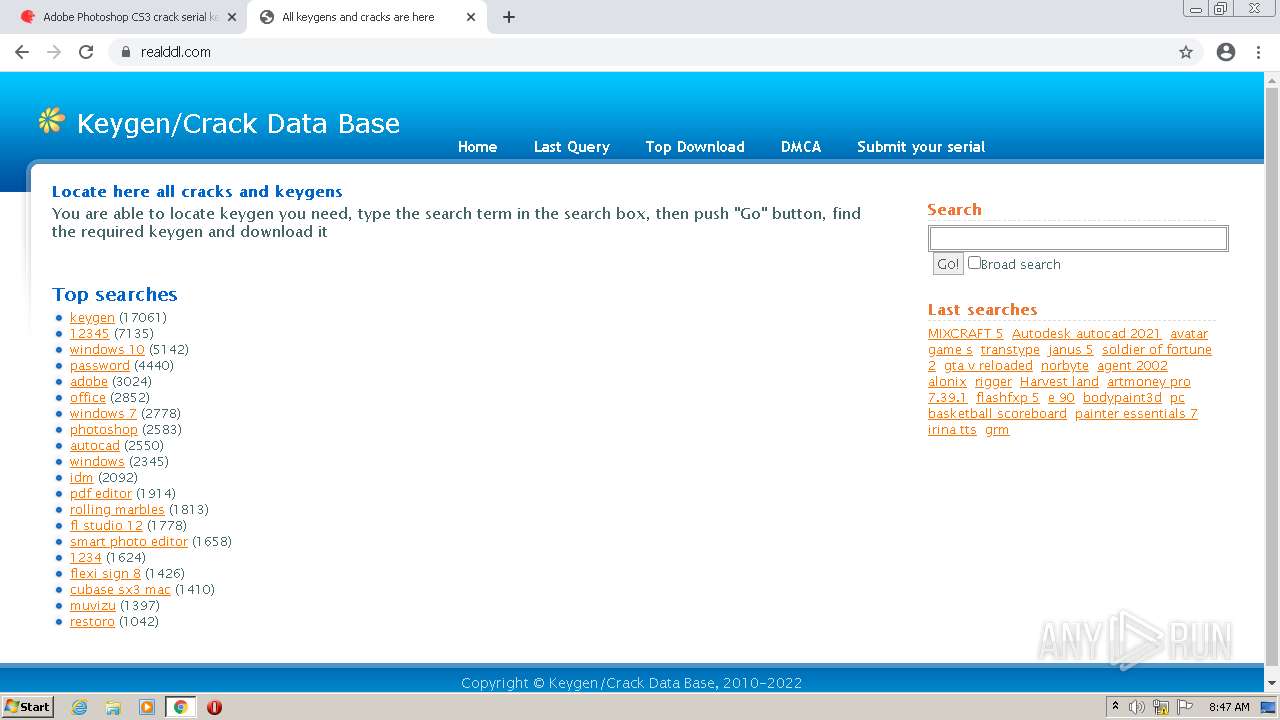
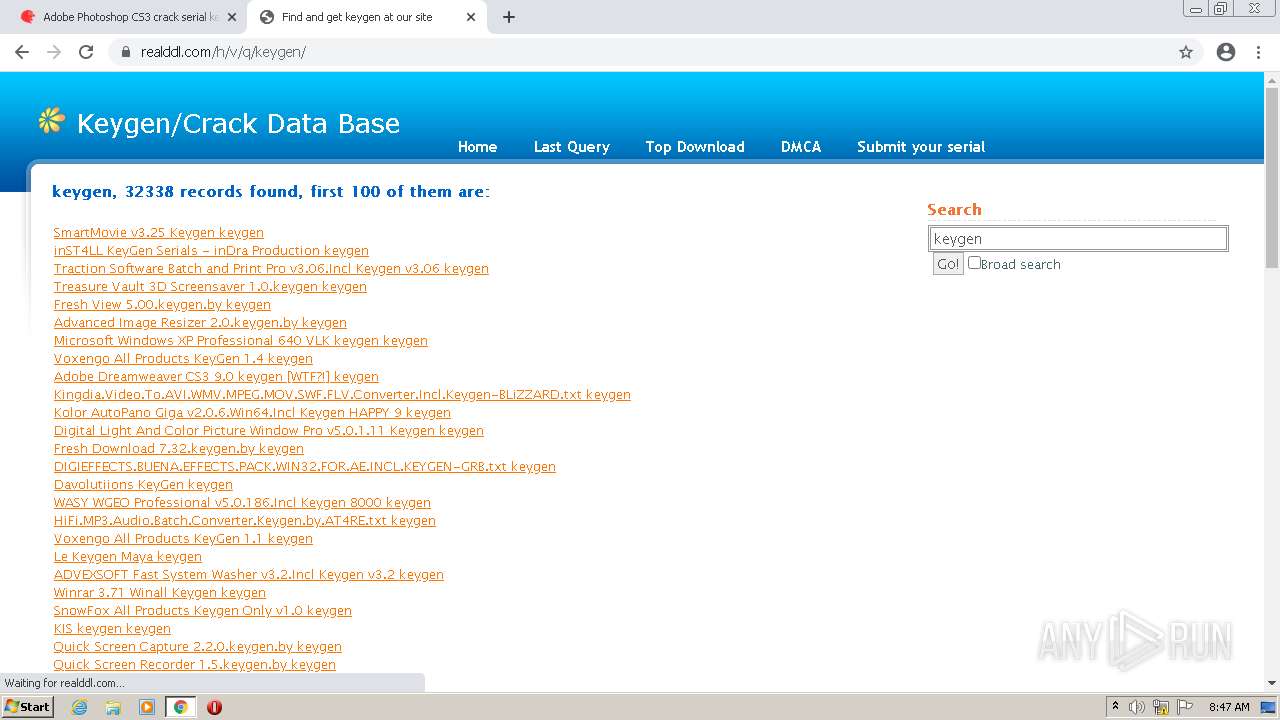
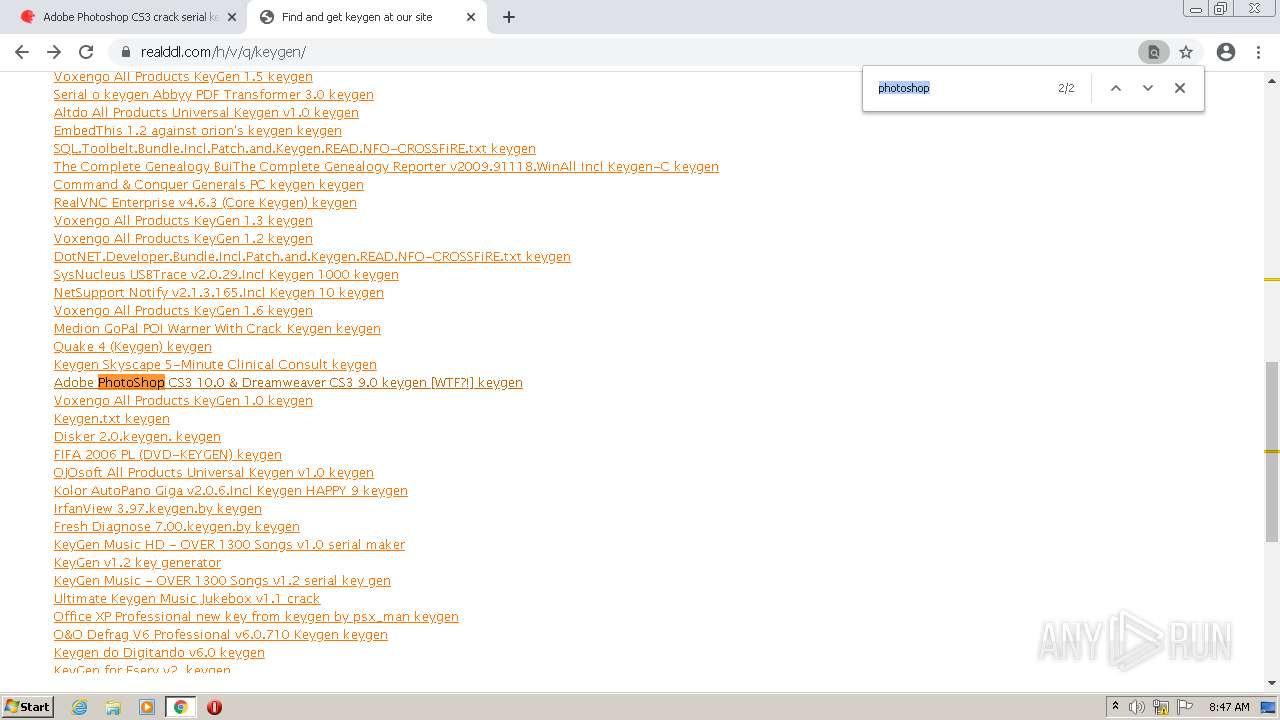
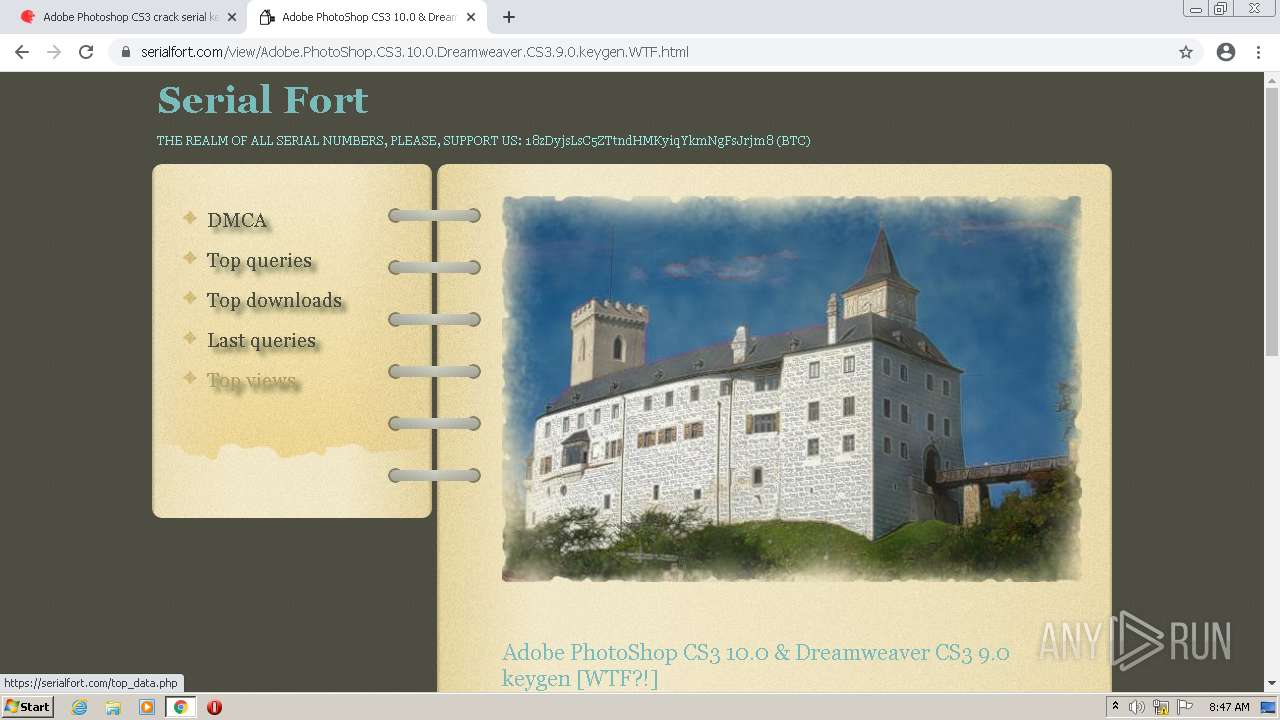
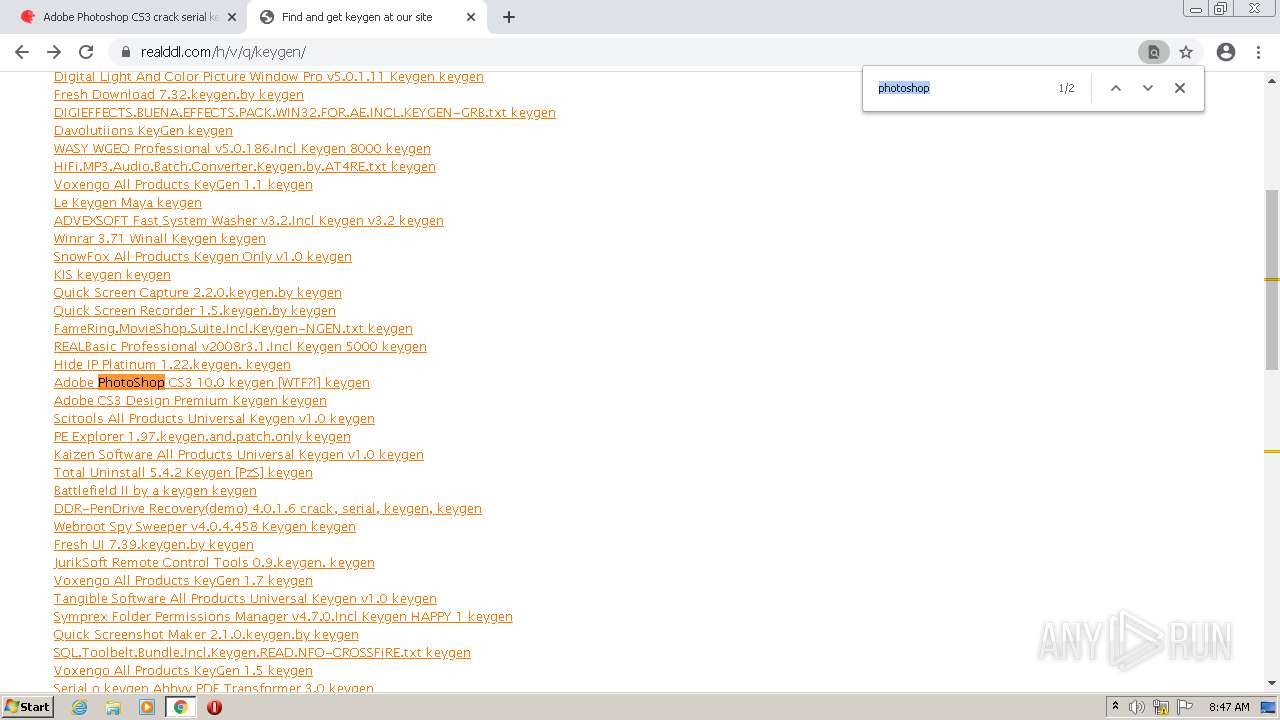
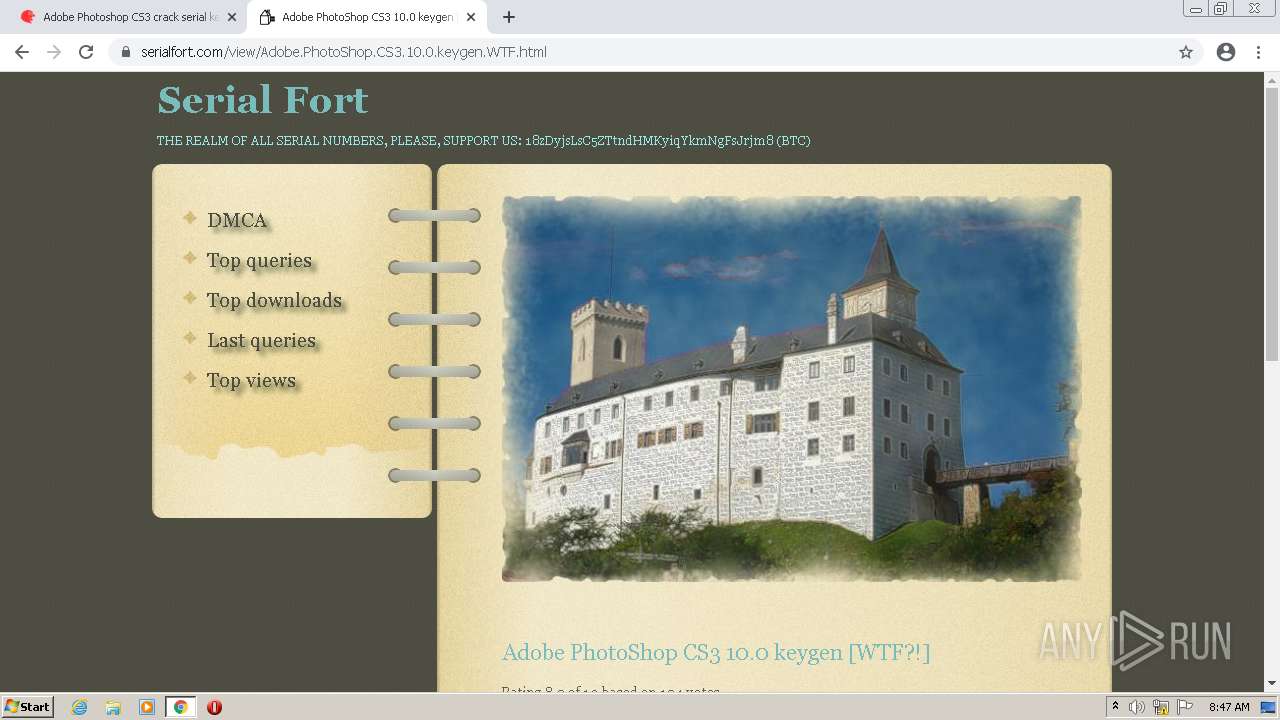
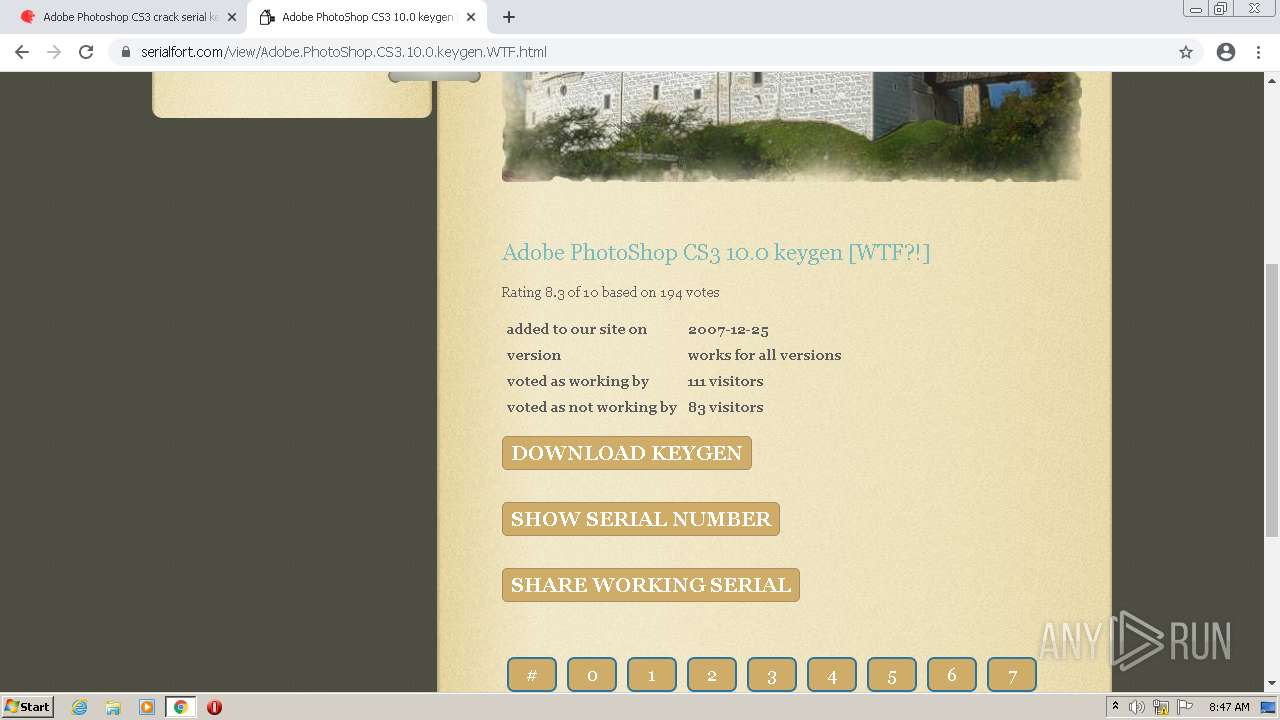
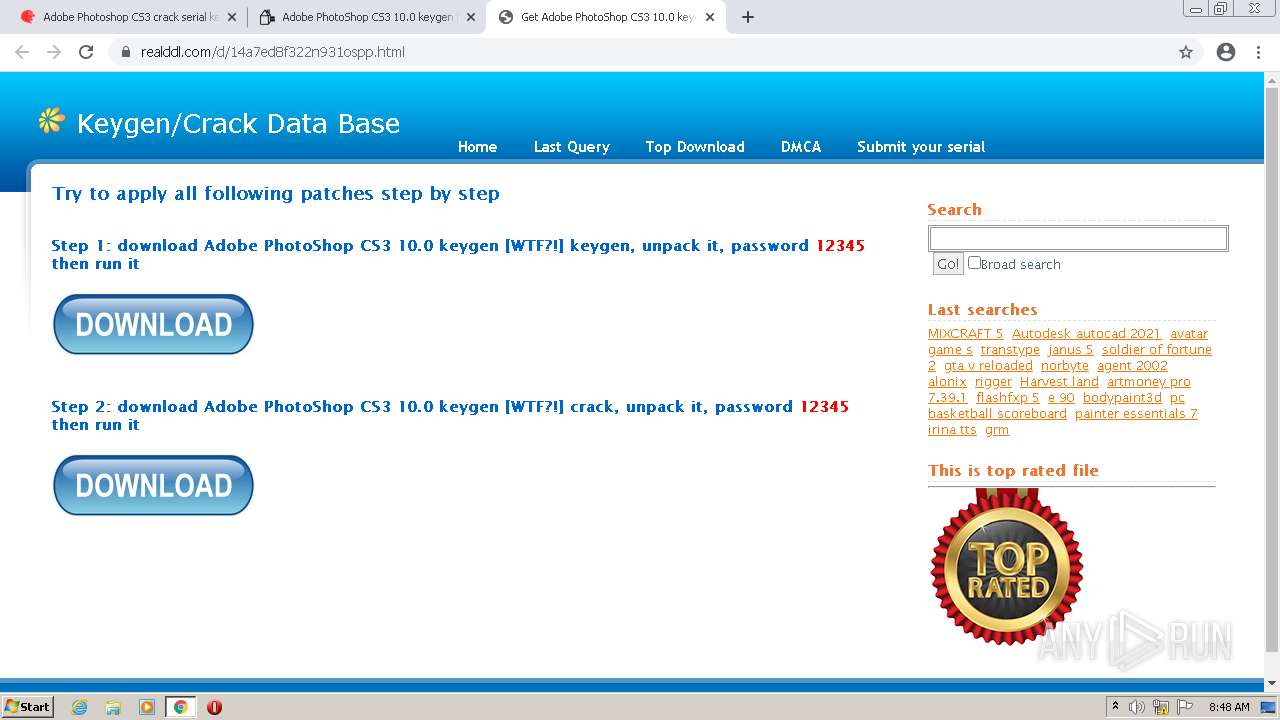
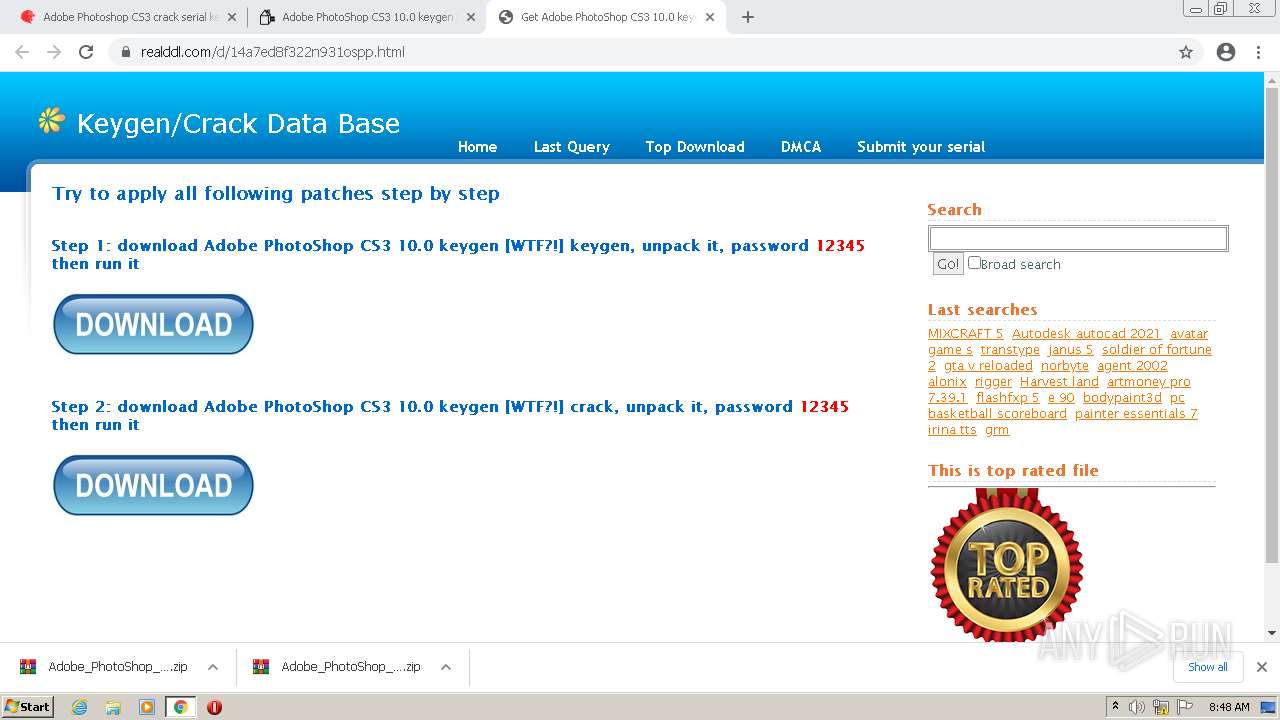
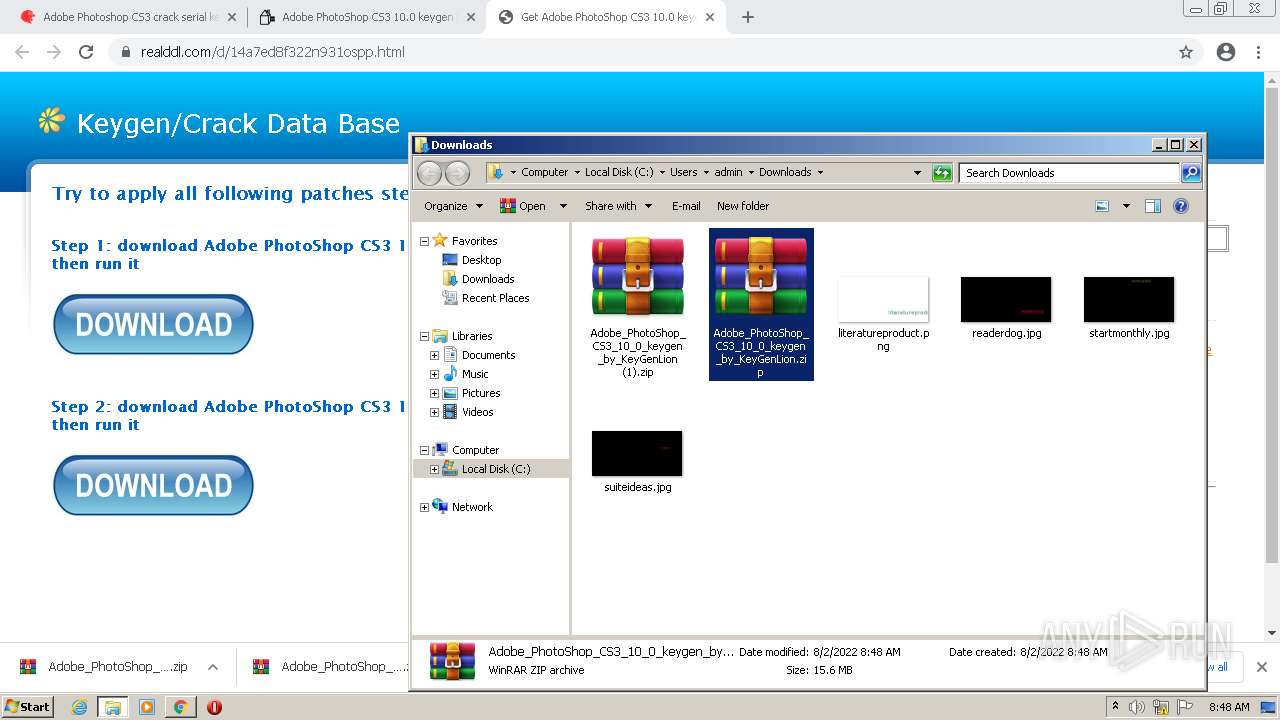
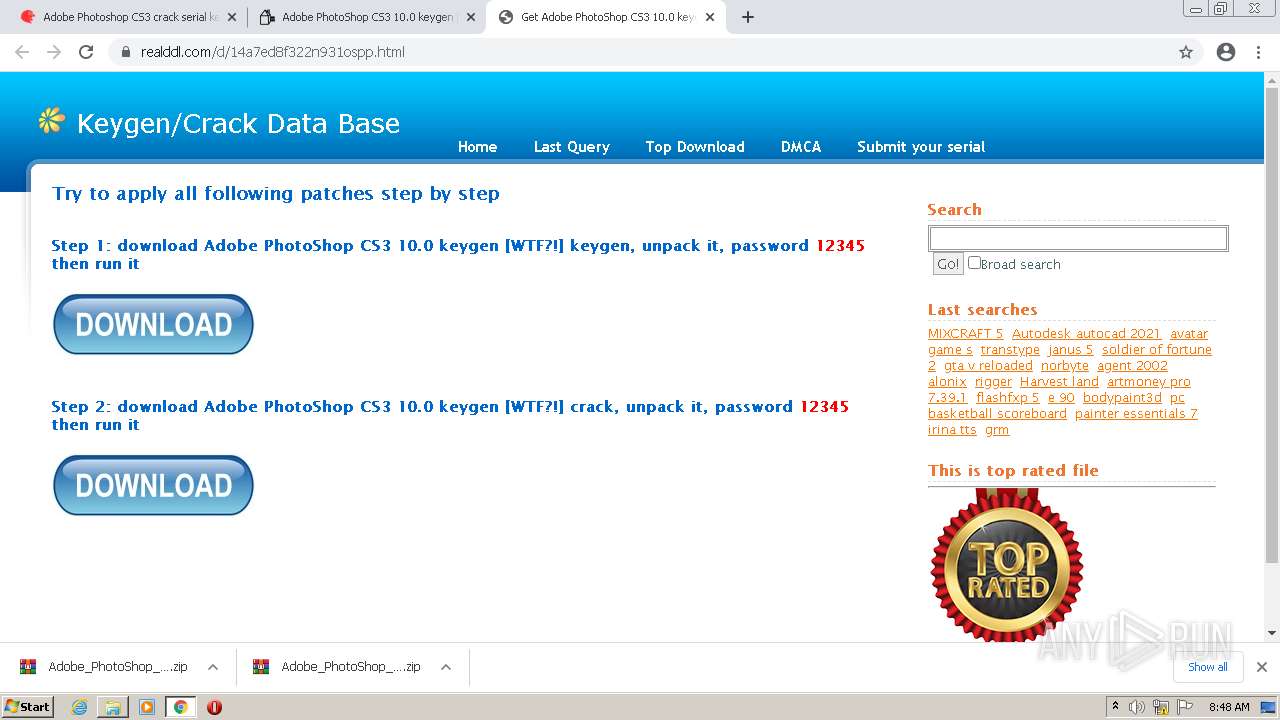
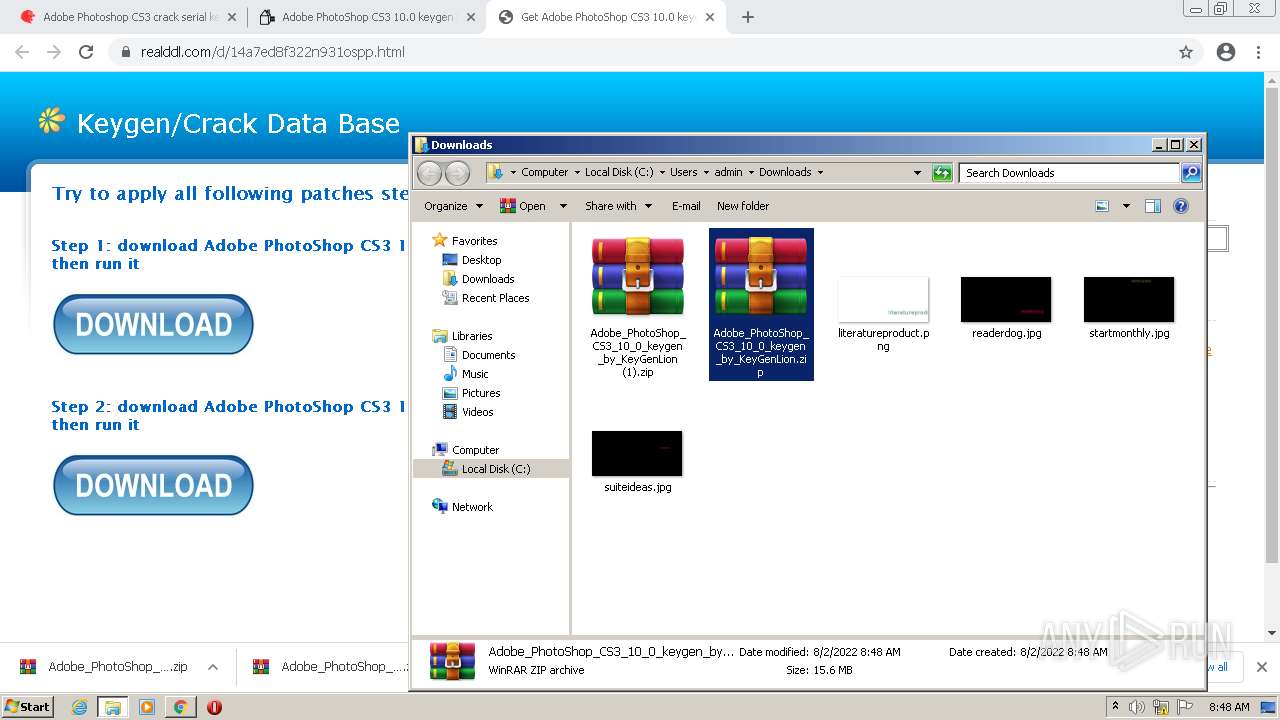
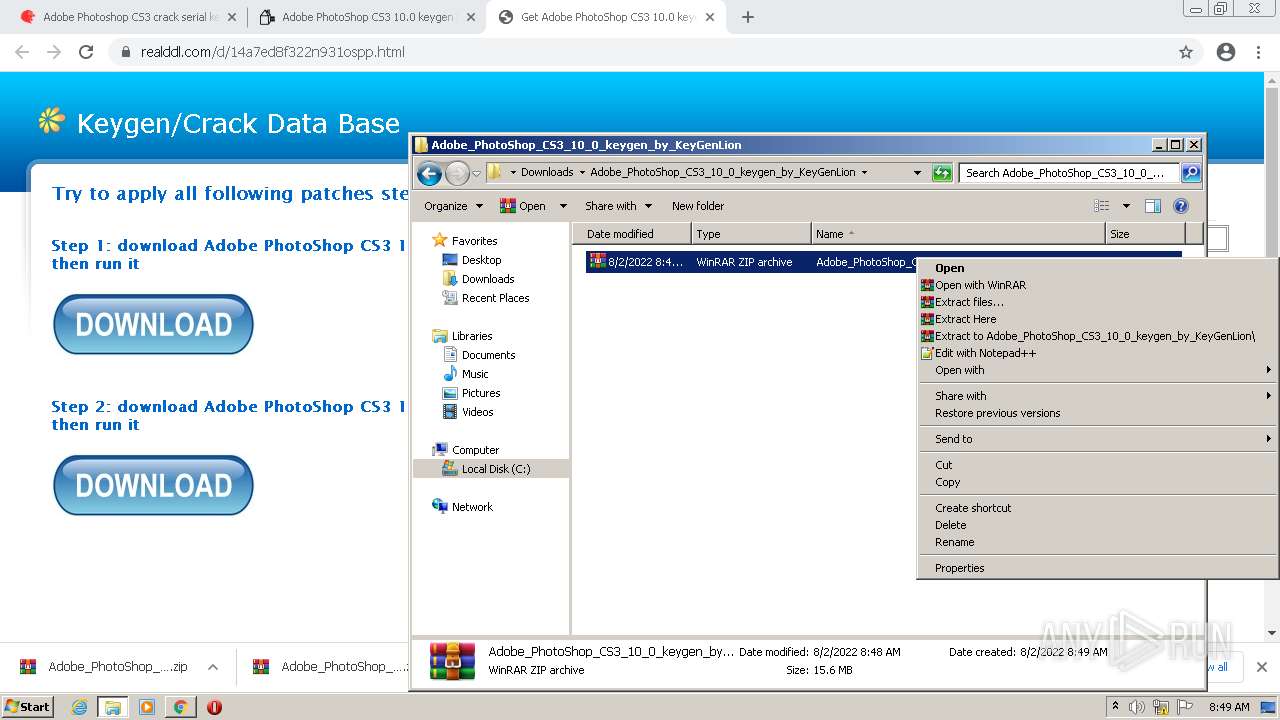
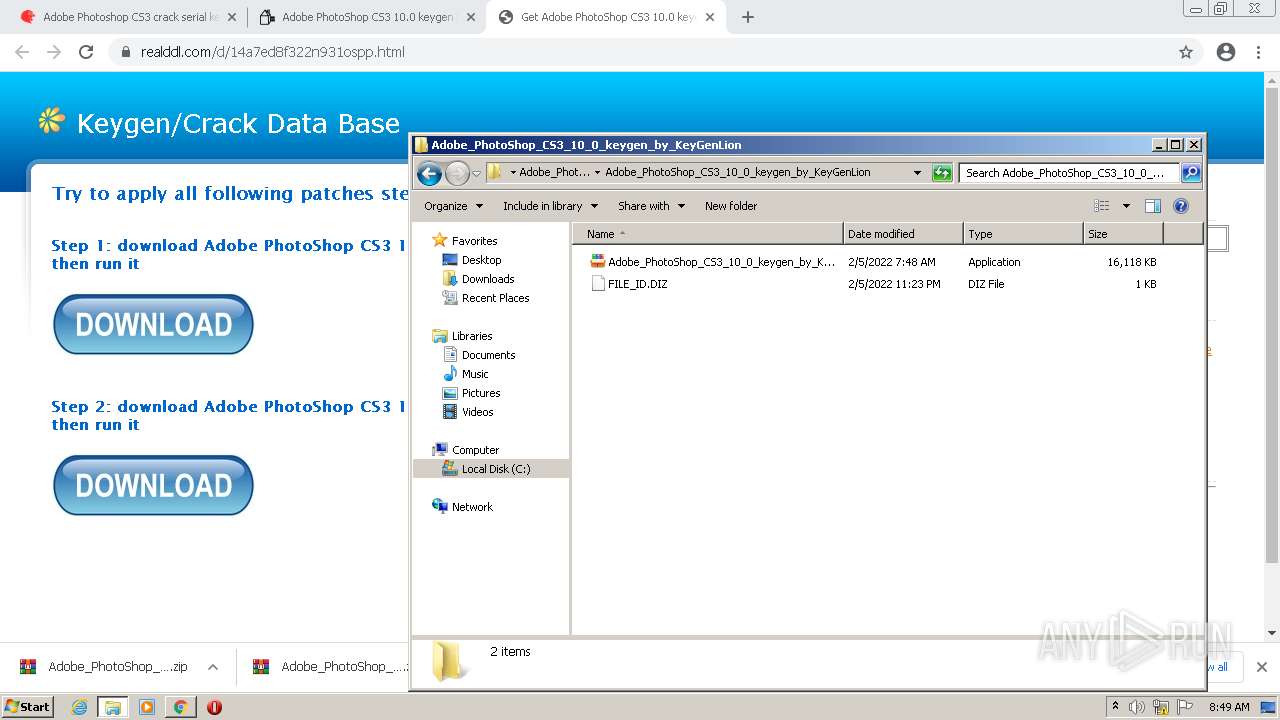
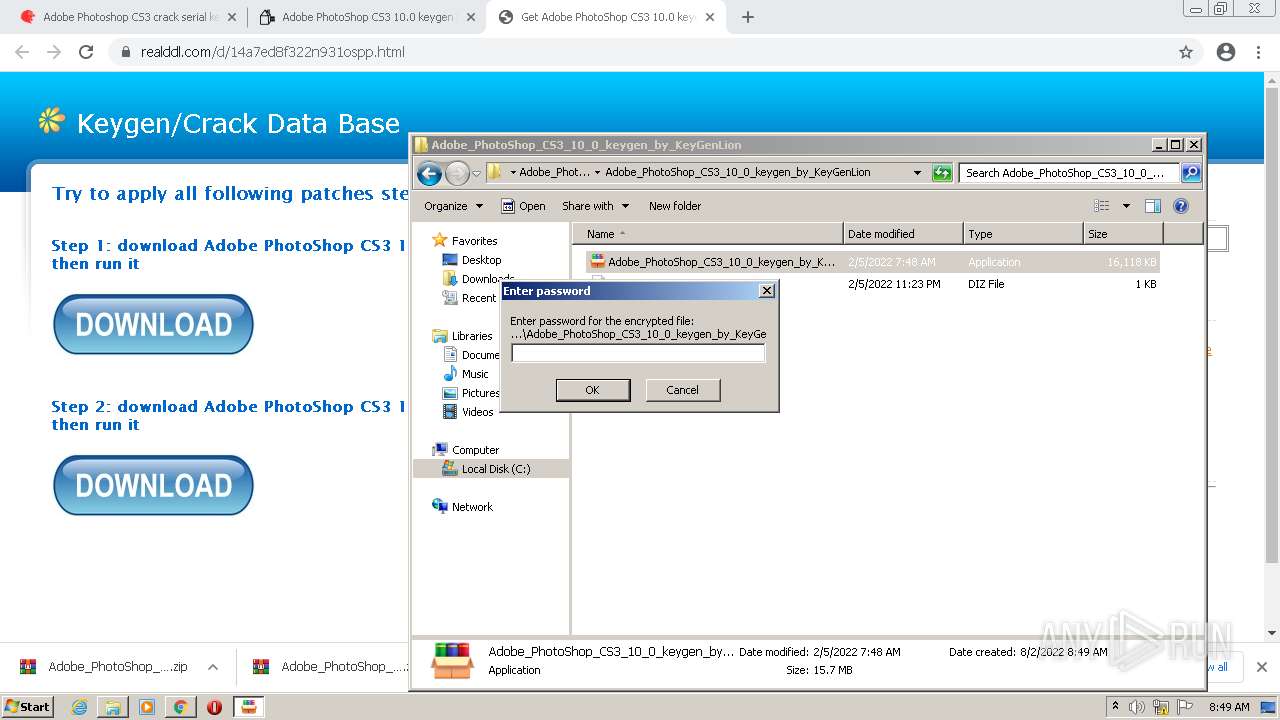
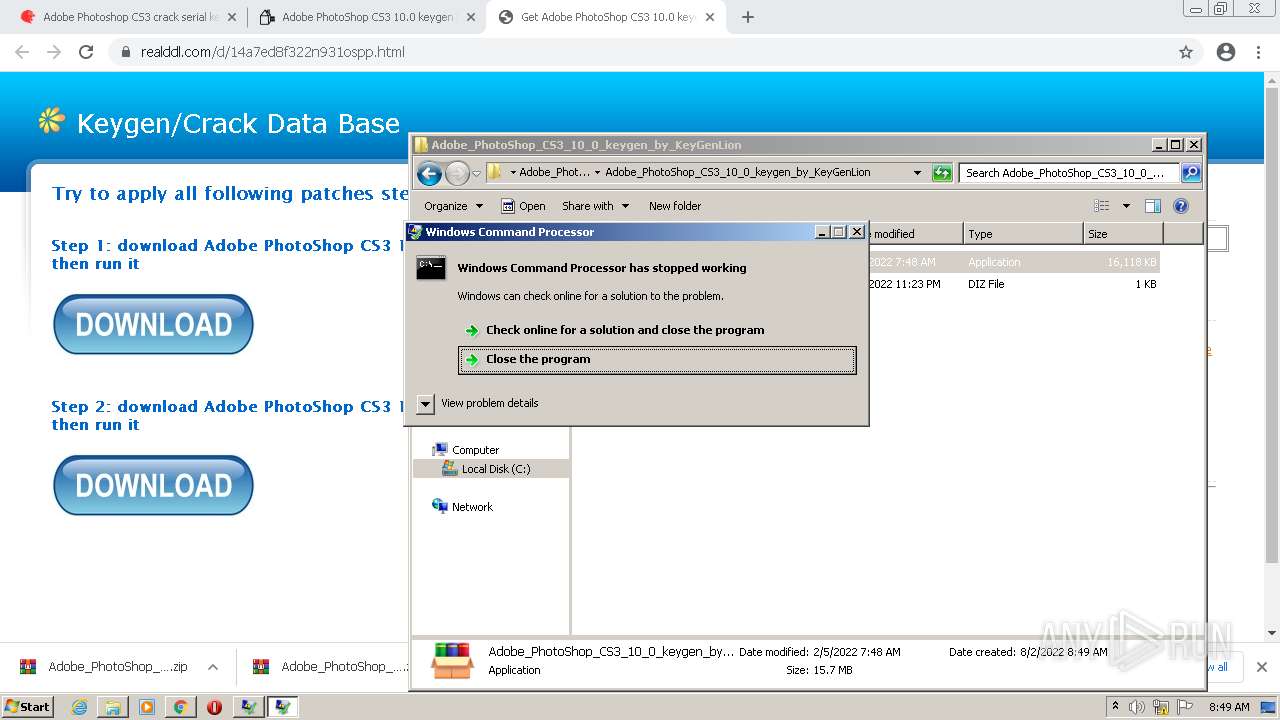
| URL: | http://www.keygenguru.com/serial/adobe_photoshop_cs3.html |
| Full analysis: | https://app.any.run/tasks/ea1f4be9-69f5-45ac-8ed4-49e3a3d0fc6b |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | August 02, 2022, 07:44:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 100DC653016262AF9F5A0A6F4B4CE800 |
| SHA1: | 39BC3ED5ABD9280BE91F24BAA271D98B87C3A1C2 |
| SHA256: | 98CEAC3316646BCFBD9A0A10CCD0AF3F3CE67AE51B1C11BF8F1DF4A028E37791 |
| SSDEEP: | 3:N1KJS4WXQyK3XmEaVeViG:Cc4FZmEeeb |
MALICIOUS
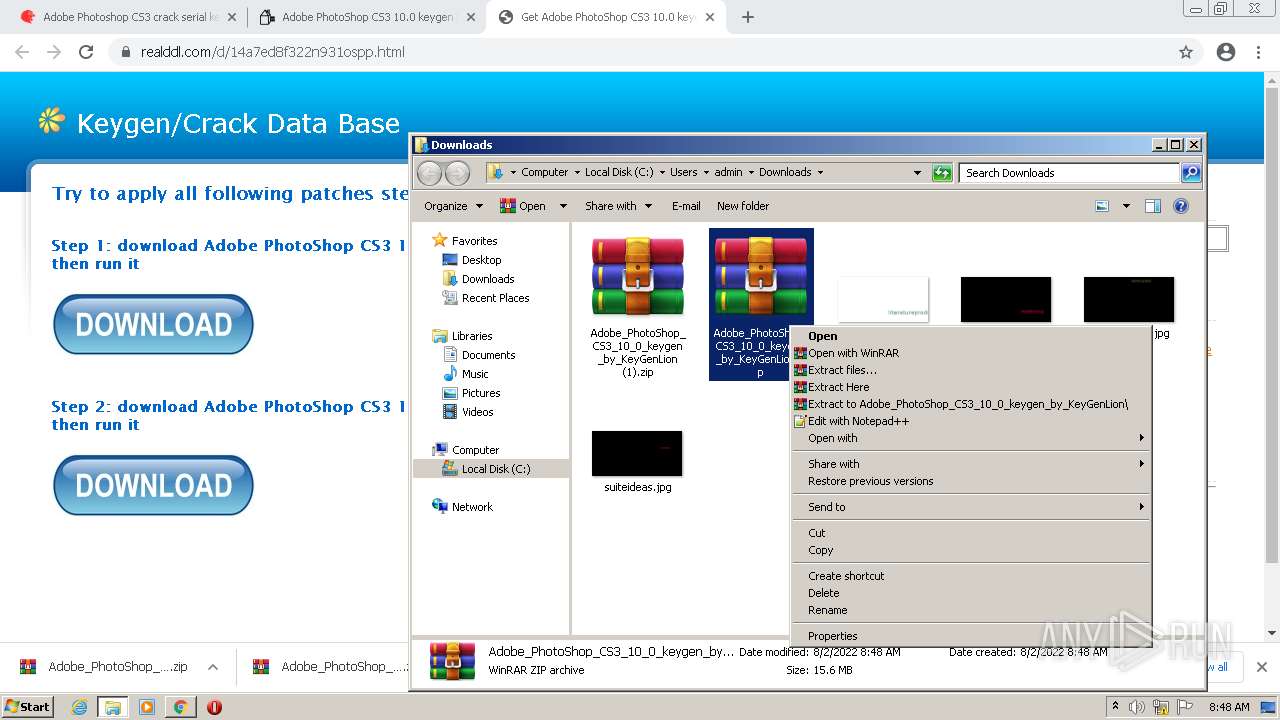
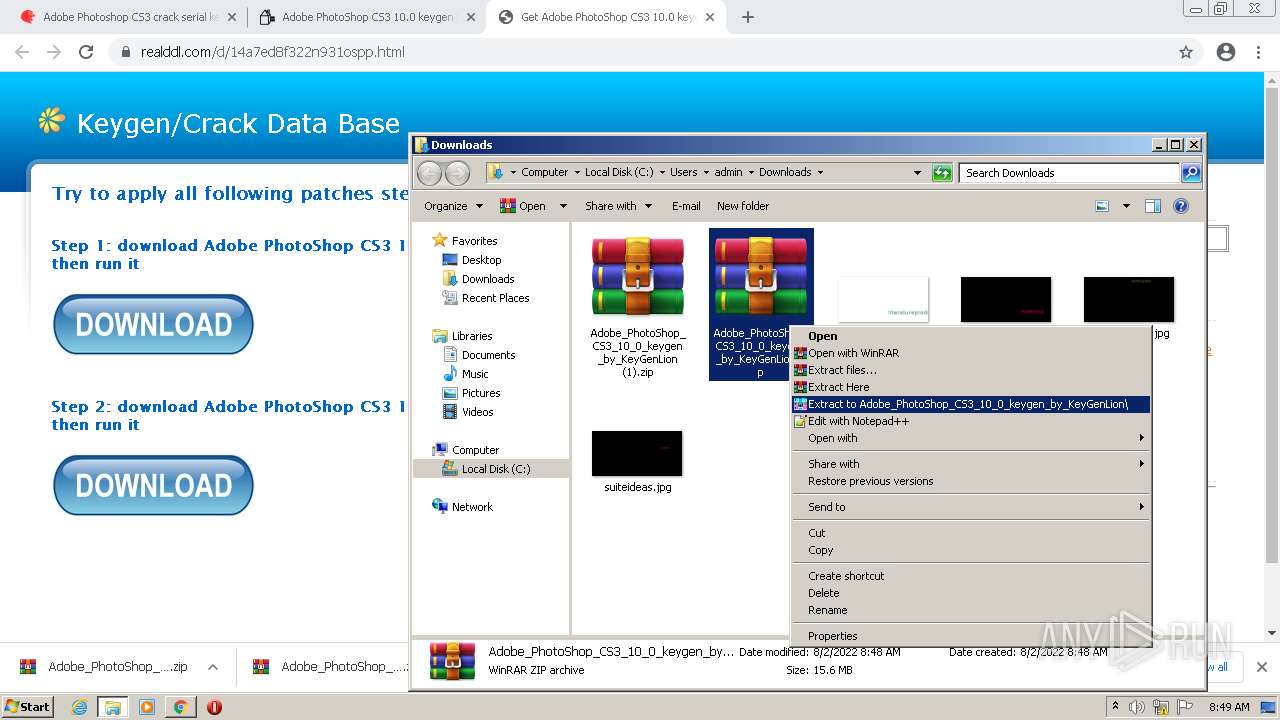
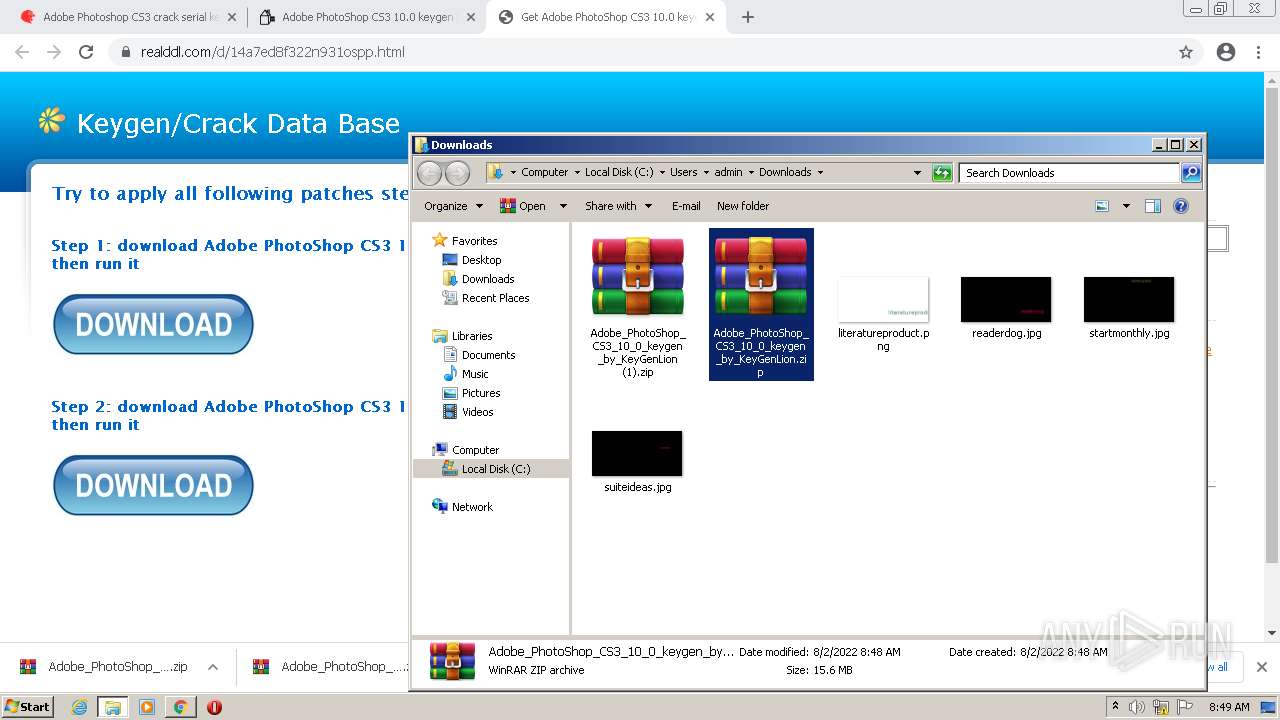
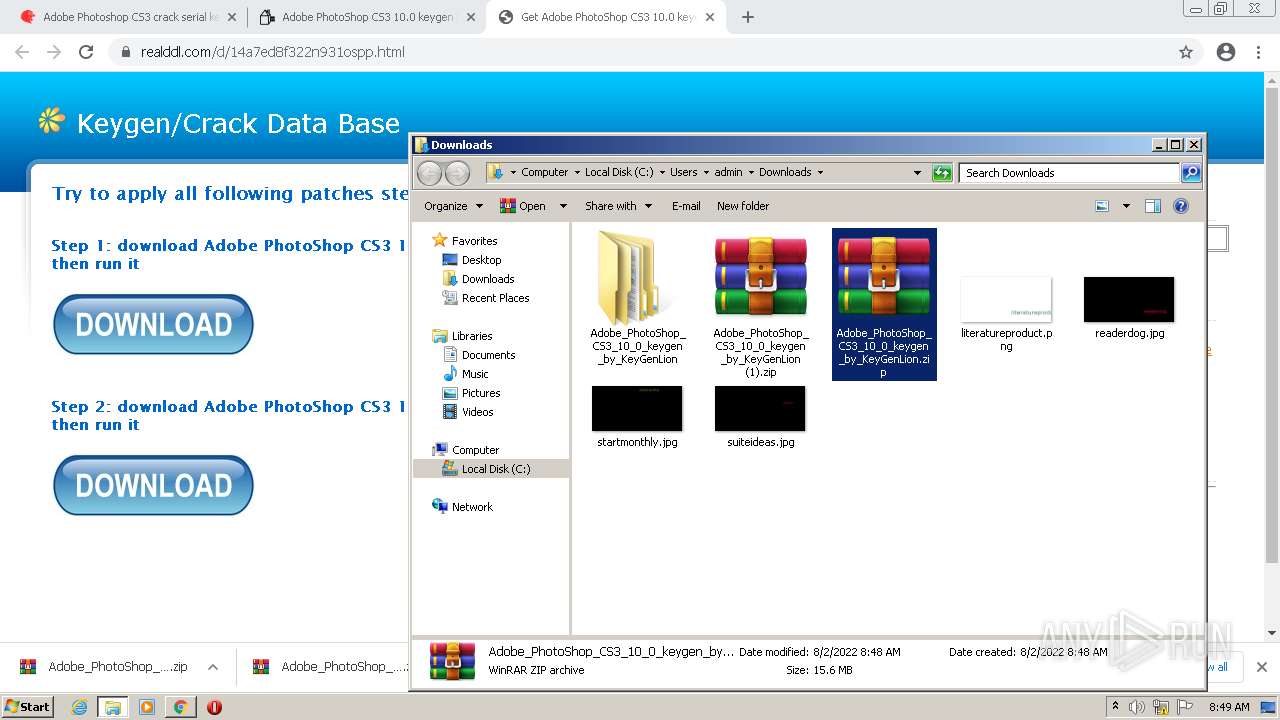
Drops executable file immediately after starts
- WinRAR.exe (PID: 2916)
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
- chrome.exe (PID: 1016)
- keygen-pr.exe (PID: 1656)
- keygen-step-4.exe (PID: 2036)
- keygen-step-6.exe (PID: 2096)
- 00004823..exe (PID: 3936)
- dngondon3.exe (PID: 2480)
- L.exe (PID: 2560)
- Crack.exe (PID: 2116)
Application was dropped or rewritten from another process
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
- keygen-pr.exe (PID: 1656)
- keygen-step-1.exe (PID: 2592)
- keygen-step-6.exe (PID: 2096)
- keygen-step-5.exe (PID: 2988)
- keygen-step-4.exe (PID: 2036)
- 00000029..exe (PID: 3304)
- 00004823..exe (PID: 3936)
- key.exe (PID: 3228)
- key.exe (PID: 2708)
- Crack.exe (PID: 2908)
- Crack.exe (PID: 2116)
- dngondon3.exe (PID: 2480)
- mp3studios_10.exe (PID: 3868)
- mp3studios_10.exe (PID: 2488)
- publisher.exe (PID: 1768)
- L.exe (PID: 2560)
- Mistit.exe (PID: 2312)
AZORULT was detected
- keygen-step-1.exe (PID: 2592)
Connects to CnC server
- keygen-step-1.exe (PID: 2592)
Writes to a start menu file
- 00004823..exe (PID: 3936)
Application was injected by another process
- Dwm.exe (PID: 548)
- taskeng.exe (PID: 272)
- ctfmon.exe (PID: 1392)
- Explorer.EXE (PID: 1080)
- DllHost.exe (PID: 2812)
- conhost.exe (PID: 3292)
- conhost.exe (PID: 2068)
- WerFault.exe (PID: 2424)
- WerFault.exe (PID: 3100)
- svchost.exe (PID: 872)
- WerFault.exe (PID: 3112)
- WerFault.exe (PID: 4088)
Runs injected code in another process
- 00004823..exe (PID: 3936)
- rundll32.exe (PID: 188)
Changes settings of System certificates
- Crack.exe (PID: 2116)
- mp3studios_10.exe (PID: 2488)
Steals credentials from Web Browsers
- key.exe (PID: 2708)
Actions looks like stealing of personal data
- key.exe (PID: 2708)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3748)
Reads the computer name
- WinRAR.exe (PID: 2056)
- WinRAR.exe (PID: 2916)
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
- keygen-step-1.exe (PID: 2592)
- keygen-pr.exe (PID: 1656)
- keygen-step-6.exe (PID: 2096)
- keygen-step-5.exe (PID: 2988)
- keygen-step-4.exe (PID: 2036)
- 00000029..exe (PID: 3304)
- key.exe (PID: 3228)
- Crack.exe (PID: 2908)
- dngondon3.exe (PID: 2480)
- Crack.exe (PID: 2116)
- Mistit.exe (PID: 2312)
- mp3studios_10.exe (PID: 3868)
- mp3studios_10.exe (PID: 2488)
- L.exe (PID: 2560)
- key.exe (PID: 2708)
- publisher.exe (PID: 1768)
Checks supported languages
- WinRAR.exe (PID: 2056)
- WinRAR.exe (PID: 2916)
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
- cmd.exe (PID: 2436)
- keygen-pr.exe (PID: 1656)
- keygen-step-1.exe (PID: 2592)
- keygen-step-5.exe (PID: 2988)
- keygen-step-6.exe (PID: 2096)
- keygen-step-4.exe (PID: 2036)
- 00000029..exe (PID: 3304)
- 00004823..exe (PID: 3936)
- Crack.exe (PID: 2908)
- key.exe (PID: 3228)
- conhost.exe (PID: 3292)
- cmd.exe (PID: 188)
- Crack.exe (PID: 2116)
- dngondon3.exe (PID: 2480)
- cmd.exe (PID: 1292)
- conhost.exe (PID: 2068)
- Mistit.exe (PID: 2312)
- L.exe (PID: 2560)
- mp3studios_10.exe (PID: 3868)
- mp3studios_10.exe (PID: 2488)
- publisher.exe (PID: 1768)
- key.exe (PID: 2708)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2916)
- chrome.exe (PID: 1016)
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
- keygen-pr.exe (PID: 1656)
- keygen-step-4.exe (PID: 2036)
- 00004823..exe (PID: 3936)
- keygen-step-6.exe (PID: 2096)
- dngondon3.exe (PID: 2480)
- Crack.exe (PID: 2116)
- L.exe (PID: 2560)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2916)
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
- chrome.exe (PID: 1016)
- keygen-pr.exe (PID: 1656)
- keygen-step-4.exe (PID: 2036)
- keygen-step-6.exe (PID: 2096)
- 00004823..exe (PID: 3936)
- dngondon3.exe (PID: 2480)
- Crack.exe (PID: 2116)
- L.exe (PID: 2560)
Reads Environment values
- keygen-step-1.exe (PID: 2592)
- 00000029..exe (PID: 3304)
- key.exe (PID: 3228)
- Mistit.exe (PID: 2312)
- L.exe (PID: 2560)
Application launched itself
- key.exe (PID: 2708)
- Crack.exe (PID: 2908)
Reads Windows owner or organization settings
- key.exe (PID: 3228)
Reads Windows Product ID
- key.exe (PID: 3228)
Reads the Windows organization settings
- key.exe (PID: 3228)
Adds / modifies Windows certificates
- Crack.exe (PID: 2116)
- mp3studios_10.exe (PID: 2488)
Executed via COM
- DllHost.exe (PID: 2372)
Reads default file associations for system extensions
- keygen-step-5.exe (PID: 2988)
Checks for external IP
- L.exe (PID: 2560)
- mp3studios_10.exe (PID: 2488)
Executed via WMI
- rundll32.exe (PID: 188)
Loads DLL from Mozilla Firefox
- key.exe (PID: 2708)
Searches for installed software
- key.exe (PID: 3228)
- key.exe (PID: 2708)
INFO
Checks supported languages
- chrome.exe (PID: 3748)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 2248)
- chrome.exe (PID: 2756)
- chrome.exe (PID: 3084)
- chrome.exe (PID: 2824)
- chrome.exe (PID: 3392)
- chrome.exe (PID: 1644)
- chrome.exe (PID: 2028)
- chrome.exe (PID: 2548)
- chrome.exe (PID: 3124)
- chrome.exe (PID: 2092)
- chrome.exe (PID: 3144)
- chrome.exe (PID: 2500)
- svchost.exe (PID: 872)
- chrome.exe (PID: 1544)
- chrome.exe (PID: 3556)
- chrome.exe (PID: 736)
- chrome.exe (PID: 1820)
- chrome.exe (PID: 2816)
- chrome.exe (PID: 2904)
- chrome.exe (PID: 2856)
- chrome.exe (PID: 4048)
- chrome.exe (PID: 4072)
- chrome.exe (PID: 1312)
- chrome.exe (PID: 2700)
- chrome.exe (PID: 2616)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 2468)
- chrome.exe (PID: 760)
- chrome.exe (PID: 2176)
- chrome.exe (PID: 3680)
- chrome.exe (PID: 1016)
- DllHost.exe (PID: 2812)
- chrome.exe (PID: 1812)
- timeout.exe (PID: 1544)
- PING.EXE (PID: 3148)
- DllHost.exe (PID: 2372)
- WerFault.exe (PID: 2424)
- WerFault.exe (PID: 3100)
- control.exe (PID: 940)
- rundll32.exe (PID: 4092)
- WerFault.exe (PID: 3112)
- rundll32.exe (PID: 188)
- WerFault.exe (PID: 4088)
- chrome.exe (PID: 1340)
Application launched itself
- chrome.exe (PID: 3748)
- chrome.exe (PID: 3084)
Reads the computer name
- chrome.exe (PID: 3392)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 3748)
- chrome.exe (PID: 2756)
- chrome.exe (PID: 2092)
- chrome.exe (PID: 2500)
- chrome.exe (PID: 3144)
- chrome.exe (PID: 1544)
- chrome.exe (PID: 2816)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 760)
- DllHost.exe (PID: 2812)
- PING.EXE (PID: 3148)
- DllHost.exe (PID: 2372)
- WerFault.exe (PID: 2424)
- WerFault.exe (PID: 3100)
- control.exe (PID: 940)
- rundll32.exe (PID: 4092)
- rundll32.exe (PID: 188)
- WerFault.exe (PID: 4088)
- WerFault.exe (PID: 3112)
Reads settings of System Certificates
- chrome.exe (PID: 3540)
- Crack.exe (PID: 2116)
- L.exe (PID: 2560)
- mp3studios_10.exe (PID: 2488)
- publisher.exe (PID: 1768)
Reads the date of Windows installation
- chrome.exe (PID: 2500)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3748)
- keygen-step-6.exe (PID: 2096)
- 00004823..exe (PID: 3936)
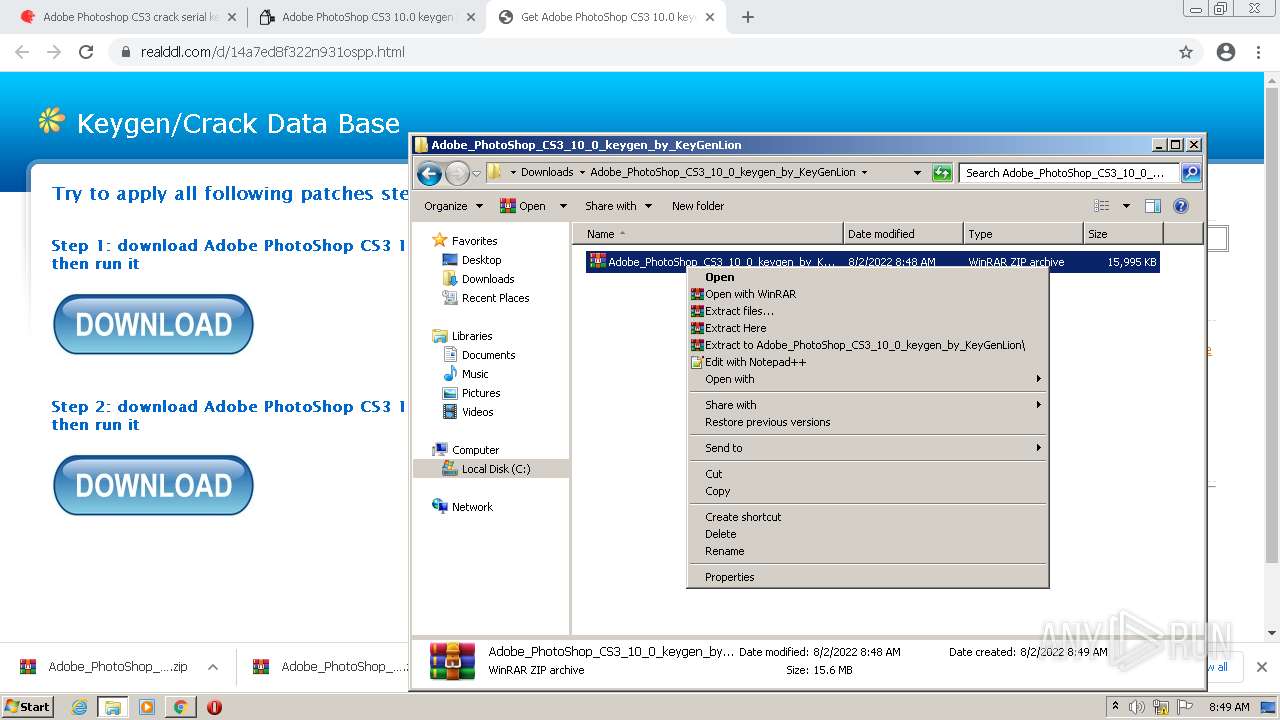
Manual execution by user
- WinRAR.exe (PID: 2916)
- WinRAR.exe (PID: 2056)
- Adobe_PhotoShop_CS3_10_0_keygen_by_KeyGenLion.exe (PID: 3184)
Checks Windows Trust Settings
- mp3studios_10.exe (PID: 2488)
- publisher.exe (PID: 1768)
Reads Microsoft Office registry keys
- key.exe (PID: 3228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
128
Monitored processes
77
Malicious processes
15
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Windows\system32\cmd.exe" /c timeout 2 && del "C:\Users\admin\AppData\Roaming\00000029..exe" | C:\Windows\system32\cmd.exe | — | 00000029..exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 188 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\db.dll",global | C:\Windows\system32\rundll32.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | taskeng.exe {A1904317-8264-4385-A3E7-2068B6FA26F7} | C:\Windows\system32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | "C:\Windows\system32\Dwm.exe" | C:\Windows\system32\Dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1036,3992185220629806008,13549850247360303811,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=592 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,3992185220629806008,13549850247360303811,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2556 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 872 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 940 | "C:\Windows\System32\control.exe" "C:\Users\admin\AppData\Local\Temp\MEf9HB.cpl", | C:\Windows\System32\control.exe | — | keygen-step-5.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1036,3992185220629806008,13549850247360303811,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1992 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1080 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
51 465
Read events
50 569
Write events
884
Delete events
12
Modification events
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3748) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
26
Suspicious files
84
Text files
208
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62E8D5FA-EA4.pma | — | |
MD5:— | SHA256:— | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\0ff91e04-4c88-4556-bc0c-005925ee72d3.tmp | text | |
MD5:— | SHA256:— | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old~RF105390.TMP | text | |
MD5:B628564B8042F6E2CC2F53710AAECDC0 | SHA256:1D3B022BDEE9F48D79E3EC1E93F519036003642D3D72D10B05CFD47F43EFBF13 | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF10518d.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:995C92837E4775CAFFE387D51ADBA520 | SHA256:51247C3464FD988B72670002D01A57FBFF1348704D325DC8FF8817ED2459D0D9 | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old | text | |
MD5:5202CA4D6AF0C37DAEC0D528CC7F2986 | SHA256:8F5B8FF94B14C36EA0CBE8FA0A4D165A632B45F834BBB7239E1A6CF6685F256C | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF10517d.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3748 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\4b463062-69b8-4b94-8ffe-6a638e5ad7b8.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
51
TCP/UDP connections
112
DNS requests
56
Threats
41
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3540 | chrome.exe | GET | 301 | 188.114.97.3:80 | http://www.keygenguru.com/serial/adobe_photoshop_cs3.html | US | — | — | malicious |
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adlz3ju63222cmxirhfexwn32dga_7495/hfnkpimlhhgieaddgfemjhofmfblmnib_7495_all_ad6untm22u64jlru4opdo25erqtq.crx3 | US | — | — | whitelisted |
— | — | HEAD | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adlz3ju63222cmxirhfexwn32dga_7495/hfnkpimlhhgieaddgfemjhofmfblmnib_7495_all_ad6untm22u64jlru4opdo25erqtq.crx3 | US | — | — | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.70 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | fli | 45.9 Kb | whitelisted |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 2.81 Mb | whitelisted |
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac4kqpd5vf6wkr67nuk3womi2oaa_9.37.2/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.37.2_all_adr6ecsctmaarsezoenukfuqk6aq.crx3 | US | fli | 45.9 Kb | whitelisted |
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjg0QUFYSnN4MFUtaEQwNDZqVGRkVkFmZw/1.0.6.0_aemomkdncapdnfajjbbcbdebjljbpmpj.crx | US | crx | 25.0 Kb | whitelisted |
— | — | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adlz3ju63222cmxirhfexwn32dga_7495/hfnkpimlhhgieaddgfemjhofmfblmnib_7495_all_ad6untm22u64jlru4opdo25erqtq.crx3 | US | crx | 25.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 188.114.97.3:80 | www.keygenguru.com | Cloudflare Inc | US | malicious |
3540 | chrome.exe | 188.114.97.3:80 | www.keygenguru.com | Cloudflare Inc | US | malicious |
3540 | chrome.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3540 | chrome.exe | 188.114.97.3:443 | www.keygenguru.com | Cloudflare Inc | US | malicious |
3540 | chrome.exe | 172.67.193.176:443 | keygenguru.com | — | US | unknown |
3540 | chrome.exe | 142.251.5.156:443 | stats.g.doubleclick.net | Google Inc. | US | unknown |
3540 | chrome.exe | 142.250.186.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
3540 | chrome.exe | 188.114.96.3:443 | www.keygenguru.com | Cloudflare Inc | US | malicious |
3540 | chrome.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3540 | chrome.exe | 142.250.184.195:443 | www.google.co.uk | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
www.keygenguru.com |
| malicious |
accounts.google.com |
| shared |
keygenguru.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
www.google.com |
| malicious |
www.google.co.uk |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2096 | keygen-step-6.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2096 | keygen-step-6.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
2096 | keygen-step-6.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2096 | keygen-step-6.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2592 | keygen-step-1.exe | A Network Trojan was detected | ET TROJAN Win32/AZORult V3.3 Client Checkin M2 |
2592 | keygen-step-1.exe | A Network Trojan was detected | AV TROJAN Azorult CnC Beacon |
2096 | keygen-step-6.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2096 | keygen-step-6.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
2096 | keygen-step-6.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2096 | keygen-step-6.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
9 ETPRO signatures available at the full report