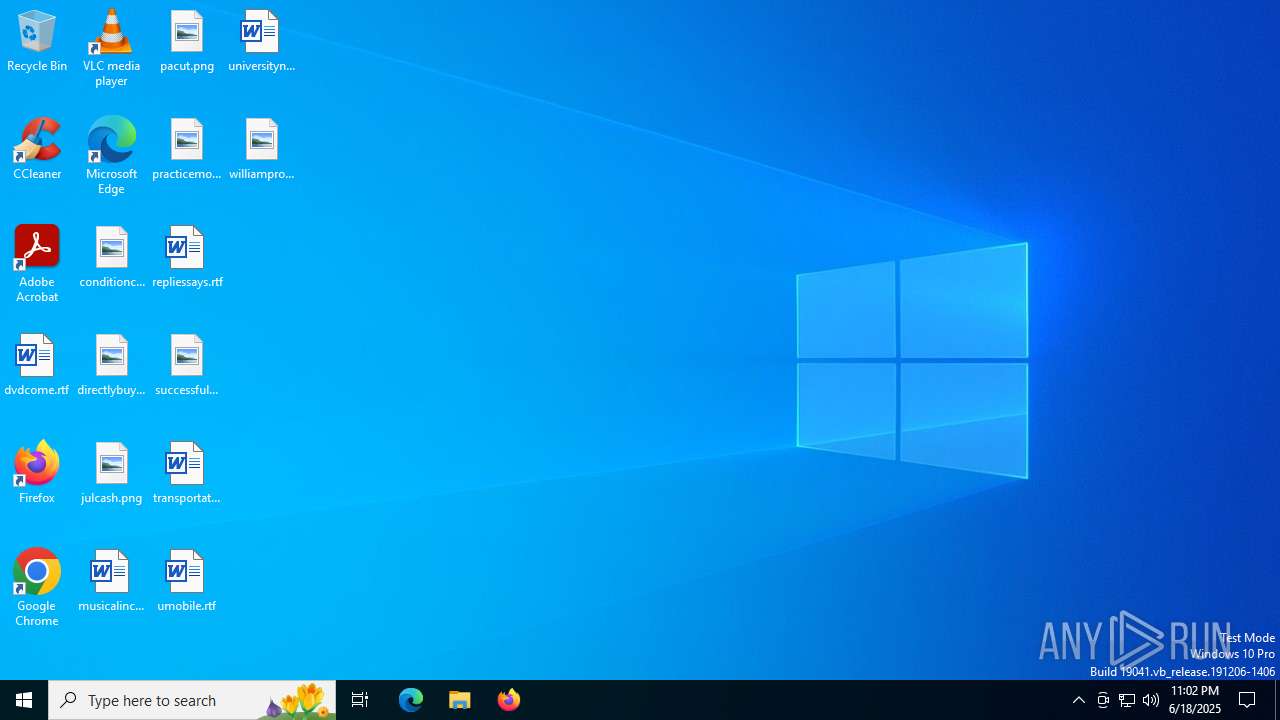
| File name: | correo_25-280322- -0.eml |
| Full analysis: | https://app.any.run/tasks/3857f2e5-127c-4e1c-b69b-0593efc4d972 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 18, 2025, 23:02:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | C4C78FDA54B177834C5B1693D83B882F |
| SHA1: | A968B785AFD6CBA16040D8FD7F0A2A197F1D3FDB |
| SHA256: | 96DE2A03E2F0359639F217028D27B38CADF0CA2F733BE20421B5BDC3ADF56C97 |
| SSDEEP: | 12288:x6MHE+Wimft6TVhVHyKXmRfJIdDZXPLGE:xNWLft6RjHyKXAYDZCE |
MALICIOUS
Phishing has been detected
- OUTLOOK.EXE (PID: 1720)
- OUTLOOK.EXE (PID: 1720)
Changes the autorun value in the registry
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8760)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
ASYNCRAT has been detected (SURICATA)
- InstallUtil.exe (PID: 8472)
ASYNCRAT has been detected (YARA)
- InstallUtil.exe (PID: 8472)
SUSPICIOUS
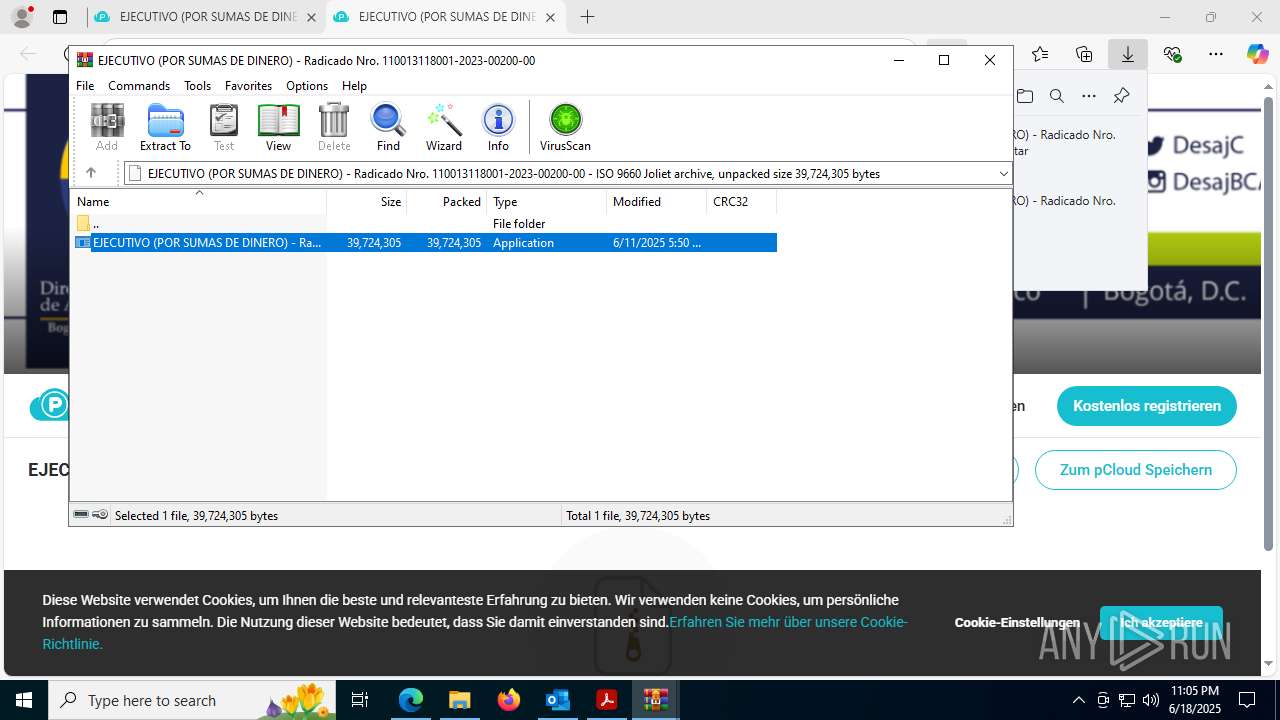
Executable content was dropped or overwritten
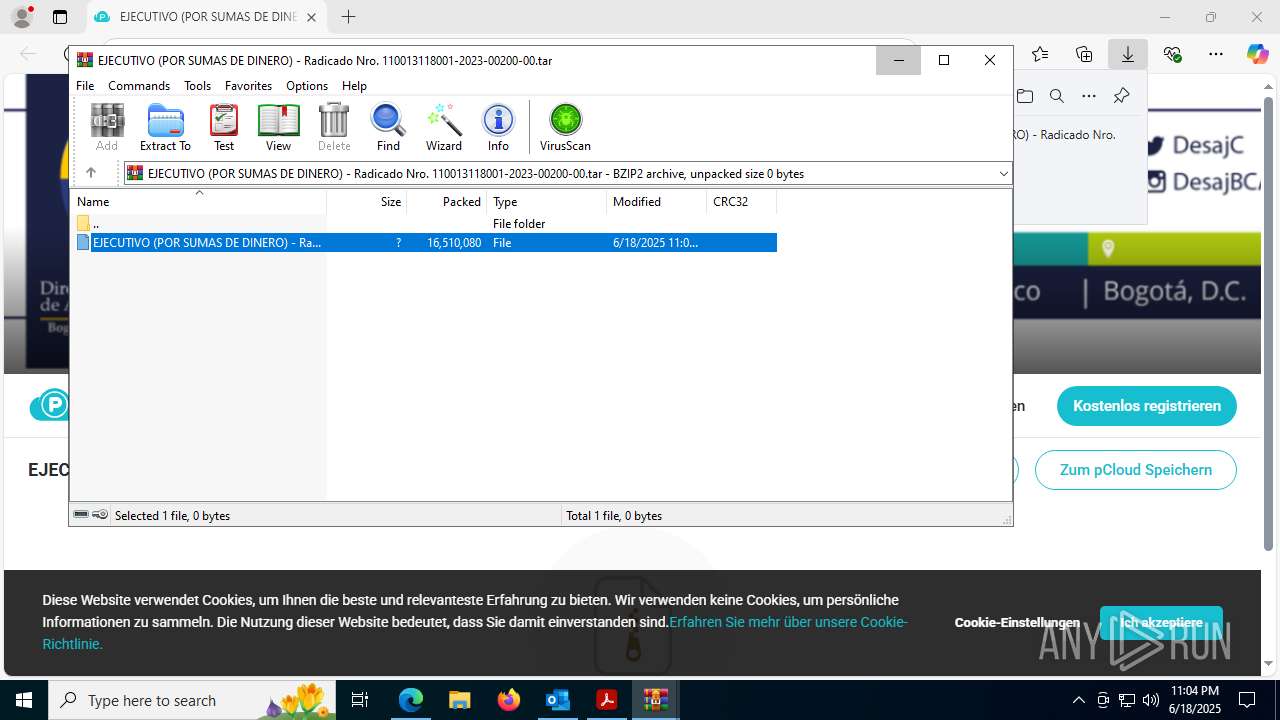
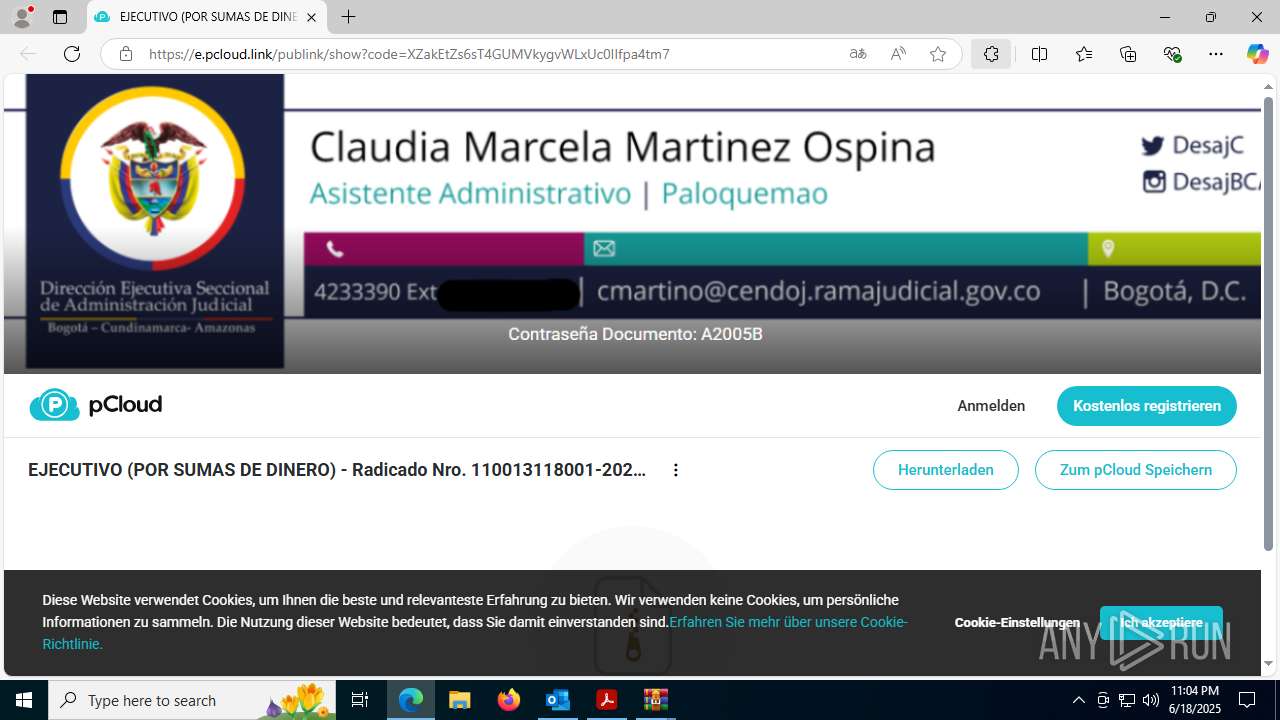
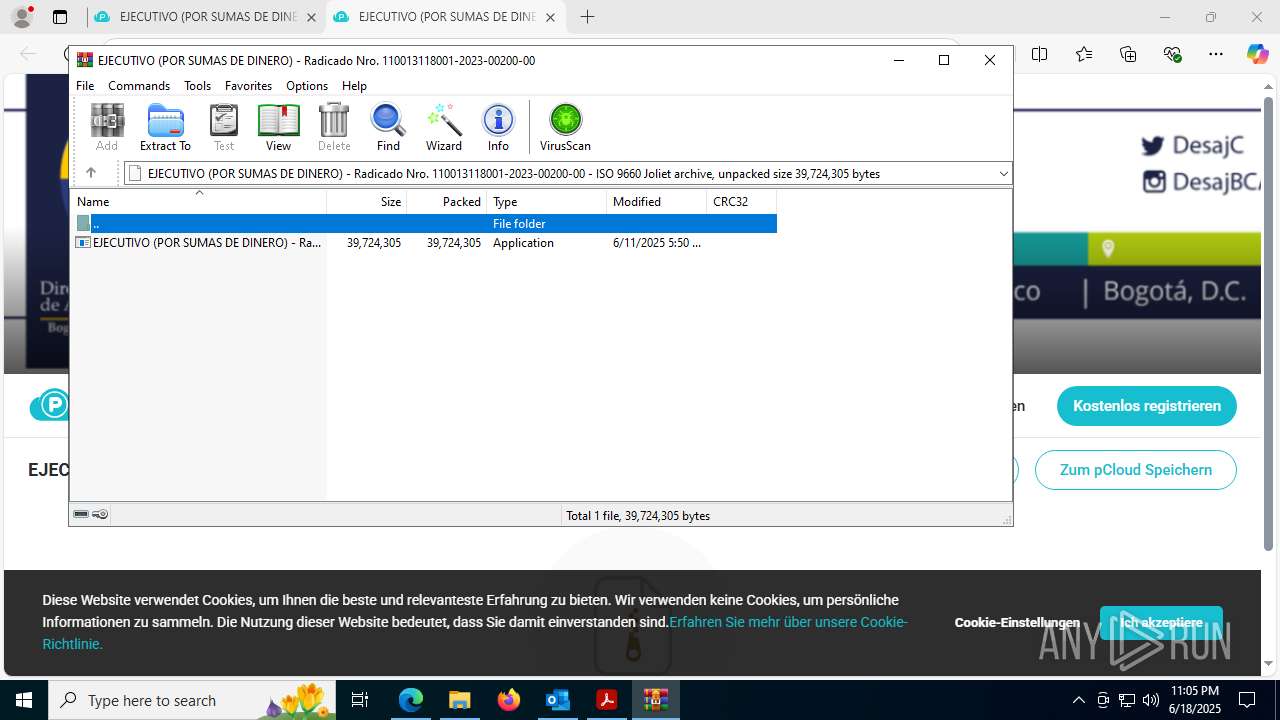
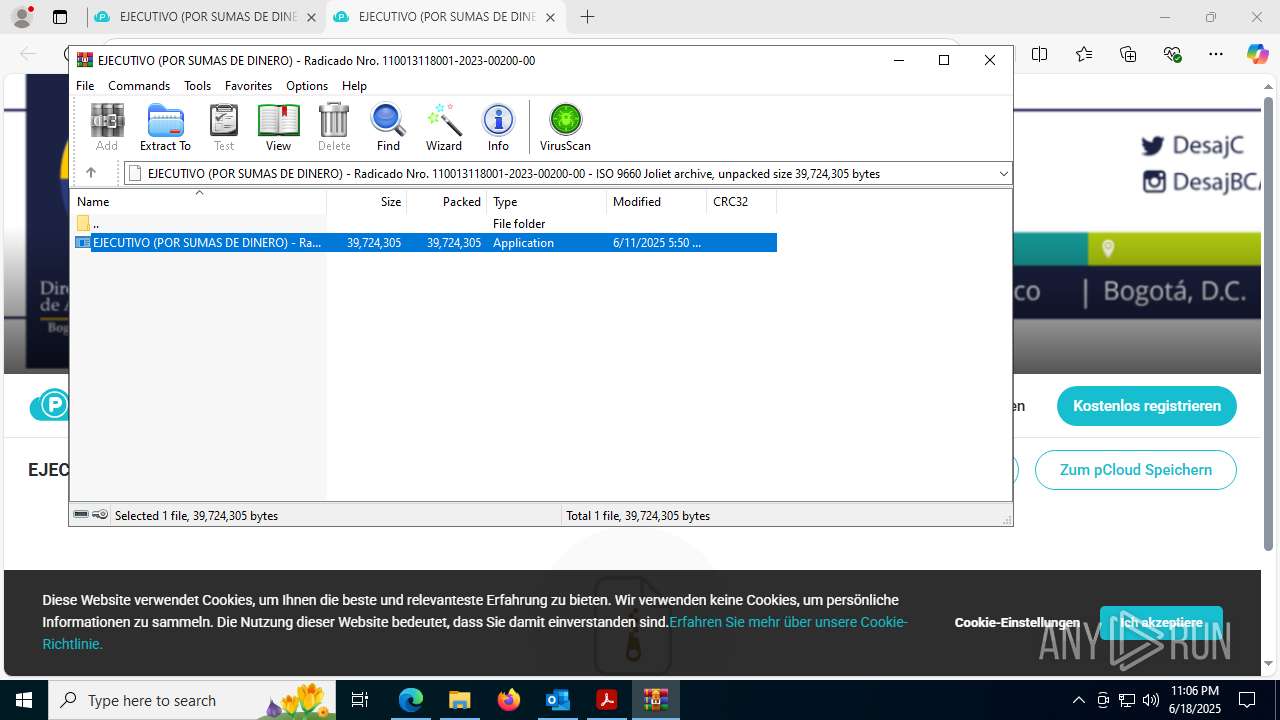
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
Process drops legitimate windows executable
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
Application launched itself
- WinRAR.exe (PID: 8008)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3900)
- WinRAR.exe (PID: 8008)
Connects to unusual port
- InstallUtil.exe (PID: 8472)
The process drops C-runtime libraries
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
Contacting a server suspected of hosting an CnC
- InstallUtil.exe (PID: 8472)
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 1472)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 8008)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 8008)
INFO
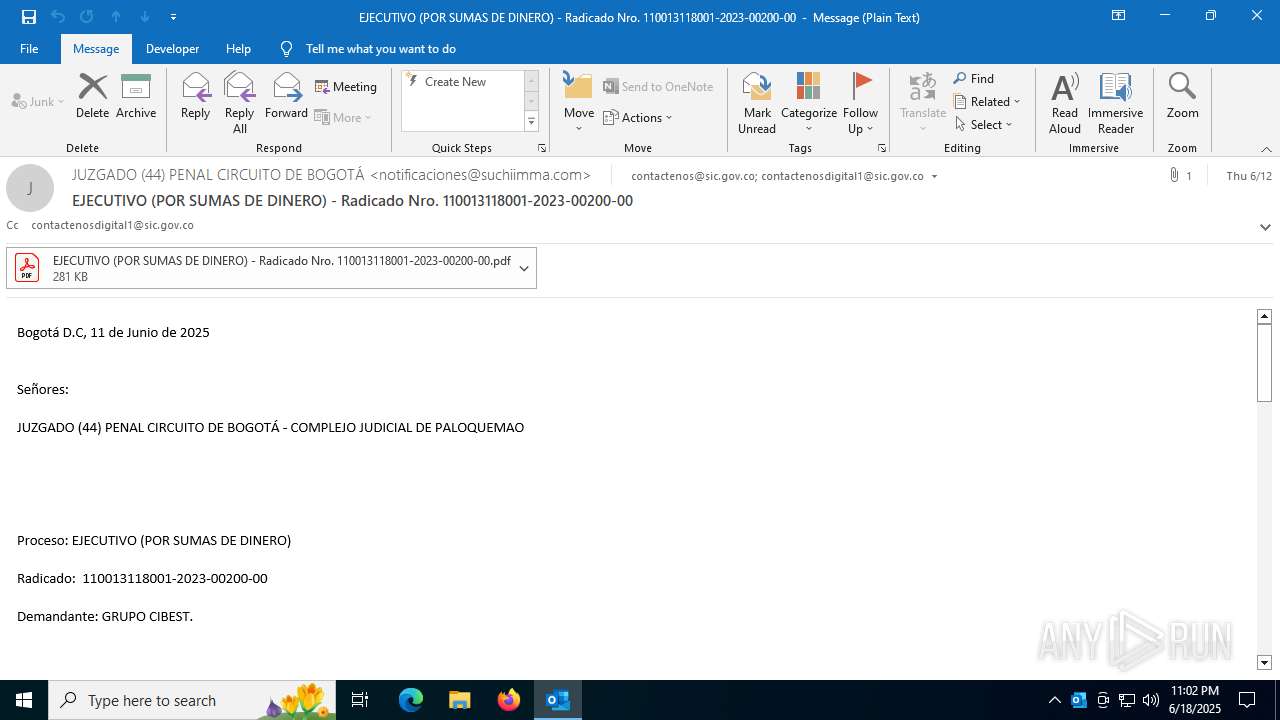
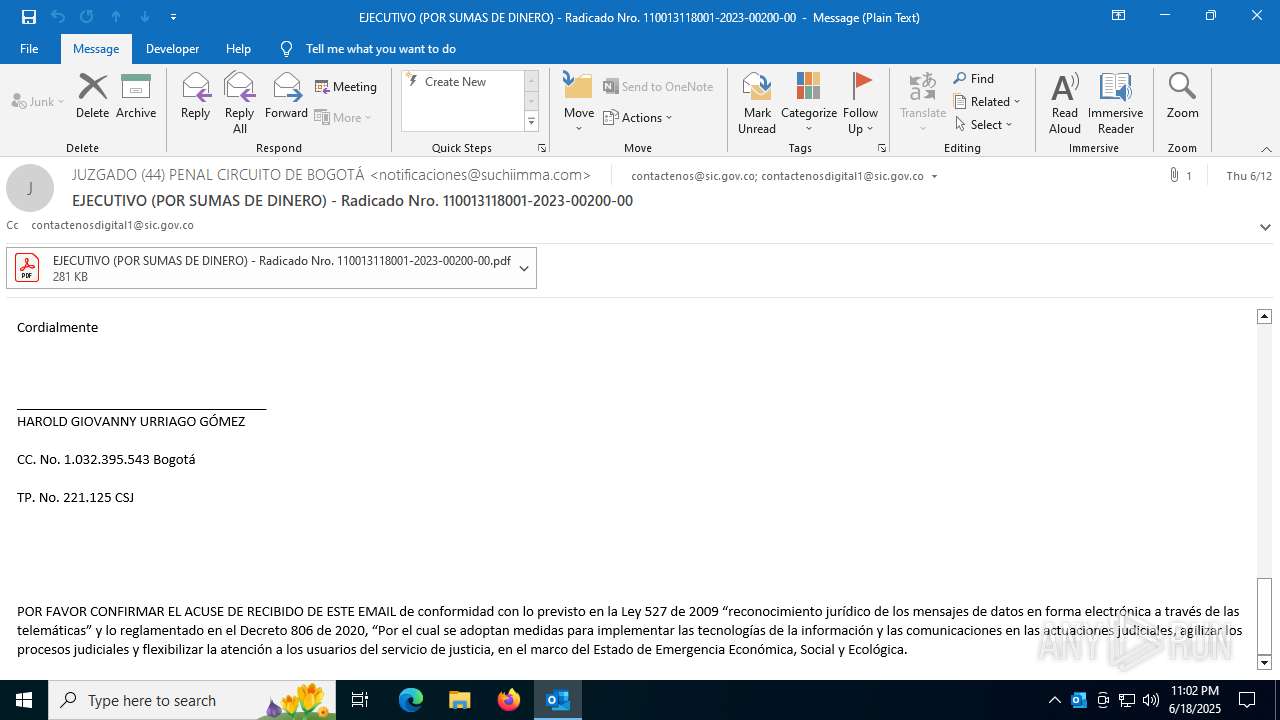
Email with attachments
- OUTLOOK.EXE (PID: 1720)
Email verification fail (SPF, DKIM or DMARC)
- OUTLOOK.EXE (PID: 1720)
Application launched itself
- Acrobat.exe (PID: 5060)
- Acrobat.exe (PID: 1932)
- AcroCEF.exe (PID: 1896)
- msedge.exe (PID: 3388)
- Acrobat.exe (PID: 7952)
Reads Microsoft Office registry keys
- Acrobat.exe (PID: 1336)
- OpenWith.exe (PID: 6268)
- msedge.exe (PID: 3388)
- OpenWith.exe (PID: 8124)
- OpenWith.exe (PID: 8396)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 6268)
- OpenWith.exe (PID: 8396)
Reads product name
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
Create files in a temporary directory
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
- MpCmdRun.exe (PID: 8128)
The sample compiled with english language support
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
Reads the computer name
- identity_helper.exe (PID: 7792)
- InstallUtil.exe (PID: 8472)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8760)
- AddInProcess32.exe (PID: 9096)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
- AddInProcess32.exe (PID: 3564)
- MpCmdRun.exe (PID: 8128)
Reads Environment values
- identity_helper.exe (PID: 7792)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
Checks supported languages
- identity_helper.exe (PID: 7792)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8252)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 8660)
- InstallUtil.exe (PID: 8472)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8760)
- AddInProcess32.exe (PID: 9096)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 7084)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 7032)
- EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.PDF.exe (PID: 6384)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
- AddInProcess32.exe (PID: 3564)
- MpCmdRun.exe (PID: 8128)
Launching a file from a Registry key
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8344)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8760)
- COMUNICO_DESPACHO_COMISORIO_No.020_PROCESO RAD.2025-00378.exe (PID: 8600)
Reads the machine GUID from the registry
- InstallUtil.exe (PID: 8472)
- AddInProcess32.exe (PID: 9096)
- AddInProcess32.exe (PID: 3564)
Reads the software policy settings
- InstallUtil.exe (PID: 8472)
- slui.exe (PID: 5424)
Checks proxy server information
- slui.exe (PID: 5424)
Manual execution by a user
- WinRAR.exe (PID: 7988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(8472) InstallUtil.exe
C2 (1)microsofteams.duckdns.org
Ports (1)7786
Version1.0.7
Options
AutoRunfalse
Mutex@"s#45AY8*56E3F4sfw%$
InstallFolder%AppData%
Certificates
Cert1MIICMDCCAZmgAwIBAgIVAKMXQVIpHTnrEavZUr9Rawv90ZRjMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIzMTAwNzAwMjYwMFoXDTM0MDcxNjAwMjYwMFowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureM3gvzzqbuBvh+7gthxBe73JnpnMjctDajWekrfePS/cToHlfCcMt/Y3OBlJ+ALfESbM6WUKqjwx01Y5IrpTcjjRSq/I9VvajkBM9RtFnLqAbc1m0vG3x55a5A3JzntjdbQFQivqlZZIW190tA+ROGGcT9gnS/aK/6FiiJyifyy0=
Keys
AES99cab1867662ba6de139f4ce4a97550fa20451214de492a621c9402a5d8cb685
SaltDcRatByqwqdanchun
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
237
Monitored processes
86
Malicious processes
11
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc3c79f208,0x7ffc3c79f214,0x7ffc3c79f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
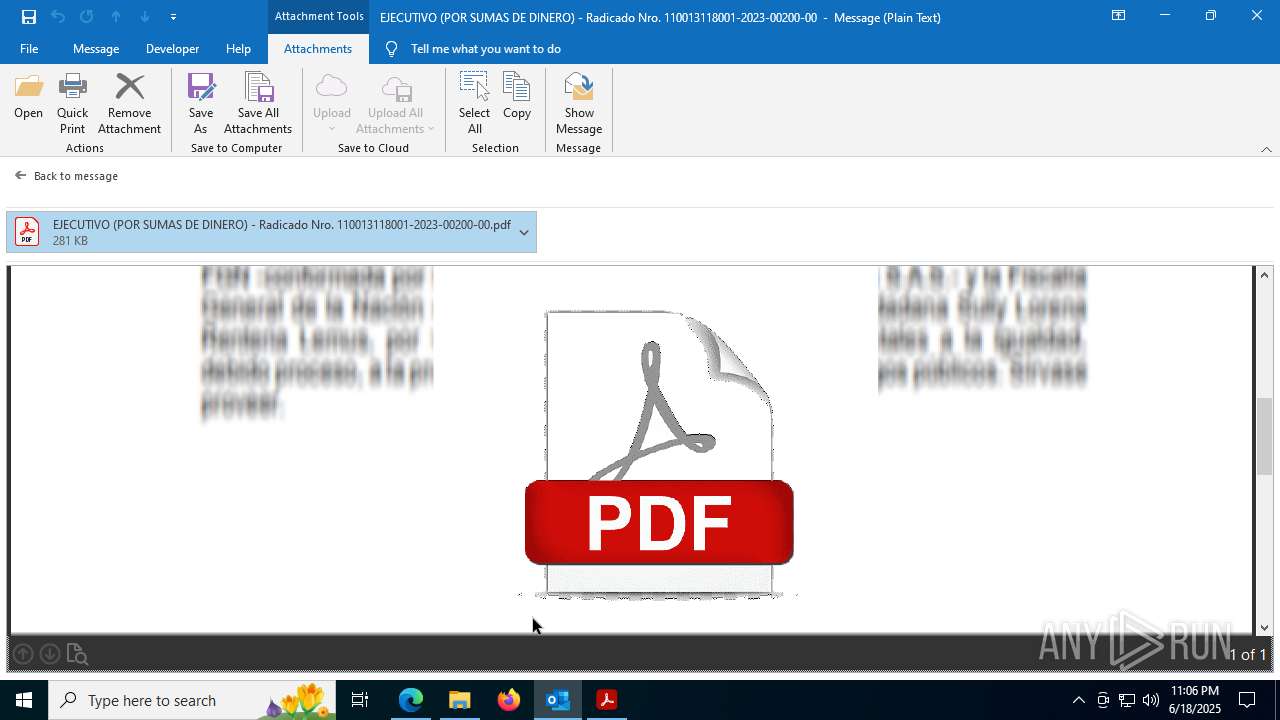
| 1336 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OYOZS7P0\EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1472 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1532 --field-trial-handle=1400,i,7979753546168573812,14070867380370395013,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 /b /id 7000_691294431 /if pdfshell_prev20f338b8-6c57-4ab6-a271-05605c2cdd1b /CR | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Downloads\EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00\EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1688 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1536 --field-trial-handle=1400,i,7979753546168573812,14070867380370395013,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\correo_25-280322- -0.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1896 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OYOZS7P0\EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | OpenWith.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1948 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --always-read-main-dll --field-trial-handle=7324,i,3952996415419640261,300046319628063204,262144 --variations-seed-version --mojo-platform-channel-handle=5756 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
51 421
Read events
49 952
Write events
1 290
Delete events
179
Modification events
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\1720 |
| Operation: | write | Name: | 0 |
Value: 0B0E10940C6D8FB505CF4DAE443BA911C8E54423004692FCFFE1D094F8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B80DD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (1720) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
82
Suspicious files
397
Text files
73
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1720 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:F16B7489F232110C51AAFDE7B5E1FCD3 | SHA256:B8FB8158FED3F6788B9CDF3B130AF165FD55F77560B9DD949E5EA734B2CF5D19 | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1336 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents-journal | binary | |
MD5:DF46C0B664EB7D67A8851CFFF799B26E | SHA256:D6AABDDE84A62AB03A03EC43645E320F7DB2414312DF9F2D0479973D4D894641 | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:BFFF48502EDA502507A31BB68626B492 | SHA256:AC3244B61BB1D221F77DB735762FF095F5EB7AB8D98396FFBE3BD623E3E372FA | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_1FF1224467F14748867FC686A5AA95C5.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OYOZS7P0\EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00.pdf | ||
MD5:335241A301EAF4F1A19B7D025C33E289 | SHA256:7D525BE95B2ABAD949D94B58D8025FE6B3DF13D861C5B234F3383DE0C2B01182 | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk6409.tmp | binary | |
MD5:333EF960119544BA00E14FECFD822E81 | SHA256:2F90F2F4435298DD4EBD7AD612C1A08D5FA4691168D24EA950937B2E71CC1FA6 | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:B3D8FEFE4F410282C02EAD0E8E216146 | SHA256:CBCBE96DD5EE809115B7A99A8D4559E72836AE33BE9CED26A81DD03A758332A3 | |||
| 1720 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OYOZS7P0\EJECUTIVO (POR SUMAS DE DINERO) - Radicado Nro. 110013118001-2023-00200-00 (002).pdf:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
105
DNS requests
97
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4040 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4040 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7332 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:1QGM78jW1J5KpSqoTD71EgRRlOOLepgUu1Q3ScRkTt4&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
8880 | svchost.exe | HEAD | 200 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750816482&P2=404&P3=2&P4=bNvxMmNQMgHBfZiRECitUFlBp7tMob8Y9gltla2xr5%2fLzpilj0ivW5CiDSEd1iZ6t6QyI0mg%2bKvpYxxsQwfZYw%3d%3d | unknown | — | — | whitelisted |
1932 | Acrobat.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
8880 | svchost.exe | GET | 200 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1750816483&P2=404&P3=2&P4=cc2zOofJm6KtPHkyG%2fL79luXHy5LxfOTOV6FU7f4fsm%2fehAGzBfNsdRy5IVt%2f0qxAAphZlXrvA9tdGJs0lzB0g%3d%3d | unknown | — | — | whitelisted |
8880 | svchost.exe | GET | 206 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750816482&P2=404&P3=2&P4=bNvxMmNQMgHBfZiRECitUFlBp7tMob8Y9gltla2xr5%2fLzpilj0ivW5CiDSEd1iZ6t6QyI0mg%2bKvpYxxsQwfZYw%3d%3d | unknown | — | — | whitelisted |
8880 | svchost.exe | GET | 206 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750816482&P2=404&P3=2&P4=bNvxMmNQMgHBfZiRECitUFlBp7tMob8Y9gltla2xr5%2fLzpilj0ivW5CiDSEd1iZ6t6QyI0mg%2bKvpYxxsQwfZYw%3d%3d | unknown | — | — | whitelisted |
8880 | svchost.exe | HEAD | 200 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1750816483&P2=404&P3=2&P4=cc2zOofJm6KtPHkyG%2fL79luXHy5LxfOTOV6FU7f4fsm%2fehAGzBfNsdRy5IVt%2f0qxAAphZlXrvA9tdGJs0lzB0g%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1136 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1720 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1720 | OUTLOOK.EXE | 2.16.106.20:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
1720 | OUTLOOK.EXE | 52.111.231.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6748 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6748 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
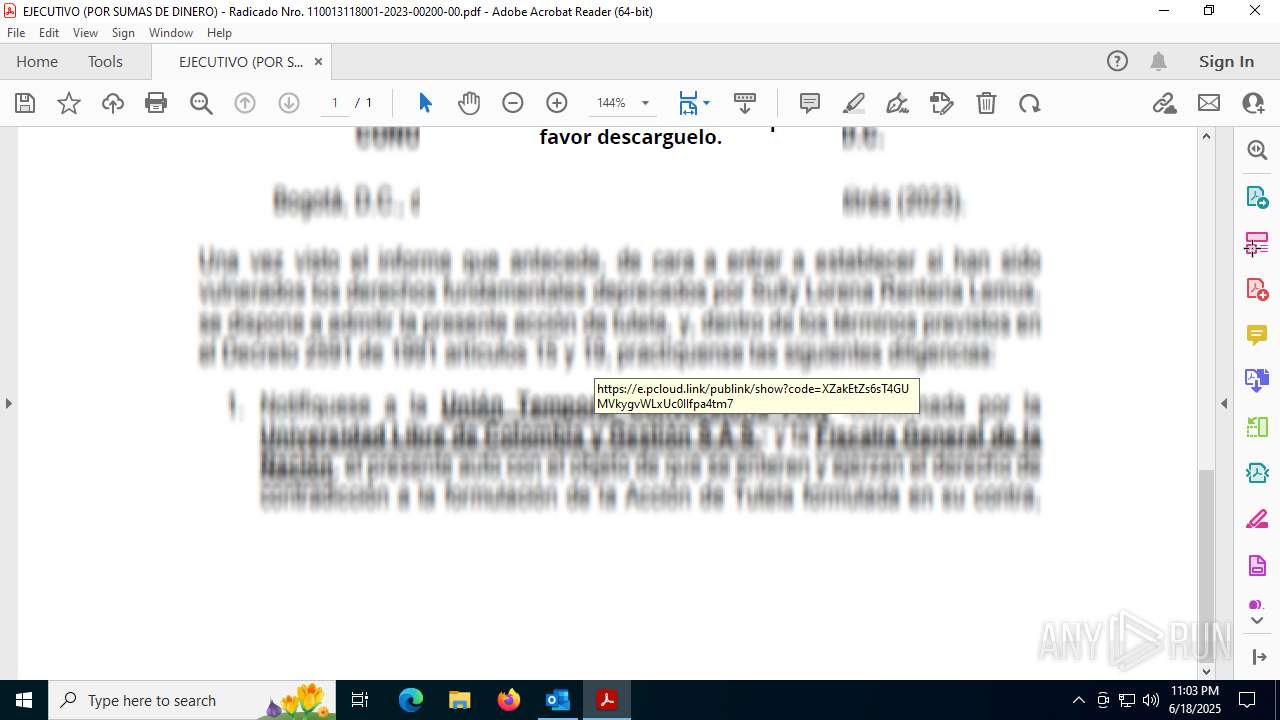
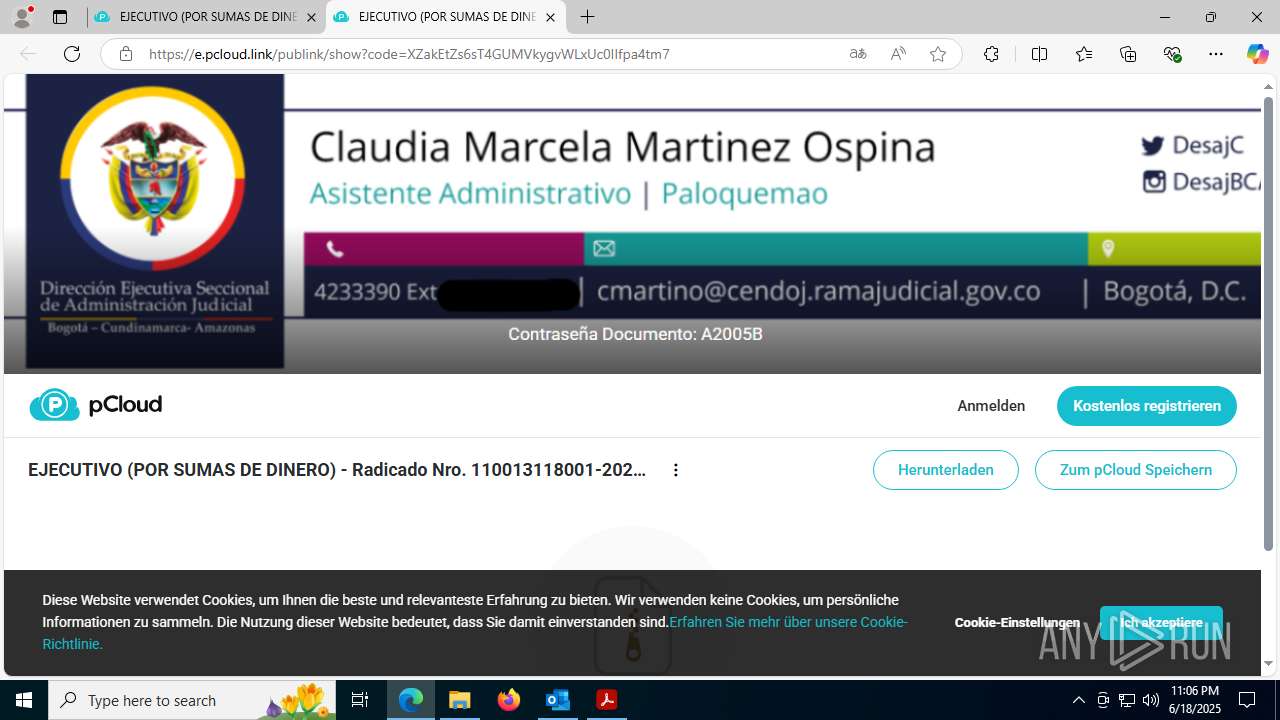
7332 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed in DNS Lookup (pcloud .com) |
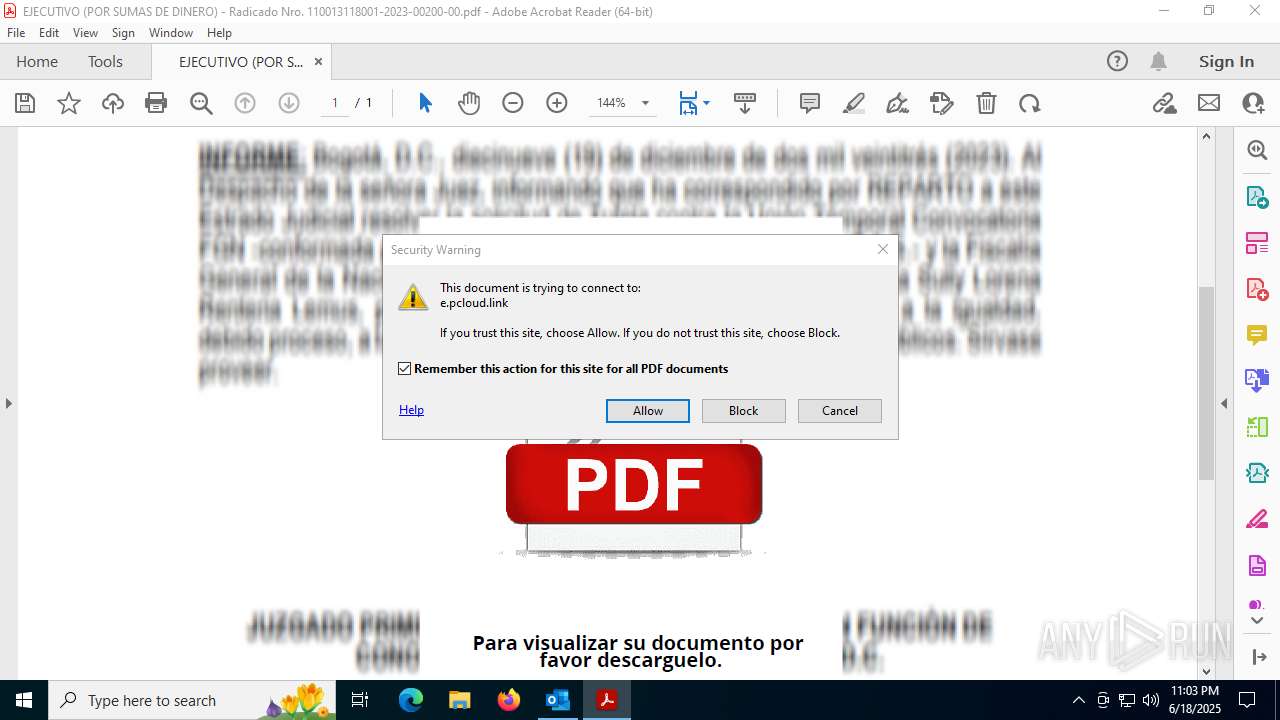
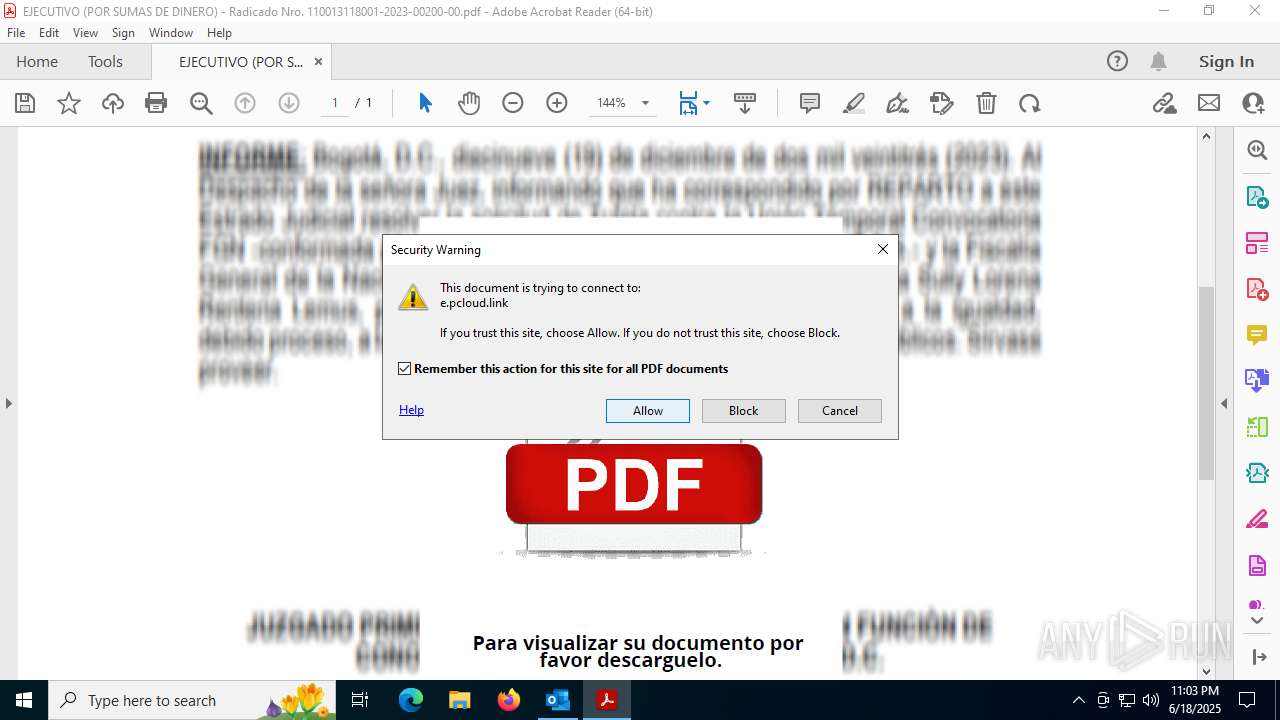
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
7332 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed in DNS Lookup (pcloud .com) |
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
7332 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed in DNS Lookup (pcloud .com) |
7332 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |