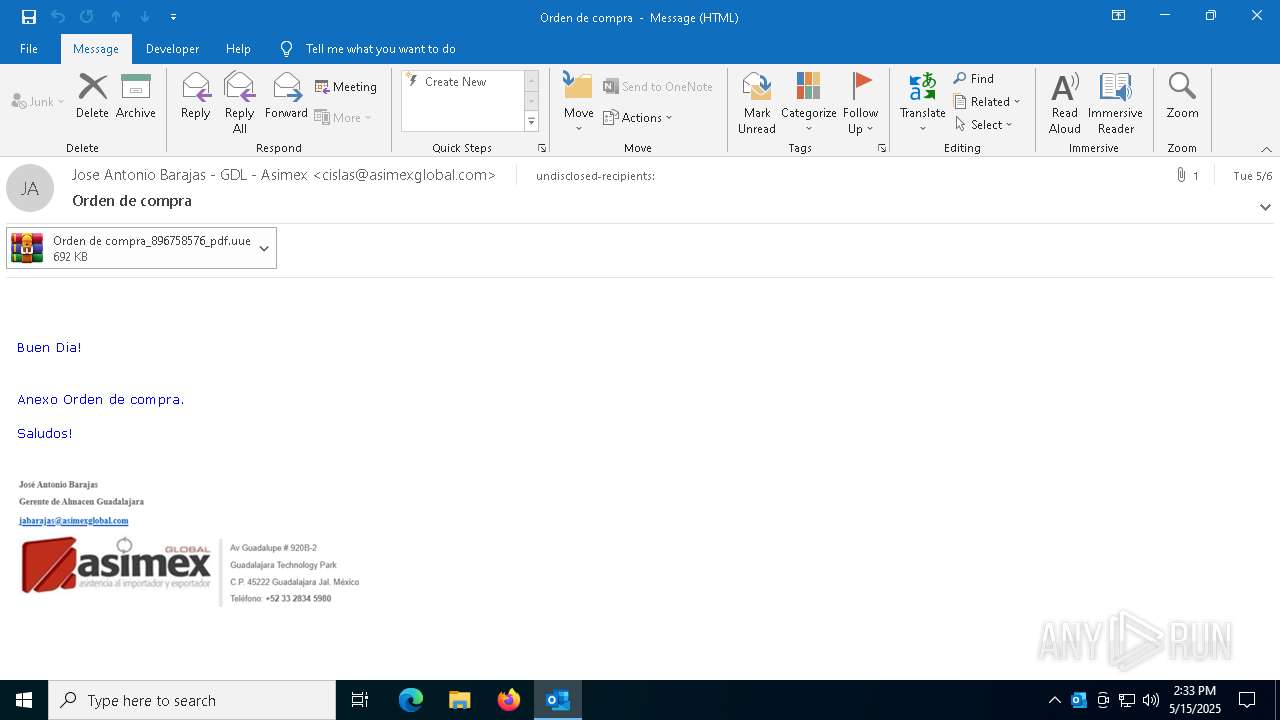
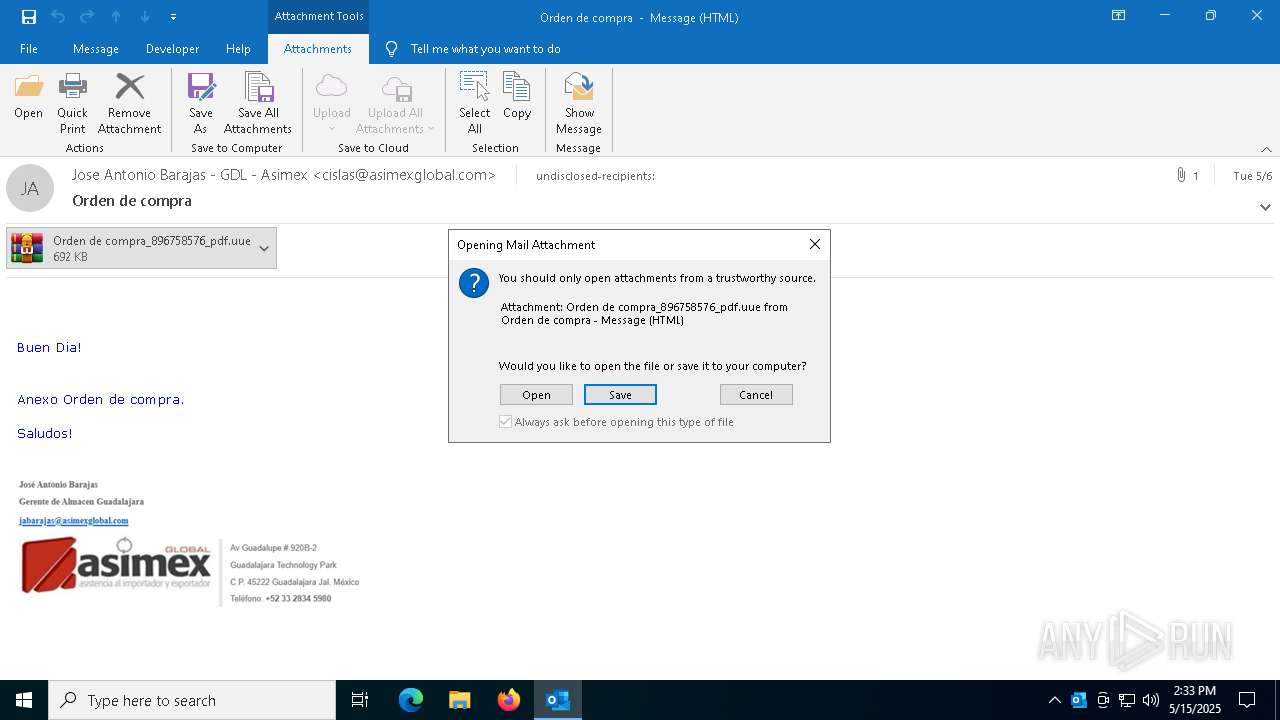
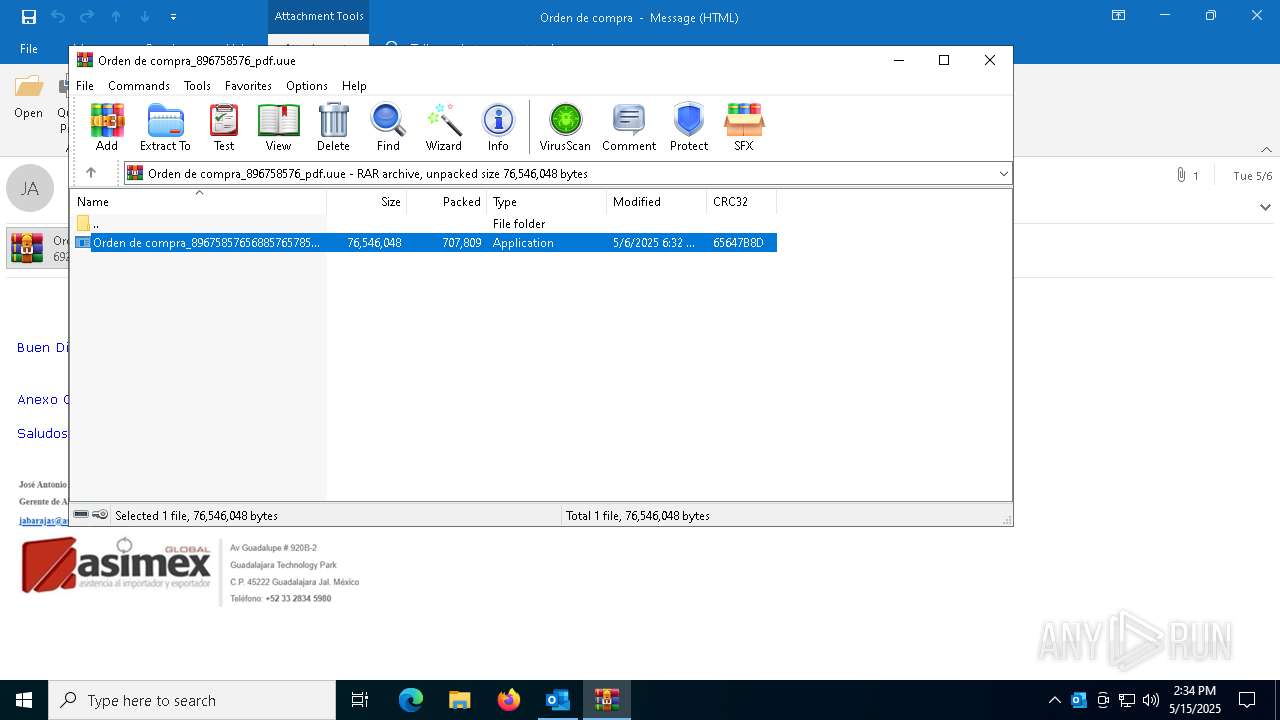
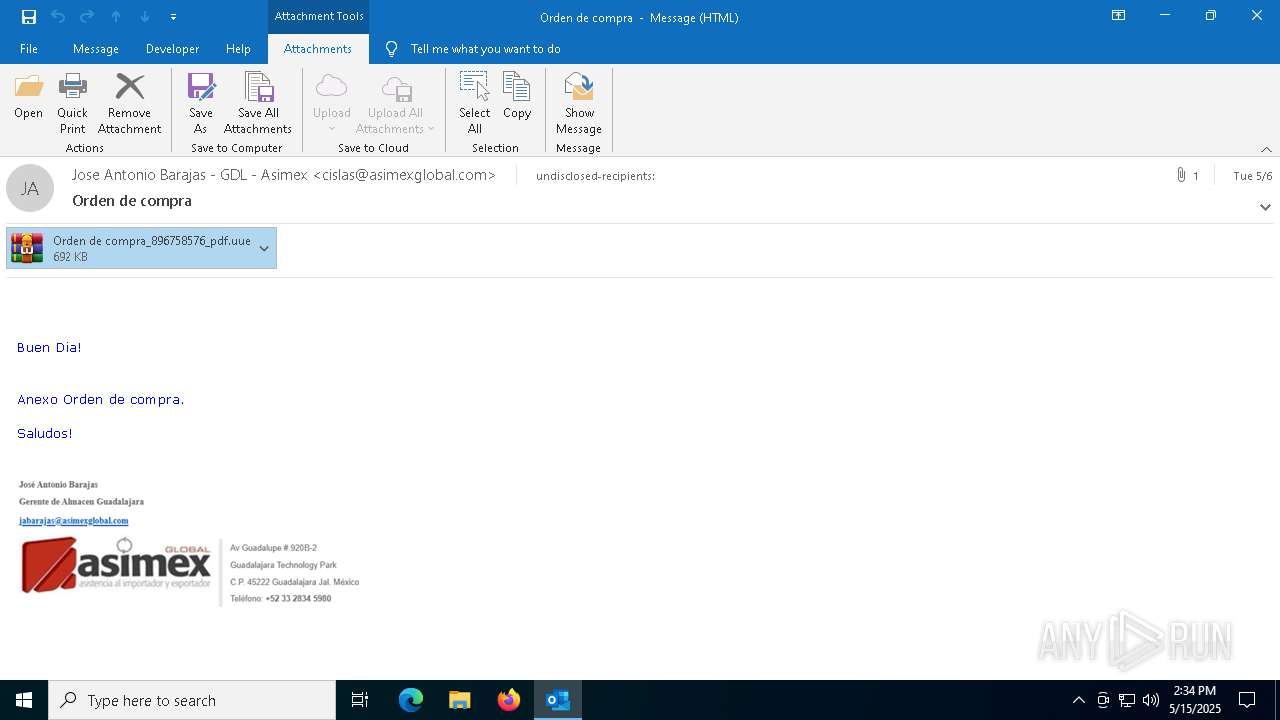
| File name: | Orden de compra.eml |
| Full analysis: | https://app.any.run/tasks/78884589-9d23-4b3c-9f7c-fe0694e0cce0 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 15, 2025, 14:33:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 610133724927F138608AB3F016B52A30 |
| SHA1: | 292C6992D1A61E3B35D3741A3C3BD1FEFA985287 |
| SHA256: | 99D3E781968BA117811CB28EF4B8CD522BD535A6C17552D679A3F7C47D2868A1 |
| SSDEEP: | 24576:AsERJuW4UJf7JsPIHXzPTRCjGSBD0C+/ENR6i:MBjXHSBL+/Ex |
MALICIOUS
AGENTTESLA has been detected (YARA)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Steals credentials from Web Browsers
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Actions looks like stealing of personal data
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
AGENTTESLA has been detected (SURICATA)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7764)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Application launched itself
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
Executable content was dropped or overwritten
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
Checks for external IP
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
- svchost.exe (PID: 2196)
There is functionality for taking screenshot (YARA)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Malware-specific behavior (creating "System.dll" in Temp)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
The process creates files with name similar to system file names
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
Connects to SMTP port
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Contacting a server suspected of hosting an CnC
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Connects to the server without a host name
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
INFO
Java executable
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
The sample compiled with english language support
- OUTLOOK.EXE (PID: 4024)
Reads the computer name
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Checks supported languages
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
Reads the machine GUID from the registry
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Checks proxy server information
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
- slui.exe (PID: 7372)
Disables trace logs
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7984)
Creates files or folders in the user directory
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
Create files in a temporary directory
- Orden de compra_896758576568857657858756857645674656745677.exe (PID: 7860)
Reads the software policy settings
- slui.exe (PID: 4408)
- slui.exe (PID: 7372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(7984) Orden de compra_896758576568857657858756857645674656745677.exe
Protocolsmtp
Hostmail.rvoccte.com
Port587
Usernamenewfile@rvoccte.com
PasswordPJtiky;+*ayY
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
146
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\Orden de compra.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4408 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7372 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7596 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "BD4B9F43-5EFA-4C7C-9DAC-B2A305BE7D97" "6D074BCD-B743-4A76-A85B-427BE9AF5190" "4024" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 7764 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\LNF332NY\Orden de compra_896758576_pdf.uue" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7860 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7764.44277\Orden de compra_896758576568857657858756857645674656745677.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7764.44277\Orden de compra_896758576568857657858756857645674656745677.exe | WinRAR.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Exit code: 0 Version: 8.0.4510.0 Modules
| |||||||||||||||
| 7984 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7764.44277\Orden de compra_896758576568857657858756857645674656745677.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7764.44277\Orden de compra_896758576568857657858756857645674656745677.exe | Orden de compra_896758576568857657858756857645674656745677.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Platform SE binary Version: 8.0.4510.0 Modules
AgentTesla(PID) Process(7984) Orden de compra_896758576568857657858756857645674656745677.exe Protocolsmtp Hostmail.rvoccte.com Port587 Usernamenewfile@rvoccte.com PasswordPJtiky;+*ayY | |||||||||||||||
Total events
17 292
Read events
15 820
Write events
1 329
Delete events
143
Modification events
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\4024 |
| Operation: | write | Name: | 0 |
Value: 0B0E10B49E3EF72DA1D242BF8E49E81738E03B230046EF98FFD4E5B4F1ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B81FD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (4024) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
2
Suspicious files
22
Text files
16
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4024 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7764 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7764.44277\Orden de compra_896758576568857657858756857645674656745677.exe | — | |
MD5:— | SHA256:— | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\13632B5E-9D61-4A4E-ACF9-4D04292F53BA | xml | |
MD5:A76BDABE77490E13FDE6B859A8AD206B | SHA256:2D8F128C80F311FE249EBDDE8899AA931CD452DC4CFCE68851B1DBF42CA85C05 | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkD19A.tmp | binary | |
MD5:8170F7CCDD71AD17652CB2AEB3304EF6 | SHA256:C380121028D448EB9428E862239F208495975C66B7CCA8909C04BBA732BE4F6A | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:CBF8314B2A8B40129DC12E85375E106A | SHA256:259F3B2C25D0A17B988A8021BC6F37D58C3EB4A637657519CC442BE17B7FED80 | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\LNF332NY\Orden de compra_896758576_pdf.uue:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\LNF332NY\Orden de compra_896758576_pdf (002).uue | compressed | |
MD5:DD1CB45C99A660C9C0473B6524003115 | SHA256:337F7EAEB98313DDF4319FDFD460DA0C8ECAD103EA6816715FFC06FECF79A15D | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:F56EEEF3E195D7CB990870CB328C0B0F | SHA256:8083507FE4FDA3DCA9372F4930B1FC0FE8FC78B28691E2FEBC14BF0DC0026A89 | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:A7E82FFD1DB5415C9F6F3BB82E8E7E71 | SHA256:CA0E28CFEC75FC149AA73604FF1C1AC040A45CCF1948118C985AE72E4FE45E9F | |||
| 4024 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:3D79B14A833A3D961EB72CBA4750305E | SHA256:0D3F2D404B9CA79FE0BD8A9613AB8CB4EFD2E6C00D58B8621DFA0A42E132507F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
35
DNS requests
20
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.21.245.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4024 | OUTLOOK.EXE | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.21.245.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1852 | RUXIMICS.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8012 | SIHClient.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | GET | 200 | 198.12.83.69:80 | http://198.12.83.69/SOYrCyIiGRkX220.bin | unknown | — | — | unknown |
1852 | RUXIMICS.exe | GET | 200 | 2.21.245.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.21.245.180:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.21.245.180:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
1852 | RUXIMICS.exe | 2.21.245.180:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
2104 | svchost.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
1852 | RUXIMICS.exe | 23.222.86.92:80 | www.microsoft.com | AKAMAI-AS | NZ | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
nleditor.osi.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | Malware Command and Control Activity Detected | ET MALWARE MSIL/Kryptik.XSY Data Exfil via SMTP |
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |
7984 | Orden de compra_896758576568857657858756857645674656745677.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration SMTP (Base64 encoded) |