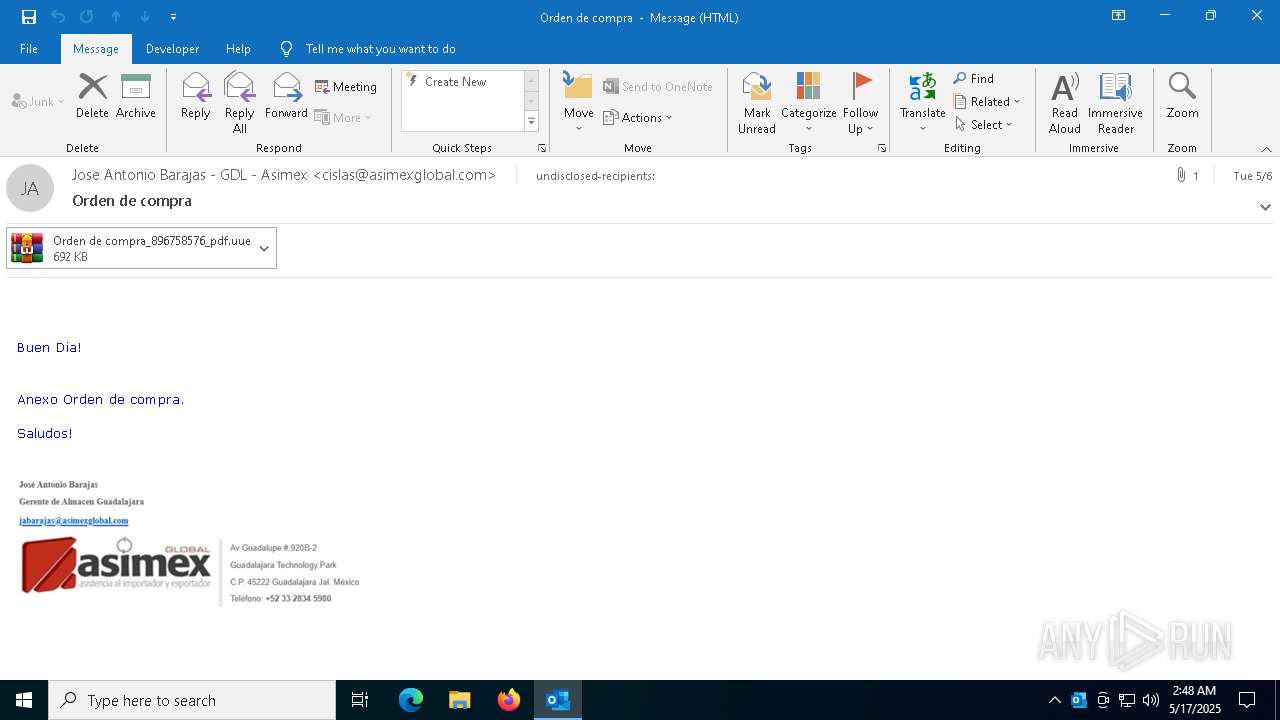
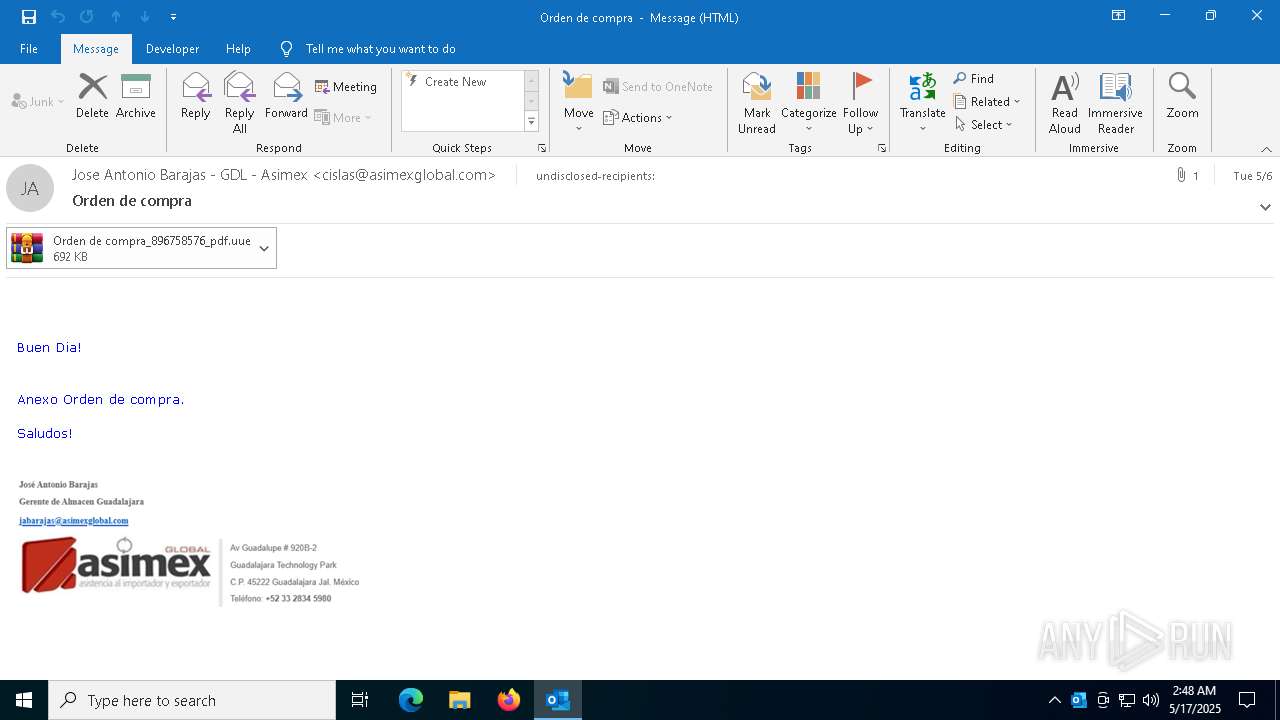
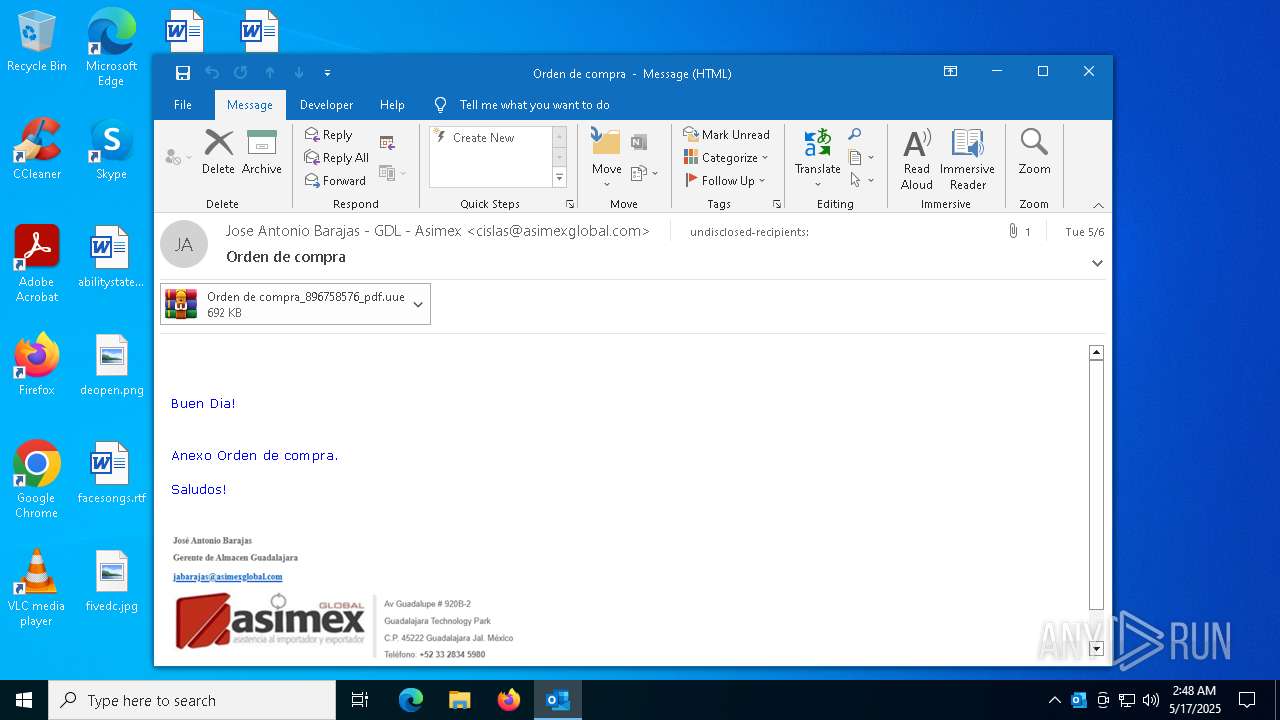
| File name: | Orden de compra.eml |
| Full analysis: | https://app.any.run/tasks/97f4655b-5d38-44f8-8cd5-e532e51019d3 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 17, 2025, 02:48:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 610133724927F138608AB3F016B52A30 |
| SHA1: | 292C6992D1A61E3B35D3741A3C3BD1FEFA985287 |
| SHA256: | 99D3E781968BA117811CB28EF4B8CD522BD535A6C17552D679A3F7C47D2868A1 |
| SSDEEP: | 24576:AsERJuW4UJf7JsPIHXzPTRCjGSBD0C+/ENR6i:MBjXHSBL+/Ex |
MALICIOUS
AGENTTESLA has been detected (YARA)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
Actions looks like stealing of personal data
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
Steals credentials from Web Browsers
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
AGENTTESLA has been detected (SURICATA)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 632)
SUSPICIOUS
The process creates files with name similar to system file names
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
Executable content was dropped or overwritten
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 5608)
Malware-specific behavior (creating "System.dll" in Temp)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 5608)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
Application launched itself
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 5608)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
Connects to the server without a host name
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 632)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
Reads security settings of Internet Explorer
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
Checks for external IP
- svchost.exe (PID: 2196)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 632)
- svchost.exe (PID: 2180)
Connects to SMTP port
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 632)
Contacting a server suspected of hosting an CnC
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 632)
There is functionality for taking screenshot (YARA)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3008)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2088)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 5608)
The sample compiled with english language support
- OUTLOOK.EXE (PID: 2136)
Java executable
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 632)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 5608)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 8020)
Create files in a temporary directory
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
Checks supported languages
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
Reads the computer name
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 6592)
Creates files or folders in the user directory
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7464)
Checks proxy server information
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
Disables trace logs
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
Reads the software policy settings
- slui.exe (PID: 7296)
Reads the machine GUID from the registry
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(7412) Orden de compra_896758576568857657858756857645674656745677.exe
Protocolsmtp
Hostmail.rvoccte.com
Port587
Usernamenewfile@rvoccte.com
PasswordPJtiky;+*ayY
(PID) Process(8020) Orden de compra_896758576568857657858756857645674656745677.exe
Protocolsmtp
Hostmail.rvoccte.com
Port587
Usernamenewfile@rvoccte.com
PasswordPJtiky;+*ayY
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
302
Monitored processes
15
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe" | C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe | Orden de compra_896758576568857657858756857645674656745677.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Version: 8.0.4510.0 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Orden de compra_896758576_pdf.uue" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\Orden de compra.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2180 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3008 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5608 | "C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe" | C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 0 Version: 8.0.4510.0 Modules
| |||||||||||||||
| 6592 | "C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe" | C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 0 Version: 8.0.4510.0 Modules
| |||||||||||||||
| 7264 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 401
Read events
17 561
Write events
1 714
Delete events
126
Modification events
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\2136 |
| Operation: | write | Name: | 0 |
Value: 0B0E100CD702D396EF5049801C4C9FABB1BC31230046EEB38CF5E2DAF1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D810D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (2136) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
5
Suspicious files
73
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2088 | WinRAR.exe | C:\Users\admin\Desktop\Orden de compra_896758576568857657858756857645674656745677.exe | — | |
MD5:— | SHA256:— | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:8E3D1C875974EB82FF41DD5B680174AE | SHA256:E42A902964D73B7AAE4F1FB3AAF38732301A9A14462EA559ED190DE957C805BA | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:B47CAC5D9E014DD9F5986E5F12596F0E | SHA256:70B9330F8BFBF2B4E8589476D7F792476BF72024F75205FF776EFDD4E28D4FA9 | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\V3NMOFM5\Orden de compra_896758576_pdf.uue:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:E9F30F590F26B118CDBFFB43F87C9A5E | SHA256:19C4F7AC10B97C7CB93F2086601B02B7BF8209164B016C8390F8B9CFE5040E8C | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFB1951A16F0EE960F.TMP | binary | |
MD5:8E25FA50277CC16E296E9464B6927642 | SHA256:1C941A727607667F46FF604F366E2A5CA9EA2DFEBA6F2B3E55FDE617010A8F7D | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFDC00A13BBEC17CE5.TMP | binary | |
MD5:421F4AECCE34DBDC0F0DDBBD73310707 | SHA256:8B29BCE07AFE4ECD56648540294DEC0AC79FE5FEFE6942E7191990974D23244B | |||
| 2136 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{DCE25F94-F33D-40E5-A340-CE490A3DBB70}.tmp | binary | |
MD5:2EB0AD78250788058FF9E56CB016F60C | SHA256:7B43853DCE03A59C8962F1E11C1A8BCE93F5915FC82E0EF7C22AD549AA21B130 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
84
DNS requests
37
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6708 | RUXIMICS.exe | GET | 200 | 2.19.250.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.250.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.19.250.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6708 | RUXIMICS.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2136 | OUTLOOK.EXE | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5428 | SIHClient.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5428 | SIHClient.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6708 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6708 | RUXIMICS.exe | 2.19.250.172:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.250.172:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 2.19.250.172:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6708 | RUXIMICS.exe | 2.20.154.94:80 | www.microsoft.com | Telkom-Internet | ZA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.154.94:80 | www.microsoft.com | Telkom-Internet | ZA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7412 | Orden de compra_896758576568857657858756857645674656745677.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7412 | Orden de compra_896758576568857657858756857645674656745677.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7412 | Orden de compra_896758576568857657858756857645674656745677.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
7412 | Orden de compra_896758576568857657858756857645674656745677.exe | Malware Command and Control Activity Detected | ET MALWARE MSIL/Kryptik.XSY Data Exfil via SMTP |
7412 | Orden de compra_896758576568857657858756857645674656745677.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
7412 | Orden de compra_896758576568857657858756857645674656745677.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration SMTP (Base64 encoded) |
8020 | Orden de compra_896758576568857657858756857645674656745677.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
8020 | Orden de compra_896758576568857657858756857645674656745677.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |