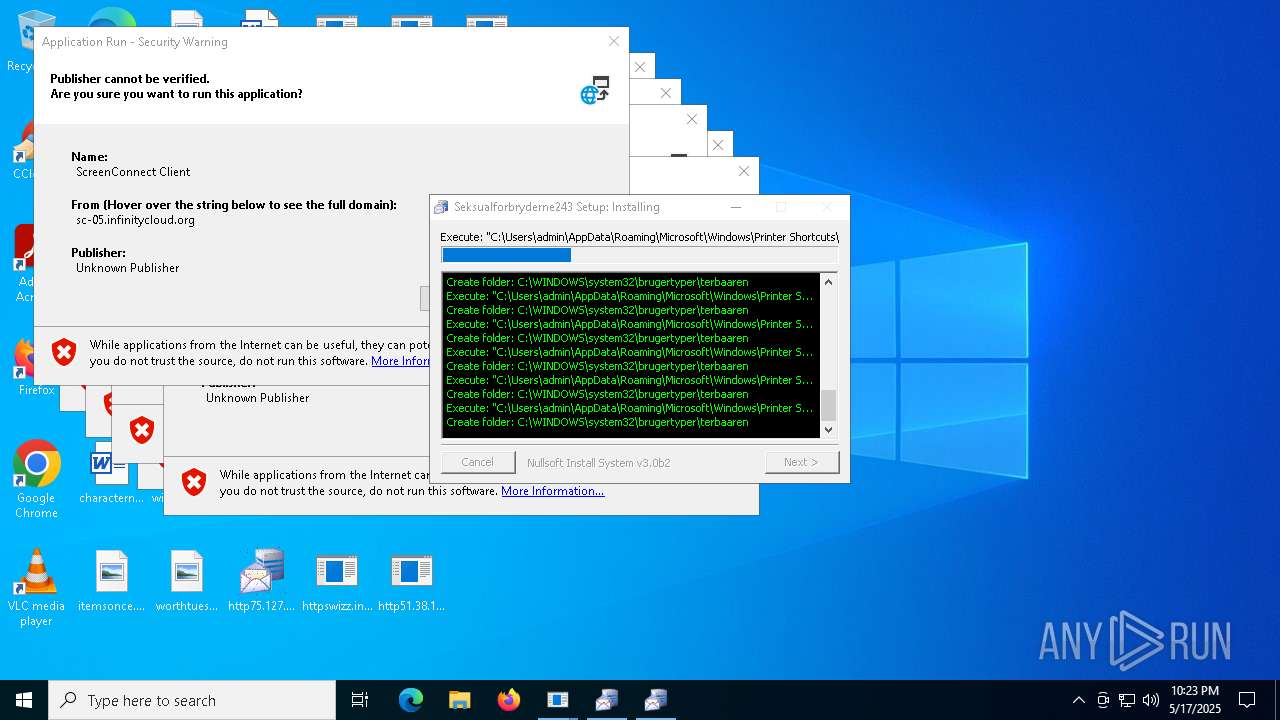
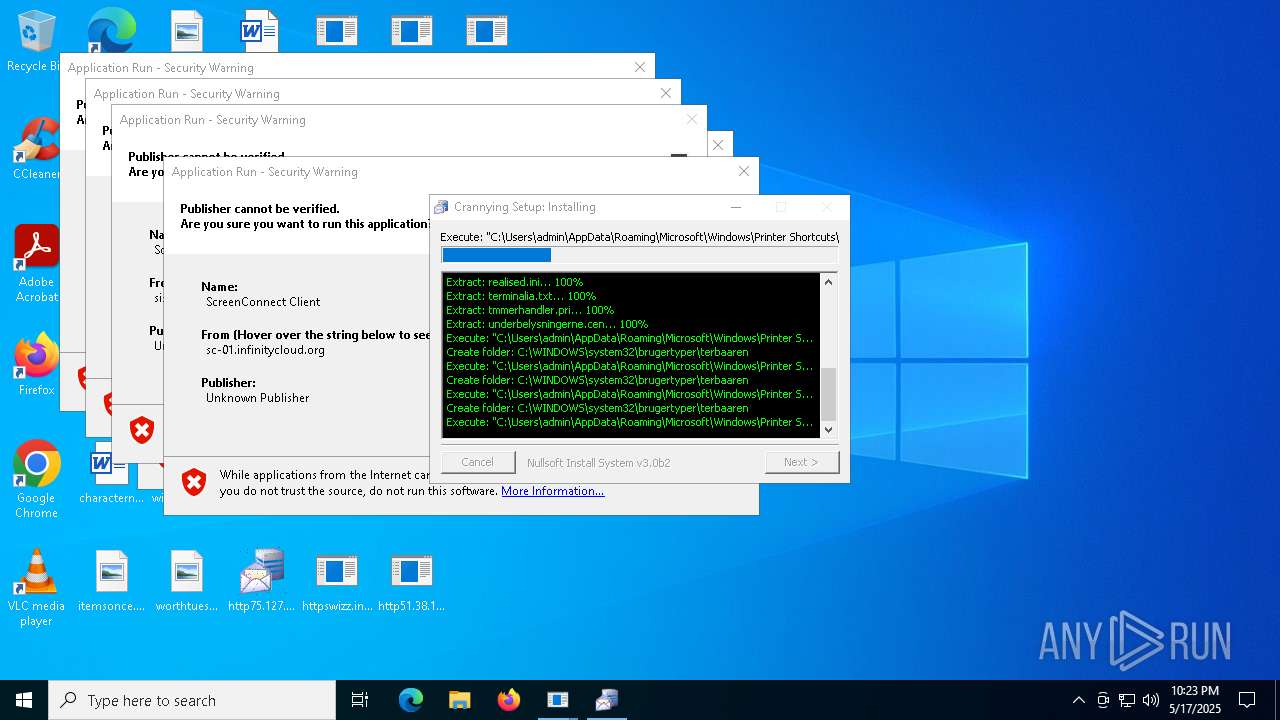
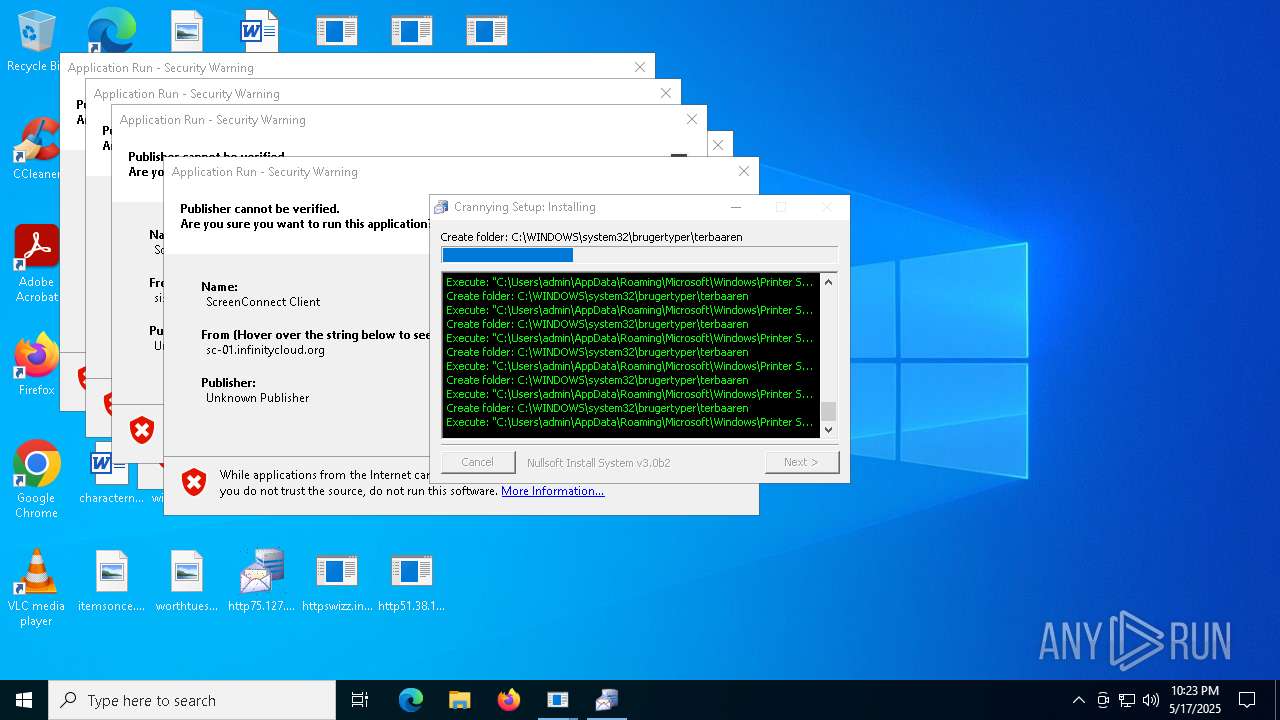
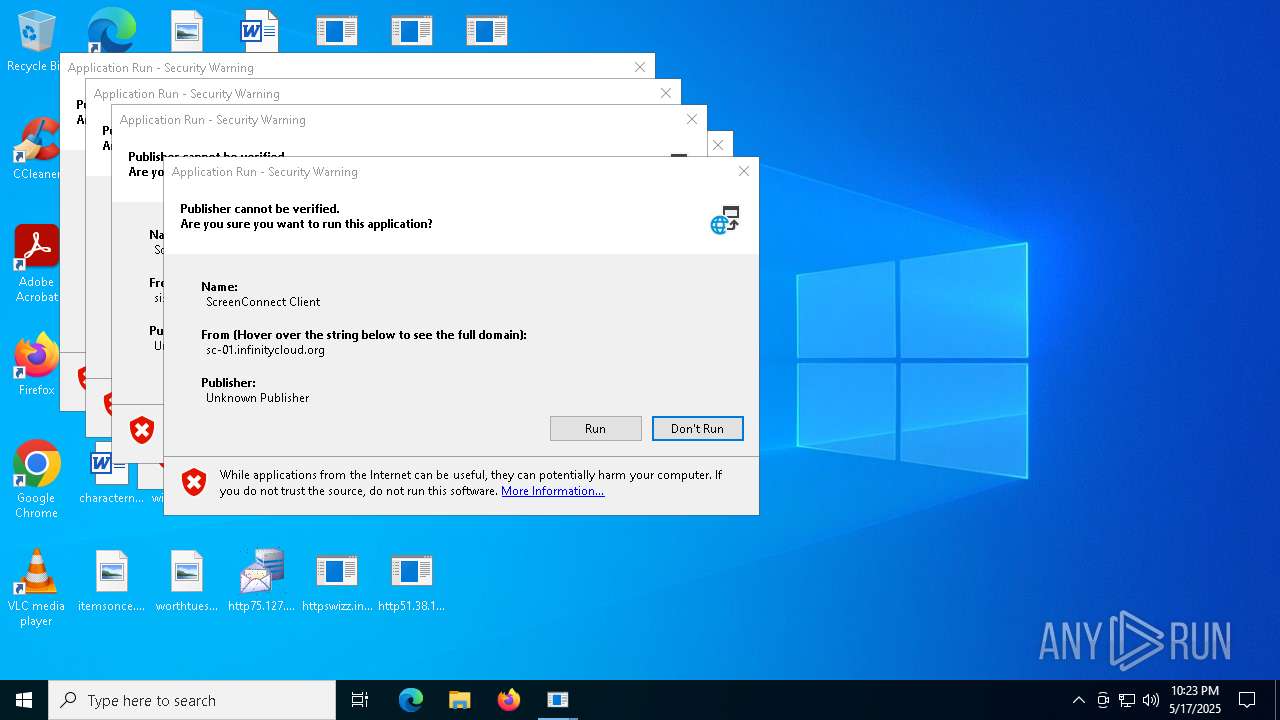
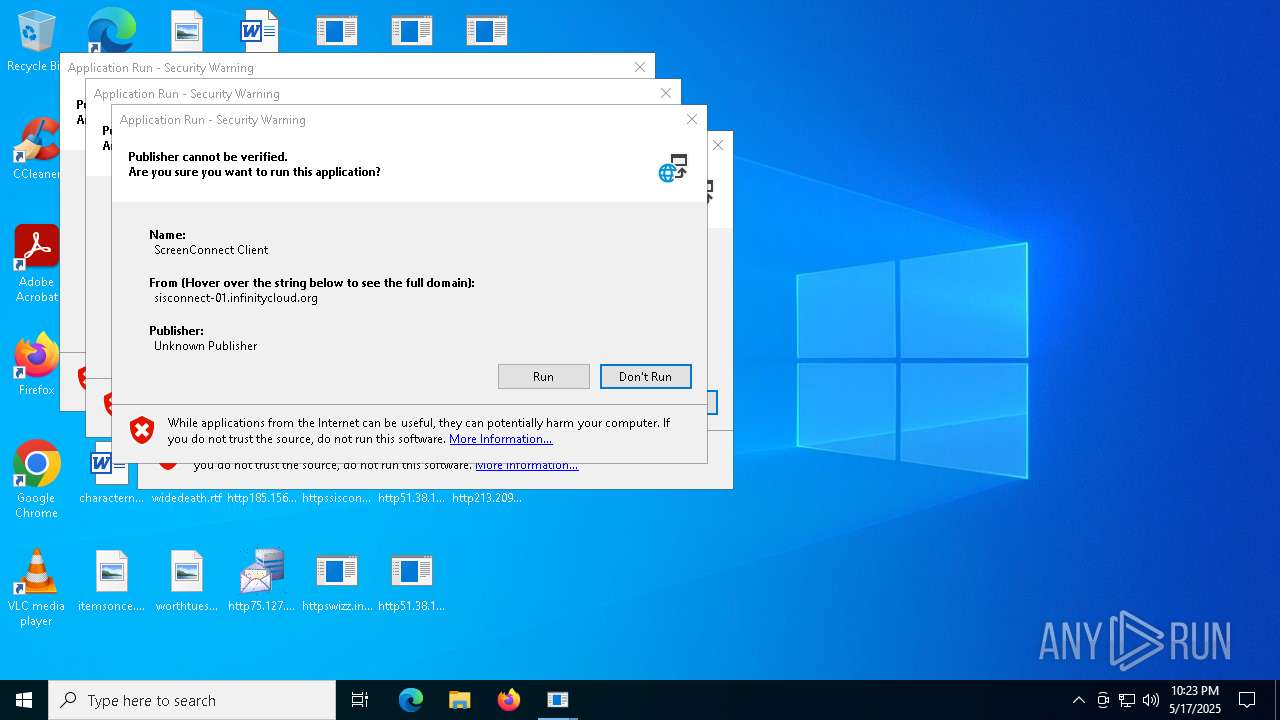
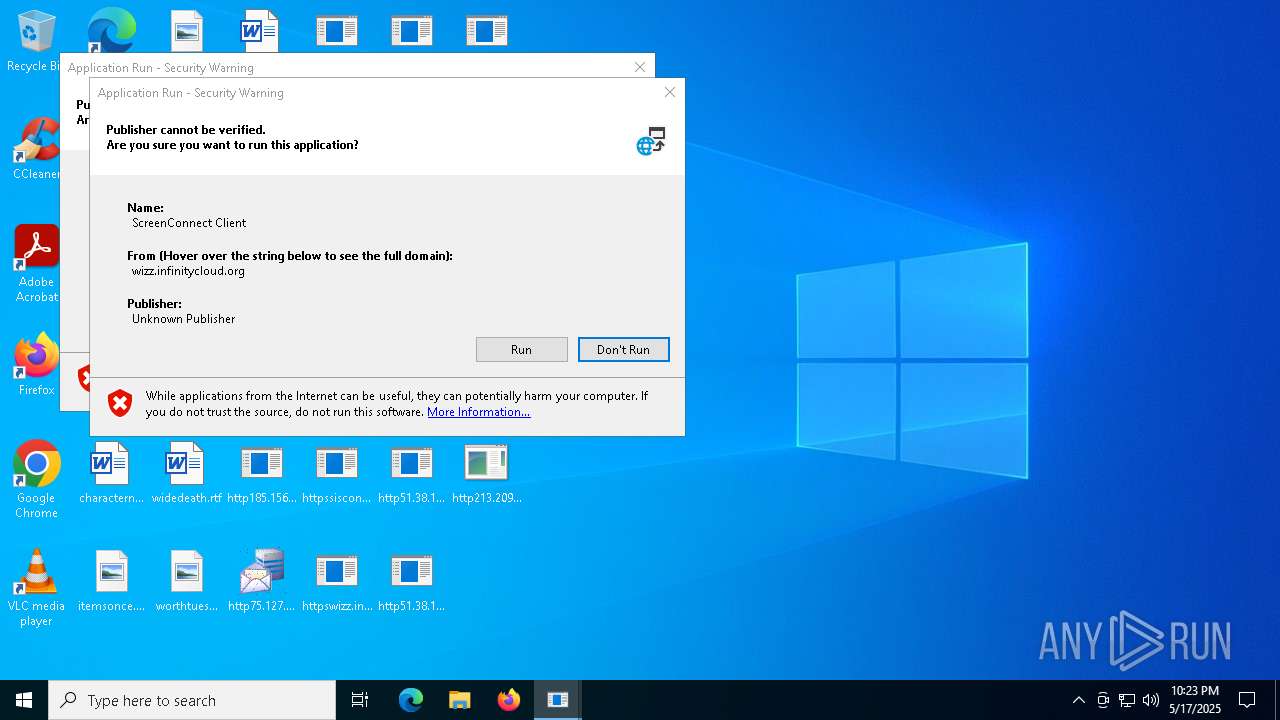
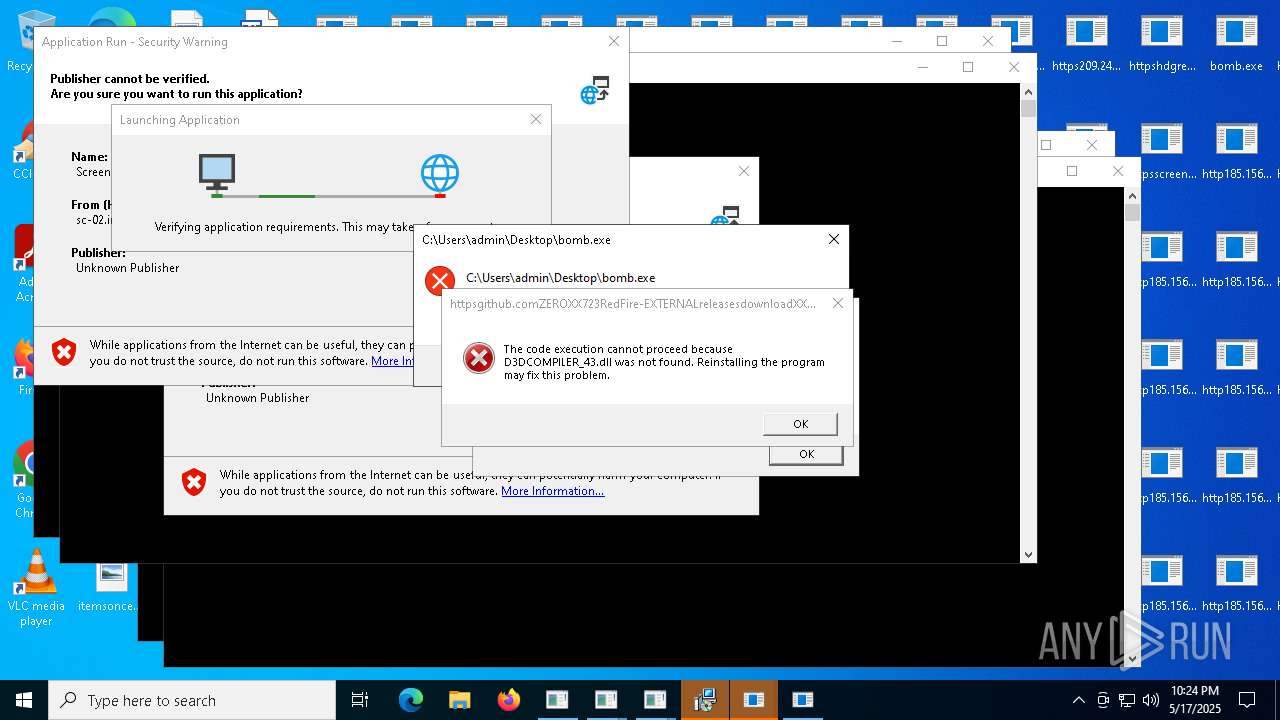
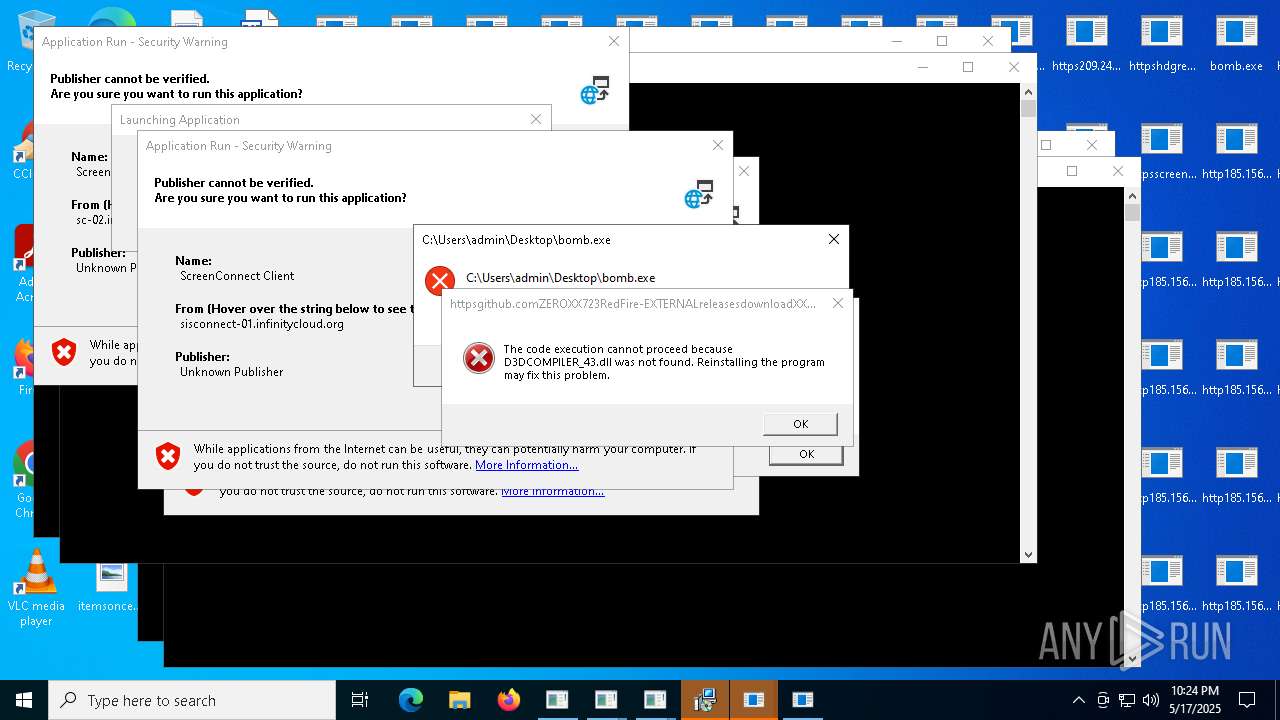
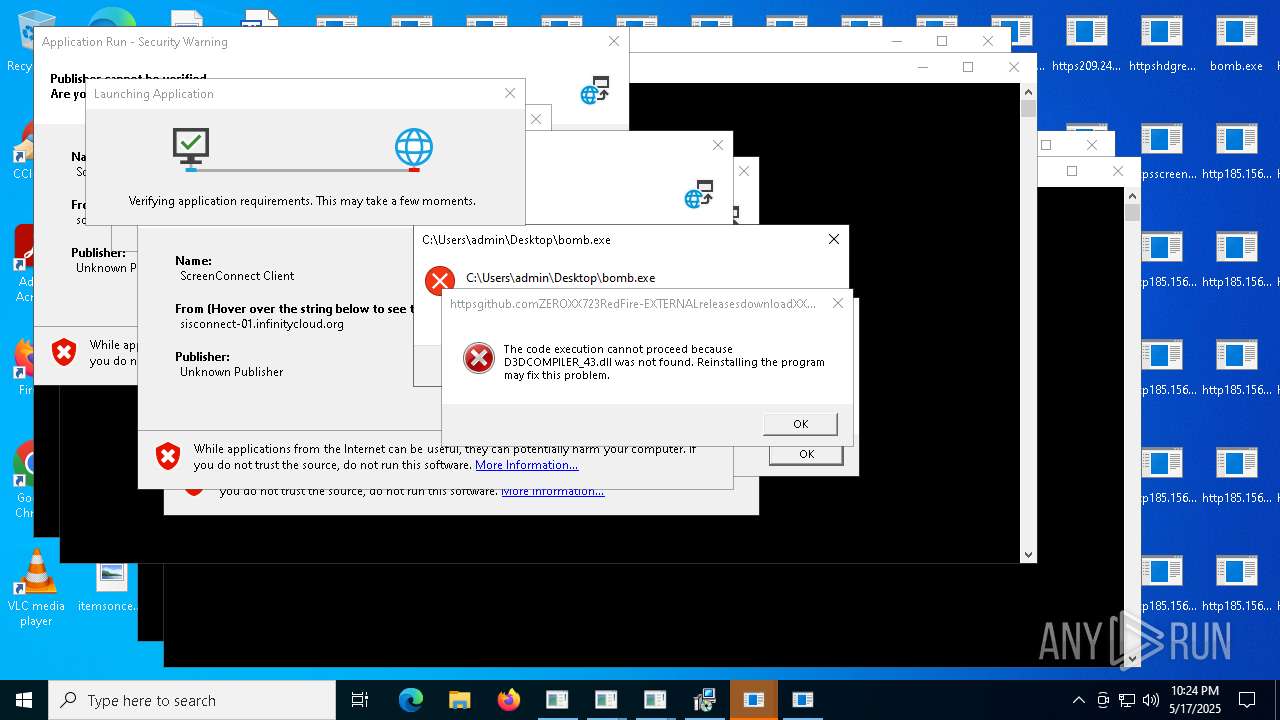
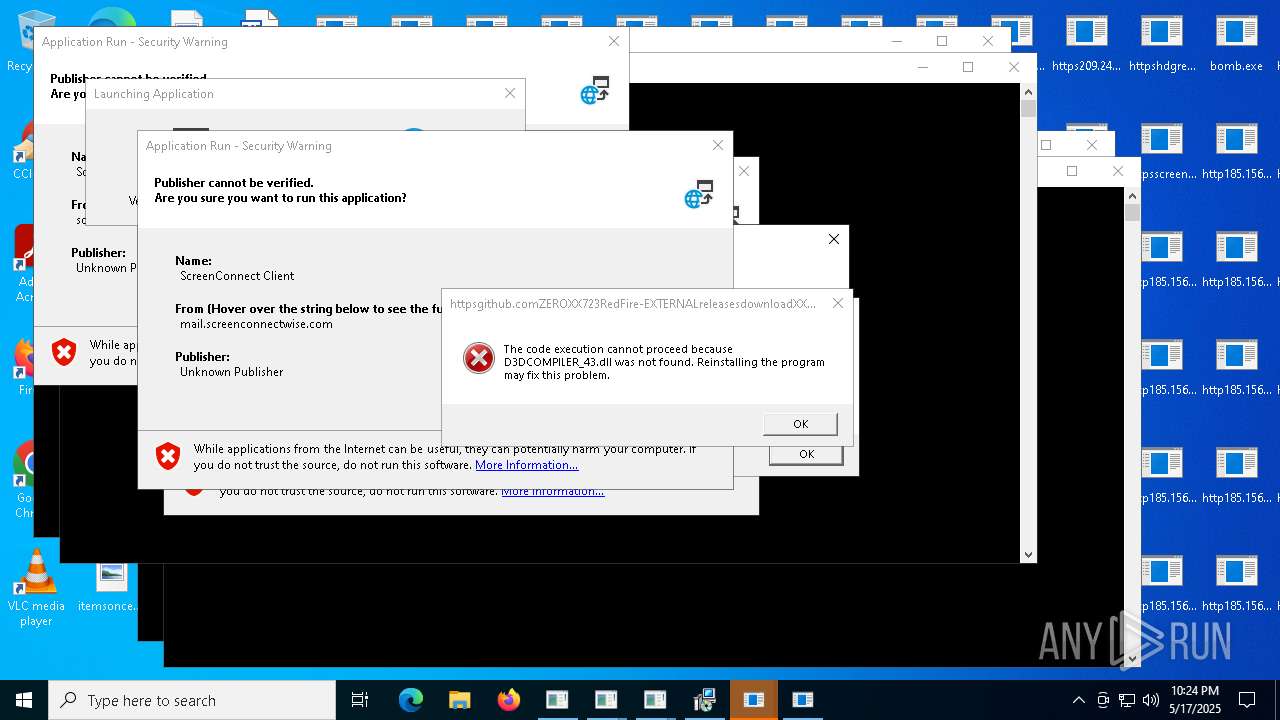
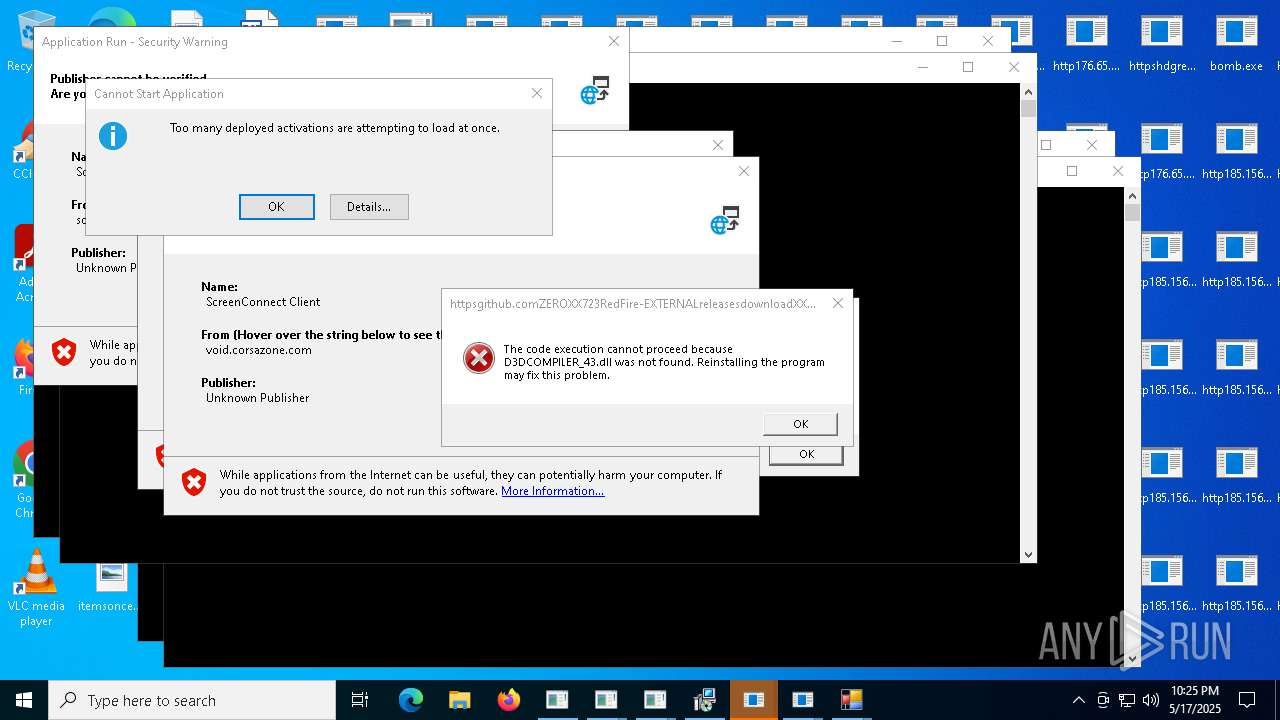
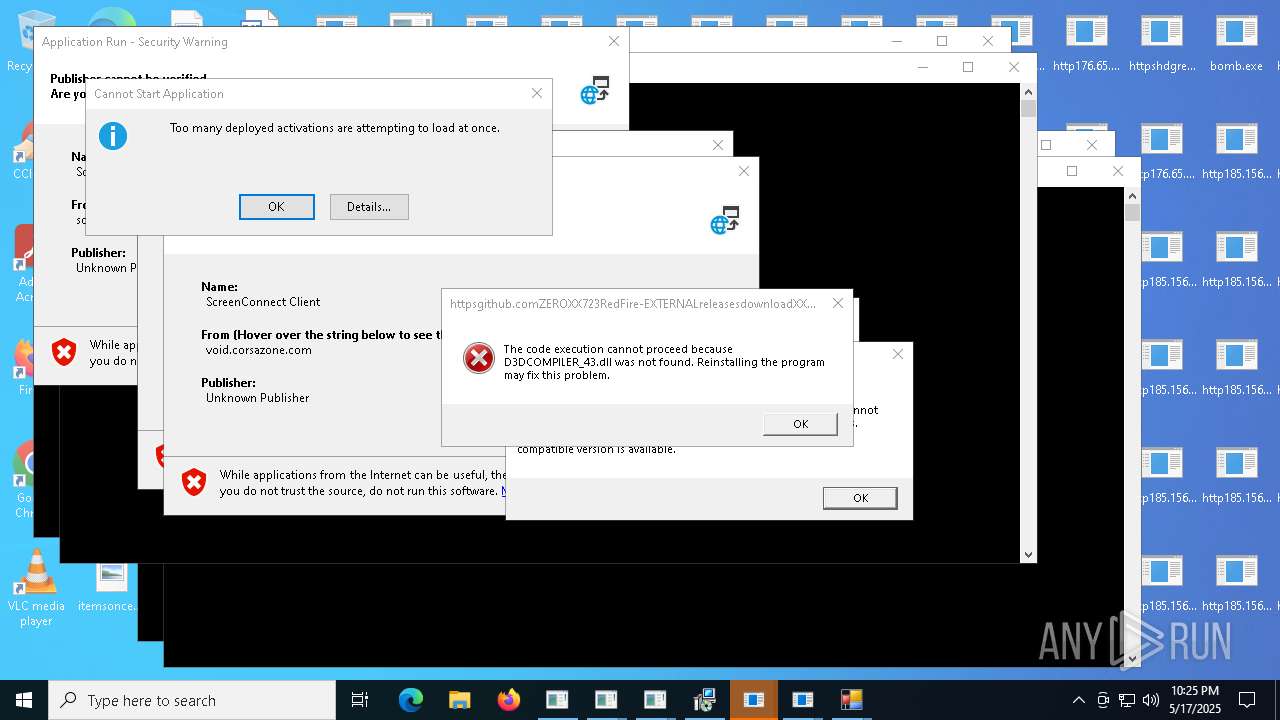
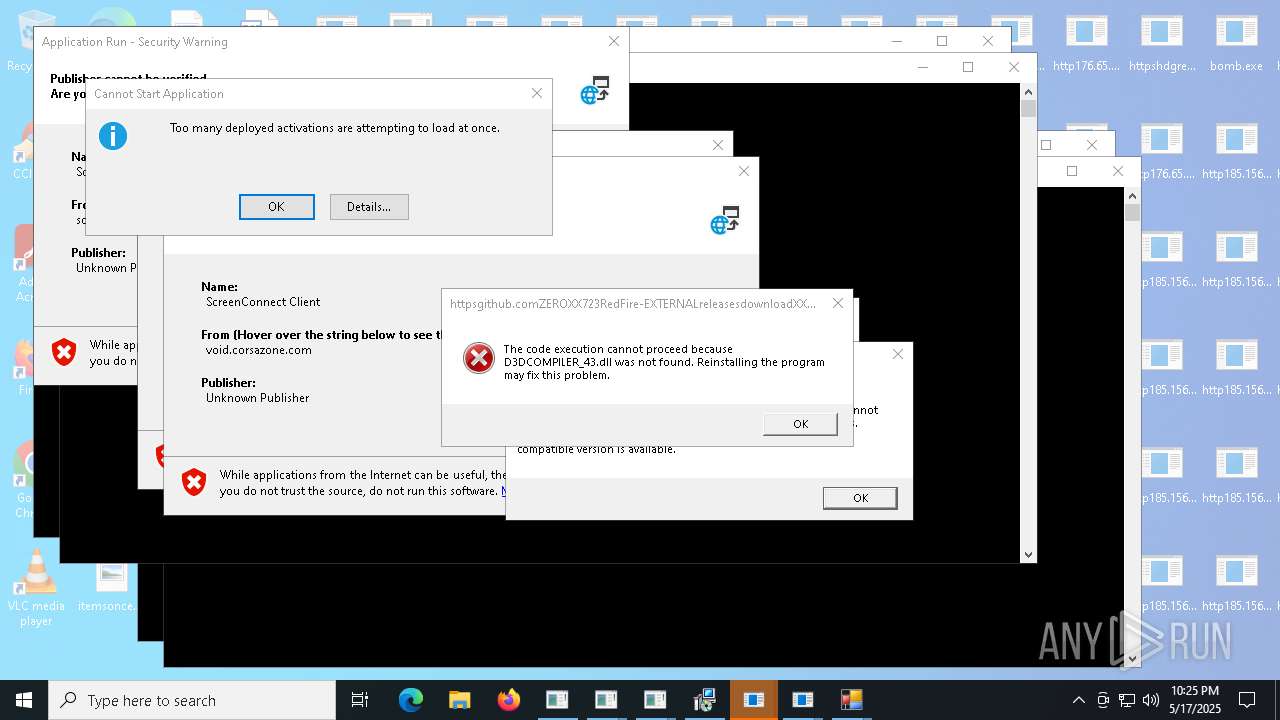
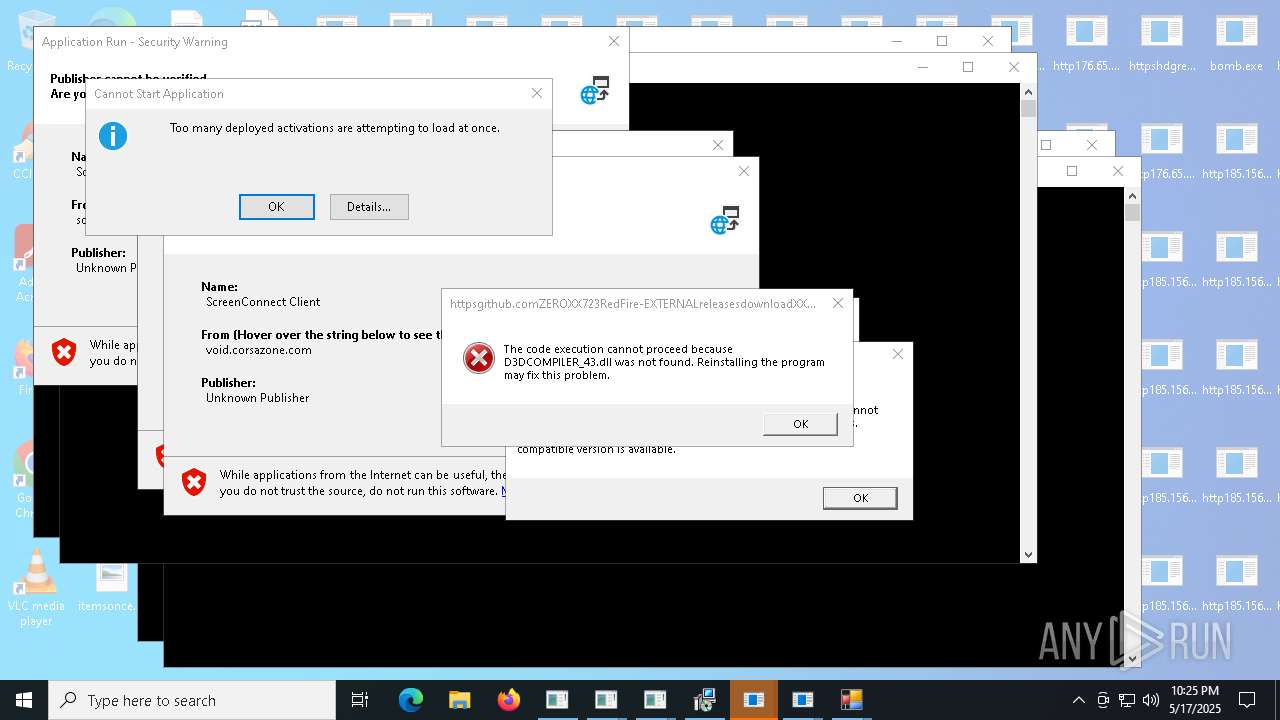
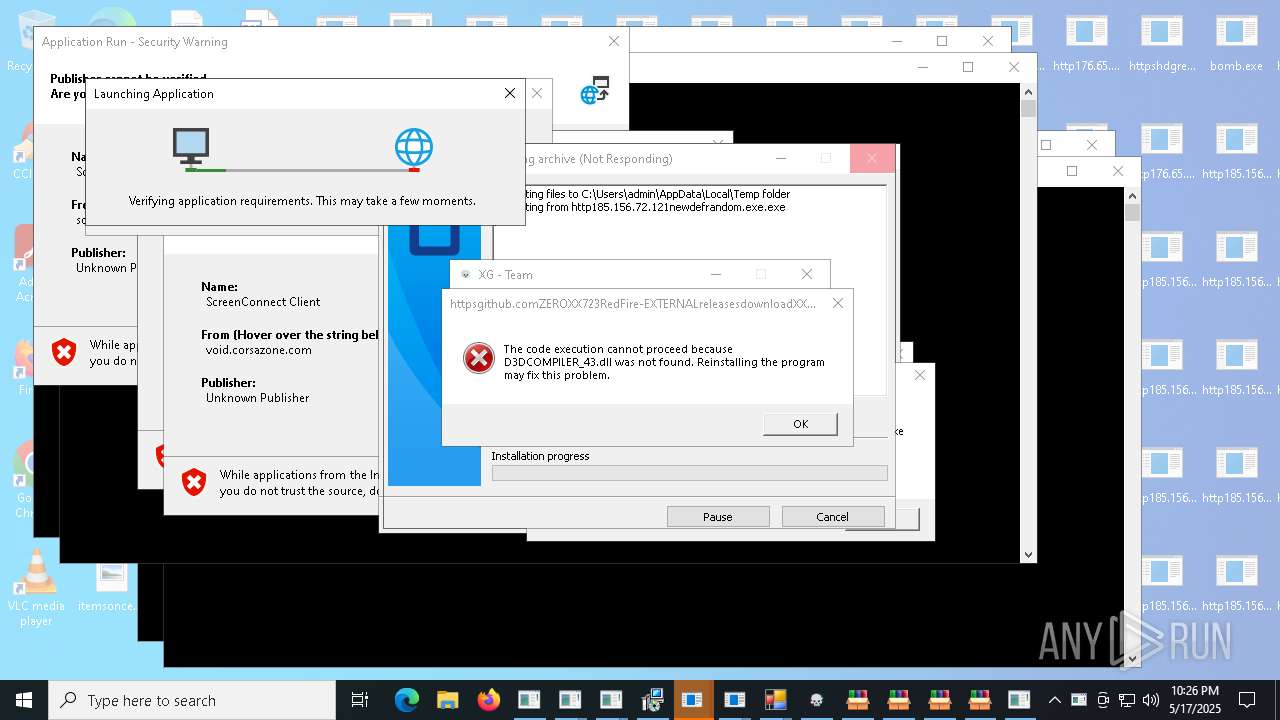
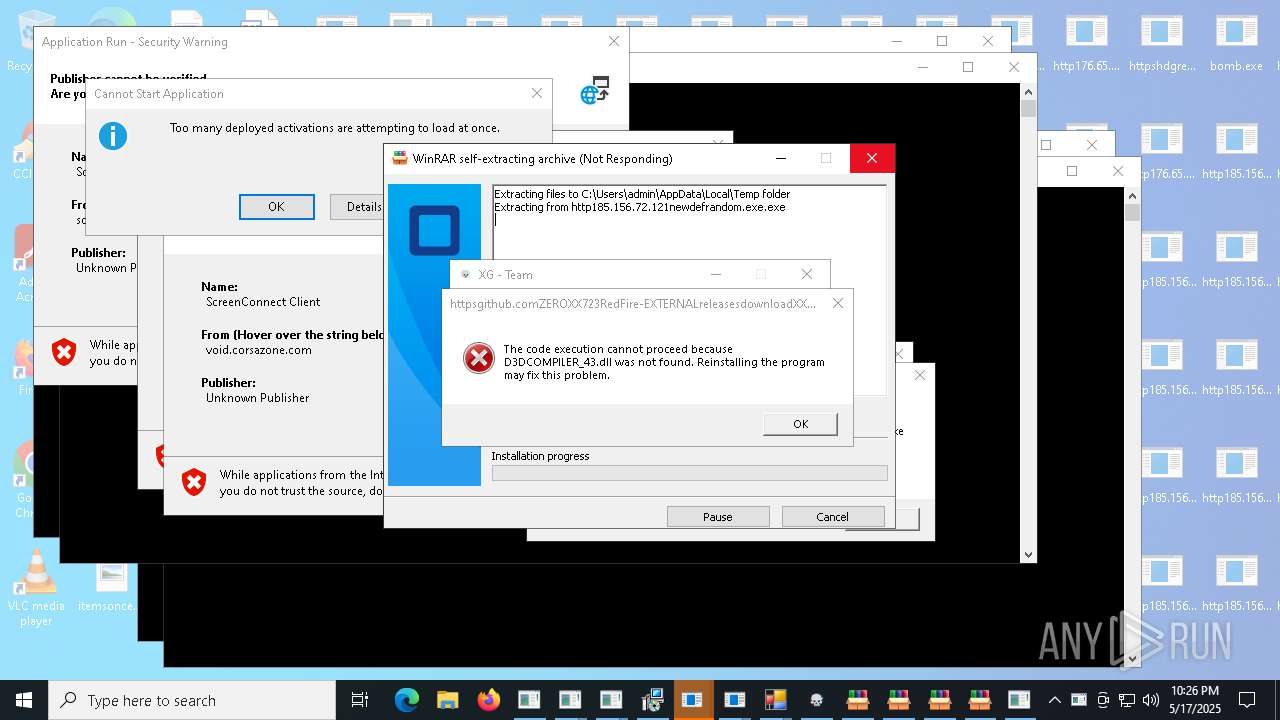
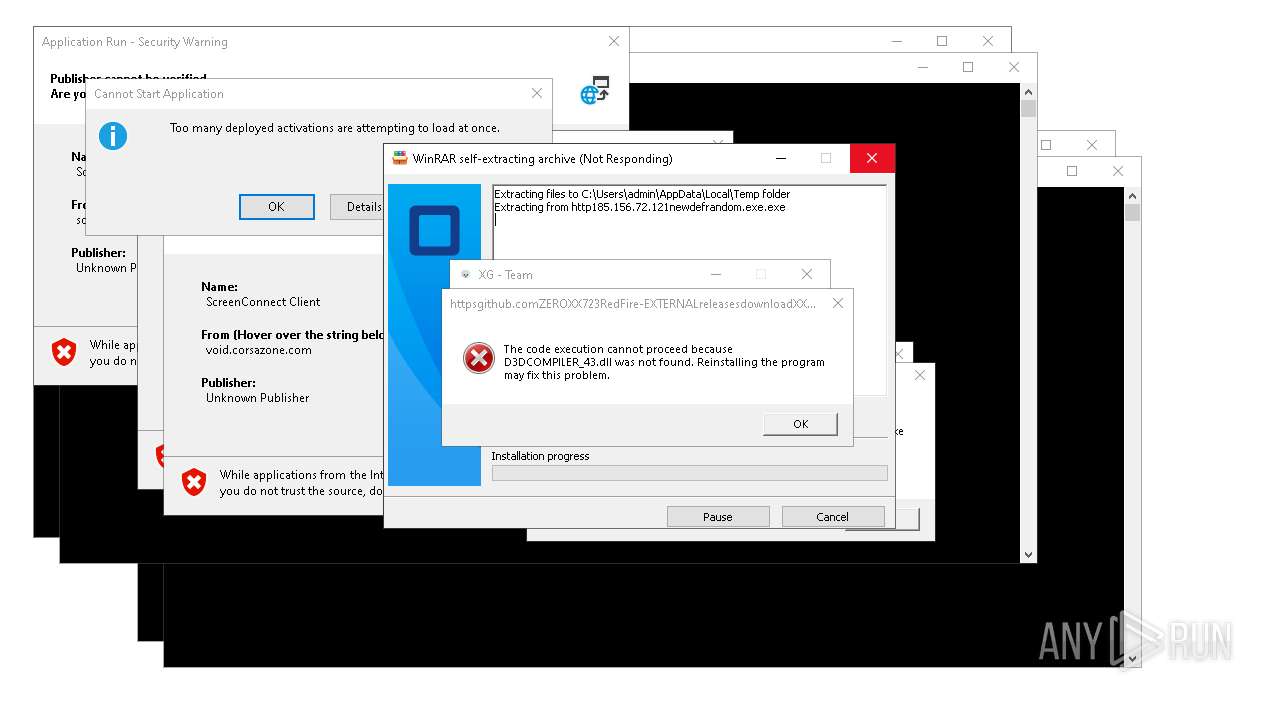
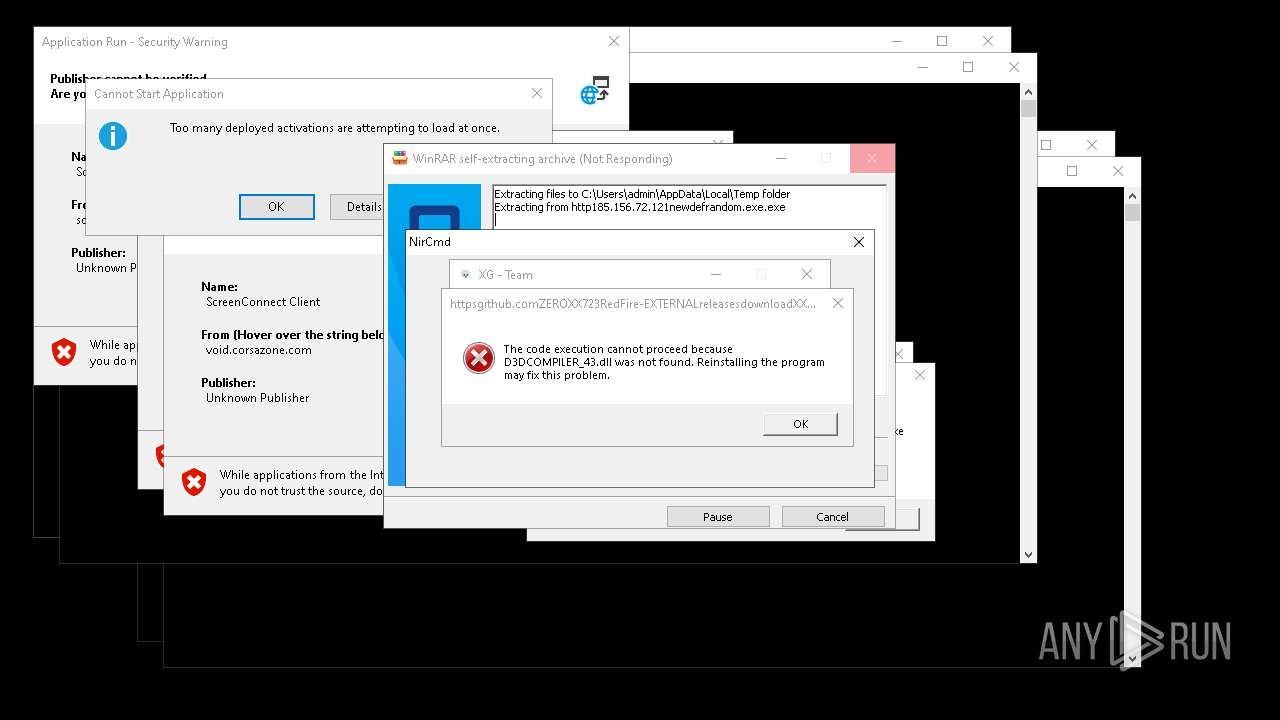
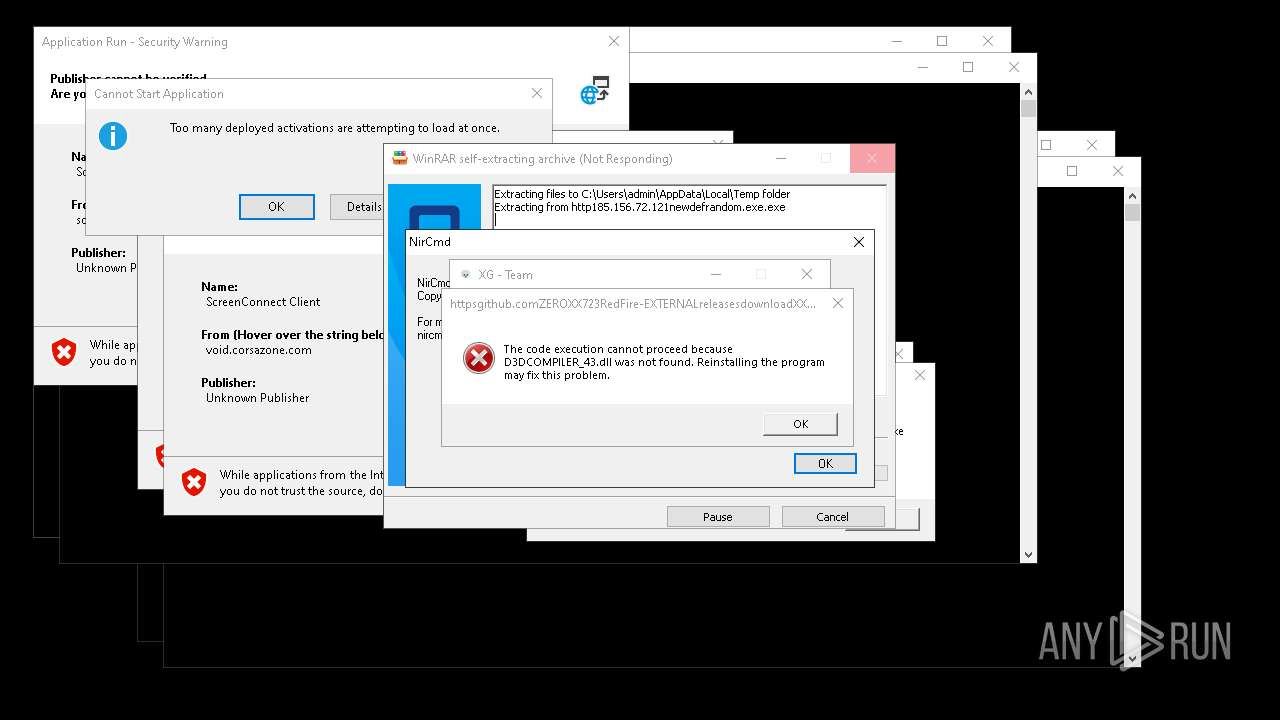
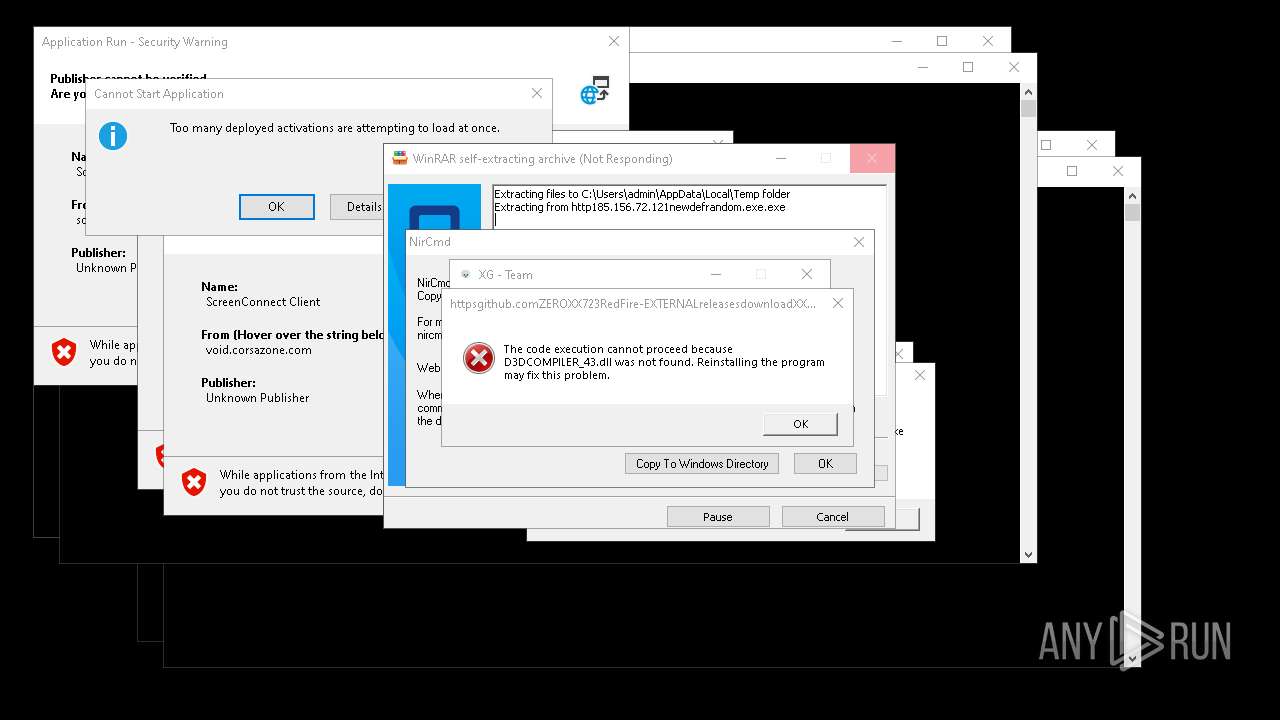
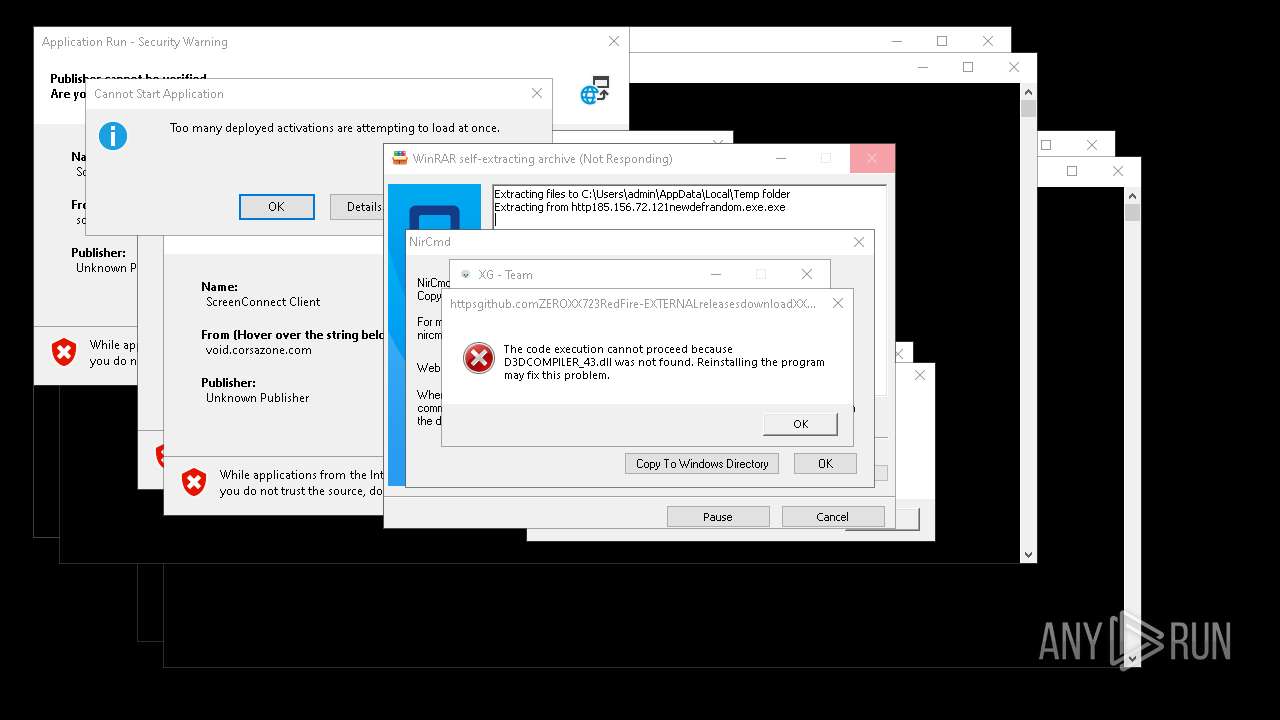
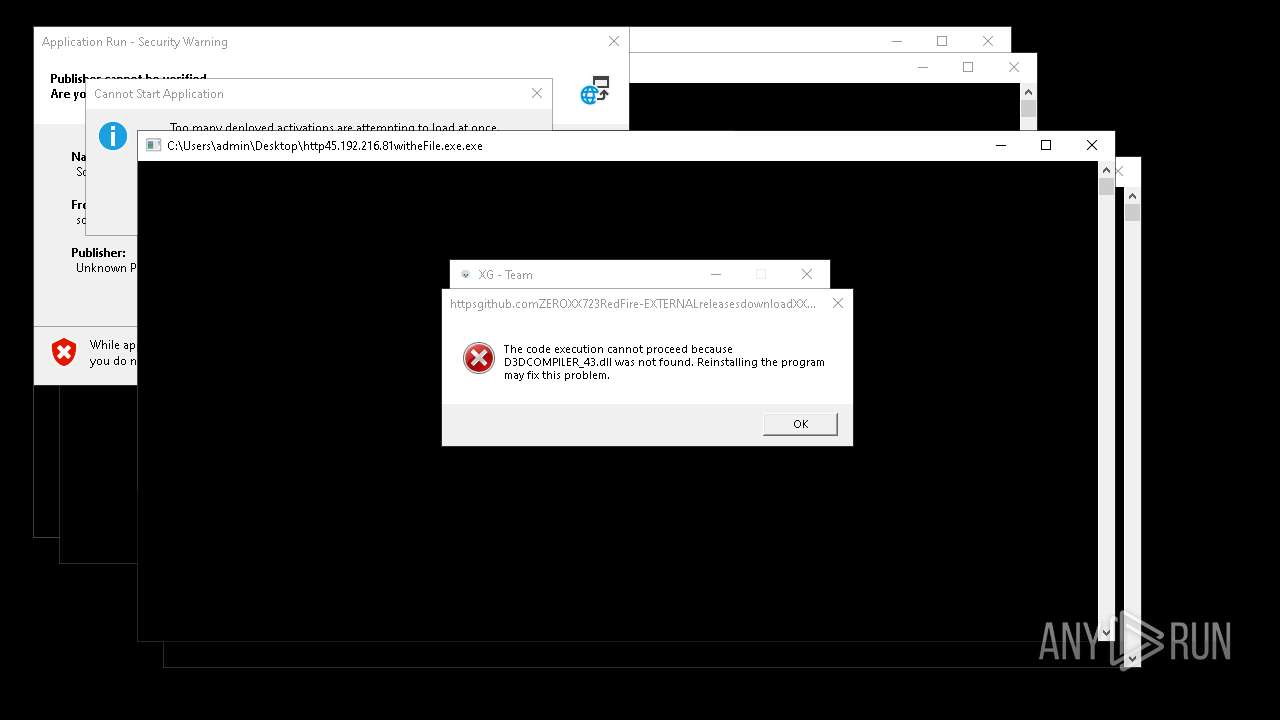
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/f84aa50f-8d83-4b0c-aa85-3f583ca20fac |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 17, 2025, 22:23:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0E2AD53C884E25F969B3A575F4BB90BB |
| SHA1: | 81E774FE109DDC9185AD3FB68995A069CE9045E0 |
| SHA256: | 990D1FF1AB883A9BACBBB6ABCF975139D9AB359B74FFBA16F1FA7A66A30E935D |
| SSDEEP: | 192:OJa0tZMoQszhl4AKd+QHzdPbwPz1OLU87glpp/bI6J4YlTtoIw:OLJQjd+qzZ0OLU870NJDoI |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- bomb.exe (PID: 6028)
Known privilege escalation attack
- dllhost.exe (PID: 7448)
GHOSTSOCKS has been found (auto)
- bomb.exe (PID: 6028)
Create files in the Startup directory
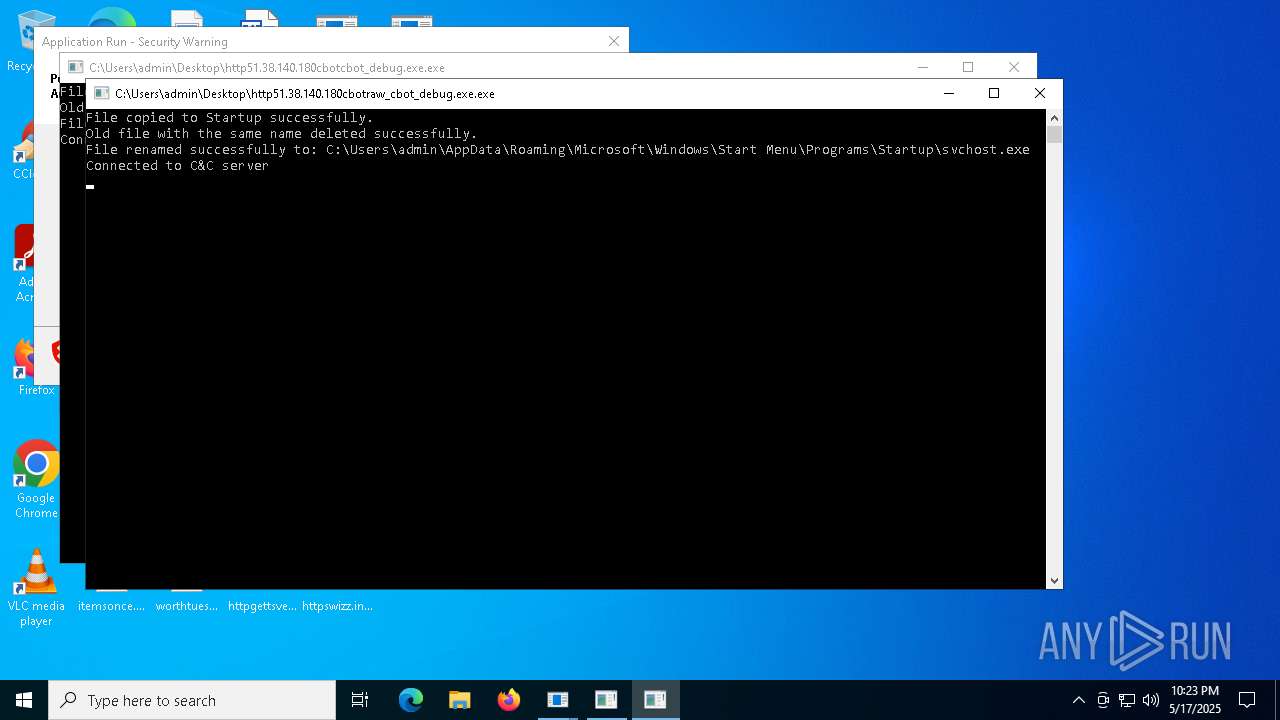
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
Executing a file with an untrusted certificate
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 7504)
- http75.127.7.164Supawn.exe.exe (PID: 11868)
- httpsgithub.comlegendary99999knjklbnkn-releasesdownloaddfbvsdfbsgfdbinferno.exe.exe (PID: 11880)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 12156)
- httpsgithub.comlegendary99999vdfsvdsfvsdfvreleasesdownloadfabdvadfvad123123213.exe.exe (PID: 12448)
Changes the autorun value in the registry
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
DCRAT has been found (auto)
- bomb.exe (PID: 6028)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1196)
DARKCRYSTAL has been detected (SURICATA)
- http51.38.140.180cbotcbot.exe.exe (PID: 5960)
Connects to the CnC server
- http51.38.140.180cbotcbot.exe.exe (PID: 5960)
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Process requests binary or script from the Internet
- bomb.exe (PID: 6028)
- bomb.exe (PID: 6032)
- bomb.exe (PID: 4208)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 6048)
- bomb.exe (PID: 6228)
- bomb.exe (PID: 4452)
- bomb.exe (PID: 2416)
- bomb.exe (PID: 2340)
- bomb.exe (PID: 2664)
- bomb.exe (PID: 1512)
- bomb.exe (PID: 2136)
- bomb.exe (PID: 7936)
- bomb.exe (PID: 7416)
- bomb.exe (PID: 5124)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 6944)
Potential Corporate Privacy Violation
- bomb.exe (PID: 6028)
- bomb.exe (PID: 6032)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 4208)
- bomb.exe (PID: 1512)
- bomb.exe (PID: 2772)
- bomb.exe (PID: 6048)
- bomb.exe (PID: 6228)
- bomb.exe (PID: 7416)
- bomb.exe (PID: 4452)
- bomb.exe (PID: 2416)
- bomb.exe (PID: 2340)
- bomb.exe (PID: 2664)
- bomb.exe (PID: 8052)
- bomb.exe (PID: 2136)
- bomb.exe (PID: 7936)
- bomb.exe (PID: 6944)
- bomb.exe (PID: 6192)
- bomb.exe (PID: 5968)
- bomb.exe (PID: 5124)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 3180)
- bomb.exe (PID: 7576)
- bomb.exe (PID: 5164)
- bomb.exe (PID: 7972)
- bomb.exe (PID: 7996)
- bomb.exe (PID: 6268)
- bomb.exe (PID: 7196)
- bomb.exe (PID: 4688)
- bomb.exe (PID: 6988)
- bomb.exe (PID: 7256)
- bomb.exe (PID: 8200)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 7836)
- bomb.exe (PID: 8012)
- bomb.exe (PID: 8208)
- bomb.exe (PID: 8312)
- bomb.exe (PID: 8080)
- bomb.exe (PID: 8320)
- bomb.exe (PID: 8232)
- bomb.exe (PID: 8460)
- bomb.exe (PID: 8448)
- bomb.exe (PID: 8416)
- bomb.exe (PID: 8592)
- bomb.exe (PID: 8716)
- bomb.exe (PID: 8564)
- bomb.exe (PID: 8512)
- bomb.exe (PID: 8352)
- bomb.exe (PID: 8676)
- bomb.exe (PID: 8732)
- bomb.exe (PID: 8424)
- bomb.exe (PID: 8304)
- bomb.exe (PID: 8628)
- bomb.exe (PID: 8536)
- bomb.exe (PID: 8652)
- bomb.exe (PID: 8816)
- bomb.exe (PID: 8804)
- bomb.exe (PID: 8760)
- bomb.exe (PID: 8880)
- bomb.exe (PID: 8836)
- bomb.exe (PID: 8952)
- bomb.exe (PID: 8944)
Reads the date of Windows installation
- bomb.exe (PID: 6028)
Connects to the server without a host name
- bomb.exe (PID: 6028)
- bomb.exe (PID: 6032)
- bomb.exe (PID: 4208)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 6048)
- bomb.exe (PID: 6228)
- bomb.exe (PID: 2416)
- bomb.exe (PID: 2340)
- bomb.exe (PID: 2664)
- bomb.exe (PID: 1512)
- bomb.exe (PID: 2136)
- bomb.exe (PID: 7936)
- bomb.exe (PID: 7416)
- bomb.exe (PID: 5124)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 6944)
- bomb.exe (PID: 4452)
Adds/modifies Windows certificates
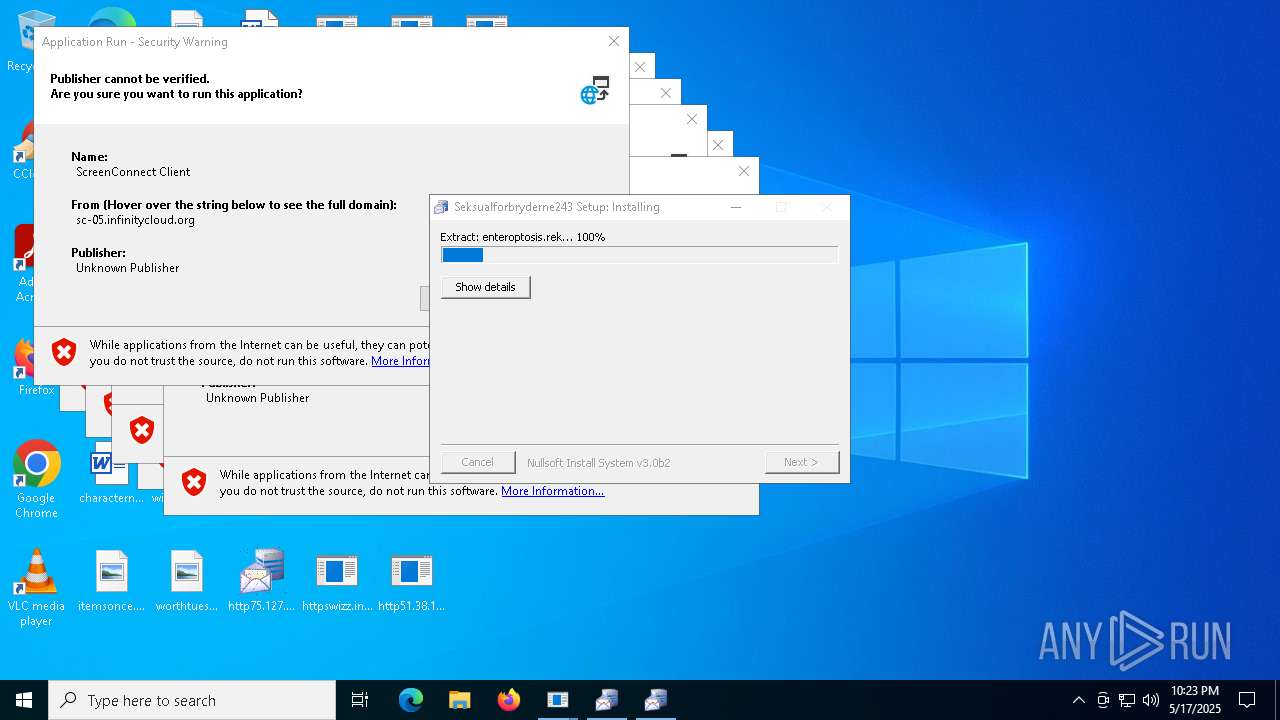
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2100)
Executable content was dropped or overwritten
- bomb.exe (PID: 6028)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2852)
- bridgesurrogatefontsvc.exe (PID: 7196)
- bridgesurrogatefontsvc.exe (PID: 8008)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- http51.38.140.180cbotcbot.exe.exe (PID: 5960)
Reads security settings of Internet Explorer
- dfsvc.exe (PID: 1812)
- bomb.exe (PID: 6028)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2852)
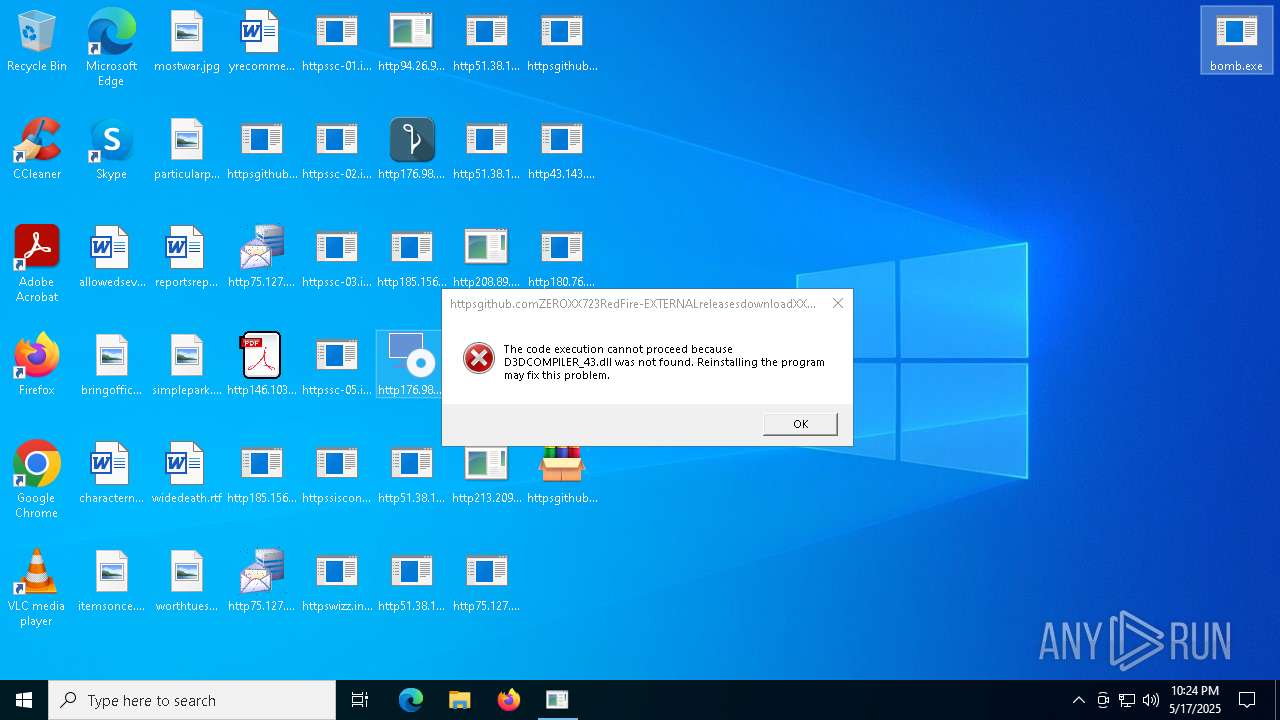
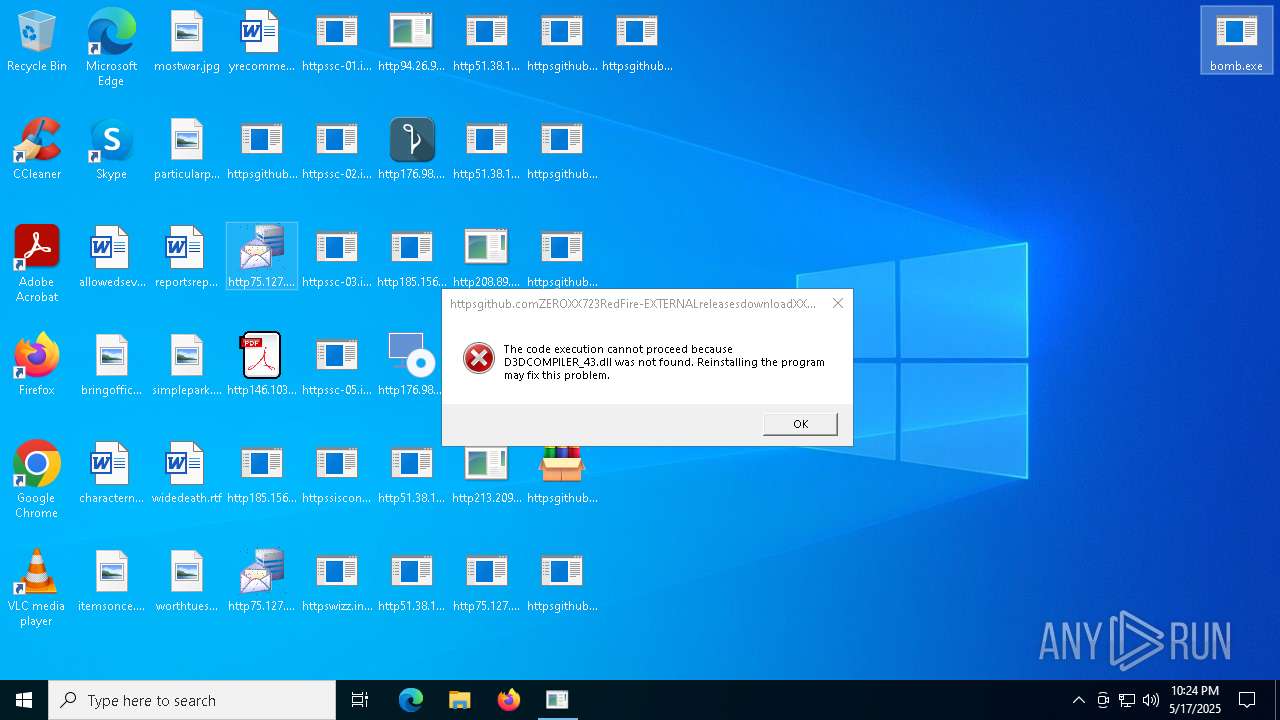
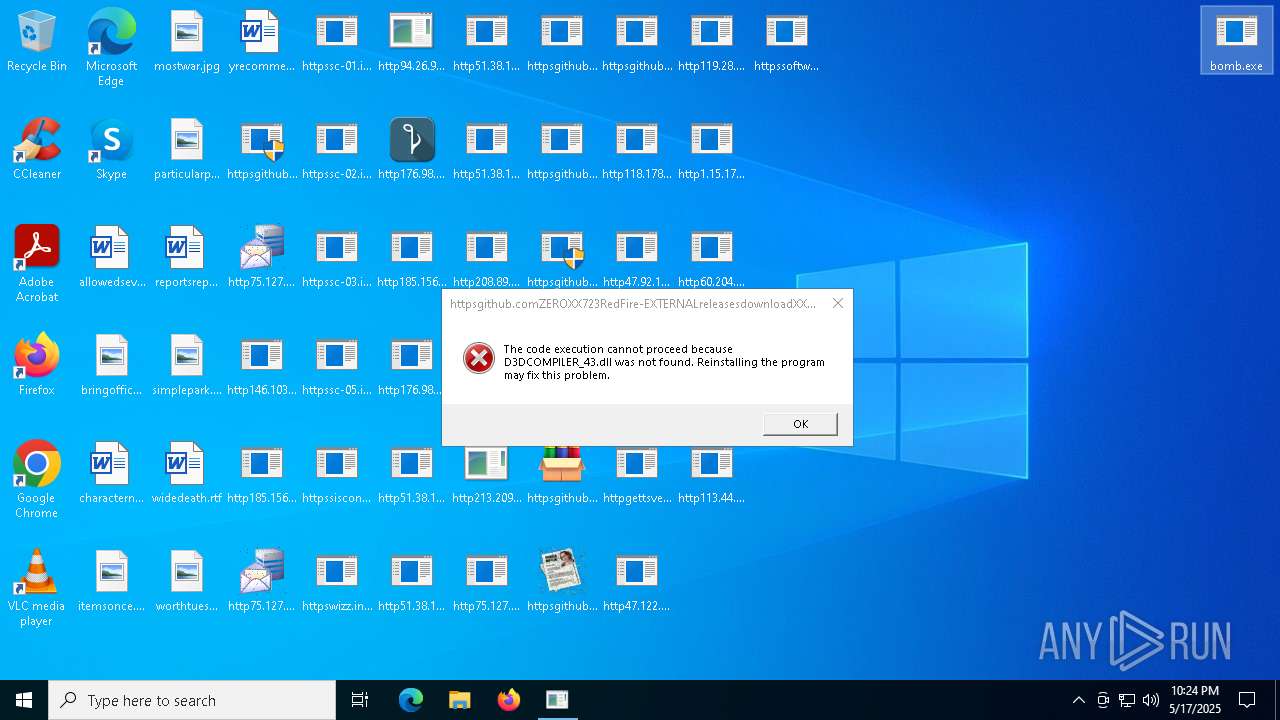
Executes application which crashes
- http146.103.7.34150TiWorker.exe.exe (PID: 1244)
- WinTemp-v4.exe (PID: 7572)
- http208.89.61.141560TiWorker.exe.exe (PID: 8092)
- http213.209.150.18alphamm.exe.exe (PID: 4736)
- http94.26.90.204kjoxca.exe.exe (PID: 8104)
Connects to unusual port
- bomb.exe (PID: 6028)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
- bomb.exe (PID: 6048)
- bomb.exe (PID: 2772)
- bomb.exe (PID: 6228)
Reads the BIOS version
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
Reads Internet Explorer settings
- dfsvc.exe (PID: 1812)
The process checks if it is being run in the virtual environment
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 5072)
Starts a Microsoft application from unusual location
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- httpsgithub.comlegendary99999knjklbnkn-releasesdownloaddfbvsdfbsgfdbinferno.exe.exe (PID: 11880)
- httpsgithub.comlegendary99999vdfsvdsfvsdfvreleasesdownloadfabdvadfvad123123213.exe.exe (PID: 12448)
Process drops legitimate windows executable
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- bomb.exe (PID: 6028)
- bomb.exe (PID: 1512)
- bomb.exe (PID: 7416)
- bomb.exe (PID: 6228)
- bomb.exe (PID: 4208)
- bomb.exe (PID: 6032)
The process creates files with name similar to system file names
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
Malware-specific behavior (creating "System.dll" in Temp)
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
Executing commands from a ".bat" file
- wscript.exe (PID: 1196)
- bridgesurrogatefontsvc.exe (PID: 8008)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 12156)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1196)
- bridgesurrogatefontsvc.exe (PID: 8008)
- bridgesurrogatefontsvc.exe (PID: 7196)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 12156)
Starts application with an unusual extension
- cmd.exe (PID: 4008)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 4008)
Application launched itself
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
- http75.127.7.164Supawn.exe.exe (PID: 7564)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
Checks for external IP
- svchost.exe (PID: 2196)
INFO
Reads the computer name
- bomb.exe (PID: 6028)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2100)
- dfsvc.exe (PID: 1812)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 5072)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 4892)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1628)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6676)
- httpssc-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6592)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6972)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 7476)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2852)
- httpsgithub.compiunildunkos8nomrawrefsheadsmainsgsdg.exe.exe (PID: 7592)
Disables trace logs
- bomb.exe (PID: 6028)
- dfsvc.exe (PID: 1812)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 7476)
Checks supported languages
- bomb.exe (PID: 6028)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2100)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 5072)
- http146.103.7.34150TiWorker.exe.exe (PID: 1244)
- dfsvc.exe (PID: 1812)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1628)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 4892)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6676)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6972)
- httpssc-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6592)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 7808)
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- http208.89.61.141560TiWorker.exe.exe (PID: 8092)
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
- http213.209.150.18alphamm.exe.exe (PID: 4736)
- http94.26.90.204kjoxca.exe.exe (PID: 8104)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 7476)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2852)
- httpsgithub.compiunildunkos8nomrawrefsheadsmainsgsdg.exe.exe (PID: 7592)
Reads the machine GUID from the registry
- bomb.exe (PID: 6028)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2100)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 4892)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1628)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6676)
- dfsvc.exe (PID: 1812)
- httpssc-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6592)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 5072)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 6972)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 7476)
Reads Environment values
- bomb.exe (PID: 6028)
- dfsvc.exe (PID: 1812)
Checks proxy server information
- bomb.exe (PID: 6028)
- dfsvc.exe (PID: 1812)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 7476)
The sample compiled with english language support
- bomb.exe (PID: 6028)
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- bomb.exe (PID: 6032)
- bomb.exe (PID: 1512)
- bomb.exe (PID: 7416)
- bomb.exe (PID: 6228)
- bomb.exe (PID: 4208)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 6048)
Reads the software policy settings
- bomb.exe (PID: 6028)
- dfsvc.exe (PID: 1812)
- http75.127.7.164emmmmmmslay.exe.exe (PID: 7476)
Reads mouse settings
- http146.103.7.34150TiWorker.exe.exe (PID: 1244)
- http208.89.61.141560TiWorker.exe.exe (PID: 8092)
- http213.209.150.18alphamm.exe.exe (PID: 4736)
- http94.26.90.204kjoxca.exe.exe (PID: 8104)
Create files in a temporary directory
- http146.103.7.34150TiWorker.exe.exe (PID: 1244)
- dfsvc.exe (PID: 1812)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
- http208.89.61.141560TiWorker.exe.exe (PID: 8092)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
- http213.209.150.18alphamm.exe.exe (PID: 4736)
- http75.127.7.164Supawn.exe.exe (PID: 7564)
- http94.26.90.204kjoxca.exe.exe (PID: 8104)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 812)
Creates files or folders in the user directory
- dfsvc.exe (PID: 1812)
- WerFault.exe (PID: 7196)
- WerFault.exe (PID: 7612)
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7880)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8024)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 7944)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
- WerFault.exe (PID: 8176)
- WerFault.exe (PID: 968)
- WerFault.exe (PID: 7352)
Process checks computer location settings
- bomb.exe (PID: 6028)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2852)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 1812)
Checks transactions between databases Windows and Oracle
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 7236)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7448)
Drops encrypted VBS script (Microsoft Script Encoder)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2852)
Changes the display of characters in the console
- cmd.exe (PID: 4008)
Manual execution by a user
- bomb.exe (PID: 1512)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 4208)
- bomb.exe (PID: 6032)
- bomb.exe (PID: 2416)
- bomb.exe (PID: 4452)
- bomb.exe (PID: 6228)
- bomb.exe (PID: 7416)
- bomb.exe (PID: 2340)
- bomb.exe (PID: 2664)
- bomb.exe (PID: 6192)
- bomb.exe (PID: 5124)
- bomb.exe (PID: 5968)
- bomb.exe (PID: 6048)
- bomb.exe (PID: 2772)
- bomb.exe (PID: 8052)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 7196)
- bomb.exe (PID: 6944)
- bomb.exe (PID: 7576)
- bomb.exe (PID: 7972)
- bomb.exe (PID: 7936)
- bomb.exe (PID: 7996)
- bomb.exe (PID: 5164)
- bomb.exe (PID: 3180)
- bomb.exe (PID: 6988)
- bomb.exe (PID: 6268)
- bomb.exe (PID: 4688)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 7836)
- bomb.exe (PID: 7256)
- bomb.exe (PID: 8080)
- bomb.exe (PID: 8012)
- bomb.exe (PID: 8200)
- bomb.exe (PID: 8208)
- bomb.exe (PID: 8304)
- bomb.exe (PID: 8232)
- bomb.exe (PID: 8312)
- bomb.exe (PID: 8320)
- bomb.exe (PID: 8352)
- bomb.exe (PID: 8416)
- bomb.exe (PID: 8460)
- bomb.exe (PID: 8424)
- bomb.exe (PID: 8448)
- bomb.exe (PID: 8512)
- bomb.exe (PID: 8564)
- bomb.exe (PID: 8716)
- bomb.exe (PID: 8536)
- bomb.exe (PID: 8592)
- bomb.exe (PID: 8628)
- bomb.exe (PID: 8676)
- bomb.exe (PID: 8652)
- bomb.exe (PID: 8760)
- bomb.exe (PID: 8732)
- bomb.exe (PID: 8804)
- bomb.exe (PID: 8816)
- bomb.exe (PID: 8836)
- bomb.exe (PID: 8952)
- bomb.exe (PID: 8916)
- bomb.exe (PID: 8880)
- bomb.exe (PID: 8996)
- bomb.exe (PID: 8944)
- bomb.exe (PID: 9028)
- bomb.exe (PID: 9076)
- bomb.exe (PID: 9040)
- bomb.exe (PID: 9136)
- bomb.exe (PID: 9144)
- bomb.exe (PID: 9200)
- bomb.exe (PID: 9208)
- bomb.exe (PID: 7964)
- bomb.exe (PID: 7956)
- bomb.exe (PID: 9292)
- bomb.exe (PID: 9300)
- bomb.exe (PID: 9316)
- bomb.exe (PID: 9400)
- bomb.exe (PID: 9480)
- bomb.exe (PID: 9364)
- bomb.exe (PID: 9384)
- bomb.exe (PID: 9496)
- bomb.exe (PID: 9540)
- bomb.exe (PID: 9552)
- bomb.exe (PID: 9572)
- bomb.exe (PID: 9584)
- bomb.exe (PID: 9676)
- bomb.exe (PID: 9664)
- bomb.exe (PID: 9652)
- bomb.exe (PID: 9692)
- bomb.exe (PID: 9776)
- bomb.exe (PID: 9764)
- bomb.exe (PID: 2136)
- bomb.exe (PID: 9840)
- bomb.exe (PID: 9864)
- bomb.exe (PID: 9968)
- bomb.exe (PID: 10068)
- bomb.exe (PID: 9960)
- bomb.exe (PID: 10100)
- bomb.exe (PID: 9980)
- bomb.exe (PID: 10028)
- bomb.exe (PID: 10128)
- bomb.exe (PID: 10164)
- bomb.exe (PID: 10192)
- bomb.exe (PID: 10216)
- bomb.exe (PID: 4008)
- bomb.exe (PID: 7676)
- bomb.exe (PID: 10316)
- bomb.exe (PID: 9908)
- bomb.exe (PID: 10268)
- bomb.exe (PID: 10260)
- bomb.exe (PID: 10348)
- bomb.exe (PID: 10440)
- bomb.exe (PID: 10364)
- bomb.exe (PID: 10400)
- bomb.exe (PID: 10428)
- bomb.exe (PID: 10488)
- bomb.exe (PID: 10532)
- bomb.exe (PID: 10520)
- bomb.exe (PID: 10568)
- bomb.exe (PID: 10592)
- bomb.exe (PID: 10612)
- bomb.exe (PID: 10600)
- bomb.exe (PID: 10724)
- bomb.exe (PID: 10712)
- bomb.exe (PID: 10788)
- bomb.exe (PID: 10820)
- bomb.exe (PID: 10840)
- bomb.exe (PID: 10860)
- bomb.exe (PID: 10888)
- bomb.exe (PID: 10980)
- bomb.exe (PID: 10920)
- bomb.exe (PID: 11016)
- bomb.exe (PID: 11008)
- bomb.exe (PID: 11060)
- bomb.exe (PID: 11116)
- bomb.exe (PID: 11072)
- bomb.exe (PID: 10700)
- bomb.exe (PID: 11144)
- bomb.exe (PID: 11176)
- bomb.exe (PID: 11204)
- bomb.exe (PID: 11228)
- bomb.exe (PID: 11260)
- bomb.exe (PID: 7884)
- bomb.exe (PID: 7816)
- bomb.exe (PID: 8412)
- bomb.exe (PID: 684)
- bomb.exe (PID: 8228)
- bomb.exe (PID: 11276)
- bomb.exe (PID: 11284)
- bomb.exe (PID: 11356)
- bomb.exe (PID: 11368)
- bomb.exe (PID: 11384)
- bomb.exe (PID: 11408)
- bomb.exe (PID: 11452)
- bomb.exe (PID: 11528)
- bomb.exe (PID: 11492)
- bomb.exe (PID: 11556)
- bomb.exe (PID: 11584)
- bomb.exe (PID: 11608)
- bomb.exe (PID: 11668)
- bomb.exe (PID: 11724)
- bomb.exe (PID: 11656)
- bomb.exe (PID: 11732)
- bomb.exe (PID: 11780)
- bomb.exe (PID: 11816)
- bomb.exe (PID: 12060)
- bomb.exe (PID: 12096)
- bomb.exe (PID: 12140)
- bomb.exe (PID: 12048)
- bomb.exe (PID: 12116)
- bomb.exe (PID: 12188)
- bomb.exe (PID: 9880)
- bomb.exe (PID: 9784)
- bomb.exe (PID: 12656)
- bomb.exe (PID: 12852)
- bomb.exe (PID: 14040)
- bomb.exe (PID: 15748)
- bomb.exe (PID: 15640)
- bomb.exe (PID: 15776)
- bomb.exe (PID: 15784)
- bomb.exe (PID: 15816)
- bomb.exe (PID: 15848)
- bomb.exe (PID: 16240)
- bomb.exe (PID: 16292)
- bomb.exe (PID: 16308)
- bomb.exe (PID: 16424)
Application based on Golang
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
Detects GO elliptic curve encryption (YARA)
- http176.98.185.87Quodlibet.exe.exe (PID: 7668)
UPX packer has been detected
- http51.38.140.180cbotcbot.exe.exe (PID: 7856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2057:01:07 19:44:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9216 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x43be |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
394
Monitored processes
257
Malicious processes
21
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | C:\WINDOWS\system32\cmd.exe /c ""C:\ChainProviderRefbrokermonitor\2yuLpzrRfY1fgKsLGMv7TtRDuZTFq.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 812 | "C:\Users\admin\Desktop\http75.127.7.164Nationalbankdirektrernes.exe.exe" | C:\Users\admin\Desktop\http75.127.7.164Nationalbankdirektrernes.exe.exe | bomb.exe | ||||||||||||
User: admin Company: R.R. Donnelley & Sons Company Integrity Level: MEDIUM Description: ACT Manufacturing Inc. Exit code: 0 Version: 3.0.0.0 Modules
| |||||||||||||||
| 968 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4736 -s 692 | C:\Windows\SysWOW64\WerFault.exe | — | http213.209.150.18alphamm.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | http176.98.185.87widsmob_denoise_win.exe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Users\admin\Desktop\http146.103.7.34150TiWorker.exe.exe" | C:\Windows\SysWOW64\svchost.exe | — | http146.103.7.34150TiWorker.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1196 | "C:\WINDOWS\System32\WScript.exe" "C:\ChainProviderRefbrokermonitor\GJRM7aIDnBk9.vbe" | C:\Windows\SysWOW64\wscript.exe | — | httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1244 | "C:\Users\admin\Desktop\http146.103.7.34150TiWorker.exe.exe" | C:\Users\admin\Desktop\http146.103.7.34150TiWorker.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 1628 | "C:\Users\admin\Desktop\httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe" | C:\Users\admin\Desktop\httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
117 856
Read events
116 842
Write events
1 005
Delete events
9
Modification events
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6028) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
63
Suspicious files
53
Text files
42
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6028 | bomb.exe | C:\Users\admin\Desktop\httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:73C786699F0E504BBABBE8D1B16CA207 | SHA256:BC9DA6A010632367BDFB471B93D0FC82E1BBE8572405E3F028438A88A77C3D37 | |||
| 1812 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\05Z8N7MP.2QH\KOVTQRCT.2Z5.application | xml | |
MD5:26817F400D192B9F4303FC5C4383C03E | SHA256:69E36FE8A71534FC3A278BB2E2964D2126FEE8014CB2FA73874A72492CD4BE06 | |||
| 1812 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\7K8W97QM.BLM\W4KK3DTG.P48.application | xml | |
MD5:3B408C34941E1A440C041B537DC672BC | SHA256:AE8FA5AE3F0B462F6391B64F521930B71108F16BCD3583DAEE555BF0D002D42A | |||
| 1812 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\JA7GA7AY.70X\RMBTLW8K.T70.application | xml | |
MD5:3B408C34941E1A440C041B537DC672BC | SHA256:AE8FA5AE3F0B462F6391B64F521930B71108F16BCD3583DAEE555BF0D002D42A | |||
| 1812 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\A2BQTGTK.1R0\KX8CNA38.QKW.application | xml | |
MD5:3B408C34941E1A440C041B537DC672BC | SHA256:AE8FA5AE3F0B462F6391B64F521930B71108F16BCD3583DAEE555BF0D002D42A | |||
| 6028 | bomb.exe | C:\Users\admin\Desktop\http185.156.72.2files6723359323FxefytI.exe.exe | executable | |
MD5:7EF7FCFDF9938FAFA37BABC36601E7DD | SHA256:40163F7C5341BD1CB29B47552827544D75B8D9EFEAD359B292B281EAD445A3A1 | |||
| 6028 | bomb.exe | C:\Users\admin\Desktop\httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:90BAE9193A83D5CF1F509ADA3CCB8608 | SHA256:67B5F6F0A1C82B52AB276D5E45E6CC73F100D2B4D1E1EB18E01E1CA47495B8A2 | |||
| 6028 | bomb.exe | C:\Users\admin\Desktop\httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:5A60E41DFB24D6EC1E40E087D1E0CFAC | SHA256:F70AEC862172714D498A172C5FAC27CCED8BEAEE5A2629C60CCA3AADF6301F86 | |||
| 6028 | bomb.exe | C:\Users\admin\Desktop\http185.156.72.2files6003232782oxDU0MW.exe.exe | executable | |
MD5:750999A63402695E1972E5FF52F68DFE | SHA256:8CC12056BF3A841E1BD61916033530AFAD5D3ABAB5512402121D24159423B67C | |||
| 6028 | bomb.exe | C:\Users\admin\Desktop\httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:07A97A749A4818950E08989ECB4719DF | SHA256:E0A8383A4C0BEB02F1004468B777A85720343BF25E09F50D23975BB91FFF4448 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
949
TCP/UDP connections
9 560
DNS requests
719
Threats
8 192
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1812 | dfsvc.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6028 | bomb.exe | GET | 200 | 176.98.185.87:80 | http://176.98.185.87/Quodlibet.exe | unknown | — | — | unknown |
1812 | dfsvc.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAuTYAUbzPZmQpmJmNW6l84%3D | unknown | — | — | whitelisted |
6028 | bomb.exe | GET | 200 | 176.98.185.87:80 | http://176.98.185.87/widsmob_denoise_win.exe | unknown | — | — | unknown |
6028 | bomb.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/raw_cbot_debug.exe | unknown | — | — | unknown |
6028 | bomb.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot.exe | unknown | — | — | unknown |
6028 | bomb.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot_debug.exe | unknown | — | — | unknown |
6028 | bomb.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/raw_cbot.exe | unknown | — | — | unknown |
7384 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6028 | bomb.exe | GET | 200 | 75.127.7.164:80 | http://75.127.7.164/Supawn.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 95.101.34.33:80 | crl.microsoft.com | Akamai International B.V. | IT | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
maper.info |
| malicious |
urlhaus.abuse.ch |
| whitelisted |
gettsveriff.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6028 | bomb.exe | Potential Corporate Privacy Violation | ET INFO IP Logger Redirect Domain in SNI |
6028 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6028 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6028 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6028 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6028 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6028 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6028 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6028 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6028 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |