT1Q7dP55SzZbFTB8GoA6aukWJmf:htmdQztsyMtiU2LOWQT1Q7dDSzzdaHmf |
MALICIOUS
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 3288)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3288)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 3288)
Application was dropped or rewritten from another process
- wiinilog.exe (PID: 2596)
Downloads executable files from IP
- EQNEDT32.EXE (PID: 3288)
SUSPICIOUS
Creates files in the user directory
- EQNEDT32.EXE (PID: 3288)
Executable content was dropped or overwritten
- wiinilog.exe (PID: 2596)
- EQNEDT32.EXE (PID: 3288)
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 3704)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3704)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:11:07 09:06:14 |
| ZipCRC: | 0x82872409 |
| ZipCompressedSize: | 358 |
| ZipUncompressedSize: | 1422 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | dotm.dotm |
|---|---|
| TotalEditTime: | 1 minute |
| Pages: | 1 |
| Words: | 1 |
| Characters: | 7 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | SPecialiST RePack |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 7 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 14 |
| LastModifiedBy: | Microsoft |
| RevisionNumber: | 1 |
| CreateDate: | 2017:09:24 17:26:00Z |
| ModifyDate: | 2017:09:24 17:27:00Z |
XMP
| Creator: | Microsoft |
|---|
Total processes
34
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2596 | "C:\Users\admin\AppData\Roaming\wiinilog.exe" | C:\Users\admin\AppData\Roaming\wiinilog.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3288 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3704 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\99e41bc7e38faf44b40023884d4e14168c6e259f807ab5fbe3b1ba2e1512ce4c.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
748
Read events
675
Write events
65
Delete events
8
Modification events
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | /n$ |
Value: 2F6E2400780E0000010000000000000000000000 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1298661393 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1298661508 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1298661509 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 780E0000687F8F4F2D77D40100000000 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | kn$ |
Value: 6B6E2400780E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | kn$ |
Value: 6B6E2400780E000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3704) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
5
Suspicious files
25
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2E2F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{706203E7-B9EC-49B0-A795-7A7D983B4B87} | — | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{60157C6E-6759-4130-96DB-BBFF7D5FD502} | — | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A0C26F31.doc | — | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BA226967.doc | — | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{6E5848D7-2C31-451F-86E2-DE5B4F138975}.FSD | binary | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3CD621AA.doc | text | |
MD5:— | SHA256:— | |||
| 3704 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{AE61C987-E616-4505-ABA6-3CB40E2558A2}.FSD | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
14
DNS requests
3
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
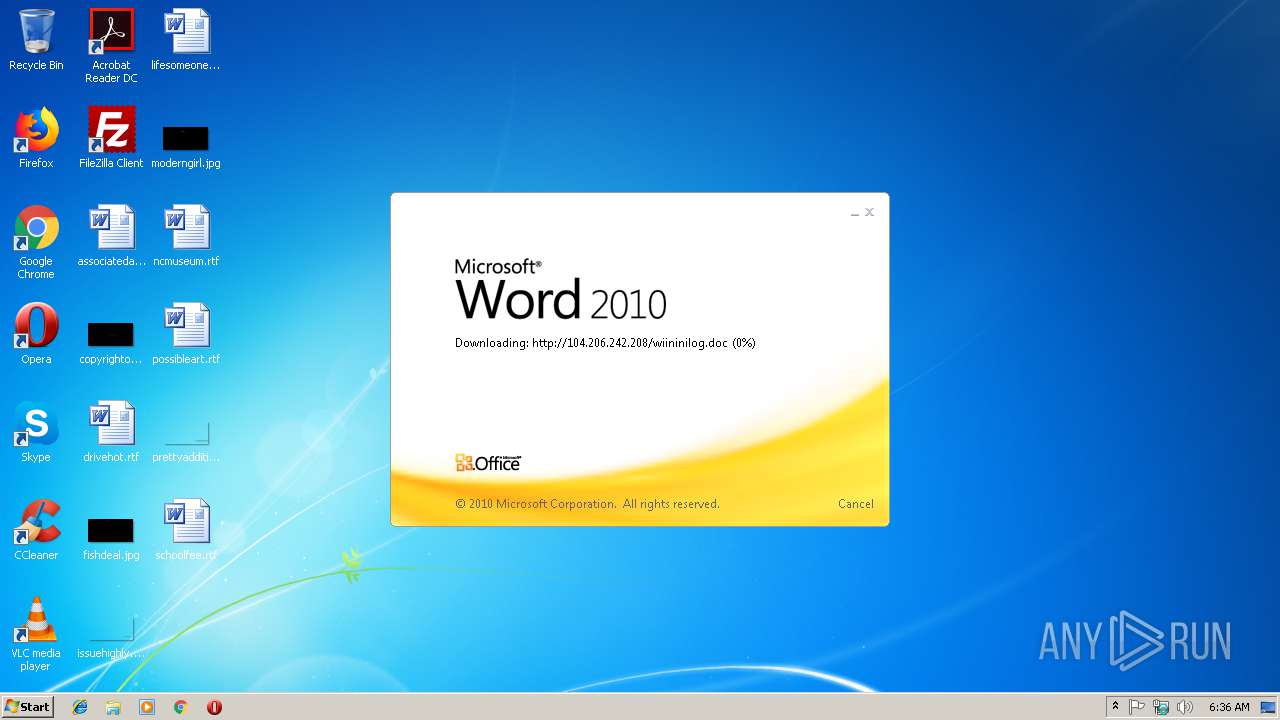
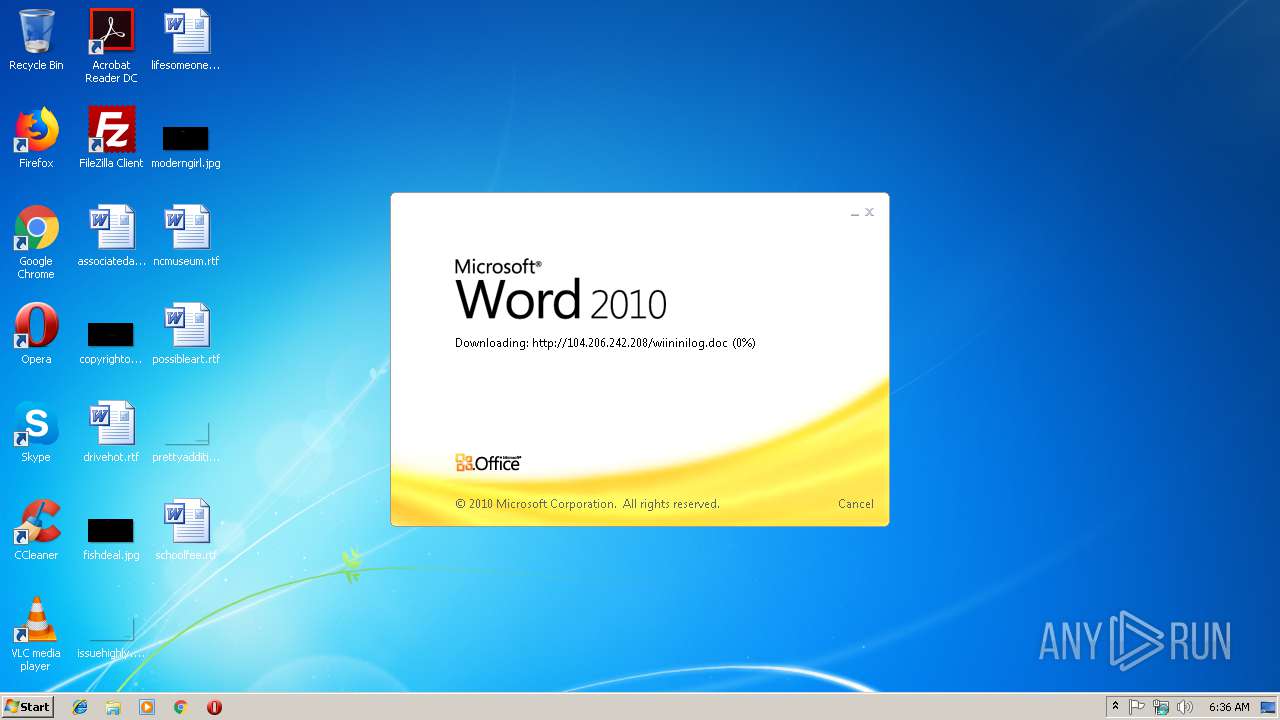
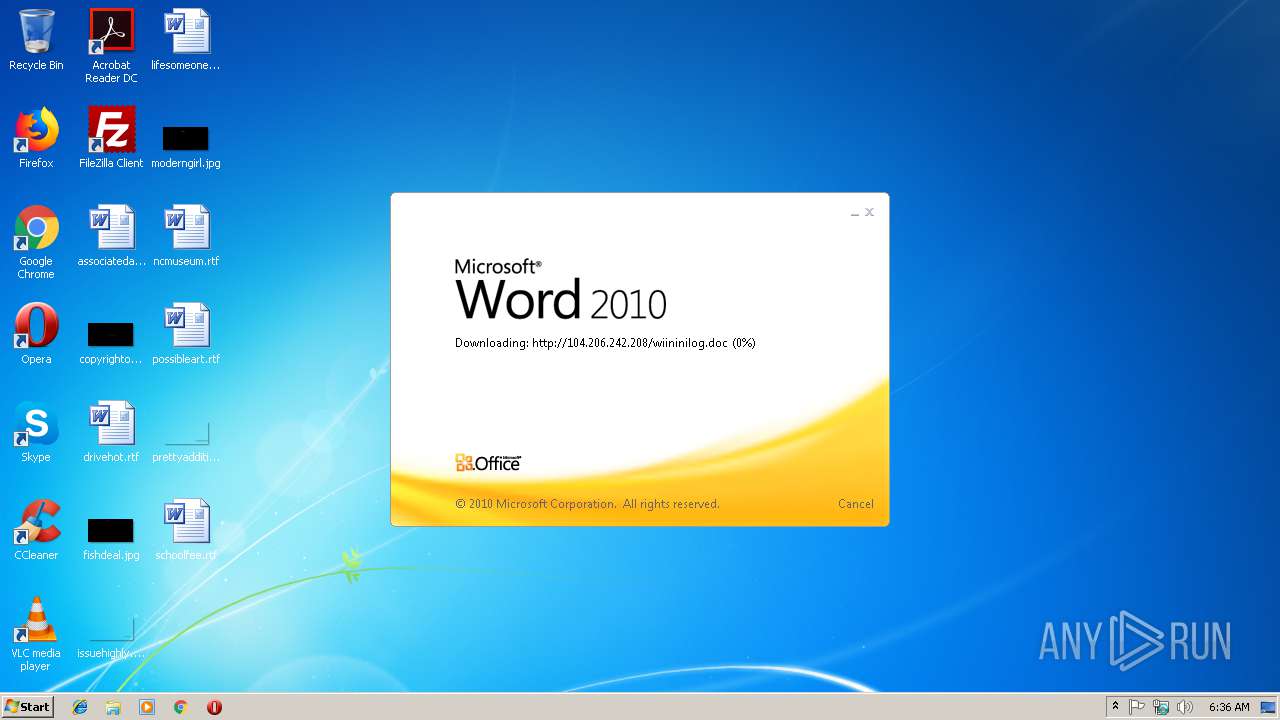
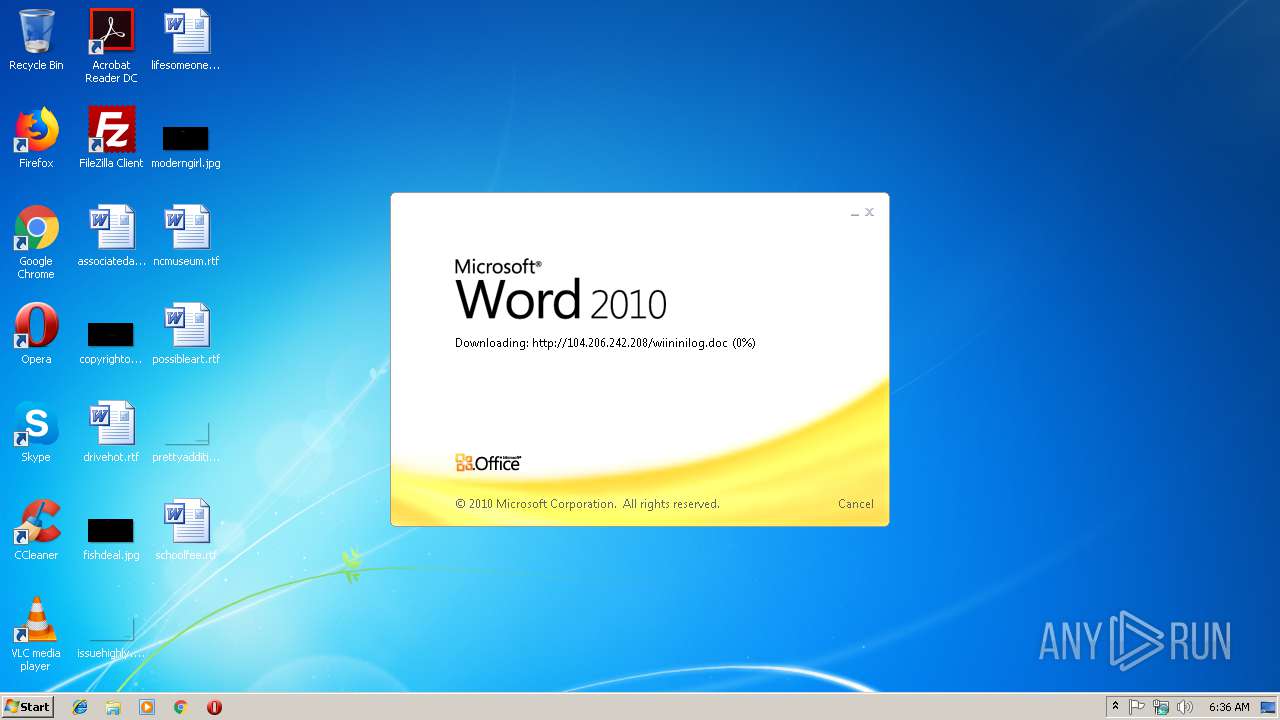
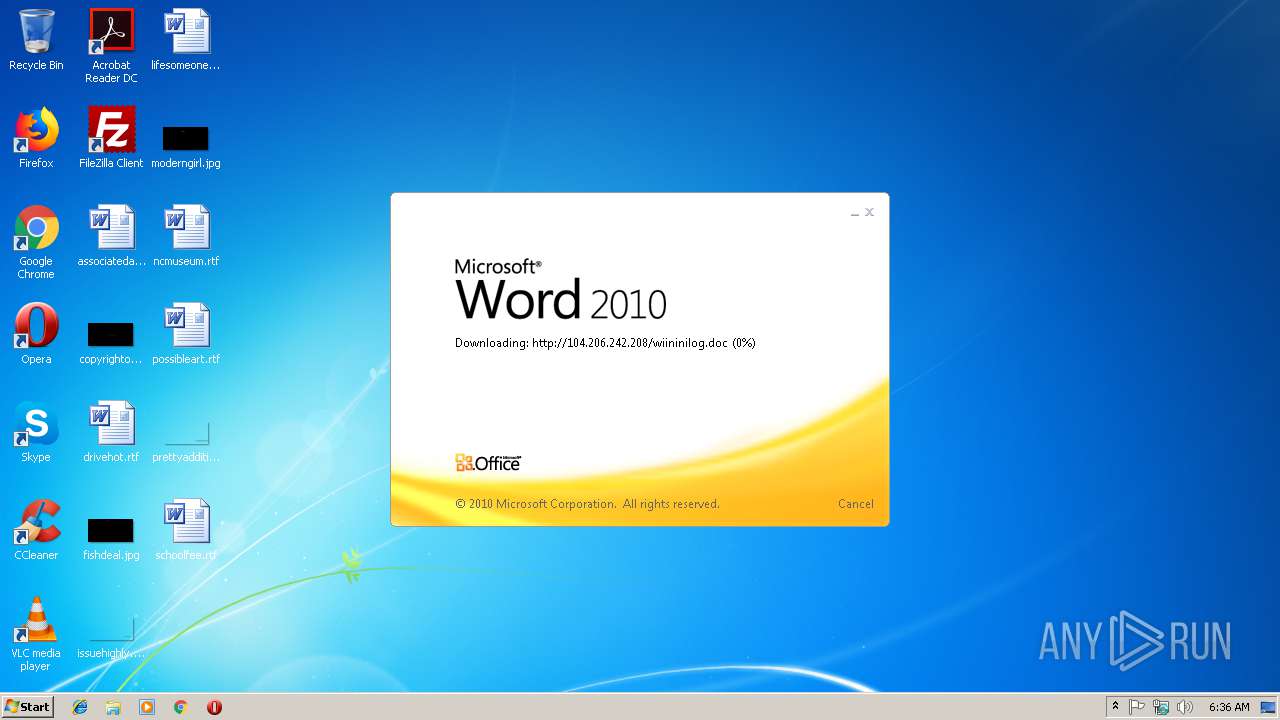
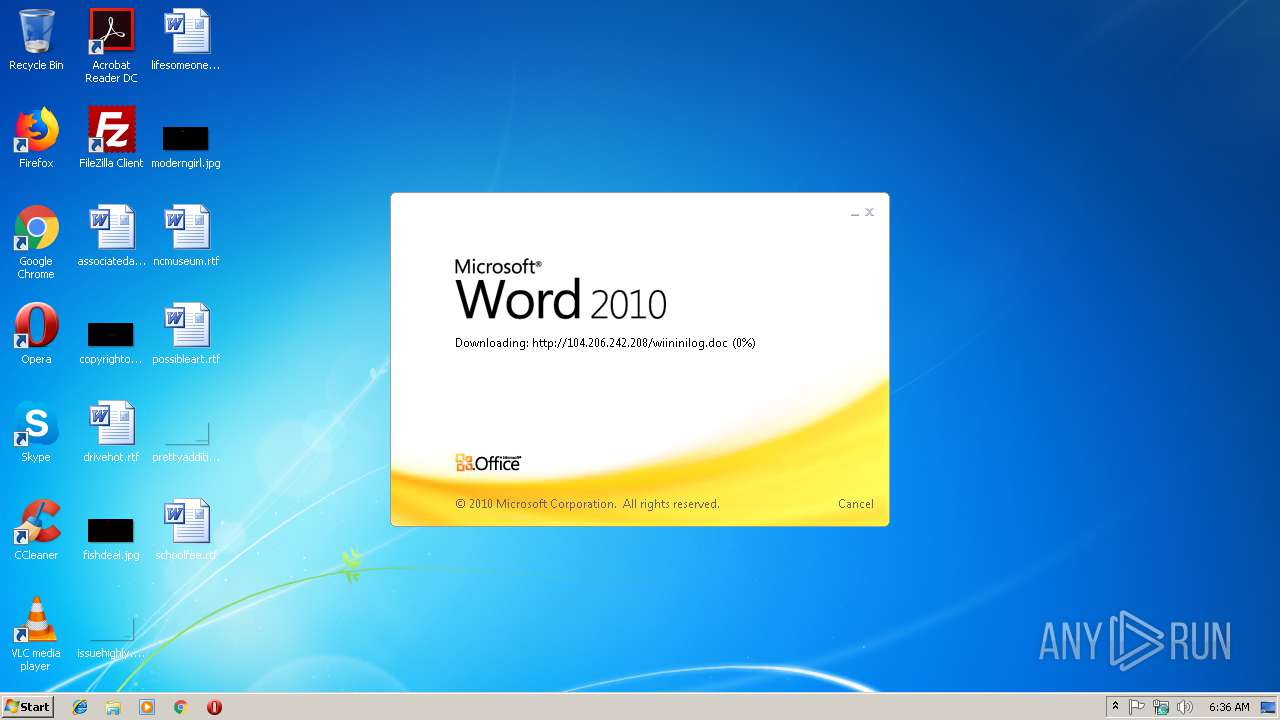
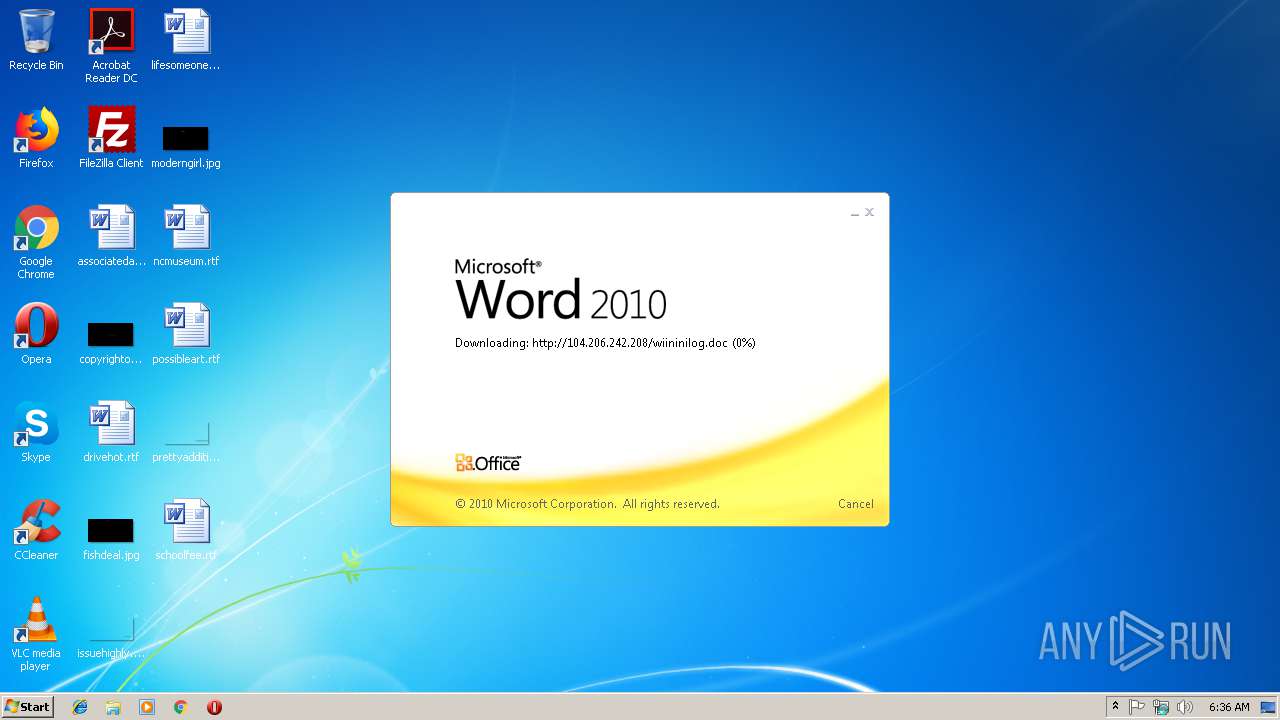
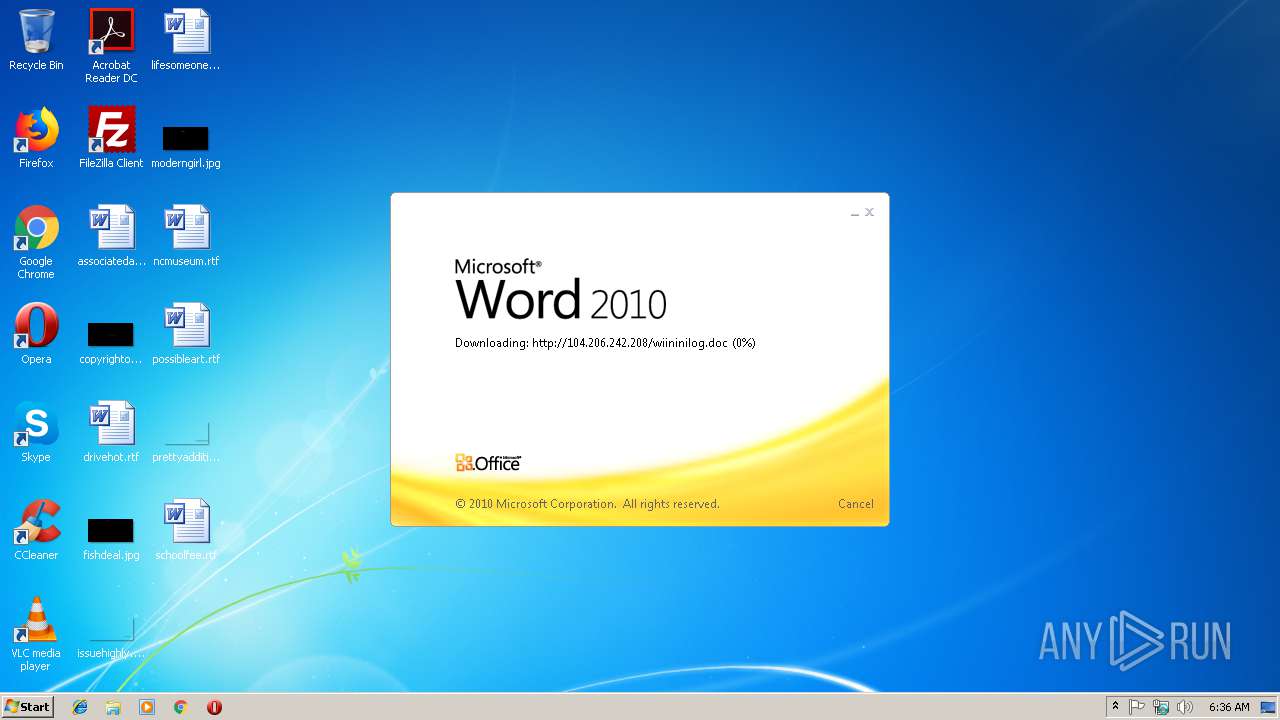
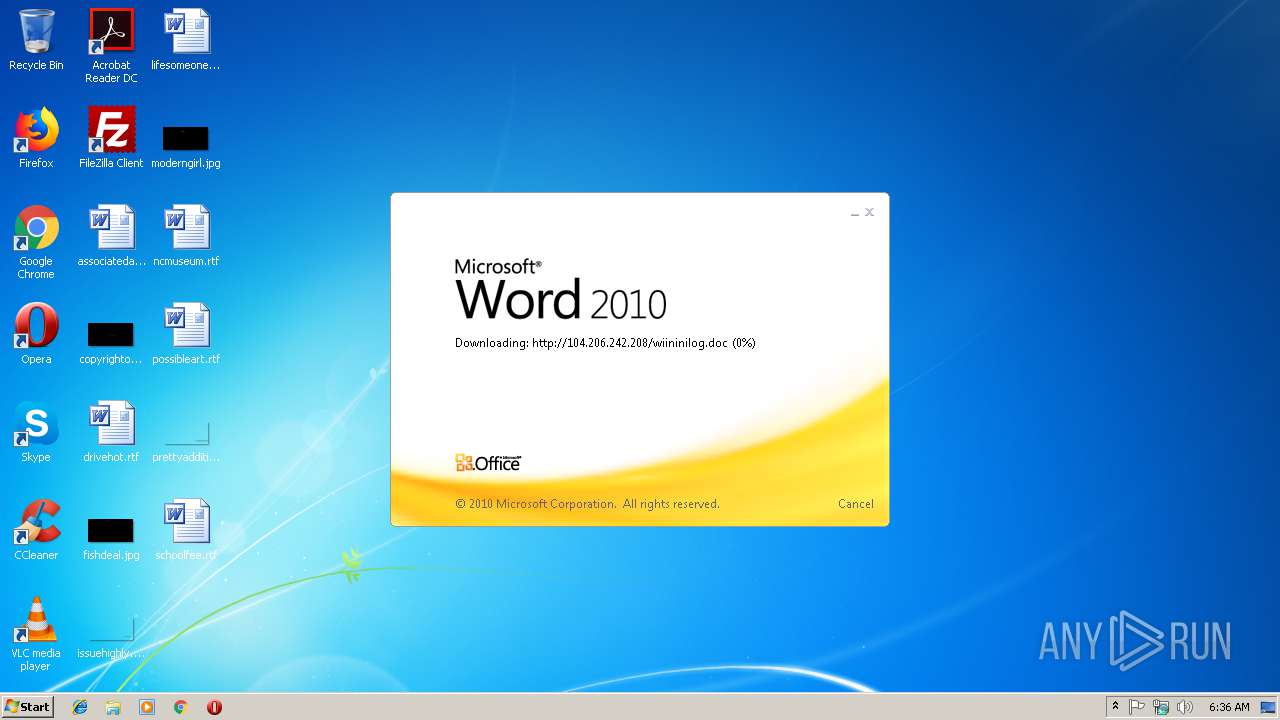
3704 | WINWORD.EXE | HEAD | 200 | 104.206.242.208:80 | http://104.206.242.208/wiininilog.doc | US | — | — | suspicious |
3704 | WINWORD.EXE | HEAD | 200 | 104.206.242.208:80 | http://104.206.242.208/wiininilog.doc | US | — | — | suspicious |
3704 | WINWORD.EXE | GET | 304 | 104.206.242.208:80 | http://104.206.242.208/wiininilog.doc | US | — | — | suspicious |
3704 | WINWORD.EXE | HEAD | 200 | 104.206.242.208:80 | http://104.206.242.208/wiininilog.doc | US | — | — | suspicious |
964 | svchost.exe | PROPFIND | 405 | 104.206.242.208:80 | http://104.206.242.208/ | US | html | 317 b | suspicious |
3704 | WINWORD.EXE | GET | 200 | 104.206.242.208:80 | http://104.206.242.208/wiininilog.doc | US | text | 7.18 Kb | suspicious |
964 | svchost.exe | PROPFIND | 405 | 104.206.242.208:80 | http://104.206.242.208/ | US | html | 317 b | suspicious |
964 | svchost.exe | PROPFIND | 405 | 104.206.242.208:80 | http://104.206.242.208/ | US | html | 317 b | suspicious |
3704 | WINWORD.EXE | HEAD | 200 | 104.206.242.208:80 | http://104.206.242.208/wiininilog.doc | US | text | 7.18 Kb | suspicious |
964 | svchost.exe | PROPFIND | 405 | 104.206.242.208:80 | http://104.206.242.208/ | US | html | 317 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
964 | svchost.exe | 104.206.242.208:80 | — | Eonix Corporation | US | suspicious |
3704 | WINWORD.EXE | 104.206.242.208:80 | — | Eonix Corporation | US | suspicious |
3288 | EQNEDT32.EXE | 104.206.242.208:80 | — | Eonix Corporation | US | suspicious |
— | — | 46.229.214.47:80 | dogoodtome.bit | — | RU | malicious |
— | — | 91.217.137.44:53 | — | Meganet-2003 LLC | RU | unknown |
— | — | 151.80.147.153:53 | — | OVH SAS | FR | malicious |
— | — | 80.233.248.109:53 | — | SIA PostMet | LV | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dogoodtome.bit |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3704 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3704 | WINWORD.EXE | A Network Trojan was detected | MALWARE [PTsecurity] Possible RTF CVE-2017-11882 document |
3288 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
3288 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3288 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
3288 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
3288 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
— | — | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
— | — | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |
— | — | Potentially Bad Traffic | ET CURRENT_EVENTS DNS Query Domain .bit |