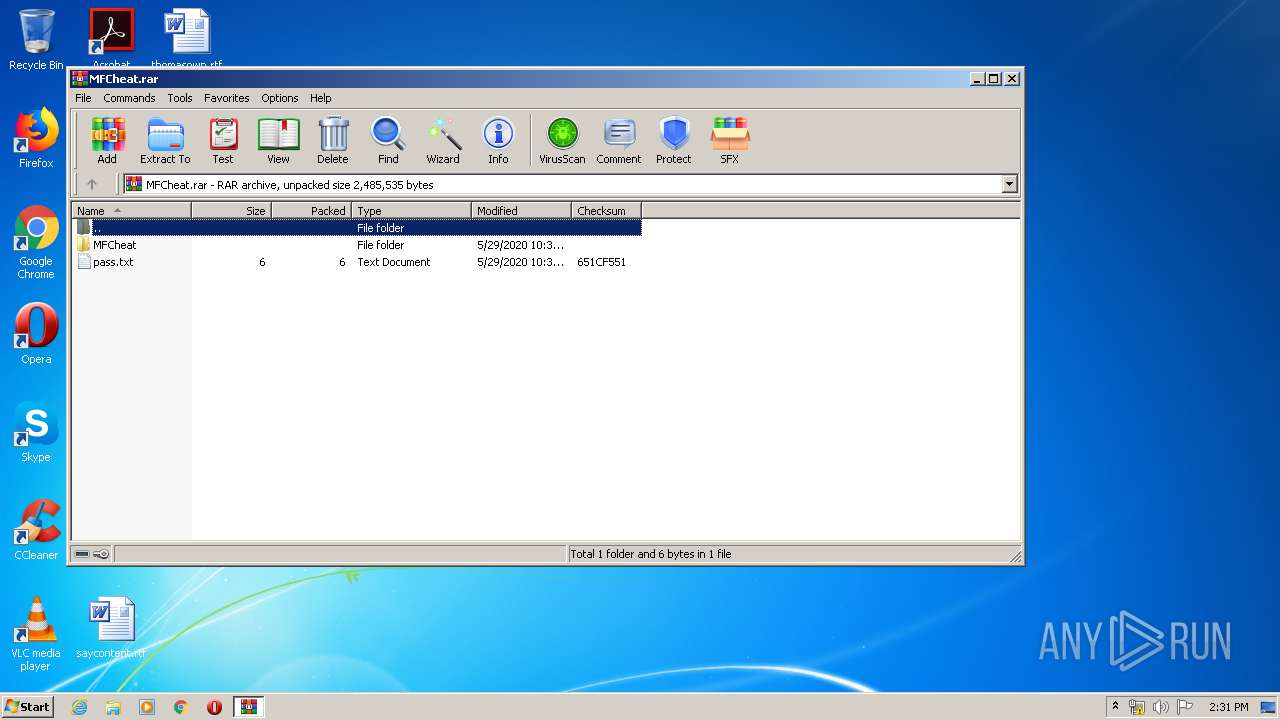
| File name: | MFCheat.rar |
| Full analysis: | https://app.any.run/tasks/8f0d720a-0750-4b40-9113-3f2f0fe469ee |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | May 30, 2020, 13:31:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F528507F9AA6A213E4029FDE9C215755 |
| SHA1: | A7C07B29DB8011C7C37422D5B90E623C9739E1A9 |
| SHA256: | 9884A0159DF2C2A70324ADDFF7D764DF036485445B235A6BBE724E2855A218DE |
| SSDEEP: | 49152:3ZqvOFH0Mlv5t2T4oVxkCITOQFMK2kWmSlOi8TraadmgekEa2tWHN+hC:bFvlBtw5VGztFTpWmcOi8Traad6a2tO |
MALICIOUS
Application was dropped or rewritten from another process
- 0EQ0hjjnRo5l5jBz0k1Y.exe (PID: 2300)
- MFCHEAT.exe (PID: 2476)
- mfcheat.exe (PID: 1460)
- mfcheat.exe (PID: 1452)
Writes to a start menu file
- cmd.exe (PID: 3156)
Loads the Task Scheduler COM API
- mfcheat.exe (PID: 1452)
Connects to CnC server
- mfcheat.exe (PID: 1452)
DCRAT was detected
- mfcheat.exe (PID: 1452)
SUSPICIOUS
Executable content was dropped or overwritten
- MFCHEAT.exe (PID: 2476)
- WinRAR.exe (PID: 2592)
- 0EQ0hjjnRo5l5jBz0k1Y.exe (PID: 2300)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 1256)
- WScript.exe (PID: 2080)
- mfcheat.exe (PID: 1460)
Executes scripts
- 0EQ0hjjnRo5l5jBz0k1Y.exe (PID: 2300)
- MFCHEAT.exe (PID: 2476)
Creates files in the user directory
- cmd.exe (PID: 3156)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3156)
Reads Environment values
- mfcheat.exe (PID: 1452)
Checks for external IP
- mfcheat.exe (PID: 1452)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
53
Monitored processes
12
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Windows\System32\cmd.exe" /c "C:\media\mfcheat.exe" | C:\Windows\System32\cmd.exe | mfcheat.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1256 | "C:\Windows\System32\WScript.exe" "C:\media\AOgBis9dgs7mRQbhCLDbG8UURZv4qG.vbs" | C:\Windows\System32\WScript.exe | — | MFCHEAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1452 | C:\media\mfcheat.exe | C:\media\mfcheat.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 0.0 Modules
| |||||||||||||||
| 1460 | "C:\media\mfcheat.exe" | C:\media\mfcheat.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.0 Modules
| |||||||||||||||
| 1704 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 1 /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | "C:\Windows\System32\WScript.exe" "C:\media\System.vbe" | C:\Windows\System32\WScript.exe | — | 0EQ0hjjnRo5l5jBz0k1Y.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2300 | 0EQ0hjjnRo5l5jBz0k1Y.exe -pdaff5951618c2bbb4744ae85d2391bcf1af37443 | C:\media\0EQ0hjjnRo5l5jBz0k1Y.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2412 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIb2592.35266\pass.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2592.35959\MFCheat\MFCHEAT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2592.35959\MFCheat\MFCHEAT.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2592 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\MFCheat.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
986
Read events
934
Write events
52
Delete events
0
Modification events
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MFCheat.rar | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2592) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
3
Suspicious files
0
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2592.35959\MFCheat\MFCHEAT.exe | executable | |
MD5:— | SHA256:— | |||
| 2476 | MFCHEAT.exe | C:\media\AOgBis9dgs7mRQbhCLDbG8UURZv4qG.vbs | text | |
MD5:— | SHA256:— | |||
| 2080 | WScript.exe | C:\media\System.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2476 | MFCHEAT.exe | C:\media\ai0L27qAJjdumlx0CG00IDBTsmakju.bat | text | |
MD5:— | SHA256:— | |||
| 2300 | 0EQ0hjjnRo5l5jBz0k1Y.exe | C:\media\zFsrvFerbE6VofEpOdBJ7vIo4LYQLJ.bat | text | |
MD5:— | SHA256:— | |||
| 2300 | 0EQ0hjjnRo5l5jBz0k1Y.exe | C:\media\vmcheck32.dll | text | |
MD5:— | SHA256:— | |||
| 2300 | 0EQ0hjjnRo5l5jBz0k1Y.exe | C:\media\System.vbe | vbe | |
MD5:— | SHA256:— | |||
| 3156 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\System.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2476 | MFCHEAT.exe | C:\media\0EQ0hjjnRo5l5jBz0k1Y.exe | executable | |
MD5:— | SHA256:— | |||
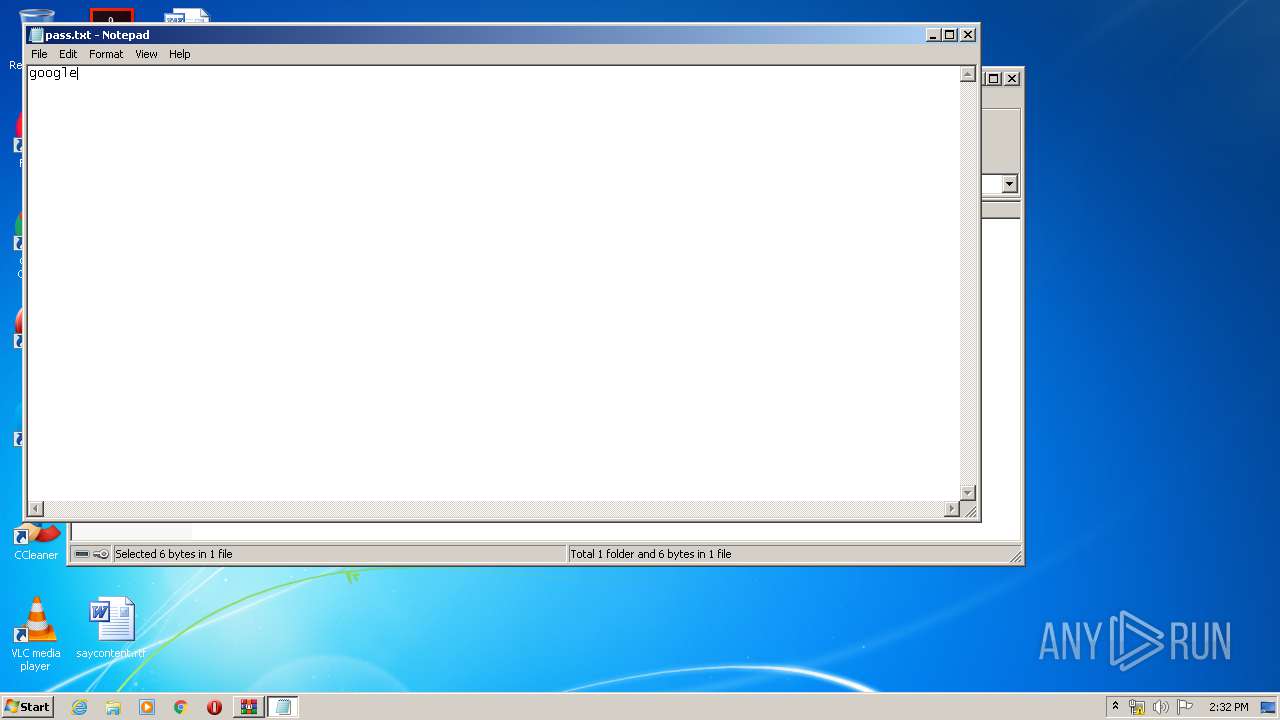
| 2592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2592.35266\pass.txt | text | |
MD5:C822C1B63853ED273B89687AC505F9FA | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
101
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1452 | mfcheat.exe | GET | 200 | 216.239.34.21:80 | http://ipinfo.io/ip | US | text | 15 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1452 | mfcheat.exe | 216.239.34.21:80 | ipinfo.io | Google Inc. | US | whitelisted |
1452 | mfcheat.exe | 45.147.197.70:80 | zzqserver.xyz | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zzqserver.xyz |
| malicious |
ipinfo.io |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1452 | mfcheat.exe | A Network Trojan was detected | ET TROJAN DCRat Initial CnC Activity |
1452 | mfcheat.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1452 | mfcheat.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1452 | mfcheat.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1452 | mfcheat.exe | A Network Trojan was detected | ET TROJAN DCRat CnC Activity |
1452 | mfcheat.exe | A Network Trojan was detected | MALWARE [PTsecurity] DCRAT |
1452 | mfcheat.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1452 | mfcheat.exe | A Network Trojan was detected | ET TROJAN DCRat CnC Activity |
1452 | mfcheat.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1452 | mfcheat.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup ipinfo.io |