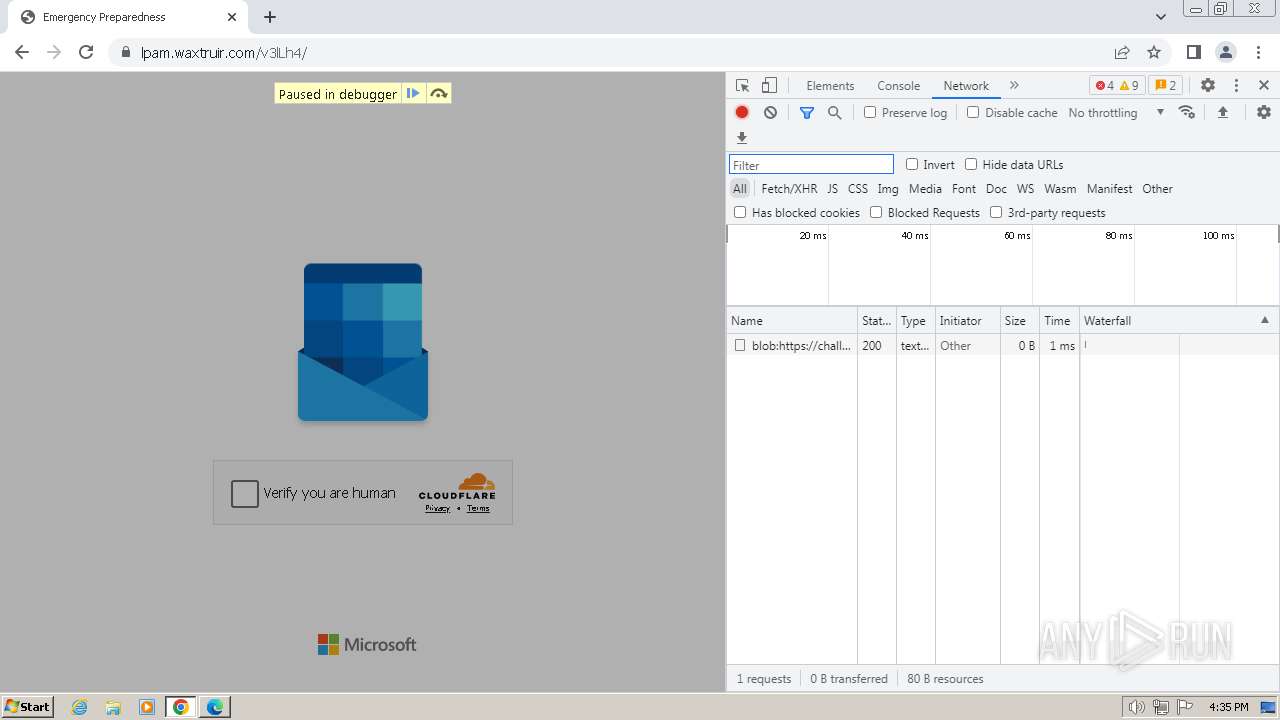
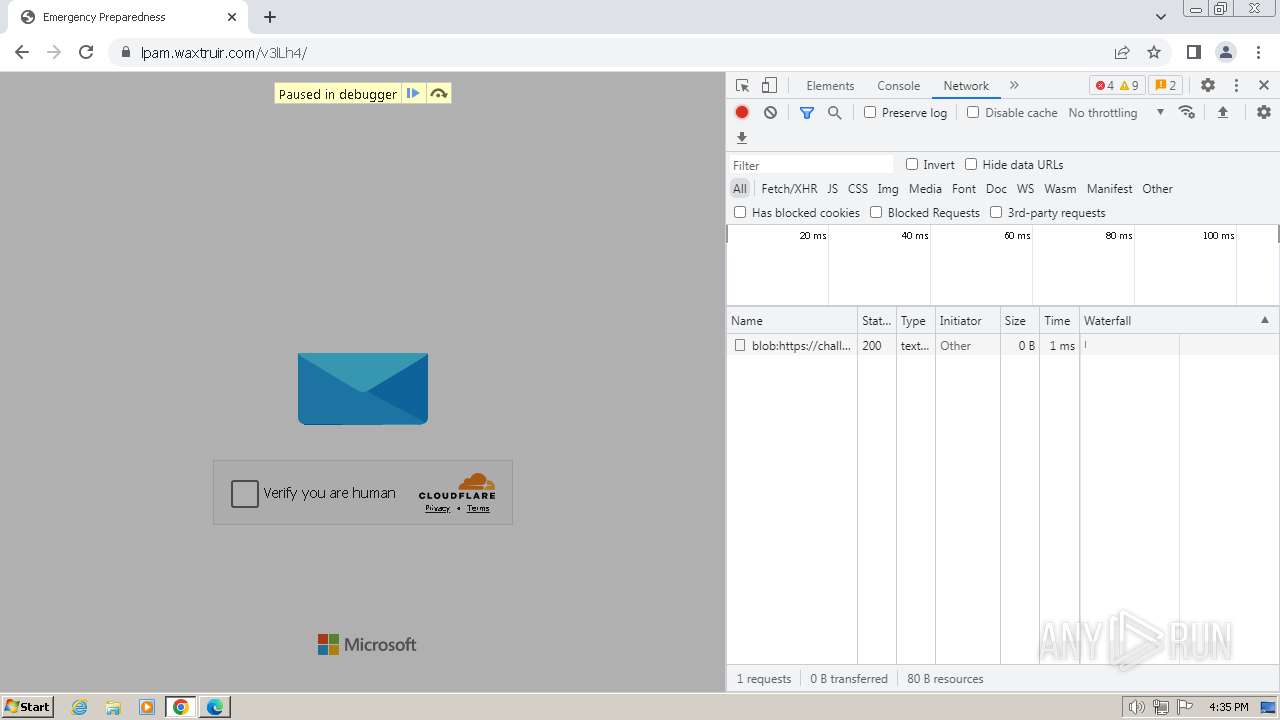
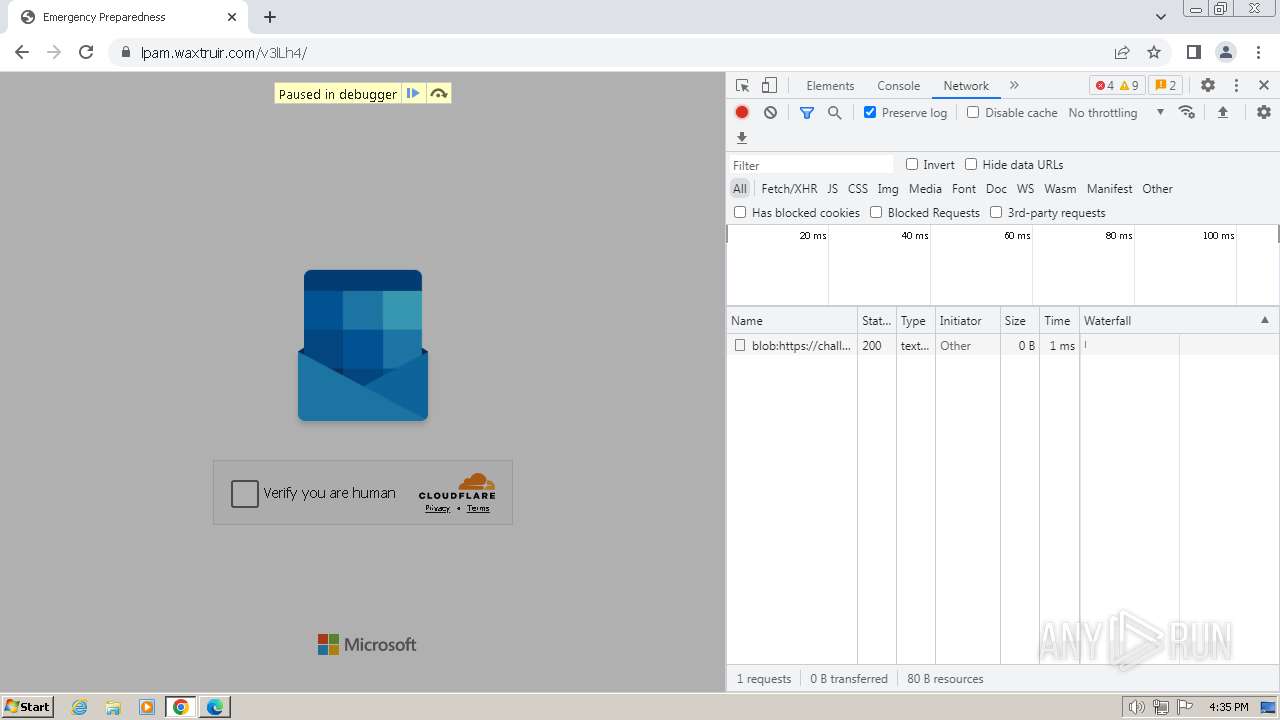
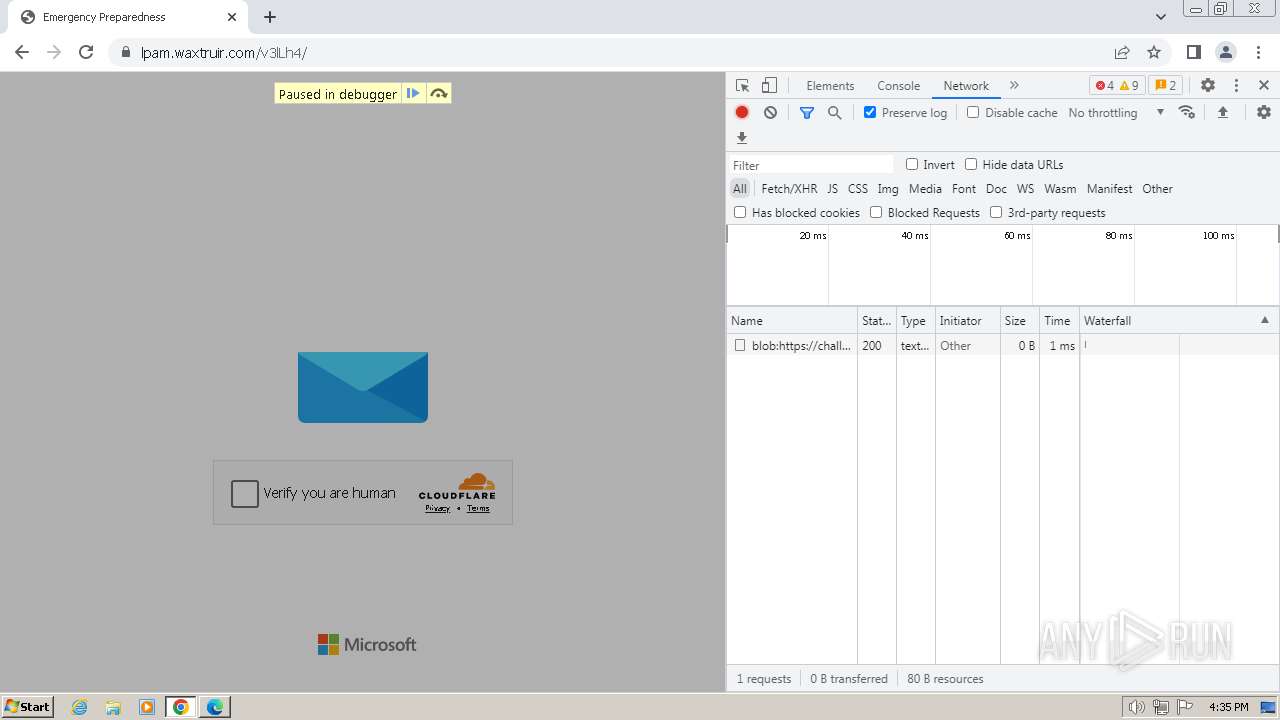
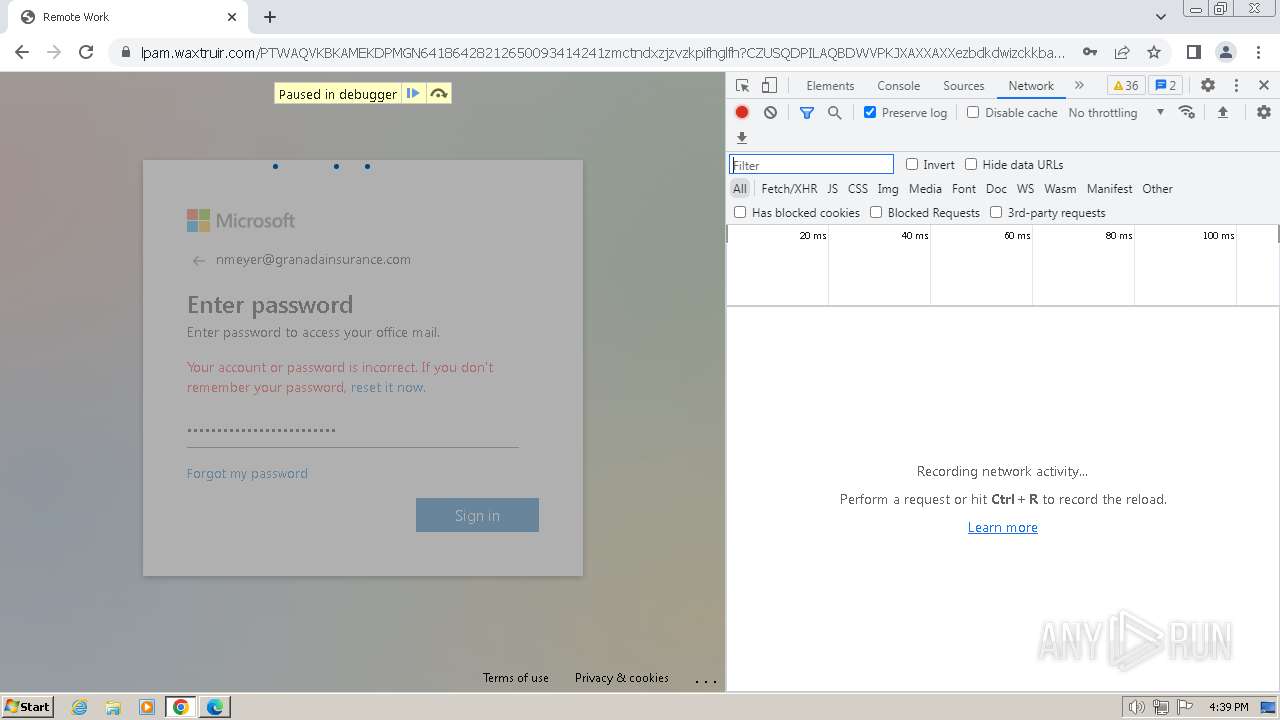
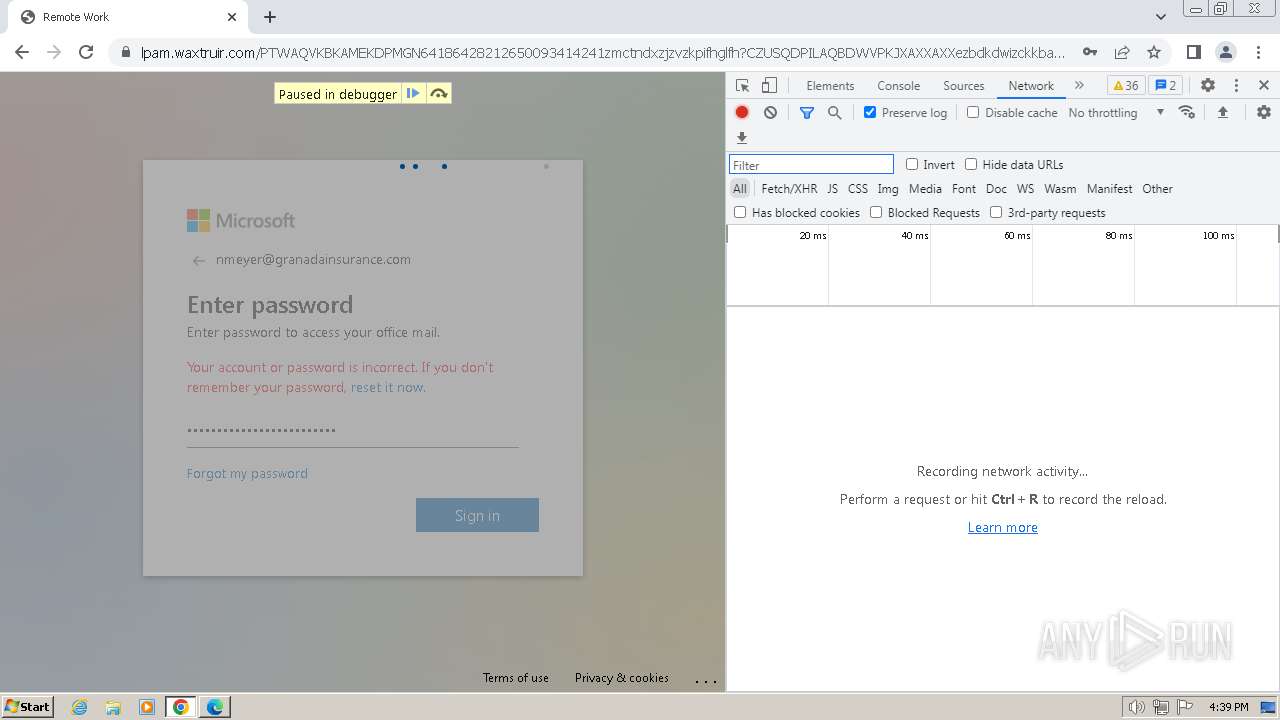
| File name: | Screenshot 2024-07-12 113128.png |
| Full analysis: | https://app.any.run/tasks/5cdf4ec0-acea-477e-a095-ce378fbc5cc5 |
| Verdict: | Malicious activity |
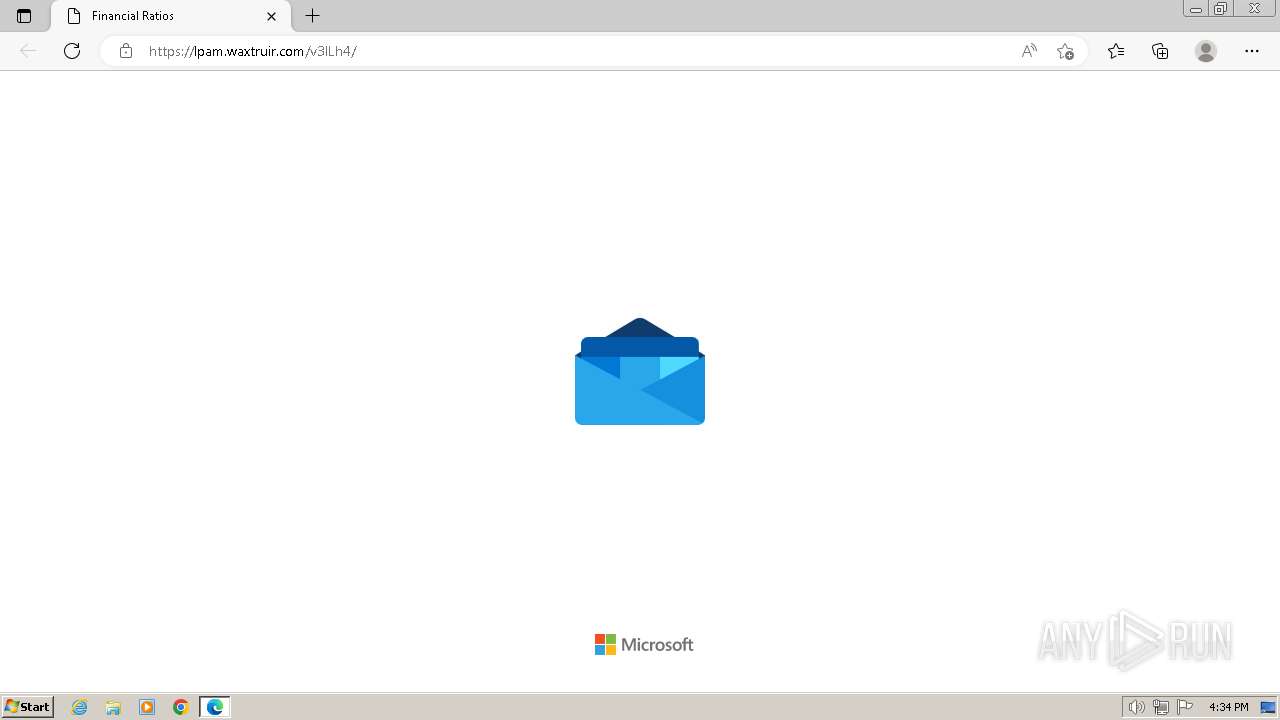
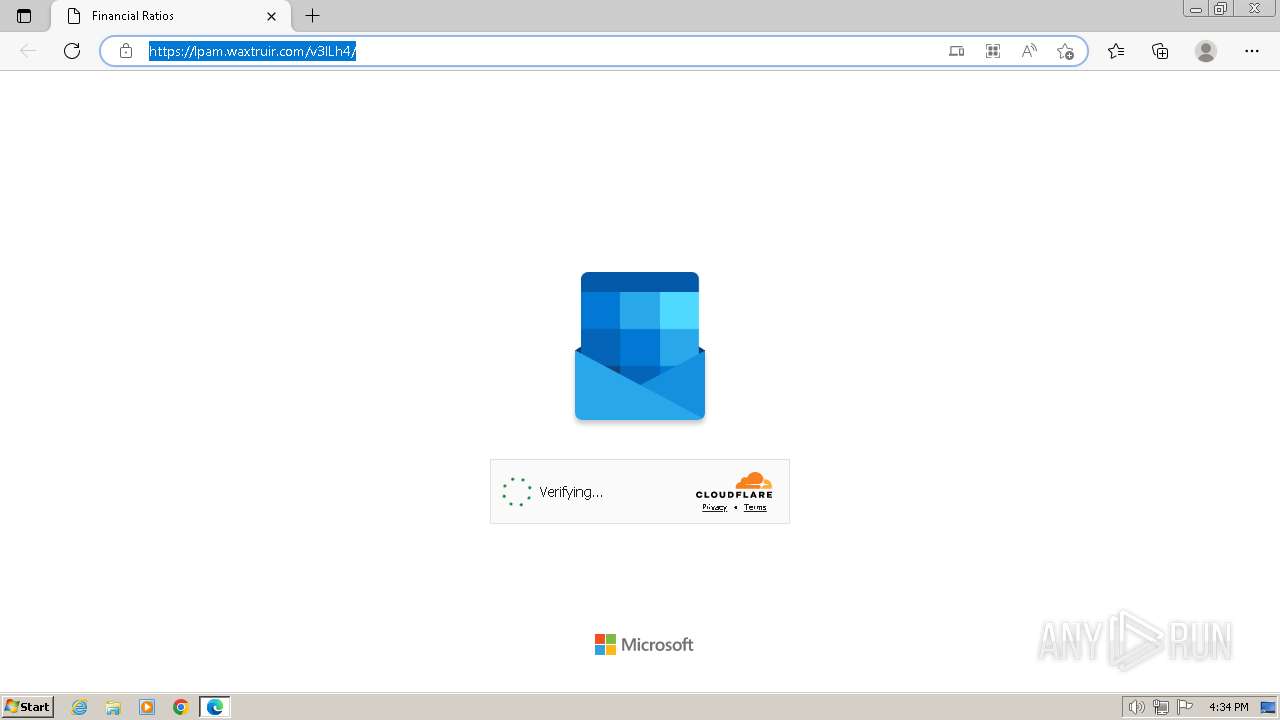
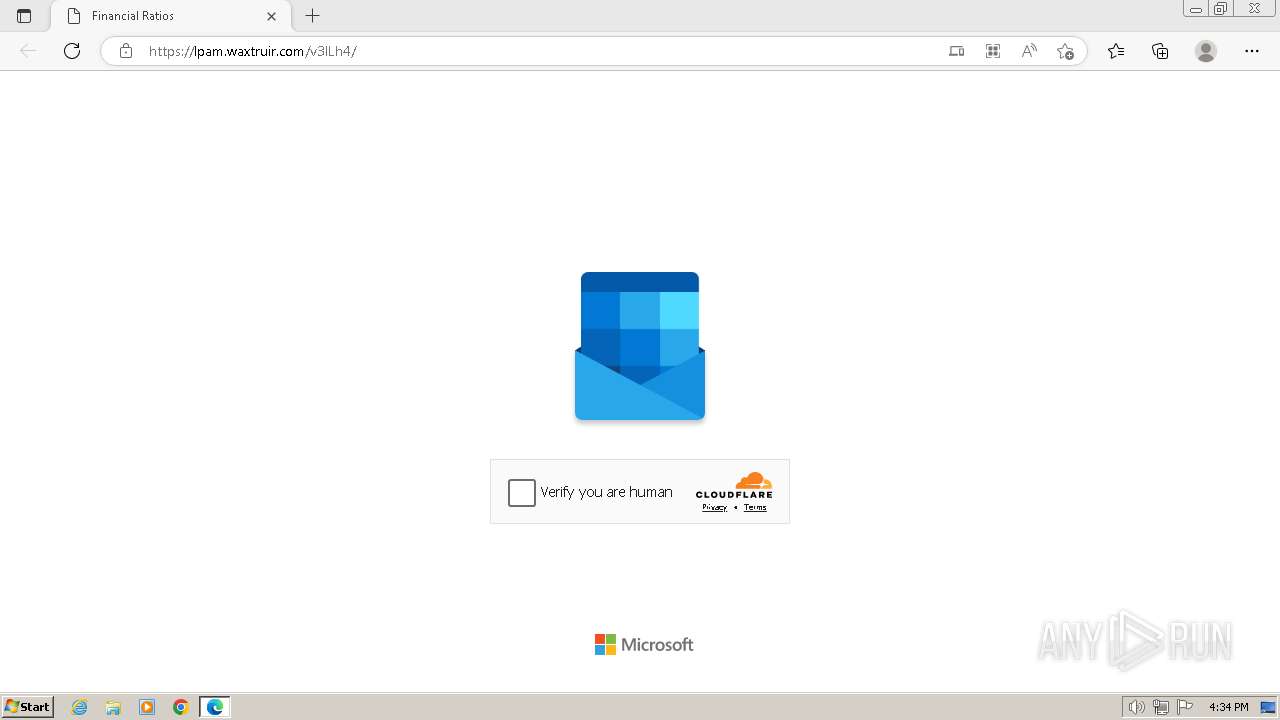
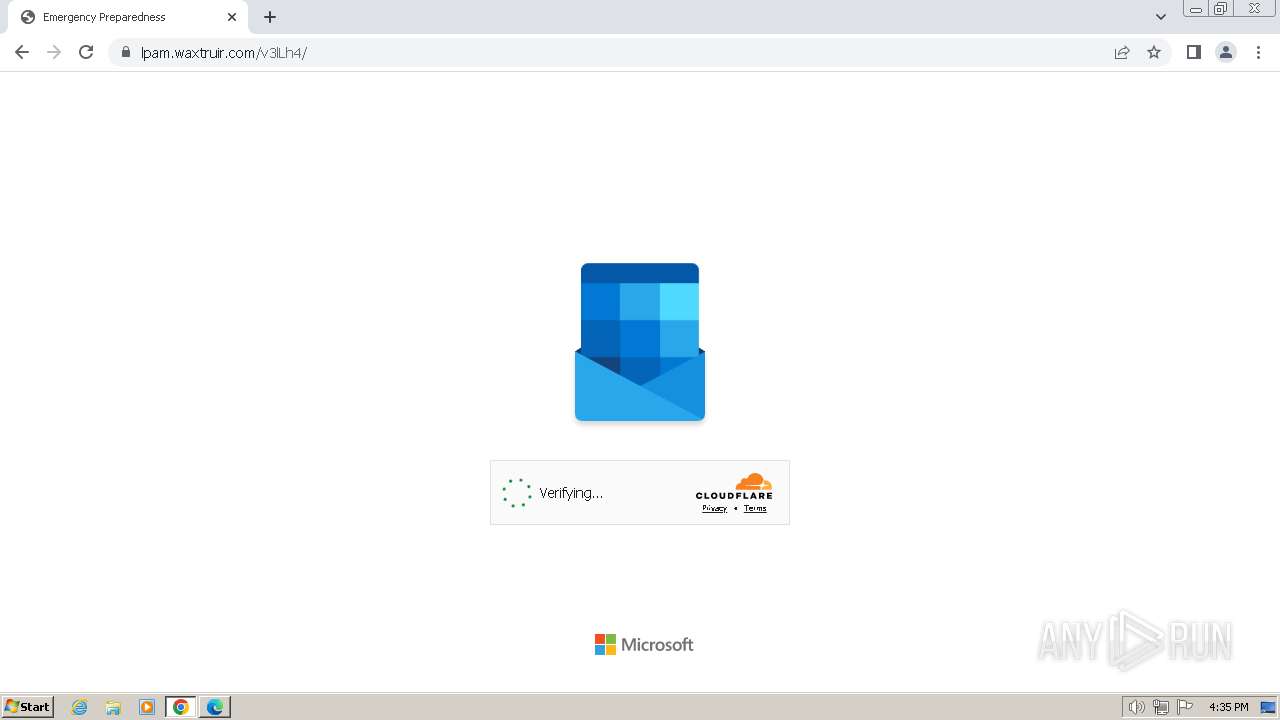
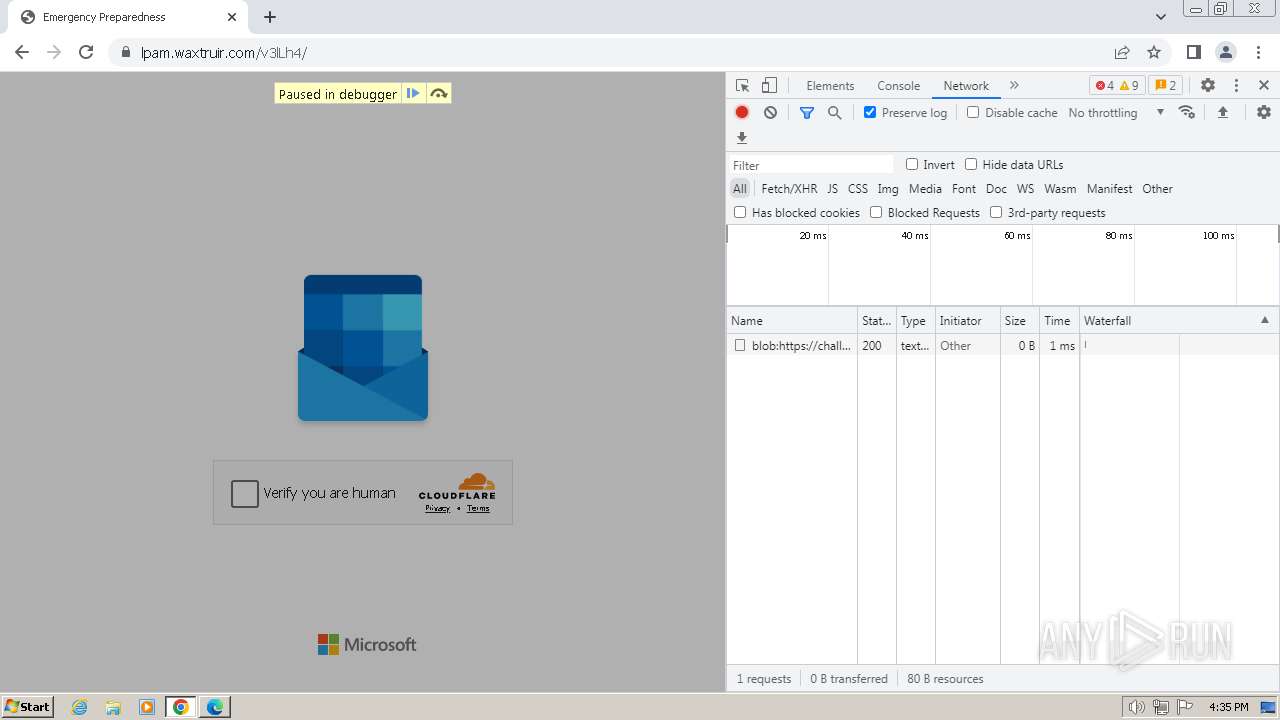
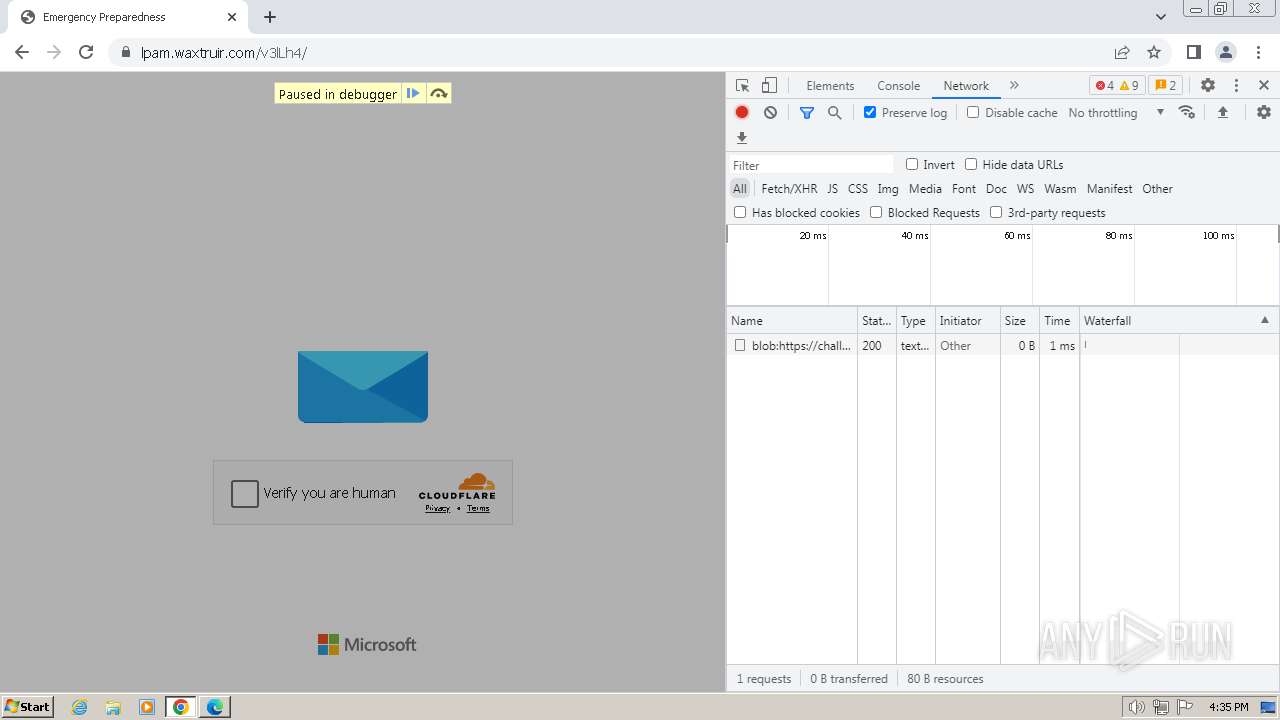
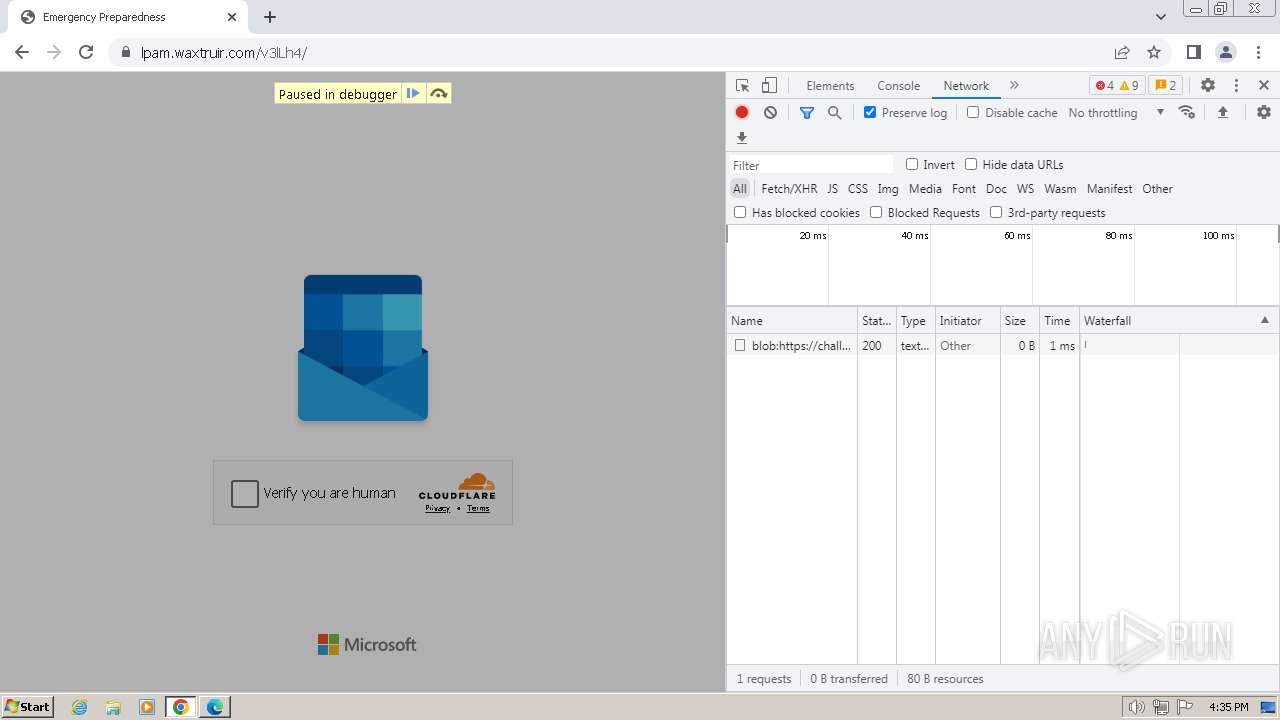
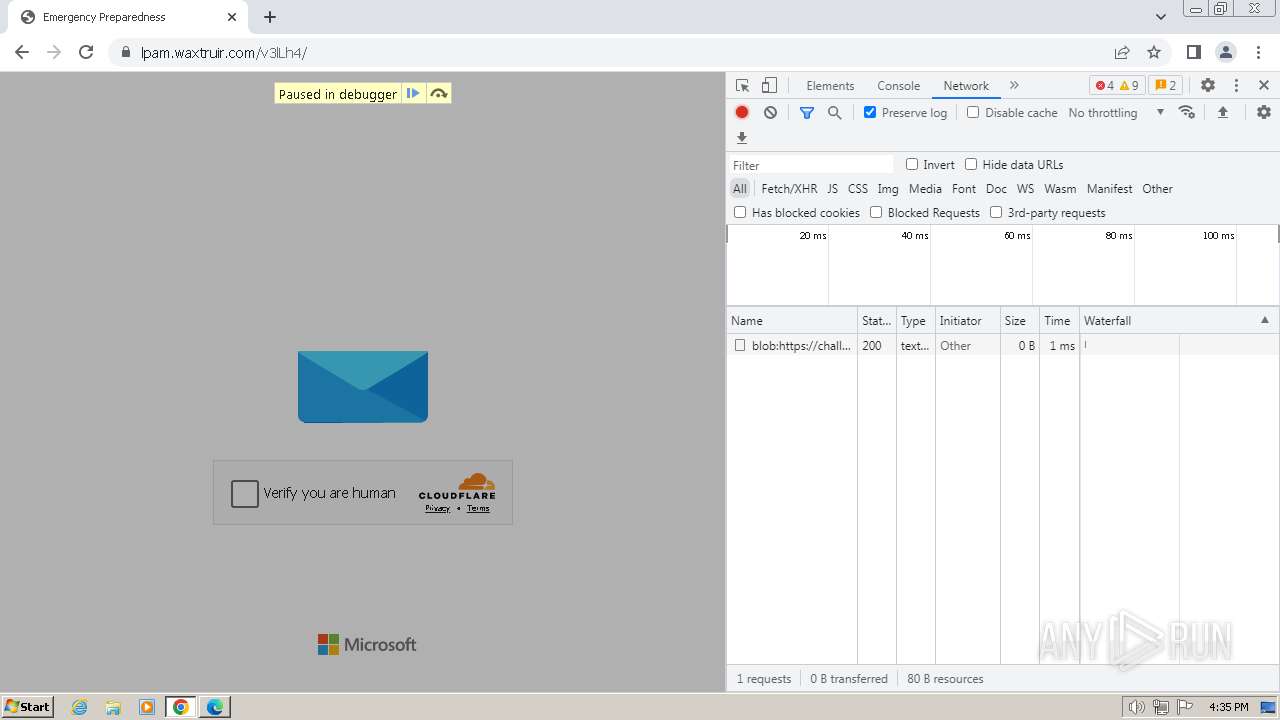
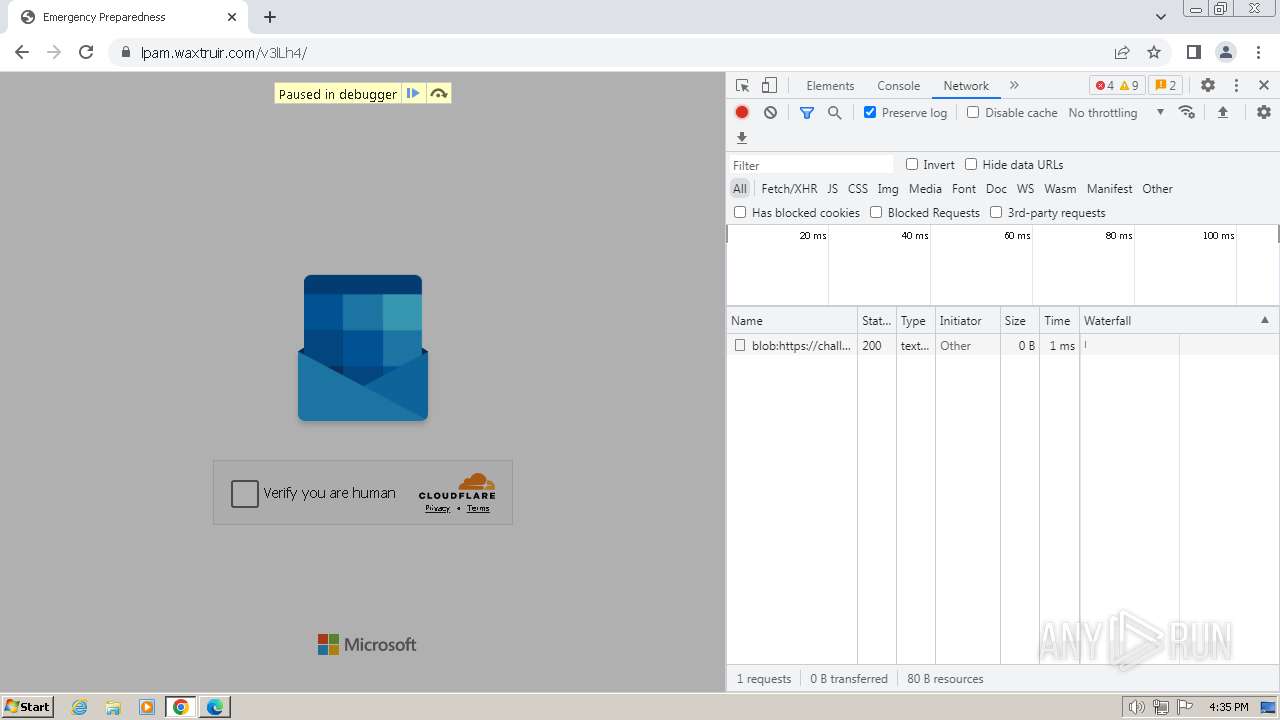
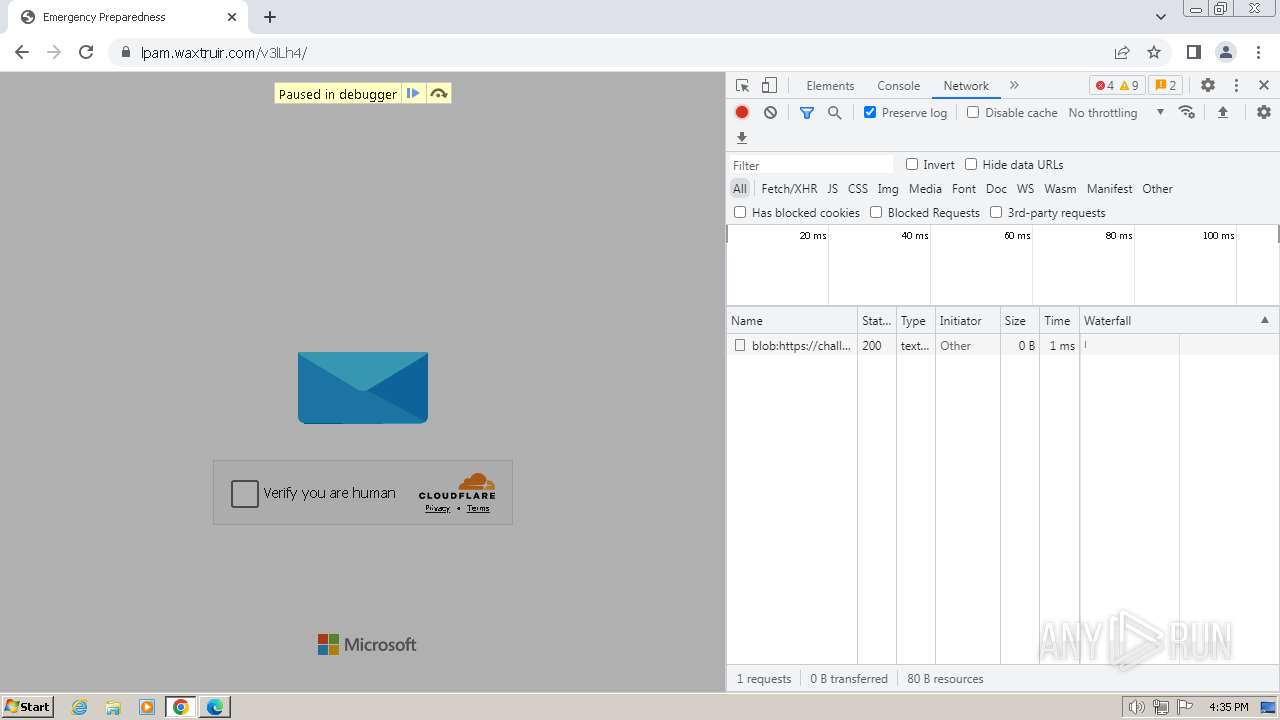
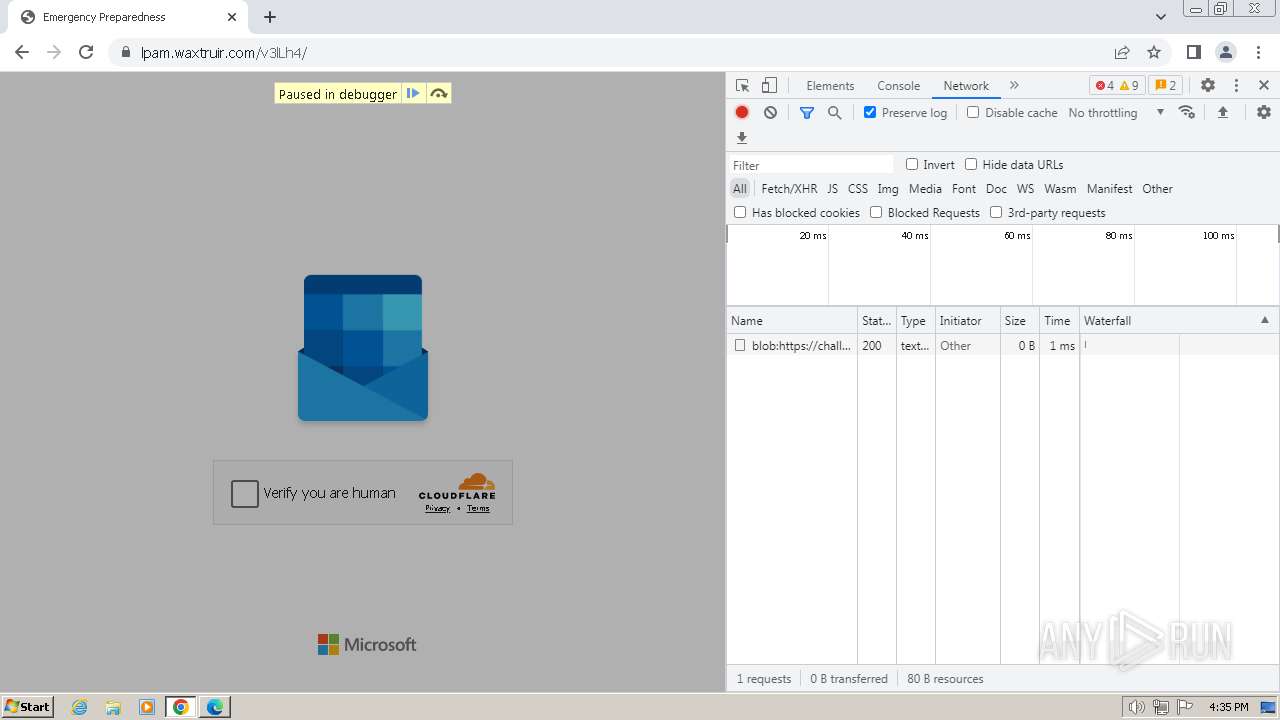
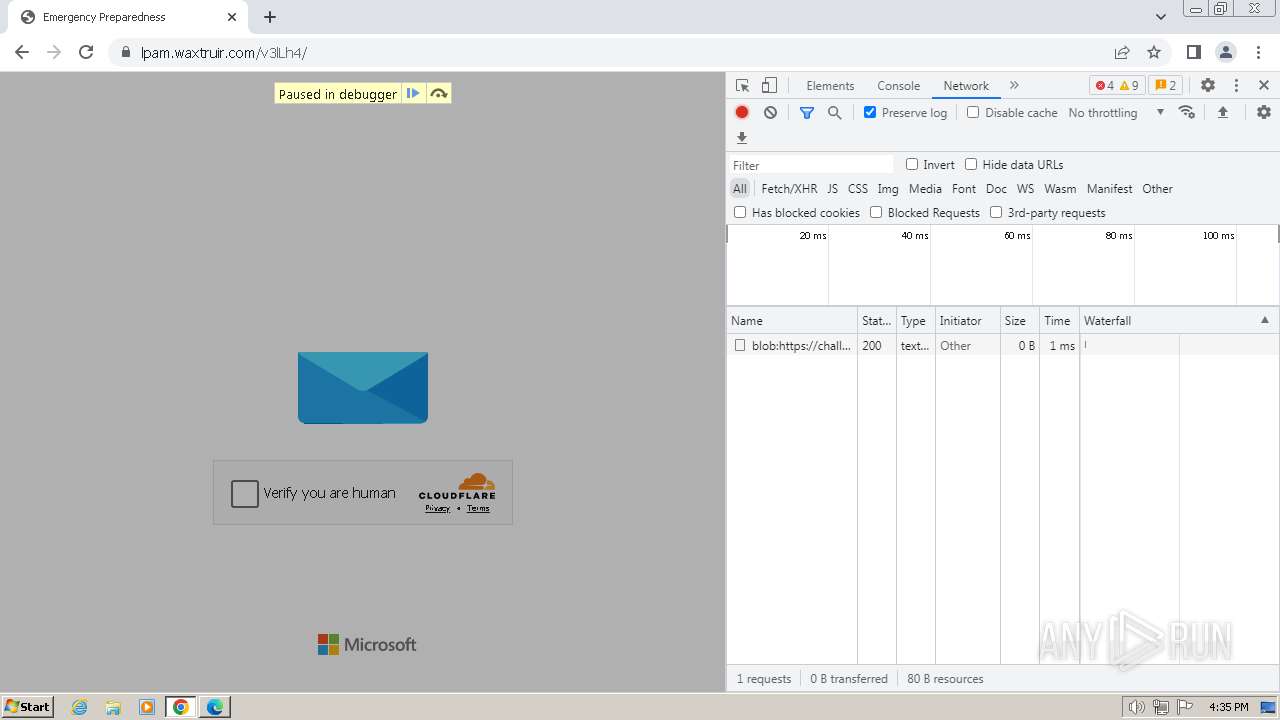
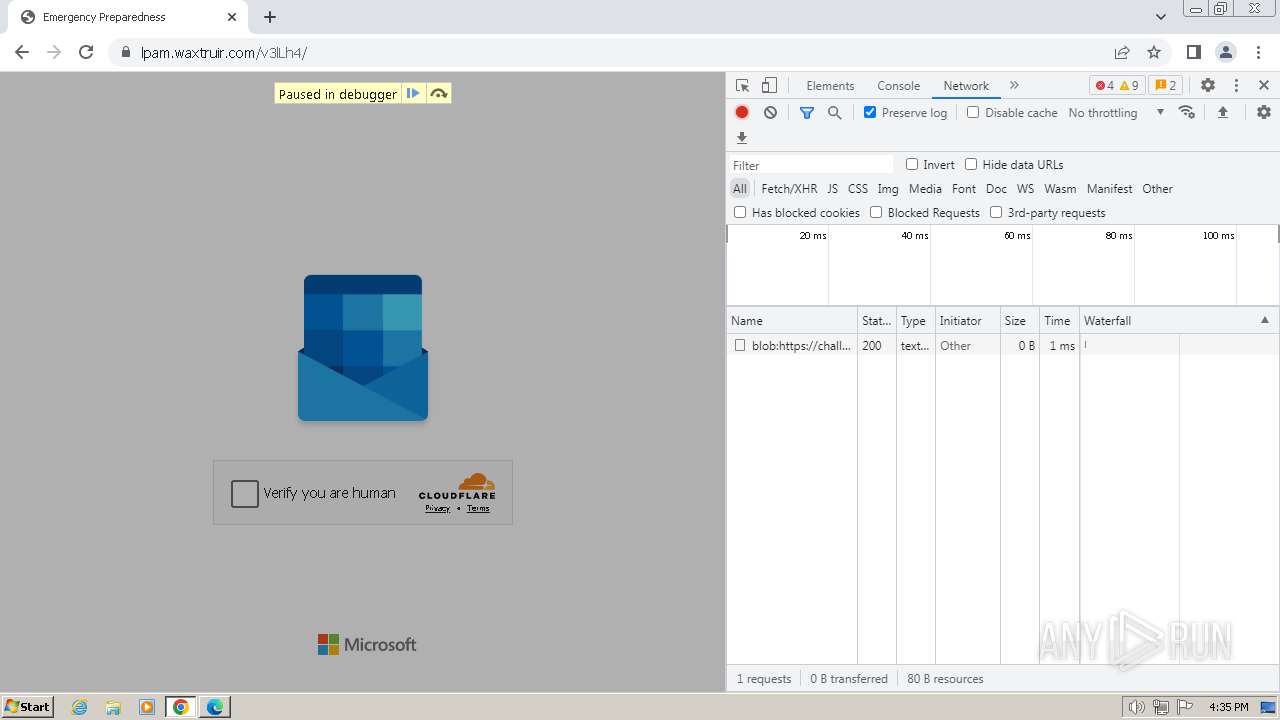
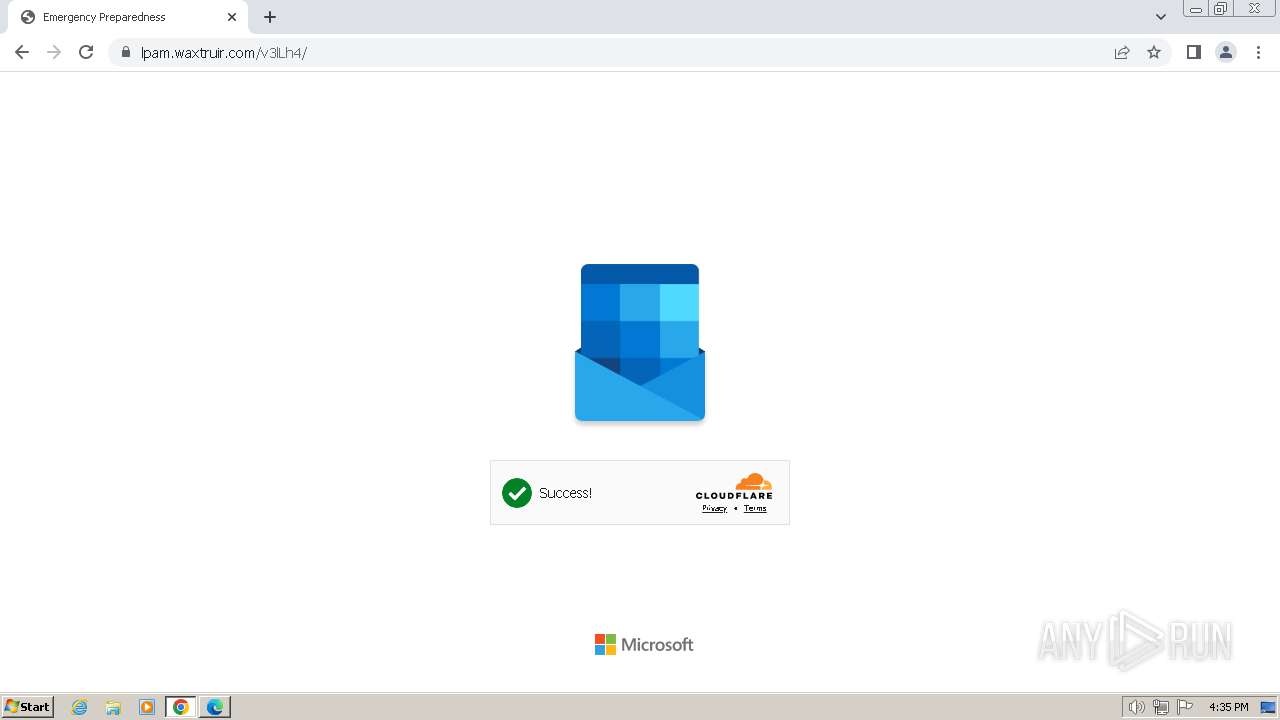
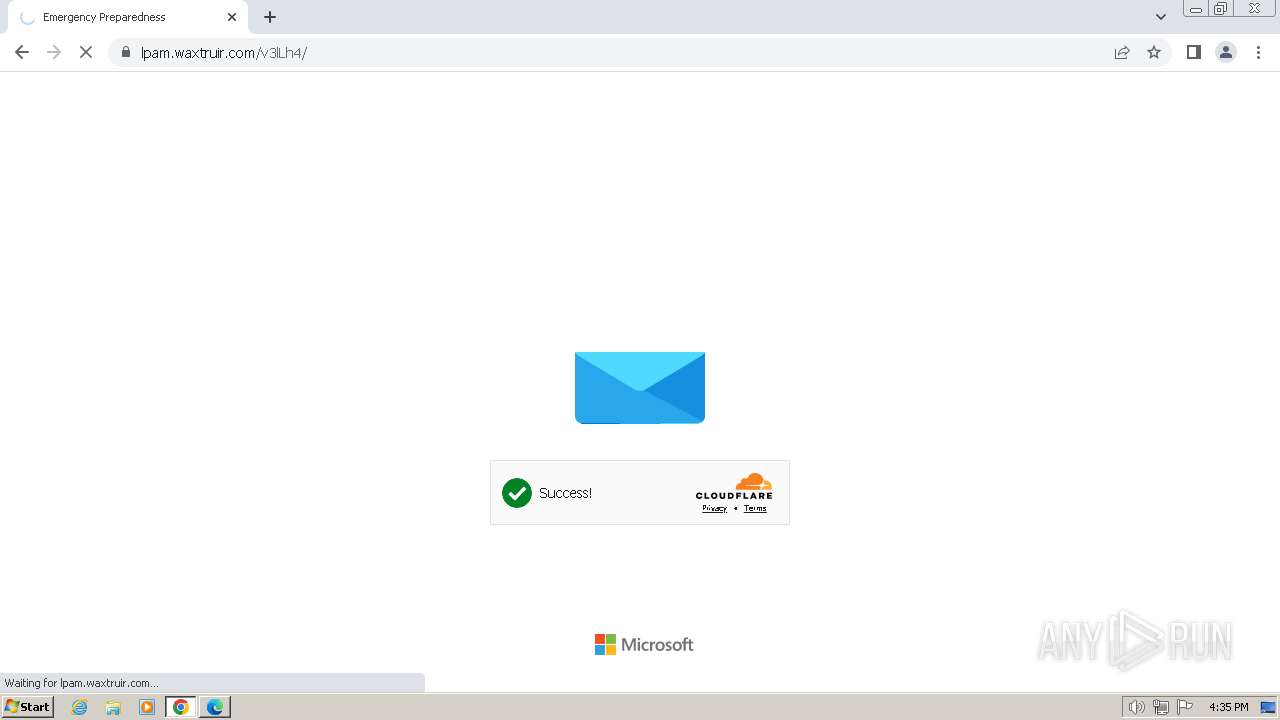
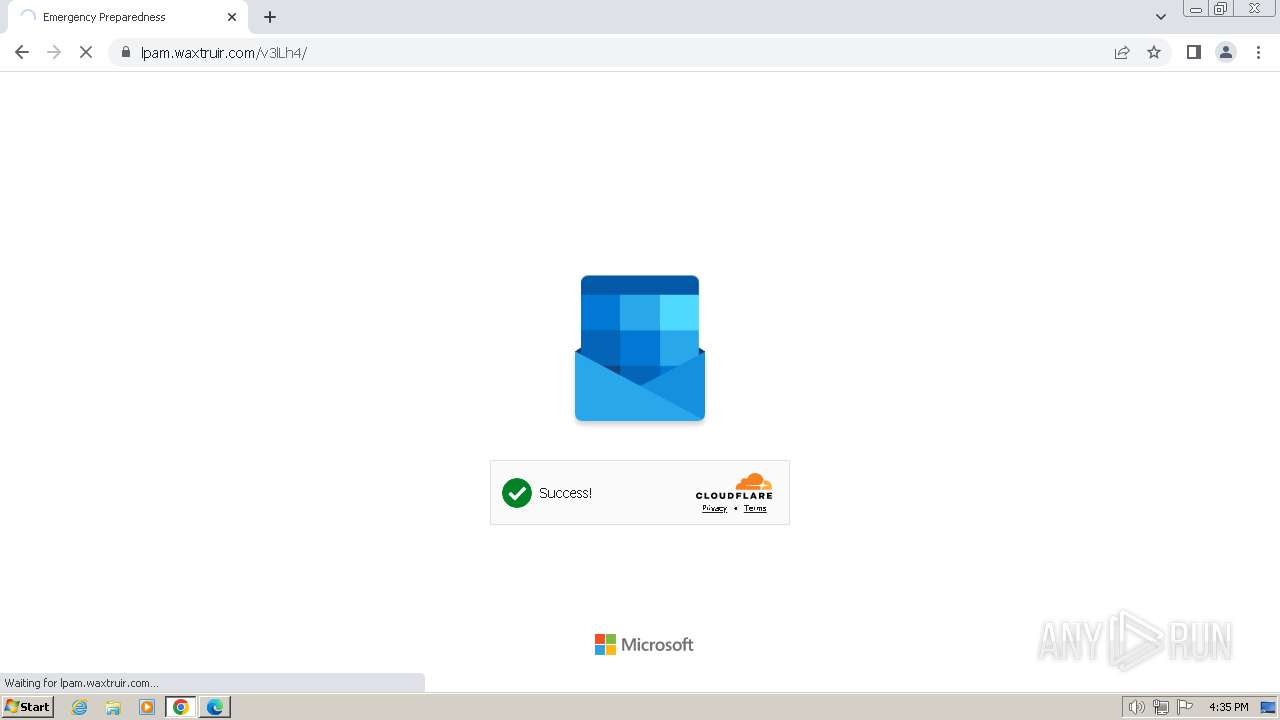
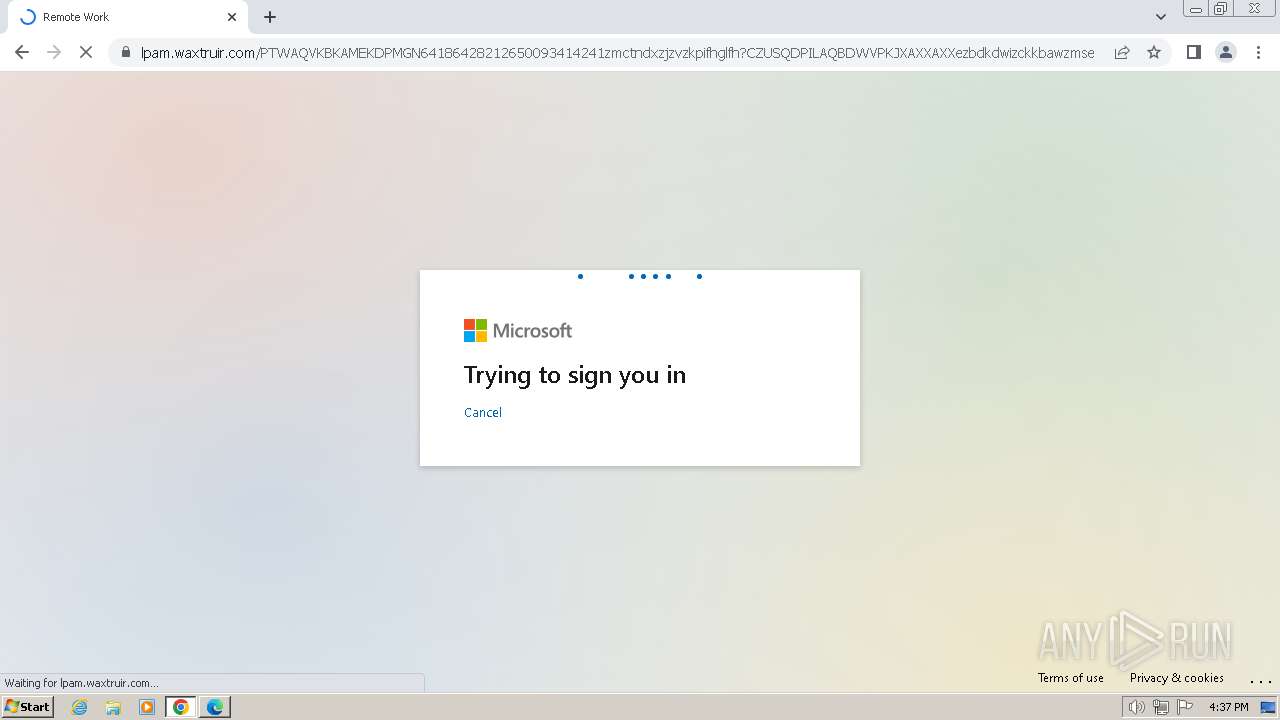
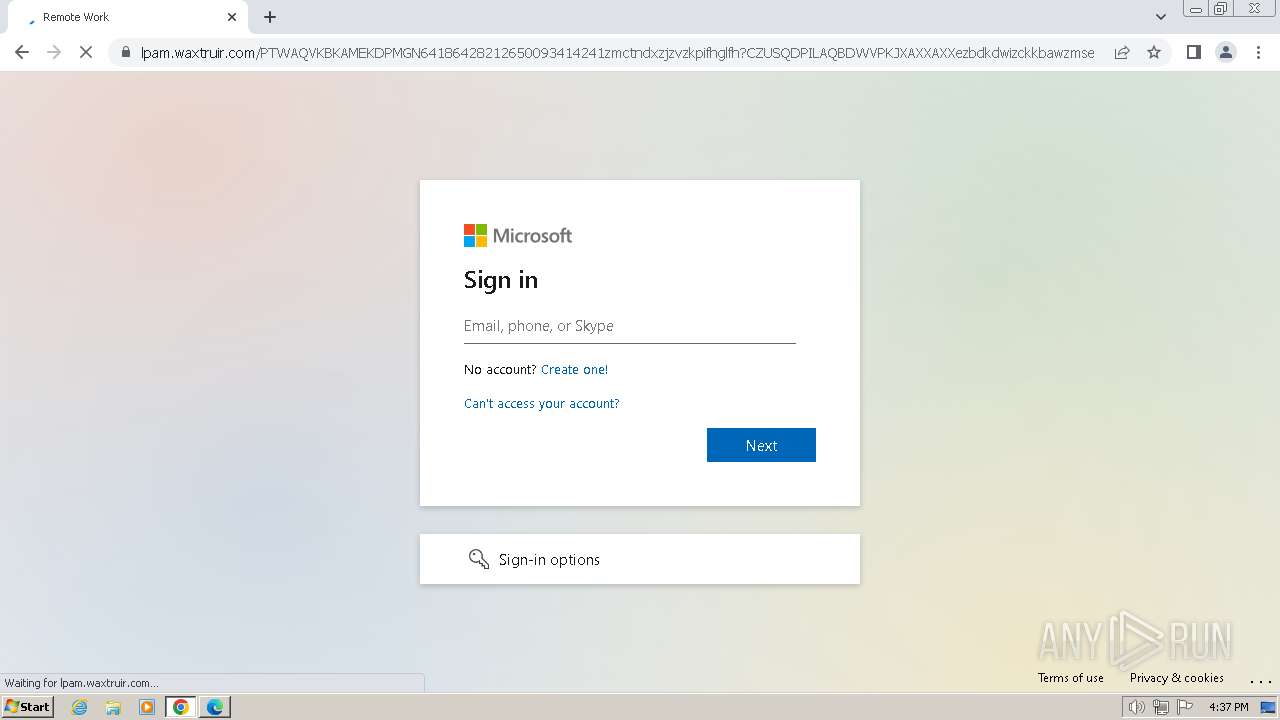
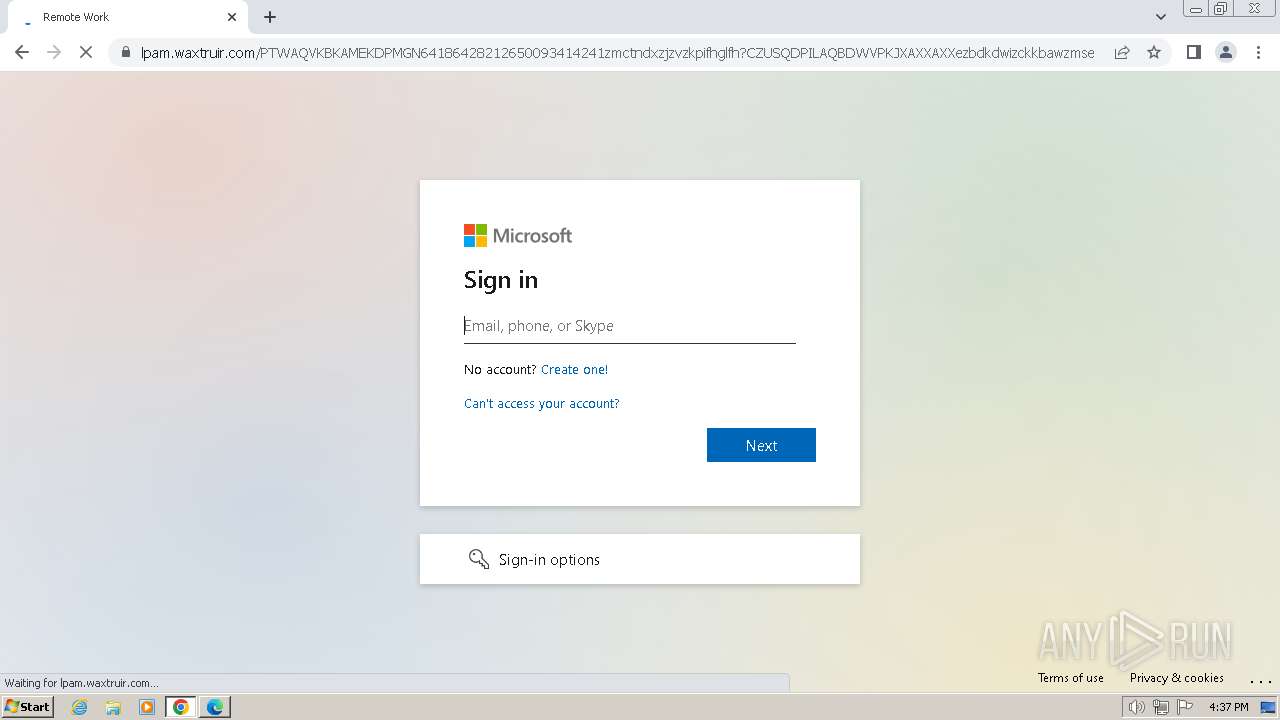
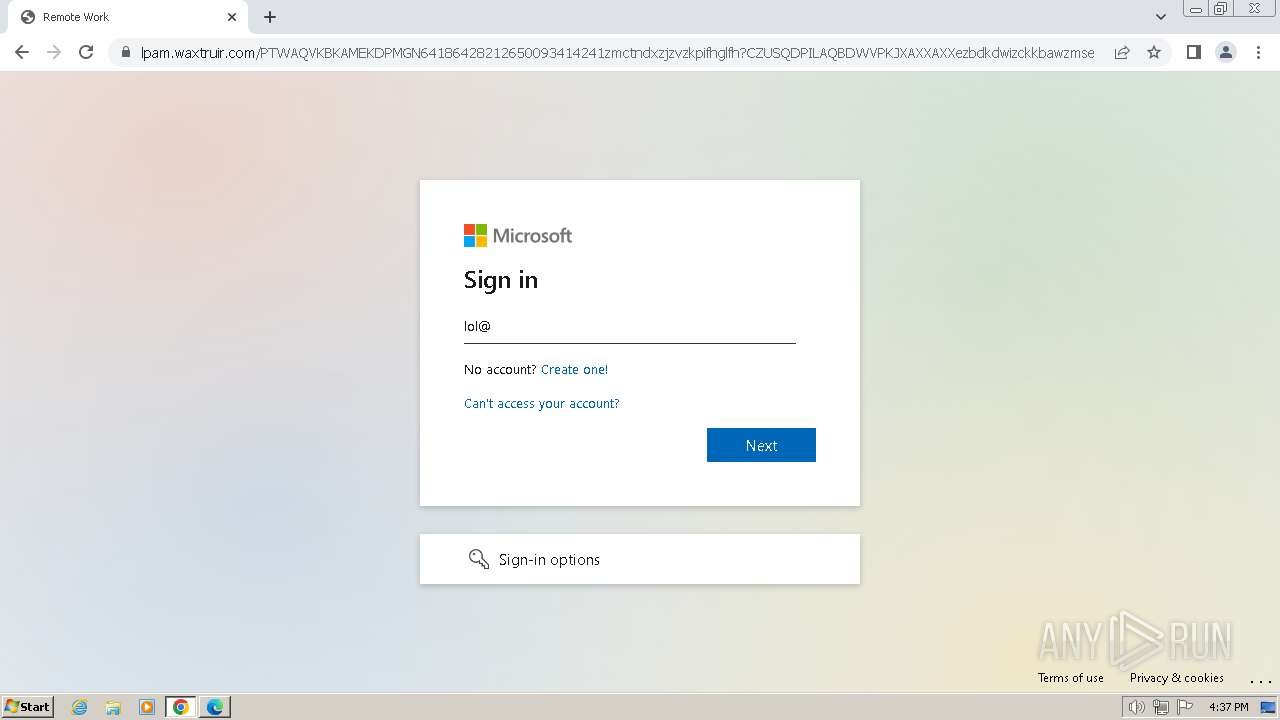
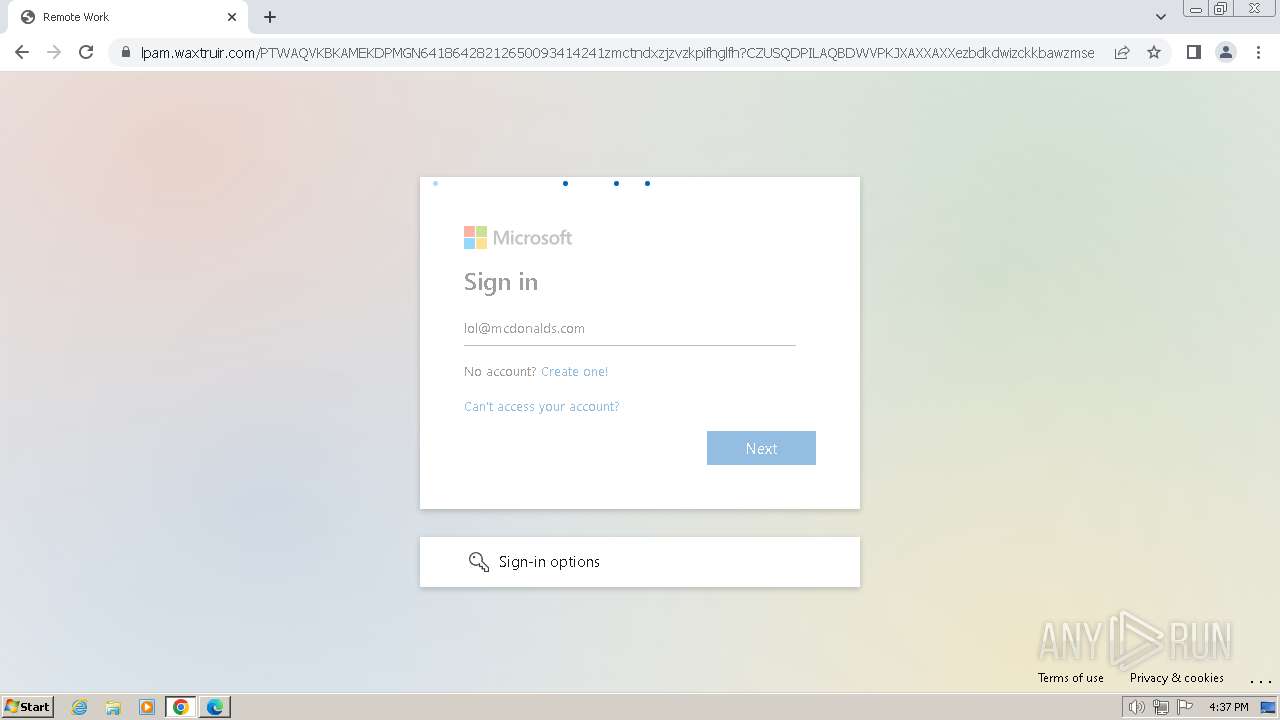
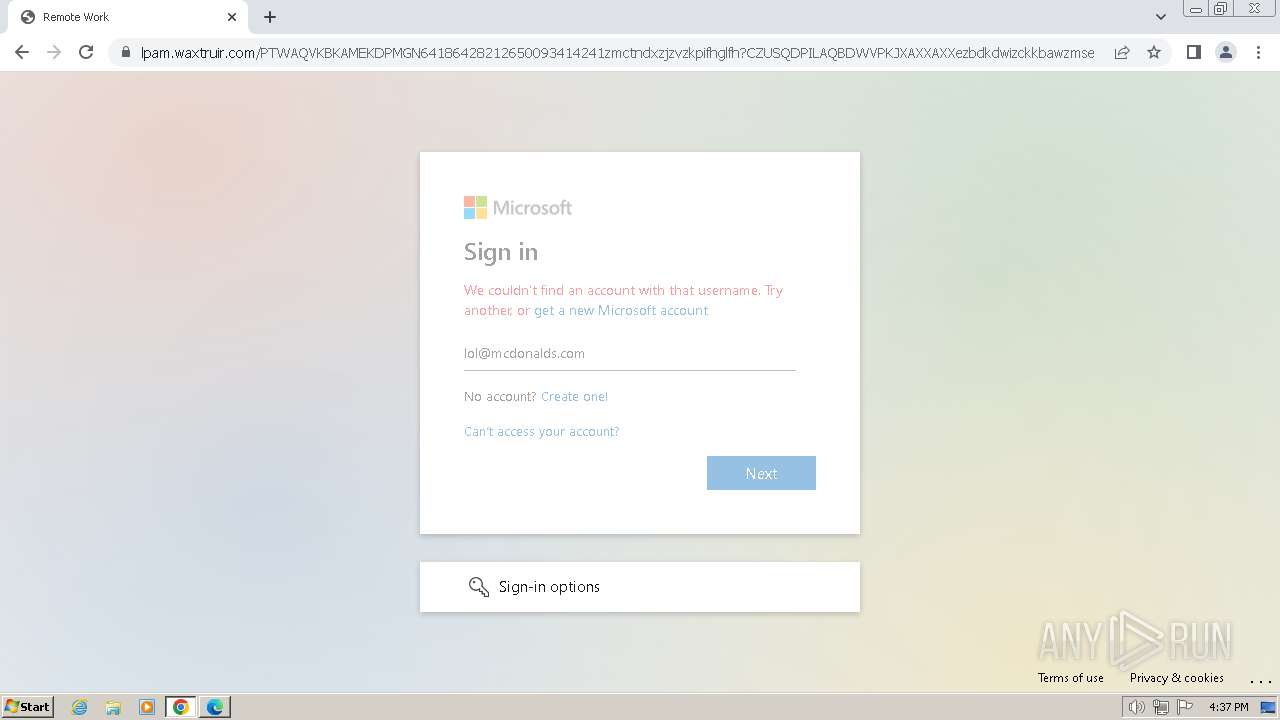
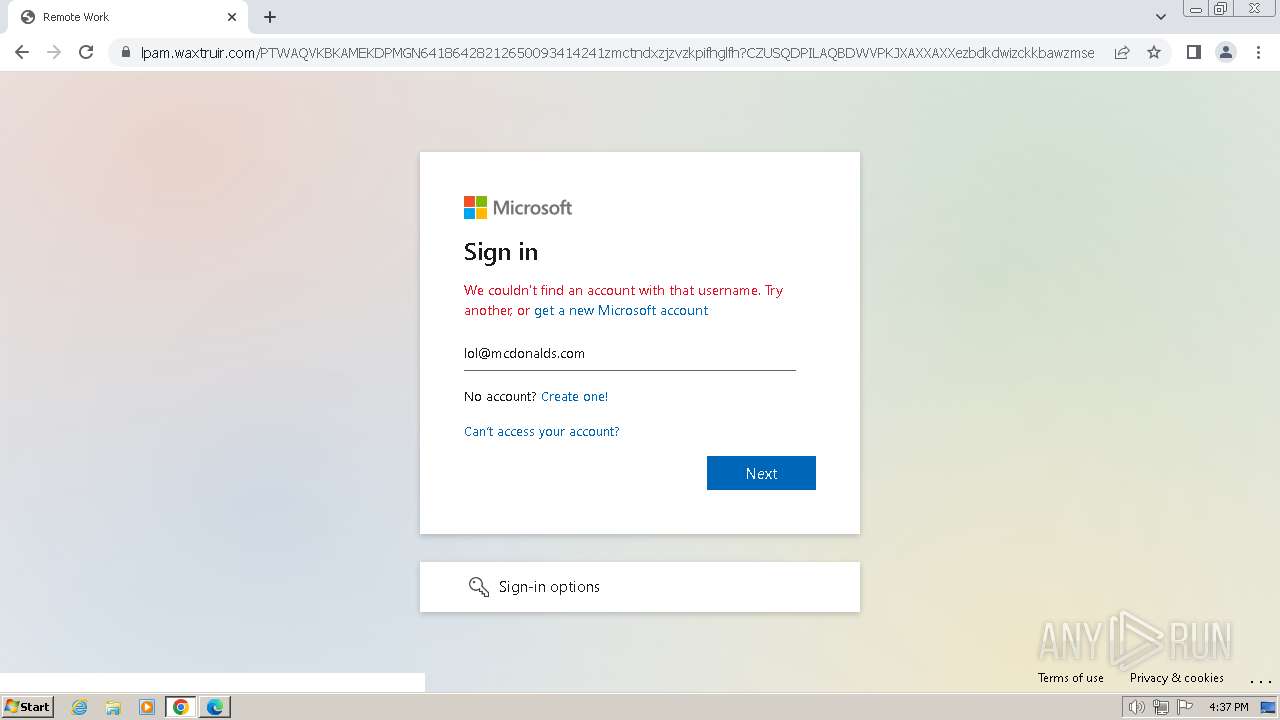
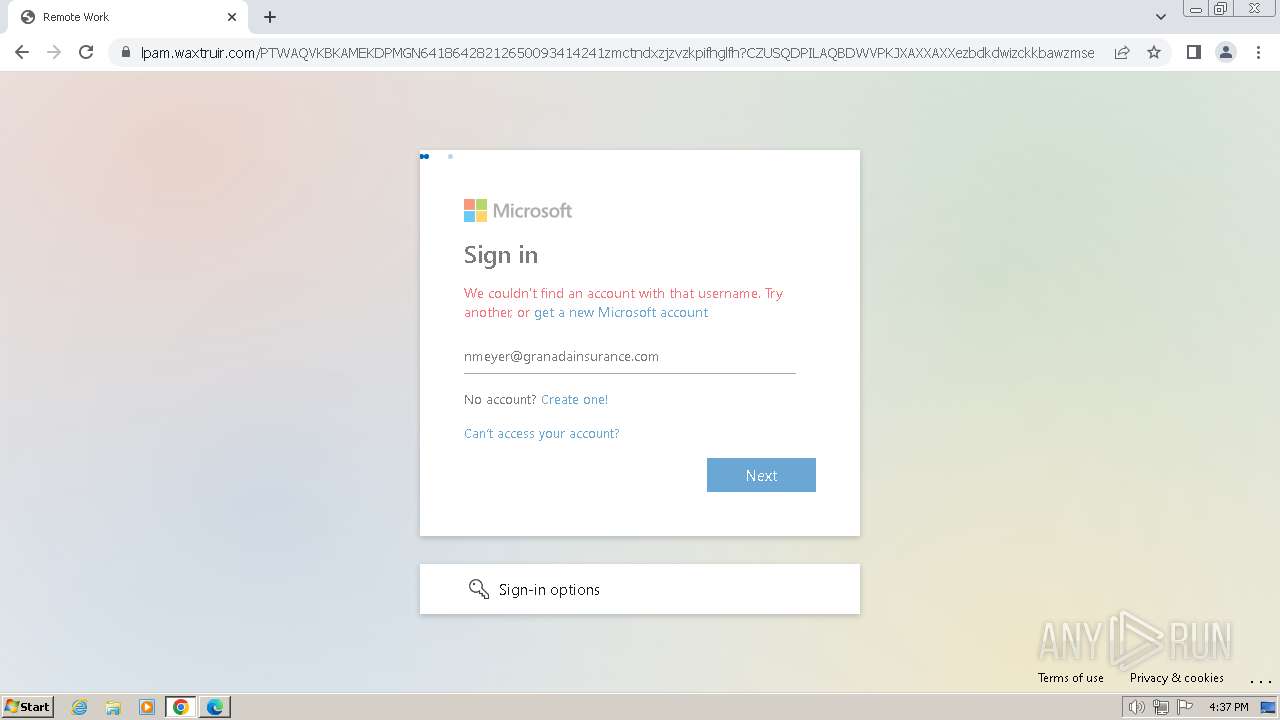
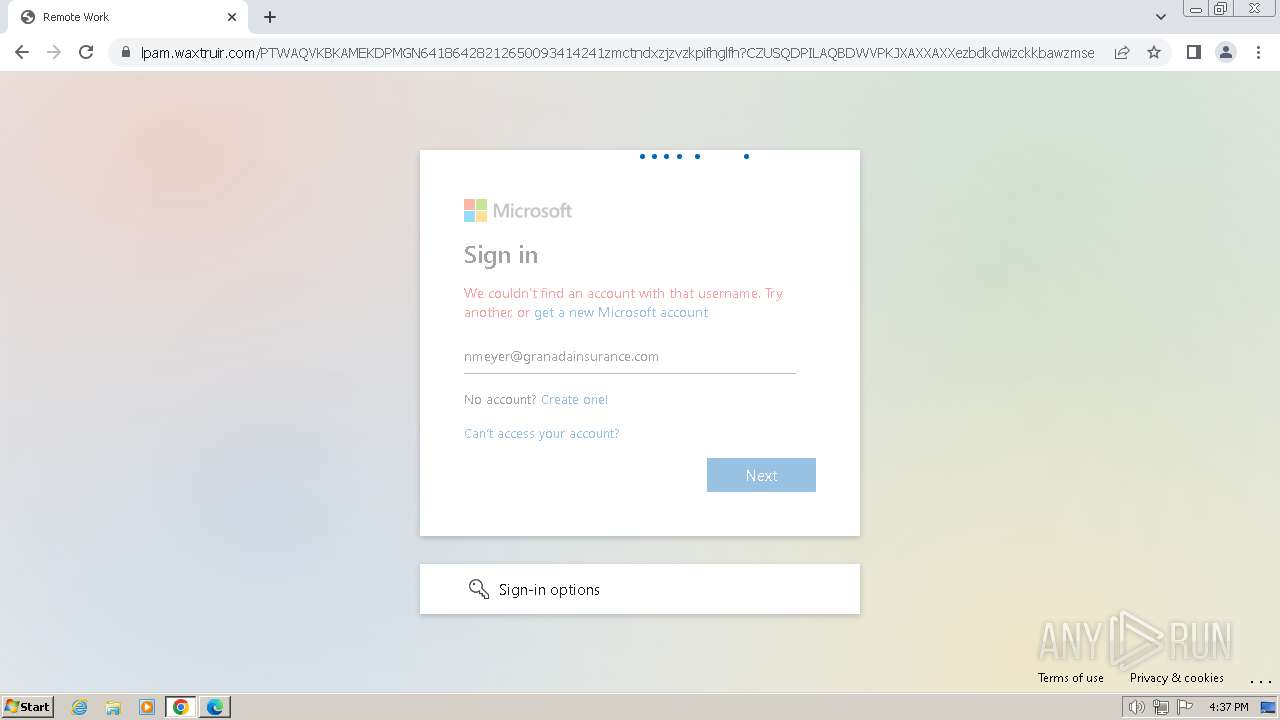
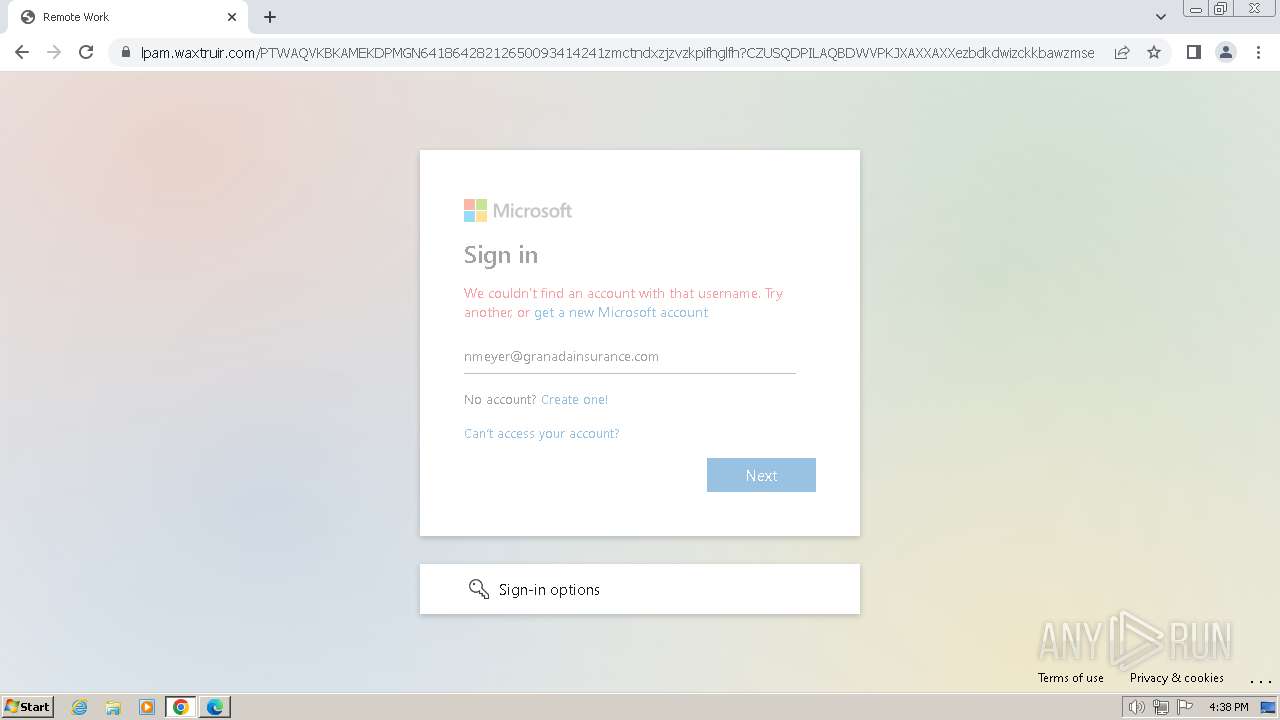
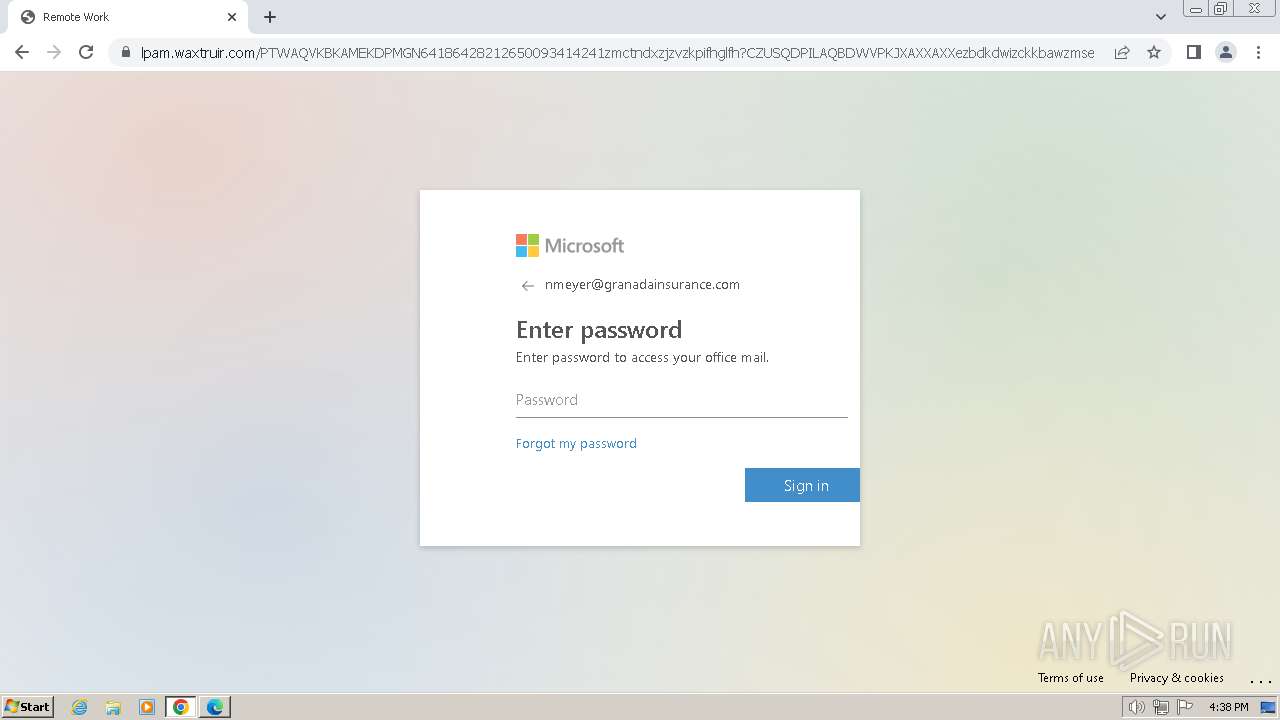
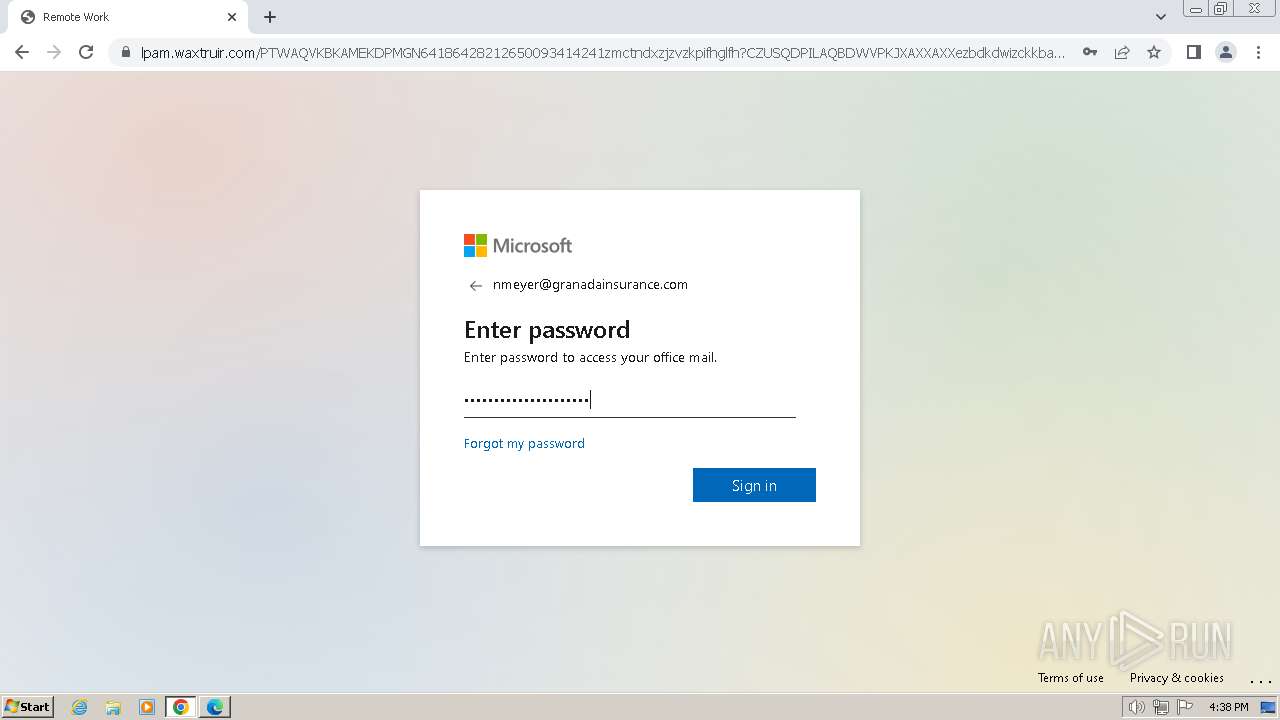
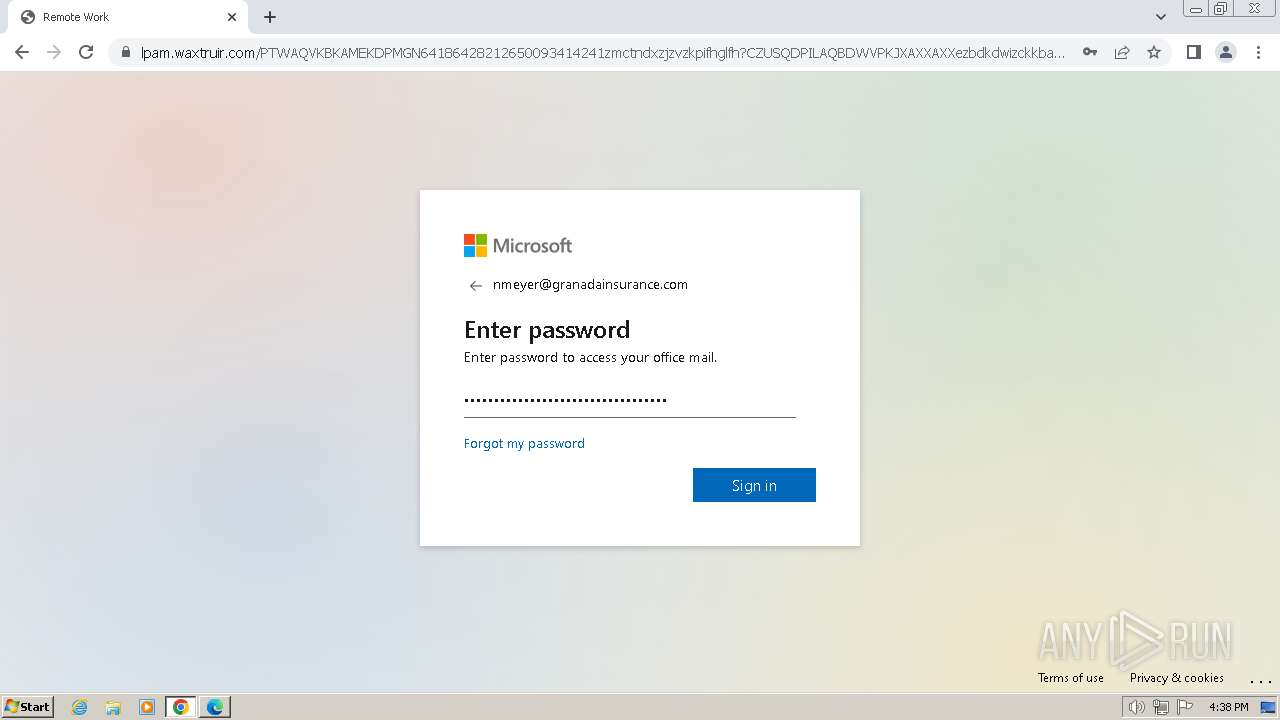
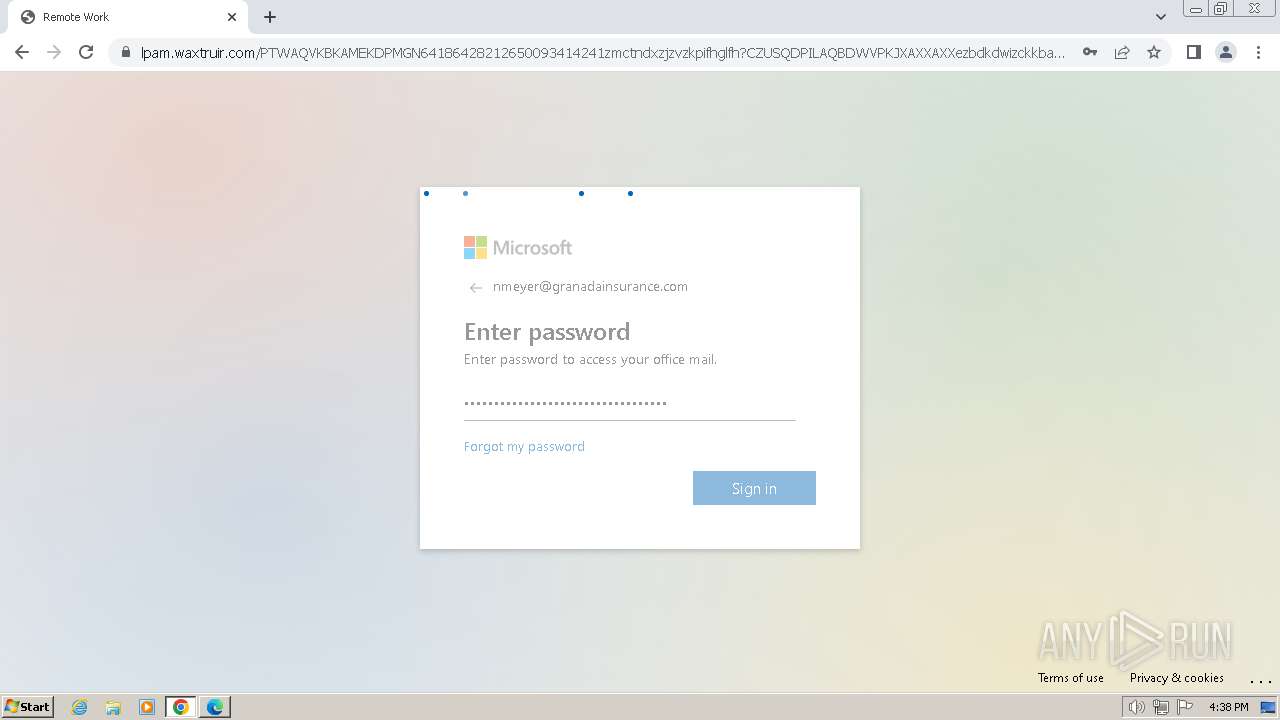
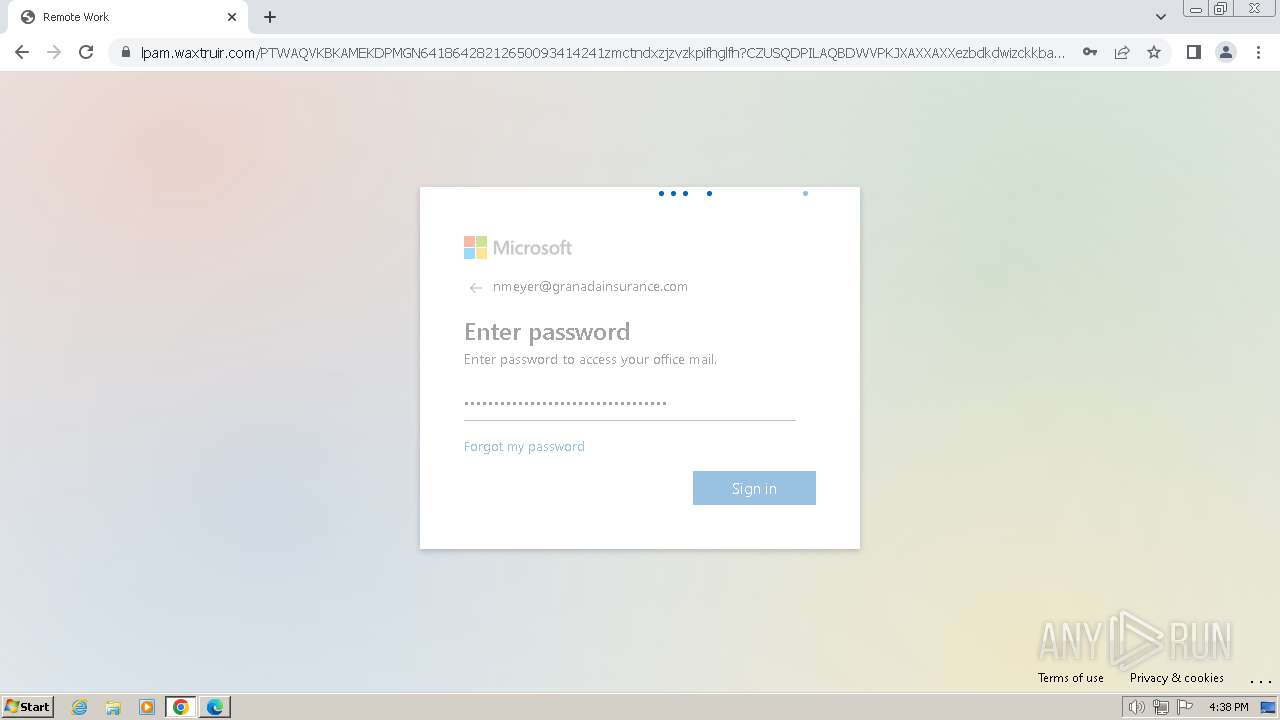
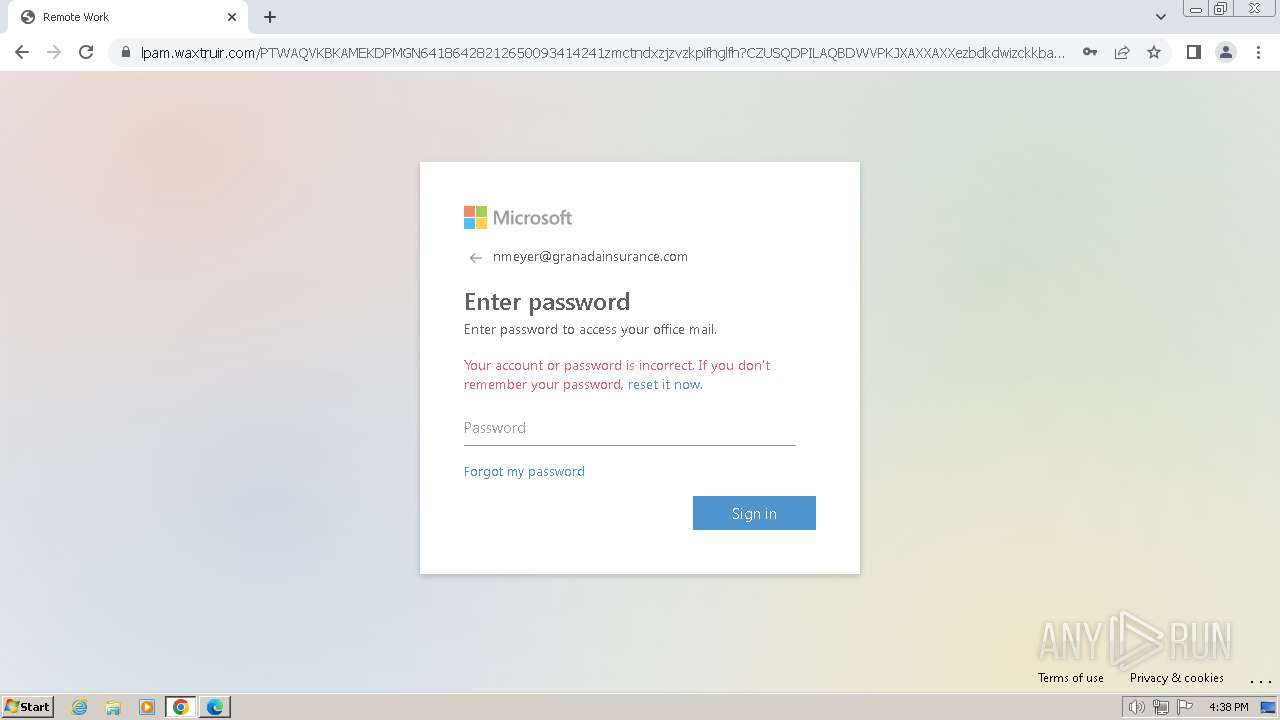
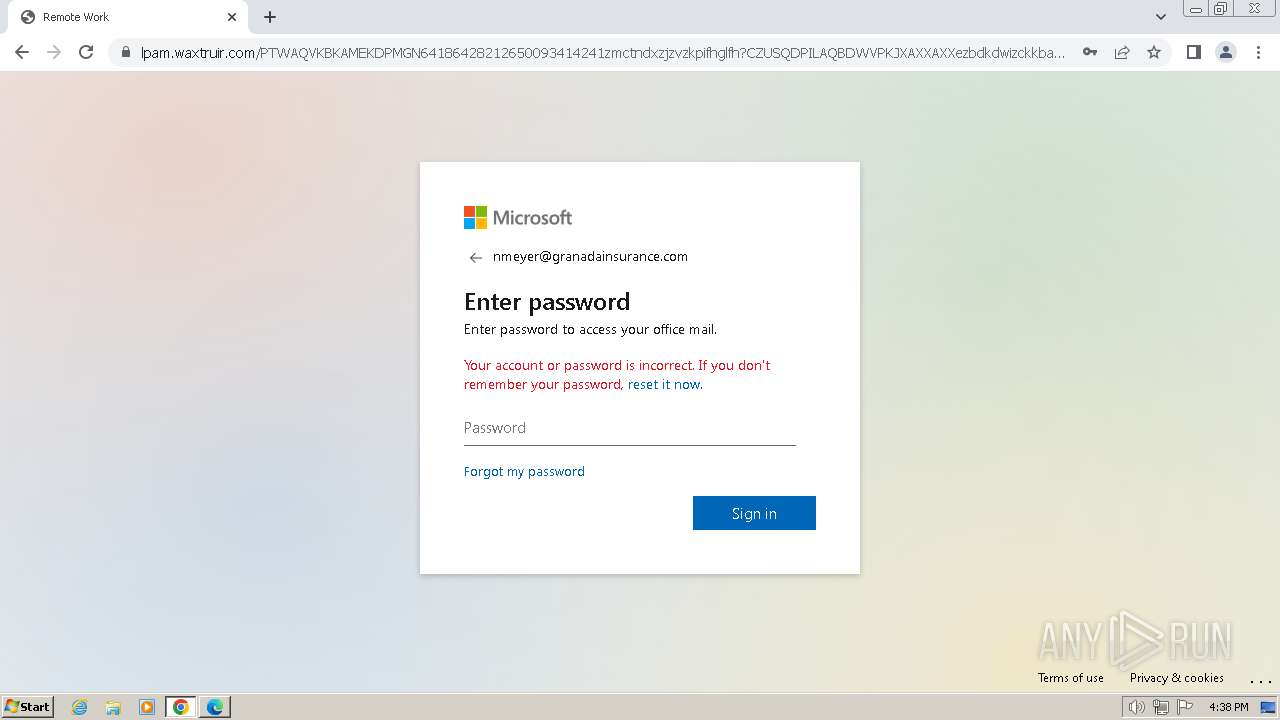
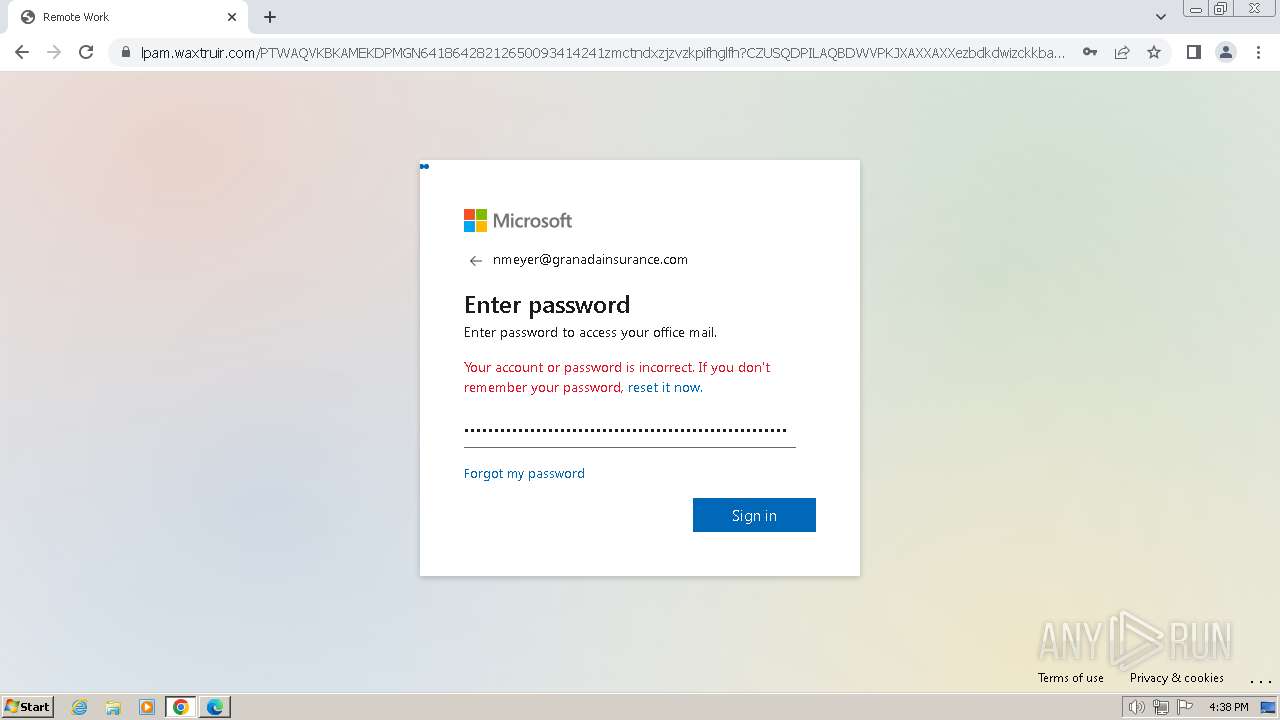
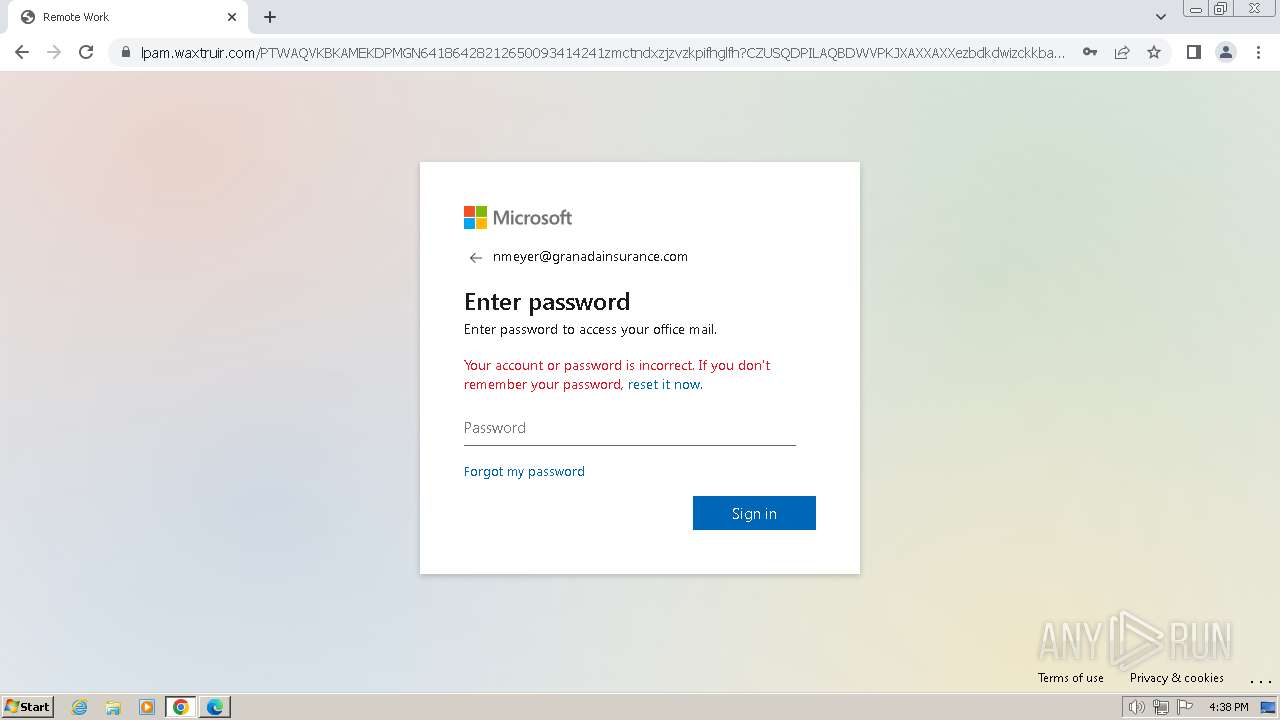
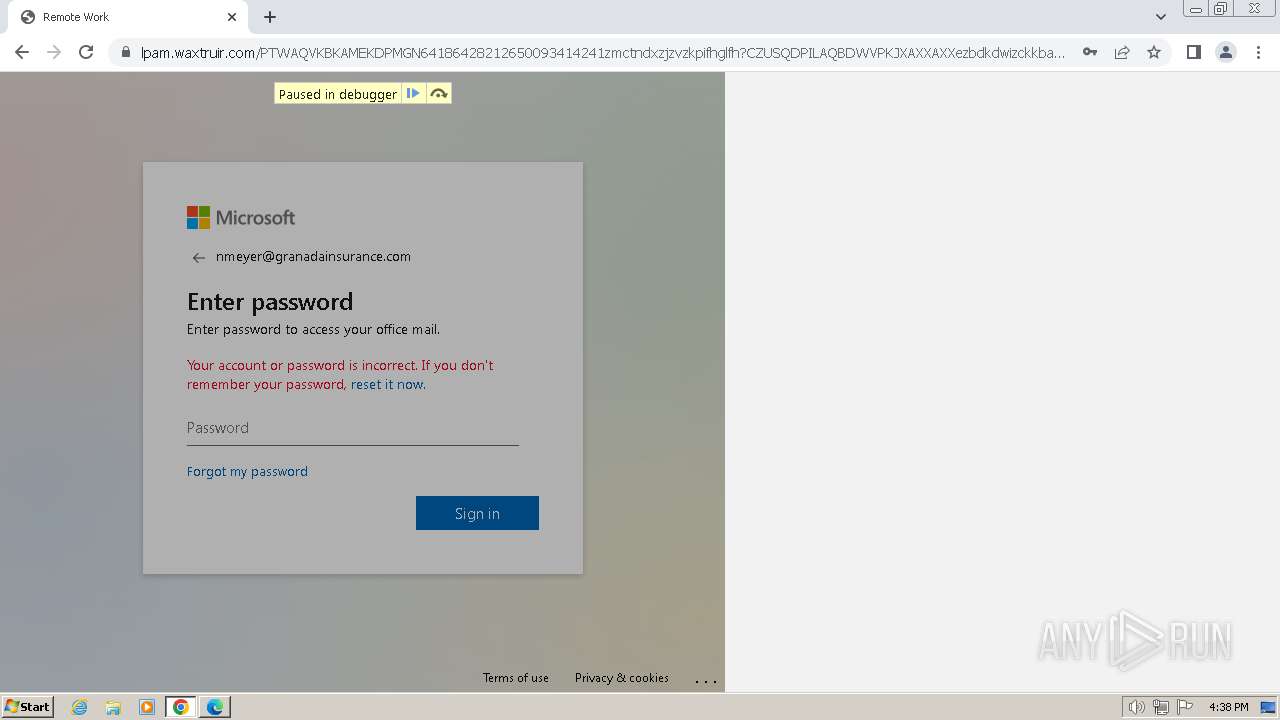
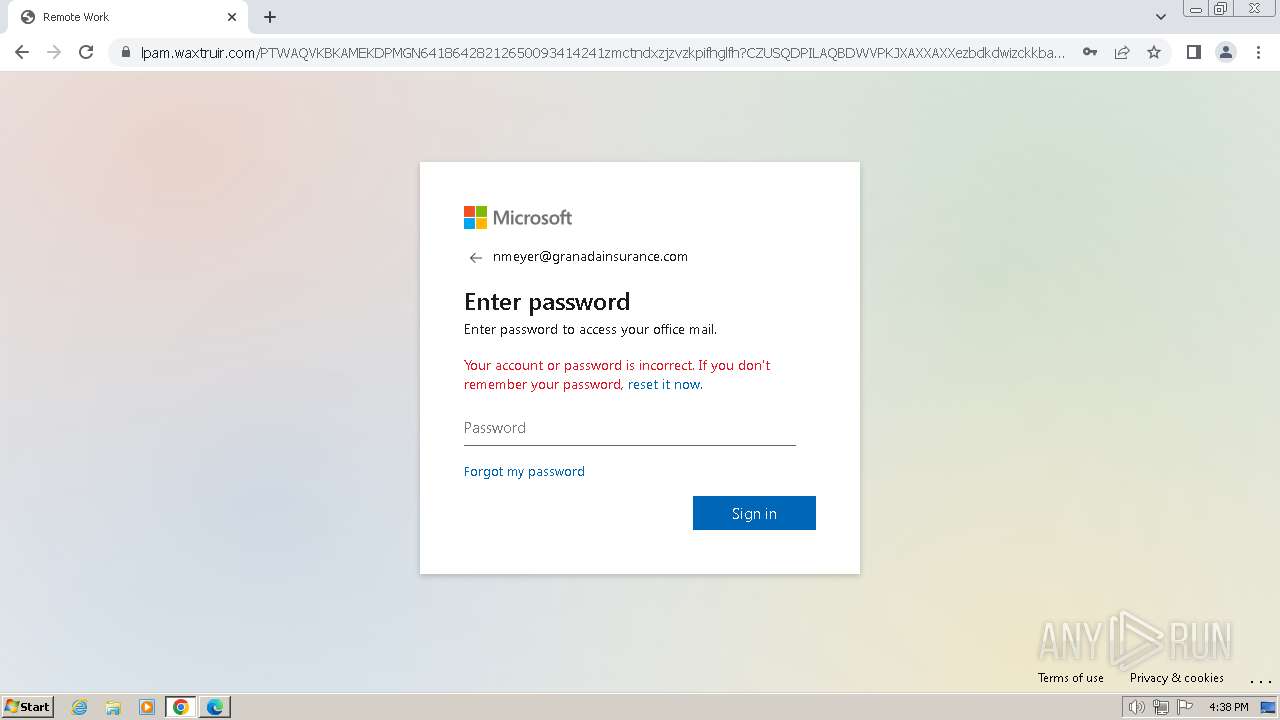
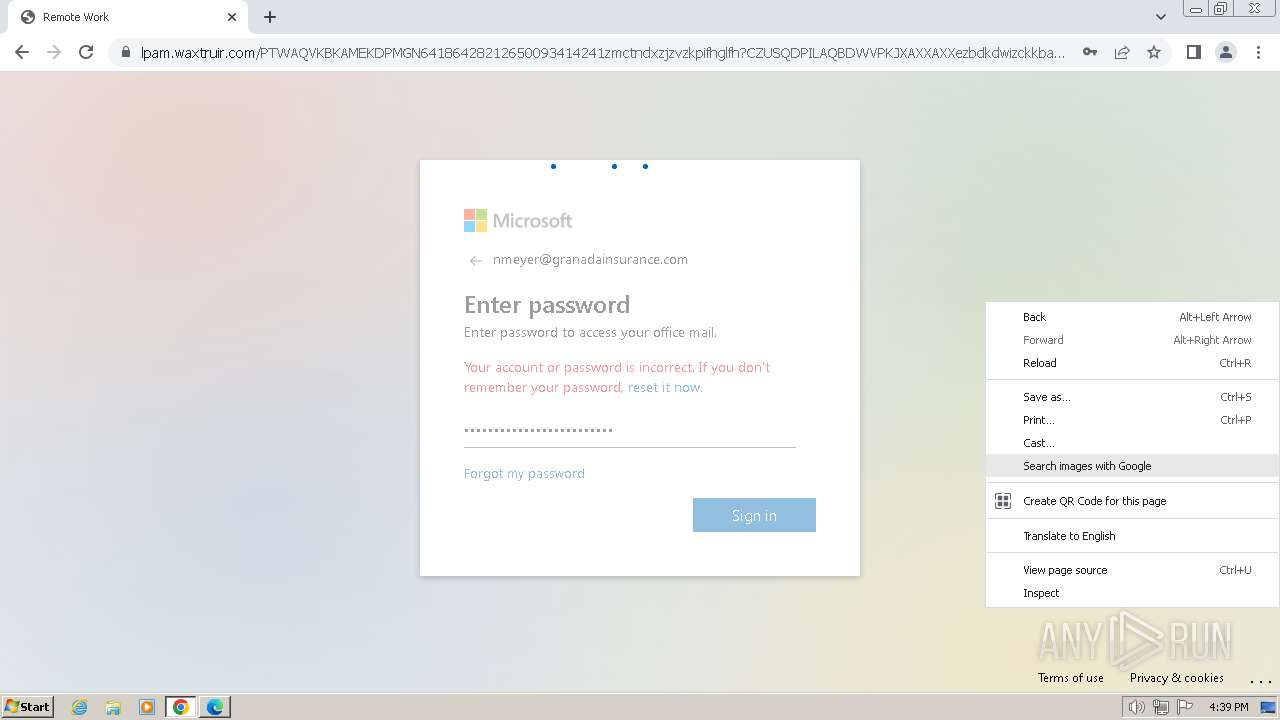
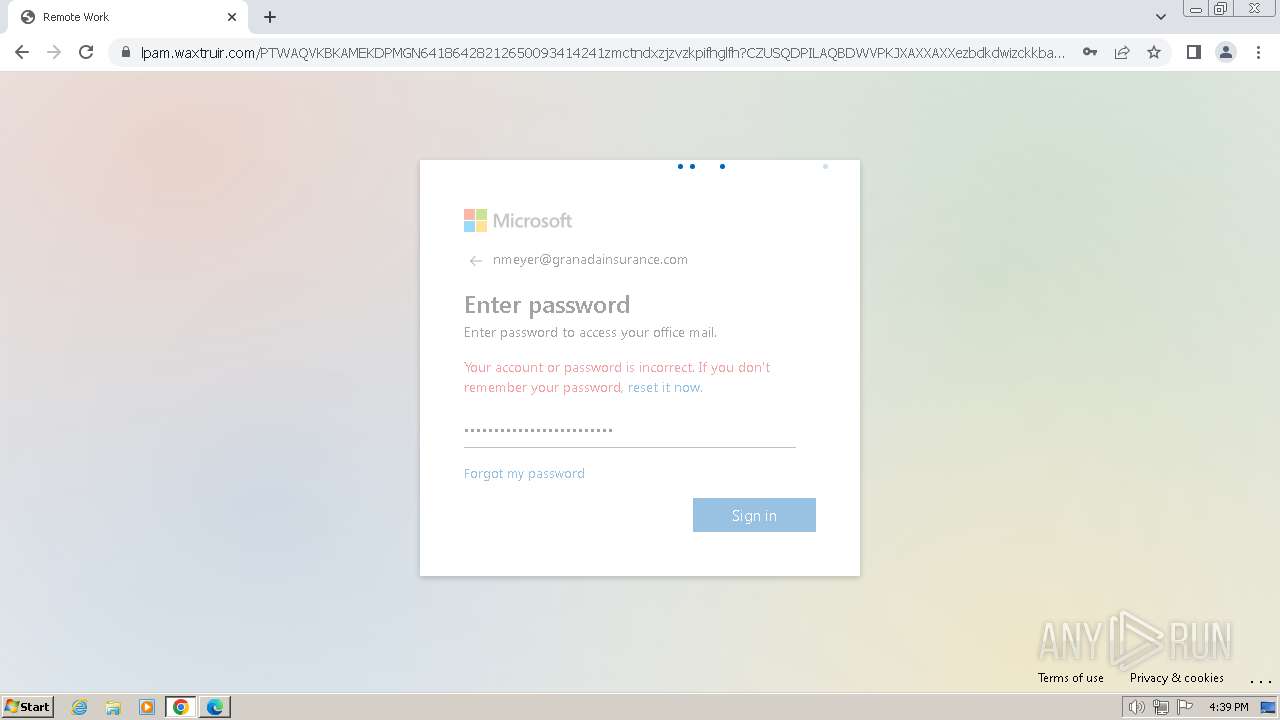
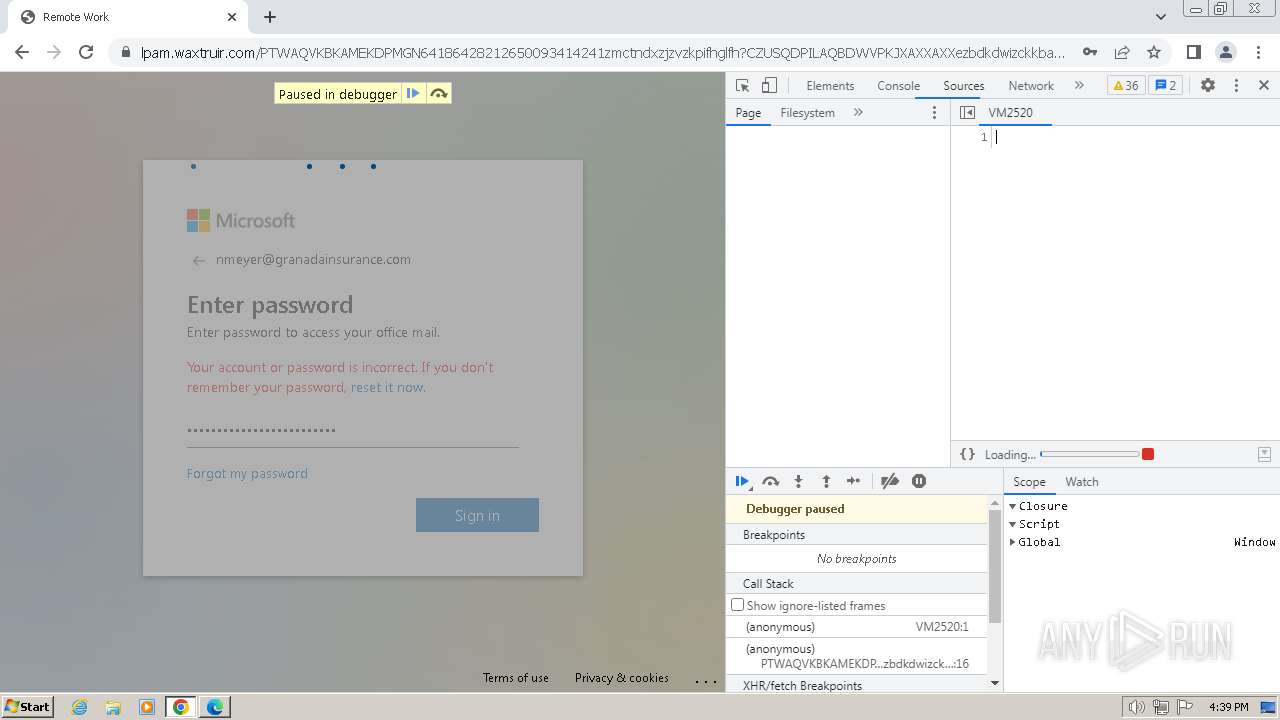
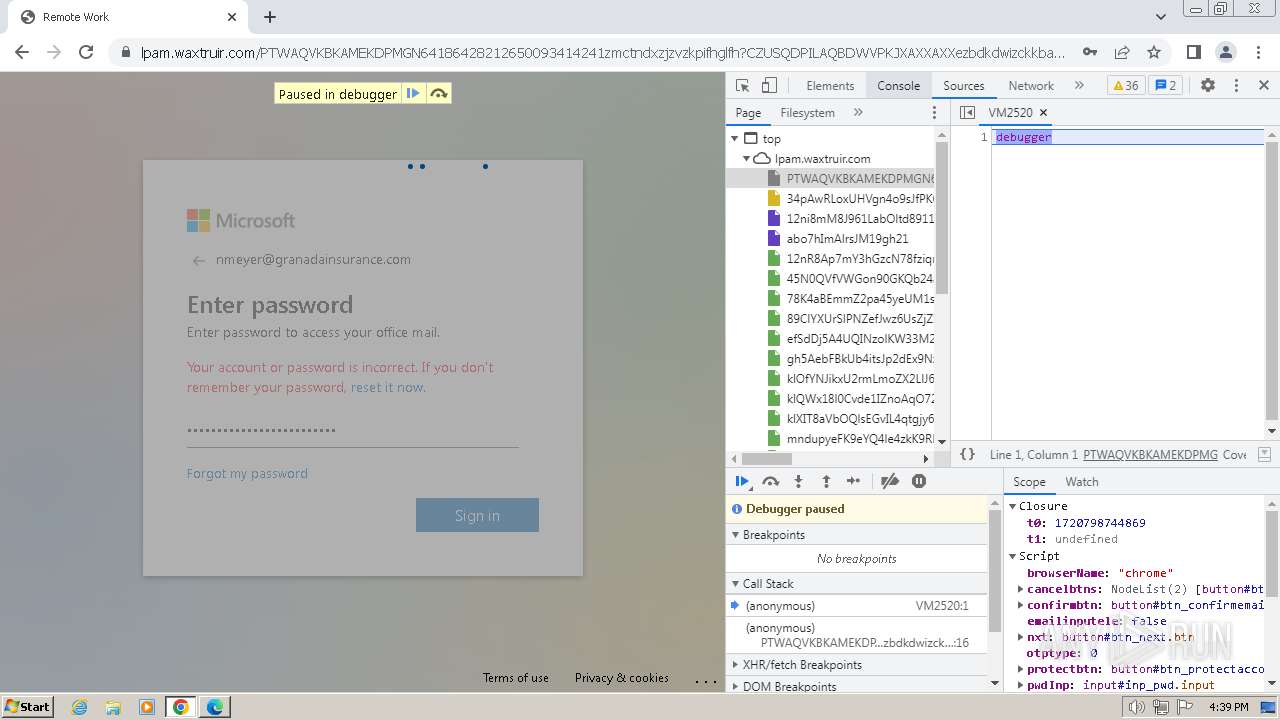
| Threats: | Tycoon 2FA is a phishing-as-a-service (PhaaS) platform designed to bypass multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts. Its advanced evasion techniques and modular architecture make it a significant threat to organizations relying on MFA for security. |
| Analysis date: | July 12, 2024, 15:34:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/png |
| File info: | PNG image data, 274 x 267, 8-bit/color RGBA, non-interlaced |
| MD5: | D52AA594B15F4BC7F8D13238BE9B6472 |
| SHA1: | 3F2C98431EA691FD9E5B69DE253DE0402A8F79B0 |
| SHA256: | 960ED6C2E71D5BD87D31479FDFC12324B69D042A0B3210420DC3C39FC746B05C |
| SSDEEP: | 192:daxRyueMP2dzLoeqKQPv5mpwsjvhoXd9WuhgQbRr3ZGv:YDe0ugeqLwdvs6Q9j0 |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 2324)
SUSPICIOUS
No suspicious indicators.INFO
Reads the Internet Settings
- explorer.exe (PID: 3416)
- explorer.exe (PID: 3520)
Application launched itself
- msedge.exe (PID: 3308)
- chrome.exe (PID: 1832)
Manual execution by a user
- chrome.exe (PID: 1832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .png | | | Portable Network Graphics (100) |
|---|
EXIF
PNG
| ImageWidth: | 274 |
|---|---|
| ImageHeight: | 267 |
| BitDepth: | 8 |
| ColorType: | RGB with Alpha |
| Compression: | Deflate/Inflate |
| Filter: | Adaptive |
| Interlace: | Noninterlaced |
| SRGBRendering: | Perceptual |
| Gamma: | 2.2 |
| PixelsPerUnitX: | 3779 |
| PixelsPerUnitY: | 3779 |
| PixelUnits: | meters |
Composite
| ImageSize: | 274x267 |
|---|---|
| Megapixels: | 0.073 |
Total processes
76
Monitored processes
39
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2264 --field-trial-handle=1160,i,1675620387467689378,6628616229275857032,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x68ce8b38,0x68ce8b48,0x68ce8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1220 --field-trial-handle=1296,i,12916468884136501232,10019529595750159657,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2124 --field-trial-handle=1160,i,1675620387467689378,6628616229275857032,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2324 --field-trial-handle=1160,i,1675620387467689378,6628616229275857032,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1516 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3268 --field-trial-handle=1296,i,12916468884136501232,10019529595750159657,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1068 --field-trial-handle=1160,i,1675620387467689378,6628616229275857032,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2112 --field-trial-handle=1160,i,1675620387467689378,6628616229275857032,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4212 --field-trial-handle=1296,i,12916468884136501232,10019529595750159657,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
19 487
Read events
19 369
Write events
111
Delete events
7
Modification events
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: B4B9DDE6A47B2F00 | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3308) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
0
Suspicious files
219
Text files
48
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF4e730.TMP | — | |
MD5:— | SHA256:— | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF4e74f.TMP | — | |
MD5:— | SHA256:— | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF4e79d.TMP | — | |
MD5:— | SHA256:— | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:CE3AC3673EB3498DDF7BEC3328D23765 | SHA256:D2304AEDC7D32192364DCDECAF7A17972F3ABF909A79646A47B66917ECA30E9A | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\54690e83-bf2e-4f55-8568-043997203108.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RF4e73f.TMP | text | |
MD5:646FEFDB4D82709E3056F5C71953783C | SHA256:7B83D8689750F64D31016F1E8AC2A4EB9D7DB406E4C9C66211D4ED17DEBFEAD9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
78
DNS requests
91
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
844 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | whitelisted |
3308 | msedge.exe | GET | 200 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?23112fcf62a80d6e | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2324 | chrome.exe | GET | 204 | 172.217.23.99:80 | http://www.gstatic.com/generate_204 | unknown | — | — | whitelisted |
844 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | whitelisted |
844 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | whitelisted |
844 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2080 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3308 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2080 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2080 | msedge.exe | 148.251.237.233:443 | hibrid.rs | Hetzner Online GmbH | DE | unknown |
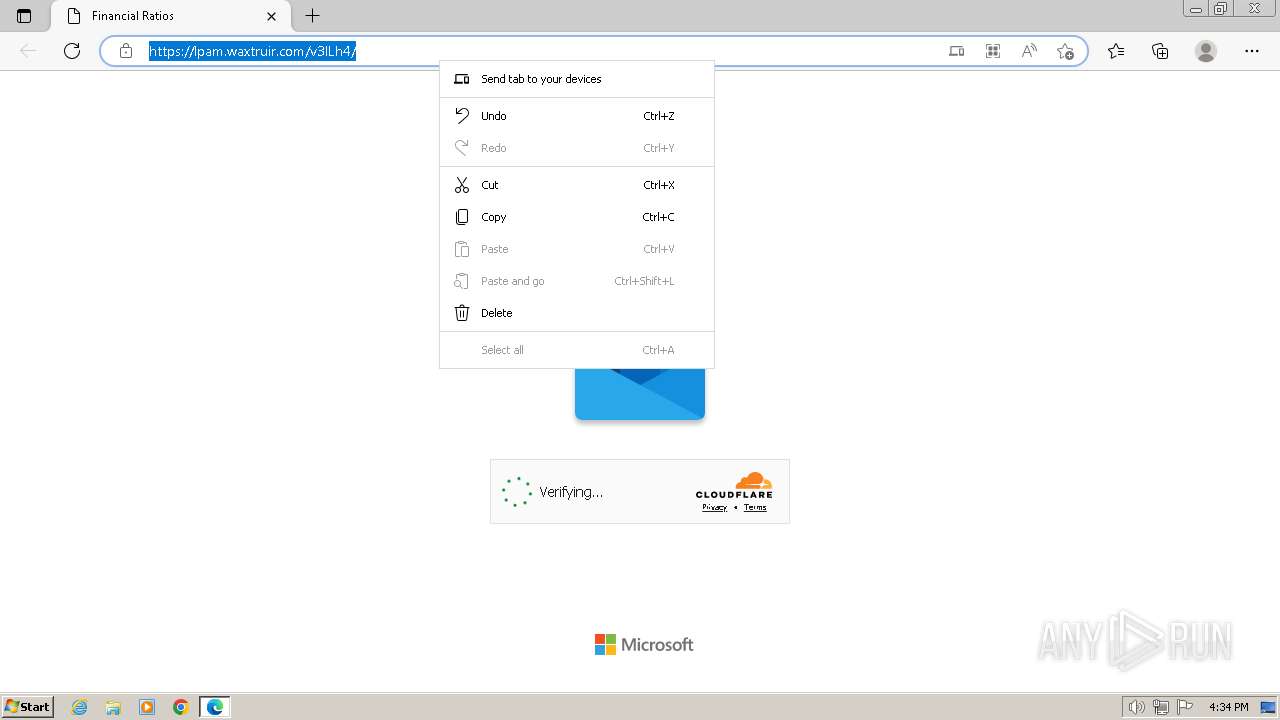
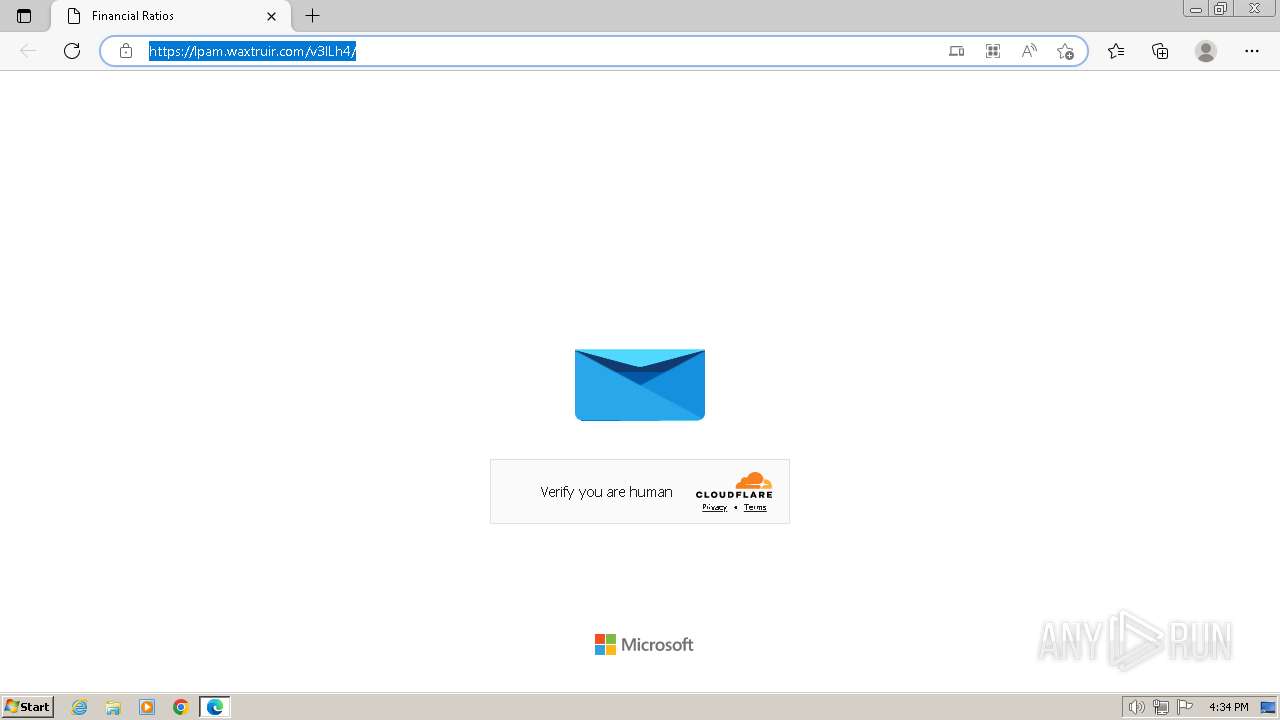
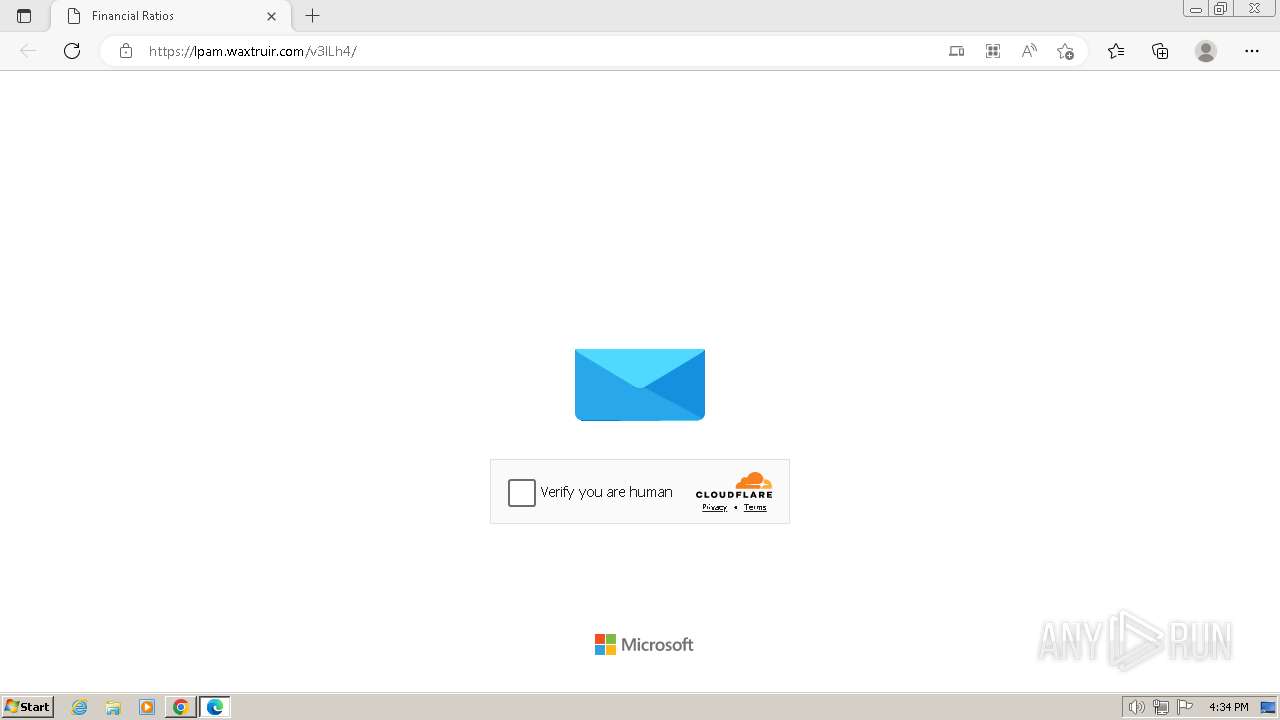
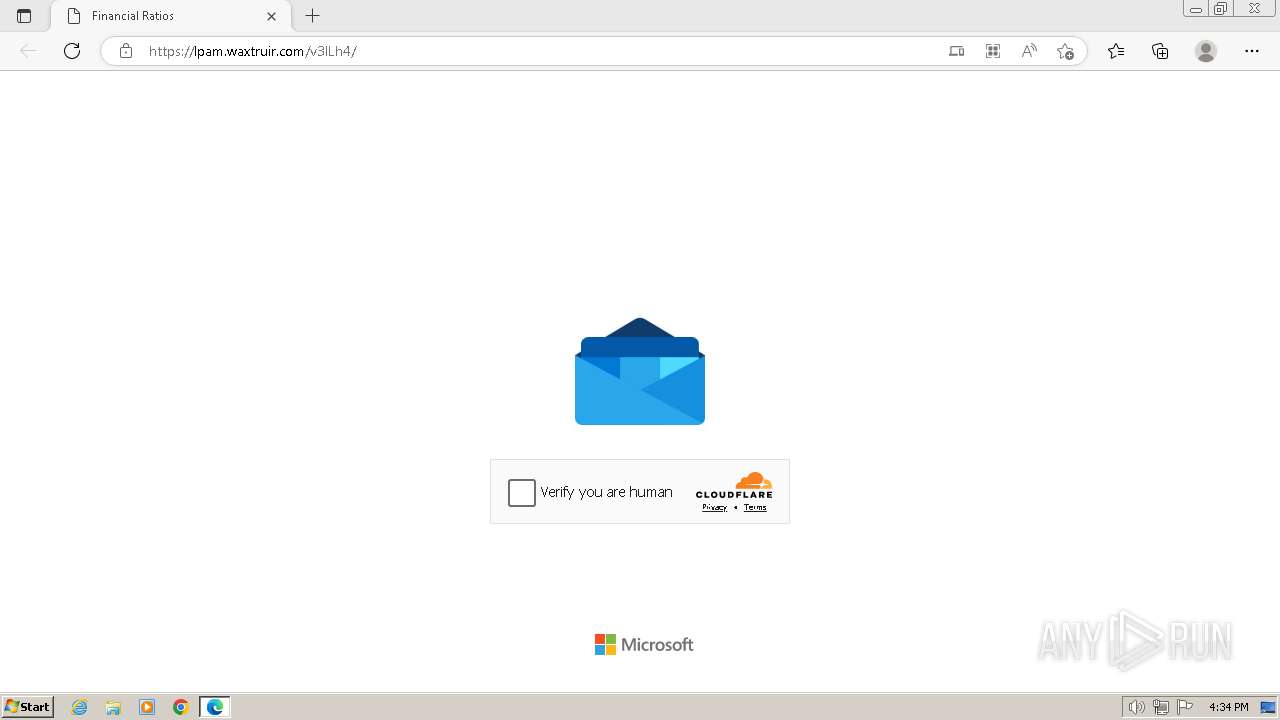
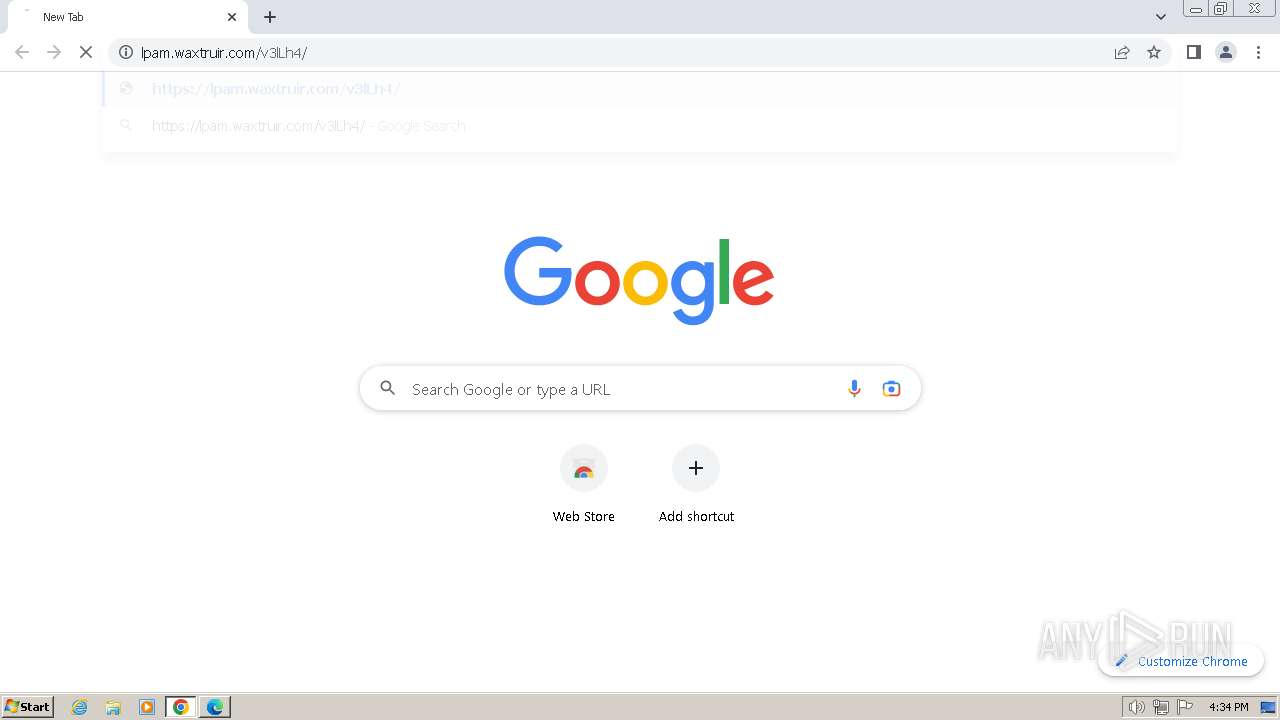
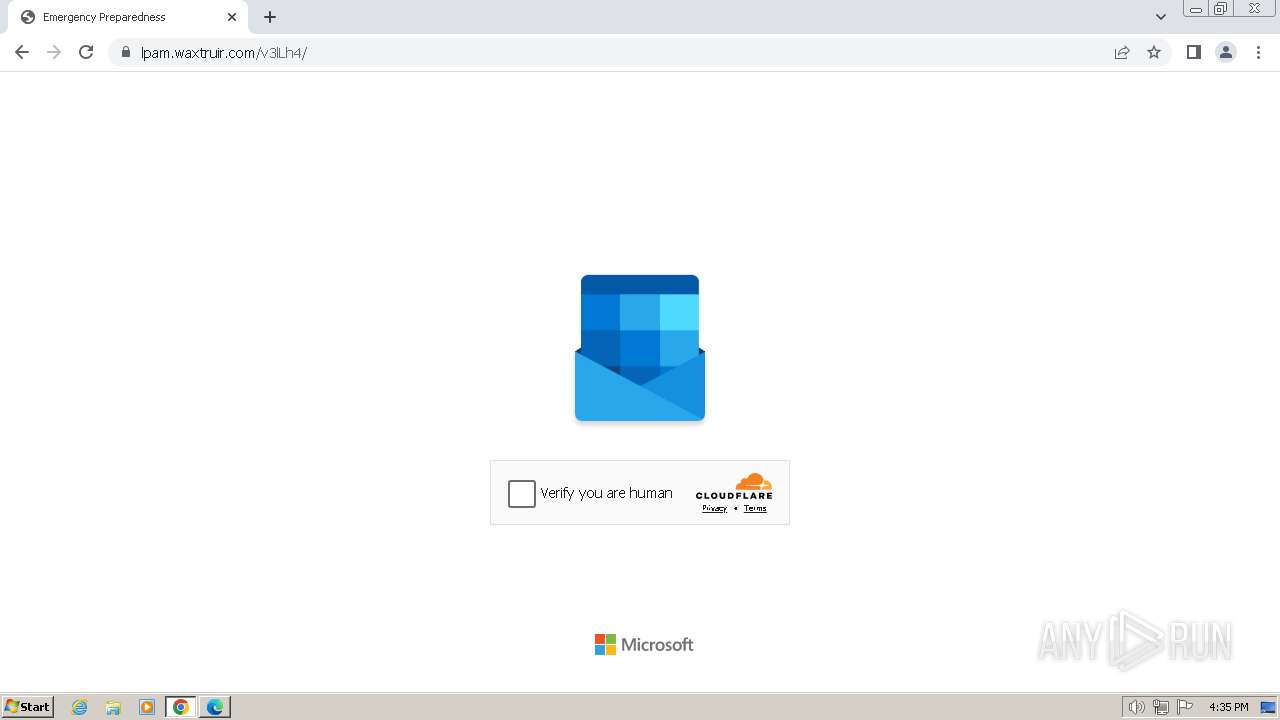
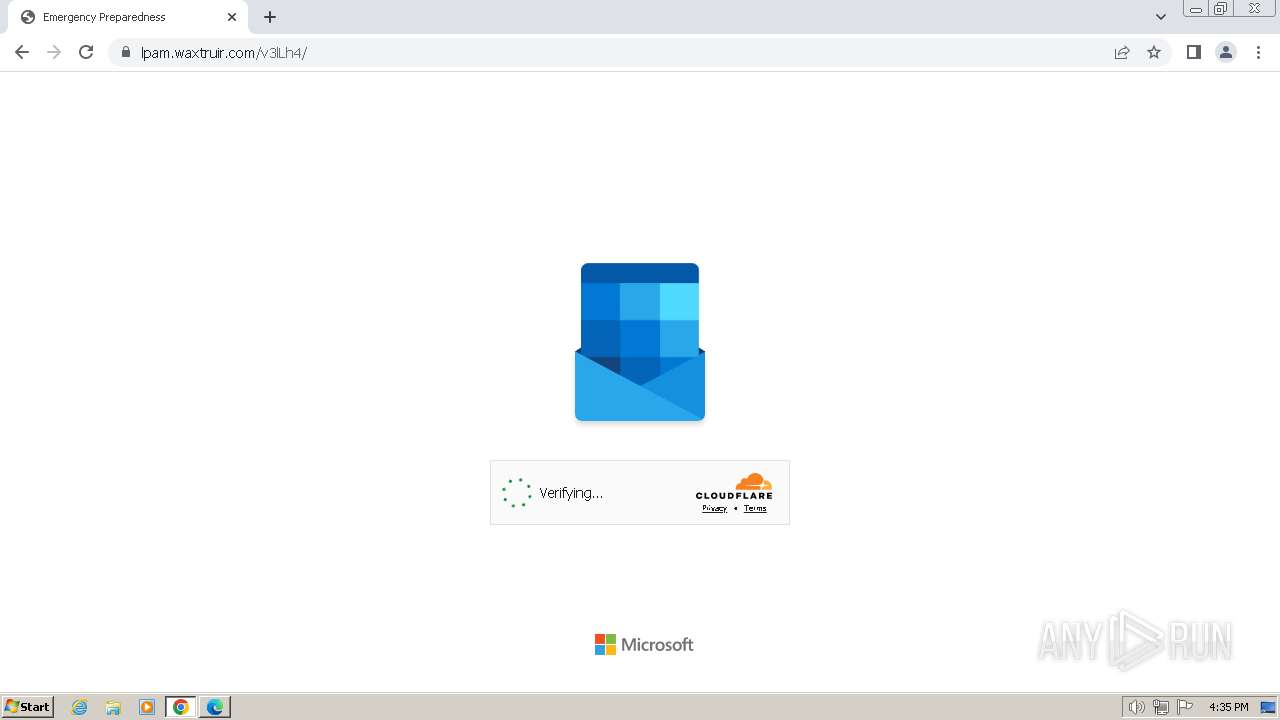
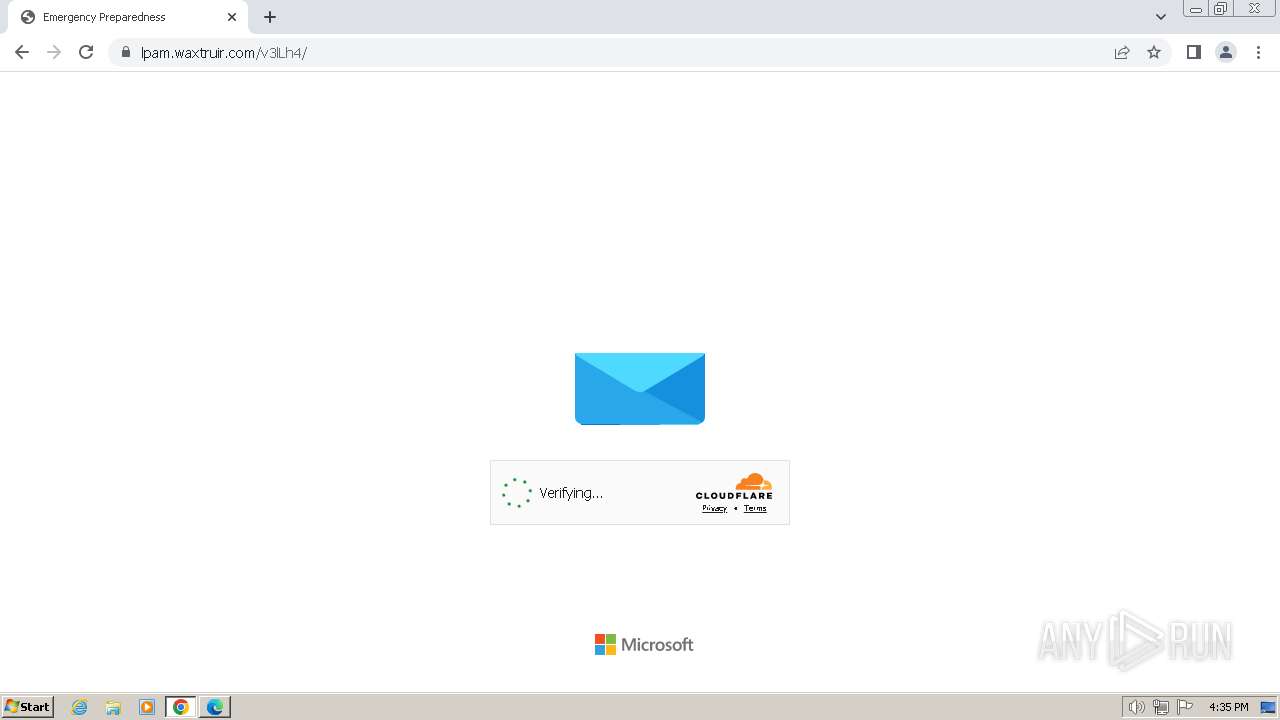
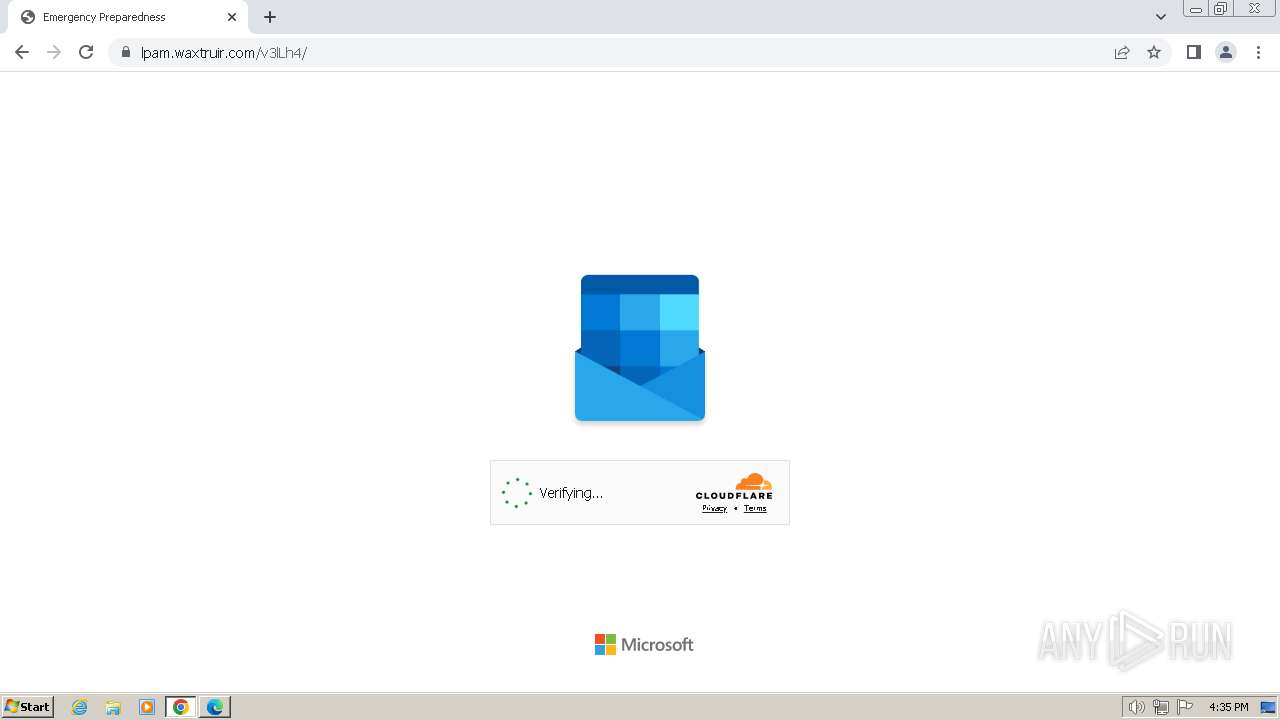
2080 | msedge.exe | 104.21.30.35:443 | lpam.waxtruir.com | CLOUDFLARENET | — | unknown |
2080 | msedge.exe | 104.17.3.184:443 | challenges.cloudflare.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
hibrid.rs |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
lpam.waxtruir.com |
| unknown |
code.jquery.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
5pxg.25bvnw8.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2080 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2080 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2080 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2324 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (DadSec) |
2324 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (DadSec) |
2324 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Bidirectional and low-latency communication CDN (cdn .socket .io) |
2324 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing (Tycoon 2FA) |
2324 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |
2324 | chrome.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |
2324 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain chain identified as Phishing |