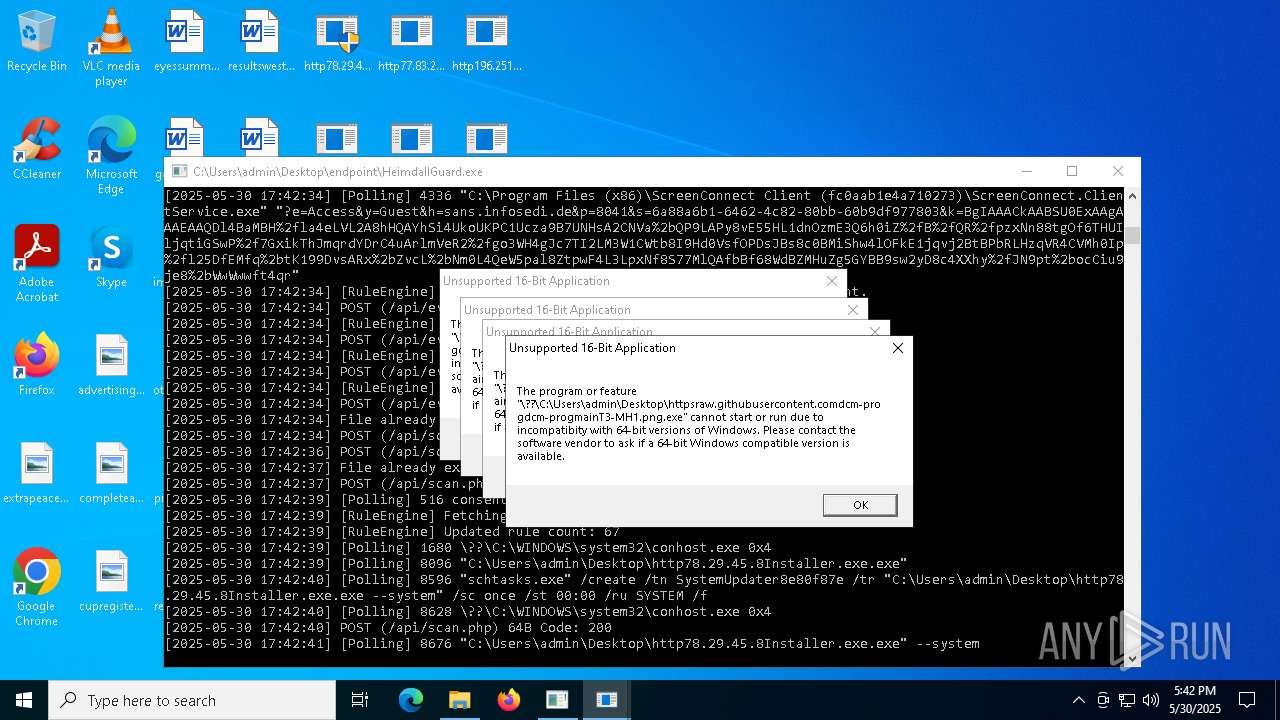
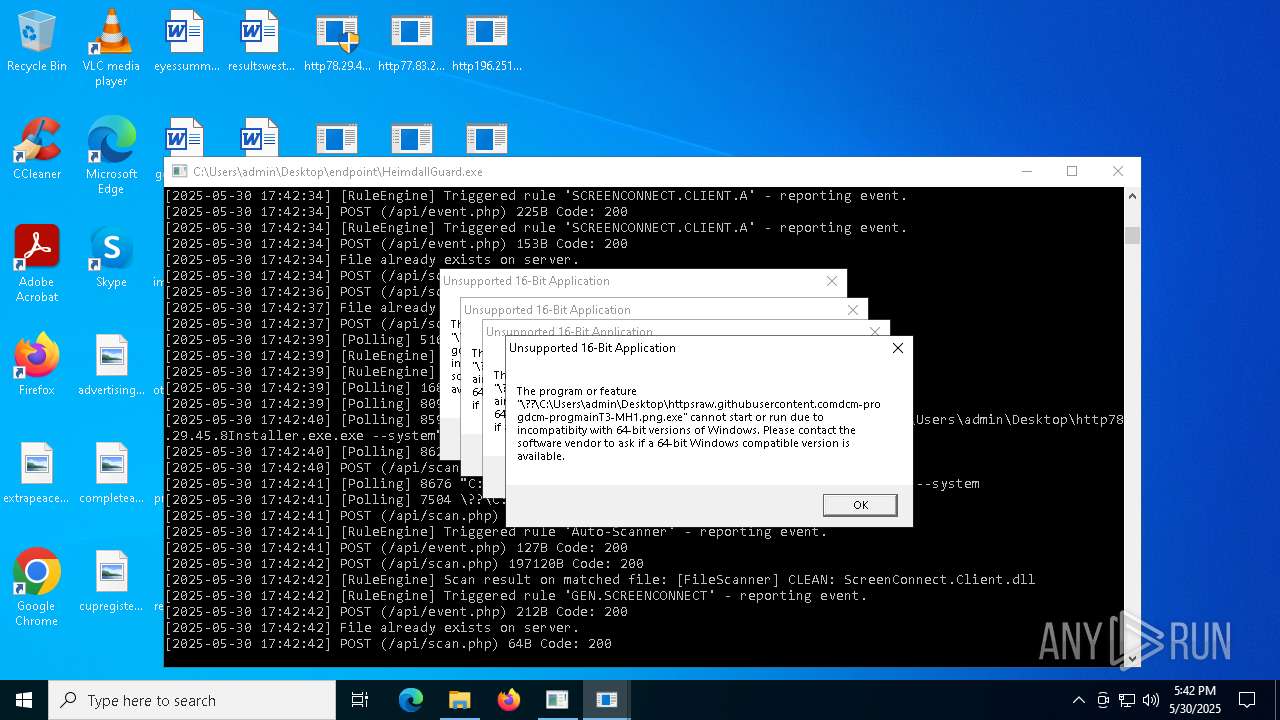
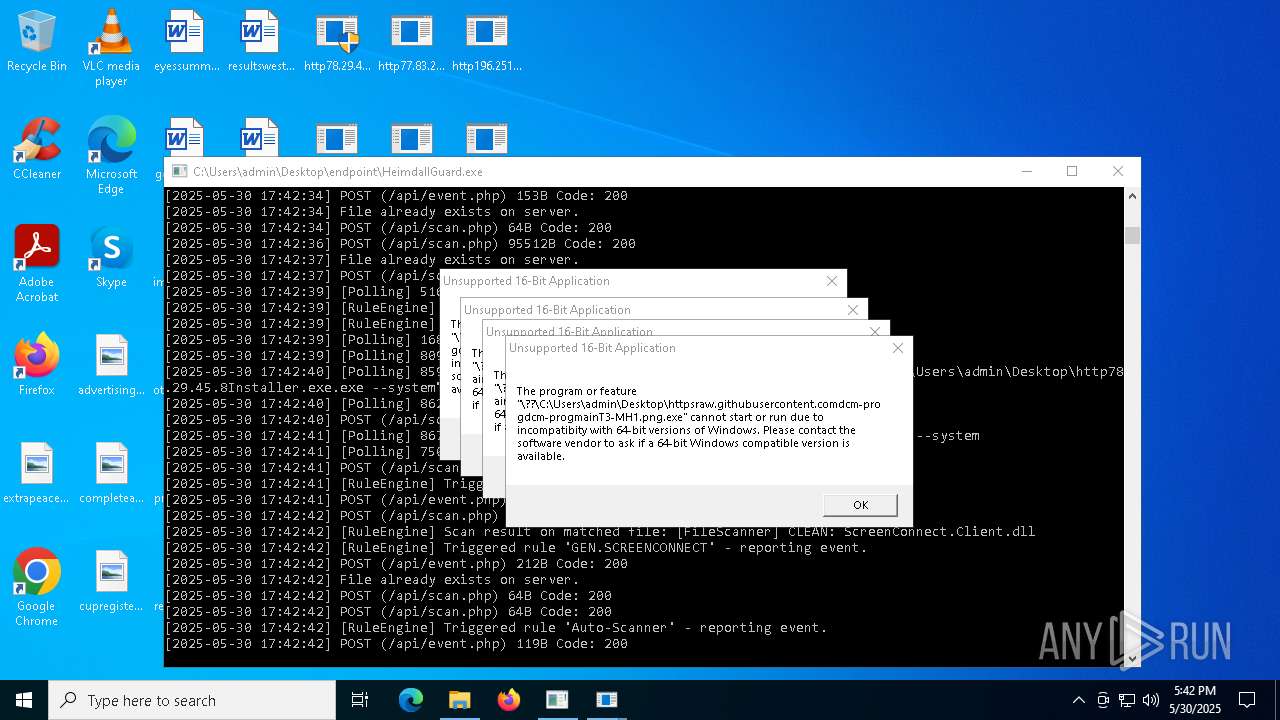
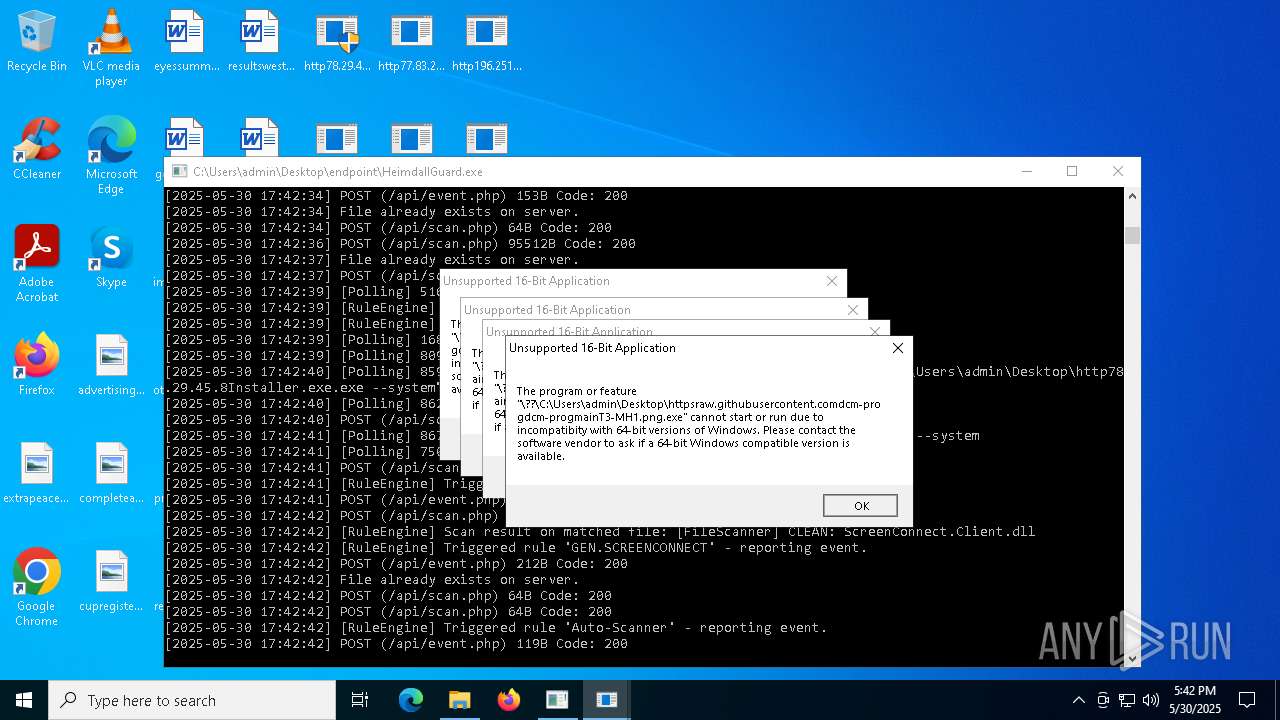
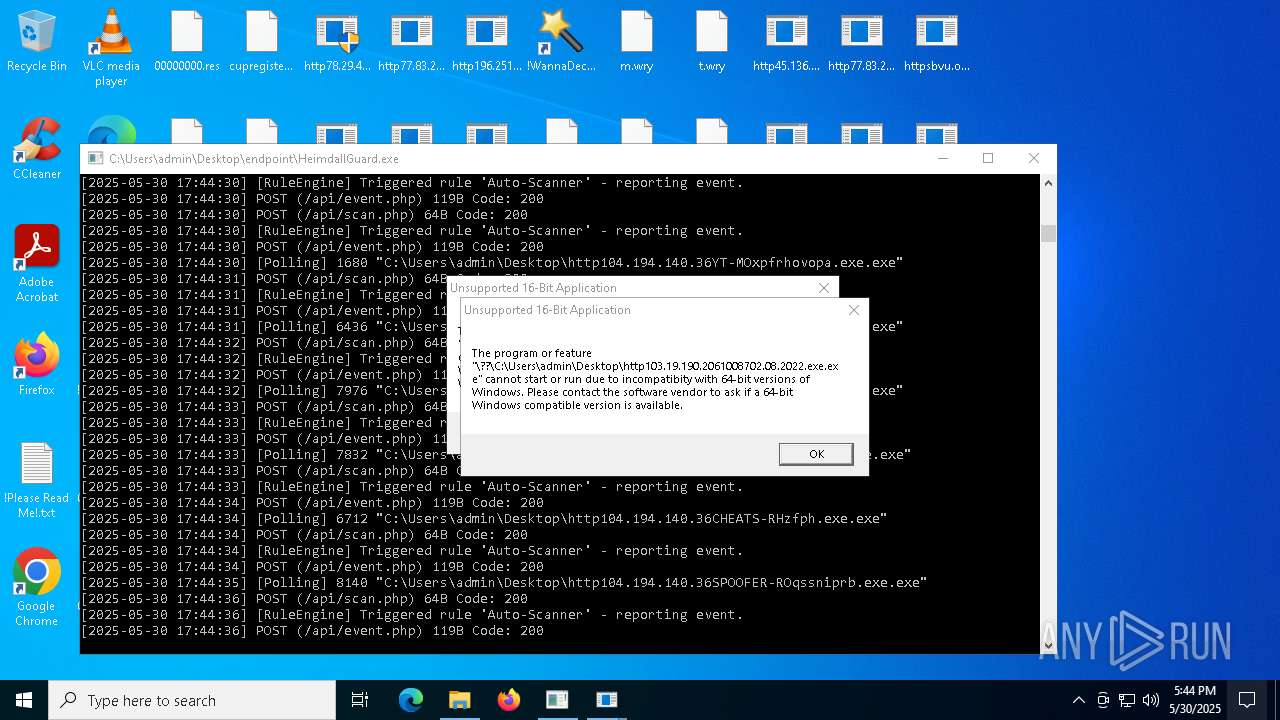
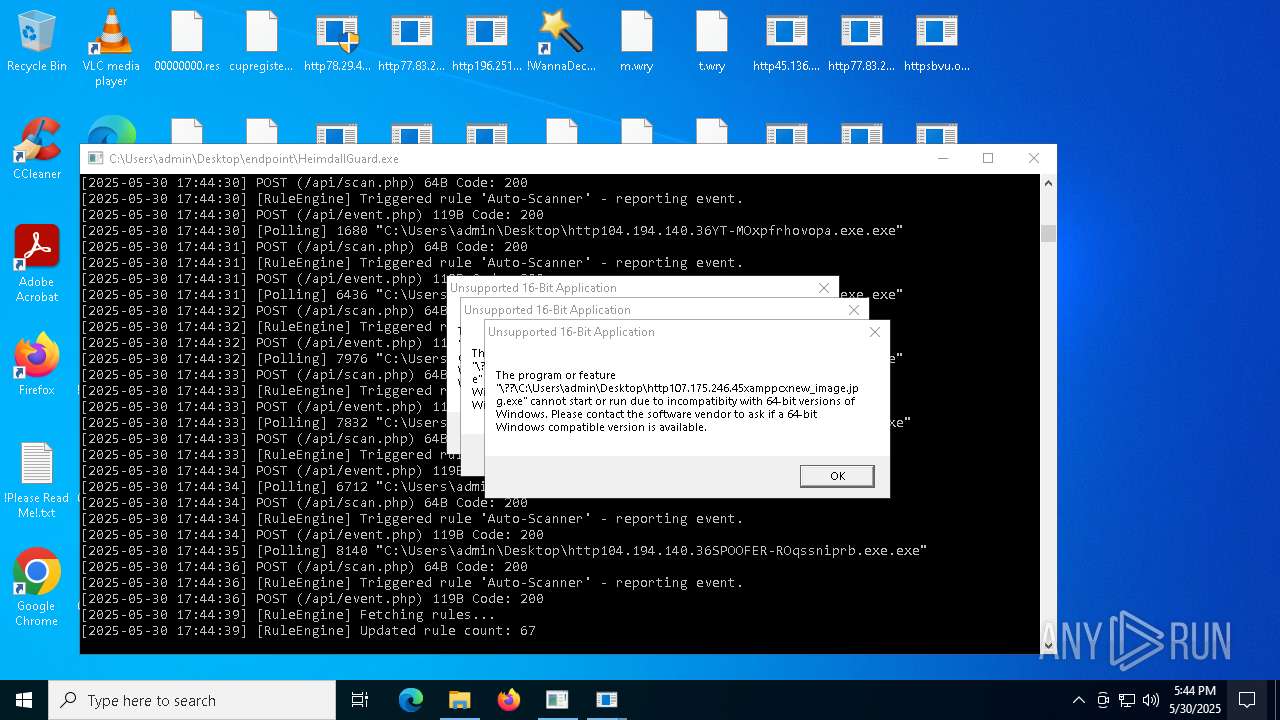
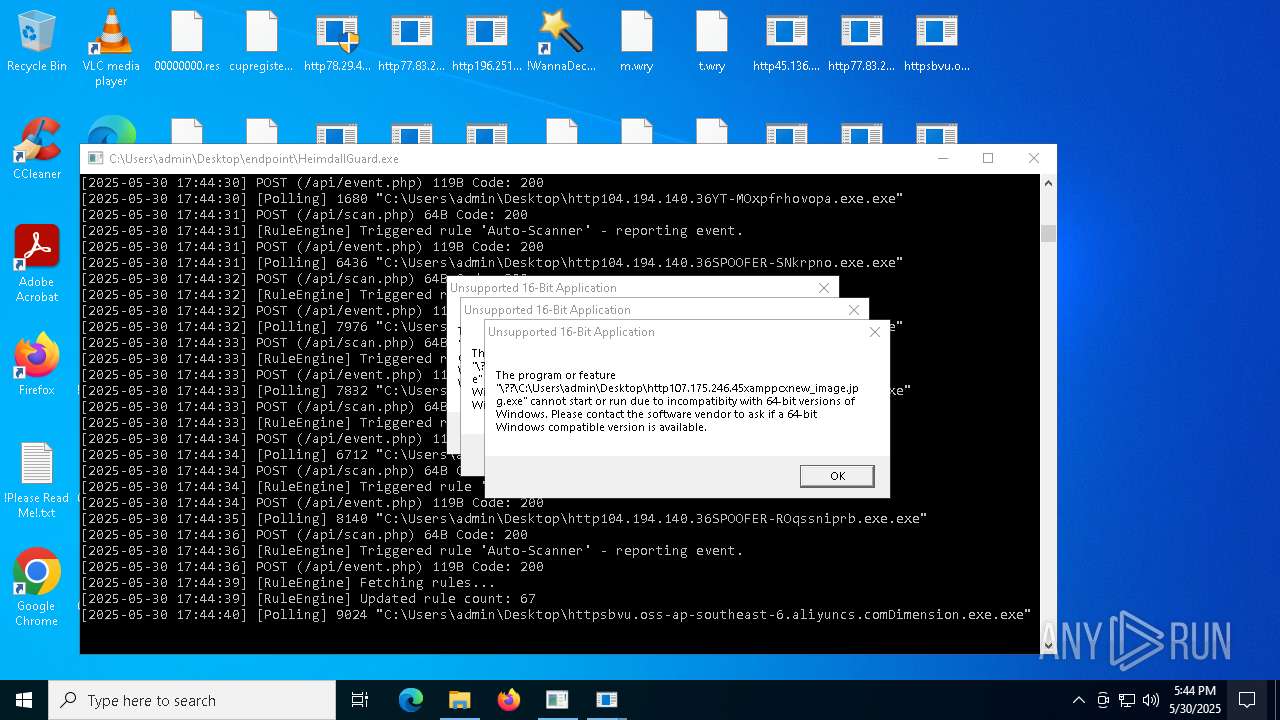
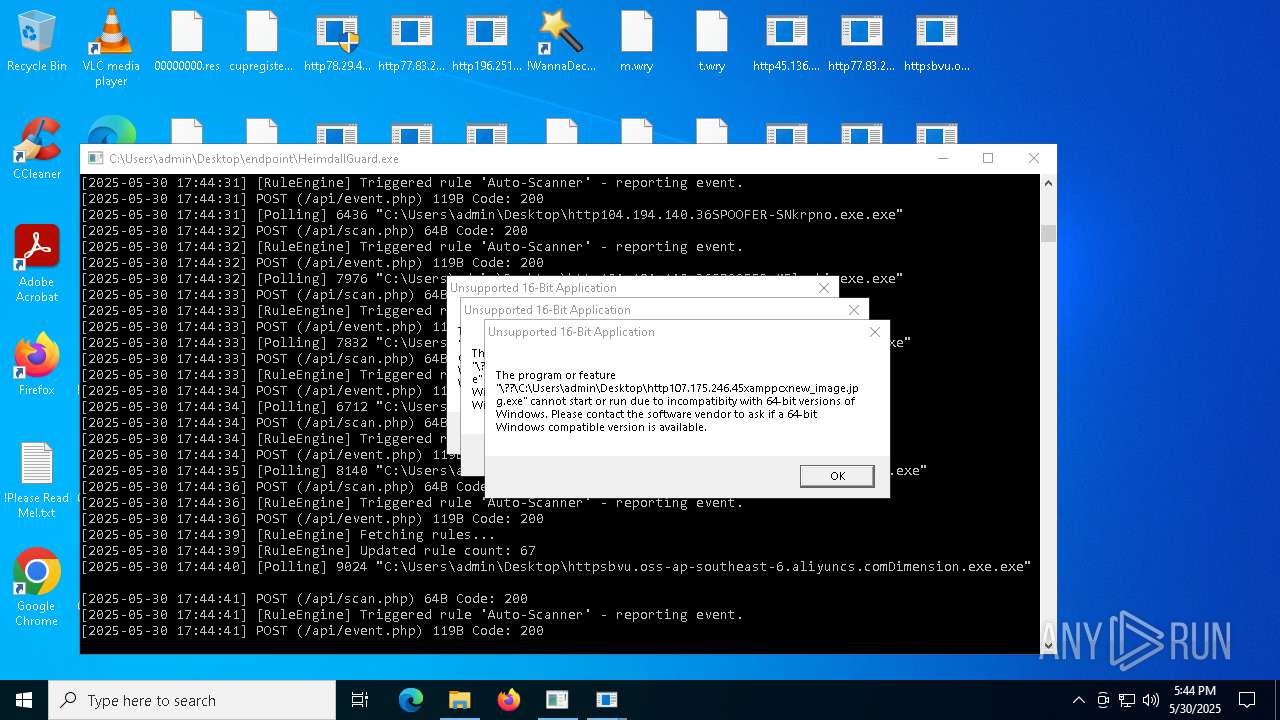
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/cb016c3d-4a5f-4cdd-aac1-edacc22eeb54 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 30, 2025, 17:40:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0E2AD53C884E25F969B3A575F4BB90BB |
| SHA1: | 81E774FE109DDC9185AD3FB68995A069CE9045E0 |
| SHA256: | 990D1FF1AB883A9BACBBB6ABCF975139D9AB359B74FFBA16F1FA7A66A30E935D |
| SSDEEP: | 192:OJa0tZMoQszhl4AKd+QHzdPbwPz1OLU87glpp/bI6J4YlTtoIw:OLJQjd+qzZ0OLU870NJDoI |
MALICIOUS
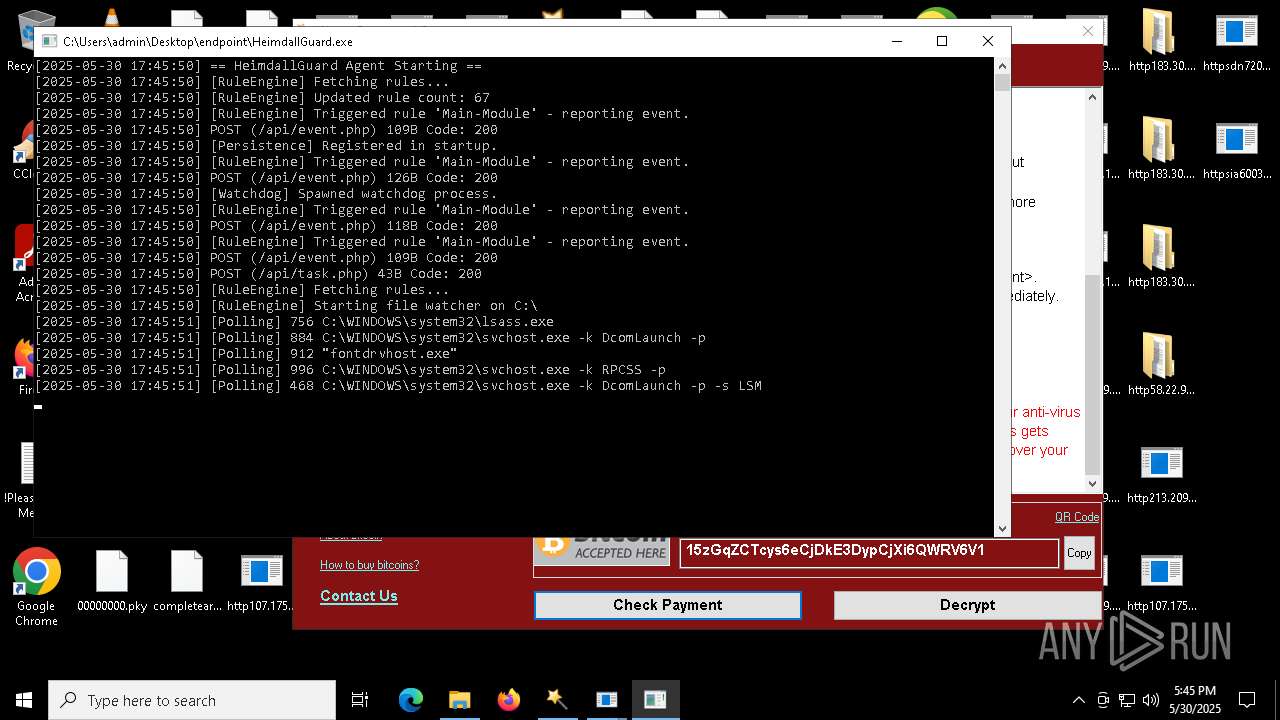
HAUSBOMBER has been detected (YARA)
- bomb.exe (PID: 4020)
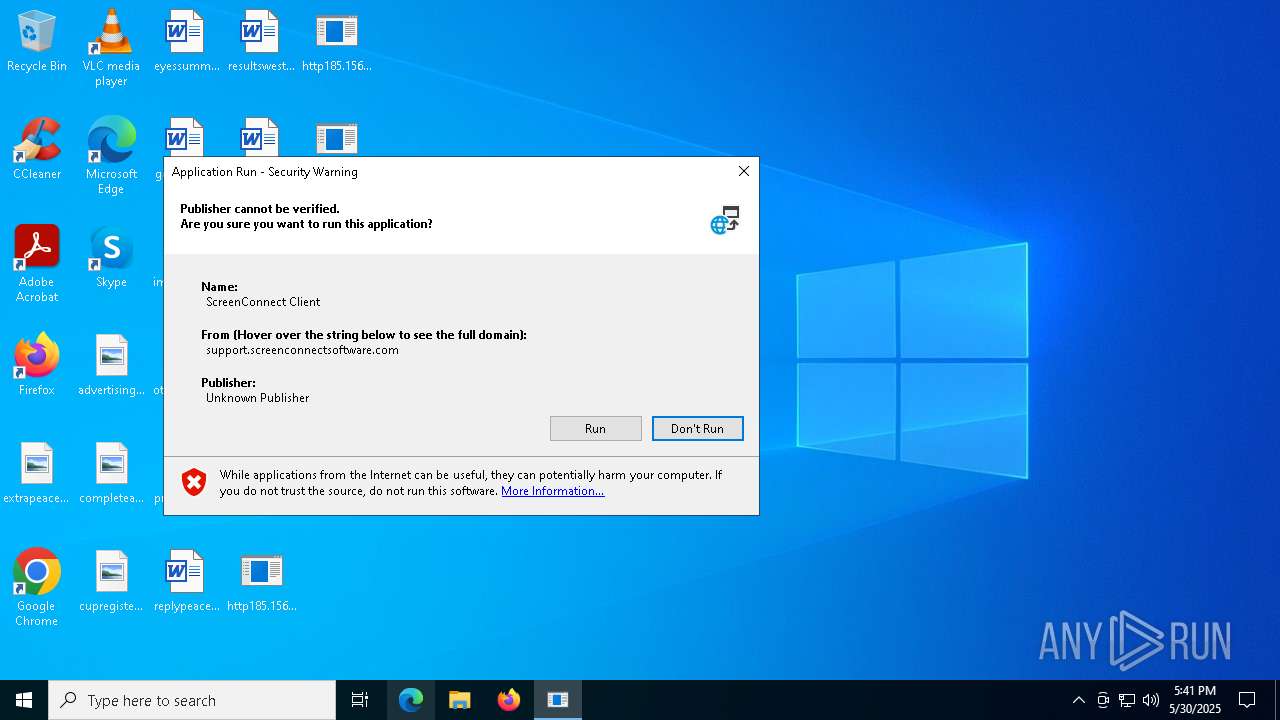
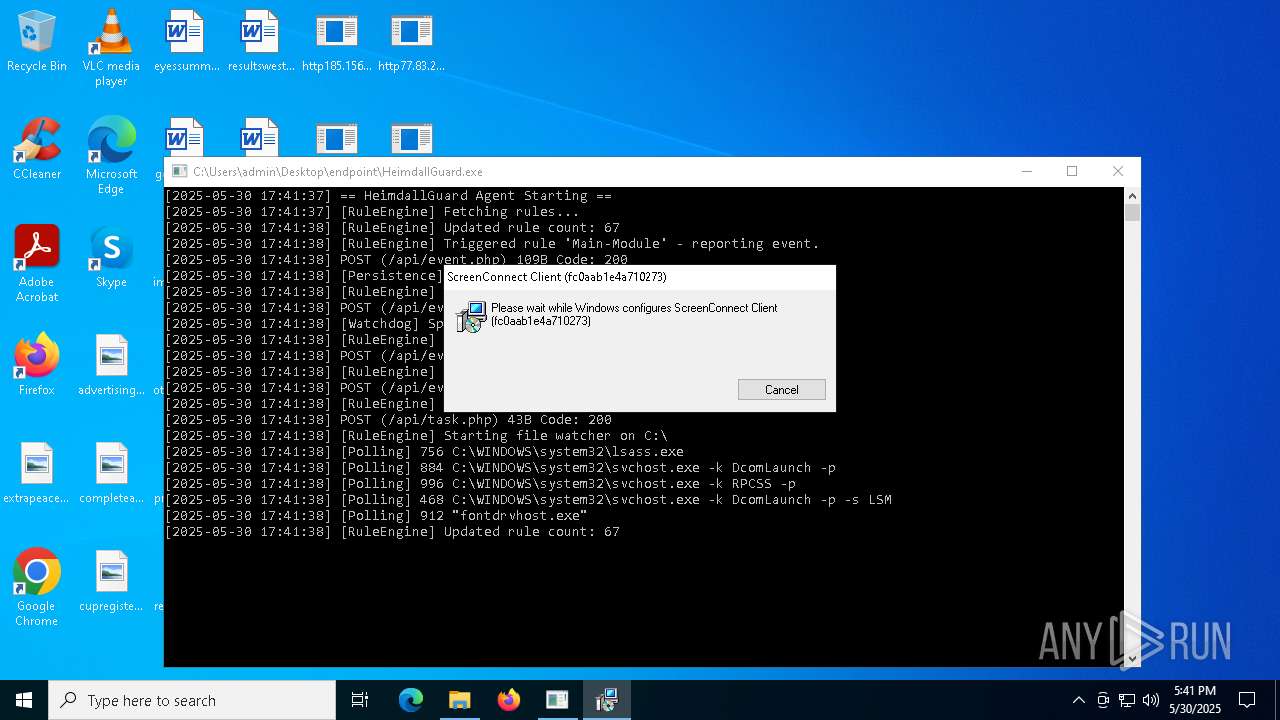
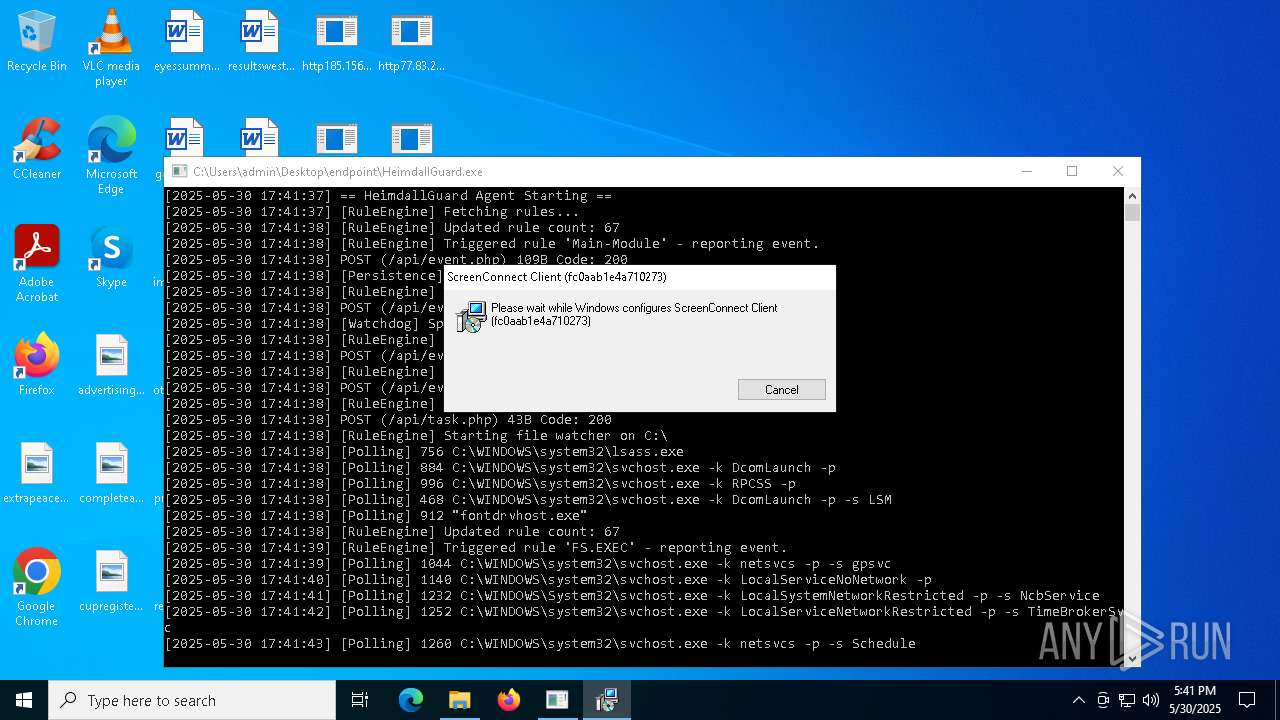
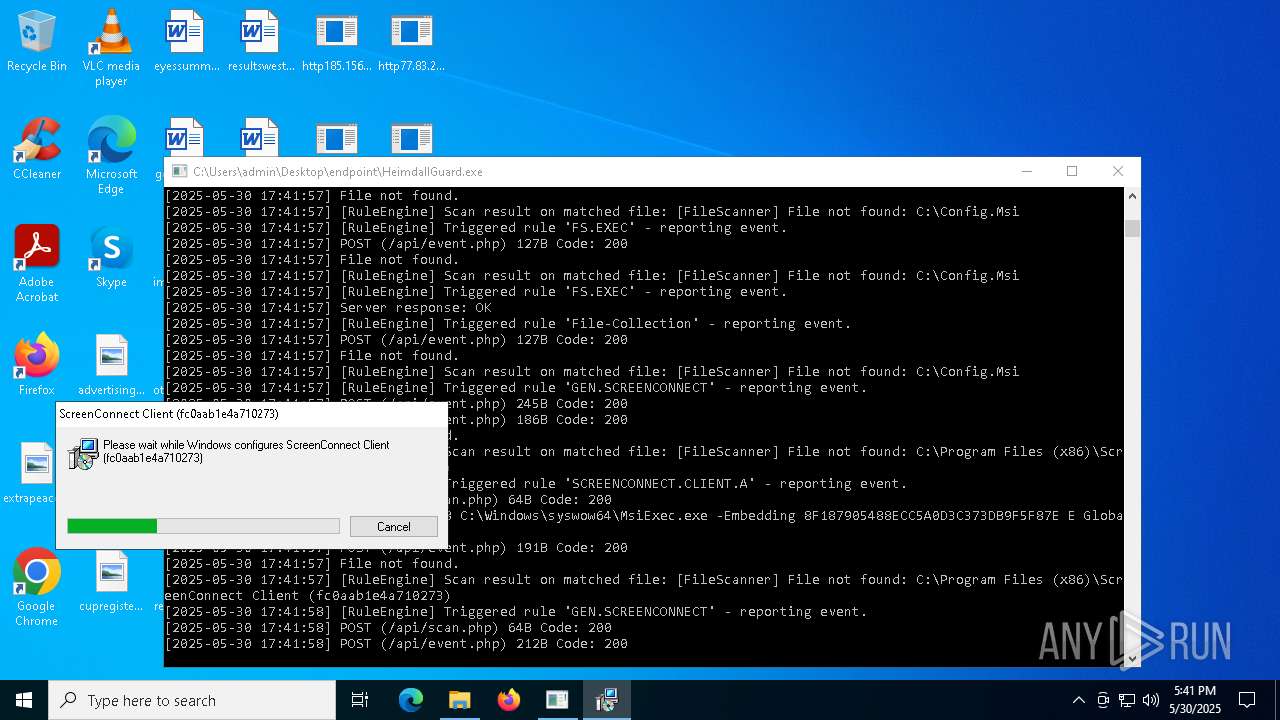
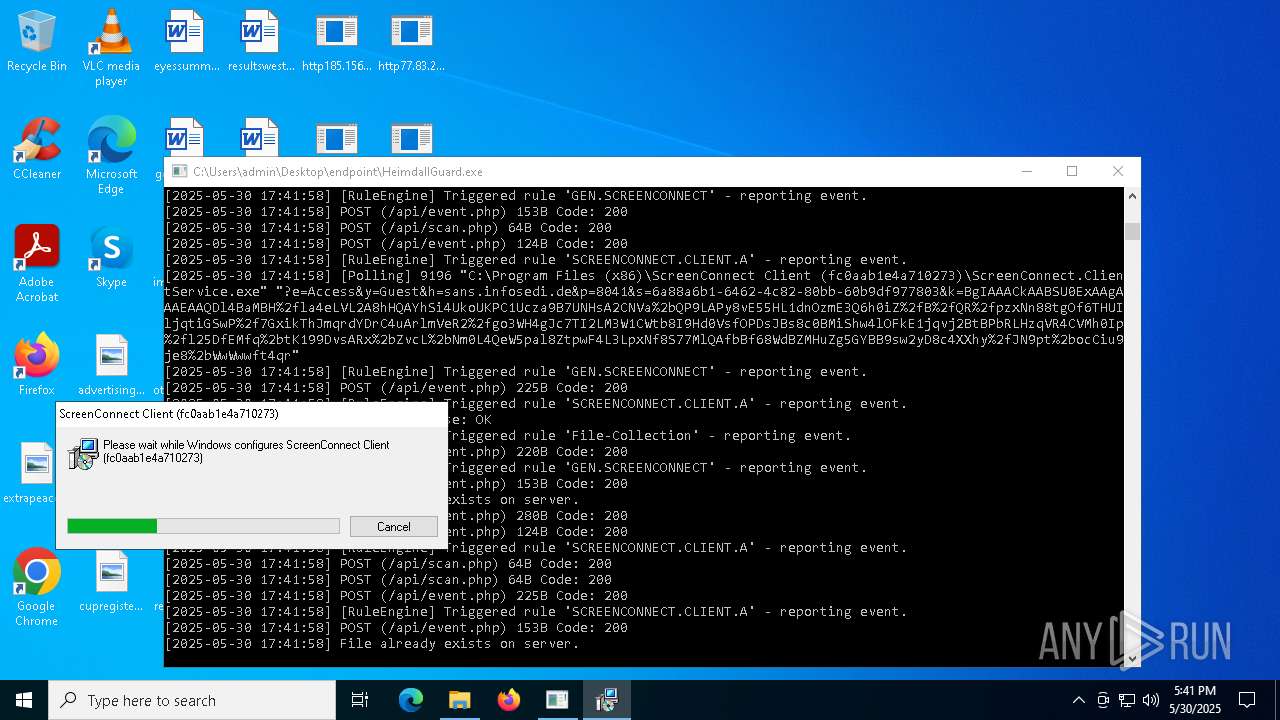
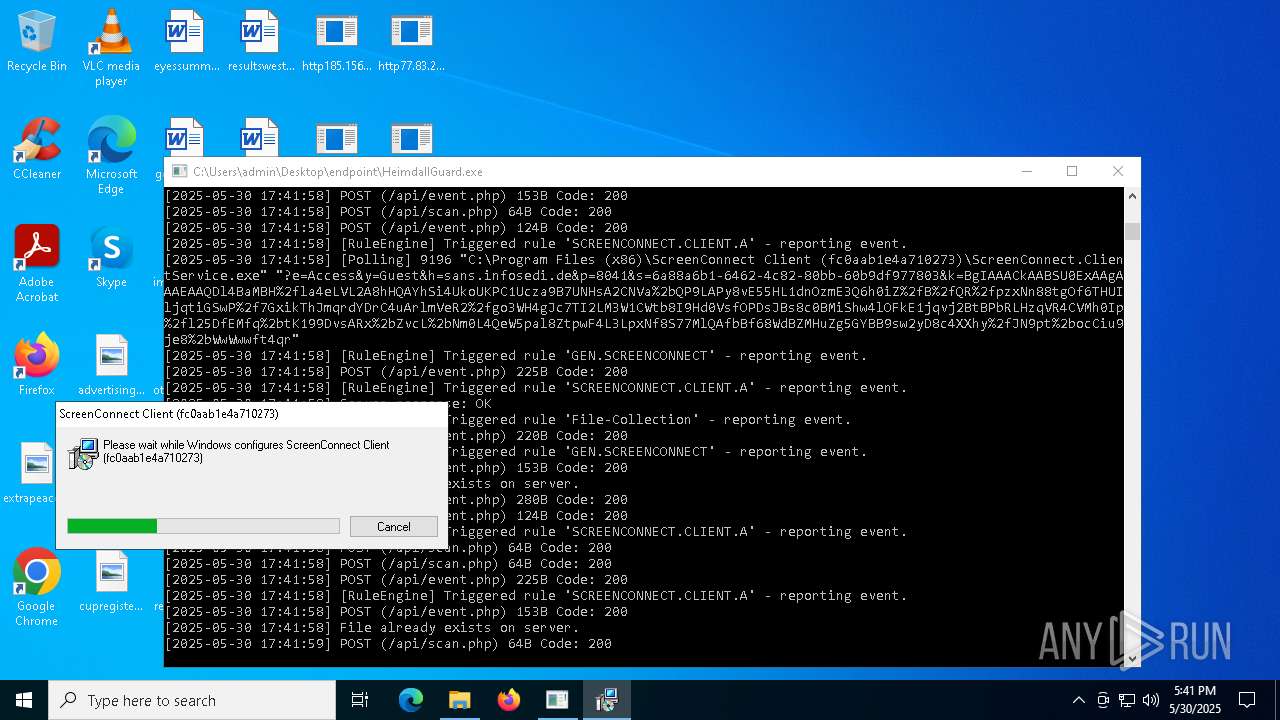
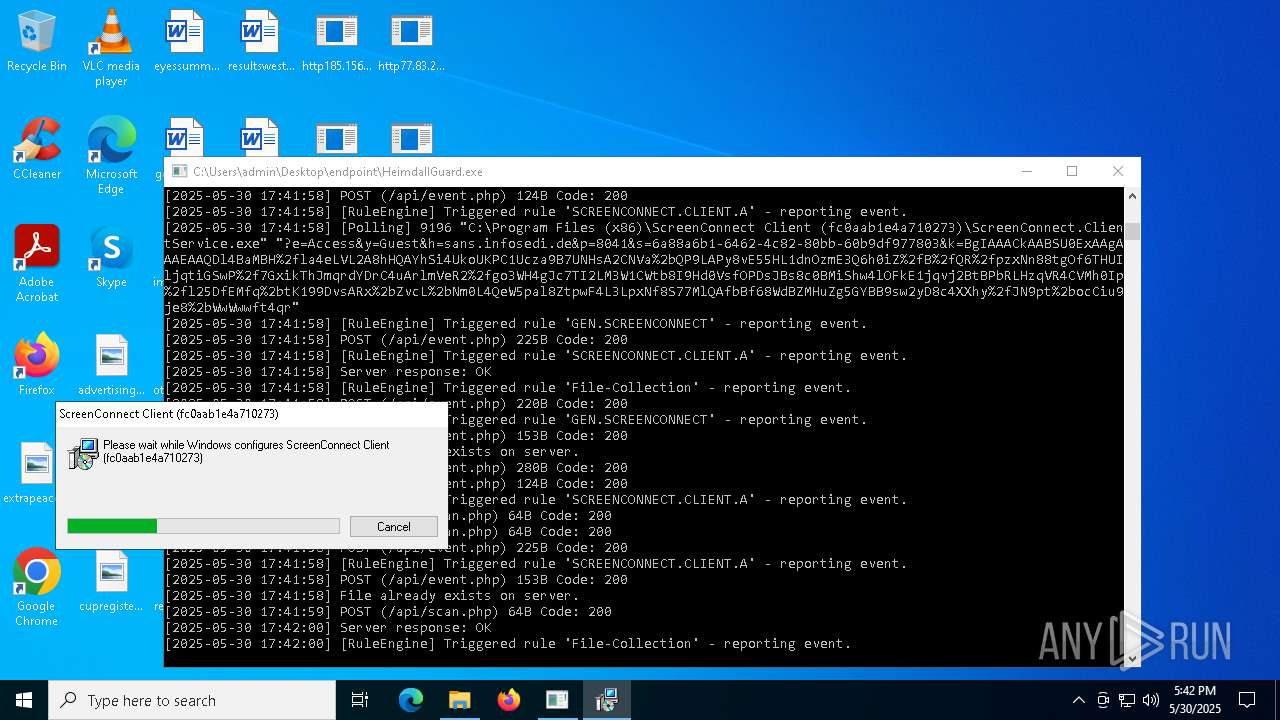
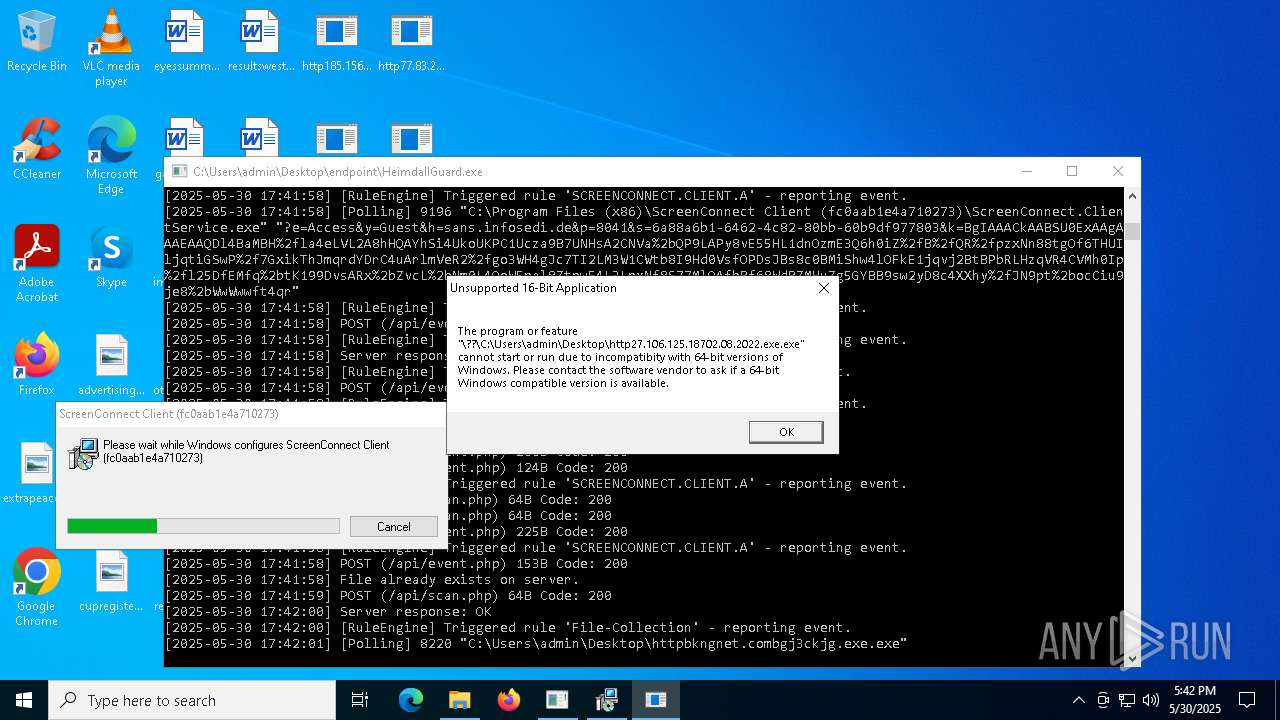
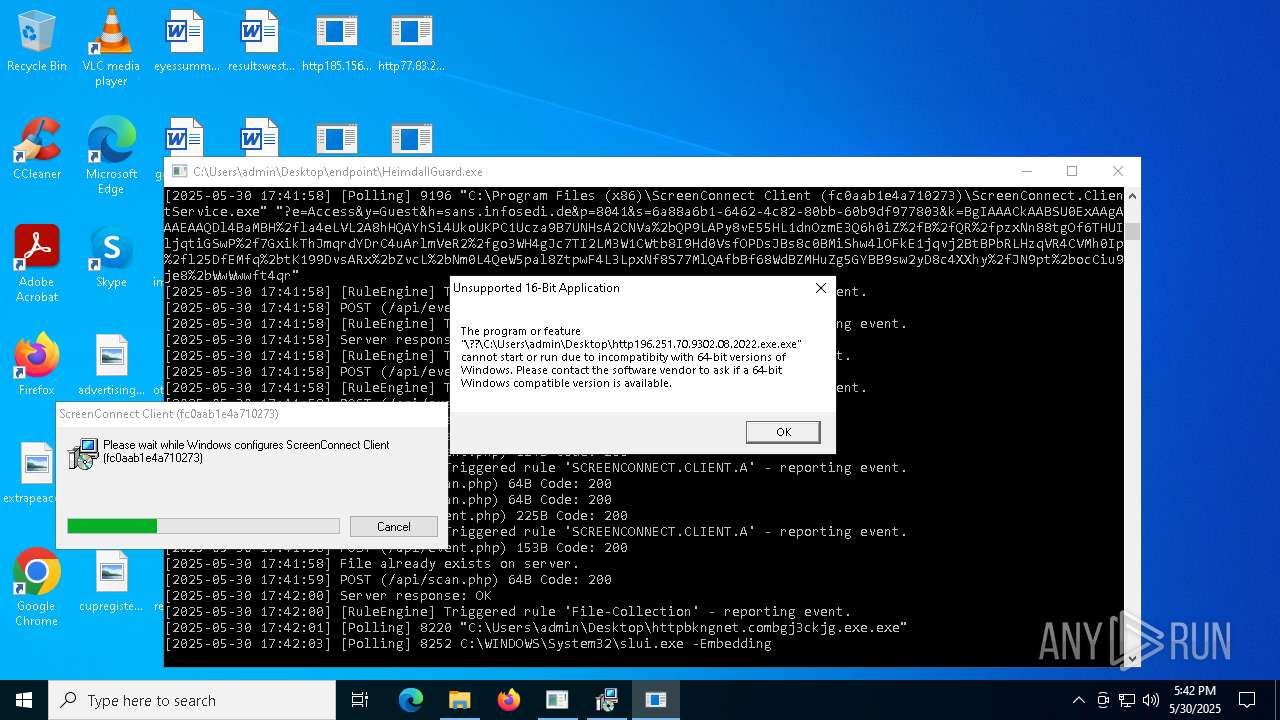
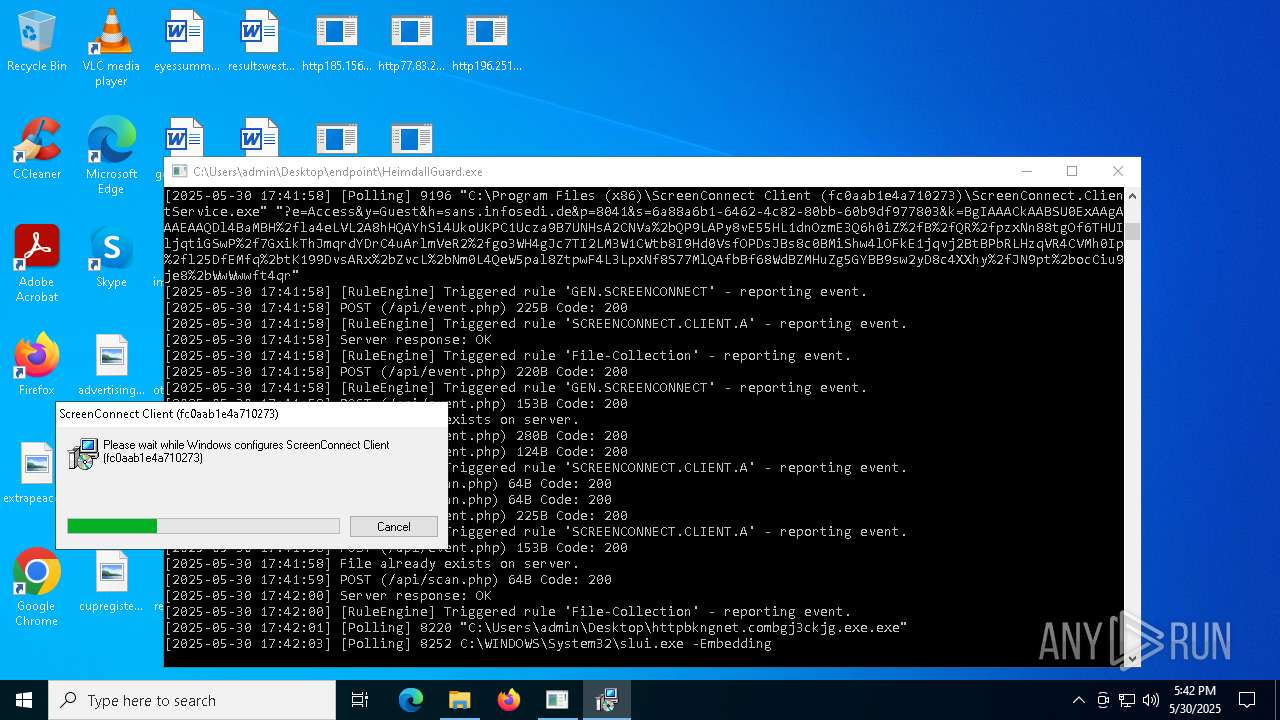
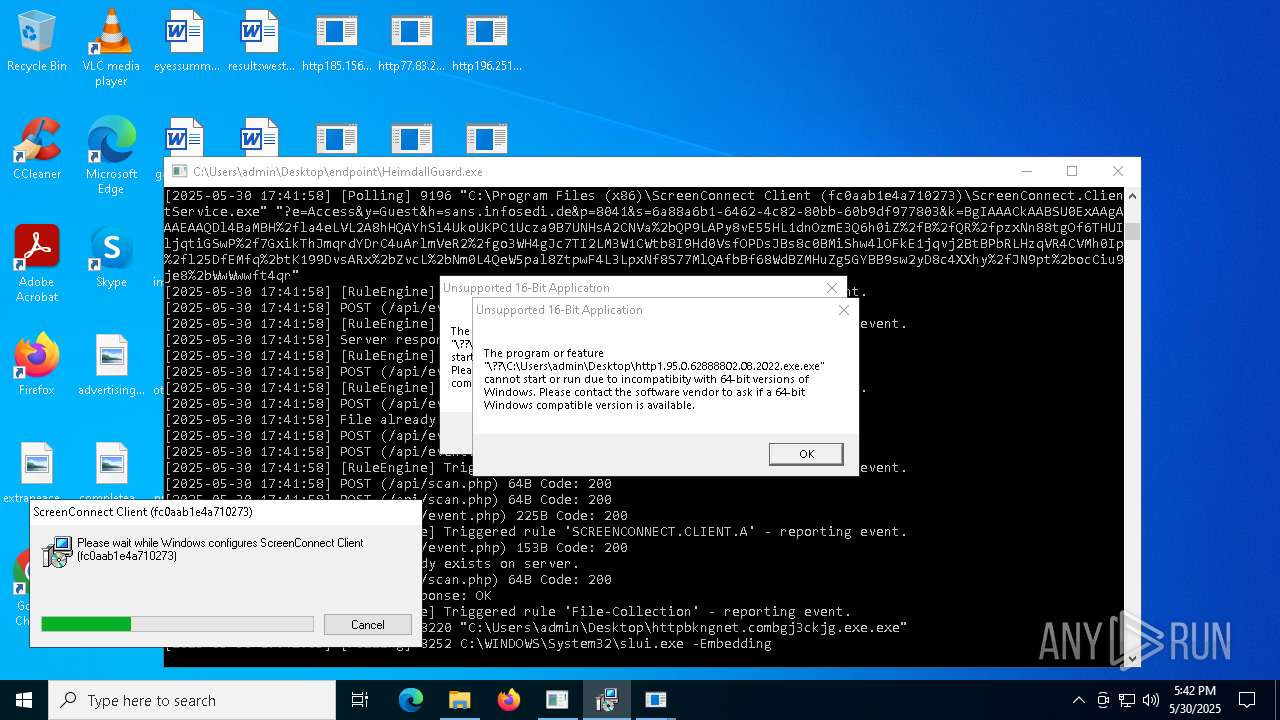
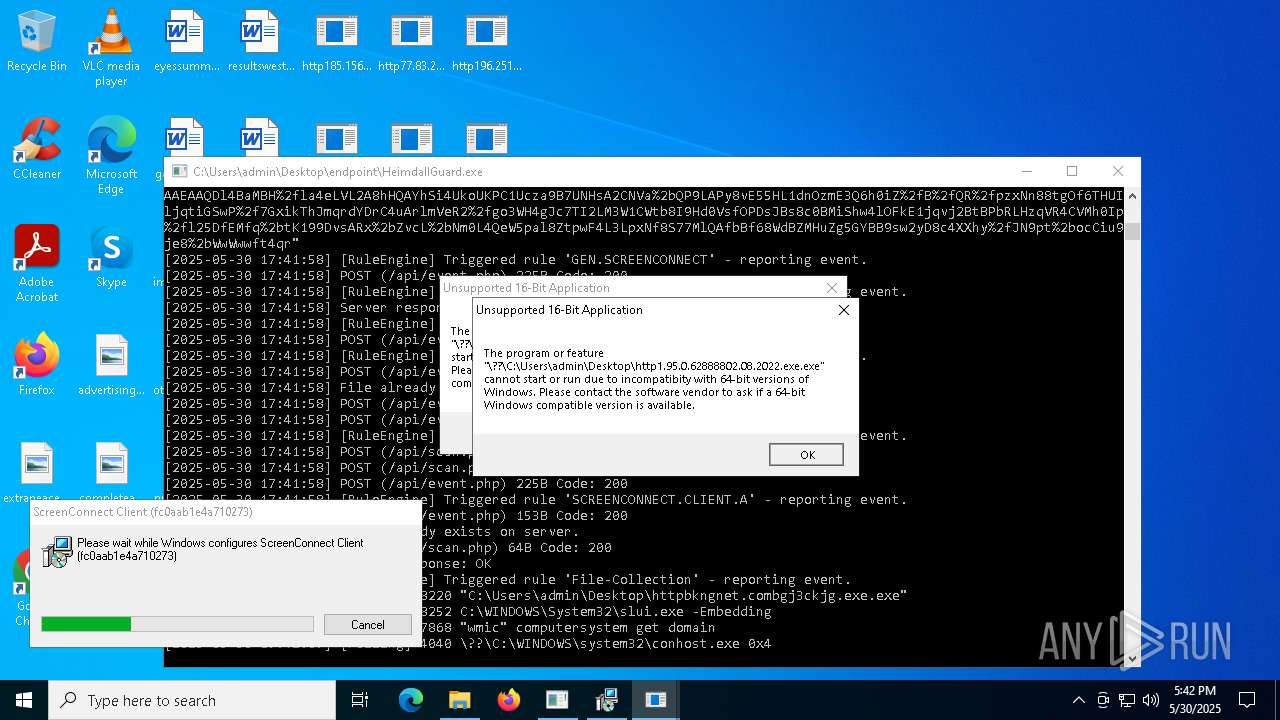
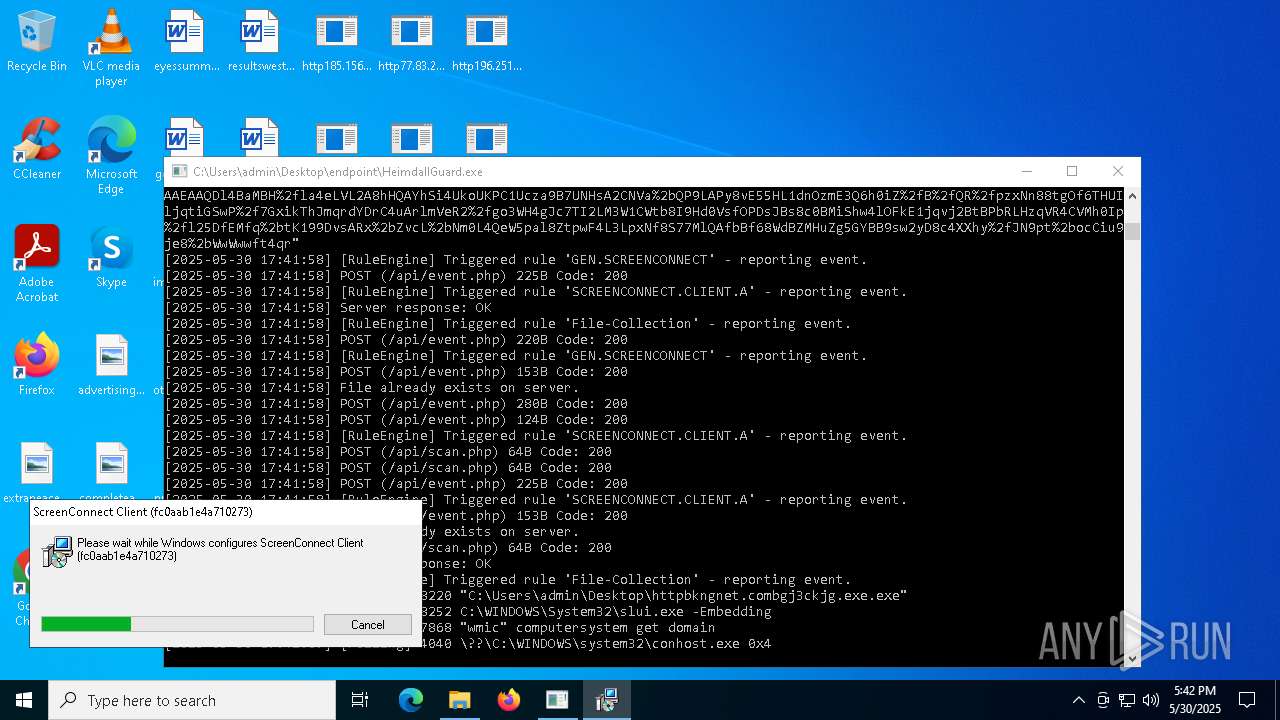
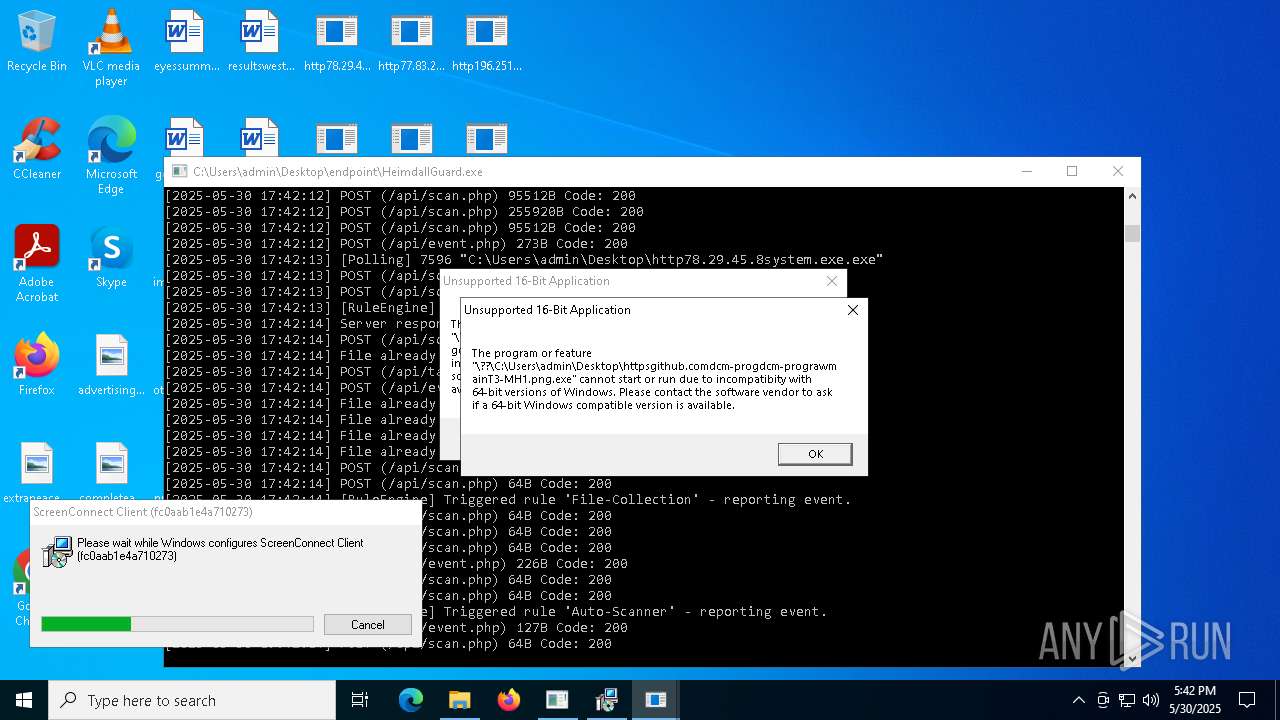
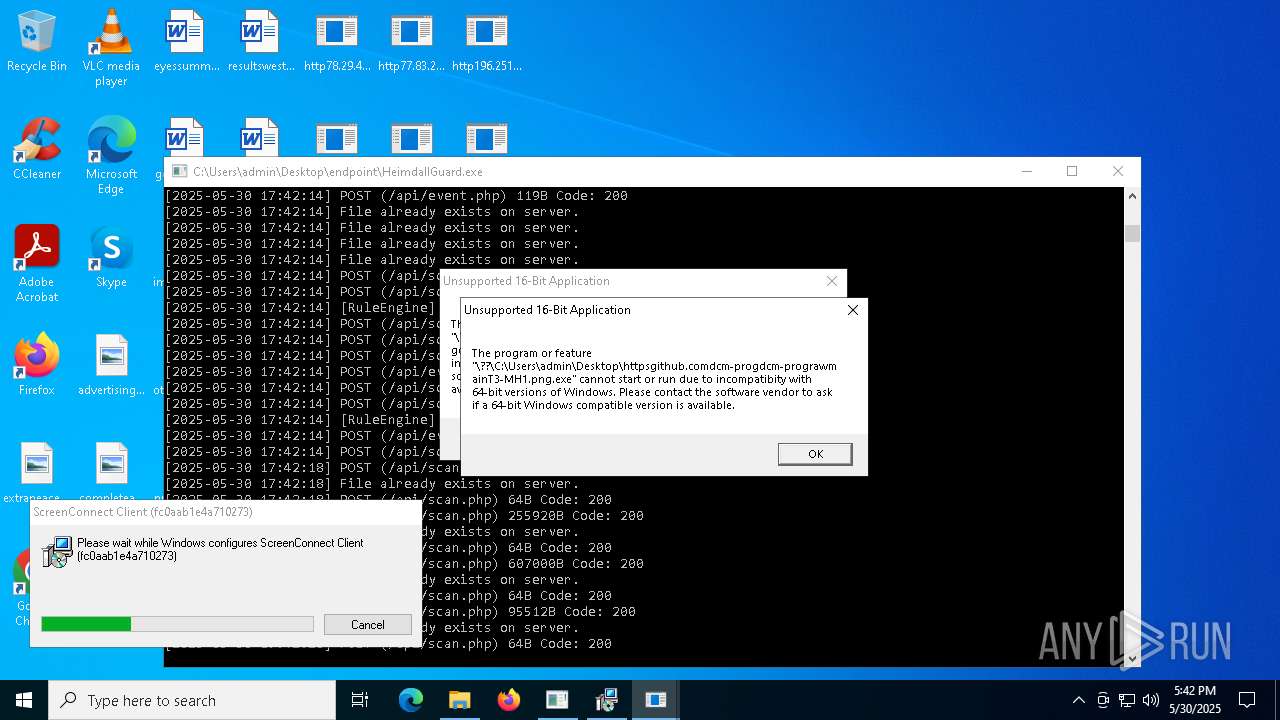
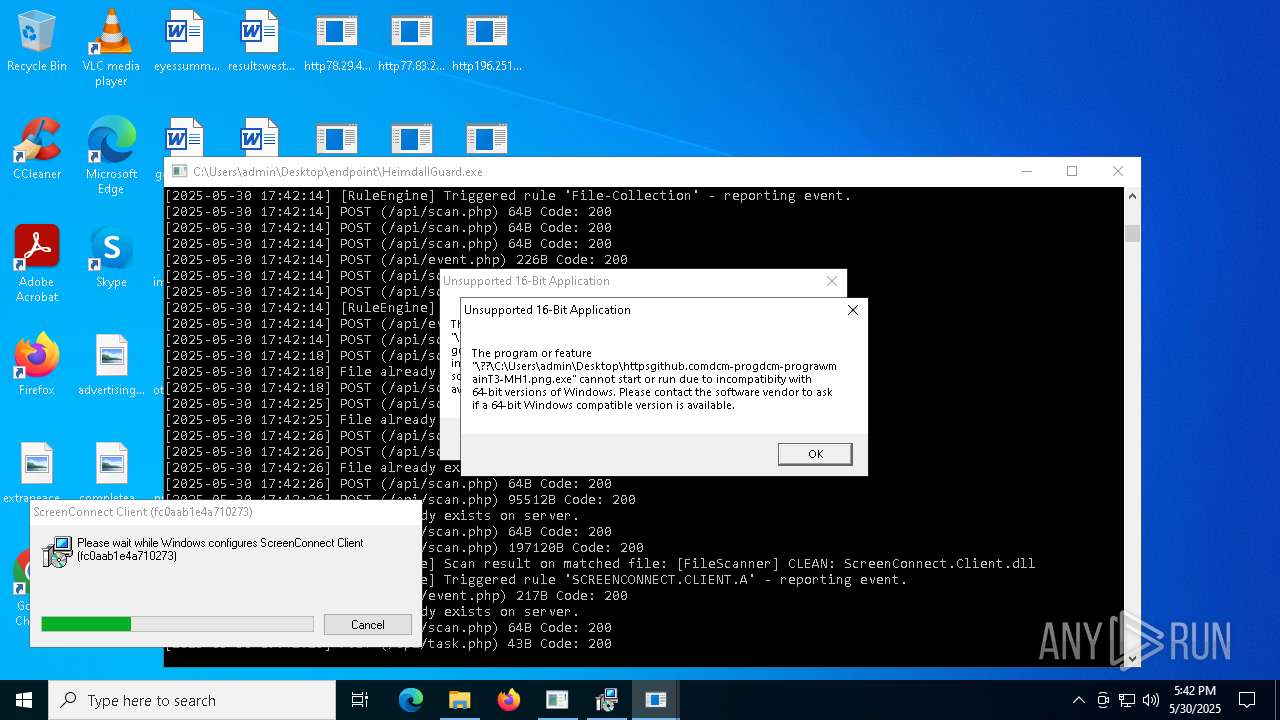
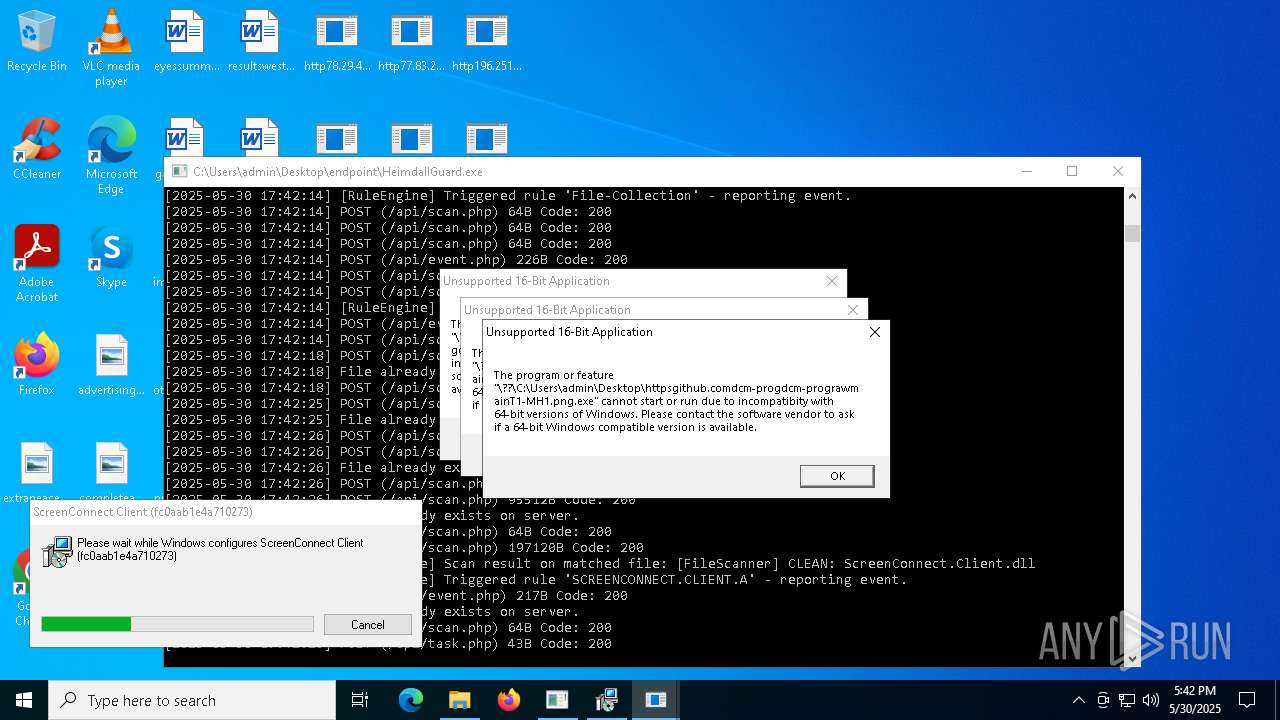
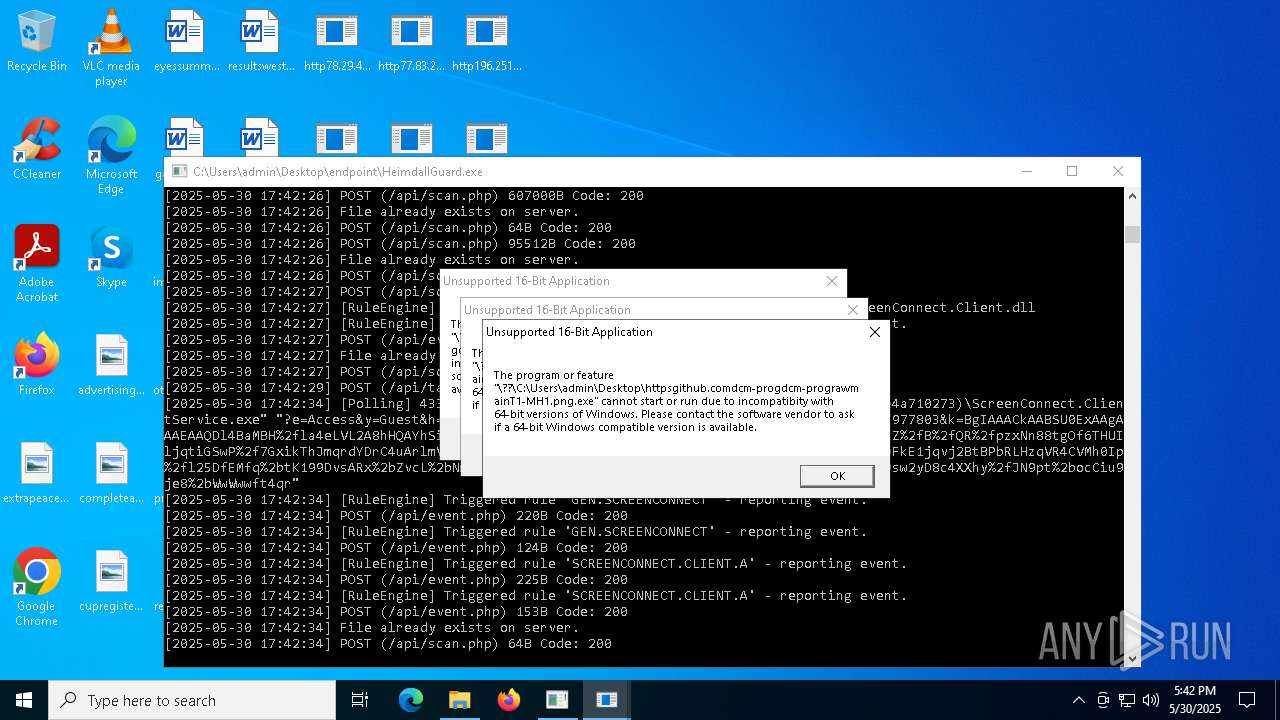
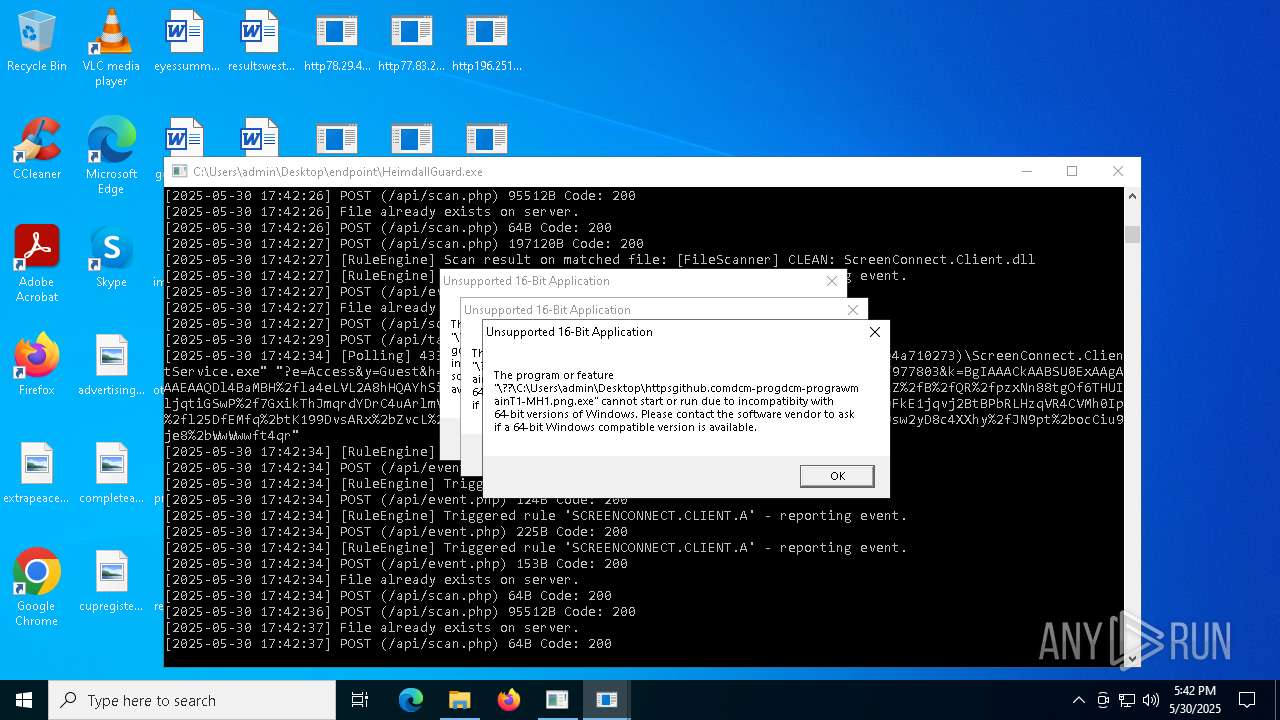
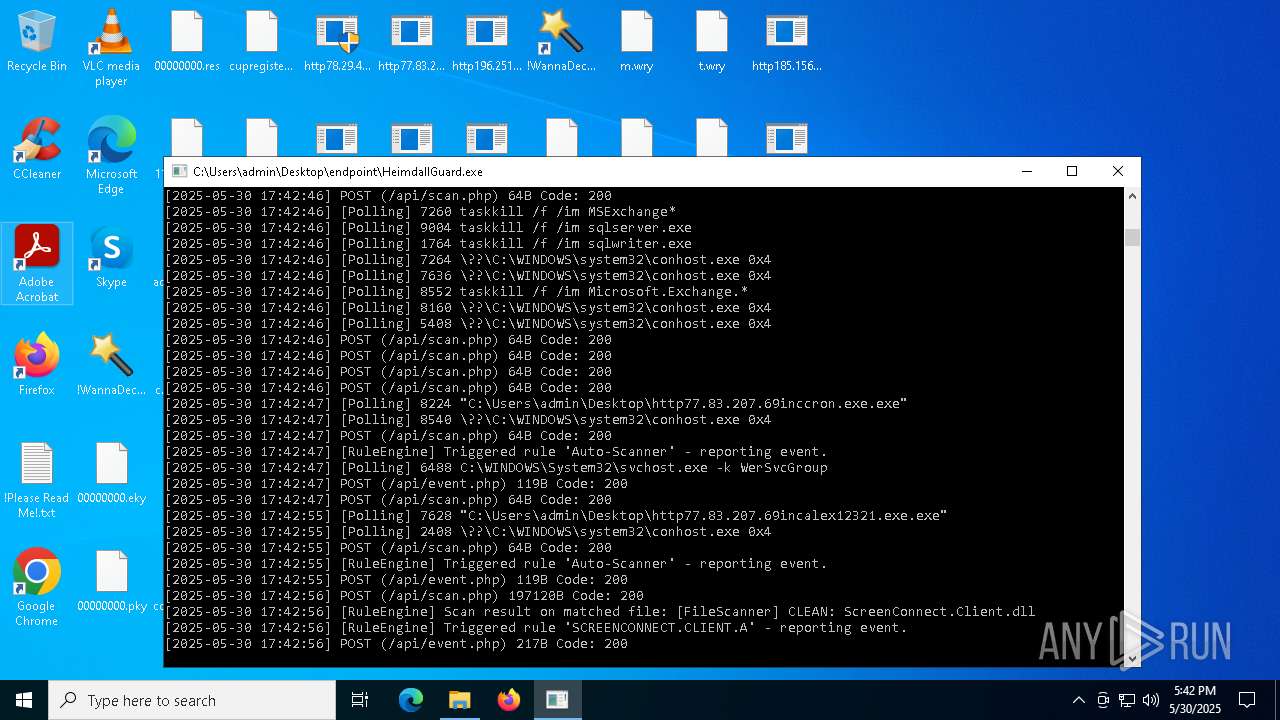
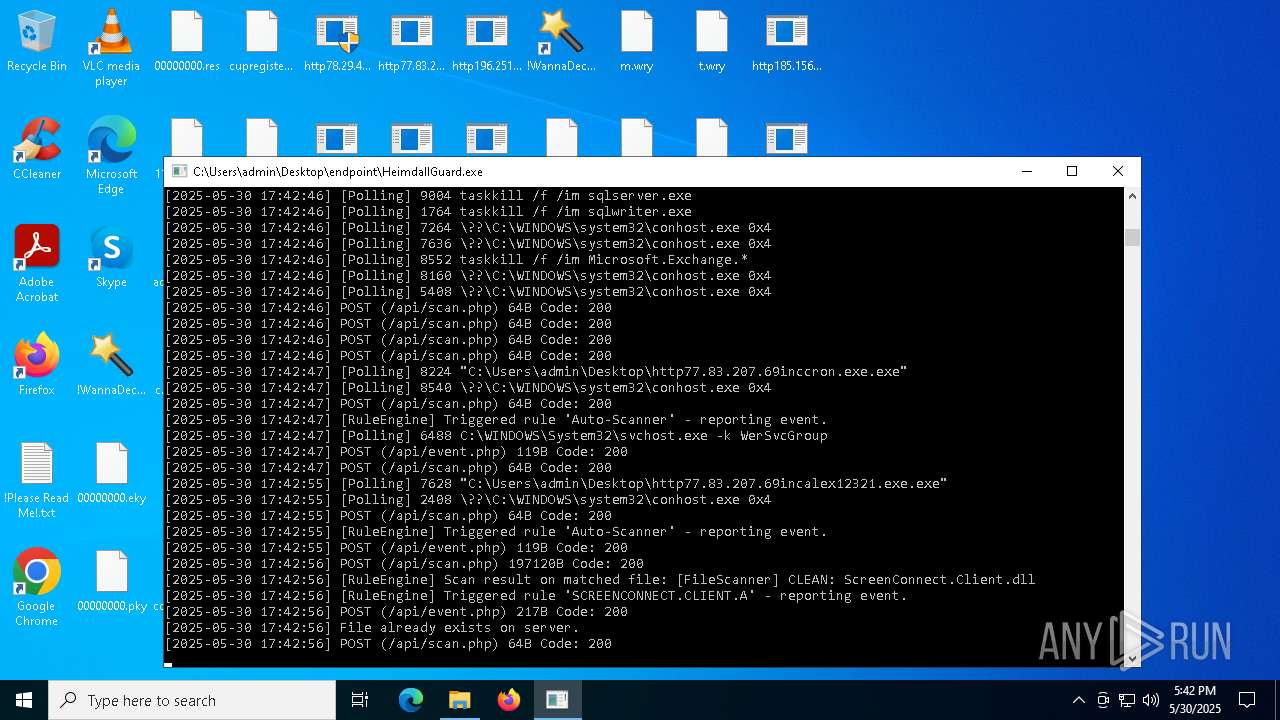
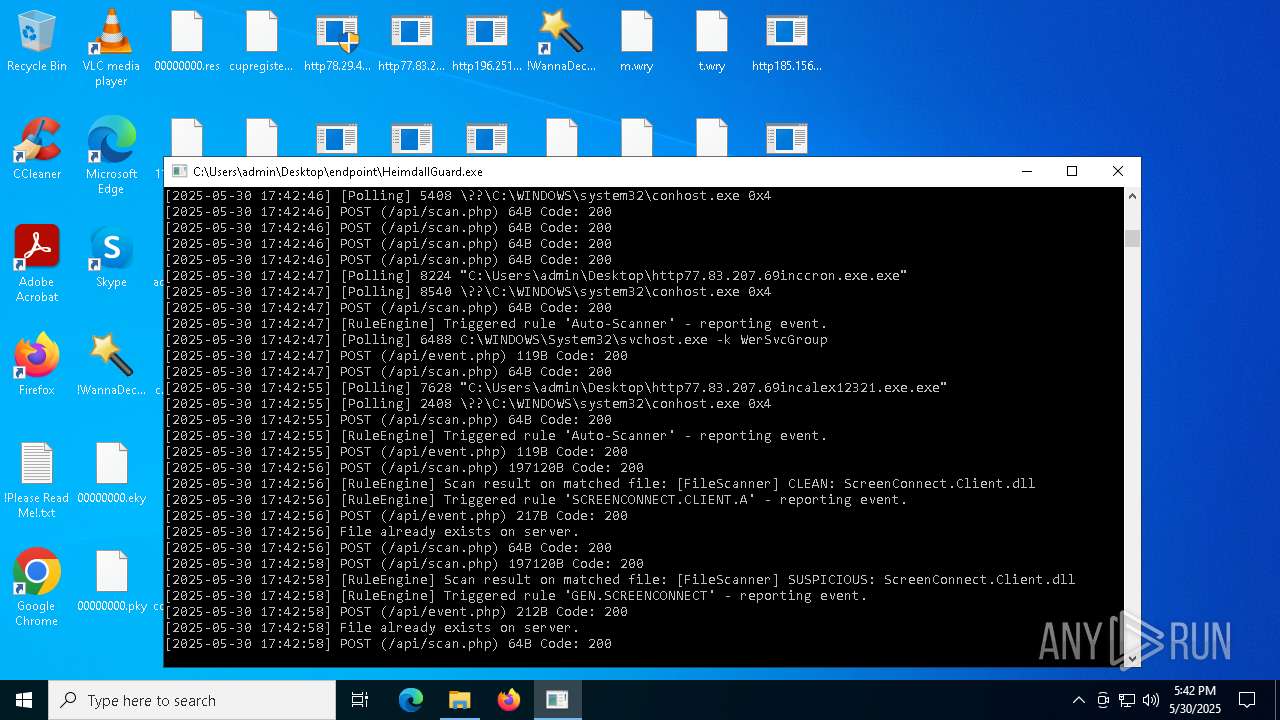
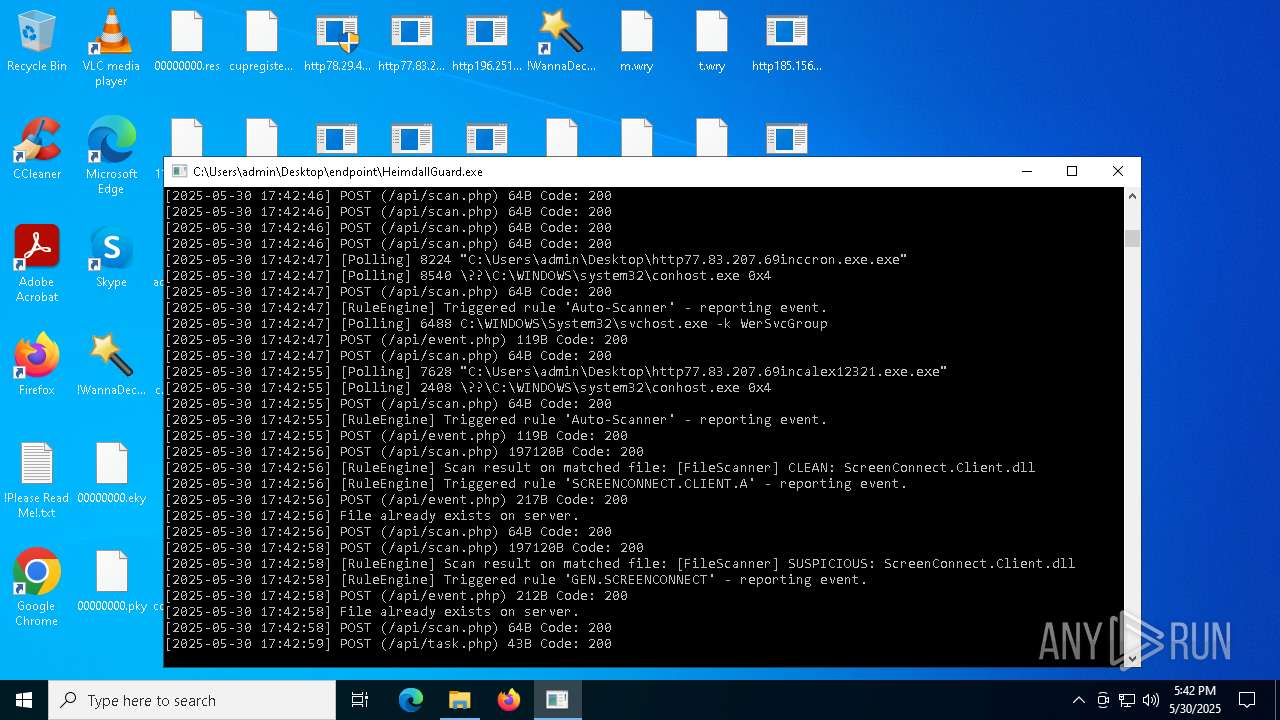
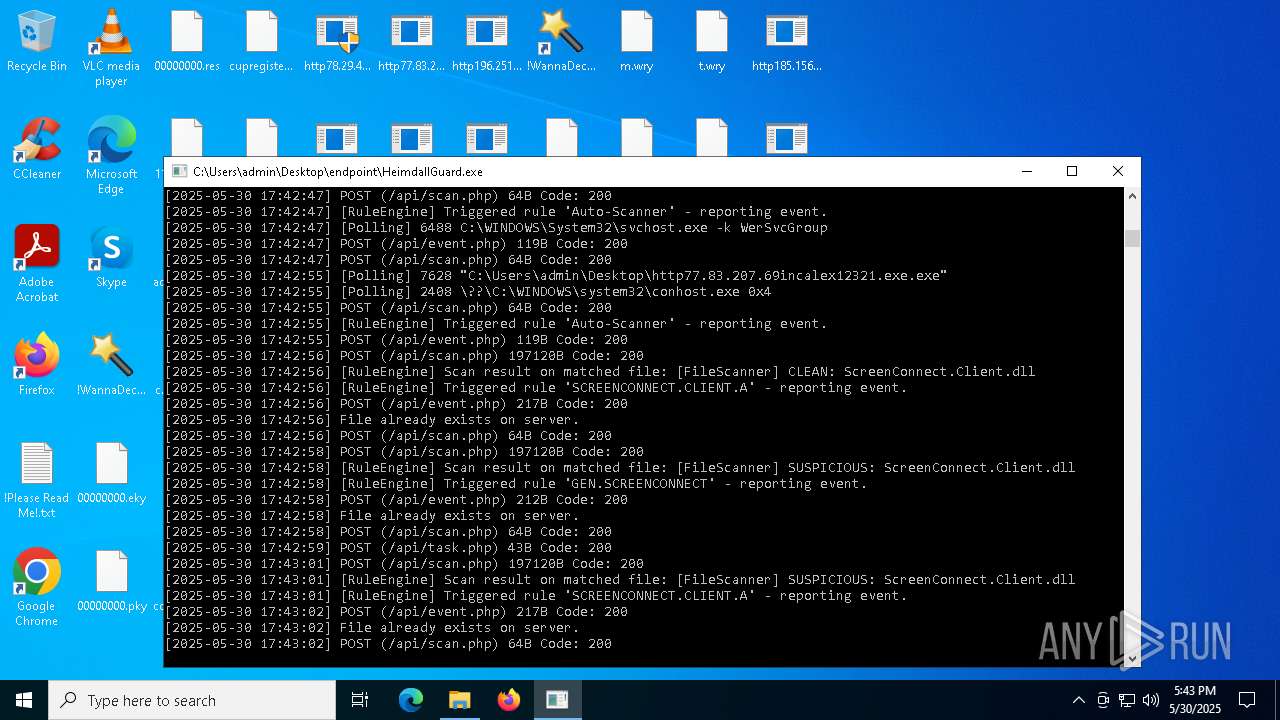
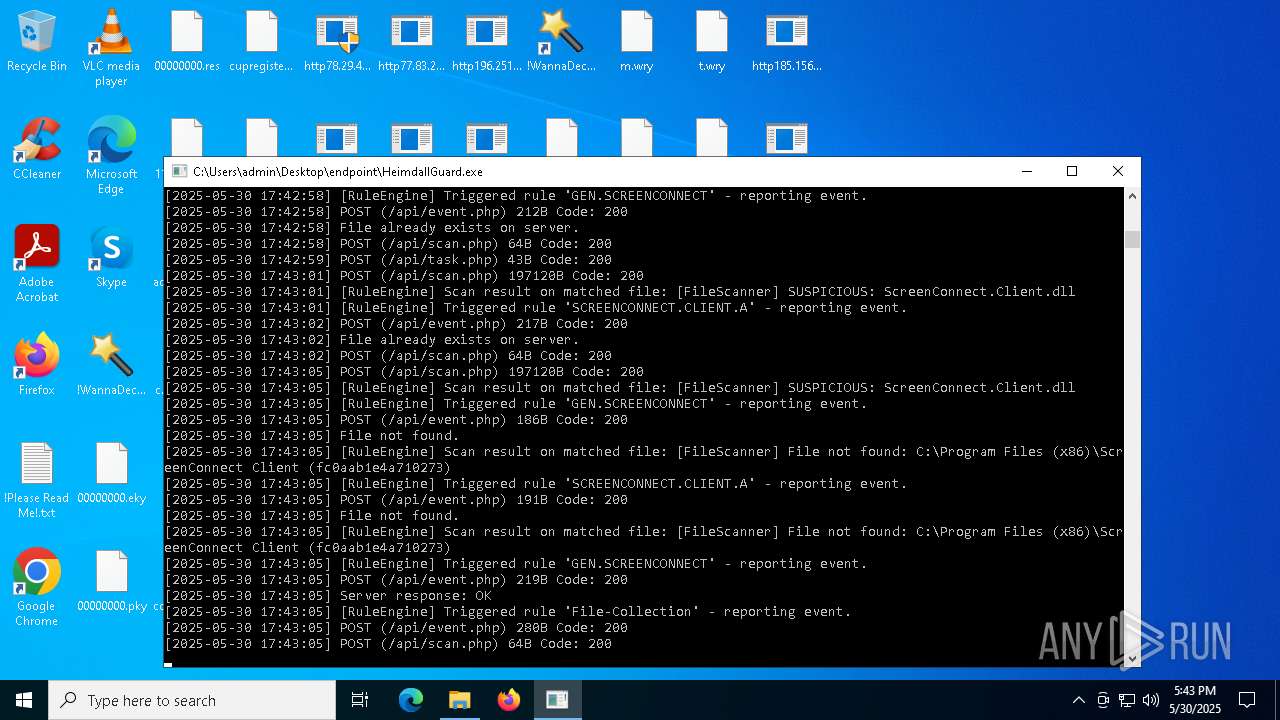
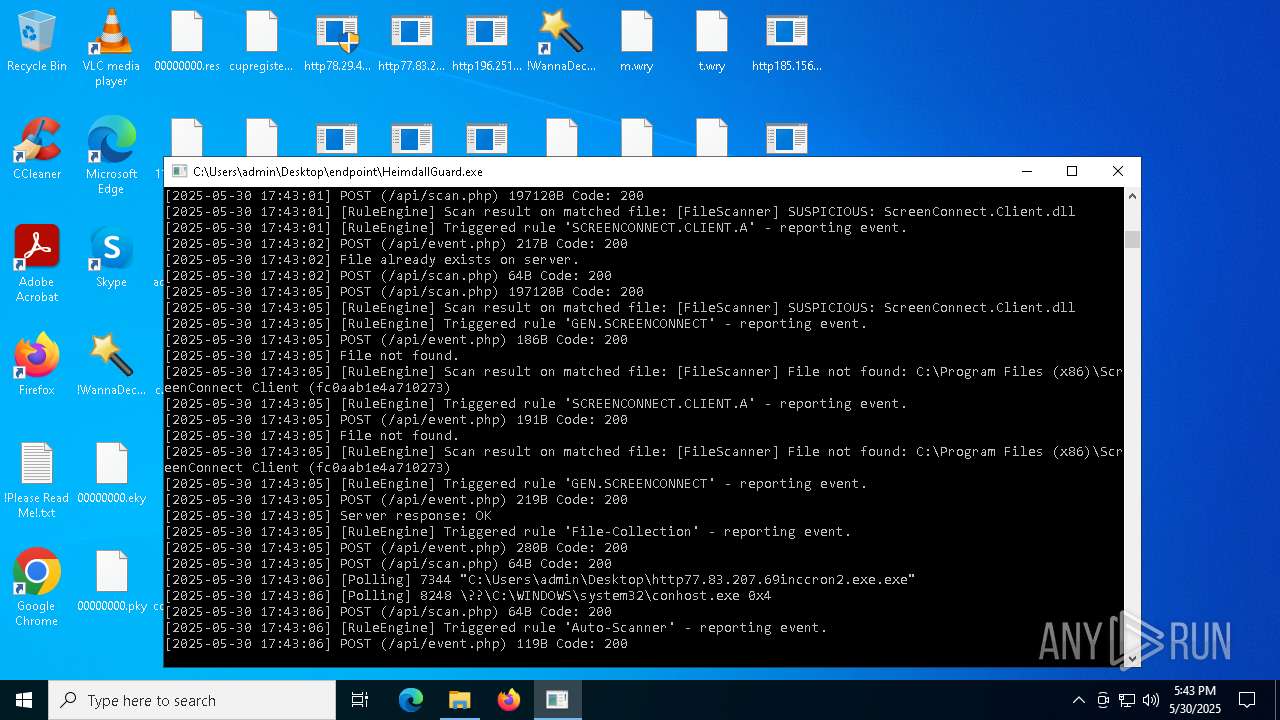
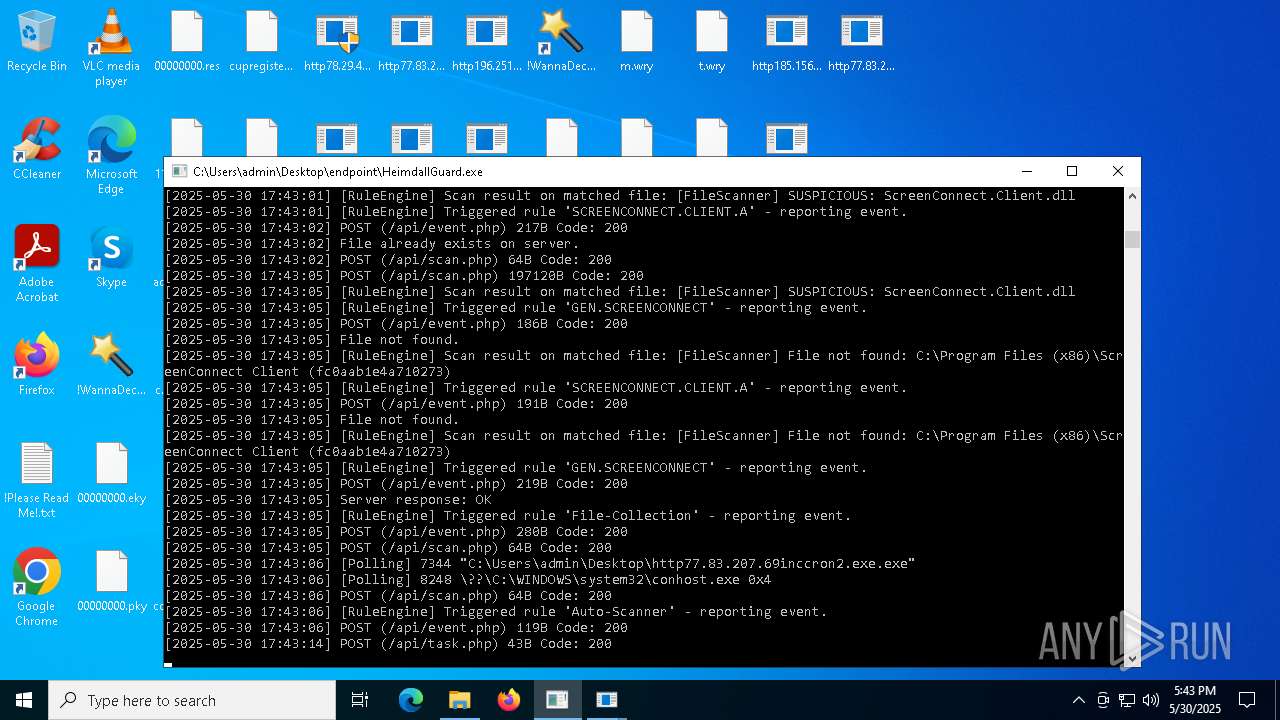
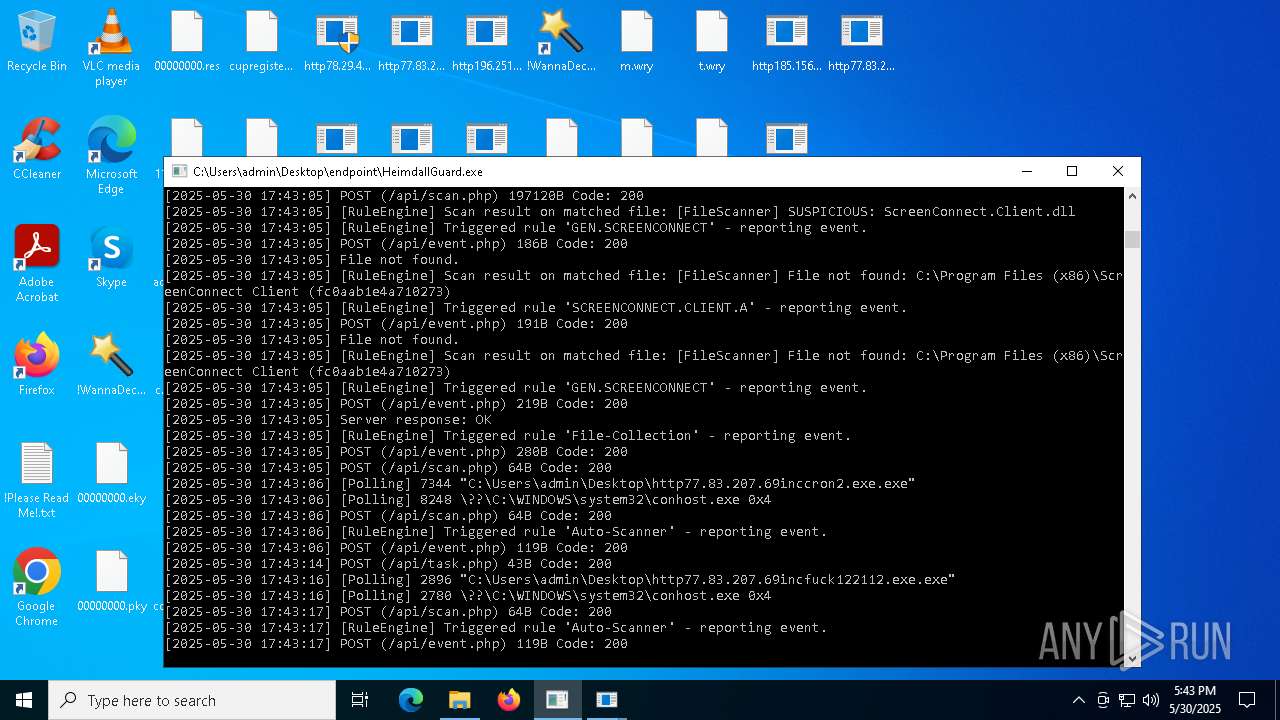
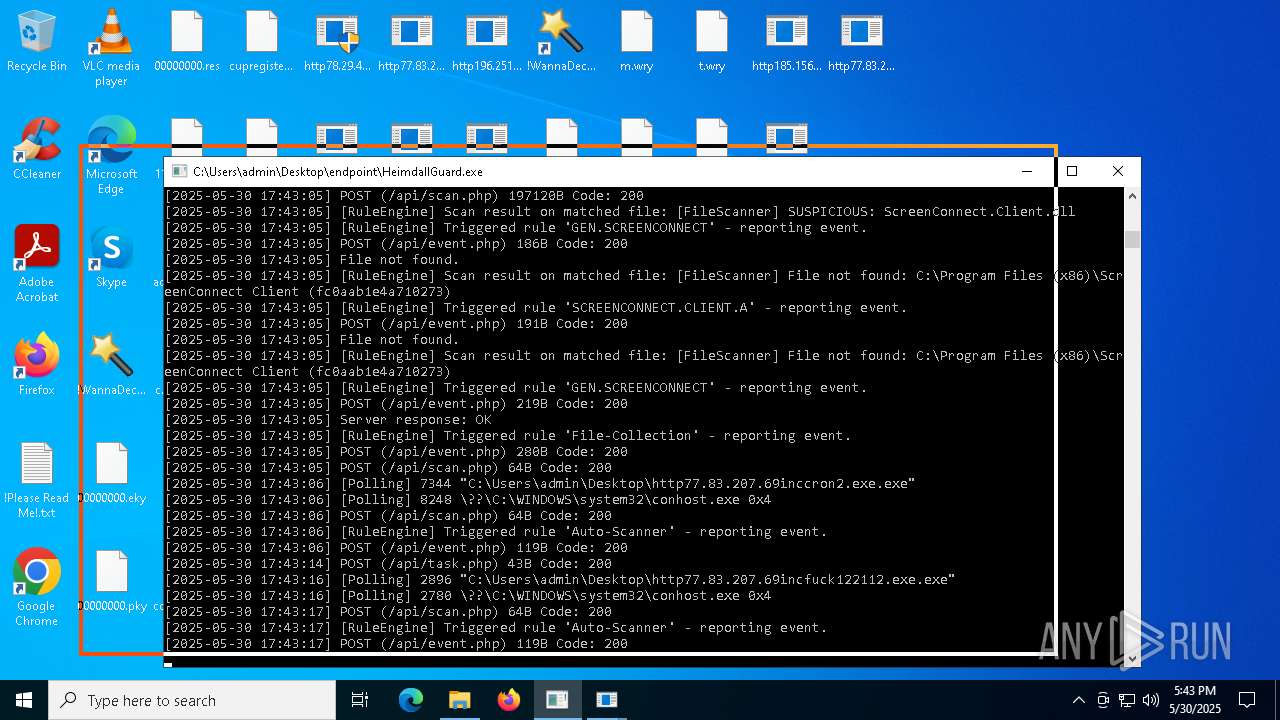
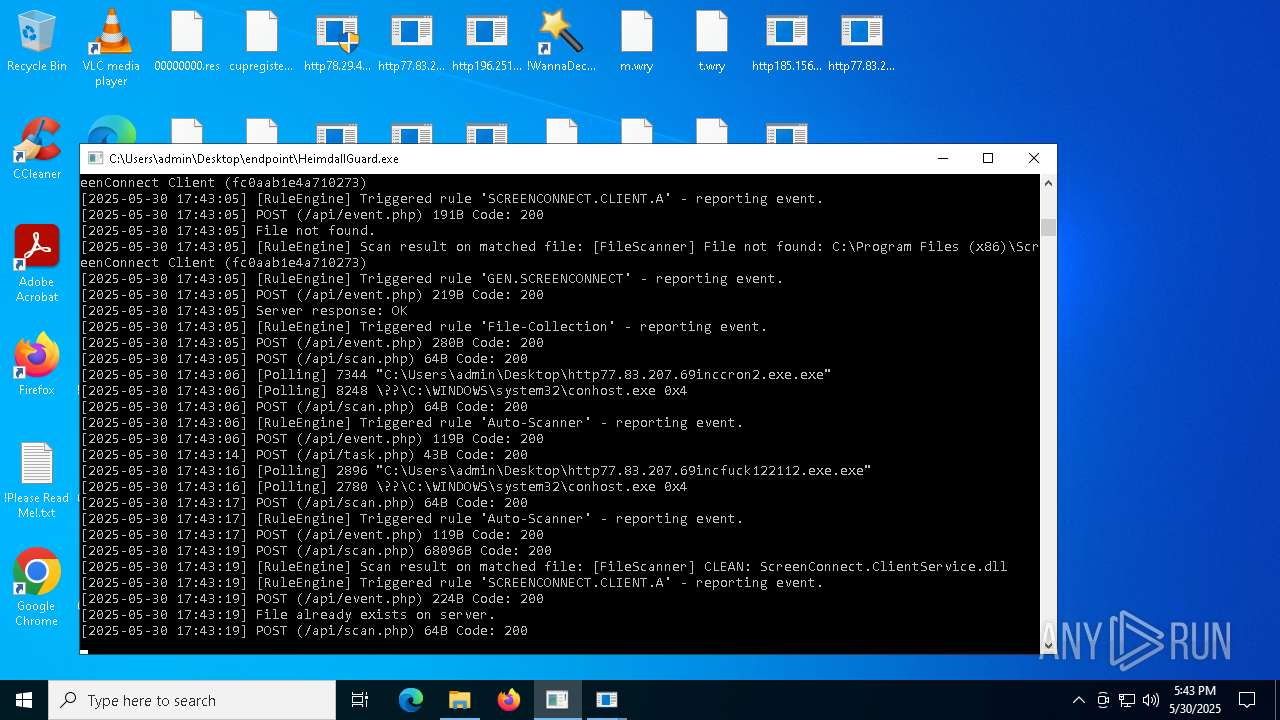
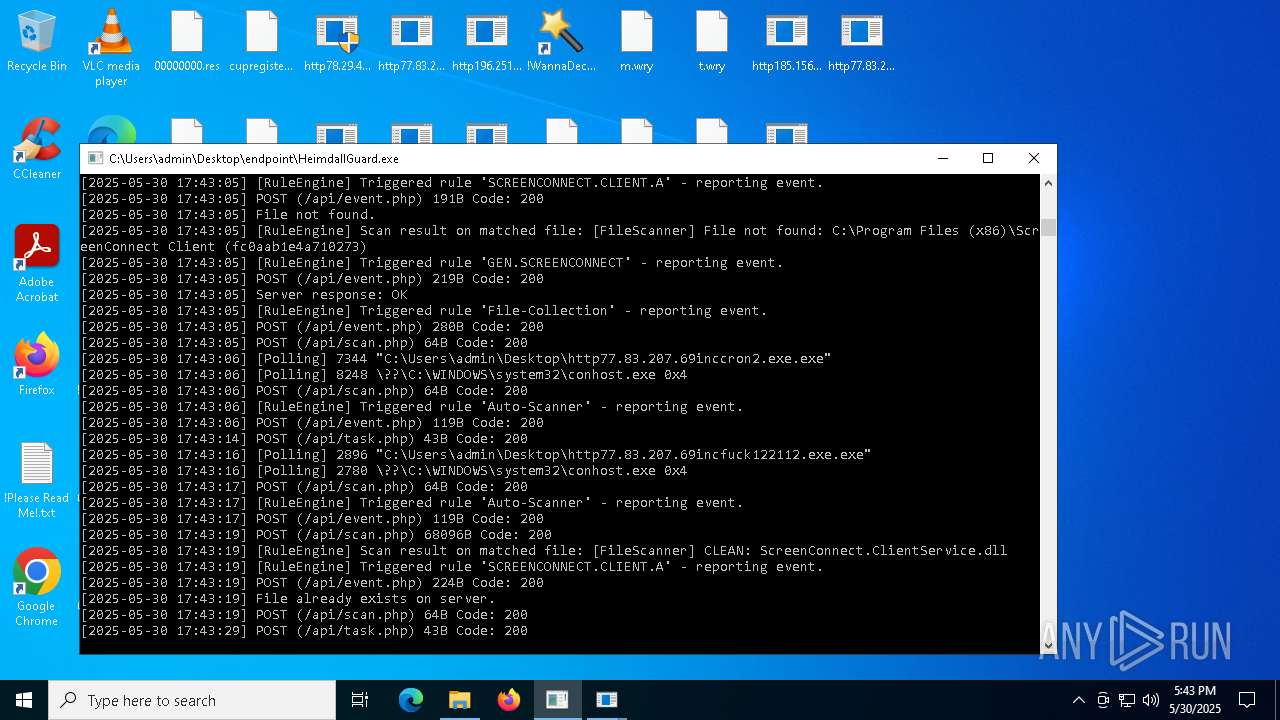
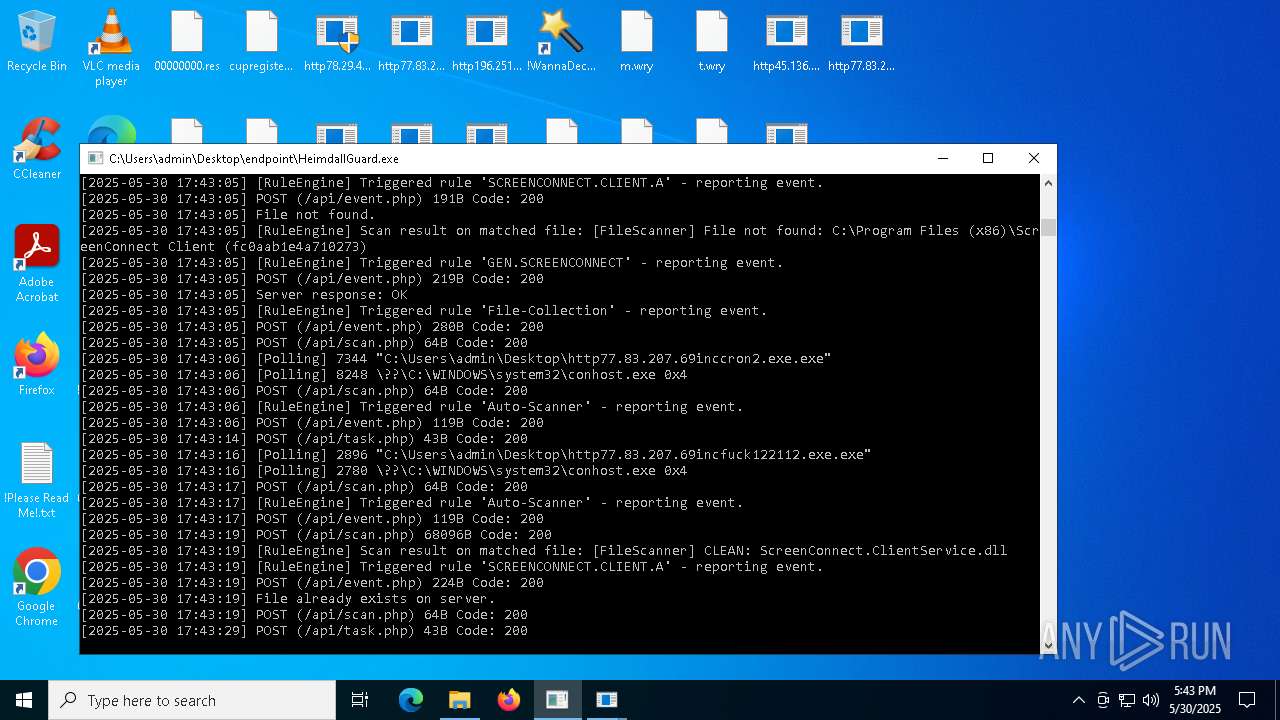
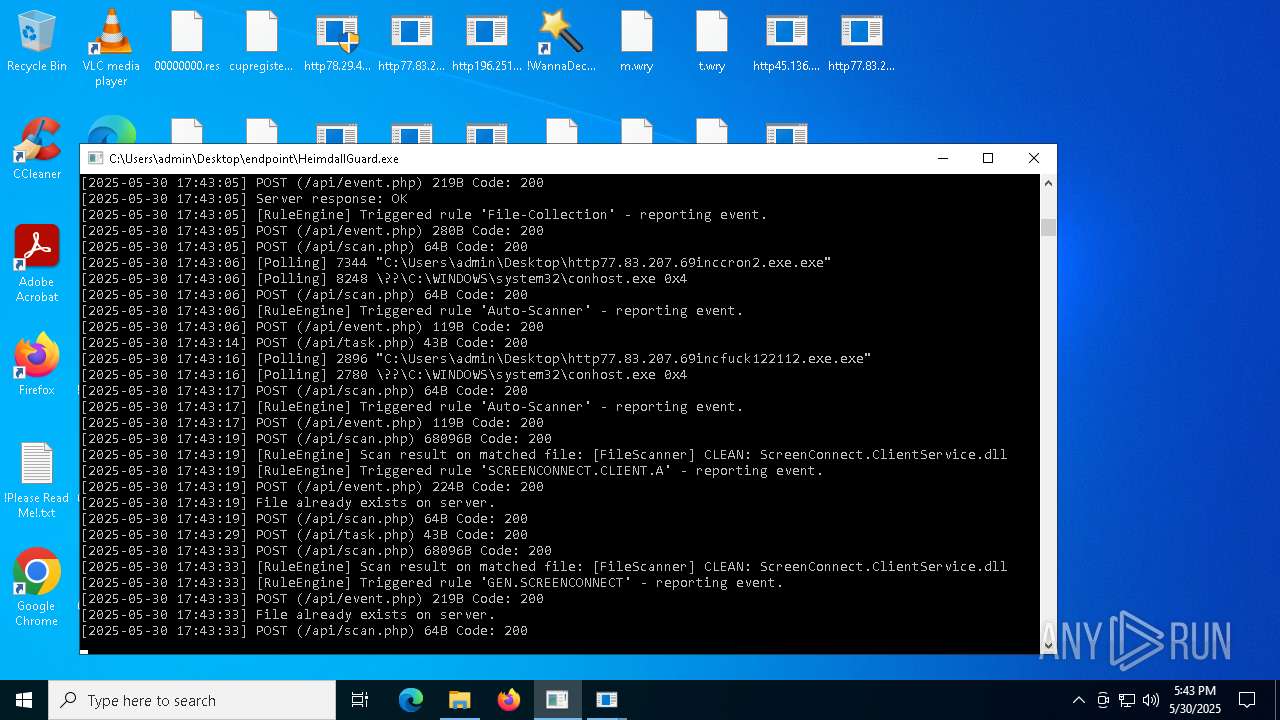
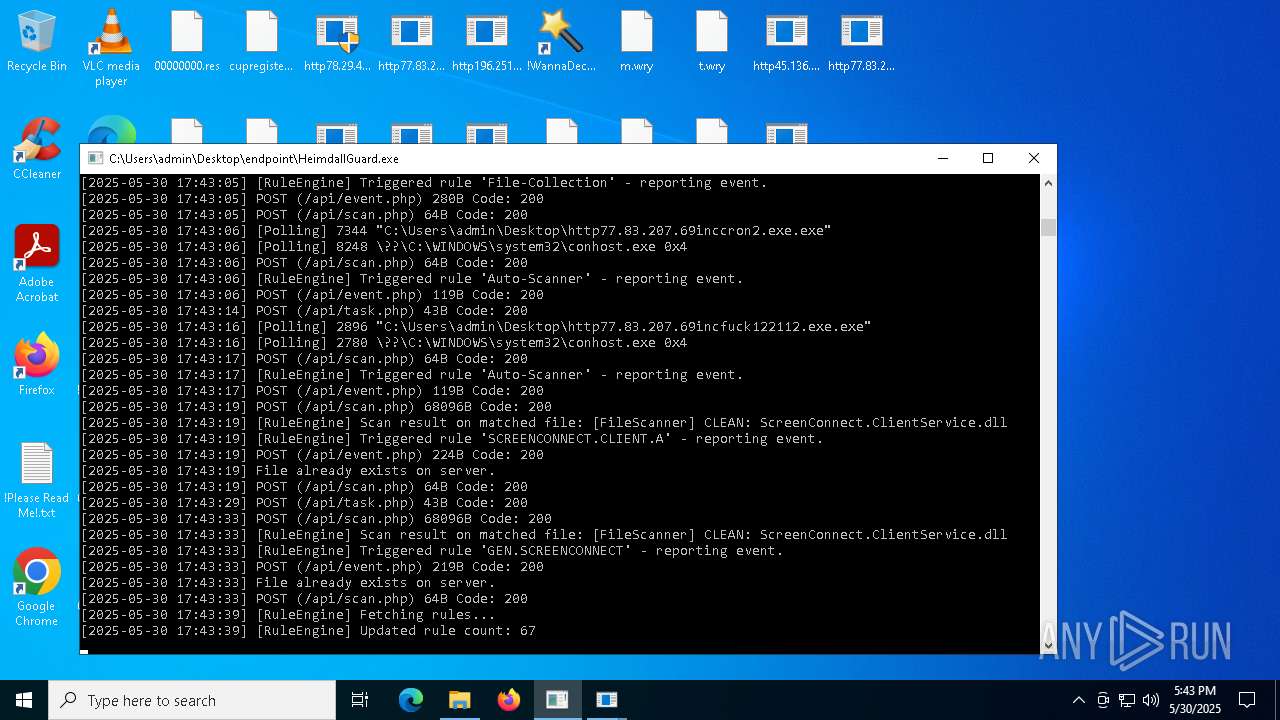
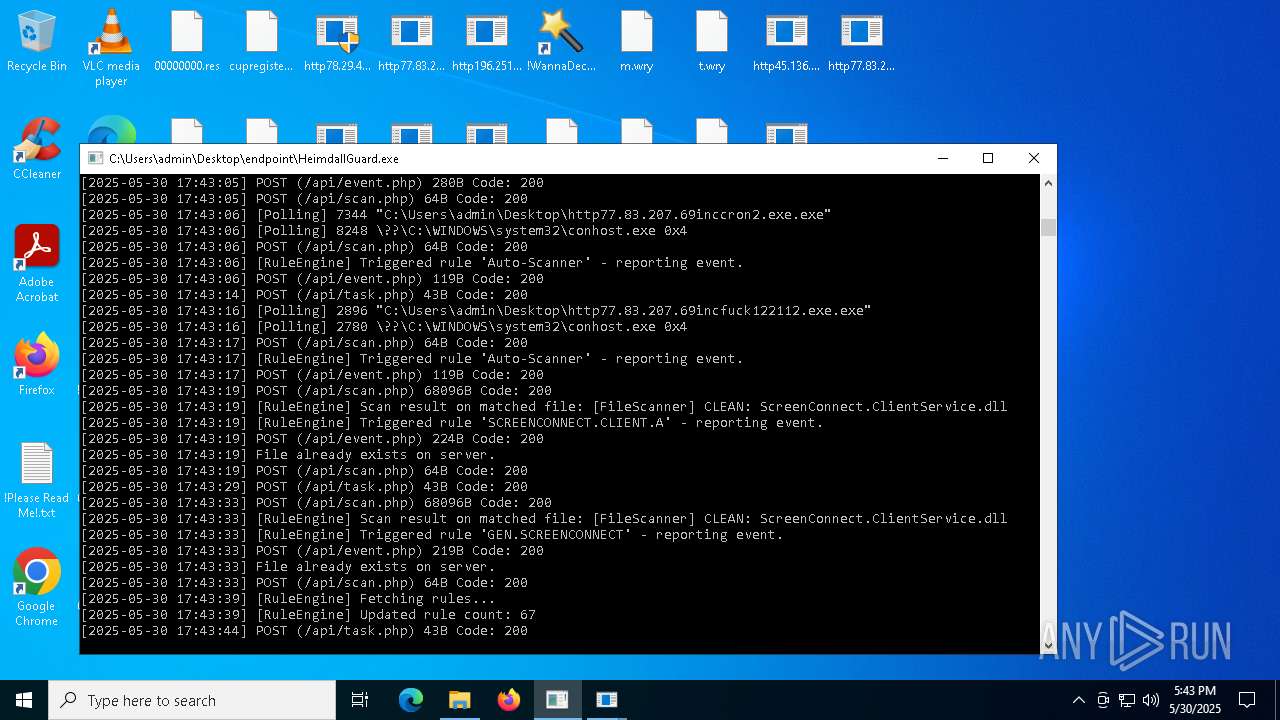
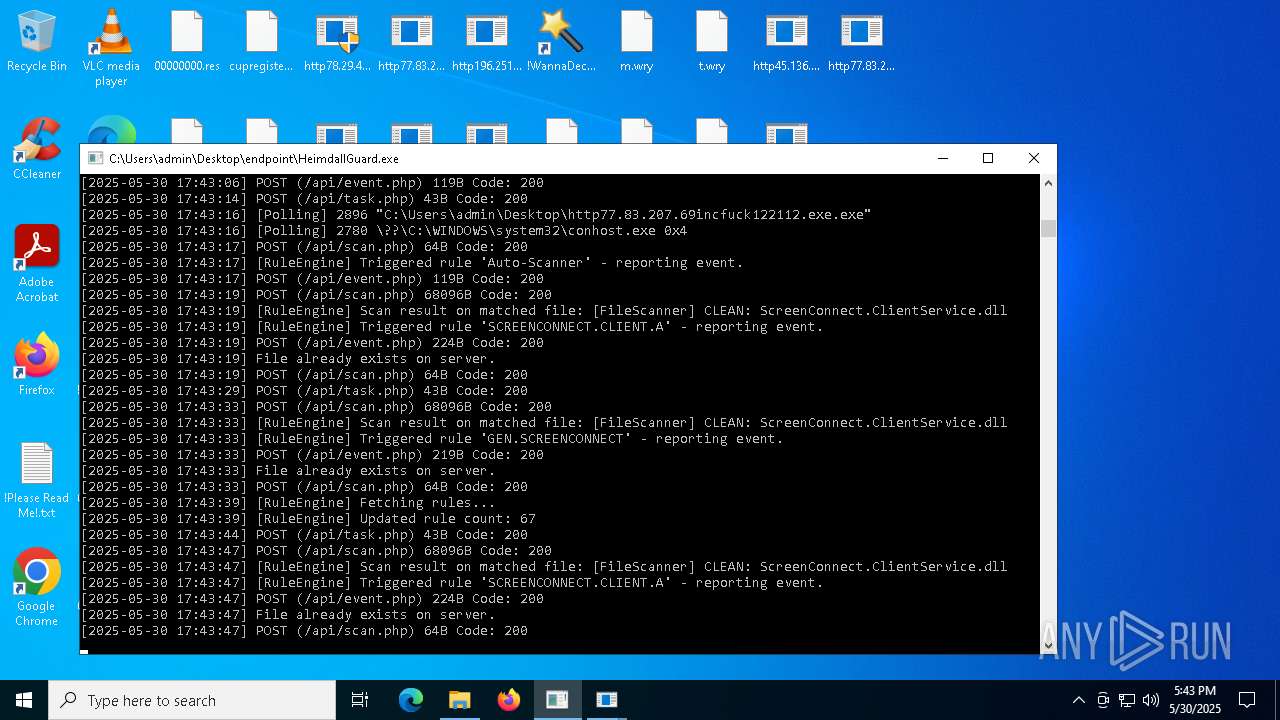
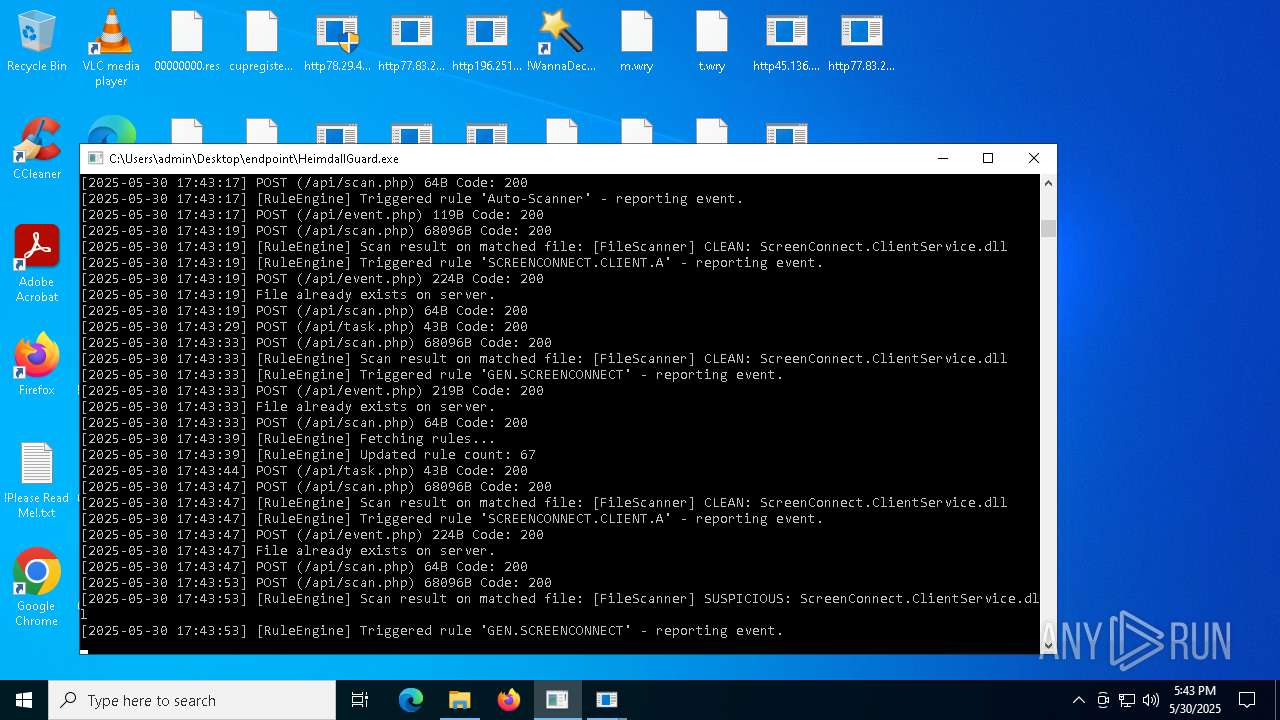
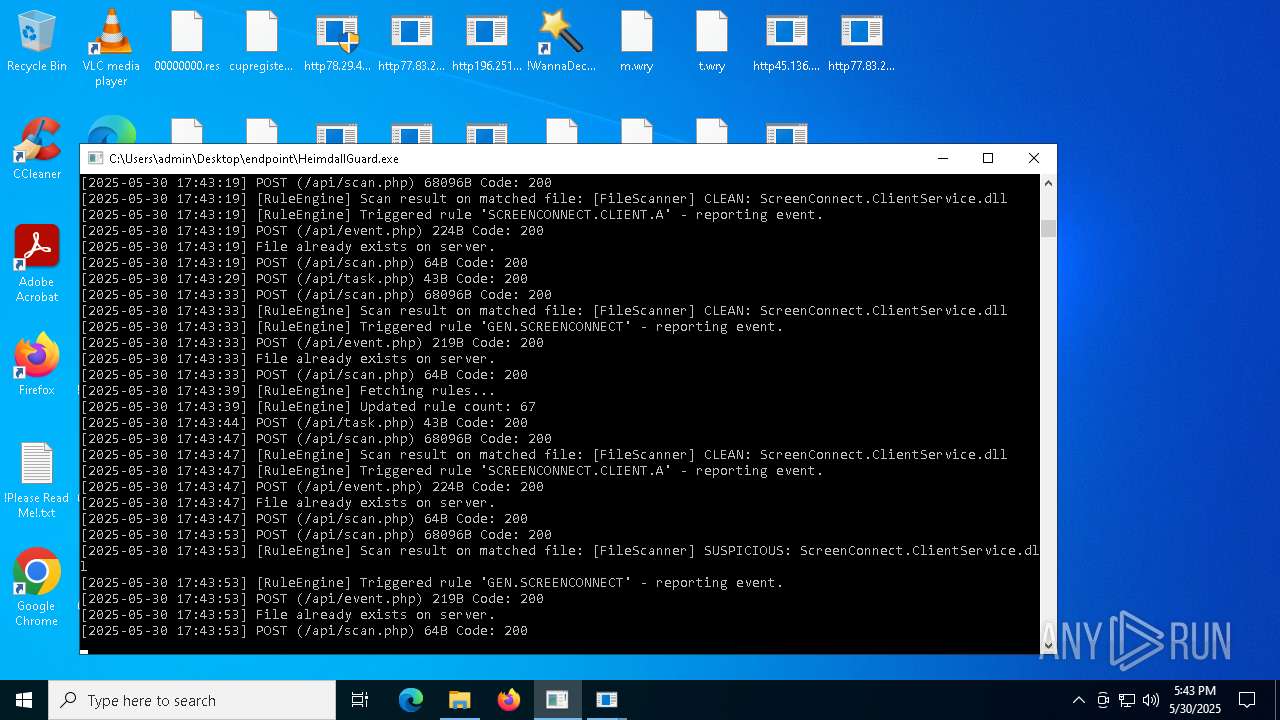
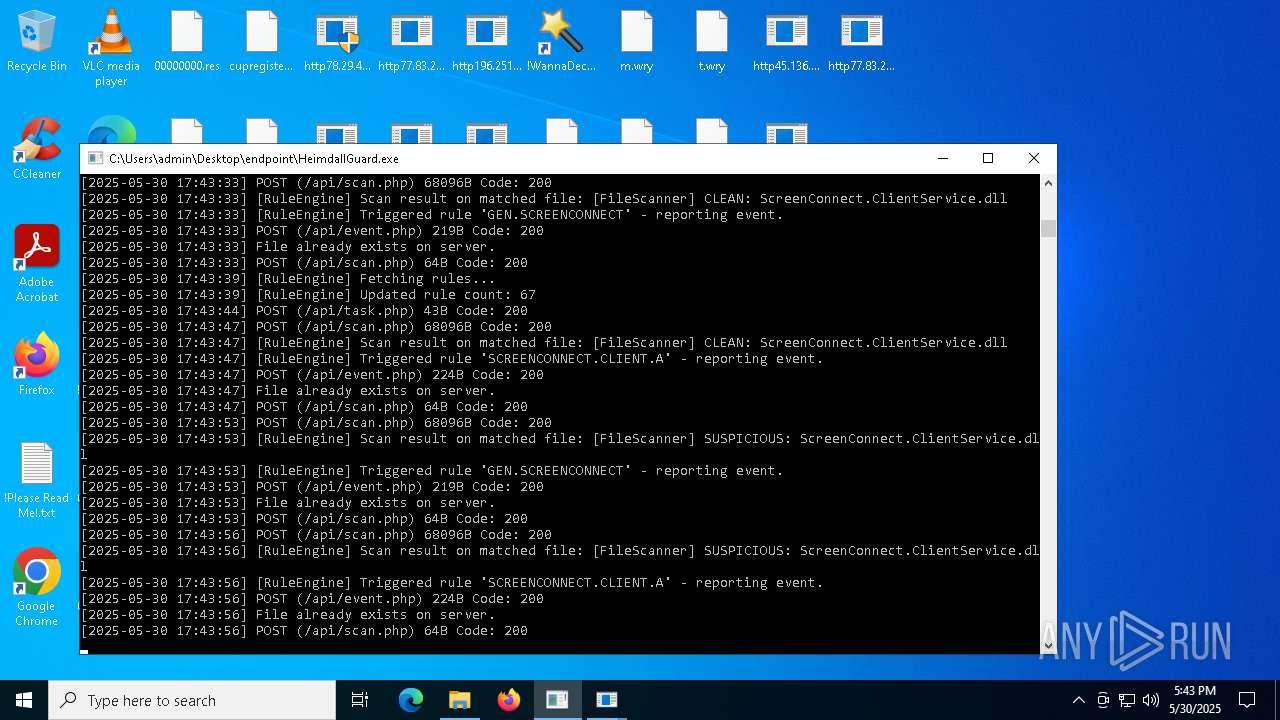
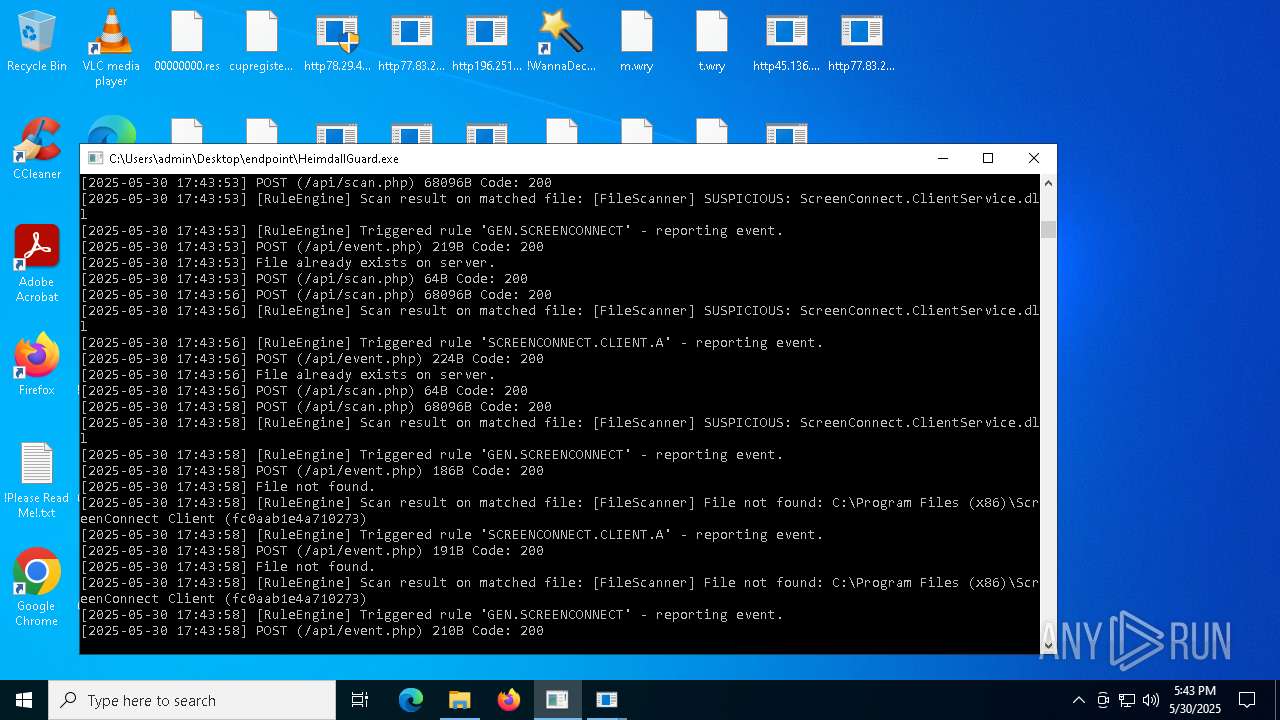
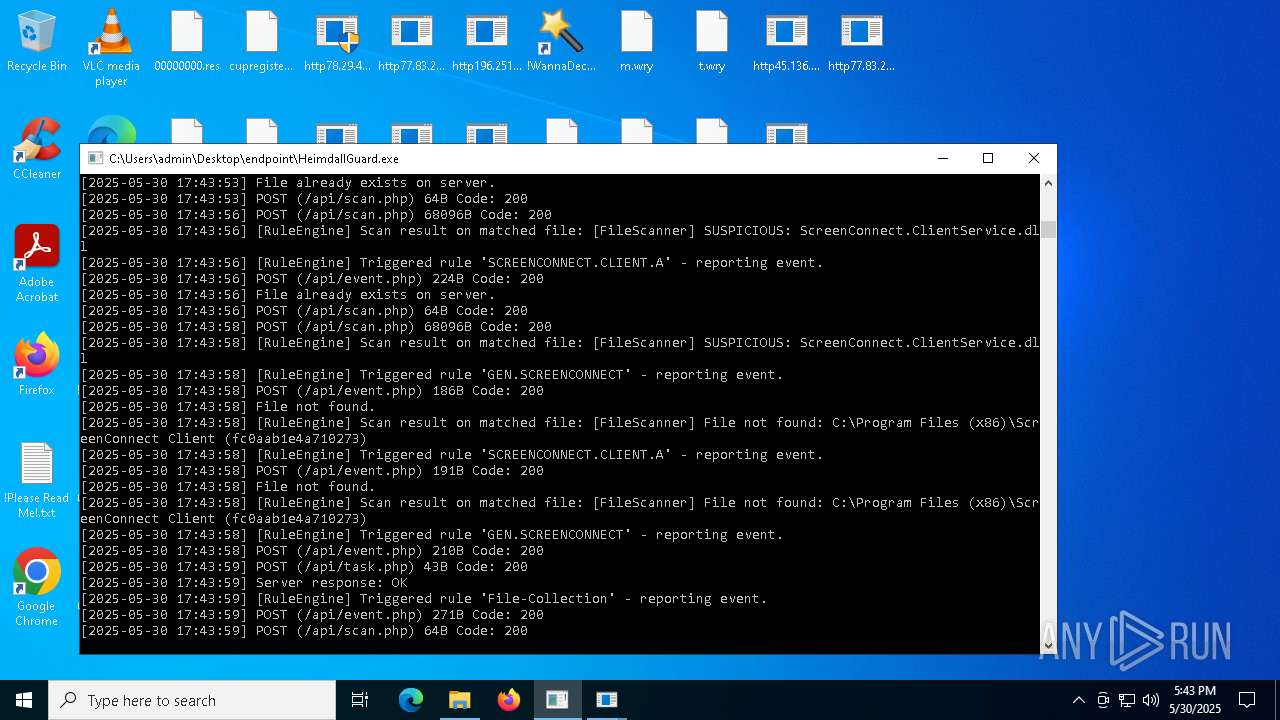
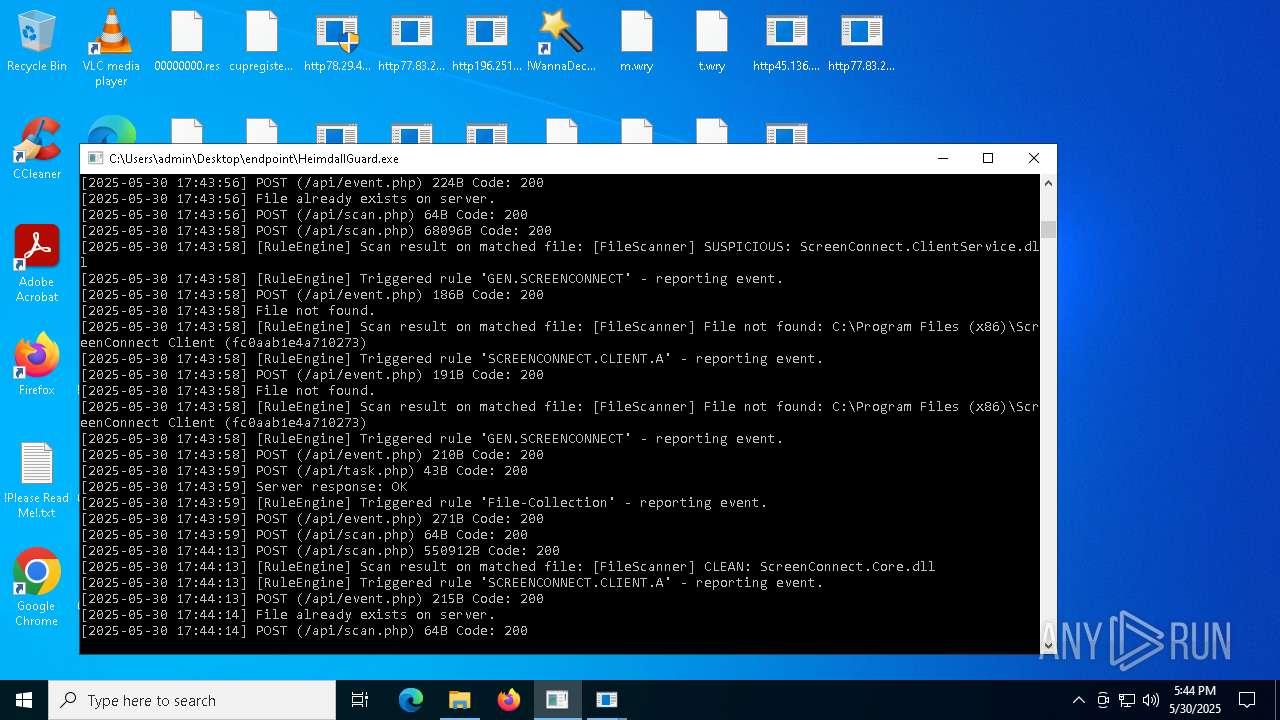
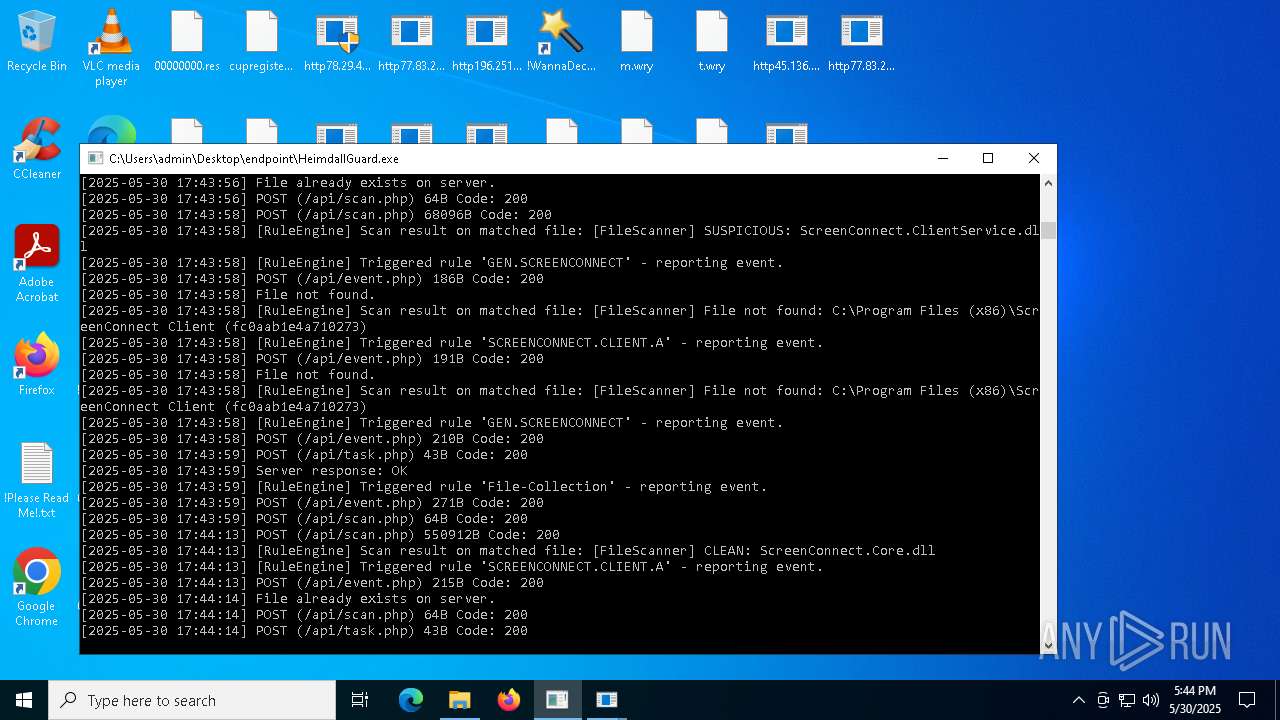
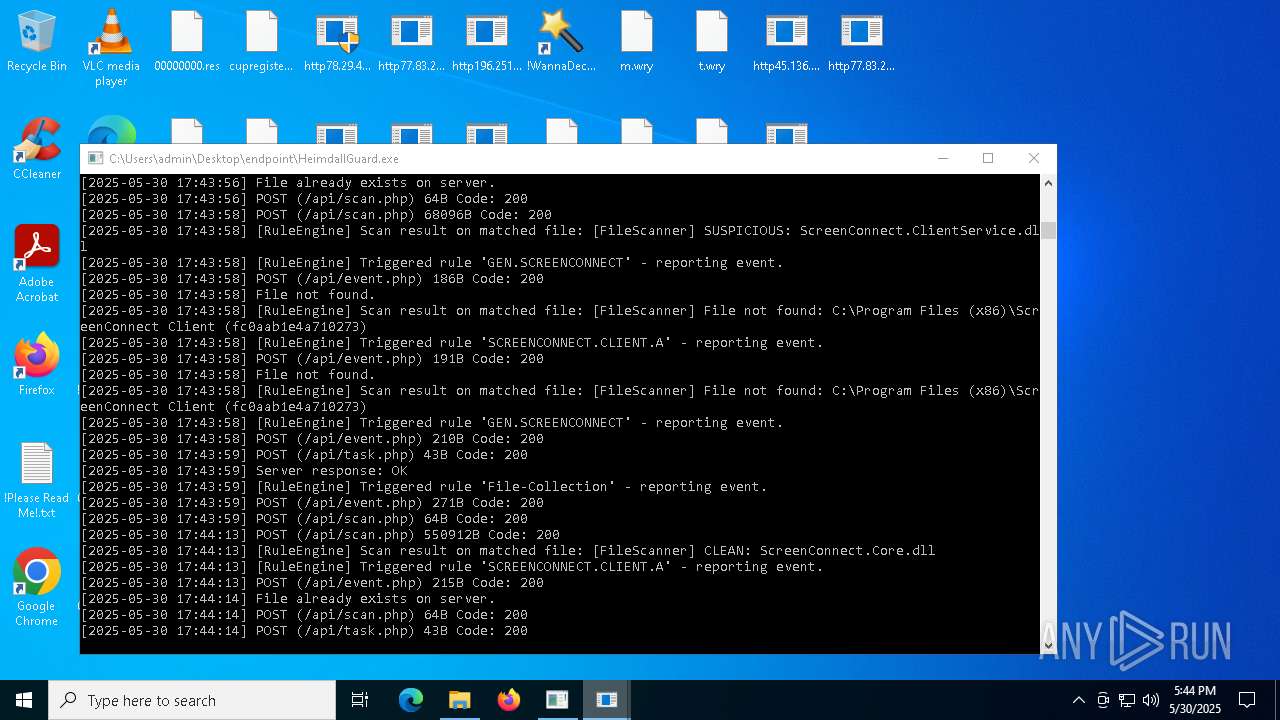
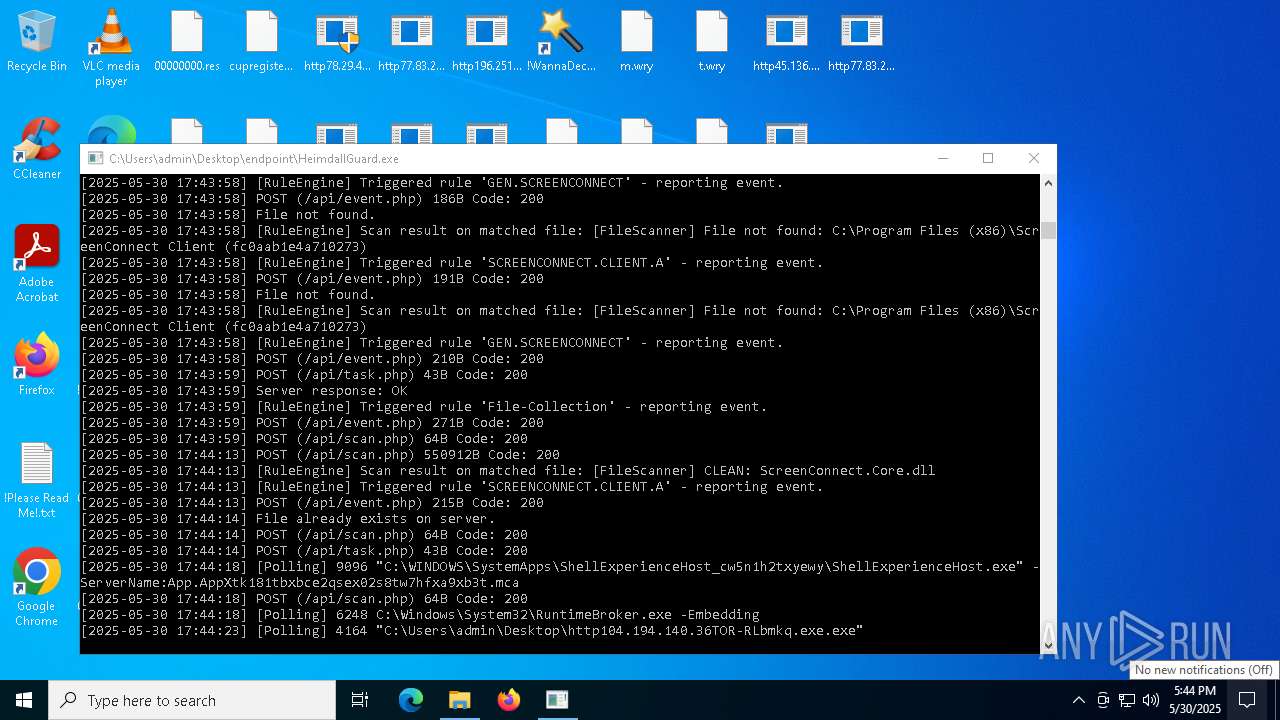
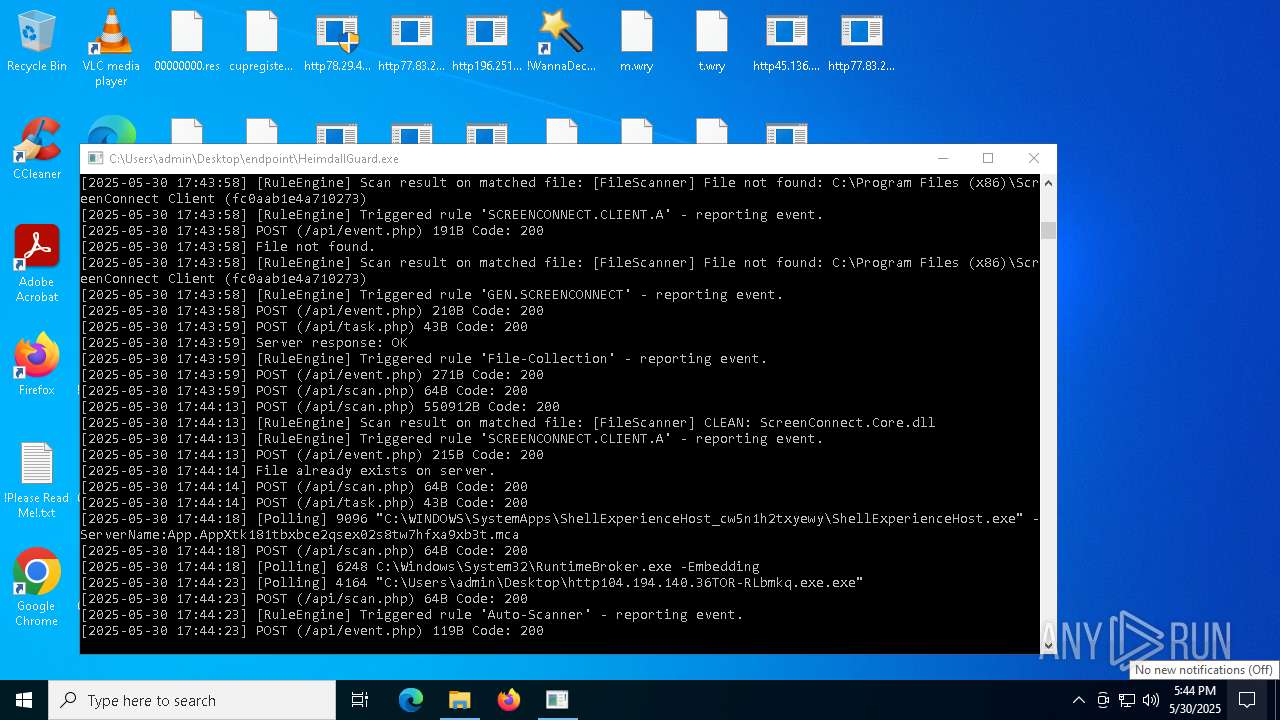
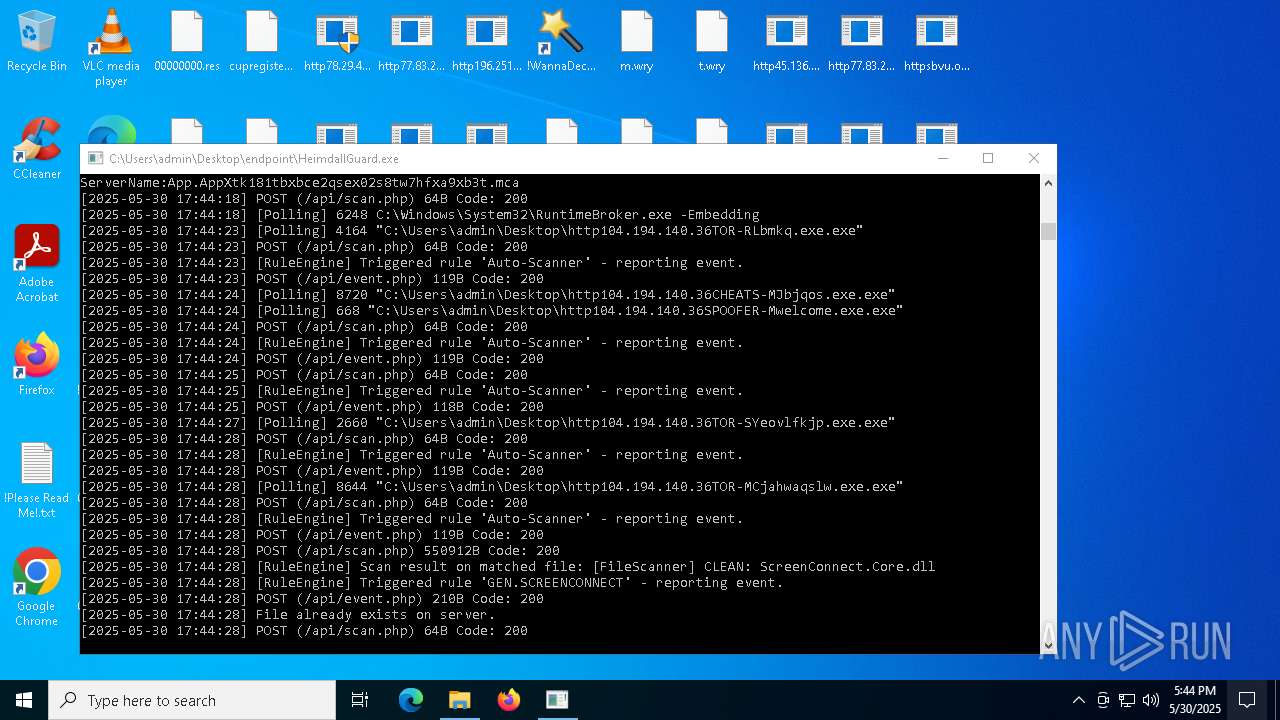
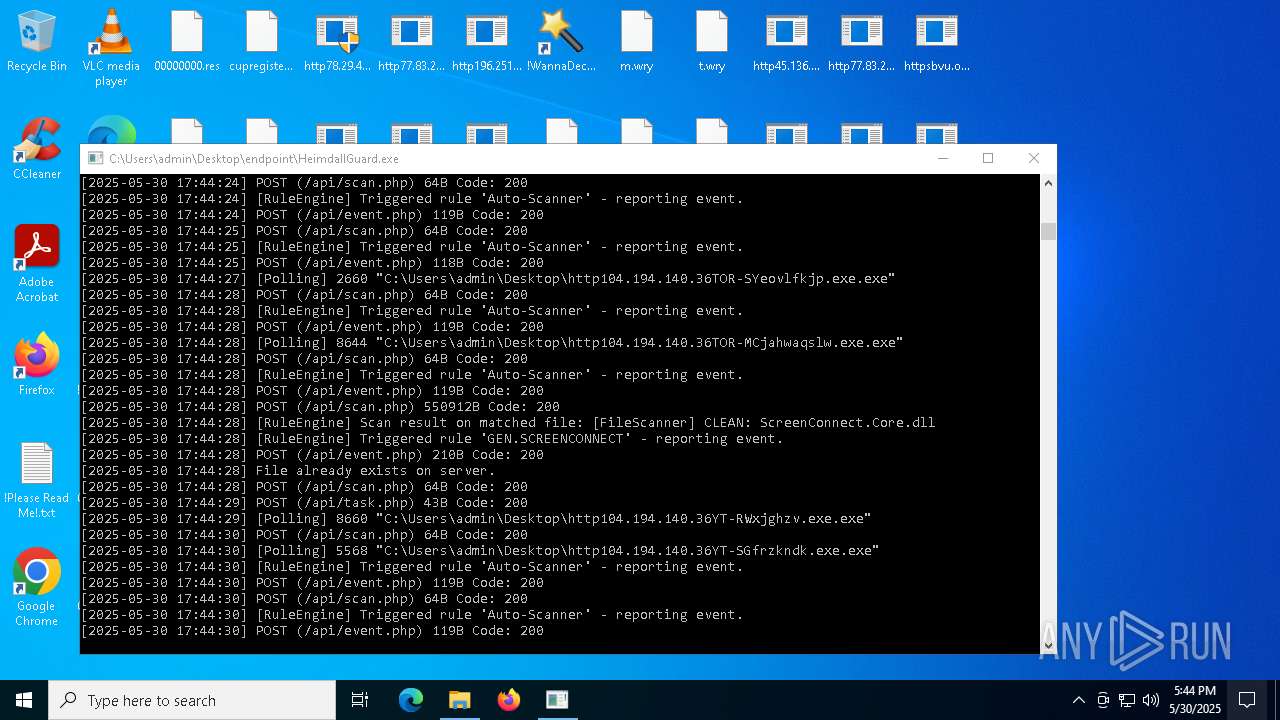
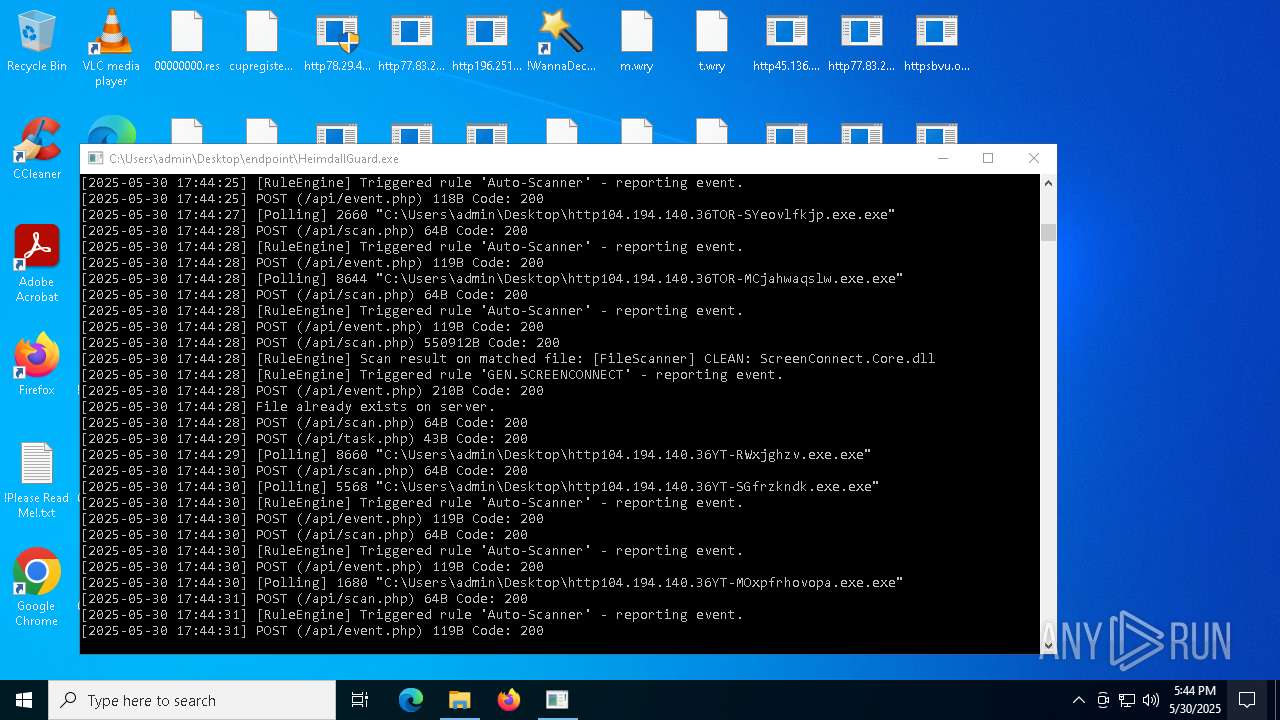
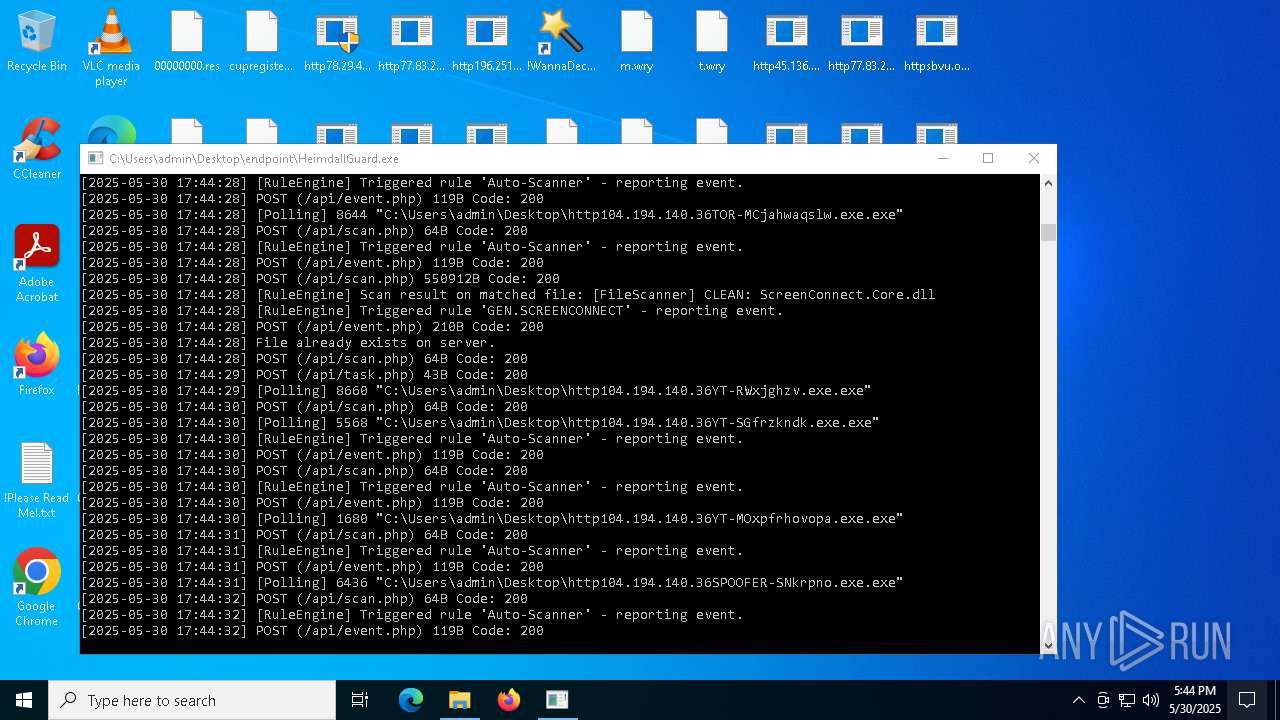
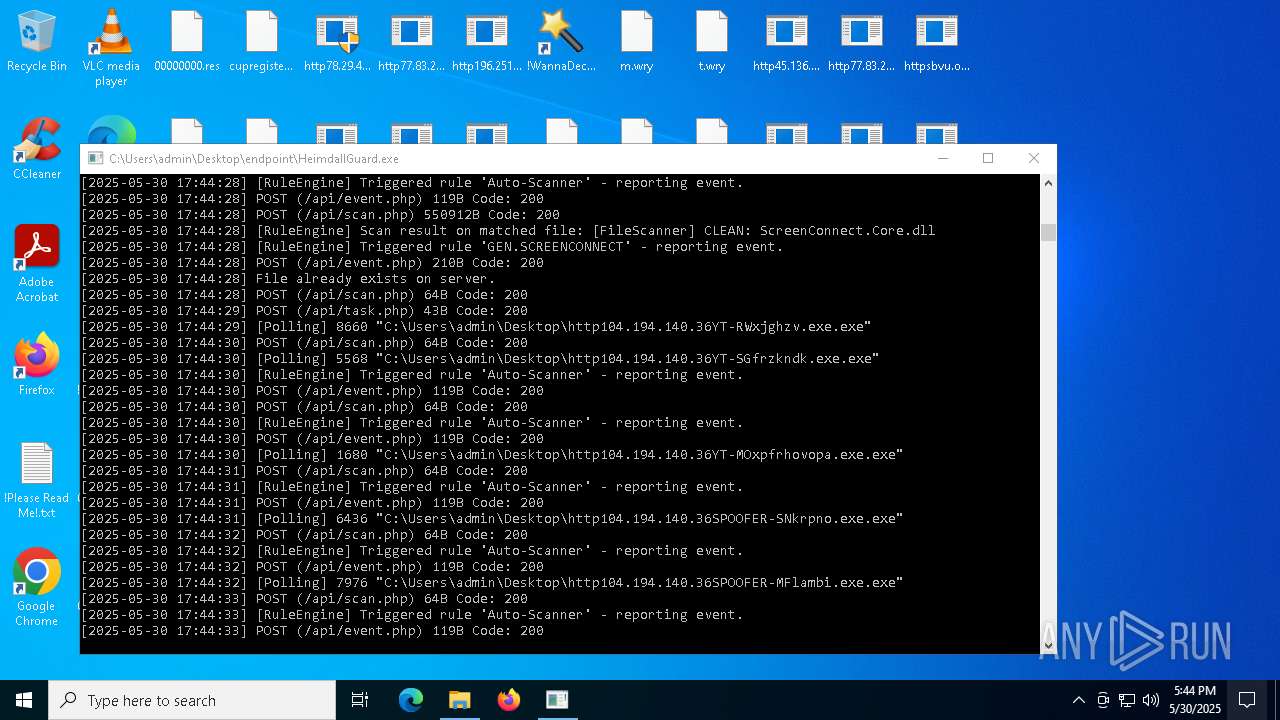
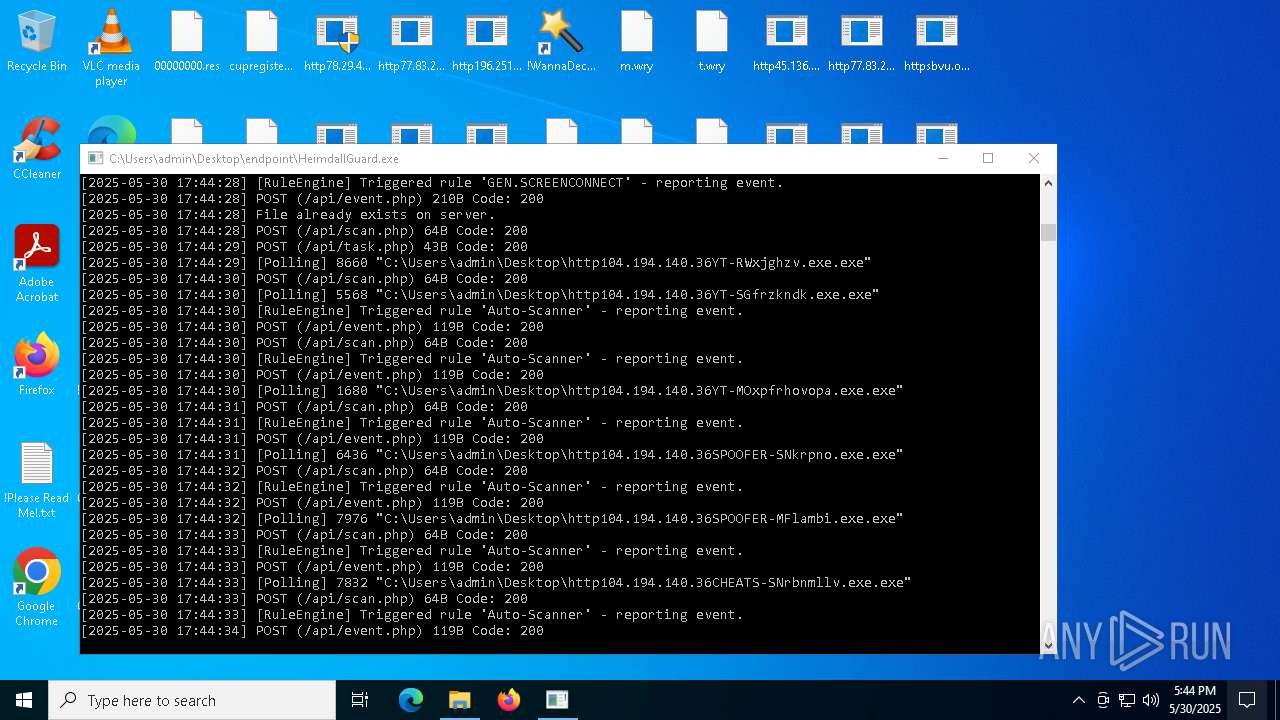
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 7260)
Changes the autorun value in the registry
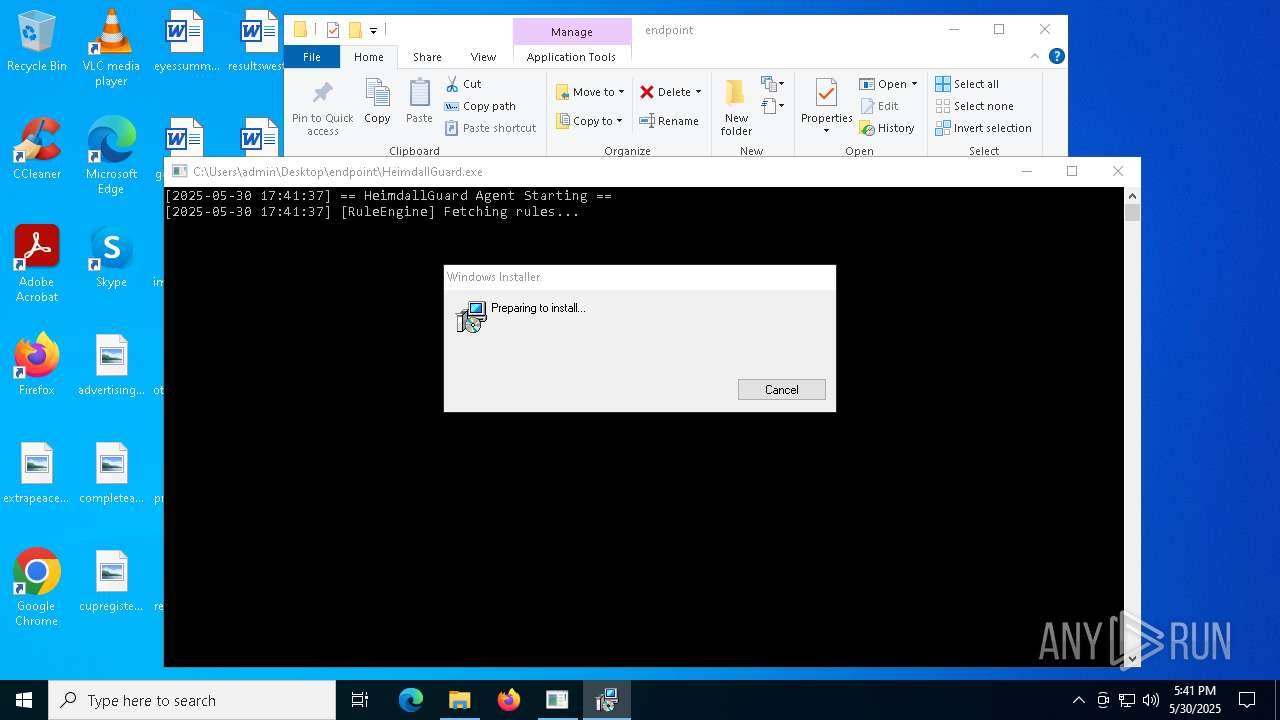
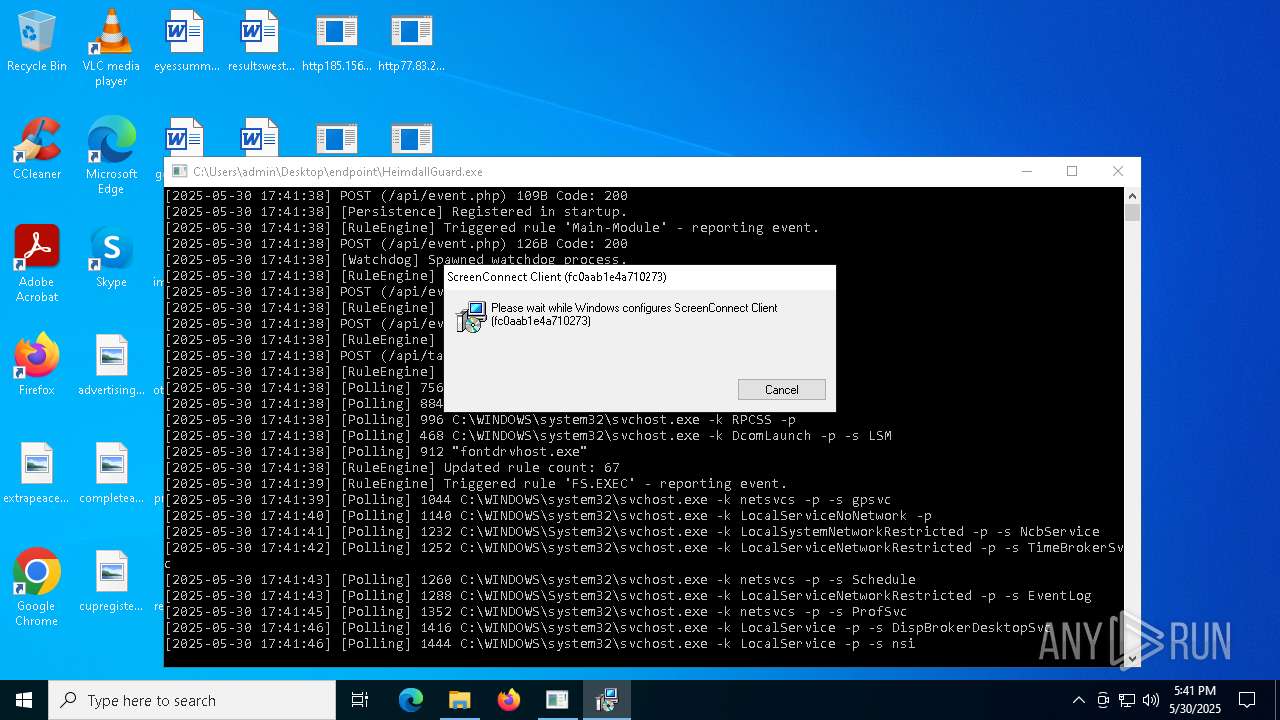
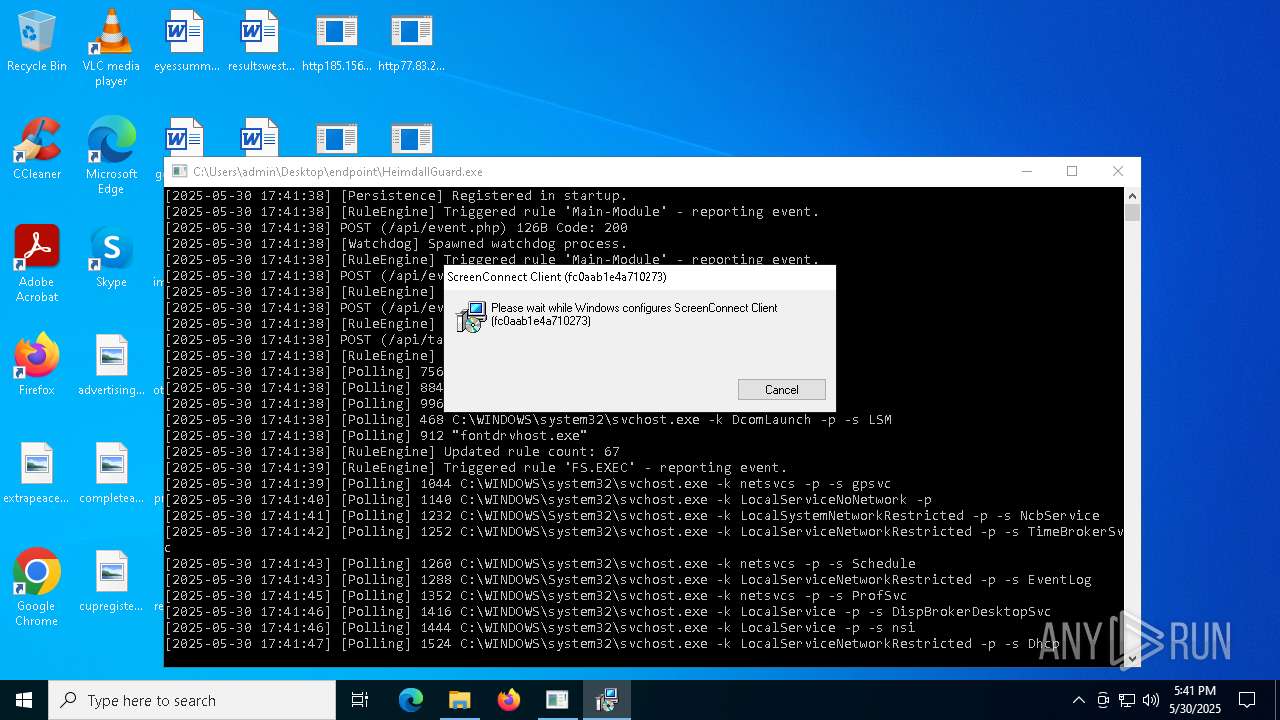
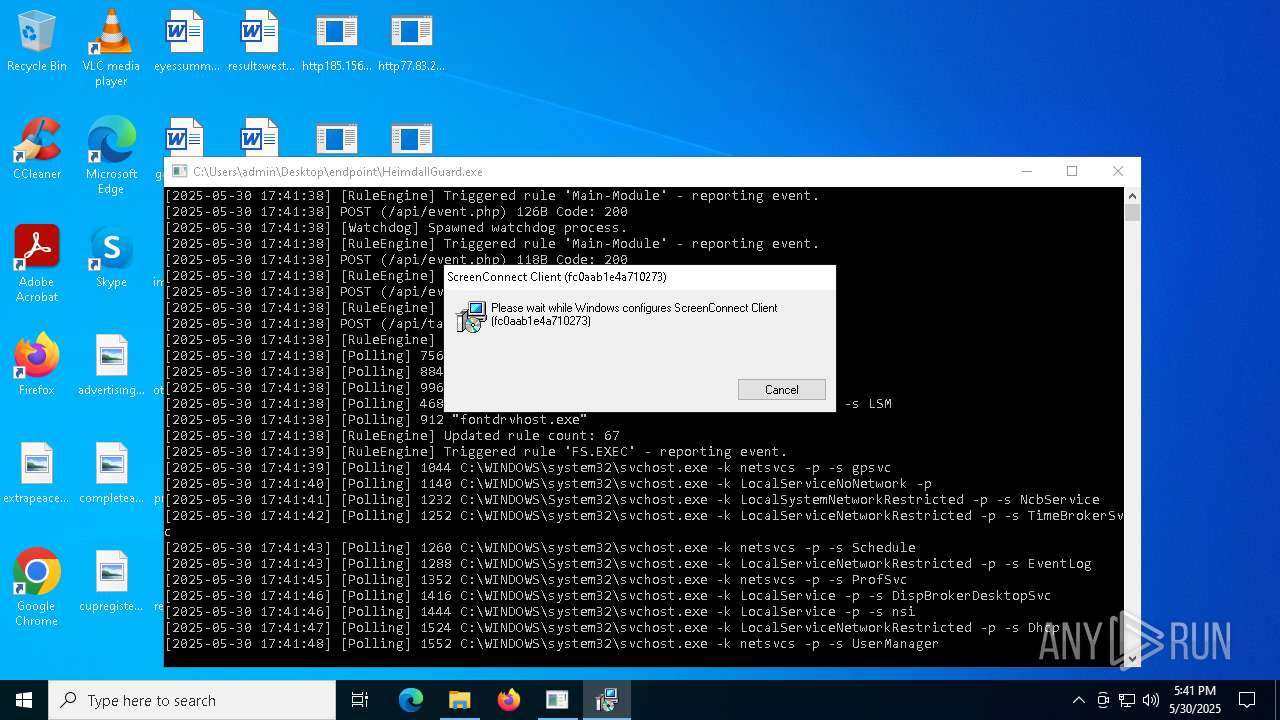
- HeimdallGuard.exe (PID: 5352)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
Connects to the CnC server
- svchost.exe (PID: 2196)
GENERIC has been found (auto)
- http107.173.47.141125dllhost.exe.exe (PID: 4424)
STEGOCAMPAIGN has been detected (SURICATA)
- bomb.exe (PID: 4020)
REVERSELOADER has been detected (SURICATA)
- bomb.exe (PID: 4020)
ASYNCRAT has been detected (SURICATA)
- httpbkngnet.combgj3ckjg.exe.exe (PID: 8220)
BRAODO has been found (auto)
- bomb.exe (PID: 4020)
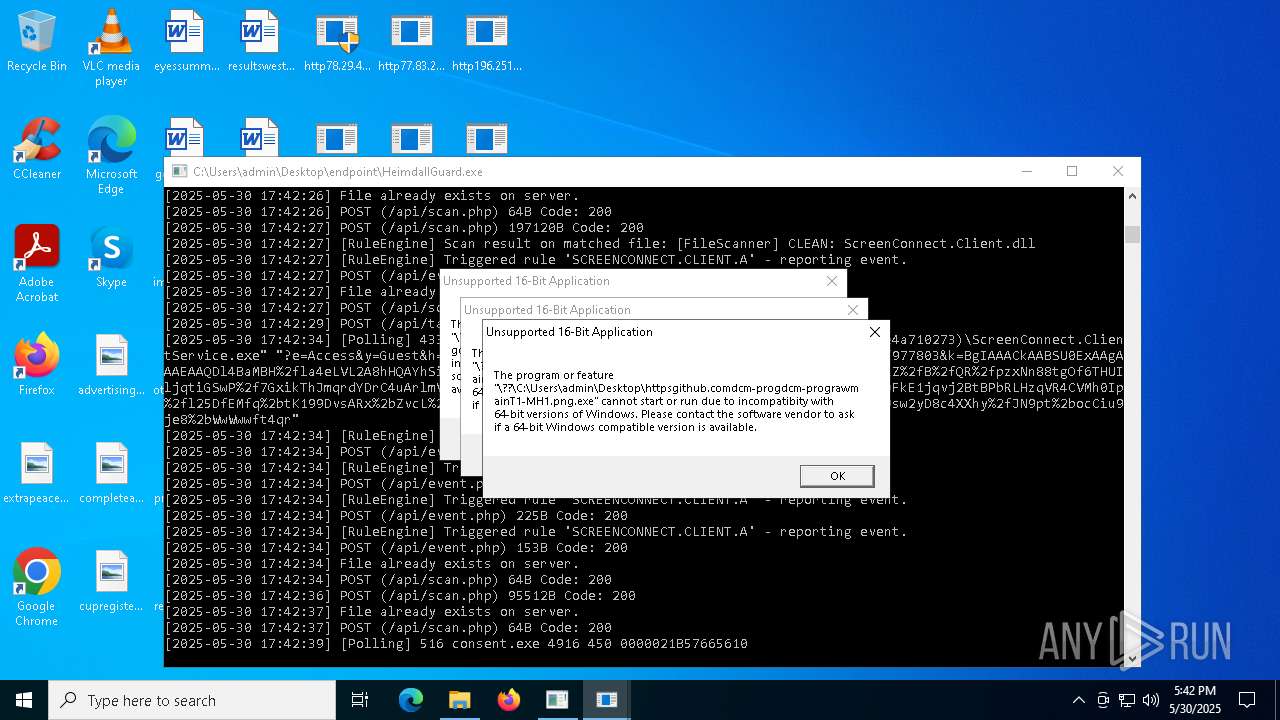
Uses Task Scheduler to run other applications
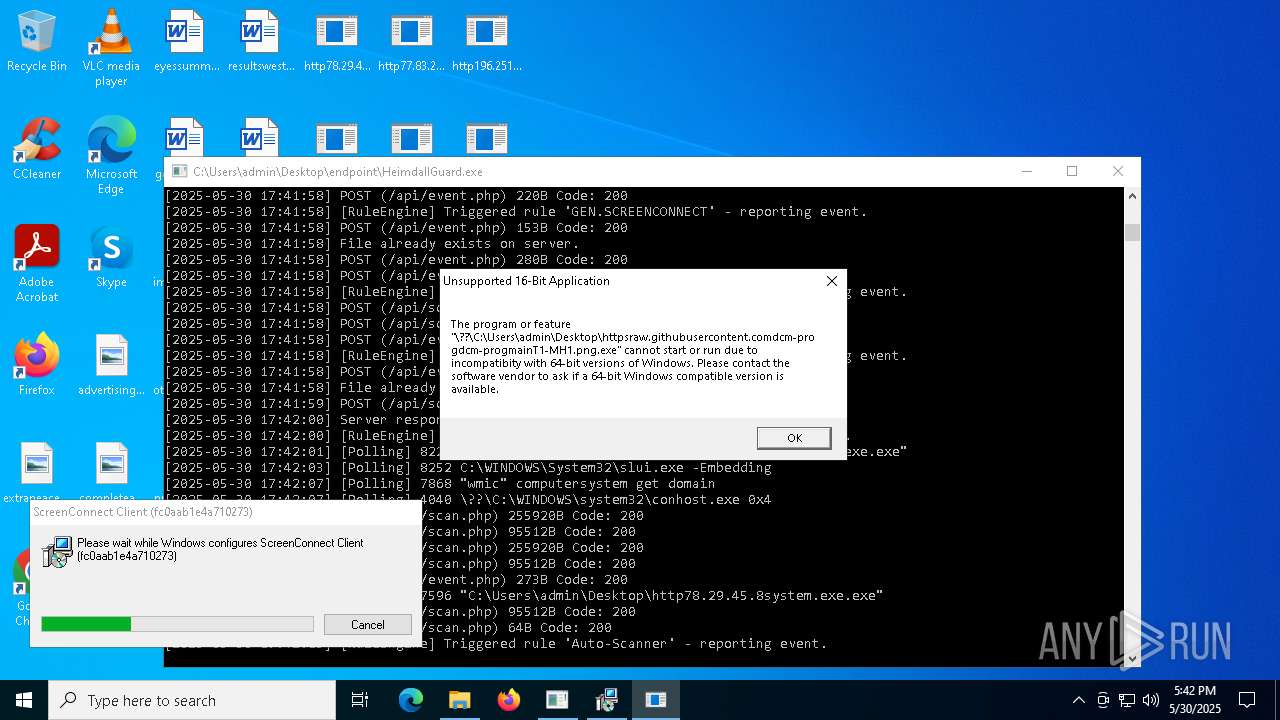
- http78.29.45.8Installer.exe.exe (PID: 8096)
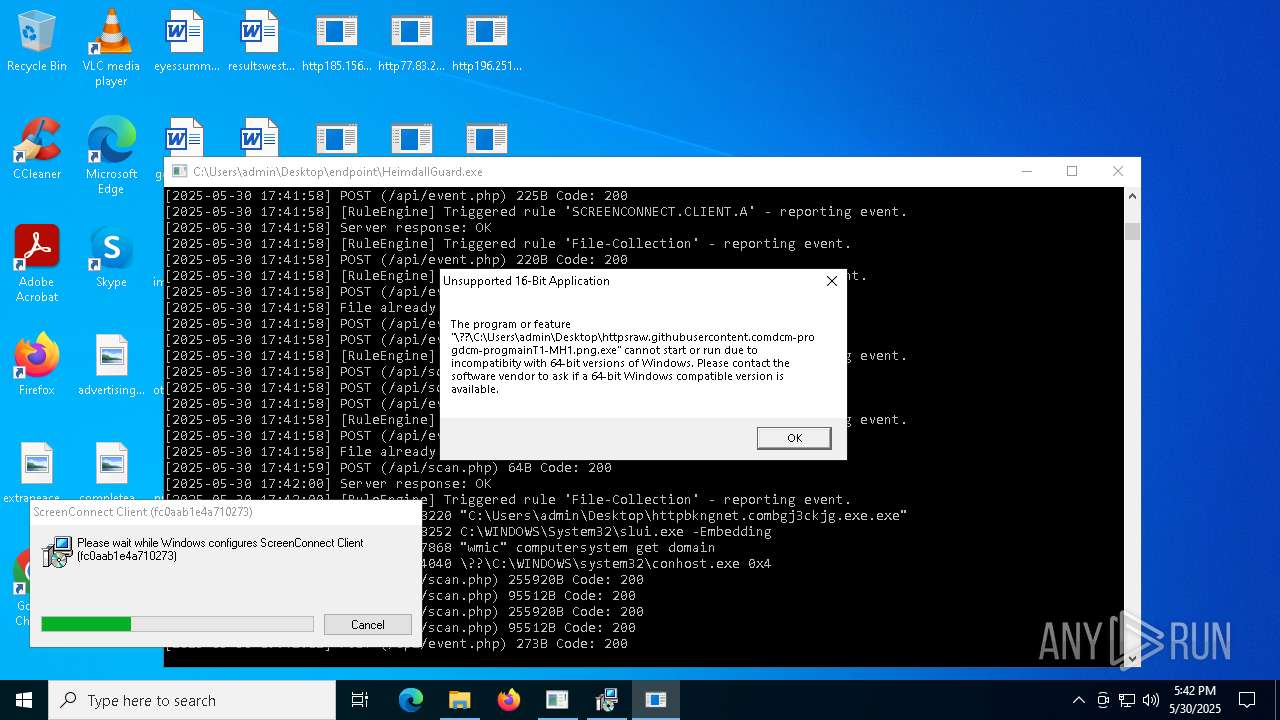
Drops known malicious image
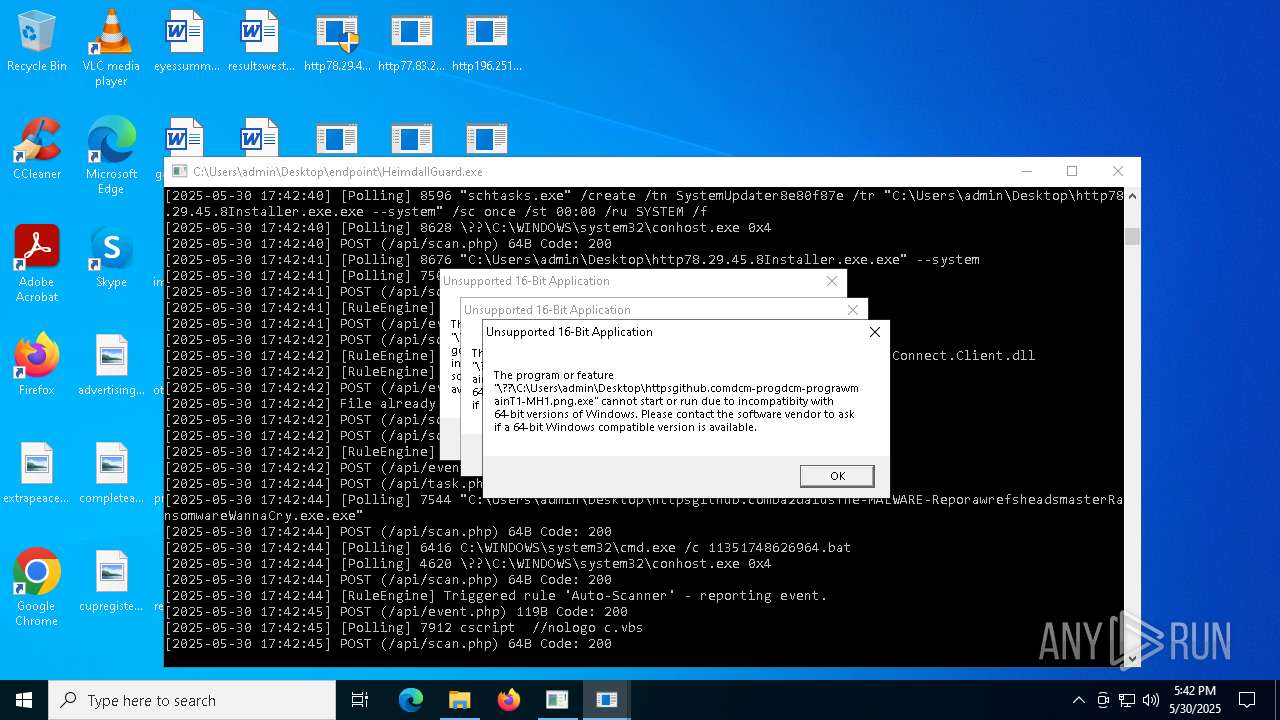
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
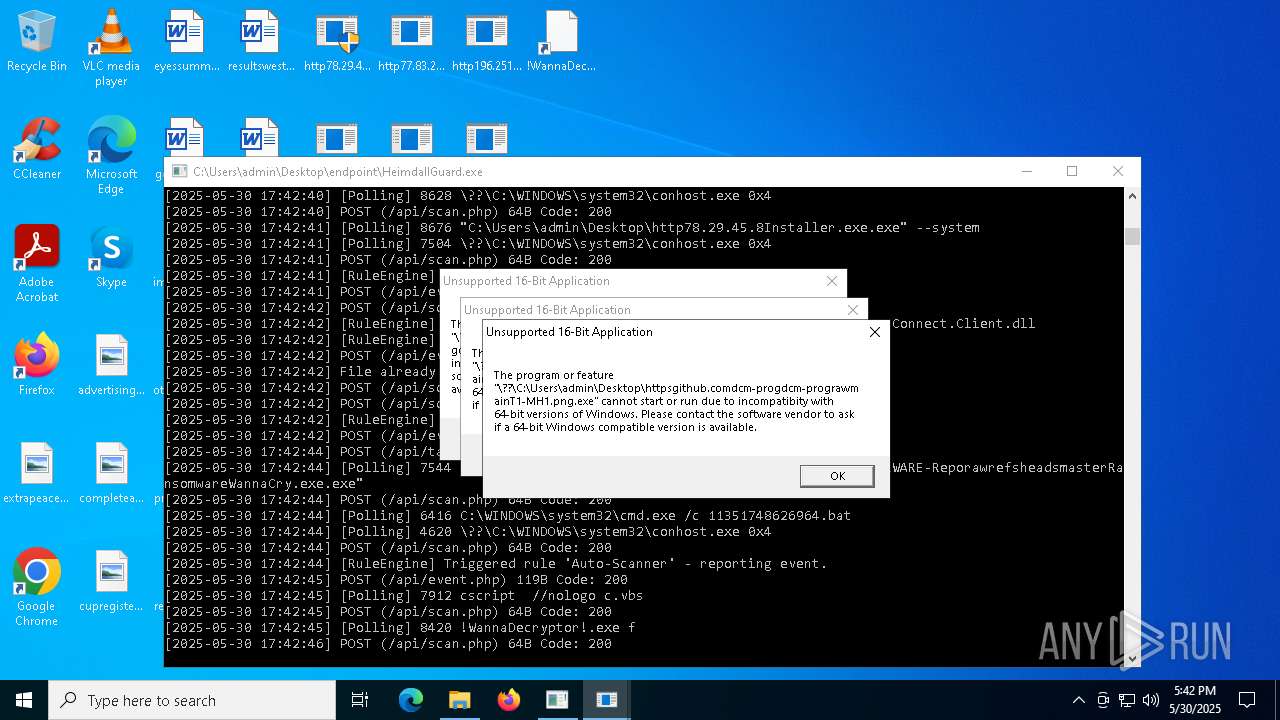
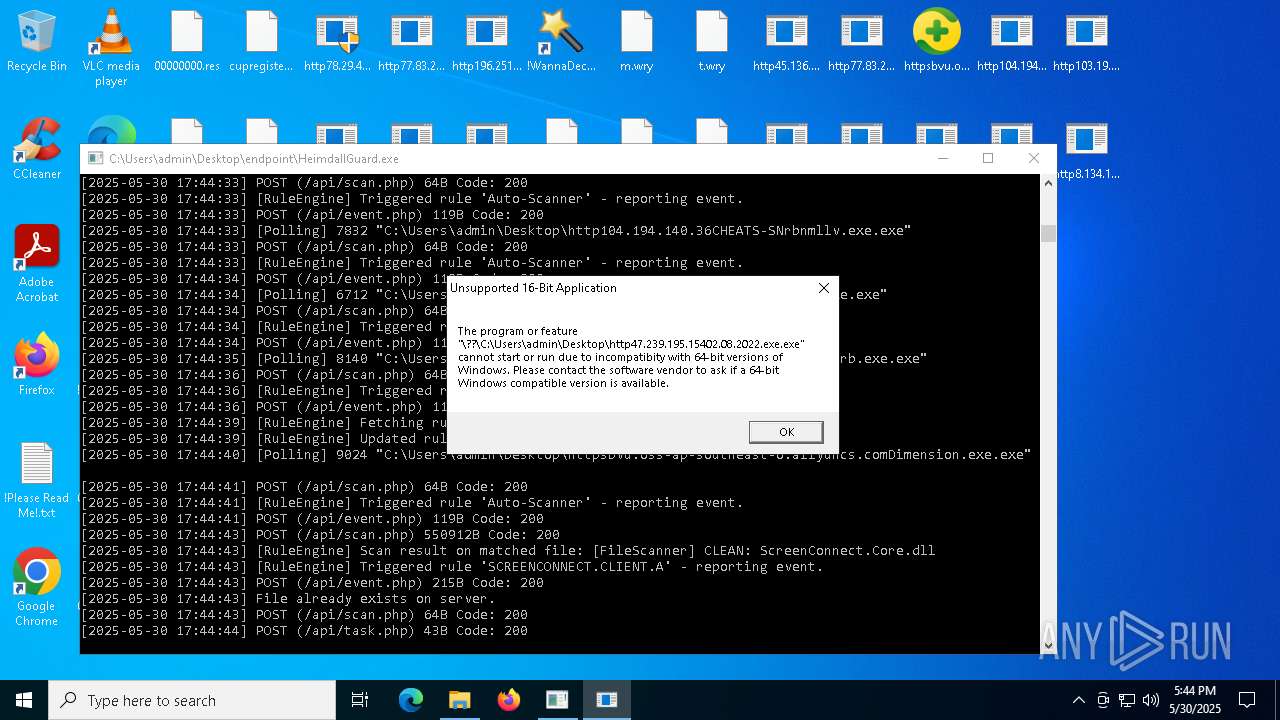
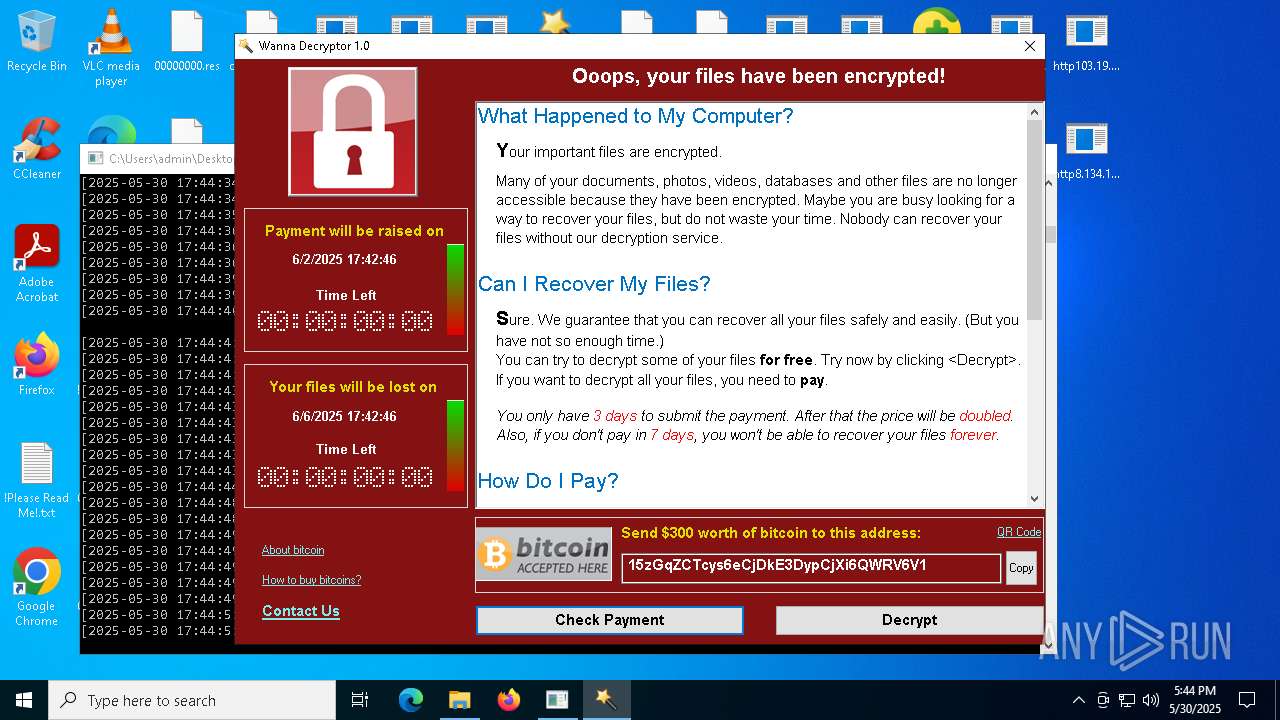
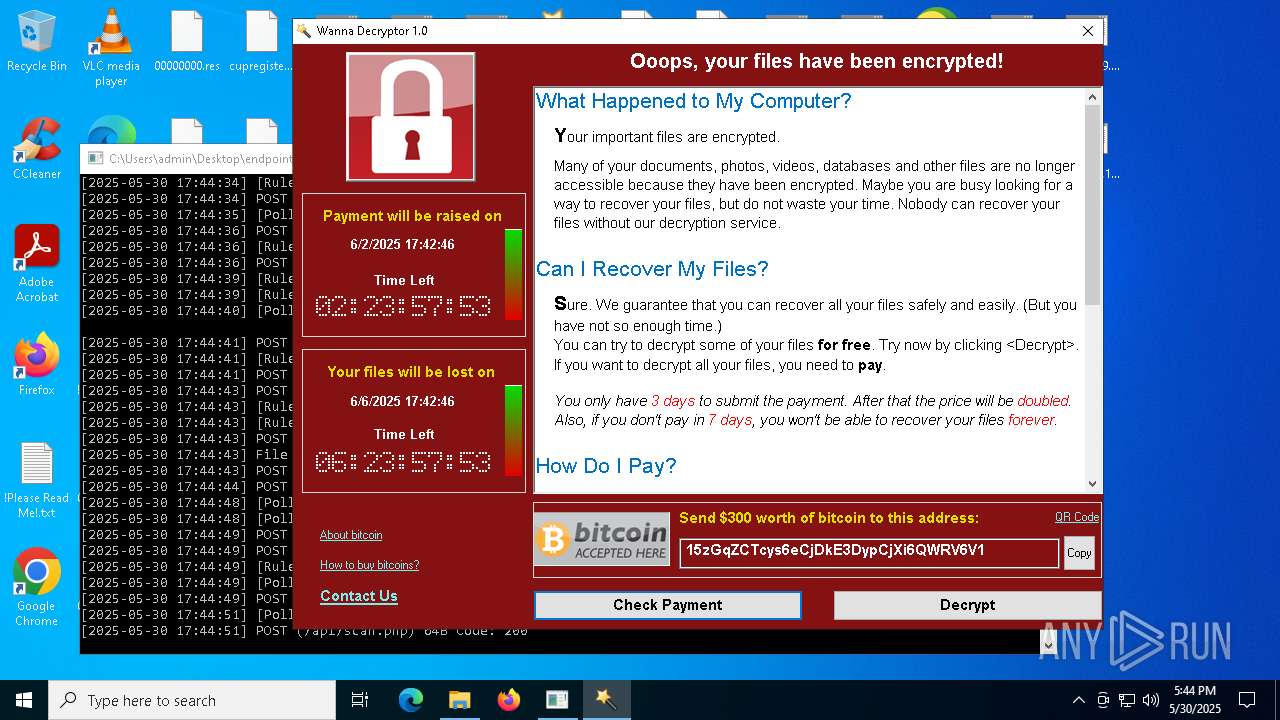
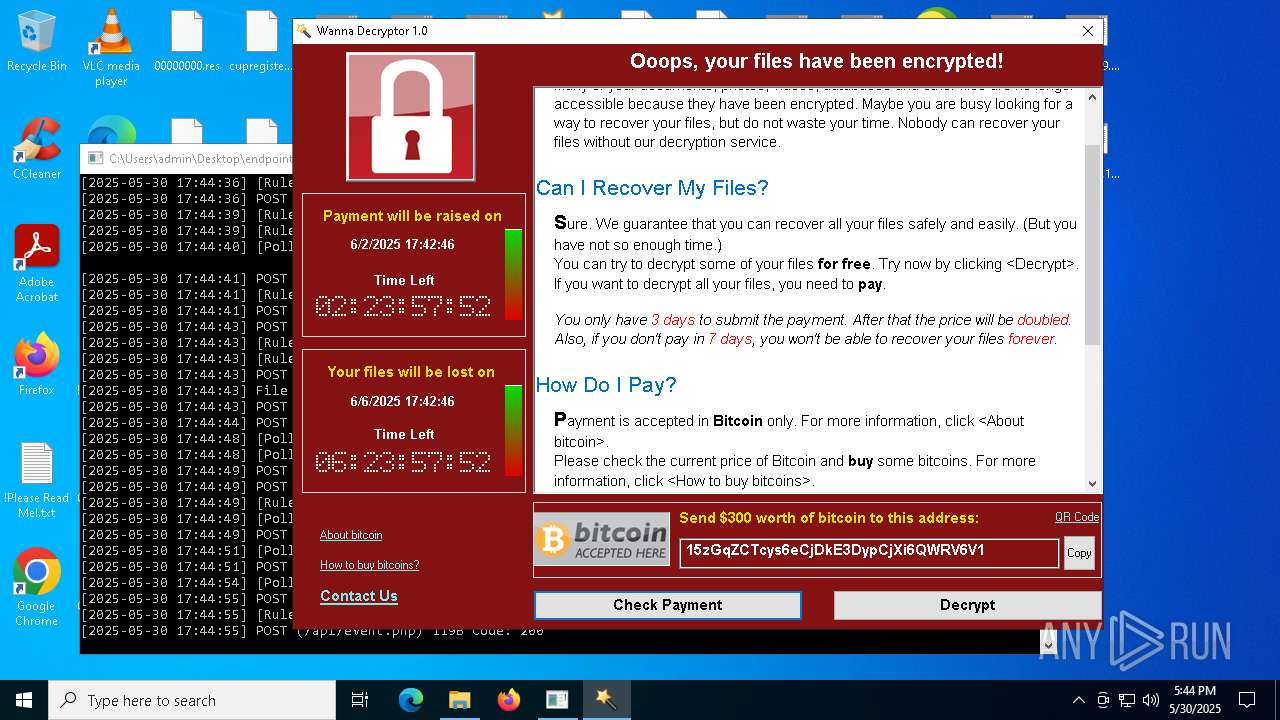
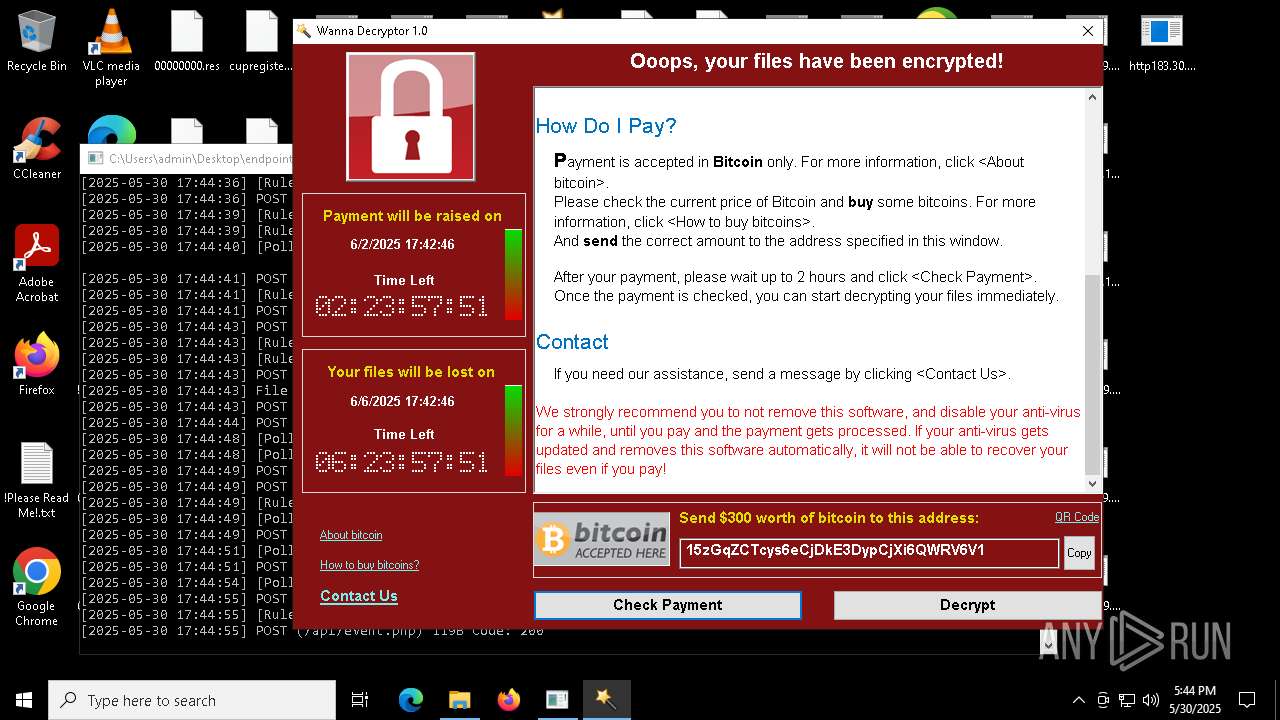
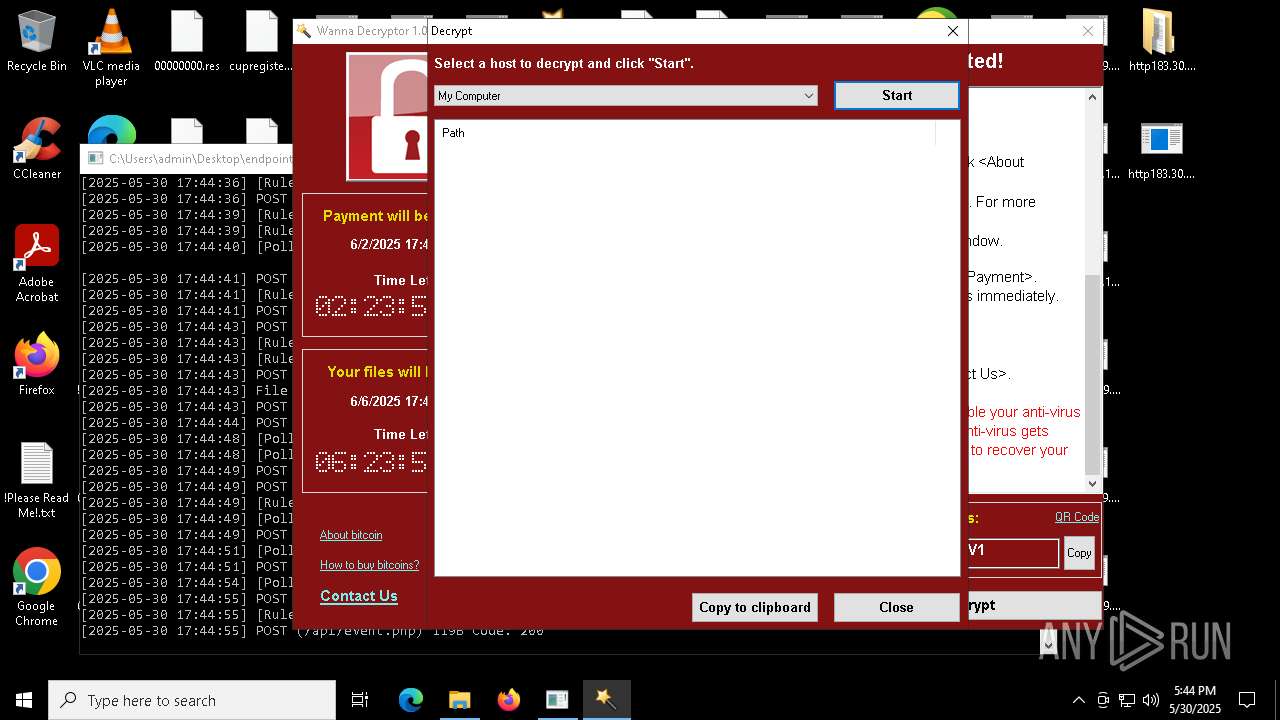
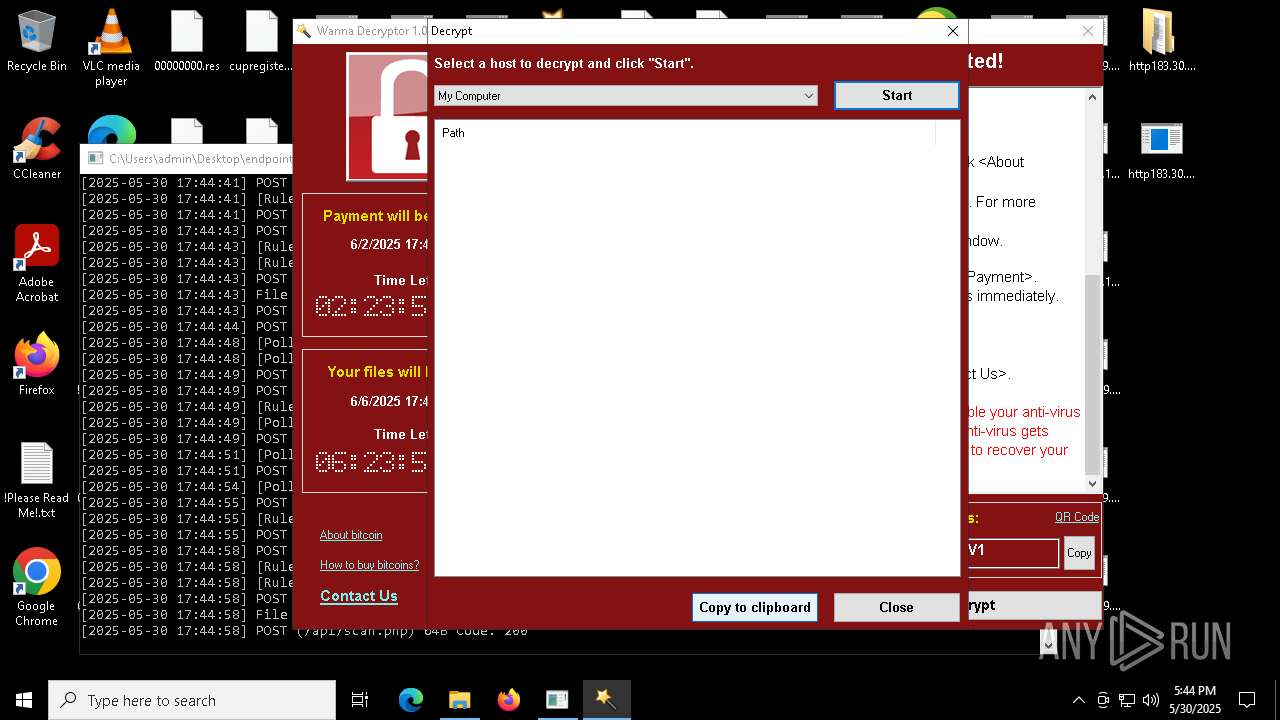
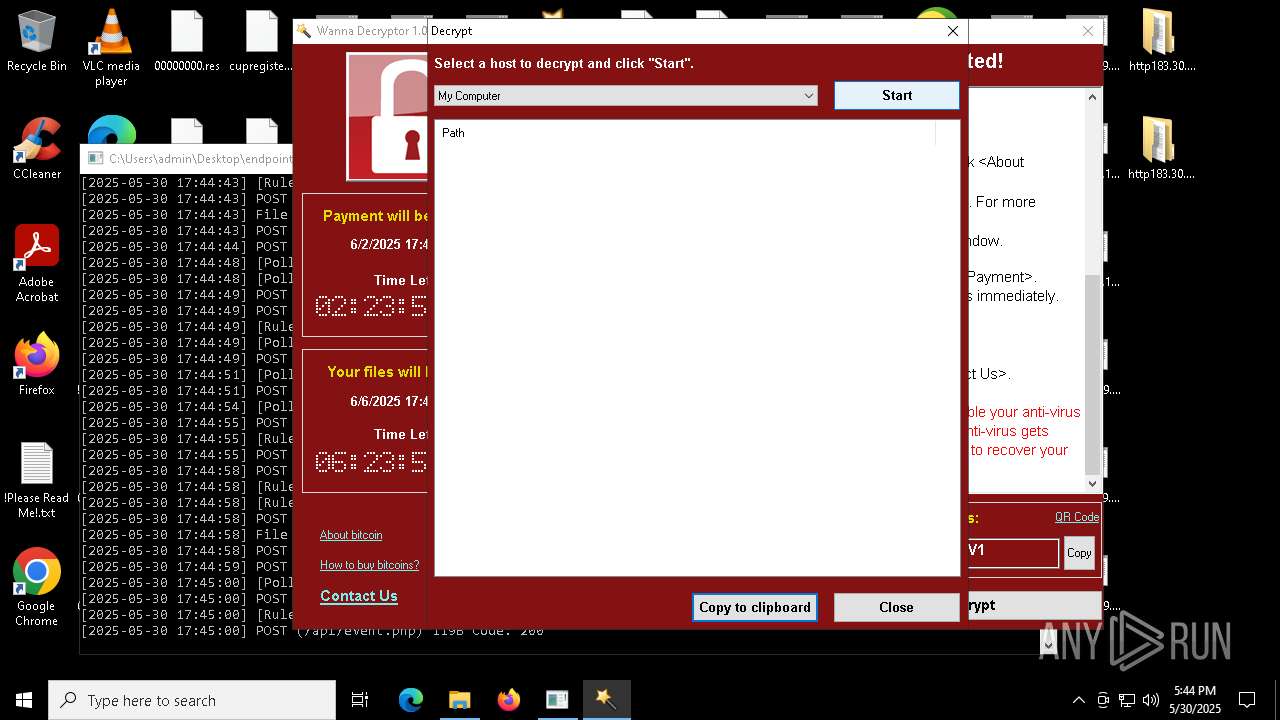
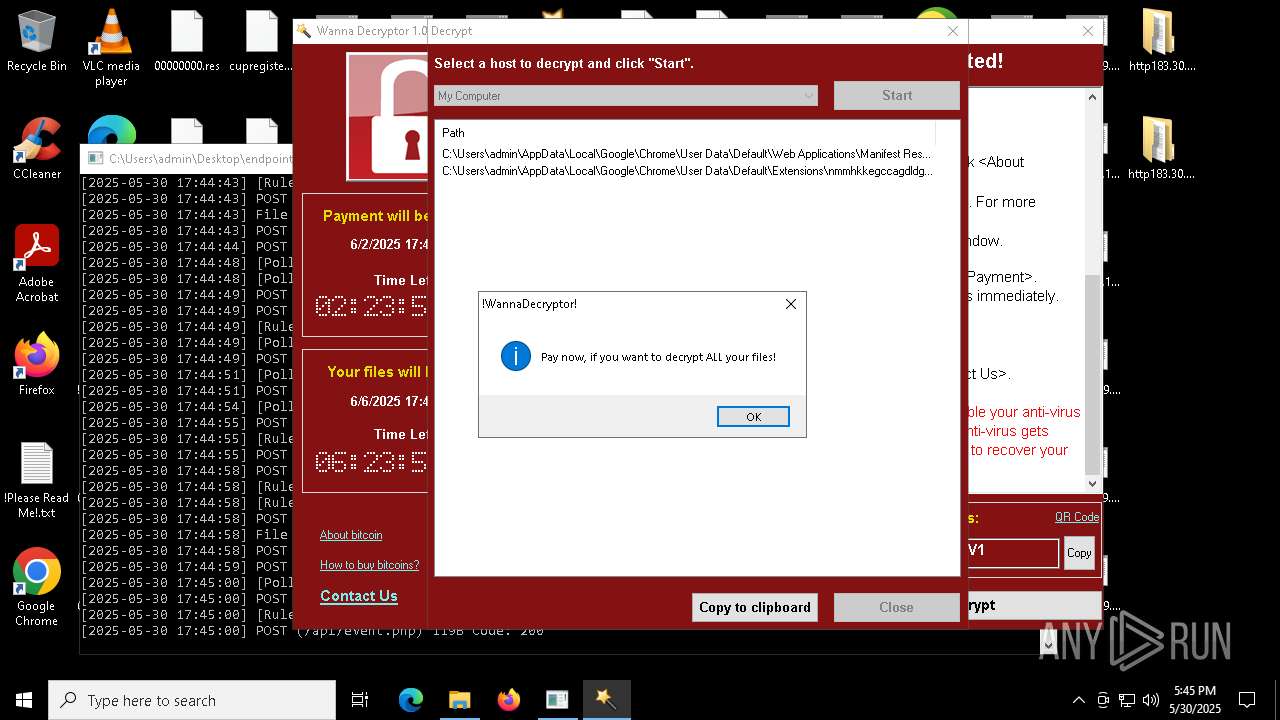
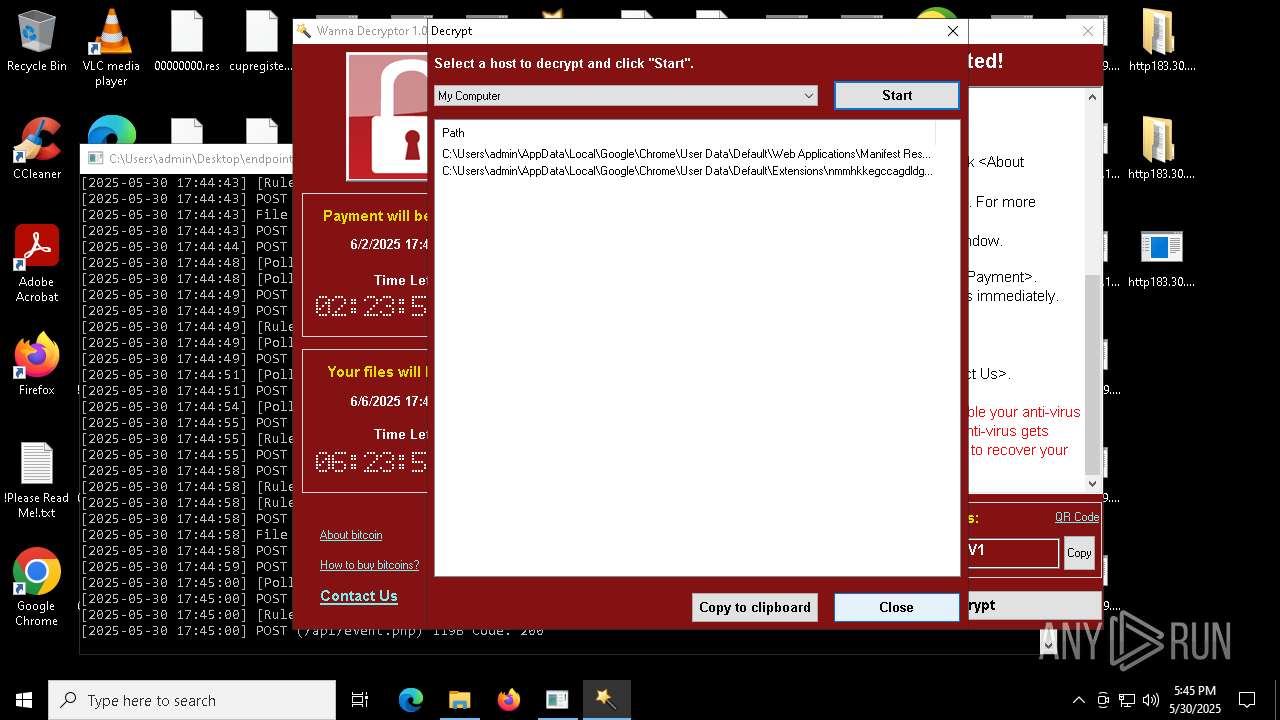
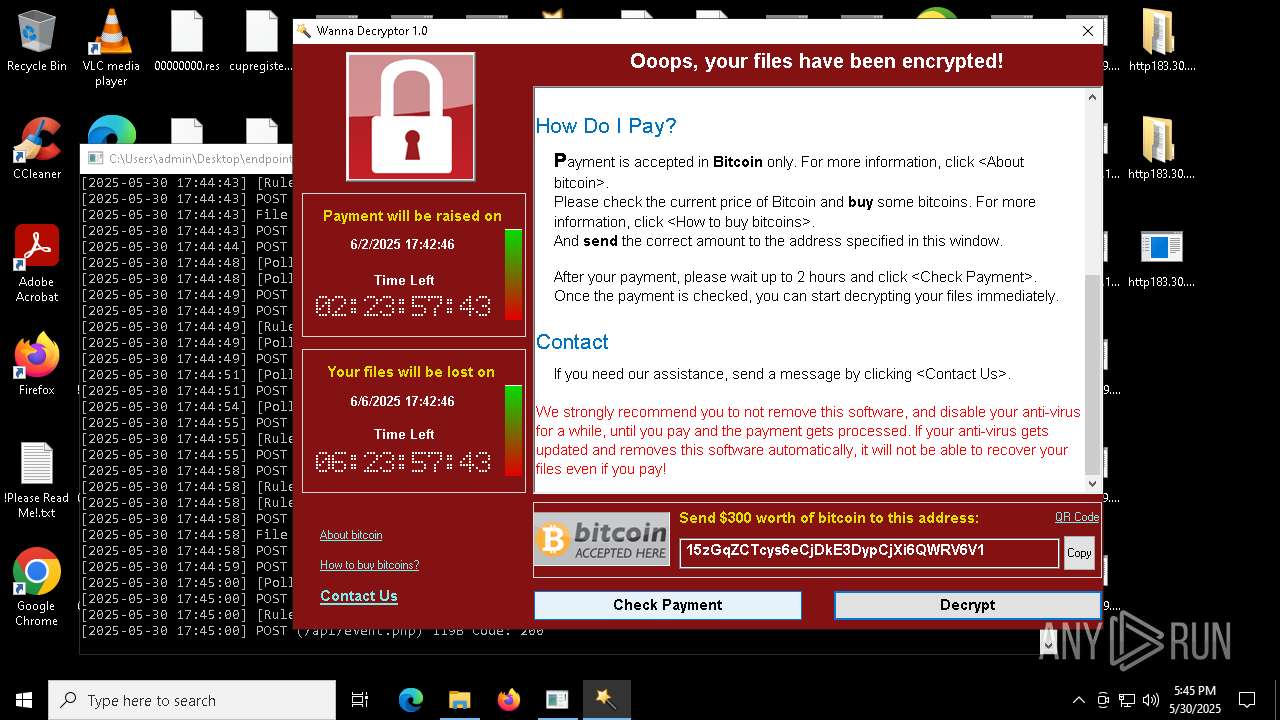
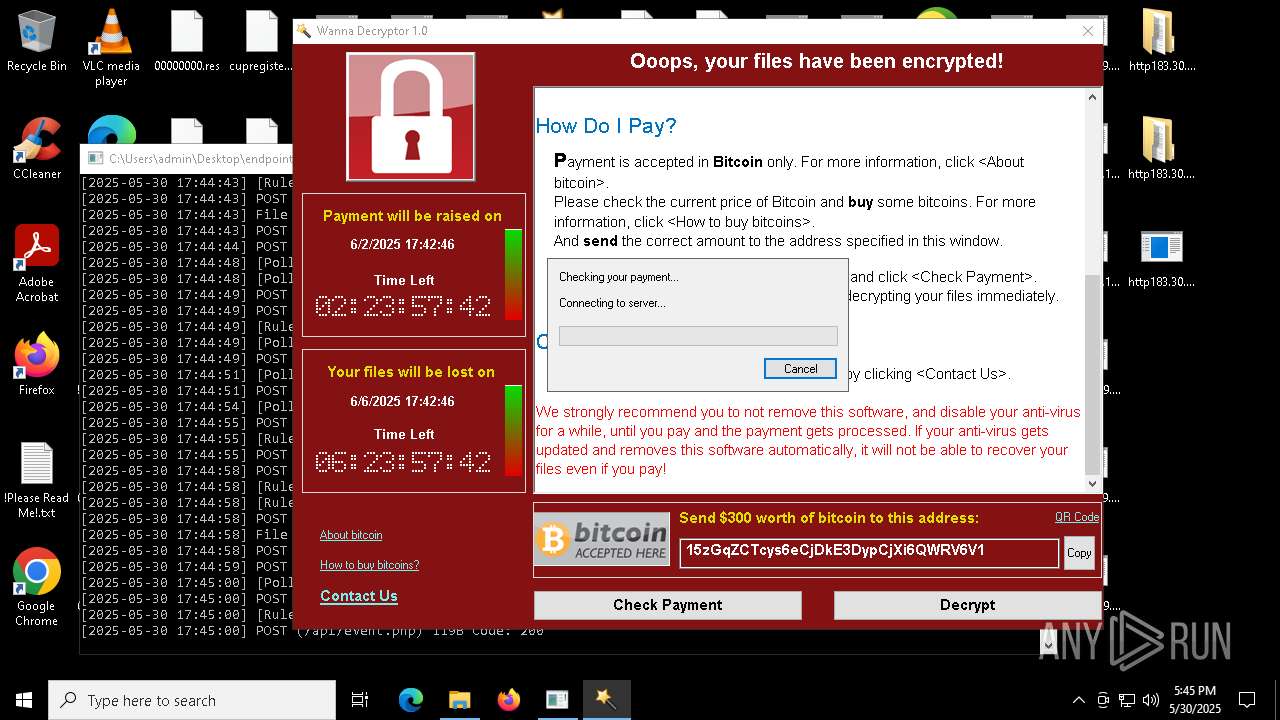
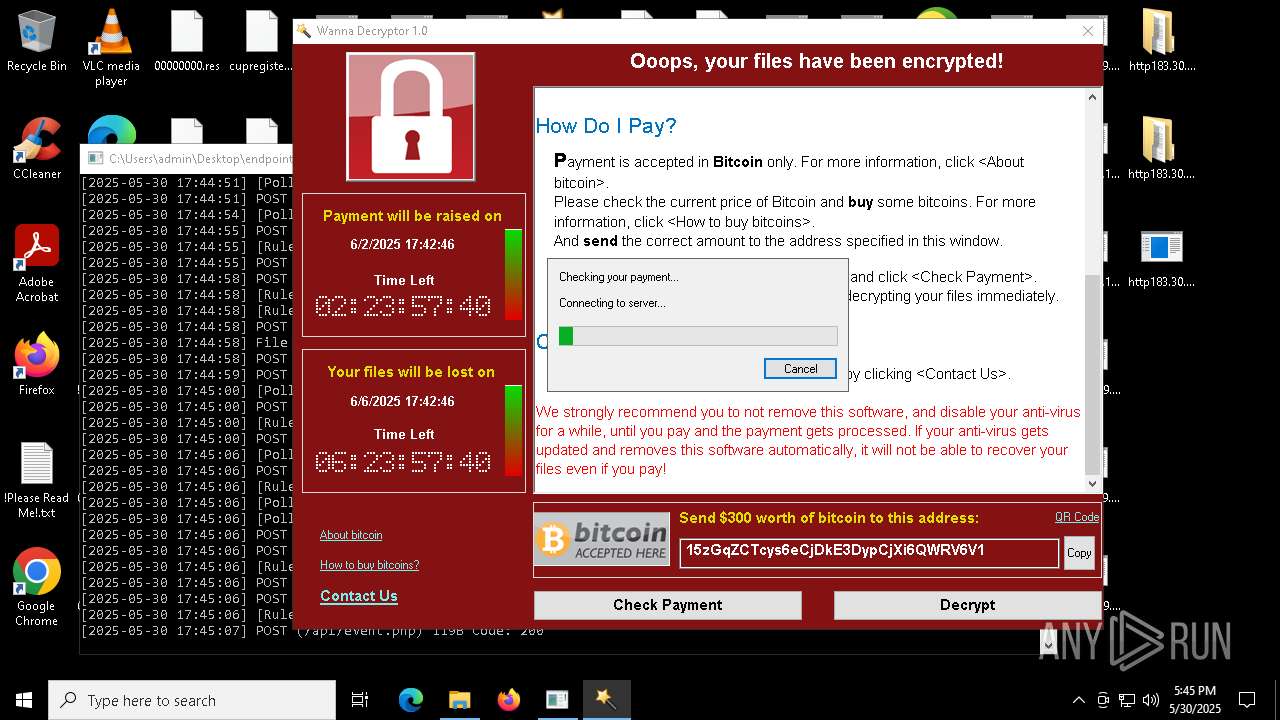
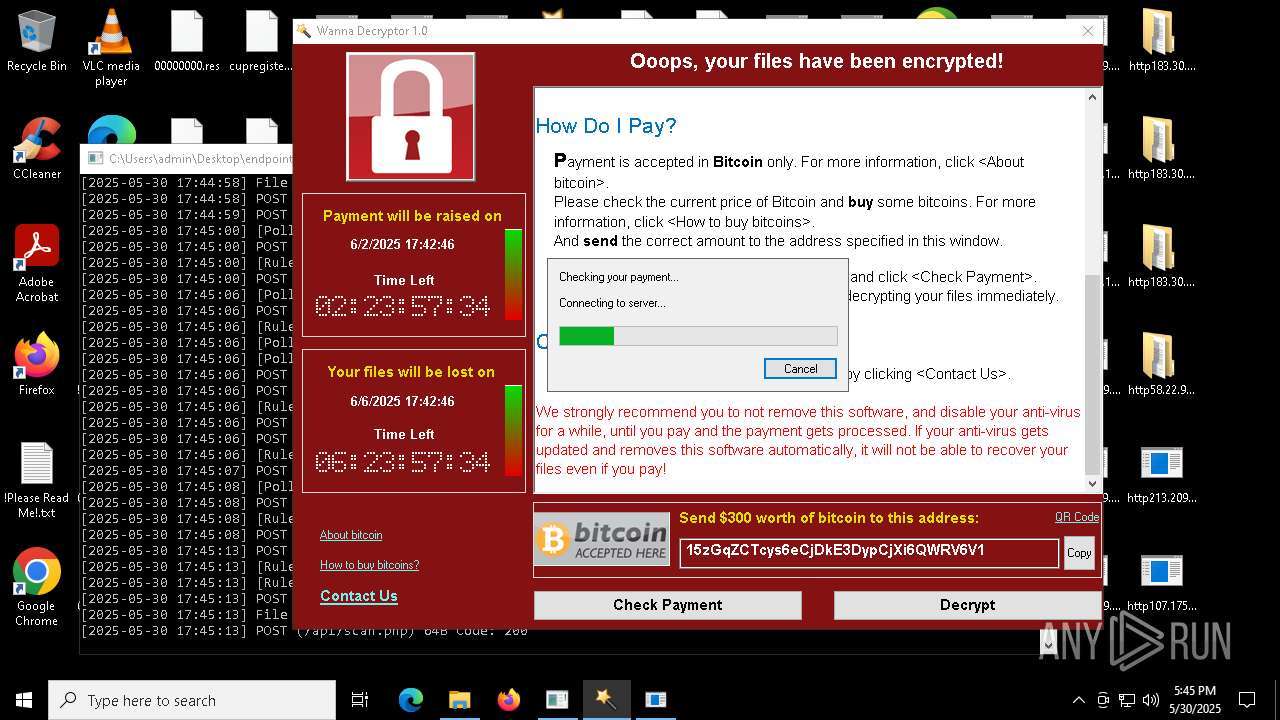
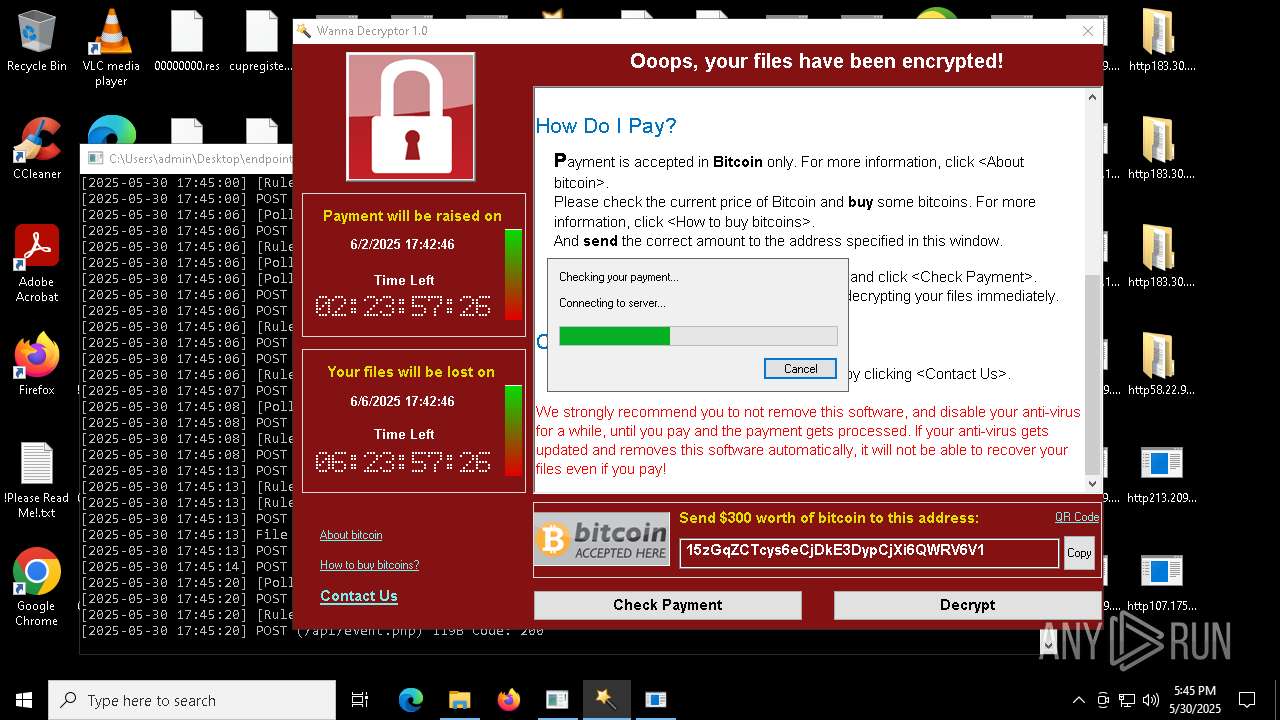
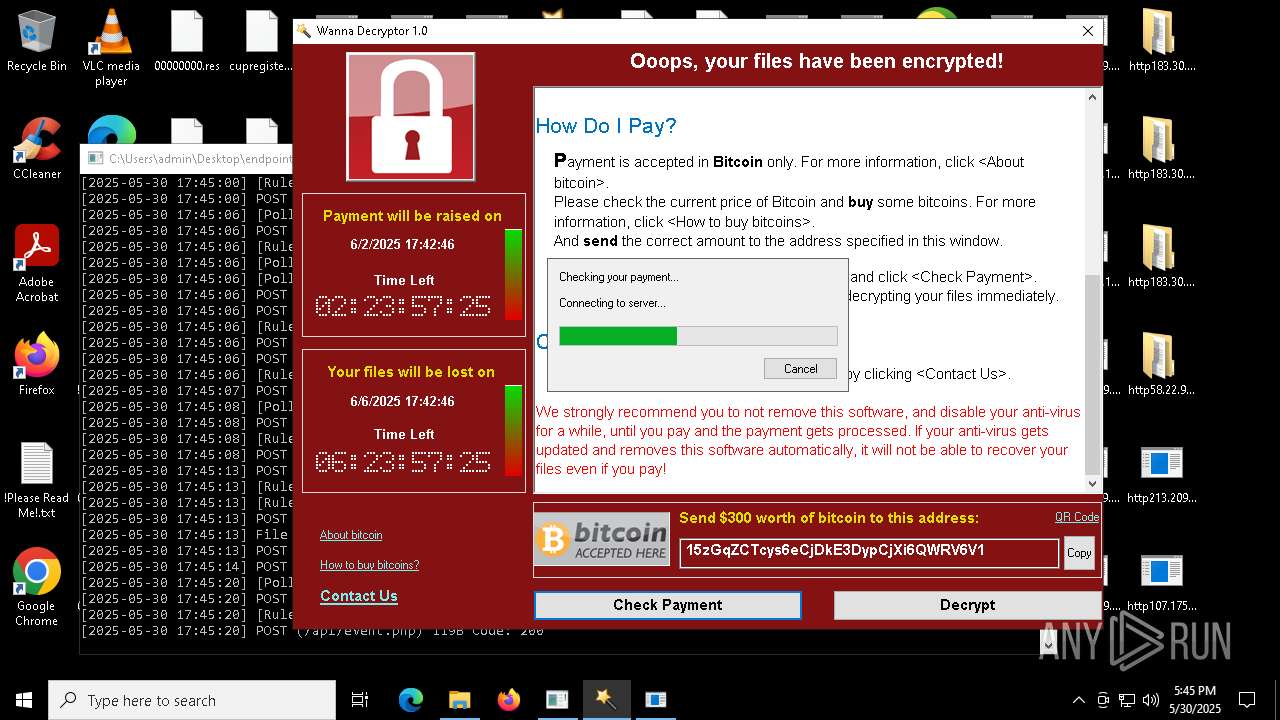
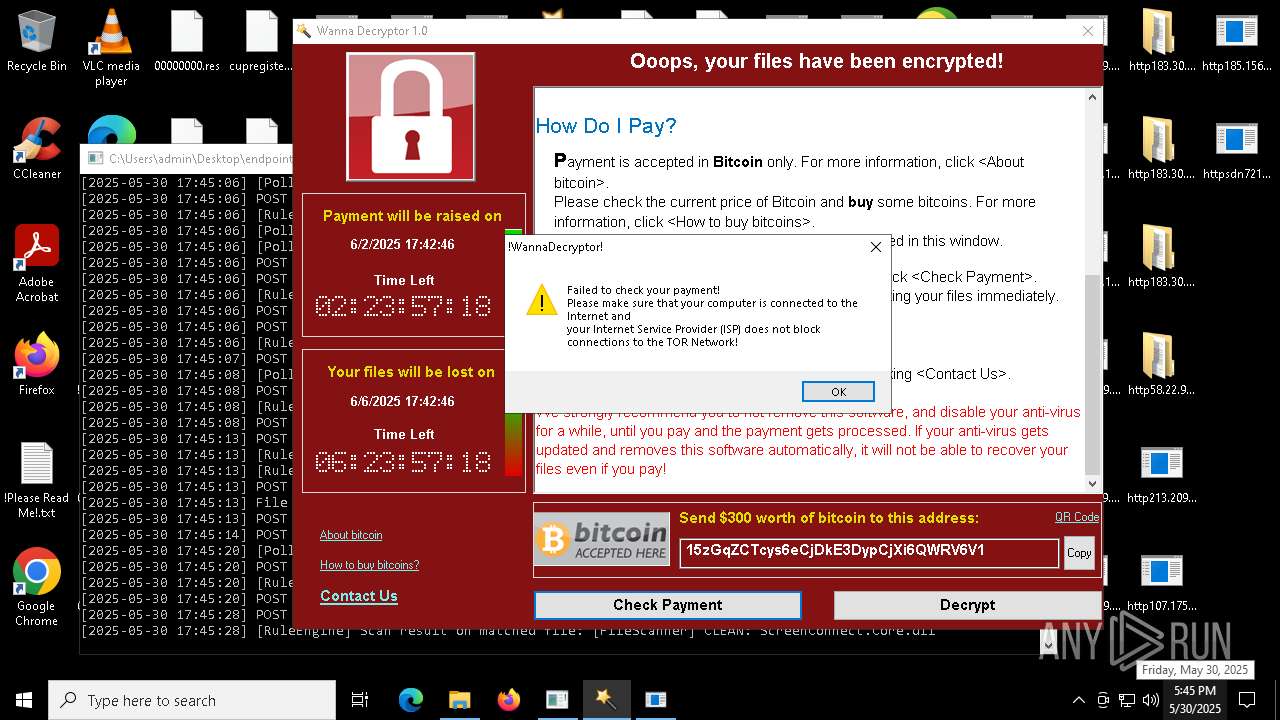
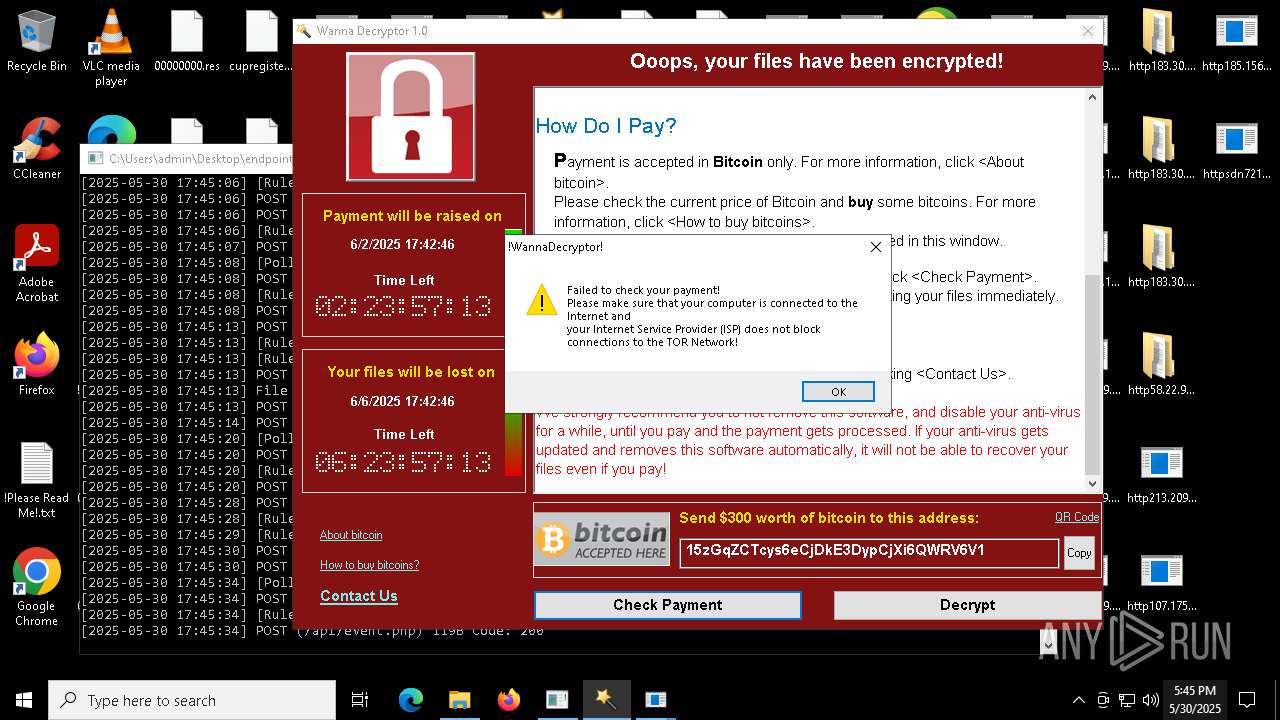
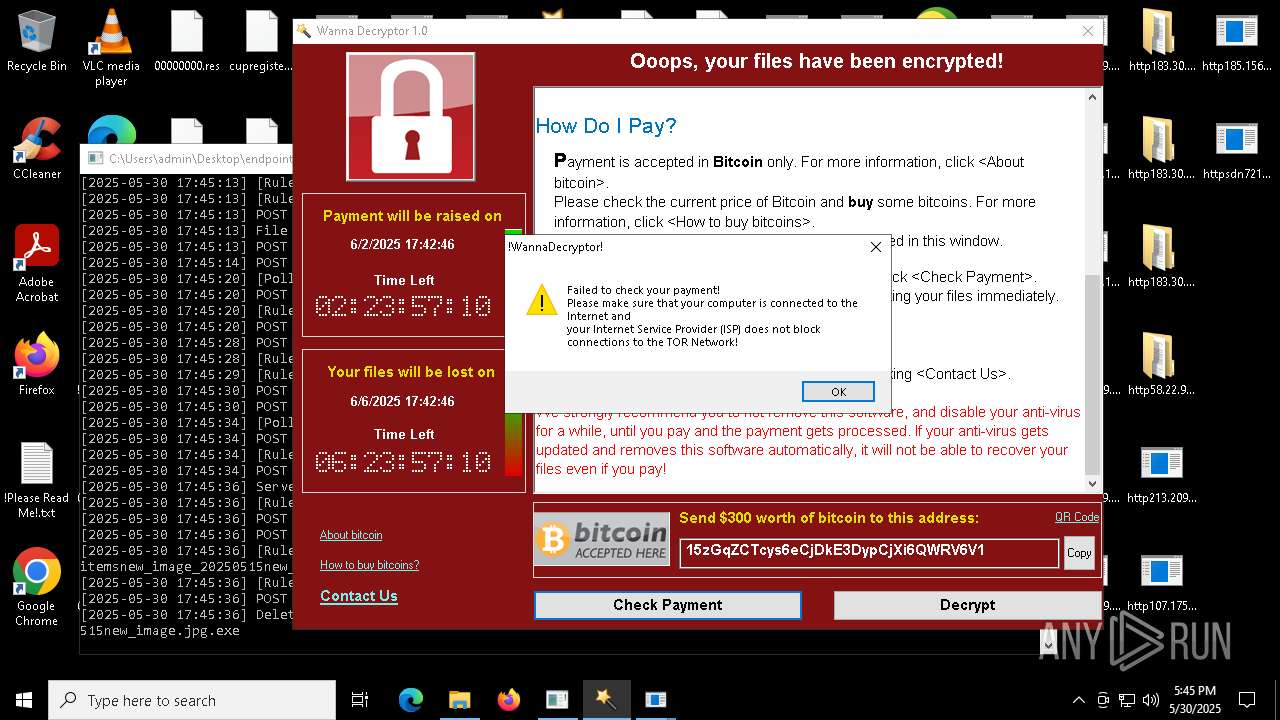
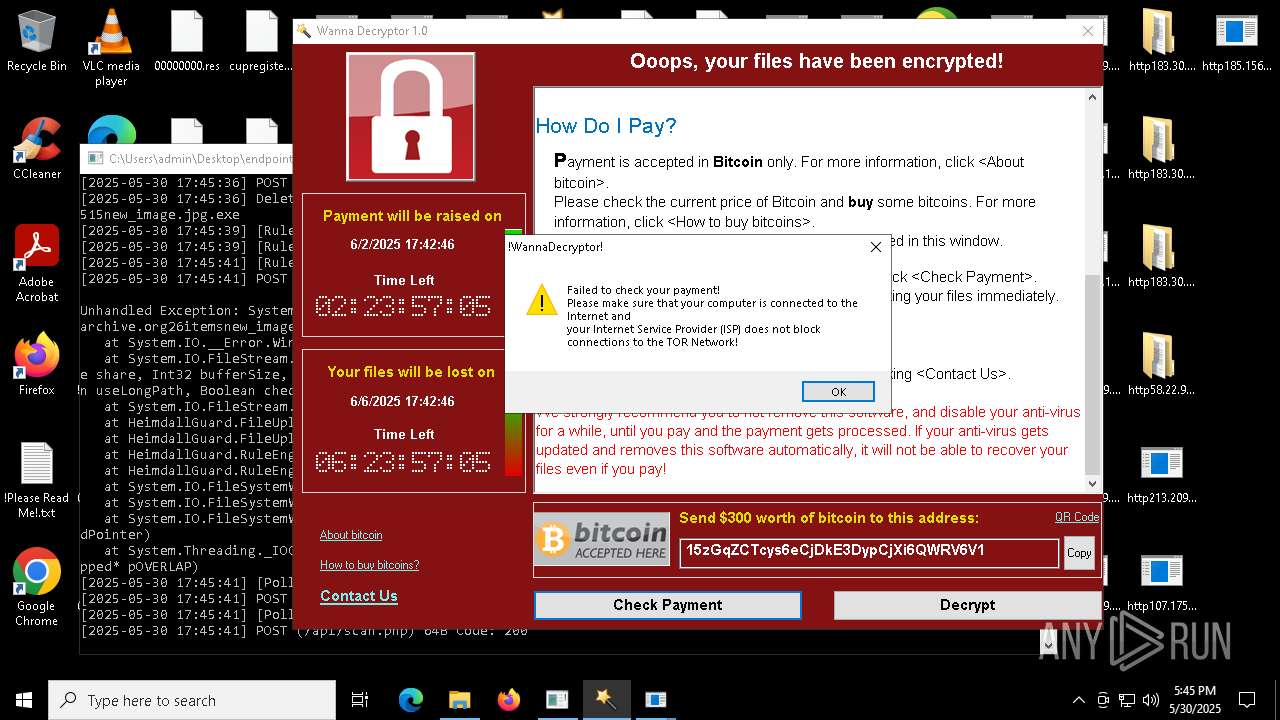
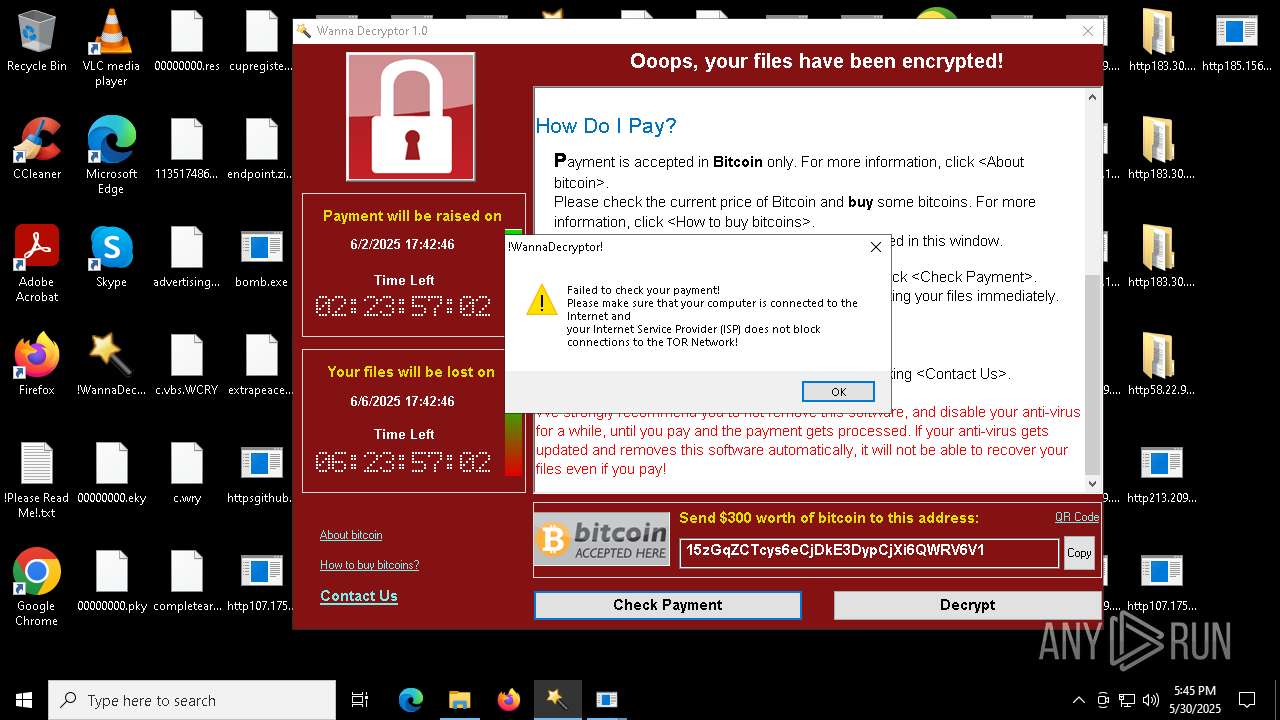
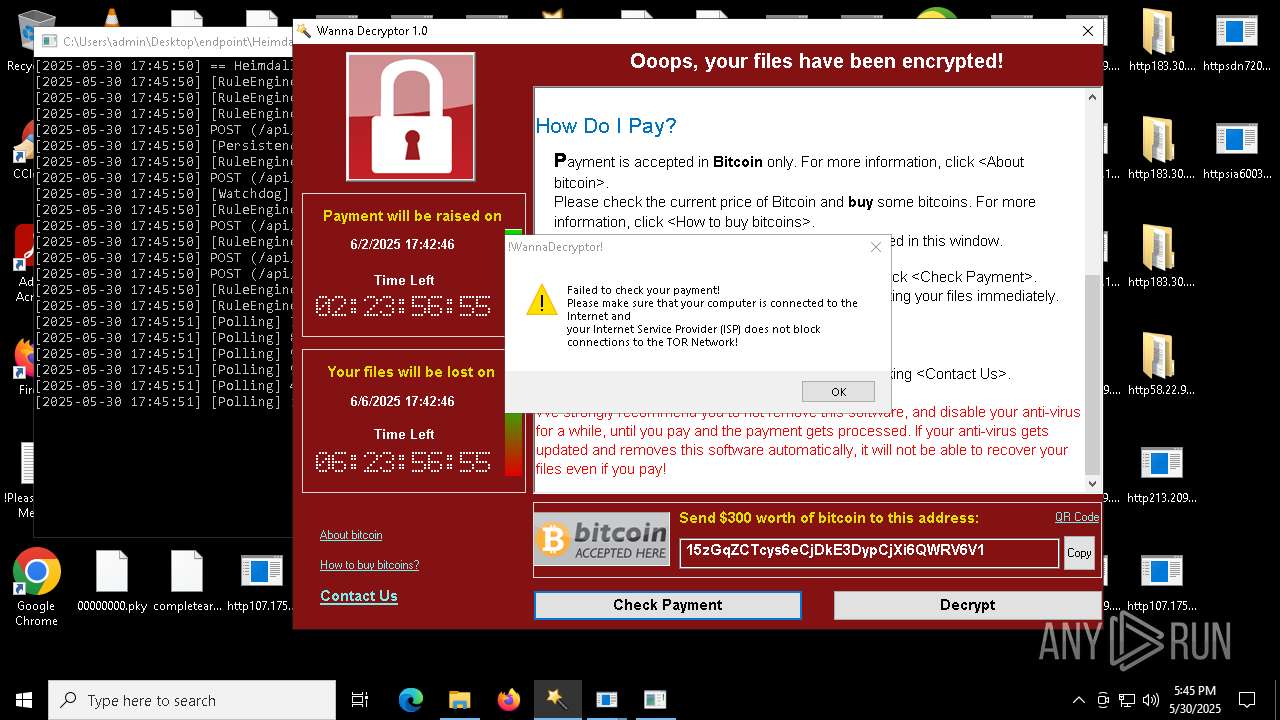
WannaCry Ransomware is detected
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
COINMINER has been found (auto)
- bomb.exe (PID: 4020)
Executing a file with an untrusted certificate
- httpsbvu.oss-ap-southeast-6.aliyuncs.comDimension.exe.exe (PID: 9024)
SUSPICIOUS
Reads the date of Windows installation
- bomb.exe (PID: 4020)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- dfsvc.exe (PID: 5400)
Reads security settings of Internet Explorer
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- ScreenConnect.ClientService.exe (PID: 8064)
- ScreenConnect.WindowsClient.exe (PID: 1660)
- ScreenConnect.ClientService.exe (PID: 7260)
- http77.83.207.69incClientSetup1.exe.exe (PID: 7456)
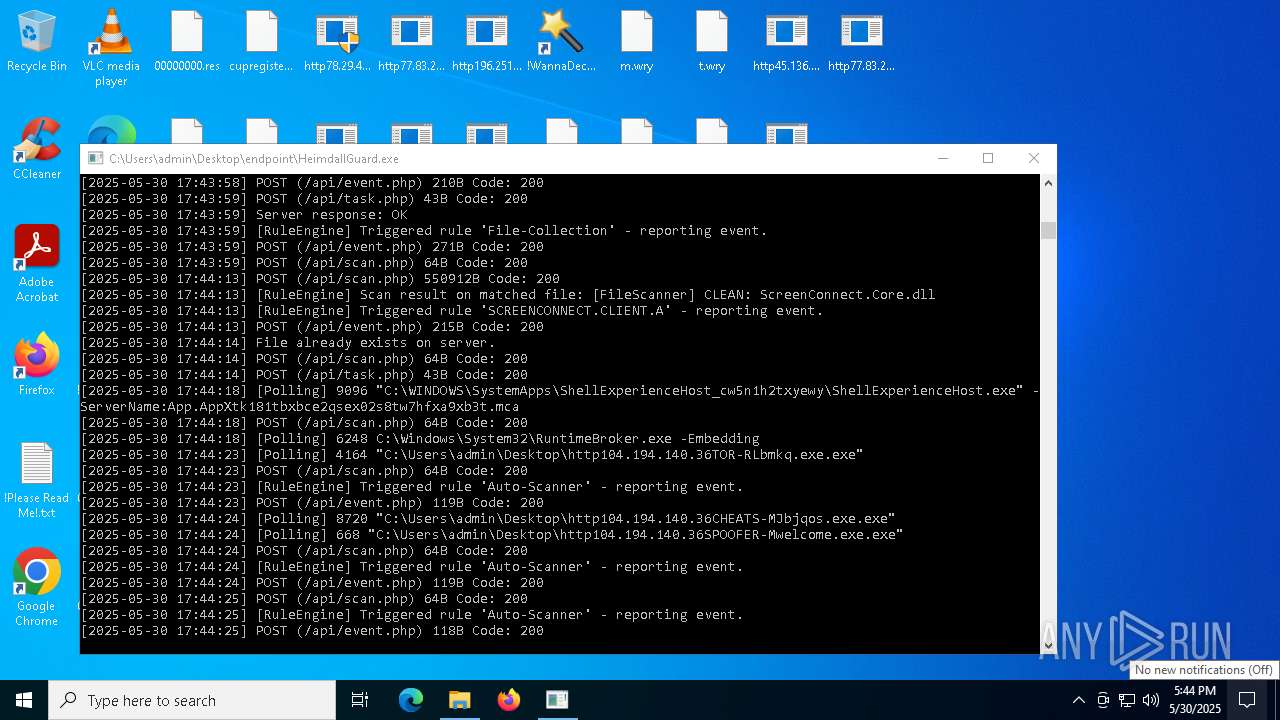
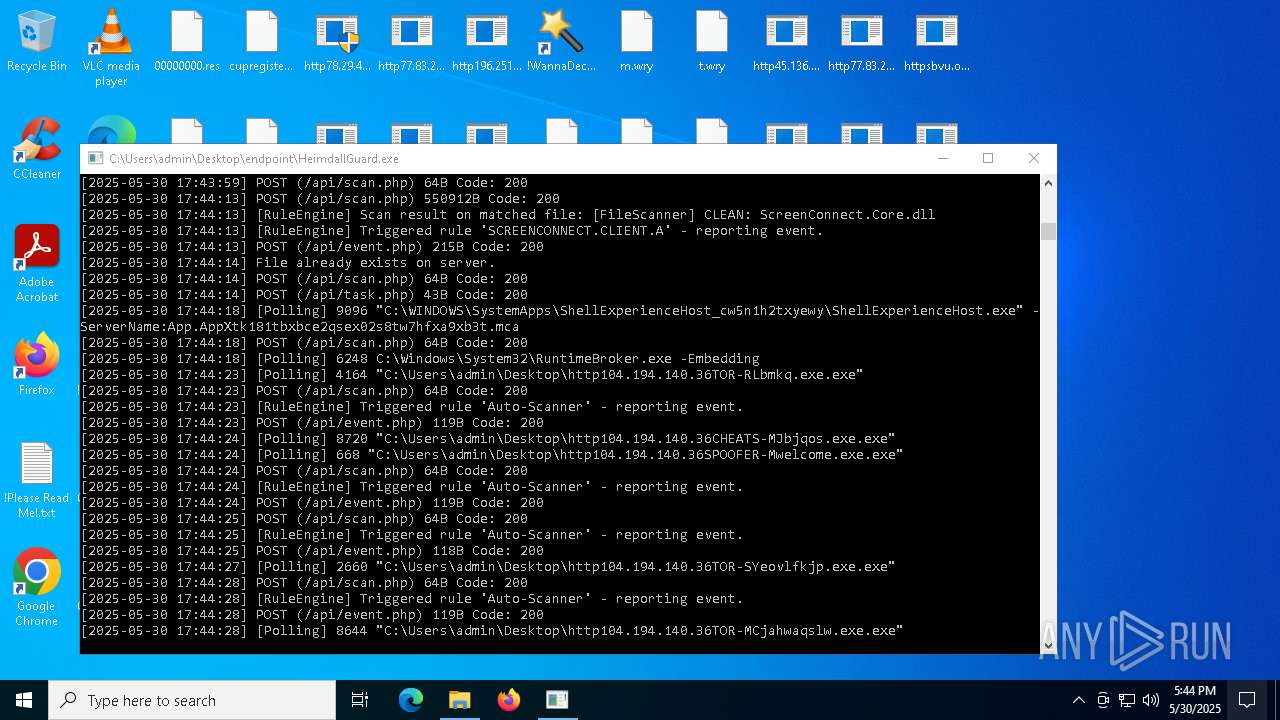
Process requests binary or script from the Internet
- bomb.exe (PID: 4020)
- http78.29.45.8Installer.exe.exe (PID: 8676)
Adds/modifies Windows certificates
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4380)
- dfsvc.exe (PID: 5400)
Connects to unusual port
- bomb.exe (PID: 4020)
- ScreenConnect.ClientService.exe (PID: 7260)
- httpbkngnet.combgj3ckjg.exe.exe (PID: 8220)
Reads Internet Explorer settings
- dfsvc.exe (PID: 5400)
Executable content was dropped or overwritten
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 4188)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7172)
- ModSolar.exe (PID: 1804)
- ModSolar.exe (PID: 7892)
- rundll32.exe (PID: 8176)
- esentutl.exe (PID: 8584)
- http78.29.45.8Installer.exe.exe (PID: 8096)
- http78.29.45.8Installer.exe.exe (PID: 8676)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 668)
- http183.30.204.281Video.scr.exe (PID: 3760)
- http183.30.204.281AV.scr.exe (PID: 6344)
- http47.239.251.98080Video.scr.exe (PID: 2236)
- http47.239.251.98080AV.scr.exe (PID: 6464)
- http183.30.204.281Photo.scr.exe (PID: 7000)
Potential Corporate Privacy Violation
- bomb.exe (PID: 4020)
- ScreenConnect.ClientService.exe (PID: 7260)
- http78.29.45.8Installer.exe.exe (PID: 8676)
Connects to the server without a host name
- bomb.exe (PID: 4020)
- http78.29.45.8Installer.exe.exe (PID: 8676)
Executes as Windows Service
- ScreenConnect.ClientService.exe (PID: 7260)
- VSSVC.exe (PID: 6808)
- ScreenConnect.ClientService.exe (PID: 9124)
- ScreenConnect.ClientService.exe (PID: 9160)
- ScreenConnect.ClientService.exe (PID: 9196)
- ScreenConnect.ClientService.exe (PID: 4336)
SCREENCONNECT mutex has been found
- ScreenConnect.ClientService.exe (PID: 7260)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 5400)
- bomb.exe (PID: 4020)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 7260)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 7260)
Starts itself from another location
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 4188)
- ModSolar.exe (PID: 1804)
- cmd.exe (PID: 8464)
Application launched itself
- HeimdallGuard.exe (PID: 5352)
- HeimdallGuard.exe (PID: 5216)
- HeimdallGuard.exe (PID: 2596)
- http183.30.204.281Photo.scr.exe (PID: 7000)
Detects ScreenConnect RAT (YARA)
- ScreenConnect.ClientService.exe (PID: 7260)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- httpbkngnet.combgj3ckjg.exe.exe (PID: 8220)
Starts CMD.EXE for commands execution
- http77.83.207.69inctot.exe.exe (PID: 7916)
- http107.173.47.141125dllhost.exe.exe (PID: 4424)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
Executing commands from a ".bat" file
- http77.83.207.69inctot.exe.exe (PID: 7916)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 7304)
There is functionality for taking screenshot (YARA)
- ScreenConnect.ClientService.exe (PID: 7260)
Executing commands from ".cmd" file
- http107.173.47.141125dllhost.exe.exe (PID: 4424)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8500)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 8584)
- alpha.pif (PID: 8632)
- alpha.pif (PID: 8656)
Created directory related to system
- alpha.pif (PID: 8632)
Starts a Microsoft application from unusual location
- alpha.pif (PID: 8632)
- alpha.pif (PID: 8656)
- http78.29.45.8Installer.exe.exe (PID: 4164)
- http78.29.45.8Installer.exe.exe (PID: 8096)
- http78.29.45.8Installer.exe.exe (PID: 8676)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
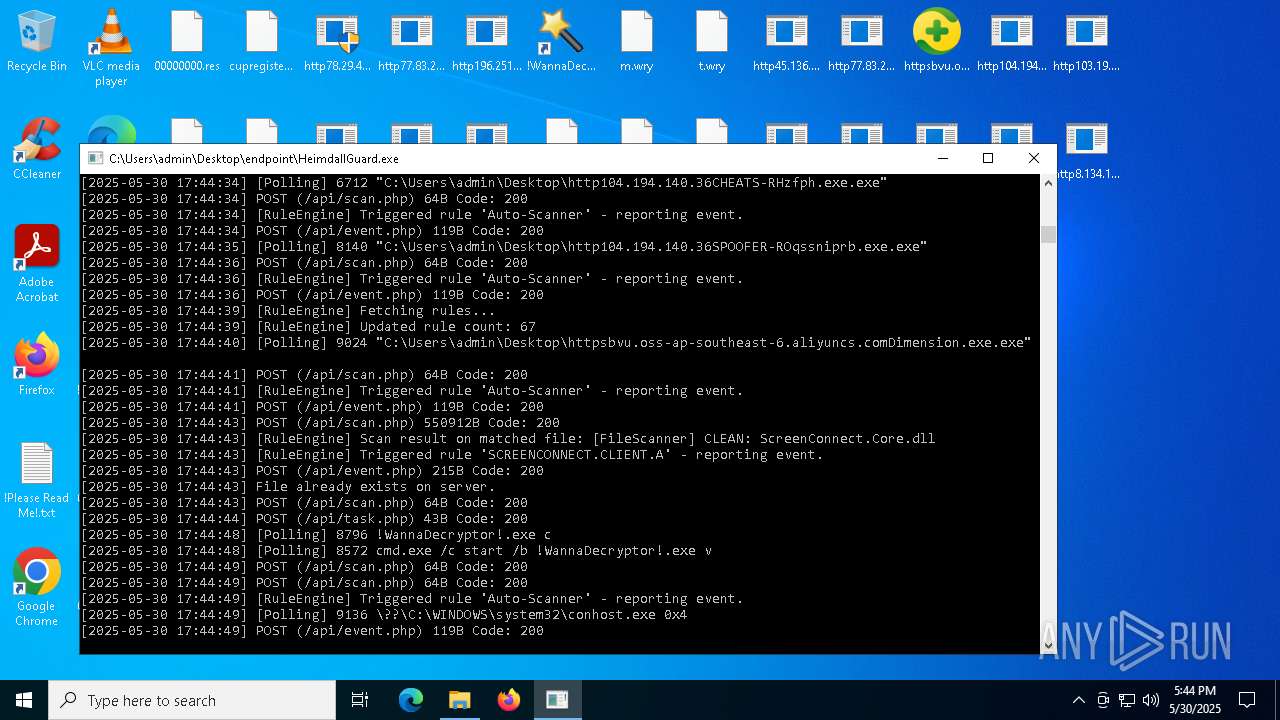
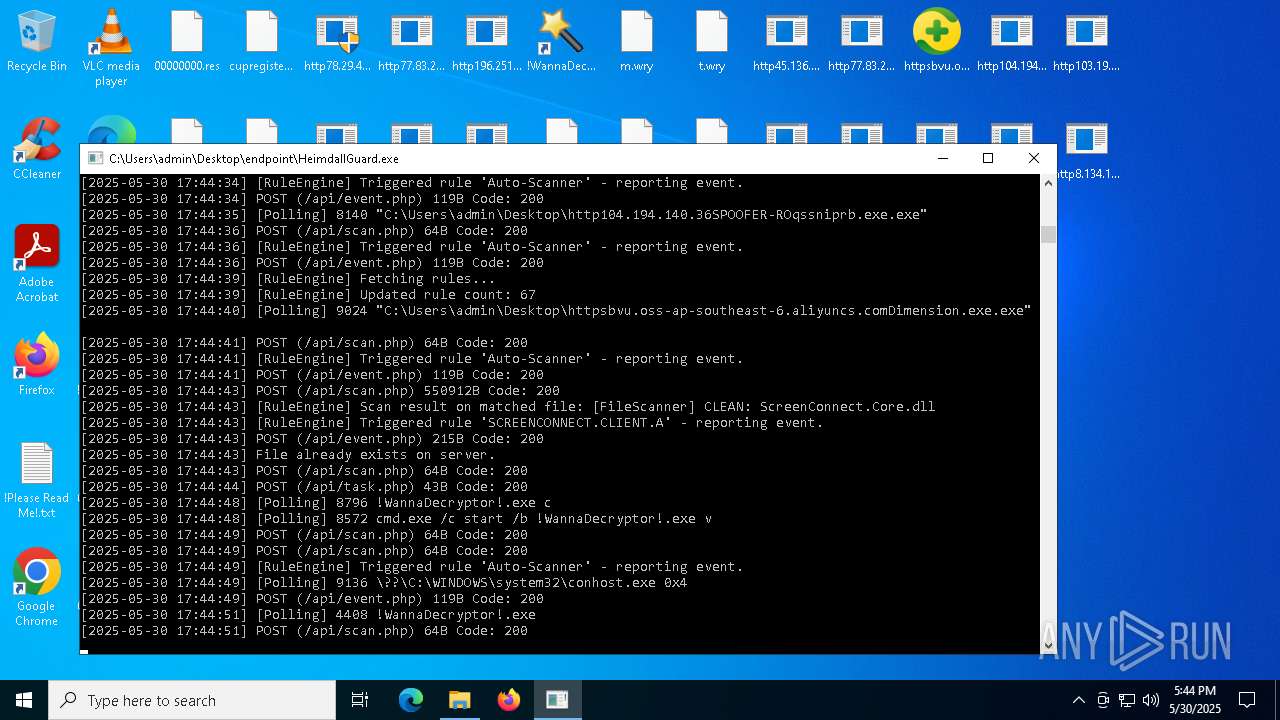
- !WannaDecryptor!.exe (PID: 8420)
- !WannaDecryptor!.exe (PID: 8796)
- !WannaDecryptor!.exe (PID: 4408)
Starts application with an unusual extension
- cmd.exe (PID: 8464)
Uses WMIC.EXE to obtain computer system information
- httpbkngnet.combgj3ckjg.exe.exe (PID: 8220)
Process drops legitimate windows executable
- http78.29.45.8Installer.exe.exe (PID: 8096)
- http78.29.45.8Installer.exe.exe (PID: 8676)
- bomb.exe (PID: 4020)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 668)
- http183.30.204.281Video.scr.exe (PID: 3760)
- http183.30.204.281AV.scr.exe (PID: 6344)
- http183.30.204.281Photo.scr.exe (PID: 7000)
- http47.239.251.98080Video.scr.exe (PID: 2236)
- http47.239.251.98080AV.scr.exe (PID: 6464)
Windows service management via SC.EXE
- sc.exe (PID: 8480)
- sc.exe (PID: 8876)
The process drops C-runtime libraries
- http78.29.45.8Installer.exe.exe (PID: 8096)
- http78.29.45.8Installer.exe.exe (PID: 8676)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 668)
- http183.30.204.281Video.scr.exe (PID: 3760)
- http183.30.204.281Photo.scr.exe (PID: 7000)
- http183.30.204.281AV.scr.exe (PID: 6344)
- http47.239.251.98080Video.scr.exe (PID: 2236)
- http47.239.251.98080AV.scr.exe (PID: 6464)
Starts SC.EXE for service management
- http78.29.45.8Installer.exe.exe (PID: 8096)
- http78.29.45.8Installer.exe.exe (PID: 8676)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8492)
The process executes via Task Scheduler
- http78.29.45.8Installer.exe.exe (PID: 8676)
The process executes VB scripts
- cmd.exe (PID: 6416)
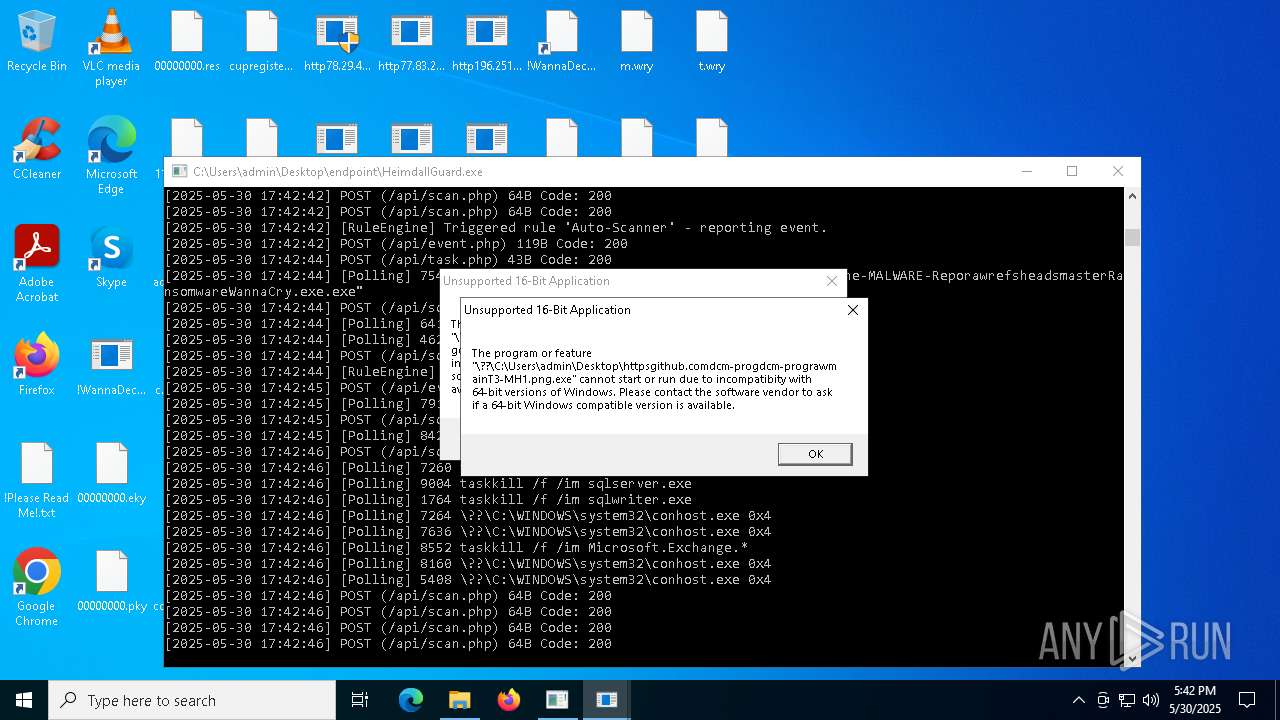
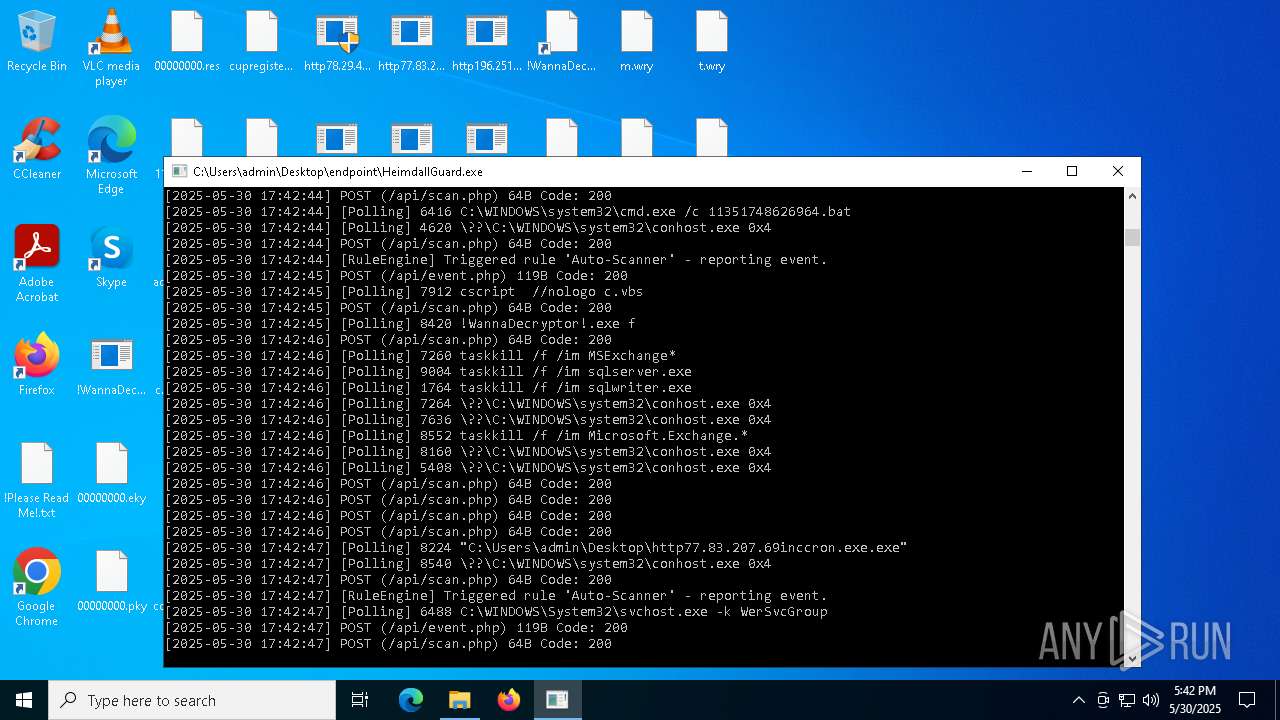
Uses TASKKILL.EXE to kill process
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
Process drops python dynamic module
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 668)
- http183.30.204.281AV.scr.exe (PID: 6344)
- http183.30.204.281Photo.scr.exe (PID: 7000)
- http183.30.204.281Video.scr.exe (PID: 3760)
- http47.239.251.98080Video.scr.exe (PID: 2236)
- http47.239.251.98080AV.scr.exe (PID: 6464)
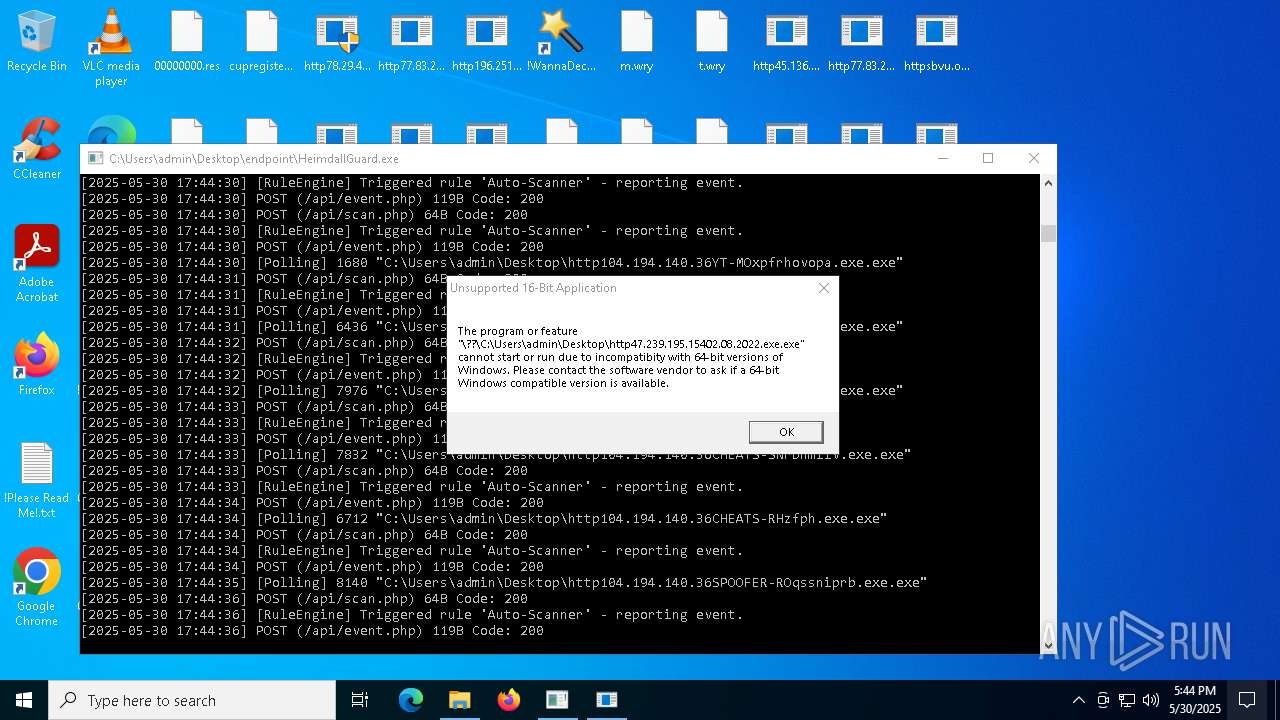
Executes application which crashes
- HeimdallGuard.exe (PID: 5352)
INFO
Reads the computer name
- bomb.exe (PID: 4020)
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4380)
- dfsvc.exe (PID: 5400)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- ScreenConnect.ClientService.exe (PID: 8064)
- ScreenConnect.WindowsClient.exe (PID: 1660)
- ScreenConnect.ClientService.exe (PID: 7260)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7172)
- ModSolar.exe (PID: 1804)
- http77.83.207.69incClientSetup1.exe.exe (PID: 7456)
- ModSolar.exe (PID: 7892)
- HeimdallGuard.exe (PID: 5352)
- msiexec.exe (PID: 7476)
- msiexec.exe (PID: 7932)
- HeimdallGuard.exe (PID: 2596)
Disables trace logs
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
- HeimdallGuard.exe (PID: 5352)
Checks supported languages
- bomb.exe (PID: 4020)
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4380)
- dfsvc.exe (PID: 5400)
- ScreenConnect.ClientService.exe (PID: 8064)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- ScreenConnect.WindowsClient.exe (PID: 1660)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 4188)
- ScreenConnect.ClientService.exe (PID: 7260)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7172)
- ModSolar.exe (PID: 1804)
- http77.83.207.69inccron1mm.exe.exe (PID: 5384)
- http77.83.207.69incClientSetup1.exe.exe (PID: 7456)
- http77.83.207.69incale11.exe.exe (PID: 7704)
- ModSolar.exe (PID: 7892)
- http77.83.207.69inccron2mm.exe.exe (PID: 7348)
- msiexec.exe (PID: 7476)
- HeimdallGuard.exe (PID: 5352)
- msiexec.exe (PID: 7932)
- http107.173.47.141125dllhost.exe.exe (PID: 4424)
- HeimdallGuard.exe (PID: 2596)
Process checks computer location settings
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- http77.83.207.69incClientSetup1.exe.exe (PID: 7456)
Reads the machine GUID from the registry
- bomb.exe (PID: 4020)
- http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe (PID: 4380)
- dfsvc.exe (PID: 5400)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- ScreenConnect.ClientService.exe (PID: 8064)
- ScreenConnect.WindowsClient.exe (PID: 1660)
- ScreenConnect.ClientService.exe (PID: 7260)
- http77.83.207.69incClientSetup1.exe.exe (PID: 7456)
- HeimdallGuard.exe (PID: 5352)
- HeimdallGuard.exe (PID: 2596)
Reads Environment values
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
Checks proxy server information
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
- HeimdallGuard.exe (PID: 5352)
Reads the software policy settings
- bomb.exe (PID: 4020)
- dfsvc.exe (PID: 5400)
- HeimdallGuard.exe (PID: 5352)
Creates files or folders in the user directory
- dfsvc.exe (PID: 5400)
- ScreenConnect.WindowsClient.exe (PID: 5624)
- ScreenConnect.ClientService.exe (PID: 7260)
- ModSolar.exe (PID: 7892)
Create files in a temporary directory
- dfsvc.exe (PID: 5400)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 4188)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7172)
- http77.83.207.69incClientSetup1.exe.exe (PID: 7456)
- ModSolar.exe (PID: 7892)
- rundll32.exe (PID: 8176)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 5400)
SCREENCONNECT has been detected
- ScreenConnect.ClientService.exe (PID: 7260)
Manual execution by a user
- WinRAR.exe (PID: 1228)
- HeimdallGuard.exe (PID: 5352)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1228)
- msiexec.exe (PID: 5228)
- msiexec.exe (PID: 7476)
The sample compiled with english language support
- bomb.exe (PID: 4020)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 4188)
- ModSolar.exe (PID: 1804)
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7172)
- ModSolar.exe (PID: 7892)
- esentutl.exe (PID: 8584)
- http78.29.45.8Installer.exe.exe (PID: 8096)
- http78.29.45.8Installer.exe.exe (PID: 8676)
- http104.194.140.36SPOOFER-Mwelcome.exe.exe (PID: 668)
- httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe (PID: 7544)
- http183.30.204.281Video.scr.exe (PID: 3760)
- http183.30.204.281AV.scr.exe (PID: 6344)
- http183.30.204.281Photo.scr.exe (PID: 7000)
- http47.239.251.98080Video.scr.exe (PID: 2236)
- http47.239.251.98080AV.scr.exe (PID: 6464)
The sample compiled with chinese language support
- http77.83.207.69incJFDGQDUS.exe.exe (PID: 7172)
- ModSolar.exe (PID: 1804)
Creates files in the program directory
- ModSolar.exe (PID: 1804)
Launch of the file from Registry key
- HeimdallGuard.exe (PID: 5352)
CONNECTWISE has been detected
- msiexec.exe (PID: 5228)
Application launched itself
- chrome.exe (PID: 7788)
Manages system restore points
- SrTasks.exe (PID: 8908)
Launch of the file from Task Scheduler
- http78.29.45.8Installer.exe.exe (PID: 8096)
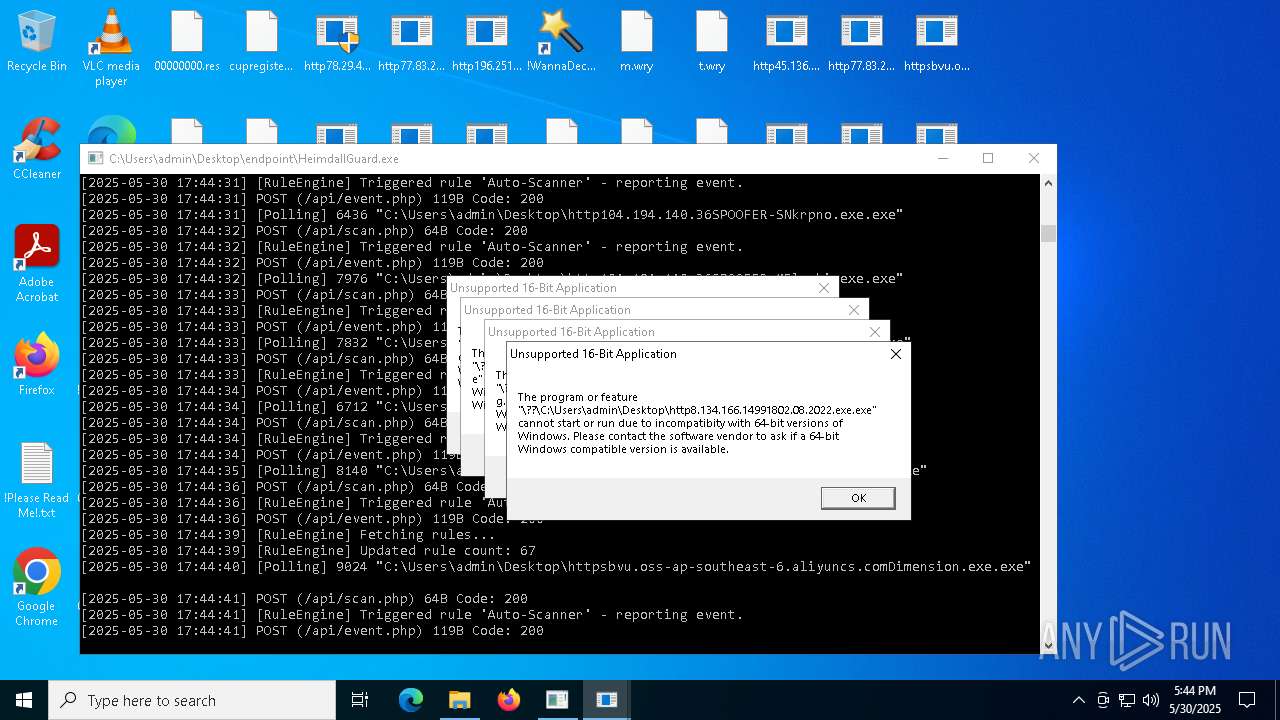
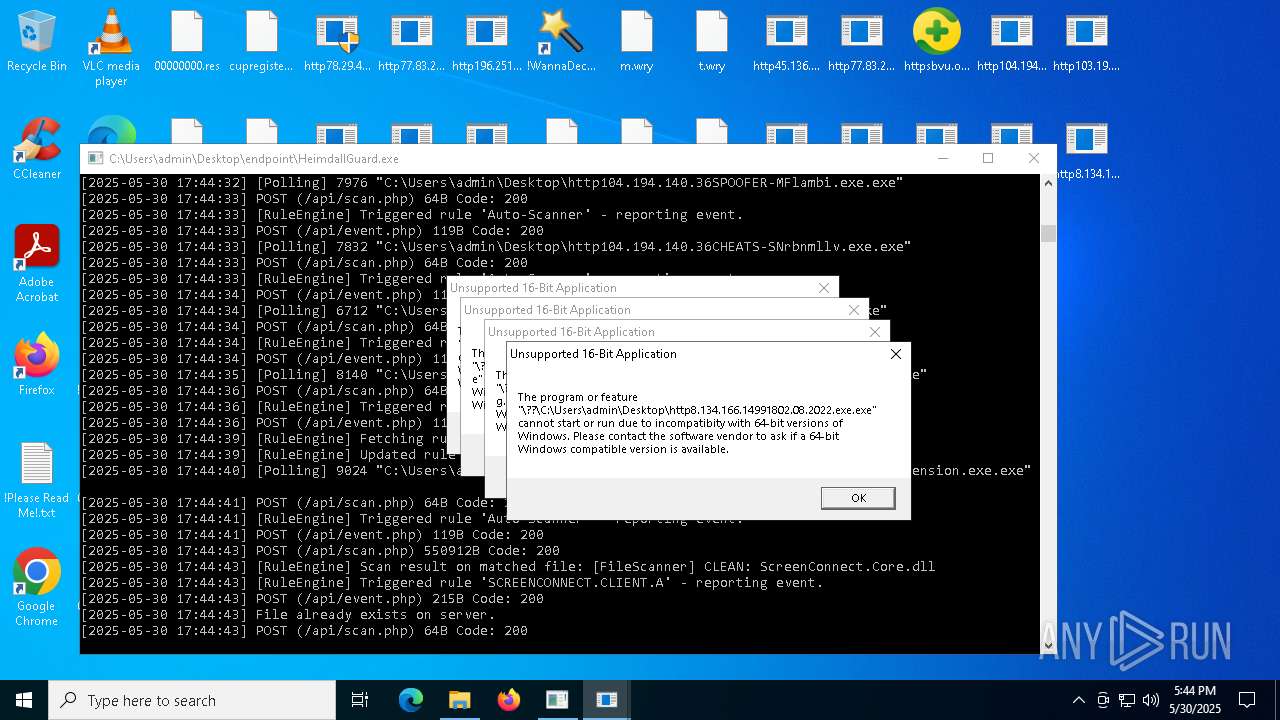
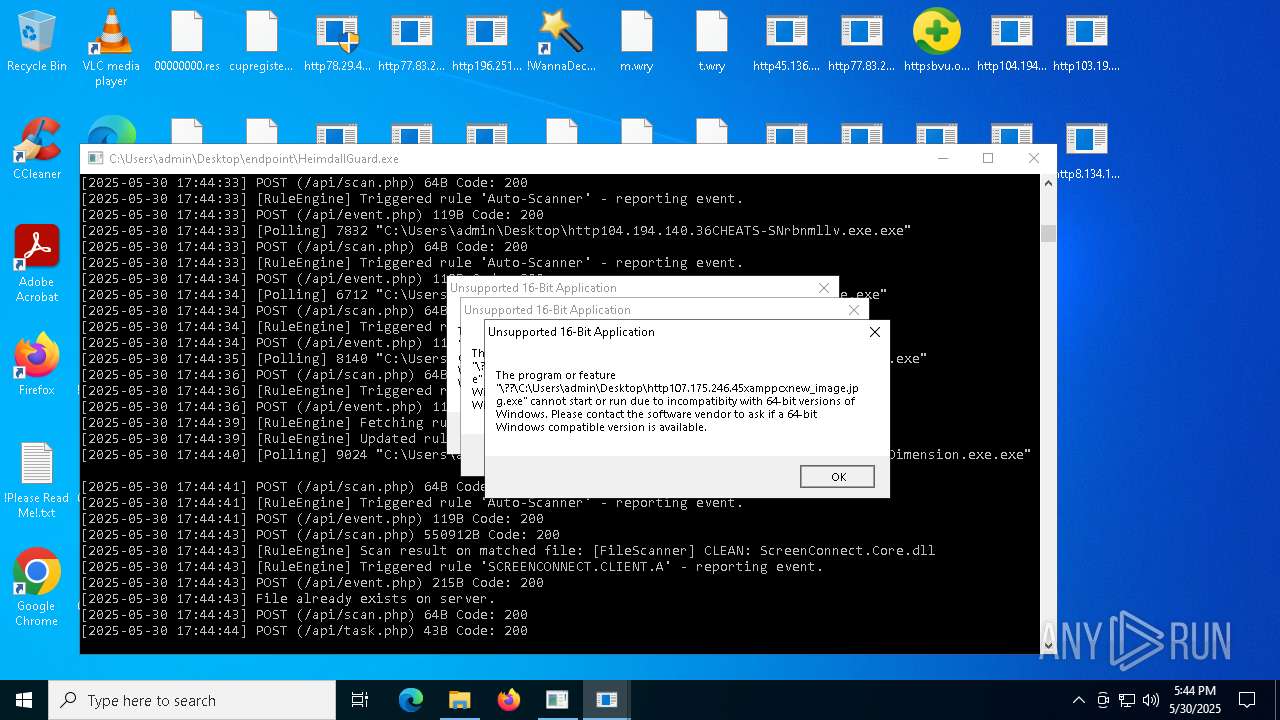
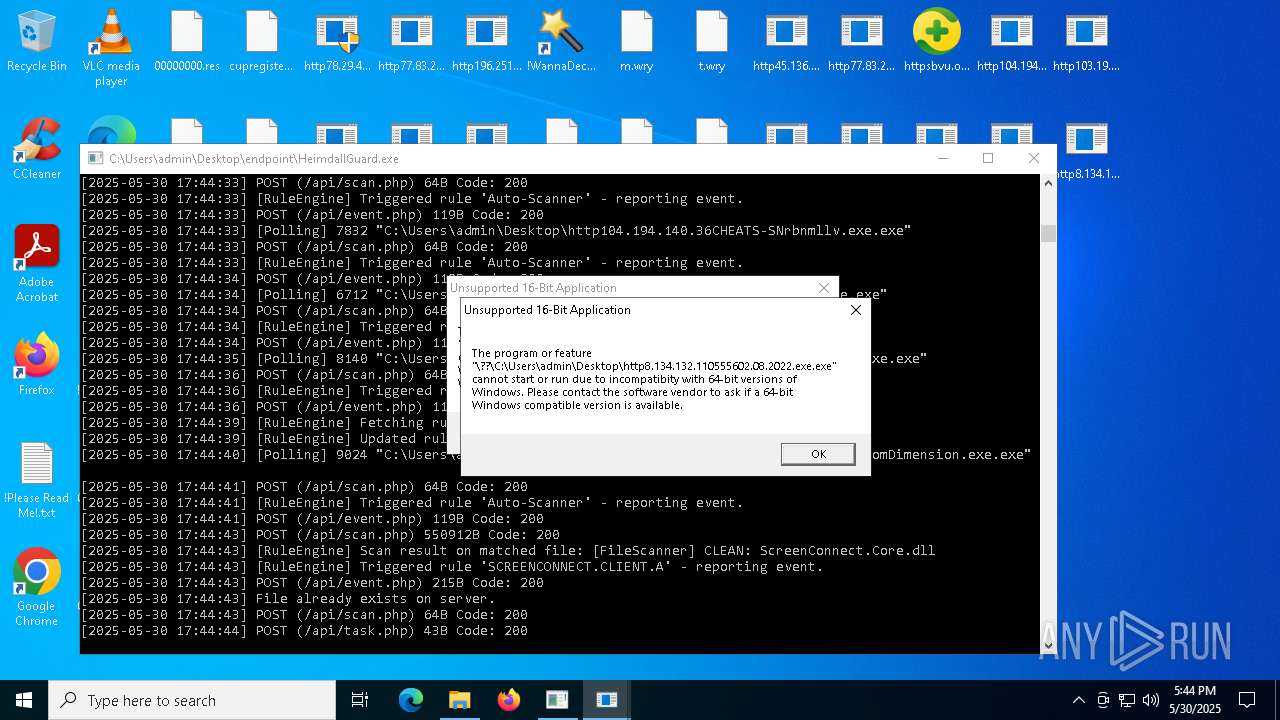
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2057:01:07 19:44:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9216 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x43be |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
280
Monitored processes
142
Malicious processes
10
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3688 --field-trial-handle=1960,i,4371724065827596369,281198550902175187,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 632 | "schtasks.exe" /run /tn SystemUpdater8e80f87e | C:\Windows\System32\schtasks.exe | — | http78.29.45.8Installer.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Users\admin\Desktop\http104.194.140.36SPOOFER-Mwelcome.exe.exe" | C:\Users\admin\Desktop\http104.194.140.36SPOOFER-Mwelcome.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\endpoint.zip" C:\Users\admin\Desktop\endpoint\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2036 --field-trial-handle=1960,i,4371724065827596369,281198550902175187,262144 --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1548 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | http77.83.207.69inccron2mm.exe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\AppData\Local\Apps\2.0\OLPD23DD.7P6\WGZ2VZ1A.Y5G\scre..tion_25b0fbb6ef7eb094_0019.0001_ffbdcb7220bffc11\ScreenConnect.WindowsClient.exe" "RunRole" "15b241d3-0532-4b77-97aa-86d29776196e" "User" | C:\Users\admin\AppData\Local\Apps\2.0\OLPD23DD.7P6\WGZ2VZ1A.Y5G\scre..tion_25b0fbb6ef7eb094_0019.0001_ffbdcb7220bffc11\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 1 Version: 25.1.10.9197 Modules
| |||||||||||||||
| 1680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | http78.29.45.8Installer.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1680 | "C:\Users\admin\Desktop\http104.194.140.36YT-MOxpfrhovopa.exe.exe" | C:\Users\admin\Desktop\http104.194.140.36YT-MOxpfrhovopa.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Oxpfrhovopa Exit code: 1 Version: 1.0.6987.13119 Modules
| |||||||||||||||
| 1764 | taskkill /f /im sqlwriter.exe | C:\Windows\SysWOW64\taskkill.exe | — | httpsgithub.comDa2dalusThe-MALWARE-ReporawrefsheadsmasterRansomwareWannaCry.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
56 779
Read events
56 232
Write events
494
Delete events
53
Modification events
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4020) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
220
Suspicious files
1 808
Text files
408
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\6ETZ0R2Z.LO0\0X44TLM6.W50\ScreenConnect.WindowsClient.exe.manifest | xml | |
MD5:5259D3B040AD978D0D23AC1E1698CBCD | SHA256:92DDF8B23746703A24F5E1FB6B9F087E98E68116AEC5DE9174D2662E53C1505E | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\932a2db58c237abd381d22df4c63a04a_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
| 4020 | bomb.exe | C:\Users\admin\Desktop\http77.83.207.69incSSA-7005-SM-34062529.pdf.exe.exe | executable | |
MD5:B28AC406FC4D1596B24B25913CB976BB | SHA256:8501047B053255F04CF9D0402BB947CEB13532B8C9BD2FA052A4647B357524B8 | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\MXOJ86PW.OW6\HK4447OL.3RG.application | xml | |
MD5:A6D87EA7D3B83528560724CC58155152 | SHA256:8D9F670912B080E8B06647FB49029DCEF895CE59615BDD285BB6F1CE47DA366E | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:72481247693FCD59305210546D9EF0DB | SHA256:4A40C24749475918DF666217C49ABD926054472B8A32EE8C70EAEE43A9F2015E | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:26A3C07BAA46D30BBC8D971741FE6764 | SHA256:FA828C8B34AEBF7C187A583F30190604D5091818BE7DE273B59C77FAD7997734 | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\6ETZ0R2Z.LO0\0X44TLM6.W50\ScreenConnect.WindowsFileManager.exe.config | xml | |
MD5:728175E20FFBCEB46760BB5E1112F38B | SHA256:87C640D3184C17D3B446A72D5F13D643A774B4ECC7AFBEDFD4E8DA7795EA8077 | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\6ETZ0R2Z.LO0\0X44TLM6.W50\ScreenConnect.Client.dll | executable | |
MD5:C2E6C1CC43EC4E4699C468357112C621 | SHA256:51BA5DB0406854015BBC30D991EC10DDADF0713856E0681DFDB1CC8E92A06D95 | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\6ETZ0R2Z.LO0\0X44TLM6.W50\ScreenConnect.WindowsClient.exe:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 5400 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\6ETZ0R2Z.LO0\0X44TLM6.W50\ScreenConnect.Windows.dll | executable | |
MD5:639DAD6CB322F7B58655A5AABB298CF9 | SHA256:D32CAF12298A7A901D086613F01E2E6AEAA2AAE88B5CED85C1EB7A9E381D4679 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
541
DNS requests
57
Threats
149
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4020 | bomb.exe | GET | 200 | 77.83.207.69:80 | http://77.83.207.69/inc/SSA-7005-SM-34062529.pdf.exe | unknown | — | — | malicious |
5400 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5400 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAuTYAUbzPZmQpmJmNW6l84%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5400 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
3304 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3304 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4020 | bomb.exe | GET | 200 | 77.83.207.69:80 | http://77.83.207.69/inc/JFDGQDUS.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
8176 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3760 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4020 | bomb.exe | 188.114.97.3:443 | maper.info | CLOUDFLARENET | NL | malicious |
4020 | bomb.exe | 142.250.185.164:443 | www.google.com | GOOGLE | US | whitelisted |
4020 | bomb.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
maper.info |
| malicious |
www.google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
support.screenconnectsoftware.com |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4020 | bomb.exe | Potential Corporate Privacy Violation | ET INFO IP Logger Redirect Domain in SNI |
4020 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS *.pdf.exe in HTTP URL |
4020 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4020 | bomb.exe | Misc activity | ET INFO Packed Executable Download |
4020 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4020 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4020 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7260 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |
4020 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4020 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |