| File name: | heisenberg.exe |
| Full analysis: | https://app.any.run/tasks/8738ec19-4a5a-42b5-beda-c0240814719b |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | August 25, 2024, 14:58:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 02CB6D1971FB53861285F273D799CED3 |
| SHA1: | 16946DB5C16D768C0D76FAB6761C65358863FC59 |
| SHA256: | 996DE893CE9219A90FA76BEAB00295734913B55A6B85DD9C227175CF4CC93E3E |
| SSDEEP: | 393216:oX6p5vshW6vD2CmG+pFuoM6oozwdeEEIbGHhTfwxkCE3:oUhG2CmTuh8jEEIi8kB3 |
MALICIOUS
Changes the autorun value in the registry
- ColorBug.exe (PID: 6468)
- reg.exe (PID: 10108)
- 6AdwCleaner.exe (PID: 7908)
- reg.exe (PID: 9024)
- FreeYoutubeDownloader.exe (PID: 7756)
- Telegram.exe (PID: 4704)
- NoMoreRansom.exe (PID: 10824)
- CockroachOnDesktop.exe (PID: 6320)
- AntivirusPro2017.exe (PID: 6204)
- Telegram.exe (PID: 11768)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 8172)
- Telegram.exe (PID: 4704)
- Telegram.exe (PID: 11768)
Create files in the Startup directory
- Telegram.exe (PID: 4704)
UAC/LUA settings modification
- Illerka.C.exe (PID: 11408)
XORed URL has been found (YARA)
- AntivirusPro2017.exe (PID: 6204)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 11720)
XWORM has been detected (SURICATA)
- Telegram.exe (PID: 11768)
Connects to the CnC server
- DeriaLock.exe (PID: 12192)
DERIALOCK has been detected (SURICATA)
- DeriaLock.exe (PID: 12192)
Troldesh is detected
- NoMoreRansom.exe (PID: 10824)
SUSPICIOUS
Executable content was dropped or overwritten
- heisenberg.exe (PID: 1288)
- BadRabbit.exe (PID: 6368)
- rundll32.exe (PID: 6360)
- Delete Windows.exe (PID: 6460)
- Antivirus2010.exe (PID: 6212)
- FakeAdwCleaner.exe (PID: 1372)
- Goose.exe (PID: 6252)
- Penis_Cursor.exe (PID: 8532)
- AntivirusPlatinum.exe (PID: 7924)
- FreeYoutubeDownloader.exe (PID: 7756)
- NoMoreRansom.exe (PID: 10824)
- You_Are_An_Idiot.exe (PID: 10524)
- Illerka.C.exe (PID: 11408)
Process drops legitimate windows executable
- heisenberg.exe (PID: 1288)
- AntivirusPlatinum.exe (PID: 7924)
Drops the executable file immediately after the start
- heisenberg.exe (PID: 1288)
- BadRabbit.exe (PID: 6368)
- Delete Windows.exe (PID: 6460)
- FakeAdwCleaner.exe (PID: 1372)
- Antivirus2010.exe (PID: 6212)
- Goose.exe (PID: 6252)
- Penis_Cursor.exe (PID: 8532)
- AntivirusPlatinum.exe (PID: 7924)
- FreeYoutubeDownloader.exe (PID: 7756)
- NoMoreRansom.exe (PID: 10824)
- Illerka.C.exe (PID: 11408)
- You_Are_An_Idiot.exe (PID: 10524)
Reads the date of Windows installation
- heisenberg.exe (PID: 1288)
- Delete Windows.exe (PID: 6460)
- AntivirusPlatinum.exe (PID: 6268)
- PizDeath.exe (PID: 8676)
- Goose.exe (PID: 6252)
- Telegram.exe (PID: 4704)
- Penis_Cursor.exe (PID: 8532)
- FreeYoutubeDownloader.exe (PID: 7756)
- 302746537.exe (PID: 8928)
- scream.exe (PID: 6240)
- PowerPoint.exe (PID: 11592)
- scream.exe (PID: 9132)
- You_Are_An_Idiot.exe (PID: 10524)
- Telegram.exe (PID: 11768)
Executing commands from a ".bat" file
- heisenberg.exe (PID: 1288)
- Delete Windows.exe (PID: 6460)
- PizDeath.exe (PID: 8676)
- 302746537.exe (PID: 8928)
Starts CMD.EXE for commands execution
- heisenberg.exe (PID: 1288)
- rundll32.exe (PID: 6360)
- Delete Windows.exe (PID: 6460)
- cmd.exe (PID: 6584)
- HMBlocker.exe (PID: 3844)
- PizDeath.exe (PID: 8676)
- 302746537.exe (PID: 8928)
- cmd.exe (PID: 7216)
Reads security settings of Internet Explorer
- heisenberg.exe (PID: 1288)
- AntivirusPlatinum.exe (PID: 6268)
- Delete Windows.exe (PID: 6460)
- HMBlocker.exe (PID: 3844)
- PizDeath.exe (PID: 8676)
- ChilledWindows.exe (PID: 6472)
- Goose.exe (PID: 6252)
- Antivirus.exe (PID: 6480)
- Telegram.exe (PID: 4704)
- Penis_Cursor.exe (PID: 8532)
- FreeYoutubeDownloader.exe (PID: 7756)
- scream.exe (PID: 6240)
- 302746537.exe (PID: 8928)
- PowerPoint.exe (PID: 11592)
- scream.exe (PID: 9132)
- Illerka.C.exe (PID: 11408)
- You_Are_An_Idiot.exe (PID: 10524)
- AntivirusPro2017.exe (PID: 6204)
- Telegram.exe (PID: 11768)
Changes internet zones settings
- Antivirus.exe (PID: 6480)
Application launched itself
- cmd.exe (PID: 6584)
- AntivirusPlatinum.exe (PID: 6268)
- cmd.exe (PID: 7216)
- PowerPoint.exe (PID: 11592)
Starts a Microsoft application from unusual location
- Hydra.exe (PID: 8248)
- Windows-KB2670838.msu.exe (PID: 10032)
- Windows-KB2670838.msu.exe (PID: 10304)
The system shut down or reboot
- HMBlocker.exe (PID: 3844)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6404)
- Trololo.exe (PID: 9932)
- cmd.exe (PID: 11756)
The process executes VB scripts
- heisenberg.exe (PID: 1288)
- PizDeath.exe (PID: 8676)
- scream.exe (PID: 6240)
- scream.exe (PID: 9132)
Starts application with an unusual extension
- cmd.exe (PID: 8472)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8728)
- cmd.exe (PID: 8840)
Creates a software uninstall entry
- FreeYoutubeDownloader.exe (PID: 7756)
The process creates files with name similar to system file names
- NoMoreRansom.exe (PID: 10824)
Creates file in the systems drive root
- rundll32.exe (PID: 6360)
The executable file from the user directory is run by the CMD process
- scream.exe (PID: 13292)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7552)
Uses WEVTUTIL.EXE to cleanup log
- cmd.exe (PID: 13200)
The process executes via Task Scheduler
- Telegram.exe (PID: 11768)
Checks for external IP
- Telegram.exe (PID: 4704)
- svchost.exe (PID: 2256)
- Telegram.exe (PID: 11768)
Contacting a server suspected of hosting an CnC
- Telegram.exe (PID: 11768)
- DeriaLock.exe (PID: 12192)
Connects to unusual port
- Telegram.exe (PID: 11768)
INFO
Process checks computer location settings
- heisenberg.exe (PID: 1288)
- Delete Windows.exe (PID: 6460)
- AntivirusPlatinum.exe (PID: 6268)
- HMBlocker.exe (PID: 3844)
- PizDeath.exe (PID: 8676)
- Goose.exe (PID: 6252)
- Telegram.exe (PID: 4704)
- Penis_Cursor.exe (PID: 8532)
- FreeYoutubeDownloader.exe (PID: 7756)
- 302746537.exe (PID: 8928)
- scream.exe (PID: 6240)
- PowerPoint.exe (PID: 11592)
- scream.exe (PID: 9132)
- You_Are_An_Idiot.exe (PID: 10524)
- Telegram.exe (PID: 11768)
Checks supported languages
- Antivirus2010.exe (PID: 6212)
- Antivirus.exe (PID: 6480)
- heisenberg.exe (PID: 1288)
- BadRabbit.exe (PID: 6368)
- CockroachOnDesktop.exe (PID: 6320)
- ChilledWindows.exe (PID: 6472)
- AntivirusPlatinum.exe (PID: 6268)
- AntivirusPro2017.exe (PID: 6204)
- ColorBug.exe (PID: 6468)
- Cool Spot Deskmate.EXE (PID: 6572)
- Delete Windows.exe (PID: 6460)
- DeriaLock.exe (PID: 7096)
- Telegram.exe (PID: 4704)
- DesktopPuzzle.exe (PID: 420)
- FakeAdwCleaner.exe (PID: 1372)
- MEMZ.exe (PID: 8412)
- HMBlocker.exe (PID: 3844)
- PizDeath.exe (PID: 8676)
- Hydra.exe (PID: 8248)
- HappyAntivirus.exe (PID: 7224)
- scream.exe (PID: 6240)
- Goose.exe (PID: 6252)
- chcp.com (PID: 9392)
- GooseDesktop.exe (PID: 9612)
- Trololo.exe (PID: 9932)
- scream.exe (PID: 9132)
- Penis_Cursor.exe (PID: 8532)
- Windows-KB2670838.msu.exe (PID: 10304)
- You_Are_An_Idiot.exe (PID: 10524)
- NoMoreRansom.exe (PID: 10824)
- 302746537.exe (PID: 8928)
- Illerka.C.exe (PID: 11408)
- InfinityCrypt.exe (PID: 11496)
- Free YouTube Downloader.exe (PID: 11644)
- FreeYoutubeDownloader.exe (PID: 7756)
- Курсор - писюн.exe (PID: 10416)
- DeriaLock.exe (PID: 12192)
- YouAreAnIdiot.exe (PID: 12844)
- scream.exe (PID: 13292)
- Telegram.exe (PID: 11768)
- PowerPoint.exe (PID: 11592)
- identity_helper.exe (PID: 13024)
Reads the computer name
- AntivirusPlatinum.exe (PID: 6268)
- heisenberg.exe (PID: 1288)
- ChilledWindows.exe (PID: 6472)
- CockroachOnDesktop.exe (PID: 6320)
- ColorBug.exe (PID: 6468)
- Cool Spot Deskmate.EXE (PID: 6572)
- Delete Windows.exe (PID: 6460)
- AntivirusPro2017.exe (PID: 6204)
- Telegram.exe (PID: 4704)
- MEMZ.exe (PID: 8412)
- PizDeath.exe (PID: 8676)
- AntivirusPlatinum.exe (PID: 7924)
- Penis_Cursor.exe (PID: 8532)
- GooseDesktop.exe (PID: 9612)
- scream.exe (PID: 6240)
- Windows-KB2670838.msu.exe (PID: 10304)
- scream.exe (PID: 9132)
- FreeYoutubeDownloader.exe (PID: 7756)
- You_Are_An_Idiot.exe (PID: 10524)
- Trololo.exe (PID: 9932)
- NoMoreRansom.exe (PID: 10824)
- 302746537.exe (PID: 8928)
- InfinityCrypt.exe (PID: 11496)
- Free YouTube Downloader.exe (PID: 11644)
- PowerPoint.exe (PID: 11592)
- Курсор - писюн.exe (PID: 10416)
- Illerka.C.exe (PID: 11408)
- DeriaLock.exe (PID: 12192)
- Telegram.exe (PID: 11768)
- identity_helper.exe (PID: 13024)
Create files in a temporary directory
- heisenberg.exe (PID: 1288)
- AntivirusPro2017.exe (PID: 6204)
- PizDeath.exe (PID: 8676)
- Goose.exe (PID: 6252)
- Penis_Cursor.exe (PID: 8532)
- You_Are_An_Idiot.exe (PID: 10524)
- Illerka.C.exe (PID: 11408)
- NoMoreRansom.exe (PID: 10824)
- 302746537.exe (PID: 8928)
Reads the machine GUID from the registry
- ChilledWindows.exe (PID: 6472)
- Delete Windows.exe (PID: 6460)
- Telegram.exe (PID: 4704)
- Hydra.exe (PID: 8248)
- PizDeath.exe (PID: 8676)
- GooseDesktop.exe (PID: 9612)
- Windows-KB2670838.msu.exe (PID: 10304)
- InfinityCrypt.exe (PID: 11496)
- Free YouTube Downloader.exe (PID: 11644)
- NoMoreRansom.exe (PID: 10824)
- DeriaLock.exe (PID: 12192)
- Telegram.exe (PID: 11768)
Checks proxy server information
- Cool Spot Deskmate.EXE (PID: 6572)
- Telegram.exe (PID: 4704)
- Antivirus.exe (PID: 6480)
- DeriaLock.exe (PID: 7096)
- ChilledWindows.exe (PID: 6472)
- DeriaLock.exe (PID: 12192)
- Telegram.exe (PID: 11768)
Creates files or folders in the user directory
- Delete Windows.exe (PID: 6460)
- DeriaLock.exe (PID: 7096)
- ChilledWindows.exe (PID: 6472)
- Telegram.exe (PID: 4704)
- InfinityCrypt.exe (PID: 11496)
- DeriaLock.exe (PID: 12192)
Dropped object may contain TOR URL's
- BadRabbit.exe (PID: 6368)
- rundll32.exe (PID: 6360)
Reads Microsoft Office registry keys
- heisenberg.exe (PID: 1288)
- PizDeath.exe (PID: 8676)
- msedge.exe (PID: 9912)
Reads Environment values
- Telegram.exe (PID: 4704)
- DeriaLock.exe (PID: 7096)
- DeriaLock.exe (PID: 12192)
- Telegram.exe (PID: 11768)
- identity_helper.exe (PID: 13024)
Changes the display of characters in the console
- chcp.com (PID: 9392)
Disables trace logs
- Telegram.exe (PID: 4704)
- DeriaLock.exe (PID: 7096)
- DeriaLock.exe (PID: 12192)
- Telegram.exe (PID: 11768)
Application launched itself
- msedge.exe (PID: 9912)
Reads CPU info
- InfinityCrypt.exe (PID: 11496)
Creates files in the program directory
- NoMoreRansom.exe (PID: 10824)
Process checks whether UAC notifications are on
- Illerka.C.exe (PID: 11408)
Reads the software policy settings
- Telegram.exe (PID: 4704)
- Telegram.exe (PID: 11768)
Mpress packer has been detected
- AntivirusPro2017.exe (PID: 6204)
UPX packer has been detected
- HMBlocker.exe (PID: 3844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6204) AntivirusPro2017.exe
Decrypted-URLs (4)http://licencecheck24.com/checking.php
http://securerem.com/buynow.php?bid=%advid%
http://securerem.com/support.html
http://twinkcam.net/images/v.php?id=%advid%
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 136704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32ee0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
419
Monitored processes
276
Malicious processes
11
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Users\admin\AppData\Local\Temp\DesktopPuzzle.exe" | C:\Users\admin\AppData\Local\Temp\DesktopPuzzle.exe | — | heisenberg.exe | |||||||||||
User: admin Company: Andy Feys Integrity Level: MEDIUM Description: Slider Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1288 | "C:\Users\admin\Desktop\heisenberg.exe" | C:\Users\admin\Desktop\heisenberg.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
| 1372 | "C:\Users\admin\AppData\Local\Temp\FakeAdwCleaner.exe" | C:\Users\admin\AppData\Local\Temp\FakeAdwCleaner.exe | heisenberg.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1692 | mspaint | C:\Windows\System32\mspaint.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 1073807364 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | mspaint | C:\Windows\System32\mspaint.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 1073807364 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2400 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\stopantivirus.bat" " | C:\Windows\System32\cmd.exe | — | heisenberg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2508 | mspaint | C:\Windows\System32\mspaint.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 1073807364 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7308 --field-trial-handle=2252,i,4900441568173332323,1661607287599247478,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
123 521
Read events
122 698
Write events
778
Delete events
45
Modification events
| (PID) Process: | (1288) heisenberg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1288) heisenberg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1288) heisenberg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1288) heisenberg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
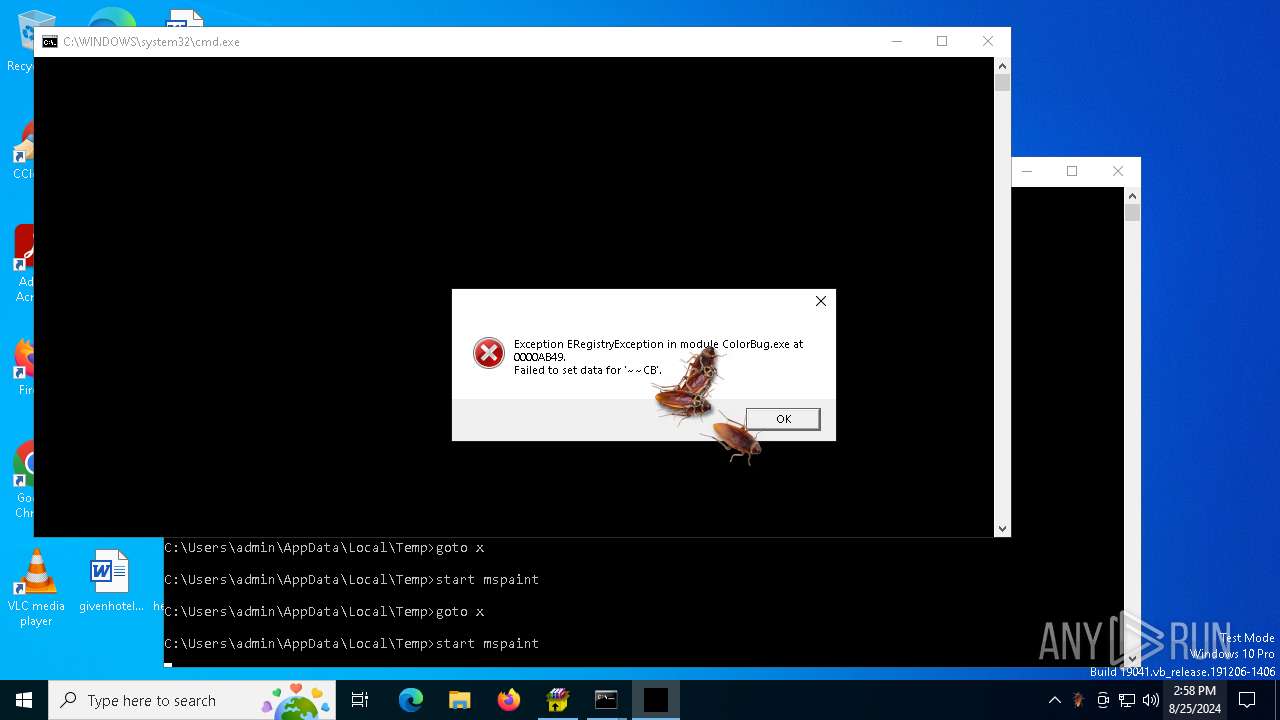
| (PID) Process: | (6468) ColorBug.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ~~CB |
Value: cb.exe | |||
| (PID) Process: | (6572) Cool Spot Deskmate.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Screen Babe Design |
| Operation: | write | Name: | DeleteList |
Value: | |||
| (PID) Process: | (6572) Cool Spot Deskmate.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Screen Babe Design |
| Operation: | write | Name: | DeleteFolder |
Value: | |||
| (PID) Process: | (6480) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\AnVi |
| Operation: | write | Name: | Settings_0 |
Value: 1 | |||
| (PID) Process: | (6480) Antivirus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | Use FormSuggest |
Value: Yes | |||
| (PID) Process: | (6480) Antivirus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3 |
| Operation: | write | Name: | 1601 |
Value: 0 | |||
Executable files
97
Suspicious files
222
Text files
158
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\Petya.A.exe | executable | |
MD5:AF2379CC4D607A45AC44D62135FB7015 | SHA256:26B4699A7B9EEB16E76305D843D4AB05E94D43F3201436927E13B3EBAFA90739 | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\Prank3.vbs | text | |
MD5:B7D4E96408D1C870570BC7C4A35387DC | SHA256:A50E401E8059FE456A0FB975F88258C8EBD2B73905657300808BB5BCEE3EC782 | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\Trololo.exe | executable | |
MD5:B6D61B516D41E209B207B41D91E3B90D | SHA256:3D0EFD55BDE5FB7A73817940BAC2A901D934B496738B7C5CAB7EA0F6228E28FE | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\stopantivirus.bat | text | |
MD5:31F028E35C7558A1EC0EA3A32227DB45 | SHA256:68FEB2C42355F24B14B0A93F927C4A830202D2511923D7253EAA590B8D6A4C01 | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\WannaCrypt0r.exe | executable | |
MD5:84C82835A5D21BBCF75A61706D8AB549 | SHA256:ED01EBFBC9EB5BBEA545AF4D01BF5F1071661840480439C6E5BABE8E080E41AA | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\scream.exe | executable | |
MD5:EE4566A61663F1A2C25B3AF887A364C9 | SHA256:5BC63DD48046CE906CA6F08A60919F48E7D1814690F0E1FFB2654334D119DC7E | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\You_Are_An_Idiot.exe | executable | |
MD5:0CFEB0915EDBDF1A298794C1669EC632 | SHA256:E90065AB6F60A1A49EA185538D6E32A6269574C96851FCB8A001A7C8A23F3084 | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\PowerPoint.exe | executable | |
MD5:70108103A53123201CEB2E921FCFE83C | SHA256:9C3F8DF80193C085912C9950C58051AE77C321975784CC069CEACD4F57D5861D | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\Windows-KB2670838.msu.exe | executable | |
MD5:6E49C75F701AA059FA6ED5859650B910 | SHA256:F91F02FD27ADA64F36F6DF59A611FEF106FF7734833DEA825D0612E73BDFB621 | |||
| 1288 | heisenberg.exe | C:\Users\admin\AppData\Local\Temp\Antivirus.exe | executable | |
MD5:C7E9746B1B039B8BD1106BCA3038C38F | SHA256:B1369BD254D96F7966047AD4BE06103830136629590182D49E5CB8680529EBD4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
286
TCP/UDP connections
206
DNS requests
169
Threats
183
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 168.156.42.60:80 | http://168.156.42.60:80/ask?t=4&u=3&a=20&m=29fa4b95&h=0 | unknown | — | — | unknown |
— | — | GET | — | 168.156.42.60:80 | http://168.156.42.60:80/ask?t=4&u=3&a=0&m=29fa4b95&h=0 | unknown | — | — | unknown |
6480 | Antivirus.exe | GET | 404 | 104.245.107.49:80 | http://searchdusty.com/avt/avtr.dat | unknown | — | — | whitelisted |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | OPTIONS | 200 | 23.32.238.91:443 | https://bzib.nelreports.net/api/report?cat=bingbusiness | unknown | — | — | unknown |
12192 | DeriaLock.exe | GET | 403 | 162.55.0.137:80 | http://arizonacode.bplaced.net/HF/SystemLocker/UNLOCKKEYS/LOGON.exe | unknown | — | — | whitelisted |
7096 | DeriaLock.exe | GET | 403 | 162.55.0.137:80 | http://arizonacode.bplaced.net/HF/SystemLocker/unlock-everybody.txt | unknown | — | — | whitelisted |
7096 | DeriaLock.exe | GET | 403 | 162.55.0.137:80 | http://arizonacode.bplaced.net/HF/SystemLocker/unlock-everybody.txt | unknown | — | — | whitelisted |
4704 | Telegram.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
6480 | Antivirus.exe | GET | 404 | 104.245.107.49:80 | http://searchdusty.com/avt/avt.dat | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 168.156.42.60:80 | — | WA-K20 | US | unknown |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 192.168.100.2:445 | — | — | — | whitelisted |
— | — | 168.156.42.60:445 | — | WA-K20 | US | unknown |
6360 | rundll32.exe | 192.168.100.2:80 | — | — | — | whitelisted |
4704 | Telegram.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
4 | System | 192.168.100.2:445 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.vikingwebscanner.com |
| malicious |
ip-api.com |
| shared |
frequentwin.com |
| unknown |
fastsofgeld.com |
| unknown |
highway-traffic.com |
| unknown |
searchdusty.com |
| whitelisted |
arizonacode.bplaced.net |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Attempt to connect to an external SMB server |
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
4704 | Telegram.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4704 | Telegram.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6480 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6480 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6480 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
7096 | DeriaLock.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M1 |
1 ETPRO signatures available at the full report