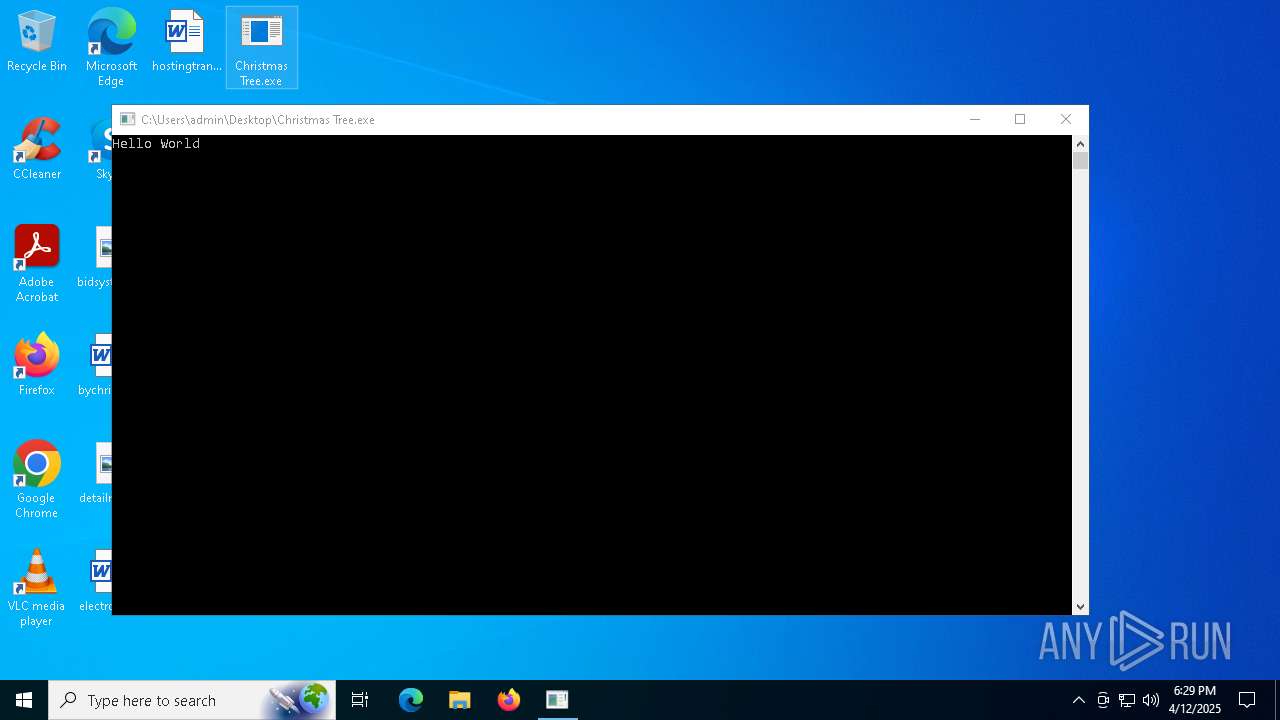
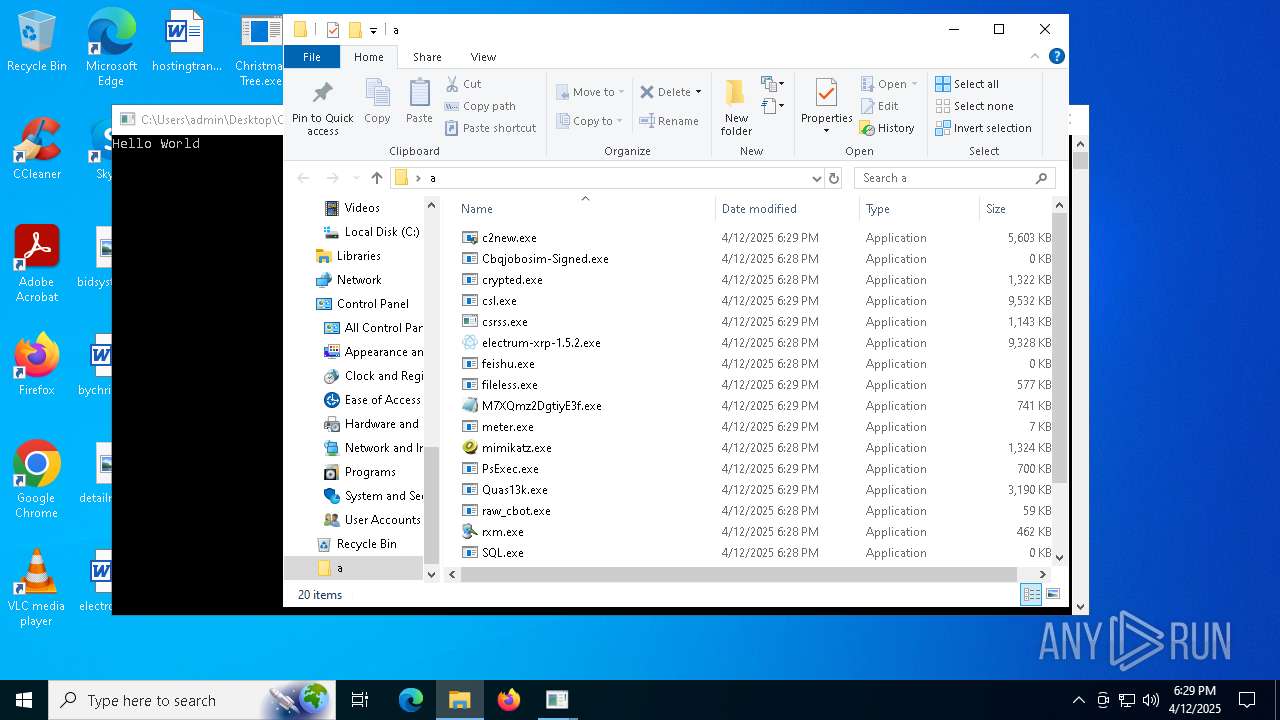
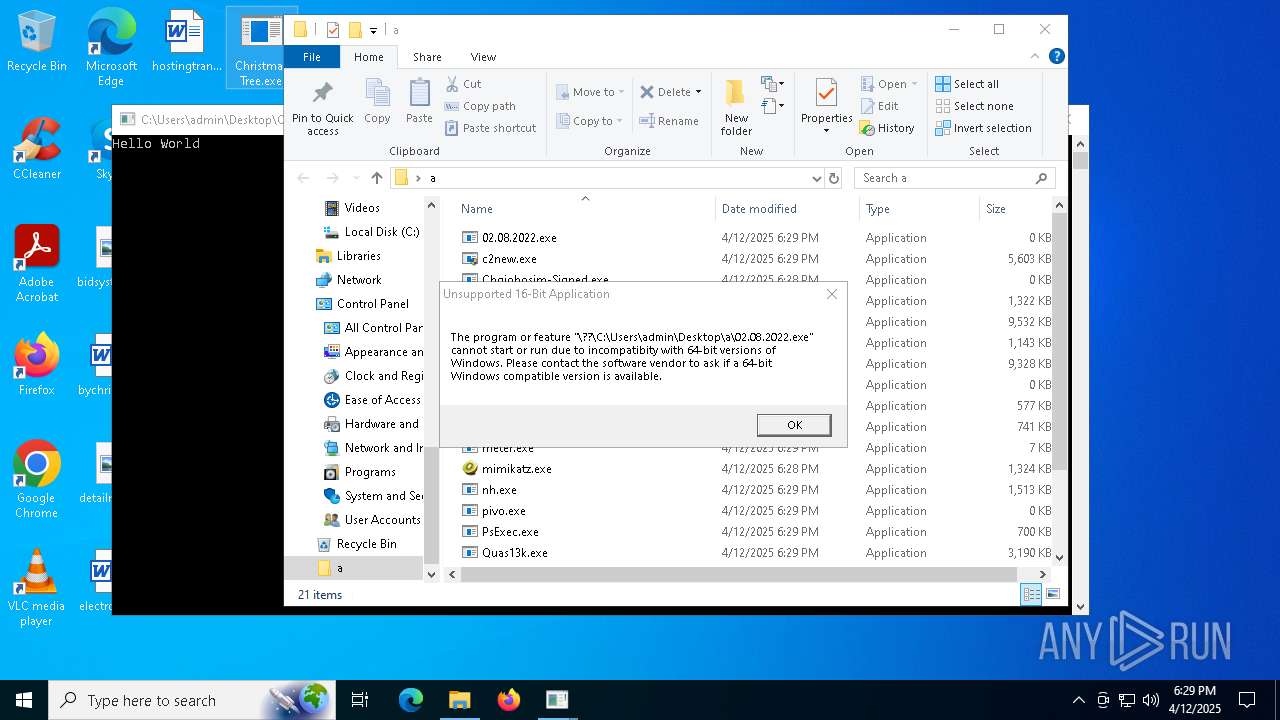
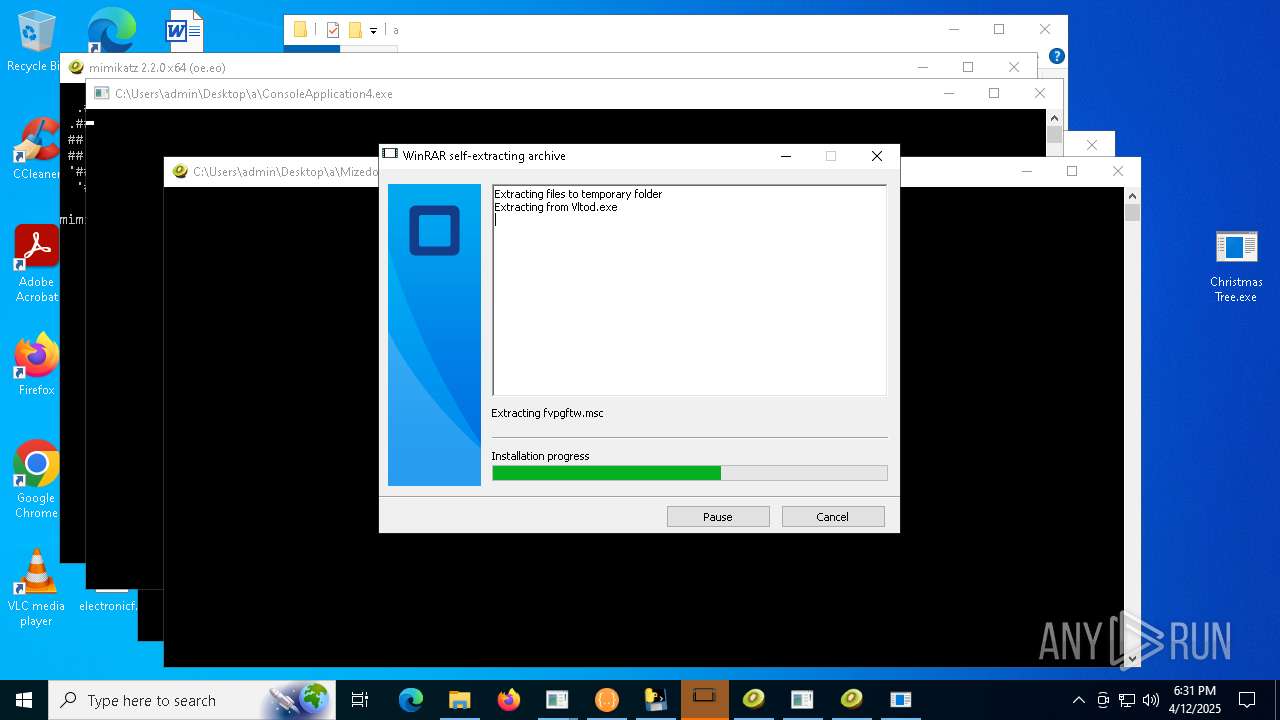
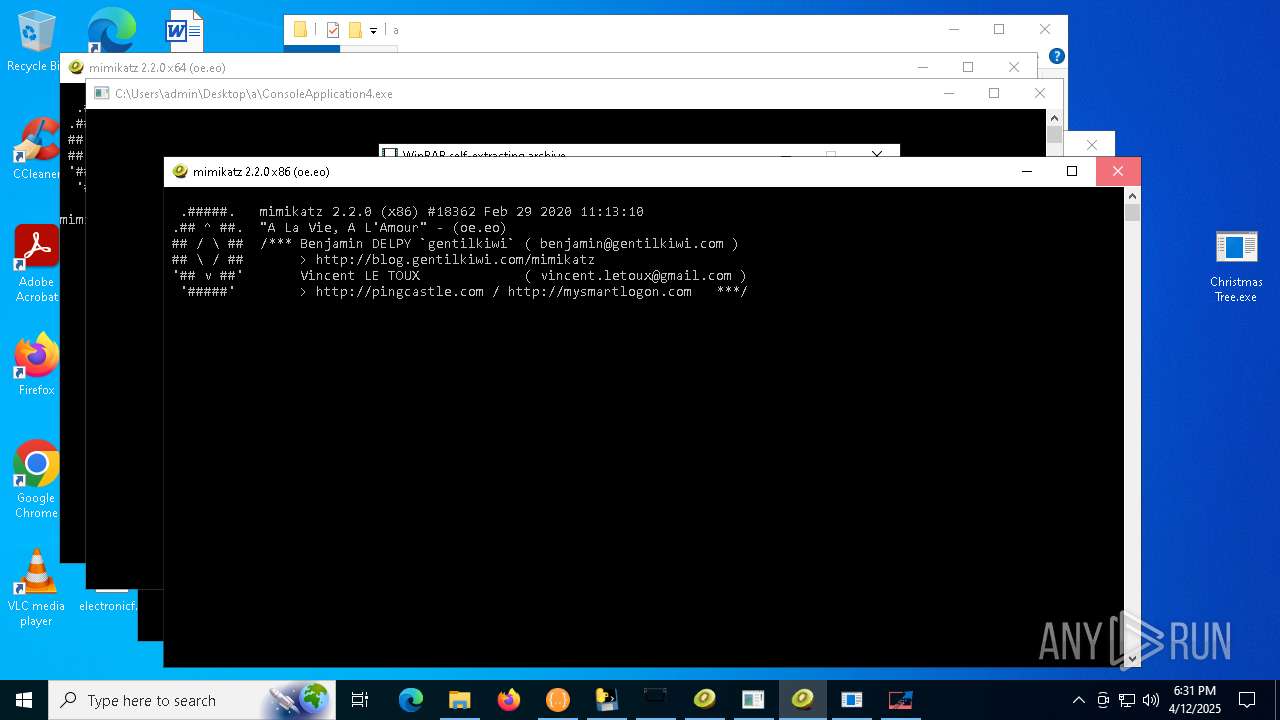
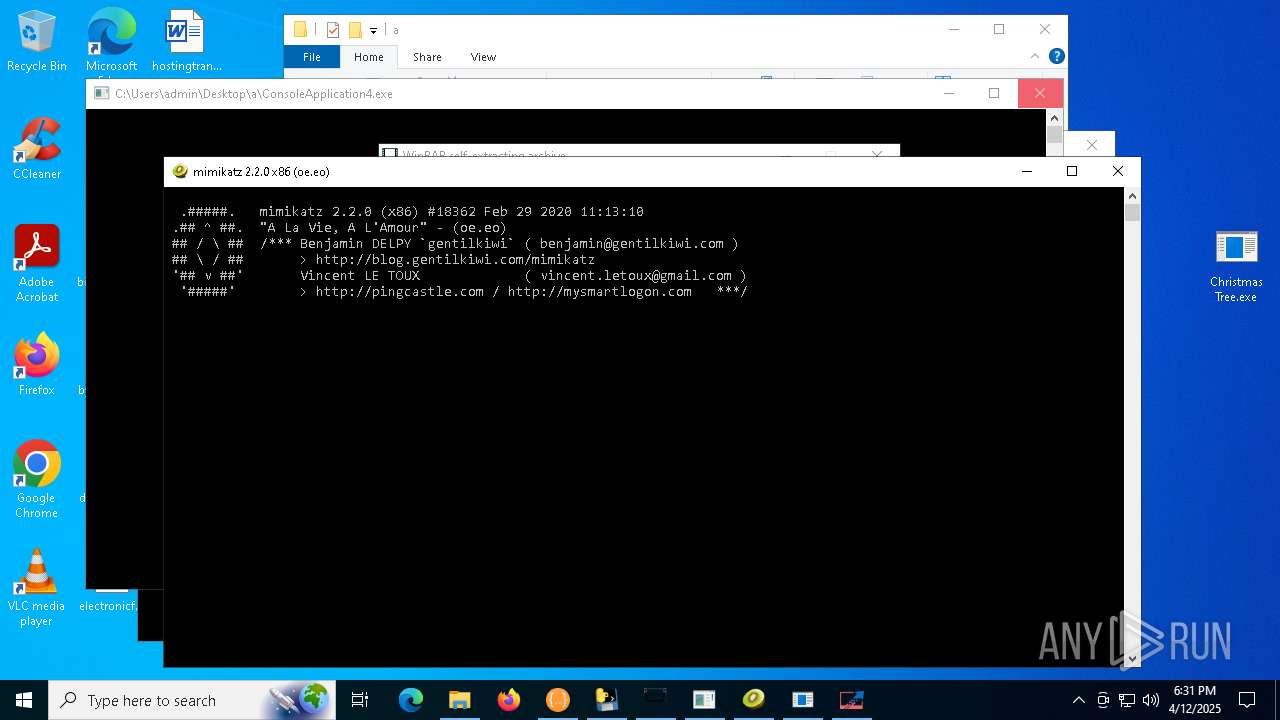
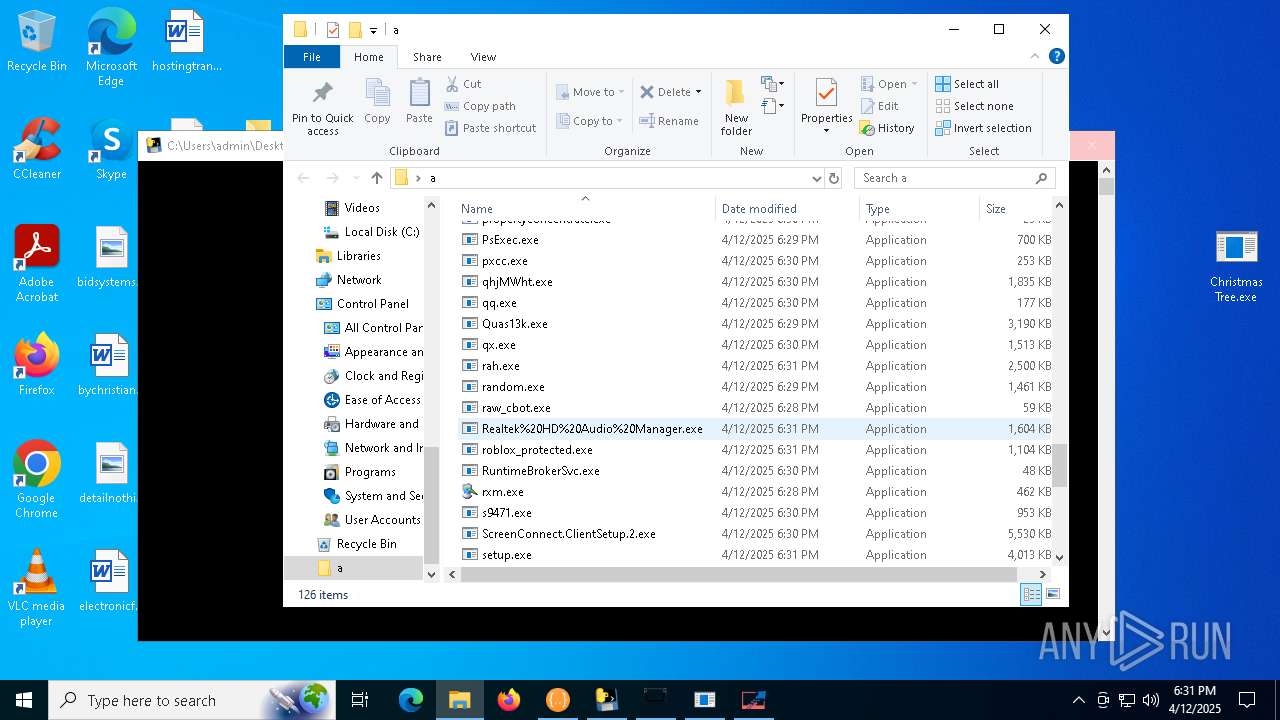
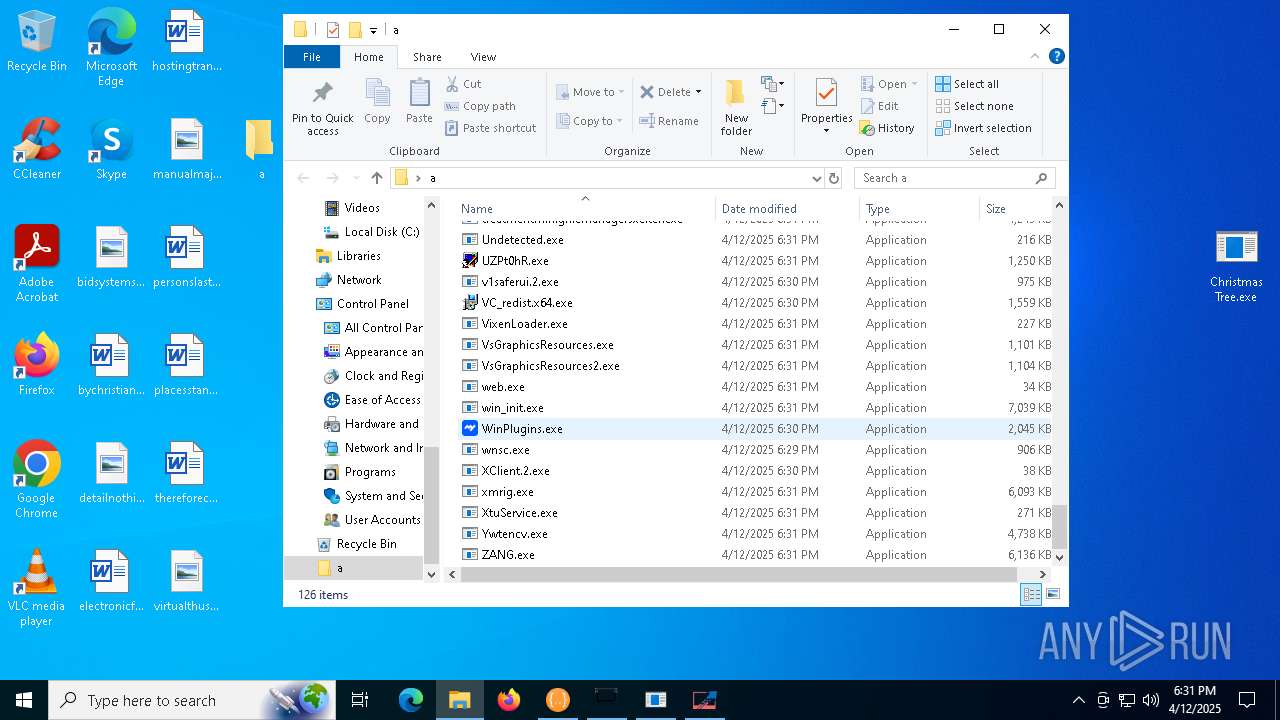
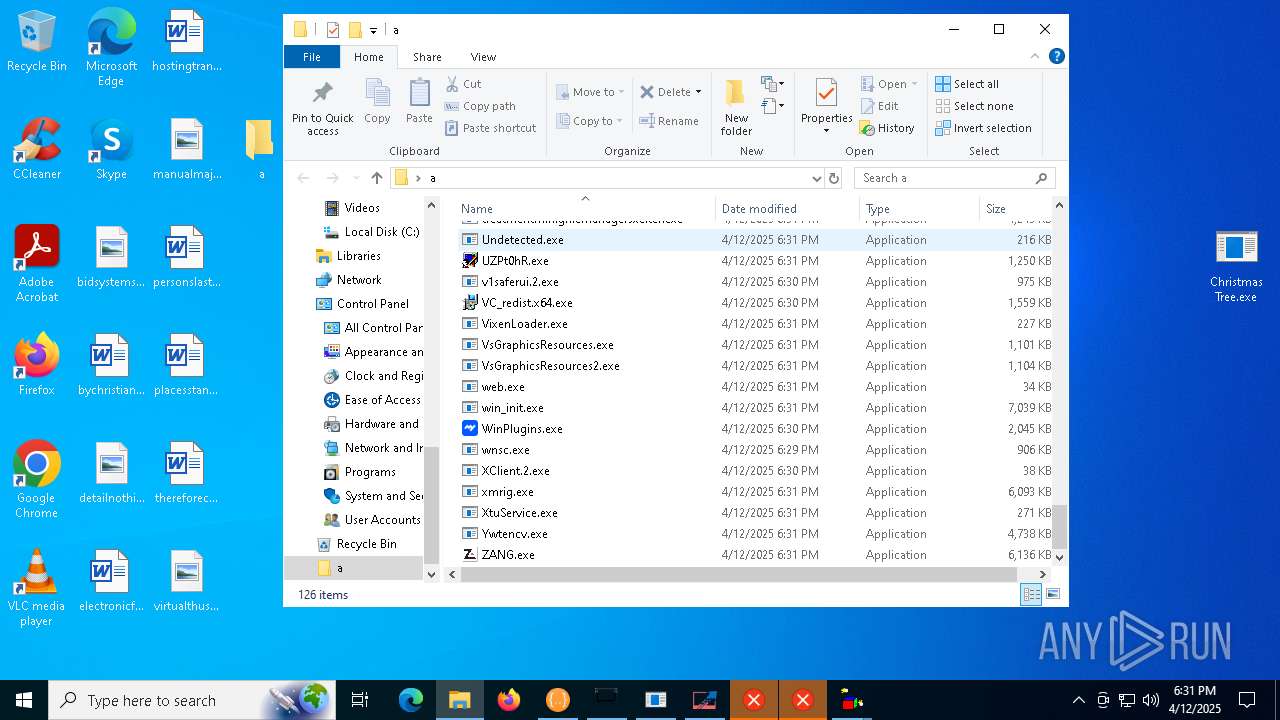
| File name: | Christmas Tree.exe |
| Full analysis: | https://app.any.run/tasks/363b5b8f-e052-4c86-a477-eae1c997975f |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | April 12, 2025, 18:28:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
Executing a file with an untrusted certificate
- rxm.exe (PID: 5964)
- pivo.exe (PID: 7260)
- jokererer.exe (PID: 716)
- crypted.41.exe (PID: 10340)
- LatestLeave.exe (PID: 11028)
- crypted.41.exe (PID: 11312)
- mixseven.exe (PID: 11892)
Create files in the Startup directory
- raw_cbot.exe (PID: 3768)
- XClient.2.exe (PID: 2404)
DCRAT has been detected (YARA)
- Christmas Tree.exe (PID: 1760)
HAUSBOMBER has been detected (YARA)
- Christmas Tree.exe (PID: 1760)
Starts Visual C# compiler
- rxm.exe (PID: 5964)
Run PowerShell with an invisible window
- powershell.exe (PID: 7100)
- powershell.exe (PID: 6248)
- powershell.exe (PID: 1496)
- powershell.exe (PID: 12808)
- powershell.exe (PID: 9056)
Uses Task Scheduler to autorun other applications
- Quas13k.exe (PID: 6596)
- explorer.exe (PID: 6648)
RANSOMWARE has been found (auto)
- Christmas Tree.exe (PID: 6904)
ASYNCRAT has been detected (SURICATA)
- nh.exe (PID: 6412)
- qx.exe (PID: 12572)
LOKIBOT mutex has been found
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- tfqHNUJxJdFp8T0.exe (PID: 8384)
- M7XQmz2DgtiyE3f.exe (PID: 11324)
Steals credentials from Web Browsers
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- qhjMWht.exe (PID: 8424)
- crypted.41.exe (PID: 11312)
- alexx111.exe (PID: 6736)
- 9sWdA2p.exe (PID: 2968)
- MSBuild.exe (PID: 10644)
Actions looks like stealing of personal data
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- s9471.exe (PID: 6404)
- qhjMWht.exe (PID: 8424)
- MSBuild.exe (PID: 9704)
- MSBuild.exe (PID: 2124)
- crypted.41.exe (PID: 11312)
- sharp.exe (PID: 11676)
- MSBuild.exe (PID: 10644)
- 9sWdA2p.exe (PID: 2968)
- alexx111.exe (PID: 6736)
GOBACKDOOR has been found (auto)
- Christmas Tree.exe (PID: 7944)
- HashDrop.exe (PID: 8896)
AMADEY has been found (auto)
- Christmas Tree.exe (PID: 8092)
Scans artifacts that could help determine the target
- M7XQmz2DgtiyE3f.exe (PID: 8008)
GENERIC has been found (auto)
- Christmas Tree.exe (PID: 7560)
- bot.exe (PID: 11884)
- javaplatform_service.exe (PID: 11428)
- javaservice_update.exe (PID: 4392)
- javaupdater_service.exe (PID: 11088)
- javaplugin_update.exe (PID: 9856)
- Christmas Tree.exe (PID: 6344)
- javasupportw.exe (PID: 12384)
- Christmas Tree.exe (PID: 8236)
- javaplugin.exe (PID: 12484)
- Christmas Tree.exe (PID: 11044)
- javaruntime_service.exe (PID: 12732)
- web.exe (PID: 12584)
- javaplugin.exe (PID: 12968)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 10872)
- mixtwo2.exe (PID: 1788)
- web.exe (PID: 12748)
- javaruntime_platform.exe (PID: 8576)
- javaupdater_service.exe (PID: 12588)
- svchost.exe (PID: 13072)
- javaservice_platform.exe (PID: 6432)
- javasupport.exe (PID: 12700)
- javaplatformw.exe (PID: 10688)
- Christmas Tree.exe (PID: 7640)
- javasupportw.exe (PID: 9864)
- javaplatform.exe (PID: 7548)
- javaruntime_service.exe (PID: 7408)
- svchost015.exe (PID: 12720)
- javaservicew.exe (PID: 7624)
Lokibot is detected
- M7XQmz2DgtiyE3f.exe (PID: 8008)
LOKIBOT has been detected (SURICATA)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
Stealers network behavior
- s9471.exe (PID: 6404)
- svchost.exe (PID: 2176)
Connects to the CnC server
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- s9471.exe (PID: 6404)
- svchost.exe (PID: 2176)
STEALC has been detected (SURICATA)
- s9471.exe (PID: 6404)
Changes the autorun value in the registry
- HashDrop.exe (PID: 8896)
- svchost.exe (PID: 13072)
- qq.exe (PID: 8608)
- reg.exe (PID: 11512)
- RuntimeBrokerSvc.exe (PID: 9276)
ADESSTEALER has been found (auto)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8112)
LUMMA has been detected (SURICATA)
- qhjMWht.exe (PID: 8424)
- svchost.exe (PID: 2176)
STEALER has been found (auto)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 7560)
VIDAR has been found (auto)
- Christmas Tree.exe (PID: 6344)
RHADAMANTHYS mutex has been found
- MSBuild.exe (PID: 10368)
- svchost.exe (PID: 10692)
VIDAR mutex has been found
- MSBuild.exe (PID: 10644)
- MSBuild.exe (PID: 11628)
Adds path to the Windows Defender exclusion list
- v1saferui.2.exe (PID: 9460)
Changes Windows Defender settings
- v1saferui.2.exe (PID: 9460)
ASYNCRAT has been found (auto)
- Christmas Tree.exe (PID: 8768)
- XClient.2.exe (PID: 2404)
LUMMA mutex has been found
- qhjMWht.exe (PID: 8424)
- MSBuild.exe (PID: 9704)
- MSBuild.exe (PID: 2124)
- crypted.41.exe (PID: 11312)
- alexx111.exe (PID: 6736)
- 9sWdA2p.exe (PID: 2968)
LUMMA has been found (auto)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 4316)
- s9471.exe (PID: 6404)
RAT has been found (auto)
- WinPlugins.exe (PID: 8076)
- Christmas Tree.exe (PID: 9736)
- neratochka.exe (PID: 12056)
SALATSTEALER has been found (auto)
- Christmas Tree.exe (PID: 10168)
Bypass execution policy to execute commands
- powershell.exe (PID: 12808)
Changes powershell execution policy (Bypass)
- propertyconcentrate.exe (PID: 12256)
SVCSTEALER mutex has been found
- qq.exe (PID: 8608)
Vulnerable driver has been detected
- updater.exe (PID: 7912)
GCLEANER has been detected (SURICATA)
- svchost015.exe (PID: 12720)
Starts CertUtil for downloading files
- cmd.exe (PID: 11068)
SUSPICIOUS
Process requests binary or script from the Internet
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- Christmas Tree.exe (PID: 6904)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10168)
Executable content was dropped or overwritten
- Christmas Tree.exe (PID: 5048)
- raw_cbot.exe (PID: 3768)
- csc.exe (PID: 6456)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- Quas13k.exe (PID: 6596)
- c2new.exe (PID: 6160)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 6344)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7640)
- HashDrop.exe (PID: 8896)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 8236)
- XClient.2.exe (PID: 2404)
- artikelv4%20%281%29.exe (PID: 8684)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9956)
- WinPlugins.exe (PID: 8076)
- bot.exe (PID: 11884)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 9792)
- javaplatform_service.exe (PID: 11428)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 11228)
- Christmas Tree.exe (PID: 10288)
- javaservice_update.exe (PID: 4392)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 9616)
- javaupdater_service.exe (PID: 11088)
- javaplugin_update.exe (PID: 9856)
- javasupportw.exe (PID: 12384)
- Christmas Tree.exe (PID: 9716)
- updater.exe (PID: 7912)
- Christmas Tree.exe (PID: 9104)
- javaplugin.exe (PID: 12484)
- Christmas Tree.exe (PID: 11044)
- javaruntime_service.exe (PID: 12732)
- Amadey.2.exe (PID: 9016)
- web.exe (PID: 12584)
- javaplugin.exe (PID: 12968)
- Christmas Tree.exe (PID: 10872)
- mixtwo2.exe (PID: 1788)
- web.exe (PID: 12748)
- qq.exe (PID: 8608)
- javaruntime_platform.exe (PID: 8576)
- javaupdater_service.exe (PID: 12588)
- XLtod.exe (PID: 4084)
- rtsf.exe (PID: 11888)
- DriverFixerProSetup_STD-SILENT.3.exe (PID: 8204)
- javaservice_platform.exe (PID: 6432)
- Christmas Tree.exe (PID: 7884)
- VC_redist.x64.exe (PID: 12300)
- javasupport.exe (PID: 12700)
- Christmas Tree.exe (PID: 10020)
- OOBebroker.exe (PID: 12960)
- javaplatformw.exe (PID: 10688)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 8632)
- svchost.exe (PID: 13072)
- javasupportw.exe (PID: 9864)
- downloader.exe (PID: 3936)
- javaruntime_service.exe (PID: 7408)
- javaplatform.exe (PID: 7548)
- v1saferui.2.exe (PID: 9460)
- svchosd.exe (PID: 10952)
- RuntimeBrokerSvc.exe (PID: 9276)
- javaservicew.exe (PID: 7624)
- svchost015.exe (PID: 12720)
- neratochka.exe (PID: 12056)
- cmd.exe (PID: 12480)
- s9471.exe (PID: 6404)
- 00000029.exe (PID: 10256)
- ProctorU.1.30.win.07.exe (PID: 9136)
- mto0wf4o.exe (PID: 8000)
- cmd.exe (PID: 6228)
Potential Corporate Privacy Violation
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 9792)
- svchost.exe (PID: 13072)
- svchost015.exe (PID: 12720)
Reads the date of Windows installation
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 7640)
- v1saferui.2.exe (PID: 8884)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9472)
- WinPlugins.exe (PID: 8076)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 10168)
Reads security settings of Internet Explorer
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- Christmas Tree.exe (PID: 8092)
- s9471.exe (PID: 6404)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- v1saferui.2.exe (PID: 8884)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 5912)
- MSBuild.exe (PID: 10644)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 10020)
- WinPlugins.exe (PID: 8076)
- Christmas Tree.exe (PID: 9736)
- Amadey.2.exe (PID: 9016)
- LatestLeave.exe (PID: 11028)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 9792)
- HHH.exe (PID: 12472)
- Christmas Tree.exe (PID: 10100)
- InstructionalPostings.exe (PID: 2124)
- Christmas Tree.exe (PID: 10168)
- svchosd.exe (PID: 10952)
- Christmas Tree.exe (PID: 7560)
- svchost015.exe (PID: 12720)
- launcher.exe (PID: 5924)
- VC_redist.x64.exe (PID: 12300)
- ScreenConnect.ClientSetup.2.exe (PID: 11464)
- tool.exe (PID: 11516)
- downloader.exe (PID: 3936)
- OOBebroker.exe (PID: 12960)
- rtsf.exe (PID: 11888)
- XLtod.exe (PID: 4084)
Process drops legitimate windows executable
- Christmas Tree.exe (PID: 5048)
- raw_cbot.exe (PID: 3768)
- artikelv4%20%281%29.exe (PID: 8684)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9792)
- qq.exe (PID: 8608)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 10020)
Connects to the server without a host name
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7560)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- s9471.exe (PID: 6404)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10168)
- svchost.exe (PID: 13072)
- svchost015.exe (PID: 12720)
Starts a Microsoft application from unusual location
- raw_cbot.exe (PID: 3768)
- crypted.exe (PID: 7240)
- UZPt0hR.exe (PID: 12068)
- qq.exe (PID: 8608)
- UZPt0hR.exe (PID: 6916)
Connects to unusual port
- raw_cbot.exe (PID: 3768)
- svchost.exe (PID: 6856)
- meter.exe (PID: 7072)
- explorer.exe (PID: 6648)
- Christmas Tree.exe (PID: 6520)
- powershell.exe (PID: 6248)
- nh.exe (PID: 6412)
- HashDrop.exe (PID: 8896)
- XClient.2.exe (PID: 2404)
- Christmas Tree.exe (PID: 8972)
- qx.exe (PID: 12572)
Uses .NET C# to load dll
- rxm.exe (PID: 5964)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4124)
- updater.exe (PID: 7912)
- tgvazx.exe (PID: 12704)
BASE64 encoded PowerShell command has been detected
- fileless.exe (PID: 6984)
- powershell.exe (PID: 7100)
Base64-obfuscated command line is found
- fileless.exe (PID: 6984)
- powershell.exe (PID: 7100)
Starts POWERSHELL.EXE for commands execution
- fileless.exe (PID: 6984)
- powershell.exe (PID: 7100)
- v1saferui.2.exe (PID: 9460)
- propertyconcentrate.exe (PID: 12256)
Application launched itself
- powershell.exe (PID: 7100)
- M7XQmz2DgtiyE3f.exe (PID: 6936)
- s9471.exe (PID: 6196)
- tfqHNUJxJdFp8T0.exe (PID: 7416)
- v1saferui.2.exe (PID: 8884)
- crypted.41.exe (PID: 10340)
- M7XQmz2DgtiyE3f.exe (PID: 8840)
- installsbot.crypt.exe (PID: 11768)
- lkkkkk.exe (PID: 12156)
- alexx111.exe (PID: 12260)
- installer_ver19.02.exe (PID: 12252)
- installer_ver12.22.exe (PID: 5928)
- taskhostw.exe (PID: 5800)
- artikelv4%20%281%29.exe (PID: 8684)
The process creates files with name similar to system file names
- Christmas Tree.exe (PID: 6904)
- Quas13k.exe (PID: 6596)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 8092)
- OOBebroker.exe (PID: 12960)
- svchosd.exe (PID: 10952)
PSEXEC has been detected
- PsExec.exe (PID: 6372)
Starts itself from another location
- Quas13k.exe (PID: 6596)
- bot.exe (PID: 11884)
- javaplatform_service.exe (PID: 11428)
- javaservice_update.exe (PID: 4392)
- javaupdater_service.exe (PID: 11088)
- javaplugin_update.exe (PID: 9856)
- javasupportw.exe (PID: 12384)
- javaplugin.exe (PID: 12484)
- javaruntime_service.exe (PID: 12732)
- javaplugin.exe (PID: 12968)
- javaruntime_platform.exe (PID: 8576)
- javaupdater_service.exe (PID: 12588)
- Amadey.2.exe (PID: 9016)
- javaservice_platform.exe (PID: 6432)
- javasupport.exe (PID: 12700)
- javaplatformw.exe (PID: 10688)
- javasupportw.exe (PID: 9864)
- javaplatform.exe (PID: 7548)
- javaruntime_service.exe (PID: 7408)
Probably fake Windows Update
- cmd.exe (PID: 2420)
- cmd.exe (PID: 12480)
- reg.exe (PID: 11512)
Starts CMD.EXE for commands execution
- wnsc.exe (PID: 7004)
- LatestLeave.exe (PID: 11028)
- InstructionalPostings.exe (PID: 2124)
- launcher.exe (PID: 5924)
- downloader.exe (PID: 3936)
- svchost.exe (PID: 13072)
- RuntimeBrokerSvc.exe (PID: 9276)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2420)
- cmd.exe (PID: 12480)
Hides command output
- cmd.exe (PID: 2420)
- cmd.exe (PID: 12480)
Contacting a server suspected of hosting an CnC
- nh.exe (PID: 6412)
- s9471.exe (PID: 6404)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- qhjMWht.exe (PID: 8424)
- svchost.exe (PID: 2176)
- qx.exe (PID: 12572)
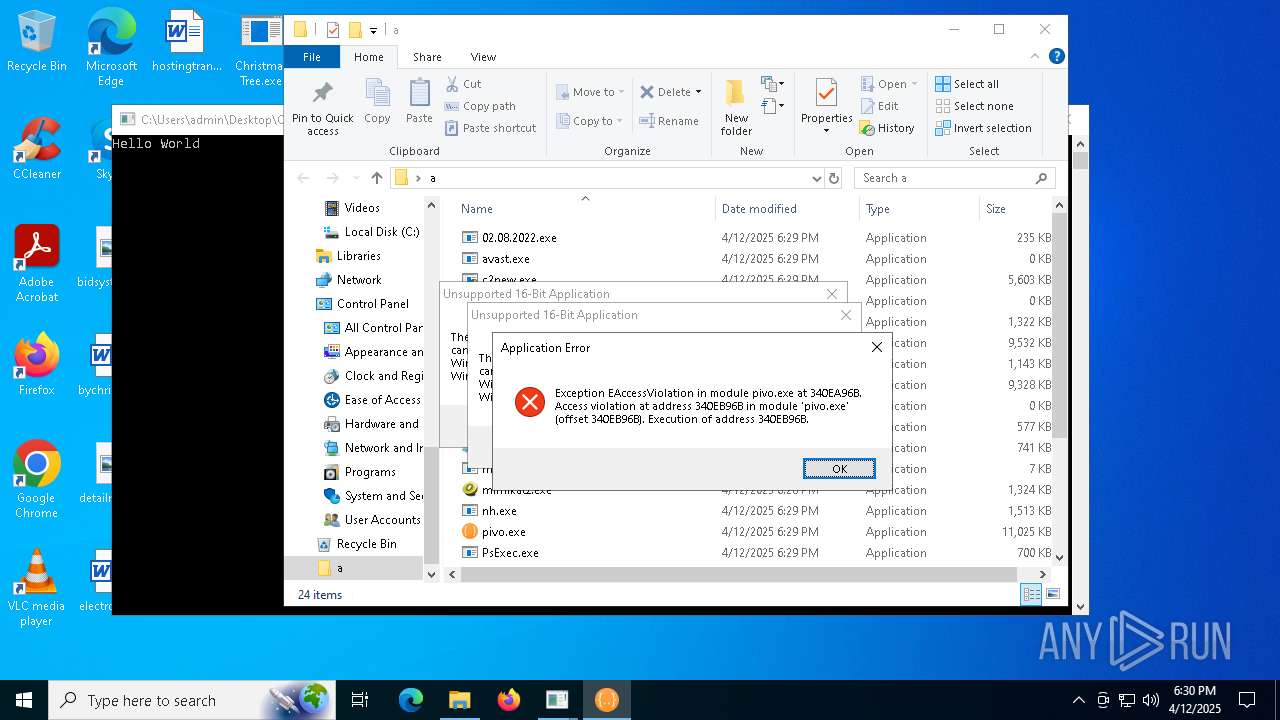
Executes application which crashes
- csrss.exe (PID: 6456)
- pivo.exe (PID: 7260)
- MSBuild.exe (PID: 10368)
- installsbot.crypt.exe (PID: 11768)
- alexx111.exe (PID: 12260)
- Mizedo.exe (PID: 12460)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7624)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 7616)
- cmd.exe (PID: 1796)
Reads the BIOS version
- qhjMWht.exe (PID: 8424)
- mixtwo2.exe (PID: 1788)
Searches for installed software
- s9471.exe (PID: 6404)
- MSBuild.exe (PID: 9704)
- MSBuild.exe (PID: 2124)
- MSBuild.exe (PID: 10644)
- qhjMWht.exe (PID: 8424)
- crypted.41.exe (PID: 11312)
- alexx111.exe (PID: 6736)
- 9sWdA2p.exe (PID: 2968)
The process checks if it is being run in the virtual environment
- Christmas Tree.exe (PID: 8460)
- svchost.exe (PID: 10692)
Script adds exclusion path to Windows Defender
- v1saferui.2.exe (PID: 9460)
The process bypasses the loading of PowerShell profile settings
- v1saferui.2.exe (PID: 9460)
- propertyconcentrate.exe (PID: 12256)
Checks for external IP
- build.exe (PID: 9588)
- svchost.exe (PID: 2176)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- sharp.exe (PID: 11676)
- HHH.exe (PID: 12472)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 11024)
- MSBuild.exe (PID: 10340)
- MSBuild.exe (PID: 10568)
- MSBuild.exe (PID: 10644)
- 9sWdA2p.exe (PID: 2968)
The process drops C-runtime libraries
- artikelv4%20%281%29.exe (PID: 8684)
Process drops python dynamic module
- artikelv4%20%281%29.exe (PID: 8684)
Possible Social Engineering Attempted
- svchost.exe (PID: 2176)
Possibly malicious use of IEX has been detected
- propertyconcentrate.exe (PID: 12256)
Executes script without checking the security policy
- powershell.exe (PID: 12808)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 7912)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2420)
Executing commands from a ".bat" file
- LatestLeave.exe (PID: 11028)
- InstructionalPostings.exe (PID: 2124)
- downloader.exe (PID: 3936)
- svchost.exe (PID: 13072)
- RuntimeBrokerSvc.exe (PID: 9276)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6228)
Modifies existing scheduled task
- schtasks.exe (PID: 7500)
- schtasks.exe (PID: 11208)
- schtasks.exe (PID: 1940)
- schtasks.exe (PID: 9340)
- schtasks.exe (PID: 9820)
Probably fake Windows Update file has been dropped
- cmd.exe (PID: 12480)
INFO
Reads the computer name
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- mimikatz.exe (PID: 2800)
- MSBuild.exe (PID: 1616)
- PLUGScheduler.exe (PID: 4124)
- Christmas Tree.exe (PID: 6520)
- fileless.exe (PID: 6984)
- Christmas Tree.exe (PID: 6904)
- PsExec.exe (PID: 6372)
- Quas13k.exe (PID: 6596)
- explorer.exe (PID: 6648)
- M7XQmz2DgtiyE3f.exe (PID: 6936)
- wnsc.exe (PID: 7004)
- taskhostw.exe (PID: 5800)
- nh.exe (PID: 6412)
- pivo.exe (PID: 7260)
- tfqHNUJxJdFp8T0.exe (PID: 7416)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 7944)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7884)
- s9471.exe (PID: 6404)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 8632)
- M7XQmz2DgtiyE3f.exe (PID: 8840)
- qhjMWht.exe (PID: 8424)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 8972)
- Amadey.2.exe (PID: 9016)
- v1saferui.2.exe (PID: 8884)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 9344)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 10288)
- MSBuild.exe (PID: 10396)
- Christmas Tree.exe (PID: 10576)
- MSBuild.exe (PID: 10568)
- Christmas Tree.exe (PID: 10872)
- MSBuild.exe (PID: 11024)
- Christmas Tree.exe (PID: 11044)
- MSBuild.exe (PID: 10340)
- Christmas Tree.exe (PID: 11228)
- MSBuild.exe (PID: 10644)
- MSBuild.exe (PID: 9276)
- MSBuild.exe (PID: 2624)
- XClient.2.exe (PID: 2404)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- MSBuild.exe (PID: 9704)
- MSBuild.exe (PID: 11236)
- artikelv4%20%281%29.exe (PID: 8684)
- MSBuild.exe (PID: 3980)
- MSBuild.exe (PID: 10660)
- MSBuild.exe (PID: 11104)
- MSBuild.exe (PID: 2124)
- crypted.41.exe (PID: 11312)
- MSBuild.exe (PID: 11292)
- MSBuild.exe (PID: 10568)
- MSBuild.exe (PID: 11628)
- MSBuild.exe (PID: 11424)
- sharp.exe (PID: 11676)
- installsbot.crypt.exe (PID: 11768)
- LatestLeave.exe (PID: 11028)
- installsbot.crypt.exe (PID: 11960)
- WinPlugins.exe (PID: 8076)
- lkkkkk.exe (PID: 11368)
- tool.exe (PID: 11516)
- alexx111.exe (PID: 12260)
- propertyconcentrate.exe (PID: 12256)
- default.2.exe (PID: 10944)
- InstructionalPostings.exe (PID: 2124)
- ScreenConnect.ClientSetup.2.exe (PID: 11464)
- mixseven.exe (PID: 11892)
- alexx111.exe (PID: 6736)
- 9sWdA2p.exe (PID: 2968)
- neratochka.exe (PID: 12056)
- invoice.exe (PID: 10800)
- ProctorU.1.30.win.07.exe (PID: 9136)
- HHH.exe (PID: 12472)
- qx.exe (PID: 12572)
- Vltod.exe (PID: 11980)
- VC_redist.x64.exe (PID: 12300)
- XLtod.exe (PID: 4084)
- rtsf.exe (PID: 11888)
- UZPt0hR.exe (PID: 12068)
- mixtwo2.exe (PID: 1788)
- web.exe (PID: 12584)
- pxcc.exe (PID: 12828)
- svchosd.exe (PID: 10952)
- Handicap_NoProtect_Ghost.exe (PID: 13156)
- RuntimeBrokerSvc.exe (PID: 9276)
- web.exe (PID: 12748)
- newnoadminpc.exe (PID: 5388)
- installer_ver12.22.exe (PID: 12996)
- installer_ver19.02.exe (PID: 13164)
- launcher.exe (PID: 5924)
- svchost015.exe (PID: 12720)
- DriverFixerProSetup_STD-SILENT.3.exe (PID: 8204)
- tzutil.exe (PID: 9976)
- downloader.exe (PID: 3936)
- VC_redist.x64.exe (PID: 9140)
- mto0wf4o.exe (PID: 8000)
- 00000029.exe (PID: 10256)
Disables trace logs
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- powershell.exe (PID: 6248)
- wnsc.exe (PID: 7004)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 9792)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 10288)
- Christmas Tree.exe (PID: 10576)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 11228)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- sharp.exe (PID: 11676)
- HHH.exe (PID: 12472)
- svchosd.exe (PID: 10952)
Checks proxy server information
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- powershell.exe (PID: 6248)
- wnsc.exe (PID: 7004)
- WerFault.exe (PID: 4828)
- Christmas Tree.exe (PID: 7388)
- WerFault.exe (PID: 7320)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7884)
- s9471.exe (PID: 6404)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9736)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 10288)
- Christmas Tree.exe (PID: 10576)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 11228)
- MSBuild.exe (PID: 10644)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- sharp.exe (PID: 11676)
- svchost015.exe (PID: 12720)
- HHH.exe (PID: 12472)
- svchosd.exe (PID: 10952)
Checks supported languages
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- raw_cbot.exe (PID: 3768)
- cvtres.exe (PID: 5072)
- mimikatz.exe (PID: 2800)
- csc.exe (PID: 6456)
- MSBuild.exe (PID: 1616)
- crypted.exe (PID: 7240)
- Christmas Tree.exe (PID: 6520)
- svchost.exe (PID: 6856)
- fileless.exe (PID: 6984)
- PLUGScheduler.exe (PID: 4124)
- Christmas Tree.exe (PID: 6904)
- csl.exe (PID: 6500)
- Quas13k.exe (PID: 6596)
- PsExec.exe (PID: 6372)
- c2new.exe (PID: 6160)
- taskhostw.exe (PID: 5800)
- wnsc.exe (PID: 7004)
- explorer.exe (PID: 6648)
- M7XQmz2DgtiyE3f.exe (PID: 6936)
- csrss.exe (PID: 6456)
- nh.exe (PID: 6412)
- Christmas Tree.exe (PID: 7388)
- pivo.exe (PID: 7260)
- tfqHNUJxJdFp8T0.exe (PID: 7416)
- updater.exe (PID: 7912)
- Christmas Tree.exe (PID: 7944)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7884)
- s9471.exe (PID: 6196)
- s9471.exe (PID: 6404)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8236)
- tfqHNUJxJdFp8T0.exe (PID: 8384)
- Christmas Tree.exe (PID: 8460)
- qhjMWht.exe (PID: 8424)
- Christmas Tree.exe (PID: 8632)
- M7XQmz2DgtiyE3f.exe (PID: 8840)
- Christmas Tree.exe (PID: 8768)
- HashDrop.exe (PID: 8896)
- Amadey.2.exe (PID: 9016)
- Christmas Tree.exe (PID: 8972)
- v1saferui.2.exe (PID: 8884)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9472)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 10168)
- fff.exe (PID: 7116)
- money.exe (PID: 7164)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9736)
- jokererer.exe (PID: 716)
- MSBuild.exe (PID: 10396)
- Christmas Tree.exe (PID: 10288)
- MSBuild.exe (PID: 10568)
- MSBuild.exe (PID: 10368)
- Christmas Tree.exe (PID: 10872)
- alex12312321.exe (PID: 10976)
- kololololo.exe (PID: 10544)
- Christmas Tree.exe (PID: 10576)
- CCTV_SK8_crypted_LAB.exe (PID: 10696)
- MSBuild.exe (PID: 11024)
- Christmas Tree.exe (PID: 11044)
- installer_ver12.03.exe (PID: 11180)
- v1saferui.2.exe (PID: 9460)
- MSBuild.exe (PID: 10340)
- Christmas Tree.exe (PID: 11228)
- MSBuild.exe (PID: 10644)
- MSBuild.exe (PID: 9276)
- crypted.64.exe (PID: 2984)
- MSBuild.exe (PID: 2624)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- XClient.2.exe (PID: 2404)
- ffffff.exe (PID: 3608)
- MSBuild.exe (PID: 11236)
- alex12321321.exe (PID: 3236)
- MSBuild.exe (PID: 9704)
- artikelv4%20%281%29.exe (PID: 8684)
- mrwipe12312.exe (PID: 9168)
- MSBuild.exe (PID: 3980)
- kollfdsf.exe (PID: 4252)
- alex1212.exe (PID: 4388)
- MSBuild.exe (PID: 10660)
- MSBuild.exe (PID: 11104)
- alex1dskfmdsf.exe (PID: 10368)
- gron12321.exe (PID: 3968)
- MSBuild.exe (PID: 2124)
- LatestLeave.exe (PID: 11028)
- crypted.41.exe (PID: 10340)
- mrwipre12.exe (PID: 8992)
- MSBuild.exe (PID: 10568)
- legendarik.exe (PID: 6328)
- crypted.41.exe (PID: 11312)
- M7XQmz2DgtiyE3f.exe (PID: 11324)
- MSBuild.exe (PID: 11292)
- WinPlugins.exe (PID: 8076)
- MSBuild.exe (PID: 11424)
- MSBuild.exe (PID: 11628)
- crypted.54.exe (PID: 11528)
- sharp.exe (PID: 11676)
- bot.exe (PID: 11884)
- mixseven.exe (PID: 11892)
- installsbot.crypt.exe (PID: 11768)
- lkkkkk.exe (PID: 11368)
- lkkkkk.exe (PID: 12156)
- javaplatform_service.exe (PID: 11428)
- tool.exe (PID: 11516)
- javaservice_update.exe (PID: 4392)
- alexx111.exe (PID: 12260)
- propertyconcentrate.exe (PID: 12256)
- InstructionalPostings.exe (PID: 2124)
- mixtwo2.exe (PID: 1788)
- default.2.exe (PID: 10944)
- 9sWdA2p.exe (PID: 2968)
- ScreenConnect.ClientSetup.2.exe (PID: 11464)
- rtsf.exe (PID: 11888)
- javaupdater_service.exe (PID: 11088)
- Vltod.exe (PID: 11980)
- XLtod.exe (PID: 4084)
- javaplugin_update.exe (PID: 9856)
- alexx111.exe (PID: 6736)
- javasupportw.exe (PID: 12384)
- invoice.exe (PID: 10800)
- neratochka.exe (PID: 12056)
- HHH.exe (PID: 12472)
- javaplugin.exe (PID: 12484)
- ProctorU.1.30.win.07.exe (PID: 9136)
- qx.exe (PID: 12572)
- web.exe (PID: 12584)
- javaruntime_service.exe (PID: 12732)
- UZPt0hR.exe (PID: 12068)
- javaplugin.exe (PID: 12968)
- OOBebroker.exe (PID: 12960)
- pxcc.exe (PID: 12828)
- Handicap_NoProtect_Ghost.exe (PID: 13156)
- svchosd.exe (PID: 10952)
- javaruntime_platform.exe (PID: 8576)
- qq.exe (PID: 8608)
- installsbot.crypt.exe (PID: 11960)
- web.exe (PID: 12748)
- RuntimeBrokerSvc.exe (PID: 9276)
- installer_ver19.02.exe (PID: 12252)
- installer_ver12.22.exe (PID: 5928)
- tgvazx.exe (PID: 12704)
- newnoadminpc.exe (PID: 5388)
- launcher.exe (PID: 5924)
- javaupdater_service.exe (PID: 12588)
- DriverFixerProSetup_STD-SILENT.3.exe (PID: 8204)
- installer_ver12.22.exe (PID: 12996)
- installer_ver19.02.exe (PID: 13164)
- javaservice_platform.exe (PID: 6432)
- javasupport.exe (PID: 12700)
- svchost015.exe (PID: 12720)
- tgvazx.exe (PID: 12308)
- javaplatformw.exe (PID: 10688)
- downloader.exe (PID: 3936)
- javasupportw.exe (PID: 9864)
- VC_redist.x64.exe (PID: 12300)
- javaplatform.exe (PID: 7548)
- tzutil.exe (PID: 9976)
- InstallUtil.exe (PID: 7720)
- expand.exe (PID: 10484)
- Mizedo.exe (PID: 12460)
- VC_redist.x64.exe (PID: 9140)
- javaruntime_service.exe (PID: 7408)
- mto0wf4o.exe (PID: 8000)
- javaservicew.exe (PID: 7624)
- artikelv4%20%281%29.exe (PID: 1700)
- w32tm.exe (PID: 5832)
- taskhostw.exe (PID: 12672)
- 00000029.exe (PID: 10256)
Reads the software policy settings
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6520)
- fileless.exe (PID: 6984)
- Christmas Tree.exe (PID: 6904)
- nh.exe (PID: 6412)
- WerFault.exe (PID: 4828)
- Christmas Tree.exe (PID: 7388)
- WerFault.exe (PID: 7320)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 7884)
- qhjMWht.exe (PID: 8424)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 9792)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 10872)
- MSBuild.exe (PID: 11024)
- MSBuild.exe (PID: 10340)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 11228)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 10020)
- MSBuild.exe (PID: 2624)
- MSBuild.exe (PID: 10396)
- MSBuild.exe (PID: 10568)
- Christmas Tree.exe (PID: 10288)
- Christmas Tree.exe (PID: 10576)
- MSBuild.exe (PID: 9276)
- MSBuild.exe (PID: 9704)
- MSBuild.exe (PID: 3980)
- MSBuild.exe (PID: 11236)
- MSBuild.exe (PID: 10660)
- MSBuild.exe (PID: 11104)
- MSBuild.exe (PID: 2124)
- crypted.41.exe (PID: 11312)
- MSBuild.exe (PID: 10568)
- MSBuild.exe (PID: 11292)
- MSBuild.exe (PID: 11424)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- sharp.exe (PID: 11676)
- MSBuild.exe (PID: 10644)
- installsbot.crypt.exe (PID: 11960)
- lkkkkk.exe (PID: 11368)
- alexx111.exe (PID: 6736)
- 9sWdA2p.exe (PID: 2968)
- invoice.exe (PID: 10800)
- web.exe (PID: 12584)
- qx.exe (PID: 12572)
- web.exe (PID: 12748)
- installer_ver12.22.exe (PID: 12996)
- installer_ver19.02.exe (PID: 13164)
- HHH.exe (PID: 12472)
- svchosd.exe (PID: 10952)
Reads Environment values
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- Quas13k.exe (PID: 6596)
- explorer.exe (PID: 6648)
- nh.exe (PID: 6412)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 10288)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 10576)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11228)
- MSBuild.exe (PID: 10644)
- qx.exe (PID: 12572)
- HHH.exe (PID: 12472)
- svchosd.exe (PID: 10952)
Reads the machine GUID from the registry
- Christmas Tree.exe (PID: 4756)
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- rxm.exe (PID: 5964)
- raw_cbot.exe (PID: 3768)
- csc.exe (PID: 6456)
- MSBuild.exe (PID: 1616)
- Christmas Tree.exe (PID: 6520)
- svchost.exe (PID: 6856)
- fileless.exe (PID: 6984)
- Christmas Tree.exe (PID: 6904)
- Quas13k.exe (PID: 6596)
- nh.exe (PID: 6412)
- wnsc.exe (PID: 7004)
- explorer.exe (PID: 6648)
- M7XQmz2DgtiyE3f.exe (PID: 6936)
- tfqHNUJxJdFp8T0.exe (PID: 7416)
- Christmas Tree.exe (PID: 7388)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8460)
- tfqHNUJxJdFp8T0.exe (PID: 8384)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8632)
- M7XQmz2DgtiyE3f.exe (PID: 8840)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 9792)
- build.exe (PID: 9588)
- Christmas Tree.exe (PID: 10288)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11228)
- Christmas Tree.exe (PID: 10020)
- XClient.2.exe (PID: 2404)
- Christmas Tree.exe (PID: 10576)
- CefSharp.BrowsersSubprocess.exe (PID: 9868)
- taskhostw.exe (PID: 5800)
- M7XQmz2DgtiyE3f.exe (PID: 11324)
- MSBuild.exe (PID: 10644)
- sharp.exe (PID: 11676)
- propertyconcentrate.exe (PID: 12256)
- ScreenConnect.ClientSetup.2.exe (PID: 11464)
- tool.exe (PID: 11516)
- HHH.exe (PID: 12472)
- ProctorU.1.30.win.07.exe (PID: 9136)
- qx.exe (PID: 12572)
- svchosd.exe (PID: 10952)
- newnoadminpc.exe (PID: 5388)
- launcher.exe (PID: 5924)
- RuntimeBrokerSvc.exe (PID: 9276)
- svchost015.exe (PID: 12720)
- InstallUtil.exe (PID: 7720)
- VC_redist.x64.exe (PID: 9140)
- mto0wf4o.exe (PID: 8000)
- 00000029.exe (PID: 10256)
Manual execution by a user
- Christmas Tree.exe (PID: 1760)
- Christmas Tree.exe (PID: 4220)
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6520)
- svchost.exe (PID: 6856)
- Christmas Tree.exe (PID: 6904)
- Christmas Tree.exe (PID: 7388)
- cmd.exe (PID: 7616)
- schtasks.exe (PID: 7624)
- schtasks.exe (PID: 7848)
- schtasks.exe (PID: 7728)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 9104)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 9716)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 9616)
- Christmas Tree.exe (PID: 9956)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9872)
- Christmas Tree.exe (PID: 10168)
- Christmas Tree.exe (PID: 9192)
- Christmas Tree.exe (PID: 9736)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 10288)
- Christmas Tree.exe (PID: 10576)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11228)
- Christmas Tree.exe (PID: 11044)
- svchost.exe (PID: 10692)
- cmd.exe (PID: 1796)
- schtasks.exe (PID: 11900)
- conhost.exe (PID: 12592)
- schtasks.exe (PID: 8908)
- schtasks.exe (PID: 8576)
- schtasks.exe (PID: 10328)
- InstallUtil.exe (PID: 7720)
- schtasks.exe (PID: 12684)
- schtasks.exe (PID: 10900)
- schtasks.exe (PID: 11564)
Creates files or folders in the user directory
- raw_cbot.exe (PID: 3768)
- WerFault.exe (PID: 7320)
- WerFault.exe (PID: 4828)
- explorer.exe (PID: 6648)
- M7XQmz2DgtiyE3f.exe (PID: 8008)
- HashDrop.exe (PID: 8896)
- build.exe (PID: 9588)
- XClient.2.exe (PID: 2404)
- sharp.exe (PID: 11676)
- MSBuild.exe (PID: 10644)
- bot.exe (PID: 11884)
- qq.exe (PID: 8608)
- svchost015.exe (PID: 12720)
- downloader.exe (PID: 3936)
- svchosd.exe (PID: 10952)
- RuntimeBrokerSvc.exe (PID: 9276)
The sample compiled with english language support
- raw_cbot.exe (PID: 3768)
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6904)
- artikelv4%20%281%29.exe (PID: 8684)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10020)
- svchost.exe (PID: 13072)
- mixtwo2.exe (PID: 1788)
- qq.exe (PID: 8608)
- Christmas Tree.exe (PID: 7884)
- XLtod.exe (PID: 4084)
- rtsf.exe (PID: 11888)
- DriverFixerProSetup_STD-SILENT.3.exe (PID: 8204)
- svchosd.exe (PID: 10952)
- ProctorU.1.30.win.07.exe (PID: 9136)
Process checks computer location settings
- Christmas Tree.exe (PID: 5048)
- Christmas Tree.exe (PID: 6520)
- Christmas Tree.exe (PID: 6904)
- Christmas Tree.exe (PID: 8092)
- Christmas Tree.exe (PID: 5912)
- Christmas Tree.exe (PID: 7884)
- Christmas Tree.exe (PID: 7944)
- Christmas Tree.exe (PID: 6344)
- Christmas Tree.exe (PID: 7640)
- v1saferui.2.exe (PID: 8884)
- Christmas Tree.exe (PID: 6440)
- Christmas Tree.exe (PID: 4316)
- Christmas Tree.exe (PID: 8112)
- Christmas Tree.exe (PID: 8236)
- Christmas Tree.exe (PID: 8768)
- Christmas Tree.exe (PID: 7560)
- Christmas Tree.exe (PID: 9344)
- Christmas Tree.exe (PID: 7388)
- Christmas Tree.exe (PID: 8972)
- Christmas Tree.exe (PID: 8408)
- Christmas Tree.exe (PID: 8460)
- Christmas Tree.exe (PID: 7756)
- Christmas Tree.exe (PID: 9260)
- Christmas Tree.exe (PID: 9472)
- Christmas Tree.exe (PID: 10020)
- Christmas Tree.exe (PID: 9104)
- WinPlugins.exe (PID: 8076)
- Christmas Tree.exe (PID: 8632)
- Christmas Tree.exe (PID: 10872)
- Christmas Tree.exe (PID: 11044)
- Christmas Tree.exe (PID: 9792)
- Christmas Tree.exe (PID: 10100)
- Christmas Tree.exe (PID: 10168)
- Amadey.2.exe (PID: 9016)
- LatestLeave.exe (PID: 11028)
- InstructionalPostings.exe (PID: 2124)
- Christmas Tree.exe (PID: 9736)
- launcher.exe (PID: 5924)
- VC_redist.x64.exe (PID: 12300)
- tool.exe (PID: 11516)
- ScreenConnect.ClientSetup.2.exe (PID: 11464)
- downloader.exe (PID: 3936)
- OOBebroker.exe (PID: 12960)
- XLtod.exe (PID: 4084)
- rtsf.exe (PID: 11888)
Create files in a temporary directory
- rxm.exe (PID: 5964)
- csc.exe (PID: 6456)
- cvtres.exe (PID: 5072)
- csrss.exe (PID: 6456)
- c2new.exe (PID: 6160)
- HashDrop.exe (PID: 8896)
- artikelv4%20%281%29.exe (PID: 8684)
- WinPlugins.exe (PID: 8076)
- LatestLeave.exe (PID: 11028)
- InstructionalPostings.exe (PID: 2124)
- Vltod.exe (PID: 11980)
- Amadey.2.exe (PID: 9016)
- tool.exe (PID: 11516)
- ScreenConnect.ClientSetup.2.exe (PID: 11464)
- HHH.exe (PID: 12472)
- XLtod.exe (PID: 4084)
- mixtwo2.exe (PID: 1788)
- svchosd.exe (PID: 10952)
- rtsf.exe (PID: 11888)
- DriverFixerProSetup_STD-SILENT.3.exe (PID: 8204)
- sharp.exe (PID: 11676)
- VC_redist.x64.exe (PID: 12300)
- XClient.2.exe (PID: 2404)
- downloader.exe (PID: 3936)
- expand.exe (PID: 10484)
- svchost.exe (PID: 13072)
- RuntimeBrokerSvc.exe (PID: 9276)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4124)
- c2new.exe (PID: 6160)
- MSBuild.exe (PID: 10644)
- s9471.exe (PID: 6404)
- UZPt0hR.exe (PID: 12068)
- svchost.exe (PID: 13072)
- v1saferui.2.exe (PID: 9460)
Reads mouse settings
- csrss.exe (PID: 6456)
Reads Microsoft Office registry keys
- M7XQmz2DgtiyE3f.exe (PID: 8008)
Reads CPU info
- s9471.exe (PID: 6404)
- build.exe (PID: 9588)
- MSBuild.exe (PID: 10644)
Attempting to use instant messaging service
- MSBuild.exe (PID: 10340)
- MSBuild.exe (PID: 11024)
- MSBuild.exe (PID: 10568)
- 9sWdA2p.exe (PID: 2968)
- svchost.exe (PID: 2176)
- web.exe (PID: 12584)
- web.exe (PID: 12748)
Reads product name
- MSBuild.exe (PID: 10644)
Drops encrypted VBS script (Microsoft Script Encoder)
- XLtod.exe (PID: 4084)
- rtsf.exe (PID: 11888)
- OOBebroker.exe (PID: 12960)
The sample compiled with japanese language support
- updater.exe (PID: 7912)
Changes file name
- cmd.exe (PID: 6228)
The sample compiled with chinese language support
- downloader.exe (PID: 3936)
Reads security settings of Internet Explorer
- svchost.exe (PID: 13072)
Application launched itself
- chrome.exe (PID: 8848)
- chrome.exe (PID: 7536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 16:32:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
659
Monitored processes
382
Malicious processes
102
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 716 | "C:\Users\admin\Desktop\a\jokererer.exe" | C:\Users\admin\Desktop\a\jokererer.exe | — | Christmas Tree.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mimikatz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mrwipe12312.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | alex1dskfmdsf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1348 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | powershell.exe -NoProfile -WindowStyle Hidden -Command "Add-MpPreference -ExclusionPath 'C:\Program Files (x86)'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | v1saferui.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | rxm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 1073807364 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1700 | "C:\Users\admin\Desktop\a\artikelv4%20%281%29.exe" | C:\Users\admin\Desktop\a\artikelv4%20%281%29.exe | — | artikelv4%20%281%29.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\Desktop\Christmas Tree.exe" | C:\Users\admin\Desktop\Christmas Tree.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 1073807364 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
207 015
Read events
206 812
Write events
197
Delete events
6
Modification events
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4756) Christmas Tree.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Christmas Tree_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
196
Suspicious files
148
Text files
110
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6456 | csc.exe | C:\Users\admin\AppData\Local\Temp\mwhuy0s2\CSCD5F2016D6F4C4058AEDAFFC7AD25B821.TMP | binary | |
MD5:38A45E6F6533DBA378AC2F1A235D9078 | SHA256:C8B7BA4E1B1B5E06FF1D1FA56D832EFB65F6CCCC29F86B0753C7F7BAB4A5676D | |||
| 5048 | Christmas Tree.exe | C:\Users\admin\Desktop\a\mimikatz.exe | executable | |
MD5:29EFD64DD3C7FE1E2B022B7AD73A1BA5 | SHA256:61C0810A23580CF492A6BA4F7654566108331E7A4134C968C2D6A05261B2D8A1 | |||
| 5964 | rxm.exe | C:\Users\admin\AppData\Local\Temp\mwhuy0s2\mwhuy0s2.cmdline | text | |
MD5:0D16D9A4633A47C44977802F2B3FA244 | SHA256:AC42809D742C821816712CAF4B1FFCFC02A485068890B12200B2D8BE0B5E7329 | |||
| 6456 | csc.exe | C:\Users\admin\AppData\Local\Temp\mwhuy0s2\mwhuy0s2.out | text | |
MD5:388BCCAD180783C2AF9BAD6F6CA9A1C9 | SHA256:A06E740E16DDA7C724272EA56405C0ADA83A121B75840CB0FCAE43237F6680AB | |||
| 5964 | rxm.exe | C:\Users\admin\AppData\Local\Temp\mwhuy0s2\mwhuy0s2.0.cs | text | |
MD5:58B10EF6BA0DA88788F1AAC56CE7E2DB | SHA256:AE11144F426028E50E77D64A66AEB954E169F627F8ABFE403791032594834520 | |||
| 4124 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 6456 | csc.exe | C:\Users\admin\AppData\Local\Temp\mwhuy0s2\mwhuy0s2.dll | executable | |
MD5:16E8C3E1F88763D008F0077622F99D38 | SHA256:6A02C2D36D3CEC4E3FD58B17070FCABF0793A33CB23E1021756172AAC24E6D62 | |||
| 4124 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 4124 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 4124 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
106
TCP/UDP connections
624
DNS requests
178
Threats
585
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4756 | Christmas Tree.exe | GET | — | 172.67.129.14:80 | http://mail.jegast.com/Downloads/SQL.exe | unknown | — | — | unknown |
— | — | GET | 200 | 23.216.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1760 | Christmas Tree.exe | GET | 404 | 172.67.156.48:80 | http://mail.workspacedoc.com/Downloads/Cbqjobosim-Signed.exe | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1760 | Christmas Tree.exe | GET | — | 188.114.96.3:80 | http://www.upt-in.com/Downloads/Cbqjobosim-Signed.exe | unknown | — | — | malicious |
5048 | Christmas Tree.exe | GET | 200 | 45.83.207.17:80 | http://45.83.207.17/cbot/raw_cbot.exe | unknown | — | — | unknown |
5048 | Christmas Tree.exe | GET | 200 | 77.223.119.85:80 | http://77.223.119.85/rxm.exe | unknown | — | — | malicious |
5964 | rxm.exe | GET | 200 | 77.223.119.85:80 | http://77.223.119.85/tb.exe | unknown | — | — | malicious |
6644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6644 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4756 | Christmas Tree.exe | 151.101.194.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
4756 | Christmas Tree.exe | 172.67.129.14:80 | mail.jegast.com | CLOUDFLARENET | US | unknown |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
mail.jegast.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
mail.workspacedoc.com |
| unknown |
www.upt-in.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] The domain has been identified as part of Storm-1747's infrastructure ( .jegast .com) |
5048 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5048 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5048 | Christmas Tree.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5048 | Christmas Tree.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
5048 | Christmas Tree.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5048 | Christmas Tree.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5964 | rxm.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5964 | rxm.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
5048 | Christmas Tree.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |