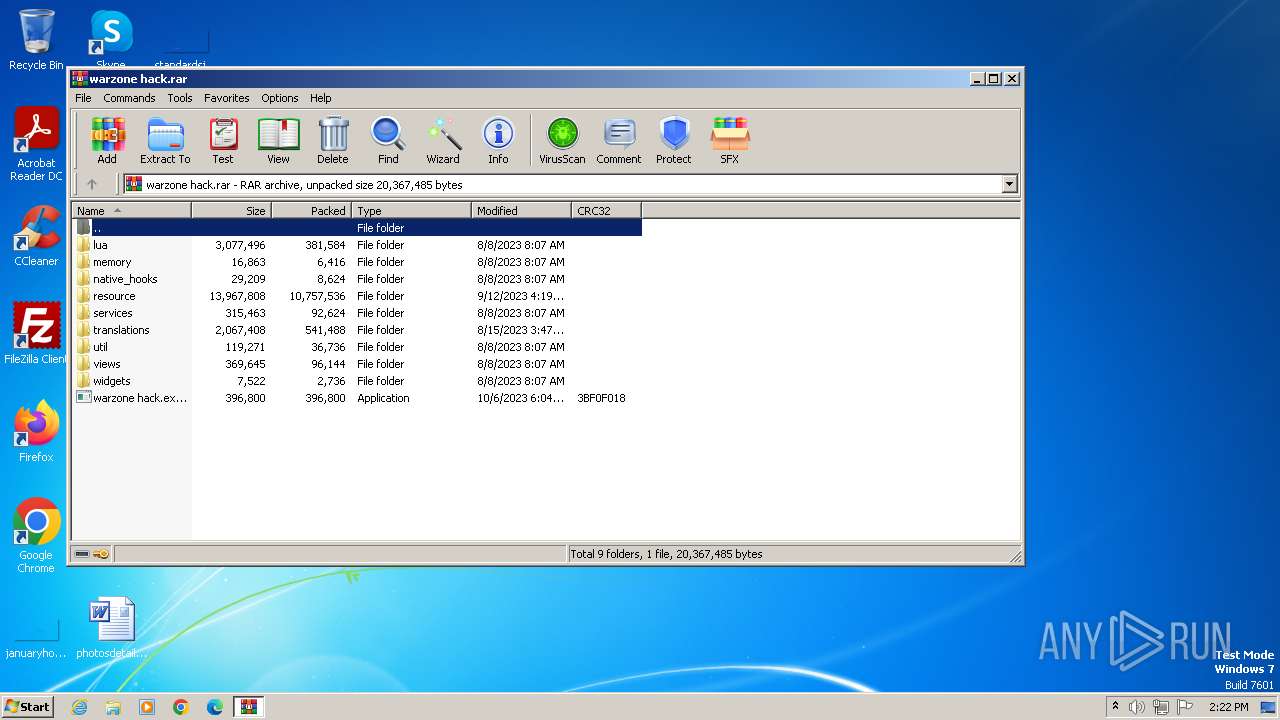
| File name: | warzone hack.rar |
| Full analysis: | https://app.any.run/tasks/02c7a98b-465d-4b9a-9f1b-1e6d754a409c |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | October 18, 2023, 13:22:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 33A32E82F674B5AD687F48496C8EEF30 |
| SHA1: | 610E773B64600790391161403AF79326B313B1CA |
| SHA256: | 95F8DD2B16AD7A747AA99EDF39DF5C929D5EB13FBD996AF5E32B3A8E03FA547E |
| SSDEEP: | 98304:5+QHjtJw3tMD9n5x53KuPe+oIipH1BQBE18teaBhMYo6rZmV+YN1jVSSYW9YmHOz:AVph0gxupJxh8F+kHg9V/GPwT |
MALICIOUS
Connects to the CnC server
- warzone hack.exe (PID: 120)
Application was dropped or rewritten from another process
- warzone hack.exe (PID: 120)
REDLINE was detected
- warzone hack.exe (PID: 120)
Steals credentials from Web Browsers
- warzone hack.exe (PID: 120)
Actions looks like stealing of personal data
- warzone hack.exe (PID: 120)
SUSPICIOUS
Connects to unusual port
- warzone hack.exe (PID: 120)
Searches for installed software
- warzone hack.exe (PID: 120)
Reads browser cookies
- warzone hack.exe (PID: 120)
INFO
Checks supported languages
- warzone hack.exe (PID: 120)
Manual execution by a user
- warzone hack.exe (PID: 120)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2752)
Reads the machine GUID from the registry
- warzone hack.exe (PID: 120)
Reads product name
- warzone hack.exe (PID: 120)
Reads Environment values
- warzone hack.exe (PID: 120)
Reads the computer name
- warzone hack.exe (PID: 120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\warzone hack.exe" | C:\Users\admin\Desktop\warzone hack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2056 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\warzone hack.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 106
Read events
3 082
Write events
24
Delete events
0
Modification events
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
15
Text files
435
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\warzone hack.exe | executable | |
MD5:3AFCD4C06C5CB6C4814962A1FE325F62 | SHA256:02531B3E37C59DF6AFCC6978CA9E09FCDDCAAB956D721EF88E29D6CD5DFEA163 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\event.cpp | text | |
MD5:7A2CAE5CEDA97114650BD88023589623 | SHA256:68DD946934E34DA6D2CB224A6CB78B6B59BFBB760799CF8124638BED049B3FE4 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\gui\base_text_element.cpp | text | |
MD5:6C02598EB8BF67044F32C9FD0F574A4B | SHA256:C7A2BCDC16724E5B90DFB6B247F1BB6C455F7399705509CED3516F2DD2EEDD9F | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\globals.hpp | text | |
MD5:63D00687D9DDC56A1B6640710CD05988 | SHA256:AB8BD76EFD6D05271D6F63C99FC70F8F840D75E518999723E933C28AC8ECA00C | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\gui\gui_element.hpp | text | |
MD5:161629B1501ECAD3A944CEDB75B71FD4 | SHA256:77FF35F47A194E6BEC96FEA0A1256A30CA307DD5B7B157E530C0179F412B8F8E | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\license.key | text | |
MD5:47C843DAF66FAB1990544A441D430E98 | SHA256:B96A19F8B0A68F67282A2FBF06F1B35EB745B1A4CDCC0D70A1FCA9BED0EE7947 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\entities.cpp | text | |
MD5:C9ECB47F9A7773B24A62052B38A47B7C | SHA256:9307F9052AB145C12568C162B9065DF14AA3302A48A77AB82A732756C9622BD4 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\command.hpp | text | |
MD5:A61E6D15FA5E0D6F559F46B880B6C90A | SHA256:D8254A35D34A8DD24AAF4AE5FF1728D792B6619E94A9E5232ADA0E2016837091 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\entities.hpp | text | |
MD5:8C88370C93D7CA395172231811CFF9AD | SHA256:763D875BB0BEBF33FF8C610337096A4BAA9143983B994A534D009AB580CB83C7 | |||
| 2752 | WinRAR.exe | C:\Users\admin\Desktop\resource\lua\bindings\command.cpp | text | |
MD5:42198E1DAC04A824203BAF1CD6F9ACD6 | SHA256:66842410E10B9B2A00C245E98FEBF9D34D8987C74B015E3ABACB3906A8E01024 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
120 | warzone hack.exe | 91.103.252.3:23000 | — | Hostglobal.plus Ltd | GB | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
120 | warzone hack.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
120 | warzone hack.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization) |
120 | warzone hack.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Outbound) |
120 | warzone hack.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Outbound) |
120 | warzone hack.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Outbound) |
120 | warzone hack.exe | A Network Trojan was detected | ET MALWARE Redline Stealer Activity (Response) |
120 | warzone hack.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |
120 | warzone hack.exe | Successful Credential Theft Detected | SUSPICIOUS [ANY.RUN] Clear Text Password Exfiltration Atempt |