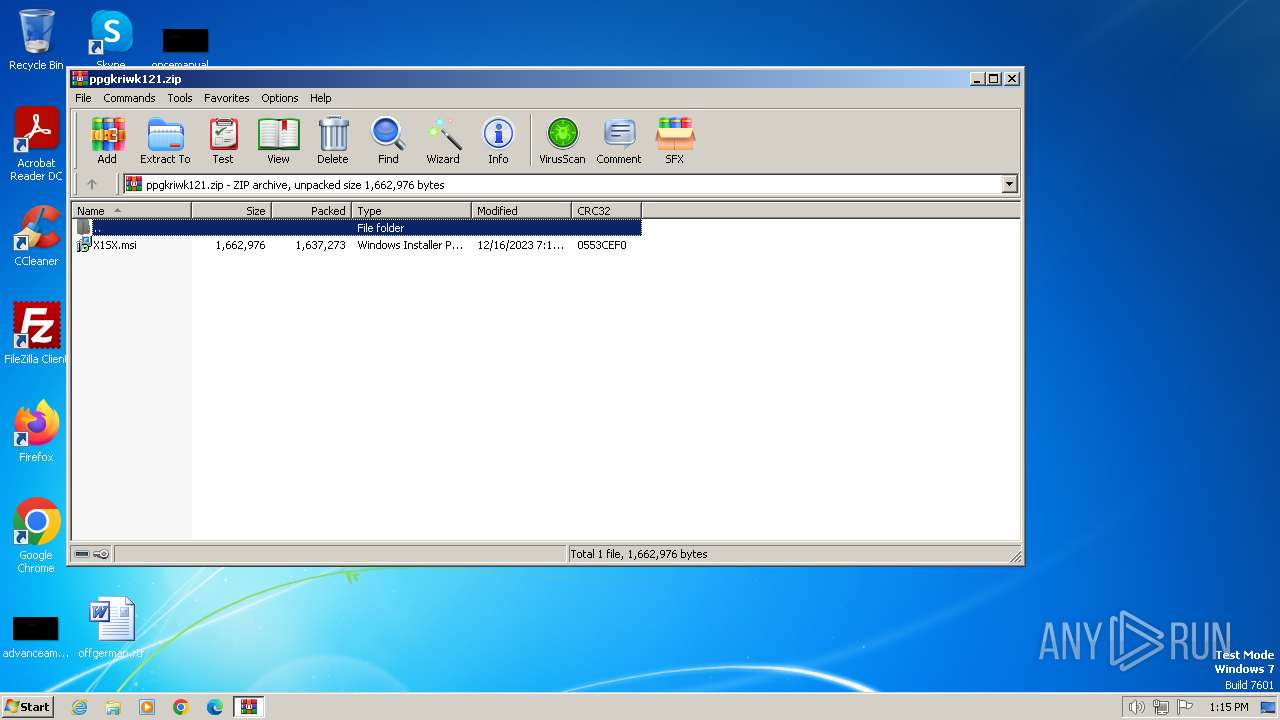
| File name: | ppgkriwk121.zip |
| Full analysis: | https://app.any.run/tasks/4eac6430-cc2b-45e1-a3fe-147b483f7611 |
| Verdict: | Malicious activity |
| Threats: | Gh0st RAT is a malware with advanced trojan functionality that enables attackers to establish full control over the victim’s system. The spying capabilities of Gh0st RAT made it a go-to tool for numerous criminal groups in high-profile attacks against government and corporate organizations. The most common vector of attack involving this malware begins with spam and phishing emails. |
| Analysis date: | December 22, 2023, 13:15:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 58A328905DEECBCF828DA5AFDE100E45 |
| SHA1: | A9373C306213E4ECBEDE14092CF519FFD5C7885A |
| SHA256: | 964872EFDC4CA14D1DEA60FBDD2A706FC55BFA469D38D22FC439D4446AD68EC5 |
| SSDEEP: | 49152:LGLjbtr4Y/gRpIIm+cW2JF5/C/tth35+AZwMFB9jgpd0IxXHc1h1C6/5t45M8kaU:L04QgvTcW2JWxJ/w+HG6I3cf46/PGQ2g |
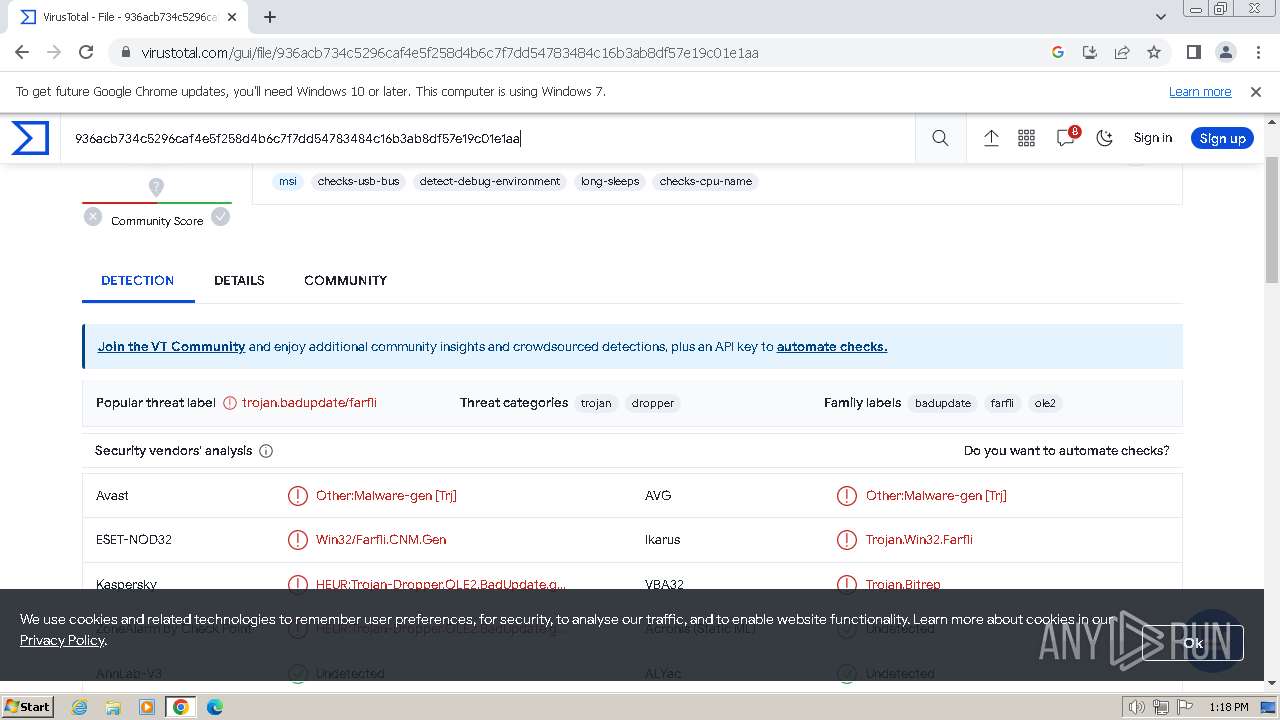
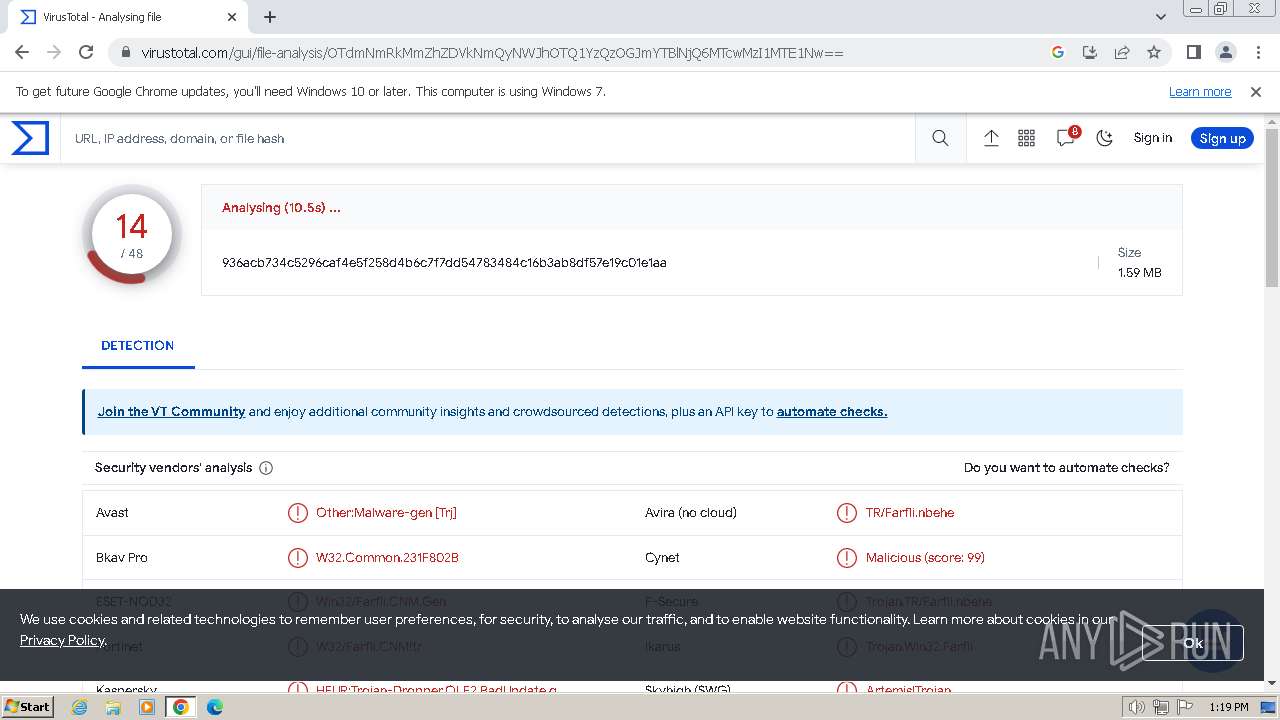
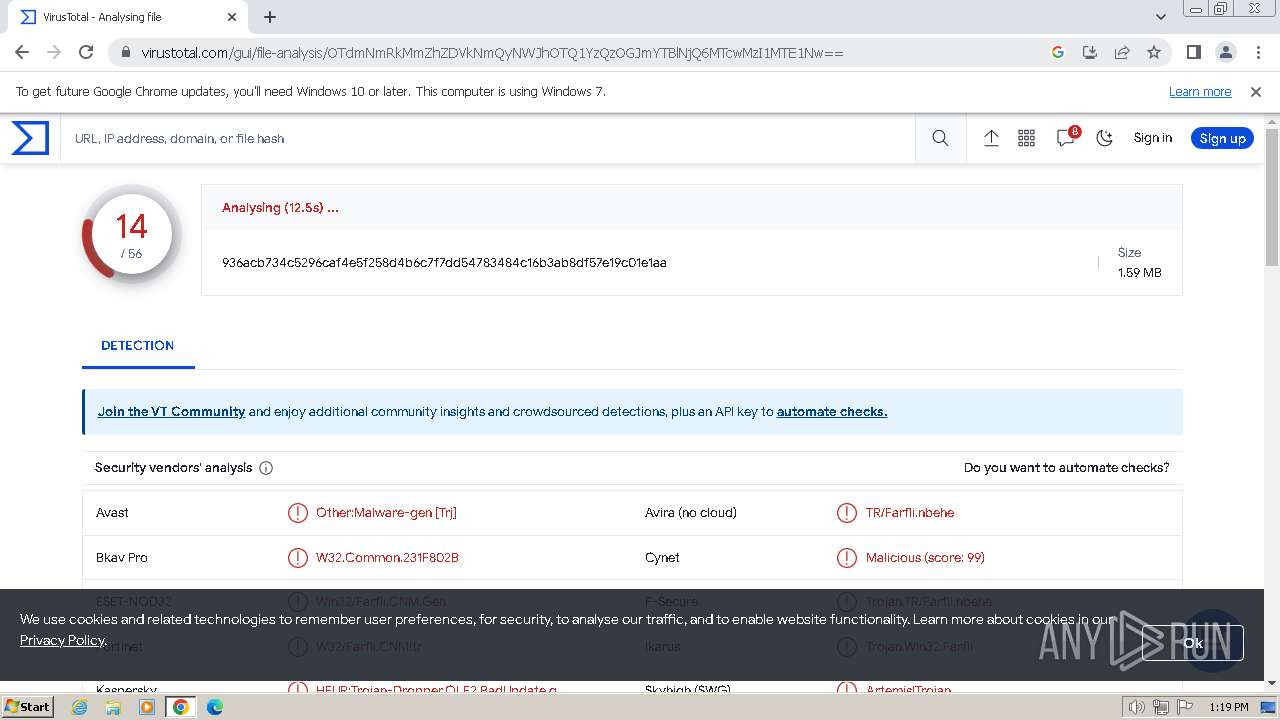
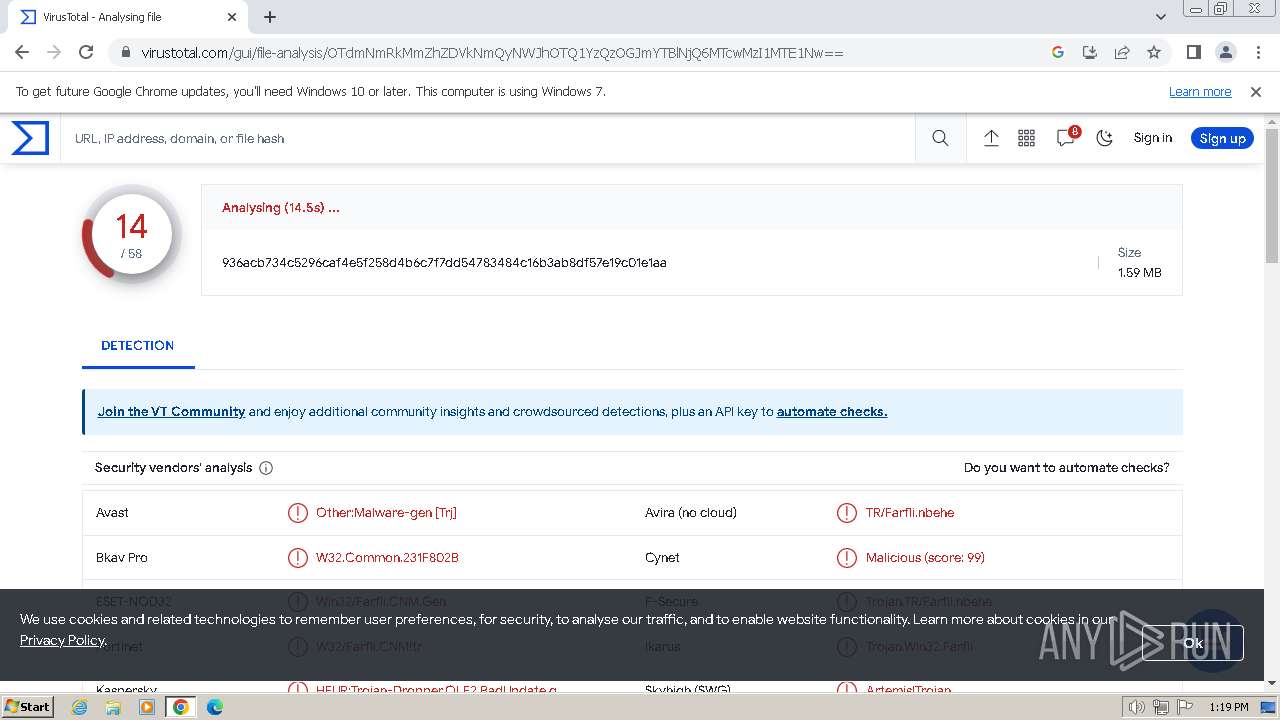
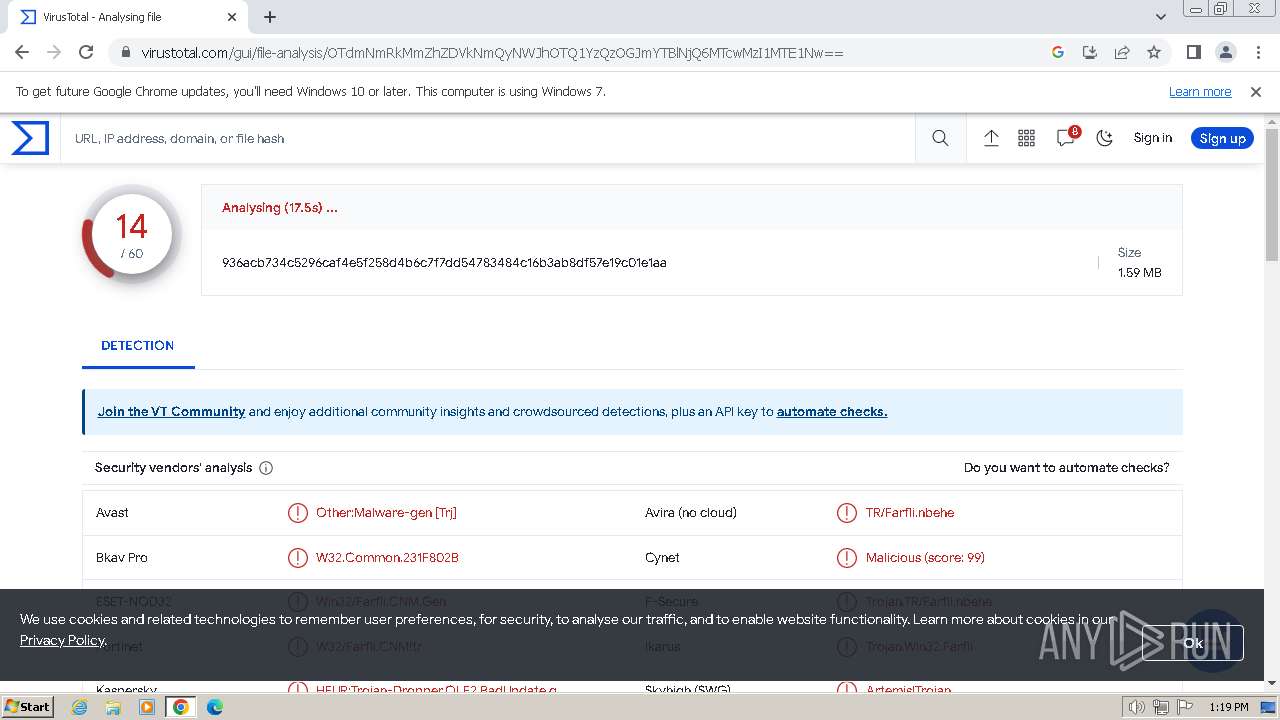
MALICIOUS
GH0ST has been detected (SURICATA)
- iusb3mon.exe (PID: 1768)
Connects to the CnC server
- iusb3mon.exe (PID: 1768)
SUSPICIOUS
Reads the Windows owner or organization settings
- microsoft.exe (PID: 2404)
- iusb3mon.exe (PID: 1768)
- iusb3mon.exe (PID: 2440)
Starts CMD.EXE for commands execution
- iusb3mon.exe (PID: 1768)
Connects to unusual port
- iusb3mon.exe (PID: 1768)
Reads the Internet Settings
- iusb3mon.exe (PID: 2440)
INFO
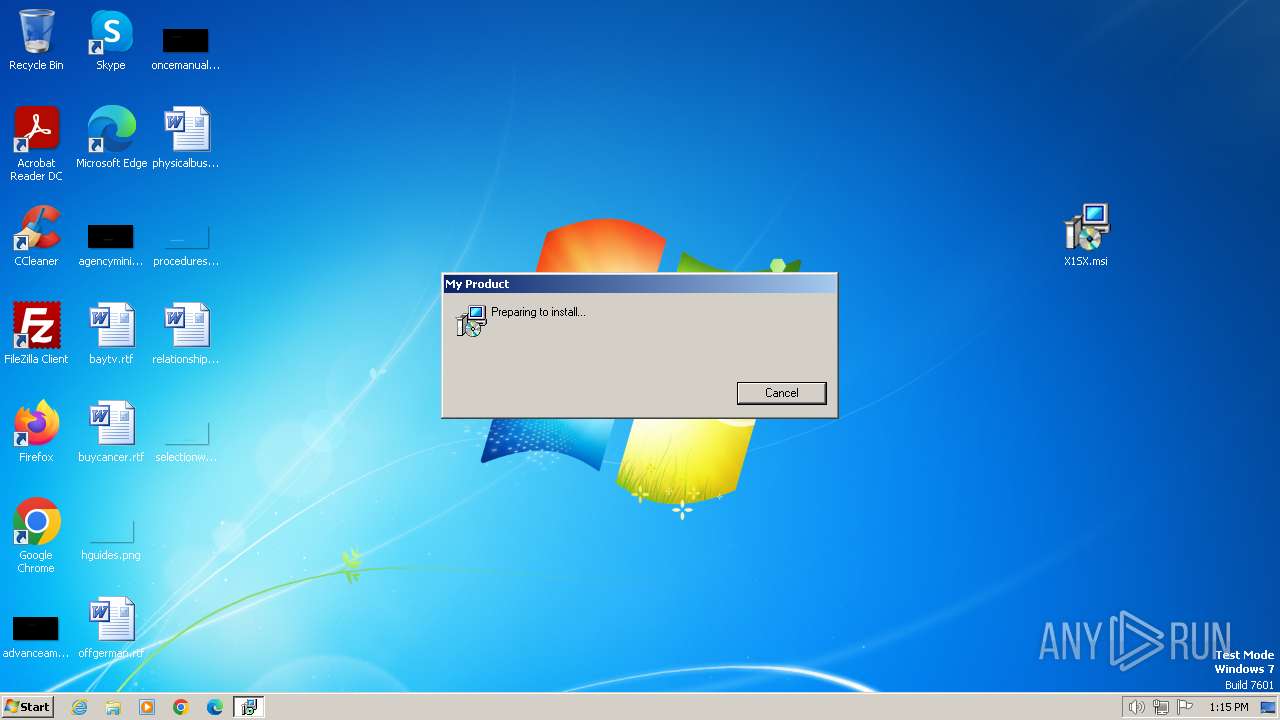
Manual execution by a user
- msiexec.exe (PID: 2420)
- chrome.exe (PID: 2476)
- wmpnscfg.exe (PID: 148)
Reads the computer name
- msiexec.exe (PID: 548)
- iusb3mon.exe (PID: 2440)
- iusb3mon.exe (PID: 1768)
- microsoft.exe (PID: 2404)
- wmpnscfg.exe (PID: 148)
Checks supported languages
- msiexec.exe (PID: 548)
- iusb3mon.exe (PID: 2440)
- microsoft.exe (PID: 2404)
- wmpnscfg.exe (PID: 148)
- iusb3mon.exe (PID: 1768)
Drops the executable file immediately after the start
- msiexec.exe (PID: 548)
- WinRAR.exe (PID: 2044)
- iusb3mon.exe (PID: 1768)
Create files in a temporary directory
- msiexec.exe (PID: 548)
- iusb3mon.exe (PID: 2440)
- iusb3mon.exe (PID: 1768)
- microsoft.exe (PID: 2404)
Executes as Windows Service
- VSSVC.exe (PID: 1652)
Reads the machine GUID from the registry
- msiexec.exe (PID: 548)
- microsoft.exe (PID: 2404)
- iusb3mon.exe (PID: 1768)
- iusb3mon.exe (PID: 2440)
Application launched itself
- iusb3mon.exe (PID: 2440)
- chrome.exe (PID: 2476)
Creates files in the program directory
- iusb3mon.exe (PID: 1768)
Reads CPU info
- iusb3mon.exe (PID: 1768)
Creates files or folders in the user directory
- iusb3mon.exe (PID: 1768)
Starts itself from another location
- iusb3mon.exe (PID: 1768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:16 15:15:40 |
| ZipCRC: | 0x0553cef0 |
| ZipCompressedSize: | 1637273 |
| ZipUncompressedSize: | 1662976 |
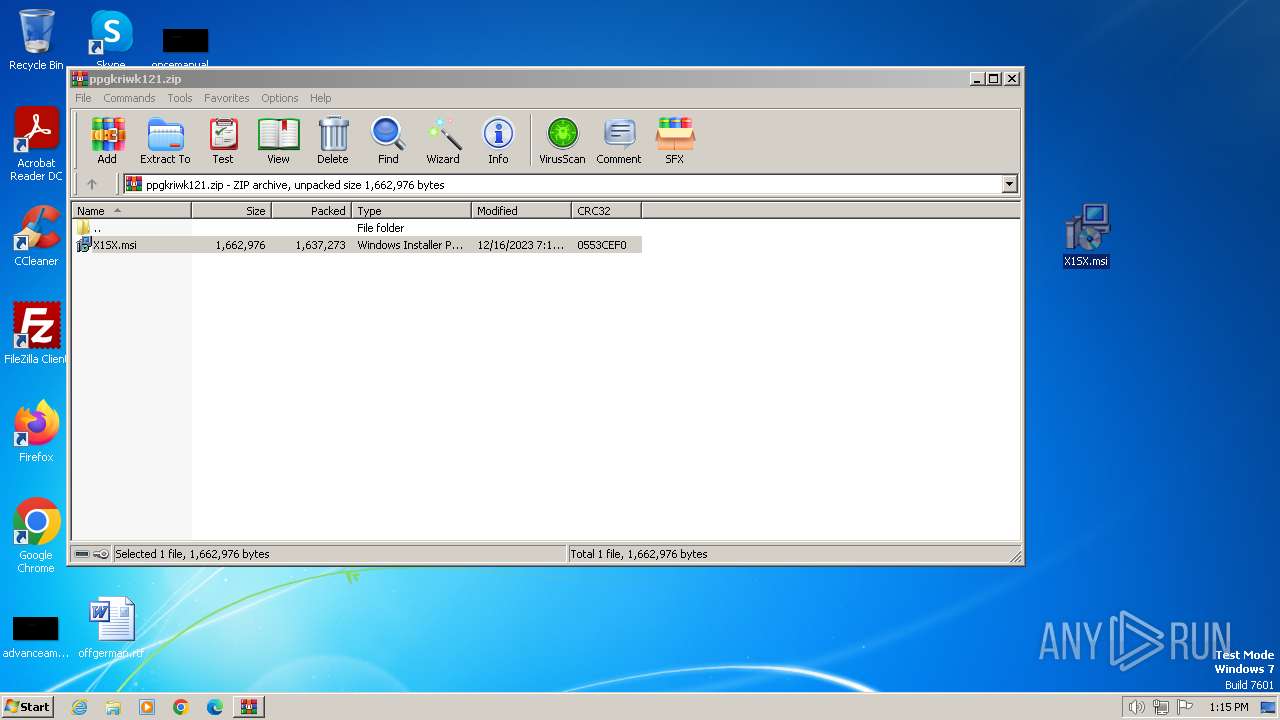
| ZipFileName: | X1SX.msi |
Total processes
84
Monitored processes
41
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --mojo-platform-channel-handle=4136 --field-trial-handle=1012,i,14625054015101785394,15888876946376100027,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=3972 --field-trial-handle=1012,i,14625054015101785394,15888876946376100027,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1556 | cmd /c echo.>c:\odbc.inst.ini | C:\Windows\System32\cmd.exe | — | iusb3mon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1652 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | "C:\ProgramData\iusb3mon.exe" | C:\ProgramData\iusb3mon.exe | iusb3mon.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: TrueUpdate Client Exit code: 0 Version: 3.8.0.0 Modules
| |||||||||||||||
| 1892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4004 --field-trial-handle=1012,i,14625054015101785394,15888876946376100027,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=3388 --field-trial-handle=1012,i,14625054015101785394,15888876946376100027,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=3108 --field-trial-handle=1012,i,14625054015101785394,15888876946376100027,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
9 381
Read events
9 151
Write events
217
Delete events
13
Modification events
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
11
Suspicious files
224
Text files
53
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 548 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 548 | msiexec.exe | C:\ProgramData\Microsoft\EdgeUpdate\Log\chuangkou.log | — | |
MD5:— | SHA256:— | |||
| 548 | msiexec.exe | C:\ProgramData\Microsoft\EdgeUpdate\Log\log.log | — | |
MD5:— | SHA256:— | |||
| 548 | msiexec.exe | C:\Windows\Installer\MSI6ADB.tmp | binary | |
MD5:8E57087FAD7199E37D4966BD47788053 | SHA256:F85EED1D8AB62758D2DD13DEBA9C1FDF97A1E973C930CC37EE866DC84C029CFC | |||
| 548 | msiexec.exe | C:\Windows\Installer\e6648.ipi | binary | |
MD5:C76BDF260E0E7DD45DEC12CDDE07D7FD | SHA256:6D5CA402DAAF7E258A00BB648D91E0D84E52AD21F9F33AF37D56D5693BACDE7E | |||
| 548 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:C66ED024405C978AC65D1B092F8A5828 | SHA256:4D901921B94703822DBD668BF51227B1A1D66513AEE010A716C0BD0AB0ADE3AC | |||
| 548 | msiexec.exe | C:\Windows\Installer\e6647.msi | executable | |
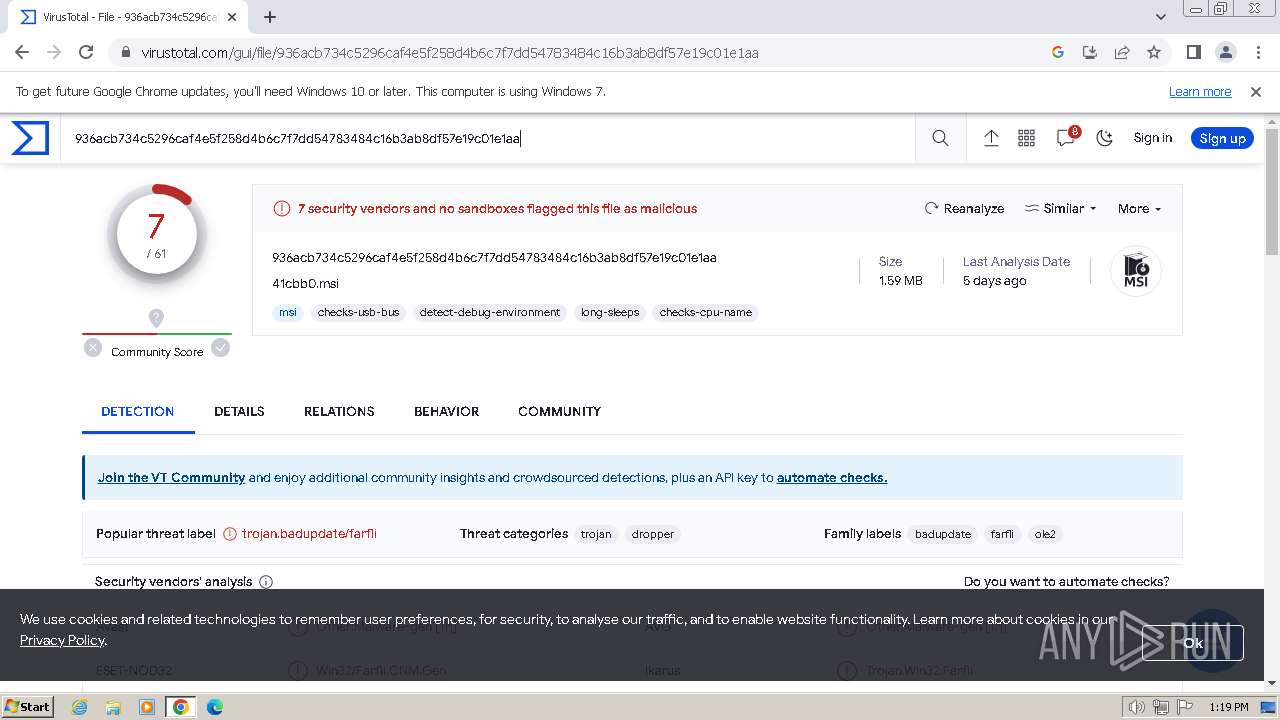
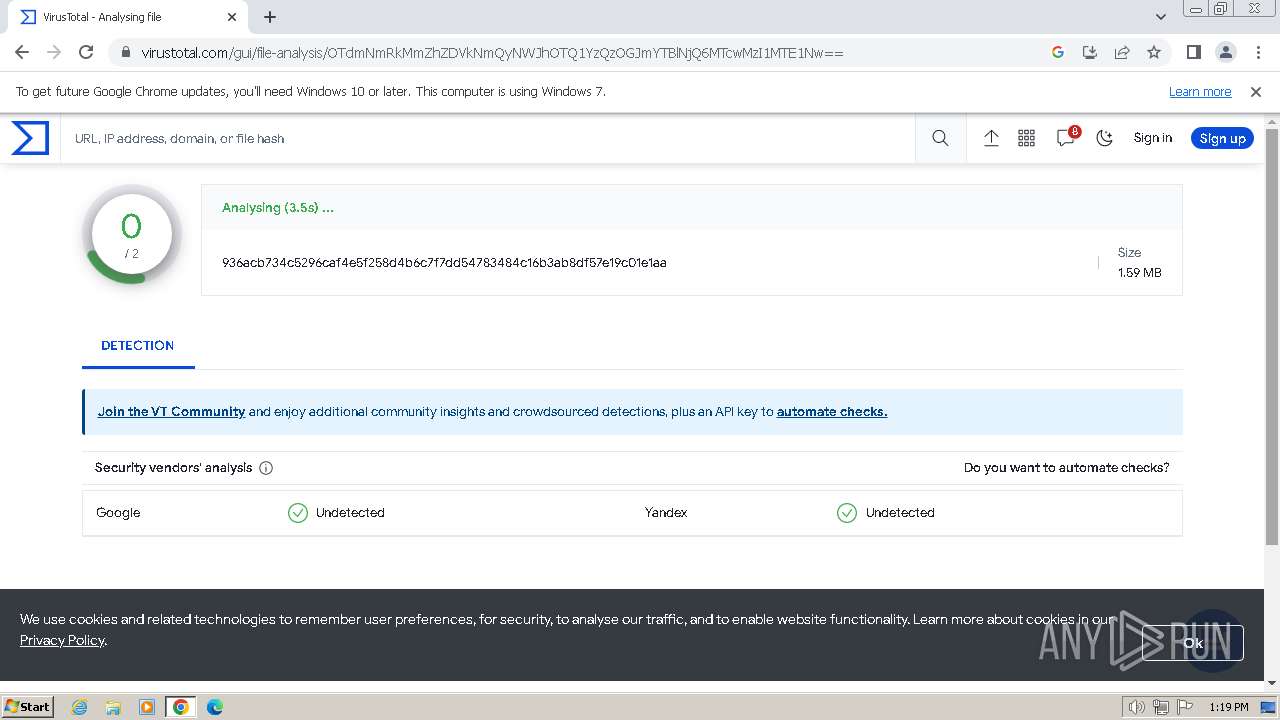
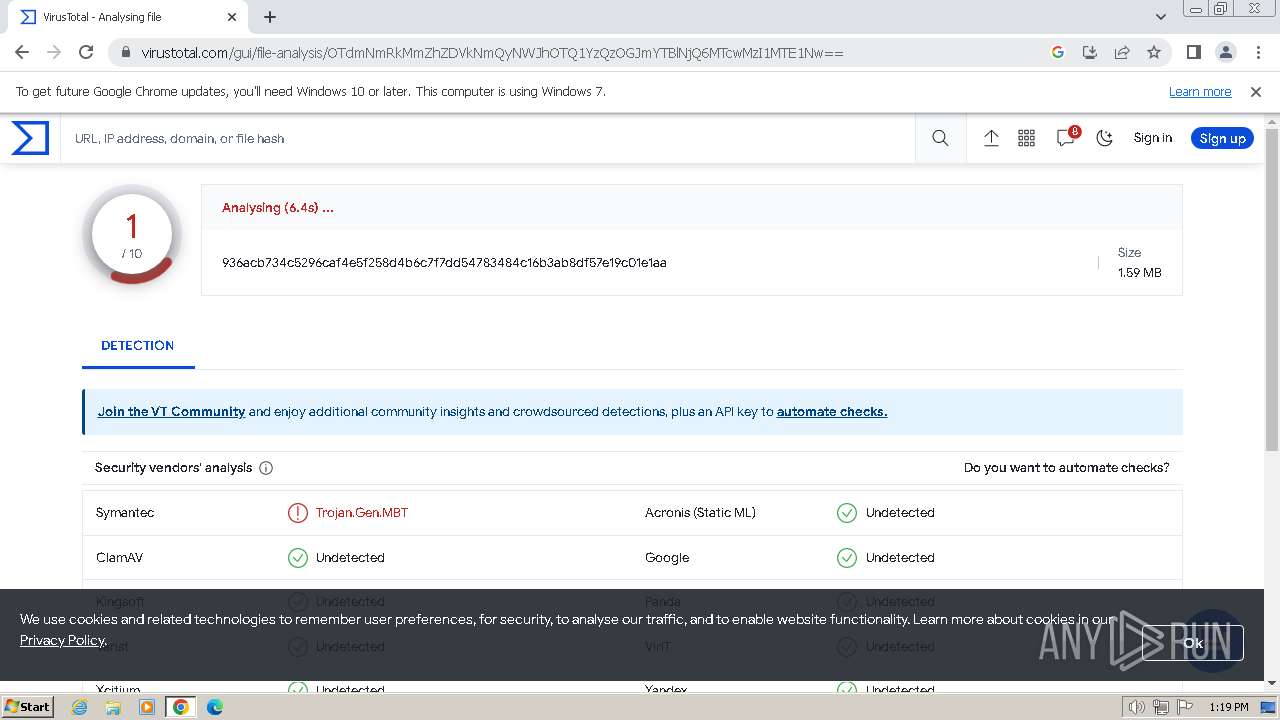
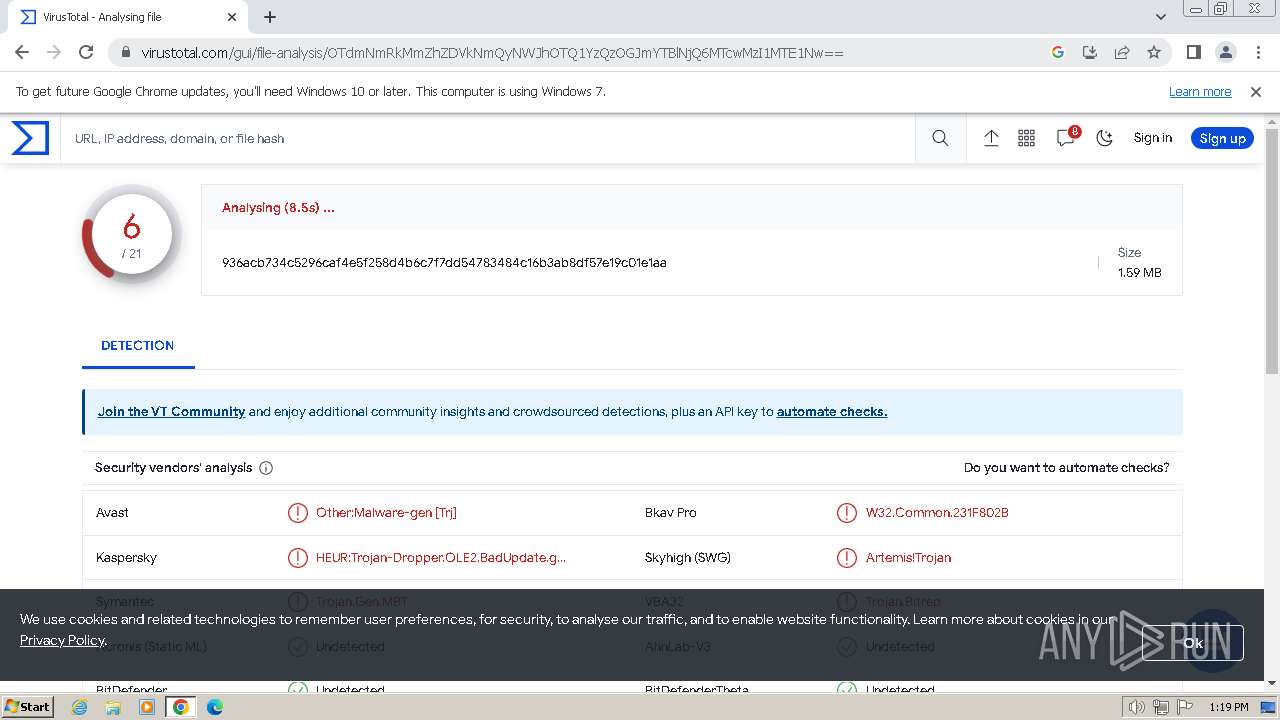
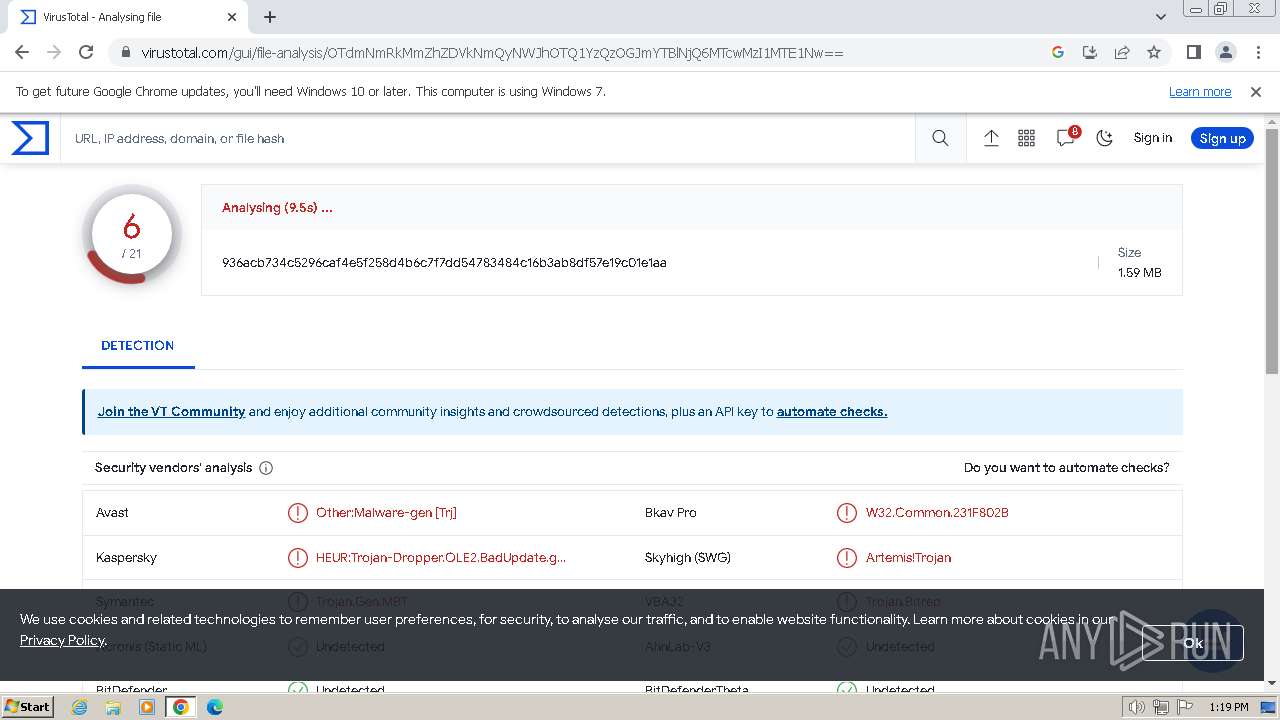
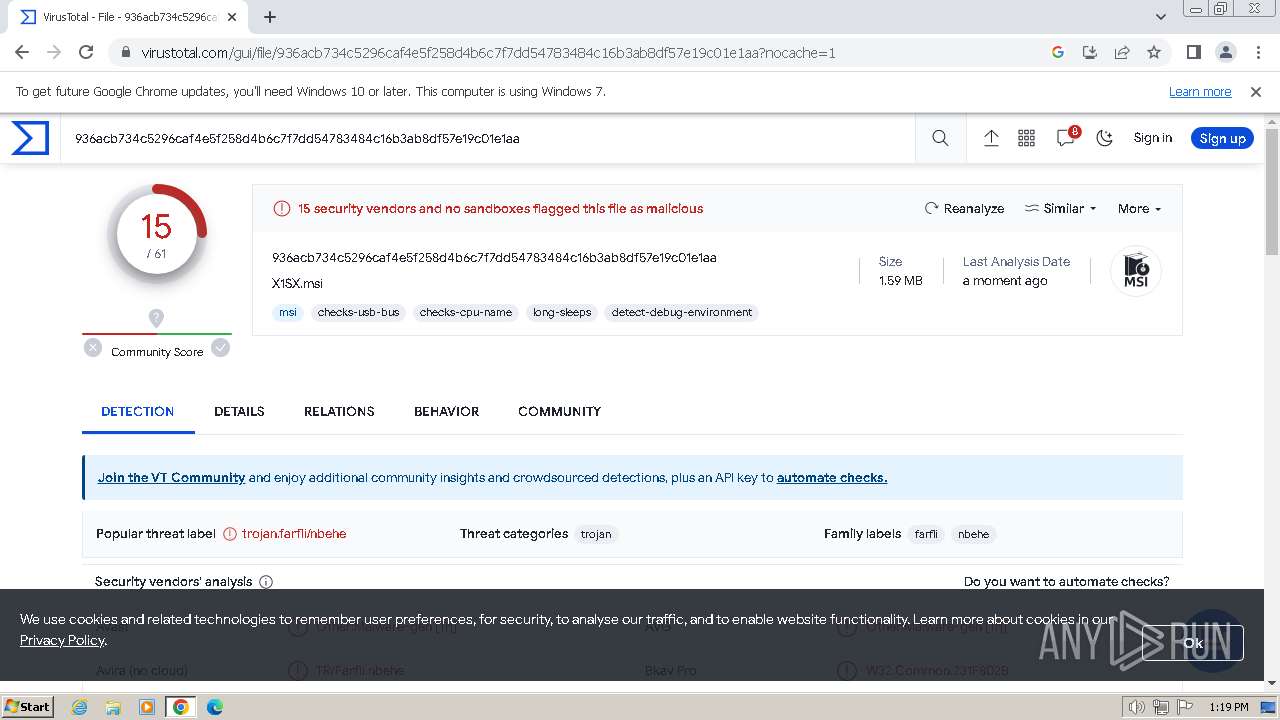
MD5:97F6DD2FAD5D6D25BA945C438BFA0E64 | SHA256:936ACB734C5296CAF4E5F258D4B6C7F7DD54783484C16B3AB8DF57E19C01E1AA | |||
| 548 | msiexec.exe | C:\ProgramData\templateWatch.dat | binary | |
MD5:82E3E0780D1278525AB0BE29CDB73FD1 | SHA256:63287523872C74F22E38DC863AA7B83F662C97DEBA737FD35E643A8677DFF540 | |||
| 548 | msiexec.exe | C:\Windows\Installer\e664a.msi | executable | |
MD5:97F6DD2FAD5D6D25BA945C438BFA0E64 | SHA256:936ACB734C5296CAF4E5F258D4B6C7F7DD54783484C16B3AB8DF57E19C01E1AA | |||
| 2044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2044.43742\X1SX.msi | executable | |
MD5:97F6DD2FAD5D6D25BA945C438BFA0E64 | SHA256:936ACB734C5296CAF4E5F258D4B6C7F7DD54783484C16B3AB8DF57E19C01E1AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
57
DNS requests
71
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | — | — | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 6.33 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 11.8 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 10.4 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 18.5 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 15.2 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 36.6 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 166 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 79.5 Kb | unknown |
856 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 689 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1768 | iusb3mon.exe | 206.238.43.197:36061 | — | — | ZA | unknown |
3028 | chrome.exe | 142.250.185.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2476 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3028 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
3028 | chrome.exe | 142.250.185.132:443 | www.google.com | GOOGLE | US | whitelisted |
3028 | chrome.exe | 142.250.185.227:443 | www.gstatic.com | GOOGLE | US | whitelisted |
3028 | chrome.exe | 216.58.206.46:443 | apis.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.virustotal.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|