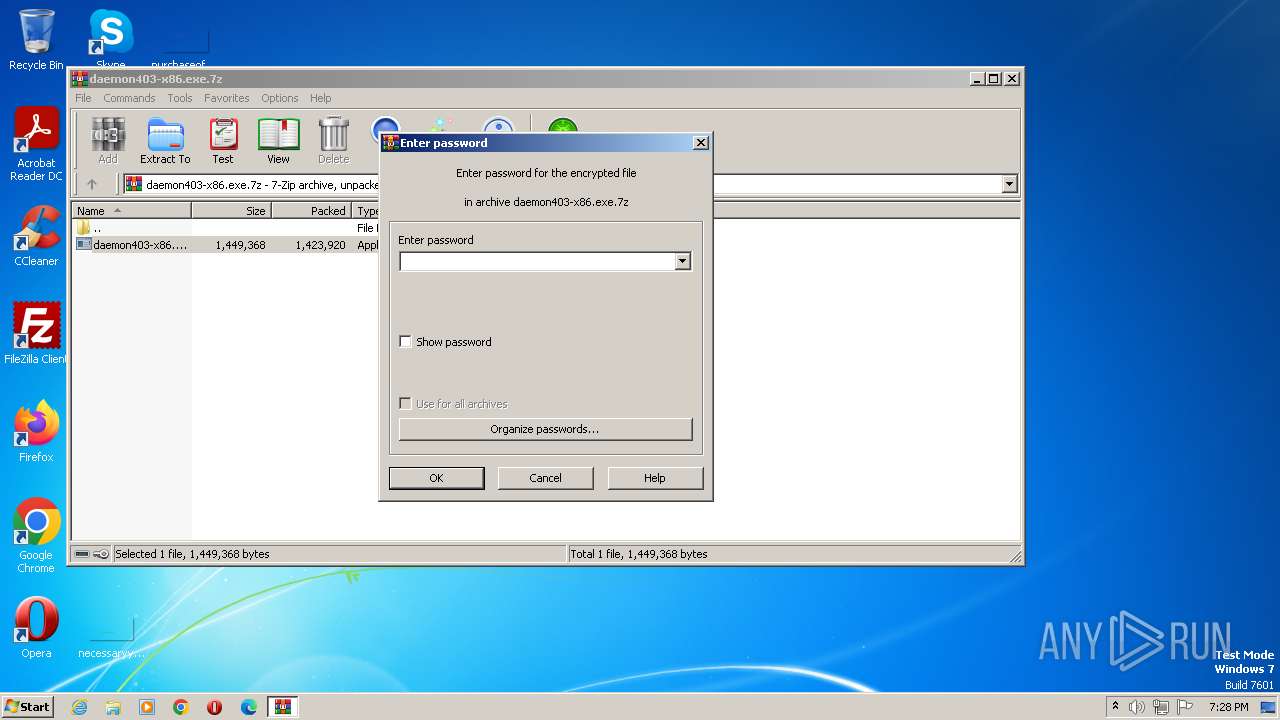
| File name: | daemon403-x86.exe.7z |
| Full analysis: | https://app.any.run/tasks/952a49f0-d3e0-4223-af34-1a2604d0a1a3 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 04, 2023, 18:27:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 096766BD67680F9B32CC2EFB23234984 |
| SHA1: | 3E5B1A4DFAF63E415BA3E2228F03B08DD287FDF5 |
| SHA256: | 95C027AAEA03D3902A577605386C30397EFF78AB9F51176C9A69EF40B92AB3F7 |
| SSDEEP: | 24576:ztBipMZDbRJdKznDj9YpS638yGTf643O95izGjAhxCiXZBaU:zYMZDbRrKzDjupSWJcg5izGjujCU |
MALICIOUS
Application was dropped or rewritten from another process
- daemon403-x86.exe (PID: 2352)
- daemon403-x86.exe (PID: 3180)
LUMMA detected by memory dumps
- daemon403-x86.exe (PID: 2352)
SUSPICIOUS
No suspicious indicators.INFO
The process checks LSA protection
- pcaui.exe (PID: 3812)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1000)
Manual execution by a user
- daemon403-x86.exe (PID: 3180)
- daemon403-x86.exe (PID: 2352)
Creates files in the program directory
- pcaui.exe (PID: 3812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1000 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\daemon403-x86.exe.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2352 | "C:\Users\admin\Desktop\daemon403-x86.exe" | C:\Users\admin\Desktop\daemon403-x86.exe | explorer.exe | ||||||||||||
User: admin Company: DT Soft Ltd. Integrity Level: HIGH Description: DAEMON Tools Setup Exit code: 0 Version: 4.03.0.0 Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\Desktop\daemon403-x86.exe" | C:\Users\admin\Desktop\daemon403-x86.exe | — | explorer.exe | |||||||||||
User: admin Company: DT Soft Ltd. Integrity Level: MEDIUM Description: DAEMON Tools Setup Exit code: 3221226540 Version: 4.03.0.0 Modules
| |||||||||||||||
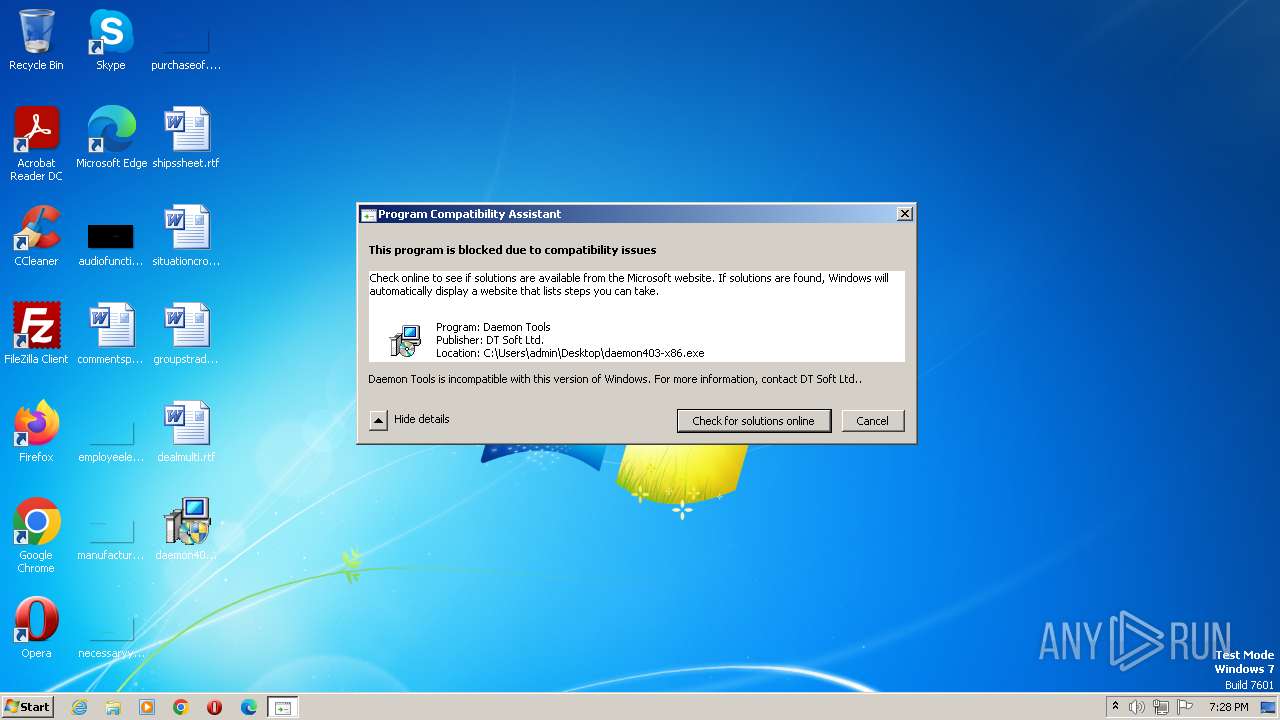
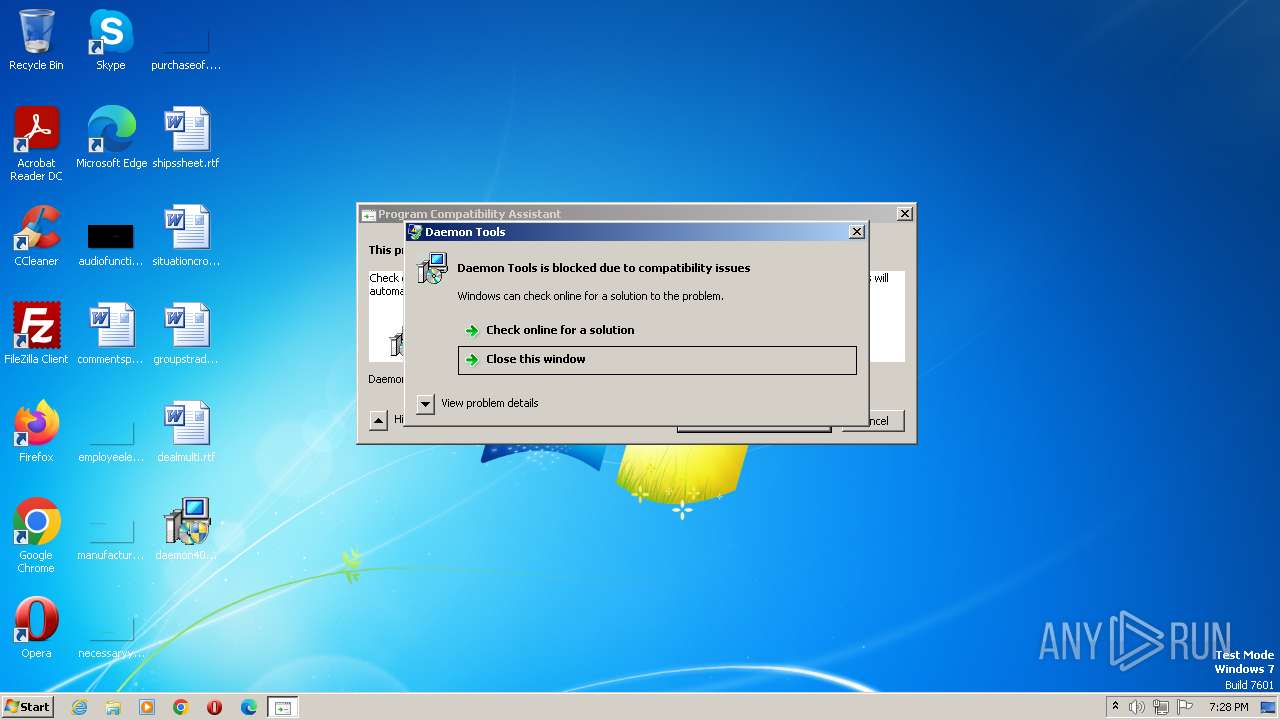
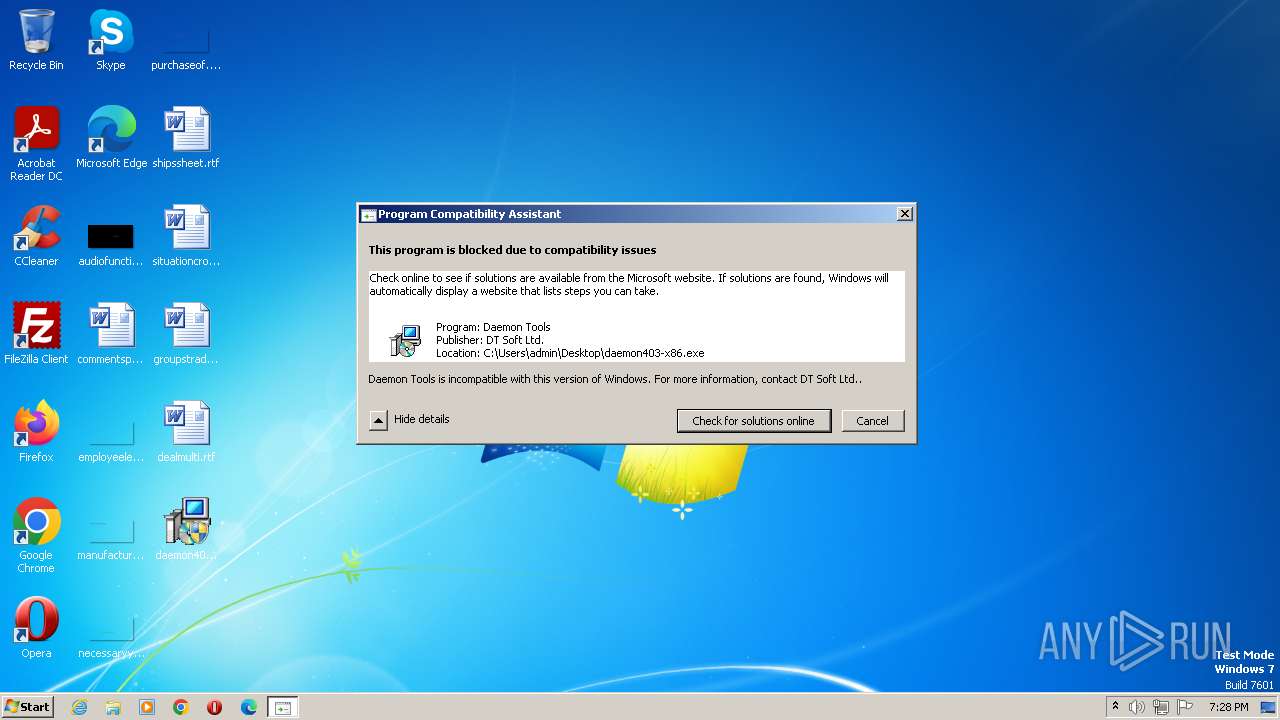
| 3812 | "C:\Windows\System32\pcaui.exe" /g {11111111-1111-1111-1111-111111111111} /x {d4e0cd3e-d8b2-4435-b9cd-bdd575512eee} /a "Daemon Tools" /v "DT Soft Ltd." /s "Daemon Tools is incompatible with this version of Windows. For more information, contact DT Soft Ltd.." /b 2 /e "C:\Users\admin\Desktop\daemon403-x86.exe" | C:\Windows\System32\pcaui.exe | — | daemon403-x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Program Compatibility Assistant User Interface Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 064
Read events
1 044
Write events
20
Delete events
0
Modification events
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3812 | pcaui.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\Critical_{11111111-1111-1_7bc61c71355e6e6751a77569baa343a7a3ea7eef_0ea31747\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1000 | WinRAR.exe | C:\Users\admin\Desktop\daemon403-x86.exe | executable | |
MD5:A3A9825B6D7A9400C8286CD09B5F1B0B | SHA256:D18C4AD4457A319649D5F860ED50D7405C3E6E8399A769AF3BF9E529C2051129 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |