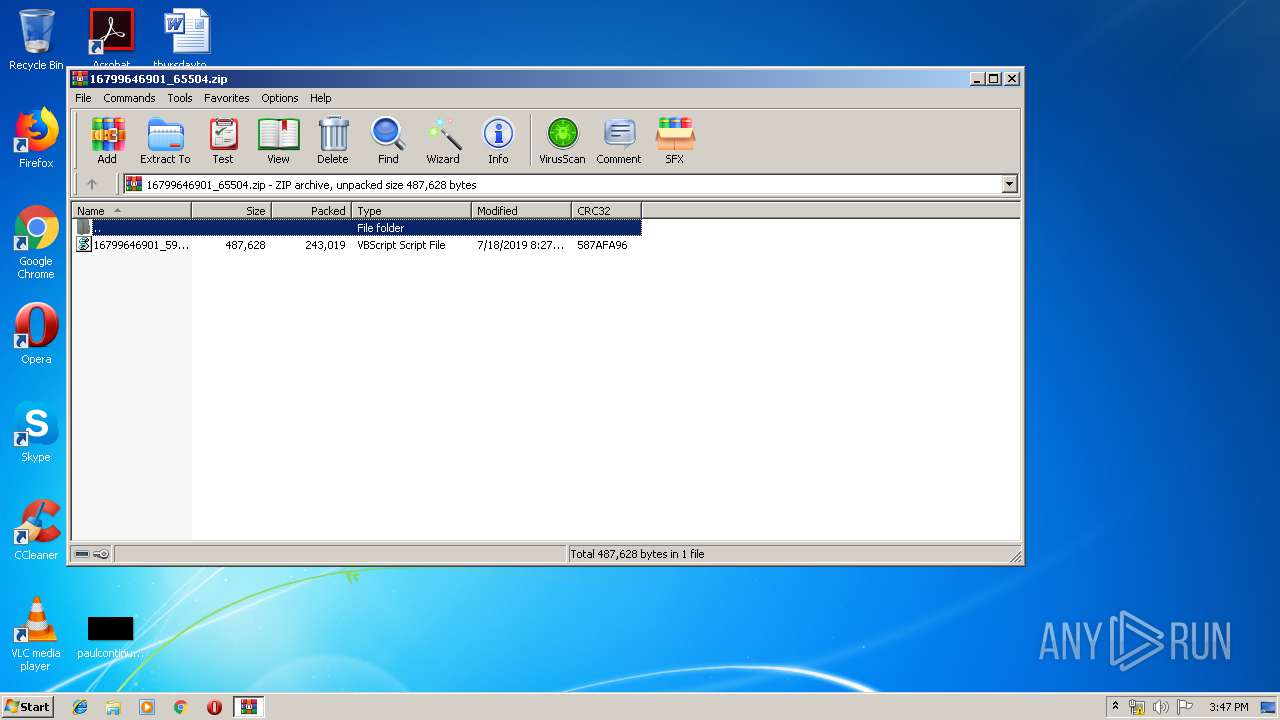
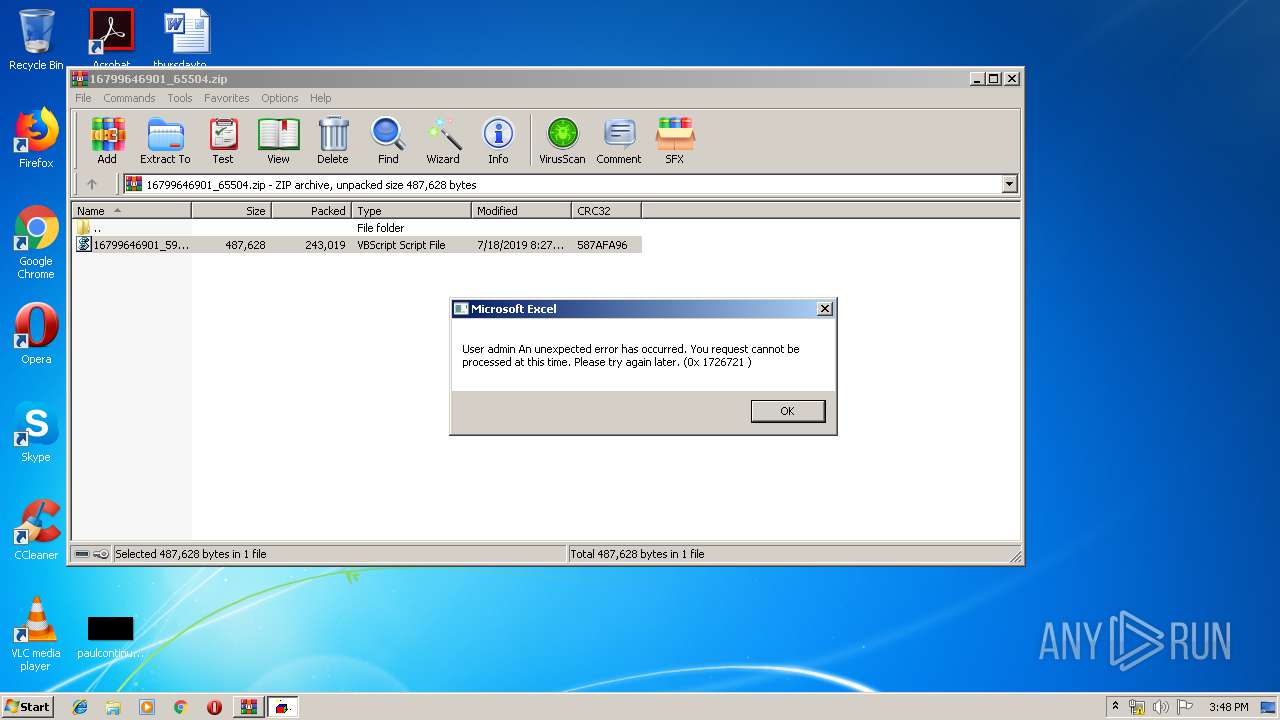
| File name: | 16799646901_65504.zip |
| Full analysis: | https://app.any.run/tasks/2d98e6ff-d61b-4443-bba1-283ba49221ae |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 18, 2019, 14:47:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C521259711B2F590B0907C8BB2B8756A |
| SHA1: | 836DC03E94CF6892D09FFABFAA40B3A80B609B5C |
| SHA256: | 96AB15660DA0DD10C7DE1E07BAFA4D3975DE5644F25BACEA82087E179FD70613 |
| SSDEEP: | 6144:zm7IewVTxwjByuw6H923h8qkcj9bEpWz8DkyxEk:mI5wjB9GkcxbMDkeEk |
MALICIOUS
AMADEY was detected
- NZiCyph.exe (PID: 3104)
- kntd.exe (PID: 2996)
Connects to CnC server
- kntd.exe (PID: 2996)
Application was dropped or rewritten from another process
- kntd.exe (PID: 2996)
- NZiCyph.exe (PID: 3104)
Changes the Startup folder
- REG.exe (PID: 272)
SUSPICIOUS
Executes scripts
- WinRAR.exe (PID: 3884)
Executable content was dropped or overwritten
- WScript.exe (PID: 2136)
- NZiCyph.exe (PID: 3104)
Starts itself from another location
- NZiCyph.exe (PID: 3104)
Executed via WMI
- NZiCyph.exe (PID: 3104)
Creates files in the program directory
- NZiCyph.exe (PID: 3104)
Uses REG.EXE to modify Windows registry
- kntd.exe (PID: 2996)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:18 20:27:16 |
| ZipCRC: | 0x587afa96 |
| ZipCompressedSize: | 243019 |
| ZipUncompressedSize: | 487628 |
| ZipFileName: | 16799646901_599788061.vbs |
Total processes
40
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /f /v Startup /t REG_SZ /d C:\ProgramData\0cdfe991b7 | C:\Windows\system32\REG.exe | kntd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2136 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3884.28196\16799646901_599788061.vbs" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2996 | c:\programdata\0cdfe991b7\kntd.exe | c:\programdata\0cdfe991b7\kntd.exe | NZiCyph.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1810.13 Modules
| |||||||||||||||
| 3104 | C:\Users\admin\AppData\Local\Temp\NZiCyph.exe | C:\Users\admin\AppData\Local\Temp\NZiCyph.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1810.13 Modules
| |||||||||||||||
| 3884 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\16799646901_65504.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
843
Read events
822
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\16799646901_65504.zip | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4802 |
Value: VBScript Script File | |||
| (PID) Process: | (3884) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | WScript.exe | C:\Users\admin\AppData\Local\Temp\QcwLytGNY.txt | — | |
MD5:— | SHA256:— | |||
| 3104 | NZiCyph.exe | C:\ProgramData\0 | — | |
MD5:— | SHA256:— | |||
| 3104 | NZiCyph.exe | C:\programdata\0cdfe991b7\kntd.exe:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2996 | kntd.exe | C:\ProgramData\0 | — | |
MD5:— | SHA256:— | |||
| 3884 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3884.28196\16799646901_599788061.vbs | text | |
MD5:— | SHA256:— | |||
| 2136 | WScript.exe | C:\Users\admin\AppData\Local\Temp\NZiCyph.exe | executable | |
MD5:— | SHA256:— | |||
| 3104 | NZiCyph.exe | C:\programdata\0cdfe991b7\kntd.exe | executable | |
MD5:— | SHA256:— | |||
| 2136 | WScript.exe | C:\Users\admin\AppData\Local\Temp\JfLOtaCFA | text | |
MD5:— | SHA256:— | |||
| 2136 | WScript.exe | C:\Users\admin\AppData\Local\Temp\QcwLytGNY.txt.zip | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
3
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2996 | kntd.exe | POST | 200 | 91.224.22.138:80 | http://sakedratto.com/f5lkB/index.php | RU | text | 6 b | malicious |
2996 | kntd.exe | POST | 200 | 77.120.115.221:80 | http://lorefensed.ru/f5lkB/index.php | UA | text | 6 b | malicious |
2996 | kntd.exe | POST | 200 | 103.136.43.235:80 | http://tincolittat.ru/f5lkB/index.php | unknown | text | 6 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2996 | kntd.exe | 91.224.22.138:80 | sakedratto.com | Domain names registrar REG.RU, Ltd | RU | malicious |
2996 | kntd.exe | 77.120.115.221:80 | lorefensed.ru | Volia | UA | malicious |
2996 | kntd.exe | 103.136.43.235:80 | tincolittat.ru | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sakedratto.com |
| malicious |
tincolittat.ru |
| malicious |
lorefensed.ru |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2996 | kntd.exe | A Network Trojan was detected | ET TROJAN Amadey CnC Check-In |
2996 | kntd.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
2996 | kntd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2996 | kntd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2996 | kntd.exe | A Network Trojan was detected | ET TROJAN Amadey CnC Check-In |
2996 | kntd.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
2996 | kntd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2996 | kntd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.Win32.Amadey |
2996 | kntd.exe | A Network Trojan was detected | ET TROJAN Amadey CnC Check-In |
2996 | kntd.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |