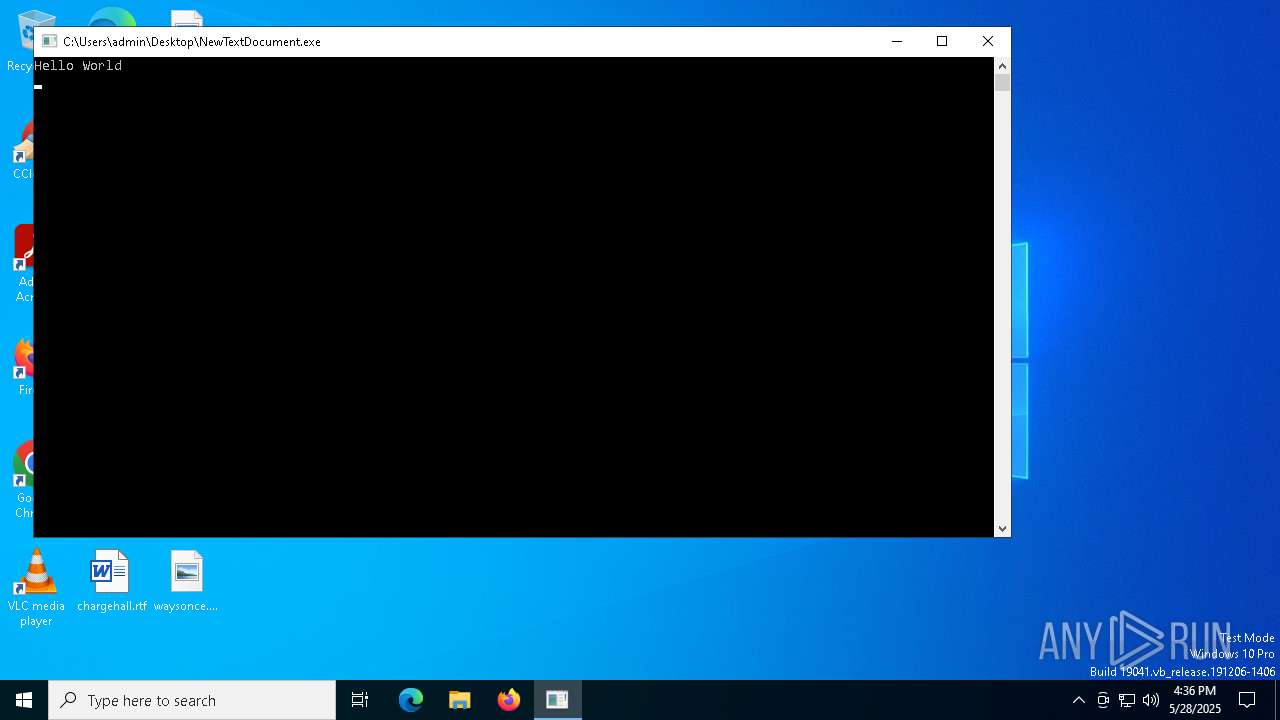
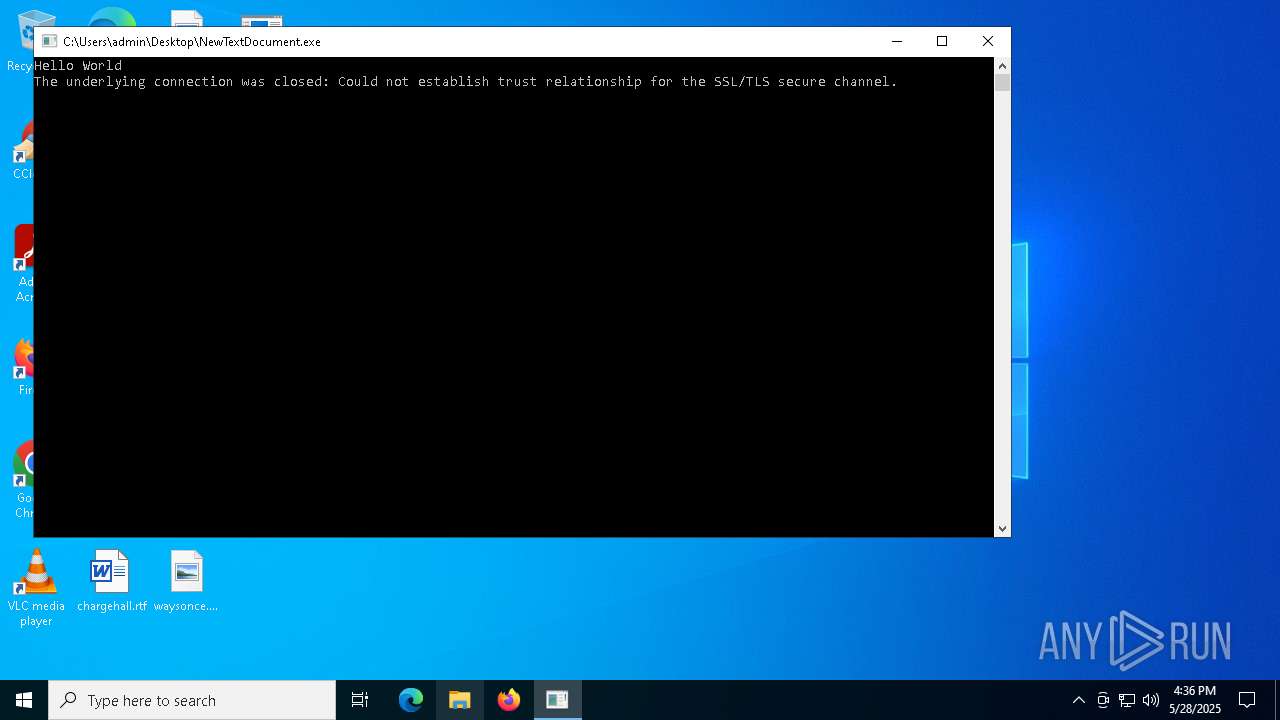
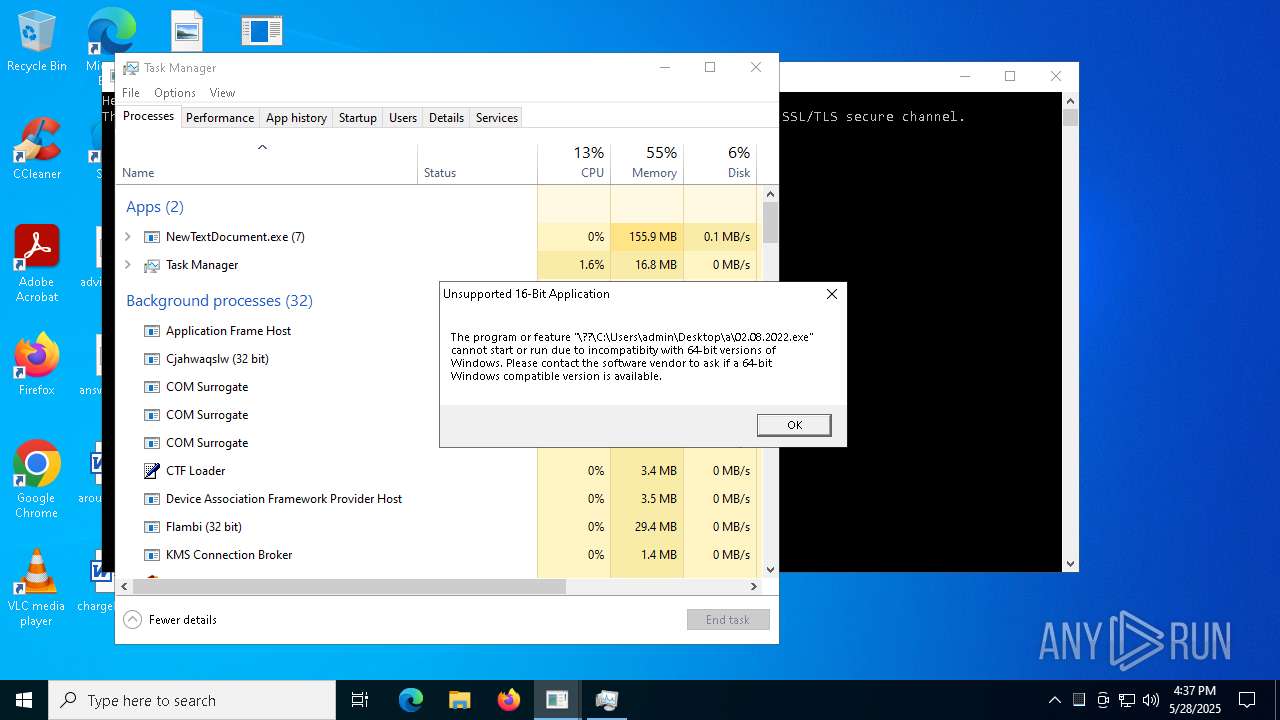
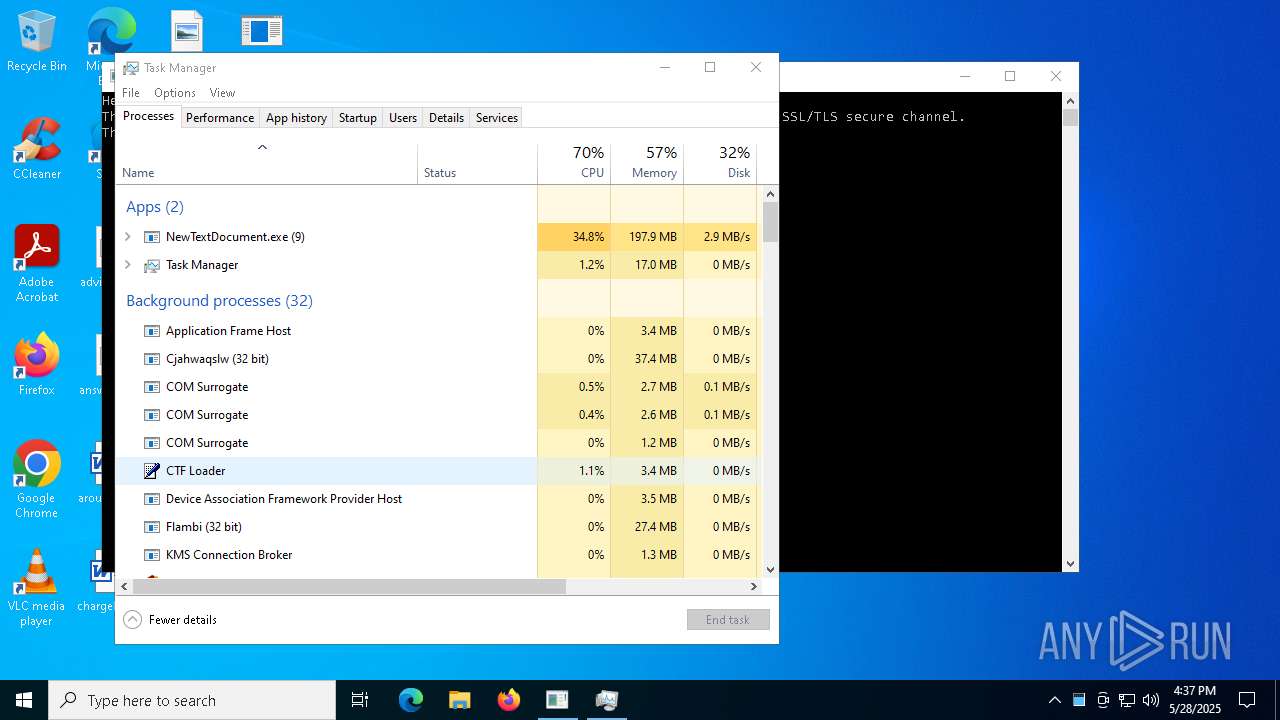
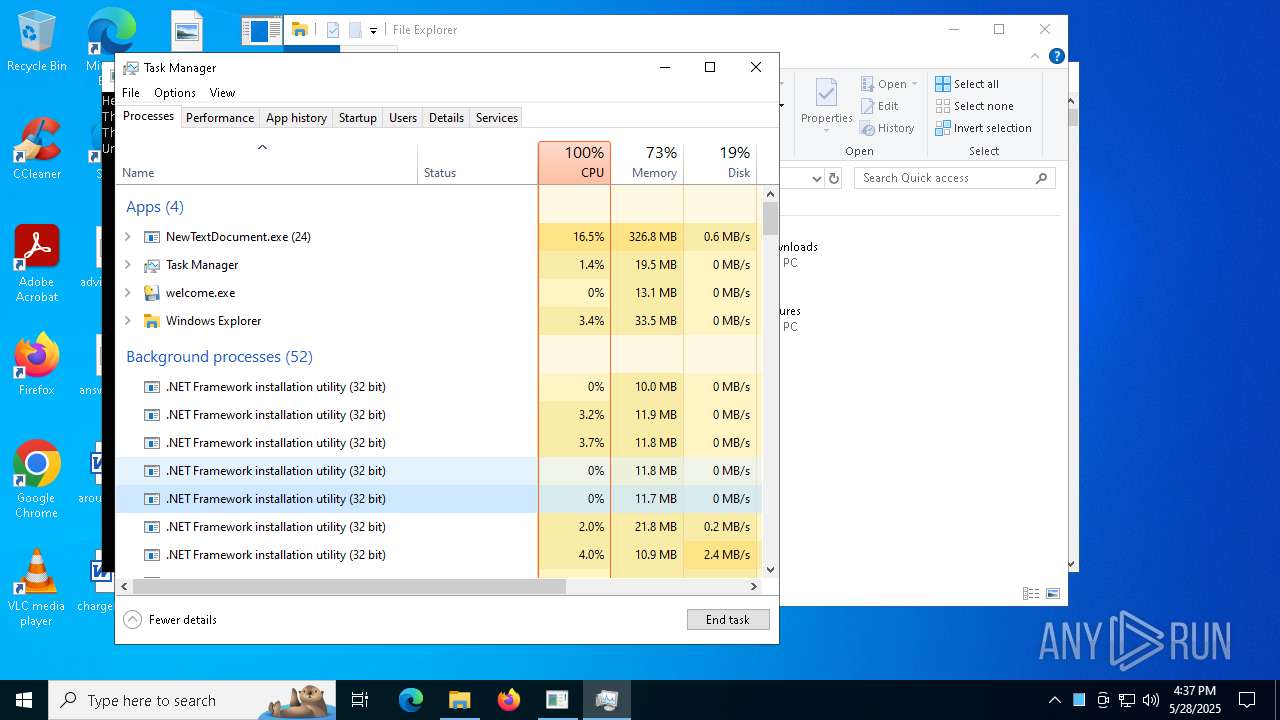
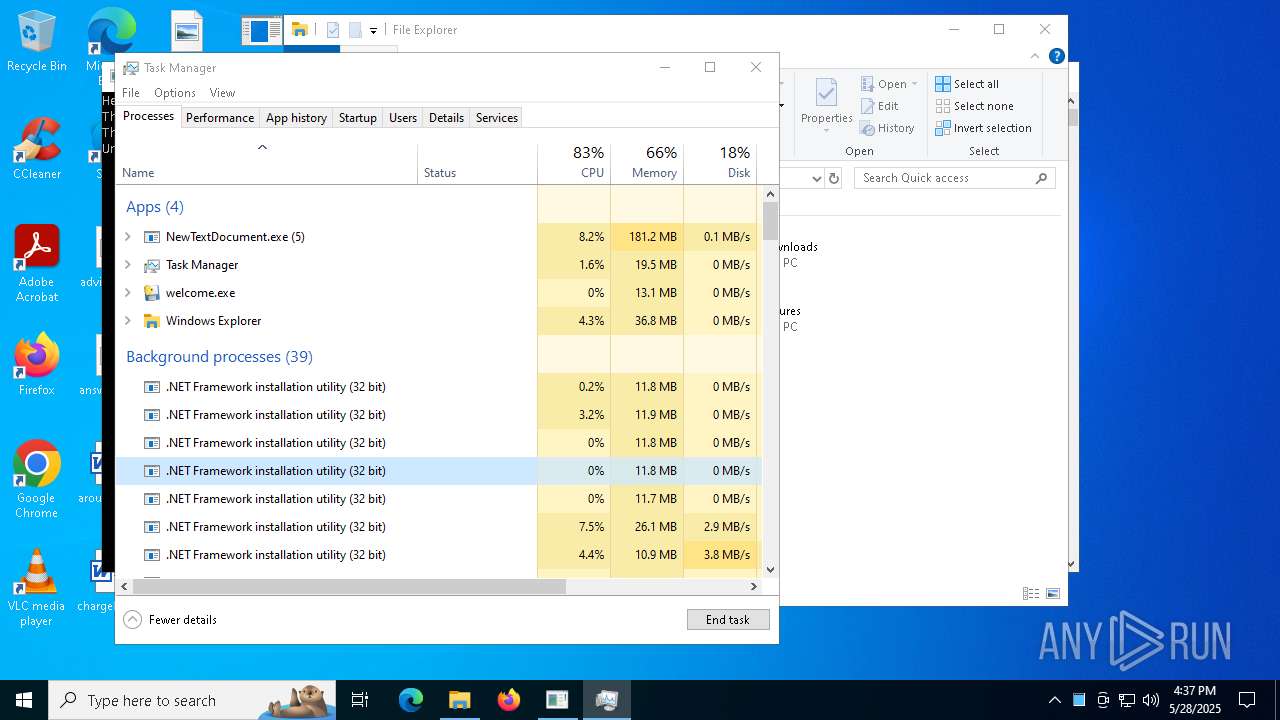
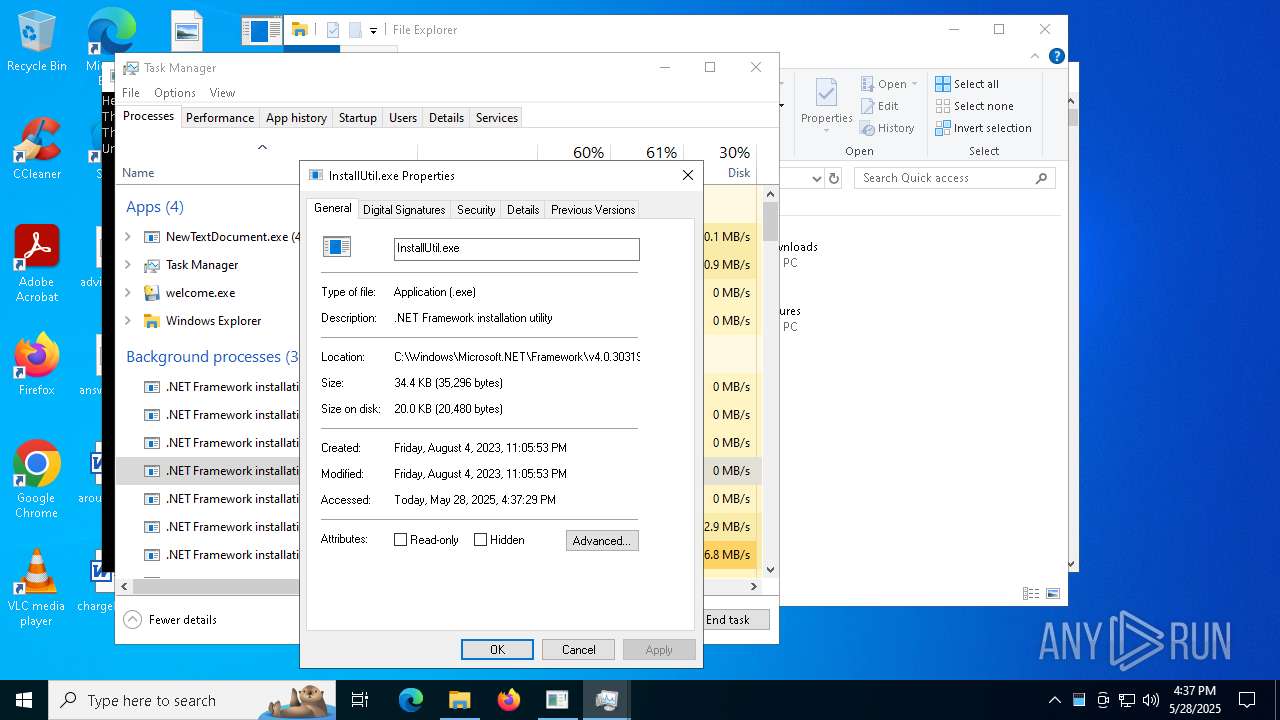
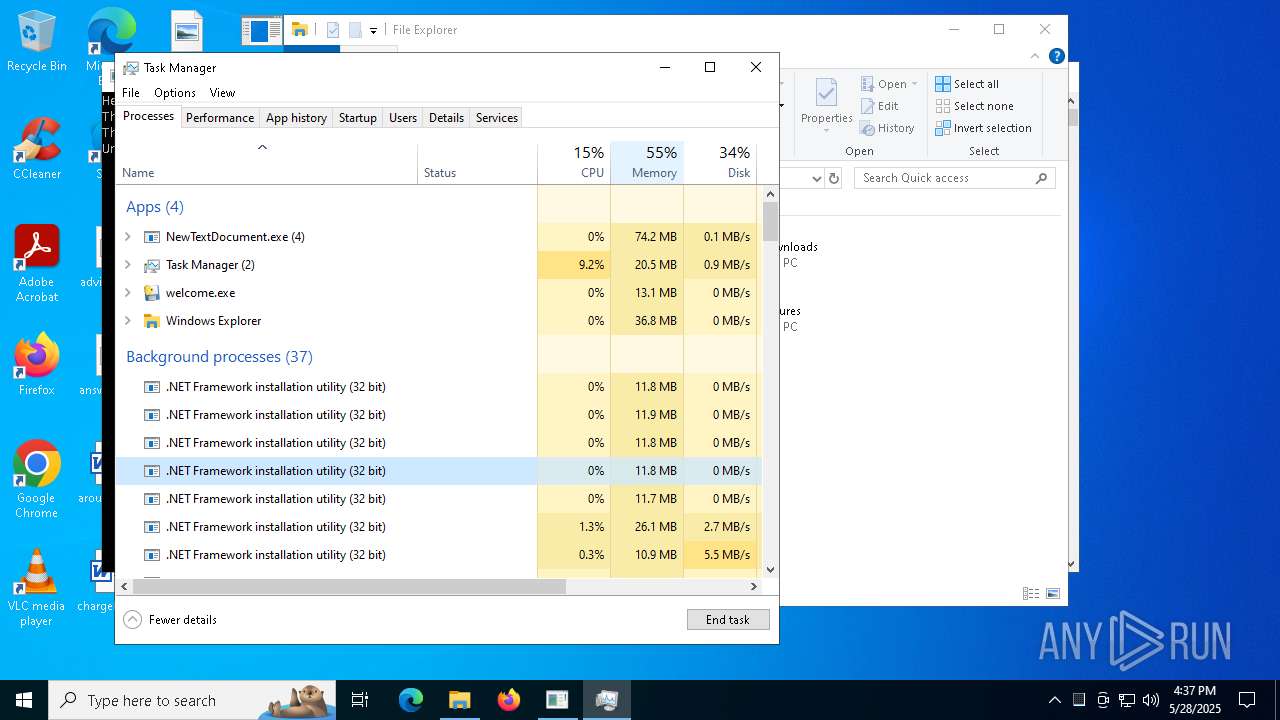
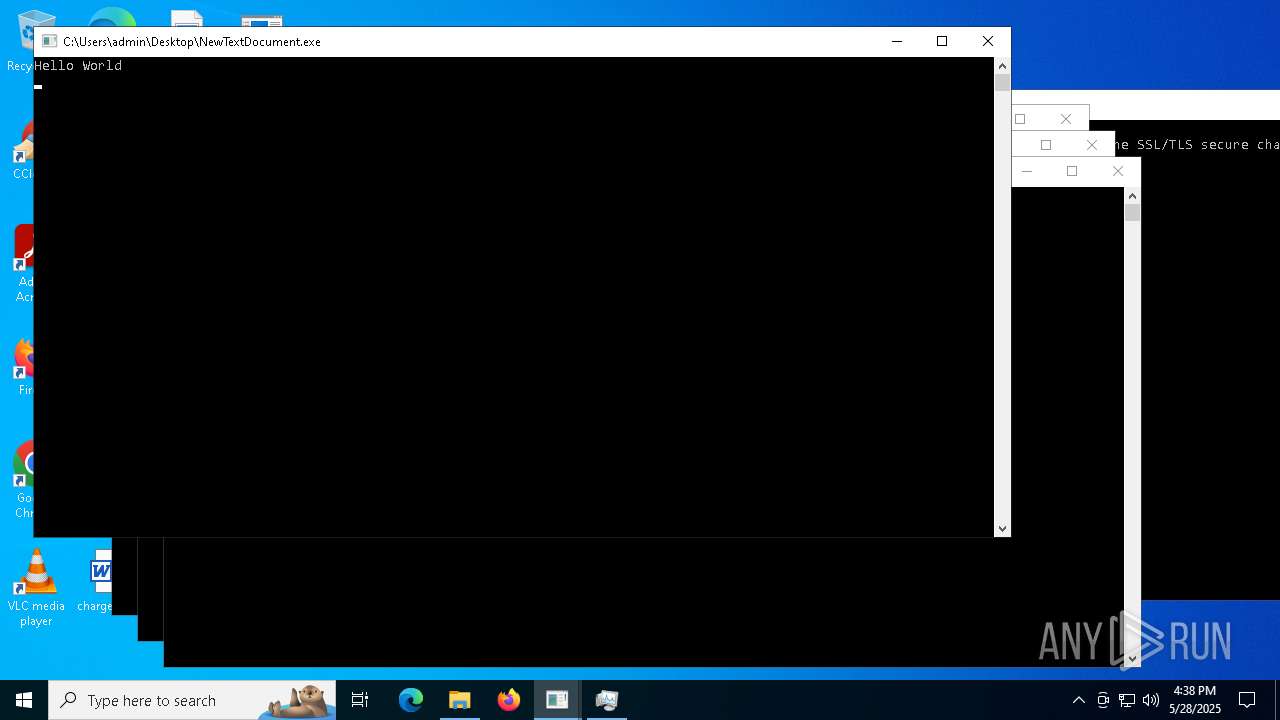
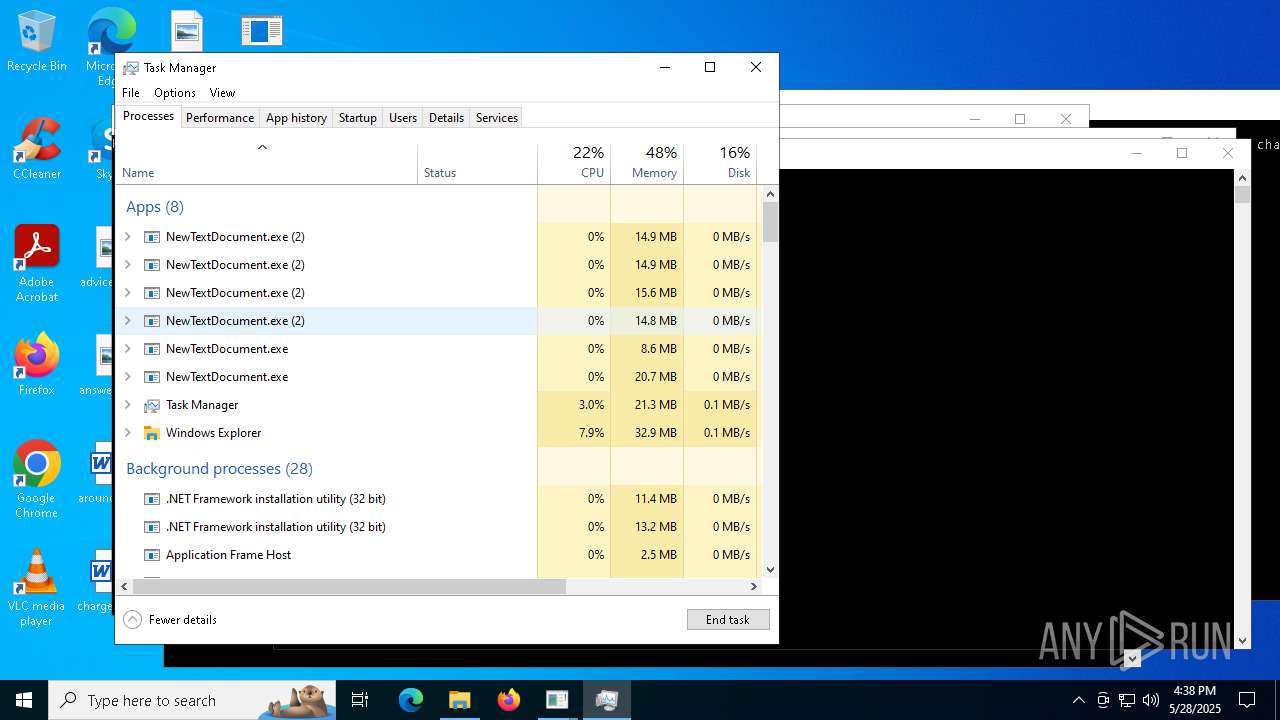
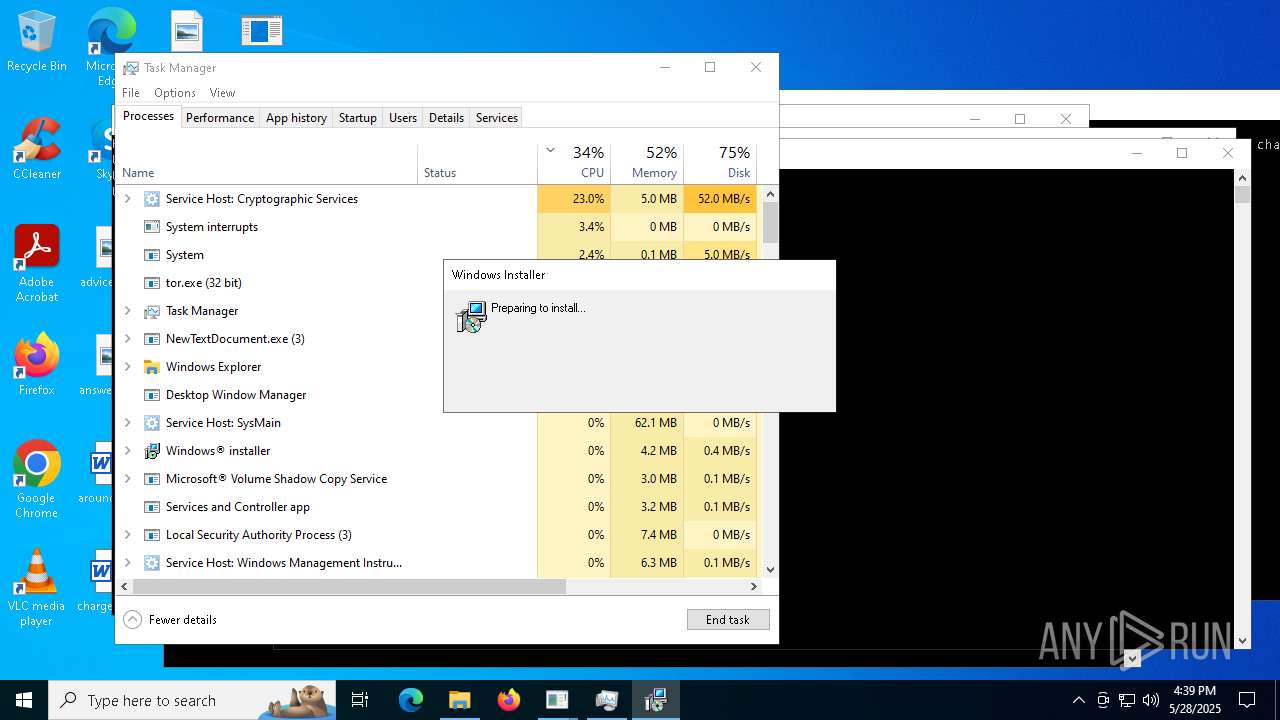
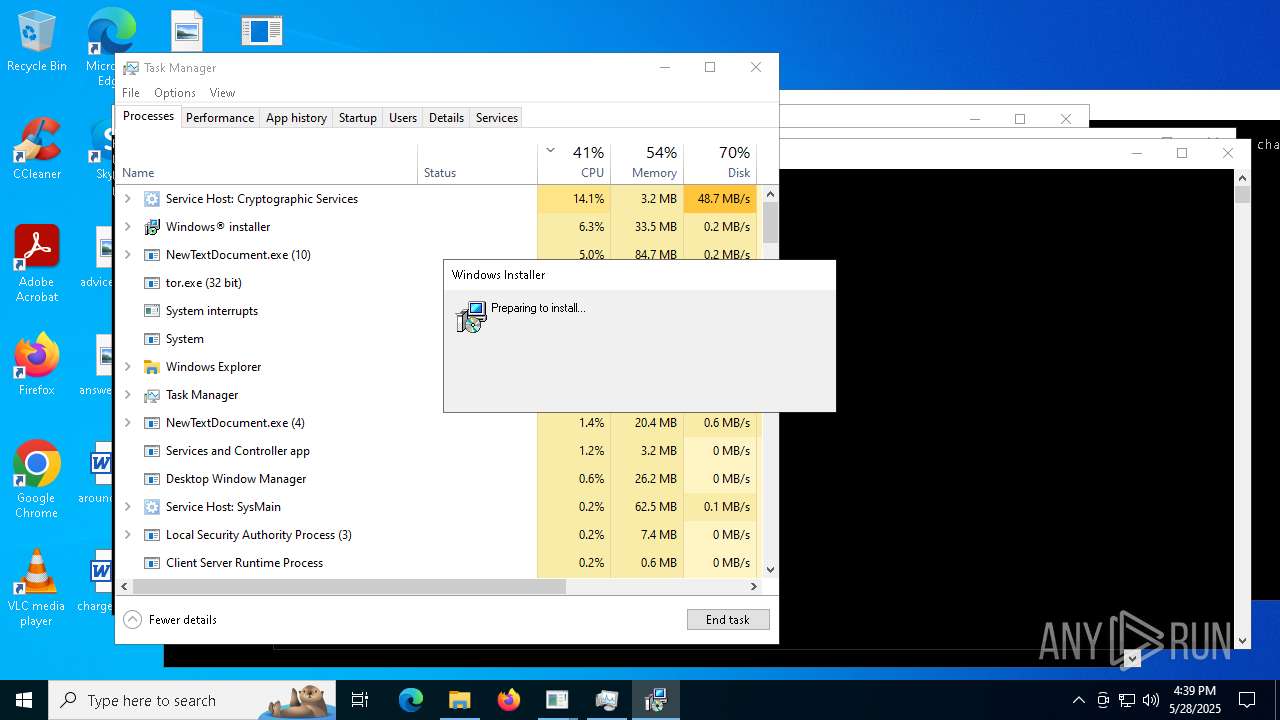
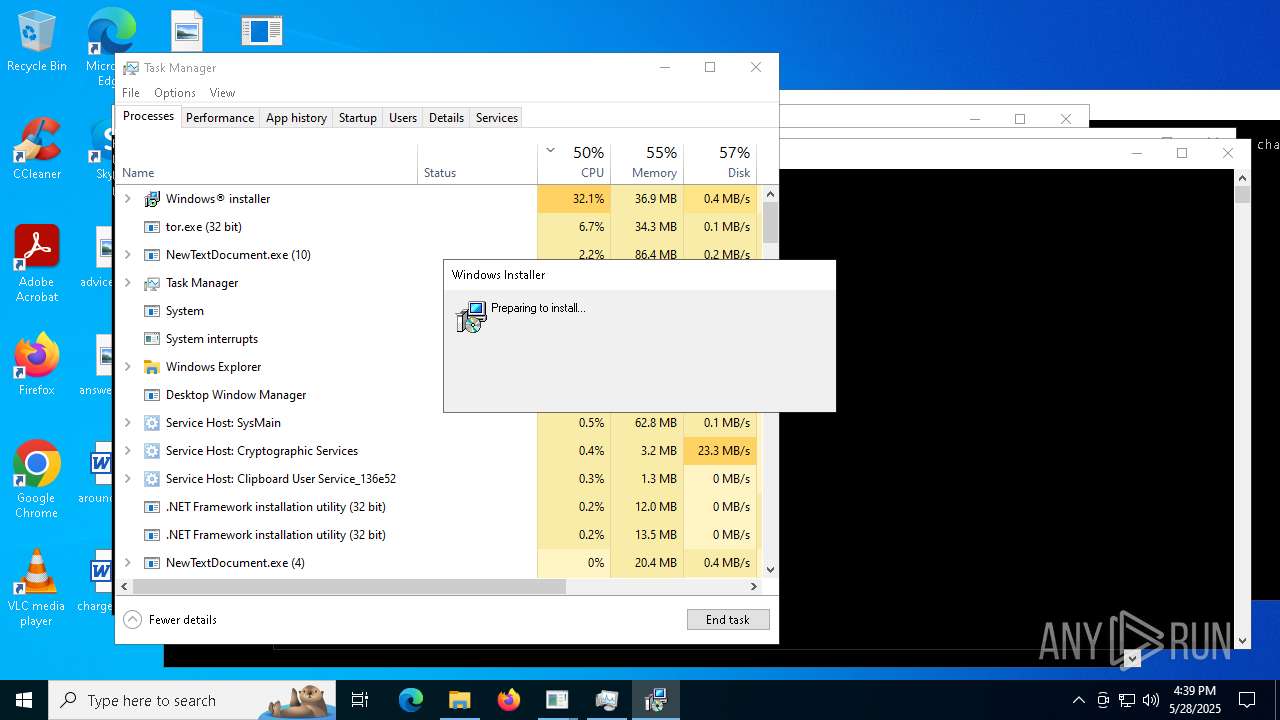
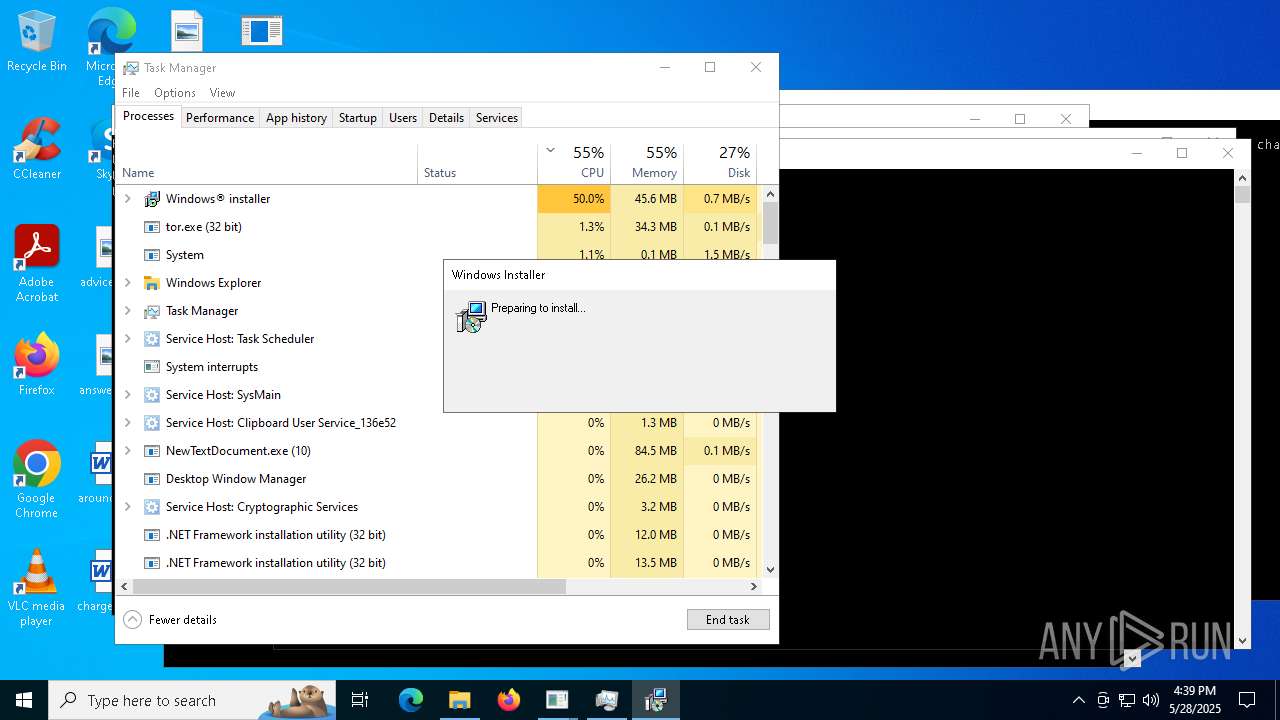
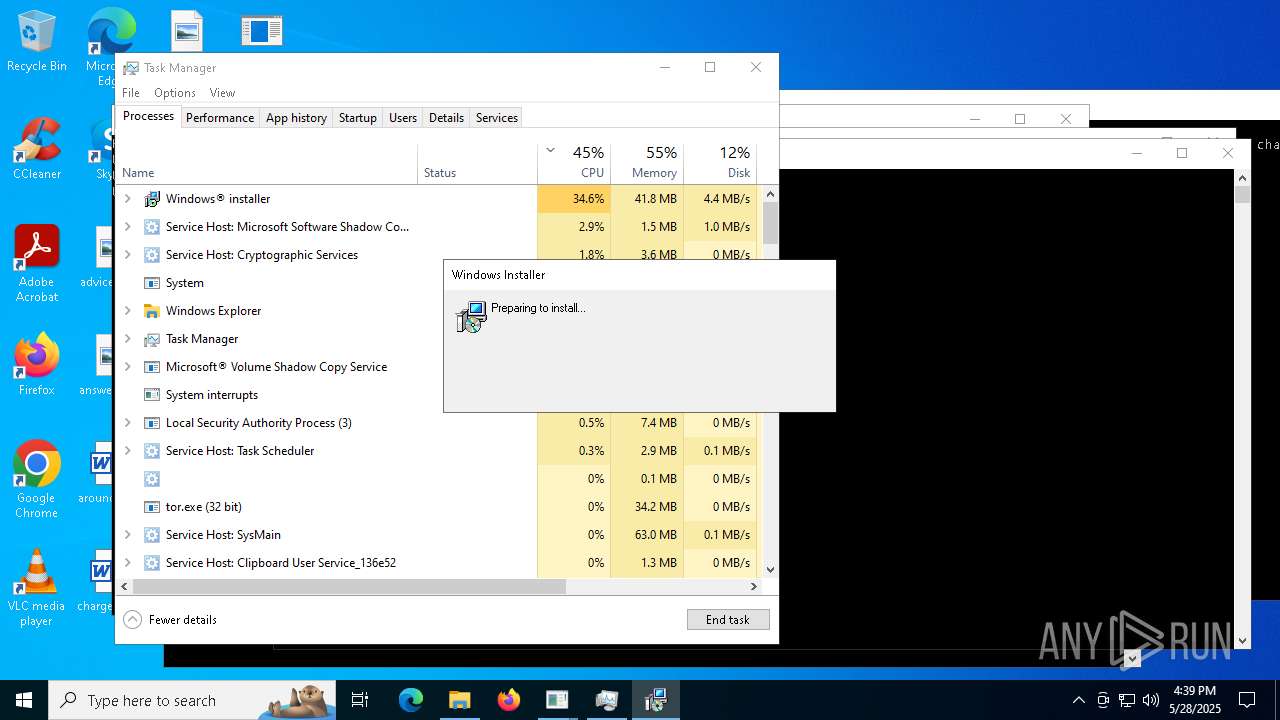
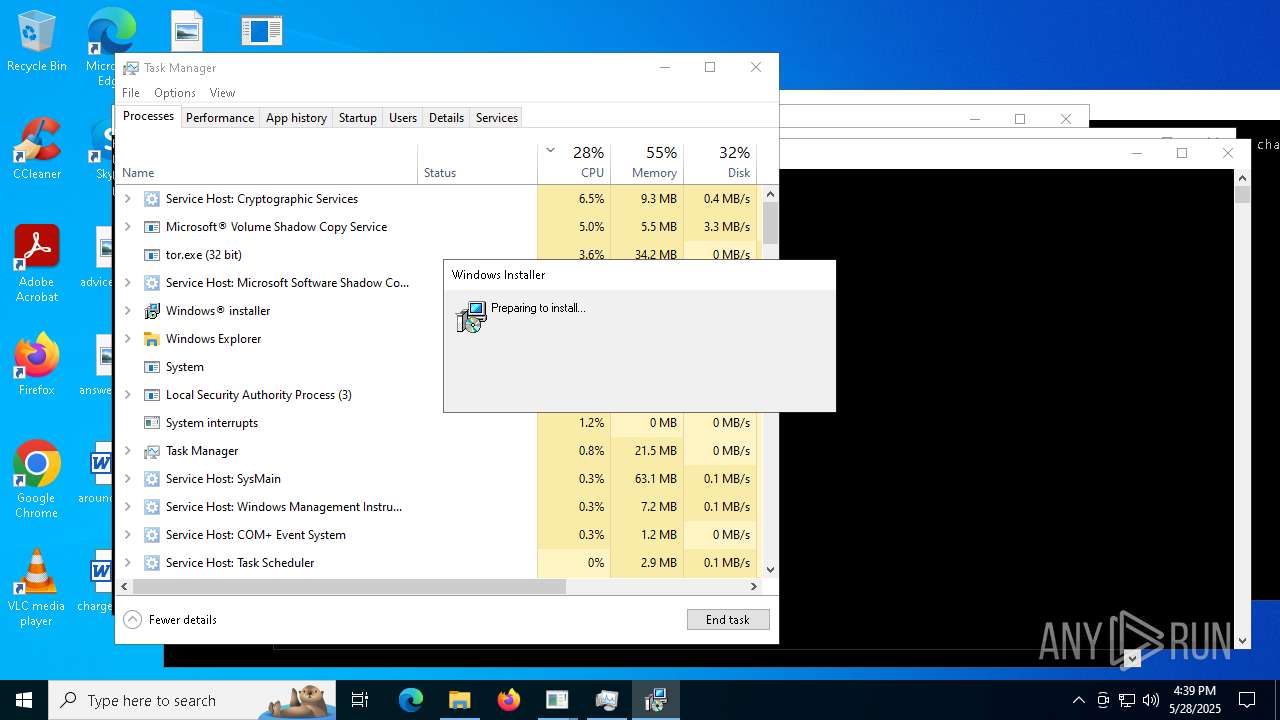
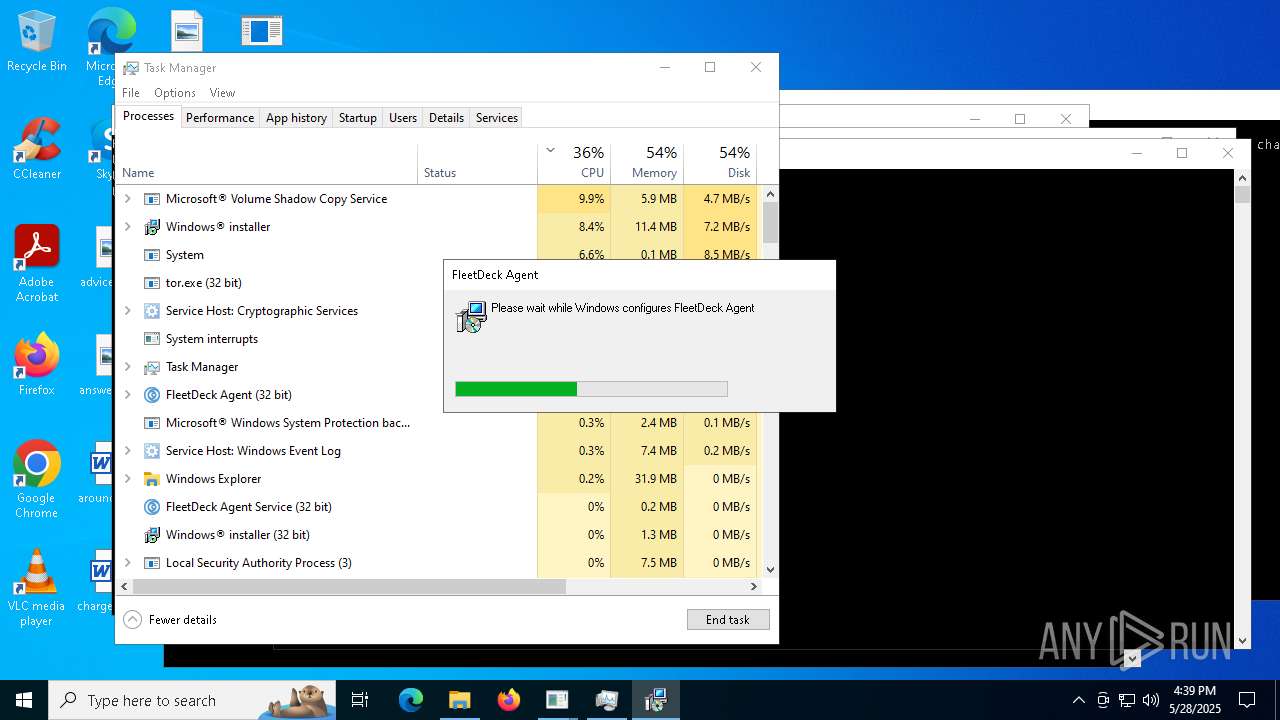
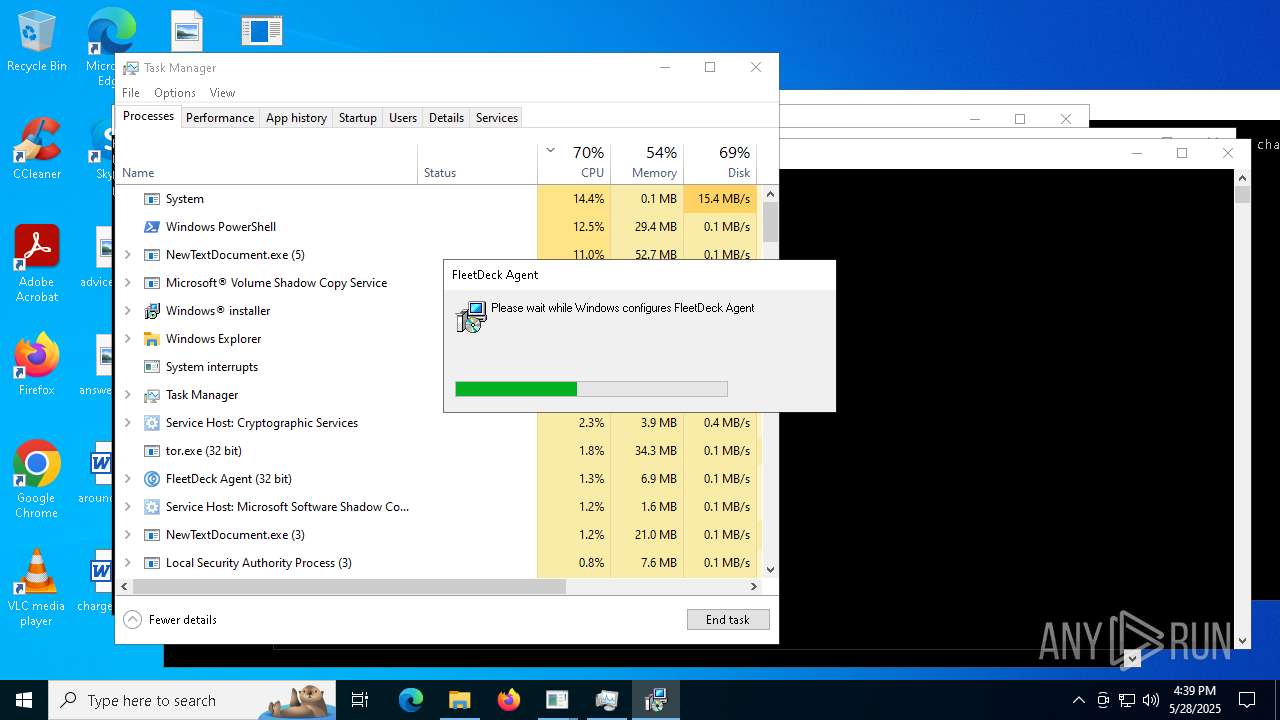
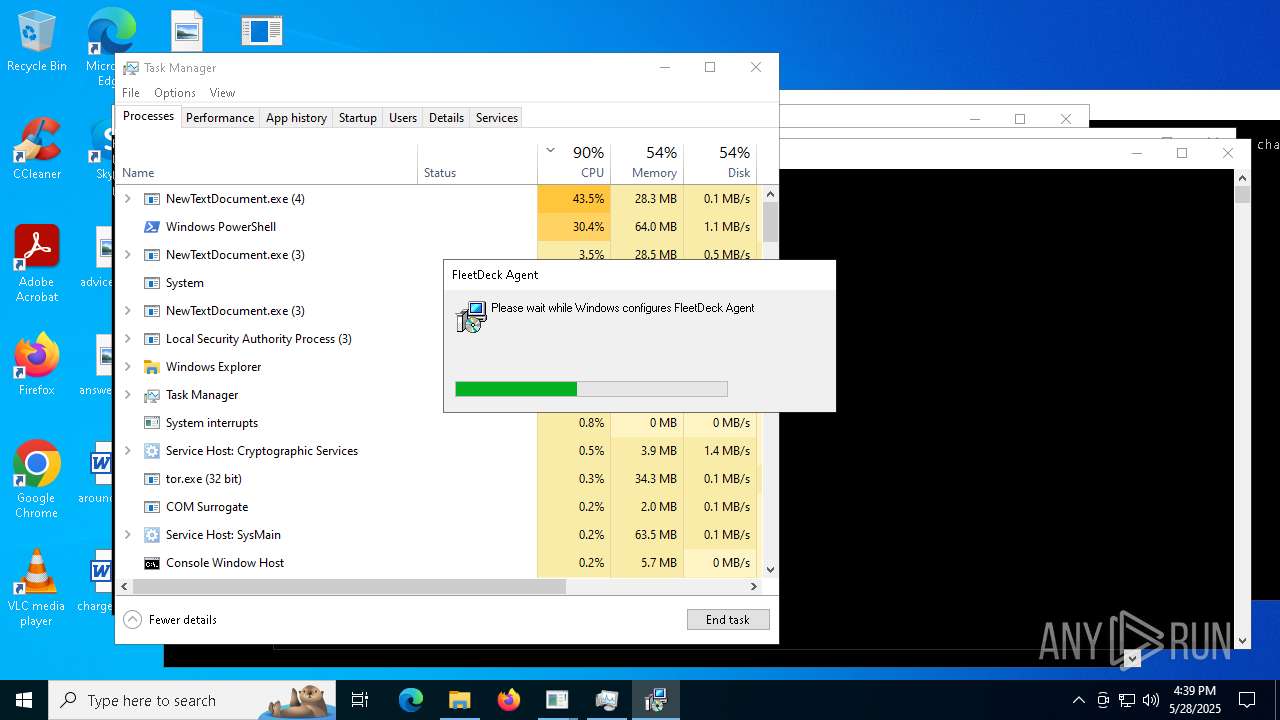
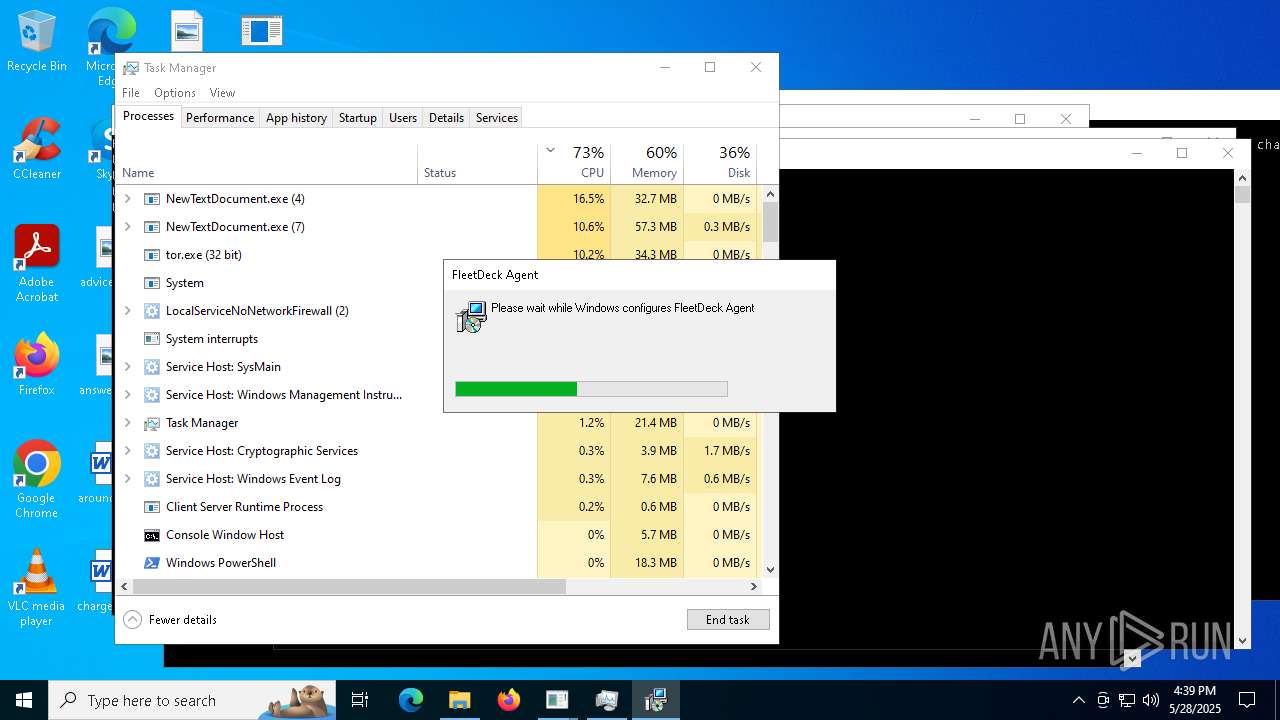
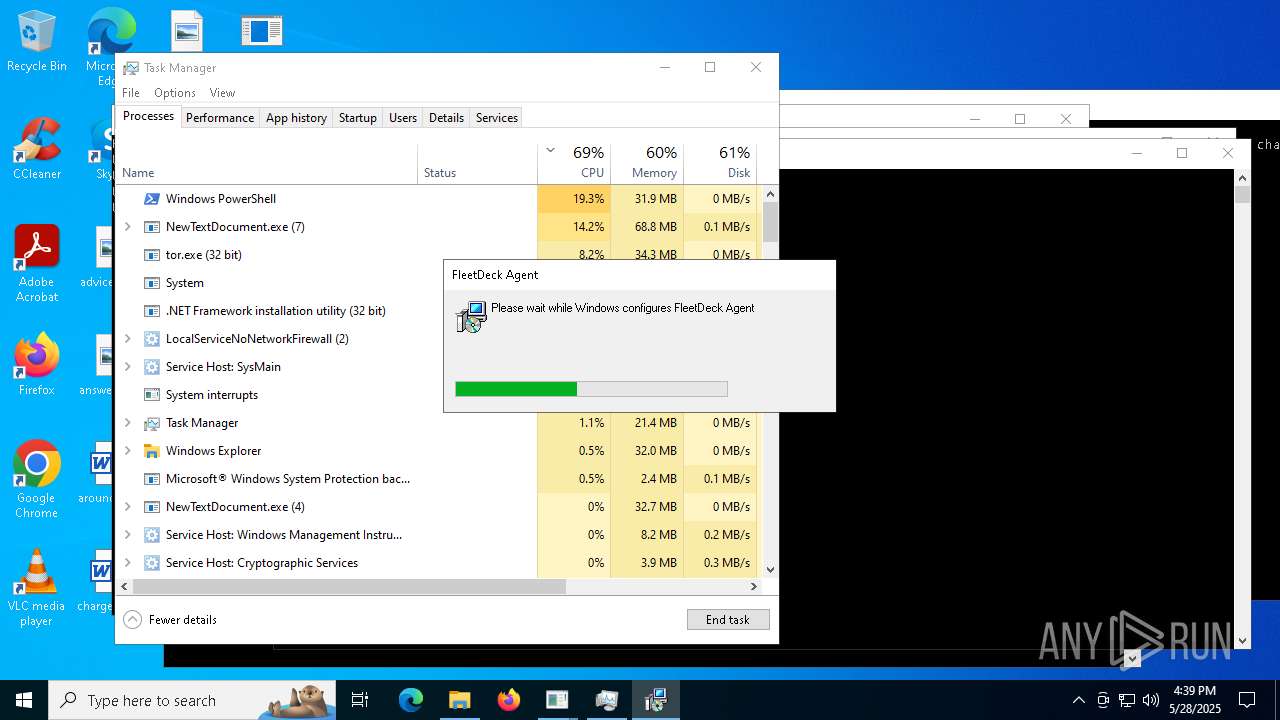
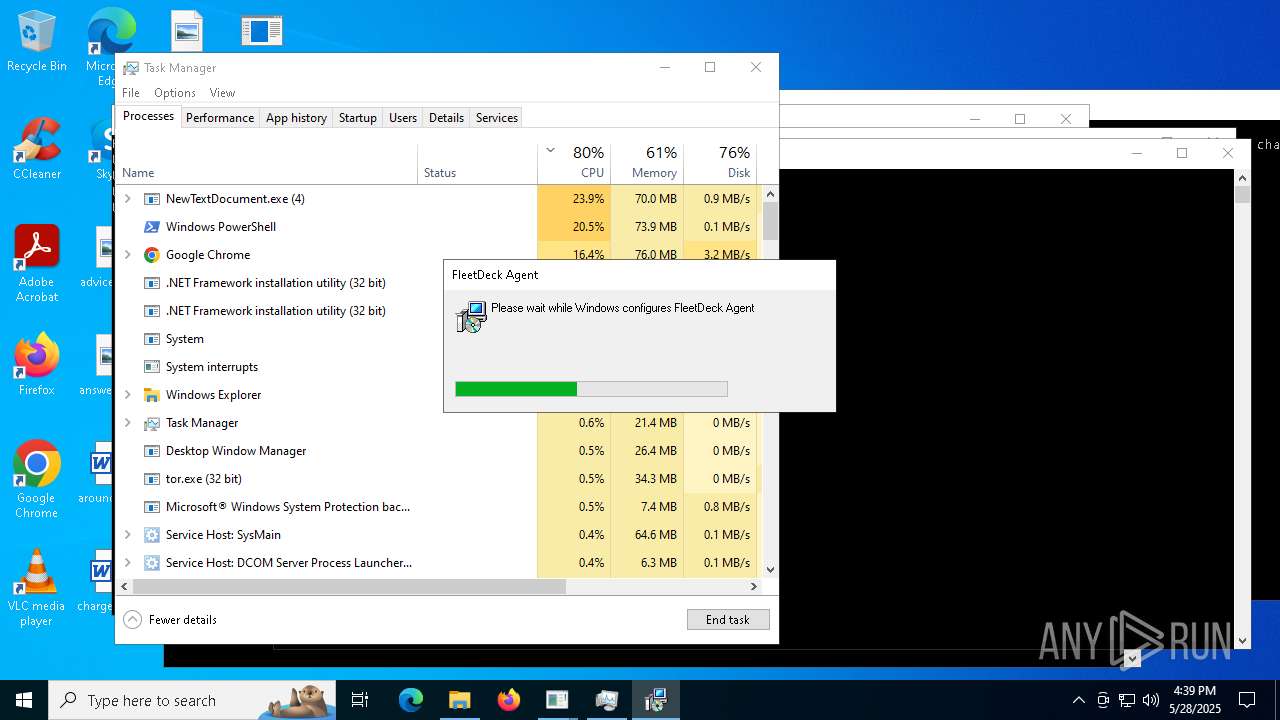
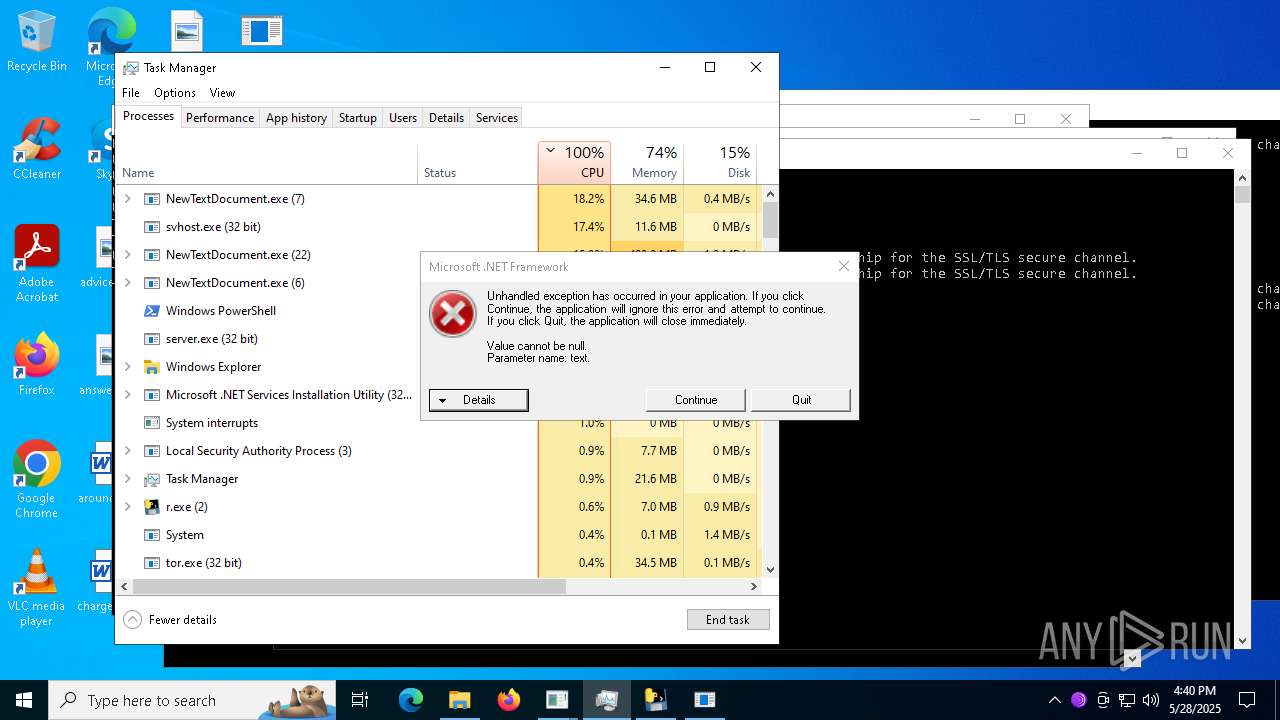
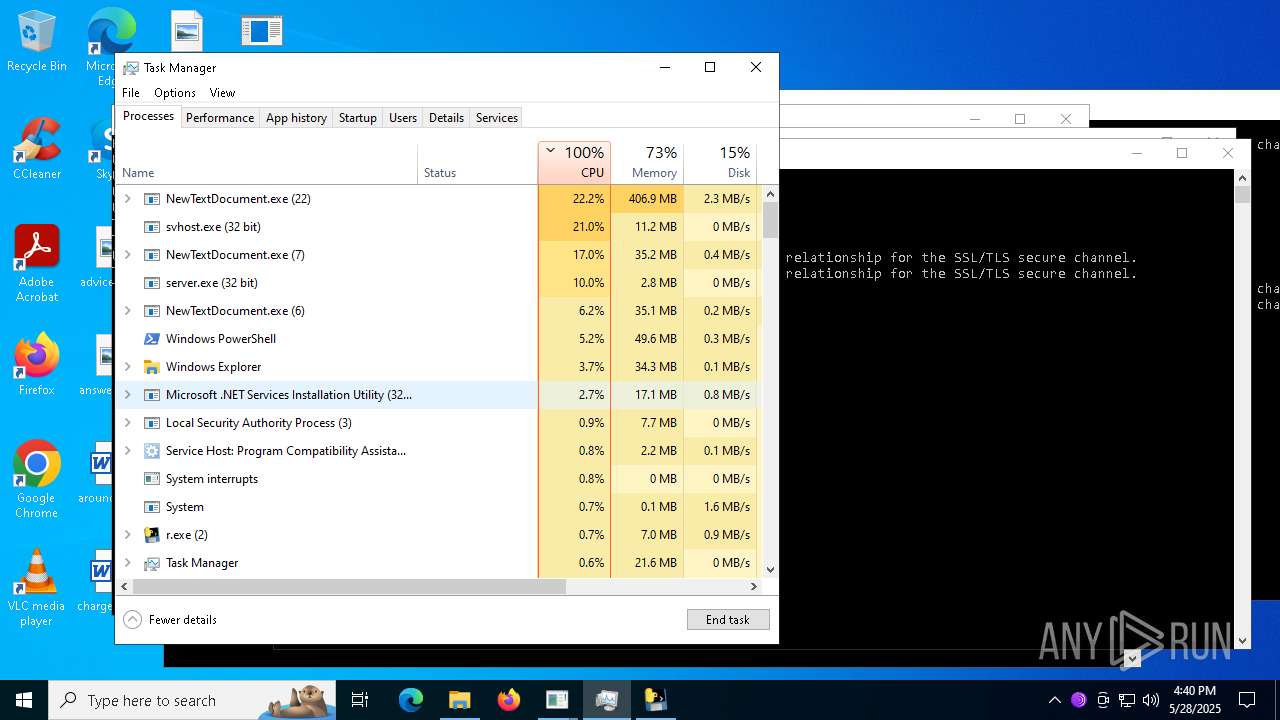
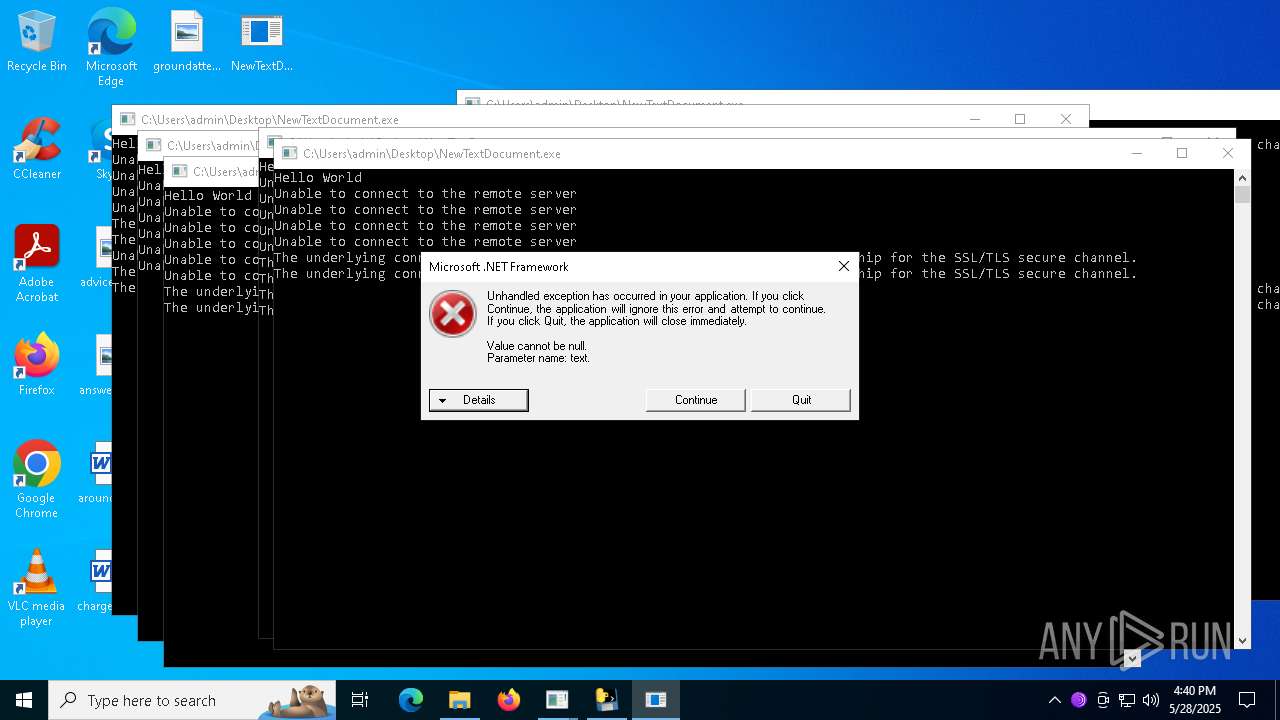
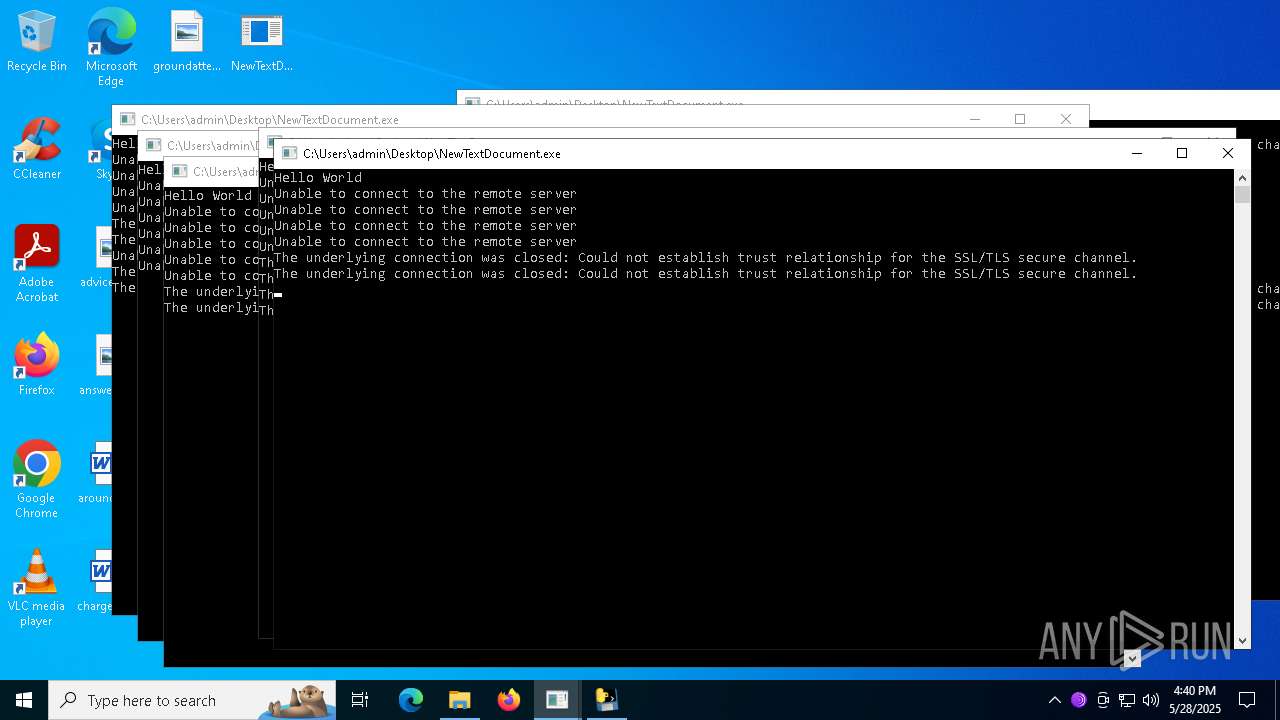
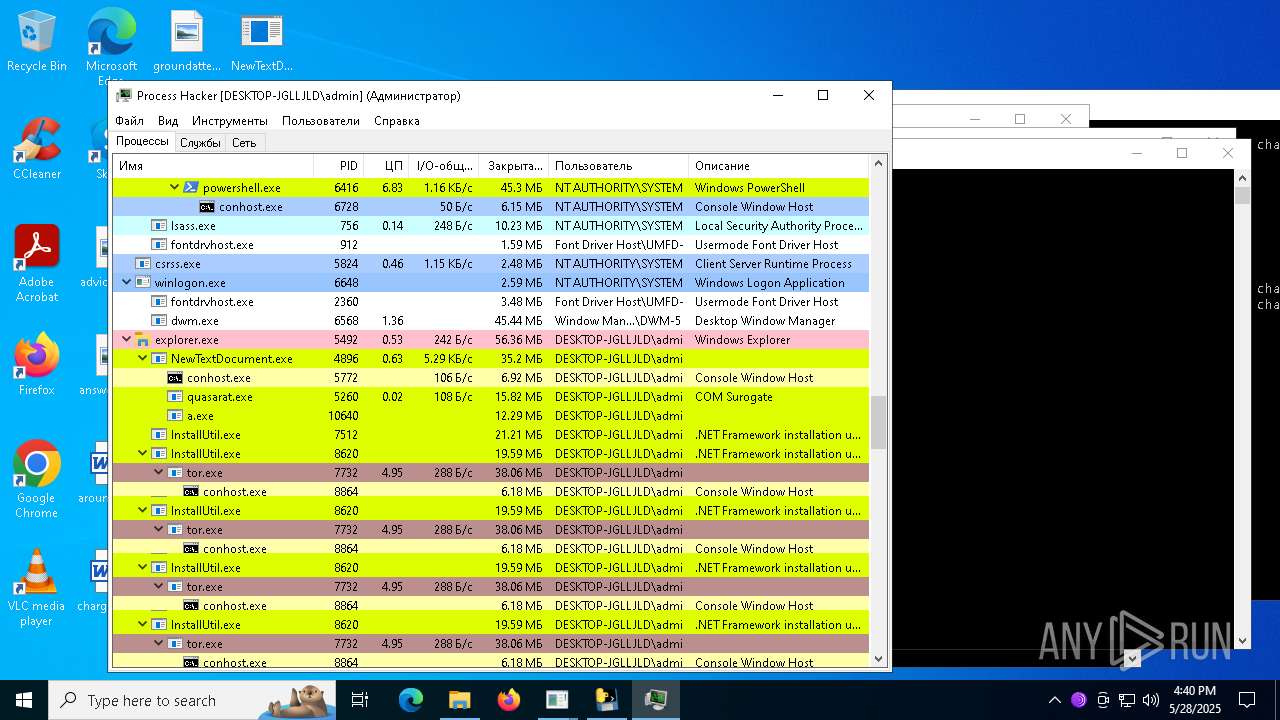
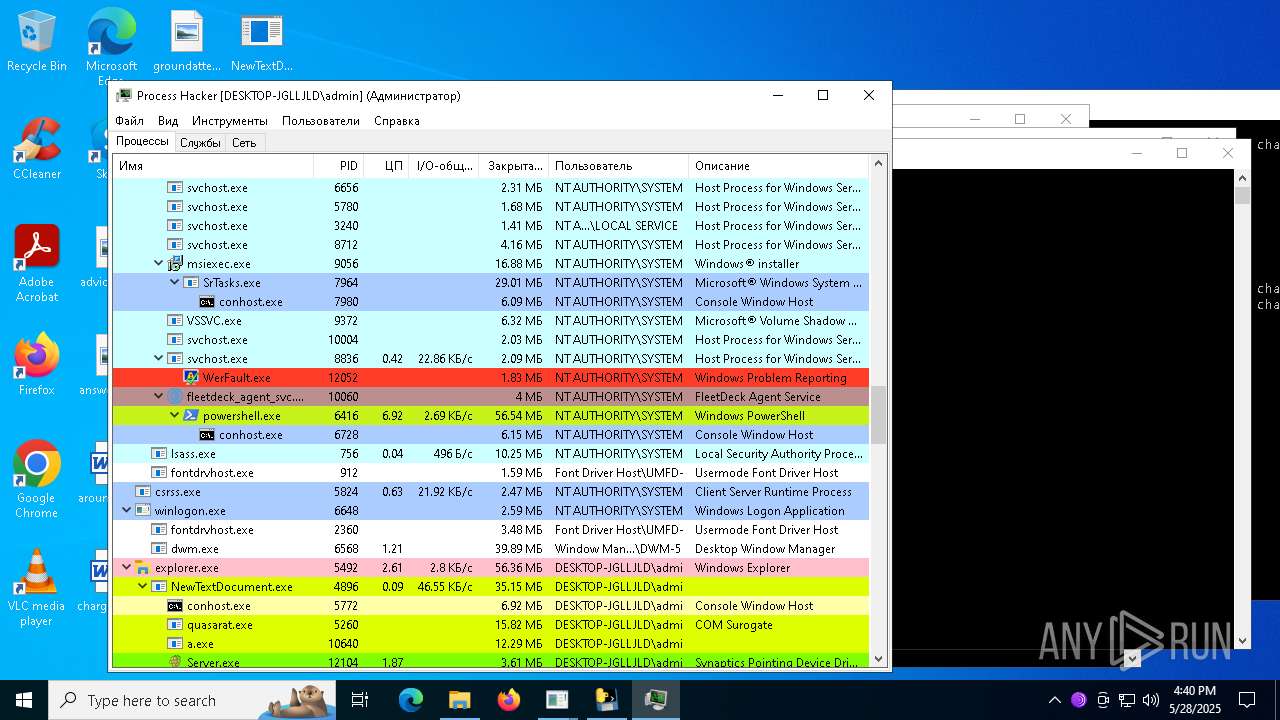
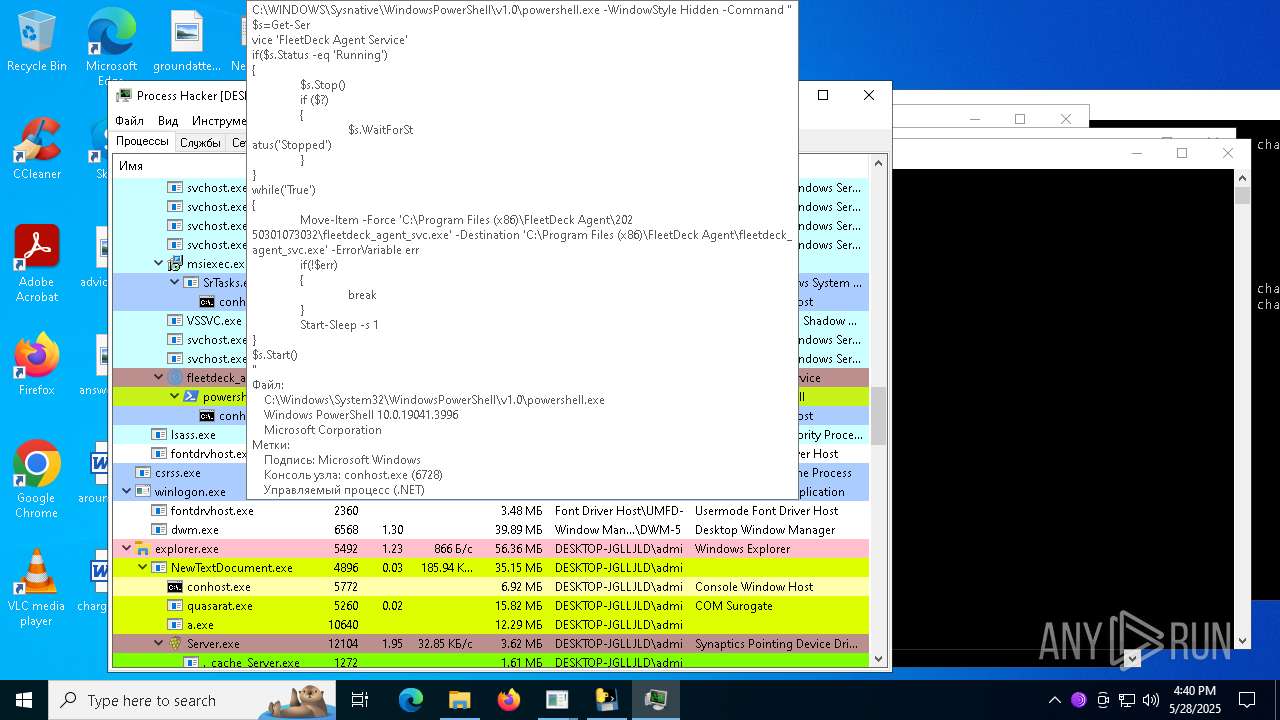
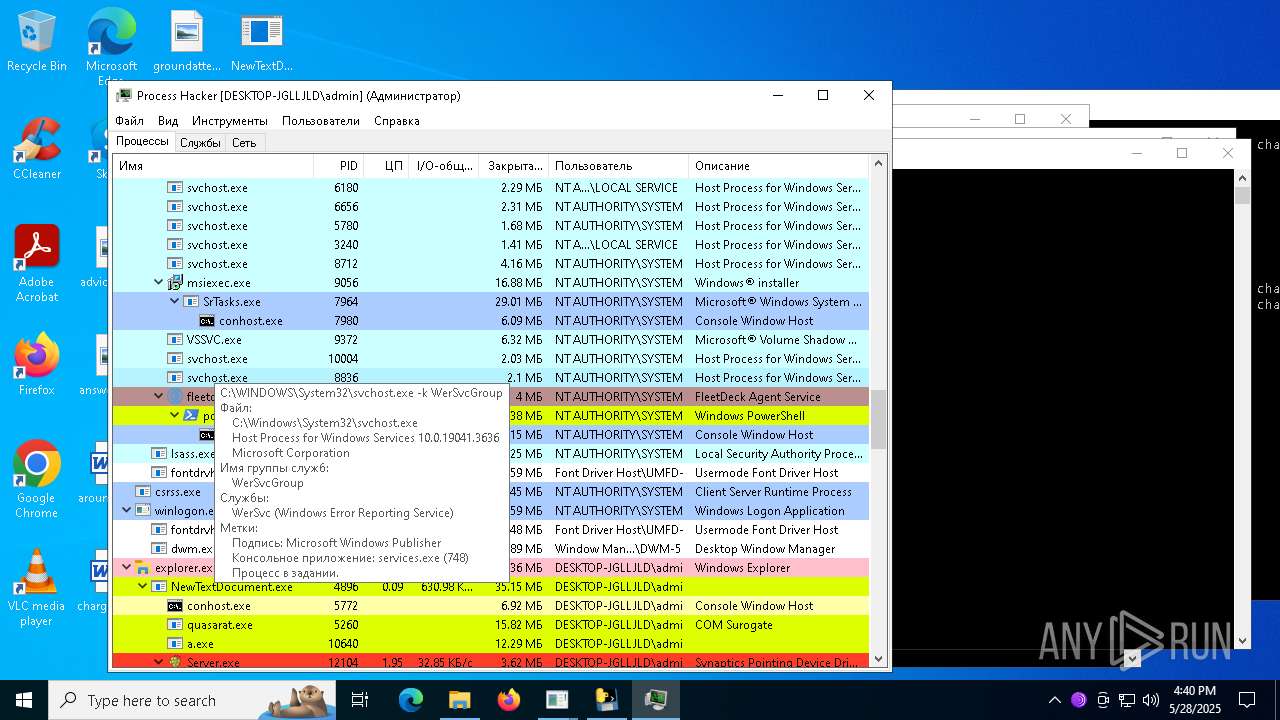
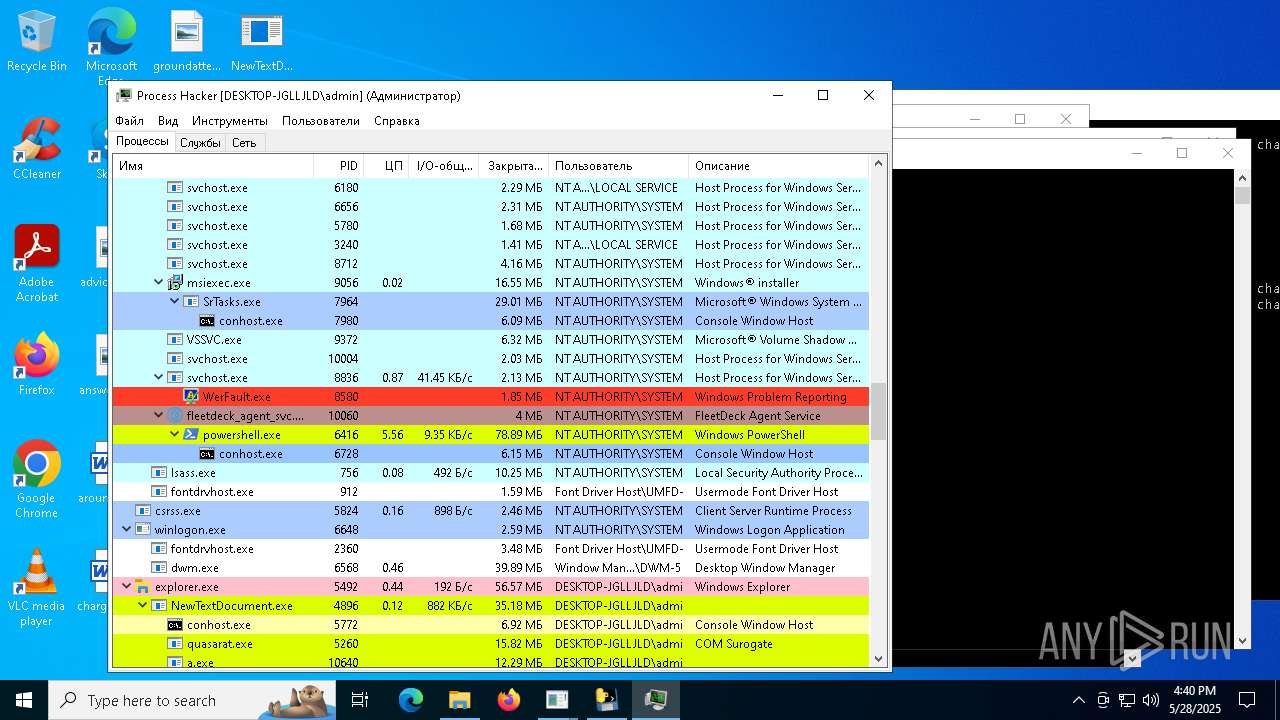
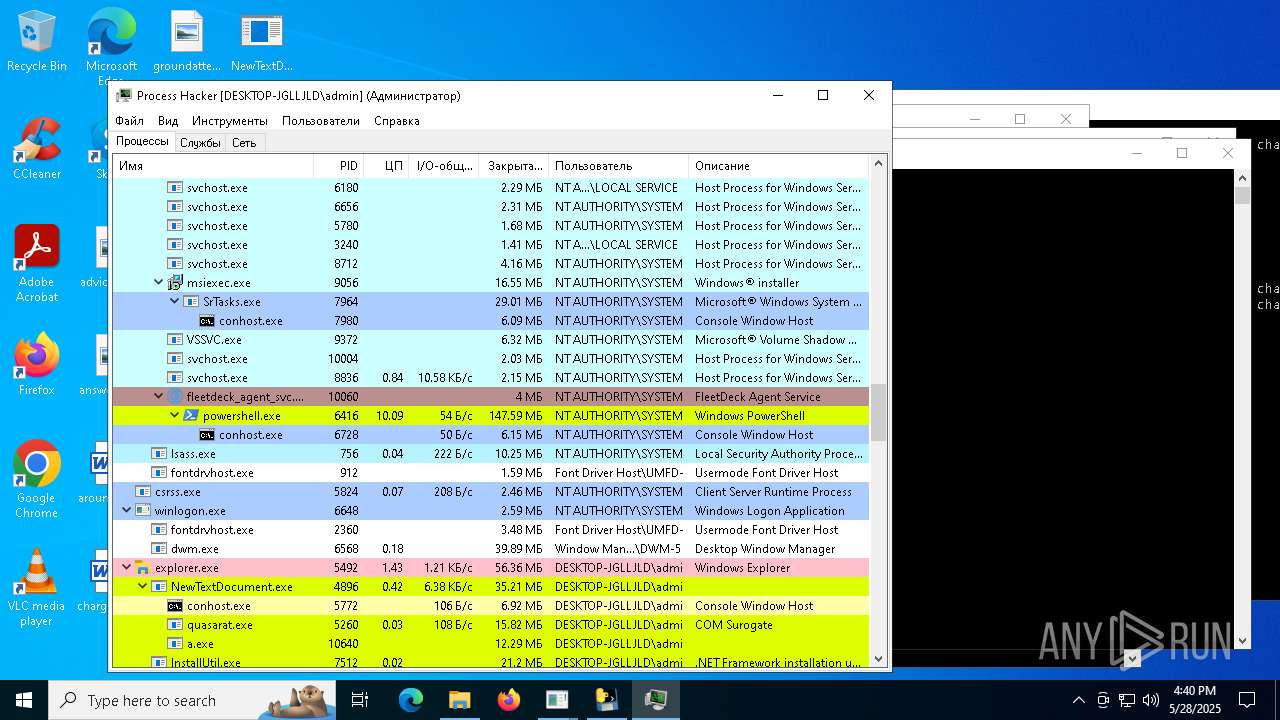
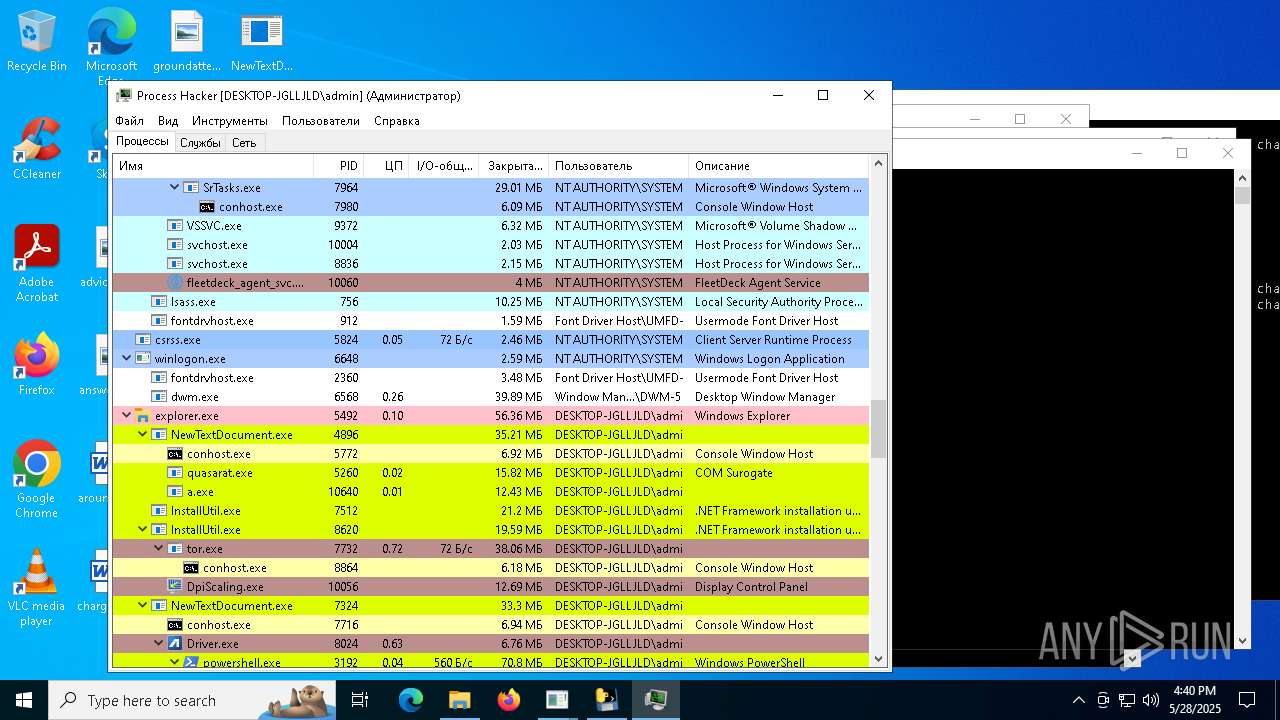
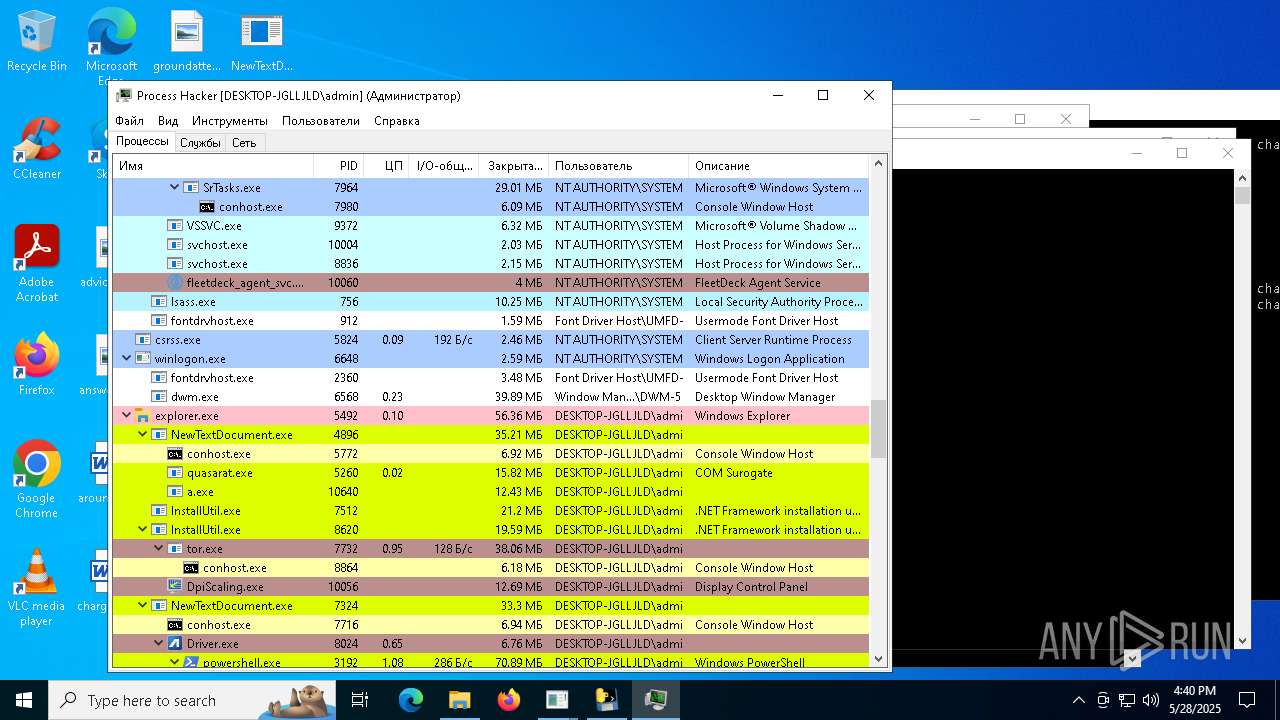
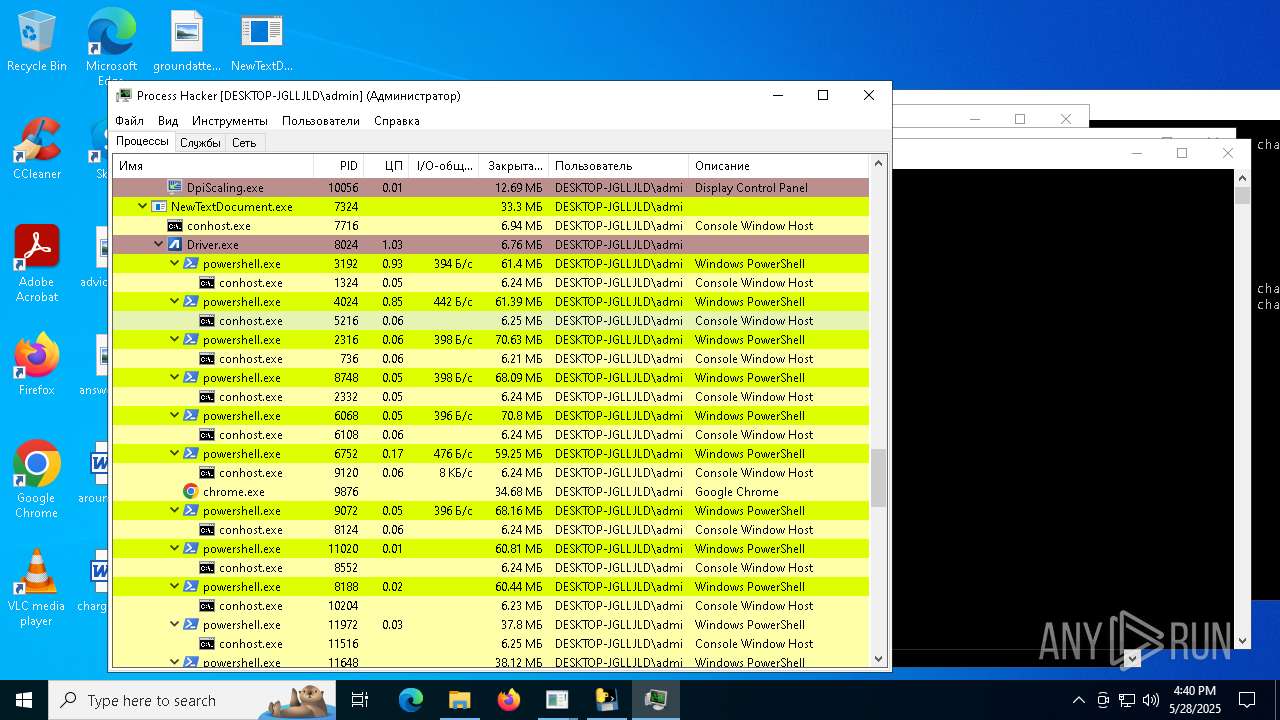
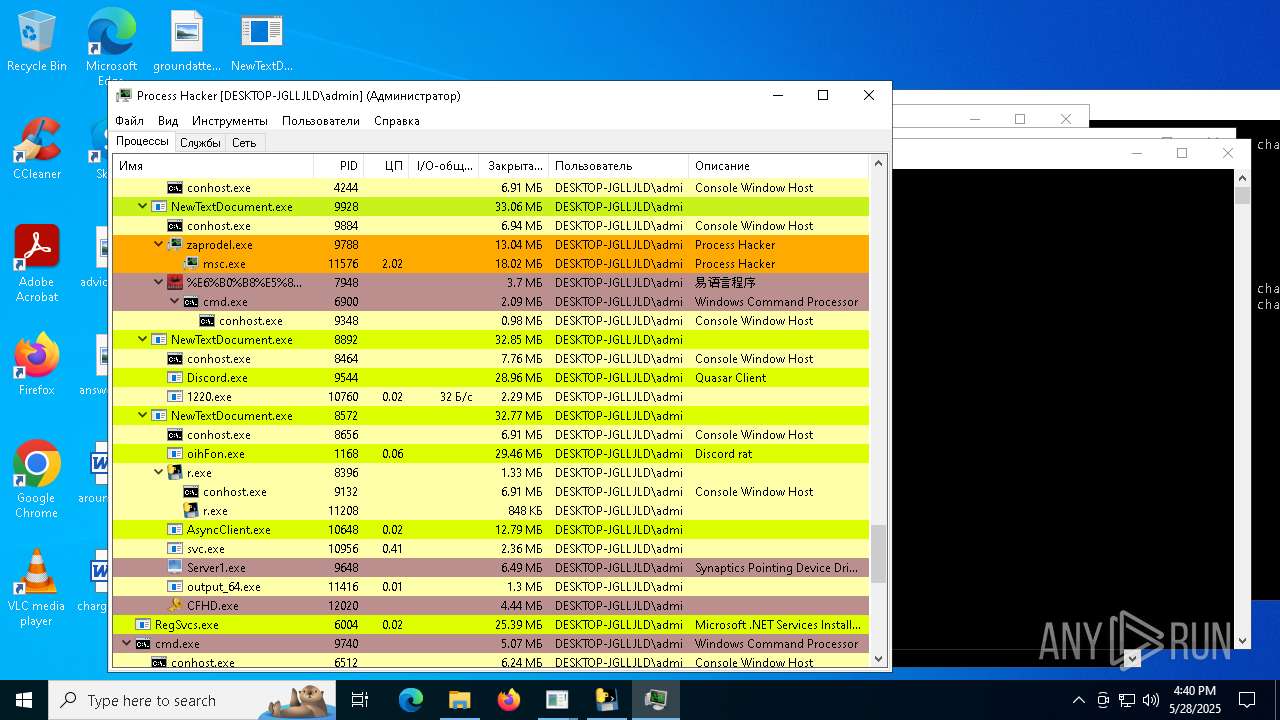
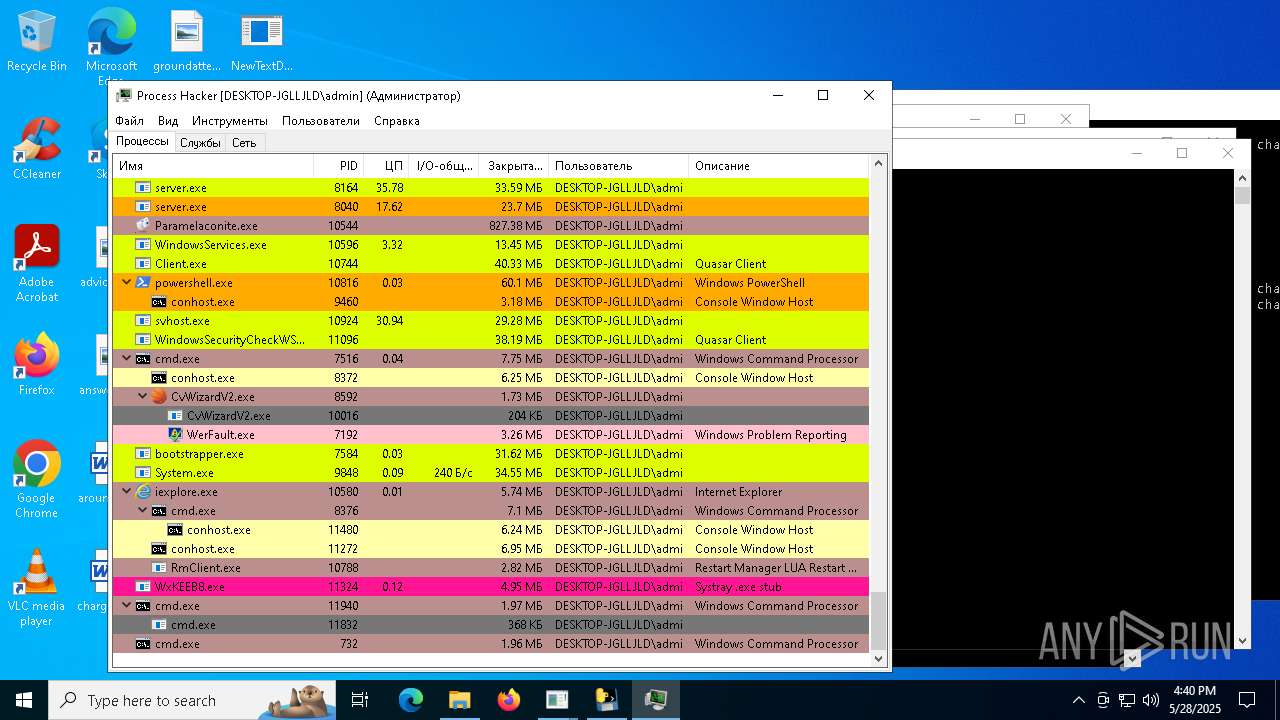
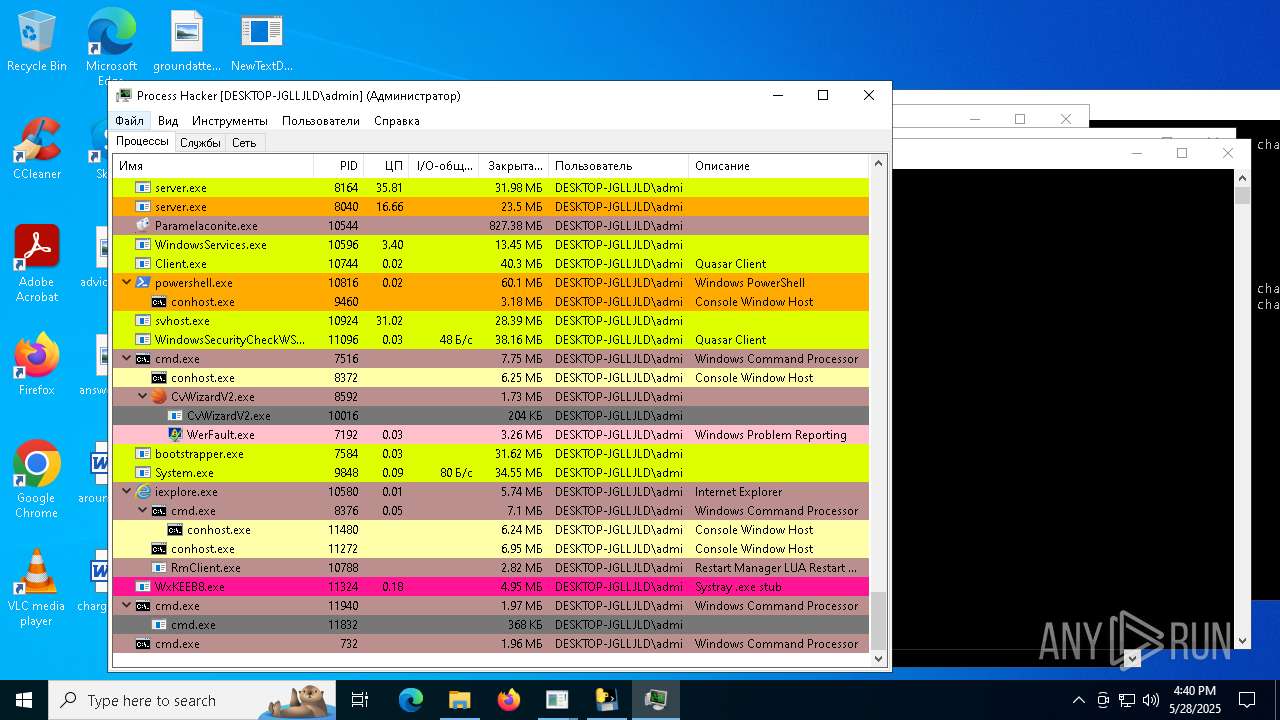
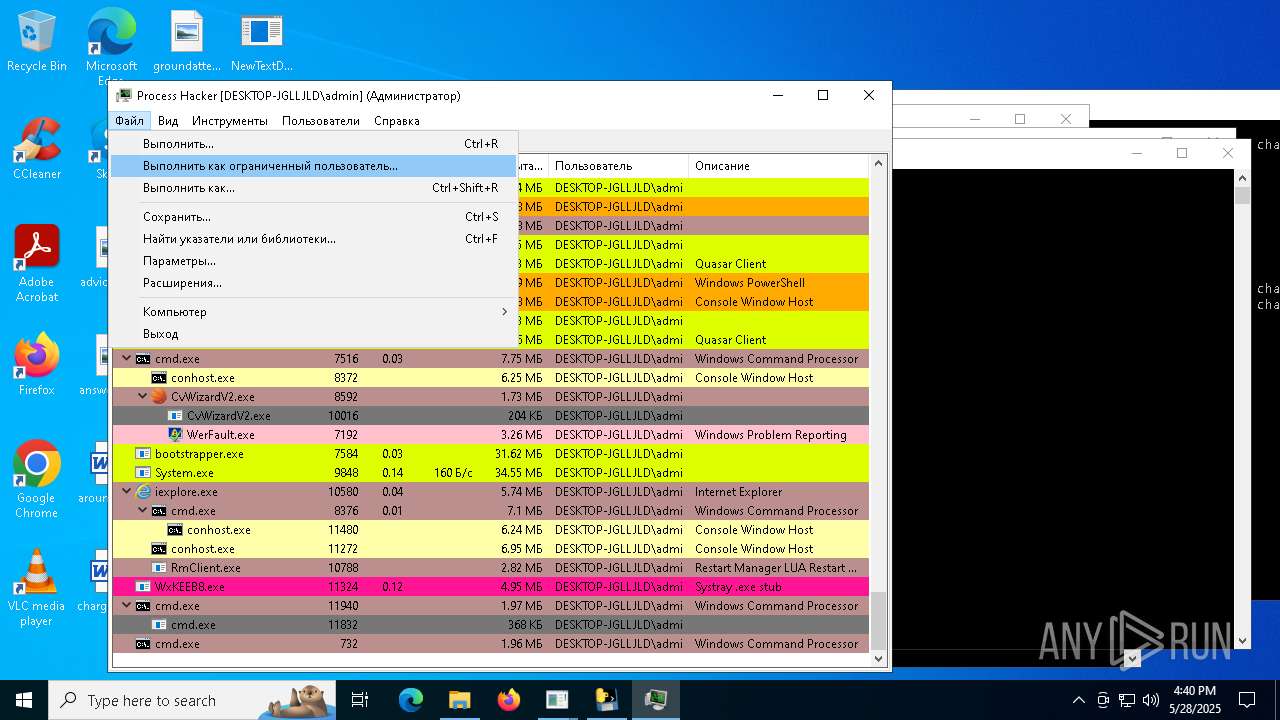
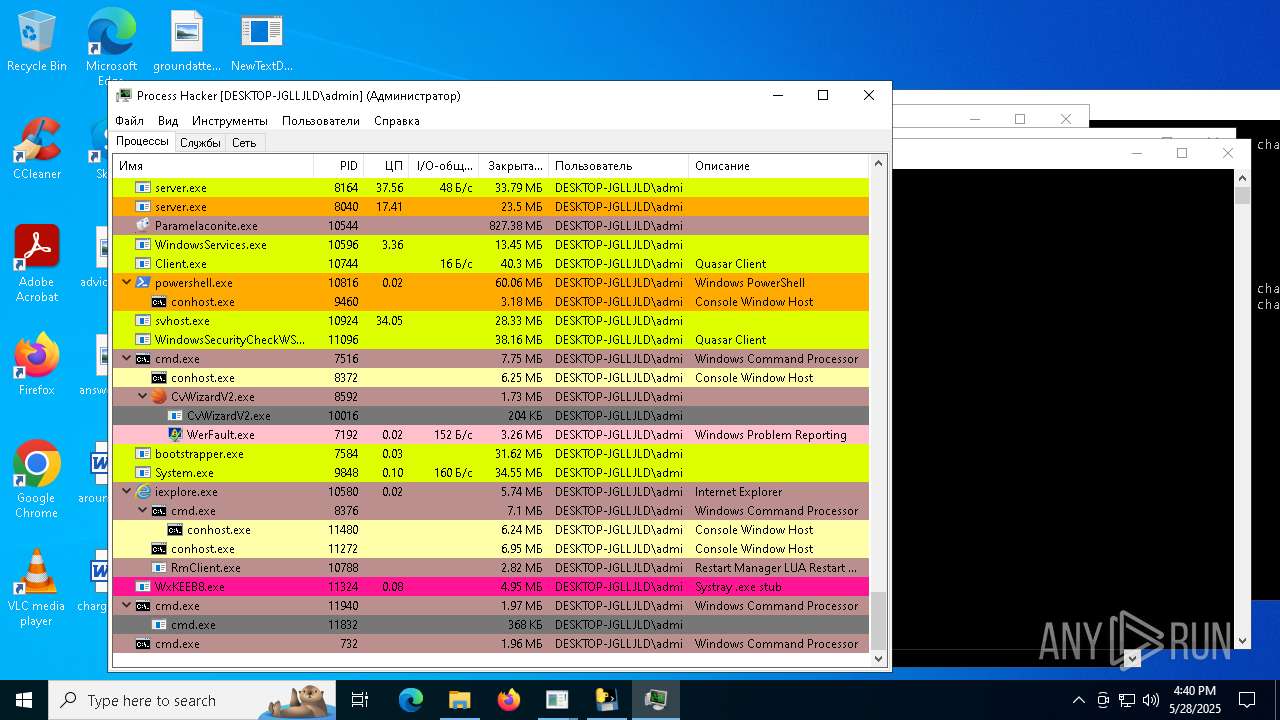
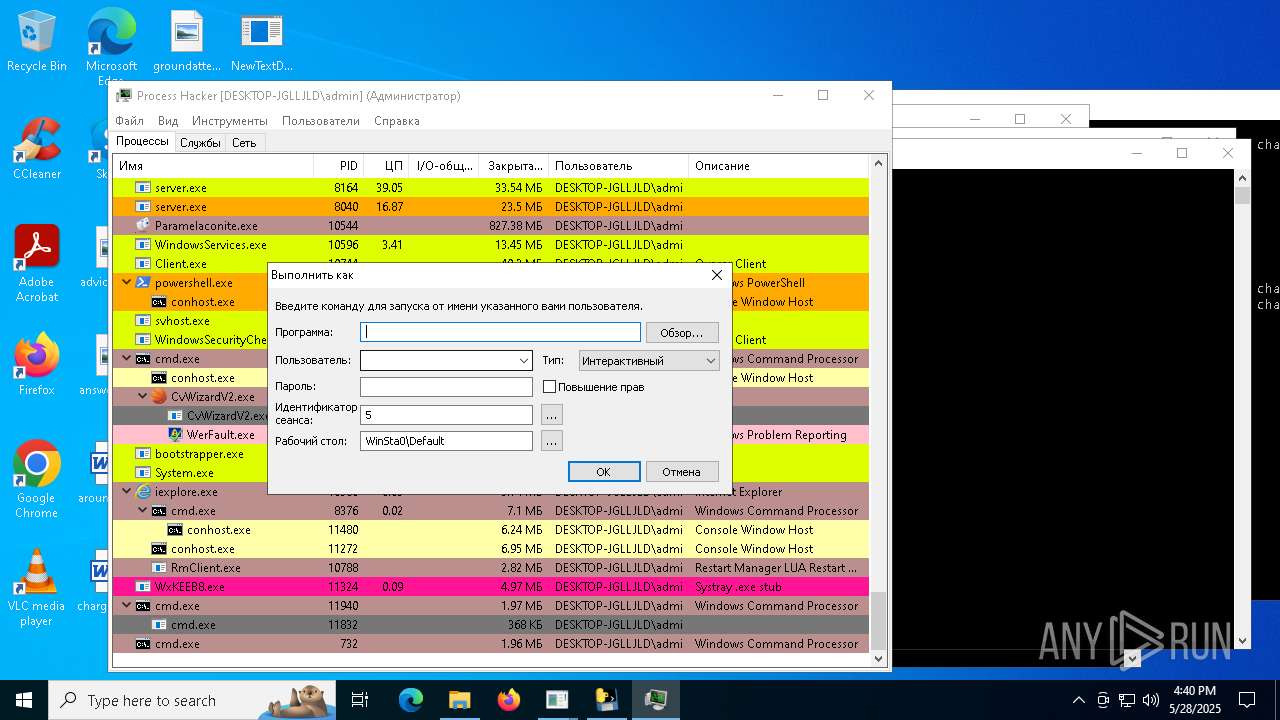
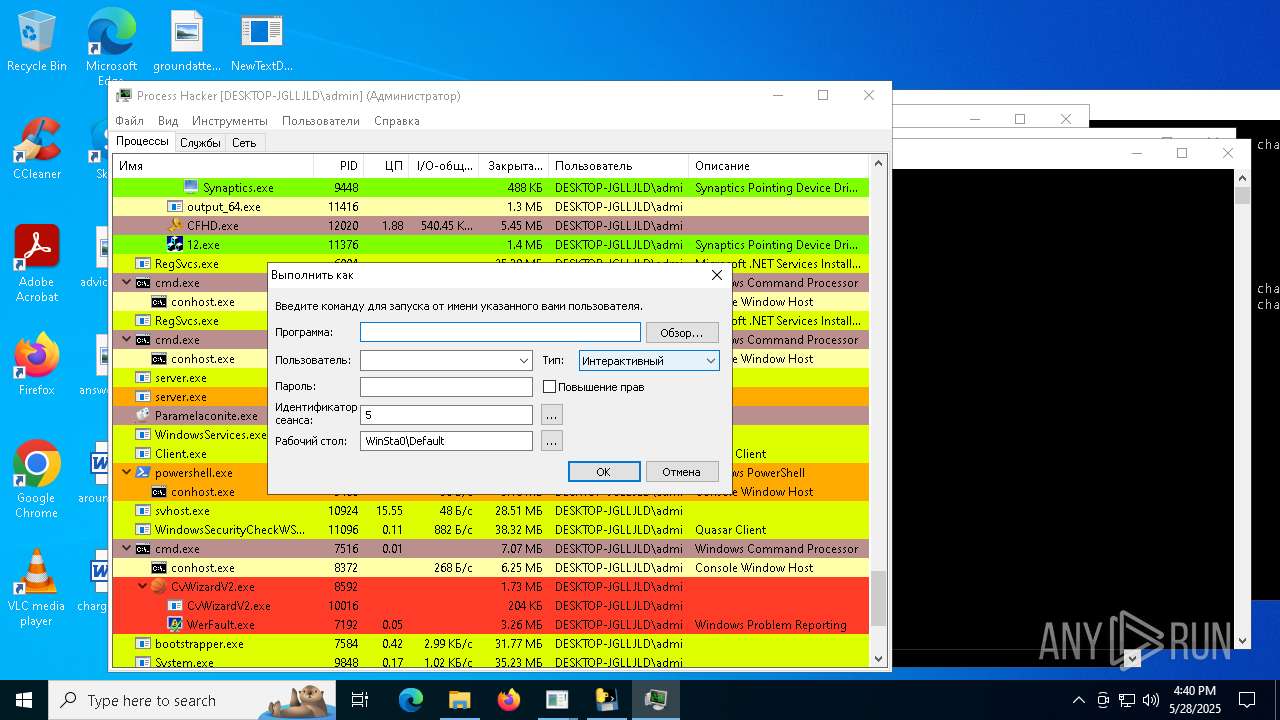
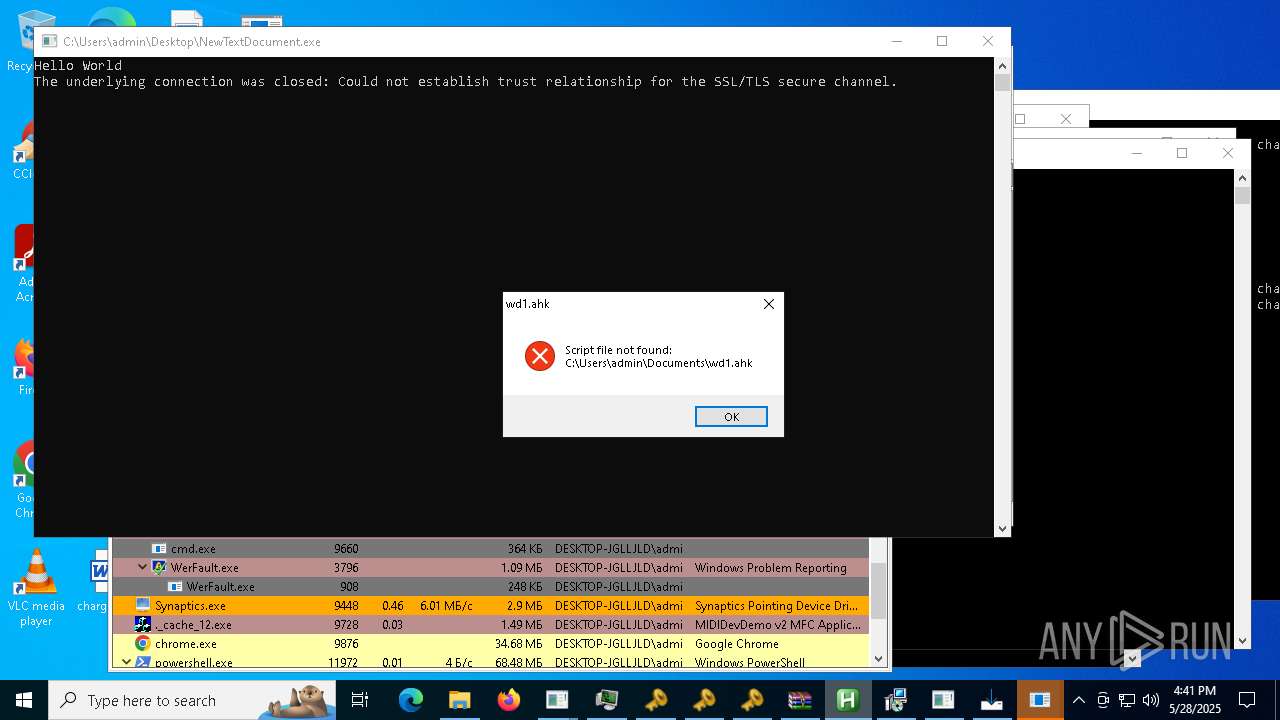
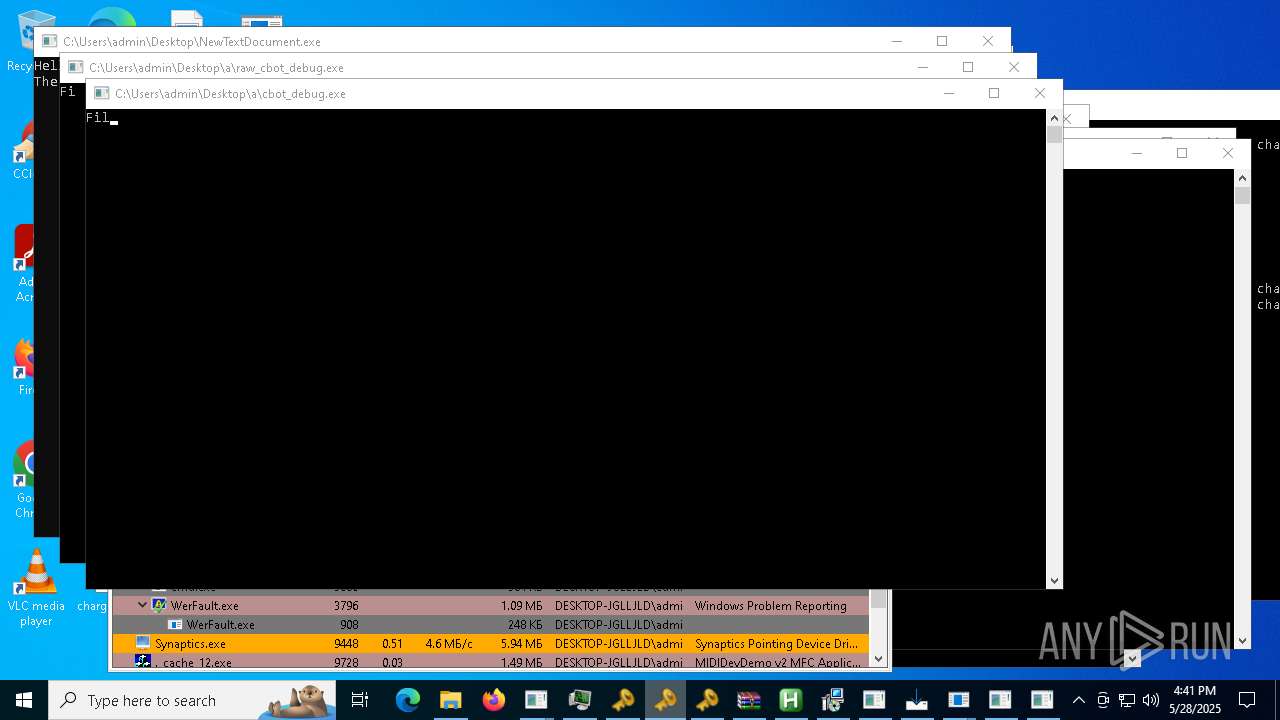
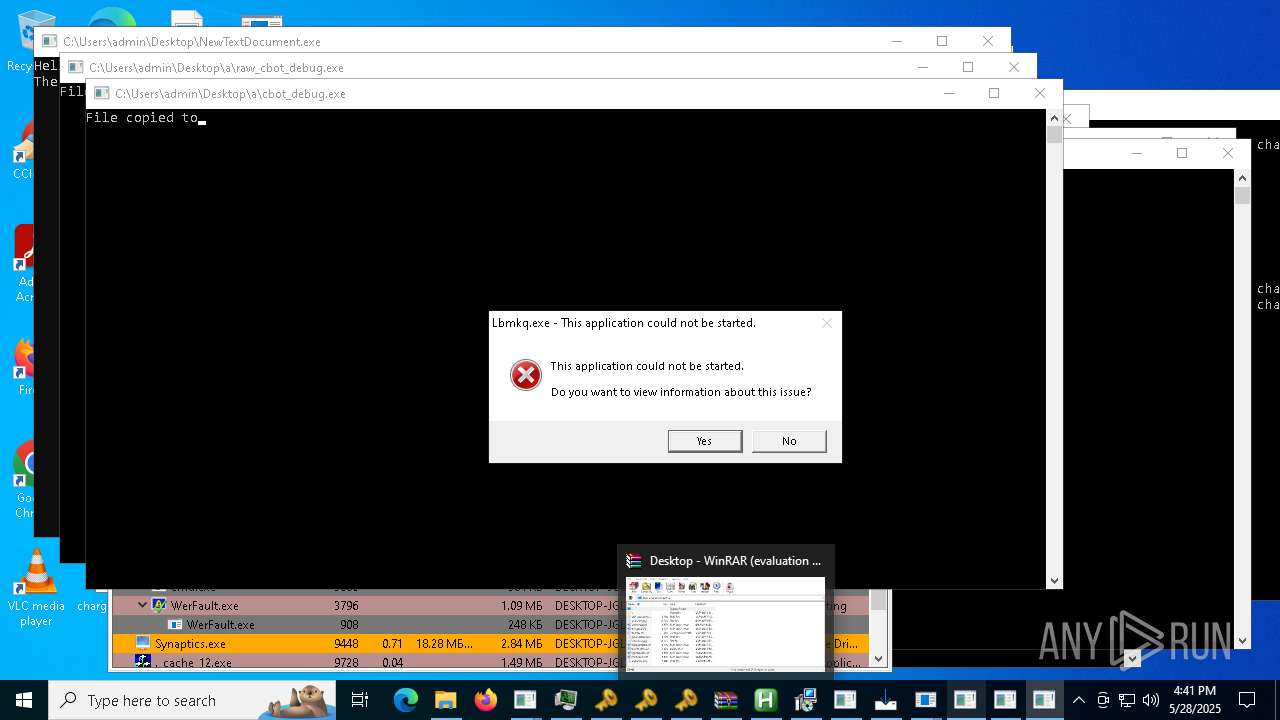
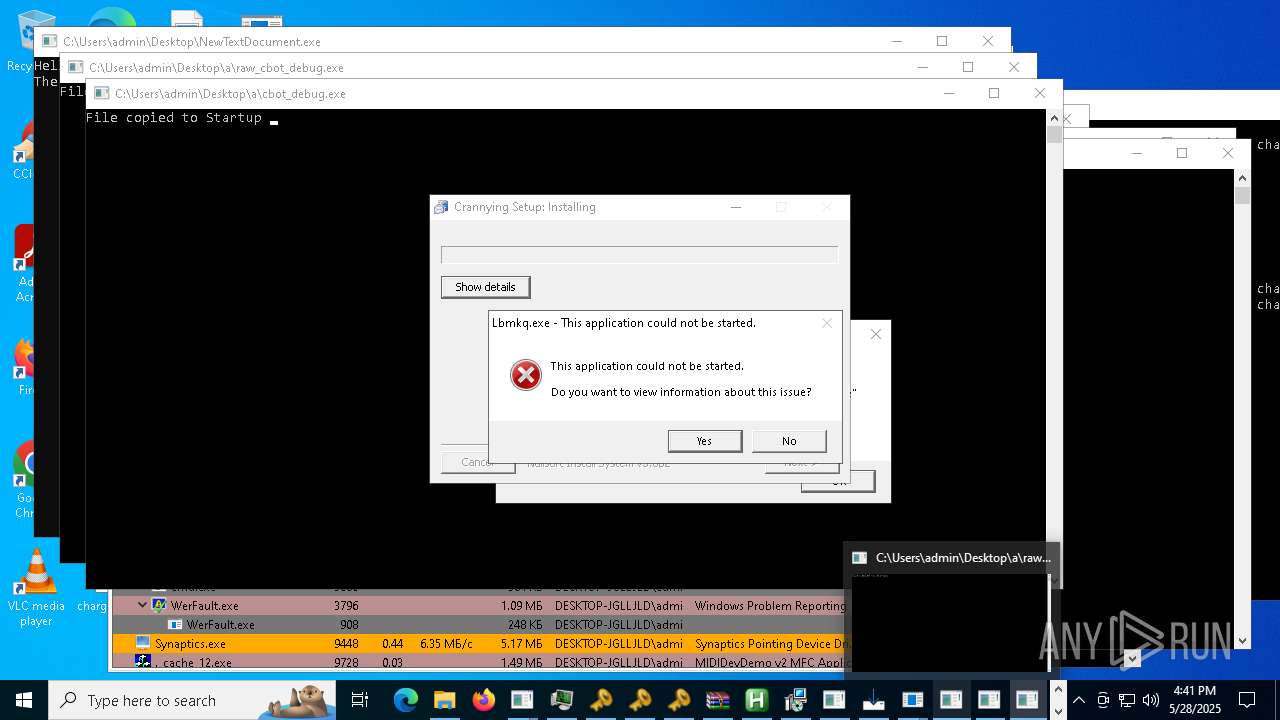
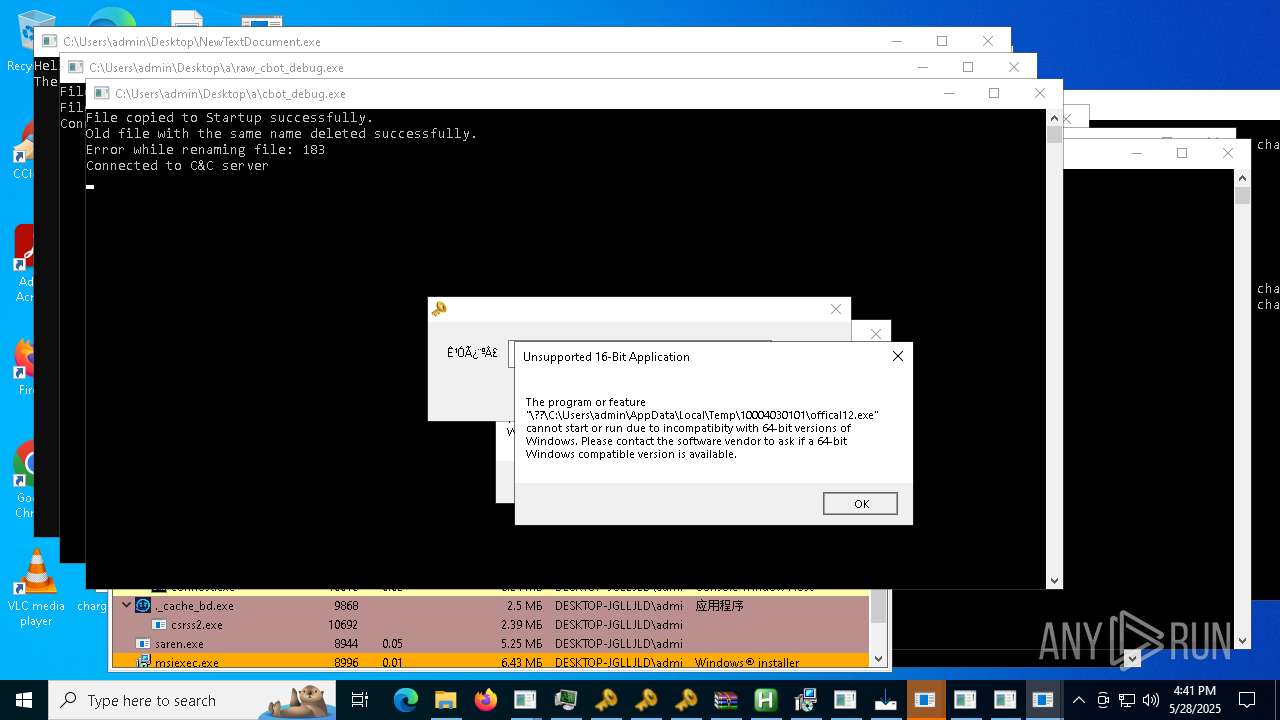
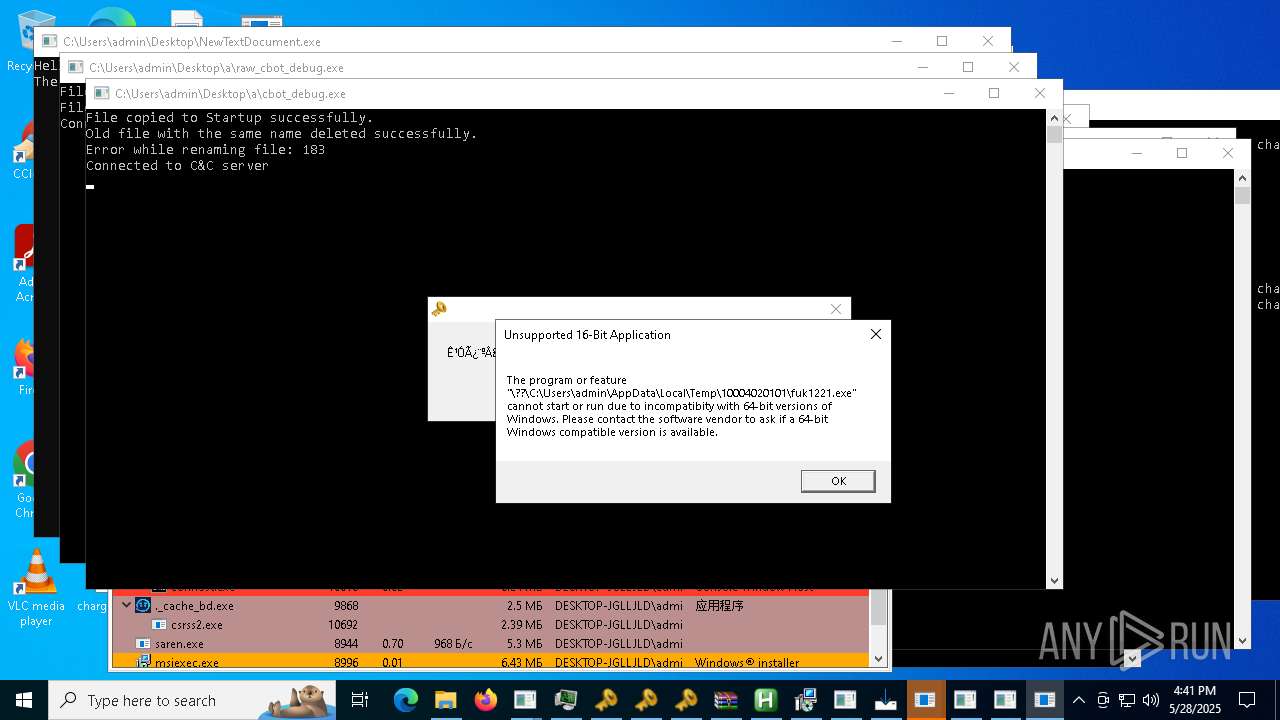
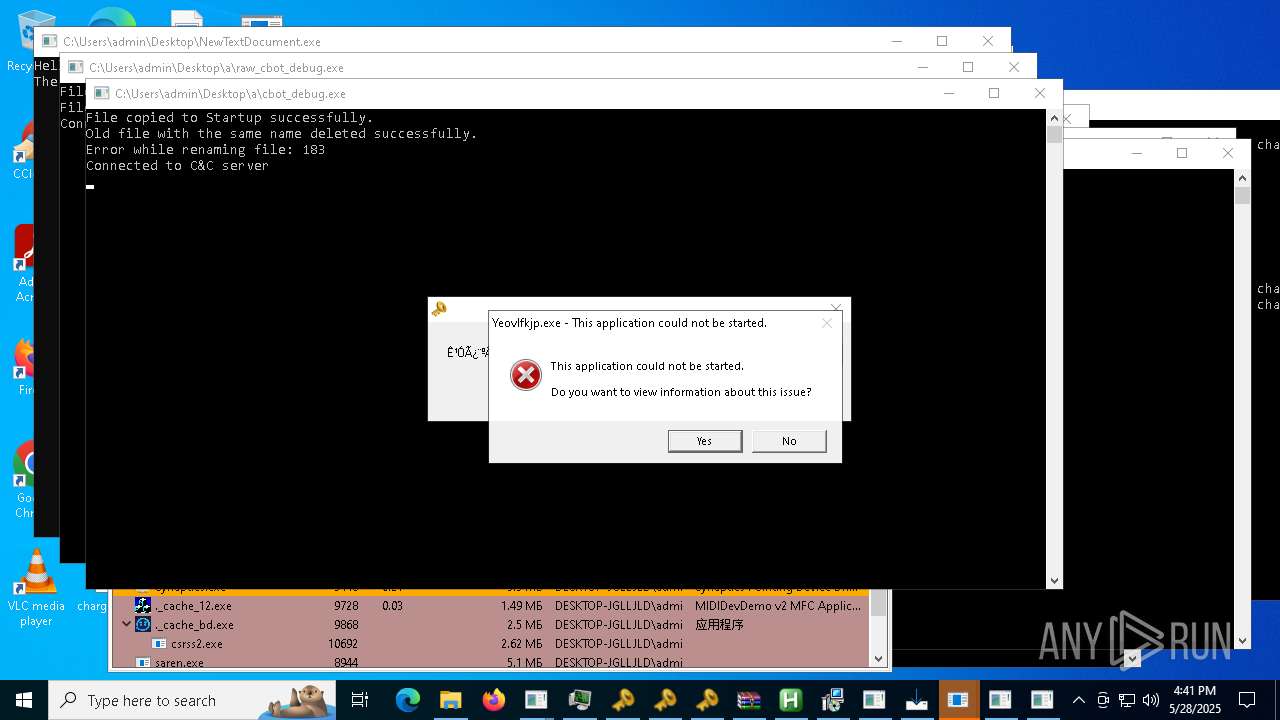
| File name: | NewTextDocument.exe |
| Full analysis: | https://app.any.run/tasks/8560deb6-60d4-4959-82b6-3f836d46ede5 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 28, 2025, 16:36:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- NewTextDocument.exe (PID: 4896)
Changes the autorun value in the registry
- Oxpfrhovopa.exe (PID: 2040)
ASYNCRAT has been detected (SURICATA)
- InstallUtil.exe (PID: 7512)
PURECRYPTER has been detected (YARA)
- Cjahwaqslw.exe (PID: 1116)
GENERIC has been found (auto)
- Eijhmtanpyiuic.exe (PID: 1628)
- Chddewmrihyrdj.exe (PID: 8784)
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 8892)
- cbot_debug.exe (PID: 3992)
- cbot.exe (PID: 8424)
Executing a file with an untrusted certificate
- Driver.exe (PID: 8024)
- Supawn.exe (PID: 11700)
- Nationalbankdirektrernes.exe (PID: 11312)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 10604)
- Gamma_app_stable_vers_107_2_setup_proVer%20(8).exe (PID: 10316)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 6004)
- RegSvcs.exe (PID: 9800)
- RegSvcs.exe (PID: 7020)
- RegSvcs.exe (PID: 2384)
- RegSvcs.exe (PID: 4948)
Known privilege escalation attack
- dllhost.exe (PID: 3268)
Run PowerShell with an invisible window
- powershell.exe (PID: 8976)
- powershell.exe (PID: 6416)
Changes Windows Defender settings
- bk_0.1.4.7.exe (PID: 8116)
Adds path to the Windows Defender exclusion list
- bk_0.1.4.7.exe (PID: 8116)
VALLEY has been found (auto)
- NewTextDocument.exe (PID: 8572)
Starts CMD.EXE for self-deleting
- ._cache_Server1.exe (PID: 11344)
- ._cache_Server.exe (PID: 1272)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 10580)
BABAR has been found (auto)
- NewTextDocument.exe (PID: 4896)
AGENTTESLA has been detected (SURICATA)
- Paramelaconite.exe (PID: 10544)
LOKI has been found (auto)
- NewTextDocument.exe (PID: 8892)
AMADEY has been detected (SURICATA)
- saren.exe (PID: 8944)
GHOSTSOCKS has been found (auto)
- NewTextDocument.exe (PID: 8572)
Connects to the CnC server
- saren.exe (PID: 8944)
- d.exe (PID: 7780)
SCREENCONNECT has been found (auto)
- NewTextDocument.exe (PID: 7324)
Starts Visual C# compiler
- qwalphaqw.exe (PID: 7488)
REDLINE has been detected (SURICATA)
- d.exe (PID: 7780)
METASTEALER has been detected (SURICATA)
- d.exe (PID: 7780)
FORMBOOK has been found (auto)
- NewTextDocument.exe (PID: 4896)
AGENTTESLA has been found (auto)
- NewTextDocument.exe (PID: 8892)
Stealers network behavior
- d.exe (PID: 7780)
GULOADER has been found (auto)
- NewTextDocument.exe (PID: 7324)
Signed with known abused certificate
- NewTextDocument.exe (PID: 7324)
COINMINER has been found (auto)
- sgsdg.exe (PID: 11828)
- sgsdg.exe (PID: 11828)
SUSPICIOUS
Executable content was dropped or overwritten
- NewTextDocument.exe (PID: 4896)
- welcome.exe (PID: 5176)
- Oxpfrhovopa.exe (PID: 2040)
- InstallUtil.exe (PID: 8620)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 8892)
- barren.exe (PID: 7620)
- esentutl.exe (PID: 2192)
- Chddewmrihyrdj.exe (PID: 8784)
- Eijhmtanpyiuic.exe (PID: 1628)
- NewTextDocument.exe (PID: 8572)
- csc.exe (PID: 9768)
- Paramelaconite.exe (PID: 3096)
- NewTextDocument.exe (PID: 9928)
- fleetdeck_agent_svc.exe (PID: 8820)
- remcos_a.exe (PID: 8004)
- FixOnline.exe (PID: 9600)
- king.exe (PID: 9028)
- AntiSpyware.exe (PID: 8576)
- Installer.exe (PID: 2780)
- r.exe (PID: 8396)
- bk_0.1.4.7.exe (PID: 8116)
- Client-built.exe (PID: 10348)
- 4De3.exe (PID: 2568)
- csc.exe (PID: 660)
- server.exe (PID: 8040)
- server.exe (PID: 8164)
- CvWizardV2.exe (PID: 10780)
- zaprodel.exe (PID: 9788)
- csc.exe (PID: 10576)
- csc.exe (PID: 10844)
- tor.exe (PID: 7732)
- csc.exe (PID: 8856)
- csc.exe (PID: 10892)
- csc.exe (PID: 10964)
- System.exe (PID: 9604)
- bootstrapper.exe (PID: 10392)
- Server1.exe (PID: 9648)
- csc.exe (PID: 10052)
- 6D9F6564C02.exe (PID: 7276)
- svhost.exe (PID: 10924)
- Server.exe (PID: 12104)
- svchost.exe (PID: 9588)
- 12.exe (PID: 11376)
- csrss2.exe (PID: 8496)
- csc.exe (PID: 5980)
- CFHD.exe (PID: 12020)
- csc.exe (PID: 9324)
- csc.exe (PID: 8588)
- Synaptics.exe (PID: 9448)
- 666.exe (PID: 9020)
- CS2.exe (PID: 12004)
- bd.exe (PID: 6760)
- csc.exe (PID: 8044)
- csc.exe (PID: 6072)
- csc.exe (PID: 7672)
- %E7%94%9F%E6%AD%BB%E7%8B%99%E5%87%BB2.exe (PID: 9920)
- csc.exe (PID: 8520)
- Adobe-ReaderInstaller.exe (PID: 9852)
- ._cache_bd.exe (PID: 9868)
- csrss2.exe (PID: 10692)
- amnew.exe (PID: 9340)
- Adobe-ReaderInstaller.tmp (PID: 11452)
- rundll32.exe (PID: 11644)
- Adobe-ReaderInstaller.exe (PID: 1116)
- raw_cbot.exe (PID: 1512)
- cbot_debug.exe (PID: 3992)
- cbot.exe (PID: 8424)
- raw_cbot_debug.exe (PID: 7984)
- NewTextDocument.exe (PID: 5204)
- Quodlibet.exe (PID: 6216)
- welcome.exe (PID: 9596)
- Nationalbankdirektrernes.exe (PID: 11312)
- Slasher.exe (PID: 9992)
- Supawn.exe (PID: 11700)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 10604)
- Alli_AI_stable_latest_release_ver_801_Setup_win.tmp (PID: 11656)
- bridgesurrogatefontsvc.exe (PID: 8992)
- addon2.exe (PID: 6700)
- Gamma_app_stable_vers_107_2_setup_proVer%20(8).exe (PID: 10316)
- Gamma_app_stable_vers_107_2_setup_proVer%20(8).tmp (PID: 11276)
- sgsdg.exe (PID: 11828)
Potential Corporate Privacy Violation
- NewTextDocument.exe (PID: 4896)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 8572)
- NewTextDocument.exe (PID: 9928)
- CFHD.exe (PID: 12020)
- svchost.exe (PID: 2196)
- CS2.exe (PID: 12004)
- %E7%94%9F%E6%AD%BB%E7%8B%99%E5%87%BB2.exe (PID: 9920)
- NewTextDocument.exe (PID: 5204)
Process drops legitimate windows executable
- welcome.exe (PID: 5176)
- r.exe (PID: 8396)
- 6D9F6564C02.exe (PID: 7276)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 8892)
- cbot.exe (PID: 8424)
- NewTextDocument.exe (PID: 4896)
- cbot_debug.exe (PID: 3992)
- raw_cbot.exe (PID: 1512)
- welcome.exe (PID: 9596)
- raw_cbot_debug.exe (PID: 7984)
- addon2.exe (PID: 6700)
- Gamma_app_stable_vers_107_2_setup_proVer%20(8).tmp (PID: 11276)
Process drops python dynamic module
- welcome.exe (PID: 5176)
- r.exe (PID: 8396)
- welcome.exe (PID: 9596)
Reads security settings of Internet Explorer
- Lbmkq.exe (PID: 1532)
- NewTextDocument.exe (PID: 4896)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Cjahwaqslw.exe (PID: 1116)
- Gfrzkndk.exe (PID: 4756)
- Wxjghzv.exe (PID: 3304)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
The process drops C-runtime libraries
- welcome.exe (PID: 5176)
- r.exe (PID: 8396)
- welcome.exe (PID: 9596)
Starts CMD.EXE for commands execution
- Lbmkq.exe (PID: 1532)
- Jbjqos.exe (PID: 2088)
- Cjahwaqslw.exe (PID: 1116)
- Yeovlfkjp.exe (PID: 6132)
- Gfrzkndk.exe (PID: 4756)
- Wxjghzv.exe (PID: 3304)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
- Eijhmtanpyiuic.exe (PID: 1628)
- Chddewmrihyrdj.exe (PID: 8784)
- remcos_a.exe (PID: 8004)
- remcos_a.exe (PID: 840)
- wscript.exe (PID: 9560)
- update.exe (PID: 7368)
- CvWizardV2.exe (PID: 10780)
- ._cache_Server1.exe (PID: 11344)
- remcos.exe (PID: 7364)
- %E6%B0%B8%E5%8A%AB.exe (PID: 7948)
- ._cache_Server.exe (PID: 1272)
- addon.exe (PID: 9476)
- wscript.exe (PID: 8272)
- addon2.exe (PID: 812)
- bridgesurrogatefontsvc.exe (PID: 8992)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 3304)
- cmd.exe (PID: 4244)
- cmd.exe (PID: 5428)
- cmd.exe (PID: 4724)
- cmd.exe (PID: 7180)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 7840)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 7296)
- cmd.exe (PID: 4920)
The process creates files with name similar to system file names
- Oxpfrhovopa.exe (PID: 2040)
Reads the date of Windows installation
- NewTextDocument.exe (PID: 4896)
Connects to the server without a host name
- NewTextDocument.exe (PID: 4896)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 8572)
- Paramelaconite.exe (PID: 10544)
- WxKEEB8.exe (PID: 11324)
- saren.exe (PID: 8944)
- dfsvc.exe (PID: 5072)
- NewTextDocument.exe (PID: 5204)
- svc.exe (PID: 10956)
Process requests binary or script from the Internet
- NewTextDocument.exe (PID: 4896)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 8572)
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 5204)
BASE64 encoded PowerShell command has been detected
- Lbmkq.exe (PID: 1532)
- Cjahwaqslw.exe (PID: 1116)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Gfrzkndk.exe (PID: 4756)
- Nkrpno.exe (PID: 7312)
- Wxjghzv.exe (PID: 3304)
- Hzfph.exe (PID: 7724)
- Flambi.exe (PID: 7568)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
- Driver.exe (PID: 8024)
There is functionality for taking screenshot (YARA)
- Lbmkq.exe (PID: 1532)
- Cjahwaqslw.exe (PID: 1116)
- welcome.exe (PID: 5176)
Base64-obfuscated command line is found
- Yeovlfkjp.exe (PID: 6132)
- Lbmkq.exe (PID: 1532)
- Cjahwaqslw.exe (PID: 1116)
- Gfrzkndk.exe (PID: 4756)
- Wxjghzv.exe (PID: 3304)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
- Jbjqos.exe (PID: 2088)
- Driver.exe (PID: 8024)
Starts POWERSHELL.EXE for commands execution
- Lbmkq.exe (PID: 1532)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Wxjghzv.exe (PID: 3304)
- Nkrpno.exe (PID: 7312)
- Gfrzkndk.exe (PID: 4756)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
- Cjahwaqslw.exe (PID: 1116)
- fleetdeck_agent_svc.exe (PID: 8328)
- Driver.exe (PID: 8024)
- fleetdeck_agent_svc.exe (PID: 8820)
- bk_0.1.4.7.exe (PID: 8116)
- fleetdeck_agent_svc.exe (PID: 10060)
Process uses IPCONFIG to renew DHCP configuration
- cmd.exe (PID: 7520)
- cmd.exe (PID: 8692)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 8212)
- cmd.exe (PID: 5048)
- cmd.exe (PID: 2084)
- cmd.exe (PID: 9480)
- cmd.exe (PID: 9848)
- cmd.exe (PID: 9960)
- cmd.exe (PID: 10100)
- cmd.exe (PID: 8608)
Contacting a server suspected of hosting an CnC
- InstallUtil.exe (PID: 7512)
- saren.exe (PID: 8944)
Connects to unusual port
- InstallUtil.exe (PID: 7512)
- InstallUtil.exe (PID: 8084)
- InstallUtil.exe (PID: 9424)
- InstallUtil.exe (PID: 10036)
- tor.exe (PID: 8268)
- tor.exe (PID: 7732)
- tor.exe (PID: 9992)
- NewTextDocument.exe (PID: 8572)
- RuntimeBroker.exe (PID: 8440)
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 9928)
- update.exe (PID: 7368)
- quasarat.exe (PID: 5260)
- AsyncClient.exe (PID: 10648)
- a.exe (PID: 10640)
- 1220.exe (PID: 10760)
- server.exe (PID: 8164)
- Client.exe (PID: 10744)
- server.exe (PID: 8040)
- bootstrapper.exe (PID: 7584)
- NewTextDocument.exe (PID: 4896)
- NewTextDocument.exe (PID: 7324)
- svhost.exe (PID: 10924)
- CFHD.exe (PID: 12020)
- WindowsSecurityCheckWSC.secureapp.exe (PID: 11096)
- CS2.exe (PID: 12004)
- %E7%94%9F%E6%AD%BB%E7%8B%99%E5%87%BB2.exe (PID: 9920)
- Paramelaconite.exe (PID: 10544)
- d.exe (PID: 7780)
- cbot.exe (PID: 8424)
- raw_cbot.exe (PID: 1512)
- svchost.exe (PID: 9588)
- cbot_debug.exe (PID: 3992)
- Quodlibet.exe (PID: 6216)
- raw_cbot_debug.exe (PID: 7984)
Application launched itself
- welcome.exe (PID: 5176)
- Paramelaconite.exe (PID: 3096)
- WerFault.exe (PID: 840)
- r.exe (PID: 8396)
- sgsdg.exe (PID: 12084)
- addon2.exe (PID: 6700)
Connects to FTP
- tor.exe (PID: 7732)
- Paramelaconite.exe (PID: 10544)
Executes as Windows Service
- VSSVC.exe (PID: 9372)
- fleetdeck_agent_svc.exe (PID: 8820)
- fleetdeck_agent_svc.exe (PID: 10060)
- vmrhmw.exe (PID: 9060)
- msc.exe (PID: 9212)
Executing commands from ".cmd" file
- Eijhmtanpyiuic.exe (PID: 1628)
- Chddewmrihyrdj.exe (PID: 8784)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8104)
- cmd.exe (PID: 8408)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 2192)
- esentutl.exe (PID: 6048)
- alpha.pif (PID: 7448)
- alpha.pif (PID: 3268)
- alpha.pif (PID: 7176)
- alpha.pif (PID: 7472)
Starts itself from another location
- cmd.exe (PID: 2108)
- cmd.exe (PID: 1568)
- AntiSpyware.exe (PID: 8576)
- Installer.exe (PID: 2780)
- FixOnline.exe (PID: 9600)
- king.exe (PID: 9028)
- 4De3.exe (PID: 2568)
- Client-built.exe (PID: 10348)
- System.exe (PID: 9604)
- bootstrapper.exe (PID: 10392)
- amnew.exe (PID: 9340)
Created directory related to system
- alpha.pif (PID: 7176)
- alpha.pif (PID: 7448)
Starts a Microsoft application from unusual location
- alpha.pif (PID: 7176)
- alpha.pif (PID: 3268)
- alpha.pif (PID: 7472)
- alpha.pif (PID: 7448)
- WxKEEB8.exe (PID: 11324)
- d.exe (PID: 7780)
- cbot_debug.exe (PID: 3992)
- raw_cbot_debug.exe (PID: 7984)
- cbot.exe (PID: 8424)
- raw_cbot.exe (PID: 1512)
- addon2.exe (PID: 6700)
- addon2.exe (PID: 812)
Starts application with an unusual extension
- cmd.exe (PID: 2108)
- cmd.exe (PID: 1568)
- Eijhmtanpyiuic.exe (PID: 1628)
- Chddewmrihyrdj.exe (PID: 8784)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Driver.exe (PID: 8024)
- RegSvcs.exe (PID: 9800)
- RegSvcs.exe (PID: 6004)
- RegSvcs.exe (PID: 7020)
- RegSvcs.exe (PID: 4948)
- RegSvcs.exe (PID: 2384)
Checks for external IP
- svchost.exe (PID: 2196)
- oihFon.exe (PID: 1168)
- update.exe (PID: 7368)
- RegSvcs.exe (PID: 6004)
- RegSvcs.exe (PID: 9800)
- RegSvcs.exe (PID: 7020)
- quasarat.exe (PID: 5260)
- Paramelaconite.exe (PID: 10544)
- RegSvcs.exe (PID: 2384)
- RegSvcs.exe (PID: 4948)
- sgsdg.exe (PID: 12084)
- sgsdg.exe (PID: 11828)
Malware-specific behavior (creating "System.dll" in Temp)
- Paramelaconite.exe (PID: 3096)
- Nationalbankdirektrernes.exe (PID: 11312)
- Supawn.exe (PID: 11700)
Executes application which crashes
- solsniper.exe (PID: 7284)
- plugmanff2.exe (PID: 7332)
- cmd.exe (PID: 9560)
- WerFault.exe (PID: 840)
- timeout.exe (PID: 11776)
- RmClient.exe (PID: 10316)
- CvWizardV2.exe (PID: 8592)
- cmd.exe (PID: 11940)
- %E6%B0%B8%E5%8A%AB.exe (PID: 7948)
- cmd.exe (PID: 732)
- 3R%BC%BC%CA%F5.exe (PID: 11860)
- csc.exe (PID: 8828)
- agodee.exe (PID: 448)
- remcos.exe (PID: 12044)
- catee.exe (PID: 8940)
- TiWorker.exe (PID: 524)
- alphamm.exe (PID: 7208)
- kjoxca.exe (PID: 9812)
The process connected to a server suspected of theft
- oihFon.exe (PID: 1168)
The process hide an interactive prompt from the user
- Driver.exe (PID: 8024)
CSC.EXE is used to compile C# code
- csc.exe (PID: 9768)
- csc.exe (PID: 660)
- csc.exe (PID: 10576)
- csc.exe (PID: 10892)
- csc.exe (PID: 10844)
- csc.exe (PID: 10964)
- csc.exe (PID: 10052)
- csc.exe (PID: 8856)
- csc.exe (PID: 8588)
- csc.exe (PID: 5980)
- csc.exe (PID: 9324)
- csc.exe (PID: 6072)
- csc.exe (PID: 7672)
- csc.exe (PID: 8044)
- csc.exe (PID: 8520)
The process executes VB scripts
- remcos_a.exe (PID: 8004)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 9740)
- cmd.exe (PID: 9076)
- cmd.exe (PID: 8376)
The process bypasses the loading of PowerShell profile settings
- Driver.exe (PID: 8024)
Script adds exclusion path to Windows Defender
- bk_0.1.4.7.exe (PID: 8116)
Contacting a server suspected of hosting an Exploit Kit
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 4896)
- NewTextDocument.exe (PID: 8572)
- NewTextDocument.exe (PID: 7324)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 8164)
- server.exe (PID: 8040)
- WindowsServices.exe (PID: 10596)
- svhost.exe (PID: 10924)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 6416)
Executing commands from a ".bat" file
- CvWizardV2.exe (PID: 10780)
- wscript.exe (PID: 8272)
Probably fake Windows Update file has been dropped
- server.exe (PID: 8040)
- server.exe (PID: 8164)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- server.exe (PID: 8040)
- server.exe (PID: 8164)
Hides command output
- cmd.exe (PID: 11940)
- cmd.exe (PID: 732)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7516)
The executable file from the user directory is run by the CMD process
- CvWizardV2.exe (PID: 8592)
Windows service management via SC.EXE
- sc.exe (PID: 4112)
Possible Social Engineering Attempted
- svchost.exe (PID: 2196)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 8828)
- net.exe (PID: 8236)
INFO
Checks proxy server information
- NewTextDocument.exe (PID: 4896)
Disables trace logs
- NewTextDocument.exe (PID: 4896)
Reads the computer name
- NewTextDocument.exe (PID: 4896)
- welcome.exe (PID: 5176)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Cjahwaqslw.exe (PID: 1116)
- Gfrzkndk.exe (PID: 4756)
- Wxjghzv.exe (PID: 3304)
- Oxpfrhovopa.exe (PID: 2040)
- Lbmkq.exe (PID: 1532)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
Reads Environment values
- NewTextDocument.exe (PID: 4896)
Checks supported languages
- NewTextDocument.exe (PID: 4896)
- welcome.exe (PID: 5176)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Cjahwaqslw.exe (PID: 1116)
- Gfrzkndk.exe (PID: 4756)
- Oxpfrhovopa.exe (PID: 2040)
- Wxjghzv.exe (PID: 3304)
- Lbmkq.exe (PID: 1532)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
Reads the machine GUID from the registry
- NewTextDocument.exe (PID: 4896)
- Lbmkq.exe (PID: 1532)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Cjahwaqslw.exe (PID: 1116)
- Gfrzkndk.exe (PID: 4756)
- Wxjghzv.exe (PID: 3304)
- Oxpfrhovopa.exe (PID: 2040)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
Reads the software policy settings
- NewTextDocument.exe (PID: 4896)
Process checks computer location settings
- NewTextDocument.exe (PID: 4896)
- Lbmkq.exe (PID: 1532)
- Yeovlfkjp.exe (PID: 6132)
- Jbjqos.exe (PID: 2088)
- Cjahwaqslw.exe (PID: 1116)
- Gfrzkndk.exe (PID: 4756)
- Wxjghzv.exe (PID: 3304)
- Nkrpno.exe (PID: 7312)
- Flambi.exe (PID: 7568)
- Hzfph.exe (PID: 7724)
- Nrbnmllv.exe (PID: 7940)
- Oqssniprb.exe (PID: 7192)
The sample compiled with english language support
- welcome.exe (PID: 5176)
- NewTextDocument.exe (PID: 7324)
- esentutl.exe (PID: 2192)
- Eijhmtanpyiuic.exe (PID: 1628)
- Chddewmrihyrdj.exe (PID: 8784)
- NewTextDocument.exe (PID: 4896)
- r.exe (PID: 8396)
- 6D9F6564C02.exe (PID: 7276)
- 12.exe (PID: 11376)
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 8572)
- NewTextDocument.exe (PID: 8892)
- cbot.exe (PID: 8424)
- raw_cbot.exe (PID: 1512)
- cbot_debug.exe (PID: 3992)
- Quodlibet.exe (PID: 6216)
- welcome.exe (PID: 9596)
- raw_cbot_debug.exe (PID: 7984)
- Alli_AI_stable_latest_release_ver_801_Setup_win.tmp (PID: 11656)
- addon2.exe (PID: 6700)
- Gamma_app_stable_vers_107_2_setup_proVer%20(8).tmp (PID: 11276)
Create files in a temporary directory
- welcome.exe (PID: 5176)
Creates files or folders in the user directory
- Oxpfrhovopa.exe (PID: 2040)
Launch of the file from Registry key
- Oxpfrhovopa.exe (PID: 2040)
Manual execution by a user
- Oxpfrhovopa.exe (PID: 7260)
- Oxpfrhovopa.exe (PID: 7284)
- Oxpfrhovopa.exe (PID: 7296)
- Oxpfrhovopa.exe (PID: 7272)
- Oxpfrhovopa.exe (PID: 7320)
- Oxpfrhovopa.exe (PID: 7372)
- Oxpfrhovopa.exe (PID: 7416)
- Oxpfrhovopa.exe (PID: 7352)
- Oxpfrhovopa.exe (PID: 7404)
- Oxpfrhovopa.exe (PID: 7428)
- Taskmgr.exe (PID: 8020)
- Taskmgr.exe (PID: 8156)
- InstallUtil.exe (PID: 7512)
- InstallUtil.exe (PID: 8964)
- InstallUtil.exe (PID: 8620)
- InstallUtil.exe (PID: 8792)
- InstallUtil.exe (PID: 8828)
- InstallUtil.exe (PID: 8944)
- InstallUtil.exe (PID: 8884)
- InstallUtil.exe (PID: 8988)
- InstallUtil.exe (PID: 9064)
- InstallUtil.exe (PID: 9032)
- InstallUtil.exe (PID: 9184)
- InstallUtil.exe (PID: 9120)
- InstallUtil.exe (PID: 9160)
- InstallUtil.exe (PID: 8196)
- InstallUtil.exe (PID: 8396)
- InstallUtil.exe (PID: 8084)
- InstallUtil.exe (PID: 8544)
- InstallUtil.exe (PID: 8316)
- InstallUtil.exe (PID: 8068)
- InstallUtil.exe (PID: 8736)
- InstallUtil.exe (PID: 3024)
- InstallUtil.exe (PID: 8896)
- InstallUtil.exe (PID: 9008)
- InstallUtil.exe (PID: 8800)
- InstallUtil.exe (PID: 9424)
- InstallUtil.exe (PID: 9564)
- InstallUtil.exe (PID: 9596)
- InstallUtil.exe (PID: 9776)
- InstallUtil.exe (PID: 9636)
- InstallUtil.exe (PID: 9672)
- InstallUtil.exe (PID: 9700)
- InstallUtil.exe (PID: 9740)
- InstallUtil.exe (PID: 9920)
- InstallUtil.exe (PID: 9784)
- InstallUtil.exe (PID: 9832)
- InstallUtil.exe (PID: 9888)
- InstallUtil.exe (PID: 10036)
- InstallUtil.exe (PID: 10236)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 9084)
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 8572)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 8156)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- Lbmkq.exe (PID: 1532)
- Cjahwaqslw.exe (PID: 1116)
- Taskmgr.exe (PID: 8156)
.NET Reactor protector has been detected
- Lbmkq.exe (PID: 1532)
- Cjahwaqslw.exe (PID: 1116)
PyInstaller has been detected (YARA)
- welcome.exe (PID: 5176)
Executable content was dropped or overwritten
- msiexec.exe (PID: 9056)
- msiexec.exe (PID: 8996)
FLEETDECK has been detected
- msiexec.exe (PID: 9056)
Attempting to use instant messaging service
- oihFon.exe (PID: 1168)
- svchost.exe (PID: 2196)
- RegSvcs.exe (PID: 9800)
- RegSvcs.exe (PID: 6004)
- RegSvcs.exe (PID: 7020)
- RegSvcs.exe (PID: 4948)
- RegSvcs.exe (PID: 2384)
Manages system restore points
- SrTasks.exe (PID: 7964)
Application launched itself
- chrome.exe (PID: 8632)
- chrome.exe (PID: 4464)
- chrome.exe (PID: 8288)
- chrome.exe (PID: 7488)
- chrome.exe (PID: 7788)
- chrome.exe (PID: 3992)
- chrome.exe (PID: 2656)
- chrome.exe (PID: 9876)
- chrome.exe (PID: 11012)
- chrome.exe (PID: 5308)
- chrome.exe (PID: 10968)
- chrome.exe (PID: 11960)
- chrome.exe (PID: 8136)
- chrome.exe (PID: 9680)
- chrome.exe (PID: 10540)
The sample compiled with chinese language support
- NewTextDocument.exe (PID: 8892)
- NewTextDocument.exe (PID: 7324)
- NewTextDocument.exe (PID: 9928)
- NewTextDocument.exe (PID: 4896)
- svchost.exe (PID: 9588)
- %E7%94%9F%E6%AD%BB%E7%8B%99%E5%87%BB2.exe (PID: 9920)
- bd.exe (PID: 6760)
The sample compiled with turkish language support
- NewTextDocument.exe (PID: 4896)
- NewTextDocument.exe (PID: 8572)
- Server1.exe (PID: 9648)
- NewTextDocument.exe (PID: 9928)
- Synaptics.exe (PID: 9448)
Connects to unusual port
- iexplore.exe (PID: 10580)
AutoHotkey executable
- NewTextDocument.exe (PID: 9928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 16:32:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
737
Monitored processes
552
Malicious processes
52
Suspicious processes
34
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "C:\Users\admin\Desktop\a\agodee.exe" | C:\Users\admin\Desktop\a\agodee.exe | NewTextDocument.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop\a\TiWorker.exe" | C:\Users\admin\Desktop\a\TiWorker.exe | NewTextDocument.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0xac,0x228,0x7ffc885cdc40,0x7ffc885cdc4c,0x7ffc885cdc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 660 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\5bt2wnrc.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\Desktop\a\bfile.exe" | C:\Users\admin\Desktop\a\bfile.exe | NewTextDocument.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: VNZXV554 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 732 | C:\WINDOWS\system32\cmd.exe /c ping -n 2 127.0.0.1 > nul && del C:\Users\admin\Desktop\a\_CACHE~2.EXE > nul | C:\Windows\SysWOW64\cmd.exe | ._cache_Server.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225477 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Users\admin\Desktop\a\addon2.exe" install | C:\Users\admin\Desktop\a\addon2.exe | addon2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: User OOBE Broker Version: 10.0.26100.3624 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | "C:\Users\admin\Desktop\a\remcos_a.exe" | C:\Users\admin\Desktop\a\remcos_a.exe | — | NewTextDocument.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3 Modules
| |||||||||||||||
Total events
325 671
Read events
323 882
Write events
1 721
Delete events
68
Modification events
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4896) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
565
Suspicious files
97
Text files
1 781
Unknown types
85
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4896 | NewTextDocument.exe | C:\Users\admin\Desktop\a\Lbmkq.exe | executable | |
MD5:310E186513483C536DCEF76D30CCA4BE | SHA256:757AAAB05424245B864102973A531D08265BD975CD5BAC14C058C8B6CA21DC9A | |||
| 4896 | NewTextDocument.exe | C:\Users\admin\Desktop\a\welcome.exe | executable | |
MD5:2345706875DE8828A9A29345CDF19043 | SHA256:08F05C275042890C674C06299F21542B706C1633DB09DDD609A1449587A9FB3E | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_tcl_data\clock.tcl | text | |
MD5:31BB1CACF5D128F77C0922800D3E111A | SHA256:BD1C2DC481A582EF9EAB301468EC7E7C3A284C57617FB2F4A8A97C22576FC762 | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_tcl_data\encoding\big5.enc | text | |
MD5:41A874778111CC218BD421CF9C795EC2 | SHA256:AD1ED201B69855BFD353BF969DFC55576DA35A963ABF1BF7FC6D8B5142A61A61 | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_tcl_data\encoding\ascii.enc | text | |
MD5:9E3A454FA480E9A99D2D5ACDAA775233 | SHA256:FB87BF197F4F485B08EA81F7534BC07D9C3A538D022424BE11011A1FE3C413FD | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_lzma.pyd | executable | |
MD5:3E73BC69EFB418E76D38BE5857A77027 | SHA256:6F48E7EBA363CB67F3465A6C91B5872454B44FC30B82710DFA4A4489270CE95C | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_tcl_data\encoding\cns11643.enc | text | |
MD5:B6A7C59E6A48D91CC2DBCB2BBA7E4510 | SHA256:8924545CC92584169138AADB64683C07BBF846A57014C2E668D23B63F43F3610 | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_tcl_data\auto.tcl | text | |
MD5:97EFA9EBE840EA051F9706504C8BD783 | SHA256:08113823951619D659EB03A1F6ACD2F9500E1264795219125A5DF7B83CABCB99 | |||
| 5176 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI51762\_decimal.pyd | executable | |
MD5:F465C15E7BACEAC920DC58A5FB922C1C | SHA256:F4A486A0CA6A53659159A404614C7E7EDCCB6BFBCDEB844F6CEE544436A826CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
162
TCP/UDP connections
545
DNS requests
122
Threats
546
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4896 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/SPOOFER-M/welcome.exe | unknown | — | — | unknown |
4896 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/TOR-S/Yeovlfkjp.exe | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4896 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/TOR-R/Lbmkq.exe | unknown | — | — | unknown |
4896 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/TOR-M/Cjahwaqslw.exe | unknown | — | — | unknown |
4896 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/YT-S/Gfrzkndk.exe | unknown | — | — | unknown |
4896 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/CHEATS-M/Jbjqos.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4896 | NewTextDocument.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
4896 | NewTextDocument.exe | 104.194.140.36:443 | — | PONYNET | US | unknown |
4896 | NewTextDocument.exe | 104.194.140.36:80 | — | PONYNET | US | unknown |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4896 | NewTextDocument.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4896 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |