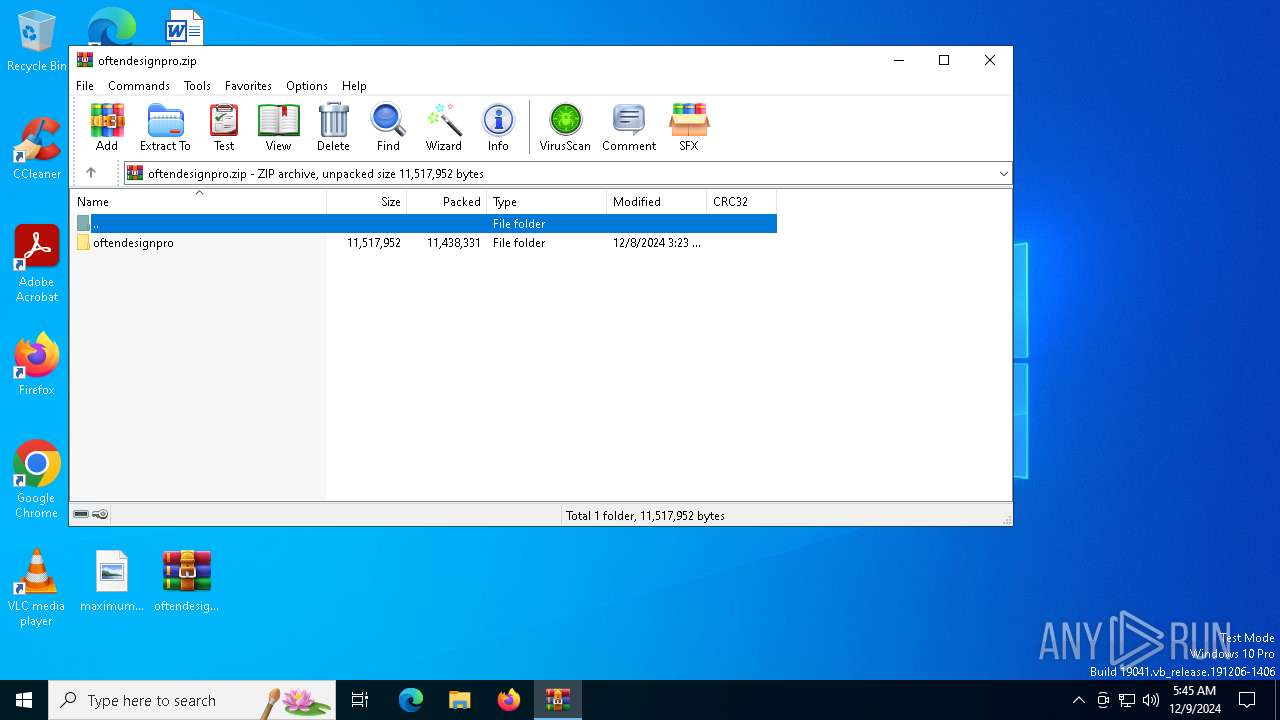
| File name: | oftendesignpro.zip |
| Full analysis: | https://app.any.run/tasks/e1ddd498-78ba-4a32-9cd8-9d0d54ccb44e |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 09, 2024, 05:45:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E5F783E5D5924CA35B54BEAB212DFD4B |
| SHA1: | BF53426BEE1D8F4D087ECE7F270D1B0CAF4D2869 |
| SHA256: | 99A88D463CB08F6198DC45A3793EF0BDA999A314023EF2784C2CD6F5B937EC94 |
| SSDEEP: | 98304:uPNz/a1BxKIiYAiahaJYa0I3EcJmNCyW8KtVvGT+flHQjSBqZt15NnZC1H4kgfyR:6MQwrpMfFXPe |
MALICIOUS
Generic archive extractor
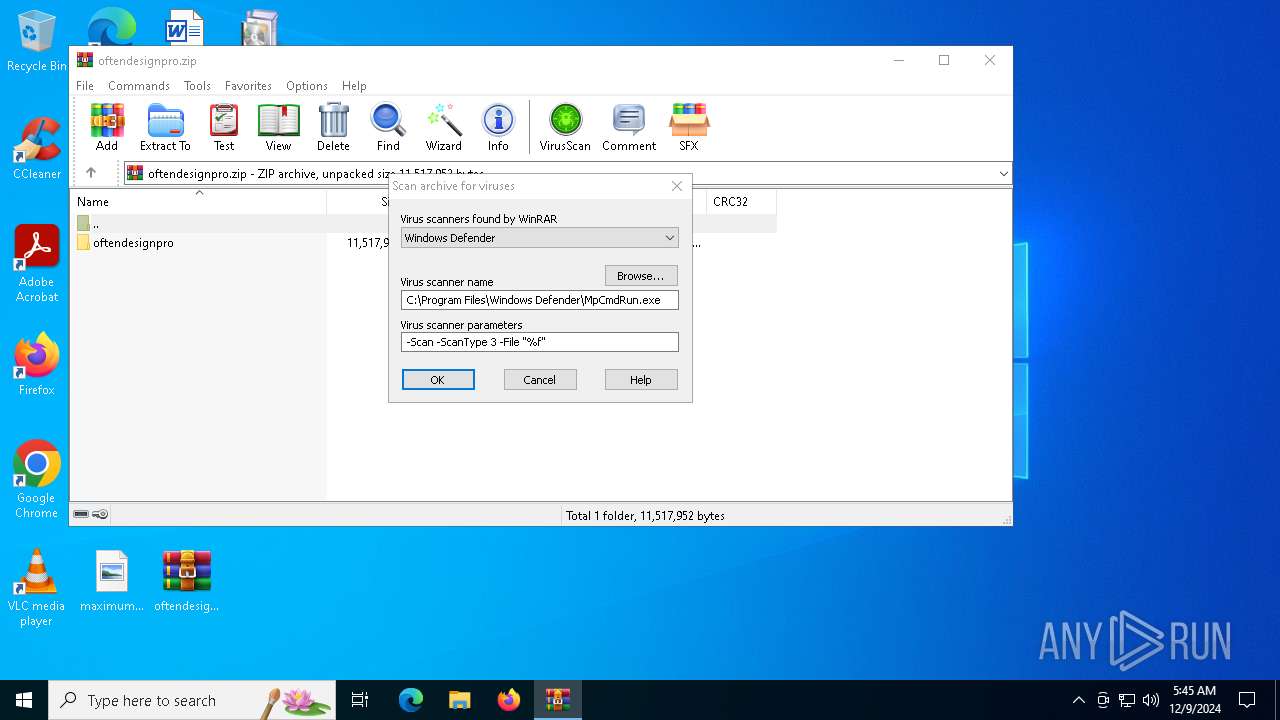
- WinRAR.exe (PID: 3532)
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 4672)
- MpCmdRun.exe (PID: 4400)
PURECRYPTER has been detected (YARA)
- oftendesign.exe (PID: 4708)
Create files in the Startup directory
- oftendesign.exe (PID: 4708)
PUREHVNC has been detected (YARA)
- InstallUtil.exe (PID: 4136)
ASYNCRAT has been detected (SURICATA)
- InstallUtil.exe (PID: 4136)
Actions looks like stealing of personal data
- InstallUtil.exe (PID: 4136)
- InstallUtil.exe (PID: 4580)
Steals credentials from Web Browsers
- InstallUtil.exe (PID: 4580)
PURECRYPTER has been detected (SURICATA)
- InstallUtil.exe (PID: 4580)
Connects to the CnC server
- InstallUtil.exe (PID: 4580)
Scans artifacts that could help determine the target
- InstallUtil.exe (PID: 4580)
PURELOGS has been detected (SURICATA)
- InstallUtil.exe (PID: 4580)
SUSPICIOUS
Process drops legitimate windows executable
- oftendesignpro.exe (PID: 5888)
- WinRAR.exe (PID: 3532)
Executable content was dropped or overwritten
- oftendesignpro.exe (PID: 5888)
- oftendesignpropre.exe (PID: 5572)
- oftendesign.exe (PID: 4708)
Starts a Microsoft application from unusual location
- oftendesignpro.exe (PID: 5888)
- oftendesignpropre.exe (PID: 5572)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3532)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3532)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3532)
The process creates files with name similar to system file names
- oftendesign.exe (PID: 4708)
Connects to unusual port
- InstallUtil.exe (PID: 4136)
- InstallUtil.exe (PID: 4580)
Connects to the server without a host name
- offtendesign.exe (PID: 556)
- oftendesign.exe (PID: 4708)
Contacting a server suspected of hosting an CnC
- InstallUtil.exe (PID: 4136)
- InstallUtil.exe (PID: 4580)
Removes files via Powershell
- powershell.exe (PID: 4624)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 4624)
Starts POWERSHELL.EXE for commands execution
- InstallUtil.exe (PID: 4580)
INFO
Create files in a temporary directory
- oftendesignpro.exe (PID: 5888)
- oftendesignpropre.exe (PID: 5572)
- MpCmdRun.exe (PID: 4672)
Manual execution by a user
- oftendesignpro.exe (PID: 5888)
- InstallUtil.exe (PID: 4136)
- InstallUtil.exe (PID: 4580)
Checks supported languages
- everyonetechnollogyovlres.exe (PID: 836)
- oftendesignpropre.exe (PID: 5572)
- oftendesignpro.exe (PID: 5888)
- oftendesign.exe (PID: 4708)
- MpCmdRun.exe (PID: 4672)
- offtendesign.exe (PID: 556)
- InstallUtil.exe (PID: 4136)
- InstallUtil.exe (PID: 4580)
- MpCmdRun.exe (PID: 4400)
Reads the machine GUID from the registry
- everyonetechnollogyovlres.exe (PID: 836)
- offtendesign.exe (PID: 556)
- InstallUtil.exe (PID: 4136)
- InstallUtil.exe (PID: 4580)
- oftendesign.exe (PID: 4708)
Reads the computer name
- oftendesign.exe (PID: 4708)
- everyonetechnollogyovlres.exe (PID: 836)
- MpCmdRun.exe (PID: 4672)
- InstallUtil.exe (PID: 4136)
- offtendesign.exe (PID: 556)
- MpCmdRun.exe (PID: 4400)
- InstallUtil.exe (PID: 4580)
Disables trace logs
- oftendesign.exe (PID: 4708)
- offtendesign.exe (PID: 556)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3532)
The process uses the downloaded file
- WinRAR.exe (PID: 3532)
Creates files or folders in the user directory
- oftendesign.exe (PID: 4708)
.NET Reactor protector has been detected
- oftendesign.exe (PID: 4708)
- InstallUtil.exe (PID: 4136)
Checks proxy server information
- offtendesign.exe (PID: 556)
- oftendesign.exe (PID: 4708)
Reads the software policy settings
- InstallUtil.exe (PID: 4136)
Reads Microsoft Office registry keys
- InstallUtil.exe (PID: 4580)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:08 07:23:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | oftendesignpro/ |
Total processes
136
Monitored processes
16
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR3532.45605\Rar$Scan9373.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\offtendesign.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\offtendesign.exe | oftendesignpropre.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: offtendesign Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 836 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\everyonetechnollogyovlres.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\everyonetechnollogyovlres.exe | — | oftendesignpro.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Proxy.Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3532 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\oftendesignpro.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4128 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR3532.1763\Rar$Scan70966.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4136 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR3532.1763" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4580 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4624 | "powershell" Start-Sleep -Seconds 10; Remove-Item -Path 'C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe' -Force | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | InstallUtil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 543
Read events
12 505
Write events
38
Delete events
0
Modification events
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\oftendesignpro.zip | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4708) oftendesign.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\oftendesign_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4708) oftendesign.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\oftendesign_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
7
Suspicious files
2
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 836 | everyonetechnollogyovlres.exe | C:\Users\admin\AppData\Local\Temp\Tmp74D5.tmp | der | |
MD5:CBC6B2AD4BF883EA7ECB41D8D86B0964 | SHA256:C8844BA7CA7DF3C75532044792065C3D2B742C389FC9FA1A6E2776ED425917AF | |||
| 5572 | oftendesignpropre.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\oftendesign.exe | executable | |
MD5:0F4BC1FB5D736A617A8733F62266945B | SHA256:C8222B9D3F4E6D8E2B9D9FC7A027BAC9D826572DA7F05ECC8AE8BA8E00F7CE91 | |||
| 4672 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:C08F5A10AC184375F5EC894711325F83 | SHA256:6EBEBA252F79077F70D52A28FDEF7A2C30594C73911891EB5626E1CA062D9204 | |||
| 4708 | oftendesign.exe | C:\Users\admin\AppData\Local\cvchost.exe | executable | |
MD5:0F4BC1FB5D736A617A8733F62266945B | SHA256:C8222B9D3F4E6D8E2B9D9FC7A027BAC9D826572DA7F05ECC8AE8BA8E00F7CE91 | |||
| 836 | everyonetechnollogyovlres.exe | C:\Users\admin\AppData\Local\Temp\Tmp7592.tmp | der | |
MD5:CBC6B2AD4BF883EA7ECB41D8D86B0964 | SHA256:C8844BA7CA7DF3C75532044792065C3D2B742C389FC9FA1A6E2776ED425917AF | |||
| 4624 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xhakxo3r.4hk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3532.45605\Rar$Scan9373.bat | text | |
MD5:2A54B5D71234411A3BD640D2736ACC88 | SHA256:247081EE7253DDB22EF50CF2CEEF117B12AE27C777D3A46E45F68D857C249826 | |||
| 3532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR3532.1763\Rar$Scan70966.bat | text | |
MD5:F8DD588179F341A4F3B9B2759BDCF560 | SHA256:9DCBFA62FA80DAD6B6F70EA485FA43E2E4F6EDEE216B9346517B63BBEF6DA94C | |||
| 4624 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:FECDBE12A0E579A804A2B3AC49756655 | SHA256:4EC462E92B45CC57CE07B0ED8425C496E6D4E87FD60833118853EB6D92E70B67 | |||
| 5572 | oftendesignpropre.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\offtendesign.exe | executable | |
MD5:85C8006A42A12B496E1A65E2198F0A49 | SHA256:C3D81F54C4F75FF0A42B0DC356B323BEEFD945B6891C8F1C7FD83FD62084B4BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
6
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3220 | svchost.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5208 | RUXIMICS.exe | GET | 200 | 2.20.245.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3220 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5208 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
556 | offtendesign.exe | GET | 200 | 185.226.181.36:80 | http://185.226.181.36/count/Rgfbp.vdf | unknown | — | — | unknown |
4708 | oftendesign.exe | GET | 200 | 185.226.181.36:80 | http://185.226.181.36/count/Curbjjrrn.vdf | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3220 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5208 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3220 | svchost.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5208 | RUXIMICS.exe | 2.20.245.138:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
3220 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4136 | InstallUtil.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
4136 | InstallUtil.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
4580 | InstallUtil.exe | A Network Trojan was detected | LOADER [ANY.RUN] PureLogs Download Attempt (LOAD) |
4580 | InstallUtil.exe | A Network Trojan was detected | STEALER [ANY.RUN] PureLogs Stealer Exfiltration |
1 ETPRO signatures available at the full report