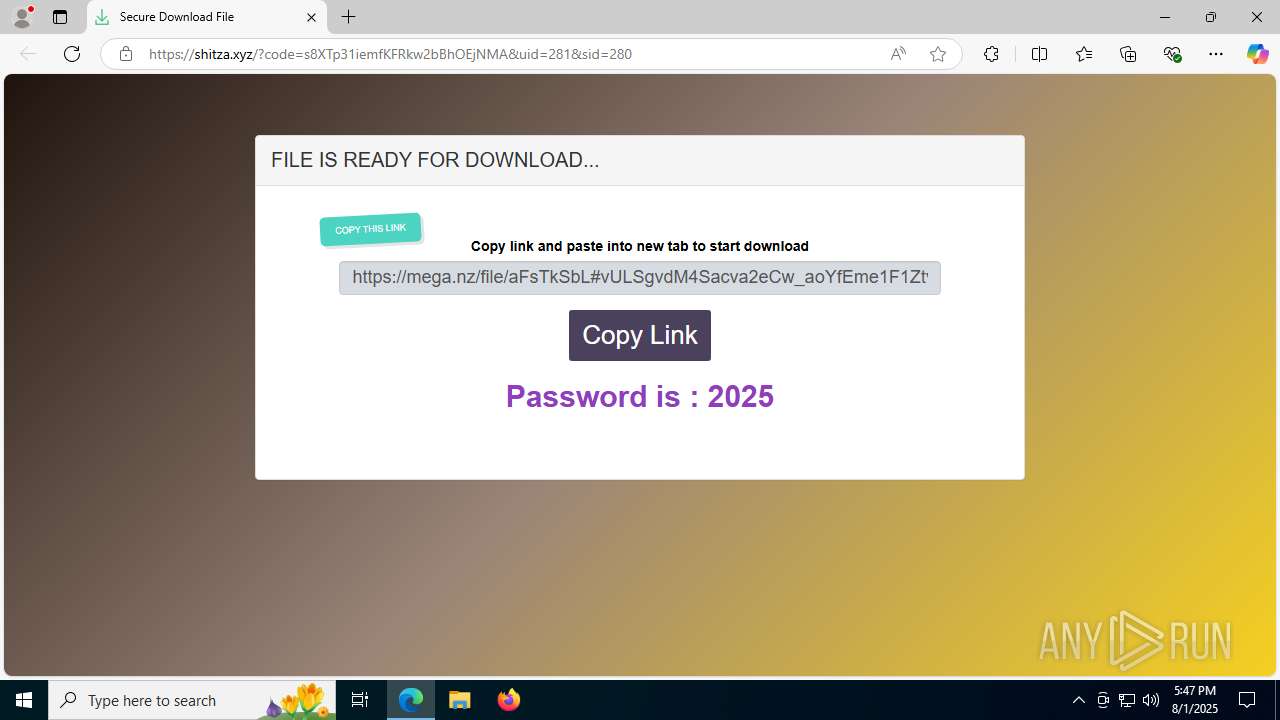
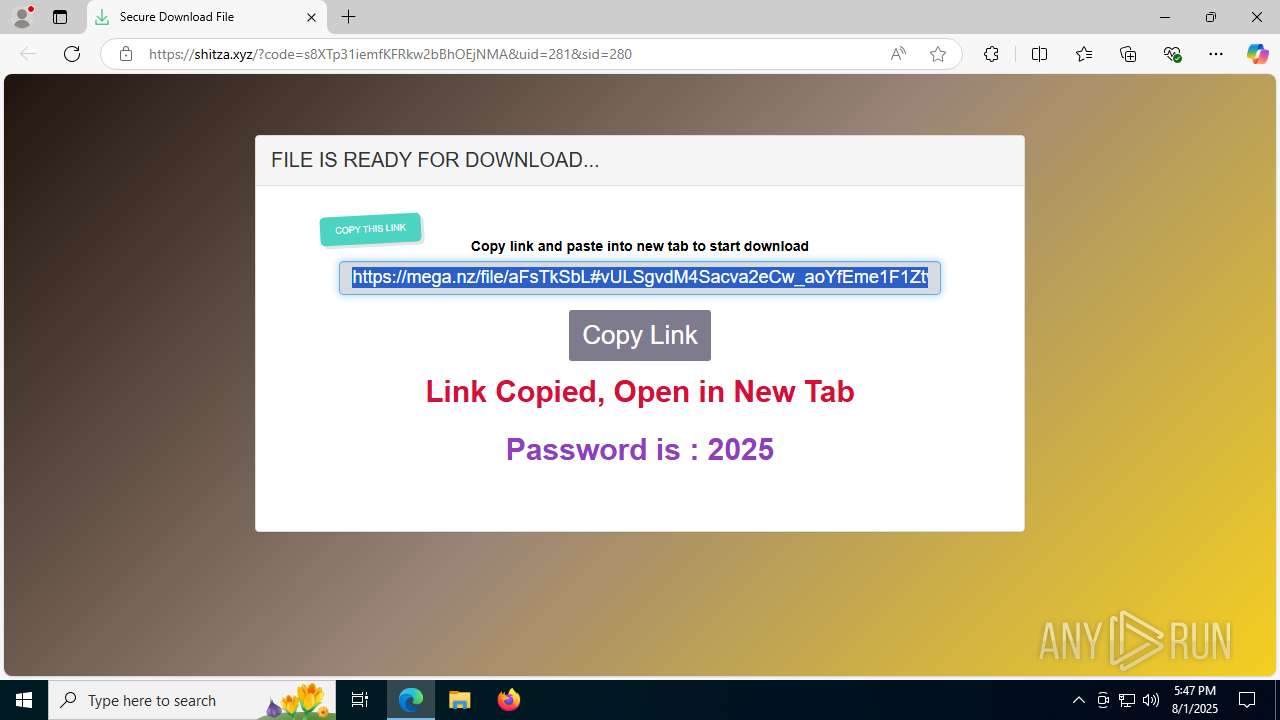
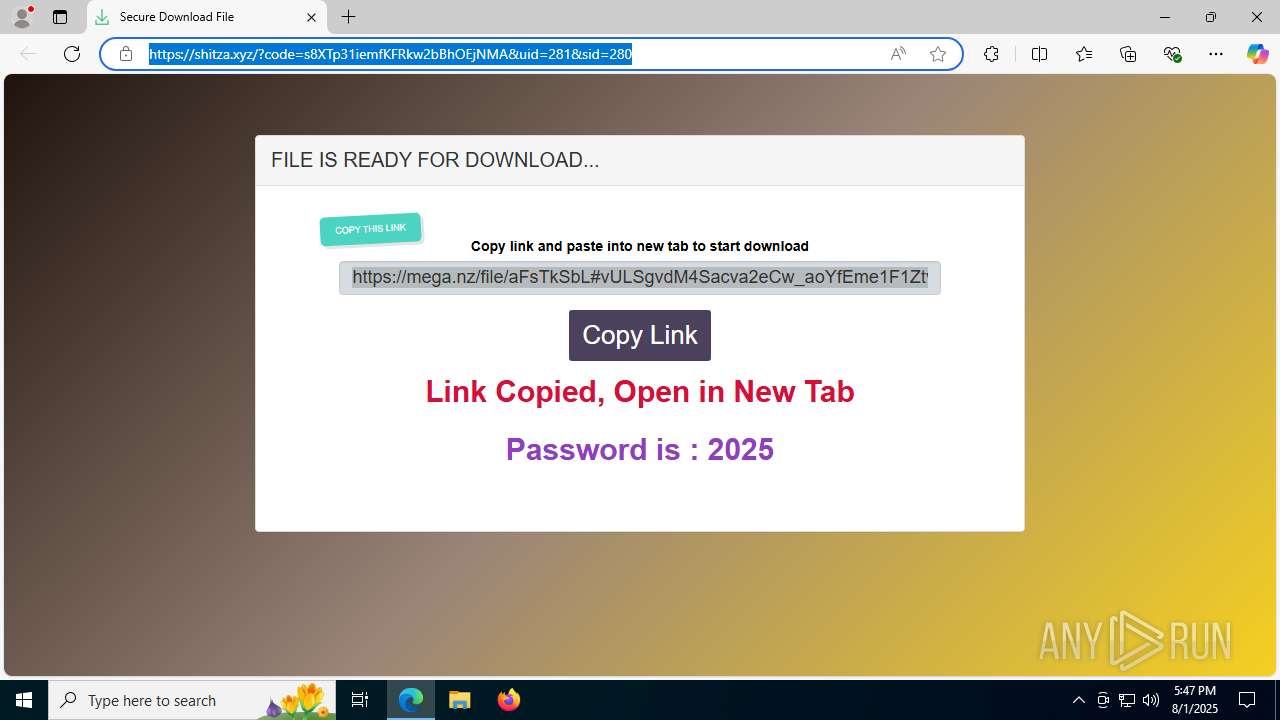
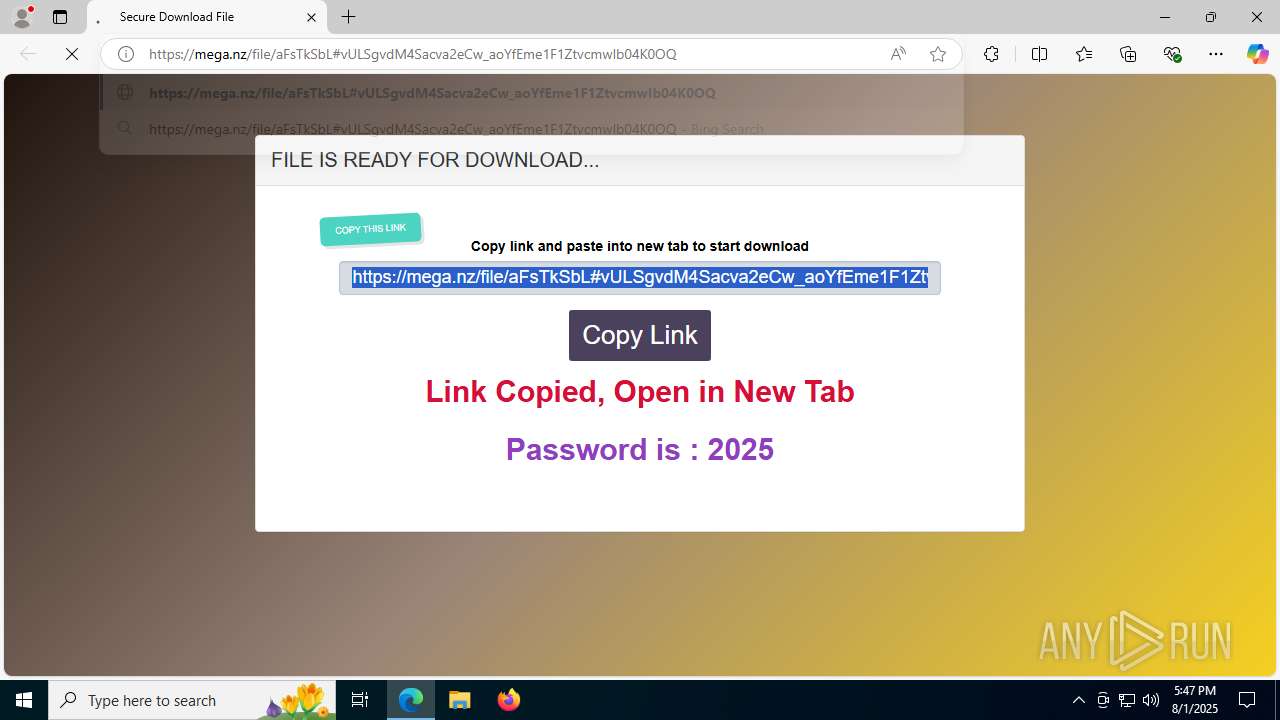
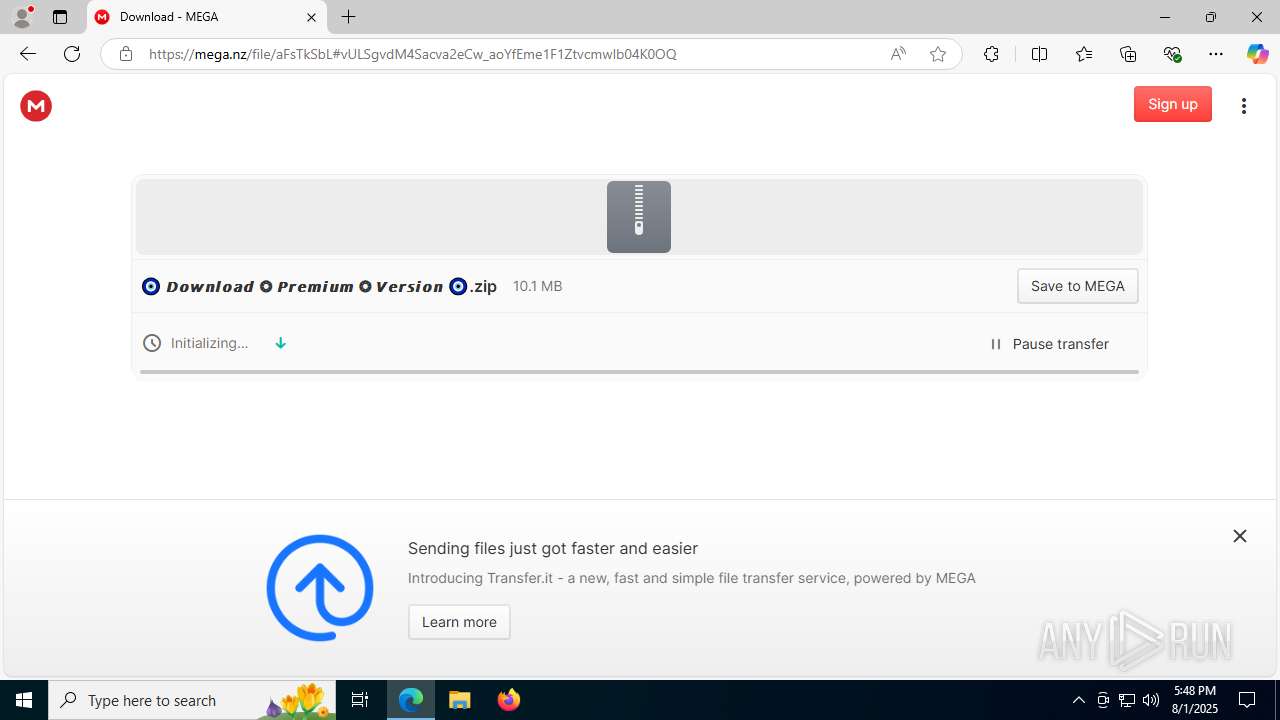
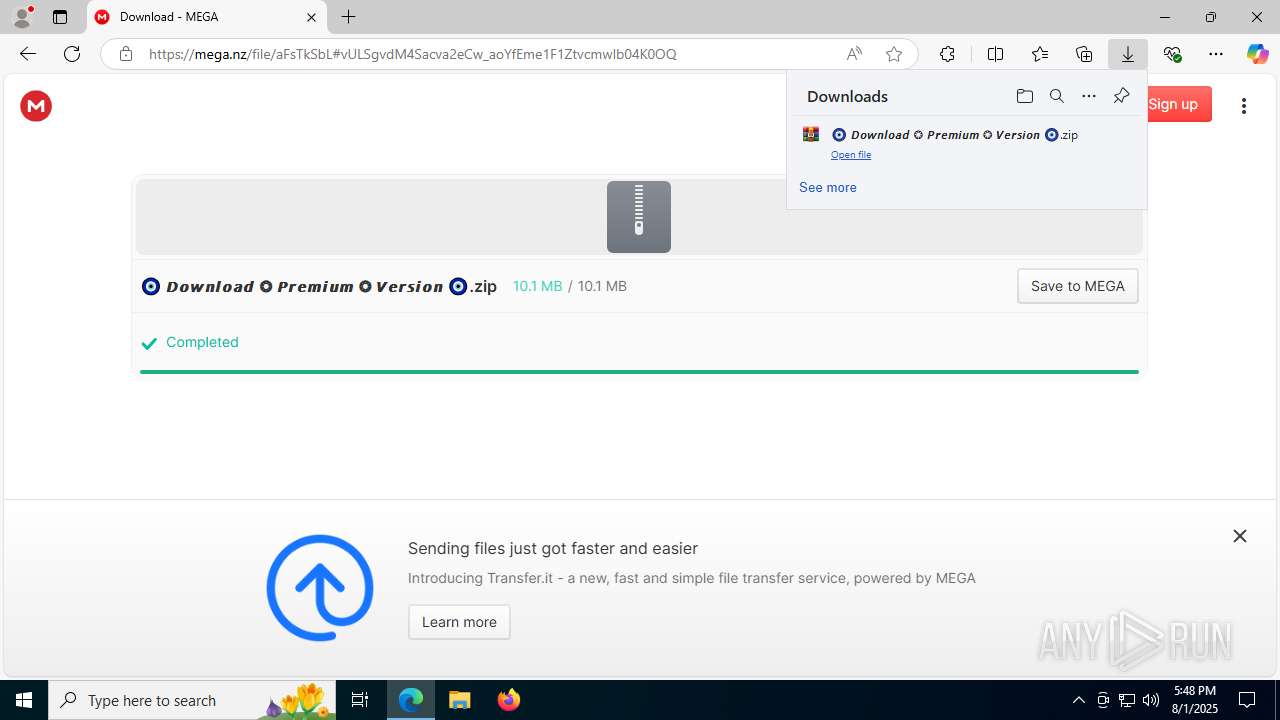
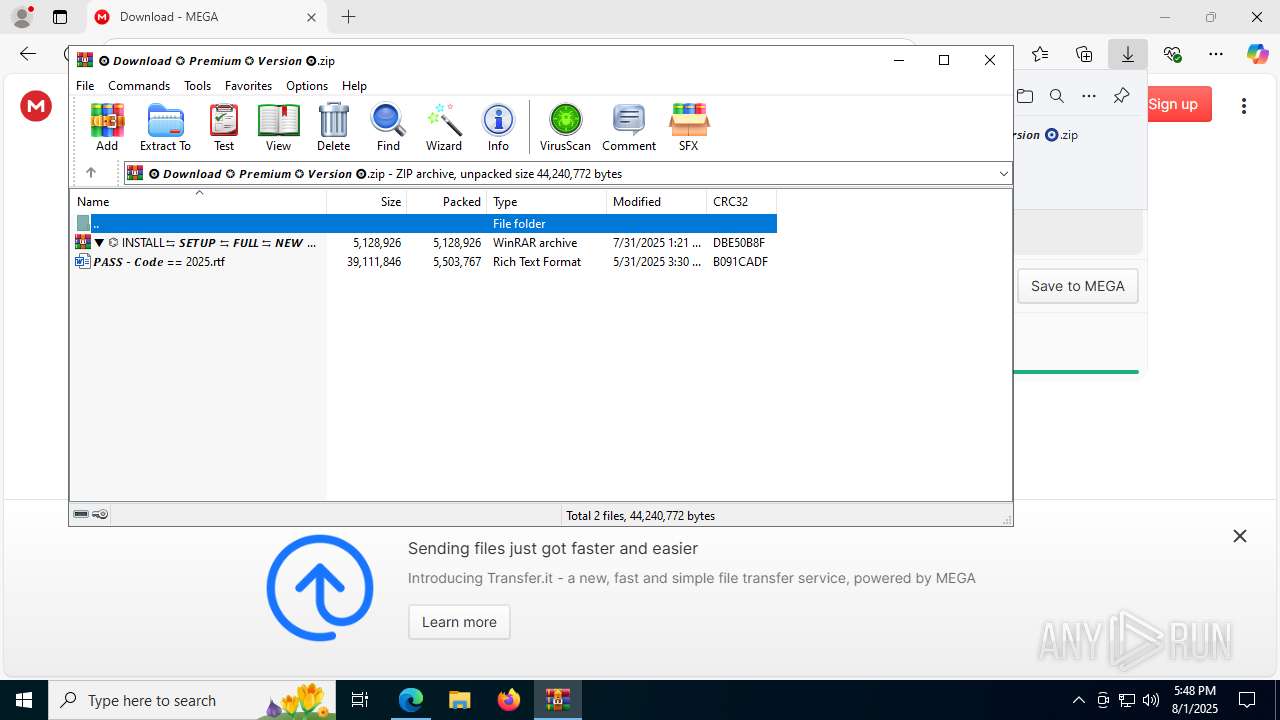
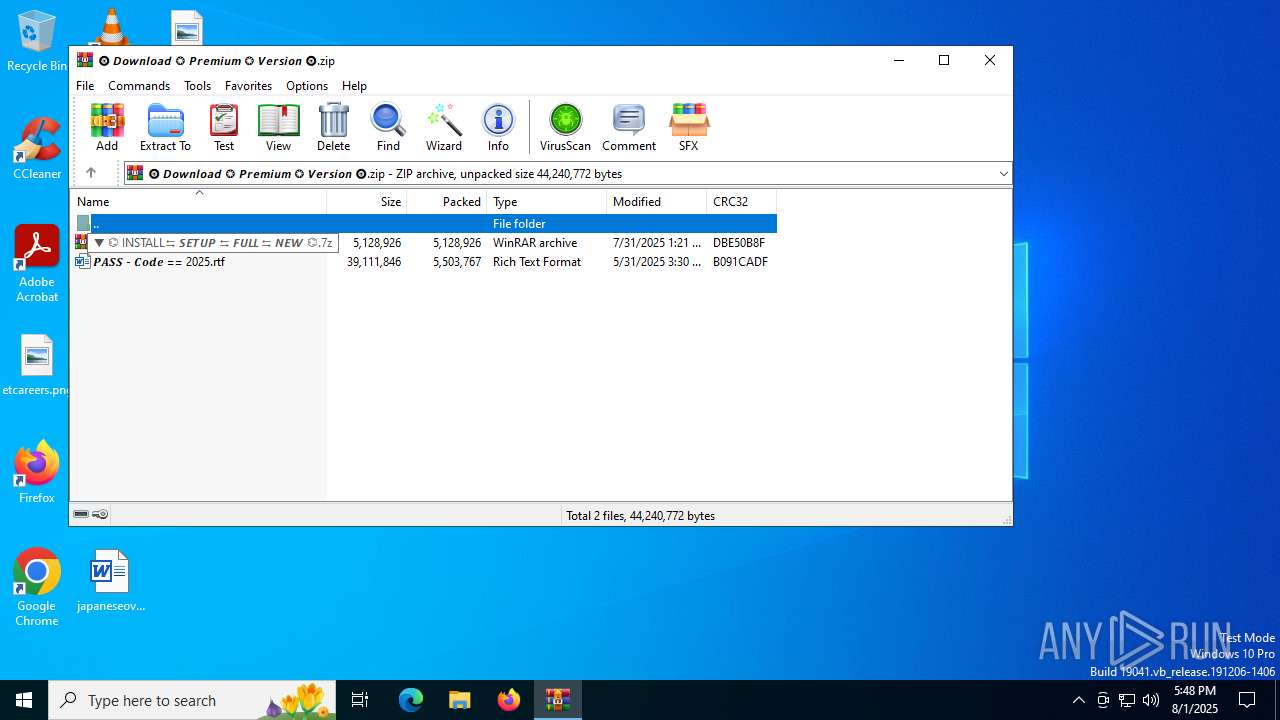
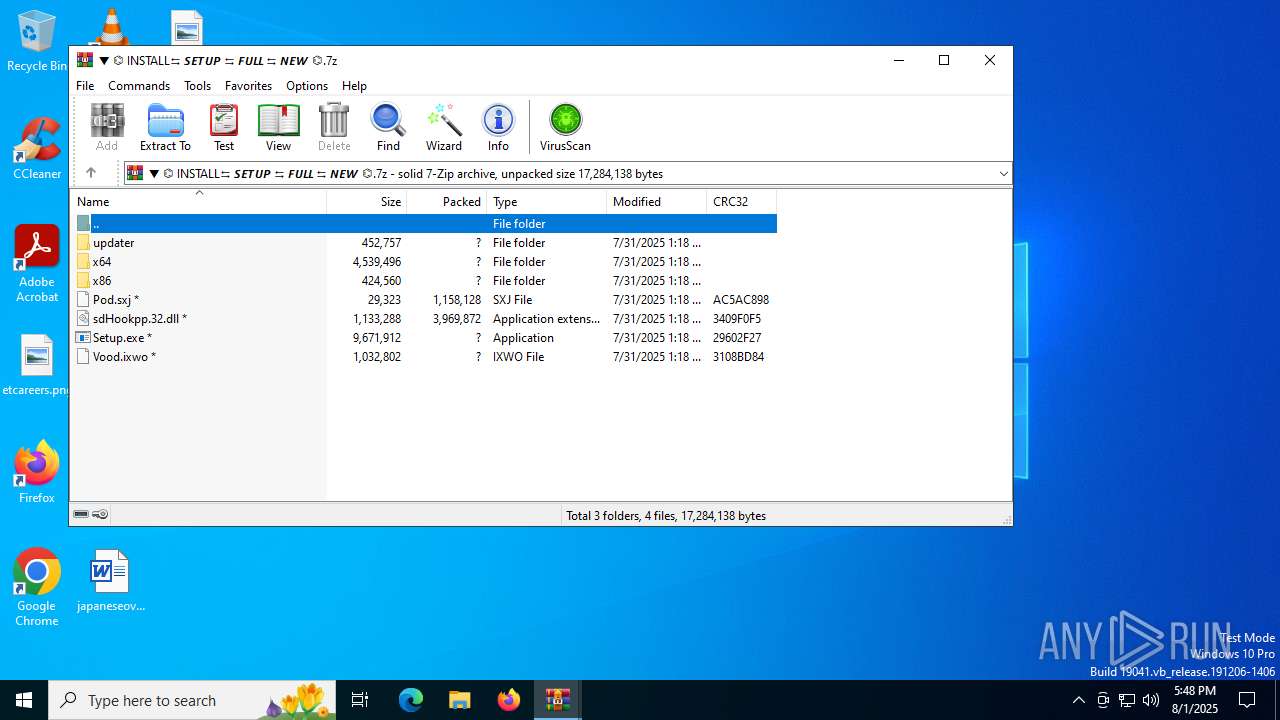
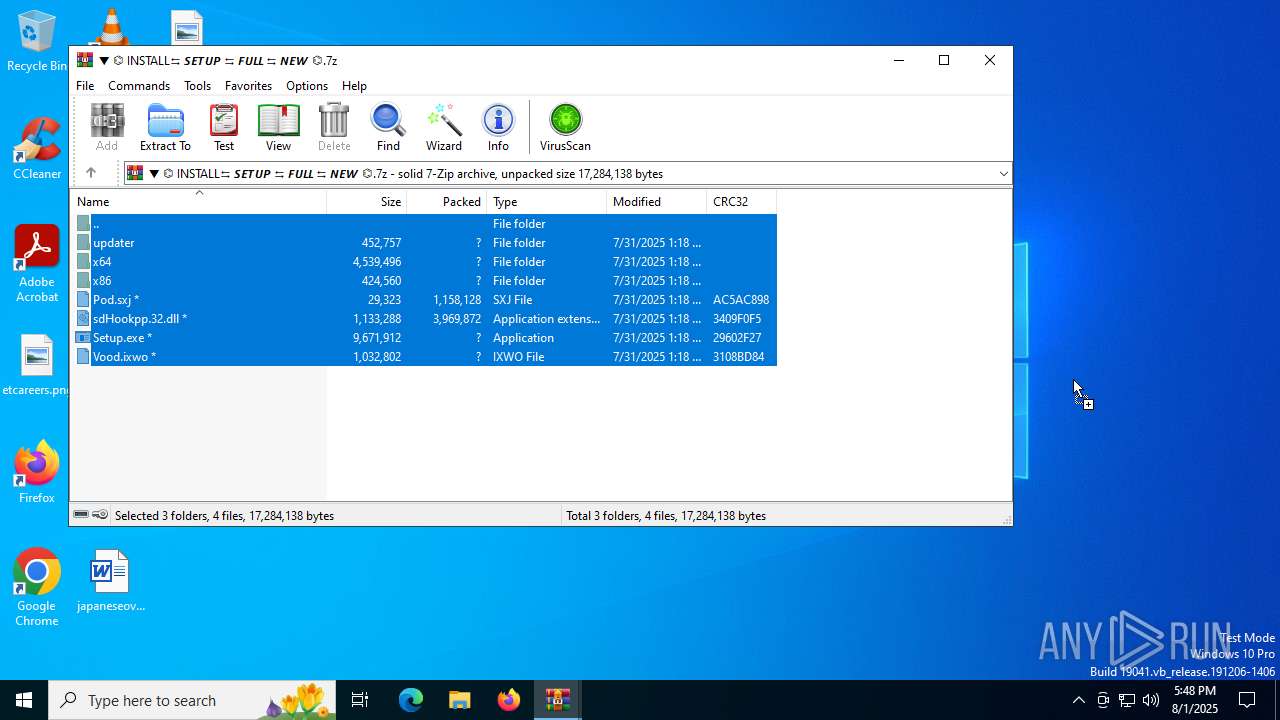
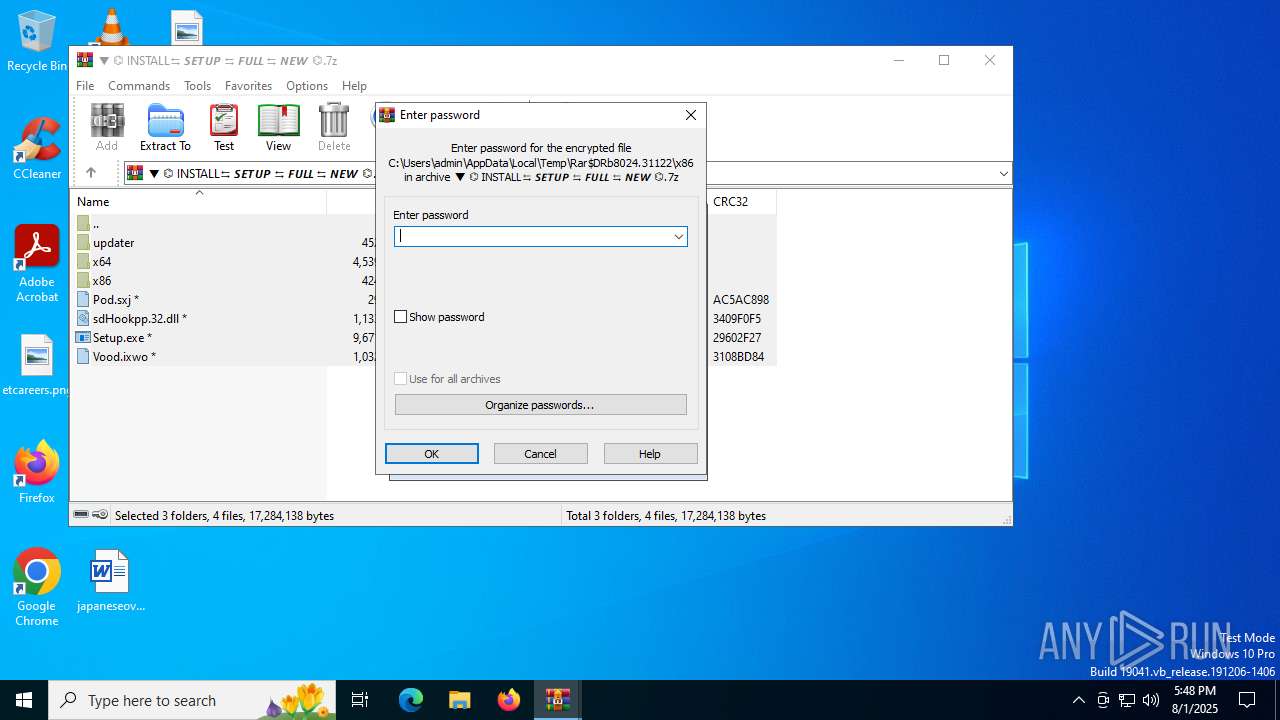
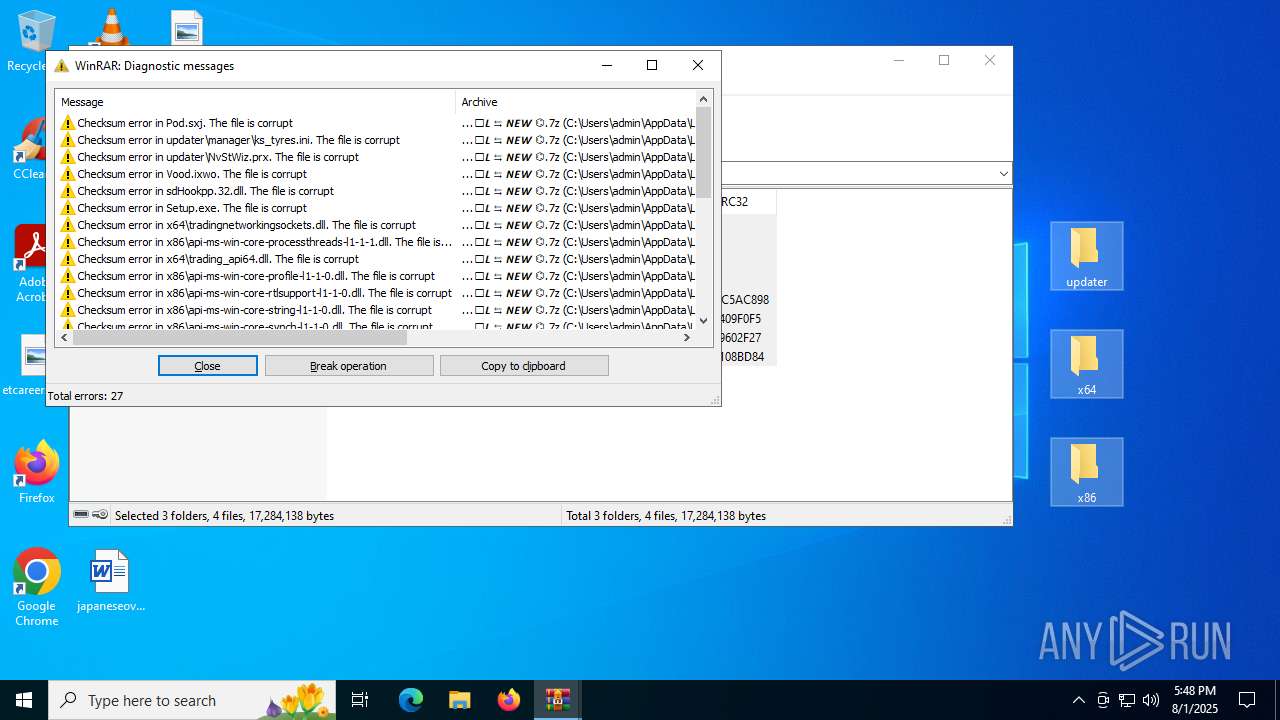
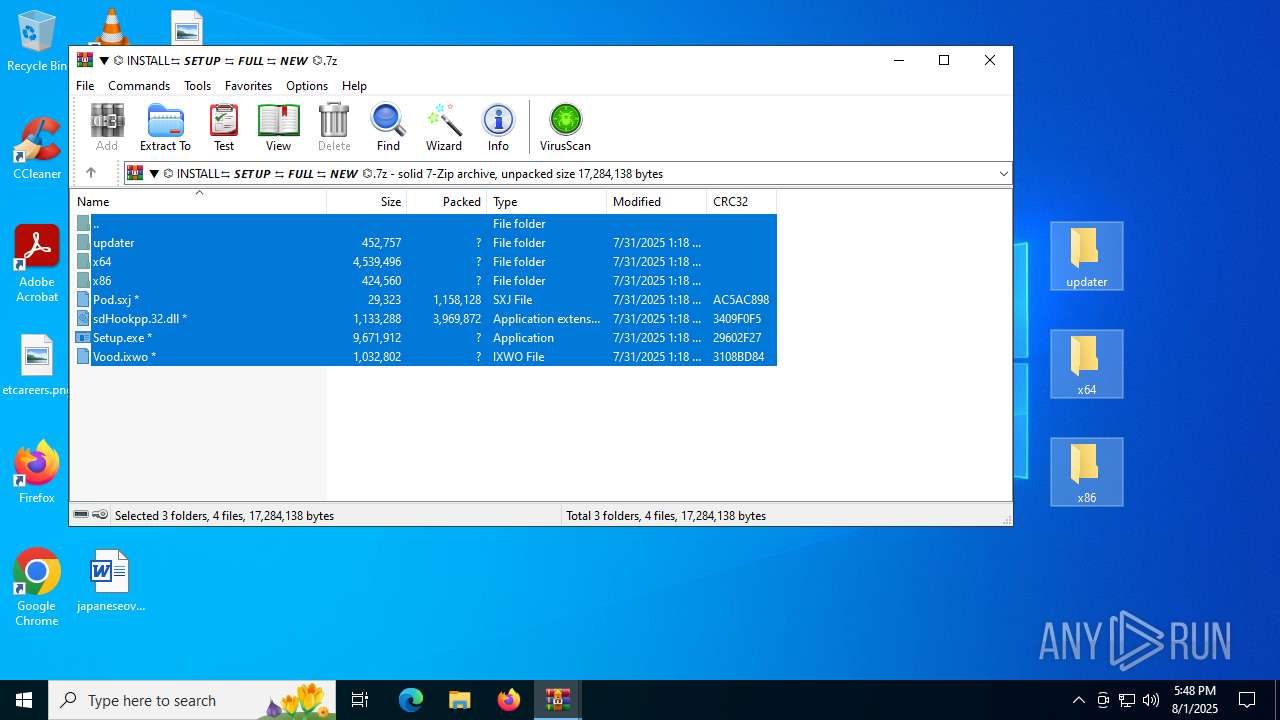
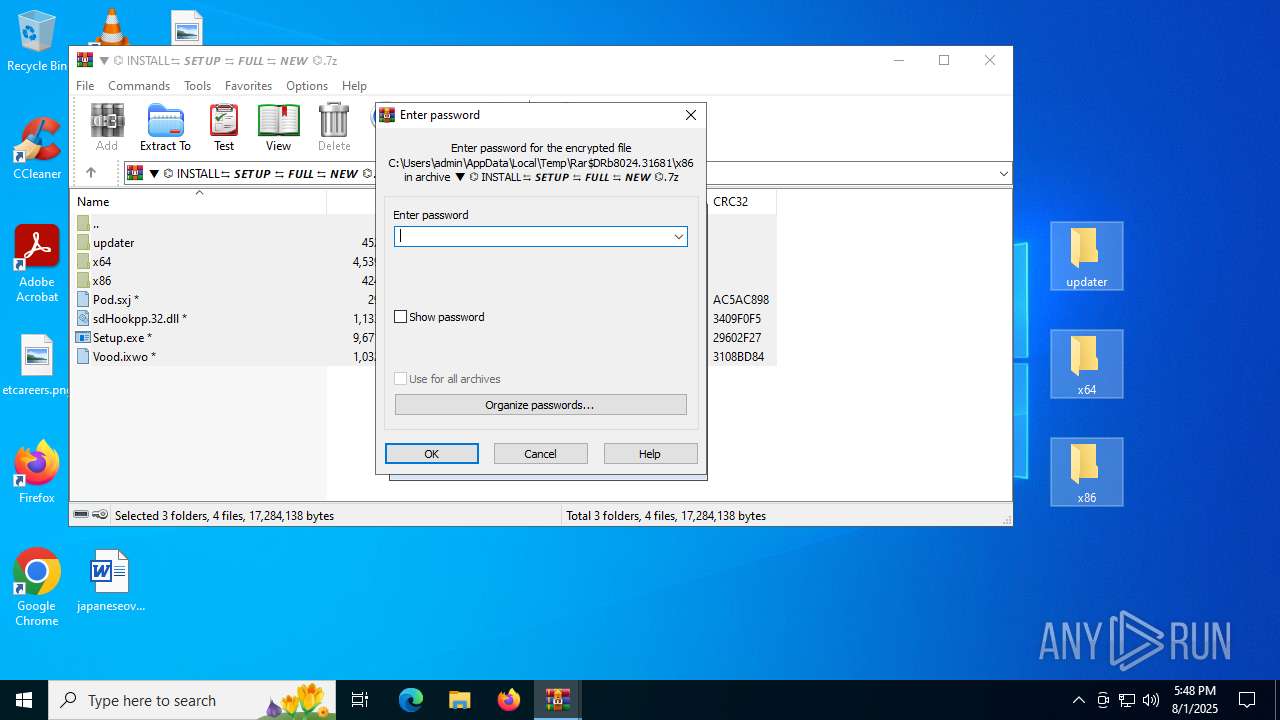
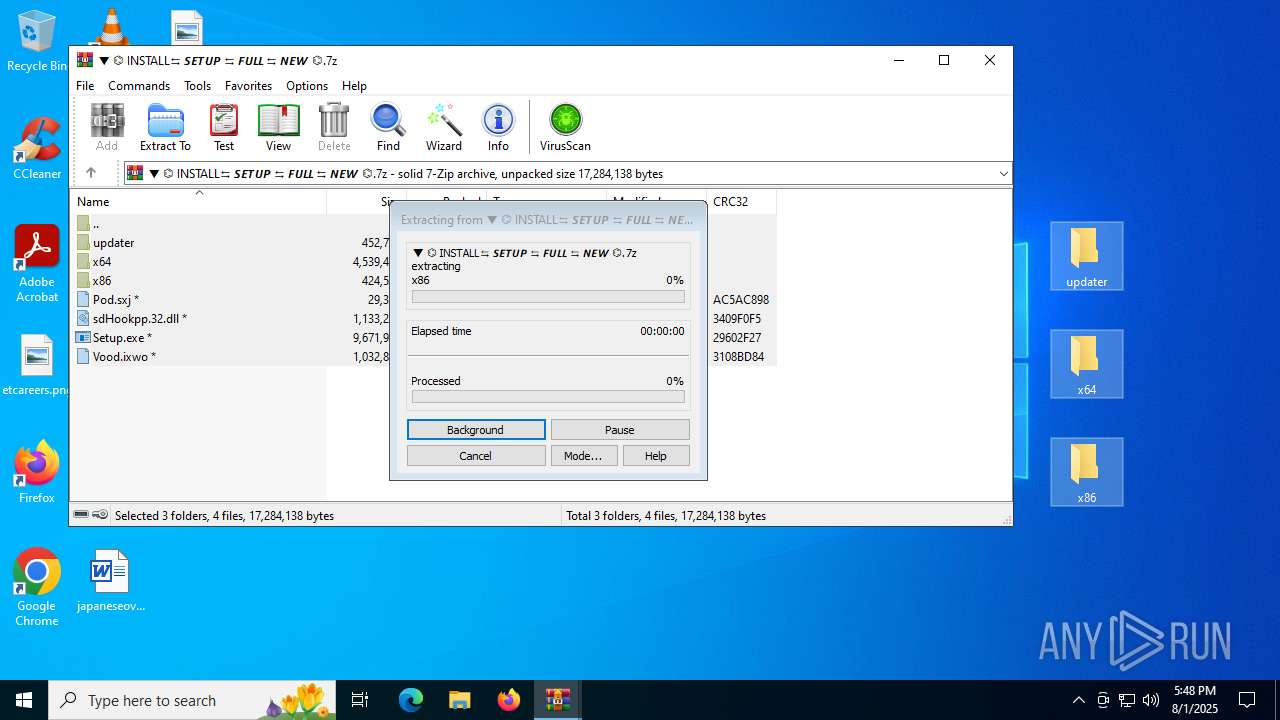
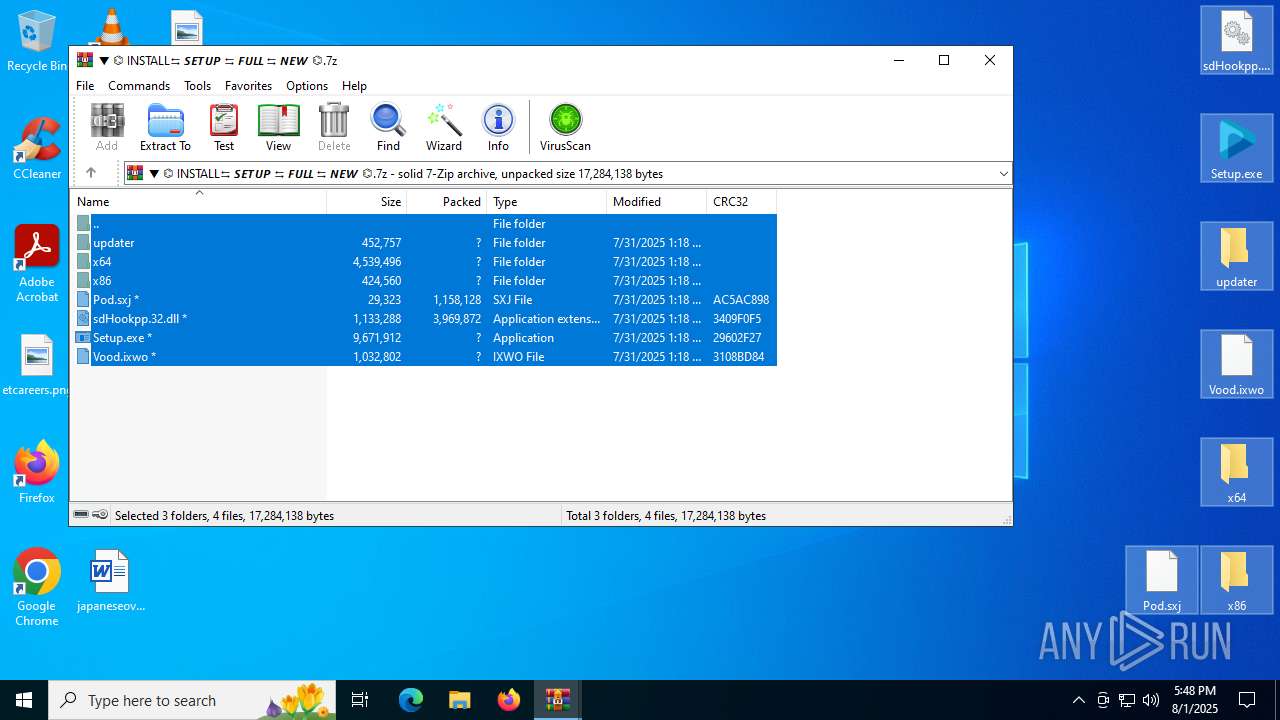
| URL: | https://shitza.xyz/?code=s8XTp31iemfKFRkw2bBhOEjNMA&uid=281&sid=280 |
| Full analysis: | https://app.any.run/tasks/5fba4e9f-2a22-415e-8f1d-f8c3ceeef94c |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | August 01, 2025, 17:46:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A587AF2B8F739733FFB63E38AAD7F05E |
| SHA1: | 4028594686F464F285E2BB7287FDFB76CD4B79C4 |
| SHA256: | 9772B6A95F7361C1231239E6E074055B7386AB240D28CDC33B733A540B1818CE |
| SSDEEP: | 3:N8AK9Gs9s+wbTWXdUAVn:2AK9Hs+w/WNUAV |
MALICIOUS
LUMMA has been detected (SURICATA)
- msedge.exe (PID: 6340)
- svchost.exe (PID: 2200)
HIJACKLOADER has been detected (YARA)
- Setup.exe (PID: 6736)
- BlaFus.exe (PID: 8052)
Actions looks like stealing of personal data
- poasm.exe (PID: 6756)
Steals credentials from Web Browsers
- poasm.exe (PID: 6756)
SHARKSTEALER has been found (auto)
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 6236)
GENERIC has been found (auto)
- BlaFus.exe (PID: 8052)
Create files in the Startup directory
- cmd.exe (PID: 5548)
Known privilege escalation attack
- dllhost.exe (PID: 7444)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- msedge.exe (PID: 6340)
There is functionality for taking screenshot (YARA)
- Setup.exe (PID: 6736)
- poasm.exe (PID: 6756)
Application launched itself
- WinRAR.exe (PID: 3652)
- cmd.exe (PID: 3732)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3652)
- Noticed.com (PID: 7284)
Process drops legitimate windows executable
- WinRAR.exe (PID: 8024)
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 6236)
Executable content was dropped or overwritten
- Setup.exe (PID: 6736)
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 8052)
- qf.exe (PID: 620)
- Noticed.com (PID: 7812)
- BlaFus.exe (PID: 6236)
The process drops C-runtime libraries
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 6236)
The process creates files with name similar to system file names
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 6236)
There is functionality for VM detection VirtualBox (YARA)
- BlaFus.exe (PID: 8052)
Get information on the list of running processes
- cmd.exe (PID: 1728)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3732)
- qf.exe (PID: 620)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1728)
The executable file from the user directory is run by the CMD process
- Noticed.com (PID: 7812)
Starts the AutoIt3 executable file
- cmd.exe (PID: 1728)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1728)
Starts application with an unusual extension
- cmd.exe (PID: 1728)
INFO
Application launched itself
- msedge.exe (PID: 6876)
- msedge.exe (PID: 7696)
Checks supported languages
- identity_helper.exe (PID: 7492)
- identity_helper.exe (PID: 2876)
- Setup.exe (PID: 6736)
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 8052)
- qf.exe (PID: 620)
- extrac32.exe (PID: 2808)
- Noticed.com (PID: 7812)
- XPFix.exe (PID: 436)
- BlaFus.exe (PID: 6236)
- Noticed.com (PID: 7284)
Reads Environment values
- identity_helper.exe (PID: 7492)
- identity_helper.exe (PID: 2876)
Reads the computer name
- identity_helper.exe (PID: 7492)
- identity_helper.exe (PID: 2876)
- Setup.exe (PID: 6736)
- poasm.exe (PID: 6756)
- BlaFus.exe (PID: 8052)
- extrac32.exe (PID: 2808)
- Noticed.com (PID: 7812)
- XPFix.exe (PID: 436)
- BlaFus.exe (PID: 6236)
- Noticed.com (PID: 7284)
Create files in a temporary directory
- Setup.exe (PID: 6736)
- BlaFus.exe (PID: 8052)
- qf.exe (PID: 620)
- extrac32.exe (PID: 2808)
- BlaFus.exe (PID: 6236)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6876)
The sample compiled with english language support
- WinRAR.exe (PID: 8024)
- Setup.exe (PID: 6736)
- poasm.exe (PID: 6756)
- Noticed.com (PID: 7812)
- BlaFus.exe (PID: 6236)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8024)
Manual execution by a user
- Setup.exe (PID: 6736)
- cmd.exe (PID: 5548)
- Noticed.com (PID: 7284)
Creates files in the program directory
- Setup.exe (PID: 6736)
- BlaFus.exe (PID: 8052)
- BlaFus.exe (PID: 6236)
Compiled with Borland Delphi (YARA)
- Setup.exe (PID: 6736)
Reads the machine GUID from the registry
- poasm.exe (PID: 6756)
- XPFix.exe (PID: 436)
- Noticed.com (PID: 7284)
Checks proxy server information
- slui.exe (PID: 7568)
- Noticed.com (PID: 7284)
Reads the software policy settings
- slui.exe (PID: 7568)
- Noticed.com (PID: 7284)
The sample compiled with chinese language support
- BlaFus.exe (PID: 8052)
Reads mouse settings
- Noticed.com (PID: 7812)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7444)
Creates files or folders in the user directory
- Noticed.com (PID: 7812)
- Noticed.com (PID: 7284)
Launching a file from the Startup directory
- cmd.exe (PID: 5548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
216
Monitored processes
73
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\ProgramData\ASUS\XPFix.exe" "C:\ProgramData\ASUS\XPFix.exe" /u | C:\ProgramData\ASUS\XPFix.exe | — | BlaFus.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: MEDIUM Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 1, 0, 0, 1013 Modules
| |||||||||||||||
| 440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5100,i,12725786239493371534,12292216717218657262,262144 --variations-seed-version --mojo-platform-channel-handle=5032 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 620 | C:\Users\admin\qf.exe | C:\Users\admin\qf.exe | poasm.exe | ||||||||||||
User: admin Company: CryptoFlowMind Elite Innovations Co Integrity Level: MEDIUM Description: Interactive blockchain brain training exercises for elite cognitive enhancement Modules
| |||||||||||||||
| 1132 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4284,i,16594631415921438719,7456962392046884036,262144 --variations-seed-version --mojo-platform-channel-handle=4292 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | poasm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 1 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1588 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3640,i,16594631415921438719,7456962392046884036,262144 --variations-seed-version --mojo-platform-channel-handle=3228 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1728 | cmd | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | findstr /V "Guam" Woman | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 285
Read events
16 174
Write events
93
Delete events
18
Modification events
| (PID) Process: | (6876) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6876) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6876) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4744) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4744) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4744) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4744) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4744) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (4744) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (6876) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
58
Suspicious files
351
Text files
124
Unknown types
63
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF18da0f.TMP | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18da3e.TMP | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF18da3e.TMP | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF18da4e.TMP | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18da4e.TMP | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6876 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF18da4e.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
121
DNS requests
97
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6340 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:IePFOPCs2ykCGQXPTYL_vpqIFyz6AHDxNz7CI5Caigs&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2460 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7536 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7536 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7924 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1754295349&P2=404&P3=2&P4=E9l3ygjB3SCIIwGKTKTUSf2r7ZinX4qF%2fSGbz95%2biUWTfbtYxeKdQvFubapbZVoHEDXLaCC3Z%2fJysaGP9KZPQA%3d%3d | unknown | — | — | whitelisted |
7924 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1754295349&P2=404&P3=2&P4=E9l3ygjB3SCIIwGKTKTUSf2r7ZinX4qF%2fSGbz95%2biUWTfbtYxeKdQvFubapbZVoHEDXLaCC3Z%2fJysaGP9KZPQA%3d%3d | unknown | — | — | whitelisted |
7924 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1754295349&P2=404&P3=2&P4=E9l3ygjB3SCIIwGKTKTUSf2r7ZinX4qF%2fSGbz95%2biUWTfbtYxeKdQvFubapbZVoHEDXLaCC3Z%2fJysaGP9KZPQA%3d%3d | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
828 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6340 | msedge.exe | 172.67.189.119:443 | shitza.xyz | CLOUDFLARENET | US | unknown |
6340 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6340 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6340 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6340 | msedge.exe | 92.123.104.53:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
shitza.xyz |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.iconbolt.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6340 | msedge.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain ( .iconbolt .com) |
6340 | msedge.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain ( .iconbolt .com) |
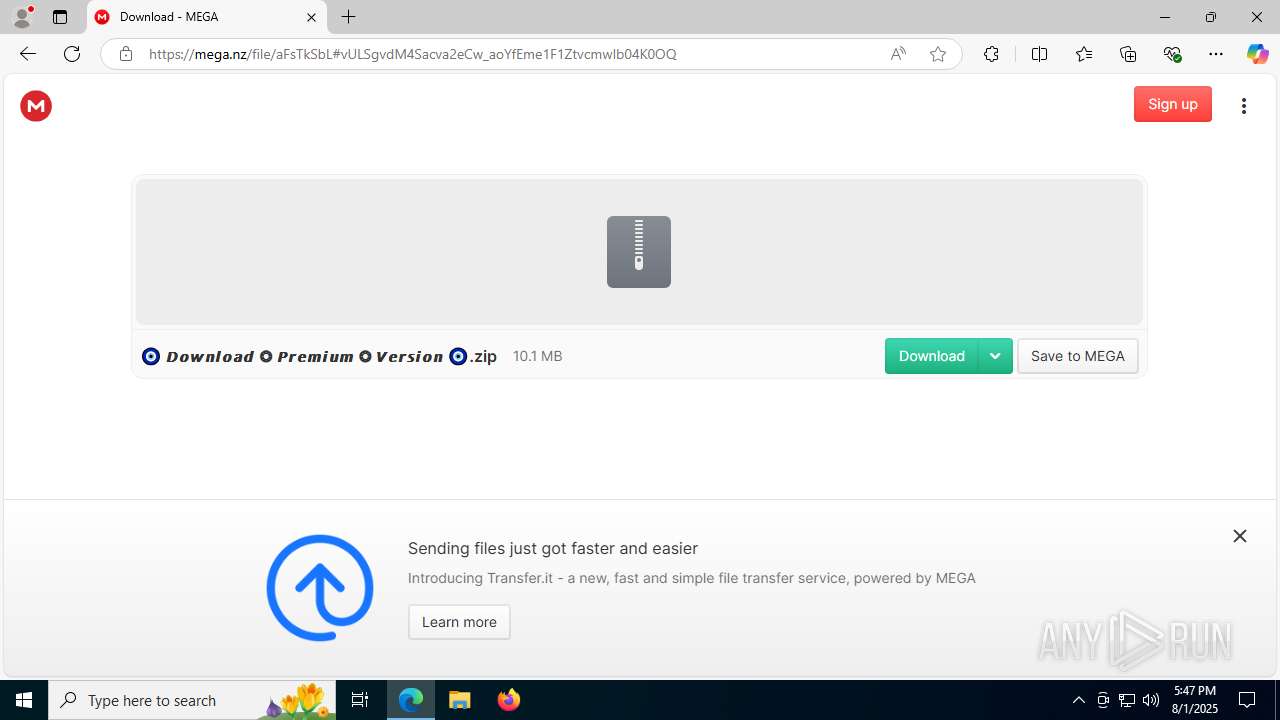
6340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
6340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |