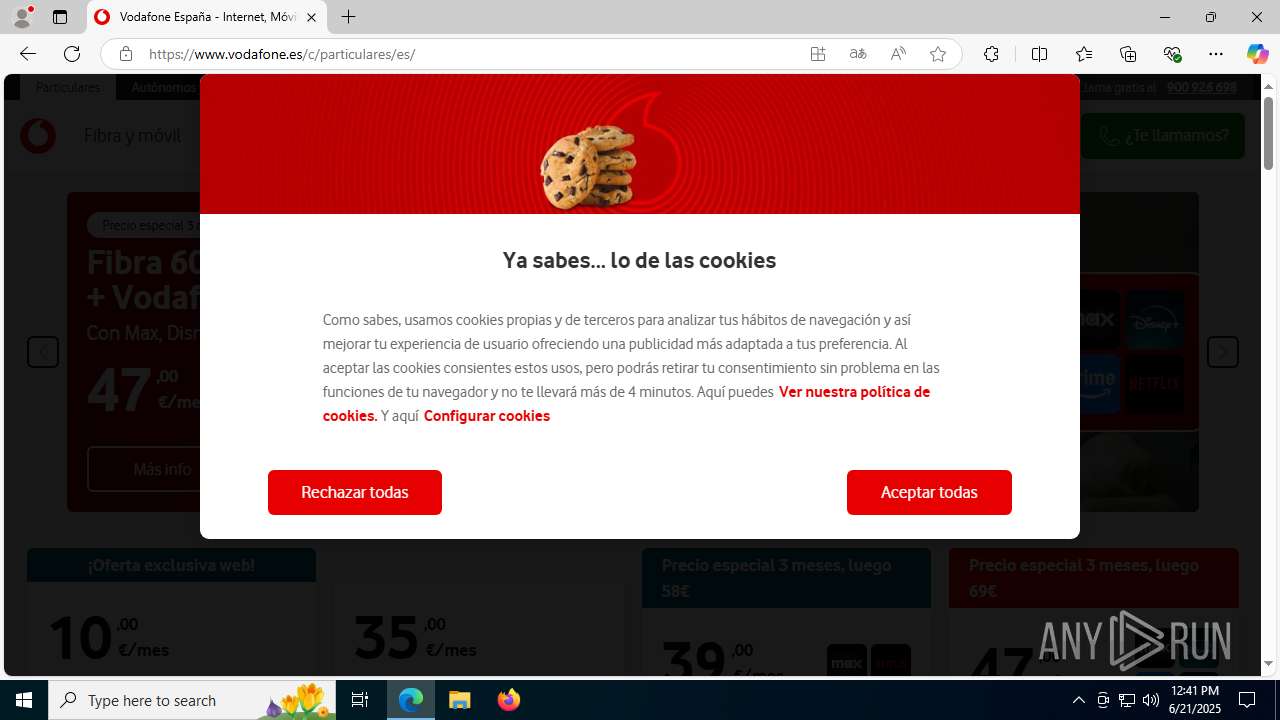
| URL: | https://e.vg/VF-V0DAF0NE |
| Full analysis: | https://app.any.run/tasks/a7b1a87e-2065-4035-9ad3-305afa62e411 |
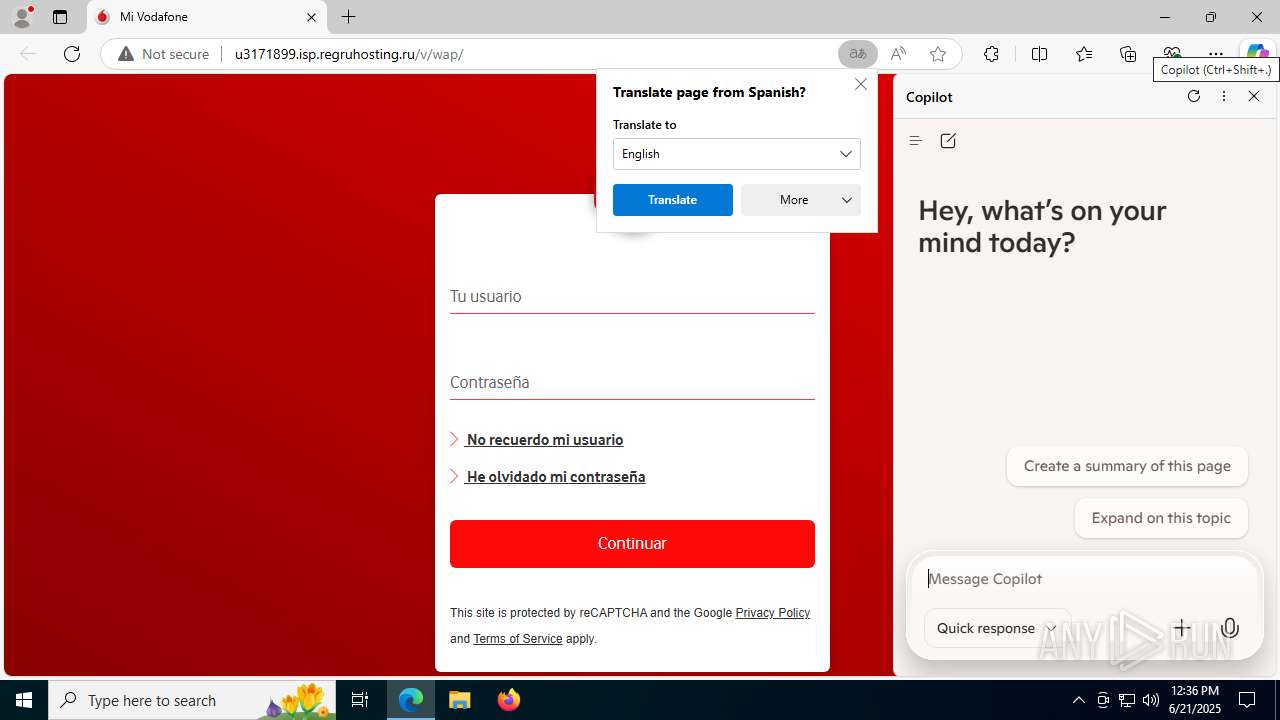
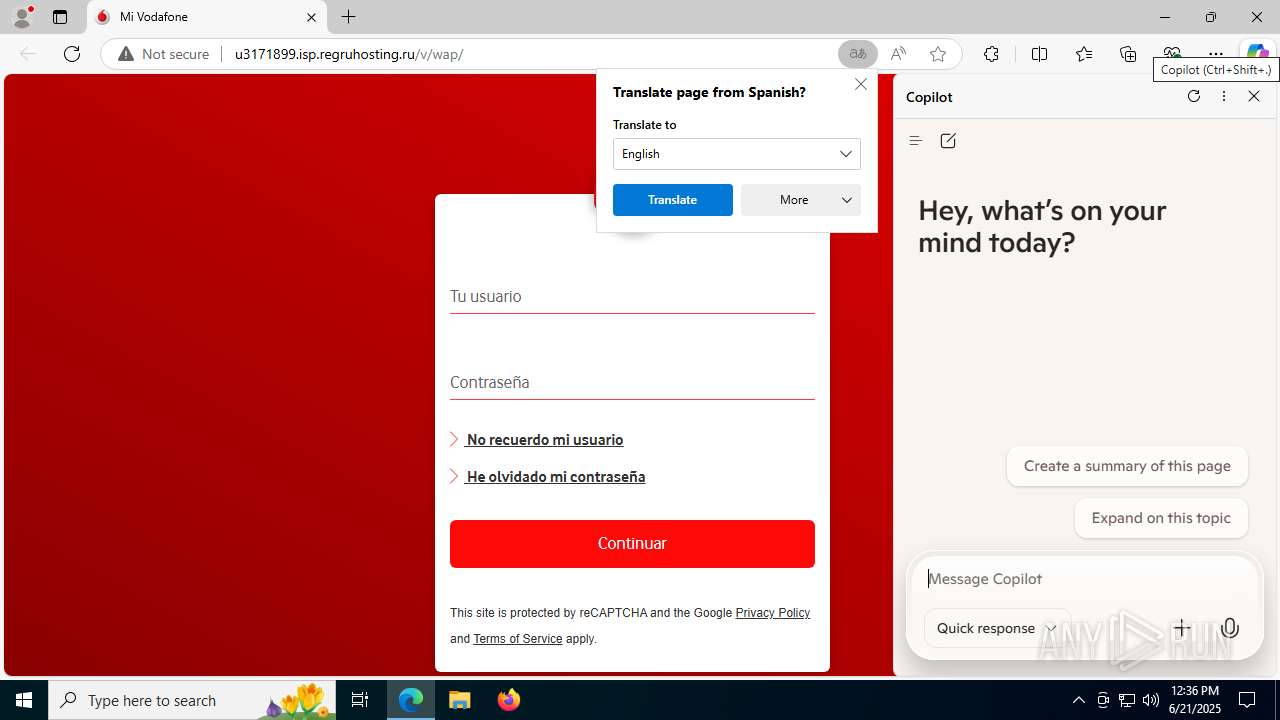
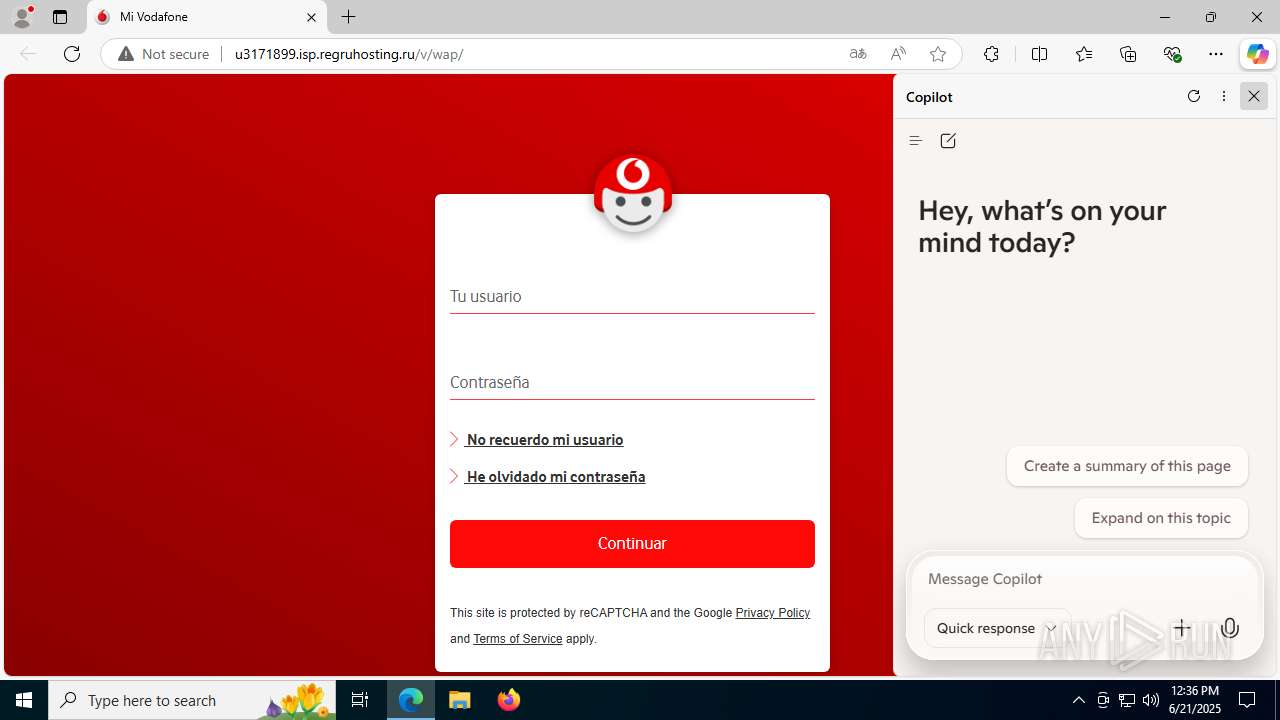
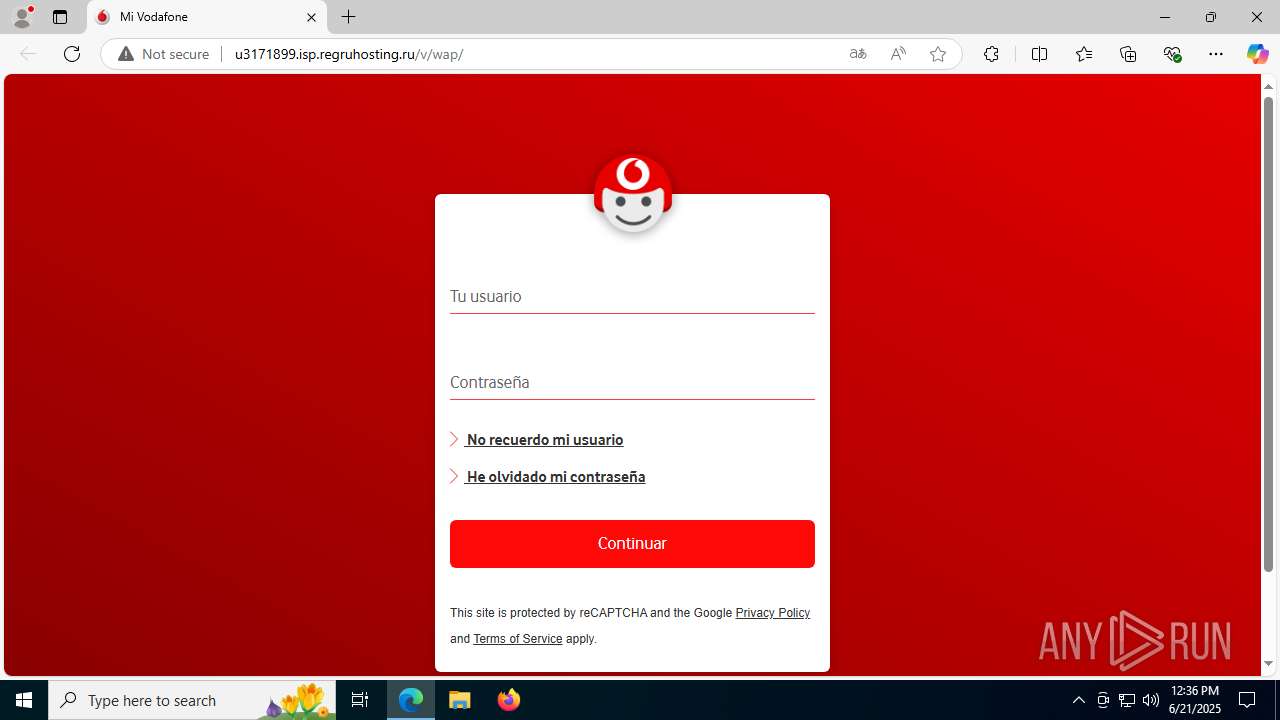
| Verdict: | Malicious activity |
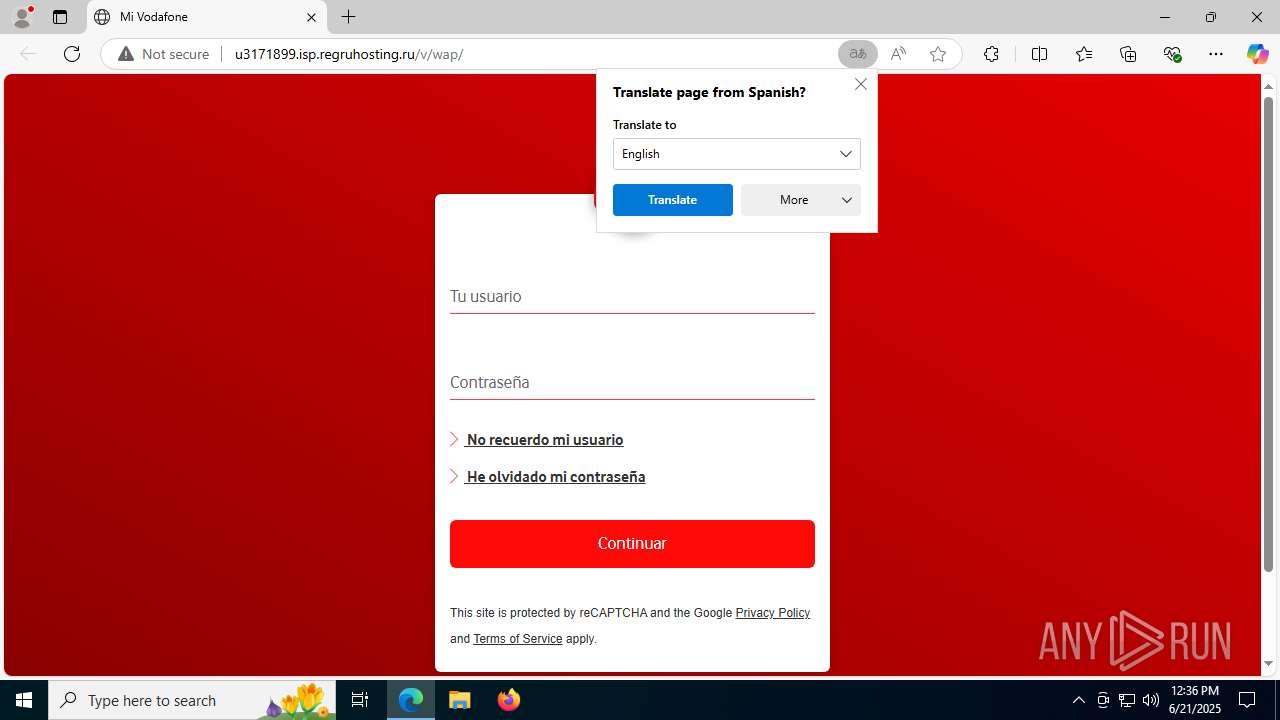
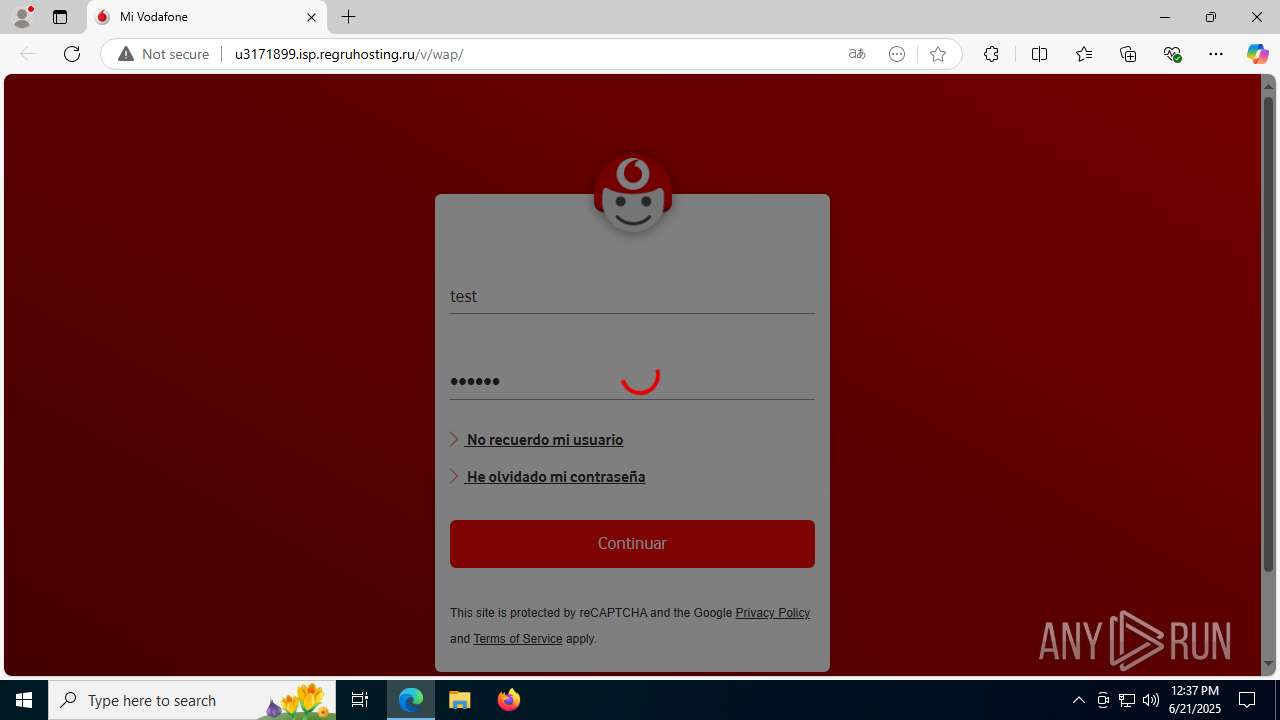
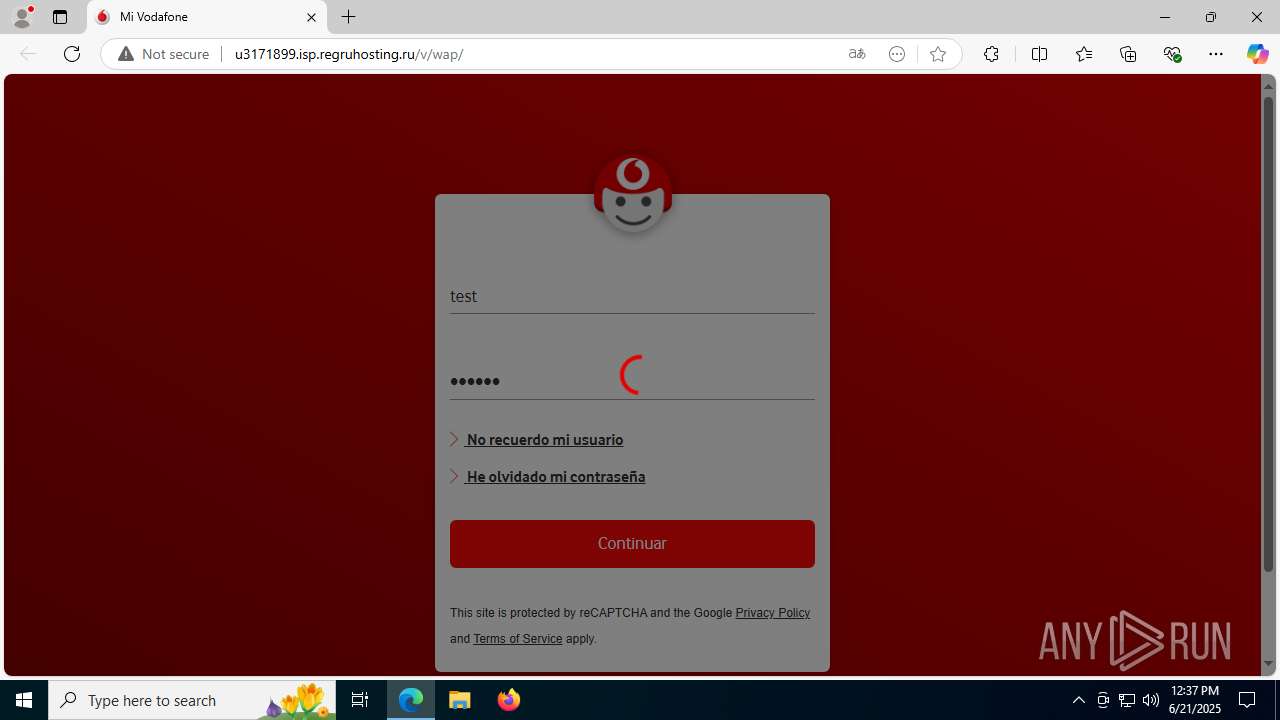
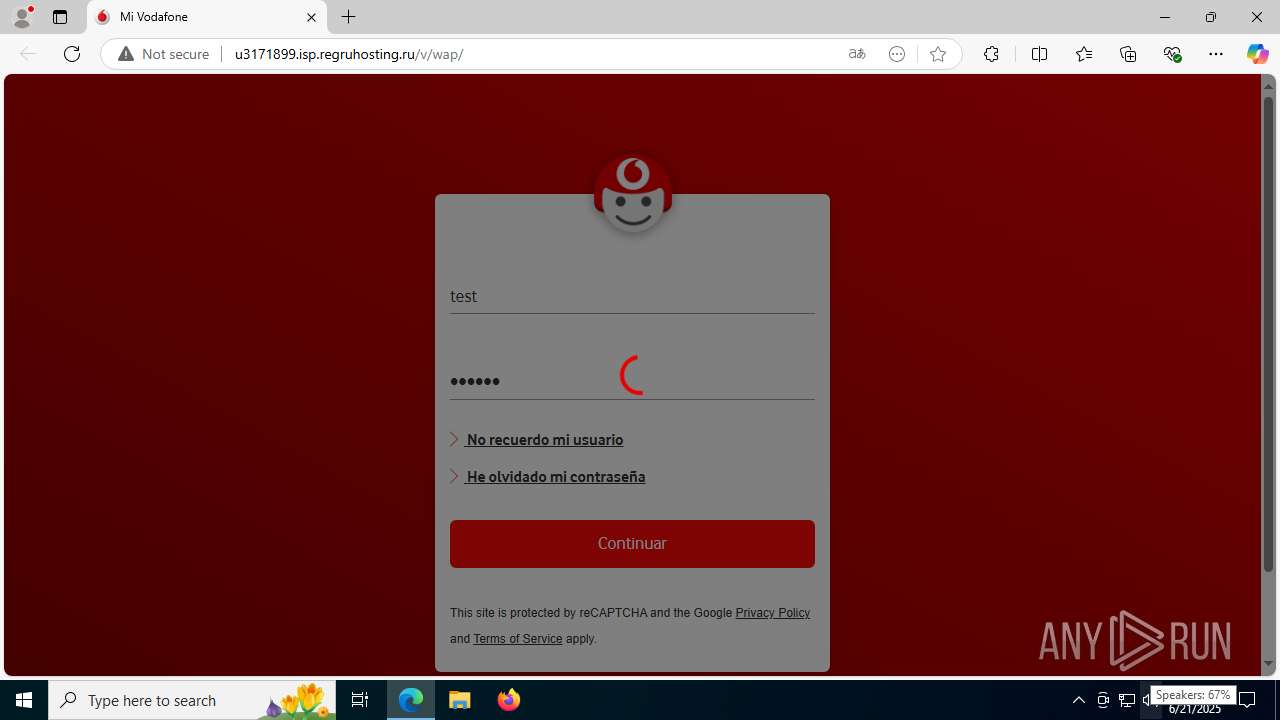
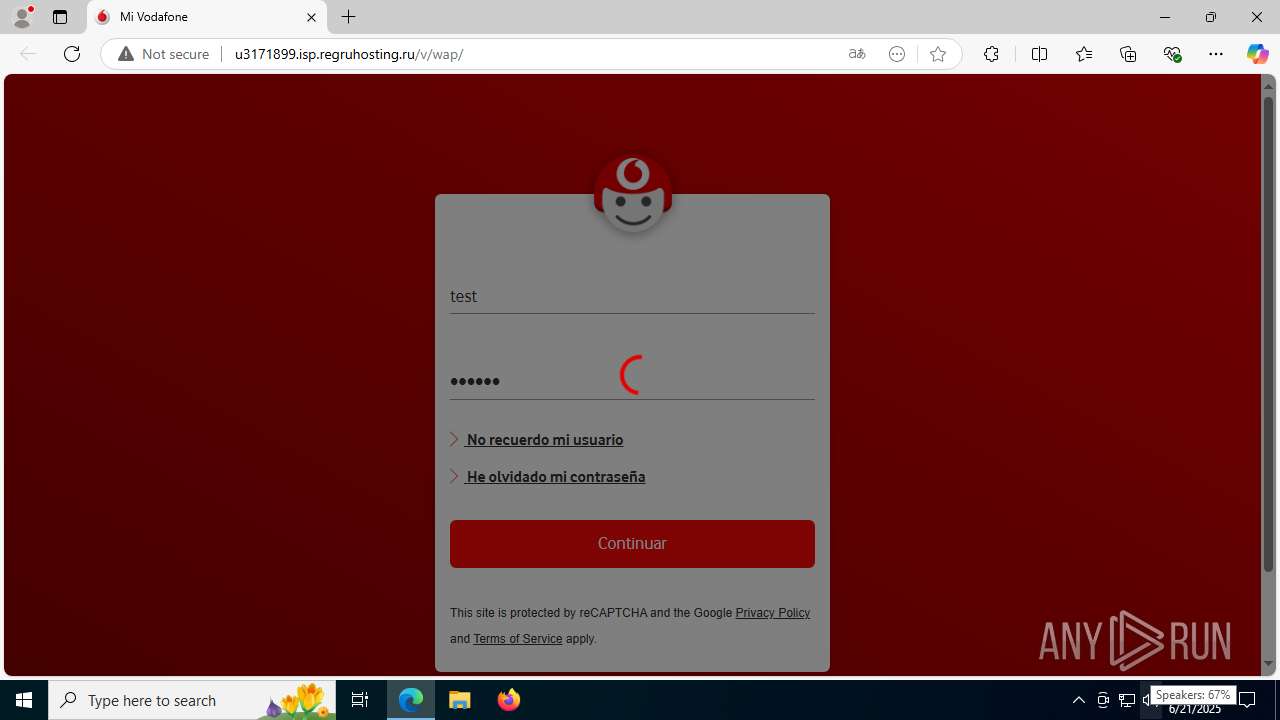
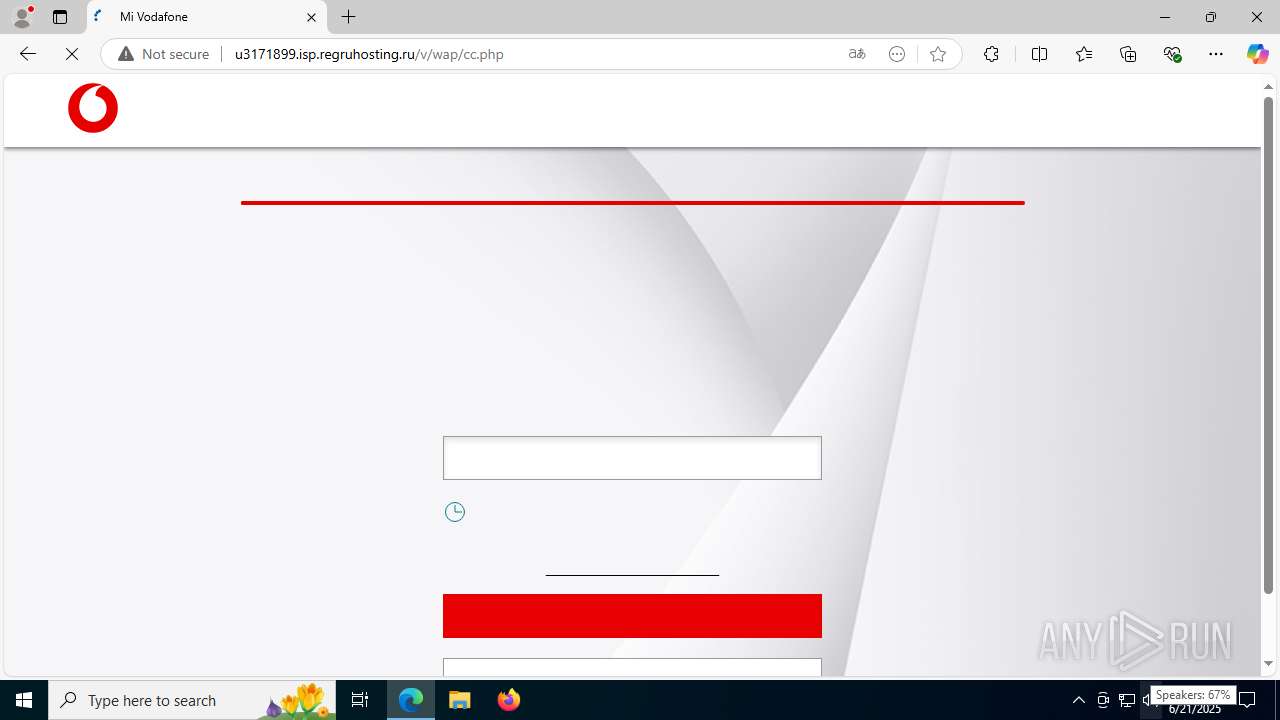
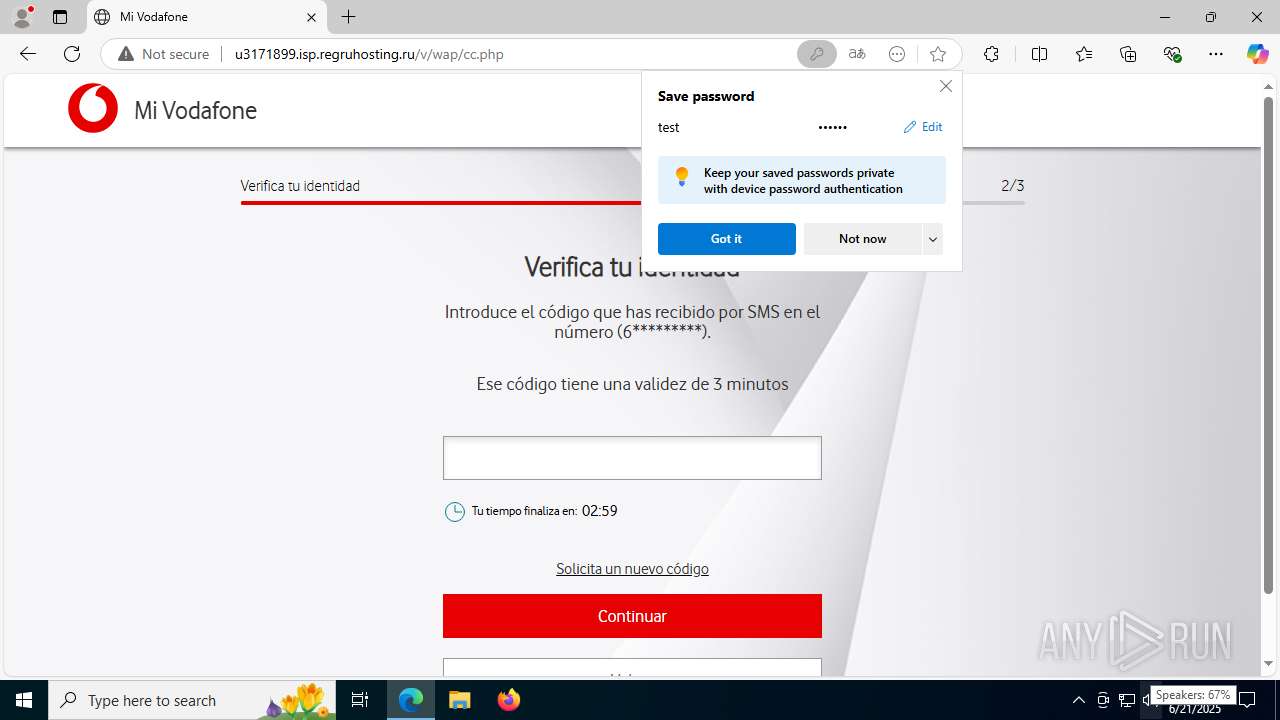
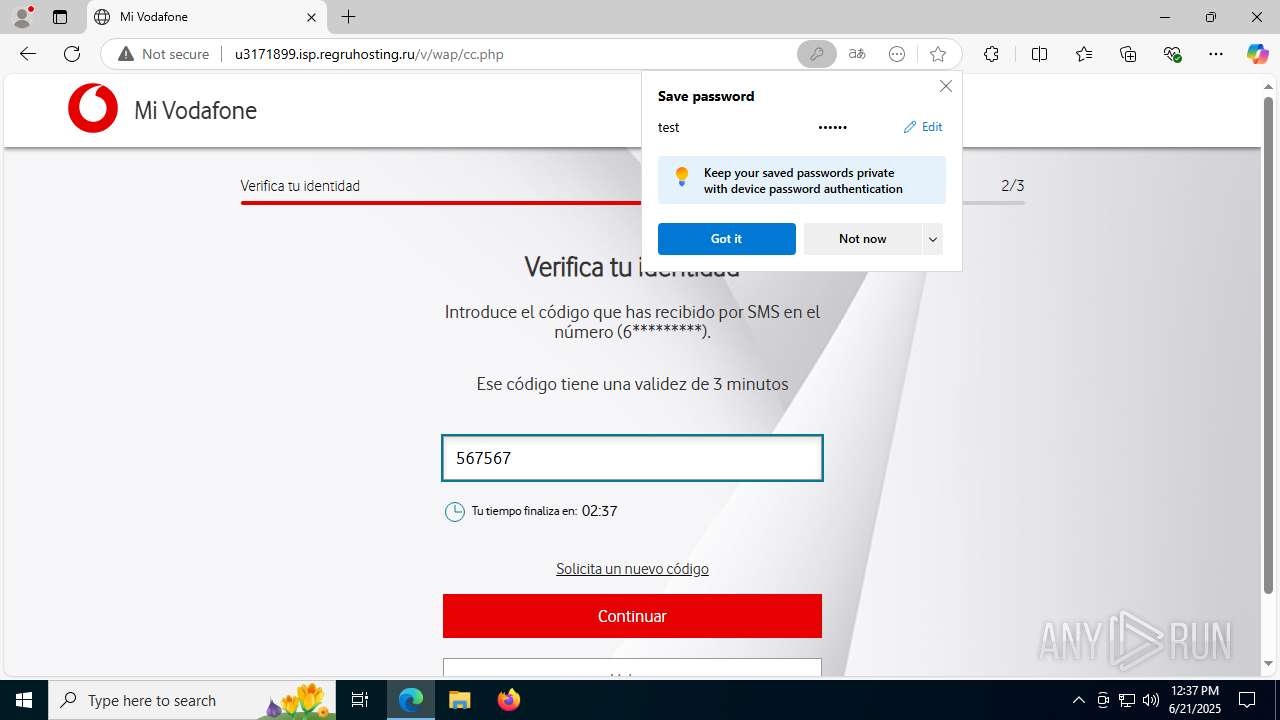
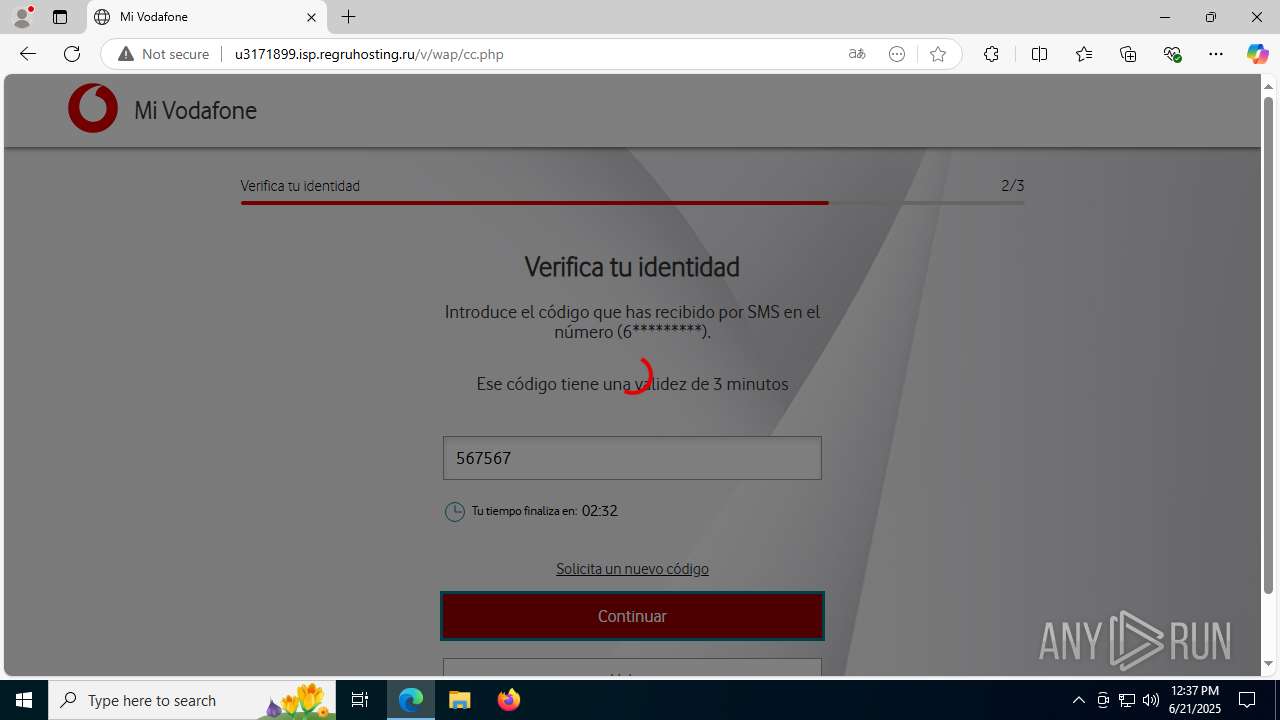
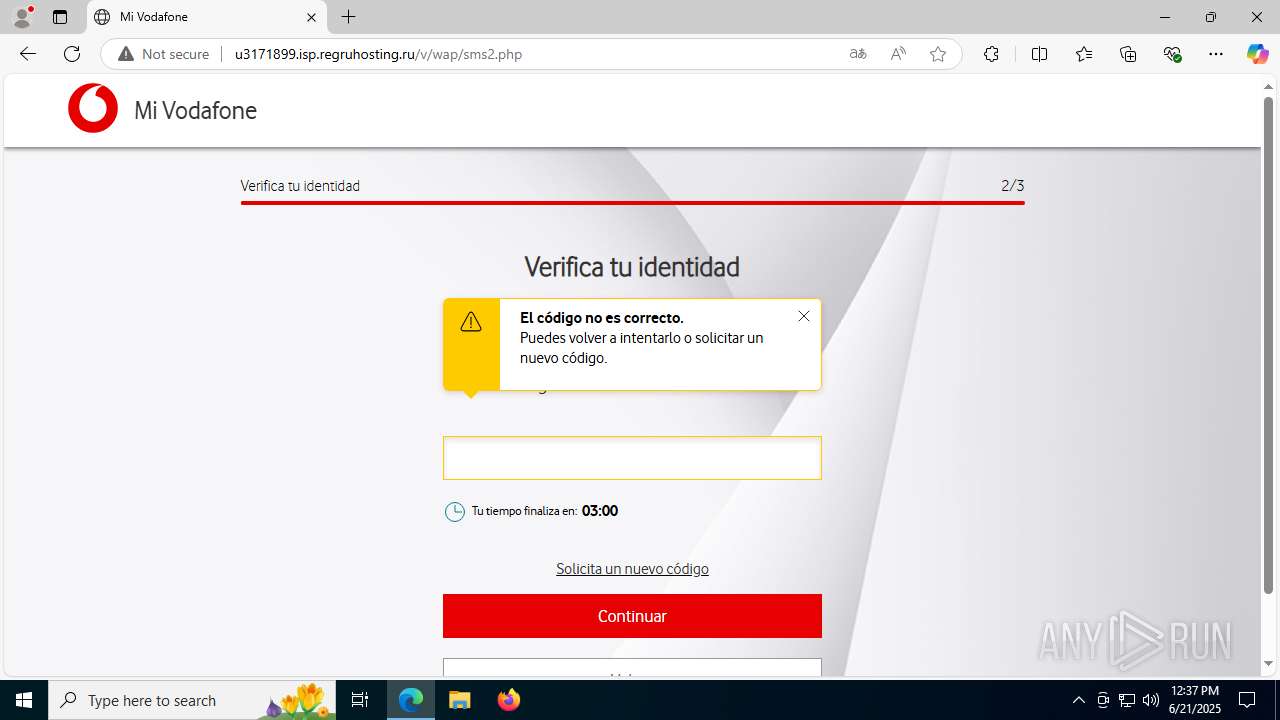
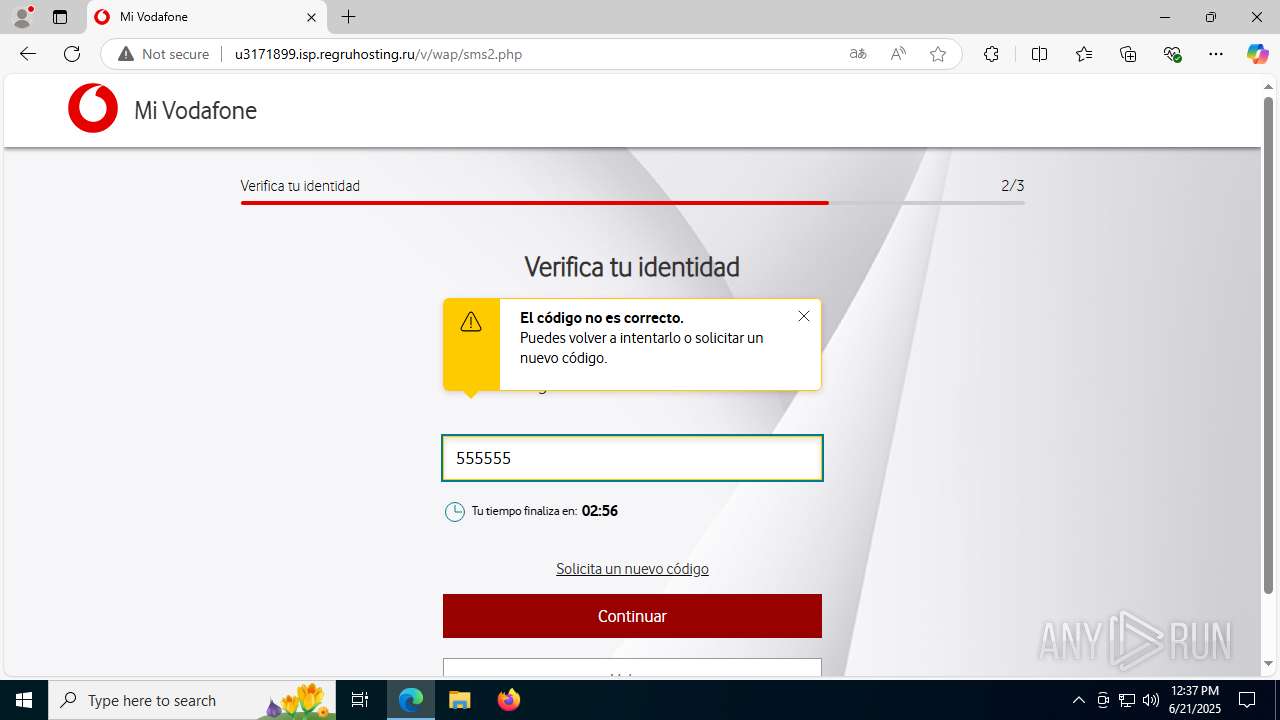
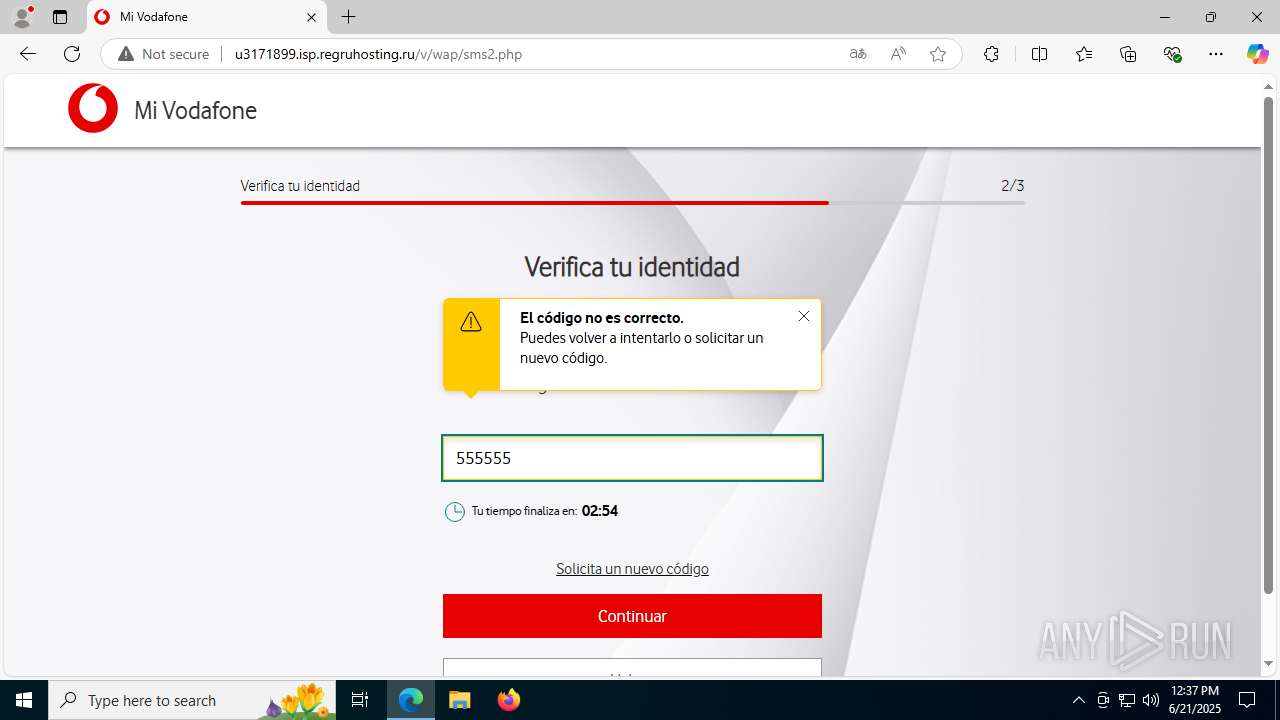
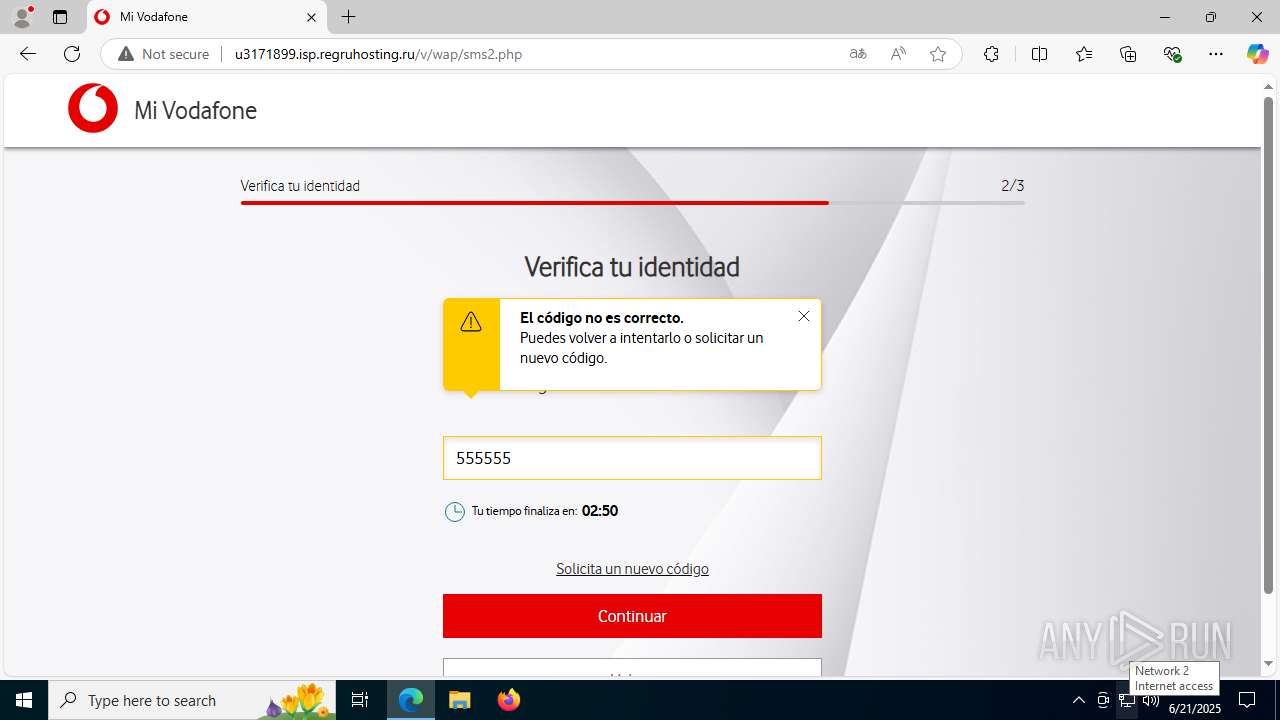
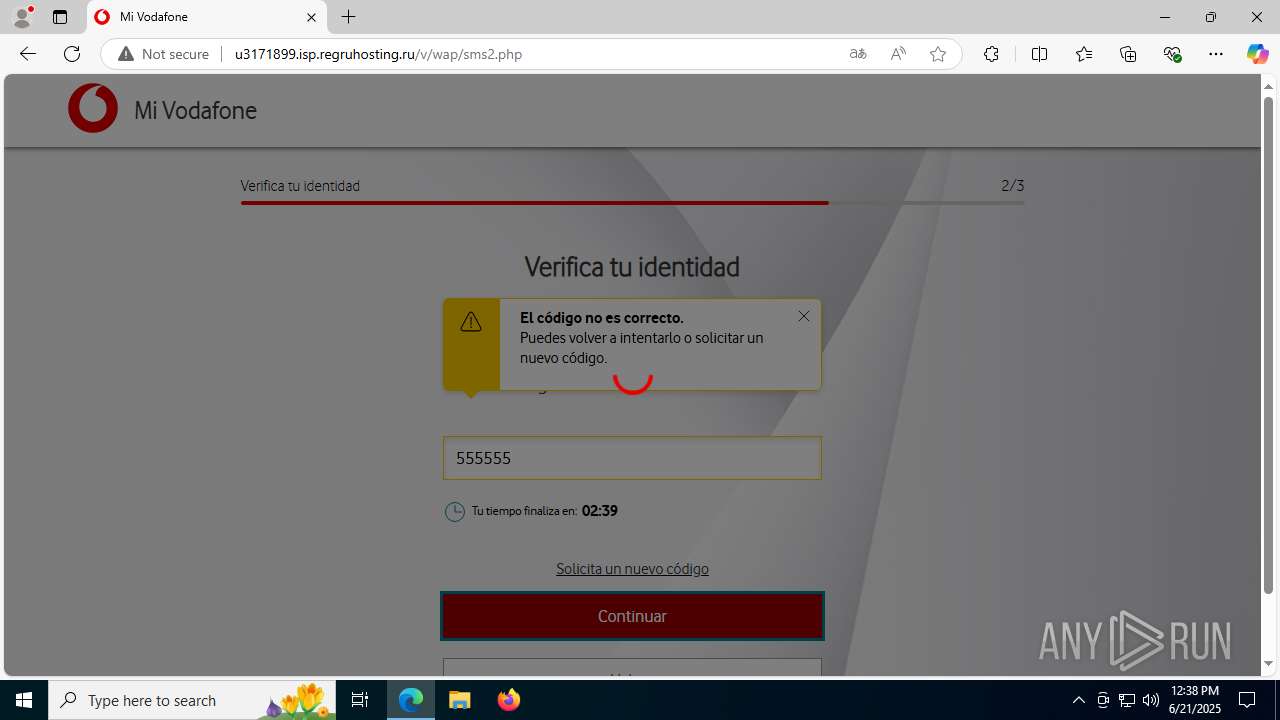
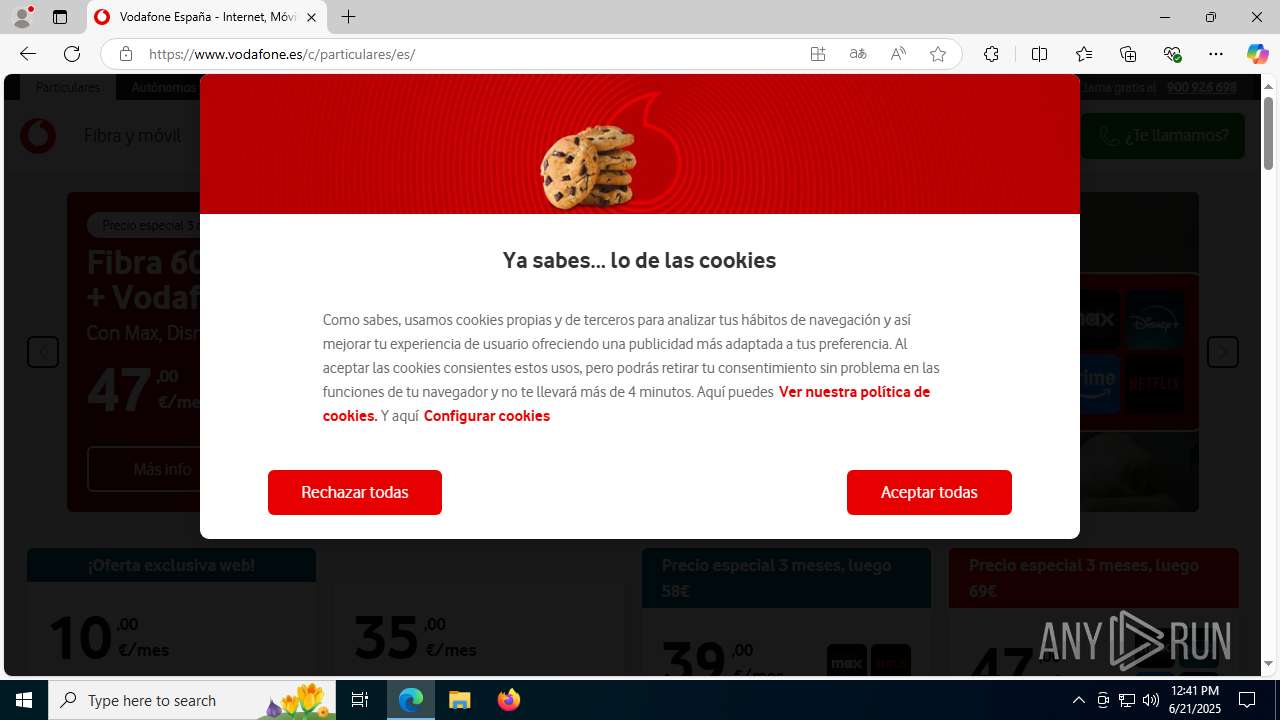
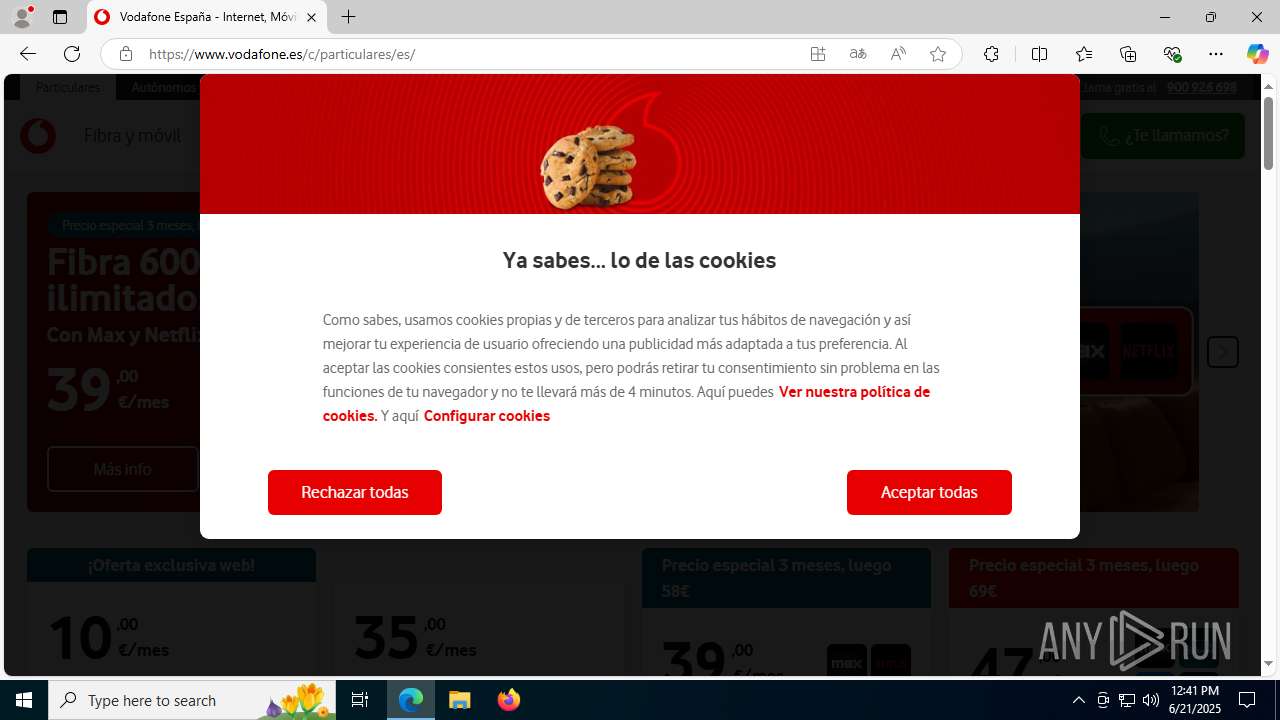
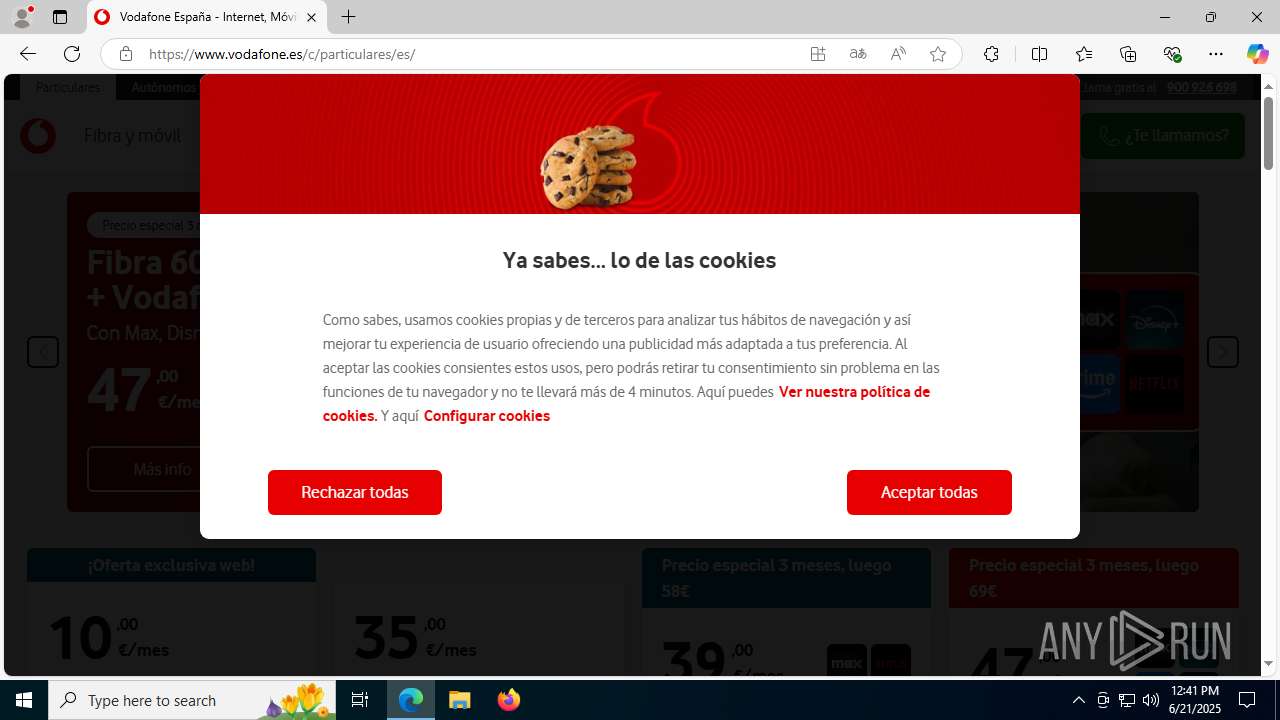
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | June 21, 2025, 12:36:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 54BB2E198117EFE86F5D011A946F69C4 |
| SHA1: | 1A819DE0525D2E19258811946C3A26A511D46555 |
| SHA256: | 96D923D4EF0442FC29321BA5F349247E72C9C855C2E0FEDF79DA16DE8EEA88C5 |
| SSDEEP: | 3:N85t:2z |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 3960)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- msedge.exe (PID: 3752)
Checks supported languages
- identity_helper.exe (PID: 7632)
Reads Environment values
- identity_helper.exe (PID: 7632)
Reads the computer name
- identity_helper.exe (PID: 7632)
Reads the software policy settings
- slui.exe (PID: 3948)
Checks proxy server information
- slui.exe (PID: 3948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
186
Monitored processes
38
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4292,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=4300 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1352 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6620,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=1344 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc431cf208,0x7ffc431cf214,0x7ffc431cf220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2348 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3636,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=3536 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2708 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6636,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=6092 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2740,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=2776 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3752 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://e.vg/VF-V0DAF0NE" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3852 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7156,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=5496 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3948 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3960 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2256,i,10450304657847663546,4194243814583413958,262144 --variations-seed-version --mojo-platform-channel-handle=2548 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
5 037
Read events
5 009
Write events
28
Delete events
0
Modification events
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 658F7F83AA962F00 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393992 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6C94C12C-F501-4873-A70E-1F8D5EAEC4C5} | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393992 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9938C02A-5152-4AF2-9F21-7E27E30F1C91} | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393992 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {40A5934B-DA30-4C98-ADAB-7EA3A23A4205} | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (3752) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
Executable files
11
Suspicious files
292
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF176810.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176820.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF176820.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF176820.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF17683f.TMP | — | |
MD5:— | SHA256:— | |||
| 3752 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
145
DNS requests
143
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3960 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:jAXE_5S06iD32aO74nzyiclvFNSmztBDR8J2Vb3KgAg&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
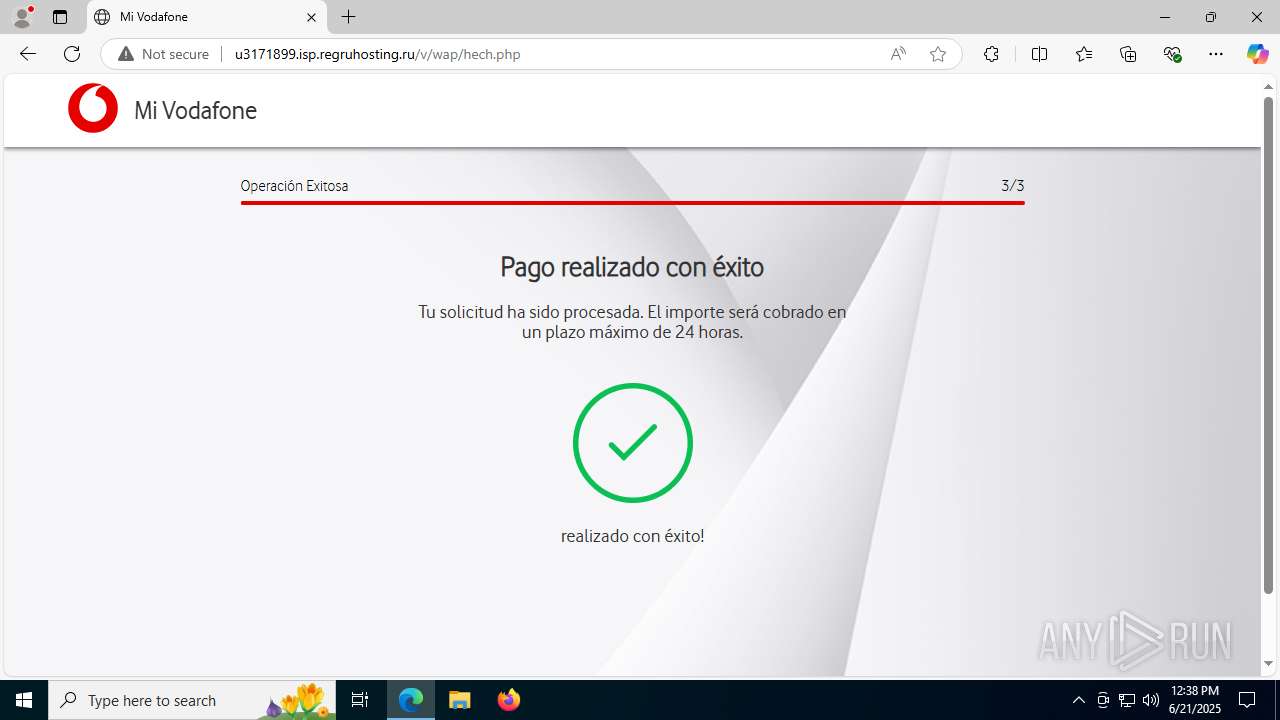
3960 | msedge.exe | GET | 302 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/ | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 200 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/ | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 200 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/style/styles.css | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 404 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/fonts/vodafone-regular.woff2 | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 200 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/style/Wink@xhdpi.png | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 200 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/style/group.gif | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 200 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/js/jquery.js | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | — | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/fonts/vodafone-bold.woff2 | unknown | — | — | whitelisted |
3960 | msedge.exe | GET | 200 | 31.31.197.16:80 | http://u3171899.isp.regruhosting.ru/v/wap/style/Vodafone-Regular.woff | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1508 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3960 | msedge.exe | 188.114.97.3:443 | e.vg | CLOUDFLARENET | NL | malicious |
3960 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3960 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3960 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3960 | msedge.exe | 92.123.104.53:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
e.vg |
| malicious |
copilot.microsoft.com |
| whitelisted |
u3171899.isp.regruhosting.ru |
| whitelisted |
www.bing.com |
| whitelisted |
assets-es.dxl.local.vodafone.es |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3960 | msedge.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (e .vg) |
3960 | msedge.exe | Misc activity | ET INFO URL Shortening Service Domain in DNS Lookup (e .vg) |
3960 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Domain was related with Tycoon Phishing |
3960 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Domain was related with Tycoon Phishing |
3960 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Domain was related with Tycoon Phishing |
3960 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Domain was related with Tycoon Phishing |