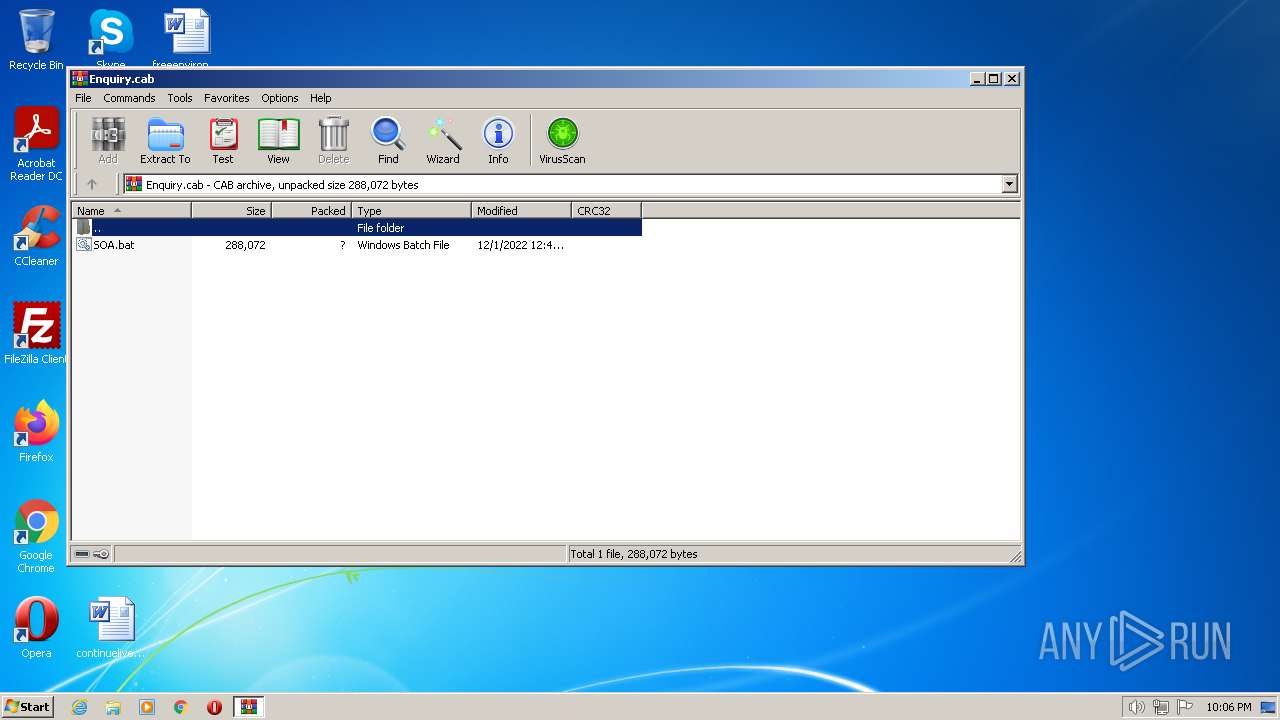
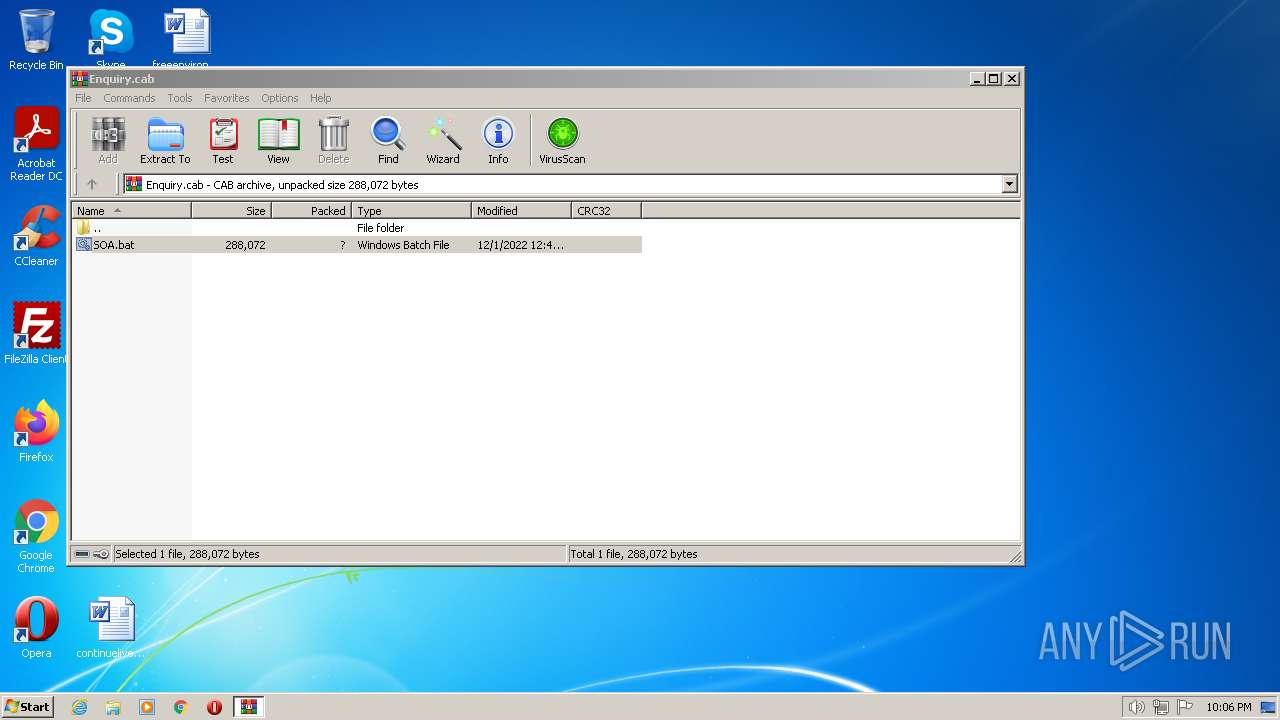
| File name: | Enquiry.cab |
| Full analysis: | https://app.any.run/tasks/fd7b053f-e405-4b17-8f80-a4f4db2d70d1 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | December 05, 2022, 22:06:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-cab-compressed |
| File info: | Microsoft Cabinet archive data, Windows 2000/XP setup, 258183 bytes, 1 file, at 0x2c +A "SOA.bat", number 1, 9 datablocks, 0x1 compression |
| MD5: | 1C833D911D5CB9CE3EF3A72DEDC45F6F |
| SHA1: | 37D84B0A0EC351CE5E1DC62BDBB8D7B351F78840 |
| SHA256: | 95A82A3F9F61A638274040FA4B681E7E3EA4102BEA51A186ED9DF934CE133342 |
| SSDEEP: | 6144:YMMd7RAt50jar3EfxJT5pZuXKCbjAxgpNGUJ:wdtAtkar3Efz+K7+NNJ |
MALICIOUS
GULOADER detected by memory dumps
- SOA.bat (PID: 2976)
- SOA.bat (PID: 2680)
Drops the executable file immediately after the start
- SOA.bat (PID: 2680)
- SOA.bat (PID: 2976)
Loads dropped or rewritten executable
- SOA.bat (PID: 2976)
- SearchProtocolHost.exe (PID: 2708)
- SOA.bat (PID: 2680)
Application was dropped or rewritten from another process
- SOA.bat (PID: 2976)
- SOA.bat (PID: 2680)
SUSPICIOUS
Executable content was dropped or overwritten
- SOA.bat (PID: 2976)
- SOA.bat (PID: 2680)
INFO
Drops a file that was compiled in debug mode
- SOA.bat (PID: 2976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .cab | | | Microsoft Cabinet Archive (100) |
|---|
Total processes
35
Monitored processes
4
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1580 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Enquiry.cab" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2680 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa1580.1830\SOA.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa1580.1830\SOA.bat | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2708 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa1580.46589\SOA.bat" | C:\Users\admin\AppData\Local\Temp\Rar$DIa1580.46589\SOA.bat | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 089
Read events
3 065
Write events
24
Delete events
0
Modification events
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Enquiry.cab | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | SOA.bat | C:\Users\admin\Nyskabendes\Tackle\Bonkammerats\iso_3166-1.xml | xml | |
MD5:— | SHA256:— | |||
| 1580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1580.1830\SOA.bat | executable | |
MD5:— | SHA256:— | |||
| 2976 | SOA.bat | C:\Users\admin\Nyskabendes\Tackle\Bonkammerats\System.Diagnostics.Tracing.dll | executable | |
MD5:4F35A5767A99C38F10A4EF1E47F07B05 | SHA256:6CCC5E59612B7B67A78F47F43F08C2BA6B094C2EA31CE9DE3FEE4197E7E438C6 | |||
| 1580 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1580.46589\SOA.bat | executable | |
MD5:— | SHA256:— | |||
| 2976 | SOA.bat | C:\Users\admin\Nyskabendes\Tackle\Bonkammerats\Bldagtiges\kassemangels\up_arrow_disabled.png | image | |
MD5:C211E38348FFE75121DA35BC5E66085E | SHA256:3C03E89D0717A94A1C98A57E15E53860D5C586151E4AE2F2D97F48892EF8A7AF | |||
| 2976 | SOA.bat | C:\Users\admin\Nyskabendes\Tackle\Bonkammerats\Fads.Dde | binary | |
MD5:— | SHA256:— | |||
| 2680 | SOA.bat | C:\Users\admin\AppData\Local\Temp\nsvD4C7.tmp\System.dll | executable | |
MD5:BE2621A78A13A56CF09E00DD98488360 | SHA256:852047023BA0CAE91C7A43365878613CFB4E64E36FF98C460E113D5088D68EF5 | |||
| 2976 | SOA.bat | C:\Users\admin\AppData\Local\Temp\nsu820.tmp\System.dll | executable | |
MD5:BE2621A78A13A56CF09E00DD98488360 | SHA256:852047023BA0CAE91C7A43365878613CFB4E64E36FF98C460E113D5088D68EF5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report