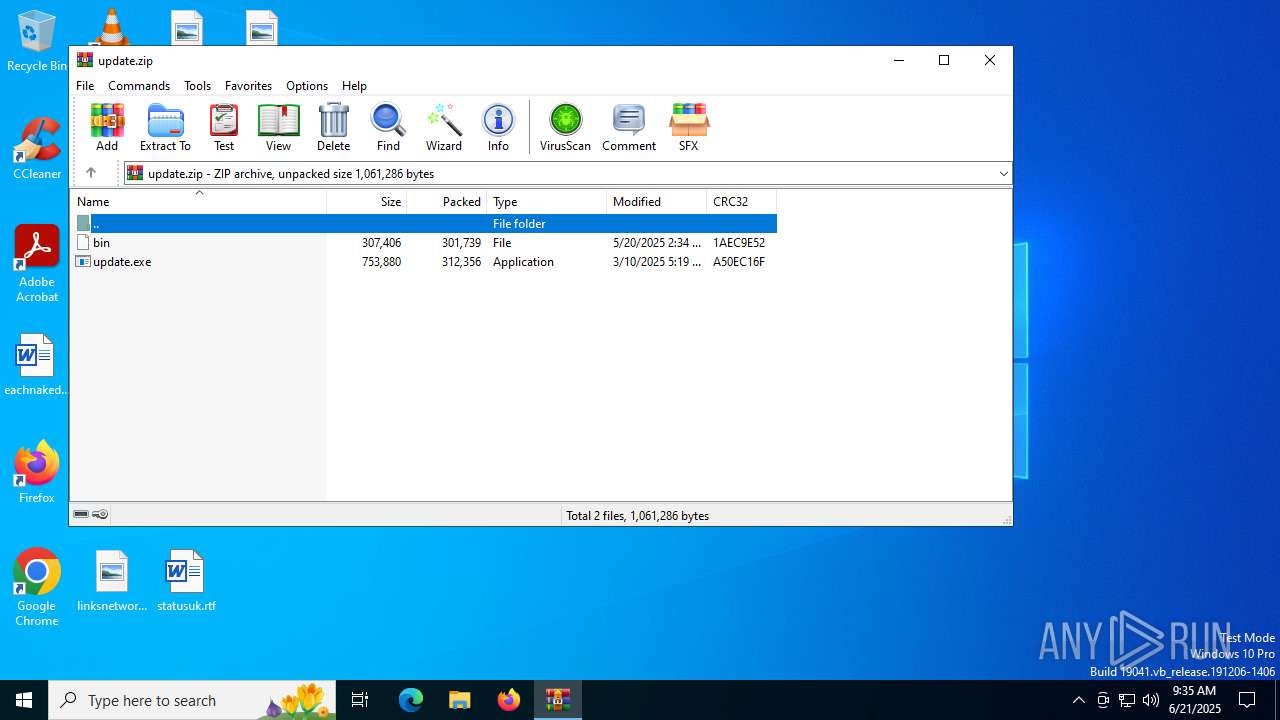
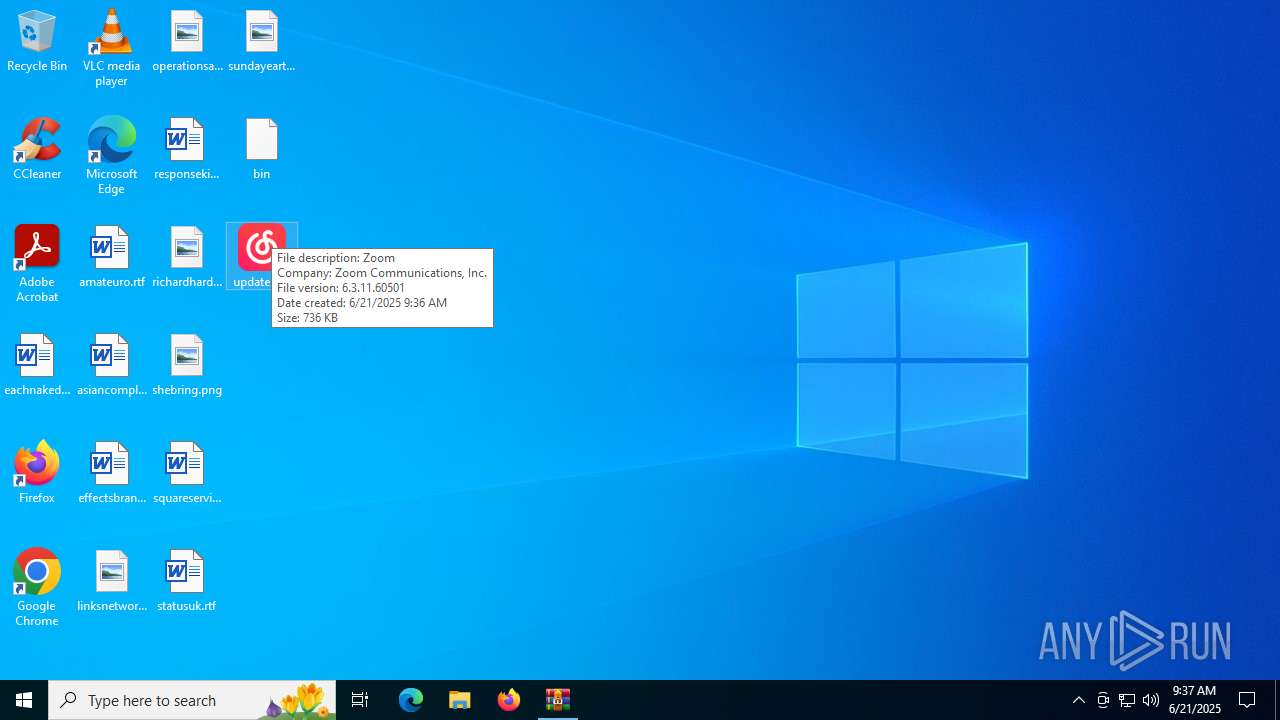
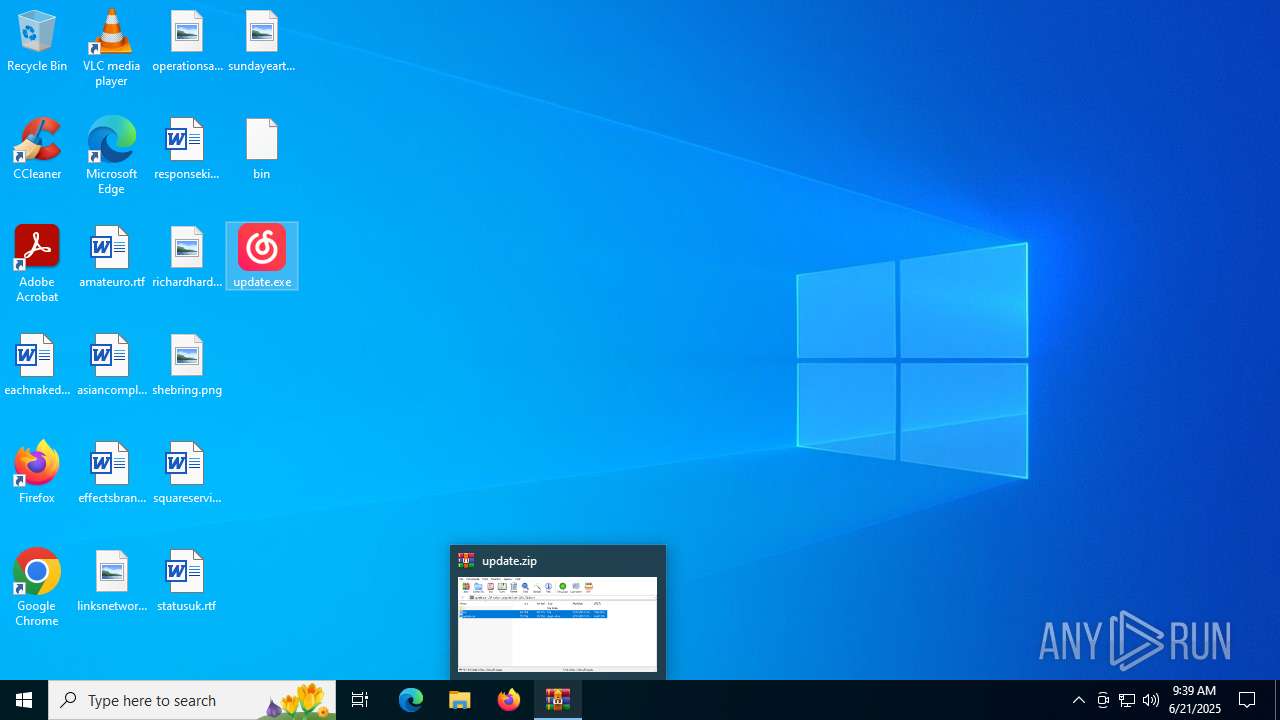
| File name: | update.zip |
| Full analysis: | https://app.any.run/tasks/bfc00e1b-b30e-41ec-8d69-434046939335 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | June 21, 2025, 09:35:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
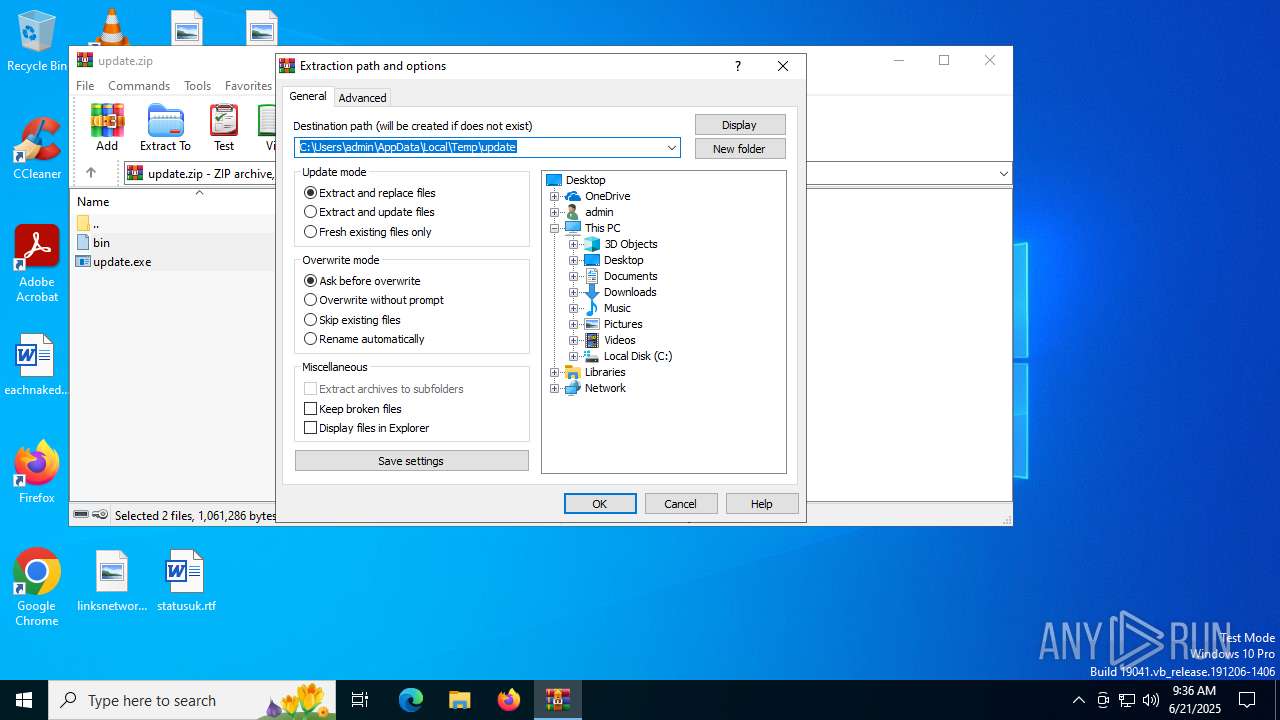
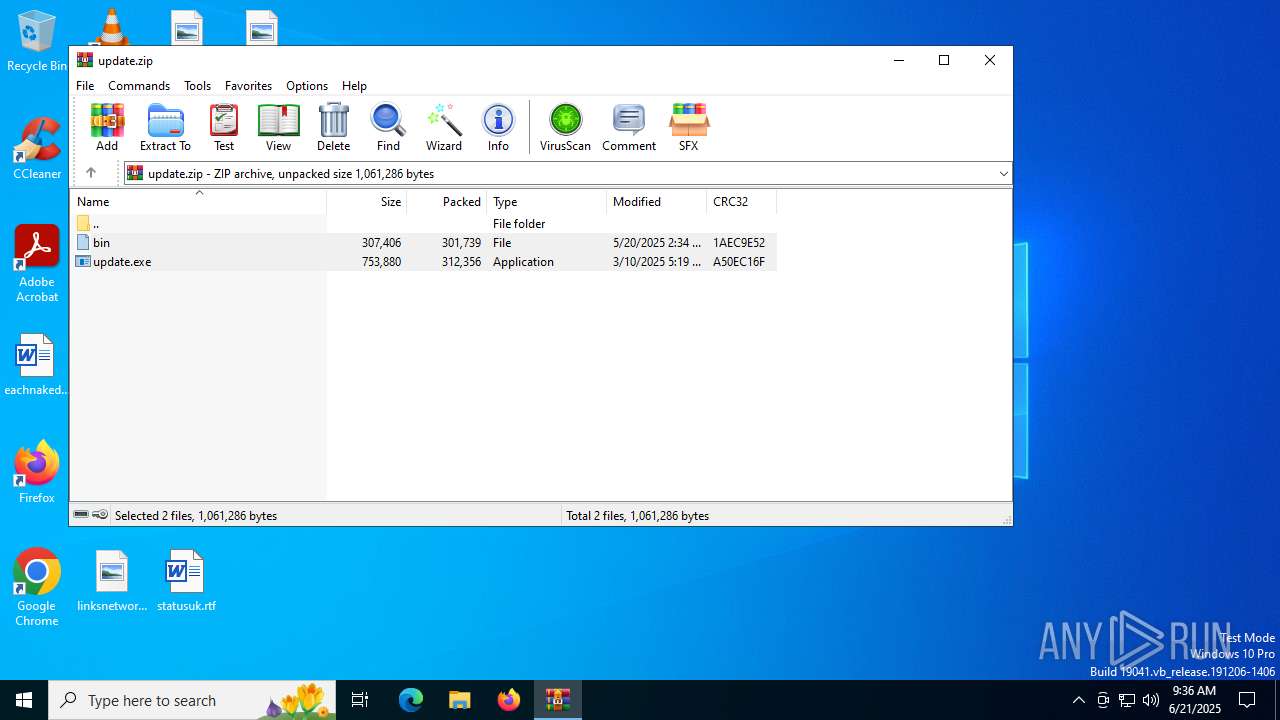
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 31A9D0B28185F46C3733D11137A09F92 |
| SHA1: | AF3F1B5DC9DD8D75C20004741937F1BA03F205E0 |
| SHA256: | 99D1A9B21F8AD54C30DDC5B7A35089C70530C771C1F860153BA7156D607C3705 |
| SSDEEP: | 24576:aXD76WC3NsraZkm5LVVgumc9KoxE97ISetuDNbUXt3nUhnO:aXD76WC3NsaZkm5LVVgumc9KoxE97ISK |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2044)
COBALTSTRIKE has been detected (YARA)
- update.exe (PID: 6220)
SUSPICIOUS
Reads security settings of Internet Explorer
- update.exe (PID: 6220)
Connects to unusual port
- update.exe (PID: 6220)
INFO
Manual execution by a user
- update.exe (PID: 6220)
The sample compiled with english language support
- WinRAR.exe (PID: 2044)
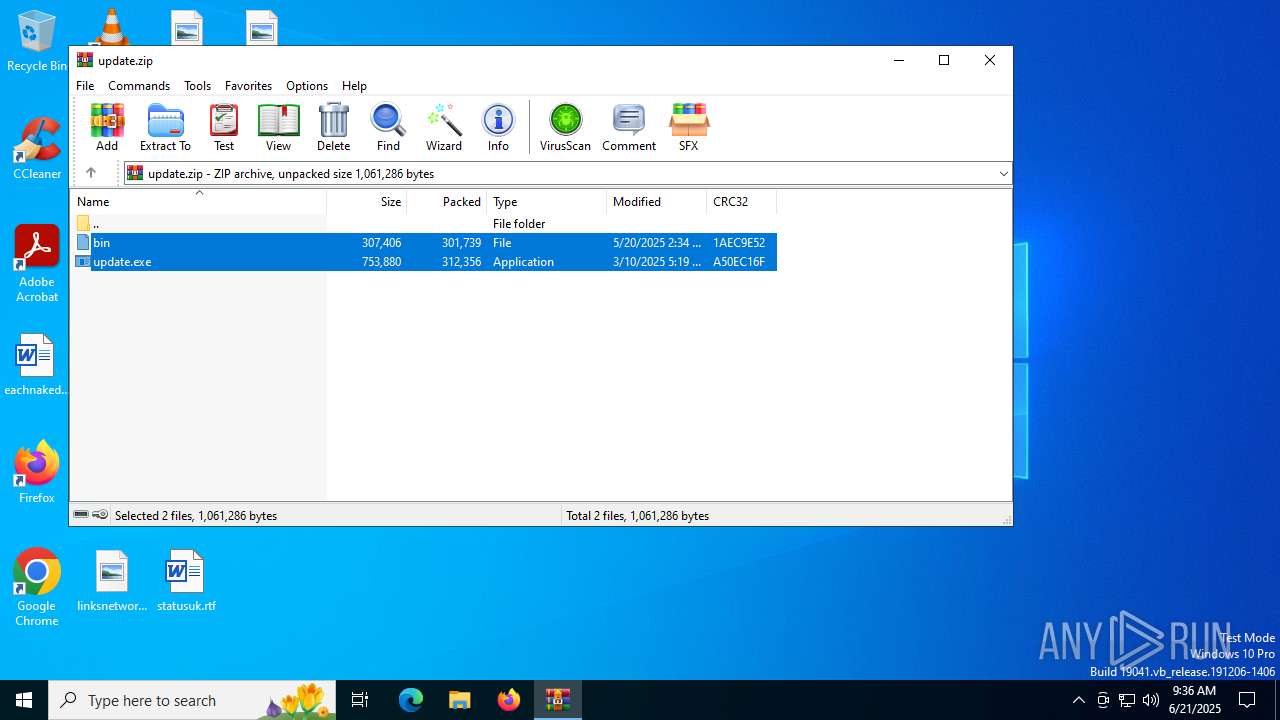
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2044)
Checks supported languages
- update.exe (PID: 6220)
Reads the computer name
- update.exe (PID: 6220)
Checks proxy server information
- update.exe (PID: 6220)
- slui.exe (PID: 1728)
Reads the machine GUID from the registry
- update.exe (PID: 6220)
Reads the software policy settings
- slui.exe (PID: 1728)
- update.exe (PID: 6220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:20 22:34:16 |
| ZipCRC: | 0x1aec9e52 |
| ZipCompressedSize: | 301739 |
| ZipUncompressedSize: | 307406 |
| ZipFileName: | bin |
Total processes
141
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1728 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\update.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
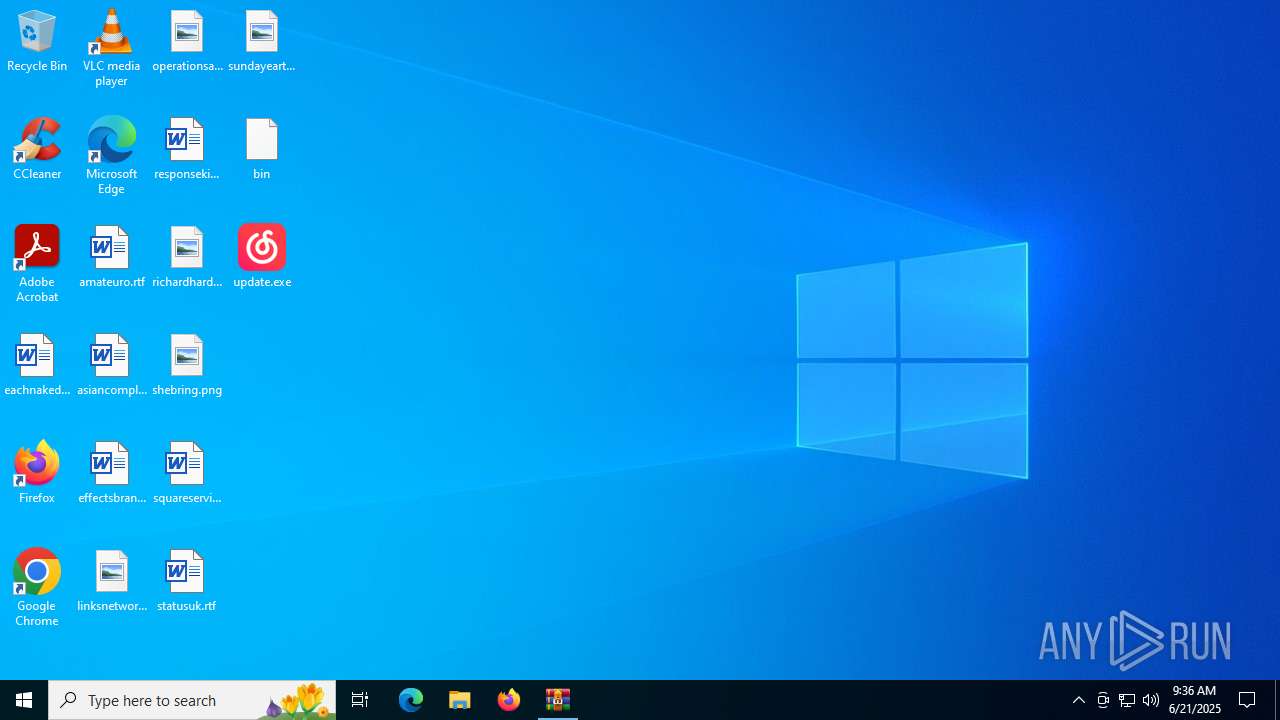
| 6220 | "C:\Users\admin\Desktop\update.exe" | C:\Users\admin\Desktop\update.exe | explorer.exe | ||||||||||||
User: admin Company: Zoom Communications, Inc. Integrity Level: MEDIUM Description: Zoom Version: 6,3,11,60501 Modules
| |||||||||||||||
Total events
6 183
Read events
6 159
Write events
11
Delete events
13
Modification events
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\update.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
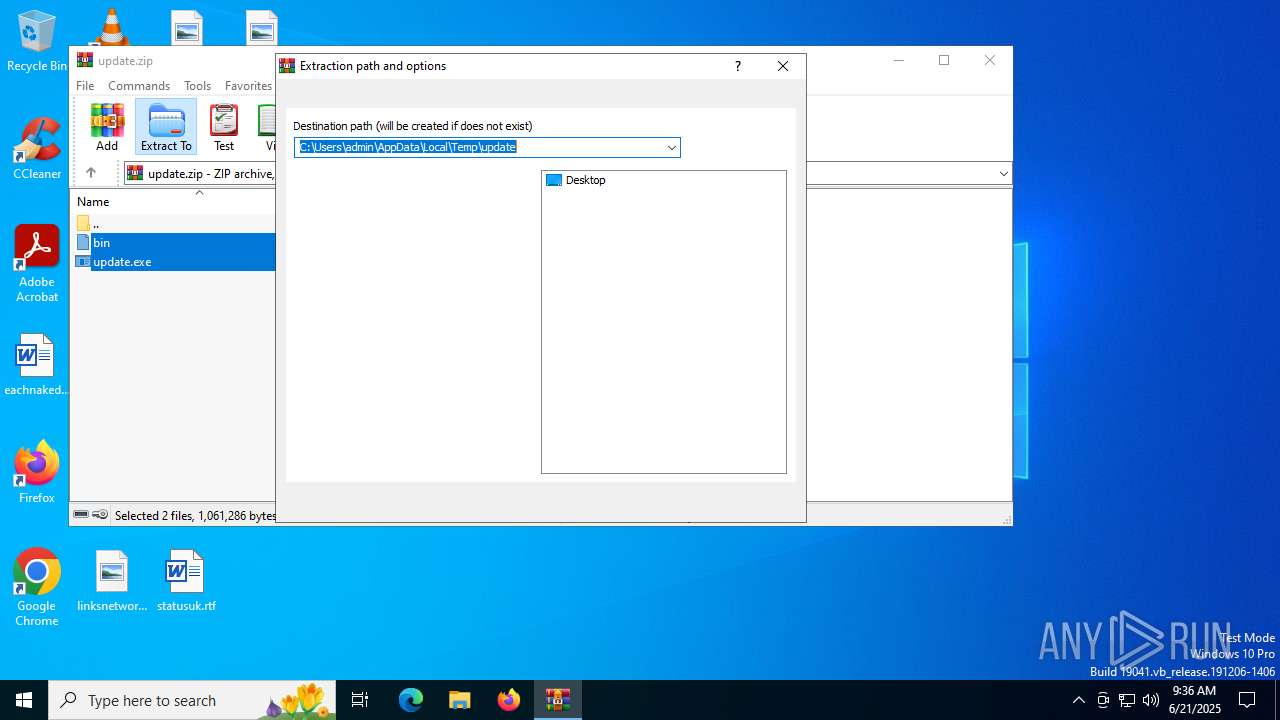
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
1
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\bin | binary | |
MD5:F6BAEF1EB00F7AB0C69F9D8001B2B814 | SHA256:9702E80EBAB8B1E6BD27F4F0C4B6927CDEB4E5AEBFDAADEAF59C7D47B7156ED9 | |||
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\update.exe | executable | |
MD5:5211F010A6081ED5E0E092A898C77D5C | SHA256:FD673AEDBAEE1AFABD33253B8955923B6054A26E2EB913676C37D0BB4191E421 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
31
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1948 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1948 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
436 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5372 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1948 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1948 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |