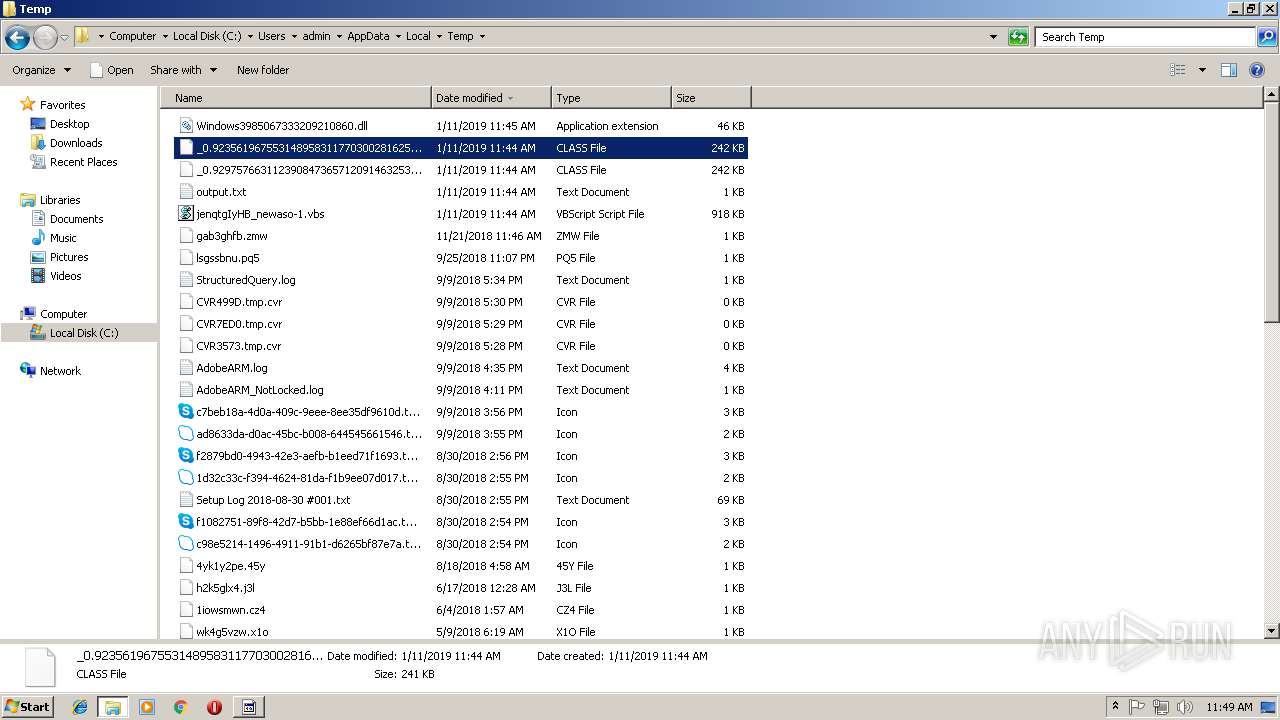
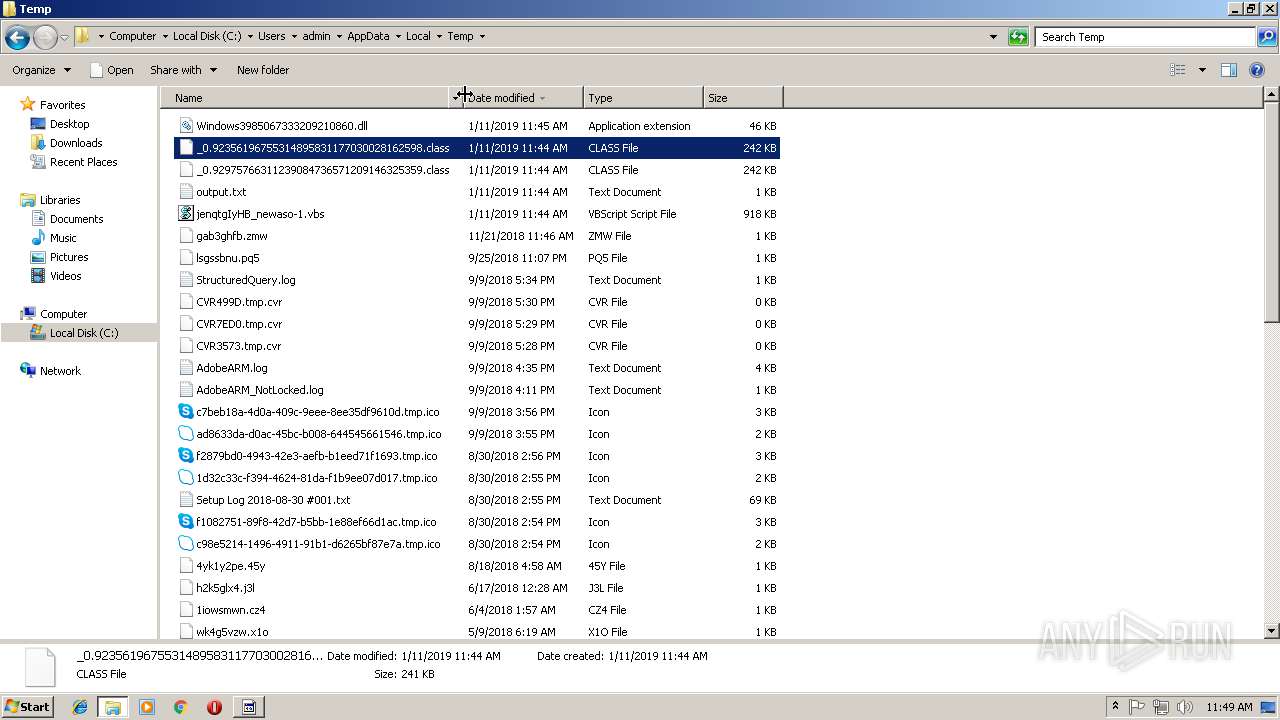
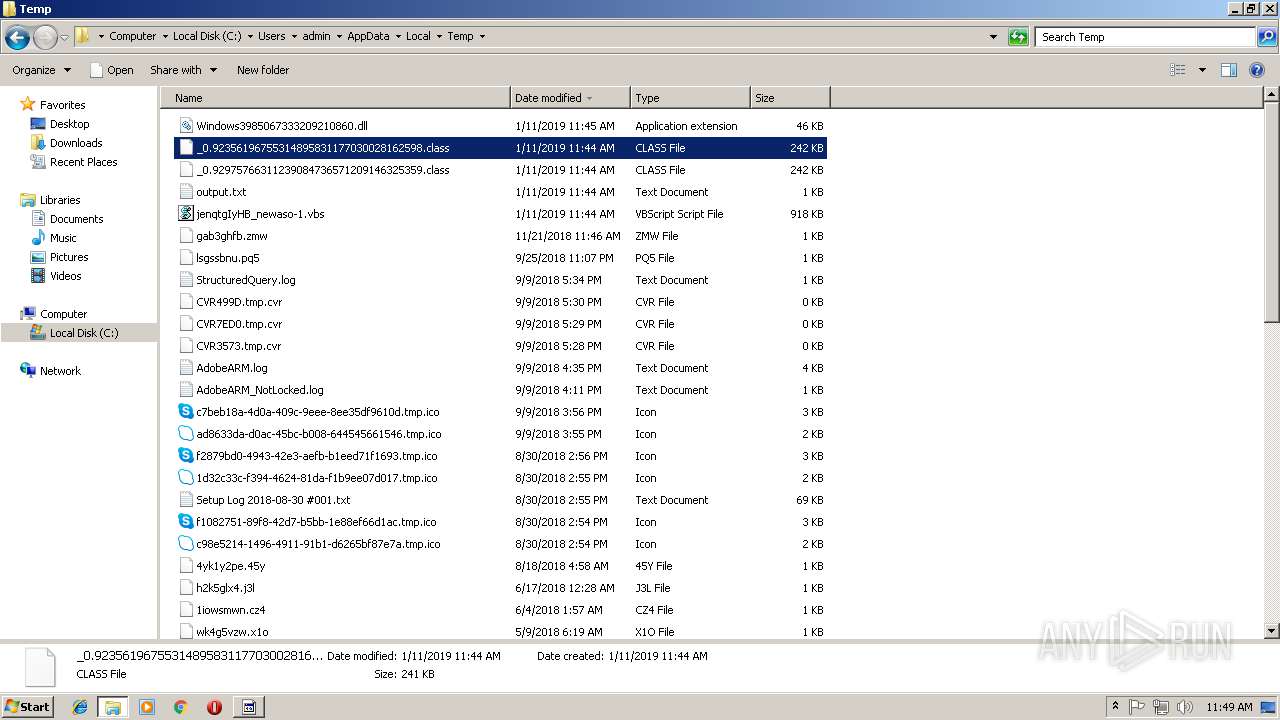
| File name: | jenqtgIyHB_newaso-1.vbs |
| Full analysis: | https://app.any.run/tasks/5b3a80a3-e16c-4ff3-8990-619fb98dce2c |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | January 11, 2019, 11:44:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines |
| MD5: | D060268AC9DED5AEF4EF02EC8746B855 |
| SHA1: | B7DDADAEF636F912E57A522B952EBBA81F208E94 |
| SHA256: | 97D49480DF6CCB207504396EDD8C99A342FFD4CA8F14A2C3B46054628FBBFB92 |
| SSDEEP: | 12288:G6N6PsB9/Sv1Im0xdCP3EG8m6UHd8J01N7mVXpVLlMnaNhUmj6EZ9e/g4S6K3CeI:GMCwRy0C0GyUc077aXOpnECI4SHK |
MALICIOUS
AdWind was detected
- java.exe (PID: 3816)
- java.exe (PID: 3076)
Loads dropped or rewritten executable
- java.exe (PID: 3816)
- javaw.exe (PID: 3344)
- javaw.exe (PID: 3888)
- javaw.exe (PID: 3752)
- WScript.exe (PID: 2960)
- java.exe (PID: 3076)
- cmd.exe (PID: 3128)
- explorer.exe (PID: 116)
Changes the autorun value in the registry
- reg.exe (PID: 3380)
- WScript.exe (PID: 2960)
- WScript.exe (PID: 2336)
Application was dropped or rewritten from another process
- java.exe (PID: 3816)
- javaw.exe (PID: 3888)
- javaw.exe (PID: 3344)
- javaw.exe (PID: 3752)
- java.exe (PID: 3076)
ADWIND was detected
- javaw.exe (PID: 3752)
Actions looks like stealing of personal data
- explorer.exe (PID: 116)
Writes to a start menu file
- WScript.exe (PID: 2336)
SUSPICIOUS
Executes scripts
- explorer.exe (PID: 116)
- cmd.exe (PID: 308)
- cmd.exe (PID: 2464)
- WScript.exe (PID: 2960)
- cmd.exe (PID: 3108)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 2196)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 2316)
Executes JAVA applets
- WScript.exe (PID: 2960)
- javaw.exe (PID: 3344)
- cmd.exe (PID: 3128)
Creates files in the user directory
- javaw.exe (PID: 3344)
- WScript.exe (PID: 2960)
- WScript.exe (PID: 2336)
- xcopy.exe (PID: 3732)
- notepad++.exe (PID: 2168)
Application launched itself
- WScript.exe (PID: 2960)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 3344)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 3344)
Starts itself from another location
- javaw.exe (PID: 3344)
Starts CMD.EXE for commands execution
- java.exe (PID: 3816)
- javaw.exe (PID: 3752)
- java.exe (PID: 3076)
- WScript.exe (PID: 2960)
- javaw.exe (PID: 3344)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3732)
- javaw.exe (PID: 3752)
Connects to unusual port
- javaw.exe (PID: 3752)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
88
Monitored processes
34
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive1114622237184961528.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 864 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1748 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive7585012980263568154.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1884 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 2128 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive5468907058527888957.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2132 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\output.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\GDIPFONTCACHEV1.DAT" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2196 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive584406034362763191.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2308 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8392861628791905762.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
52 542
Read events
51 879
Write events
663
Delete events
0
Modification events
| (PID) Process: | (2960) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2960) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\UwwogLCzsN |
| Operation: | write | Name: | |
Value: false - 1/11/2019 | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UwwogLCzsN |
Value: wscript.exe //B "C:\Users\admin\AppData\Roaming\UwwogLCzsN.vbs" | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | UwwogLCzsN |
Value: wscript.exe //B "C:\Users\admin\AppData\Roaming\UwwogLCzsN.vbs" | |||
| (PID) Process: | (2960) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | ntfsmgr |
Value: "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\ntfsmgr.jar" | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2336) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\WScript_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
111
Suspicious files
10
Text files
83
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3344 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive4596543679496563502.vbs | — | |
MD5:— | SHA256:— | |||
| 3816 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive1493447988114851523.vbs | — | |
MD5:— | SHA256:— | |||
| 2960 | WScript.exe | C:\Users\admin\AppData\Roaming\UwwogLCzsN.vbs | text | |
MD5:— | SHA256:— | |||
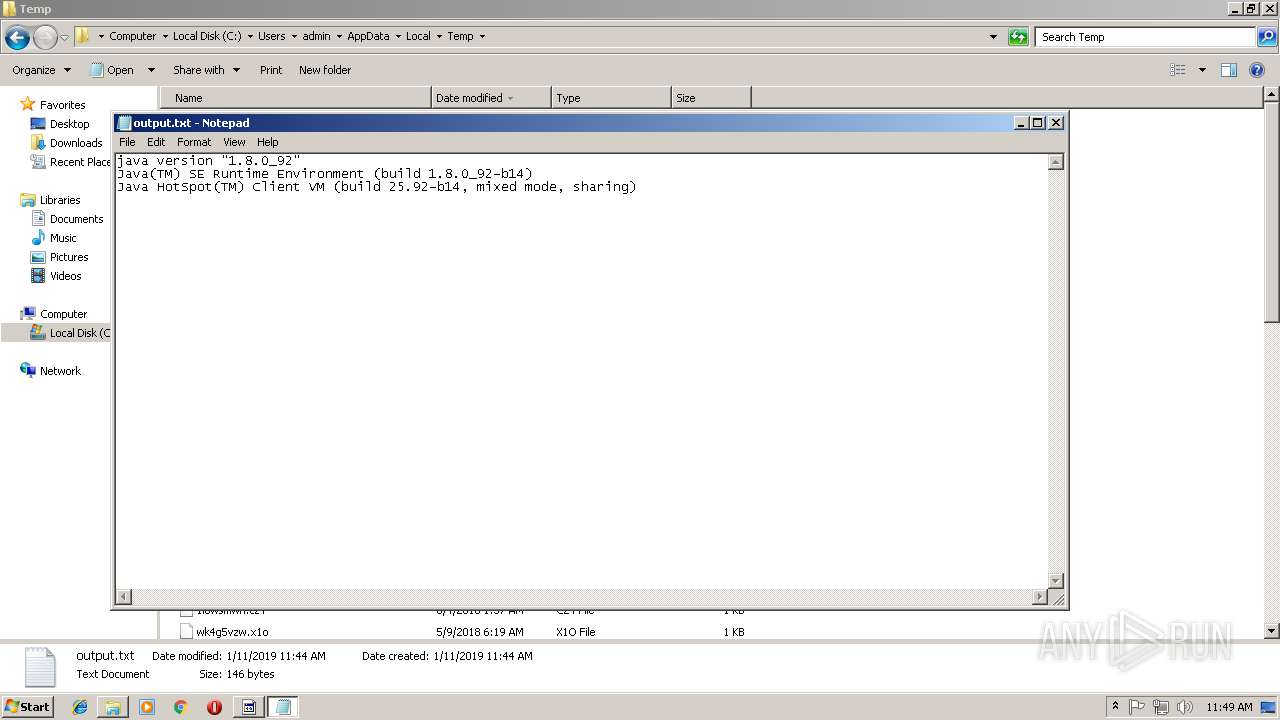
| 3128 | cmd.exe | C:\Users\admin\AppData\Local\Temp\output.txt | text | |
MD5:— | SHA256:— | |||
| 2336 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\UwwogLCzsN.vbs | text | |
MD5:— | SHA256:— | |||
| 3816 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3344 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3888 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2960 | WScript.exe | C:\Users\admin\AppData\Roaming\ntfsmgr.jar | java | |
MD5:— | SHA256:— | |||
| 3344 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\83aa4cc77f591dfc2374580bbd95f6ba_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 195.138.255.24:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | DE | der | 727 b | whitelisted |
— | — | GET | 200 | 195.138.255.24:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | DE | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3752 | javaw.exe | 185.125.205.77:7524 | asorock0011.ddns.net | — | DE | malicious |
1884 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
— | — | 195.138.255.24:80 | ocsp.usertrust.com | AS33891 Netzbetrieb GmbH | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
goz.unknowncrypter.com |
| malicious |
asorock0011.ddns.net |
| malicious |
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3752 | javaw.exe | A Network Trojan was detected | ET TROJAN Possible Adwind SSL Cert (assylias.Inc) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|