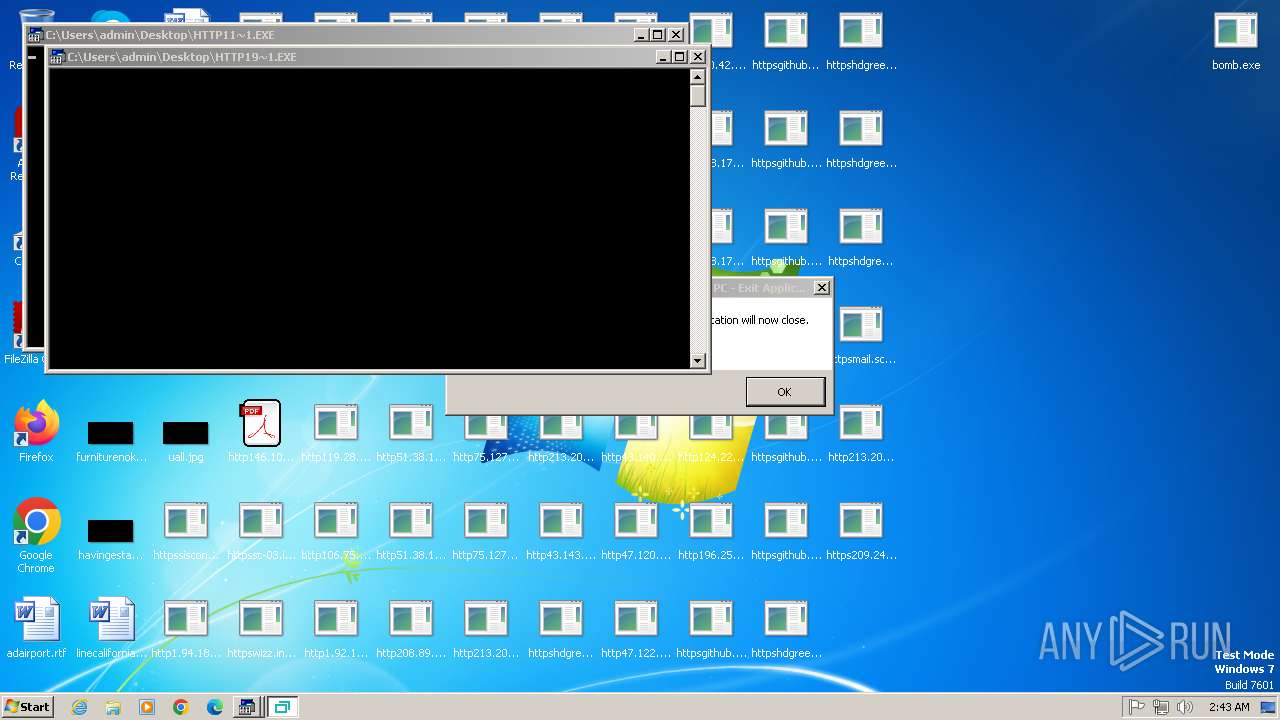
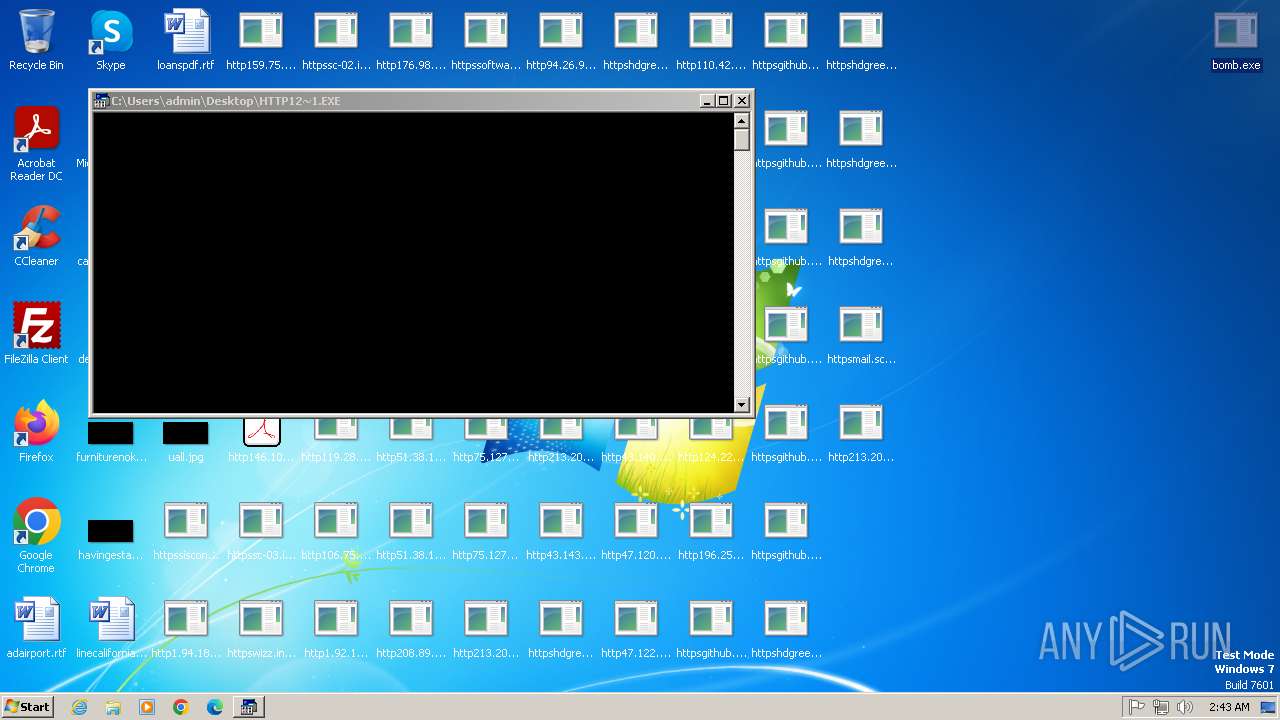
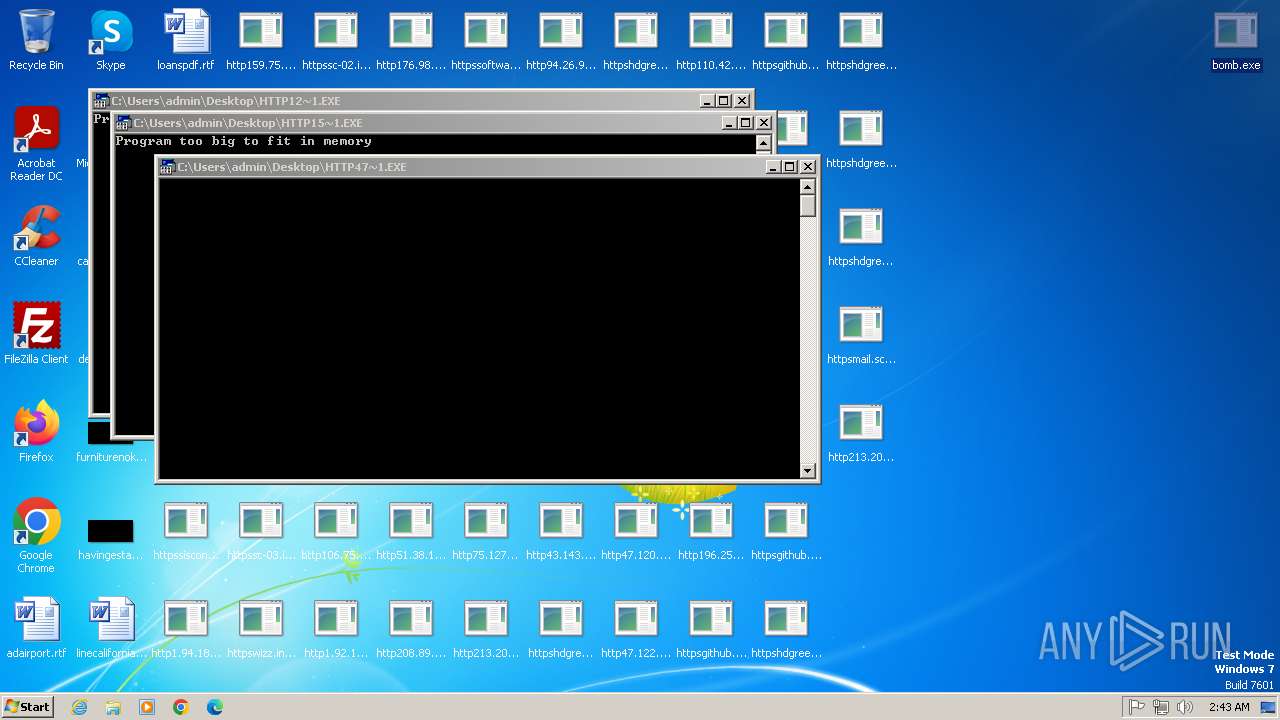
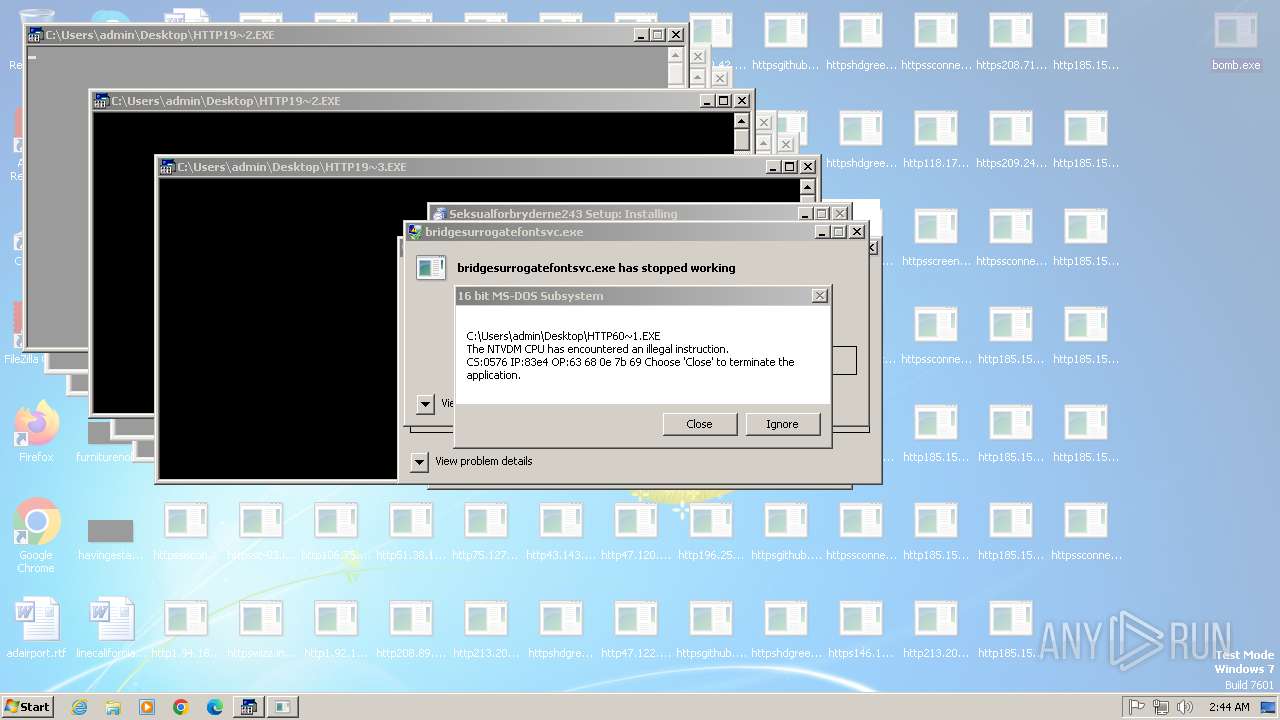
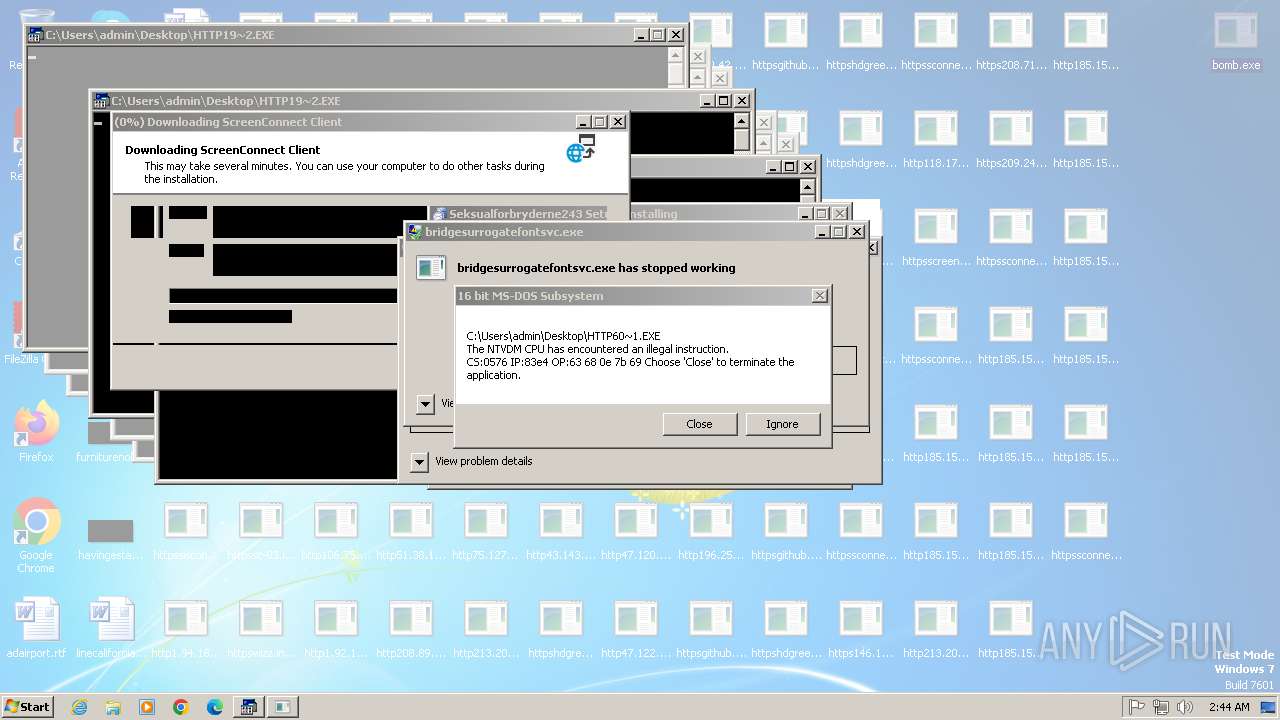
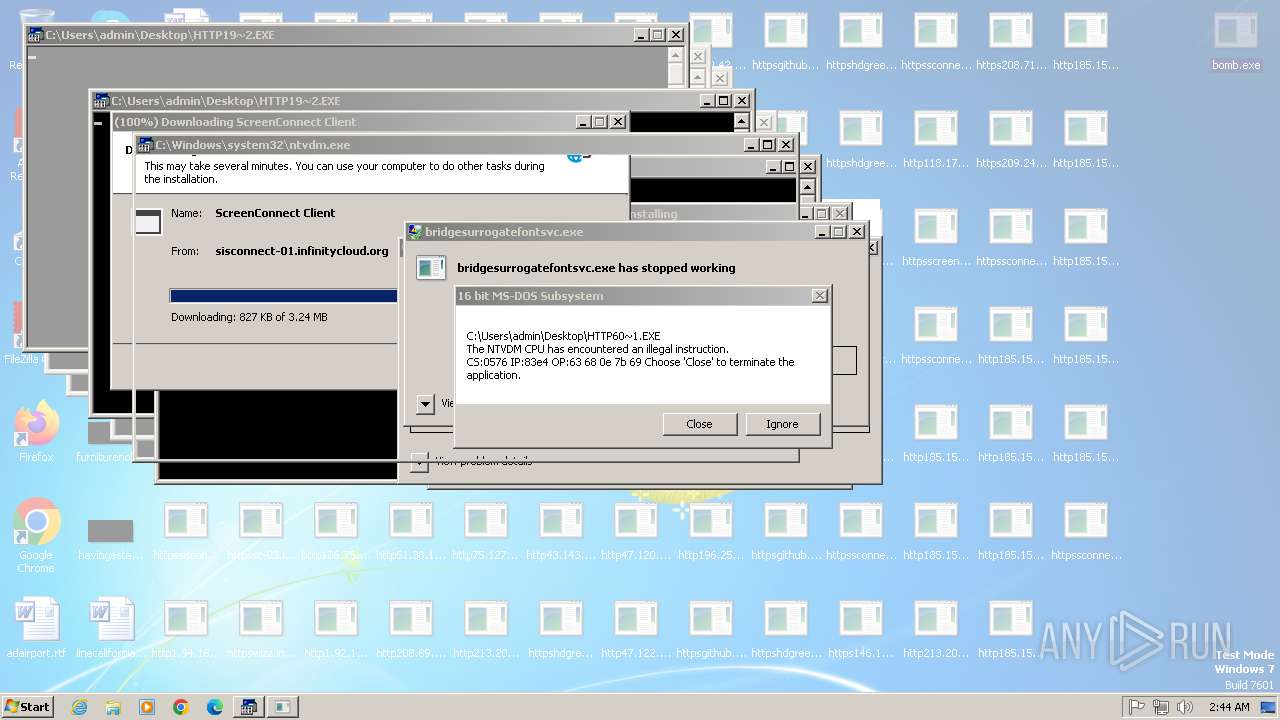
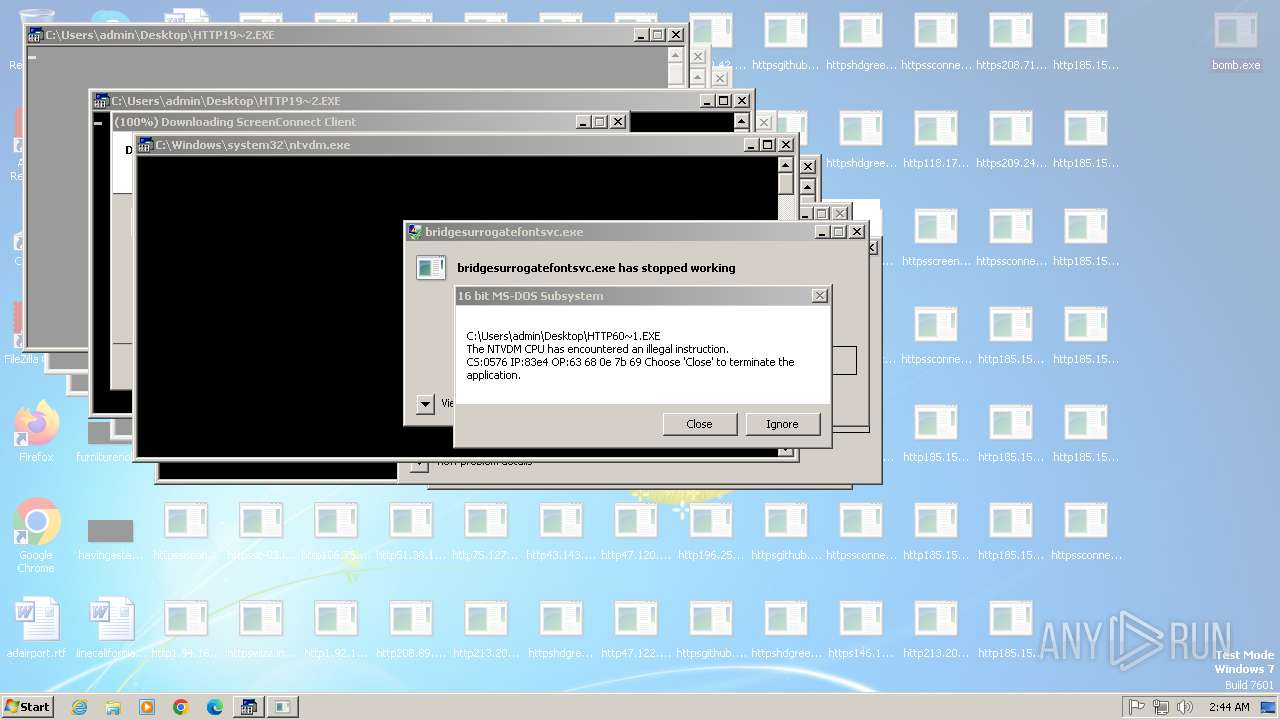
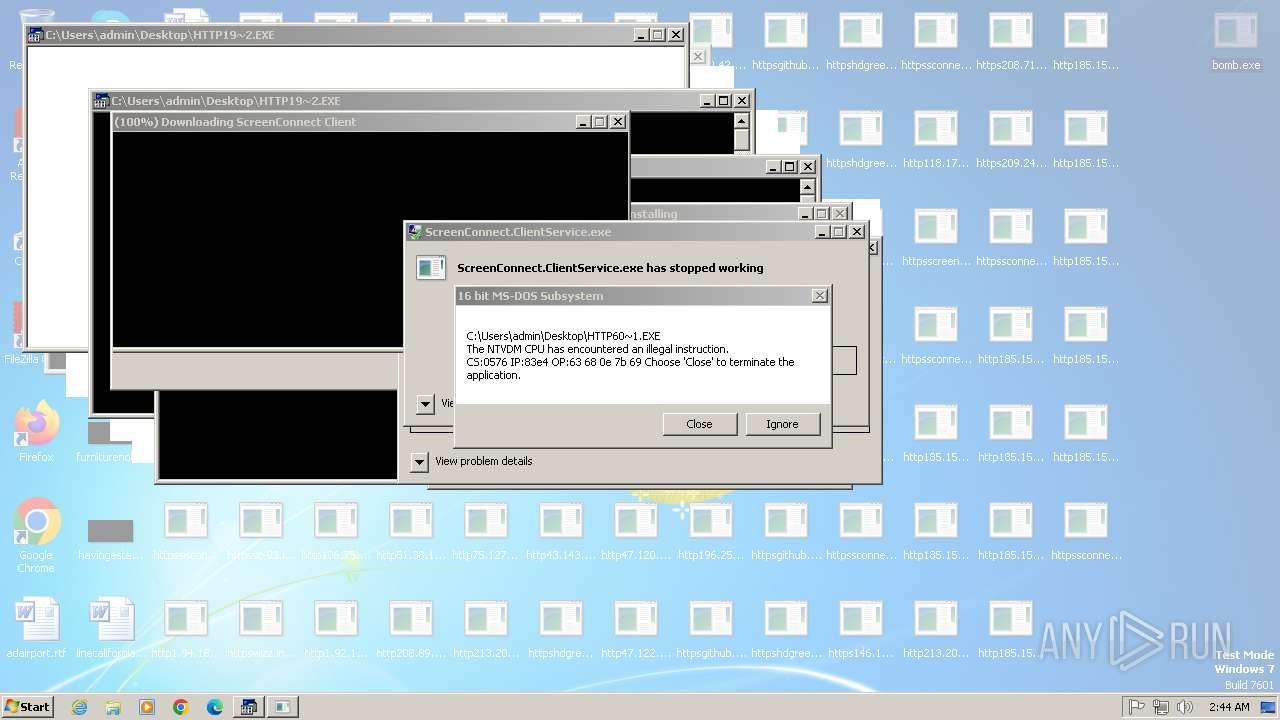
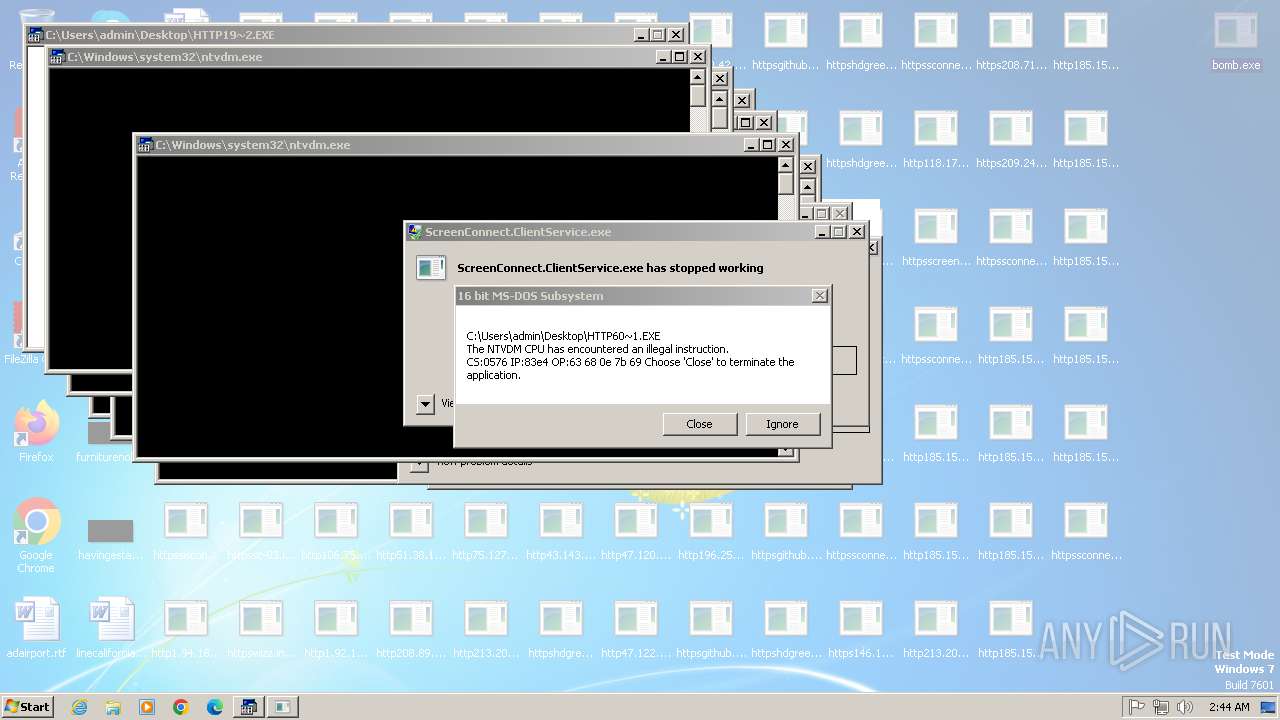
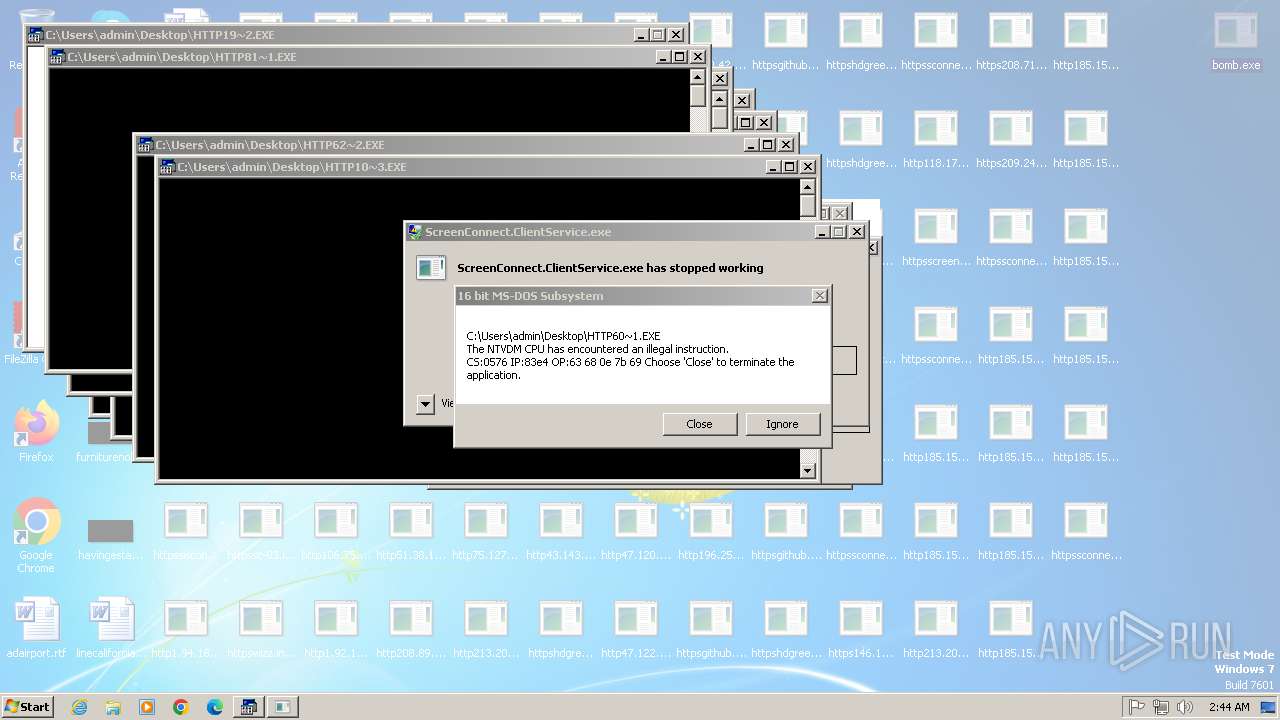
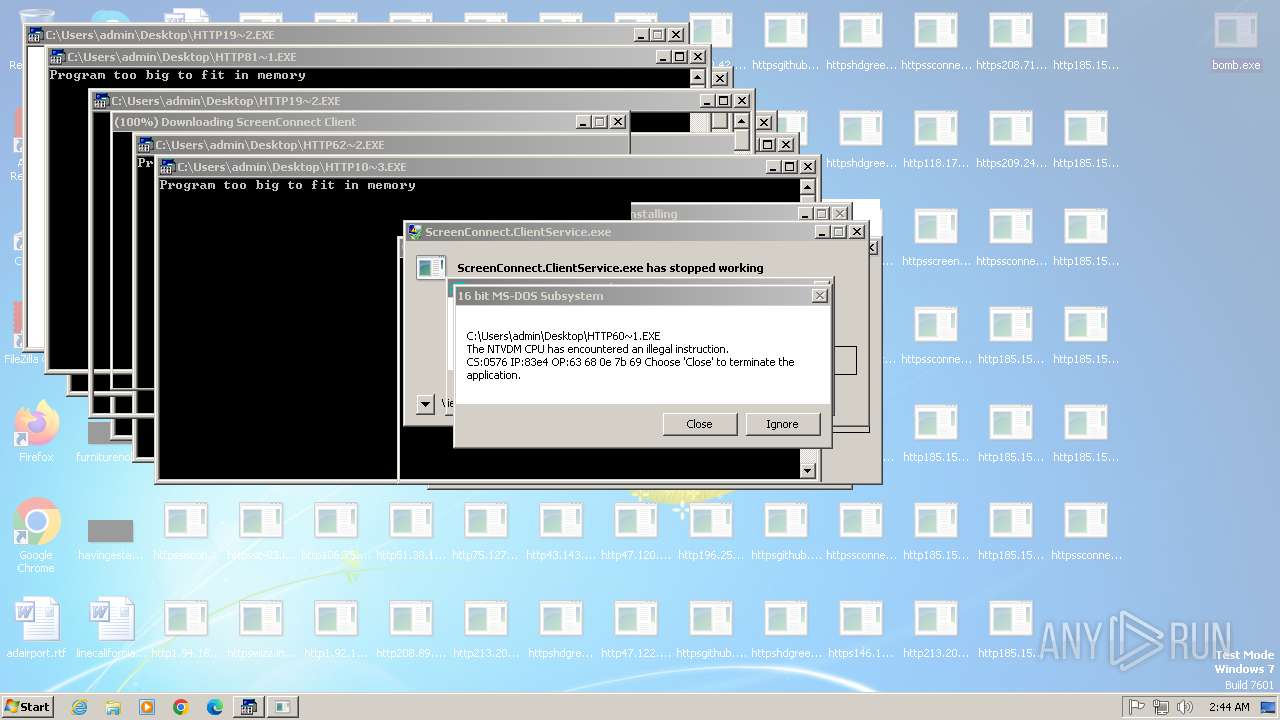
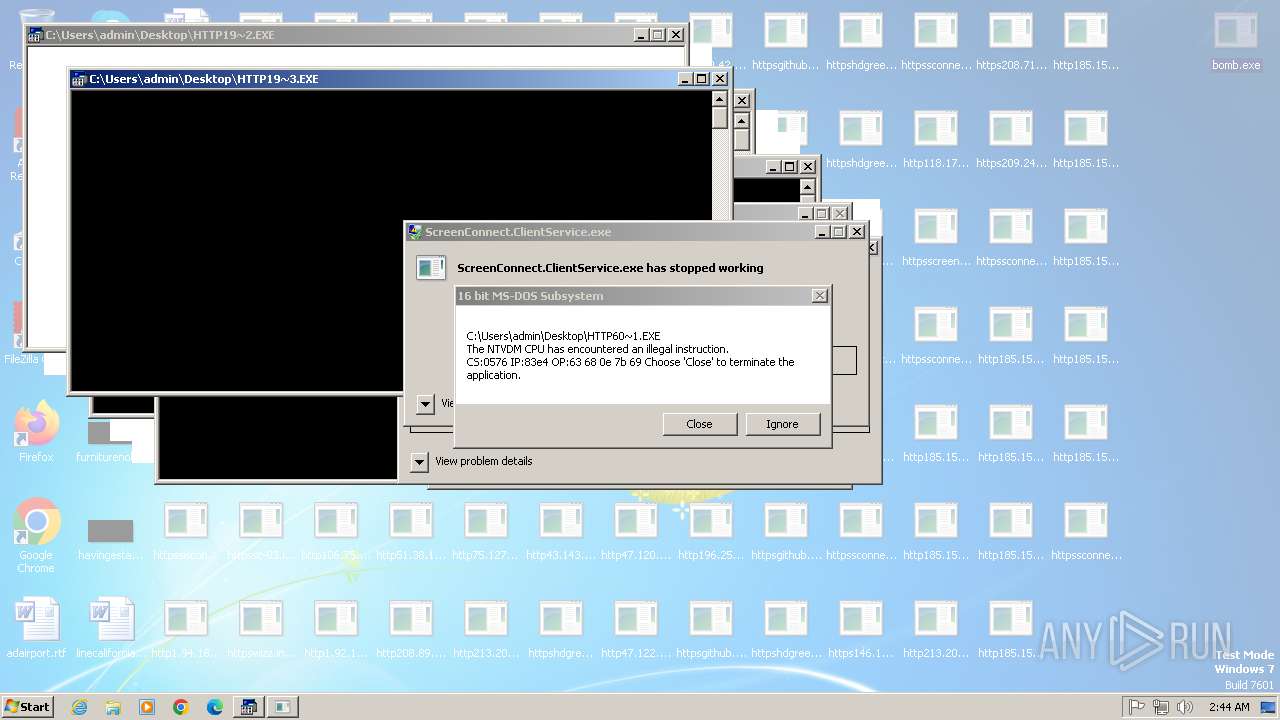
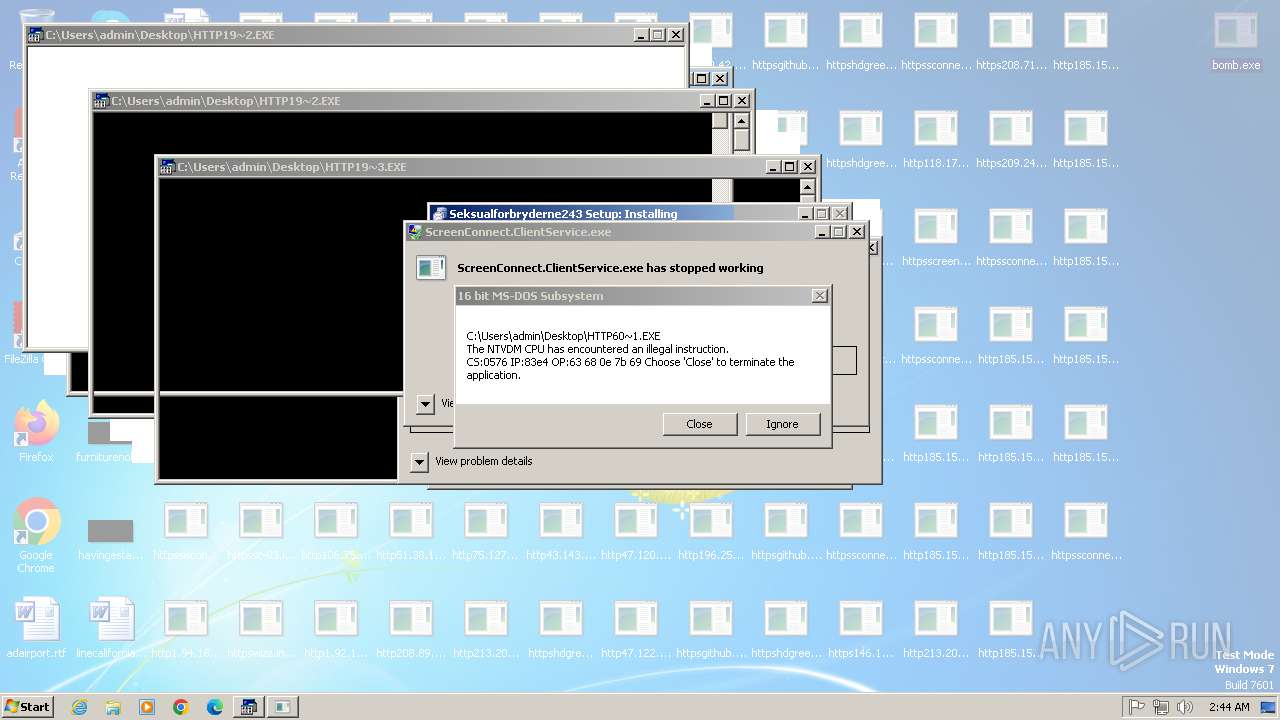
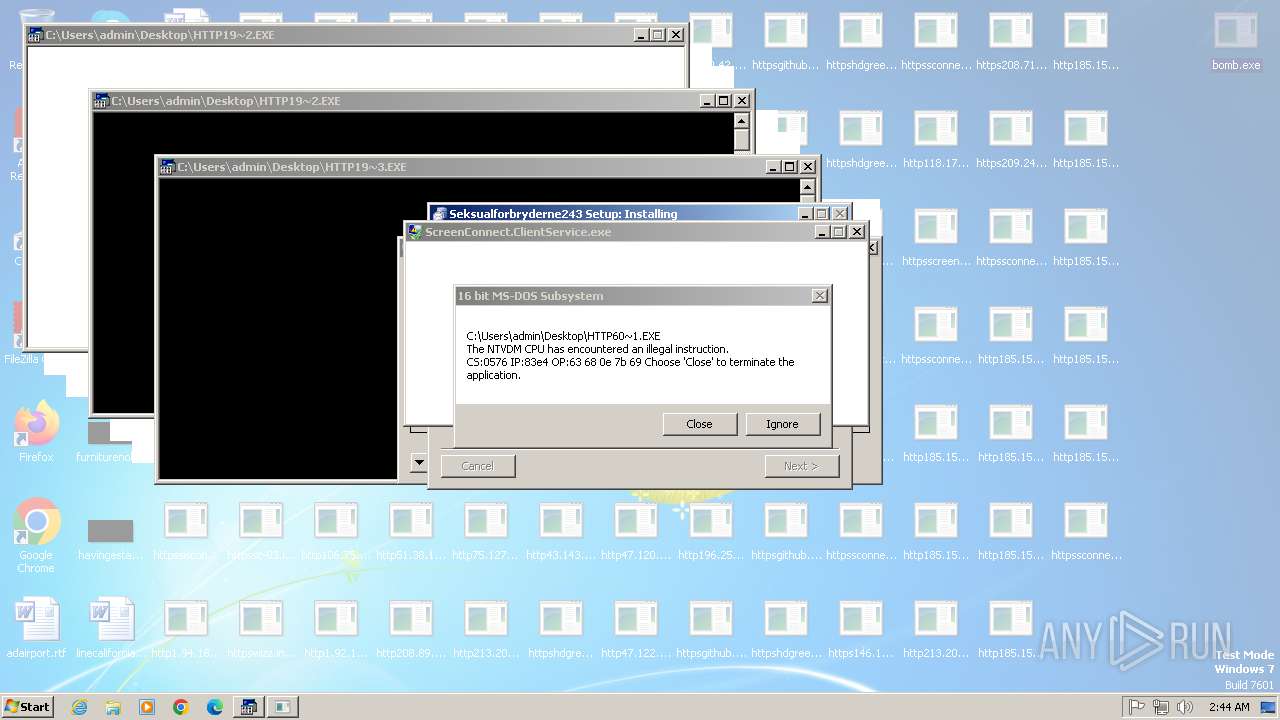
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/8d2bdd29-8703-460b-ac09-94549f198196 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 01:42:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0E2AD53C884E25F969B3A575F4BB90BB |
| SHA1: | 81E774FE109DDC9185AD3FB68995A069CE9045E0 |
| SHA256: | 990D1FF1AB883A9BACBBB6ABCF975139D9AB359B74FFBA16F1FA7A66A30E935D |
| SSDEEP: | 192:OJa0tZMoQszhl4AKd+QHzdPbwPz1OLU87glpp/bI6J4YlTtoIw:OLJQjd+qzZ0OLU870NJDoI |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- bomb.exe (PID: 2480)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
Create files in the Startup directory
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
Antivirus name has been found in the command line (generic signature)
- sfc.exe (PID: 2956)
GHOSTSOCKS has been found (auto)
- bomb.exe (PID: 2480)
FORMBOOK has been detected (YARA)
- sfc.exe (PID: 2956)
ASYNCRAT has been detected (YARA)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
ASYNCRAT has been detected (SURICATA)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
DCRAT has been found (auto)
- bomb.exe (PID: 3120)
Executing a file with an untrusted certificate
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 9324)
- http75.127.7.164Supawn.exe.exe (PID: 11292)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 11868)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 8704)
- http75.127.7.164Supawn.exe.exe (PID: 10480)
- httpsgithub.comlegendary99999lsdmfvkjsmndvareleasesdownloadfdvasdfvadvfaCompoundsTrim.exe.exe (PID: 9580)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 10168)
- http75.127.7.164Supawn.exe.exe (PID: 14872)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 9176)
- httpsgithub.comlegendary99999vdfsvgdfsavsdfvsreleasesdownloaddafbadfbwdfbaLatitudeVsnet.exe.exe (PID: 16440)
- httpsgithub.comlegendary99999dfdsffdsfdsreleasesdownloaddsfdfsdsfdsfgoldik121212.exe.exe (PID: 17864)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- ScreenConnect.WindowsClient.exe (PID: 17980)
- ScreenConnect.WindowsClient.exe (PID: 5796)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- ScreenConnect.WindowsClient.exe (PID: 4472)
FORMBOOK has been detected (SURICATA)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 4072)
Stealers network behavior
- bomb.exe (PID: 3120)
Uses Task Scheduler to run other applications
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
LOKIBOT has been detected (SURICATA)
- svchost.exe (PID: 17376)
Connects to the CnC server
- svchost.exe (PID: 17376)
- bomb.exe (PID: 4072)
STEGOCAMPAIGN has been detected (SURICATA)
- bomb.exe (PID: 3100)
LUMMA has been found (auto)
- bomb.exe (PID: 2208)
XWORM has been detected (SURICATA)
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
STEALER has been found (auto)
- bomb.exe (PID: 4012)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 14172)
- RegSvcs.exe (PID: 21252)
RDP has been found (auto)
- bomb.exe (PID: 3192)
GENERIC has been found (auto)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 120)
SUSPICIOUS
Reads the Internet Settings
- bomb.exe (PID: 2480)
- dfsvc.exe (PID: 1800)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- ScreenConnect.ClientService.exe (PID: 2428)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- ScreenConnect.ClientService.exe (PID: 2796)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- ScreenConnect.ClientService.exe (PID: 2516)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 3100)
Reads settings of System Certificates
- bomb.exe (PID: 2480)
- dfsvc.exe (PID: 1800)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2536)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1504)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1180)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 3712)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2716)
- bomb.exe (PID: 3664)
Adds/modifies Windows certificates
- httpsmail.viewyourstatementonline.comBinwork_approval_pdf3.Client.exe.exe (PID: 2592)
- dfsvc.exe (PID: 1800)
- bomb.exe (PID: 2480)
Connects to unusual port
- bomb.exe (PID: 2480)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 580)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 548)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 1092)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- bomb.exe (PID: 3848)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- bomb.exe (PID: 4352)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 4200)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 4484)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 920)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 4500)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 4772)
- bomb.exe (PID: 4864)
- bomb.exe (PID: 4916)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 120)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 692)
- bomb.exe (PID: 5232)
- ScreenConnect.WindowsClient.exe (PID: 5796)
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
- ScreenConnect.WindowsClient.exe (PID: 17980)
- bomb.exe (PID: 4828)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 9588)
- bomb.exe (PID: 956)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 4160)
- bomb.exe (PID: 5632)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 13208)
- bomb.exe (PID: 17200)
- bomb.exe (PID: 6804)
- ScreenConnect.WindowsClient.exe (PID: 4472)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 13132)
Executable content was dropped or overwritten
- bomb.exe (PID: 2480)
- dfsvc.exe (PID: 1800)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 4092)
- sfc.exe (PID: 2956)
- httpsgithub.compopa339nef5rawrefsheadsmainSlasher.exe.exe (PID: 2536)
- bomb.exe (PID: 4796)
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
- bridgesurrogatefontsvc.exe (PID: 7484)
- bomb.exe (PID: 3396)
- svchost.exe (PID: 17376)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 548)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 2012)
- powershell.exe (PID: 21244)
- bomb.exe (PID: 692)
- bomb.exe (PID: 120)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 4408)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 9324)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 9588)
Potential Corporate Privacy Violation
- bomb.exe (PID: 2480)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 580)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 2224)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 120)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 4200)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 548)
- bomb.exe (PID: 848)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 956)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 920)
- bomb.exe (PID: 692)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 4160)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- bomb.exe (PID: 4352)
- bomb.exe (PID: 4476)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 4464)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- bomb.exe (PID: 4392)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 4500)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 4804)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 4908)
- bomb.exe (PID: 4816)
- bomb.exe (PID: 4772)
- bomb.exe (PID: 4864)
- bomb.exe (PID: 4484)
- bomb.exe (PID: 4916)
- bomb.exe (PID: 4400)
- bomb.exe (PID: 5004)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 5112)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 4548)
- bomb.exe (PID: 5240)
- bomb.exe (PID: 5232)
- bomb.exe (PID: 4936)
- bomb.exe (PID: 5216)
- bomb.exe (PID: 4796)
- bomb.exe (PID: 4828)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 12256)
- bomb.exe (PID: 12236)
- ScreenConnect.WindowsClient.exe (PID: 17980)
- ScreenConnect.WindowsClient.exe (PID: 5796)
- bomb.exe (PID: 7704)
- bomb.exe (PID: 8176)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 1104)
- bomb.exe (PID: 6804)
- bomb.exe (PID: 2768)
- bomb.exe (PID: 12176)
- bomb.exe (PID: 13208)
- bomb.exe (PID: 13200)
- bomb.exe (PID: 13192)
- bomb.exe (PID: 13216)
- bomb.exe (PID: 13256)
- bomb.exe (PID: 5632)
- bomb.exe (PID: 13288)
- bomb.exe (PID: 13152)
- bomb.exe (PID: 13092)
- bomb.exe (PID: 13280)
- bomb.exe (PID: 13140)
- bomb.exe (PID: 13240)
- bomb.exe (PID: 13224)
- bomb.exe (PID: 13264)
- bomb.exe (PID: 13248)
- bomb.exe (PID: 9588)
- bomb.exe (PID: 13160)
- bomb.exe (PID: 13100)
- bomb.exe (PID: 13184)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- bomb.exe (PID: 13272)
- bomb.exe (PID: 17200)
- bomb.exe (PID: 17128)
- bomb.exe (PID: 17060)
- bomb.exe (PID: 17136)
- bomb.exe (PID: 17168)
- bomb.exe (PID: 17036)
- bomb.exe (PID: 17044)
- bomb.exe (PID: 17112)
- bomb.exe (PID: 17068)
- bomb.exe (PID: 17004)
- bomb.exe (PID: 17096)
- bomb.exe (PID: 16996)
- bomb.exe (PID: 17160)
- bomb.exe (PID: 17028)
- bomb.exe (PID: 17176)
- bomb.exe (PID: 17052)
- bomb.exe (PID: 17120)
- bomb.exe (PID: 17104)
- bomb.exe (PID: 17076)
- bomb.exe (PID: 17144)
- bomb.exe (PID: 17184)
- bomb.exe (PID: 17020)
- bomb.exe (PID: 17192)
- bomb.exe (PID: 17152)
- bomb.exe (PID: 17088)
- bomb.exe (PID: 17012)
- bomb.exe (PID: 16988)
- ScreenConnect.WindowsClient.exe (PID: 4472)
- bomb.exe (PID: 13084)
Connects to the server without a host name
- bomb.exe (PID: 2480)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 580)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 548)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 956)
- bomb.exe (PID: 920)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 5232)
- bomb.exe (PID: 848)
- bomb.exe (PID: 4796)
- bomb.exe (PID: 4936)
- bomb.exe (PID: 5216)
- bomb.exe (PID: 4816)
- bomb.exe (PID: 4352)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 4200)
- bomb.exe (PID: 4916)
- bomb.exe (PID: 2224)
- bomb.exe (PID: 4828)
- bomb.exe (PID: 4160)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 5004)
- bomb.exe (PID: 4548)
- bomb.exe (PID: 12256)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 6804)
- bomb.exe (PID: 1104)
- bomb.exe (PID: 12176)
- bomb.exe (PID: 8176)
- svchost.exe (PID: 17376)
- bomb.exe (PID: 9588)
- bomb.exe (PID: 5632)
- bomb.exe (PID: 7704)
- bomb.exe (PID: 2768)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 120)
- bomb.exe (PID: 4864)
- http45.152.149.15musicLamno.exe.exe (PID: 18176)
- bomb.exe (PID: 13160)
- bomb.exe (PID: 13224)
- bomb.exe (PID: 13132)
- bomb.exe (PID: 17200)
- bomb.exe (PID: 13084)
- bomb.exe (PID: 13280)
- bomb.exe (PID: 13288)
- bomb.exe (PID: 13200)
- bomb.exe (PID: 13256)
- bomb.exe (PID: 13184)
- bomb.exe (PID: 13264)
Process requests binary or script from the Internet
- bomb.exe (PID: 2480)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 580)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 548)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 4352)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 956)
- bomb.exe (PID: 920)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 4200)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 4796)
- bomb.exe (PID: 5232)
- bomb.exe (PID: 848)
- bomb.exe (PID: 4936)
- bomb.exe (PID: 5216)
- bomb.exe (PID: 4816)
- bomb.exe (PID: 4484)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 4916)
- bomb.exe (PID: 2224)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 4864)
- bomb.exe (PID: 4828)
- bomb.exe (PID: 4160)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 692)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 5004)
- bomb.exe (PID: 5240)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 4548)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 6804)
- bomb.exe (PID: 12256)
- bomb.exe (PID: 1104)
- bomb.exe (PID: 9588)
- bomb.exe (PID: 12176)
- bomb.exe (PID: 8176)
- bomb.exe (PID: 5632)
- bomb.exe (PID: 7704)
- bomb.exe (PID: 2768)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 13224)
- bomb.exe (PID: 120)
- bomb.exe (PID: 13160)
- bomb.exe (PID: 13132)
- bomb.exe (PID: 13200)
- bomb.exe (PID: 13084)
- bomb.exe (PID: 17200)
- bomb.exe (PID: 13288)
- bomb.exe (PID: 13280)
- bomb.exe (PID: 13256)
- bomb.exe (PID: 13184)
- bomb.exe (PID: 13208)
- bomb.exe (PID: 13264)
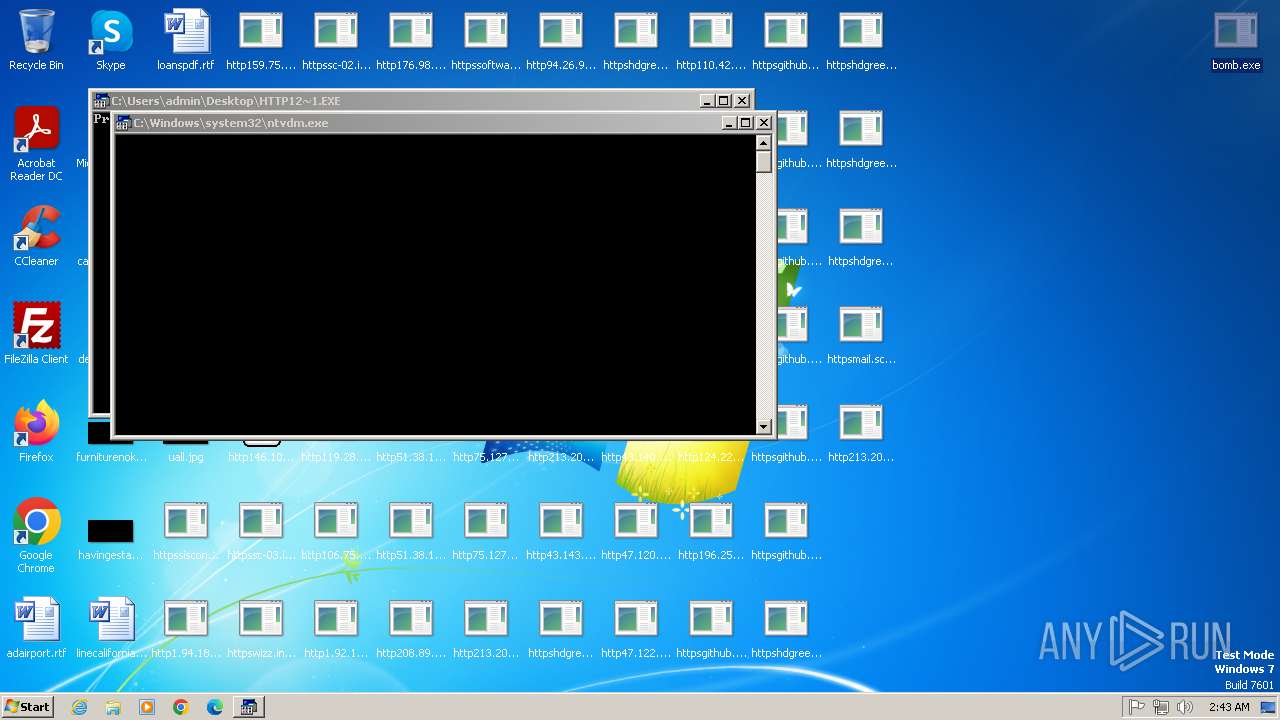
Creates file in the systems drive root
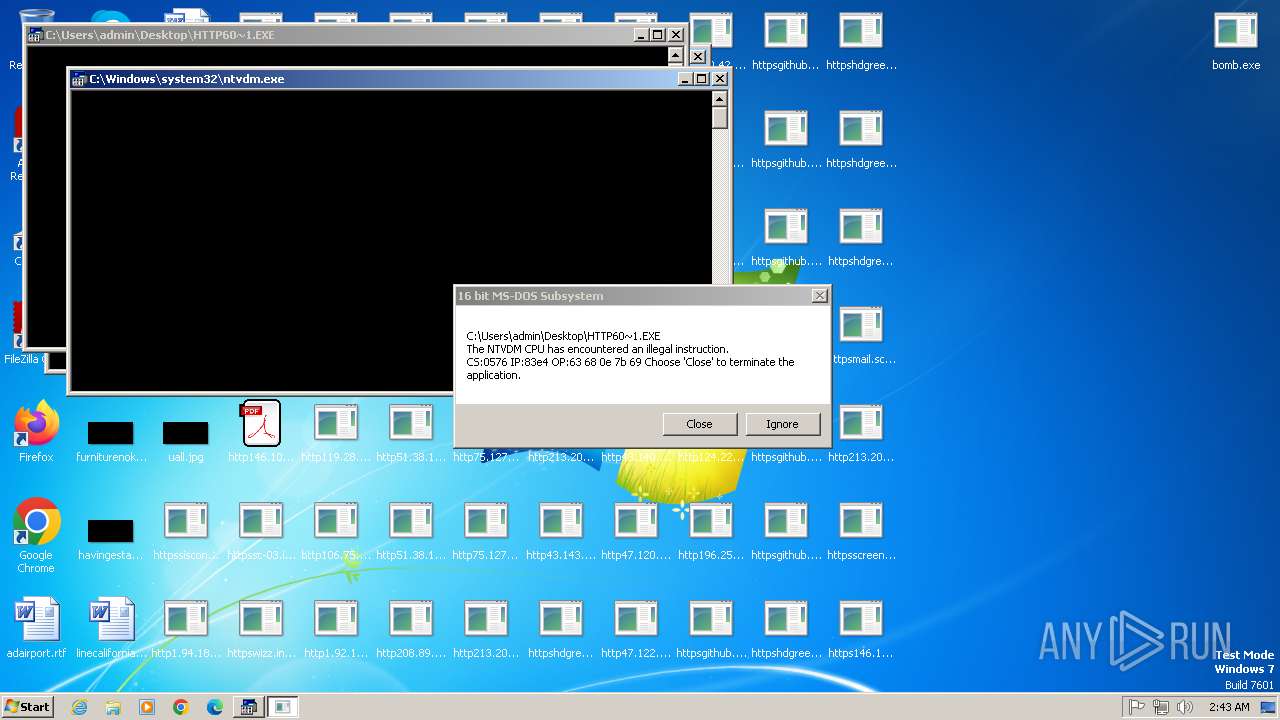
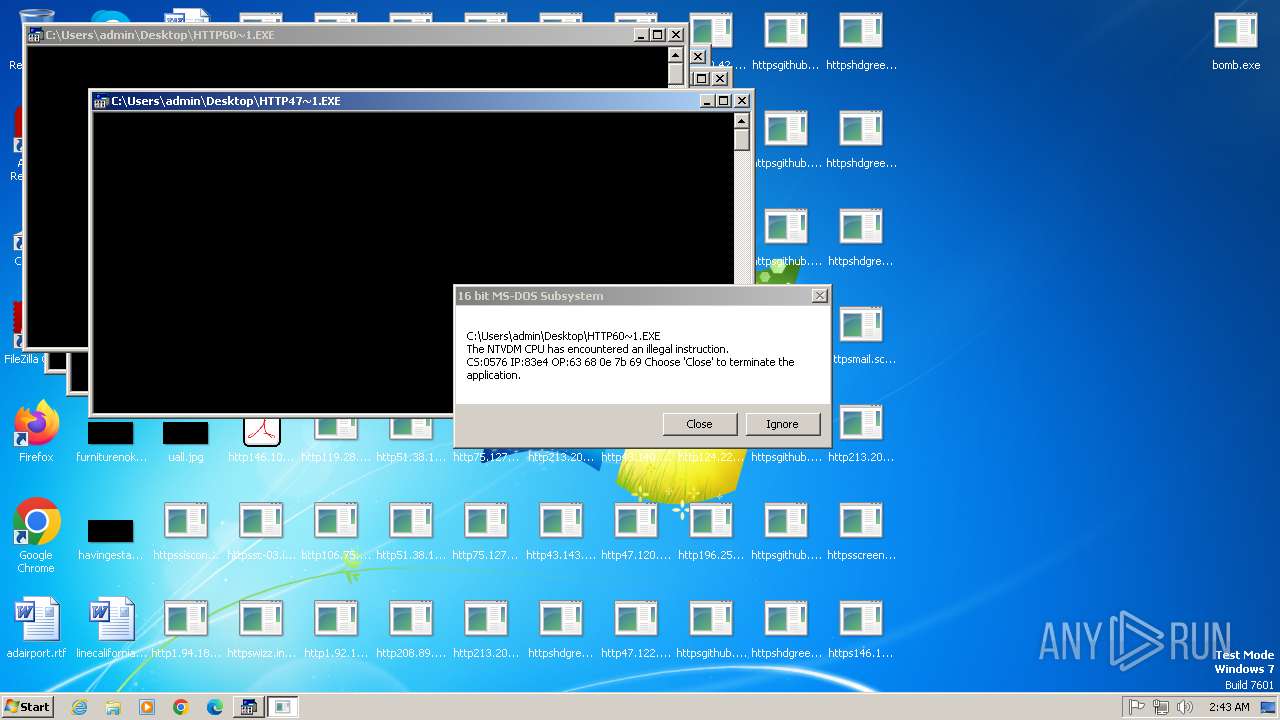
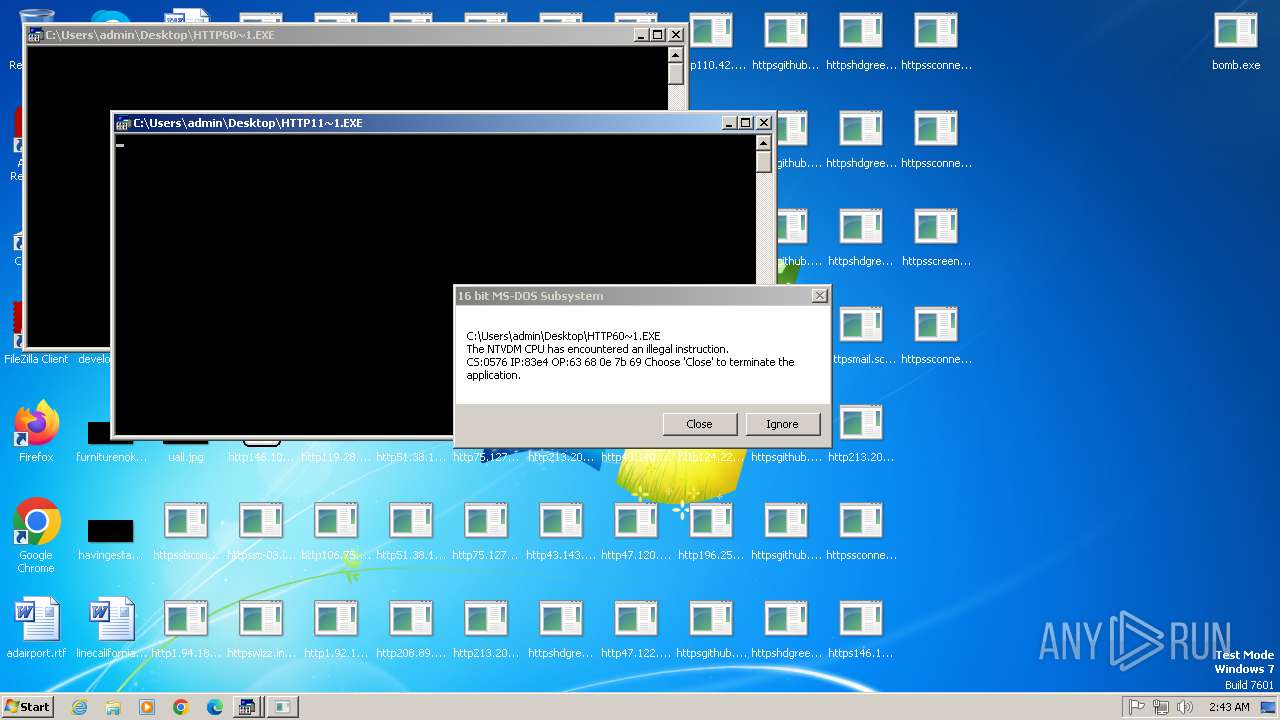
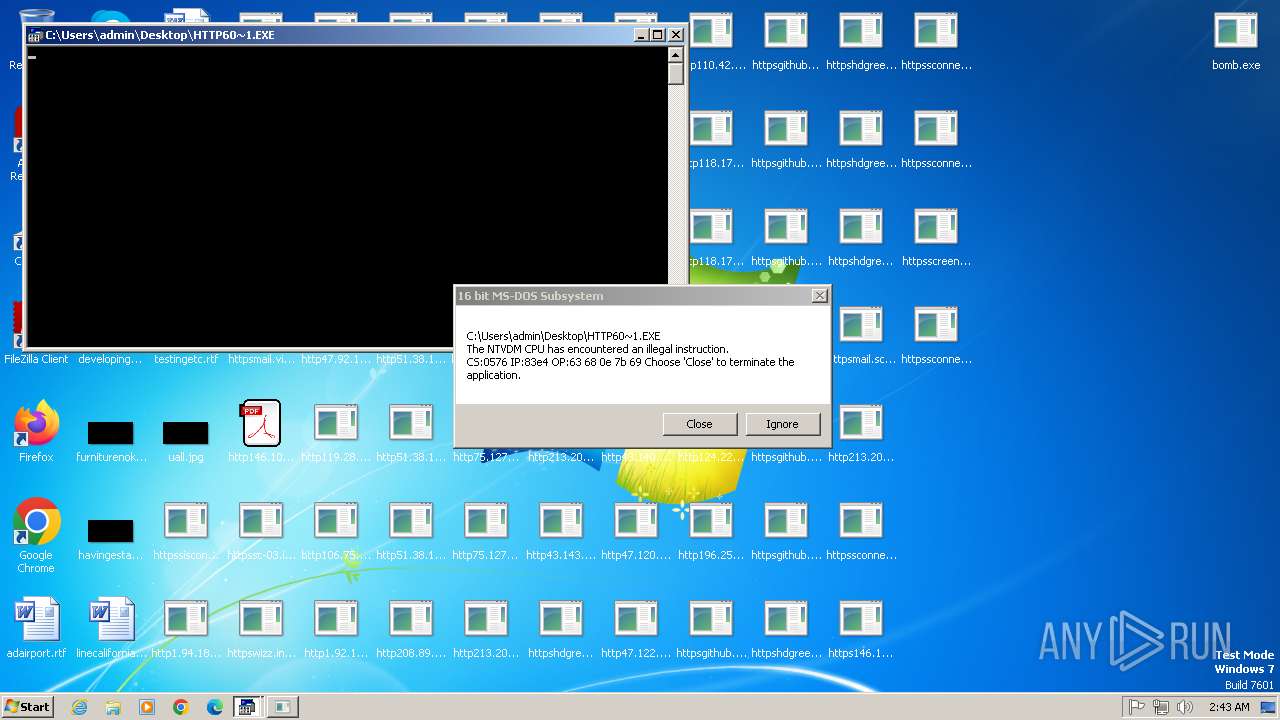
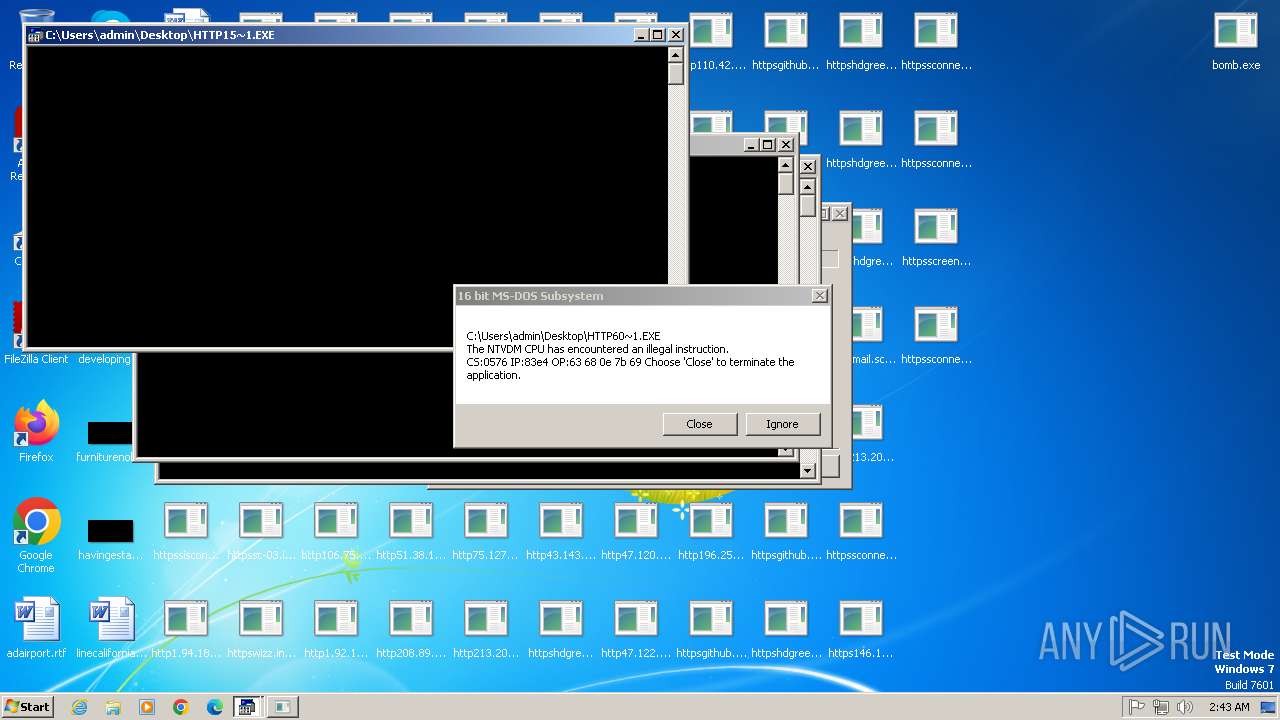
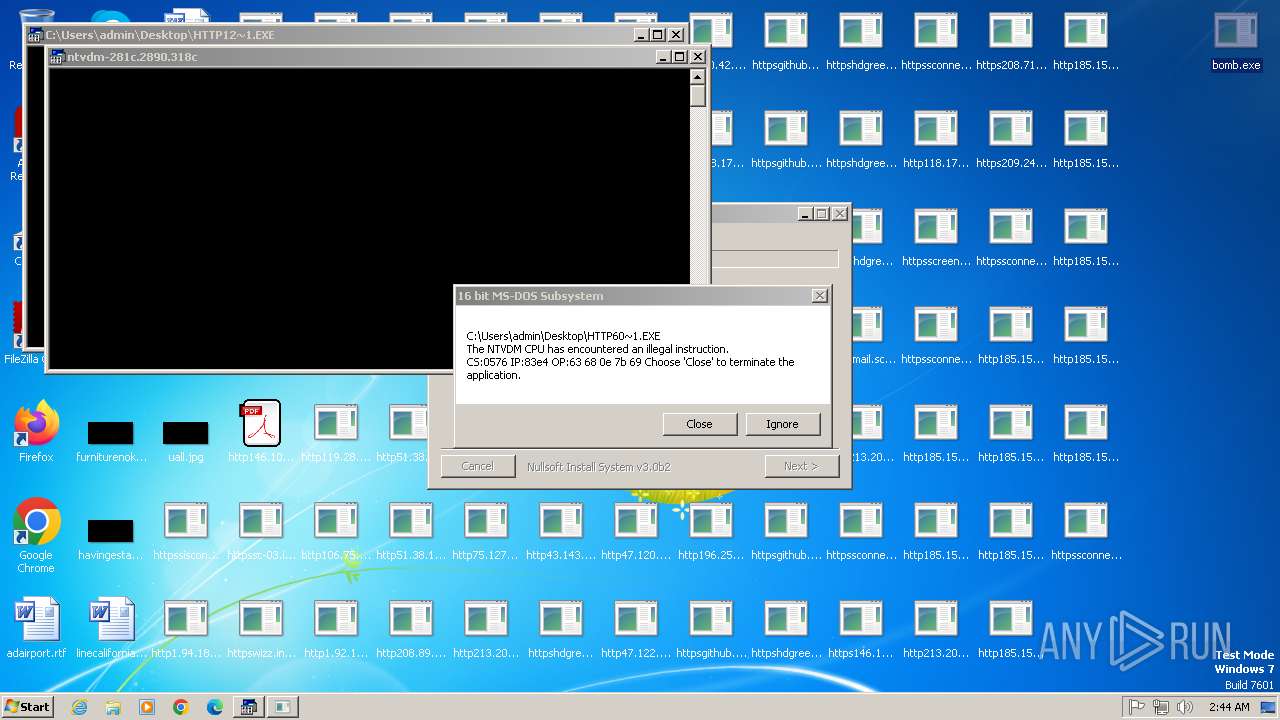
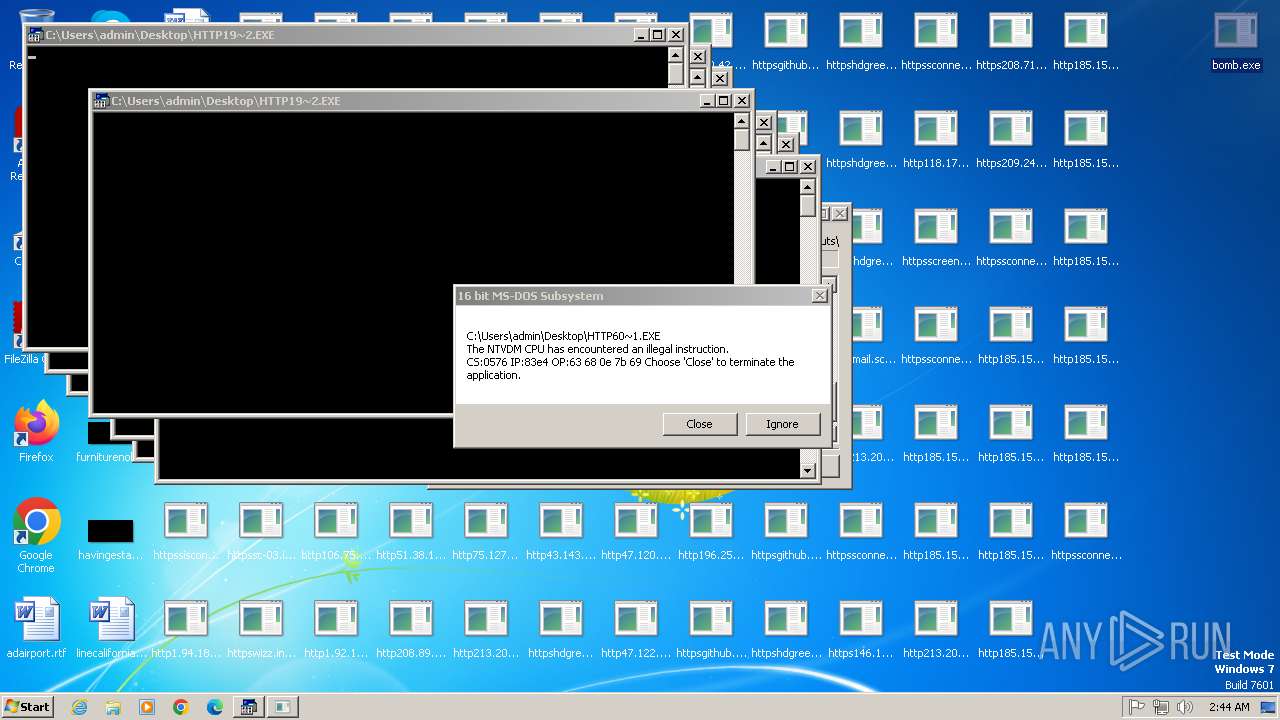
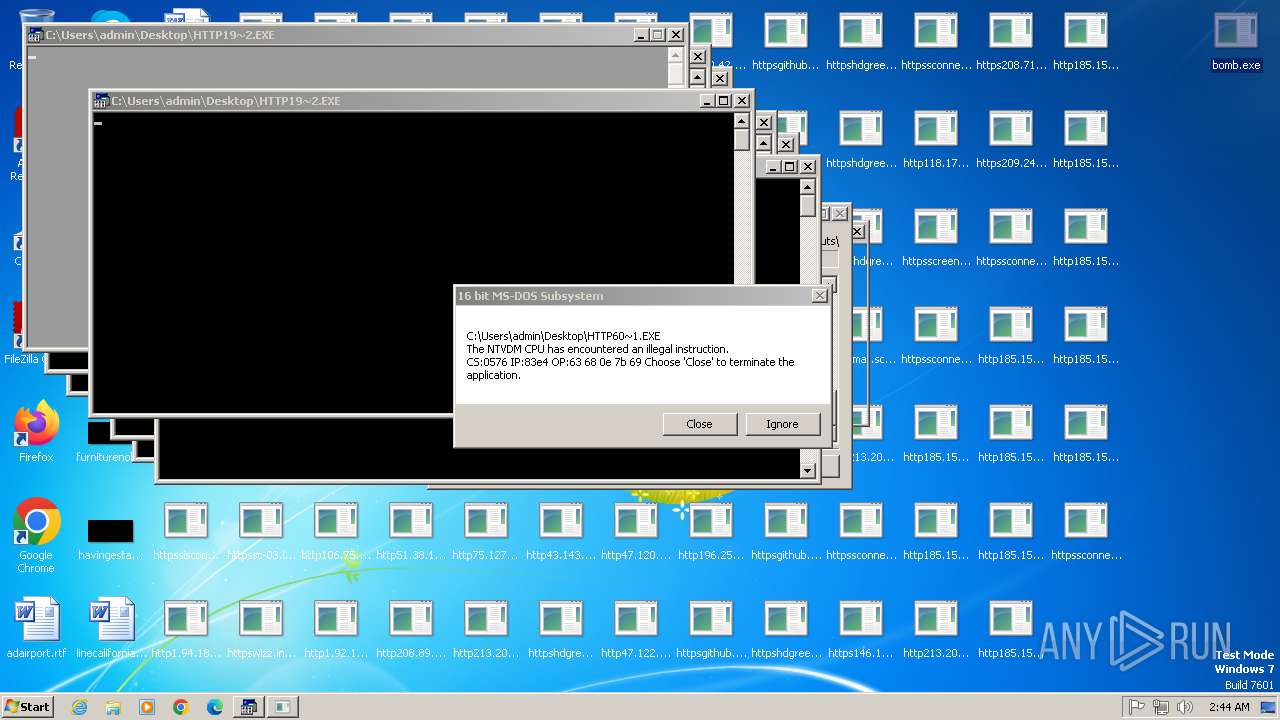
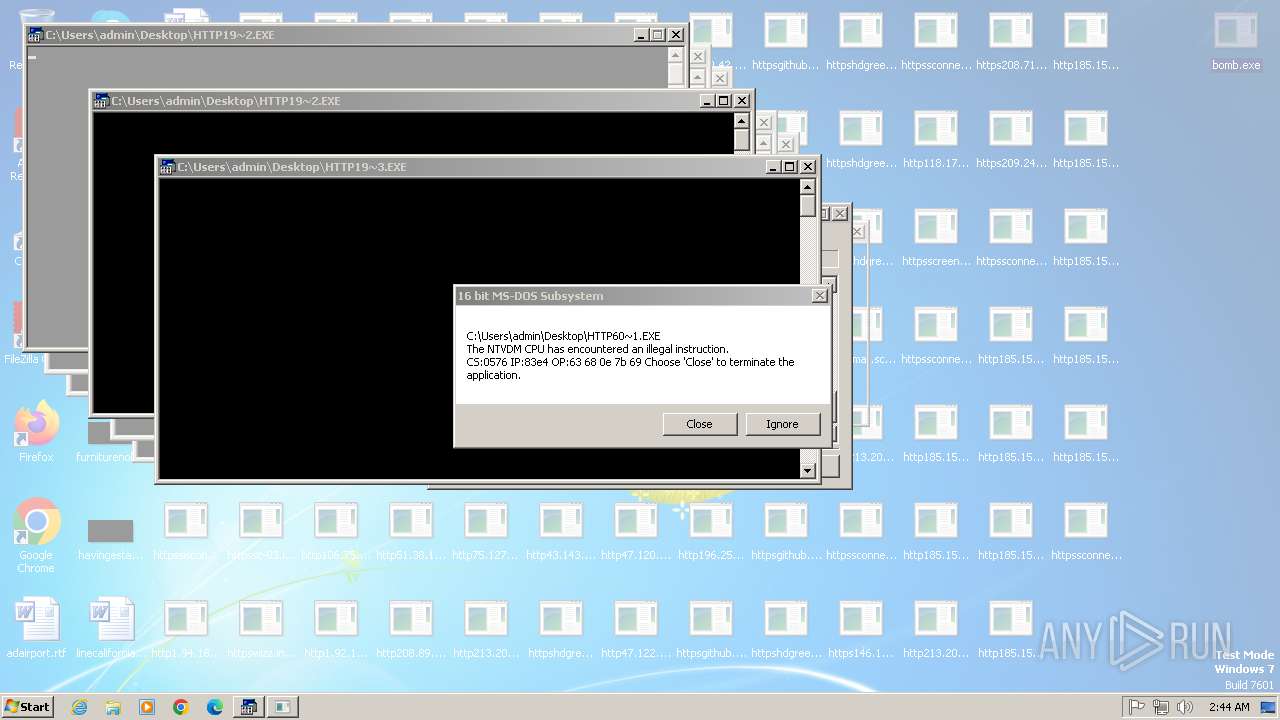
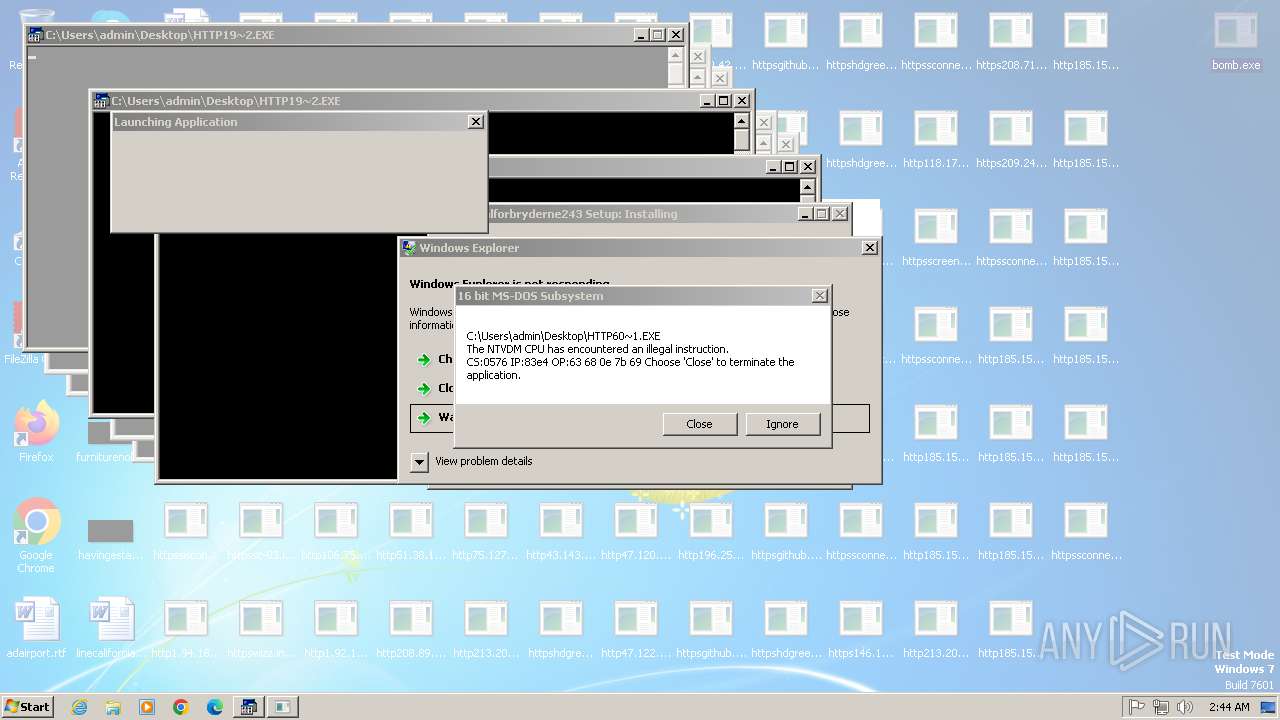
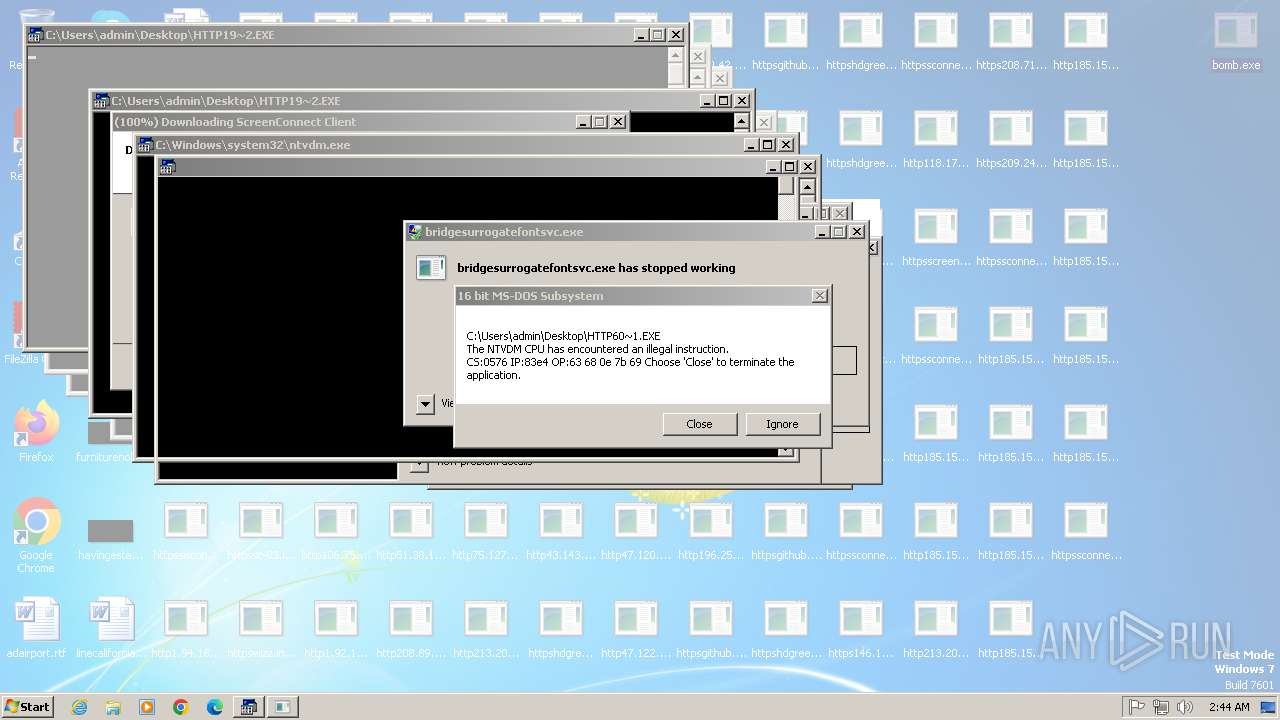
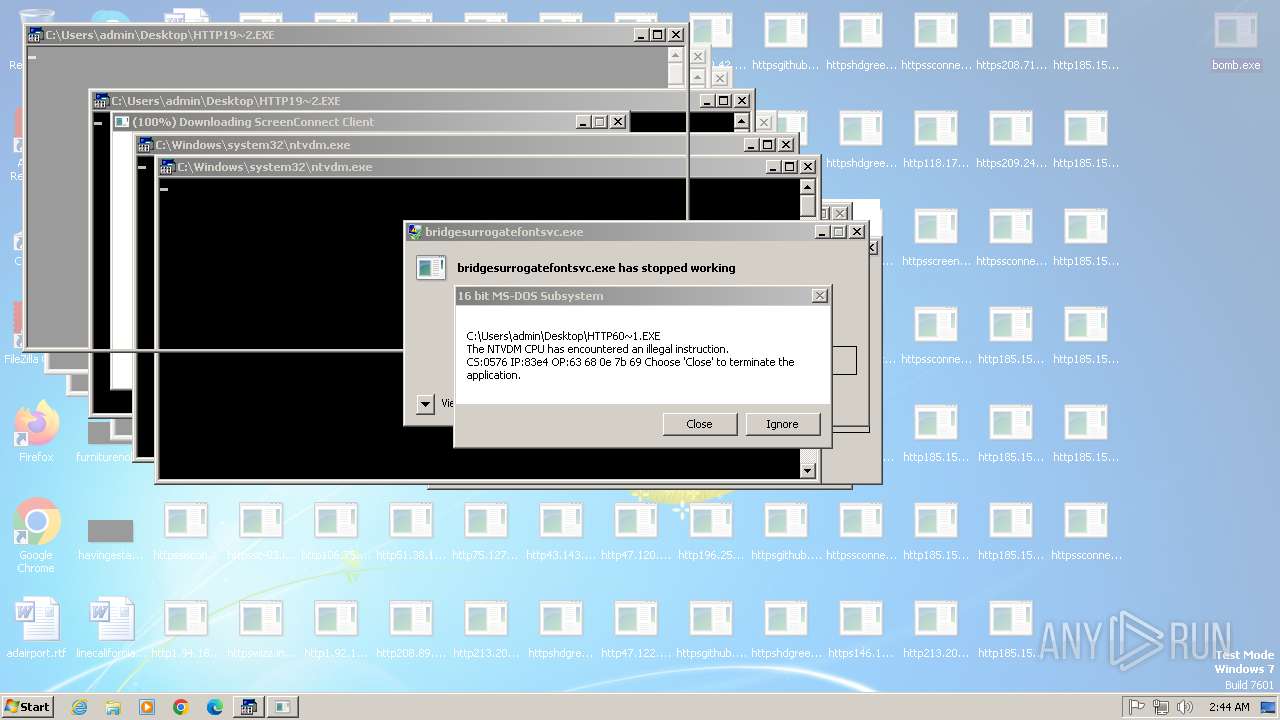
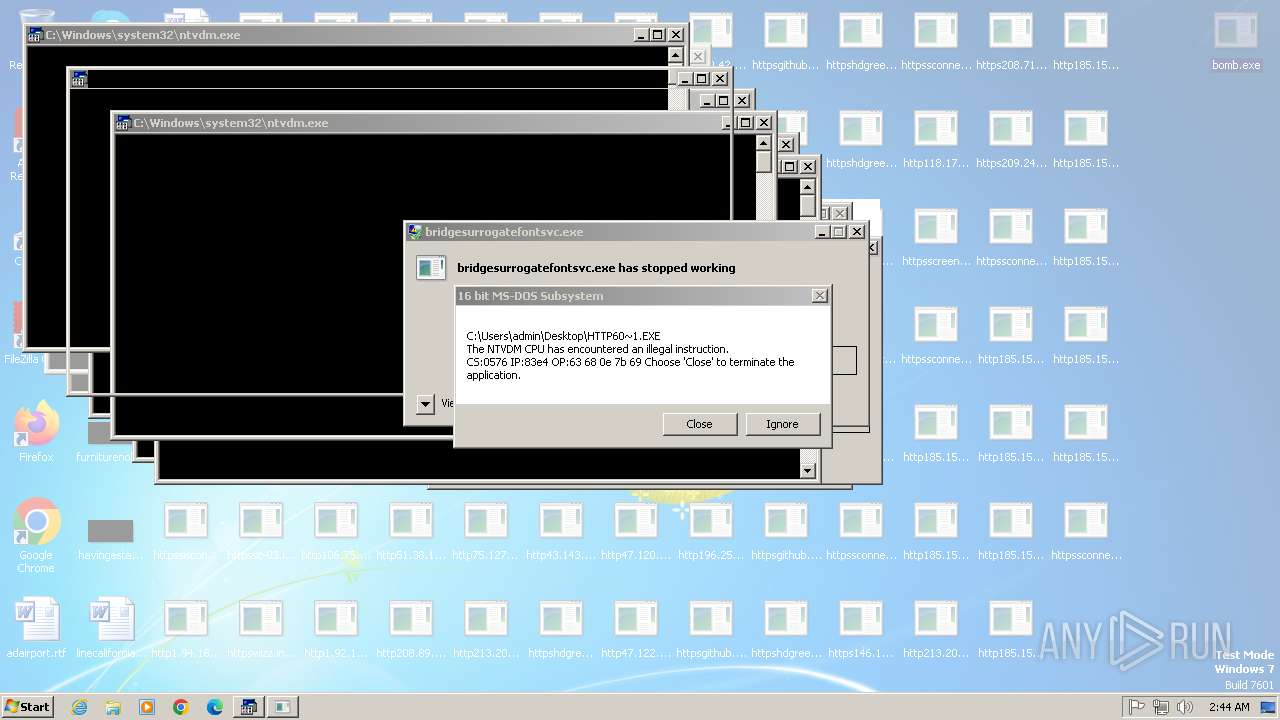
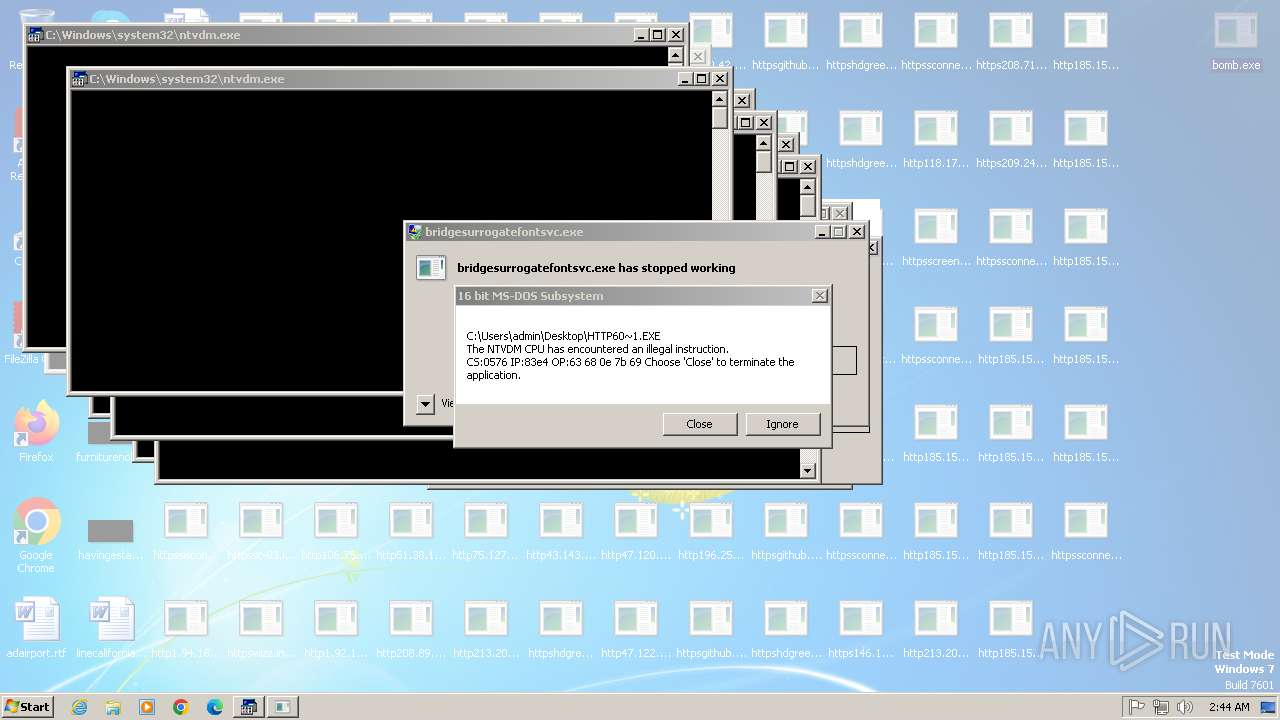
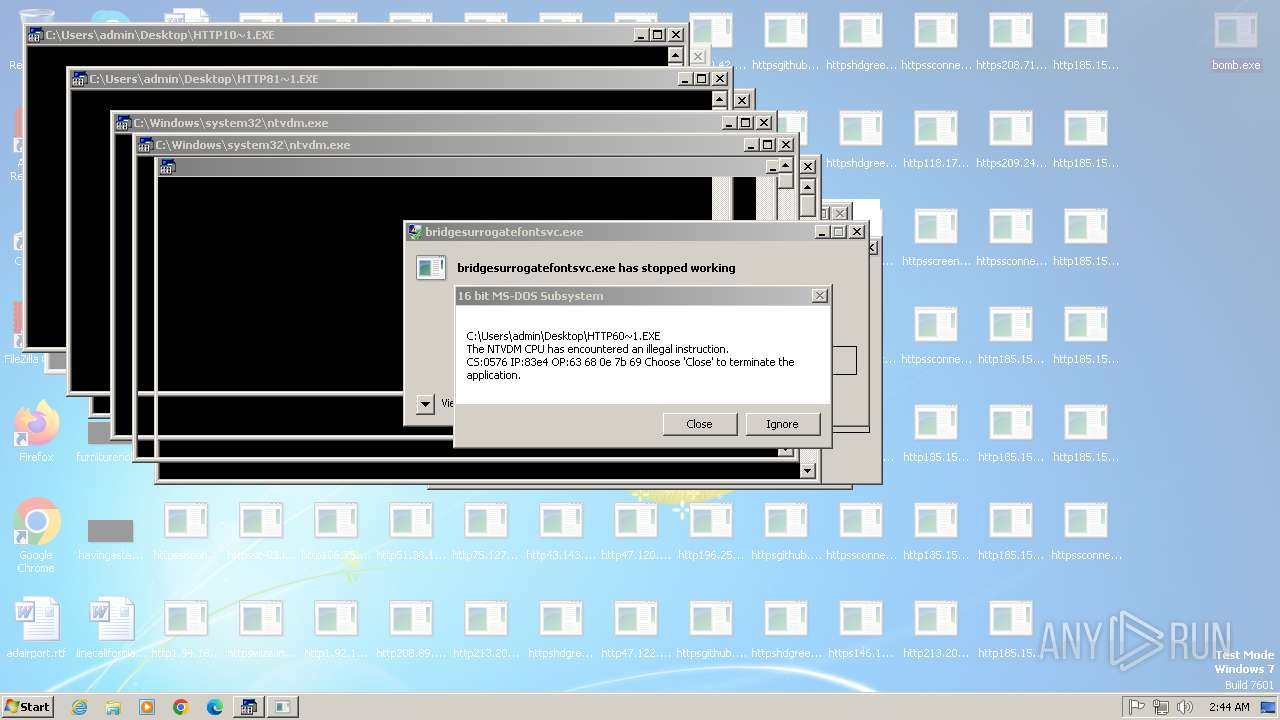
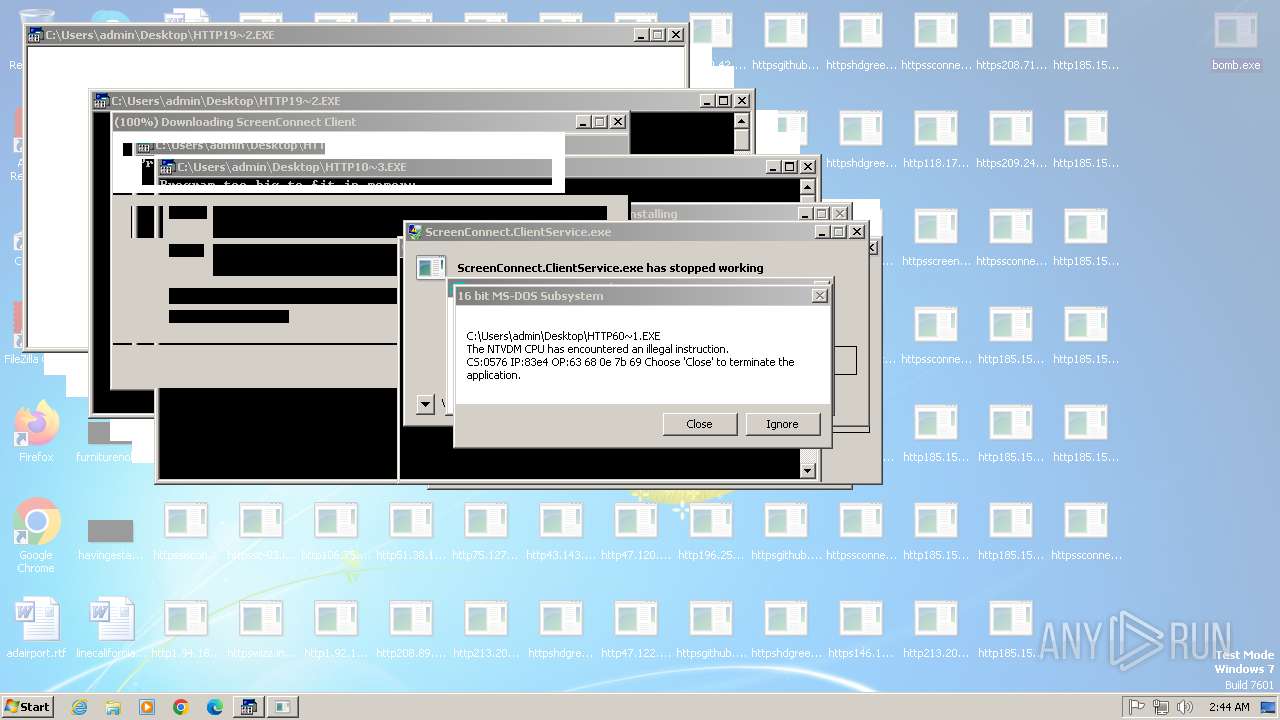
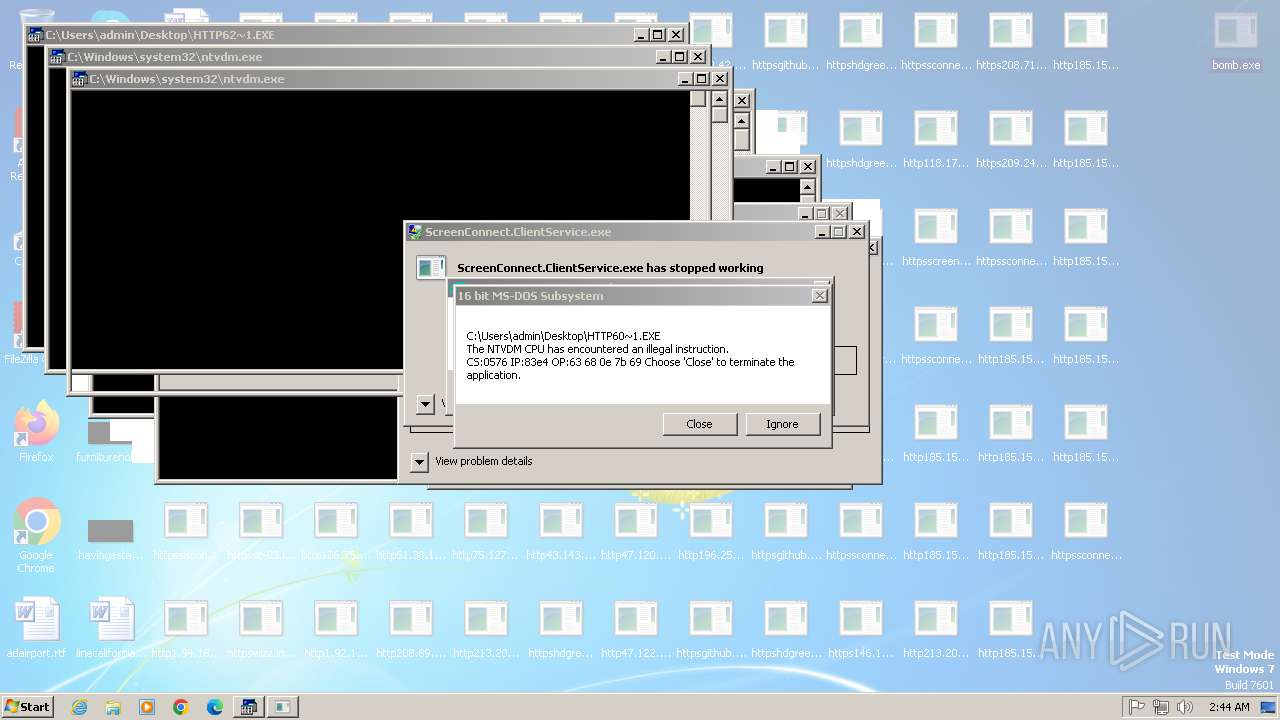
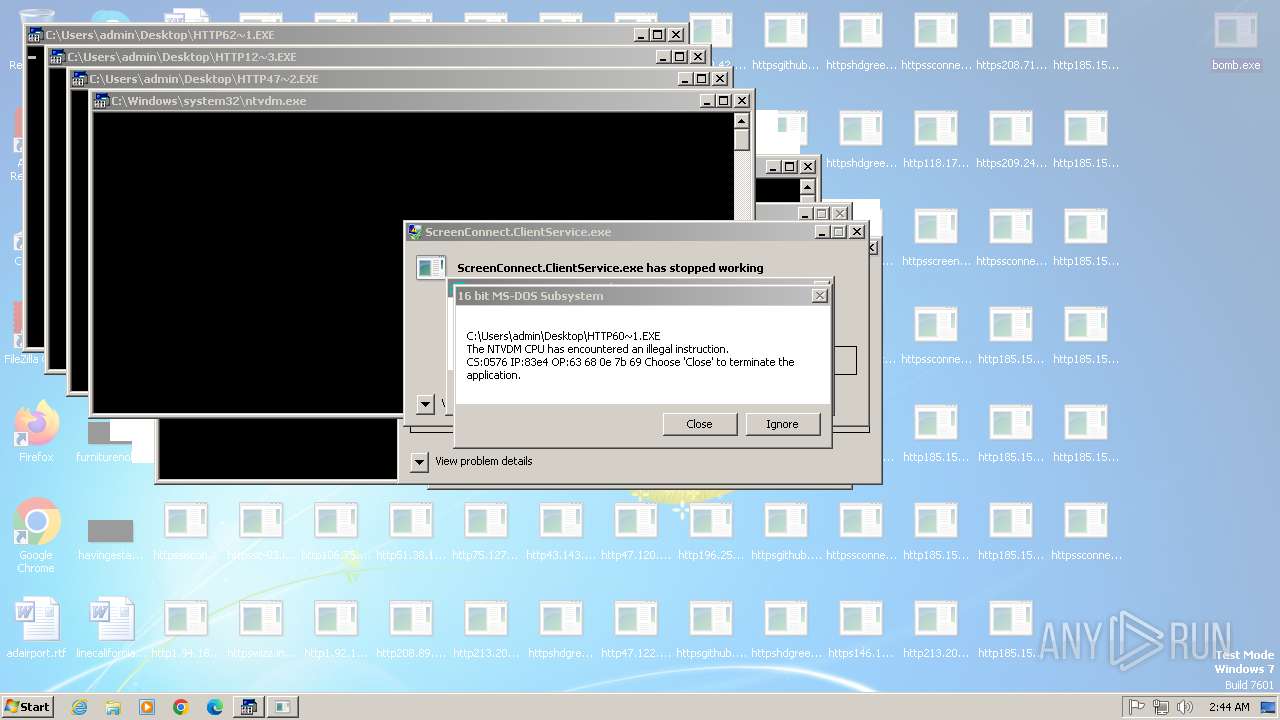
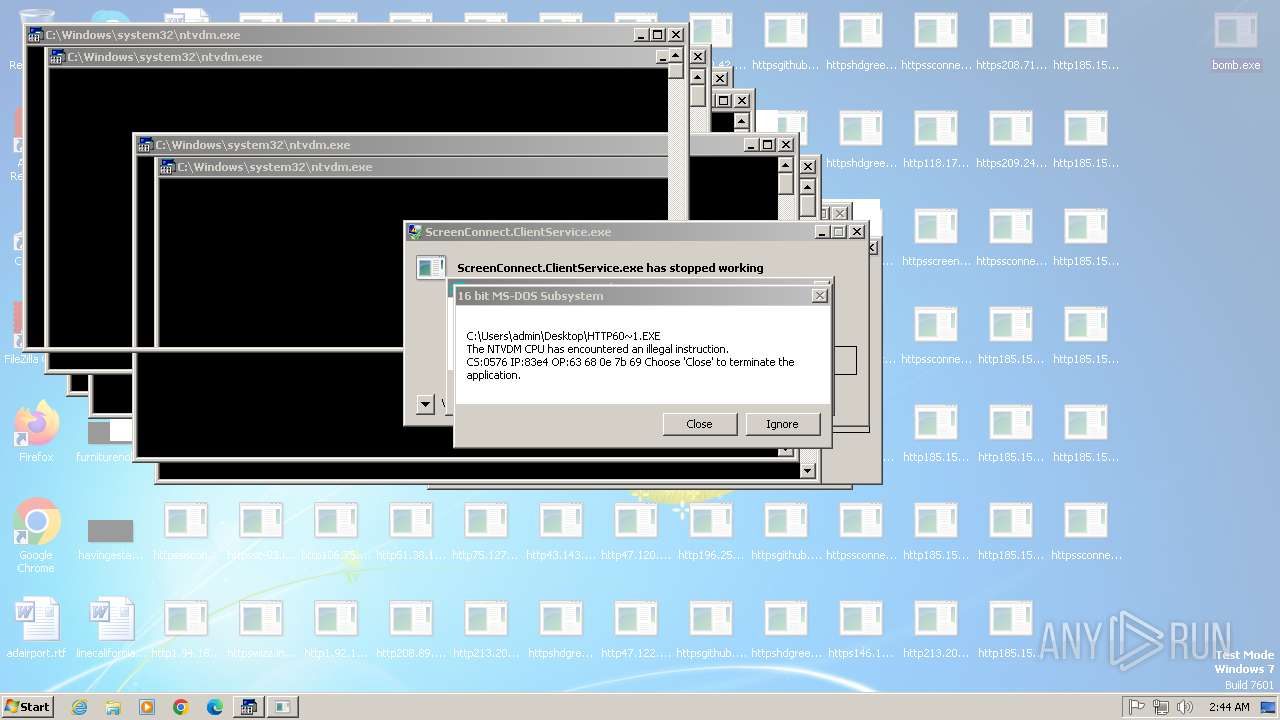
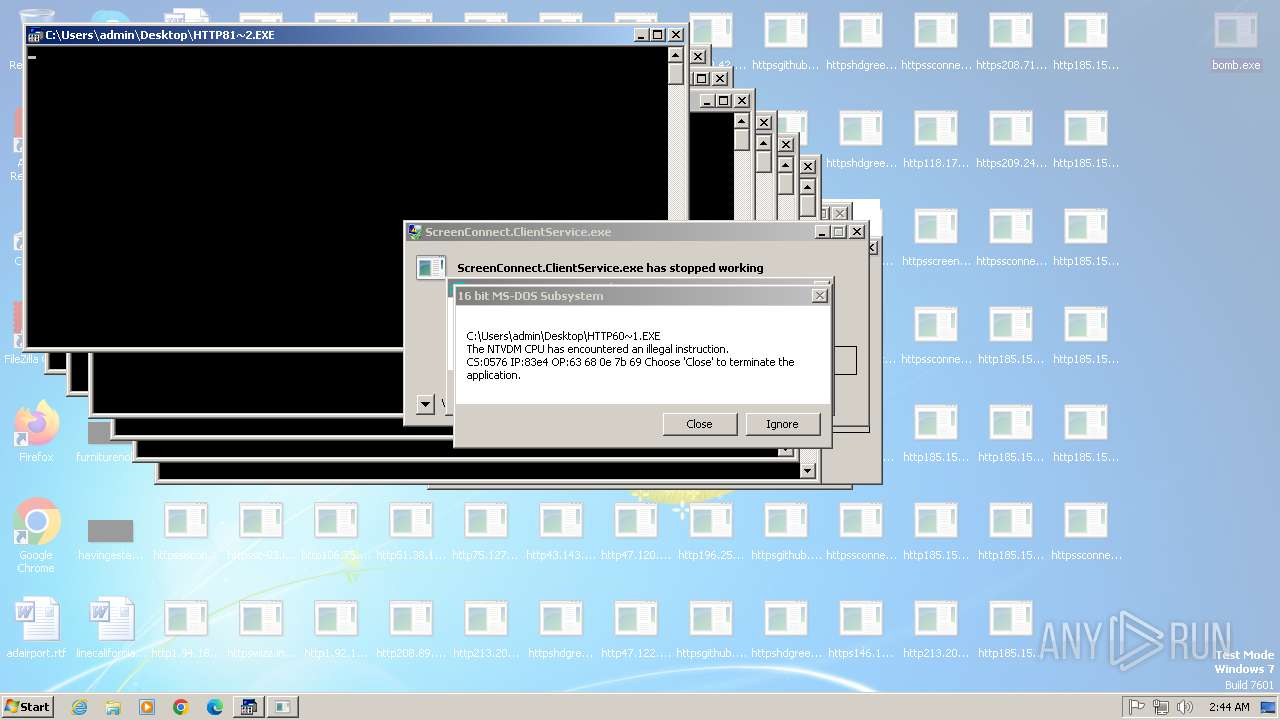
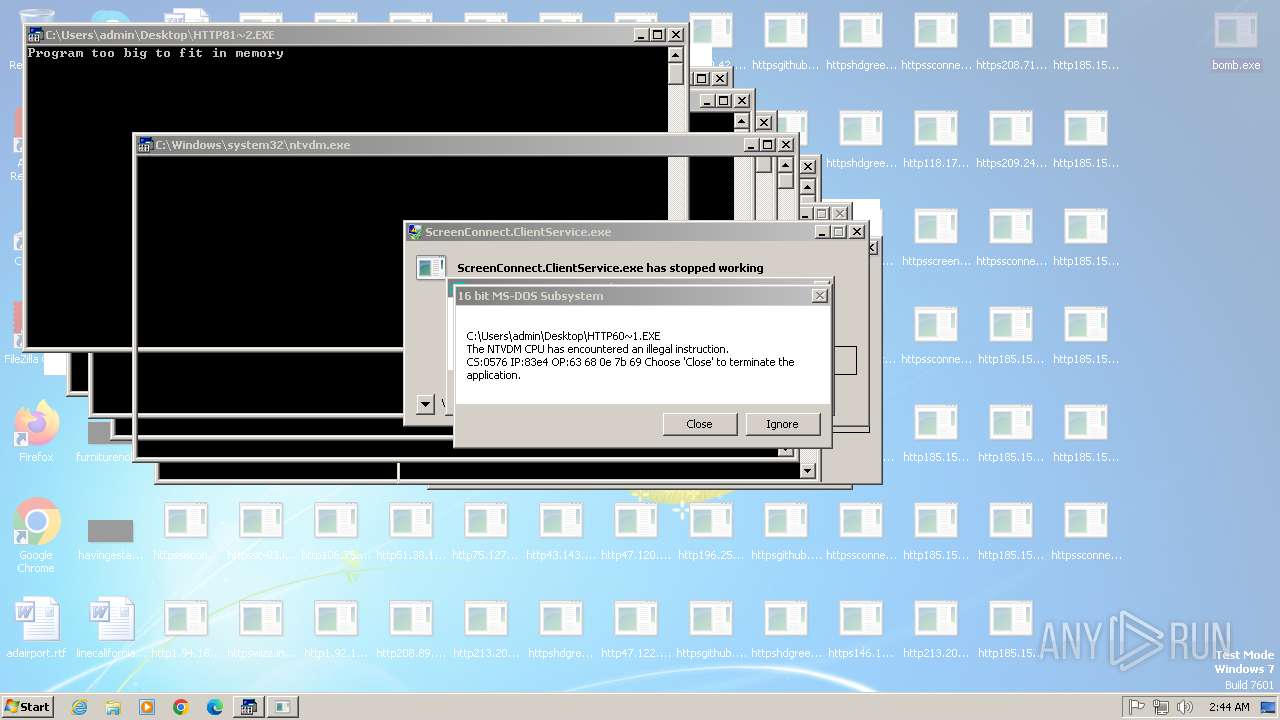
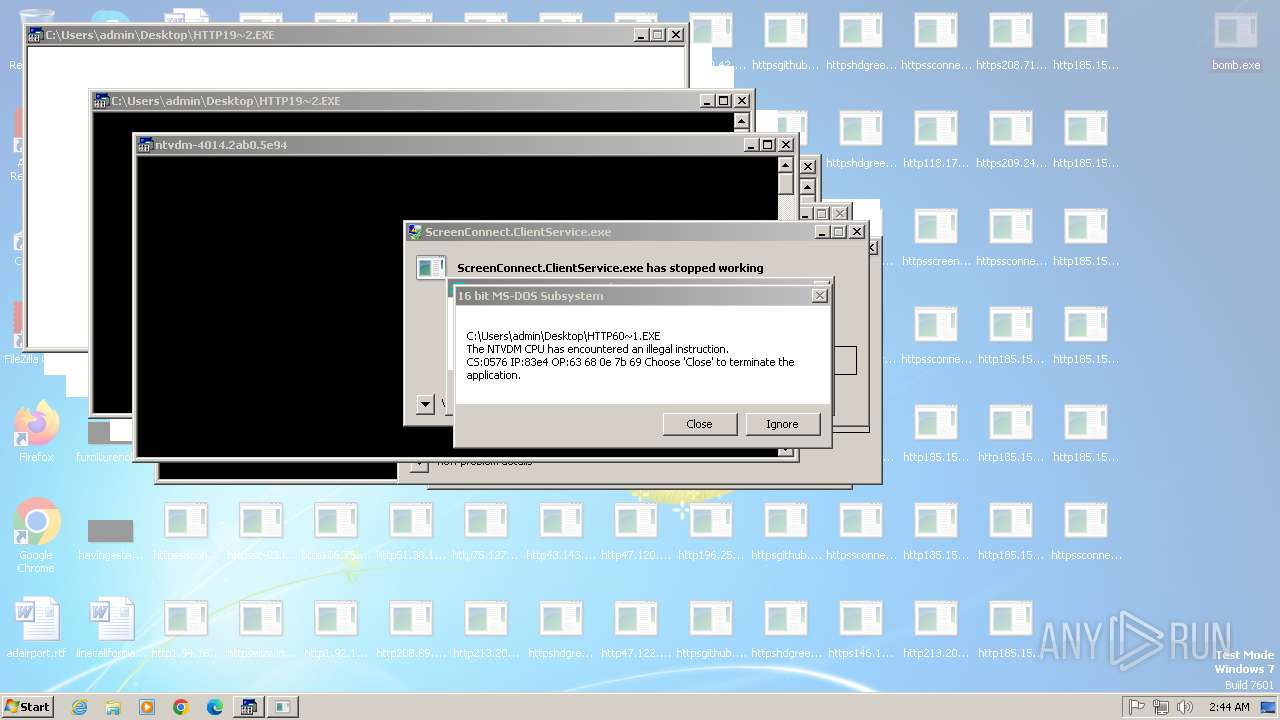
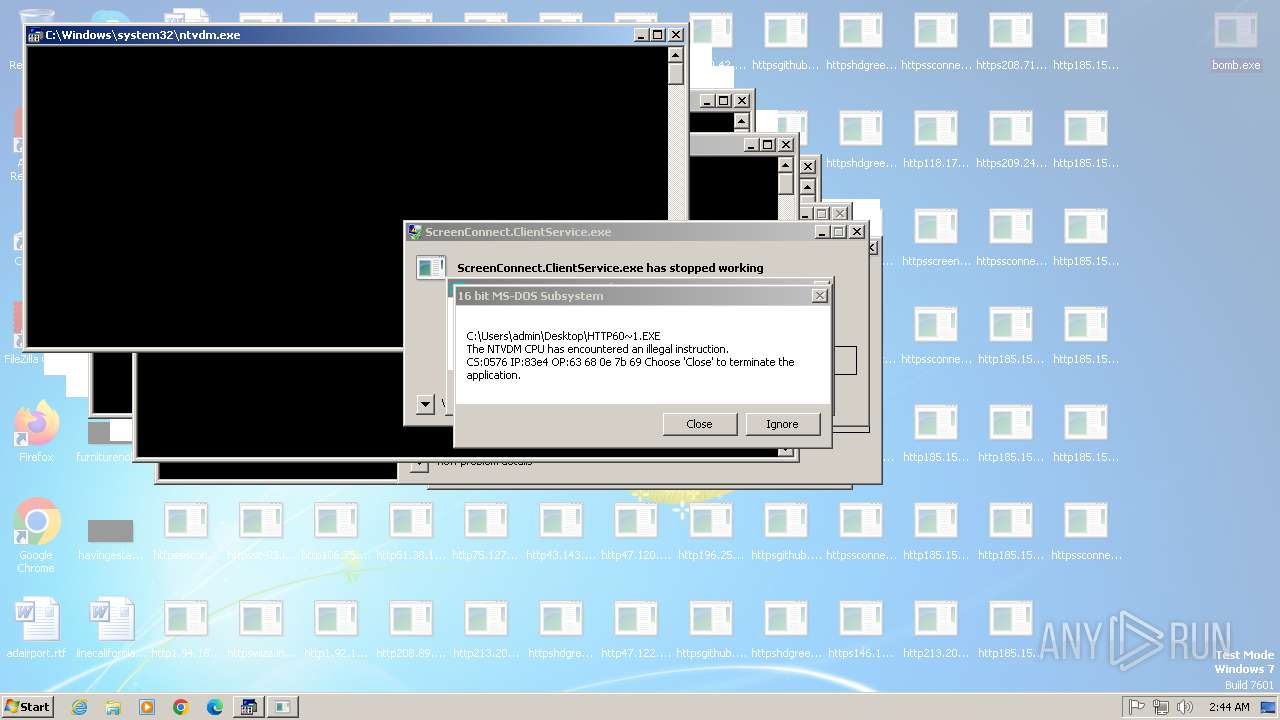
- ntvdm.exe (PID: 3876)
Reads security settings of Internet Explorer
- dfsvc.exe (PID: 1800)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- bomb.exe (PID: 2480)
- ScreenConnect.ClientService.exe (PID: 2428)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- ScreenConnect.ClientService.exe (PID: 2796)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- ScreenConnect.ClientService.exe (PID: 2516)
Reads Internet Explorer settings
- dfsvc.exe (PID: 1800)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 1800)
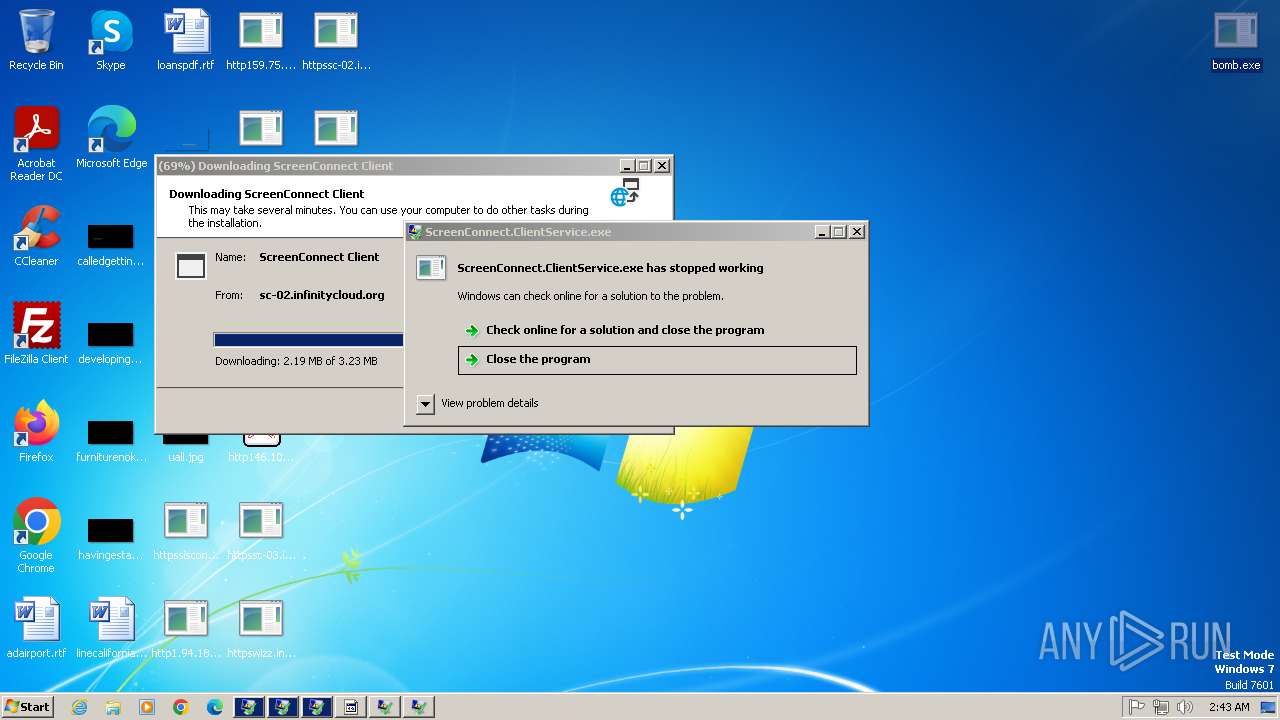
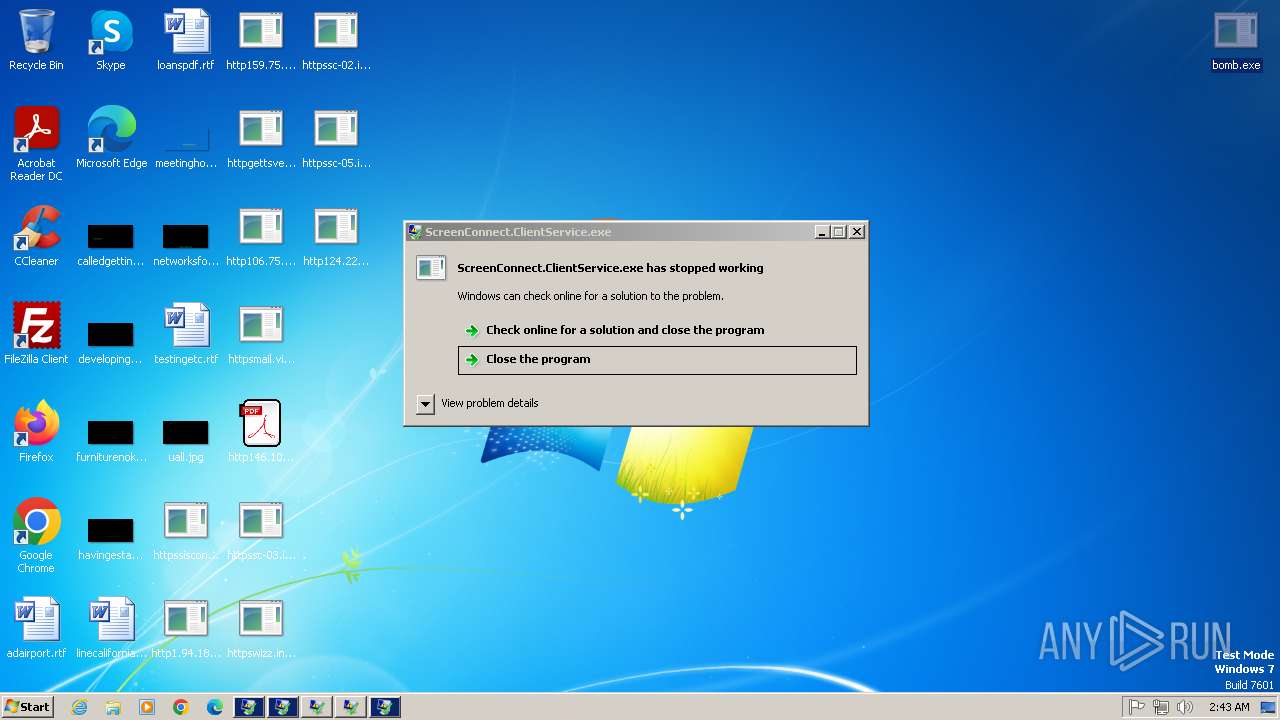
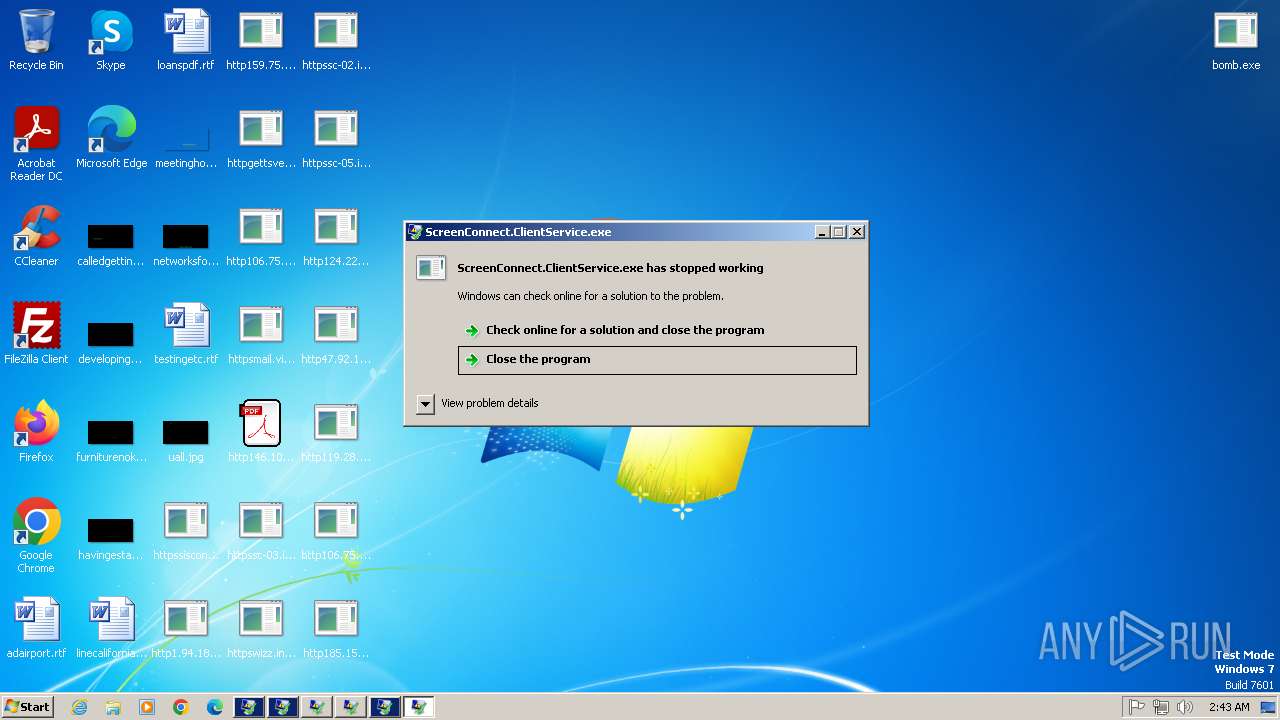
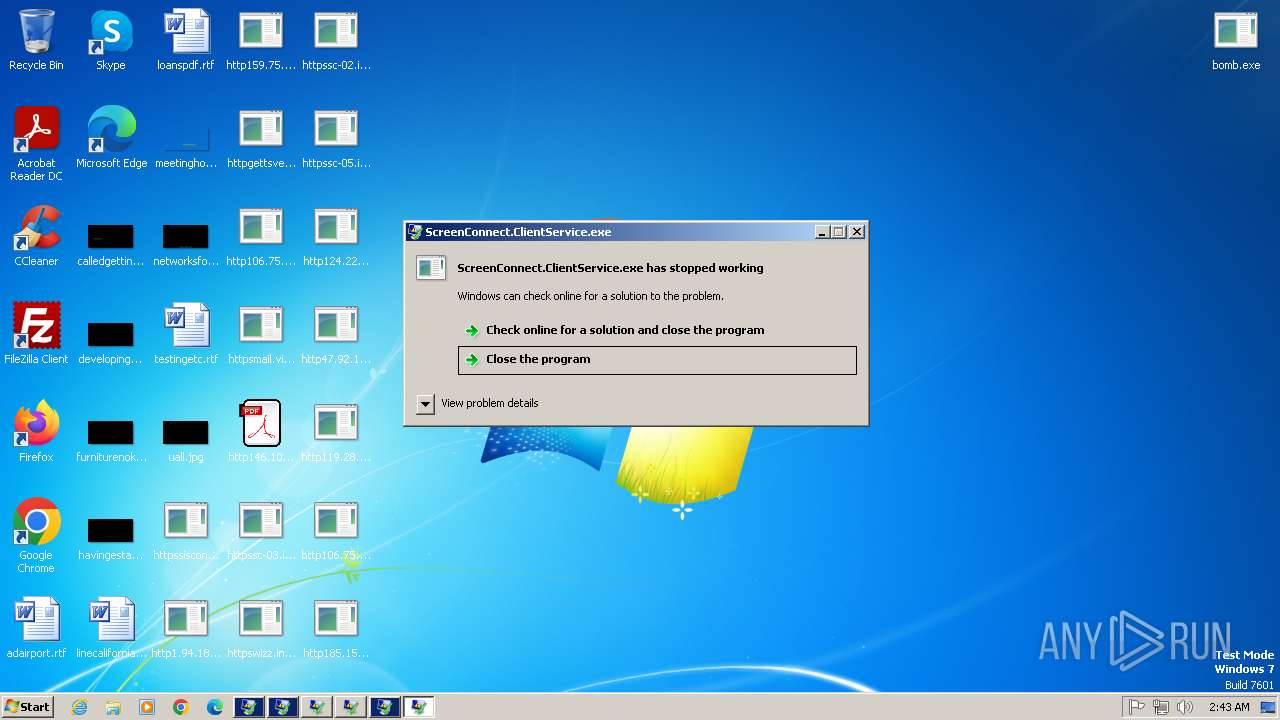
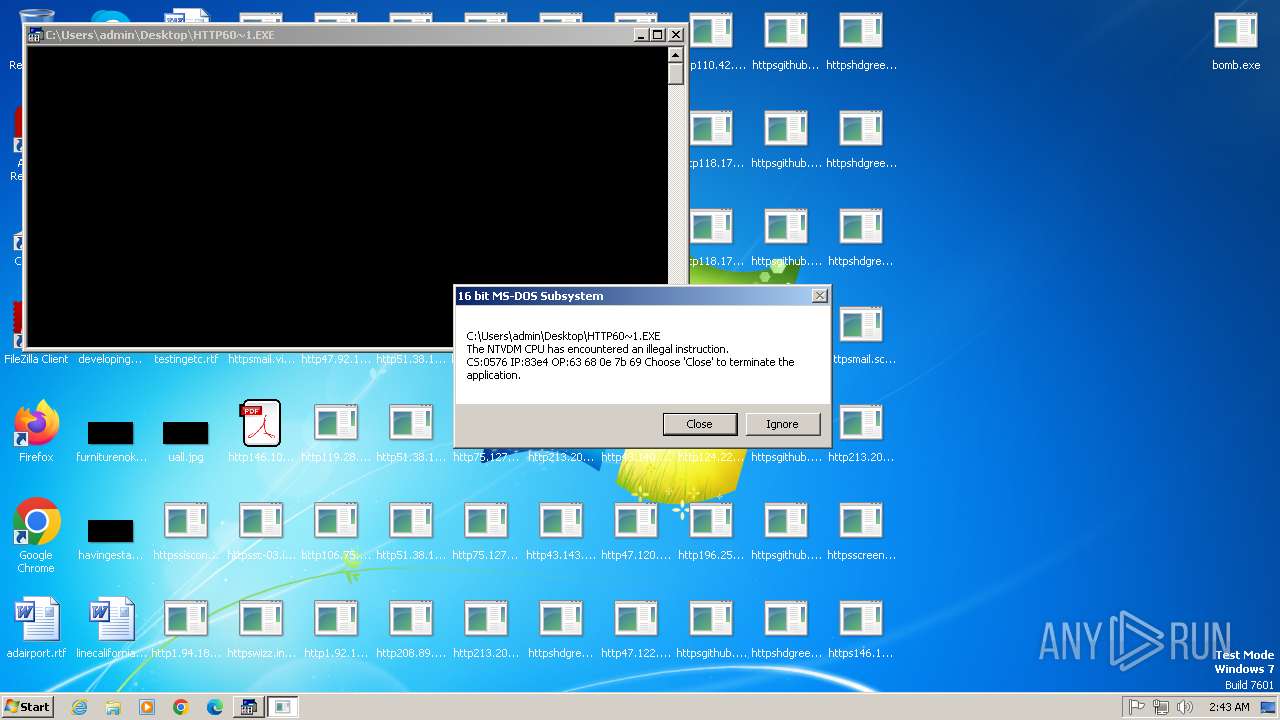
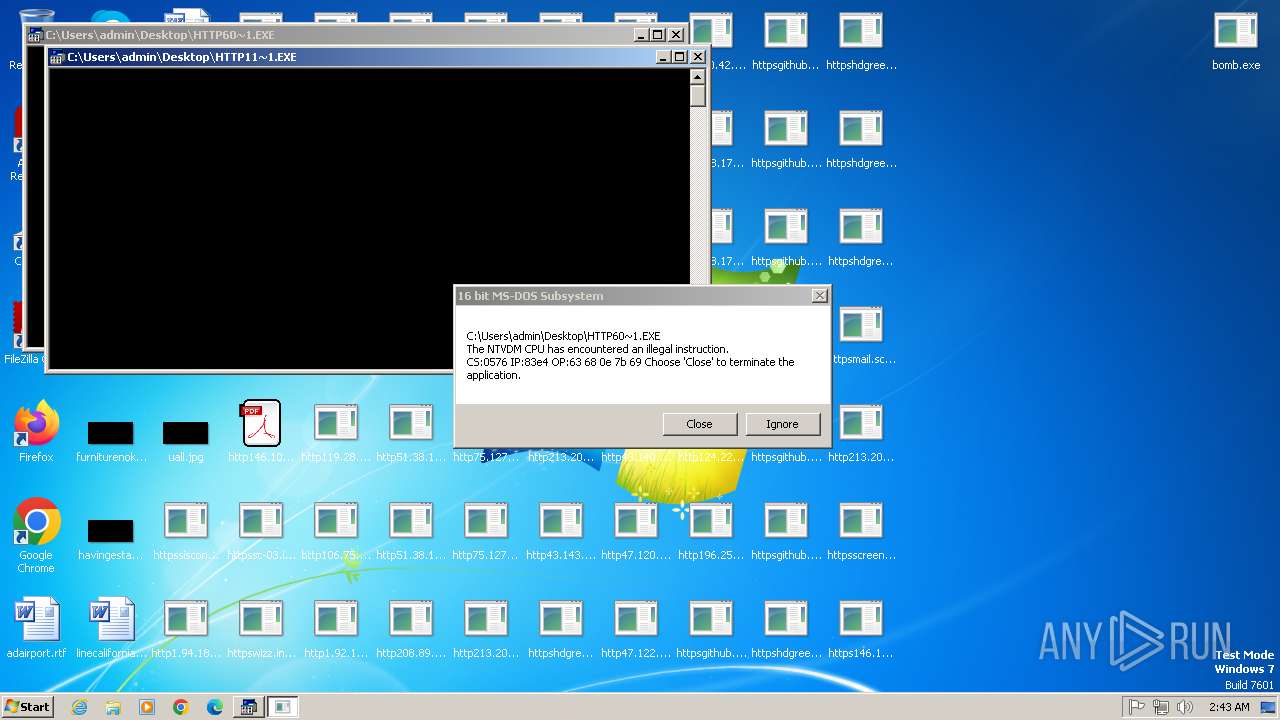
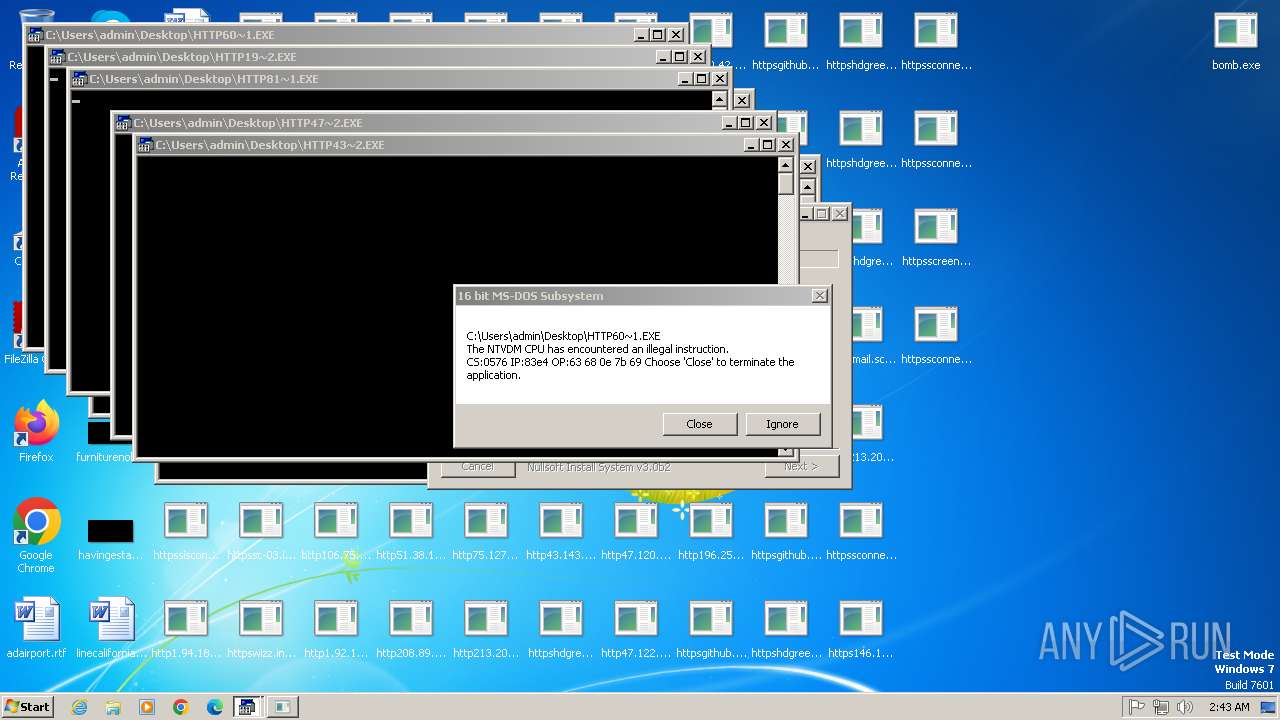
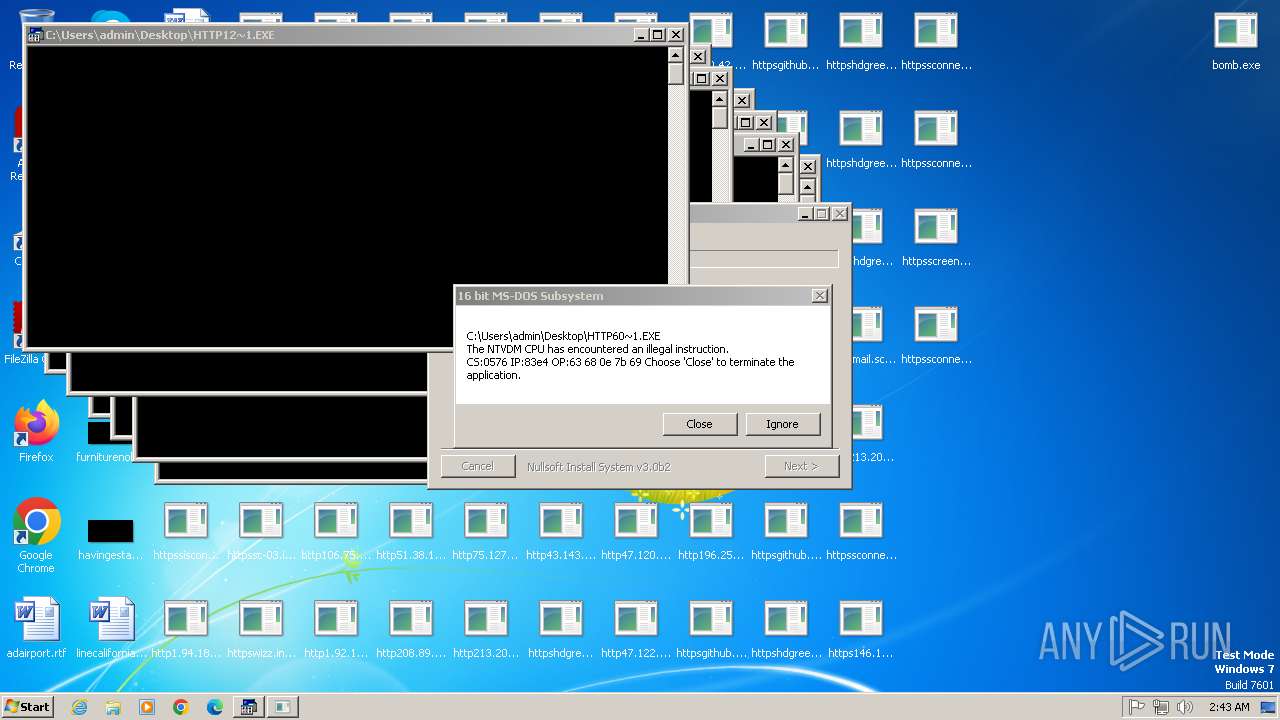
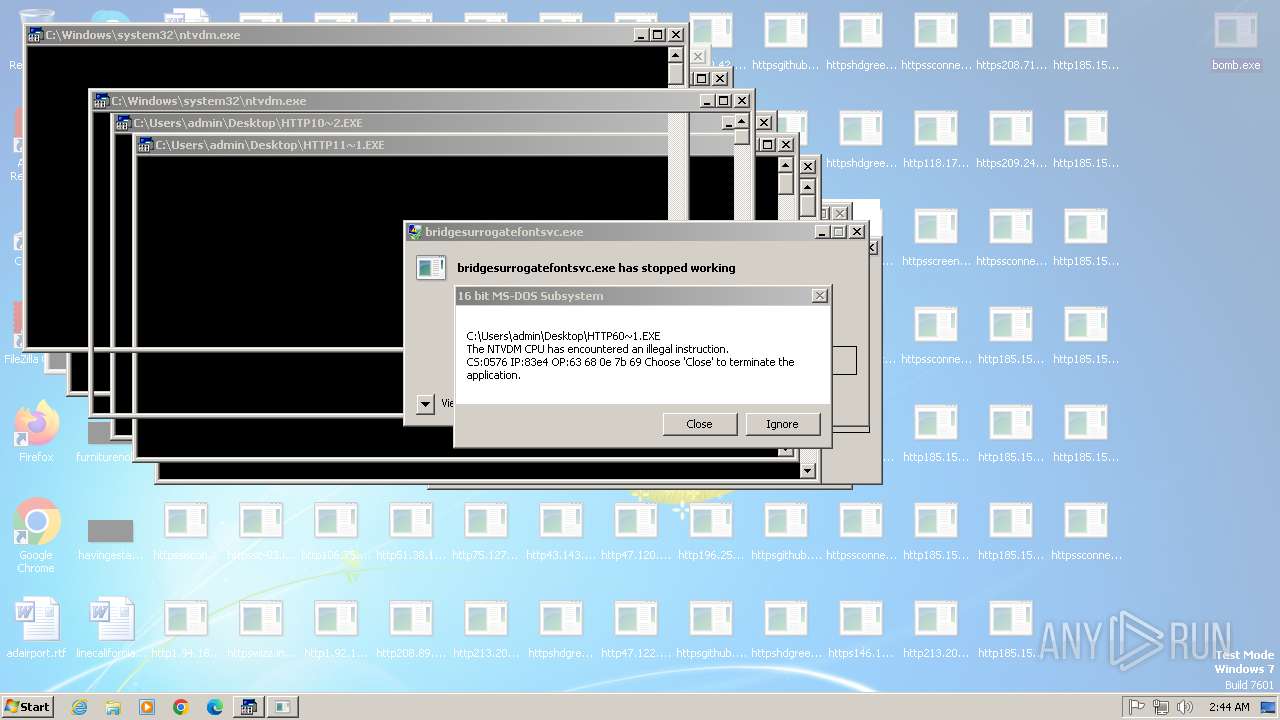
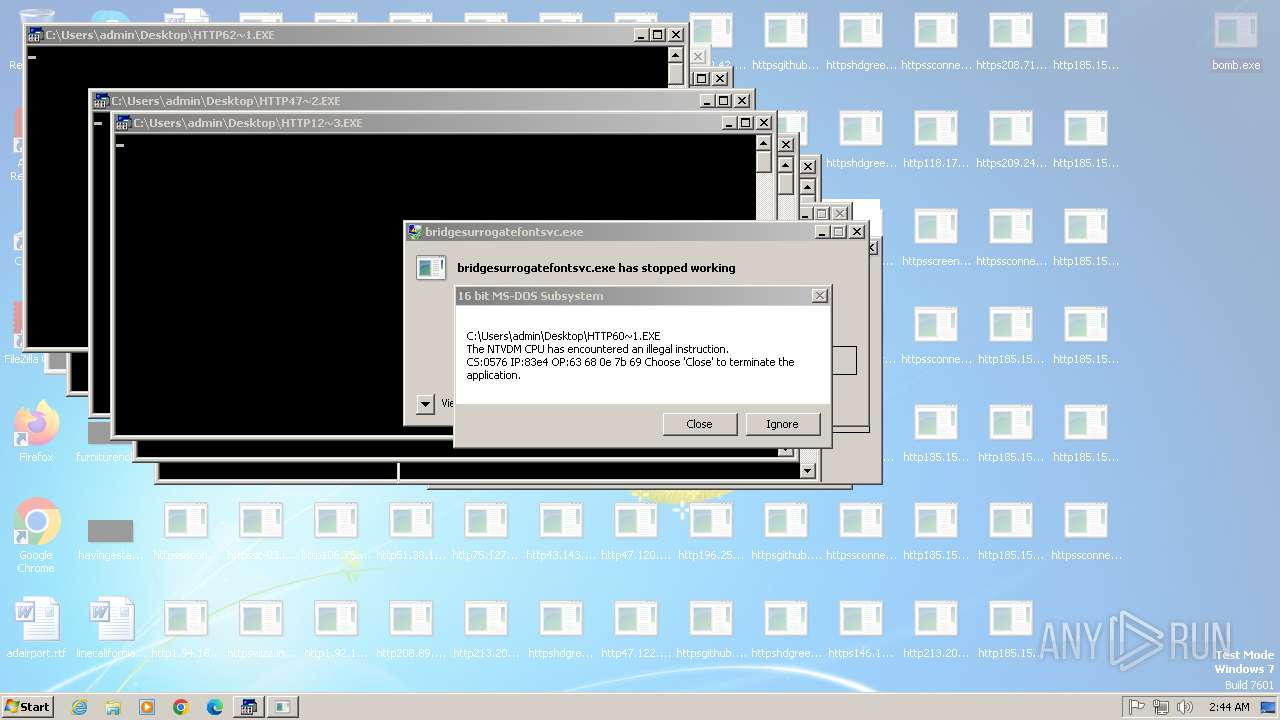
Executes application which crashes
- svchost.exe (PID: 3412)
Process drops legitimate windows executable
- bomb.exe (PID: 2480)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 920)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 956)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 4392)
- bomb.exe (PID: 4400)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 5112)
- bomb.exe (PID: 4936)
- bomb.exe (PID: 5240)
- bomb.exe (PID: 4804)
- bomb.exe (PID: 5232)
- bomb.exe (PID: 848)
- bomb.exe (PID: 4796)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 4476)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 5216)
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 5004)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 548)
- bomb.exe (PID: 120)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 12256)
- bomb.exe (PID: 1104)
- bomb.exe (PID: 8176)
- bomb.exe (PID: 6804)
- bomb.exe (PID: 12176)
- bomb.exe (PID: 7704)
- bomb.exe (PID: 2768)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 13224)
- bomb.exe (PID: 13160)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 13288)
- bomb.exe (PID: 13200)
- bomb.exe (PID: 13084)
- bomb.exe (PID: 13280)
- bomb.exe (PID: 13256)
- bomb.exe (PID: 13184)
- bomb.exe (PID: 13264)
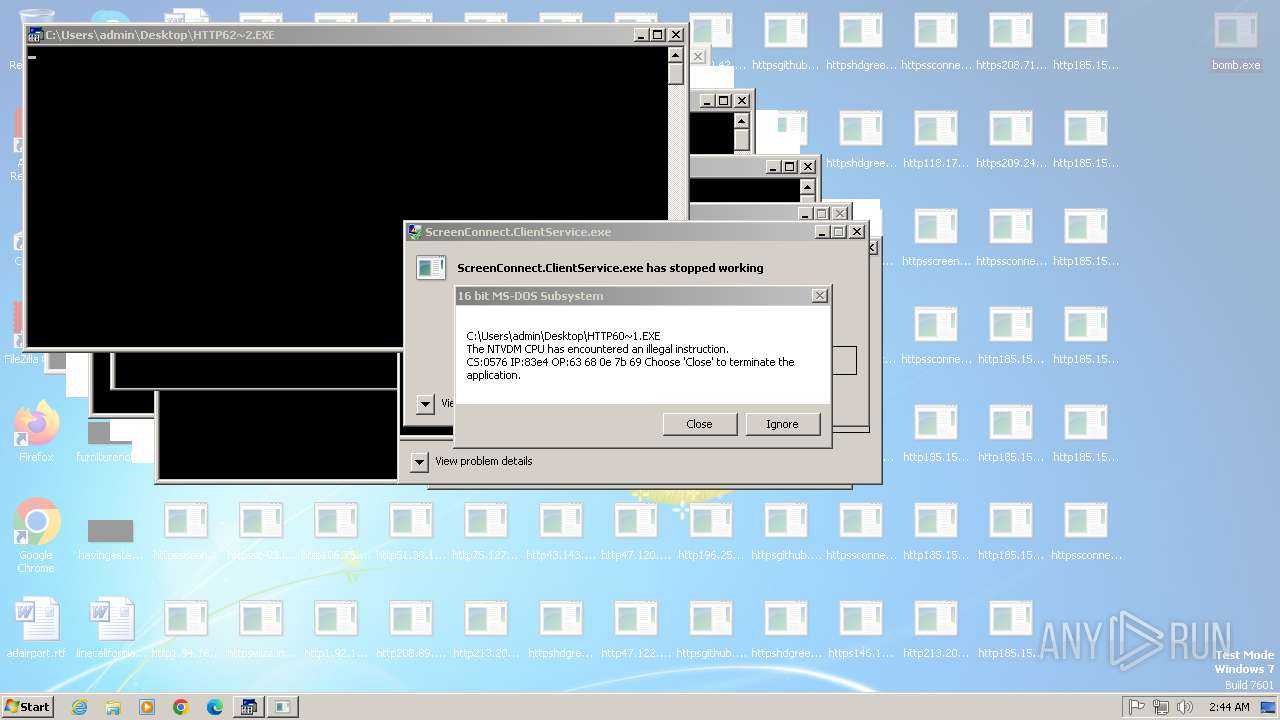
Detects ScreenConnect RAT (YARA)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- ScreenConnect.WindowsClient.exe (PID: 3808)
- ScreenConnect.WindowsClient.exe (PID: 3804)
There is functionality for taking screenshot (YARA)
- ScreenConnect.WindowsClient.exe (PID: 3808)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- ScreenConnect.WindowsClient.exe (PID: 3804)
Contacting a server suspected of hosting an CnC
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
- svchost.exe (PID: 17376)
- bomb.exe (PID: 4072)
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
Uses WMIC.EXE to obtain computer system information
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
Process drops SQLite DLL files
- sfc.exe (PID: 2956)
Starts a Microsoft application from unusual location
- http213.209.150.210jsXClient.exe.exe (PID: 11564)
- http213.209.150.210jsXClient.exe.exe (PID: 10888)
- http213.209.150.210jsXClient.exe.exe (PID: 2728)
- http213.209.150.210jsXClient.exe.exe (PID: 12780)
- http213.209.150.210jsXClient.exe.exe (PID: 12864)
- http213.209.150.210jsXClient.exe.exe (PID: 15028)
Executing commands from a ".bat" file
- wscript.exe (PID: 3952)
- wscript.exe (PID: 15332)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3952)
- wscript.exe (PID: 15332)
Starts POWERSHELL.EXE for commands execution
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 12320)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 12828)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 15288)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 14084)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 17836)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18020)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 13380)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12468)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16580)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 11788)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18092)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 15928)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 14072)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18340)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17776)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 7792)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 13024)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12860)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 14296)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18000)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 15340)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11652)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18600)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18628)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18584)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18812)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19156)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19304)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 20028)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12592)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18676)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12816)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17320)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 9692)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22544)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11896)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19764)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 24480)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18392)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 20864)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18556)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 6516)
Base64-obfuscated command line is found
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 12320)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 12828)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 15288)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 14084)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18020)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 13380)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12468)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16580)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 11788)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 17836)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18092)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 14072)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 15928)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18340)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17776)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 7792)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 13024)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12860)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18000)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 14296)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 15340)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11652)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18600)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18628)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18584)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18812)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19156)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19304)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 20028)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12592)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18676)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12816)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17320)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22544)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 9692)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19764)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11896)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 24480)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18392)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 20864)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18556)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 6516)
BASE64 encoded PowerShell command has been detected
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 12828)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 12320)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18020)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 15288)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 14084)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12468)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 13380)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 16580)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18092)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 17836)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 11788)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 14072)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 15928)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18340)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17776)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 7792)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 13024)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12860)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18000)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 14296)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 15340)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11652)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 18600)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18628)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18584)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18812)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19156)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19304)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 20028)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12592)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18676)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 12816)
- httpsraw.githubusercontent.comauracodersigmatoiletestoragerefsheadsmaindownloadclient.exe.exe (PID: 17320)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 9692)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 22544)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 11896)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 19764)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 24480)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18392)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 20864)
- httpsgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 18556)
- httpgithub.comauracodersigmatoiletestoragerawrefsheadsmaindownloadclient.exe.exe (PID: 6516)
Crypto Currency Mining Activity Detected
- bomb.exe (PID: 1092)
- bomb.exe (PID: 3340)
Checks for external IP
- svchost.exe (PID: 1080)
- RegSvcs.exe (PID: 14172)
- RegSvcs.exe (PID: 21252)
Malware-specific behavior (creating "System.dll" in Temp)
- http75.127.7.164Nationalbankdirektrernes.exe.exe (PID: 9324)
Contacting a server suspected of hosting an Exploit Kit
- bomb.exe (PID: 4520)
- bomb.exe (PID: 2012)
INFO
Disables trace logs
- bomb.exe (PID: 2480)
- dfsvc.exe (PID: 1800)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 4092)
Checks supported languages
- bomb.exe (PID: 2480)
- httpsmail.viewyourstatementonline.comBinwork_approval_pdf3.Client.exe.exe (PID: 2592)
- dfsvc.exe (PID: 1800)
- http146.103.7.34150TiWorker.exe.exe (PID: 1400)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2536)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1180)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1504)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 3712)
- ScreenConnect.WindowsClient.exe (PID: 3804)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2716)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 3120)
- ScreenConnect.WindowsClient.exe (PID: 3808)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 3780)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- bomb.exe (PID: 580)
- bomb.exe (PID: 548)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 3964)
- ScreenConnect.ClientService.exe (PID: 2428)
- bomb.exe (PID: 3540)
- ScreenConnect.ClientService.exe (PID: 2796)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- ScreenConnect.ClientService.exe (PID: 2516)
- http176.98.185.87Quodlibet.exe.exe (PID: 2968)
- bomb.exe (PID: 120)
- bomb.exe (PID: 848)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 920)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 956)
- ScreenConnect.WindowsClient.exe (PID: 3768)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 2224)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 692)
- bomb.exe (PID: 4200)
- bomb.exe (PID: 4160)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 4340)
Reads the computer name
- bomb.exe (PID: 2480)
- httpsmail.viewyourstatementonline.comBinwork_approval_pdf3.Client.exe.exe (PID: 2592)
- dfsvc.exe (PID: 1800)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2536)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1504)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1180)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2716)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 3712)
- ScreenConnect.WindowsClient.exe (PID: 3804)
- ScreenConnect.WindowsClient.exe (PID: 3808)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3192)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- ScreenConnect.WindowsClient.exe (PID: 3768)
- bomb.exe (PID: 580)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 548)
- ScreenConnect.ClientService.exe (PID: 2428)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- ScreenConnect.ClientService.exe (PID: 2796)
- ScreenConnect.ClientService.exe (PID: 2516)
- bomb.exe (PID: 120)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 848)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 920)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 956)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 2224)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 692)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 4160)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 4200)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 2012)
Reads the software policy settings
- bomb.exe (PID: 2480)
- dfsvc.exe (PID: 1800)
- bomb.exe (PID: 3664)
Reads the machine GUID from the registry
- bomb.exe (PID: 2480)
- httpsmail.viewyourstatementonline.comBinwork_approval_pdf3.Client.exe.exe (PID: 2592)
- httpssc-03.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2536)
- dfsvc.exe (PID: 1800)
- httpswizz.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1504)
- httpssc-05.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 1180)
- httpssisconnect-01.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 2716)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
- ScreenConnect.WindowsClient.exe (PID: 3804)
- ScreenConnect.WindowsClient.exe (PID: 3808)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- httpssc-02.infinitycloud.orgbinsupport.client.exei=&e=Support&y=Guest&r=.exe (PID: 3712)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- ScreenConnect.WindowsClient.exe (PID: 3768)
- ScreenConnect.ClientService.exe (PID: 2428)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- ScreenConnect.ClientService.exe (PID: 2796)
- ScreenConnect.ClientService.exe (PID: 2516)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3680)
Reads Environment values
- bomb.exe (PID: 2480)
- dfsvc.exe (PID: 1800)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 2904)
Create files in a temporary directory
- bomb.exe (PID: 2480)
- http146.103.7.34150TiWorker.exe.exe (PID: 1400)
- dfsvc.exe (PID: 1800)
Creates files or folders in the user directory
- dfsvc.exe (PID: 1800)
- httpgettsveriff.combgj3ckjg.exe.exe (PID: 1268)
- ScreenConnect.WindowsClient.exe (PID: 3804)
- ScreenConnect.WindowsClient.exe (PID: 3808)
- ScreenConnect.WindowsClient.exe (PID: 2792)
- ScreenConnect.WindowsClient.exe (PID: 3768)
- ScreenConnect.WindowsClient.exe (PID: 2132)
- ScreenConnect.WindowsClient.exe (PID: 3432)
- bomb.exe (PID: 2480)
The sample compiled with english language support
- bomb.exe (PID: 2480)
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 548)
- bomb.exe (PID: 580)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 920)
- bomb.exe (PID: 2700)
- sfc.exe (PID: 2956)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 956)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 4816)
- bomb.exe (PID: 4864)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 4392)
- bomb.exe (PID: 4400)
- bomb.exe (PID: 5112)
- bomb.exe (PID: 5240)
- bomb.exe (PID: 4804)
- bomb.exe (PID: 4936)
- bomb.exe (PID: 4796)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 4476)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 5232)
- bomb.exe (PID: 848)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 4352)
- bomb.exe (PID: 5216)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 3396)
- svchost.exe (PID: 17376)
- bomb.exe (PID: 4548)
- bomb.exe (PID: 5004)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 4916)
- bomb.exe (PID: 9588)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 12256)
- bomb.exe (PID: 1104)
- bomb.exe (PID: 12176)
- bomb.exe (PID: 8176)
- bomb.exe (PID: 6804)
- bomb.exe (PID: 7704)
- bomb.exe (PID: 2768)
- bomb.exe (PID: 13224)
- bomb.exe (PID: 120)
- bomb.exe (PID: 13160)
- bomb.exe (PID: 13200)
- bomb.exe (PID: 13288)
- bomb.exe (PID: 13084)
- bomb.exe (PID: 13256)
- bomb.exe (PID: 13280)
- bomb.exe (PID: 13264)
- bomb.exe (PID: 13184)
Reads mouse settings
- http146.103.7.34150TiWorker.exe.exe (PID: 1400)
Checks proxy server information
- dfsvc.exe (PID: 1800)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 1800)
Manual execution by a user
- bomb.exe (PID: 3664)
- bomb.exe (PID: 3672)
- bomb.exe (PID: 2932)
- bomb.exe (PID: 3036)
- bomb.exe (PID: 3152)
- bomb.exe (PID: 3120)
- bomb.exe (PID: 3100)
- bomb.exe (PID: 3784)
- bomb.exe (PID: 1076)
- bomb.exe (PID: 4072)
- bomb.exe (PID: 3448)
- bomb.exe (PID: 4012)
- bomb.exe (PID: 4032)
- bomb.exe (PID: 3848)
- bomb.exe (PID: 4092)
- bomb.exe (PID: 2904)
- bomb.exe (PID: 3340)
- bomb.exe (PID: 3780)
- bomb.exe (PID: 3192)
- bomb.exe (PID: 3396)
- bomb.exe (PID: 3680)
- bomb.exe (PID: 1092)
- bomb.exe (PID: 548)
- bomb.exe (PID: 580)
- bomb.exe (PID: 3892)
- bomb.exe (PID: 3964)
- bomb.exe (PID: 3540)
- bomb.exe (PID: 2320)
- bomb.exe (PID: 848)
- bomb.exe (PID: 120)
- bomb.exe (PID: 4028)
- bomb.exe (PID: 3056)
- bomb.exe (PID: 3072)
- bomb.exe (PID: 2012)
- bomb.exe (PID: 2700)
- bomb.exe (PID: 956)
- bomb.exe (PID: 2208)
- bomb.exe (PID: 2224)
- bomb.exe (PID: 1936)
- bomb.exe (PID: 692)
- bomb.exe (PID: 2844)
- bomb.exe (PID: 4132)
- bomb.exe (PID: 4160)
- bomb.exe (PID: 4152)
- bomb.exe (PID: 4216)
- bomb.exe (PID: 4200)
- bomb.exe (PID: 4228)
- bomb.exe (PID: 4244)
- bomb.exe (PID: 4340)
- bomb.exe (PID: 4352)
- bomb.exe (PID: 4392)
- bomb.exe (PID: 4400)
- bomb.exe (PID: 4408)
- bomb.exe (PID: 4476)
- bomb.exe (PID: 4484)
- bomb.exe (PID: 4464)
- bomb.exe (PID: 4520)
- bomb.exe (PID: 4500)
- bomb.exe (PID: 920)
- bomb.exe (PID: 4528)
- bomb.exe (PID: 4548)
- bomb.exe (PID: 4780)
- bomb.exe (PID: 4788)
- bomb.exe (PID: 4804)
- bomb.exe (PID: 4812)
- bomb.exe (PID: 4796)
- bomb.exe (PID: 4828)
- bomb.exe (PID: 4864)
- bomb.exe (PID: 4816)
- bomb.exe (PID: 4908)
- bomb.exe (PID: 5004)
- bomb.exe (PID: 4936)
- bomb.exe (PID: 4916)
- bomb.exe (PID: 5112)
- bomb.exe (PID: 4772)
- bomb.exe (PID: 5140)
- bomb.exe (PID: 5192)
- bomb.exe (PID: 5200)
- bomb.exe (PID: 5216)
- bomb.exe (PID: 5208)
- bomb.exe (PID: 5232)
- bomb.exe (PID: 5240)
- bomb.exe (PID: 12040)
- bomb.exe (PID: 12176)
- bomb.exe (PID: 12236)
- bomb.exe (PID: 8176)
- bomb.exe (PID: 9588)
- bomb.exe (PID: 12256)
- bomb.exe (PID: 7704)
- bomb.exe (PID: 6804)
- bomb.exe (PID: 5632)
- bomb.exe (PID: 1104)
- bomb.exe (PID: 2768)
- bomb.exe (PID: 2780)
- bomb.exe (PID: 13140)
- bomb.exe (PID: 13152)
- bomb.exe (PID: 13132)
- bomb.exe (PID: 13192)
- bomb.exe (PID: 13184)
- bomb.exe (PID: 13172)
- bomb.exe (PID: 13200)
- bomb.exe (PID: 13264)
- bomb.exe (PID: 13084)
- bomb.exe (PID: 13092)
- bomb.exe (PID: 13100)
- bomb.exe (PID: 13160)
- bomb.exe (PID: 13208)
- bomb.exe (PID: 13240)
- bomb.exe (PID: 13288)
- bomb.exe (PID: 13216)
- bomb.exe (PID: 13272)
- bomb.exe (PID: 13248)
- bomb.exe (PID: 13232)
- bomb.exe (PID: 13224)
- bomb.exe (PID: 13256)
- bomb.exe (PID: 13280)
- bomb.exe (PID: 17004)
- bomb.exe (PID: 16996)
- bomb.exe (PID: 17012)
- bomb.exe (PID: 17028)
- bomb.exe (PID: 16988)
- bomb.exe (PID: 17020)
- bomb.exe (PID: 17104)
- bomb.exe (PID: 17136)
- bomb.exe (PID: 17068)
- bomb.exe (PID: 17160)
- bomb.exe (PID: 17060)
- bomb.exe (PID: 17044)
- bomb.exe (PID: 17036)
- bomb.exe (PID: 17076)
- bomb.exe (PID: 17052)
- bomb.exe (PID: 17144)
- bomb.exe (PID: 17112)
- bomb.exe (PID: 17176)
- bomb.exe (PID: 17128)
- bomb.exe (PID: 17168)
- bomb.exe (PID: 17088)
- bomb.exe (PID: 17200)
- bomb.exe (PID: 17192)
- bomb.exe (PID: 17096)
- bomb.exe (PID: 17152)
- bomb.exe (PID: 17184)
- bomb.exe (PID: 17120)
SCREENCONNECT has been detected
- ScreenConnect.ClientService.exe (PID: 2428)
The sample compiled with chinese language support
- bomb.exe (PID: 4520)
- bomb.exe (PID: 3848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(1268) httpgettsveriff.combgj3ckjg.exe.exe
C2 (5)hkfasfsafg.click
hfjwfheiwf.click
jfhaowhfjk.click
hfjaohf9q3.click
fshjaifhajfa.click
Ports (1)7777
VersionLoaderPanel
Options
AutoRunfalse
Mutexdxrfuhttmneigievnhg
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVALJH4bdfPPE5dyMevD9KJERdSx3xMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDExvYWRlciBQYW5lbDETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDczMDE2NDgyM1oXDTM1MDUwOTE2NDgyM1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignaturemoARP2ilwwb46Uu1bzWUZTVB0GP7xM1q5BnrWDDw/ApLcb7eUPvM2UqnQm36fmkch/34sLs3cF2TQ83qC33yp5CHQOErcSBGropIhfXoUeA33XKMACcksz/aLy4PuEXsPY3ksQgefpI86mp1dHrGy2H9yJpEhouz4mfmkakhbD8=
Keys
AESdafd84b99a3f7311fddcf50b1199ddec6bb1f973d6f536a98a289a9af59b0c98
SaltLoaderPanel
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2057:01:07 19:44:57+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9216 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x43be |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
719
Monitored processes
520
Malicious processes
105
Suspicious processes
30
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 148 | "C:\Users\admin\Desktop\http146.103.7.34150TiWorker.exe.exe" | C:\Windows\System32\svchost.exe | — | http146.103.7.34150TiWorker.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 580 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 692 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 848 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 956 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 1076 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 1.0.0.0 Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
723 413
Read events
716 653
Write events
5 795
Delete events
965
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6D39D73C | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2480) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
206
Suspicious files
248
Text files
398
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | bomb.exe | C:\Users\admin\Desktop\httpsmail.viewyourstatementonline.comBinwork_approval_pdf3.Client.exe.exe | executable | |
MD5:B6B1C343F11CD79788320A048D66D09F | SHA256:ABDB5AB588FB23C2F7B2F813F5CDB0BF29BF1411FEE95EB5E2C26E790BA42C87 | |||
| 2480 | bomb.exe | C:\Users\admin\AppData\Local\Temp\Tar4746.tmp | binary | |
MD5:109CAB5505F5E065B63D01361467A83B | SHA256:6F02B247446740E75781C5C99C42F4C27C774226BE13EFE8F1254F028940133F | |||
| 1800 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\E62QAX1K.3E4\03X0KQ51.JV6.application | xml | |
MD5:DA69D38B0DCF29670D4601D8565E6833 | SHA256:D1BE7F3014B3804D836E04308D831E7AB31EDEE627643A926D45224B66FC194B | |||
| 2480 | bomb.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:082E15AED73D717A541232C2860641BB | SHA256:C4C39D6D6A36C4AC3A87AA532C64D95175ACF89BAB09902D42B61953E20ED808 | |||
| 3876 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs4F74.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 3876 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs4EE6.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 1800 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\TQ0DM7Q8.PMA\D1DWL8PG.CHL.application | xml | |
MD5:26817F400D192B9F4303FC5C4383C03E | SHA256:69E36FE8A71534FC3A278BB2E2964D2126FEE8014CB2FA73874A72492CD4BE06 | |||
| 1800 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\70NZXYOV.5EB\HYMW96BR.M6Y\ScreenConnect.WindowsClient.exe.manifest | xml | |
MD5:E1A62C7B0B94E2FBE0D27D9C679B9A97 | SHA256:D44B7BDA547BBBEAB6060EDD2207E97DBC43C28AA08522B2108866C1AC023DBD | |||
| 1800 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\932a2db58c237abd381d22df4c63a04a_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
| 2480 | bomb.exe | C:\Users\admin\Desktop\http146.103.7.34150TiWorker.exe.exe | executable | |
MD5:AD60FC98CFA36FD229FD46AABC71B260 | SHA256:C17E8C6B860A83B92AD9426113FED857076924F0DE5D7ED0E6ECACD032DF67A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
525
TCP/UDP connections
2 589
DNS requests
63
Threats
2 312
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2480 | bomb.exe | GET | 200 | 47.92.142.110:1234 | http://47.92.142.110:1234/02.08.2022.exe | unknown | — | — | unknown |
2480 | bomb.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?710948169414ac43 | unknown | — | — | whitelisted |
2480 | bomb.exe | GET | 200 | 146.103.7.34:80 | http://146.103.7.34/150/TiWorker.exe | unknown | — | — | unknown |
2480 | bomb.exe | GET | 200 | 193.46.217.4:80 | http://gettsveriff.com/bgj3/ckjg.exe | unknown | — | — | unknown |
2480 | bomb.exe | GET | 200 | 106.75.71.42:80 | http://106.75.71.42/02.08.2022.exe | unknown | — | — | malicious |
1800 | dfsvc.exe | GET | 200 | 2.23.77.188:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | — | — | whitelisted |
2480 | bomb.exe | GET | 200 | 124.221.66.34:80 | http://124.221.66.34/02.08.2022.exe | unknown | — | — | unknown |
2480 | bomb.exe | GET | 200 | 176.98.185.87:80 | http://176.98.185.87/Quodlibet.exe | unknown | — | — | unknown |
2480 | bomb.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot_debug.exe | unknown | — | — | unknown |
2480 | bomb.exe | GET | 200 | 176.98.185.87:80 | http://176.98.185.87/widsmob_denoise_win.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2480 | bomb.exe | 188.114.96.3:443 | maper.info | CLOUDFLARENET | NL | malicious |
2480 | bomb.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
2480 | bomb.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2480 | bomb.exe | 146.103.7.34:443 | — | — | BE | unknown |
2480 | bomb.exe | 159.75.84.224:80 | — | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
2480 | bomb.exe | 1.94.181.67:28088 | — | Huawei Cloud Service data center | CN | malicious |
2480 | bomb.exe | 106.75.78.139:33333 | — | China Mobile Communications Group Co., Ltd. | CN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
maper.info |
| malicious |
www.google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
gettsveriff.com |
| unknown |
mail.viewyourstatementonline.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
sc-03.infinitycloud.org |
| unknown |
wizz.infinitycloud.org |
| unknown |
sc-02.infinitycloud.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2480 | bomb.exe | Potential Corporate Privacy Violation | ET INFO IP Logger Redirect Domain in SNI |
2480 | bomb.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2480 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2480 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2480 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2480 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2480 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2480 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2480 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2480 | bomb.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|