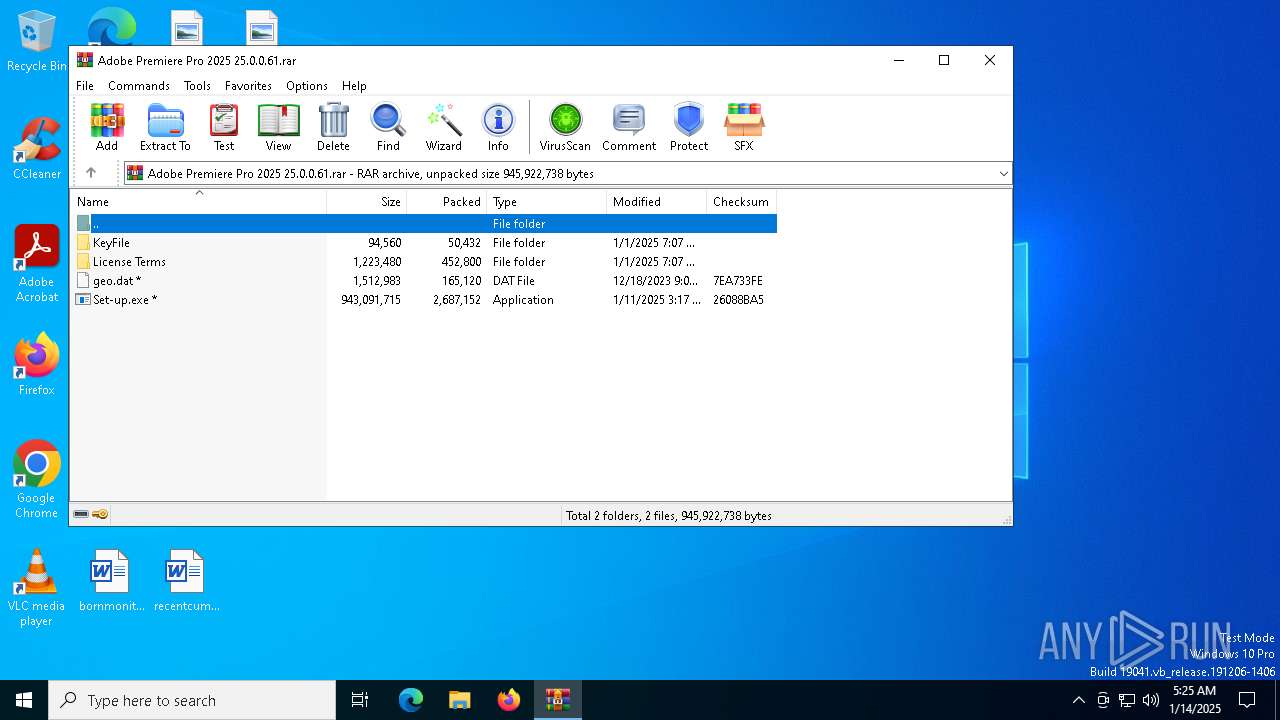
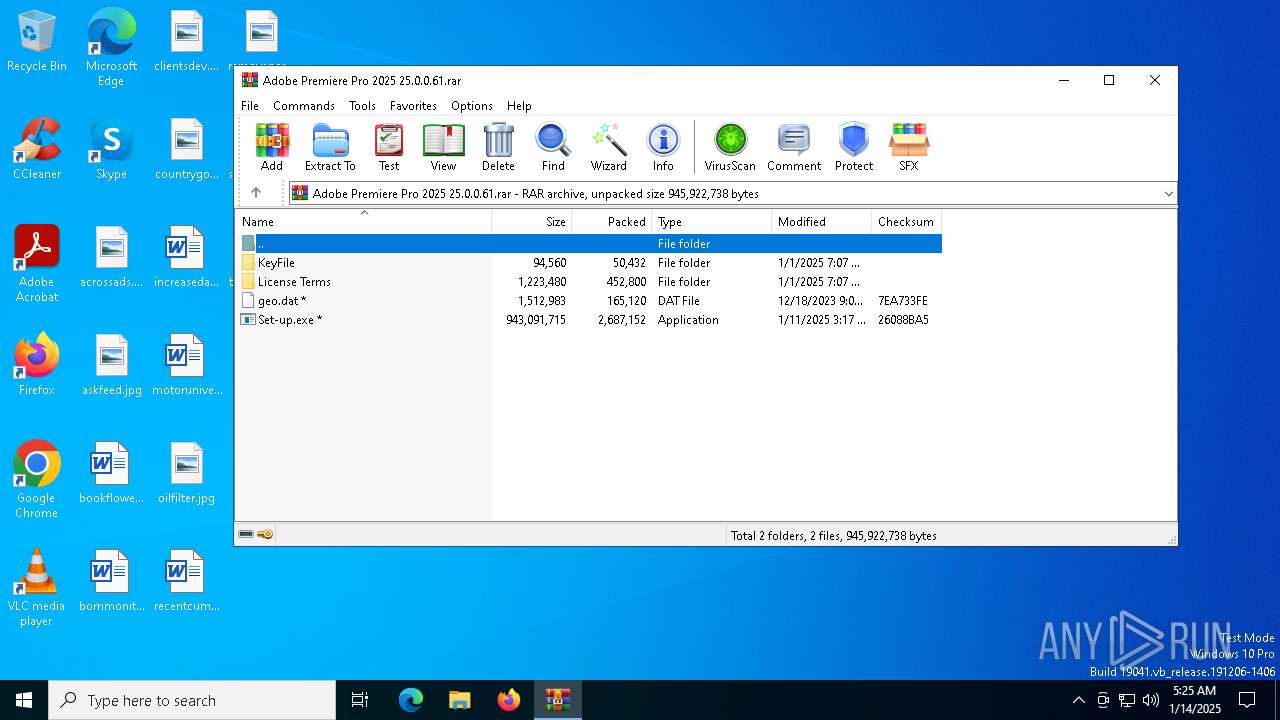
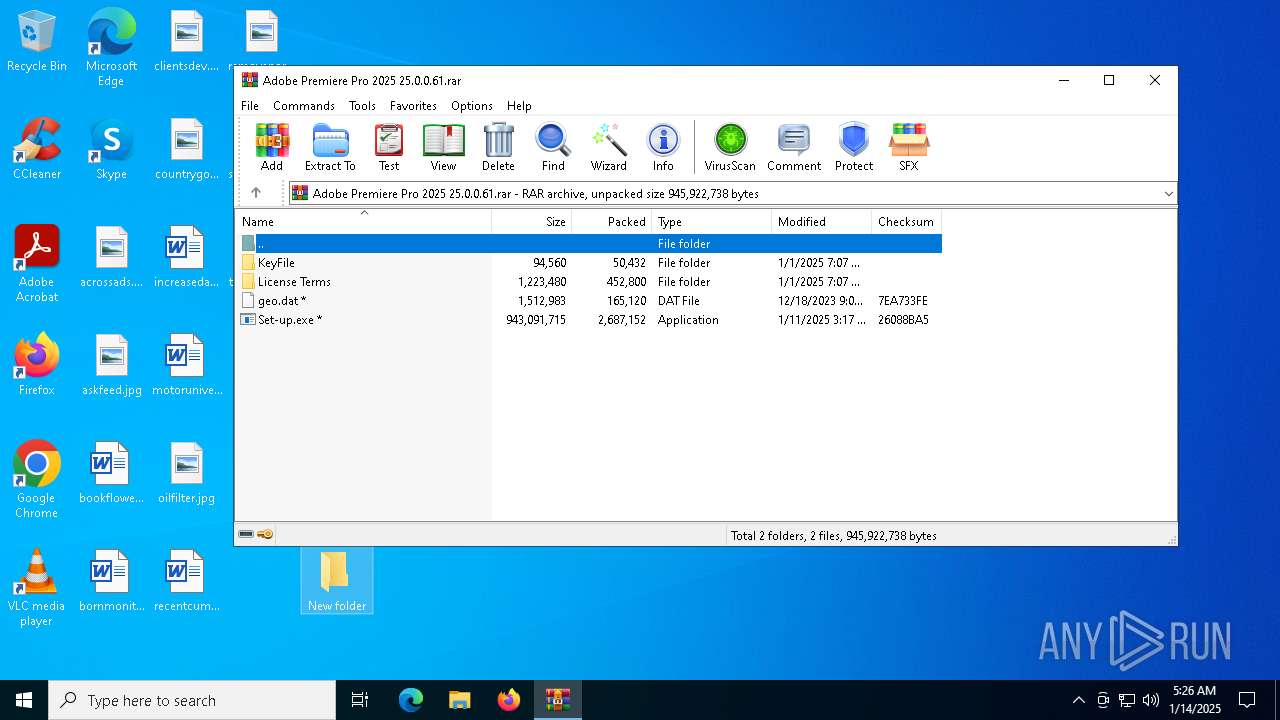
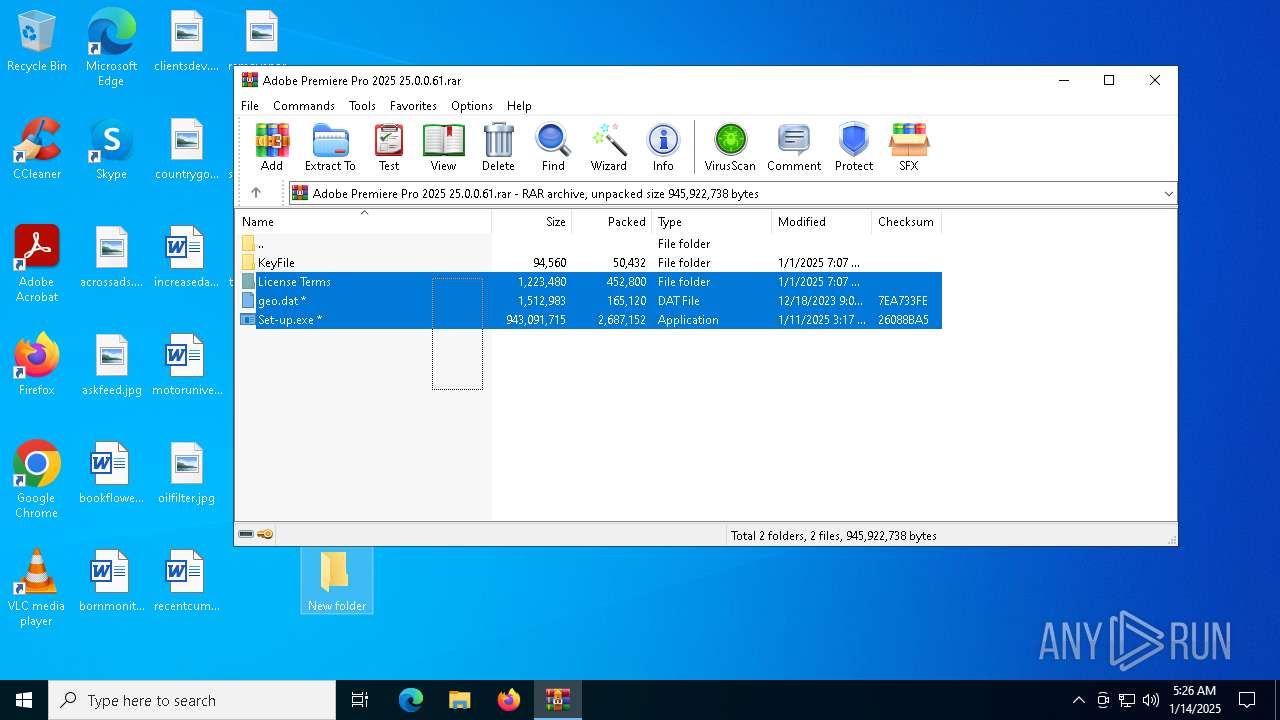
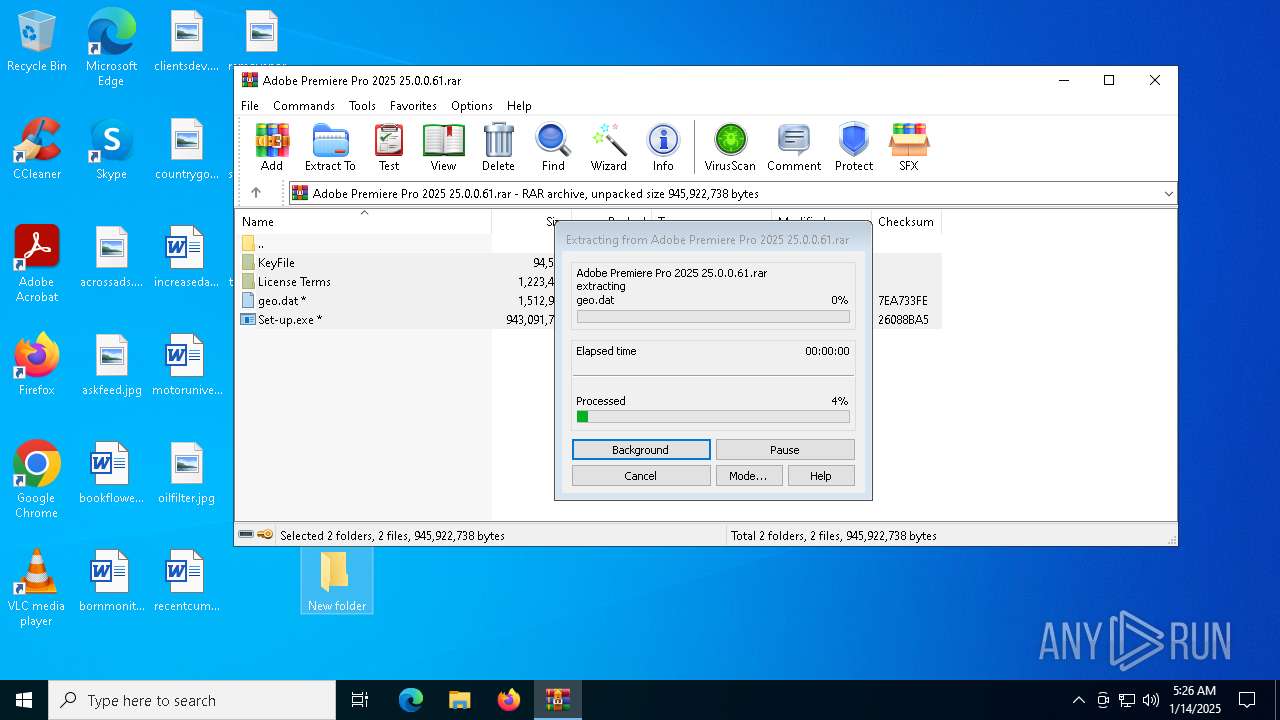
| File name: | Adobe Premiere Pro 2025 25.0.0.61.rar |
| Full analysis: | https://app.any.run/tasks/eab715fc-71a0-4c23-af8a-fb46a04b803e |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 14, 2025, 05:25:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7CE77D72D9724D7B5569E1141B03273F |
| SHA1: | 2DF50146DDAB7BB70FA024BBBA227ECFDACACD24 |
| SHA256: | 97B5C3B4B01E06A03B8D5070EC9DE2DB537416BF40462167D8C2F45EB2702C41 |
| SSDEEP: | 98304:JgW9fg5EDNXS11l63edKsPtjACd0bUEvtcOwB4pfxKAaoz+ZFF+c9pgPOKjz/fyP:gXZ |
MALICIOUS
LUMMA mutex has been found
- BitLockerToGo.exe (PID: 3848)
Steals credentials from Web Browsers
- BitLockerToGo.exe (PID: 3848)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 3848)
LUMMA has been detected (YARA)
- BitLockerToGo.exe (PID: 3848)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6016)
WINSCP has been detected
- Set-up.exe (PID: 2216)
There is functionality for communication over UDP network (YARA)
- Set-up.exe (PID: 2216)
Found regular expressions for crypto-addresses (YARA)
- Set-up.exe (PID: 2216)
Searches for installed software
- BitLockerToGo.exe (PID: 3848)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6016)
The sample compiled with german language support
- WinRAR.exe (PID: 6016)
The sample compiled with spanish language support
- WinRAR.exe (PID: 6016)
The sample compiled with japanese language support
- WinRAR.exe (PID: 6016)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6016)
Reads the computer name
- BitLockerToGo.exe (PID: 3848)
Reads the software policy settings
- BitLockerToGo.exe (PID: 3848)
The sample compiled with Italian language support
- WinRAR.exe (PID: 6016)
The sample compiled with russian language support
- WinRAR.exe (PID: 6016)
Manual execution by a user
- Set-up.exe (PID: 2216)
The sample compiled with chinese language support
- WinRAR.exe (PID: 6016)
The sample compiled with korean language support
- WinRAR.exe (PID: 6016)
The sample compiled with portuguese language support
- WinRAR.exe (PID: 6016)
The sample compiled with french language support
- WinRAR.exe (PID: 6016)
Checks supported languages
- Set-up.exe (PID: 2216)
- BitLockerToGo.exe (PID: 3848)
The process uses the downloaded file
- WinRAR.exe (PID: 6016)
Application based on Golang
- Set-up.exe (PID: 2216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
132
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2216 | "C:\Users\admin\Desktop\New folder\Set-up.exe" | C:\Users\admin\Desktop\New folder\Set-up.exe | explorer.exe | ||||||||||||
User: admin Company: Martin Prikryl Integrity Level: MEDIUM Description: WinSCP: SFTP, FTP, WebDAV, S3 and SCP client Exit code: 666 Version: 6.3.4.14955 Modules
| |||||||||||||||
| 3652 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | Set-up.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6016 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Adobe Premiere Pro 2025 25.0.0.61.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 472
Read events
4 451
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Adobe Premiere Pro 2025 25.0.0.61.rar | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
19
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\Set-up.exe | — | |
MD5:— | SHA256:— | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\geo.dat | binary | |
MD5:79423DAA2BF4F352B7B18DDE5E4ACCAD | SHA256:E8DA9867F215B070F5A2D184AA6473279B06C06C8C8C7D9610548A3BC501CBFA | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\License Terms\150\LocalDB\Binn\SqlUserInstance.dll | executable | |
MD5:26F2FFE2B77E18F02AD44DFE0976C084 | SHA256:EC41019A6AE2874E75D5856E845EB42B2ADA2E738467B11E44868061F552C617 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\KeyFile\1049\sqlsysclrtypes_keyfile.dll | executable | |
MD5:5E54CB9759D1A9416F51AC1E759BBCCF | SHA256:F7E5CAE32E2EC2C35346954BFB0B7352F9A697C08586E52494A71EF00E40D948 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\KeyFile\1033\sqlsysclrtypes_keyfile.dll | executable | |
MD5:5E54CB9759D1A9416F51AC1E759BBCCF | SHA256:F7E5CAE32E2EC2C35346954BFB0B7352F9A697C08586E52494A71EF00E40D948 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\License Terms\150\LocalDB\Binn\Resources\it-IT\SqlUserInstance.rll.mui | executable | |
MD5:2950C68D38391AB2C206E5AB231C0945 | SHA256:F58EEC9CECE4BBB1ABE97241CFCBBEE35A6CEAFCF8A39AFBA122693AF13A42F3 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\License Terms\150\LocalDB\Binn\Resources\ko-KR\SqlUserInstance.rll.mui | executable | |
MD5:BA2E9AC880F22762DB631E4F183D9D25 | SHA256:626CC8832025D12F8CB79E11ECDE52AD499053E2E7C9ABAF785DE5C7F5CC1AB6 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\License Terms\150\LocalDB\Binn\Resources\ru-RU\SqlUserInstance.rll.mui | executable | |
MD5:951E8BEDF4AA6A878E98206D88B6D0E8 | SHA256:0C9F35B1A60054E5455201EDE66F021D5B4EDE92D0BA2ADD88CFBC910C632691 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\License Terms\150\LocalDB\Binn\Resources\zh-CN\SqlUserInstance.rll.mui | executable | |
MD5:FC5831D92A79C879D6DA3A30351EBE24 | SHA256:2F8BA9E830FB7937F34A1278525DF941B684D453134A676F21C358B127070859 | |||
| 6016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6016.18394\License Terms\150\LocalDB\Binn\Resources\en-US\SqlUserInstance.rll.mui | executable | |
MD5:FC4F82A8DE54CCB30DE50D9981AC6839 | SHA256:F98754389A248C07098A28AADD445863AB73273497803CDE52CC90EC6CEBB359 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6236 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7100 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7100 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
440 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |