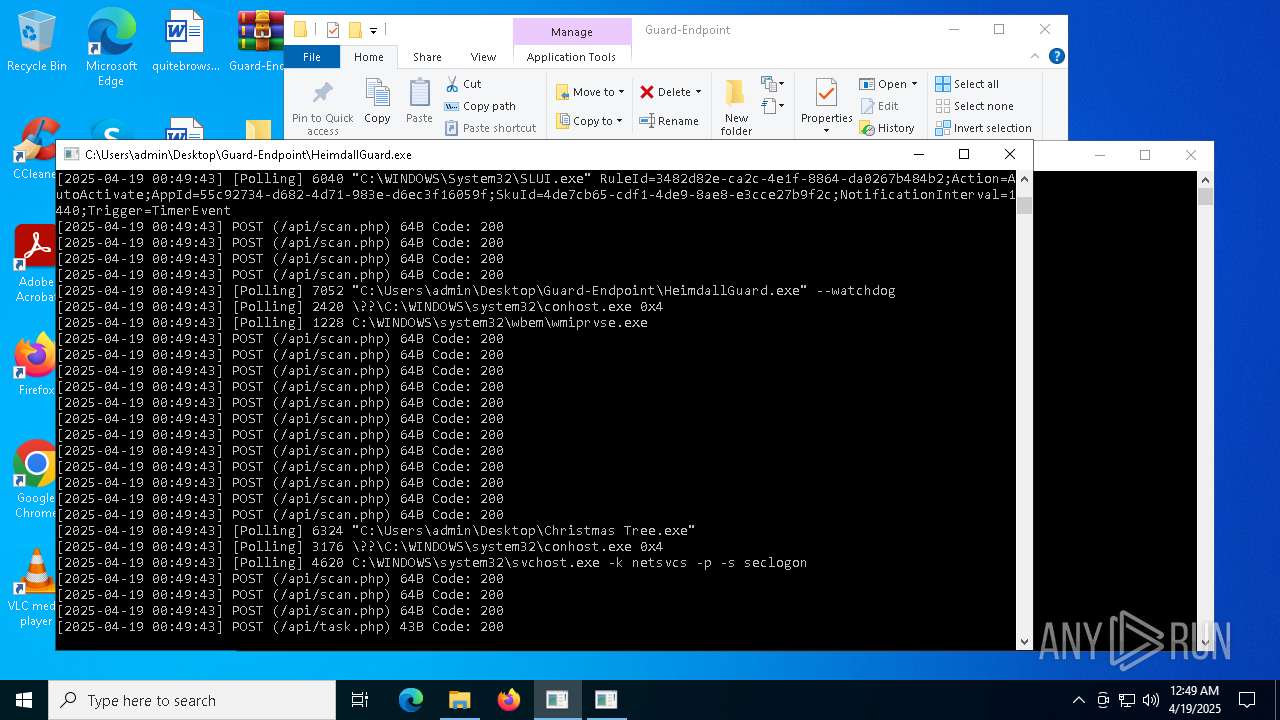
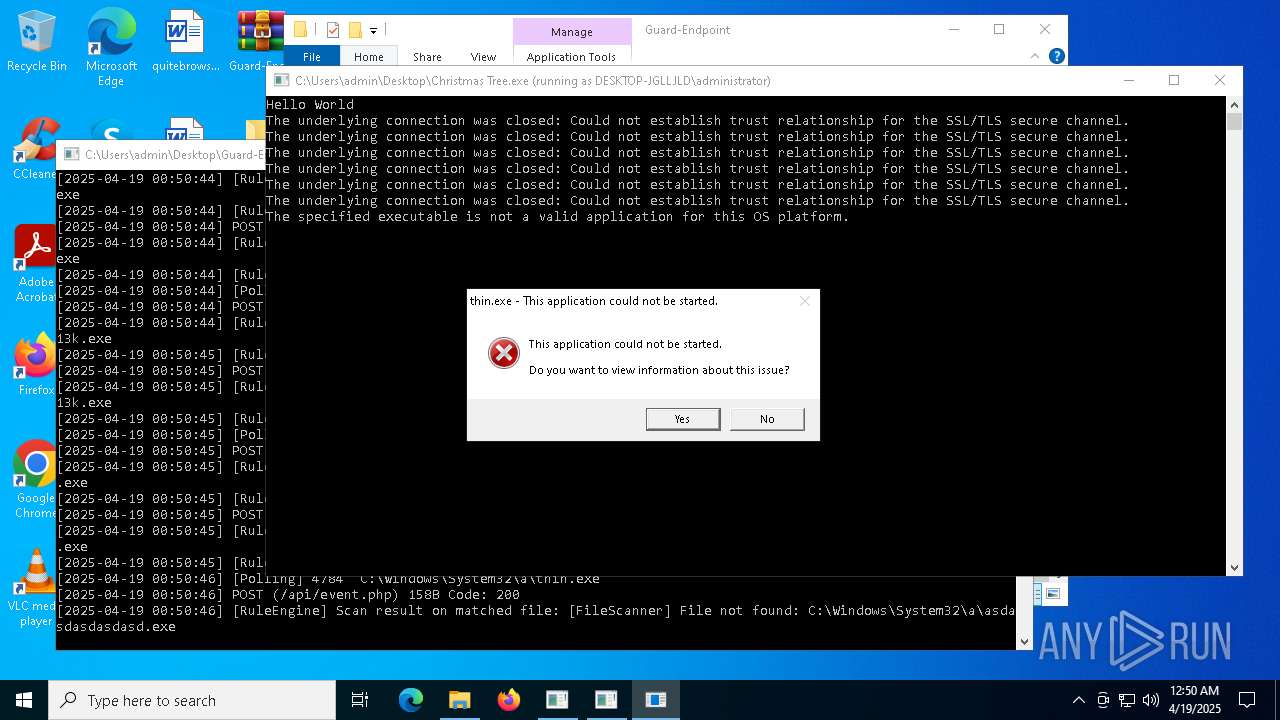
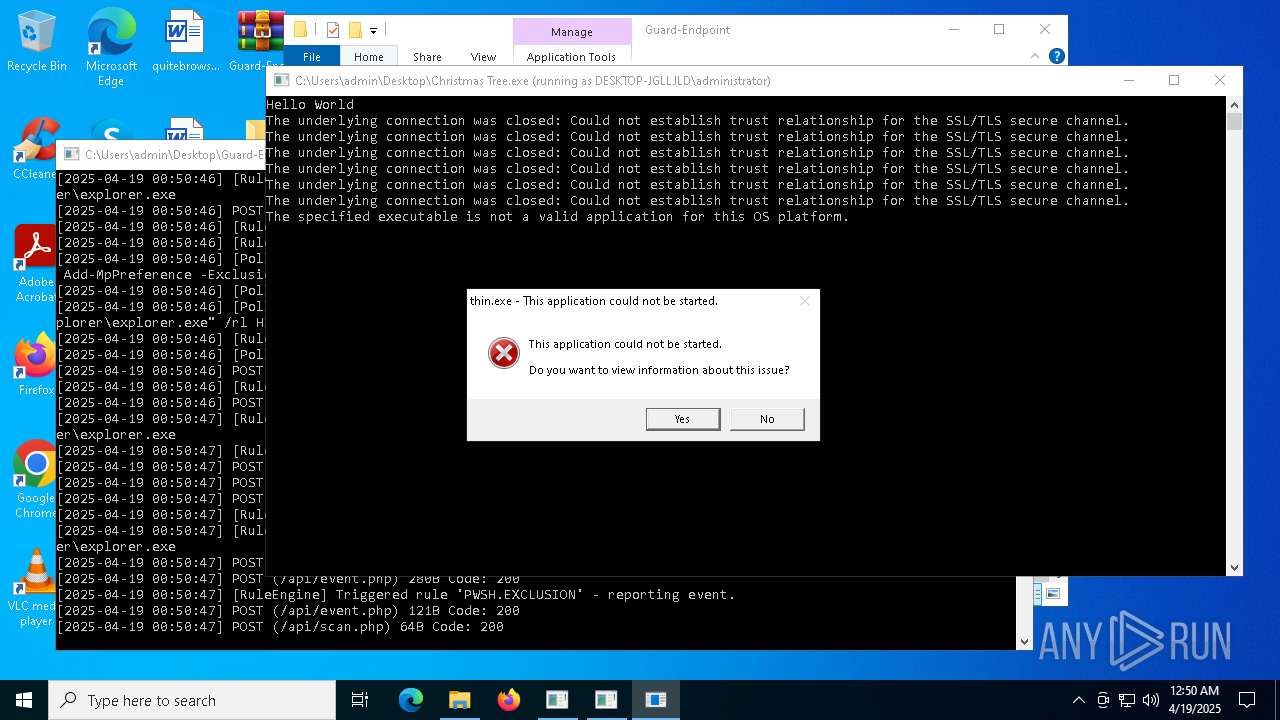
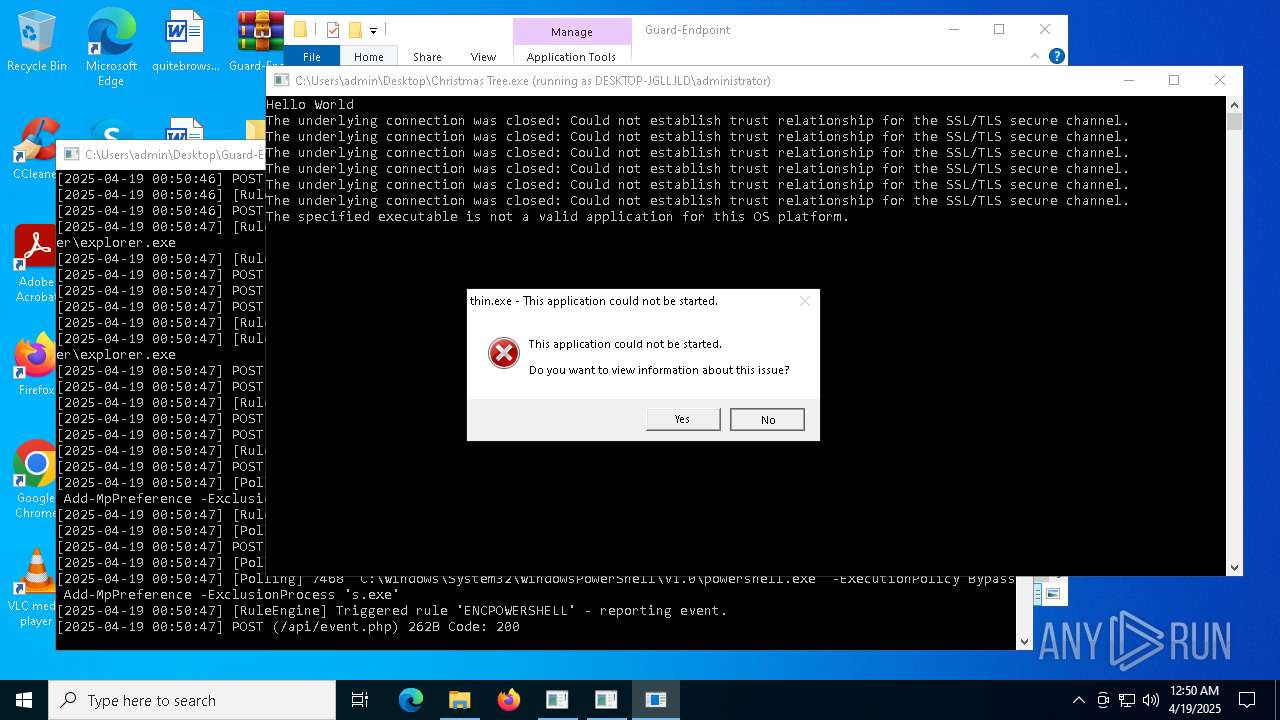
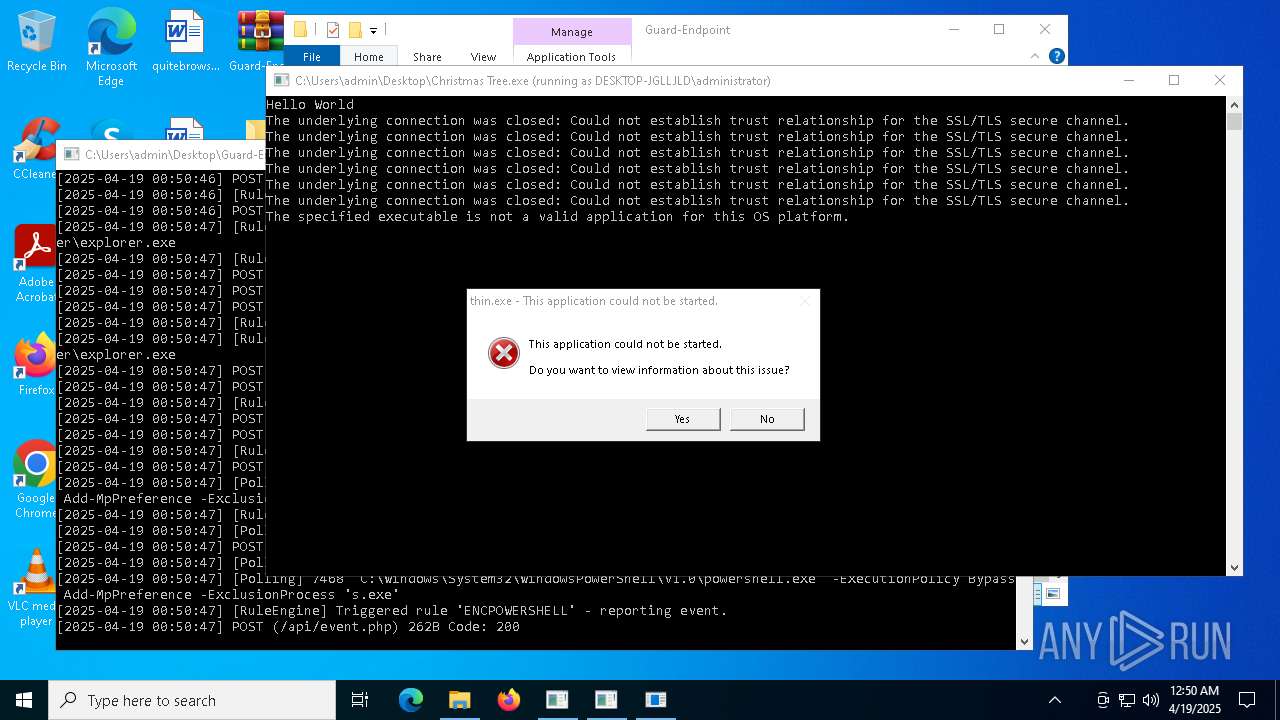
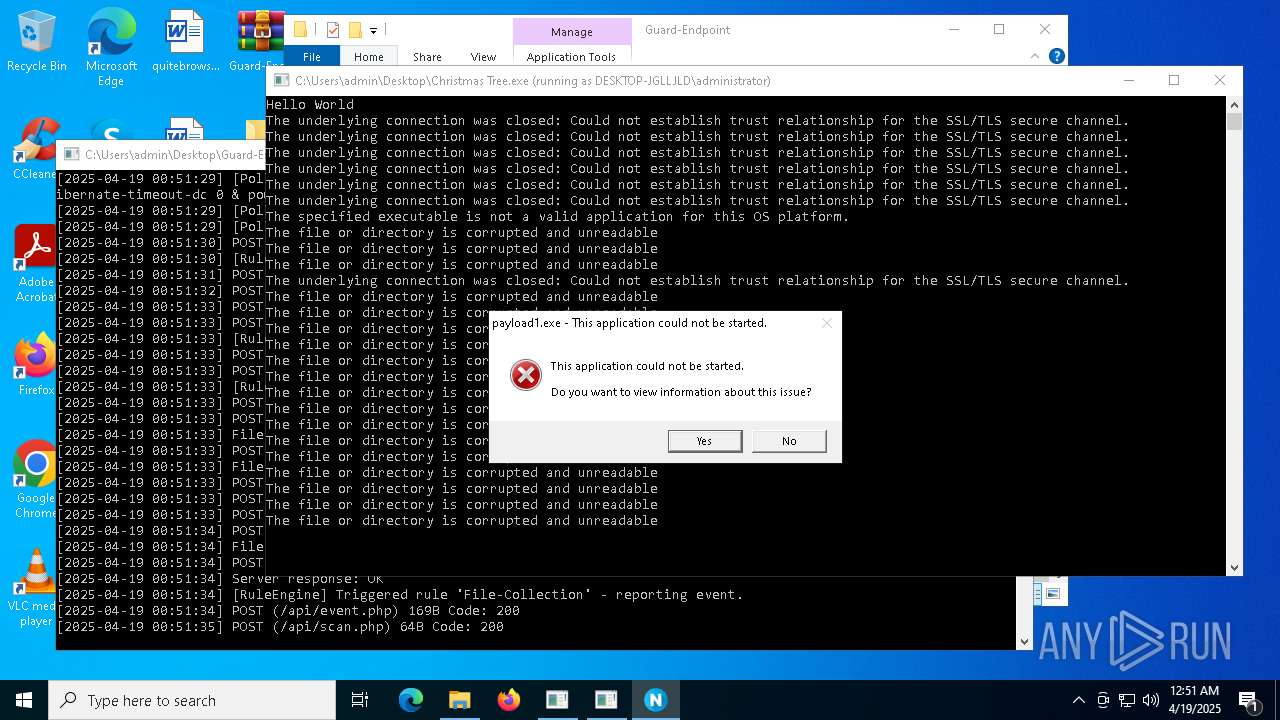
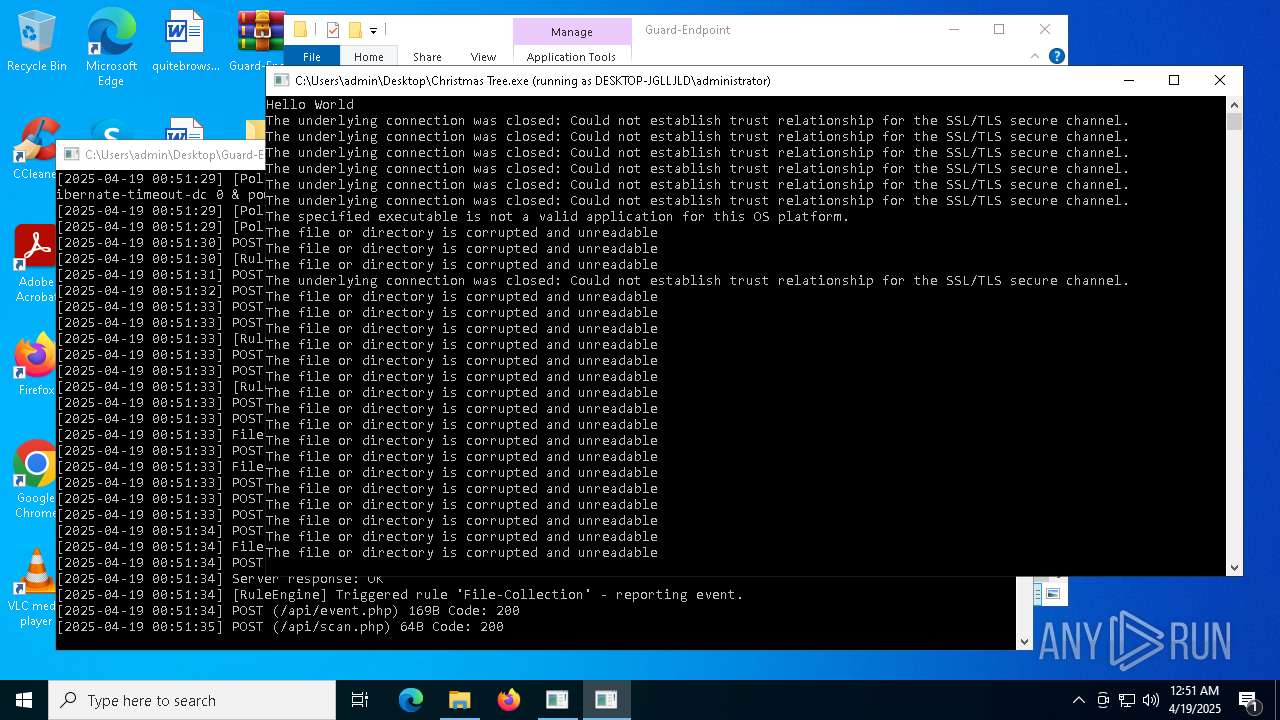
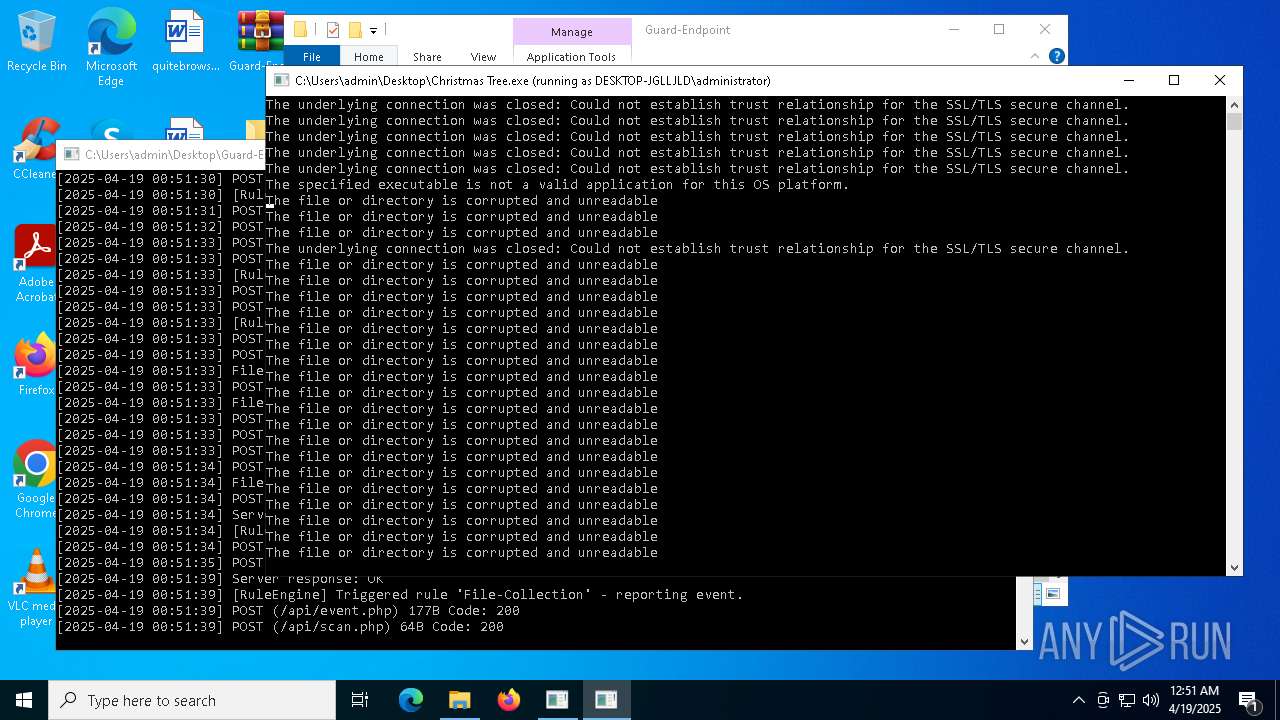
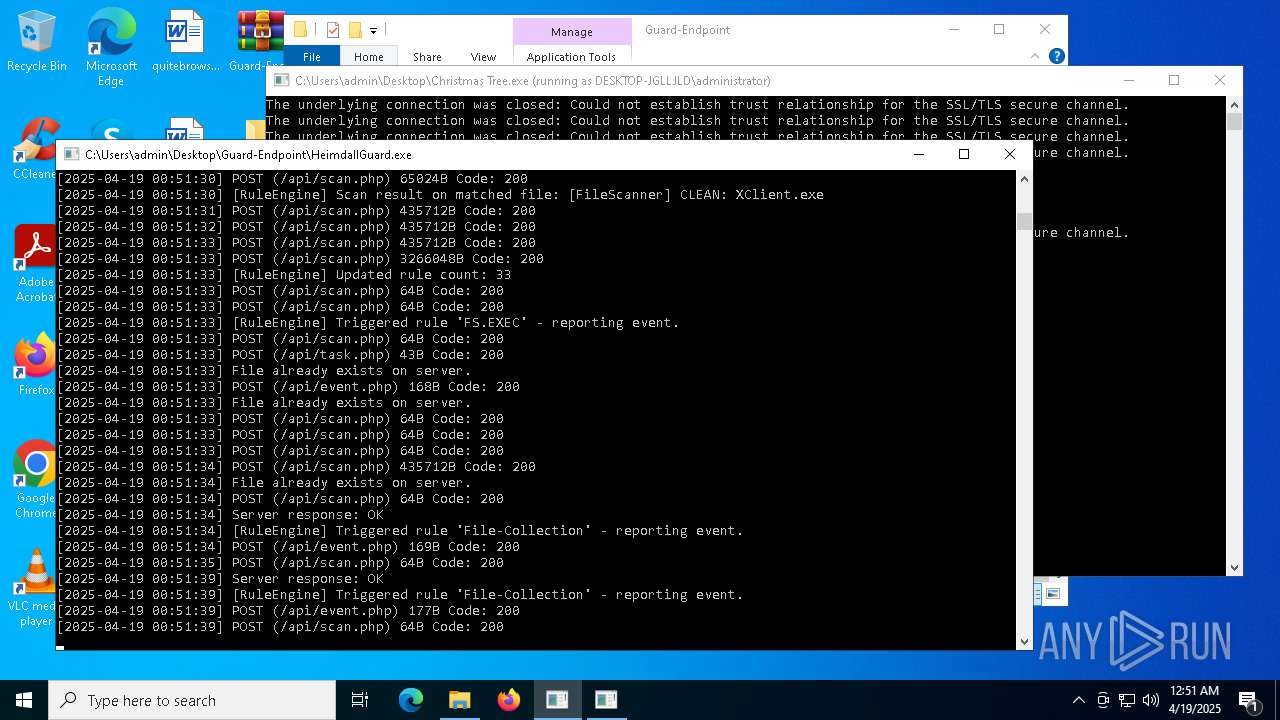
| File name: | Christmas Tree.exe |
| Full analysis: | https://app.any.run/tasks/9deb1588-2acb-4371-9a12-55a0855e3875 |
| Verdict: | Malicious activity |
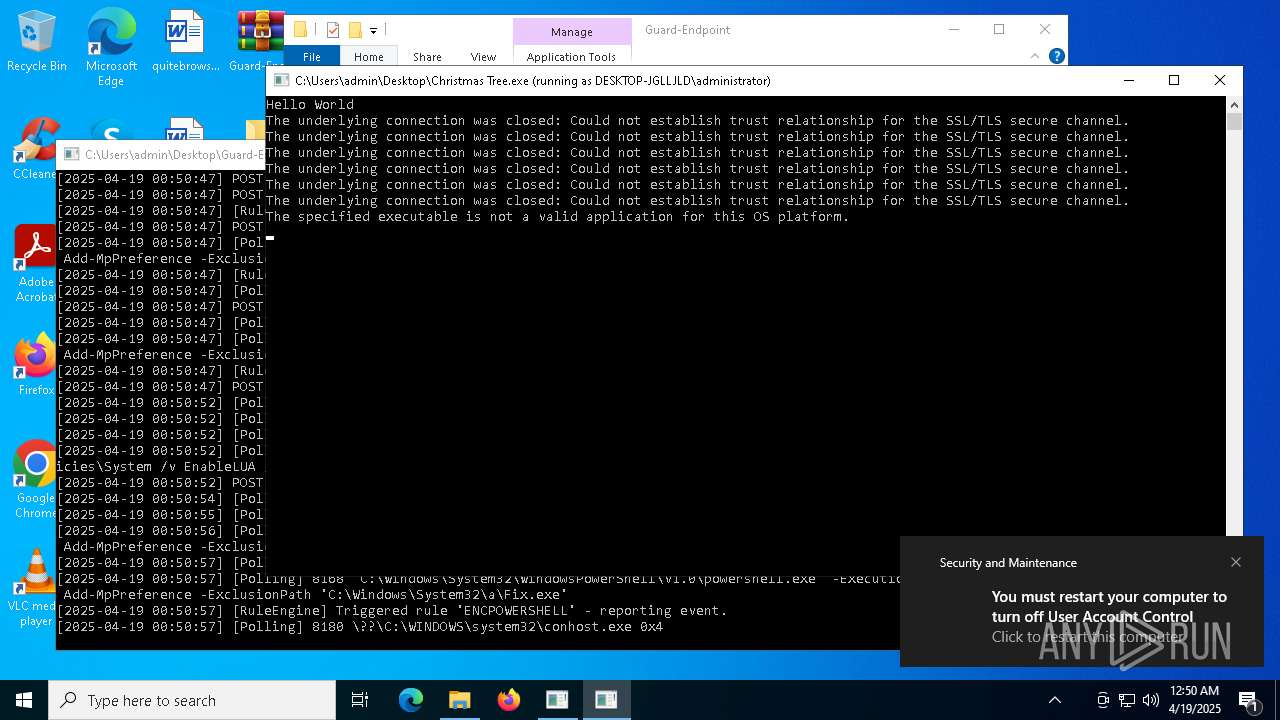
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | April 19, 2025, 00:49:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
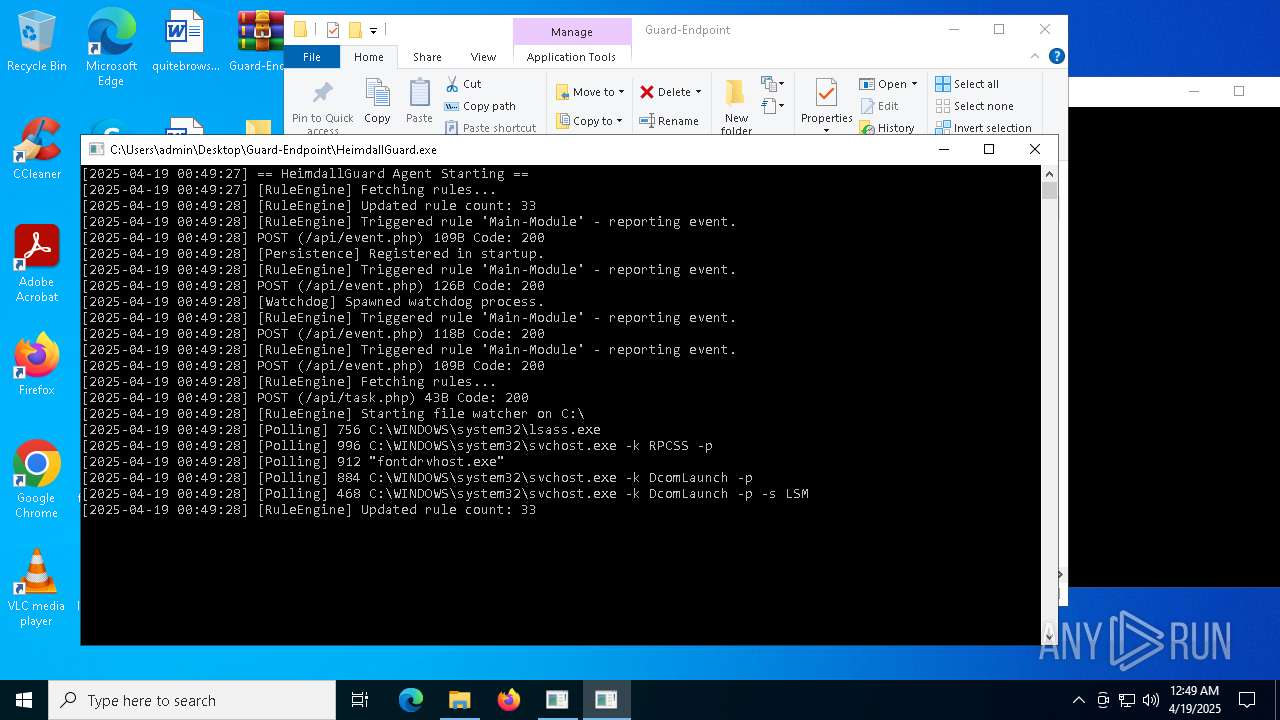
Changes the autorun value in the registry
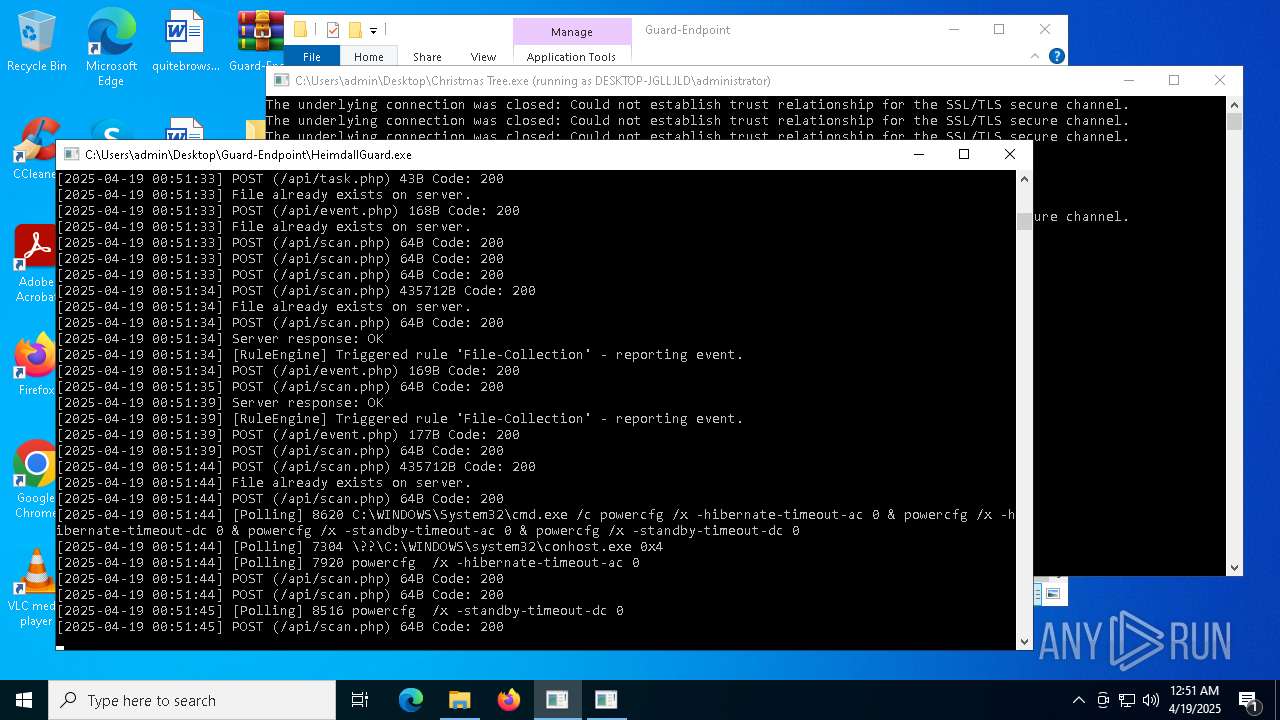
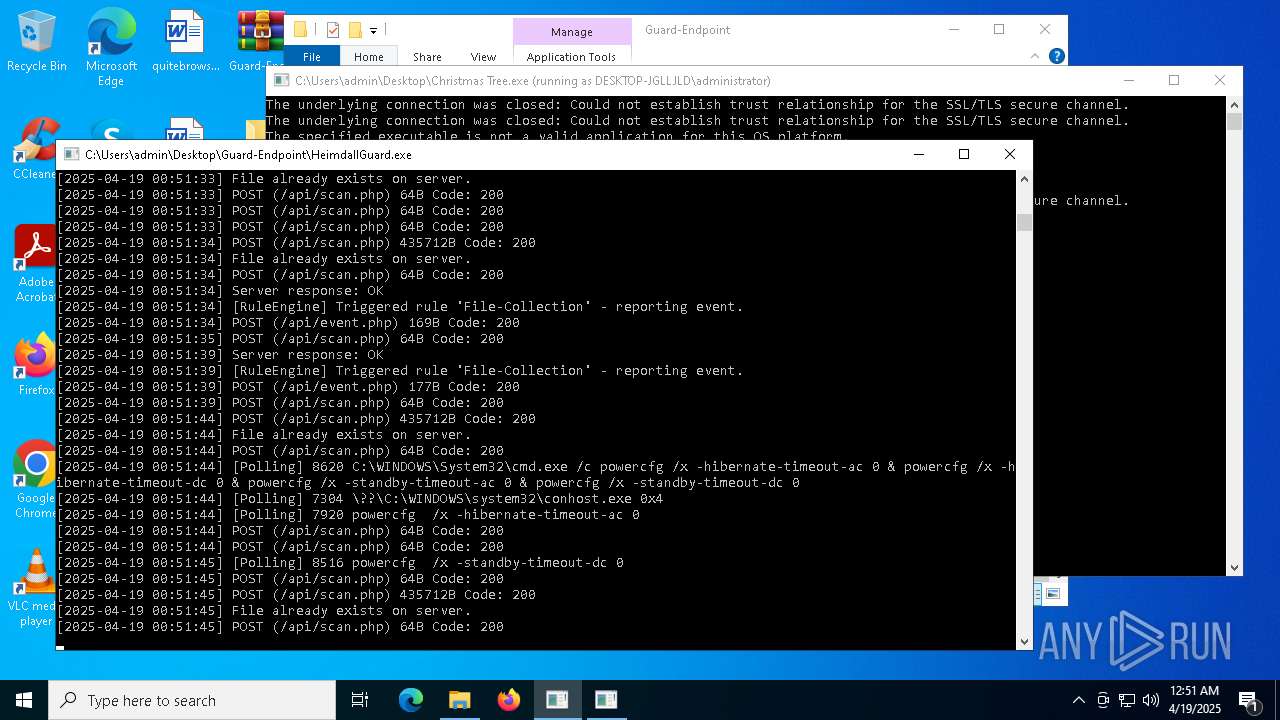
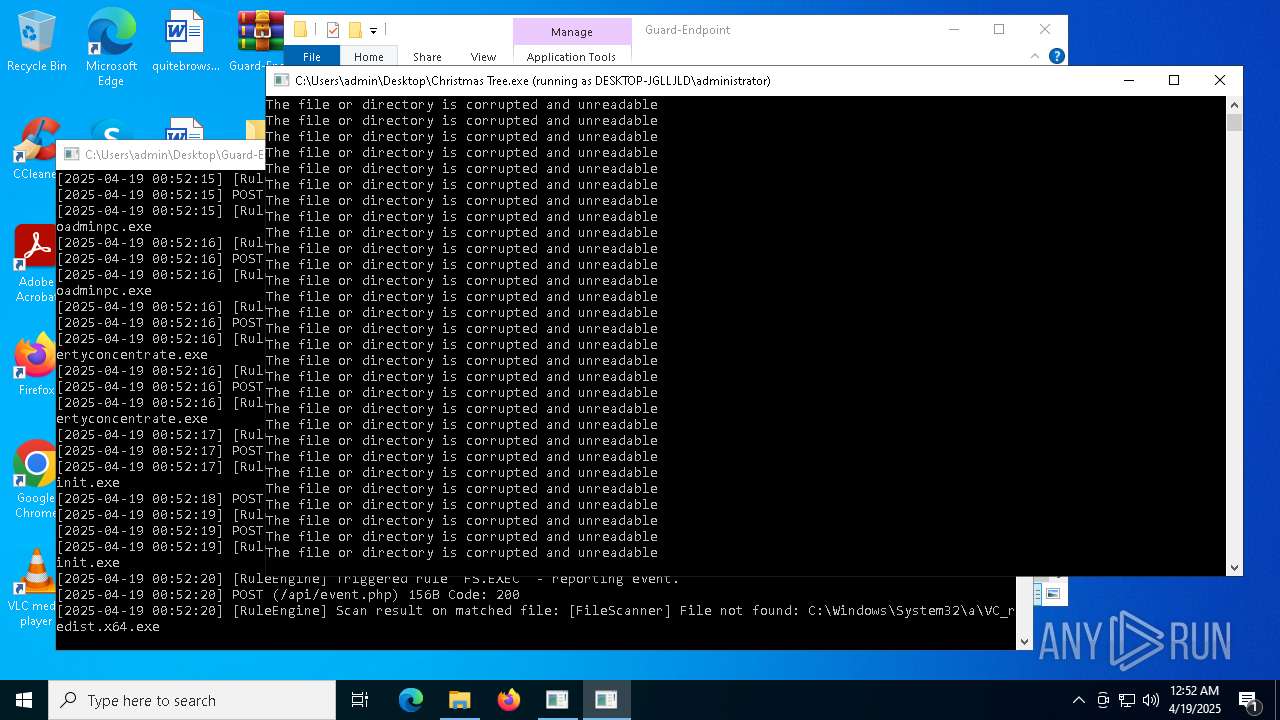
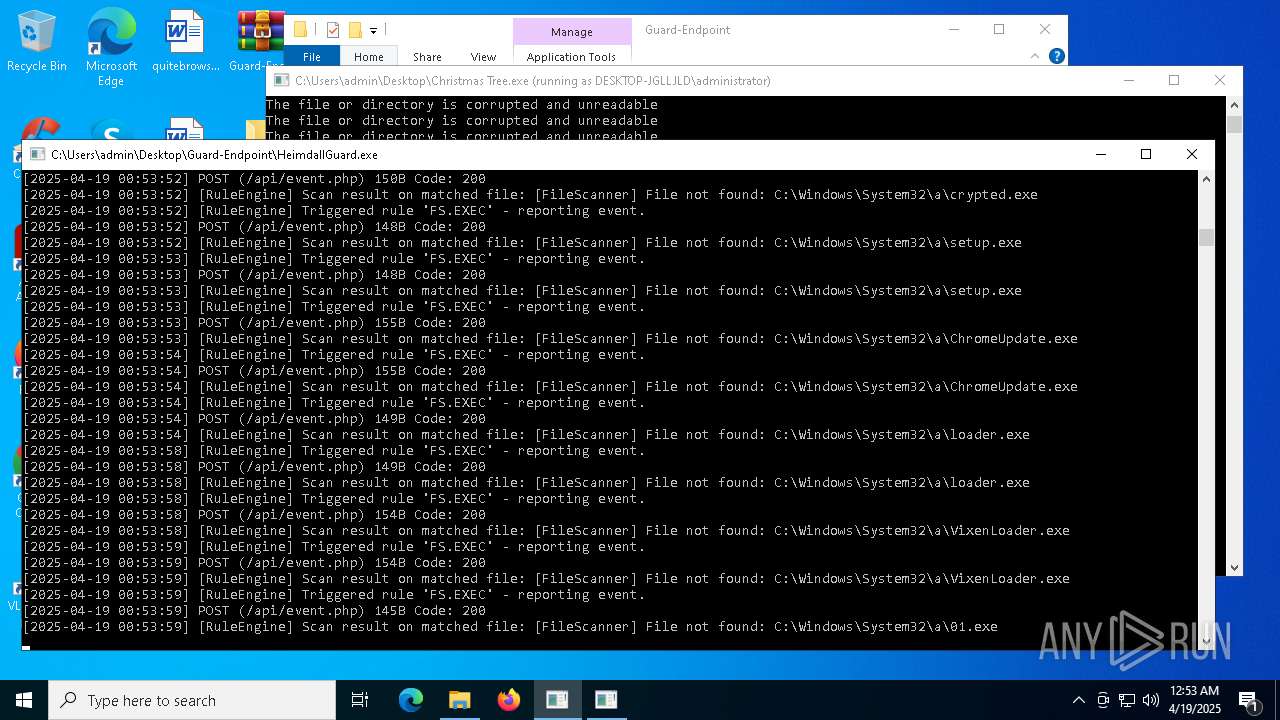
- HeimdallGuard.exe (PID: 2772)
- ULauncher.exe (PID: 5892)
- remcos_a.exe (PID: 7700)
- Device2.exe (PID: 8264)
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- Host.exe (PID: 5736)
QUASAR has been detected (SURICATA)
- S123.exe (PID: 1328)
QUASAR has been detected (YARA)
- S123.exe (PID: 1328)
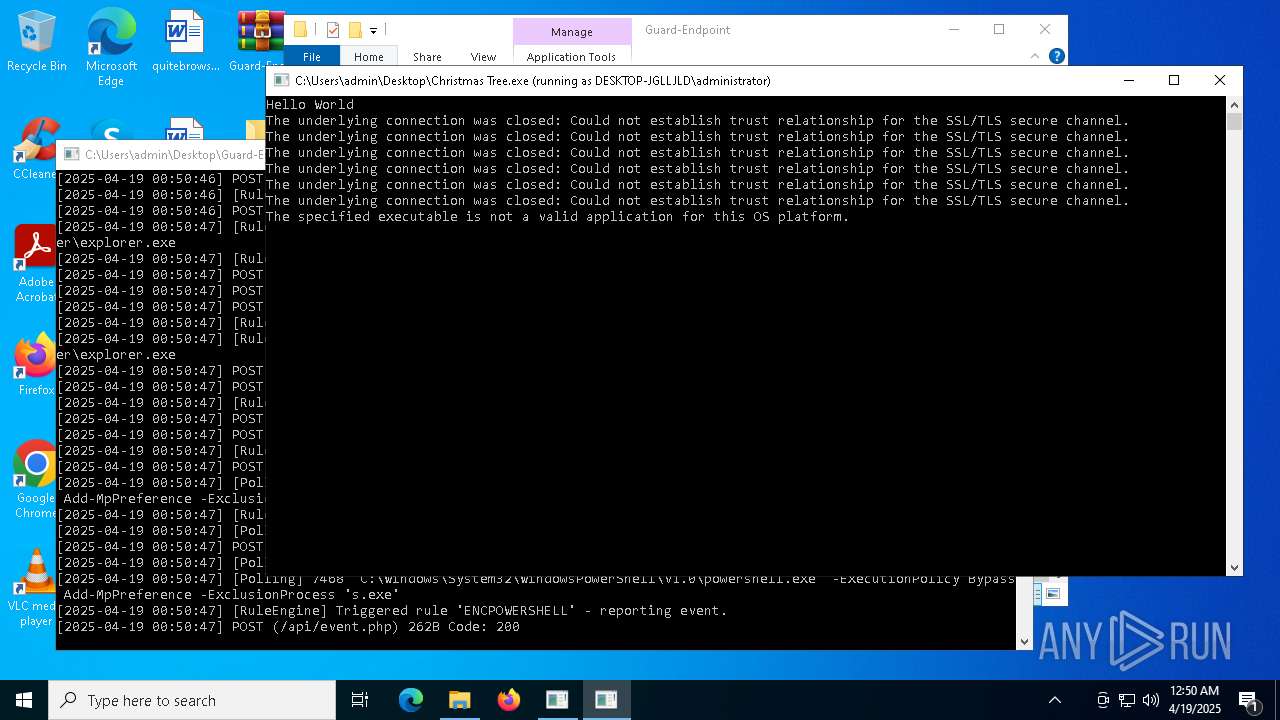
Connects to the CnC server
- S123.exe (PID: 1328)
HAUSBOMBER has been detected (YARA)
- Christmas Tree.exe (PID: 6324)
Executing a file with an untrusted certificate
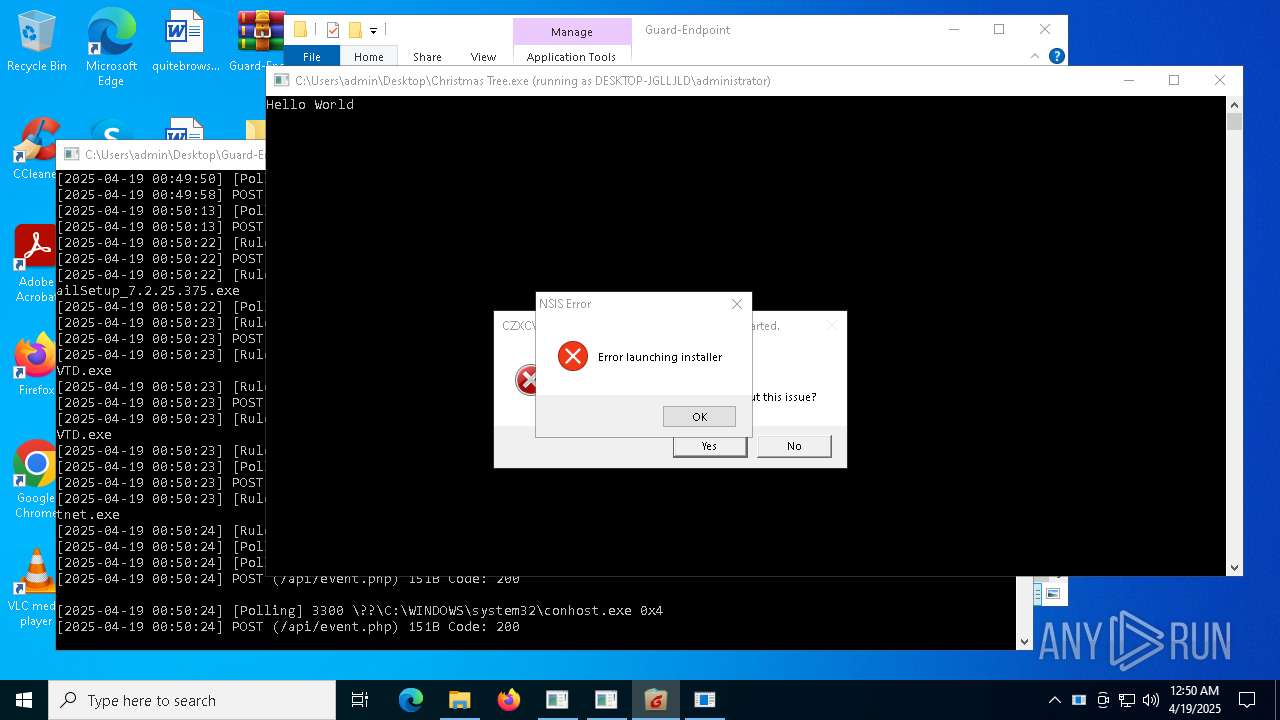
- FoxmailSetup_7.2.25.375.exe (PID: 1748)
- brbotnet.exe (PID: 2908)
METERPRETER has been detected (SURICATA)
- Christmas Tree.exe (PID: 6324)
GENERIC has been found (auto)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
QUASAR has been found (auto)
- Christmas Tree.exe (PID: 6324)
- Quas13k.exe (PID: 668)
Changes Windows Defender settings
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
Bypass execution policy to execute commands
- powershell.exe (PID: 1004)
- powershell.exe (PID: 6004)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 7468)
- powershell.exe (PID: 8012)
- powershell.exe (PID: 8168)
- powershell.exe (PID: 8204)
- powershell.exe (PID: 8764)
- powershell.exe (PID: 8640)
- powershell.exe (PID: 8460)
- powershell.exe (PID: 9192)
- powershell.exe (PID: 8784)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 8732)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
Uses Task Scheduler to autorun other applications
- Quas13k.exe (PID: 668)
- explorer.exe (PID: 7440)
- RuntimeBroker.exe (PID: 7264)
- RuntimeBroker.exe (PID: 8424)
- bootstrapper.exe (PID: 8076)
- bootstrapper.exe (PID: 8872)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- Host.exe (PID: 5736)
Create files in the Startup directory
- Cloudy.exe (PID: 5216)
- ULauncher.exe (PID: 5892)
- raw_cbot.exe (PID: 7432)
- Device2.exe (PID: 8264)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- Host.exe (PID: 5736)
Uses Task Scheduler to run other applications
- ULauncher.exe (PID: 5892)
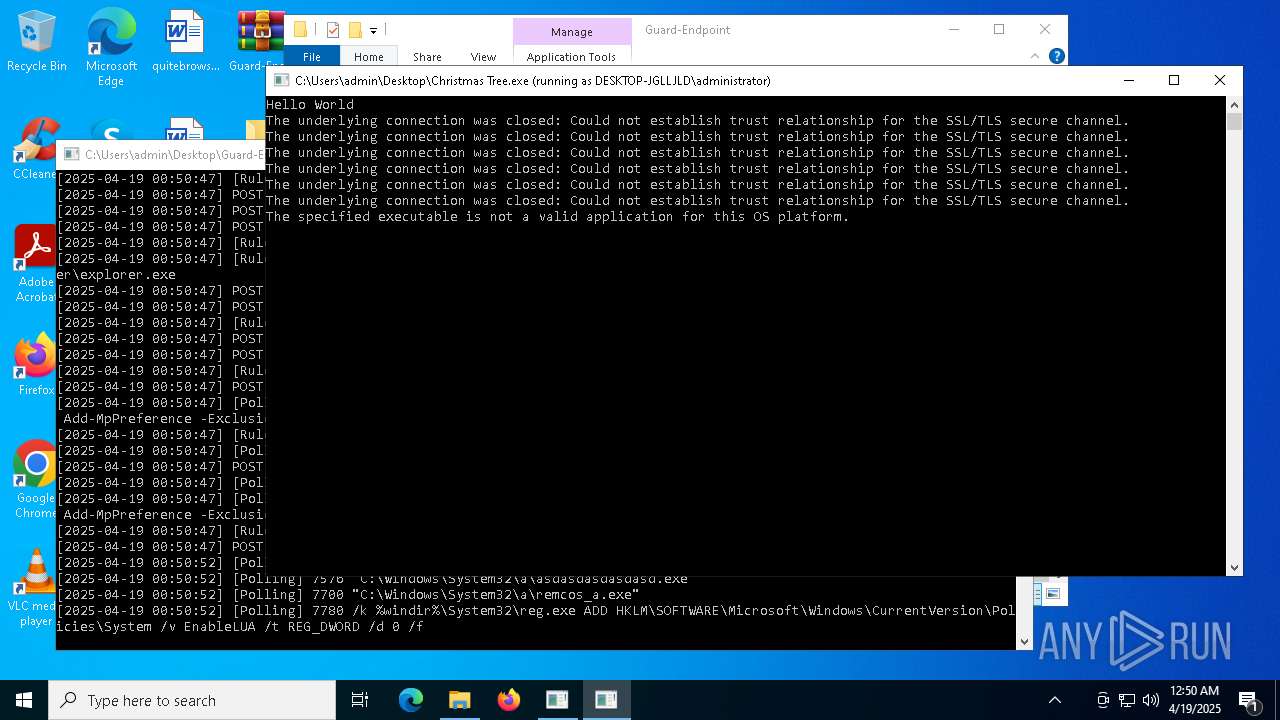
REMCOS mutex has been found
- remcos_a.exe (PID: 7700)
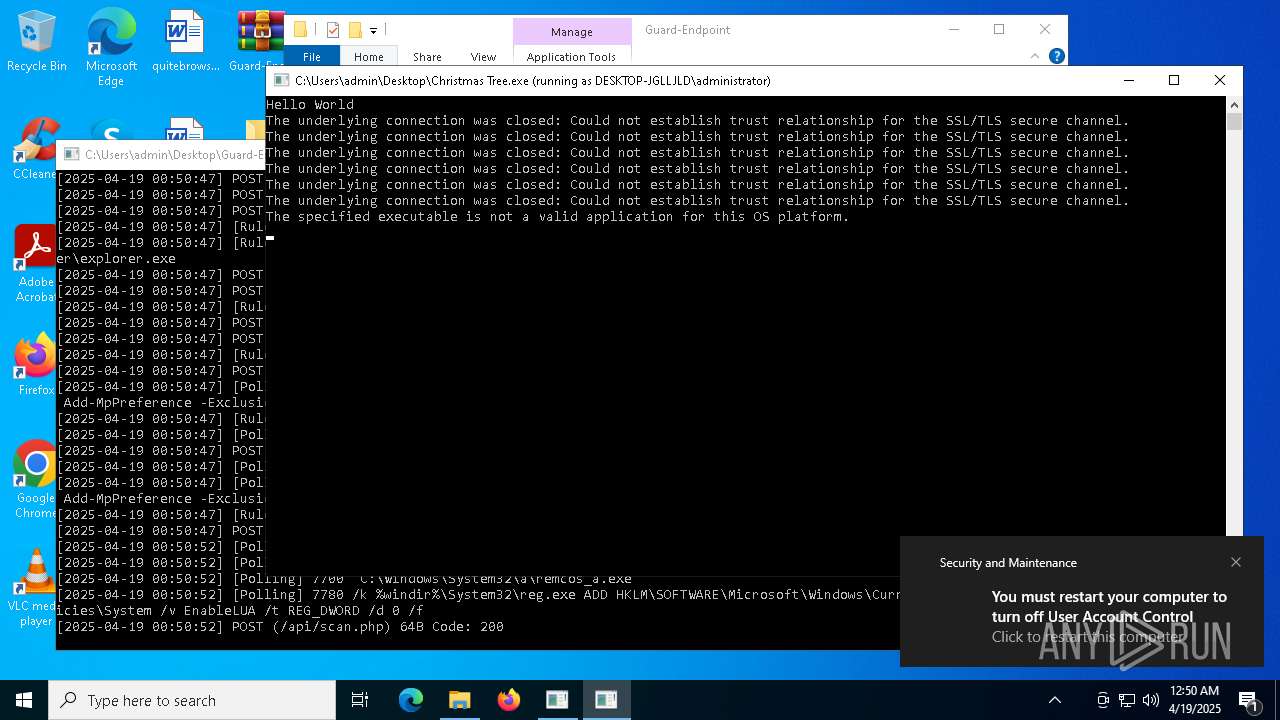
UAC/LUA settings modification
- reg.exe (PID: 8048)
REMCOS has been detected
- remcos_a.exe (PID: 7700)
RAT has been found (auto)
- Christmas Tree.exe (PID: 6324)
- RuntimeBroker.exe (PID: 7264)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
NJRAT has been found (auto)
- Christmas Tree.exe (PID: 6324)
- Device2.exe (PID: 8264)
NjRAT is detected
- Device2.exe (PID: 8264)
NESHTA mutex has been found
- taskhostw.exe (PID: 8040)
RANSOMWARE has been found (auto)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
LUMMA has been found (auto)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
ADESSTEALER has been found (auto)
- Christmas Tree.exe (PID: 6324)
- Christmas Tree.exe (PID: 6324)
COINMINER has been found (auto)
- c2new.exe (PID: 9080)
- Christmas Tree.exe (PID: 6324)
TOOL has been found (auto)
- Christmas Tree.exe (PID: 6324)
STEALER has been found (auto)
- Christmas Tree.exe (PID: 6324)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
SALATSTEALER has been found (auto)
- Christmas Tree.exe (PID: 6324)
BOTNET has been found (auto)
- Christmas Tree.exe (PID: 6324)
Vulnerable driver has been detected
- updater.exe (PID: 9092)
PURELOGS has been found (auto)
- Christmas Tree.exe (PID: 6324)
SUSPICIOUS
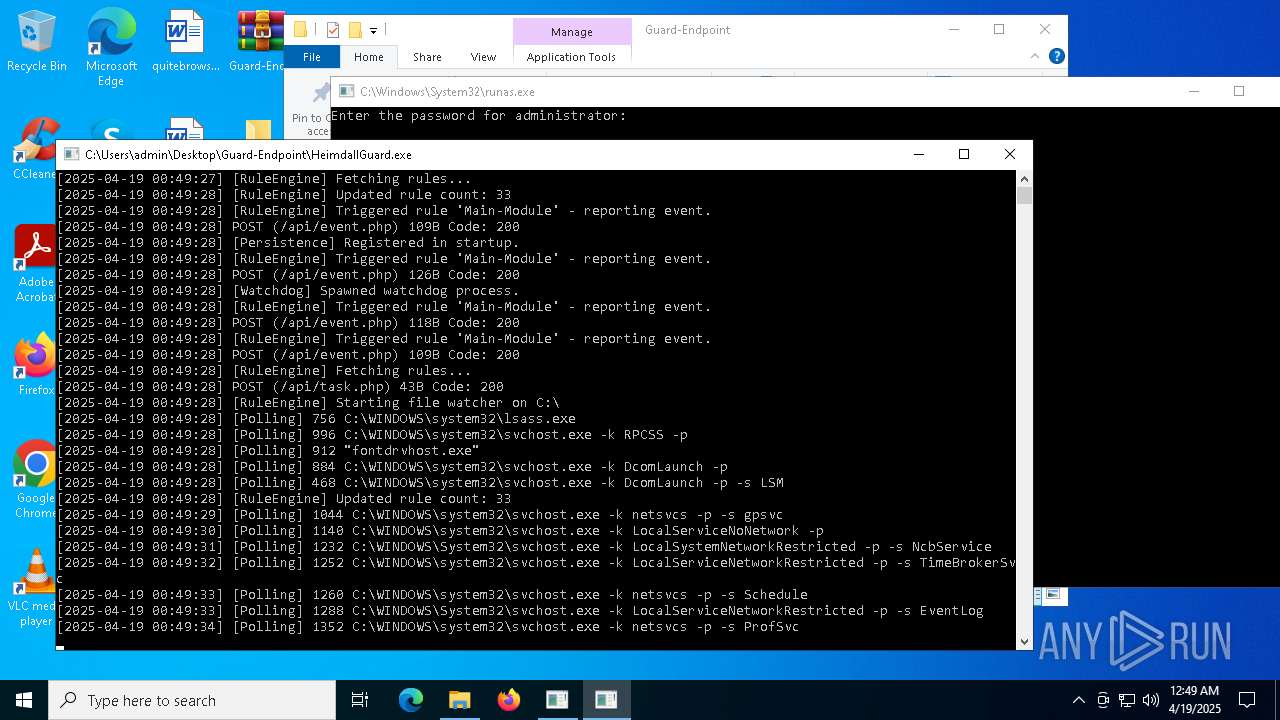
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 5156)
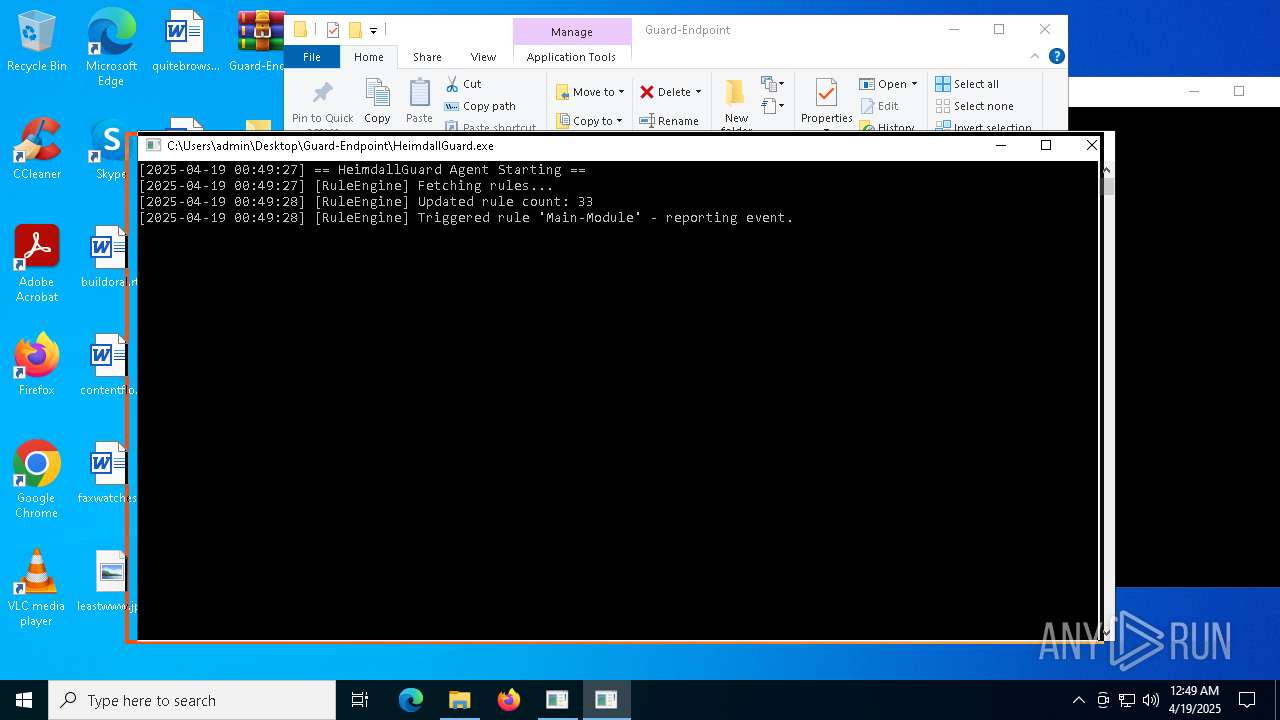
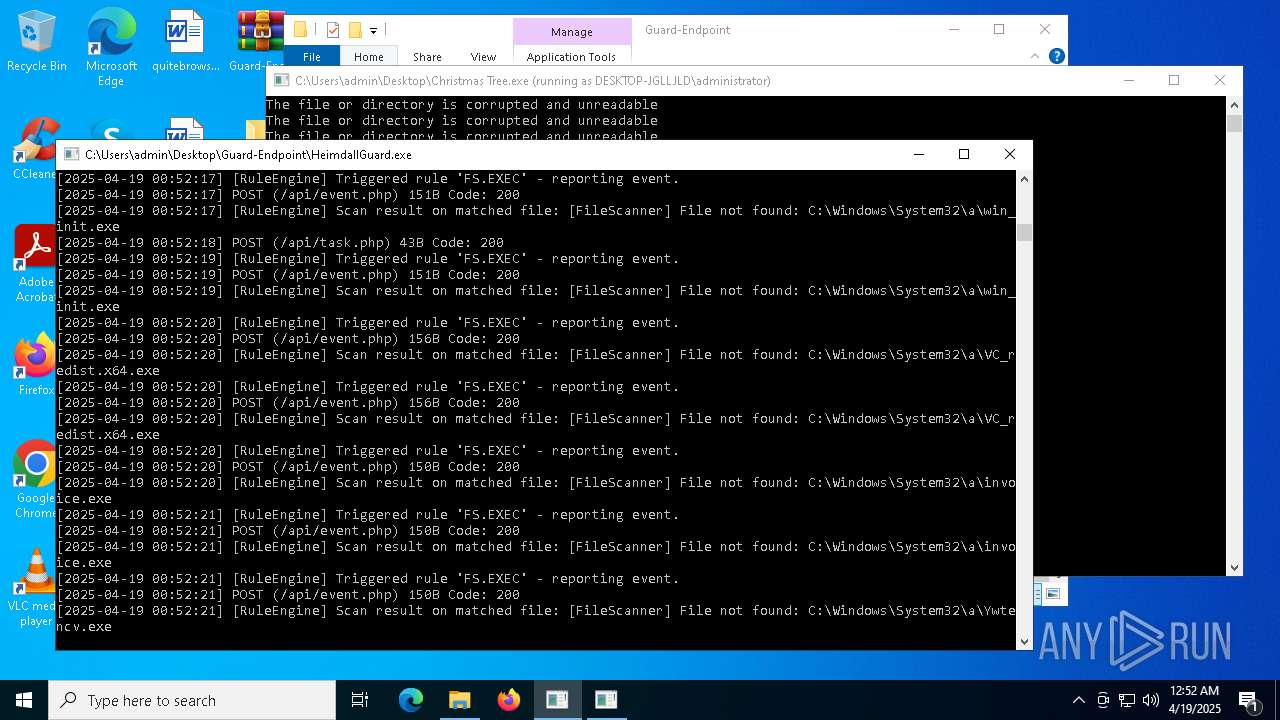
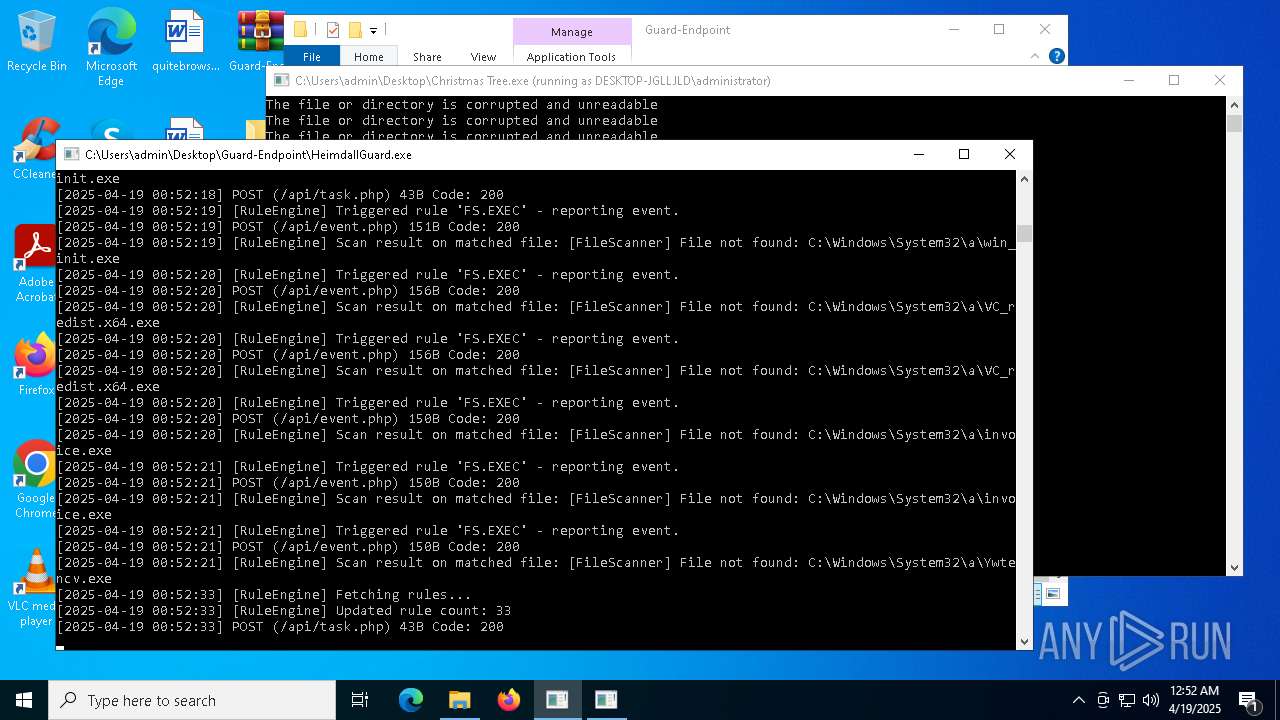
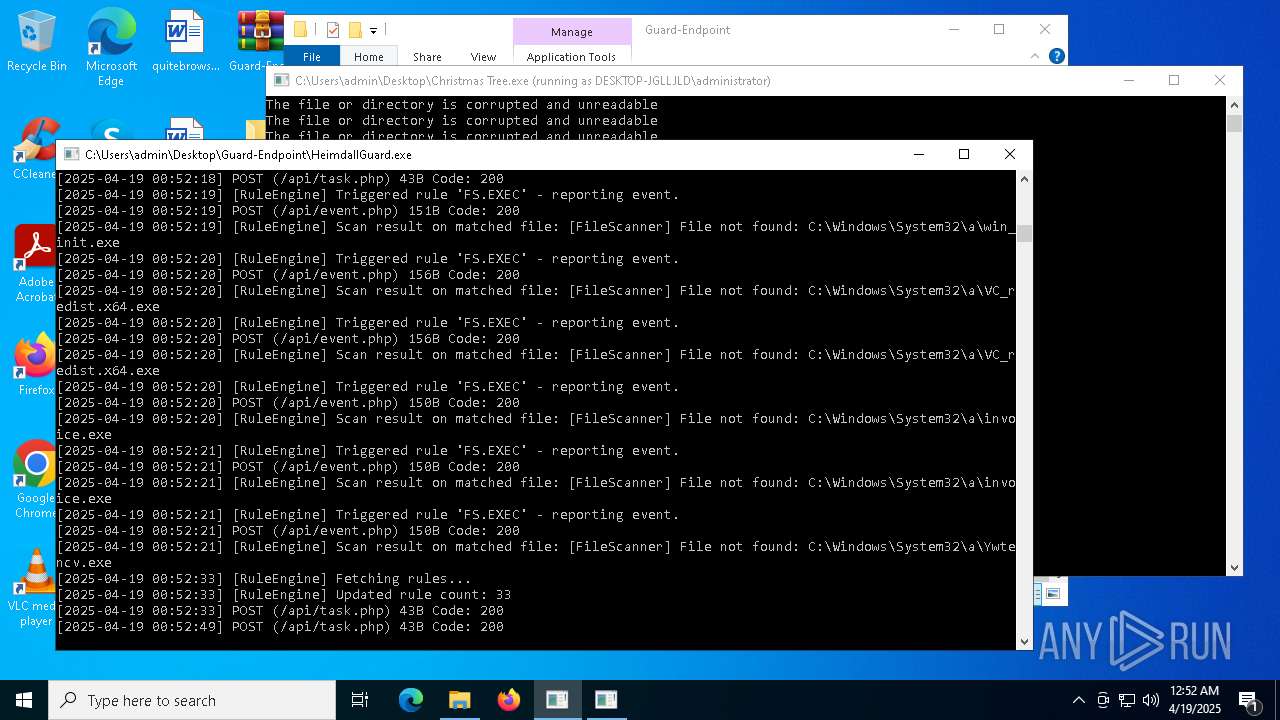
Application launched itself
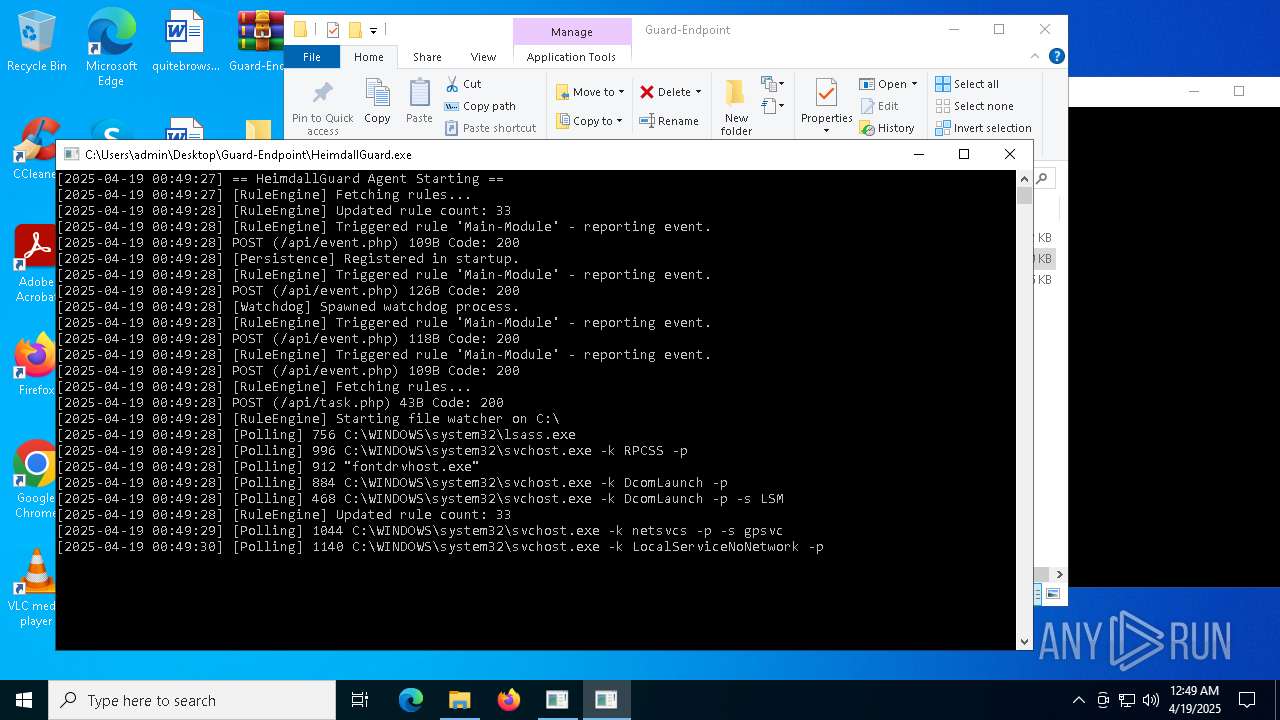
- HeimdallGuard.exe (PID: 2772)
Connects to the server without a host name
- Christmas Tree.exe (PID: 6324)
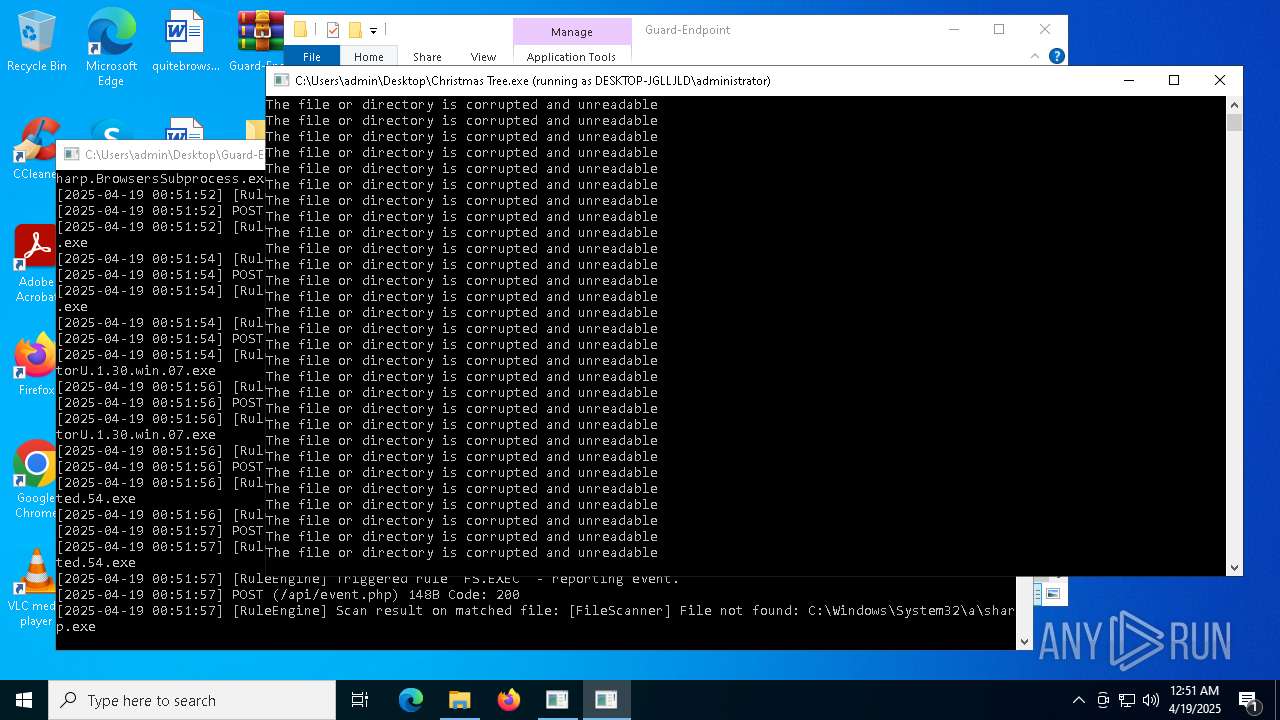
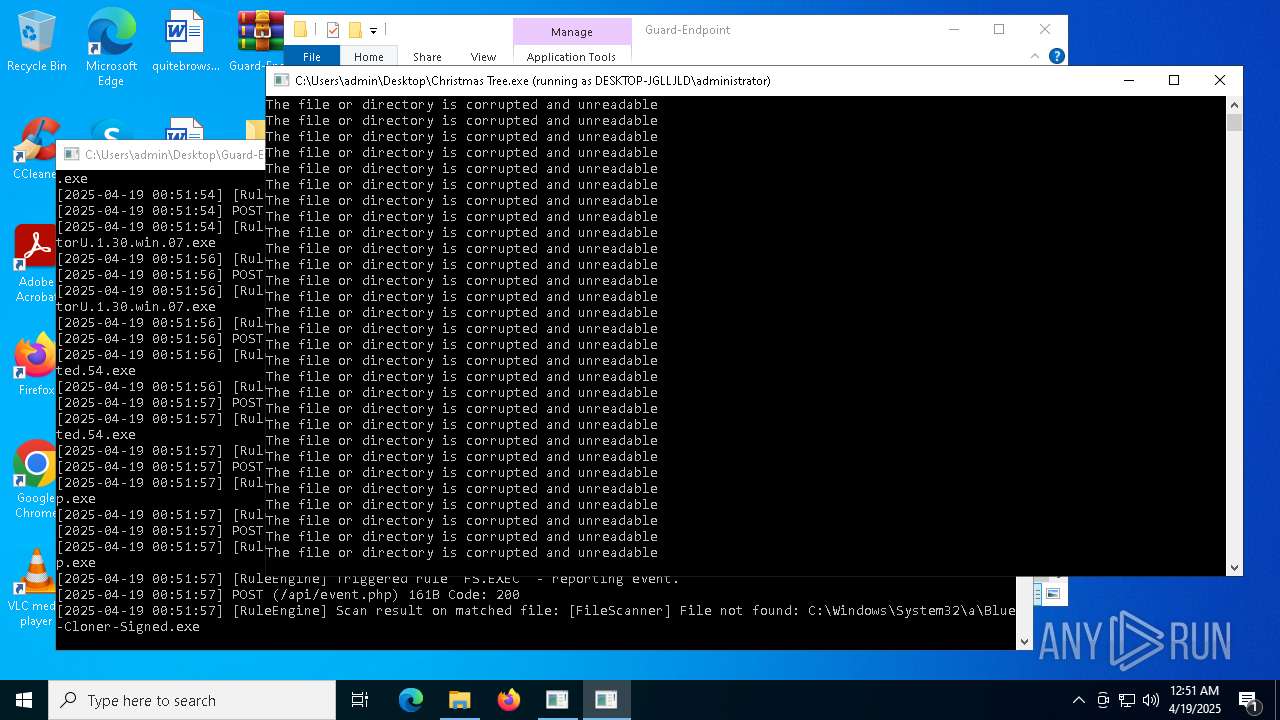
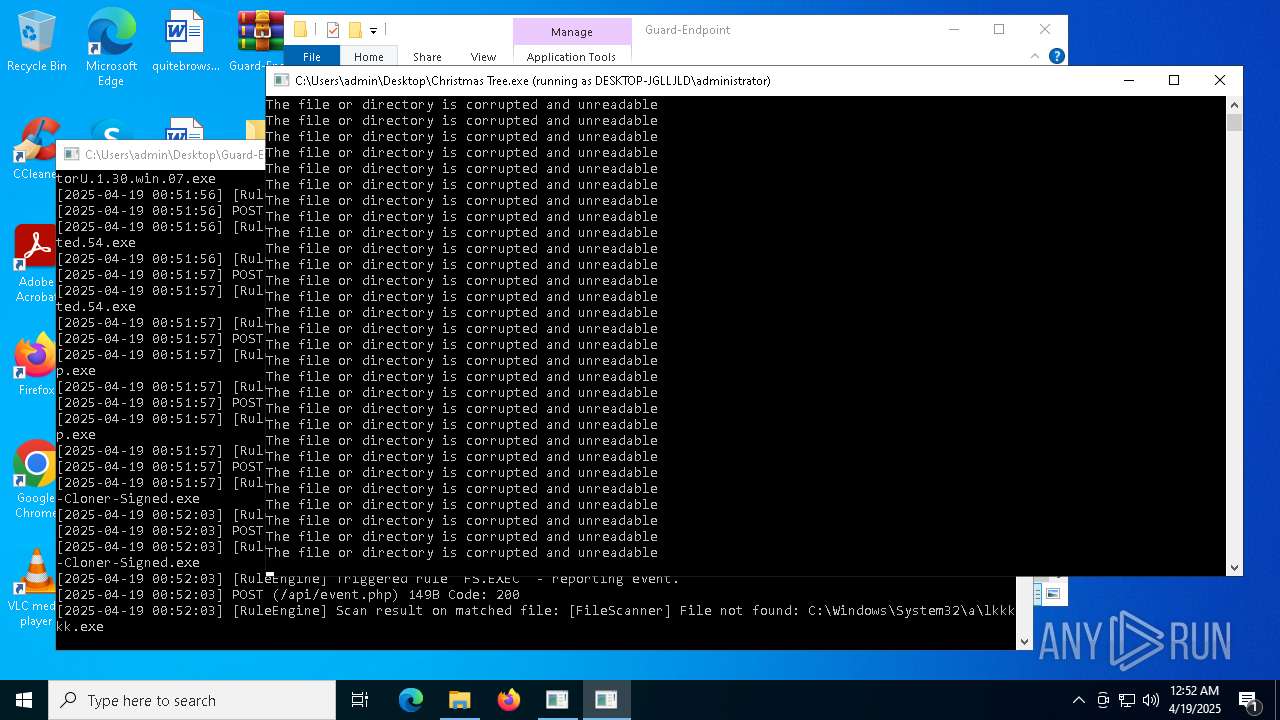
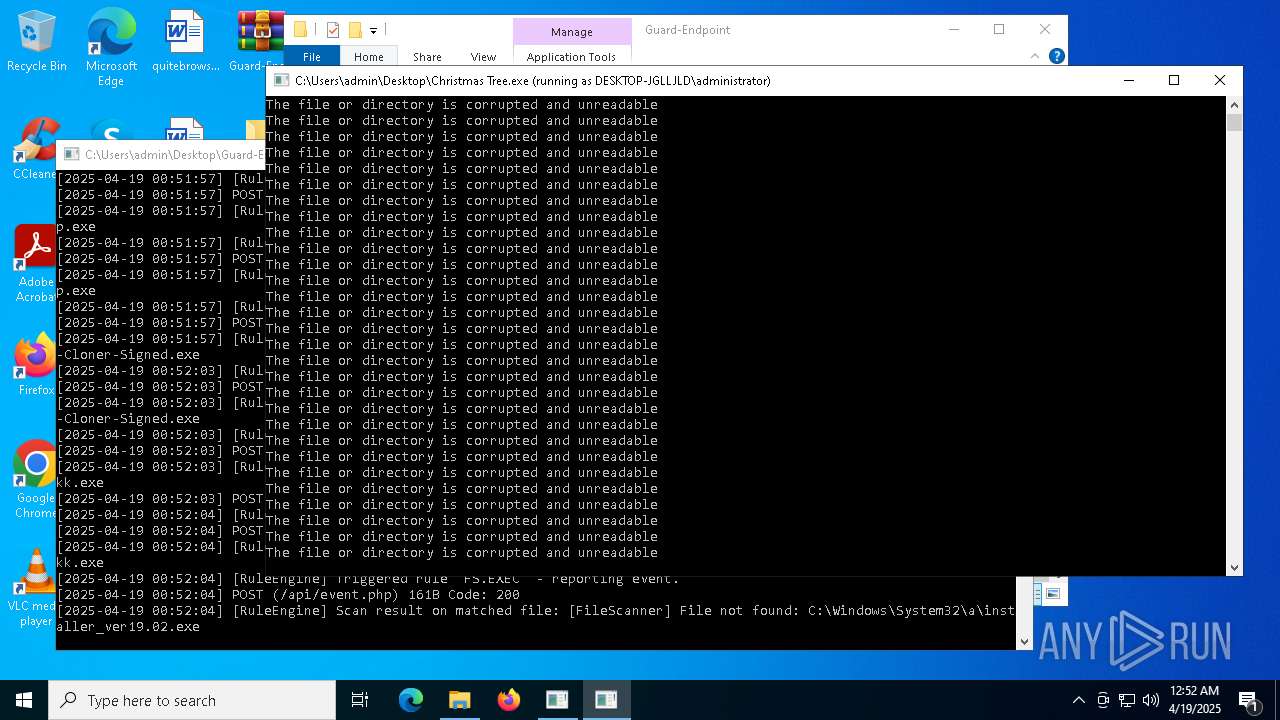
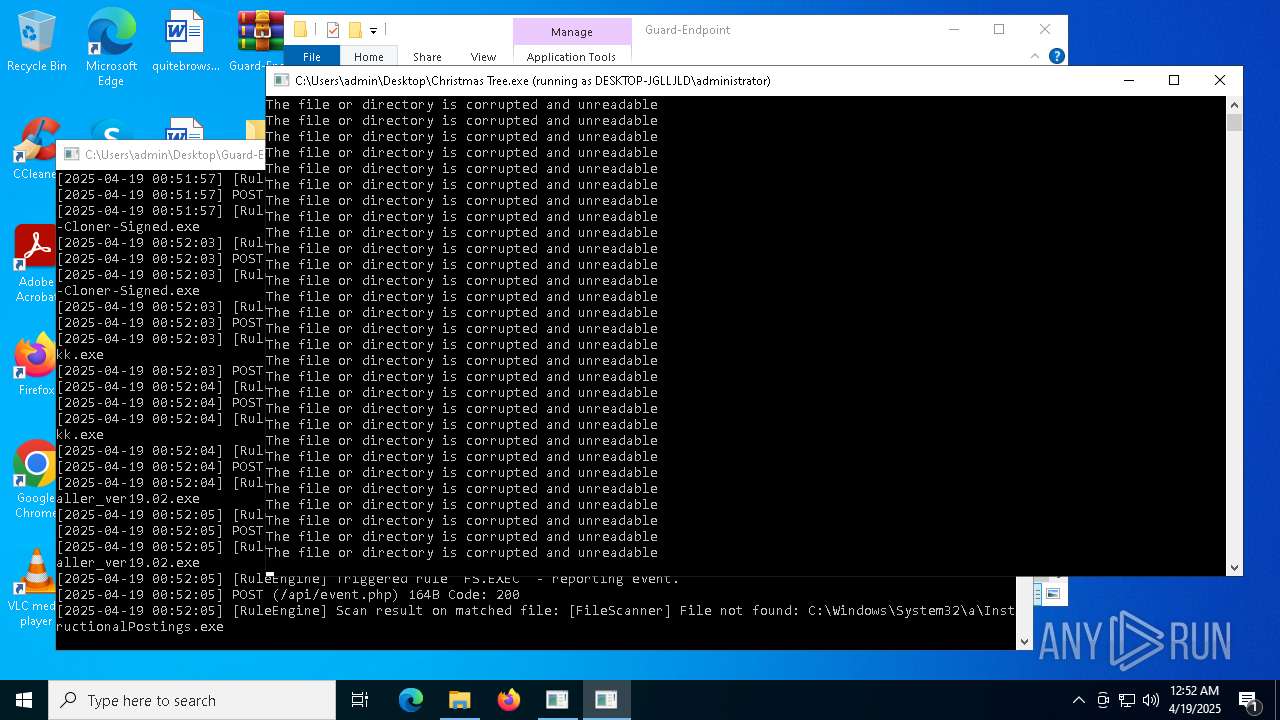
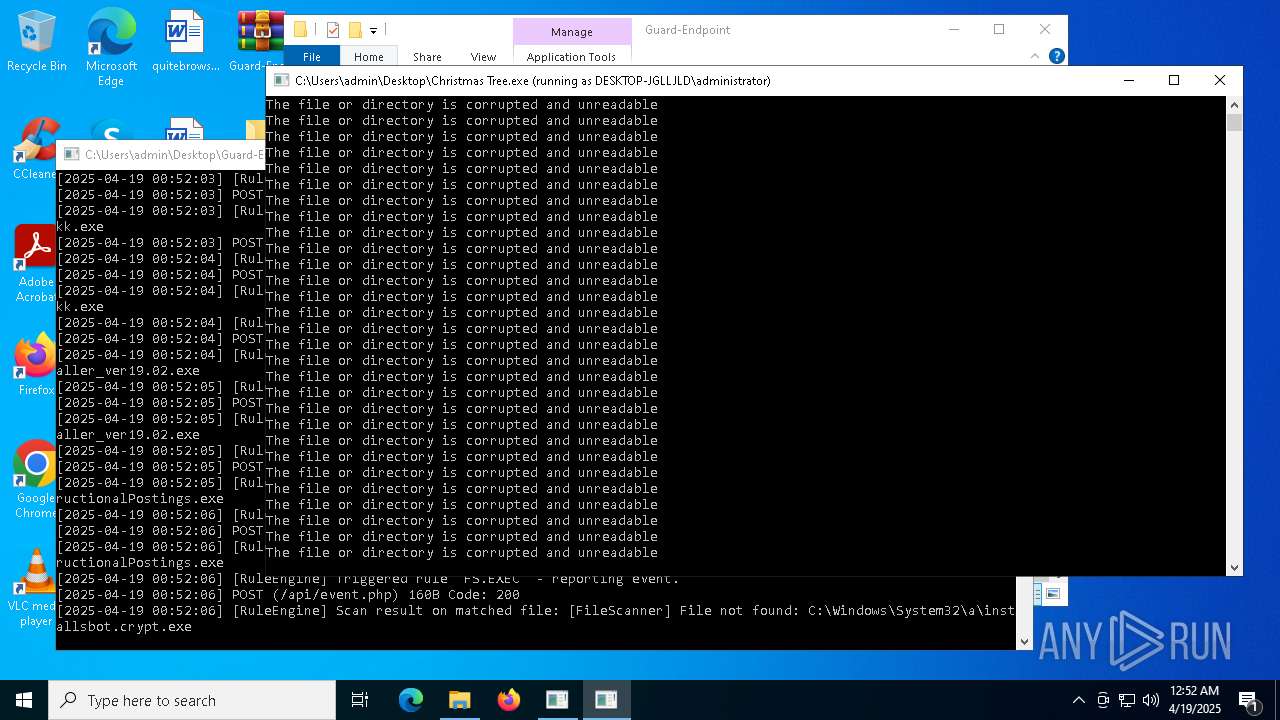
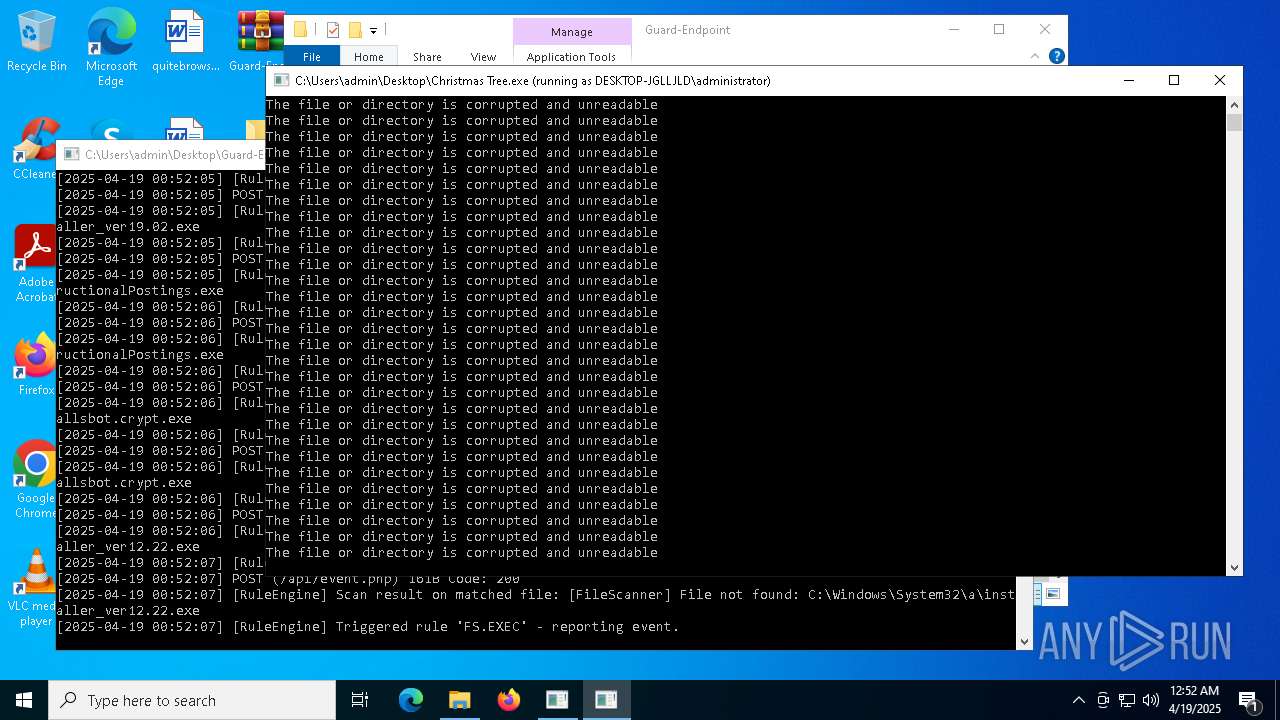
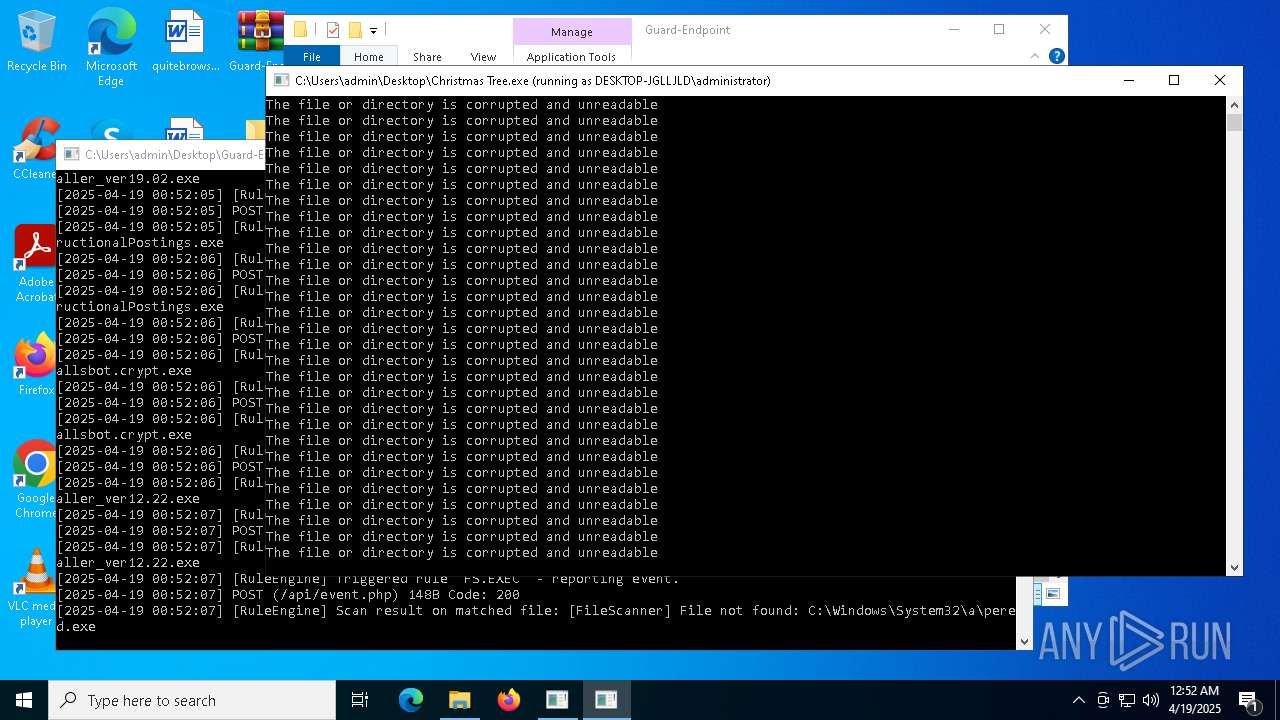
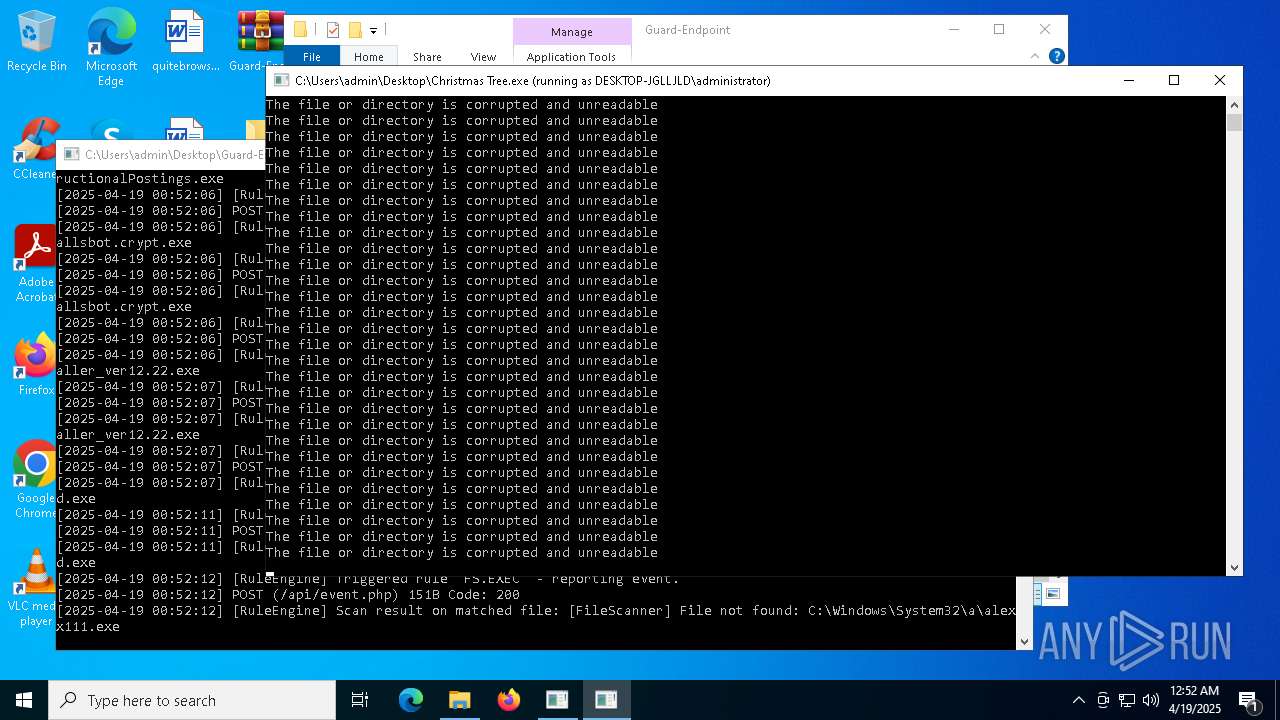
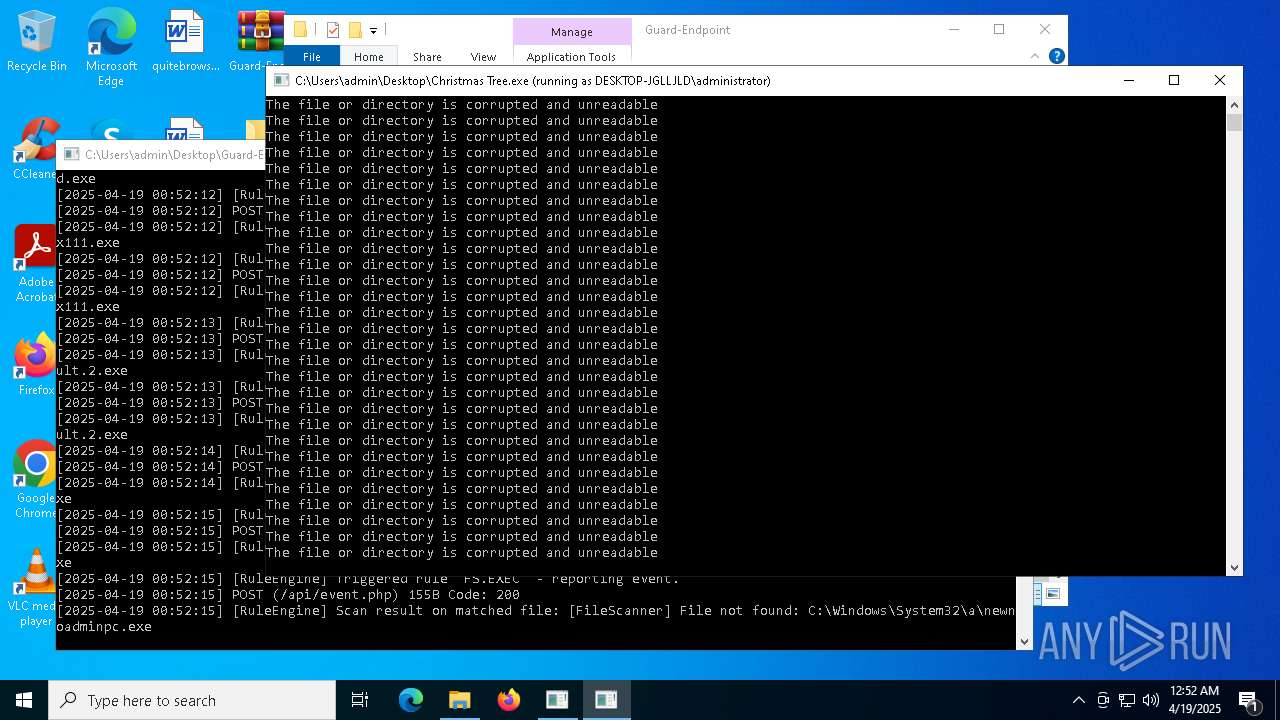
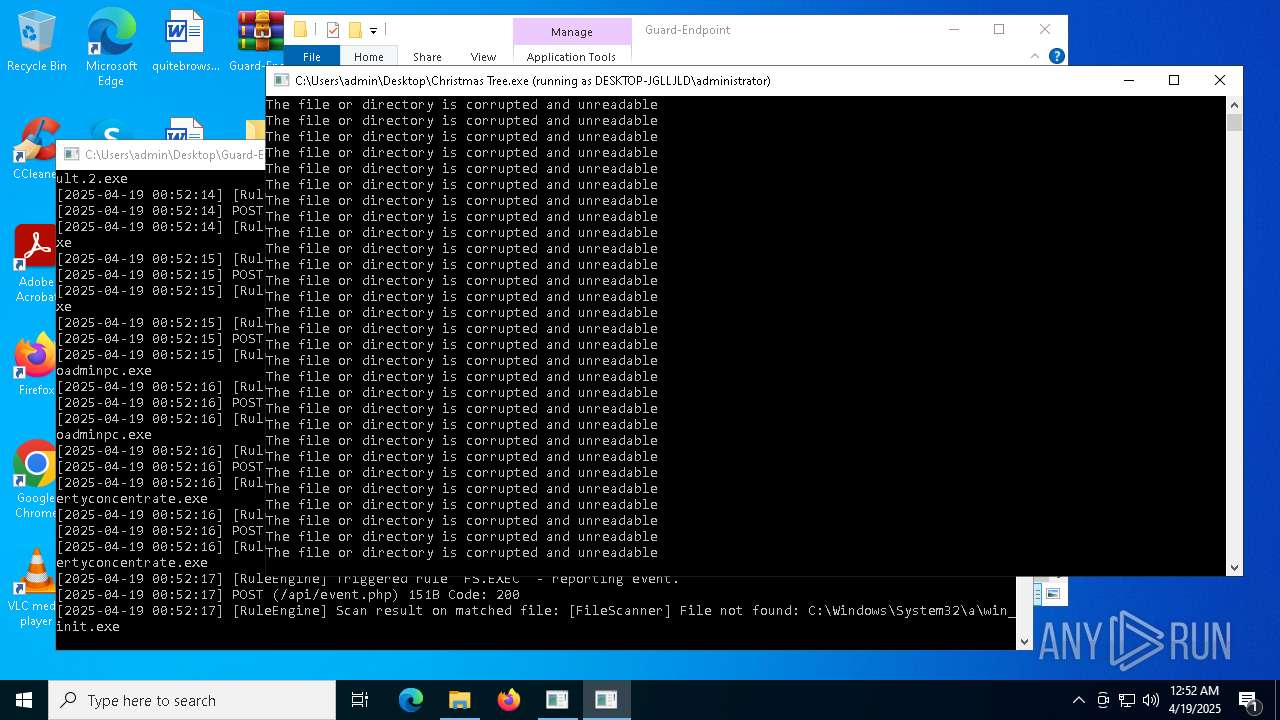
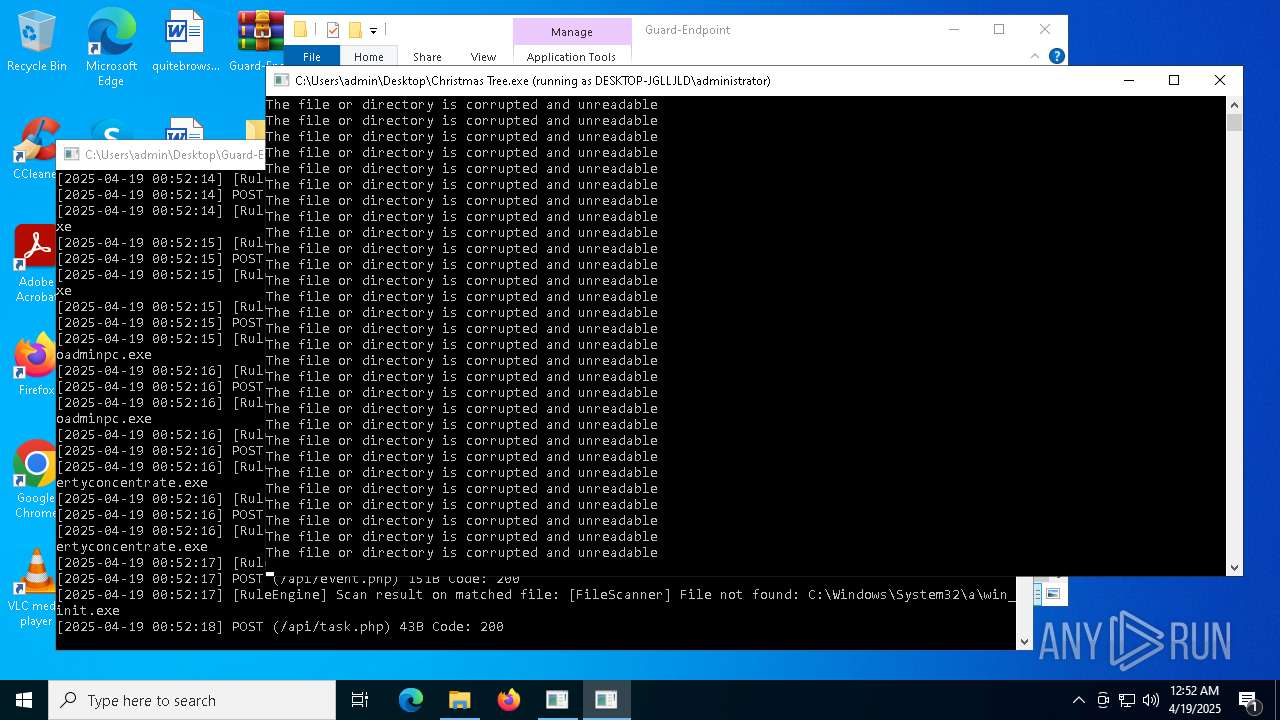
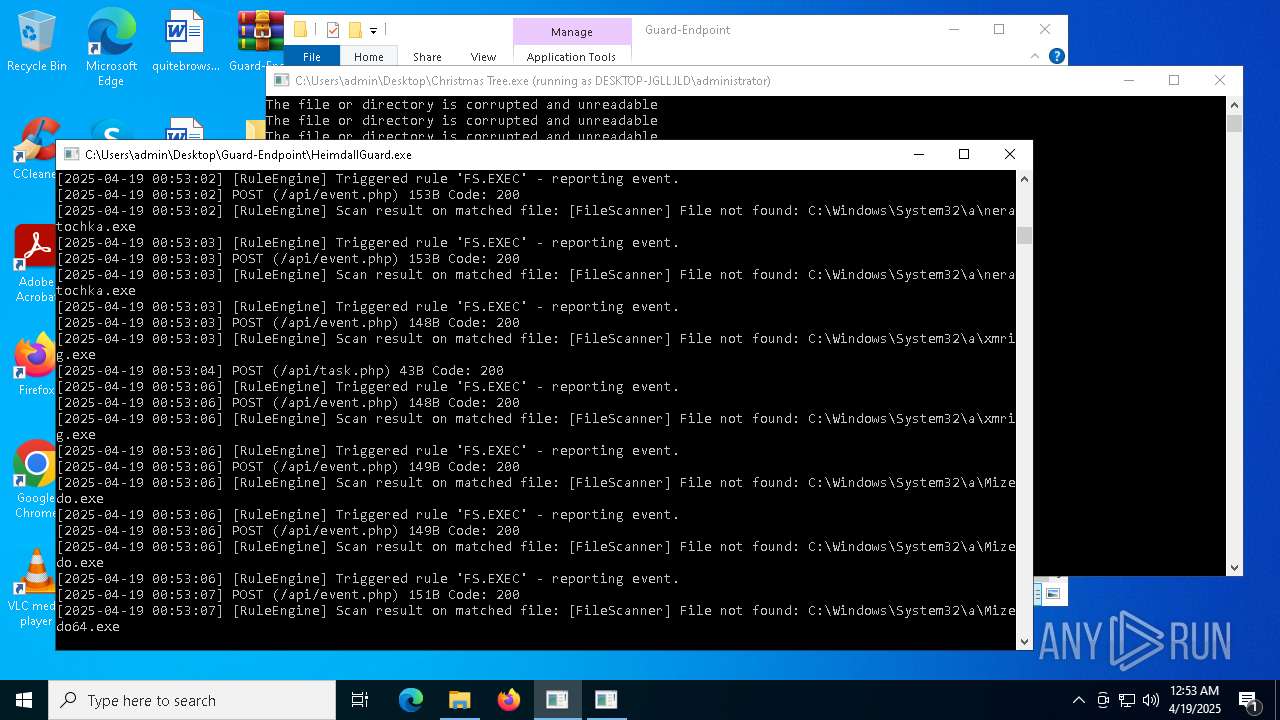
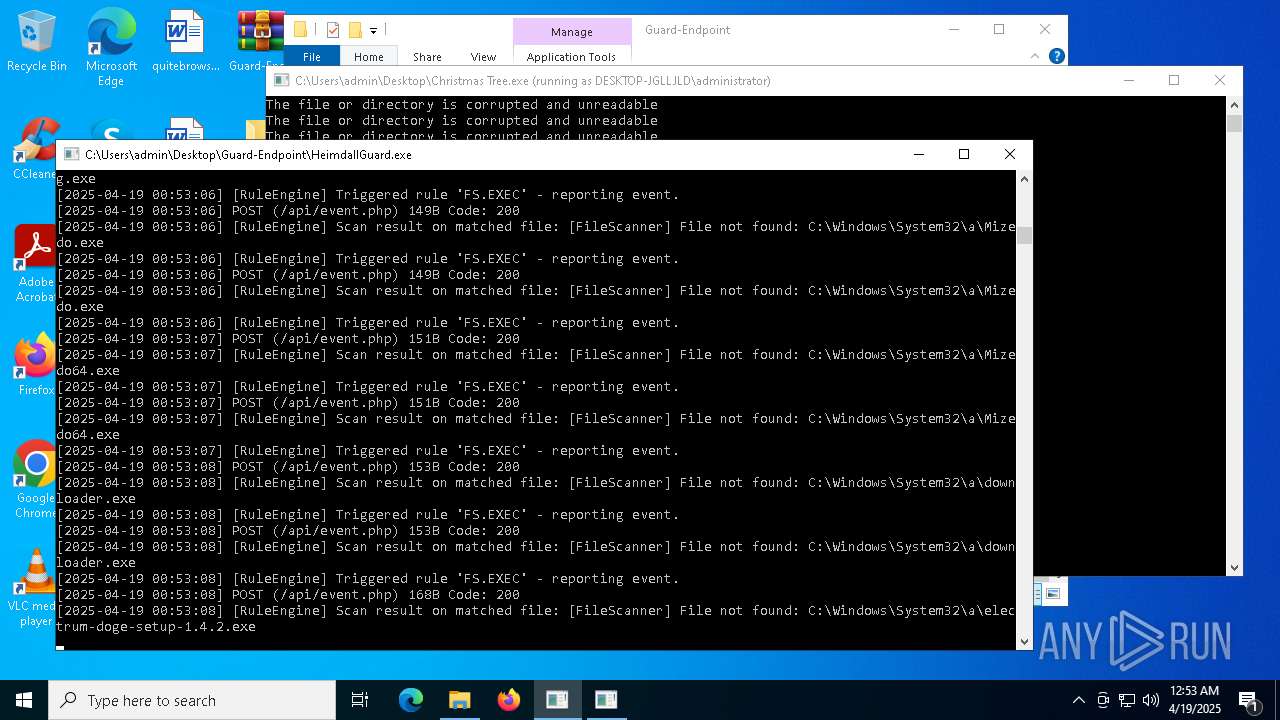
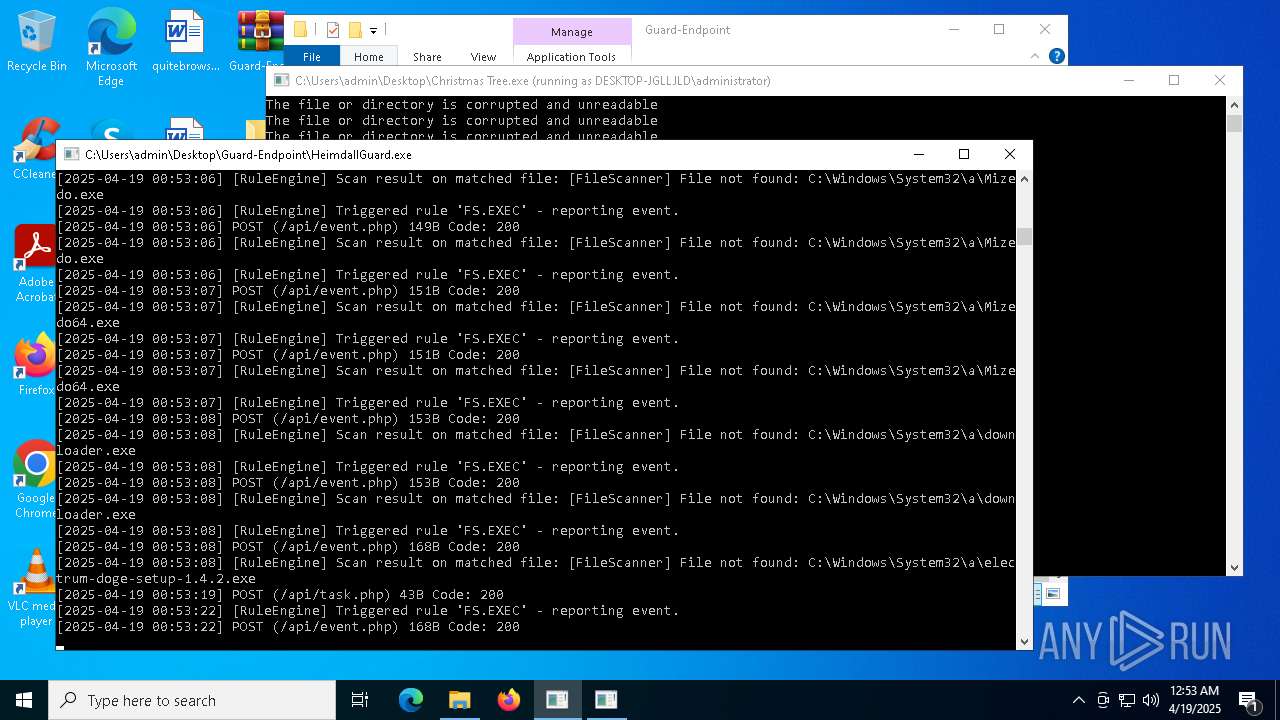
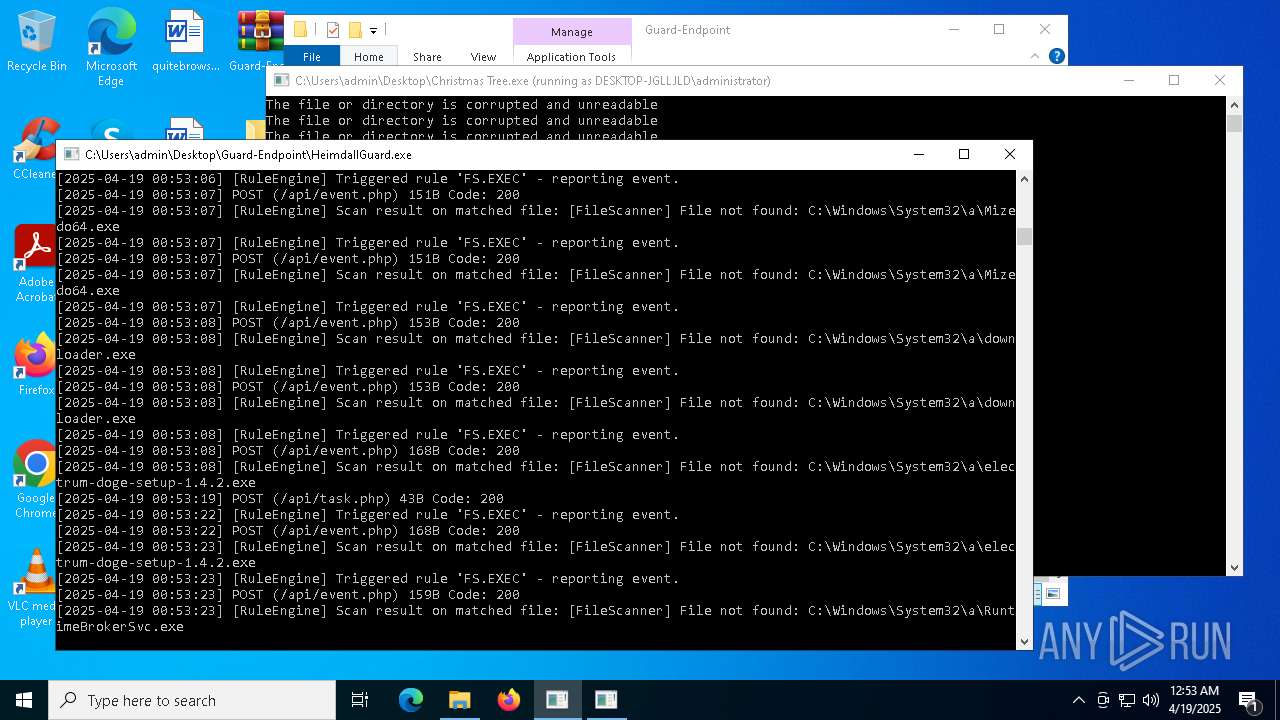
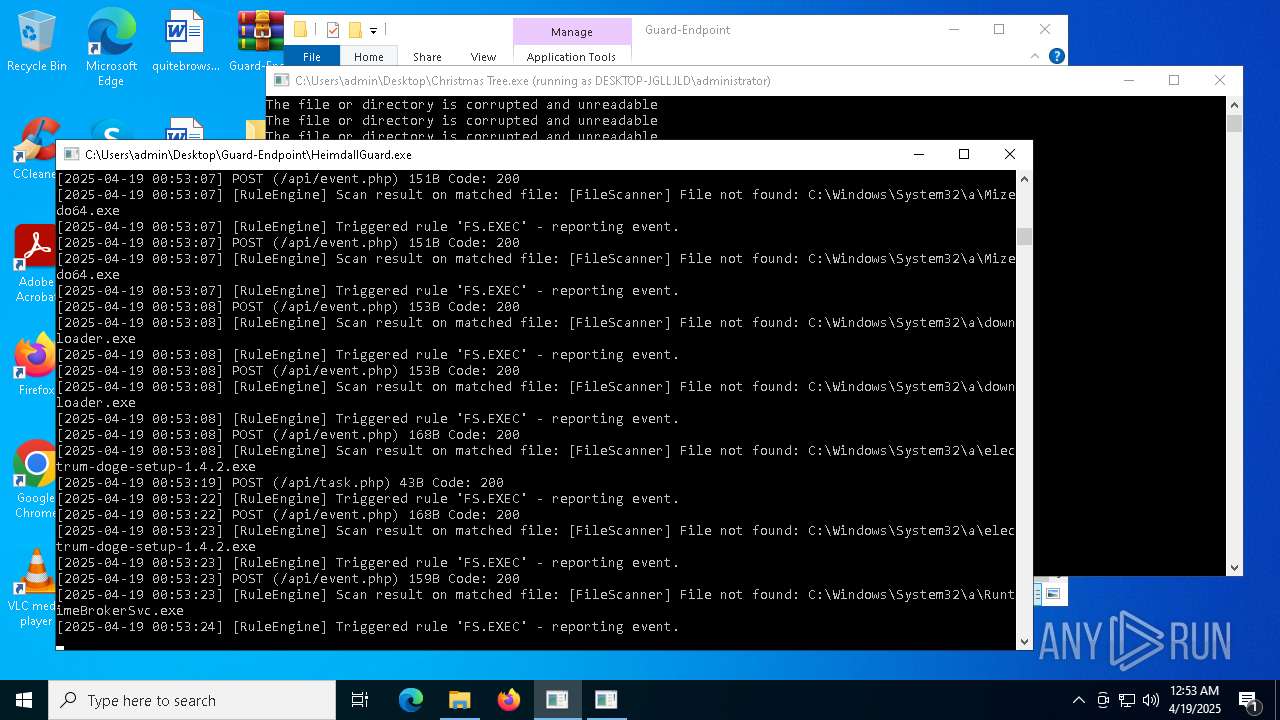
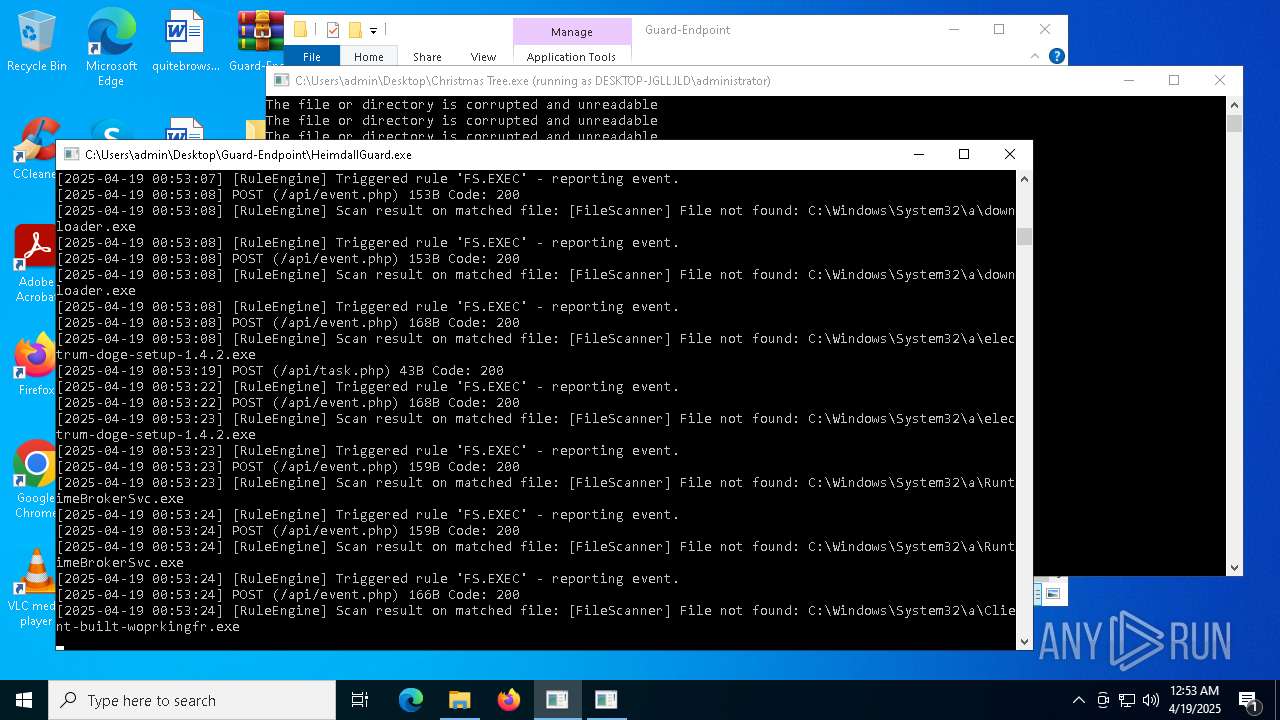
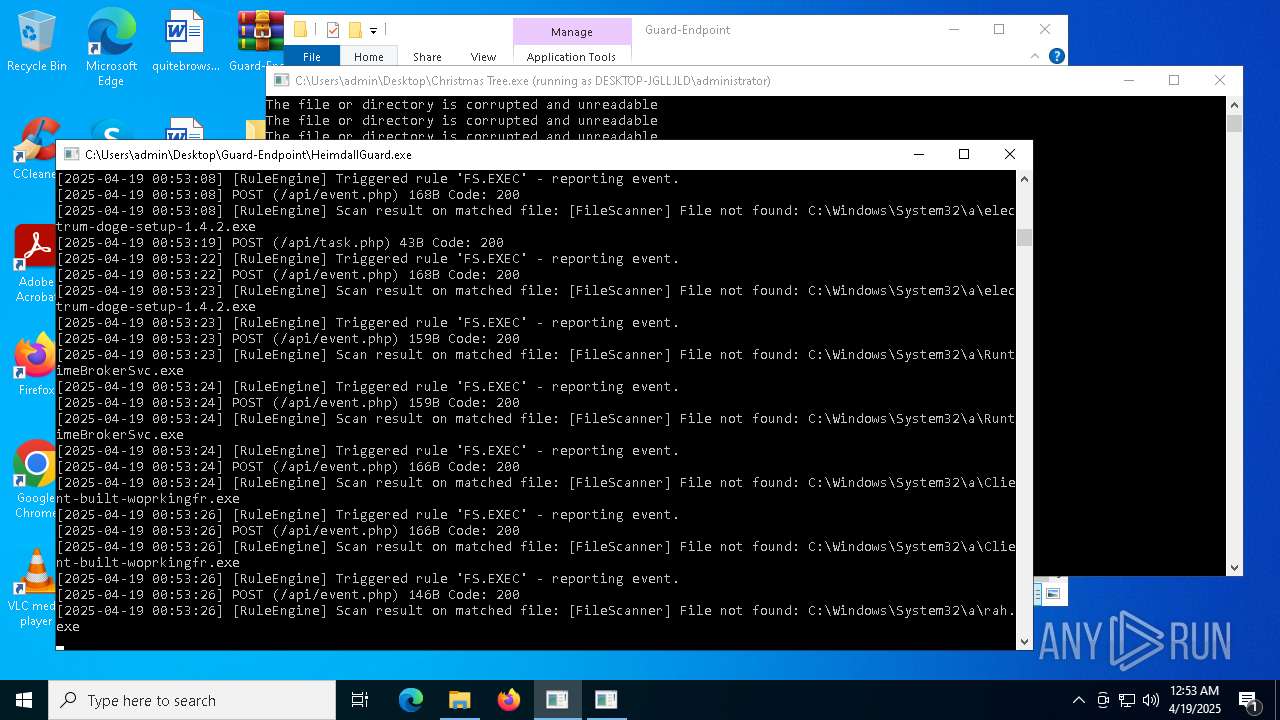
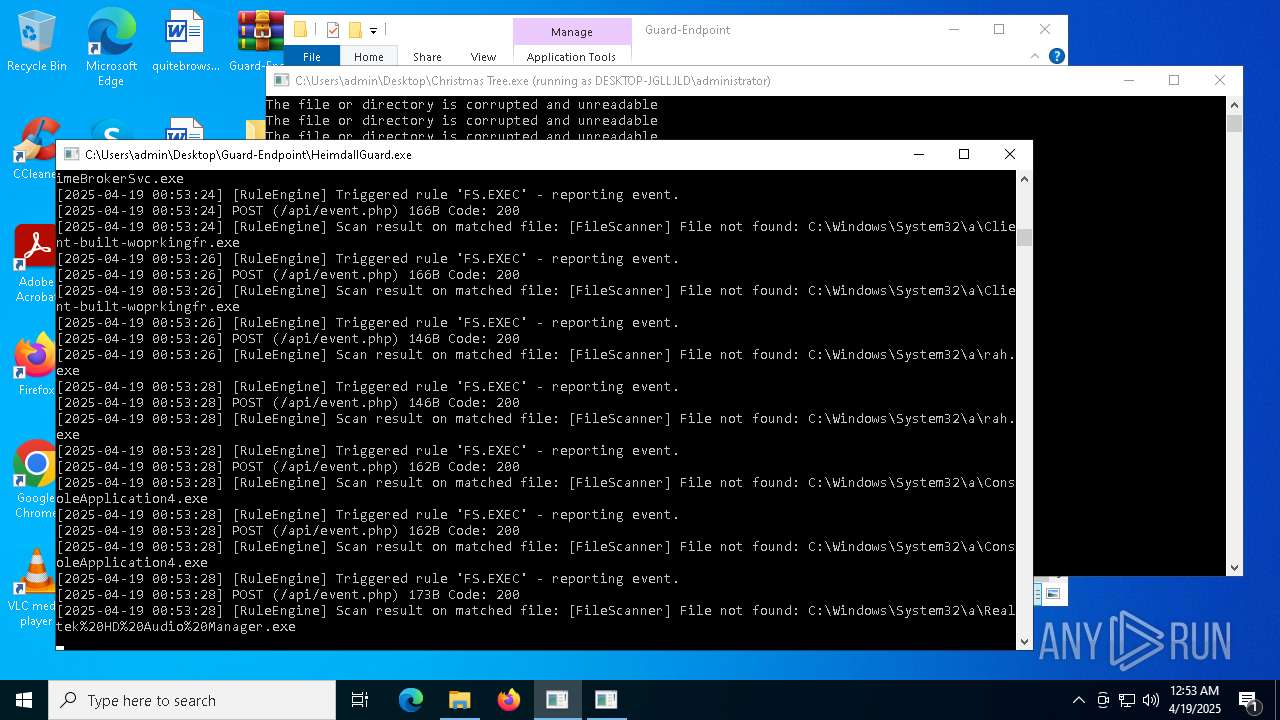
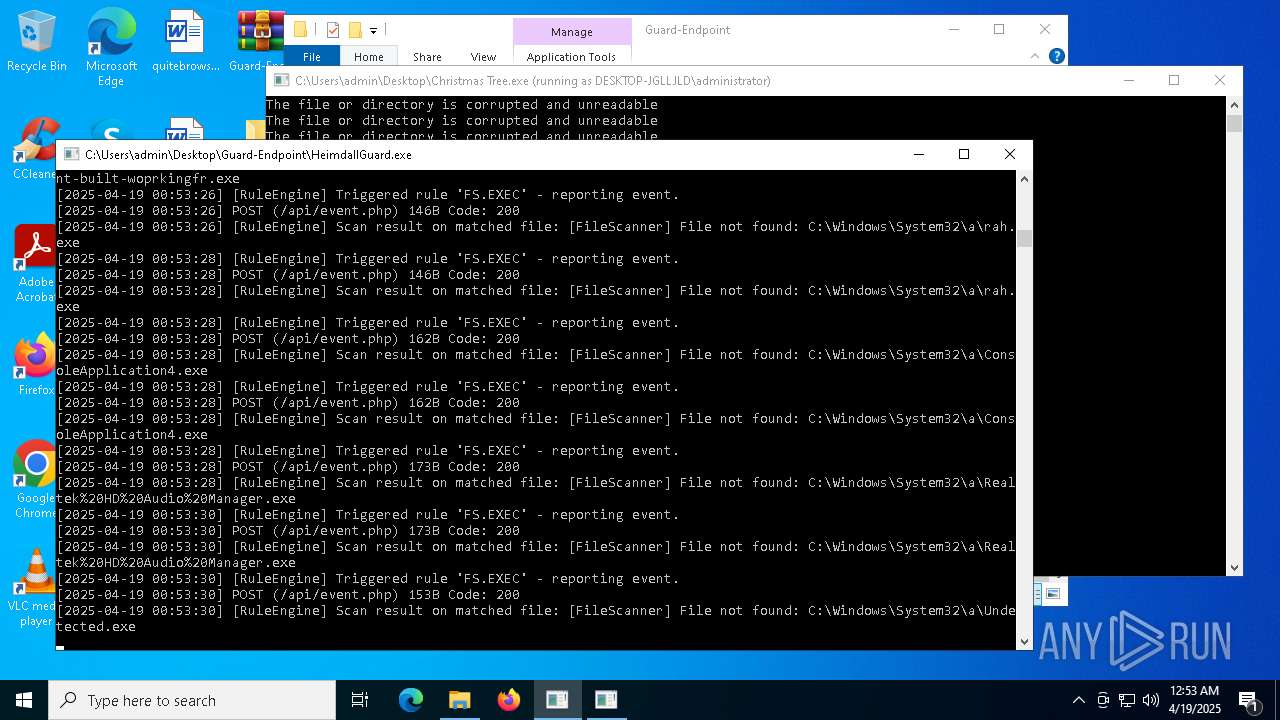
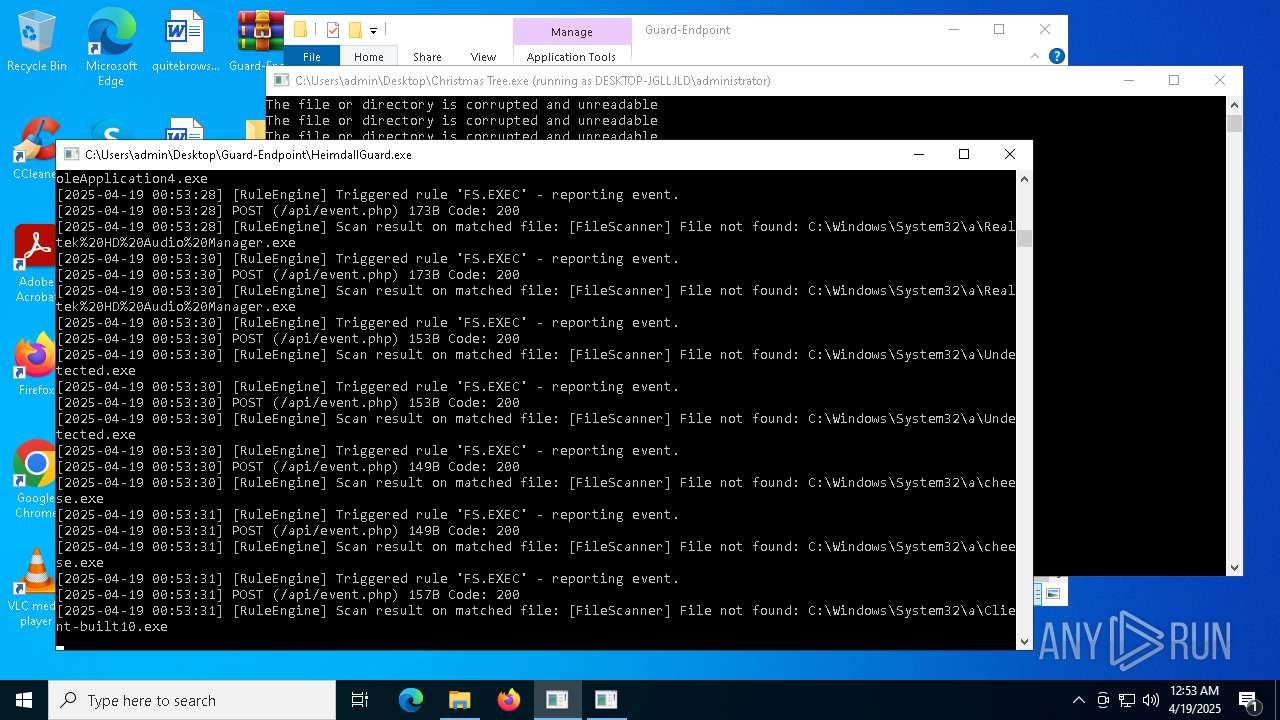
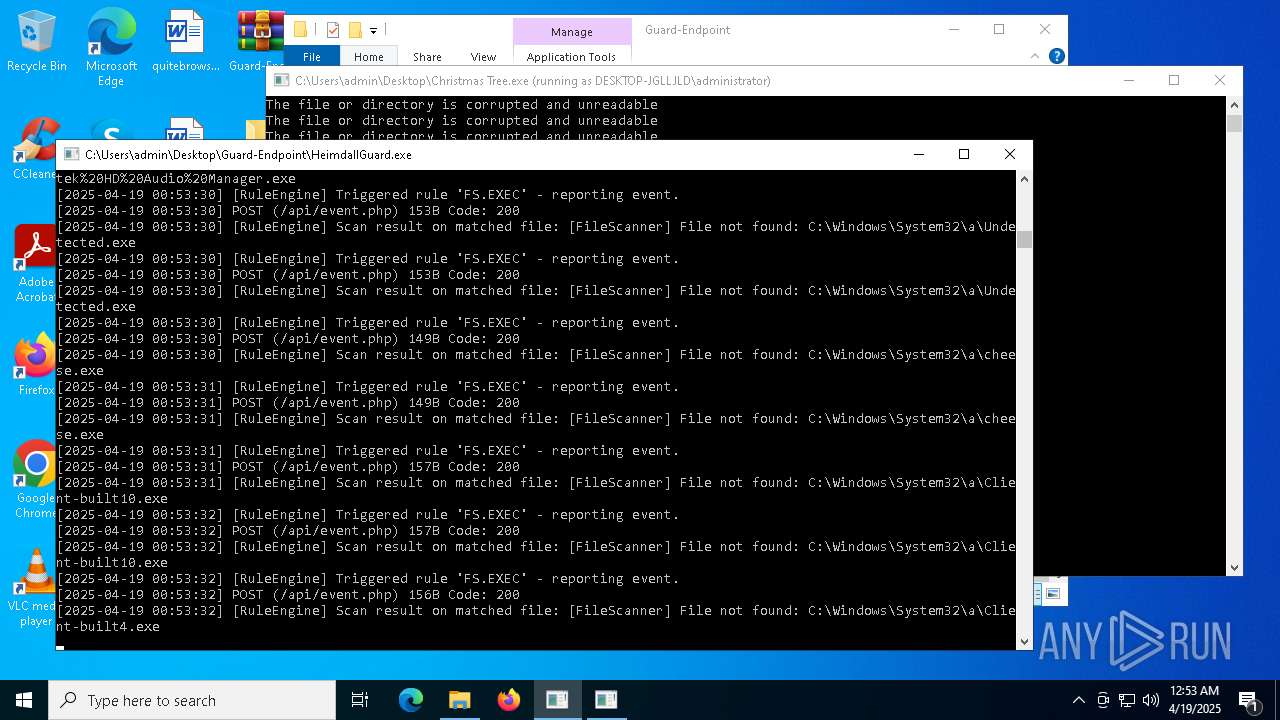
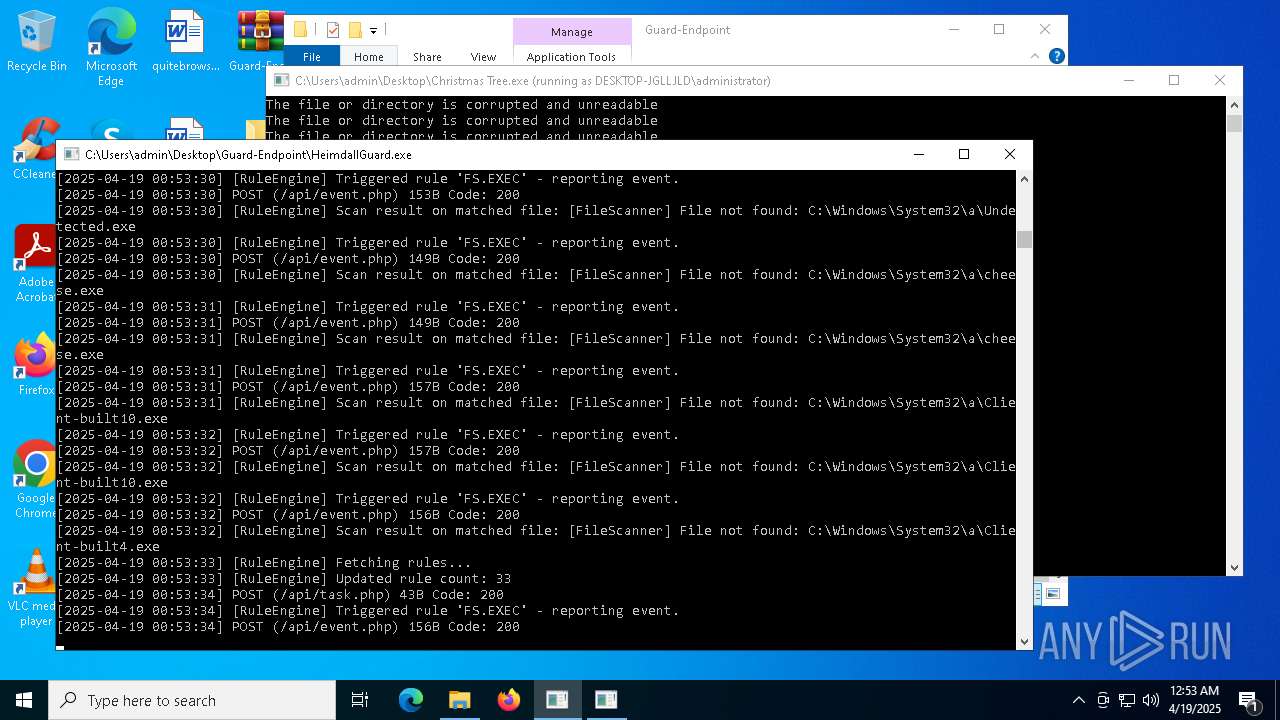
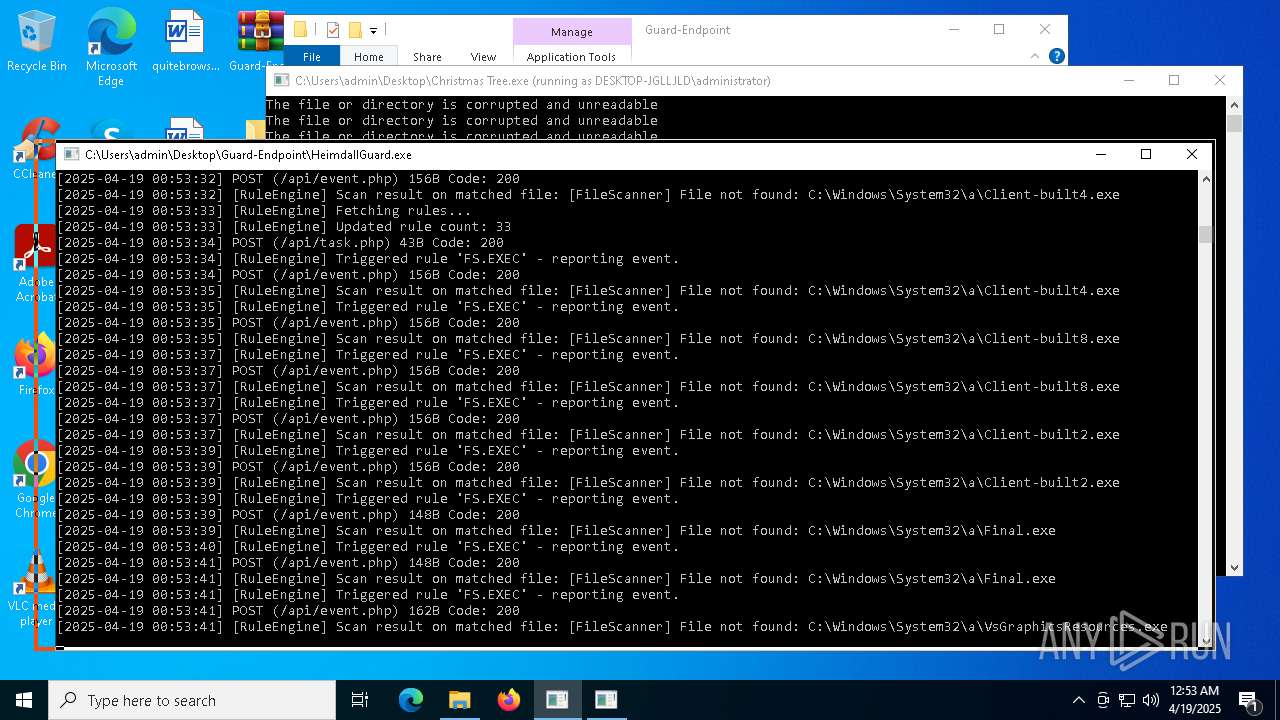
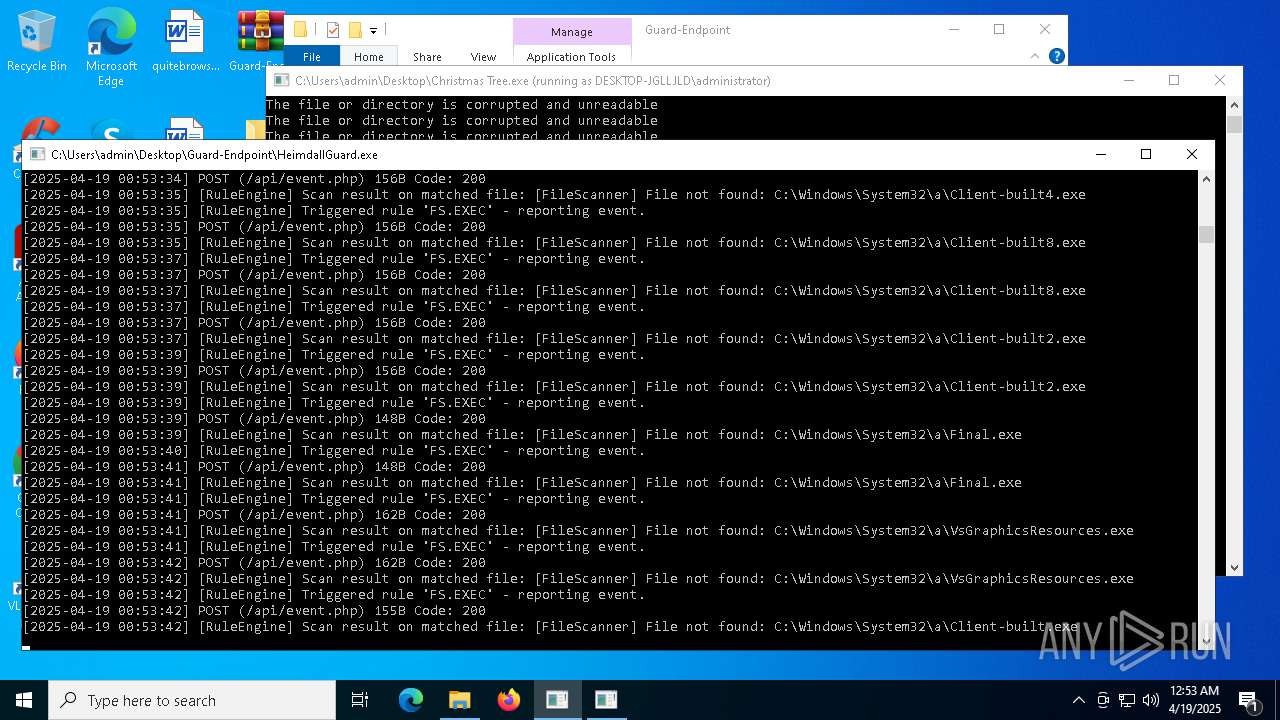
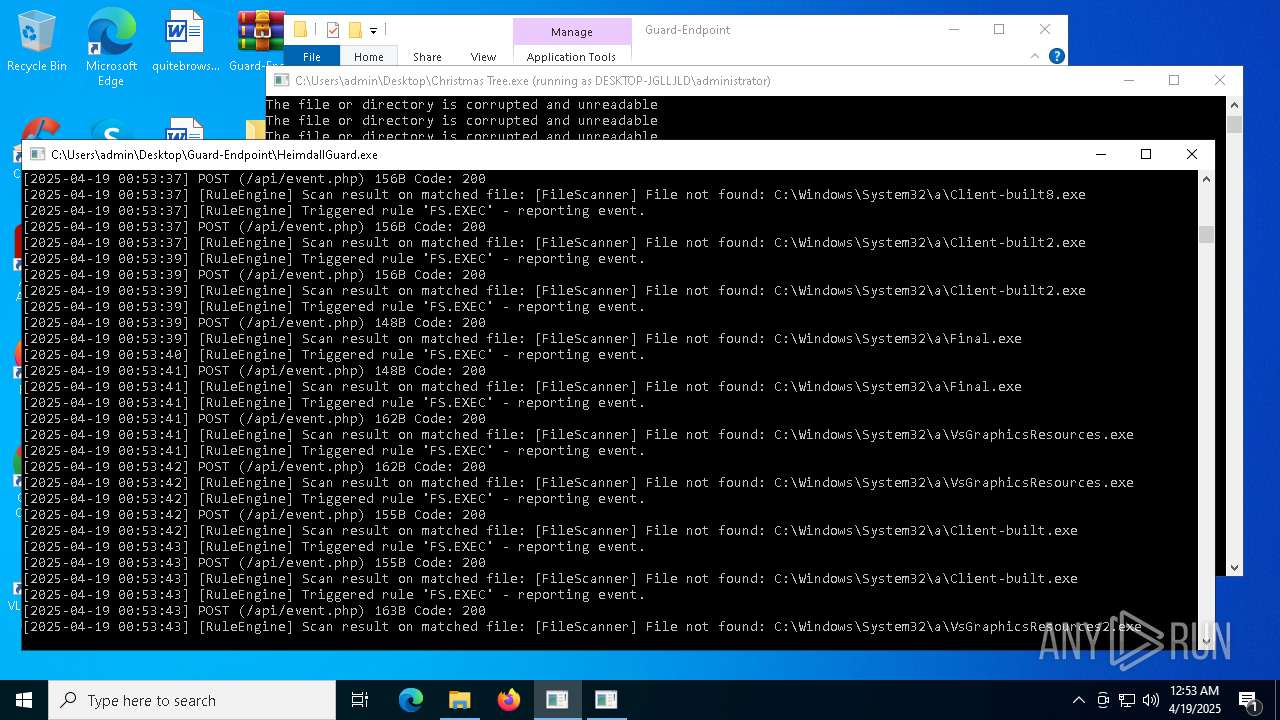
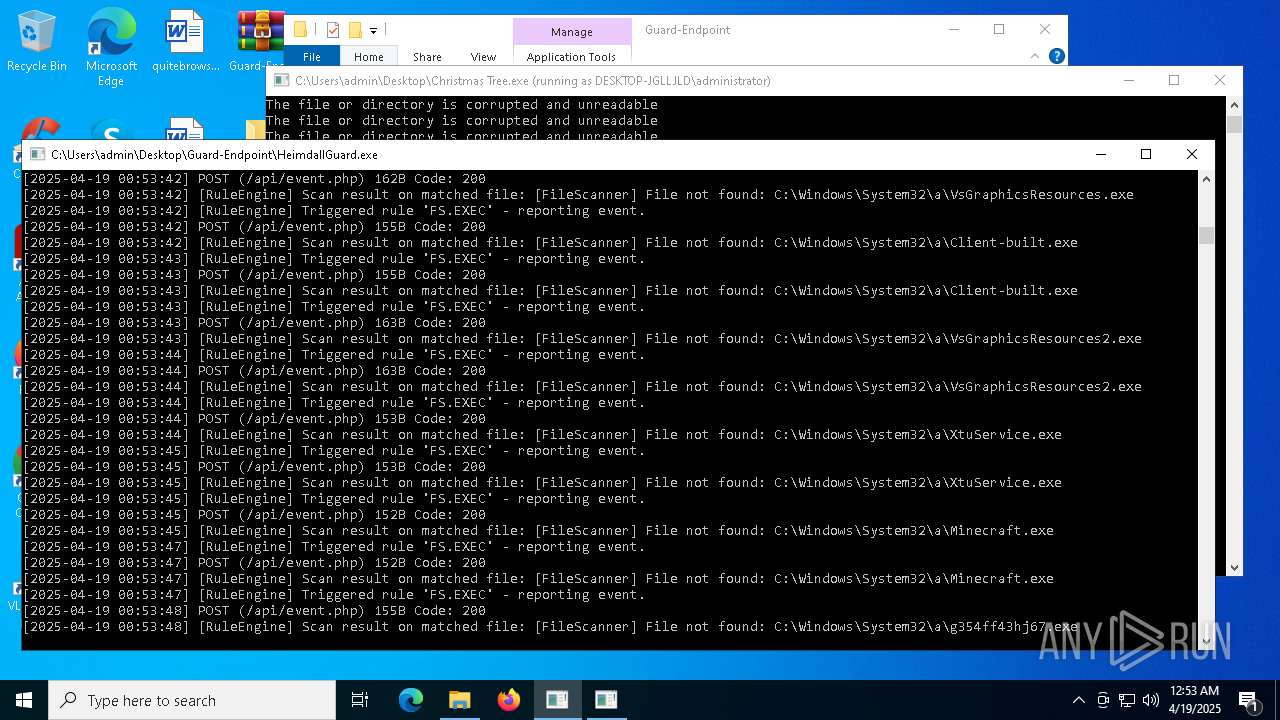
Executable content was dropped or overwritten
- Christmas Tree.exe (PID: 6324)
- Cloudy.exe (PID: 5216)
- ULauncher.exe (PID: 5892)
- RuntimeBroker.exe (PID: 7264)
- bootstrapper.exe (PID: 8076)
- raw_cbot.exe (PID: 7432)
- Device2.exe (PID: 8264)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- Host.exe (PID: 5736)
- c2new.exe (PID: 9080)
- updater.exe (PID: 9092)
- Quas13k.exe (PID: 668)
Process requests binary or script from the Internet
- Christmas Tree.exe (PID: 6324)
Potential Corporate Privacy Violation
- Christmas Tree.exe (PID: 6324)
- svchost.exe (PID: 2196)
Reads the date of Windows installation
- Christmas Tree.exe (PID: 6324)
- XClient.exe (PID: 4628)
- ULauncher.exe (PID: 5892)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
- s.exe (PID: 1096)
Reads security settings of Internet Explorer
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- brbotnet.exe (PID: 2908)
- ULauncher.exe (PID: 5892)
- asdasdasdasdasd.exe (PID: 7576)
- Fix.exe (PID: 2560)
- ShellExperienceHost.exe (PID: 6560)
- csrss.exe (PID: 3796)
- XClient.exe (PID: 4628)
- hkcmd.exe (PID: 732)
- Host.exe (PID: 5736)
- s.exe (PID: 1096)
Contacting a server suspected of hosting an CnC
- S123.exe (PID: 1328)
Checks for external IP
- svchost.exe (PID: 2196)
- Cloudy.exe (PID: 5216)
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- ULauncher.exe (PID: 5892)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
There is functionality for taking screenshot (YARA)
- S123.exe (PID: 1328)
Connects to unusual port
- Christmas Tree.exe (PID: 6324)
- remcos_a.exe (PID: 7700)
- asdasdasdasdasd.exe (PID: 7576)
- explorer.exe (PID: 7440)
- Cloudy.exe (PID: 5216)
- raw_cbot.exe (PID: 7432)
- RuntimeBroker.exe (PID: 8424)
- ULauncher.exe (PID: 5892)
- bootstrapper.exe (PID: 8872)
- Device2.exe (PID: 8264)
- Host.exe (PID: 5736)
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- explorer.exe (PID: 7400)
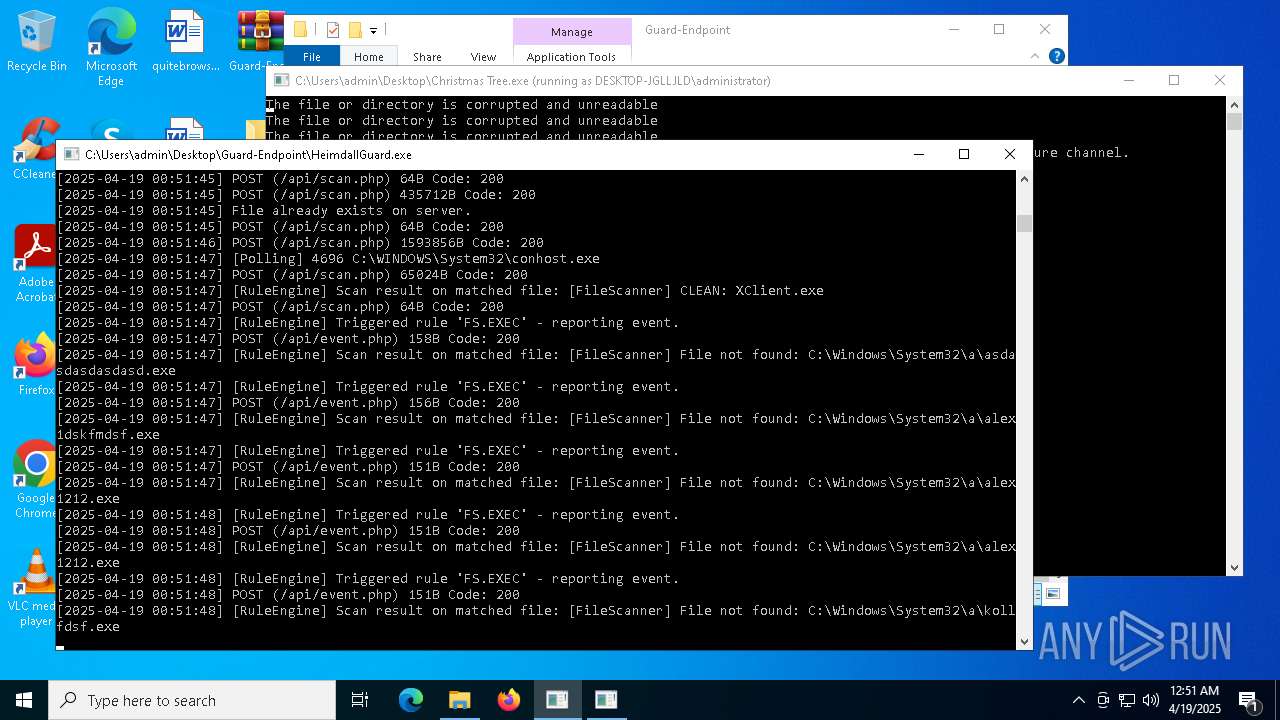
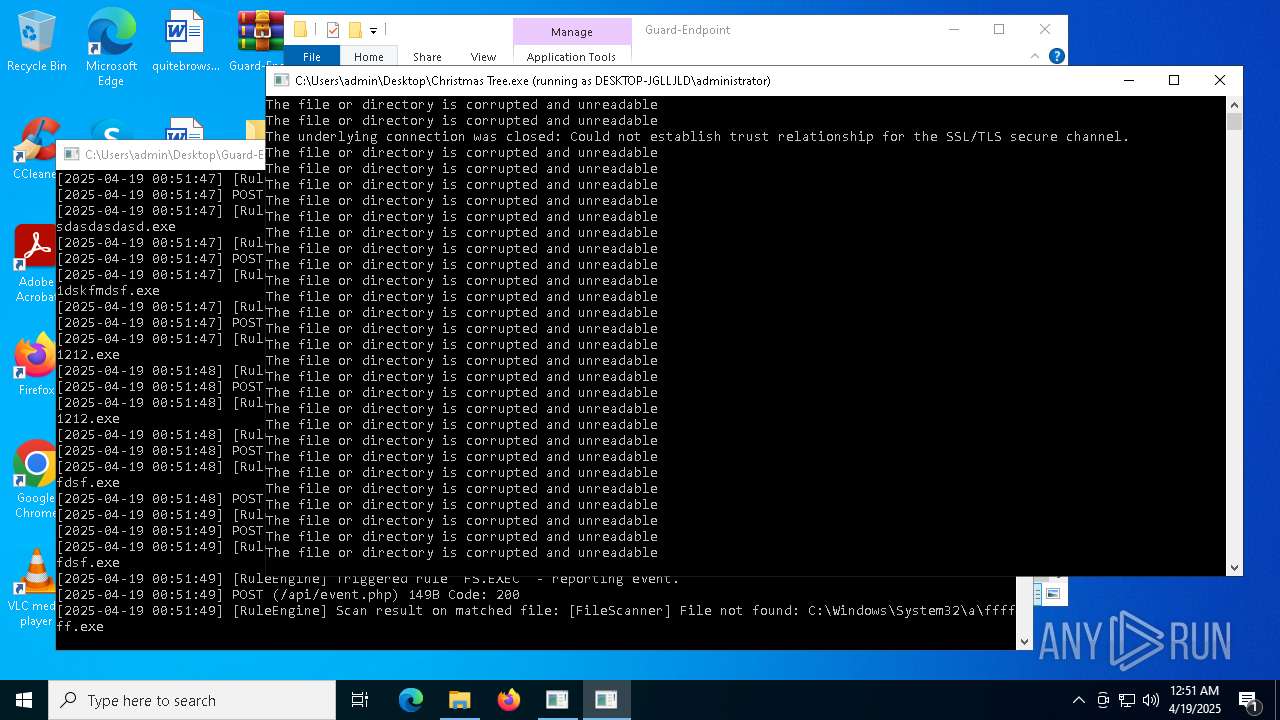
The process creates files with name similar to system file names
- Christmas Tree.exe (PID: 6324)
- Quas13k.exe (PID: 668)
- Fix.exe (PID: 2560)
- Host.exe (PID: 5736)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- Host.exe (PID: 5736)
Starts itself from another location
- Quas13k.exe (PID: 668)
- RuntimeBroker.exe (PID: 7264)
- bootstrapper.exe (PID: 8076)
Starts CMD.EXE for commands execution
- remcos_a.exe (PID: 7700)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7780)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ULauncher.exe (PID: 5892)
Executes application which crashes
- hkcmd.exe (PID: 732)
- csrss.exe (PID: 3796)
Process drops legitimate windows executable
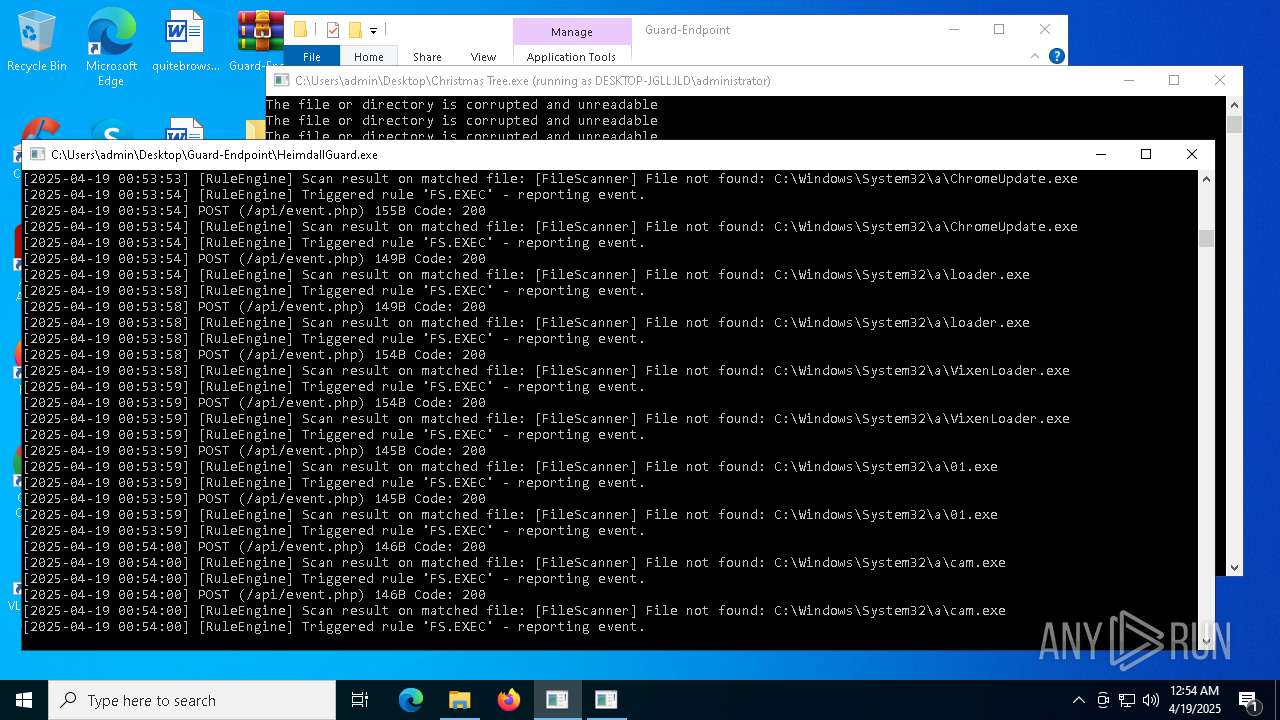
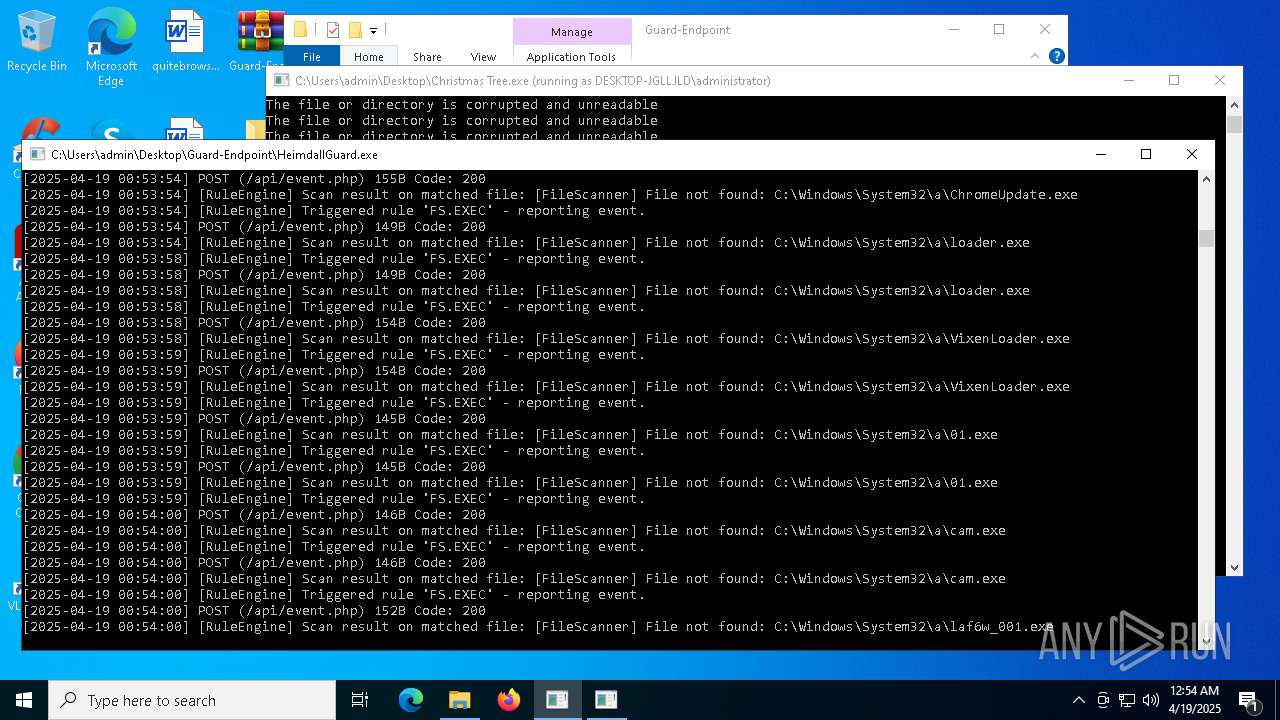
- Christmas Tree.exe (PID: 6324)
The process checks if it is being run in the virtual environment
- BruterV3.1.exe (PID: 8780)
- Christmas Tree.exe (PID: 6324)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Device2.exe (PID: 8264)
Mutex name with non-standard characters
- taskhostw.exe (PID: 8040)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7340)
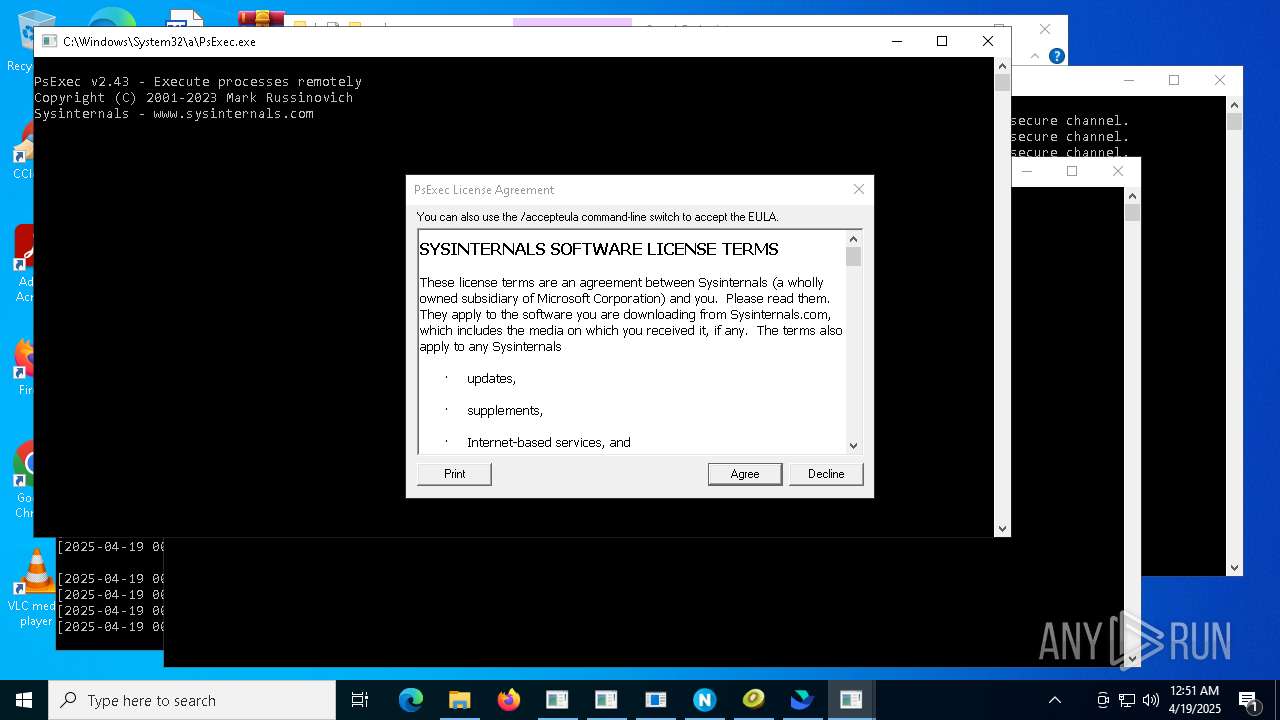
PSEXEC has been detected
- PsExec.exe (PID: 8736)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 8496)
- cmd.exe (PID: 8620)
The process executes via Task Scheduler
- updater.exe (PID: 9092)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 9092)
INFO
Manual execution by a user
- WinRAR.exe (PID: 5544)
- HeimdallGuard.exe (PID: 1188)
- HeimdallGuard.exe (PID: 2772)
- cmd.exe (PID: 8496)
- schtasks.exe (PID: 7340)
- schtasks.exe (PID: 516)
- schtasks.exe (PID: 8092)
- cmd.exe (PID: 8620)
- schtasks.exe (PID: 7220)
- conhost.exe (PID: 4696)
- explorer.exe (PID: 7400)
Reads the machine GUID from the registry
- HeimdallGuard.exe (PID: 1188)
- HeimdallGuard.exe (PID: 2772)
- HeimdallGuard.exe (PID: 7052)
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- XClient.exe (PID: 4628)
- Cloudy.exe (PID: 5216)
- s.exe (PID: 1096)
- Fix.exe (PID: 2560)
- Quas13k.exe (PID: 668)
- ULauncher.exe (PID: 5892)
- Host.exe (PID: 5736)
- asdasdasdasdasd.exe (PID: 7576)
- explorer.exe (PID: 7440)
- RuntimeBroker.exe (PID: 7264)
- bootstrapper.exe (PID: 8076)
- RuntimeBroker.exe (PID: 8424)
- BruterV3.1.exe (PID: 8780)
- bootstrapper.exe (PID: 8872)
- Device2.exe (PID: 8264)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5544)
Checks supported languages
- HeimdallGuard.exe (PID: 2772)
- HeimdallGuard.exe (PID: 1188)
- HeimdallGuard.exe (PID: 7052)
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- CZXCVTD.exe (PID: 924)
- FoxmailSetup_7.2.25.375.exe (PID: 1748)
- brbotnet.exe (PID: 2908)
- nvnc.exe (PID: 4740)
- hkcmd.exe (PID: 732)
- CONVERTER.exe (PID: 4012)
- snd16061.exe (PID: 6476)
- csrss.exe (PID: 3796)
- XClient.exe (PID: 4628)
- Cloudy.exe (PID: 5216)
- s.exe (PID: 1096)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
- Quas13k.exe (PID: 668)
- thin.exe (PID: 4784)
- ULauncher.exe (PID: 5892)
- explorer.exe (PID: 7440)
- asdasdasdasdasd.exe (PID: 7576)
- remcos_a.exe (PID: 7700)
- RuntimeBroker.exe (PID: 7264)
- ShellExperienceHost.exe (PID: 6560)
- bootstrapper.exe (PID: 8076)
- Device2.exe (PID: 8264)
- RuntimeBroker.exe (PID: 8424)
- BruterV3.1.exe (PID: 8780)
- bootstrapper.exe (PID: 8872)
- 1.exe (PID: 8884)
- payload1.exe (PID: 9012)
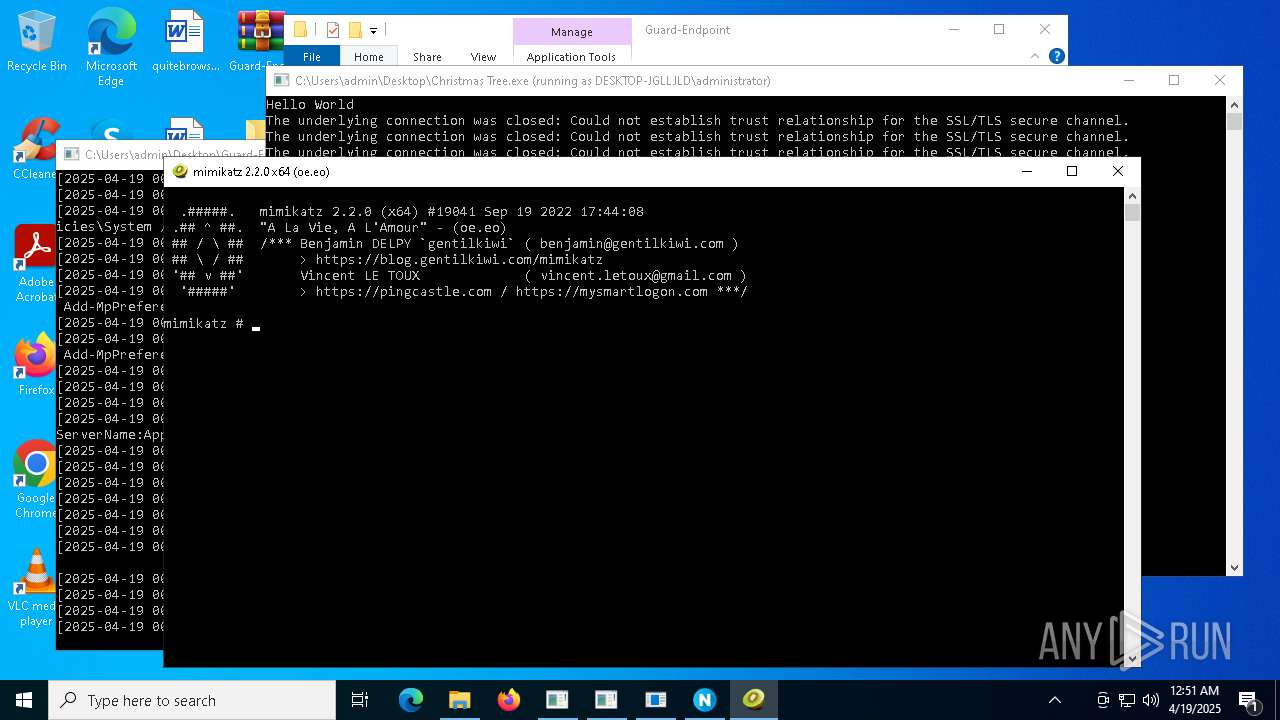
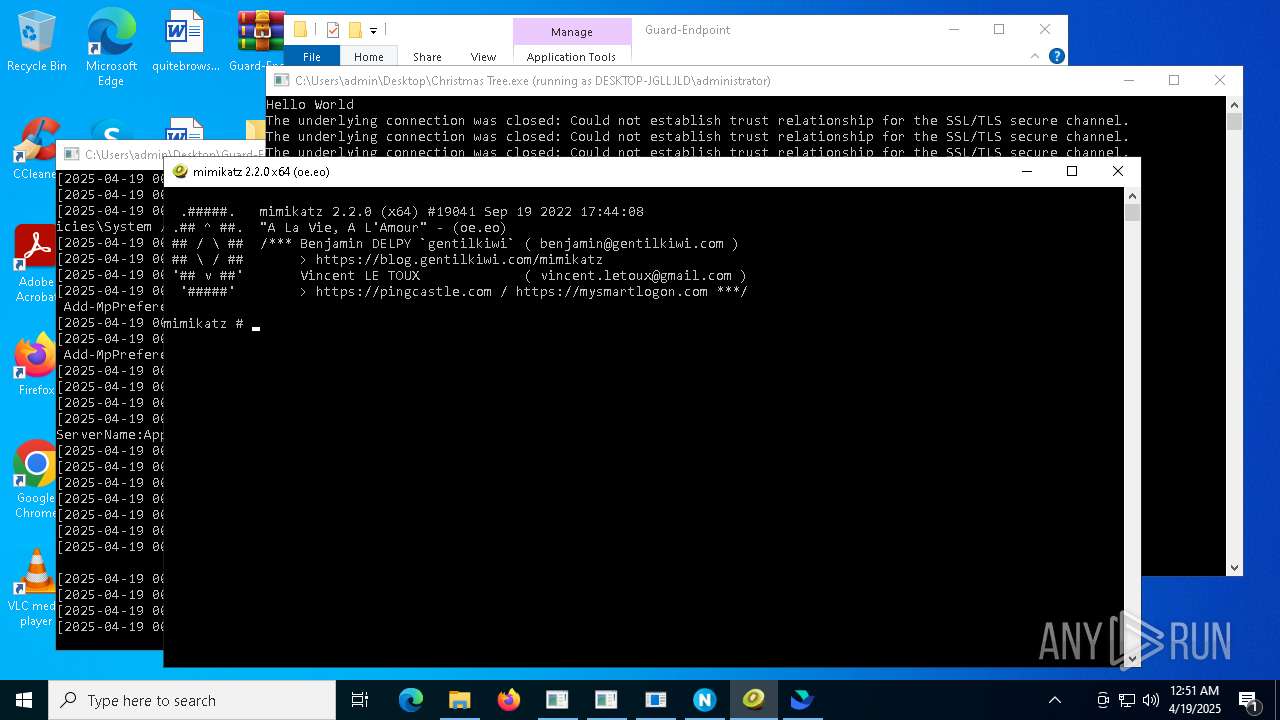
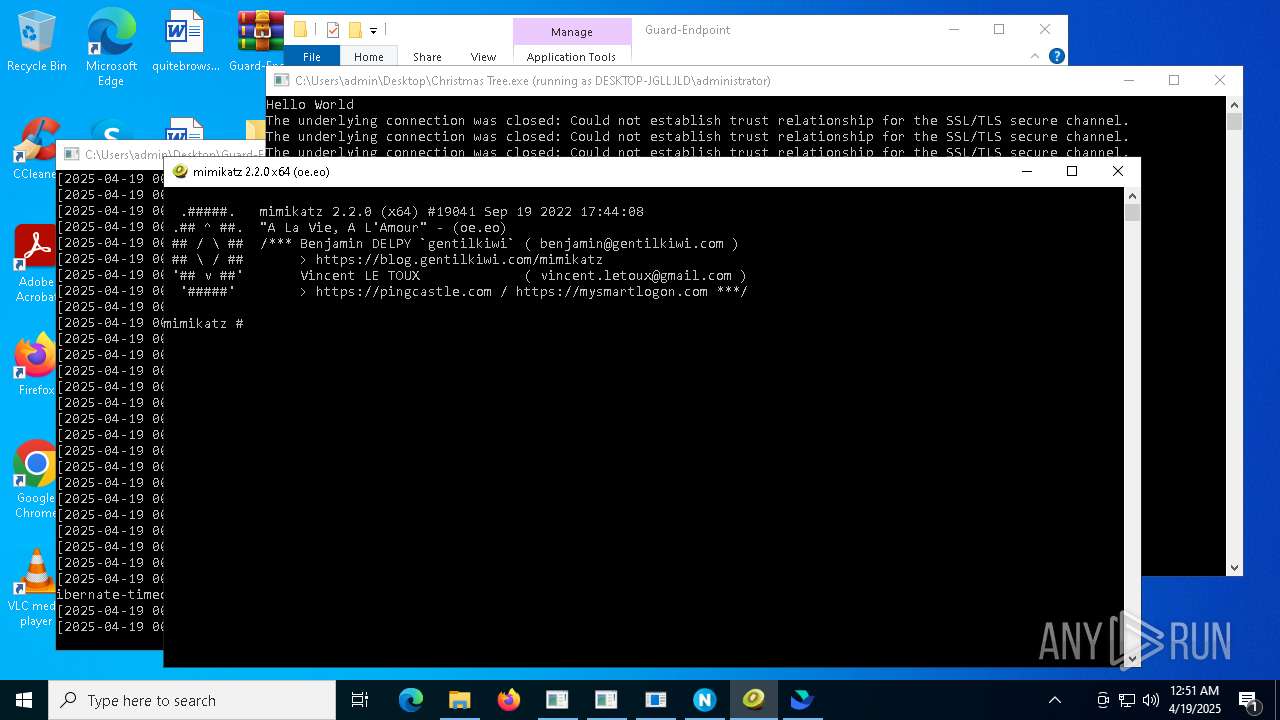
- mimikatz.exe (PID: 8404)
- csl.exe (PID: 7176)
- PsExec.exe (PID: 8736)
- c2new.exe (PID: 9080)
- taskhostw.exe (PID: 8040)
- updater.exe (PID: 9092)
- feishu.exe (PID: 7740)
Reads the computer name
- HeimdallGuard.exe (PID: 2772)
- HeimdallGuard.exe (PID: 1188)
- HeimdallGuard.exe (PID: 7052)
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- FoxmailSetup_7.2.25.375.exe (PID: 1748)
- brbotnet.exe (PID: 2908)
- CZXCVTD.exe (PID: 924)
- snd16061.exe (PID: 6476)
- XClient.exe (PID: 4628)
- Cloudy.exe (PID: 5216)
- s.exe (PID: 1096)
- CONVERTER.exe (PID: 4012)
- ULauncher.exe (PID: 5892)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
- thin.exe (PID: 4784)
- Quas13k.exe (PID: 668)
- explorer.exe (PID: 7440)
- asdasdasdasdasd.exe (PID: 7576)
- remcos_a.exe (PID: 7700)
- RuntimeBroker.exe (PID: 7264)
- ShellExperienceHost.exe (PID: 6560)
- csrss.exe (PID: 3796)
- bootstrapper.exe (PID: 8076)
- hkcmd.exe (PID: 732)
- RuntimeBroker.exe (PID: 8424)
- BruterV3.1.exe (PID: 8780)
- bootstrapper.exe (PID: 8872)
- 1.exe (PID: 8884)
- payload1.exe (PID: 9012)
- Device2.exe (PID: 8264)
- feishu.exe (PID: 7740)
- PsExec.exe (PID: 8736)
- mimikatz.exe (PID: 8404)
Disables trace logs
- HeimdallGuard.exe (PID: 2772)
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- XClient.exe (PID: 4628)
- Cloudy.exe (PID: 5216)
- s.exe (PID: 1096)
- ULauncher.exe (PID: 5892)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
Reads the software policy settings
- HeimdallGuard.exe (PID: 2772)
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- ULauncher.exe (PID: 5892)
- slui.exe (PID: 6876)
Checks proxy server information
- HeimdallGuard.exe (PID: 2772)
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- Cloudy.exe (PID: 5216)
- ULauncher.exe (PID: 5892)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
- csrss.exe (PID: 3796)
- hkcmd.exe (PID: 732)
- slui.exe (PID: 6876)
Reads Environment values
- Christmas Tree.exe (PID: 6324)
- S123.exe (PID: 1328)
- Cloudy.exe (PID: 5216)
- Quas13k.exe (PID: 668)
- XClient.exe (PID: 4628)
- s.exe (PID: 1096)
- ULauncher.exe (PID: 5892)
- explorer.exe (PID: 7440)
- asdasdasdasdasd.exe (PID: 7576)
- Host.exe (PID: 5736)
- Fix.exe (PID: 2560)
- RuntimeBroker.exe (PID: 7264)
- bootstrapper.exe (PID: 8076)
- RuntimeBroker.exe (PID: 8424)
- BruterV3.1.exe (PID: 8780)
- bootstrapper.exe (PID: 8872)
- Device2.exe (PID: 8264)
The sample compiled with chinese language support
- Christmas Tree.exe (PID: 6324)
Process checks computer location settings
- brbotnet.exe (PID: 2908)
Creates files in the program directory
- remcos_a.exe (PID: 7700)
- s.exe (PID: 1096)
- c2new.exe (PID: 9080)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
- ULauncher.exe (PID: 5892)
The sample compiled with english language support
- Christmas Tree.exe (PID: 6324)
- raw_cbot.exe (PID: 7432)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 8012)
- powershell.exe (PID: 8764)
- powershell.exe (PID: 8640)
- powershell.exe (PID: 8204)
- powershell.exe (PID: 8460)
- powershell.exe (PID: 9192)
- powershell.exe (PID: 8784)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 8732)
- powershell.exe (PID: 8168)
- powershell.exe (PID: 7468)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8012)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 8168)
- powershell.exe (PID: 7468)
- powershell.exe (PID: 8764)
- powershell.exe (PID: 8204)
- powershell.exe (PID: 8640)
- powershell.exe (PID: 8460)
- powershell.exe (PID: 9192)
- powershell.exe (PID: 8784)
- powershell.exe (PID: 5020)
- powershell.exe (PID: 8732)
The sample compiled with japanese language support
- updater.exe (PID: 9092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(1328) S123.exe
Version1.4.1
C2 (2)118.195.162.44:443
Sub_DirSubDir
Install_NameClient.exe
Mutex68d5e2b3-4339-4659-a181-0c8f9f98a553
StartupQuasar Client Startup
Tagtest2
LogDirLogs
SignatureItx+iqkvtAHU0ddWUZIBXYd/SsF44lLiuVg1y9tF8zG+oaV0ZDHZcgLmFdV/L0i3nytWBcfDlhsfvA49gHjtjane29uAbGgiSgWwJ08RoiSbs0Bb8AAPrJsSZPa5R+ru0D/B5MDH83s0wasVTOLhYqpZIhB5jIgxoWa6Rg/D6NpggEQB7ZiV44BLR686HNCq+HcTovLPnmdmndhogjg+Gn3KSlvctkBAB3k4R8Z9K26W9QfxgHMomQvI7VVIWQzvcndtrUEtKoKB3xht5B0/e0u4PvRrYkEW6wTgcbhQOIEB...
CertificateMIIE9DCCAtygAwIBAgIQAJ3N+Lg26iiv+teE8eSluTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDQxNjA5NDIwOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlKRXqa4ec5vGBeQC55RFDLVLGjIX7bzKxlR1/NiZ088j9UE85fqpmuewJsRJwH40vpDJ6VqG...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 16:32:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
269
Monitored processes
128
Malicious processes
21
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\System32\schtasks.exe /create /f /ru "System" /tn "GoogleUpdateTaskMachineQC" /xml "C:\Users\ADMINI~1\AppData\Local\Temp\flaevwjwirpw.xml" | C:\Windows\System32\schtasks.exe | explorer.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Windows\System32\a\Quas13k.exe" | C:\Windows\System32\a\Quas13k.exe | Christmas Tree.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Description: Quasar Client Exit code: 3 Version: 1.4.1 Modules
| |||||||||||||||
| 732 | "C:\Windows\System32\a\hkcmd.exe" | C:\Windows\System32\a\hkcmd.exe | Christmas Tree.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 872 | "schtasks" /create /tn "MicrosoftQuasUpdate" /sc ONLOGON /tr "C:\WINDOWS\system32\explorer\explorer.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Quas13k.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | "C:\Windows\System32\a\CZXCVTD.exe" | C:\Windows\System32\a\CZXCVTD.exe | — | Christmas Tree.exe | |||||||||||
User: Administrator Integrity Level: HIGH Description: CZXCVTD Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1004 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionPath 'C:\Windows\System32\a\XClient.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | XClient.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1004 | powercfg /x -hibernate-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Windows\System32\a\s.exe" | C:\Windows\System32\a\s.exe | Christmas Tree.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Description: Version: 1.0.0.0 Modules
| |||||||||||||||
| 1188 | "C:\Users\admin\Desktop\Guard-Endpoint\HeimdallGuard.exe" | C:\Users\admin\Desktop\Guard-Endpoint\HeimdallGuard.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: HeimdallGuard Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1328 | "C:\Windows\System32\a\S123.exe" | C:\Windows\System32\a\S123.exe | Christmas Tree.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Description: Quasar Client Version: 1.4.1 Modules
Quasar(PID) Process(1328) S123.exe Version1.4.1 C2 (2)118.195.162.44:443 Sub_DirSubDir Install_NameClient.exe Mutex68d5e2b3-4339-4659-a181-0c8f9f98a553 StartupQuasar Client Startup Tagtest2 LogDirLogs SignatureItx+iqkvtAHU0ddWUZIBXYd/SsF44lLiuVg1y9tF8zG+oaV0ZDHZcgLmFdV/L0i3nytWBcfDlhsfvA49gHjtjane29uAbGgiSgWwJ08RoiSbs0Bb8AAPrJsSZPa5R+ru0D/B5MDH83s0wasVTOLhYqpZIhB5jIgxoWa6Rg/D6NpggEQB7ZiV44BLR686HNCq+HcTovLPnmdmndhogjg+Gn3KSlvctkBAB3k4R8Z9K26W9QfxgHMomQvI7VVIWQzvcndtrUEtKoKB3xht5B0/e0u4PvRrYkEW6wTgcbhQOIEB... CertificateMIIE9DCCAtygAwIBAgIQAJ3N+Lg26iiv+teE8eSluTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDQxNjA5NDIwOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlKRXqa4ec5vGBeQC55RFDLVLGjIX7bzKxlR1/NiZ088j9UE85fqpmuewJsRJwH40vpDJ6VqG... | |||||||||||||||
Total events
133 765
Read events
133 191
Write events
572
Delete events
2
Modification events
| (PID) Process: | (5544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2772) HeimdallGuard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\HeimdallGuard_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2772) HeimdallGuard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\HeimdallGuard_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2772) HeimdallGuard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\HeimdallGuard_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2772) HeimdallGuard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\HeimdallGuard_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2772) HeimdallGuard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\HeimdallGuard_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2772) HeimdallGuard.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\HeimdallGuard_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
137
Suspicious files
66
Text files
58
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\FoxmailSetup_7.2.25.375.exe | — | |
MD5:— | SHA256:— | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\csrss.exe | executable | |
MD5:BEDA5984A652D9931902980A4D7C258B | SHA256:F919AD3A0B960E8665024B04DE0D5E9B9B8BCFD50276CB6AD03AC3A5FF8F1A48 | |||
| 5544 | WinRAR.exe | C:\Users\admin\Desktop\Guard-Endpoint\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\S123.exe | executable | |
MD5:233A781D28BD3B3A86178C48AF135297 | SHA256:8C4EDF15B2E0BFAAF67D12A3E17E0D6D314EA1DF16965C8C1D7D2B83F3BC1C36 | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\s.exe | executable | |
MD5:9315B5F908CE50B71309CA55161662FE | SHA256:459AD6ACB7E74E8A521F696417734CCC726EC7864B7ED501EC0BEB20B8234141 | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\ULauncher.exe | executable | |
MD5:1668D6A350C1FB747238D593F9E3257C | SHA256:A573C684BDC1F9B0BCF67A5933E72CC820BBF4CE5AD2AFCF10957D2C18312190 | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\Cloudy.exe | executable | |
MD5:DF8B7081B4E73EC77C418C69F9B6E67B | SHA256:F7E2D59D77B6C034F80A08DCCA6C863C443F0D74B2073DD3925C4E959E5150B6 | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\Fix.exe | executable | |
MD5:D2CF70A5C96400F161F3712647D38FA8 | SHA256:89705482C72962237A2FA30D85F7C037E48C0B0D326C064465E63C86BD24E40D | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\hkcmd.exe | executable | |
MD5:05EF4CA659965C1D3FAA58077B0F9943 | SHA256:00B229DE51C409D79B0084465543C9197F797D4A835290EBF72CBCE75CFB2044 | |||
| 6324 | Christmas Tree.exe | C:\Windows\System32\a\XClient.exe | executable | |
MD5:2113213C070E570FBD35F235FC9D333F | SHA256:E9D9C5D88C74839C7FCC4419C101139ACC438542EDCE4CB490D6CA81C0A1C719 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
1 244
DNS requests
70
Threats
182
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6488 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6488 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6324 | Christmas Tree.exe | GET | 200 | 118.195.162.44:80 | http://118.195.162.44/S123.exe | unknown | — | — | unknown |
6324 | Christmas Tree.exe | GET | 200 | 176.65.134.79:80 | http://176.65.134.79/HOST/FoxmailSetup_7.2.25.375.exe | unknown | — | — | malicious |
6324 | Christmas Tree.exe | GET | 200 | 176.65.134.79:80 | http://176.65.134.79/HOST/CZXCVTD.exe | unknown | — | — | malicious |
6324 | Christmas Tree.exe | GET | — | 196.251.71.139:80 | http://196.251.71.139/vnc/nvnc.exe | unknown | — | — | unknown |
6324 | Christmas Tree.exe | GET | 200 | 45.136.15.39:80 | http://45.136.15.39/02.08.2022.exe | unknown | — | — | malicious |
6324 | Christmas Tree.exe | GET | 200 | 176.65.134.79:80 | http://176.65.134.79/hosting/CONVERTER.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2772 | HeimdallGuard.exe | 172.67.194.159:443 | countervector.pro | CLOUDFLARENET | US | unknown |
6488 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
countervector.pro |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6324 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6324 | Christmas Tree.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6324 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6324 | Christmas Tree.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6324 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6324 | Christmas Tree.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6324 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6324 | Christmas Tree.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1328 | S123.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
1328 | S123.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |