| File name: | Ancalog Exploit Builder AchillePower.rar |
| Full analysis: | https://app.any.run/tasks/9d189b71-9cd4-44d2-b67f-936083dc9069 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | July 15, 2018, 11:34:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FB11F6D5AC9DFEFA6C9BB37E2103058C |
| SHA1: | D183B0A09B51C75CC0843C69542BA437292D5B90 |
| SHA256: | 9947E7706F0D321310340C526BAD437BBEC54A714E9F032C9634361DA22D01E7 |
| SSDEEP: | 98304:4iHN+VOEkLojG2XCSjWF0kb43dRZjLlBg3QX/2nYW:4aN+VoojGS6+VLlBz/2T |
MALICIOUS
Application was dropped or rewritten from another process
- AncalogBuilder.exe (PID: 2500)
- AncalogBuilder.exe (PID: 2284)
- svchost.exe (PID: 992)
- AncalogBuilder.exe (PID: 2256)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3132)
- AncalogBuilder.exe (PID: 2256)
Changes the autorun value in the registry
- svchost.exe (PID: 992)
Detected Hawkeye Keylogger
- svchost.exe (PID: 992)
SUSPICIOUS
Executable content was dropped or overwritten
- svchost.exe (PID: 992)
- AncalogBuilder.exe (PID: 2500)
- 7zFM.exe (PID: 600)
Checks for external IP
- svchost.exe (PID: 992)
Creates executable files which already exist in Windows
- AncalogBuilder.exe (PID: 2500)
Creates files in the user directory
- svchost.exe (PID: 992)
INFO
Dropped object may contain URL's
- 7zFM.exe (PID: 600)
- AncalogBuilder.exe (PID: 2500)
- svchost.exe (PID: 992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
43
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\Ancalog Exploit Builder AchillePower.rar" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 992 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" 0 | C:\Users\admin\AppData\Local\Temp\svchost.exe | AncalogBuilder.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Phulli Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
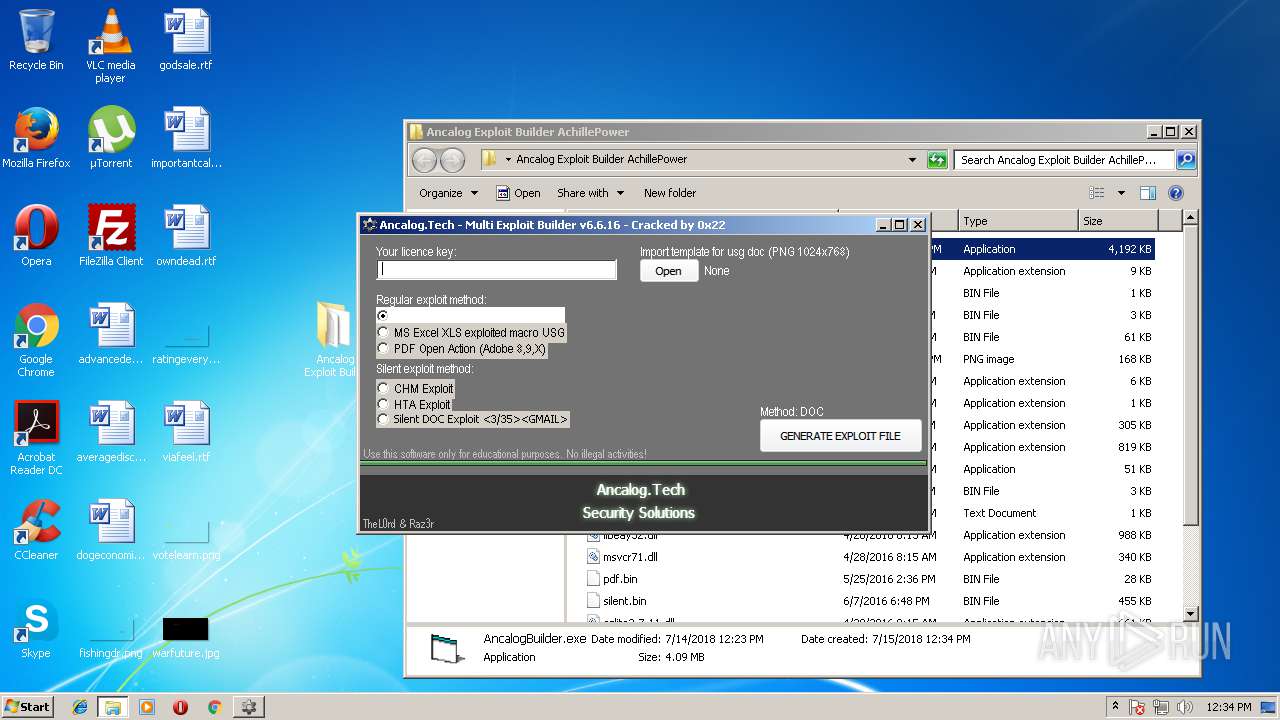
| 2256 | "C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe" 0 | C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe | AncalogBuilder.exe | ||||||||||||
User: admin Company: ancalog.tech Integrity Level: HIGH Description: Ancalog Multi Exploit Builder Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2284 | "C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe" 0 | C:\Users\admin\AppData\Local\Temp\AncalogBuilder.exe | — | AncalogBuilder.exe | |||||||||||
User: admin Company: ancalog.tech Integrity Level: MEDIUM Description: Ancalog Multi Exploit Builder Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2500 | "C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower\AncalogBuilder.exe" | C:\Users\admin\Desktop\Ancalog Exploit Builder AchillePower\AncalogBuilder.exe | explorer.exe | ||||||||||||
User: admin Company: BreakingSecurity.net Integrity Level: MEDIUM Exit code: 0 Version: 1.01.0001 Modules
| |||||||||||||||
| 3028 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 | |||||||||||||||
| 3132 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
788
Read events
758
Write events
30
Delete events
0
Modification events
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0041006E00630061006C006F00670020004500780070006C006F006900740020004200750069006C00640065007200200041006300680069006C006C00650050006F007700650072002E007200610072005C000000 | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (600) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar5 |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000003F00000001000000640000000F00000001000000640000000D00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000003600000001000000640000005A00000001000000640000005F00000001000000640000001F00000001000000640000002000000001000000640000002E00000001000000640000003E0000000100000064000000 | |||
Executable files
10
Suspicious files
5
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\cap.bin | text | |
MD5:— | SHA256:— | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\enable-macro.png | image | |
MD5:— | SHA256:— | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\doc.bin | binary | |
MD5:— | SHA256:— | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\fl.dll | document | |
MD5:— | SHA256:— | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\hta.bin | html | |
MD5:— | SHA256:— | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\AncalogBuilder.exe | executable | |
MD5:— | SHA256:— | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\as.dll | document | |
MD5:3E708E0E21631A387D76738AAEBD5C82 | SHA256:65DB0EBD77ABBA9DB0406765FDED0EA13EBF49E9A3CEB7B4FA6069B46DF3D370 | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\hhc.exe | executable | |
MD5:7A7935B7BDE566AC60B5EF995B9DAF83 | SHA256:3E96894609819AE3D595FF6E0FBE9CE6C9AC17BDEDA256B994831992F668CB99 | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\exp.dll | xml | |
MD5:A535A7FE2B64CACF4D84CCDCBB644A76 | SHA256:2656DD6689ABE758A9A4B72E7ADBA1A2CEBA9FEAA375700C794A9E7C8BC618E1 | |||
| 600 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8521519A\Ancalog Exploit Builder AchillePower\fg.dll | text | |
MD5:948905E39EA0C6A42A81AC19F756F093 | SHA256:989713BA5D8C72EB57C38EE9A939FB45FEF21B6C259328197F59A7A59F11CE4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
992 | svchost.exe | GET | 403 | 104.16.16.96:80 | http://whatismyipaddress.com/ | US | text | 100 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
992 | svchost.exe | 104.16.16.96:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |