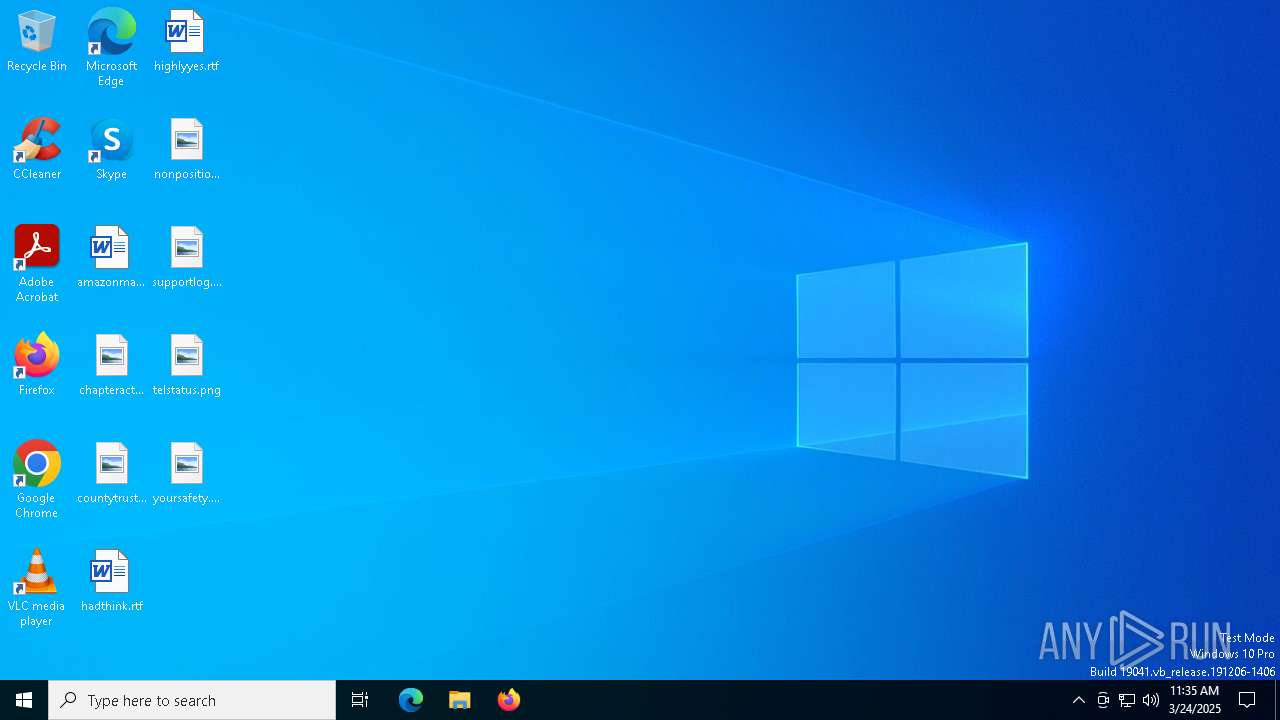
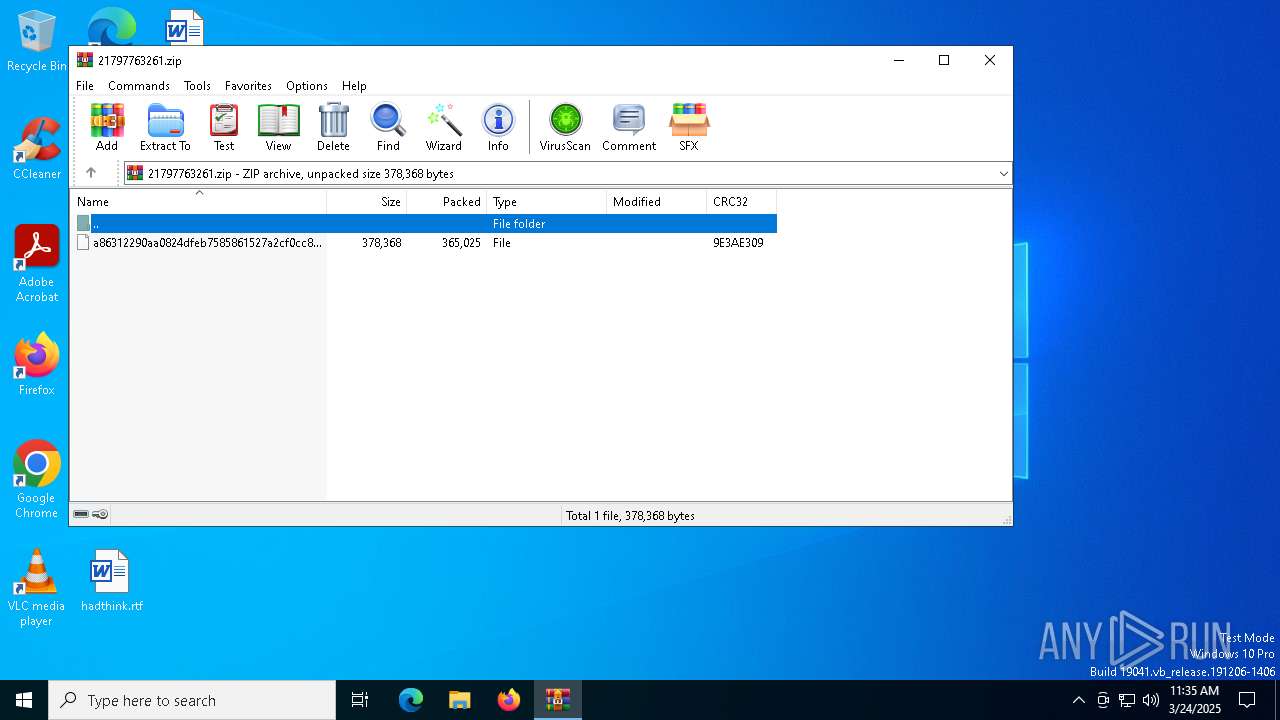
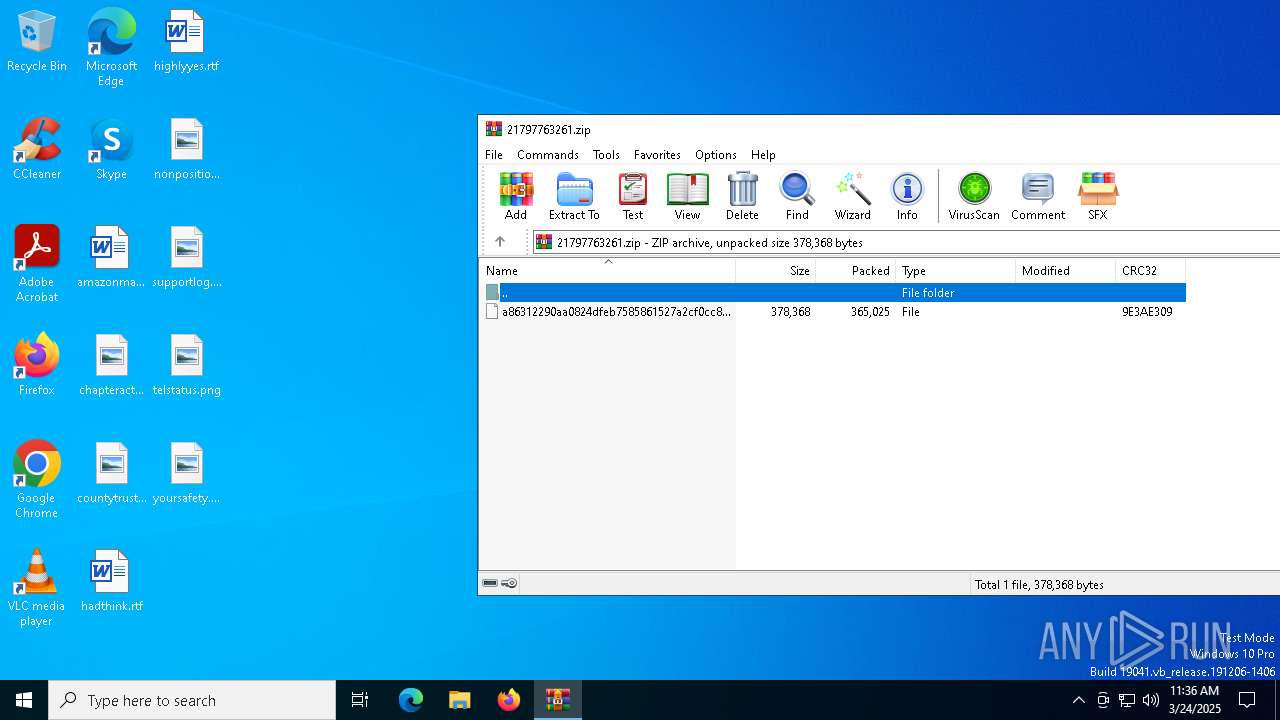
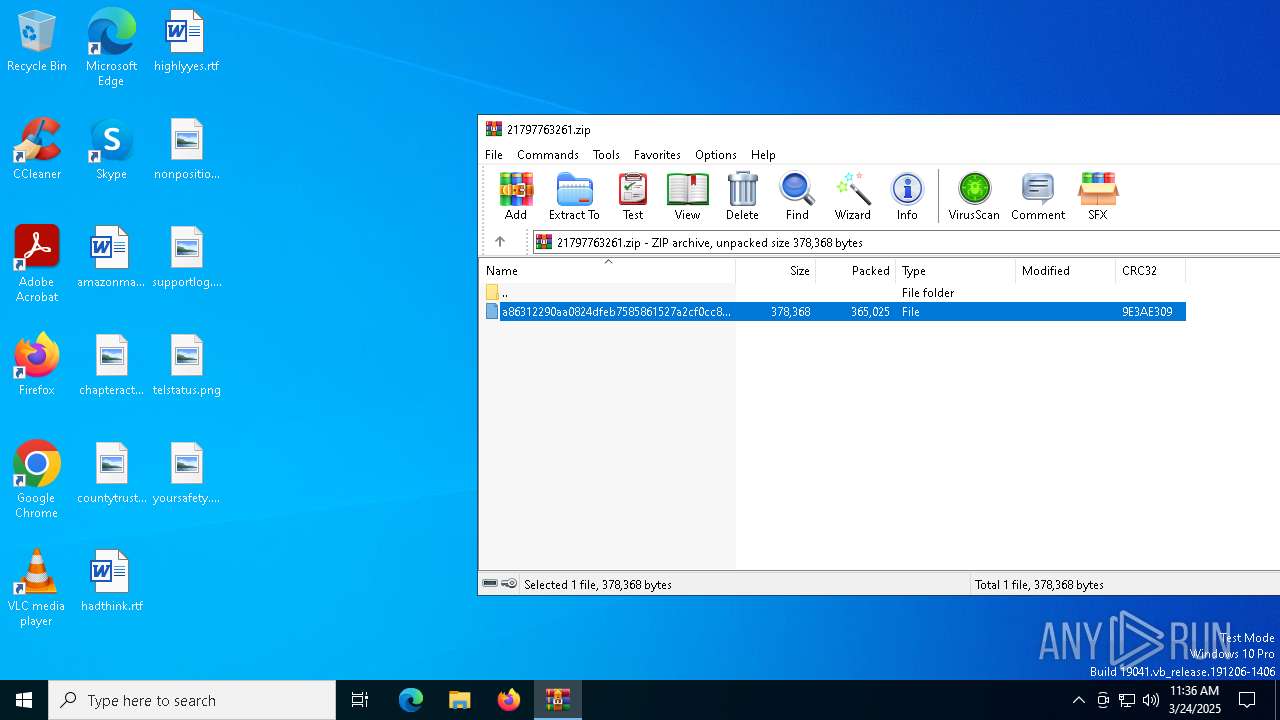
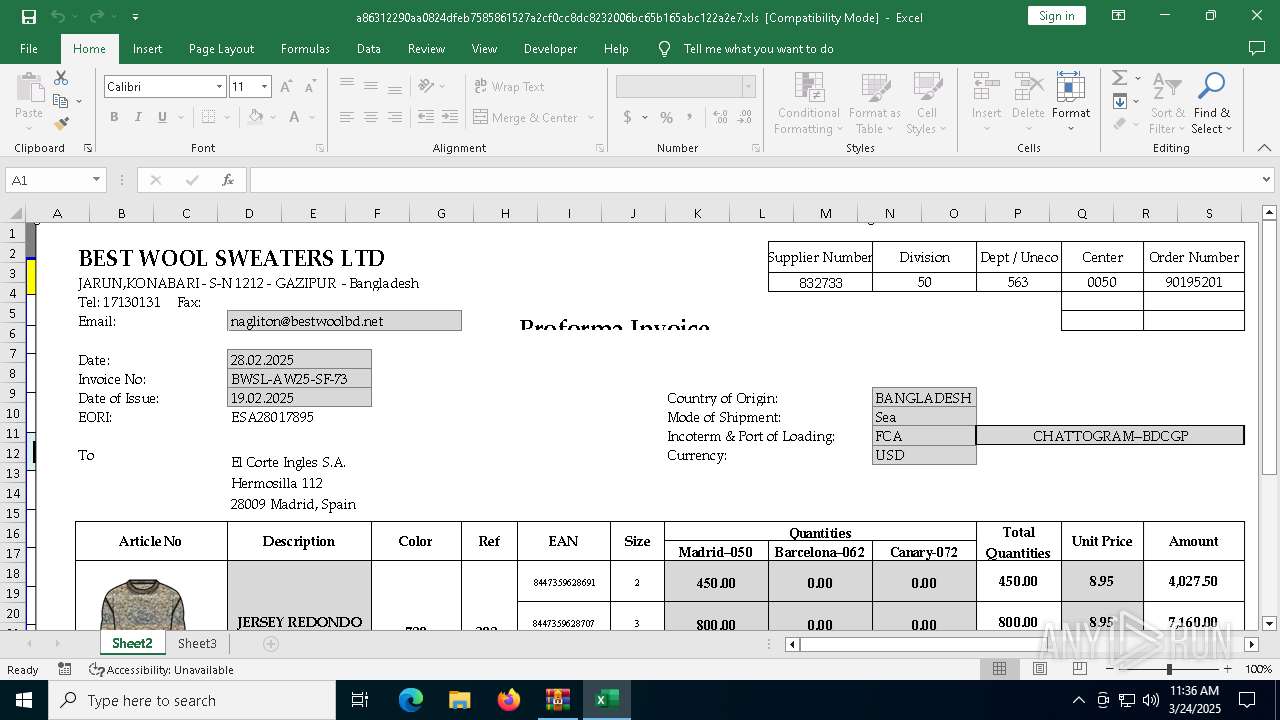
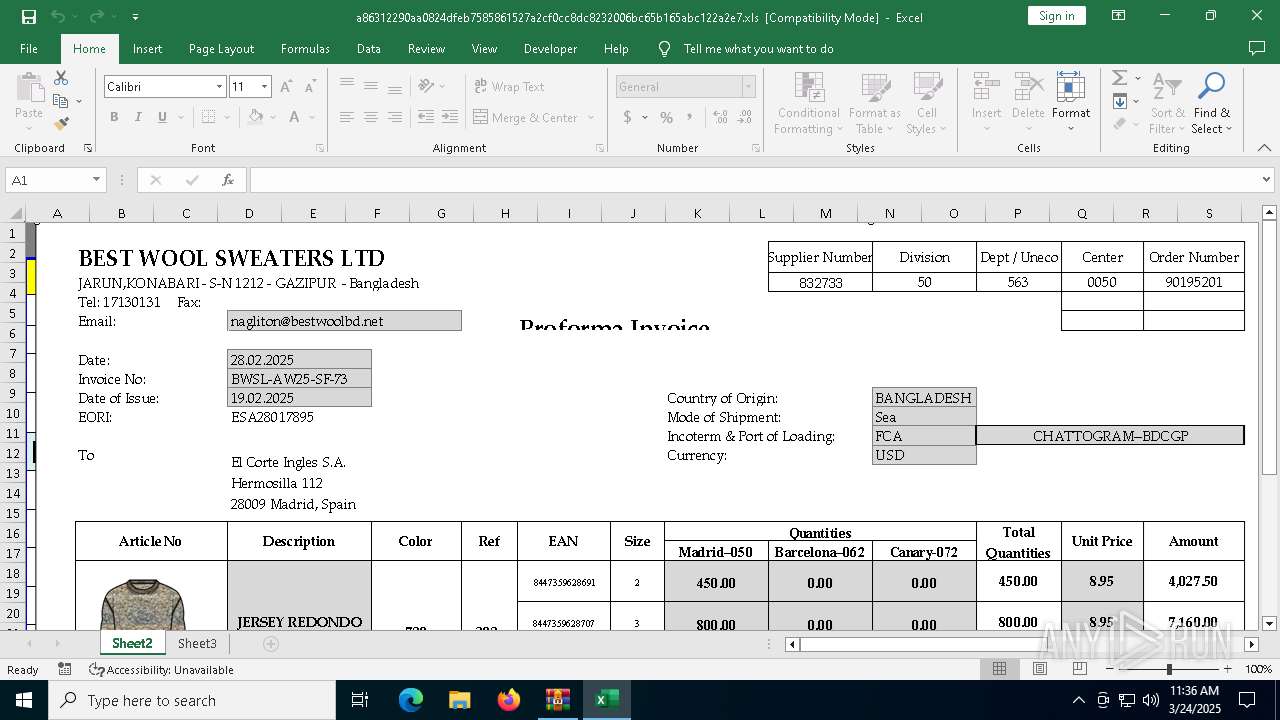
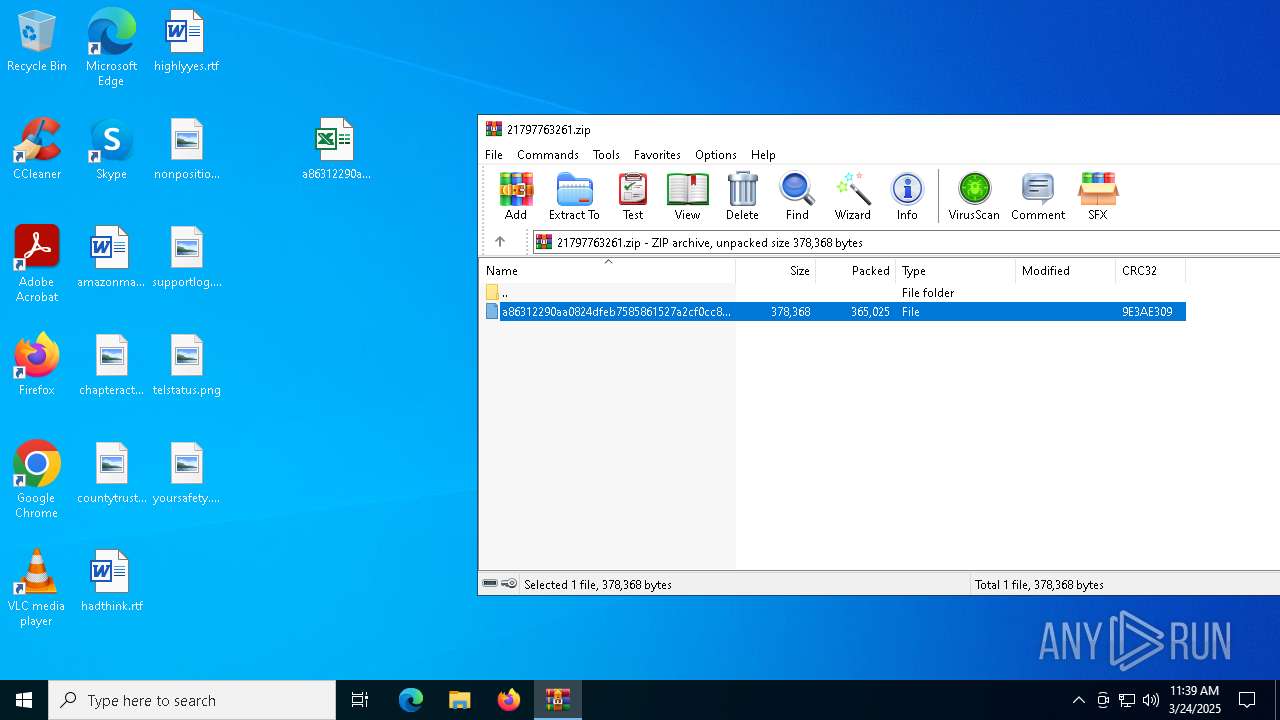
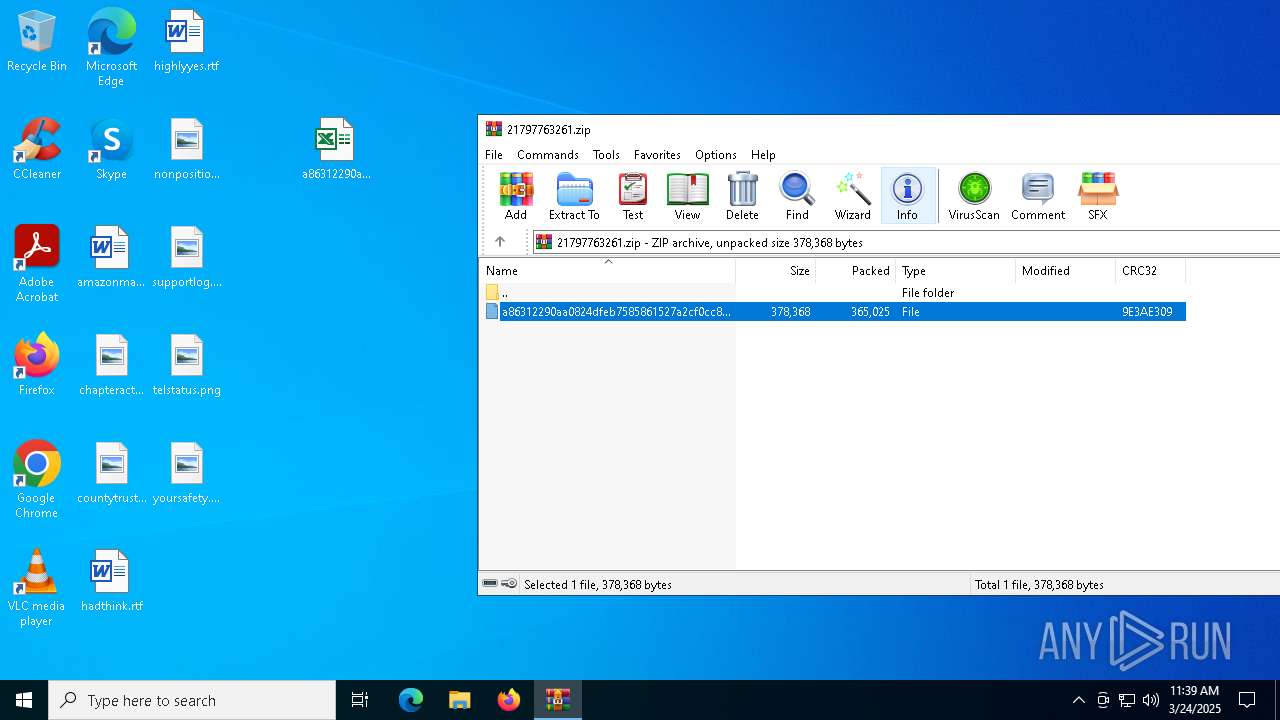
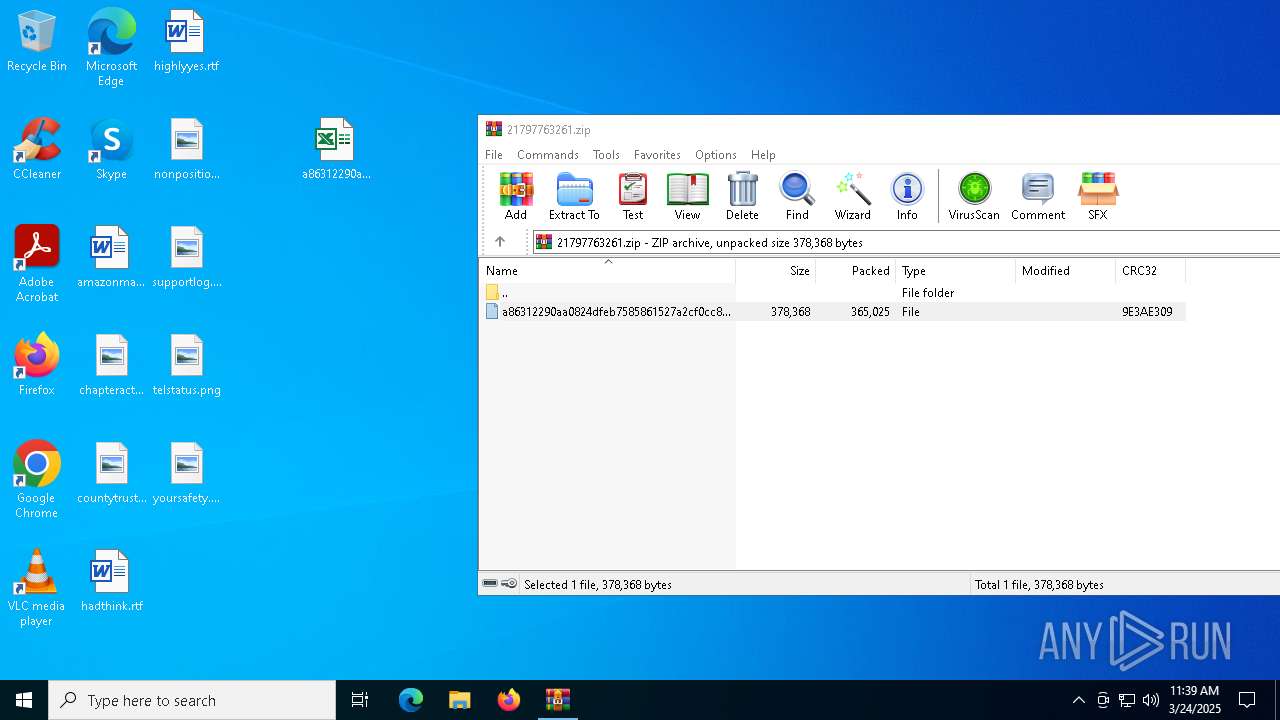
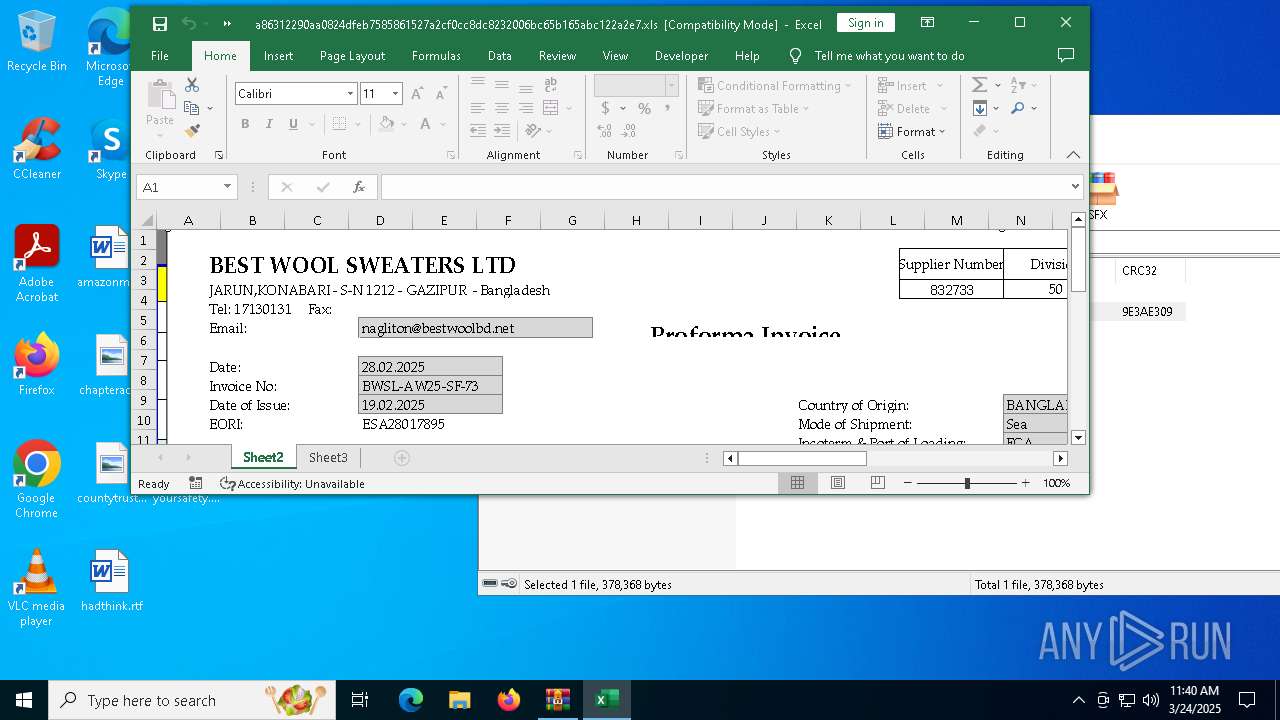
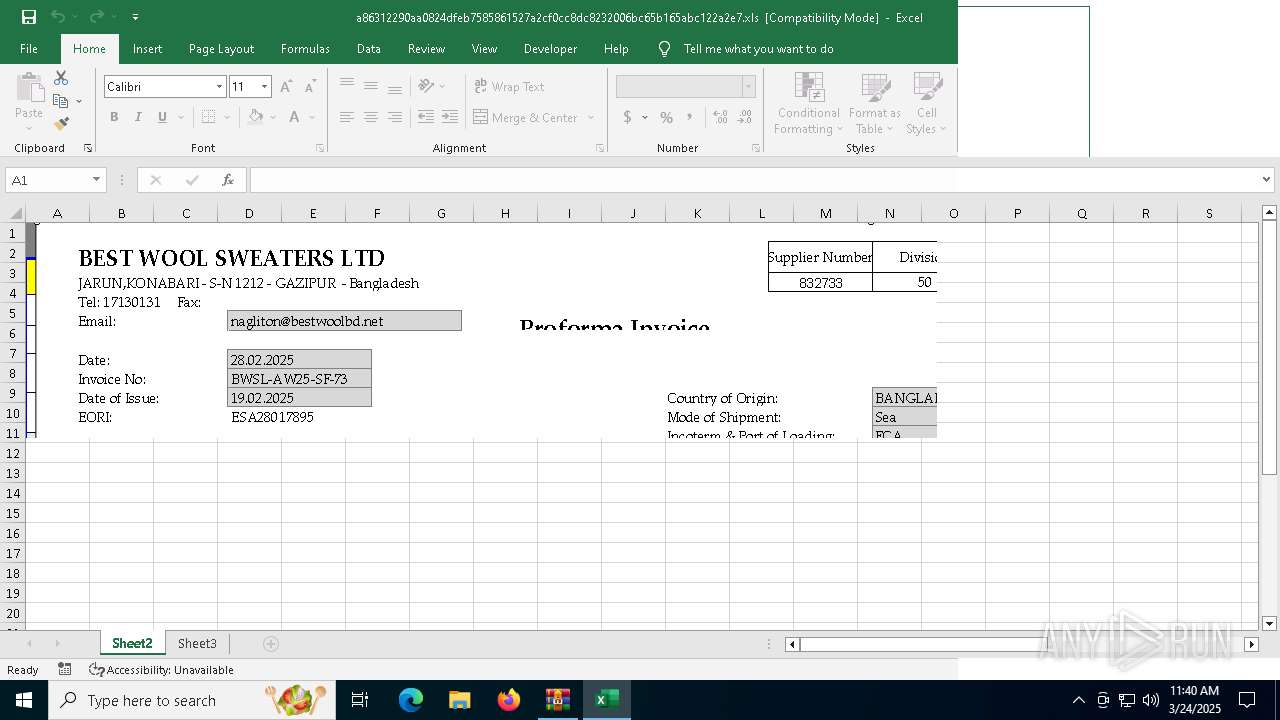
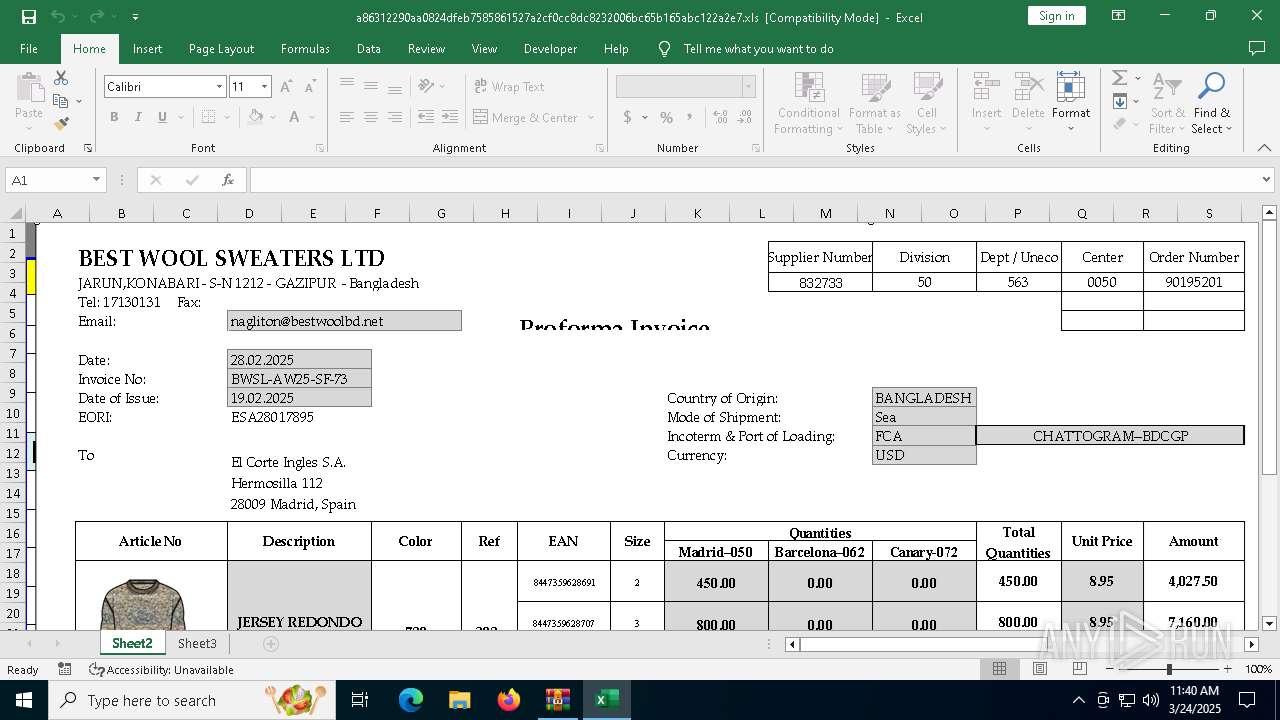
| File name: | 21797763261.zip |
| Full analysis: | https://app.any.run/tasks/21dfd893-1eb2-4f58-99cc-b9de08faaa03 |
| Verdict: | Malicious activity |
| Threats: | MassLogger is a credential stealer and keylogger first identified in April 2020. It has been actively used in cyber campaigns to exfiltrate sensitive information from compromised systems. It is designed for easy use by less tech-savvy actors and is prominent for the capability of spreading via USB drives. It targets both individuals and organizations in various industries, mostly in Europe and the USA. |
| Analysis date: | March 24, 2025, 11:35:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 78737FB33DE64230B980E85DFC796A39 |
| SHA1: | A6D63BDBD8CCE9BFCE74C0E4A32152147A553634 |
| SHA256: | 973ED5CF175A41839783BDC8FE03C5C66C3D73582D48FD12103222AA5EBE5738 |
| SSDEEP: | 12288:U3g6xdWsK8I5D3yKWrsUJf79ABdpRE9RxkviBGWi7+HCz:U3g6LLK8IJ1WrLx9ABPRC/oiBNi7+HCz |
MALICIOUS
STEALER has been found (auto)
- WinRAR.exe (PID: 7284)
SUSPICIOUS
Creates file in the systems drive root
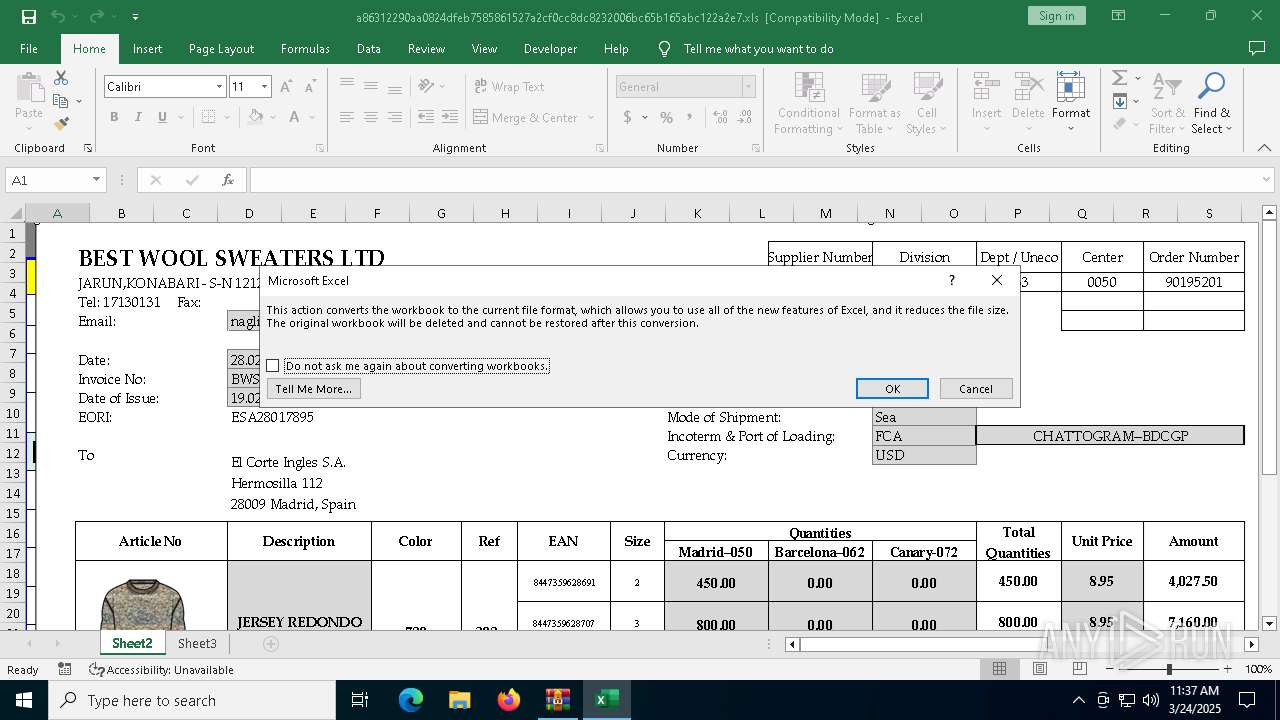
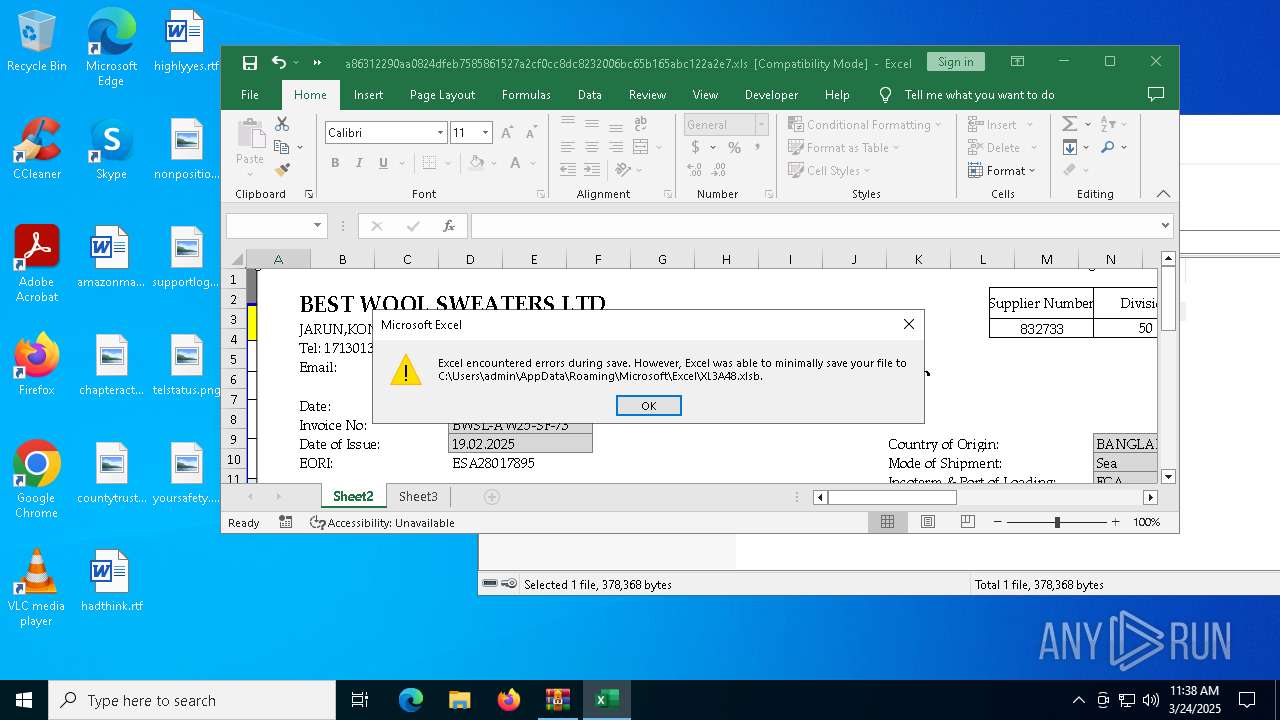
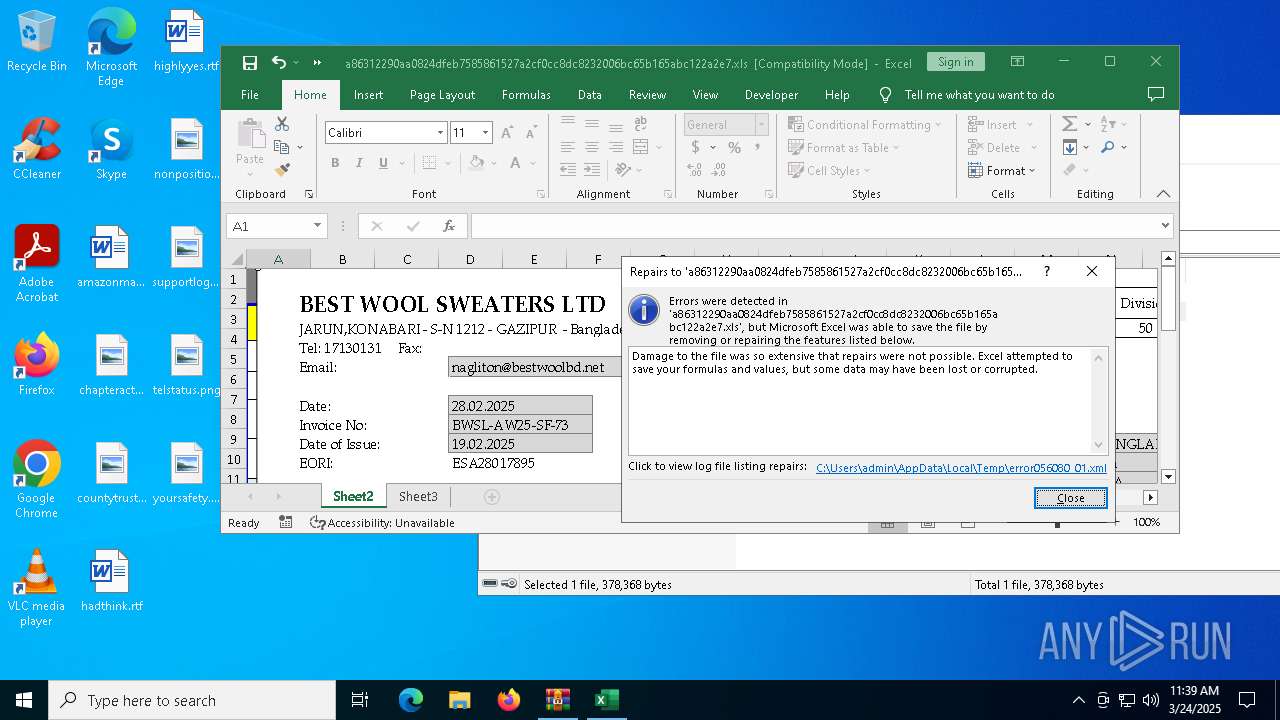
- EXCEL.EXE (PID: 5608)
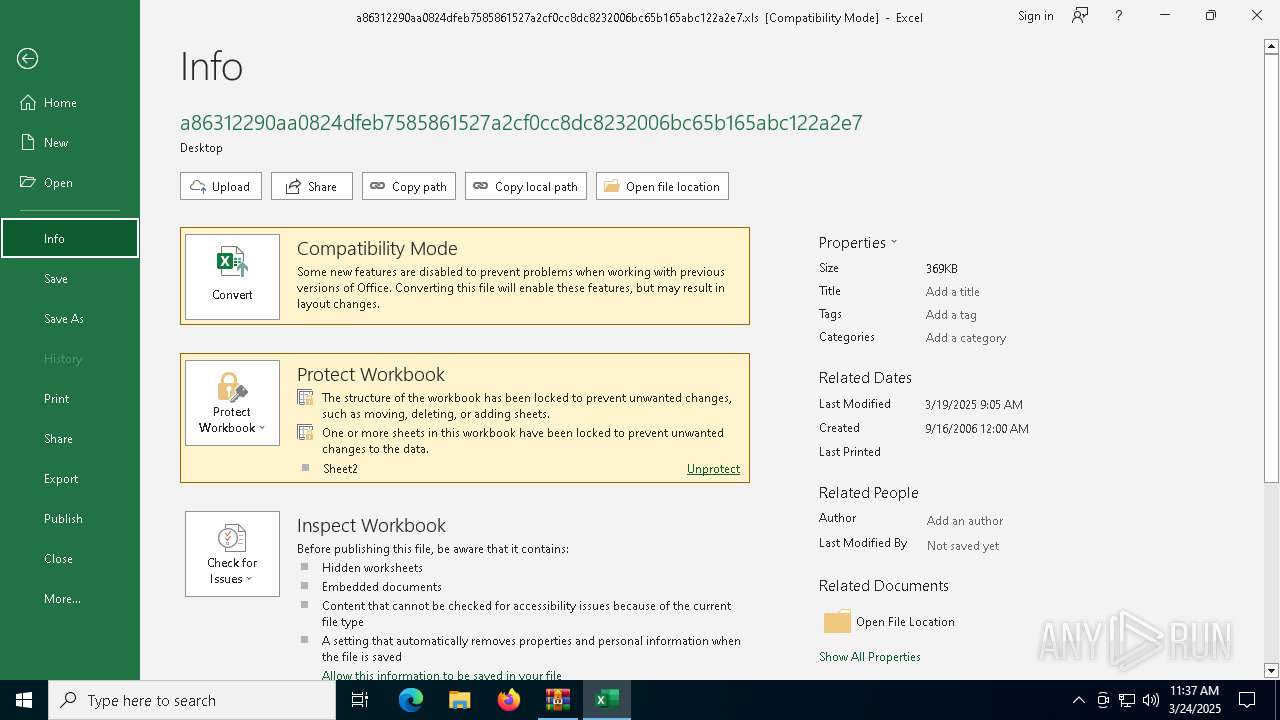
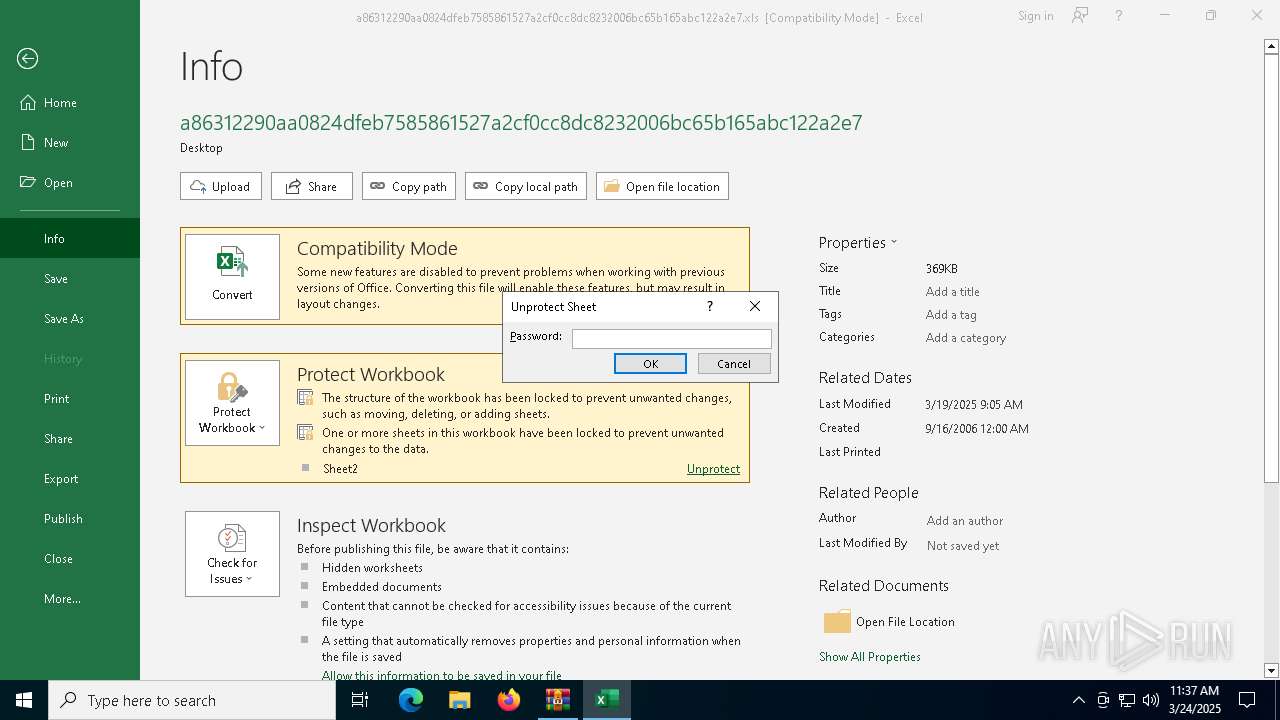
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 7952)
INFO
Manual execution by a user
- EXCEL.EXE (PID: 5608)
- EXCEL.EXE (PID: 6988)
- EXCEL.EXE (PID: 4228)
Reads the software policy settings
- slui.exe (PID: 7452)
- slui.exe (PID: 7840)
Checks proxy server information
- slui.exe (PID: 7840)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 7952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x9e3ae309 |
| ZipCompressedSize: | 365025 |
| ZipUncompressedSize: | 378368 |
| ZipFileName: | a86312290aa0824dfeb7585861527a2cf0cc8dc8232006bc65b165abc122a2e7 |
Total processes
154
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
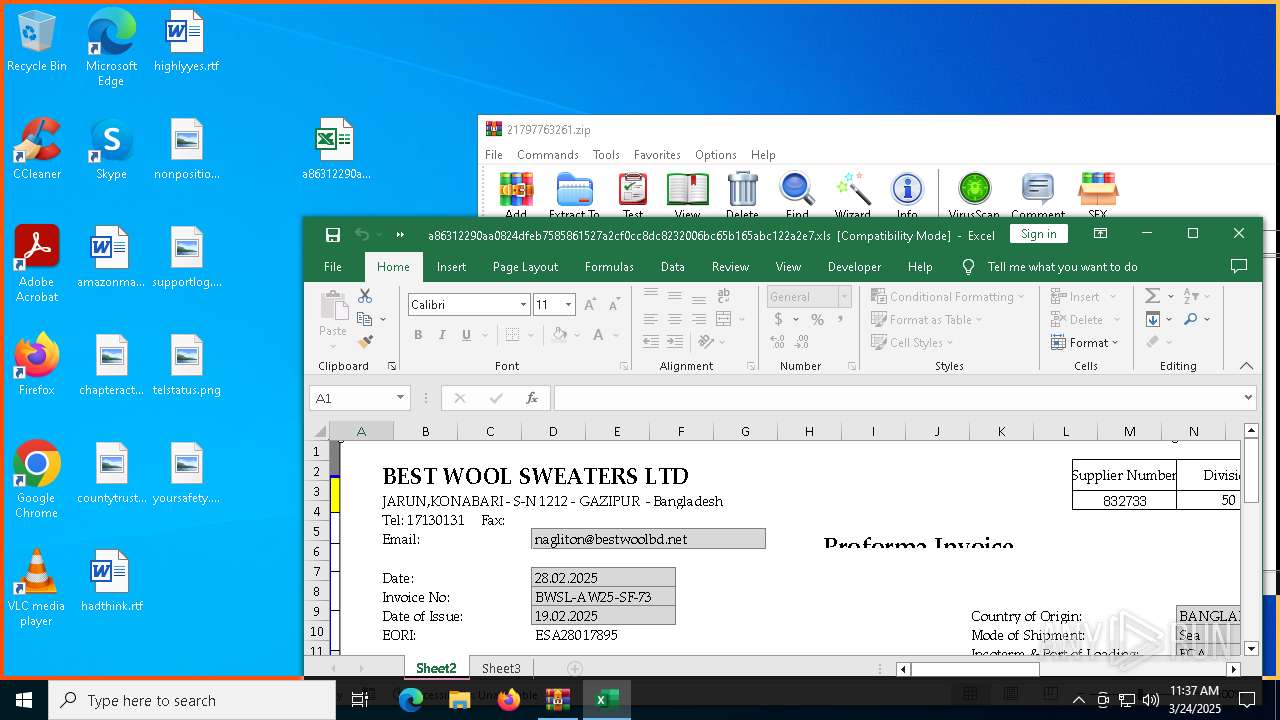
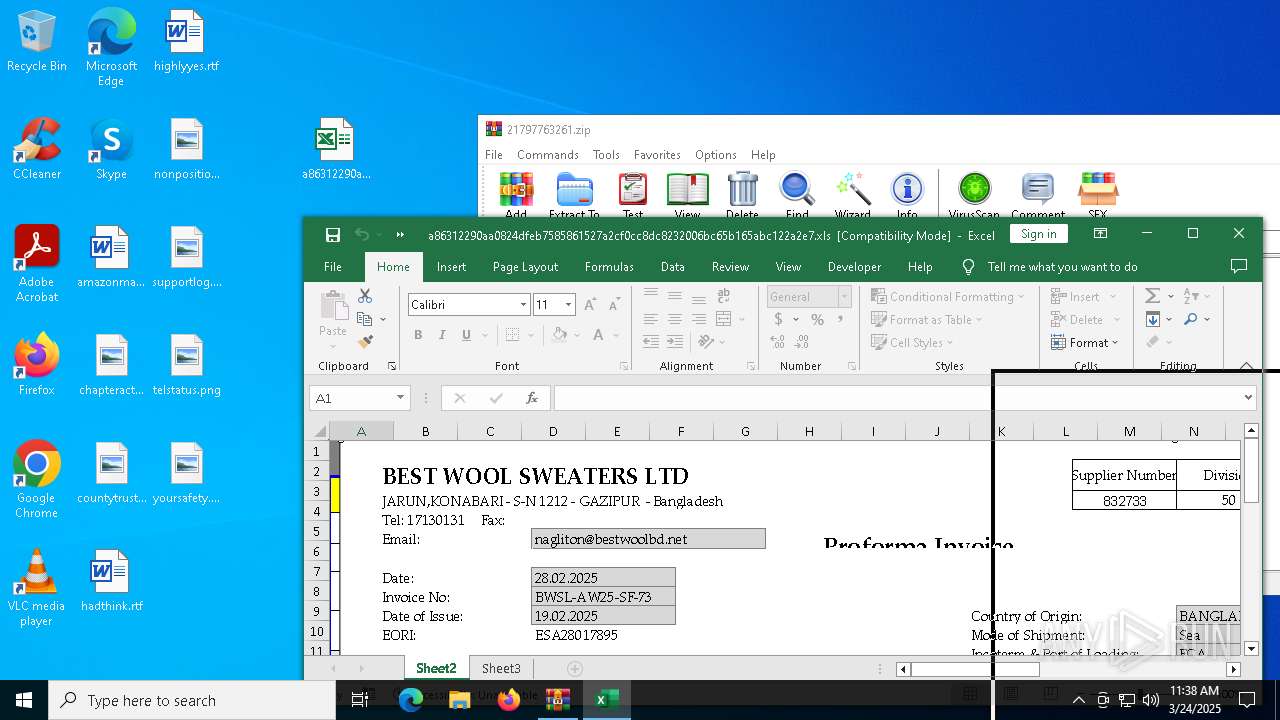
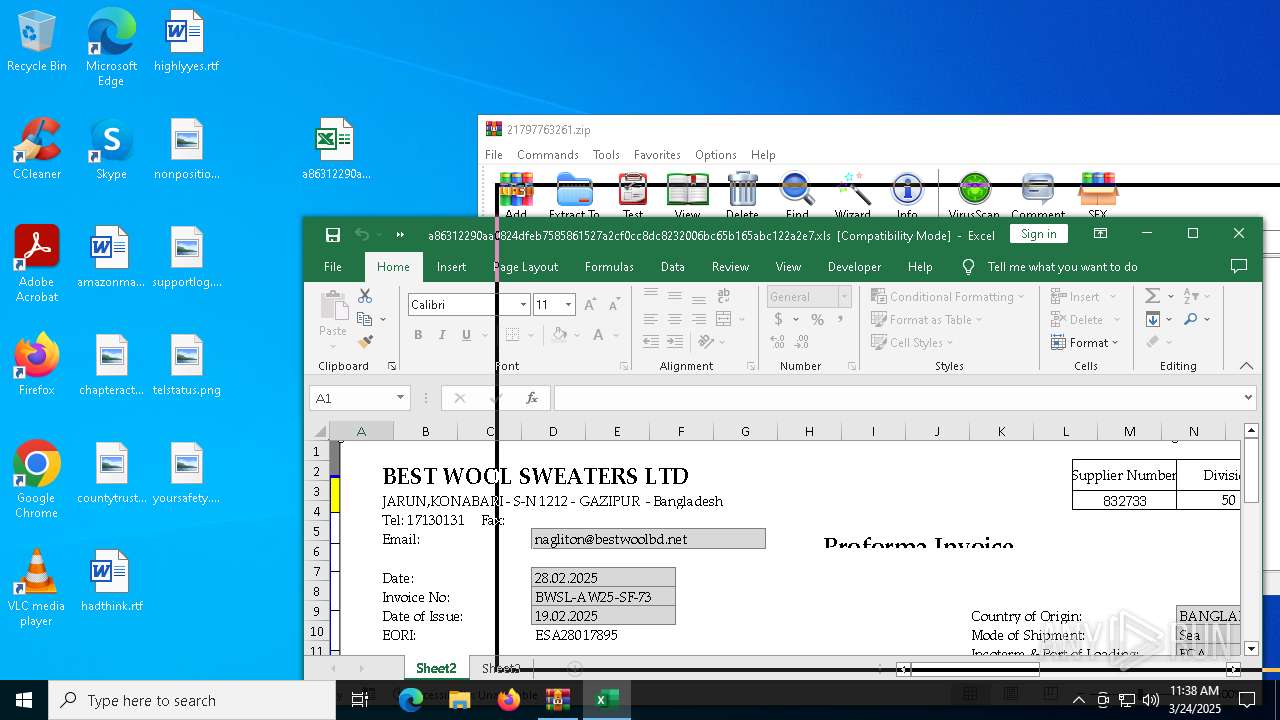
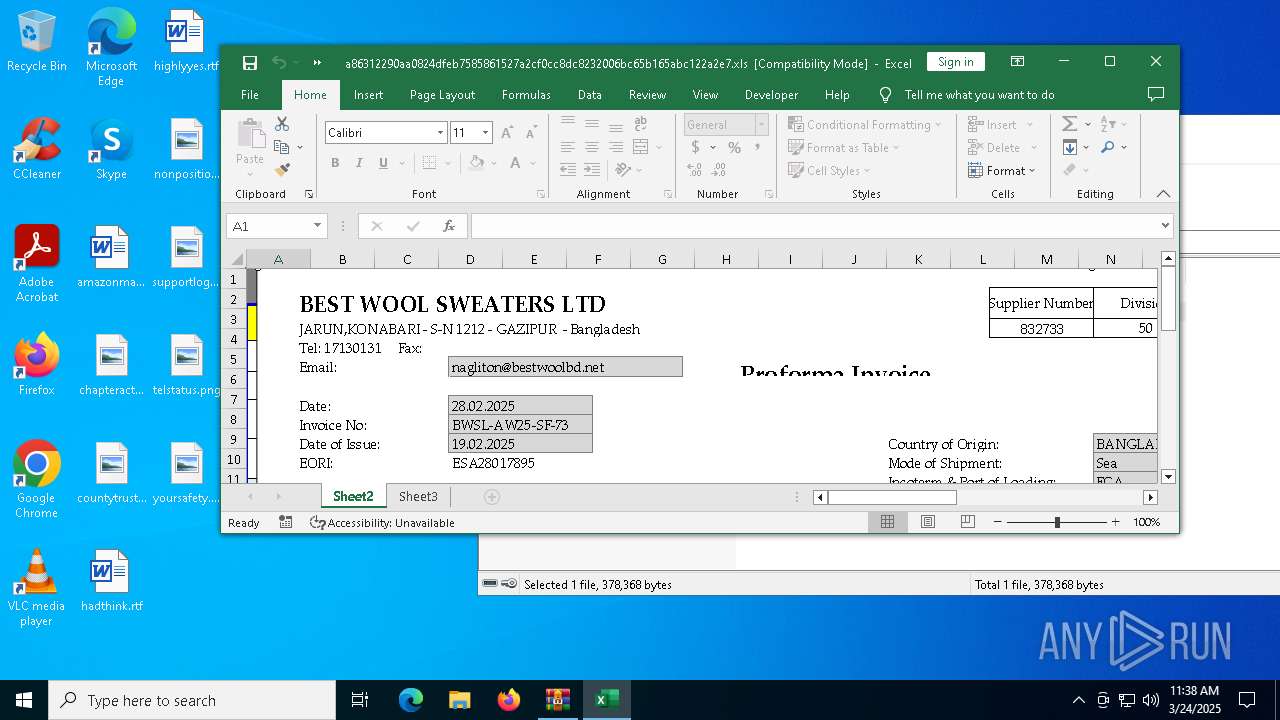
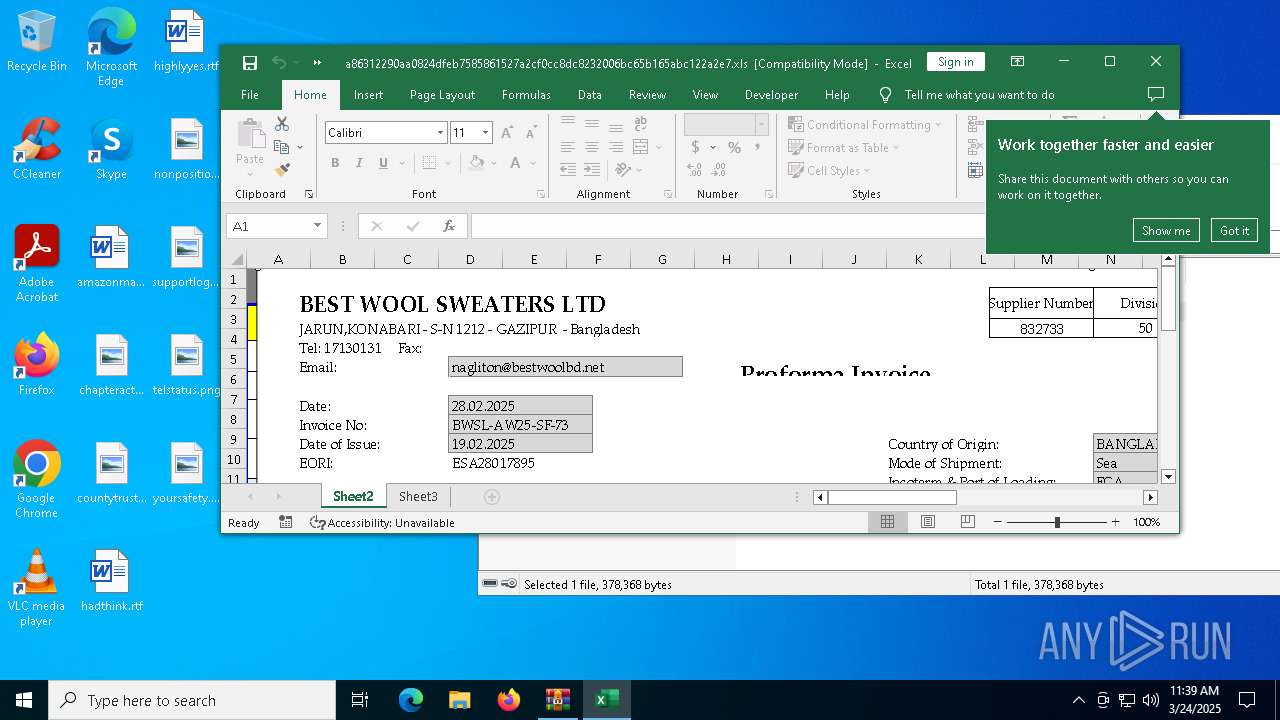
| 4228 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\a86312290aa0824dfeb7585861527a2cf0cc8dc8232006bc65b165abc122a2e7.xls" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5608 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\a86312290aa0824dfeb7585861527a2cf0cc8dc8232006bc65b165abc122a2e7.xls" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6988 | "C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7284 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\21797763261.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7420 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7452 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7840 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7952 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 270
Read events
31 441
Write events
1 658
Delete events
171
Modification events
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\21797763261.zip | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7284) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5608) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
Executable files
1
Suspicious files
67
Text files
51
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:700E70C259179FD46C9485B6D01AB186 | SHA256:1234E9C7F092C61FE5F61CF4E7C4B3A49651E5481FAF842A30E3899B3EA35330 | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:2596CB236EBCA768CA81740AA9B81B59 | SHA256:73FDE9934B086CF0956B22493F9AB7B094D144B48A3B06E995FD3E644B6BAA0C | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\2E84245D-8D26-4161-92AB-45FDBE3212D5 | xml | |
MD5:4ABA12918FF98359668EB39718743A94 | SHA256:7024AB8558890650C088C72687ECC0C8B97691CFEB863F40DA65EE8AD60EF8E5 | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:2000AFAEDA25093B1A0345646992CB86 | SHA256:94D81DD5A9519FAB086146D0979B9583B59D2FE293817407EC0039438671F71E | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\a86312290aa0824dfeb7585861527a2cf0cc8dc8232006bc65b165abc122a2e7.xls.LNK | binary | |
MD5:0FE2236CAEA648C60F2959AABBB823C9 | SHA256:43CD046300AF2D879DBBC4AA2B5FA1B5D7E1055B53D5EC1E8E23FB663C307BA5 | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\F93B580A.emf | binary | |
MD5:CFF90A3CCF7BA1823850124A38708D99 | SHA256:316A90A680EFD255C7F58FC943AFBA04A1D8768C485F1D39EBB9E28FEBCDD63A | |||
| 7284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7284.47306\a86312290aa0824dfeb7585861527a2cf0cc8dc8232006bc65b165abc122a2e7 | document | |
MD5:82E42DCC359251E2345F5A056546E769 | SHA256:A86312290AA0824DFEB7585861527A2CF0CC8DC8232006BC65B165ABC122A2E7 | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:32222D0F7DF1A8B398756CF85107B8B6 | SHA256:761C1E34E67A4BB2A60BBF57DCFF5632BBF1FD32AE7D796BB731E675BEA4CA3B | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:24ECF772A1387AD0255A38E432F3AC56 | SHA256:A4FD1D04E17745923BF51F2BD6351E22117A0842BD6B6FABF084D803FA0763DC | |||
| 5608 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json | binary | |
MD5:C1AE3BCF1E90583A6F77D255C39E84D0 | SHA256:EF1DABA96078BC69F9FCBA5202EE154E972977AD99F9A38D44768D72B6DAC7E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
91
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7620 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2284 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4228 | EXCEL.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5608 | EXCEL.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 104.124.11.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 104.124.11.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |